Patents
Literature
89 results about "Cross-site scripting" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
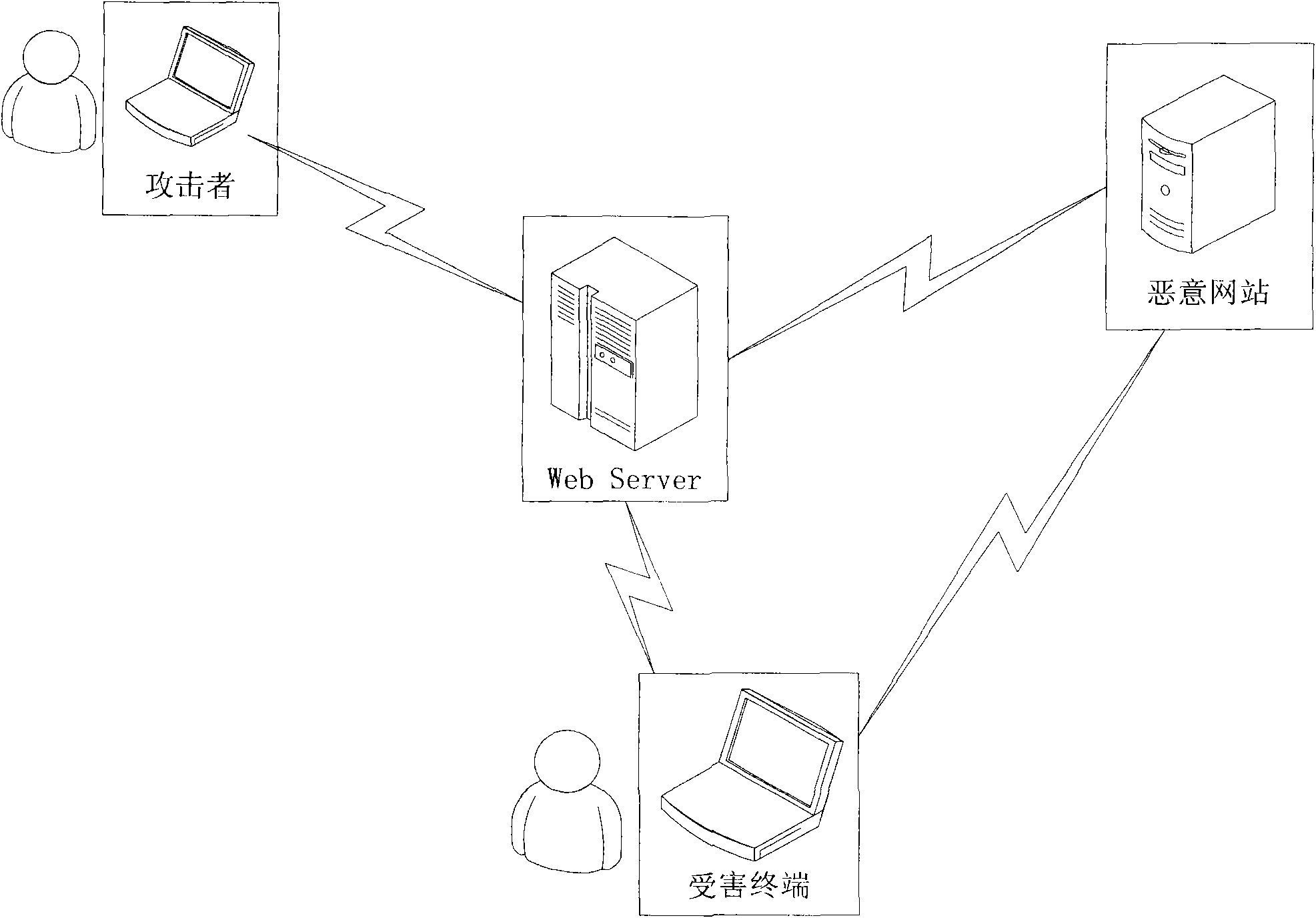
Cross-site scripting (XSS) is a type of computer security vulnerability typically found in web applications. XSS enables attackers to inject client-side scripts into web pages viewed by other users. A cross-site scripting vulnerability may be used by attackers to bypass access controls such as the same-origin policy. Cross-site scripting carried out on websites accounted for roughly 84% of all security vulnerabilities documented by Symantec up until 2007. In 2017, XSS was still considered a major threat vector. XSS effects vary in range from petty nuisance to significant security risk, depending on the sensitivity of the data handled by the vulnerable site and the nature of any security mitigation implemented by the site's owner network.
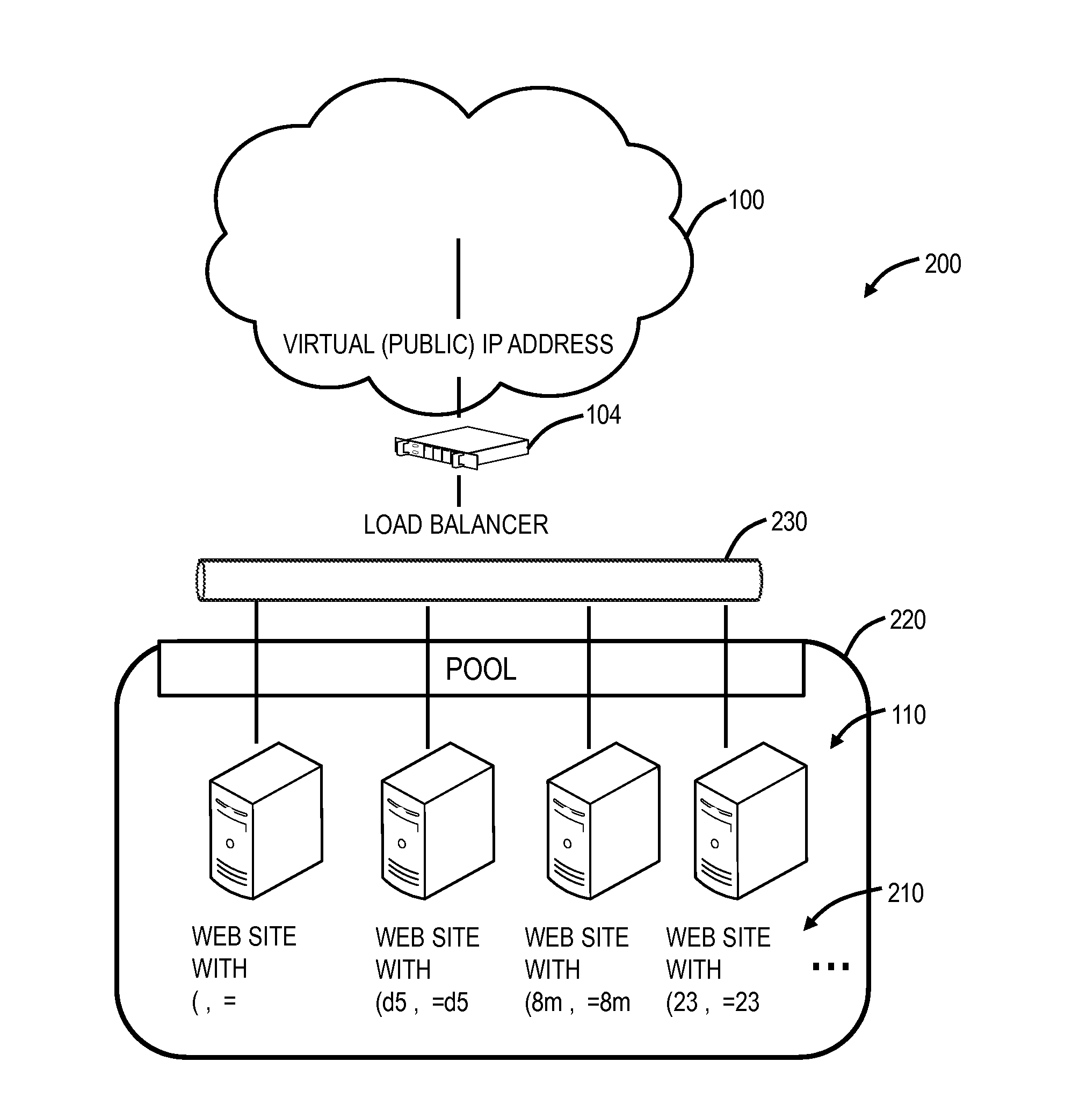
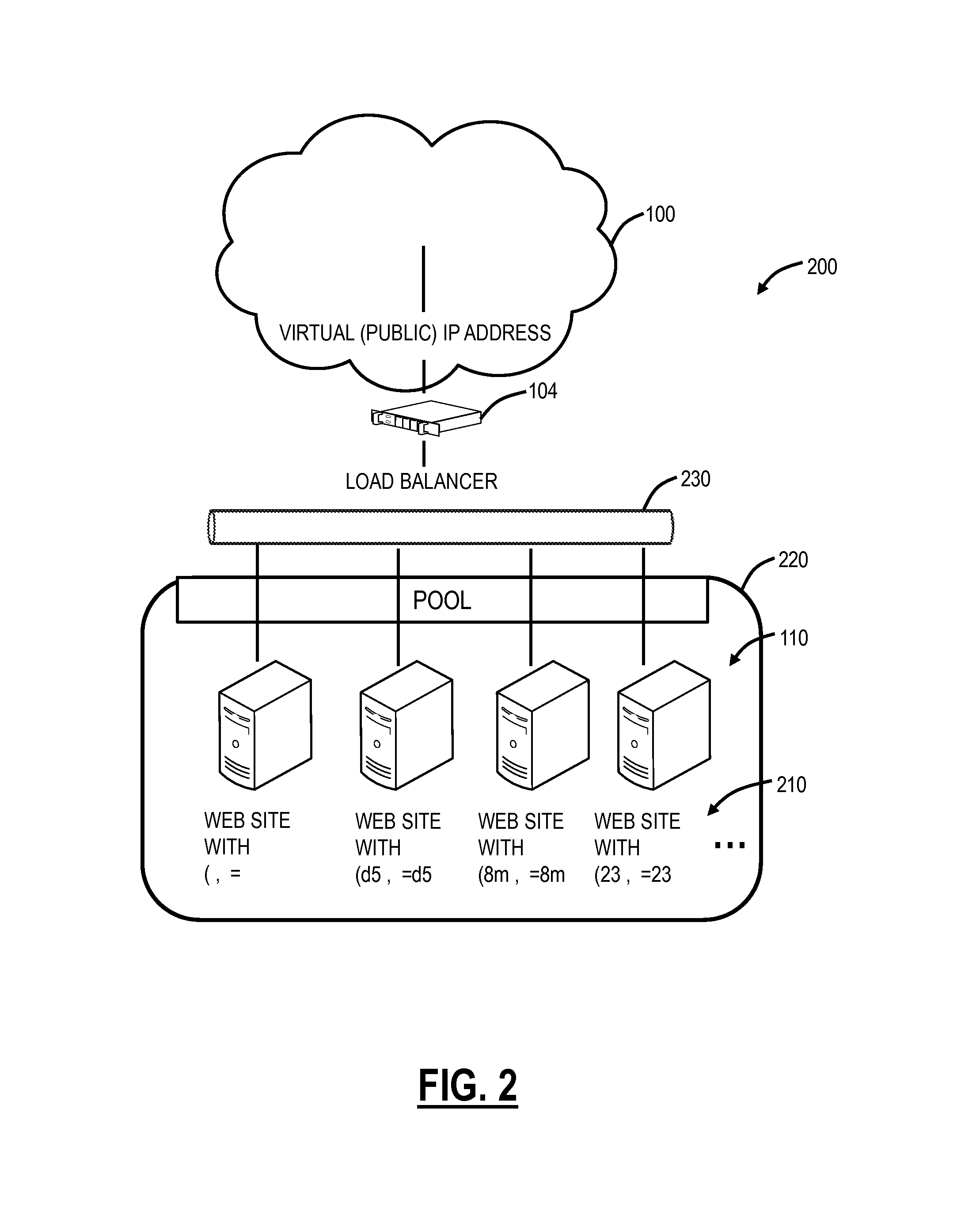
Automated detection of cross site scripting vulnerabilities
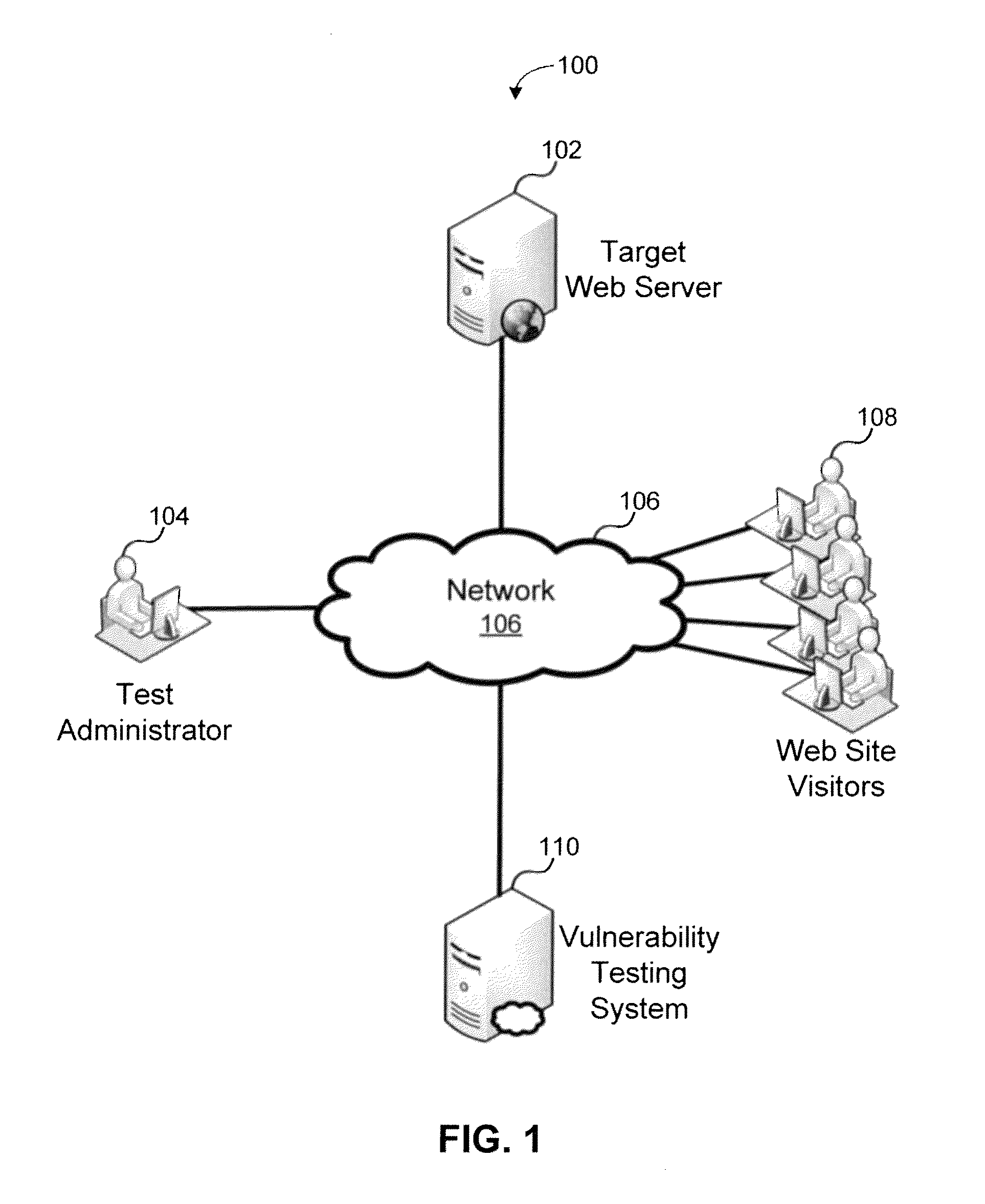
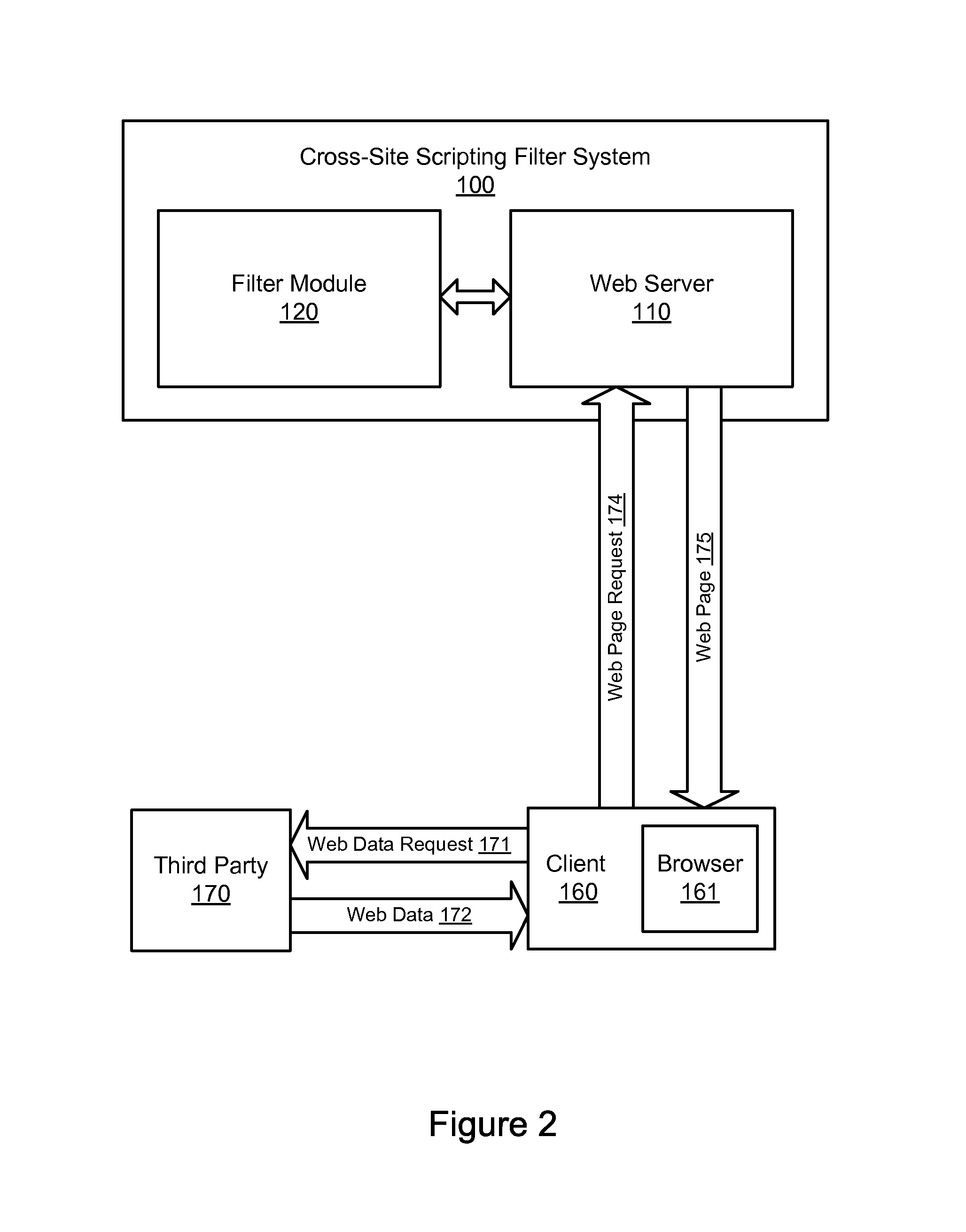
An automated method and system for testing a web site for vulnerability to a cross site scripting (XSS) attack are disclosed. The automated tool injects a tracer value into both GET and POST form data, and monitors the resultant HTML to determine whether the tracer value is returned to the local machine by the server to which it was sent. If the tracer value is returned, the automated tool attempts to exploit the web site by injecting a non-malicious script as part of an input value for some form data, based on the location in the returned HTML in which the returned tracer value was found. If the exploit is successful, as indicated by the non-malicious script, the automated tool logs the exploit to a log file that a user can review at a later time, e.g., to assist in debugging the web site.
Owner:MICROSOFT TECH LICENSING LLC
Systems and methods for client-side vulnerability scanning and detection
InactiveUS8752183B1Avoid hard activationImprove accuracyMemory loss protectionError detection/correctionObfuscationWeb browser
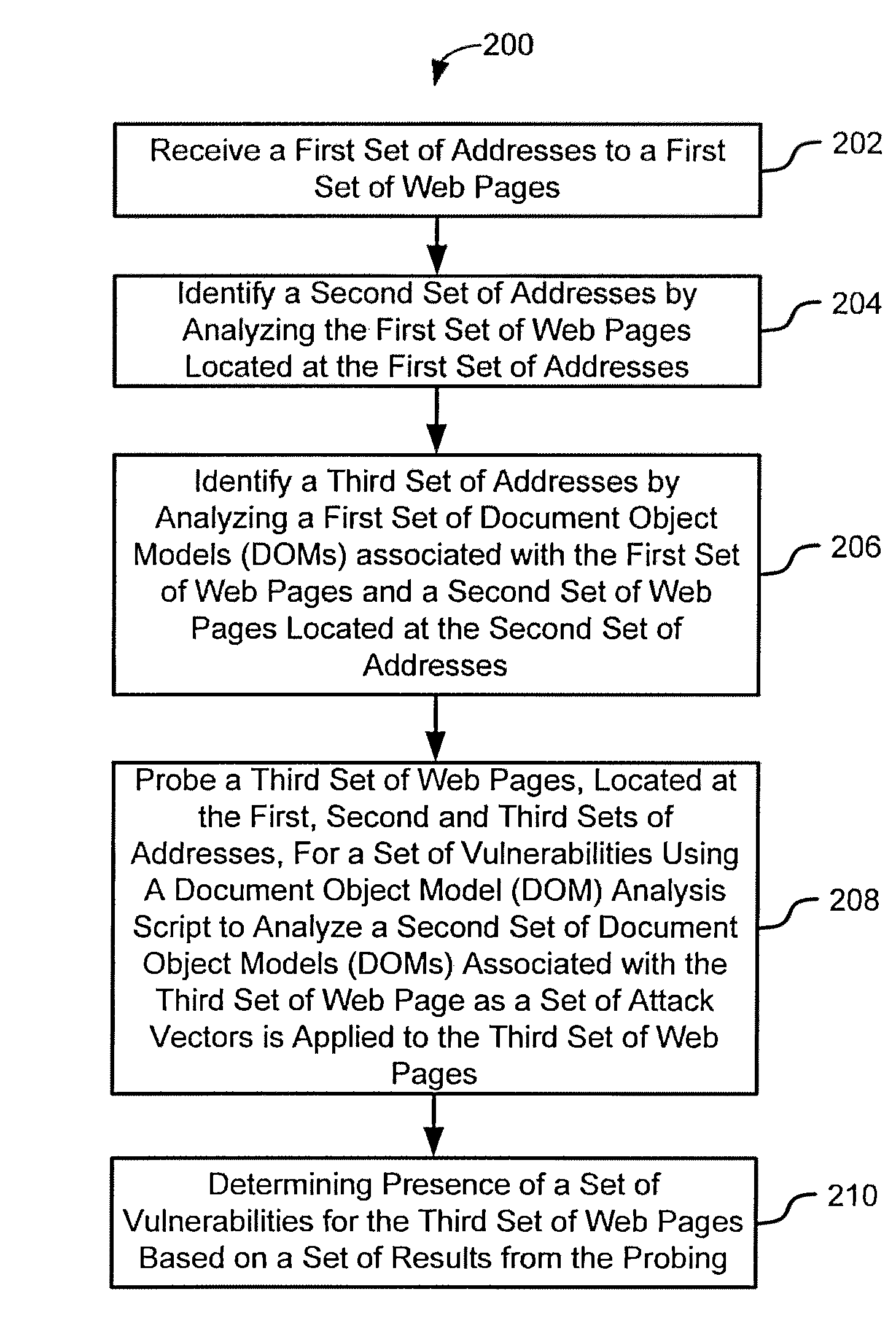
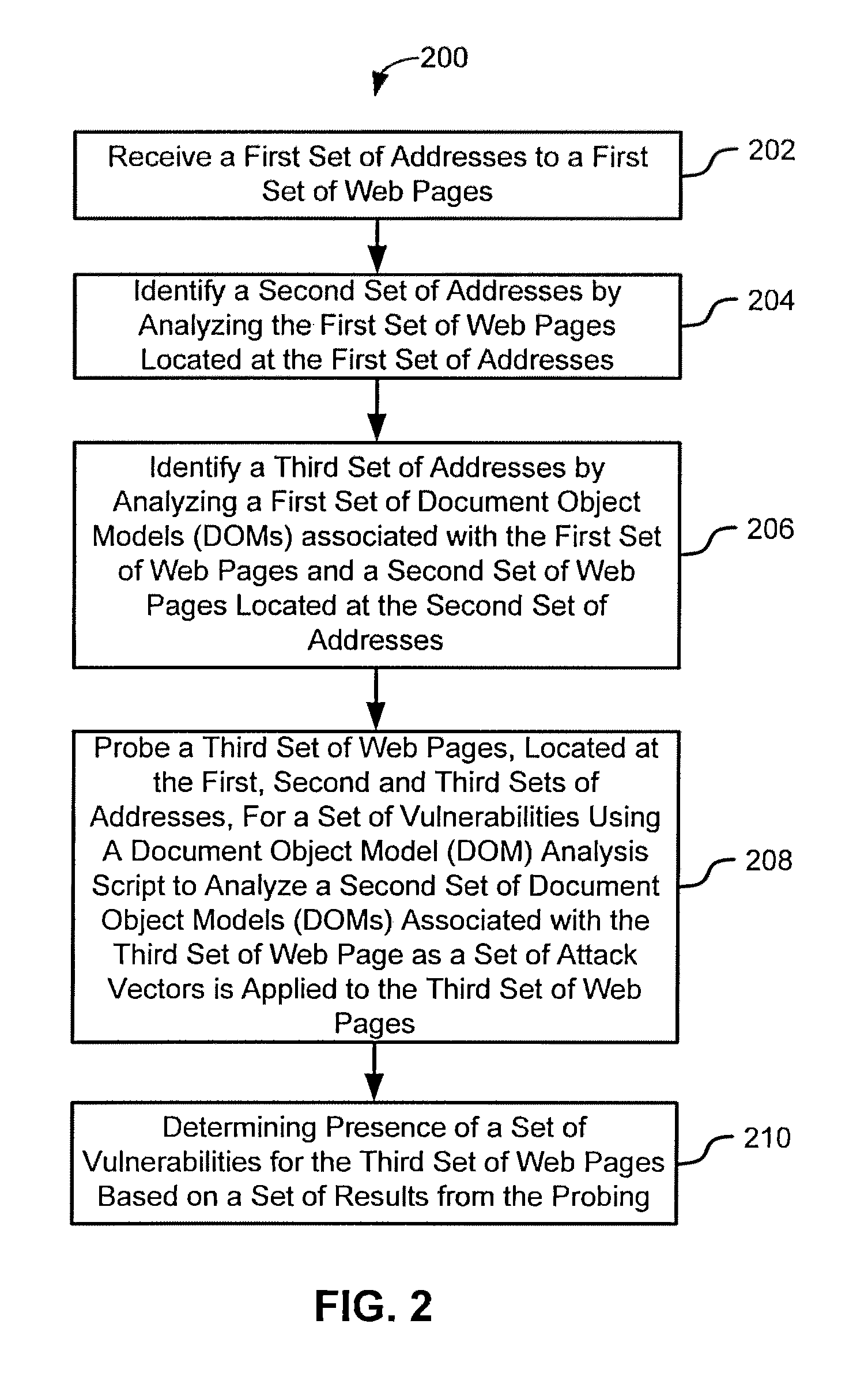
Various embodiments presented herein relate to scanning for and detecting web page vulnerabilities, including cross-site scripting (XSS). Some embodiments are configured to scan for and detect vulnerabilities of a target web page using a client-based approach, which may employ a remotely-controlled web browser application capable of generating a document object model (DOM) for the target web page as it is accessed. Some embodiments may scan for and detect web page vulnerabilities by monitoring the DOM associated with a targeted web page as one or more attack vectors are applied to the target web page. Certain embodiments are capable of detecting web page vulnerabilities independent of the complexity or presence of an event model, or obfuscation of the malicious code (e.g., XSS code). Target web pages that are scanned may include those associated with an application coded in a web browser-supported language, such a Rich Internet Application (RIA).
Owner:HOYT TECH
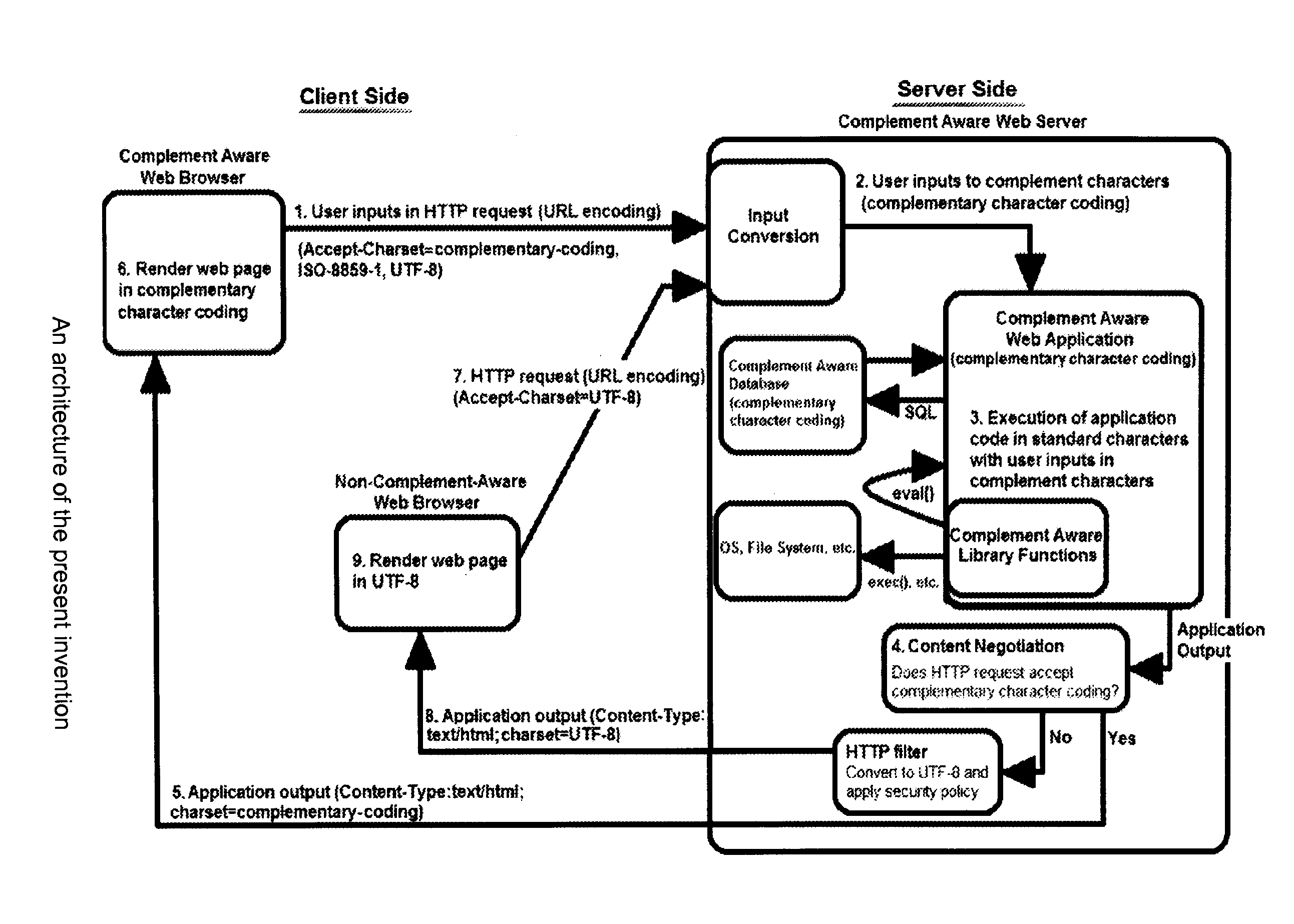
Complementary Character Encoding for Preventing Input Injection in Web Applications
InactiveUS20110252475A1Reduce overheadPreventing executionMemory loss protectionError detection/correctionSQL injectionLexical analysis
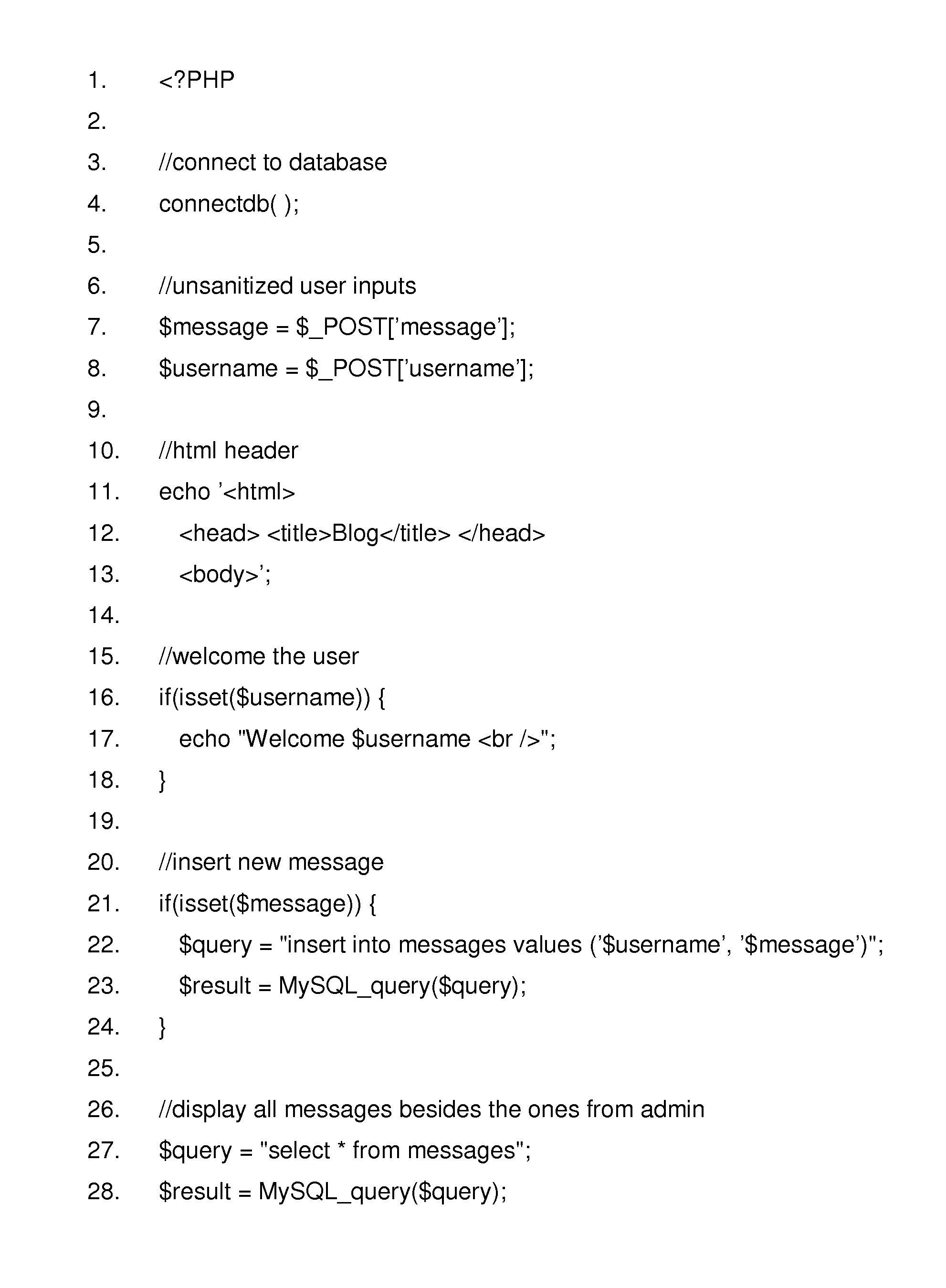
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
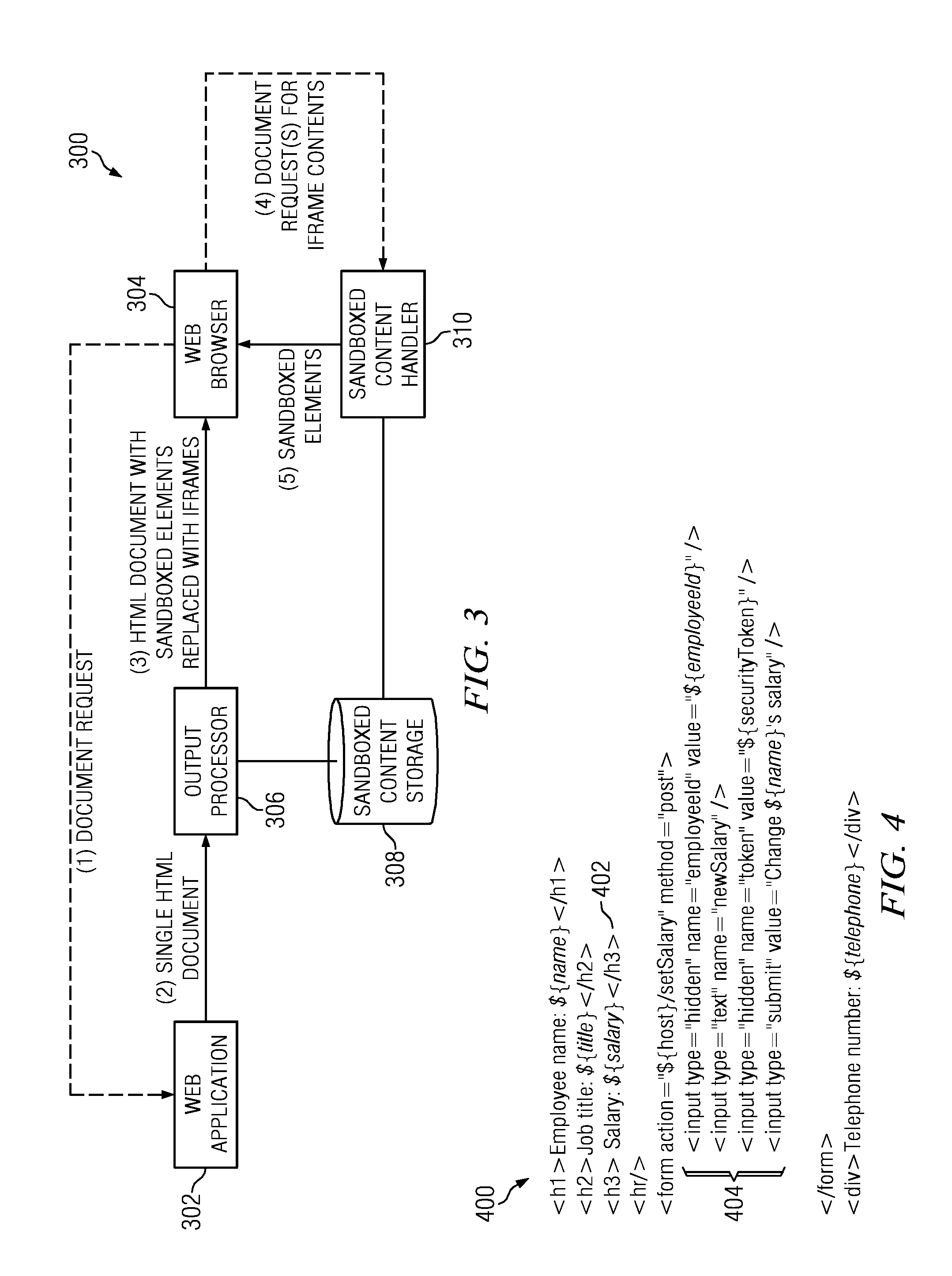
Method and apparatus for serving content elements of a markup language document protected against cross-site scripting attack
ActiveUS8856874B2Protected contentDigital data processing detailsMultiple digital computer combinationsDomain nameWeb application
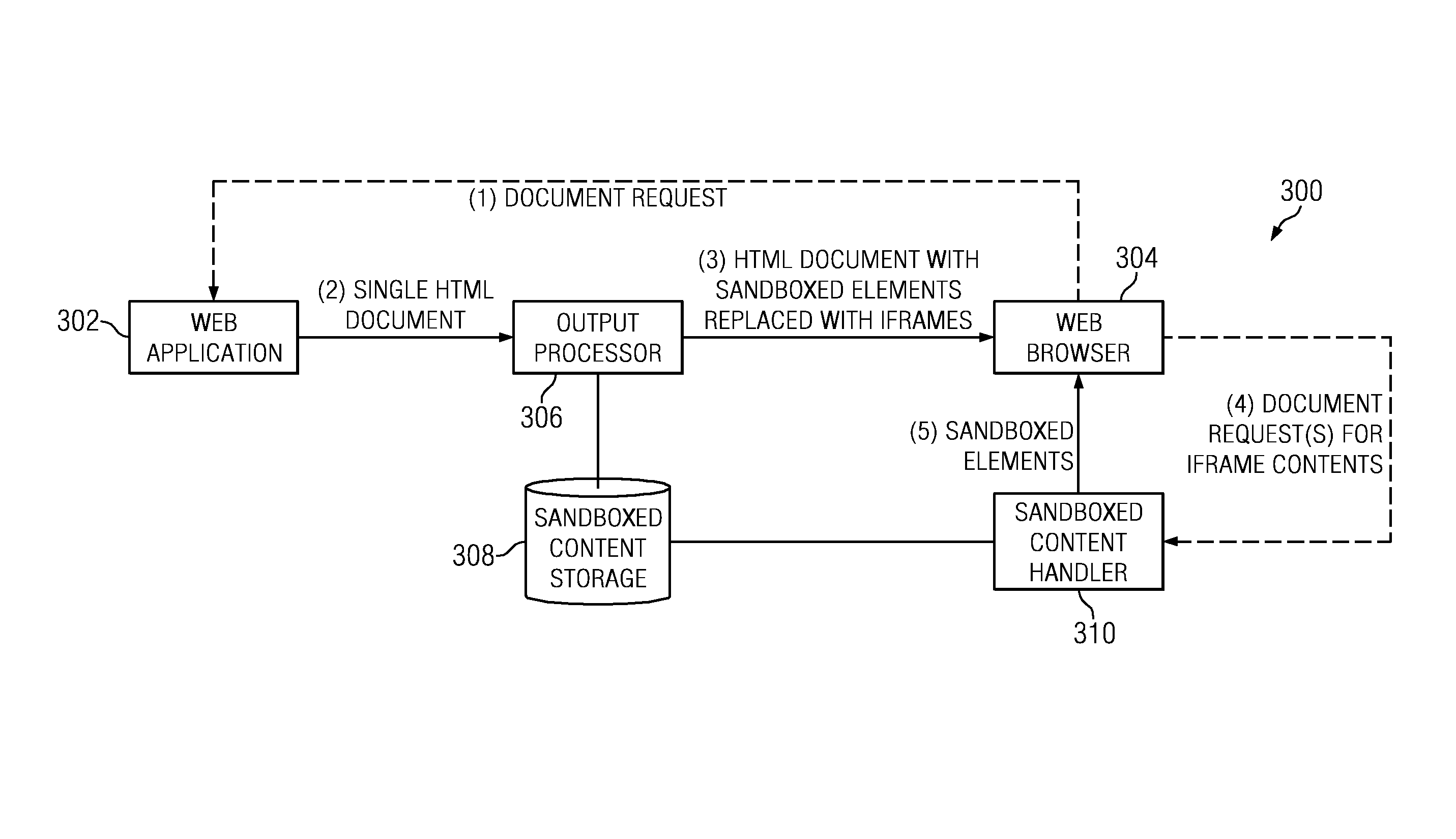
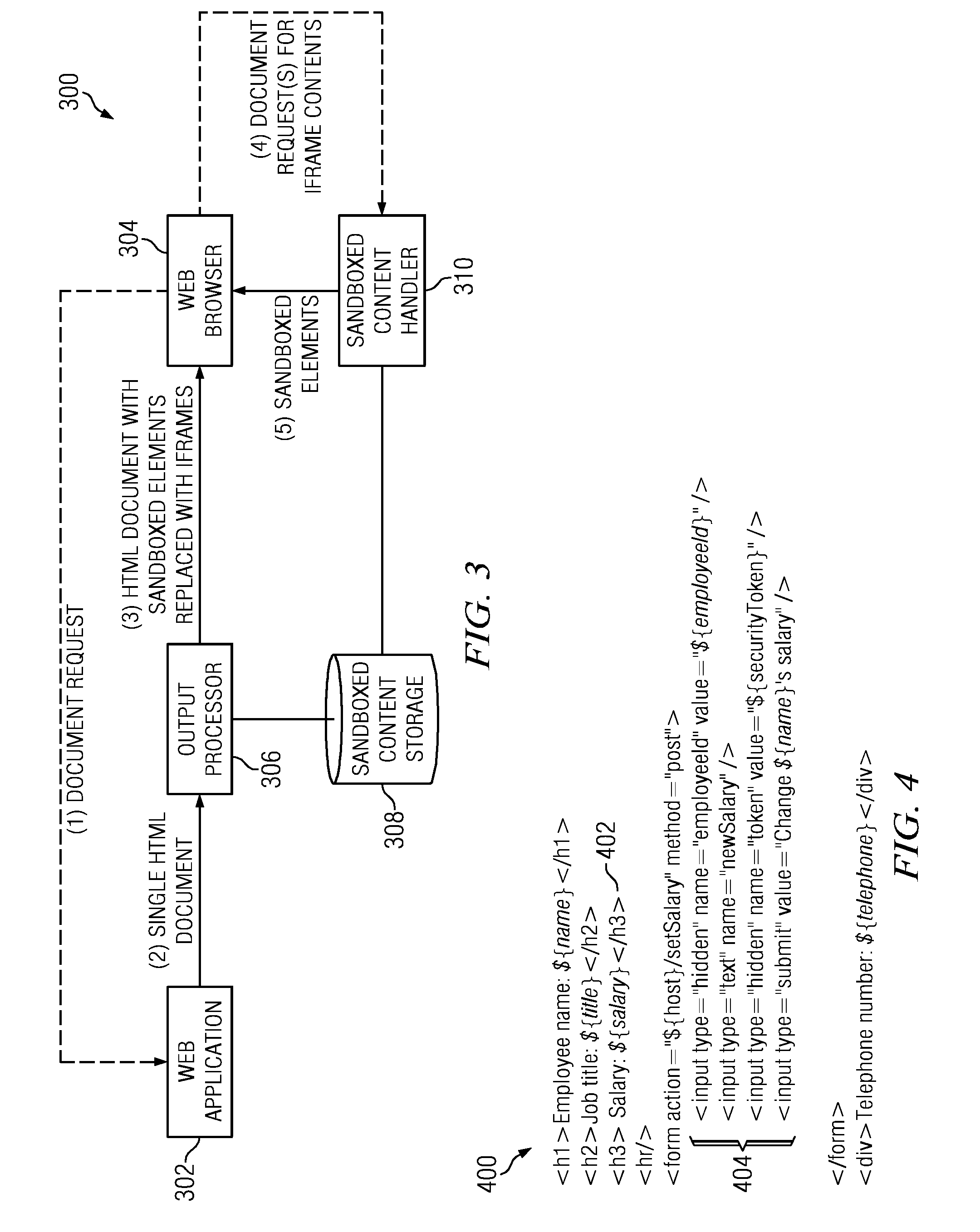
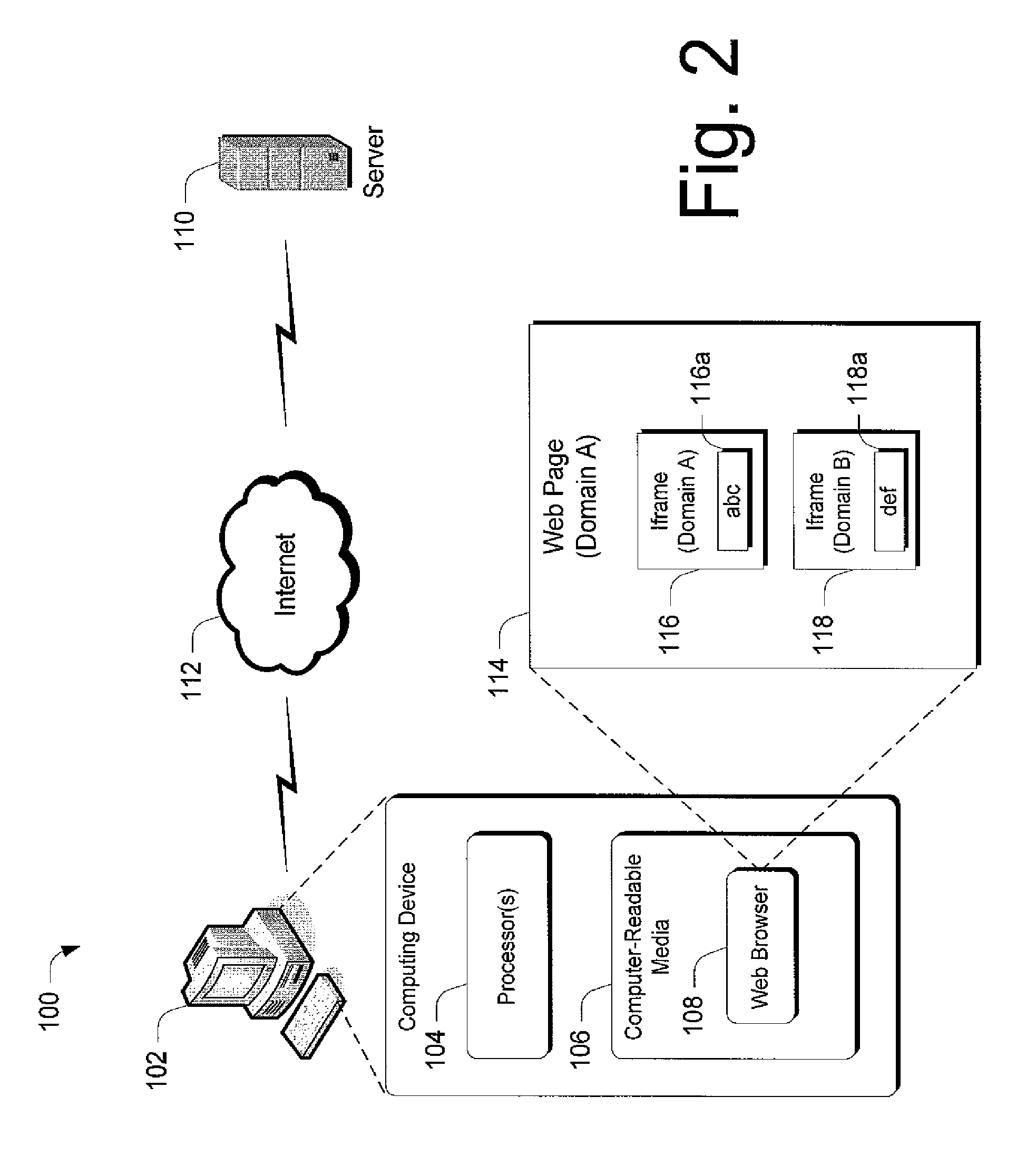
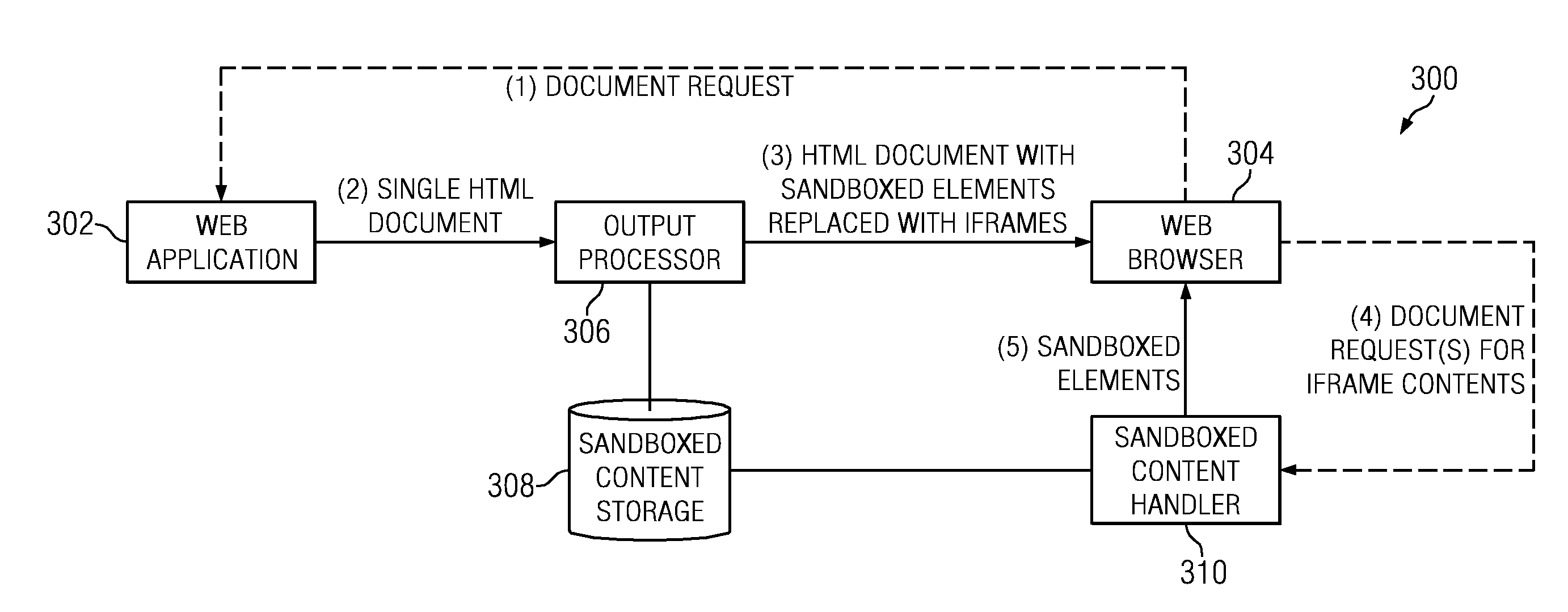
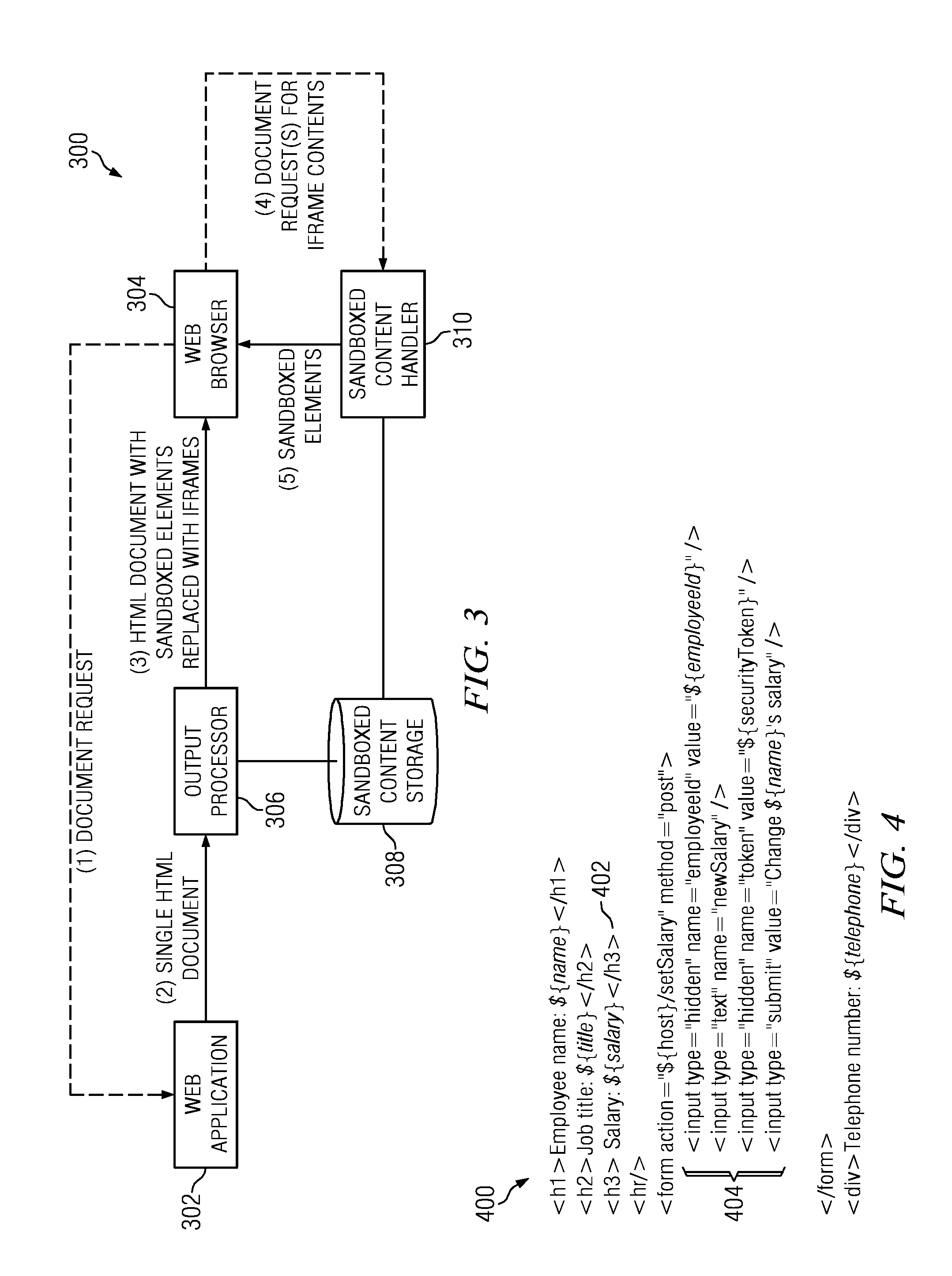
A web application decomposed into one or more domain sandboxes ensures that the contents of each sandbox are protected from attacks on the web application outside that sandbox. Sandboxing is achieved on a per-element basis by identifying content that should be put under protection, generating a secure domain name for the identified content, and replacing the identified content with a unique reference (e.g., an iframe) to the generated secure domain. The identified content is then served only from the generated secure domain using a content handler.
Owner:IBM CORP
Method and apparatus for protecting markup language document against cross-site scripting attack
ActiveUS20110289546A1Protected contentDigital data processing detailsUser identity/authority verificationDomain nameWeb application
A method for decomposing a web application into one or more domain sandboxes ensures that the contents of each sandbox are protected from attacks on the web application outside that sandbox. Sandboxing is achieved on a per-element basis by identifying content that should be put under protection, generating a secure domain name for the identified content, and replacing the identified content with a unique reference (e.g., an iframe) to the generated secure domain. The identified content is then served only from the generated secure domain.
Owner:FINJAN BLUE INC
Method and system for improved internet security via HTTP-only cookies
ActiveUS7359976B2Reduce the amount of damageAvoid damageComputer security arrangementsMultiple digital computer combinationsClient-side scriptingClient-side
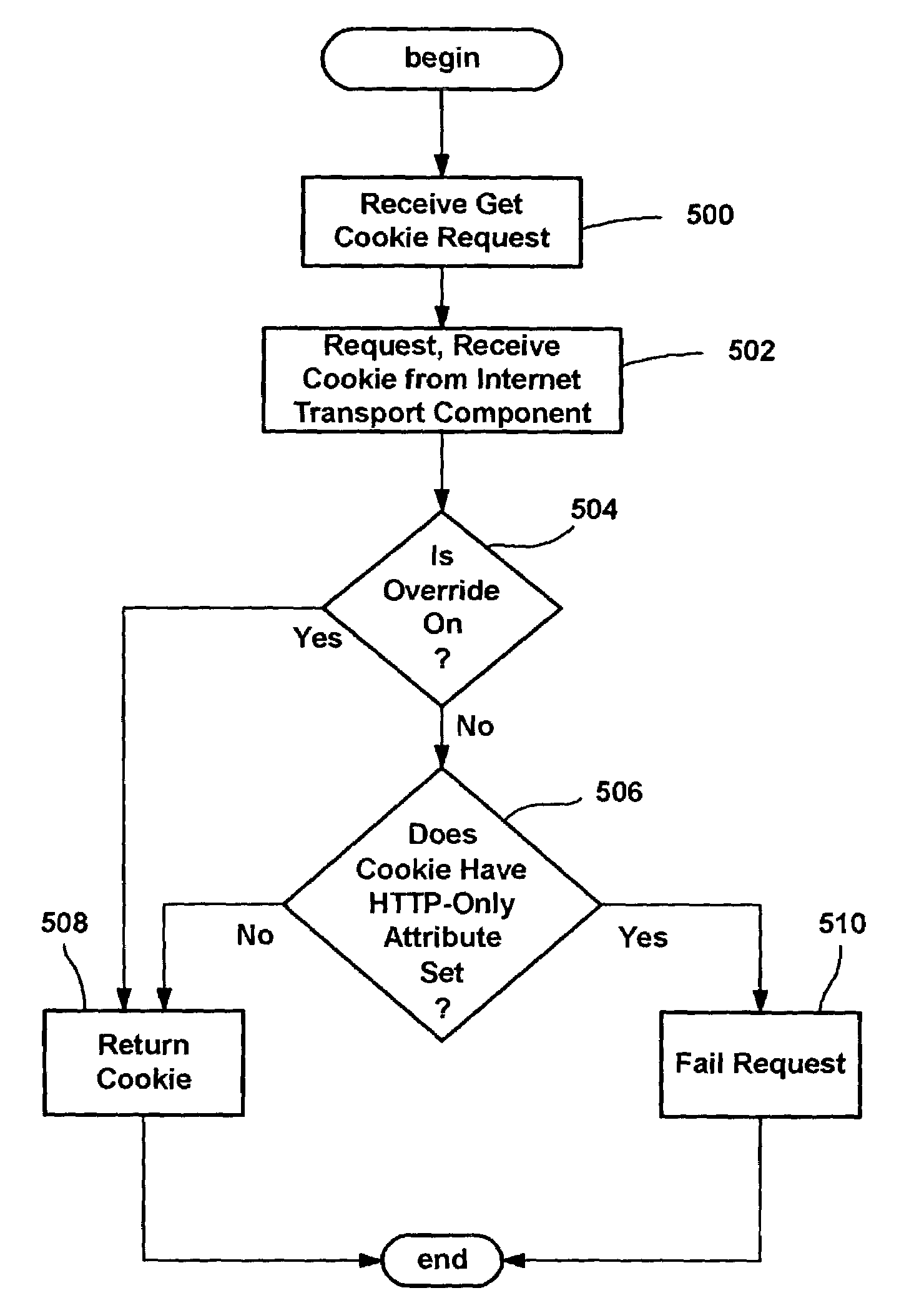
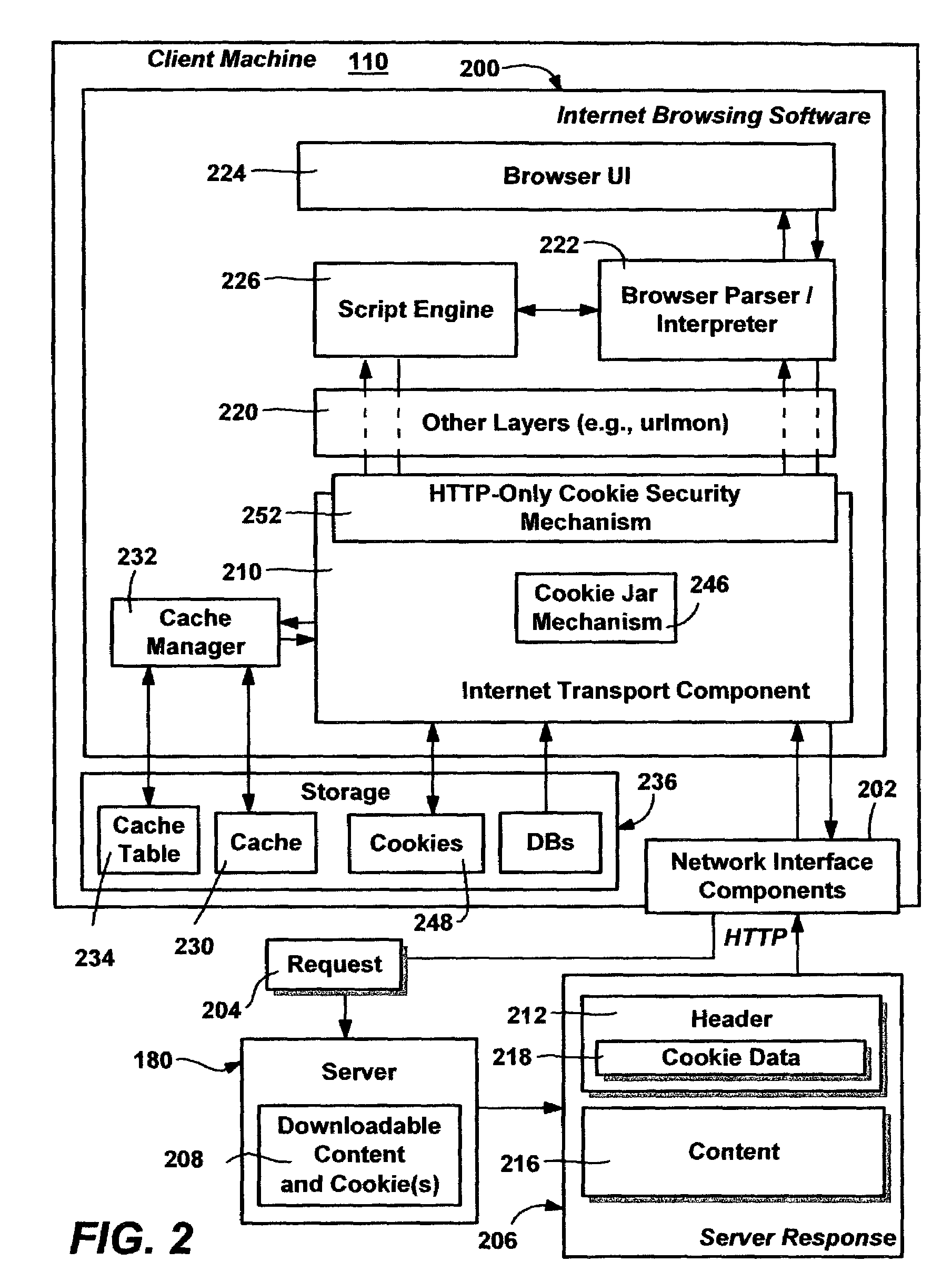
A system and method that prevents certain cookies, as specified by an Internet server, from being accessed through client-side script, thereby mitigating the amount of damage that cross-site scripting attacks can accomplish. The server marks selected cookies with an attribute that flags such cookies as being protected, and a security mechanism in the client prevents protected cookies from being accessed via script. A protected (flagged) cookie can still be accessed by the server, (e.g., via HTTP), while non-flagged cookies can be accessed by the server or script. An API or similar layer implements the security mechanism that checks for the attribute, and fails requests for any cookies having that attribute set. The present invention can also be adapted to prevent a malicious script from overwriting existing HTTP-only cookies on a client machine.
Owner:MICROSOFT TECH LICENSING LLC
Method, system, and computer program product for avoiding cross-site scripting attacks
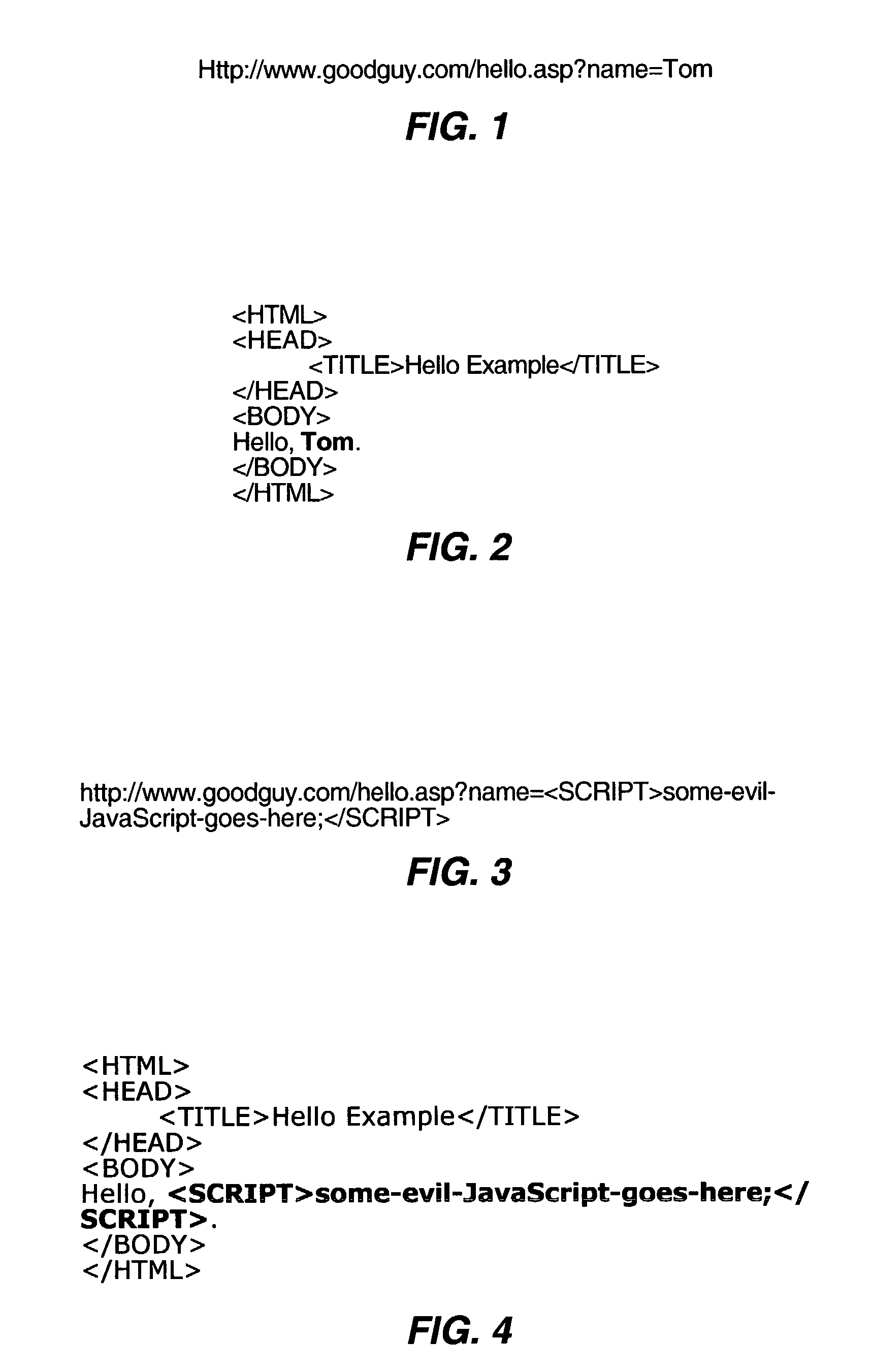
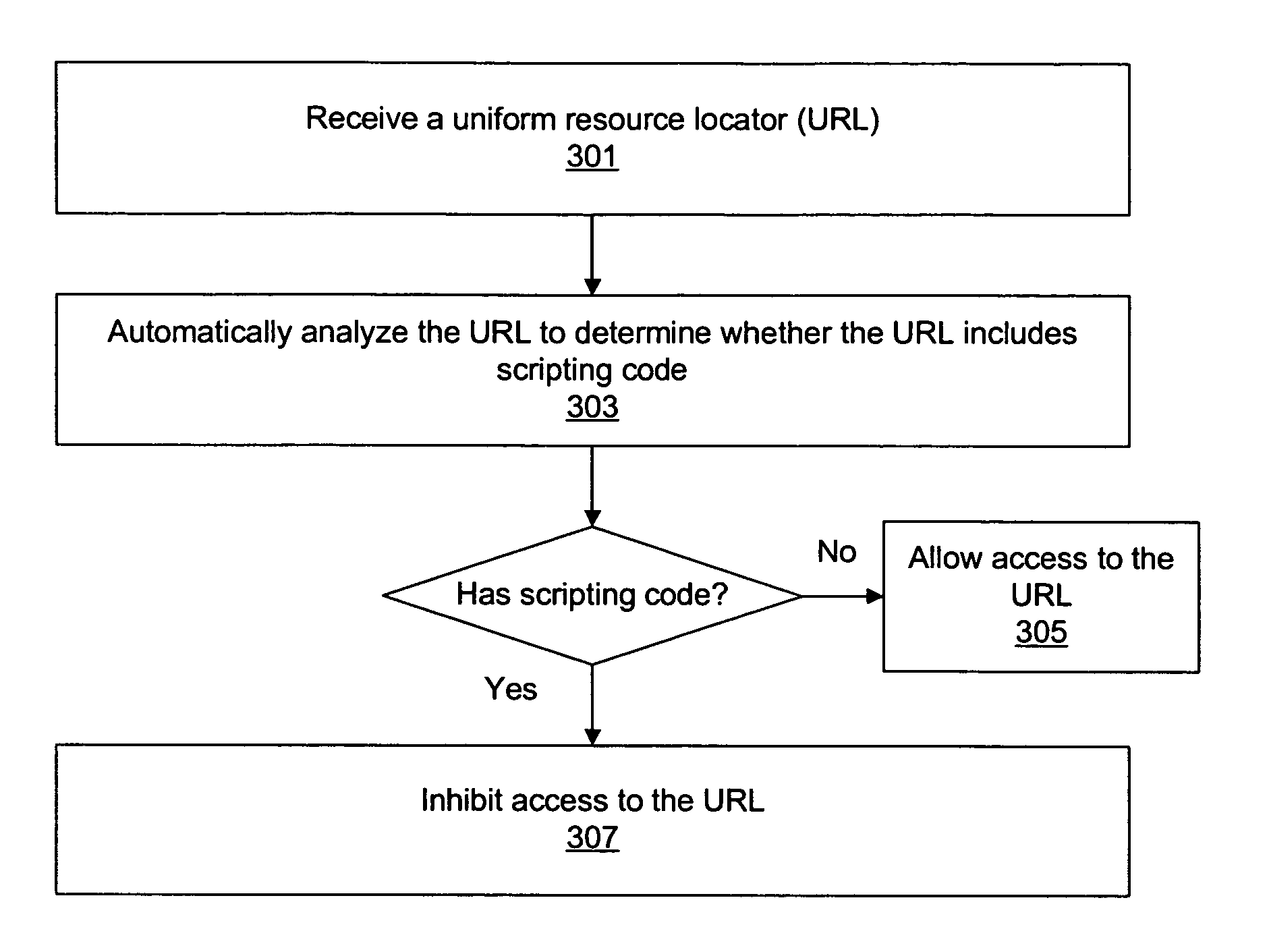
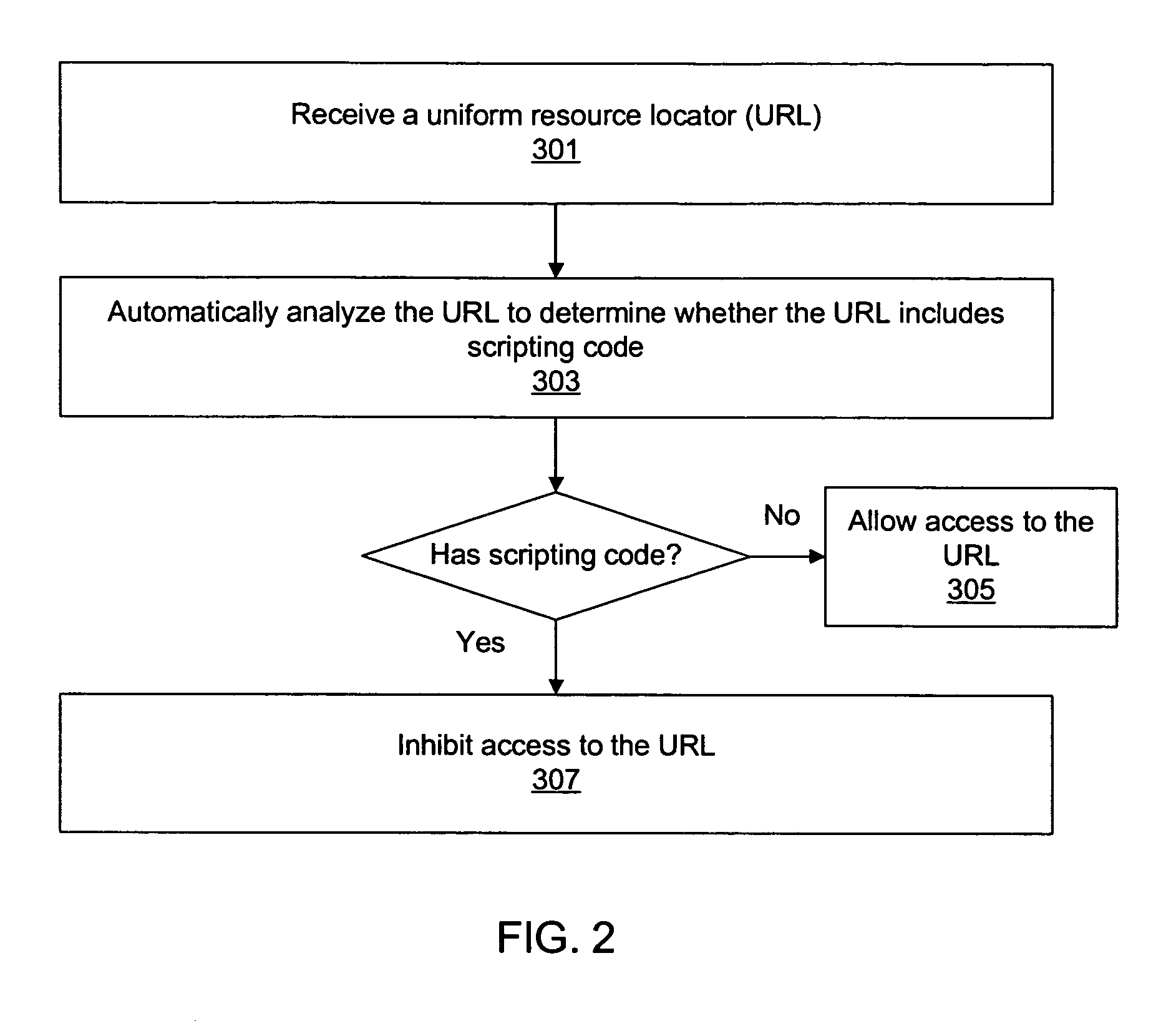
A system and method for protecting a user against a cross-site scripting attack or other network attack that relies on scripting code embedded within a uniform resource locator (URL) are described. Validation software executing on a client computer system may intercept a URL in response to a user providing the URL to a web browser or other client application. The validation software may analyze the URL to determine whether the URL includes scripting code. If the URL includes scripting code then the validation software may block the client application from accessing the URL or may otherwise inhibit access to the URL.
Owner:SYMANTEC CORP
Method and device for detecting cross site scripting
InactiveCN101901221AEfficient and accurate distinctionGuaranteed to passPlatform integrity maintainanceSpecial data processing applicationsNetwork terminationPattern matching
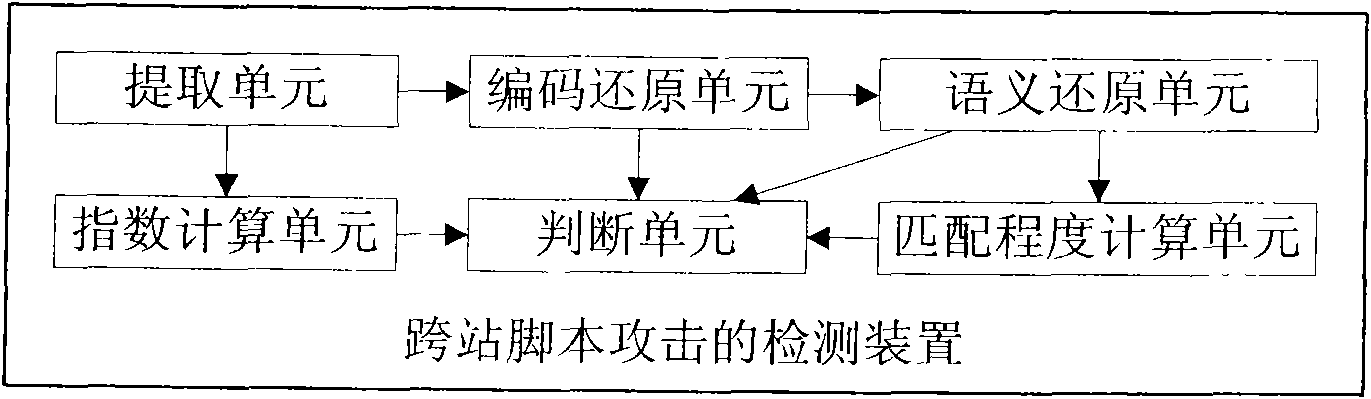
The invention provides a device for detecting cross site scripting. The device comprises an index calculating unit, an extracting unit, a code restoring unit, a semantics restoring unit, a matching degree calculating unit and a judging unit which cooperate with each other; and malicious cross site scripts entrained in a Web page are identified and extracted by a comprehensive HTML label analysis methods (comprising four methods, namely EJSRF analysis, JavaScript code deformation analysis, JavaScript semantics denaturation analysis and XSS attack characteristic mode matching). The cross site script identification and extraction technology taking HTML label analysis as a core can efficiently and accurately distinguish a normal JavaScript from the malicious cross site scripts in the Web page to make network security detection equipment and a network terminal accurately identify and filter the Web page which contains the malicious cross site scripts, and simultaneously guarantee legal Web page (without entrained malicious cross site scripts) normally pass.
Owner:BEIJING VENUS INFORMATION TECH +1
Moving target defense against cross-site scripting
ActiveUS20150222657A1Avoid running timeMemory loss protectionError detection/correctionClient-sideWeb page
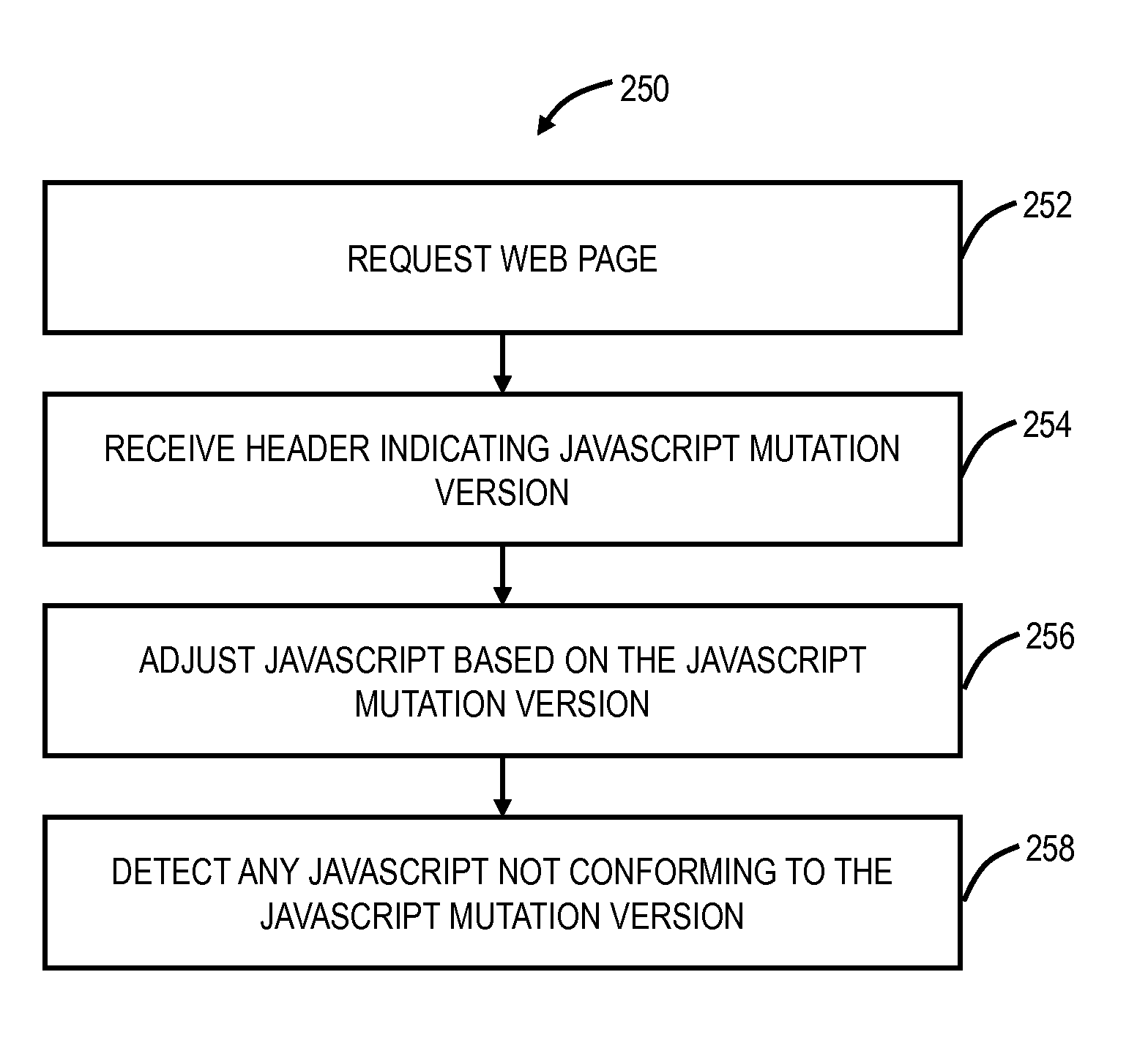
A method, in a server, implementing a moving target defense against cross-site scripting includes receiving a request for a web page, wherein the server has N versions of the web page each with a mutated version of JavaScript; selecting a web page of the N versions; and sending an indication of the mutated version of JavaScript associated with the web page in response to the request. Another method, in a client device, using a moving target defense against cross-site scripting includes requesting a web page; receiving an indication of a mutated version of JavaScript for the web page; and adjusting a JavaScript interpreter based on the mutated version of JavaScript for the web page.
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL
Moving target defense against cross-site scripting
ActiveUS20150096006A1Avoid running timeDigital data processing detailsComputer security arrangementsWeb pageJavaScript
A method, in a server, implementing a moving target defense against cross-site scripting includes receiving a request for a web page, wherein the server has N versions of the web page each with a mutated version of JavaScript; selecting a web page of the N versions; and sending an indication of the mutated version of JavaScript associated with the web page in response to the request. Another method, in a client device, using a moving target defense against cross-site scripting includes requesting a web page; receiving an indication of a mutated version of JavaScript for the web page; and adjusting a JavaScript interpreter based on the mutated version of JavaScript for the web page.
Owner:THE UNIV OF NORTH CAROLINA AT CHAPEL HILL
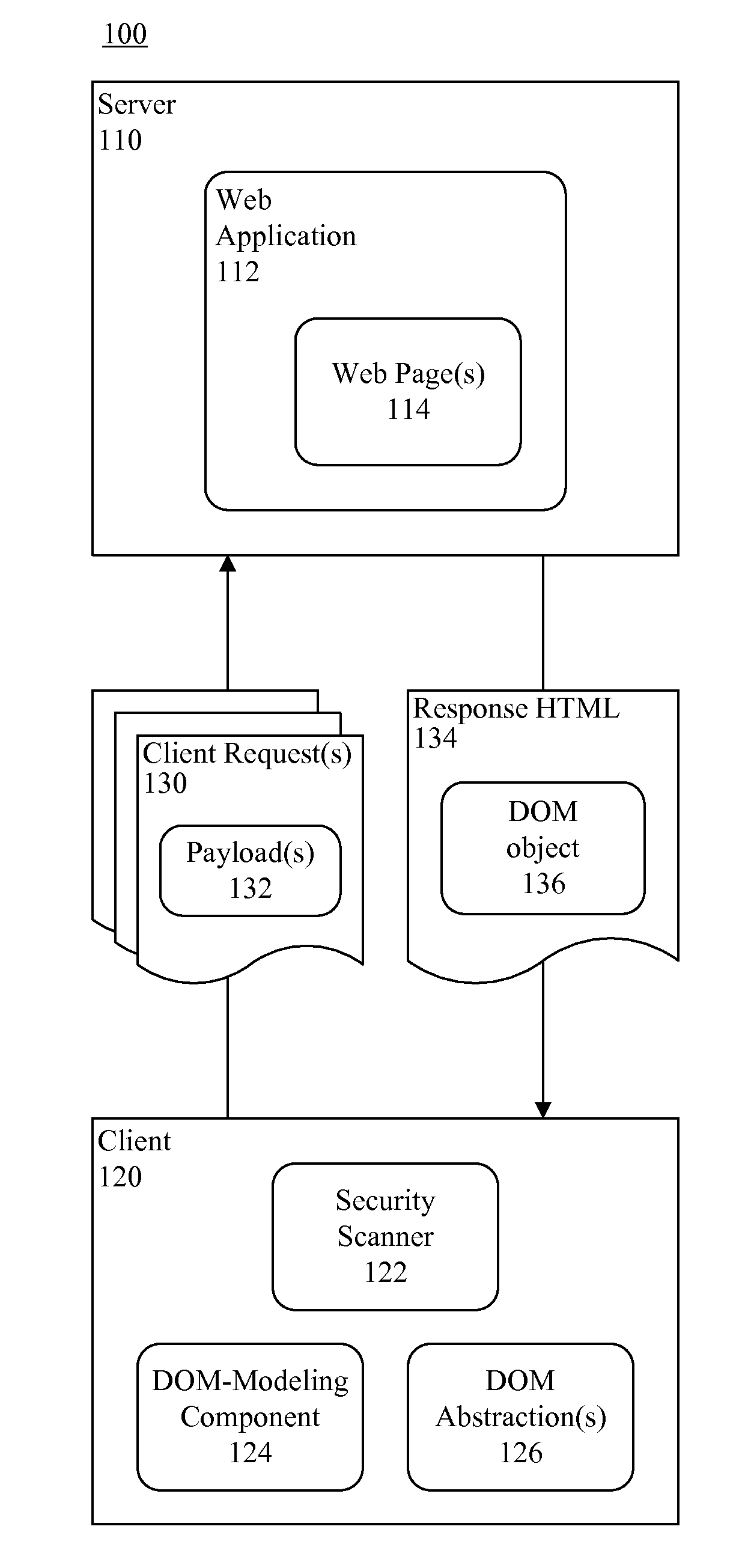
Detection of DOM-based cross-site scripting vulnerabilities
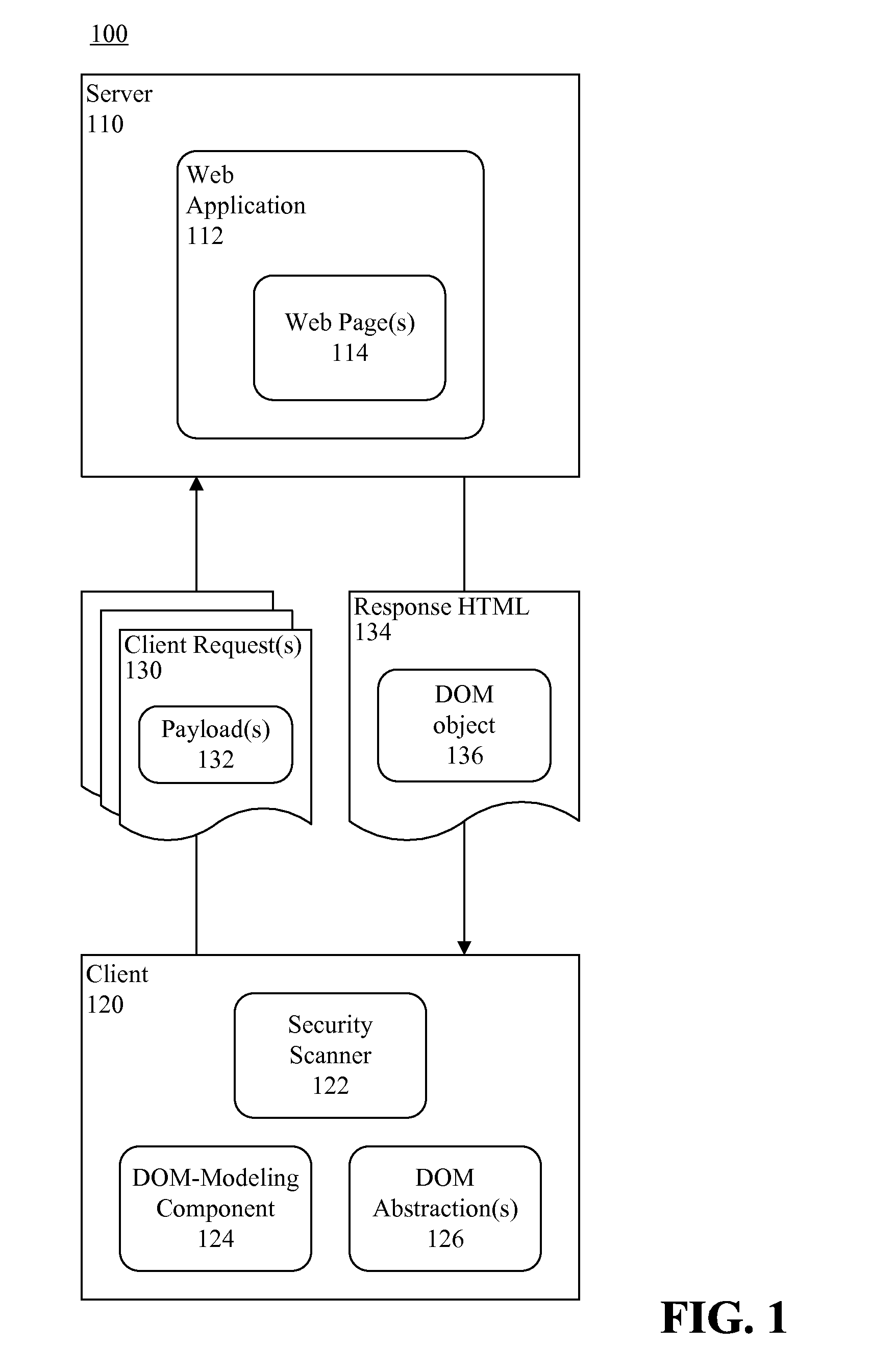
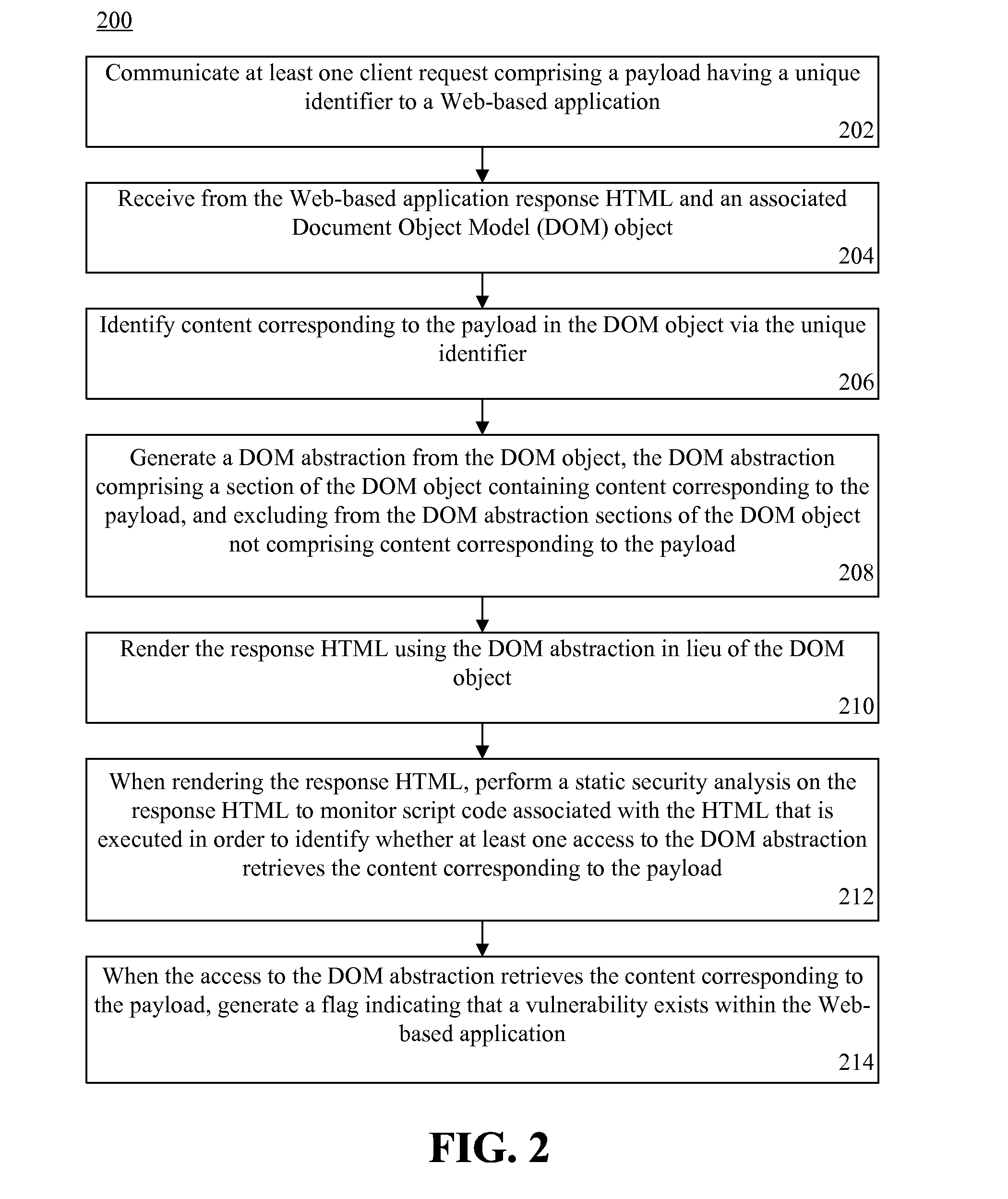
InactiveUS20130111595A1Memory loss protectionError detection/correctionUnique identifierApplication software
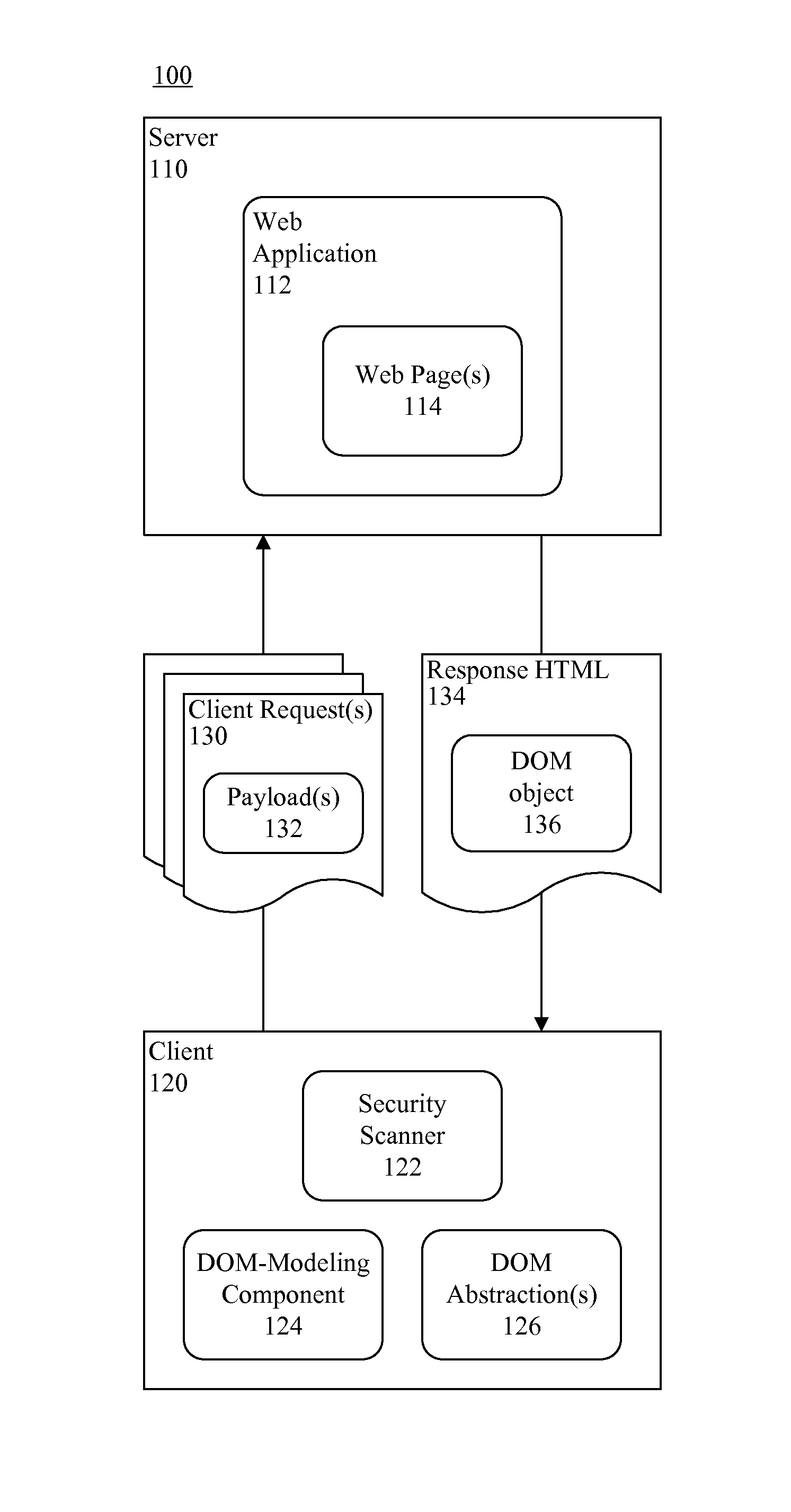
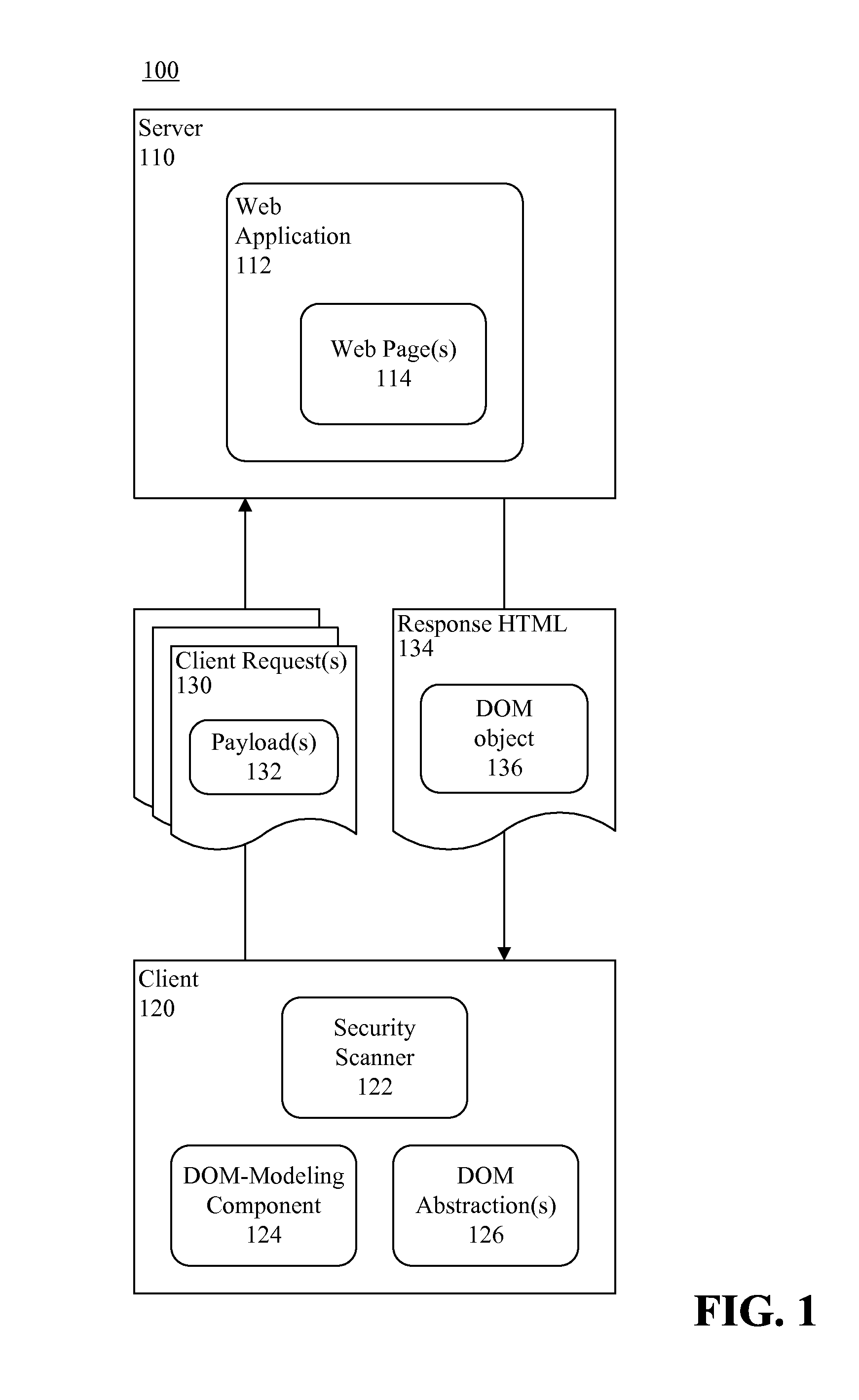
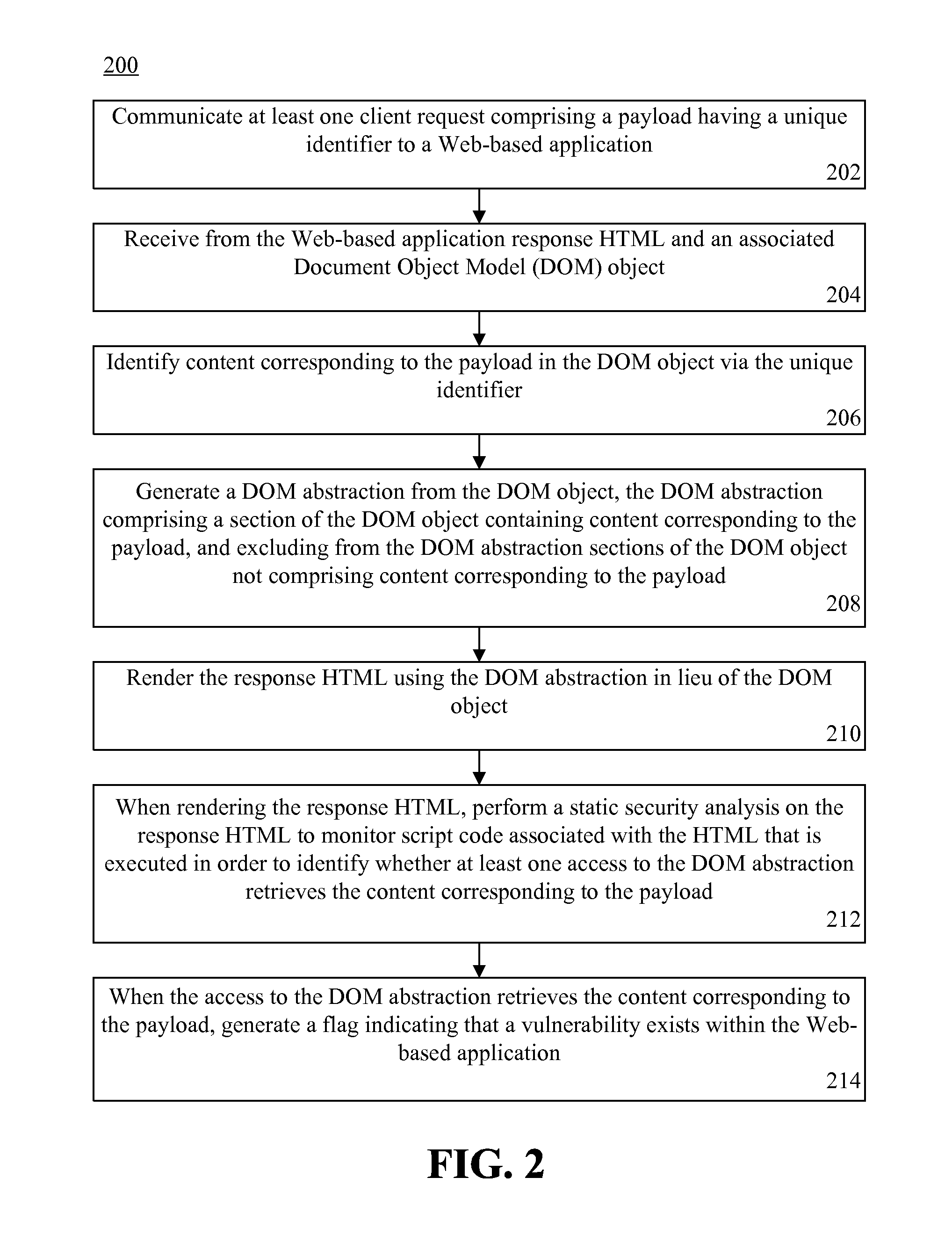
Testing a Web-based application for security vulnerabilities. At least one client request including a payload having a unique identifier can be communicated to the Web-based application. Response HTML and an associated Document Object Model (DOM) object can be received from the Web-based application. Content corresponding to the payload can be identified in the DOM object via the unique identifier. A section of the DOM object including the payload can be identified as un-trusted.
Owner:IBM CORP
XSS (Cross Site Scripting) testing method and XSS testing system based on DOM (Document Object Model)
ActiveCN102999420APrecise positioningGuaranteed accuracySoftware testing/debuggingAlgorithmData mining
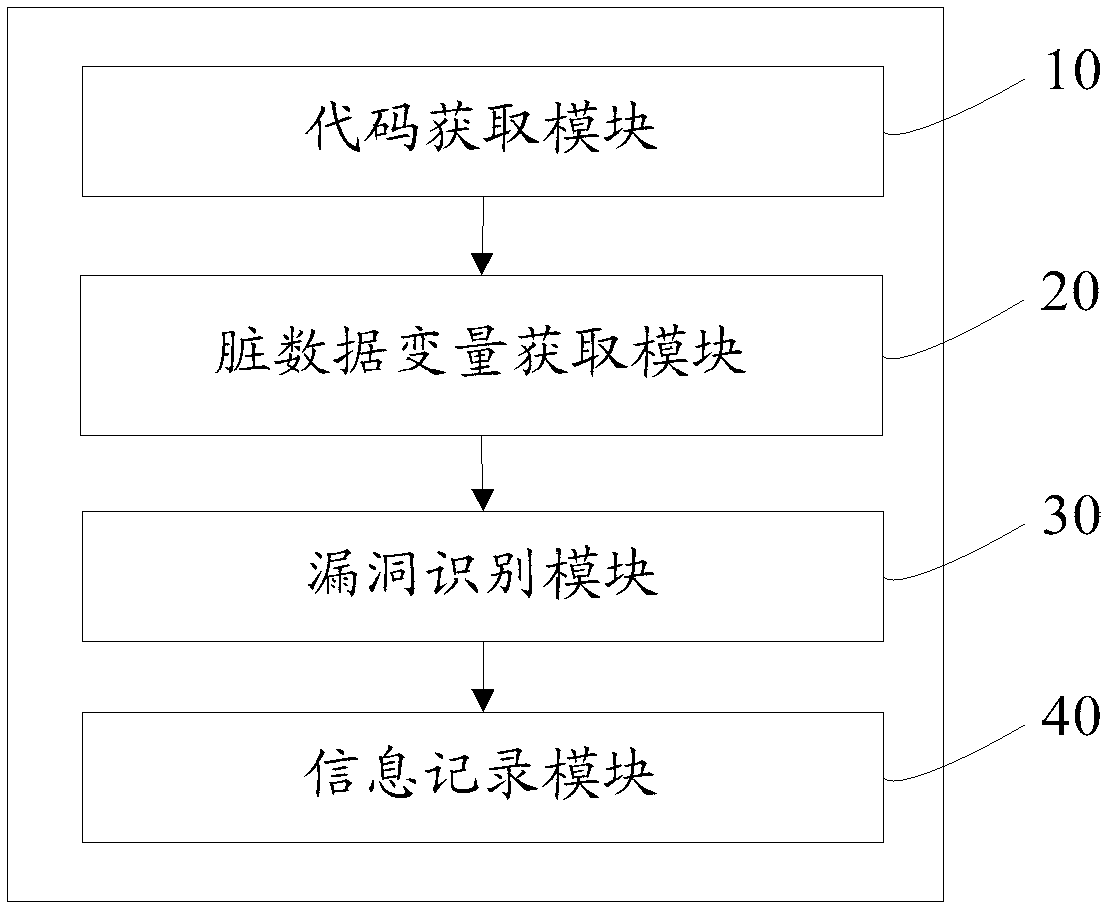
The invention provides an XSS (Cross Site Scripting) testing method based on a DOM (Document Object Model). The XSS testing method comprises the following steps of obtaining source codes of a destination page, and extracting script codes in the source codes; traversing all the script codes, and obtaining all dirty data inlets and variables passed by the dirty data inlets from the script codes by utilizing a predefined dirty data inlet; traversing all the script codes again, obtaining output functions in the script codes, extracting parameters of the output functions for being matched with the dirty data inlets and the variables passed by the dirty data inlets, and determining that bugs exist if the parameters of the output functions can be matched with the dirty data inlets and the variables passed by the dirty data inlets; and recording information of the bugs. The invention also provides an XSS testing device based on the DOM for realizing the XSS testing method. According to the XSS testing method based on the DOM and the XSS testing device based on the DOM, which are provided by the invention, the problem that XSS based on the DOM cannot be accurately tested can be solved.
Owner:ALIBABA GRP HLDG LTD
Methods for determining cross-site scripting and related vulnerabilities in applications
ActiveUS20150264082A1Memory loss protectionError detection/correctionProgramming languageComputerized system
The invention provides computer-implemented methods and computer systems for testing applications such as web-based (HTTP) applications for cross-site scripting (XSS) and related security vulnerabilities and permits the discovery of previously unknown XSS and related vulnerabilities in applications without relying on known or previously generated static XSS signatures. The invention may be applied to any type of XSS or related vulnerability for any variation of application code.
Owner:BELVA KENNETH F
Complementary character encoding for preventing input injection in web applications
InactiveUS8615804B2Appropriate treatmentImprove efficiencyMemory loss protectionError detection/correctionSQL injectionLexical analysis
Method to prevent the effect of web application injection attacks, such as SQL injection and cross-site scripting (XSS), which are major threats to the security of the Internet. Method using complementary character coding, a new approach to character level dynamic tainting, which allows efficient and precise taint propagation across the boundaries of server components, and also between servers and clients over HTTP. In this approach, each character has two encodings, which can be used to distinguish trusted and untrusted data. Small modifications to the lexical analyzers in components such as the application code interpreter, the database management system, and (optionally) the web browser allow them to become complement aware components, capable of using this alternative character coding scheme to enforce security policies aimed at preventing injection attacks, while continuing to function normally in other respects. This approach overcomes some weaknesses of previous dynamic tainting approaches by offering a precise protection against persistent cross-site scripting attacks, as taint information is maintained when data is passed to a database and later retrieved by the application program. The technique is effective on a group of vulnerable benchmarks and has low overhead.
Owner:POLYTECHNIC INSTITUTE OF NEW YORK UNIVERSITY
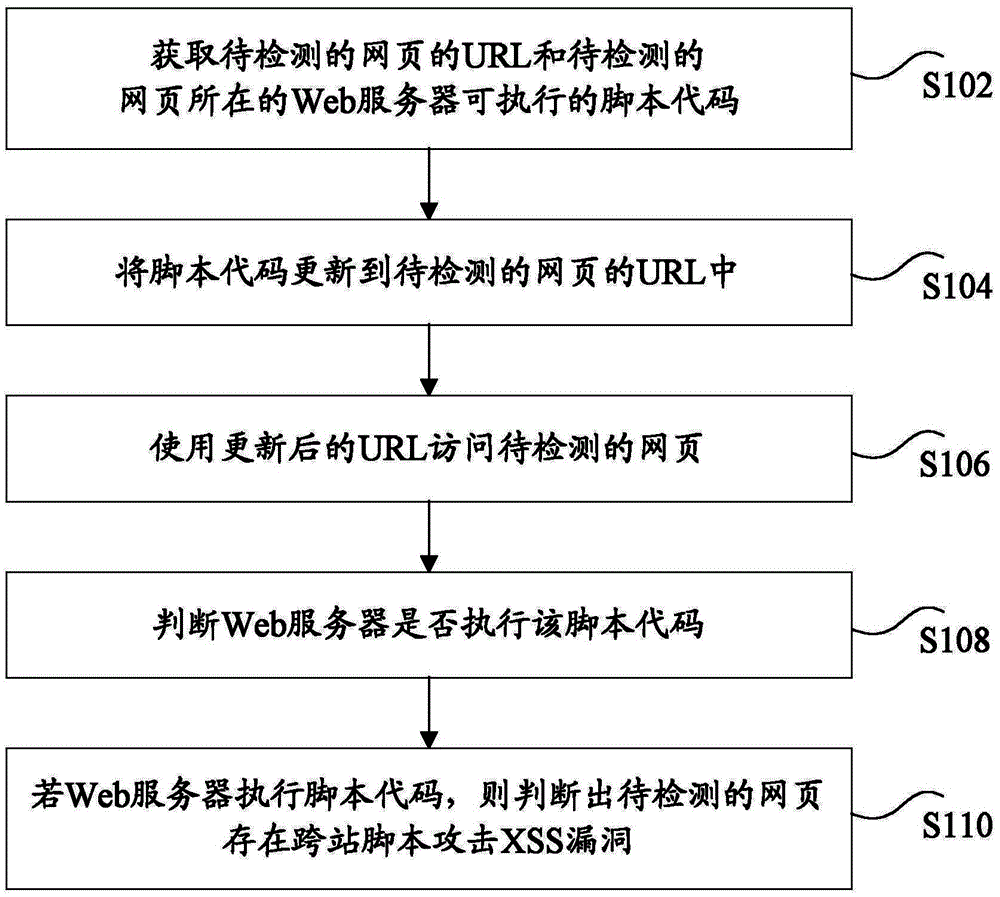
XSS vulnerability detection method and device
InactiveCN105282096AEasy to reportImprove accuracyPlatform integrity maintainanceData switching networksWeb serviceUniform resource locator
The invention discloses an XSS vulnerability detection method and device. The method comprises that a URL of a webpage to be detected and an executable script code of a Web server of the webpage to be detected are obtained; the script code is updated in the URL of the webpage to be detected; the updated URL is used to access the webpage to be detected; whether the Web server executes the script code is detected; and if the Web server executes the script code, it is determined that XSS vulnerability exists in the webpage to be detected. The method and device of the invention can be used to solve the technical problem that a detection result obtained via an XSS vulnerability detection scheme based on matching and analysis of webpage files is lower in accuracy.
Owner:TENCENT TECH (SHENZHEN) CO LTD
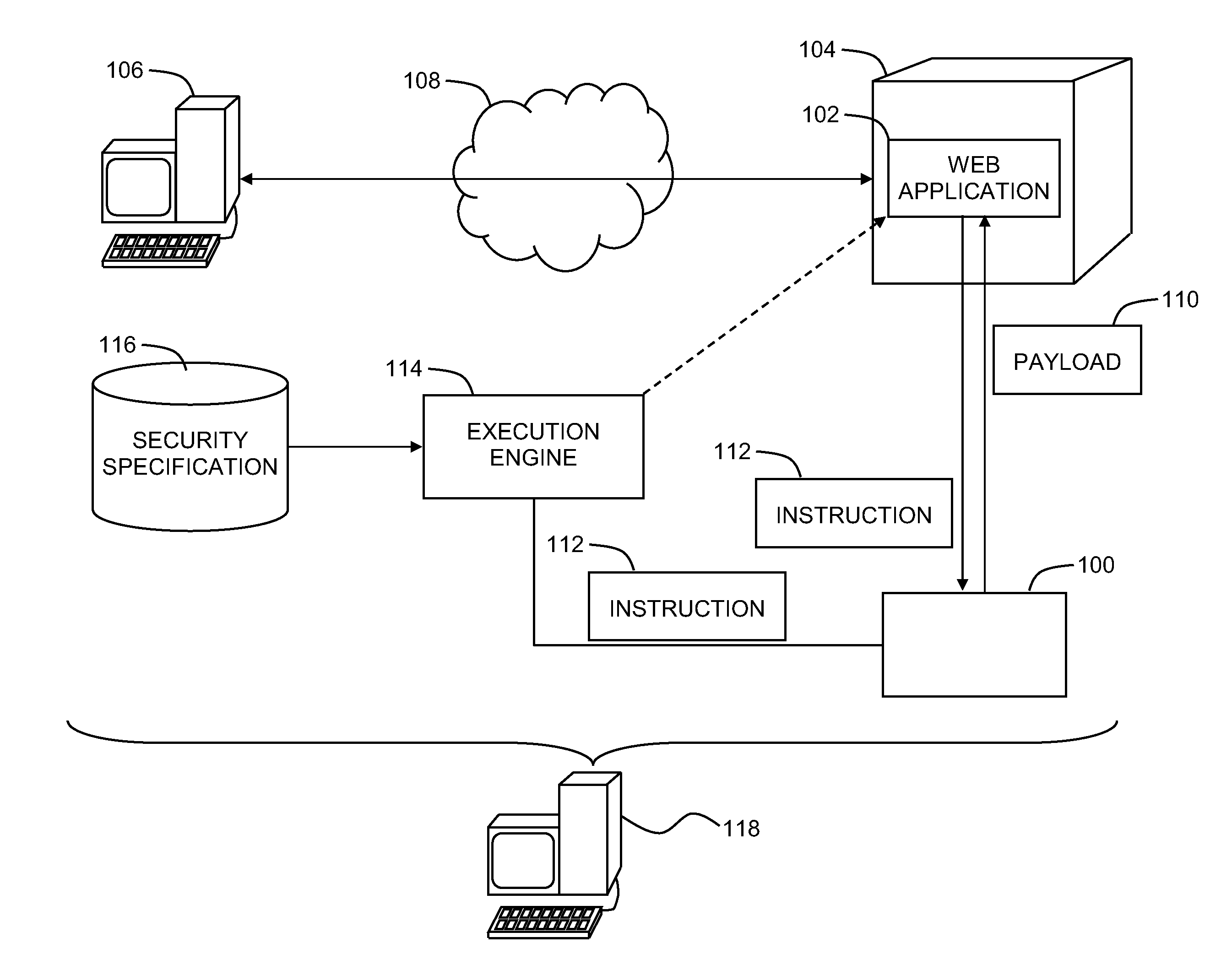
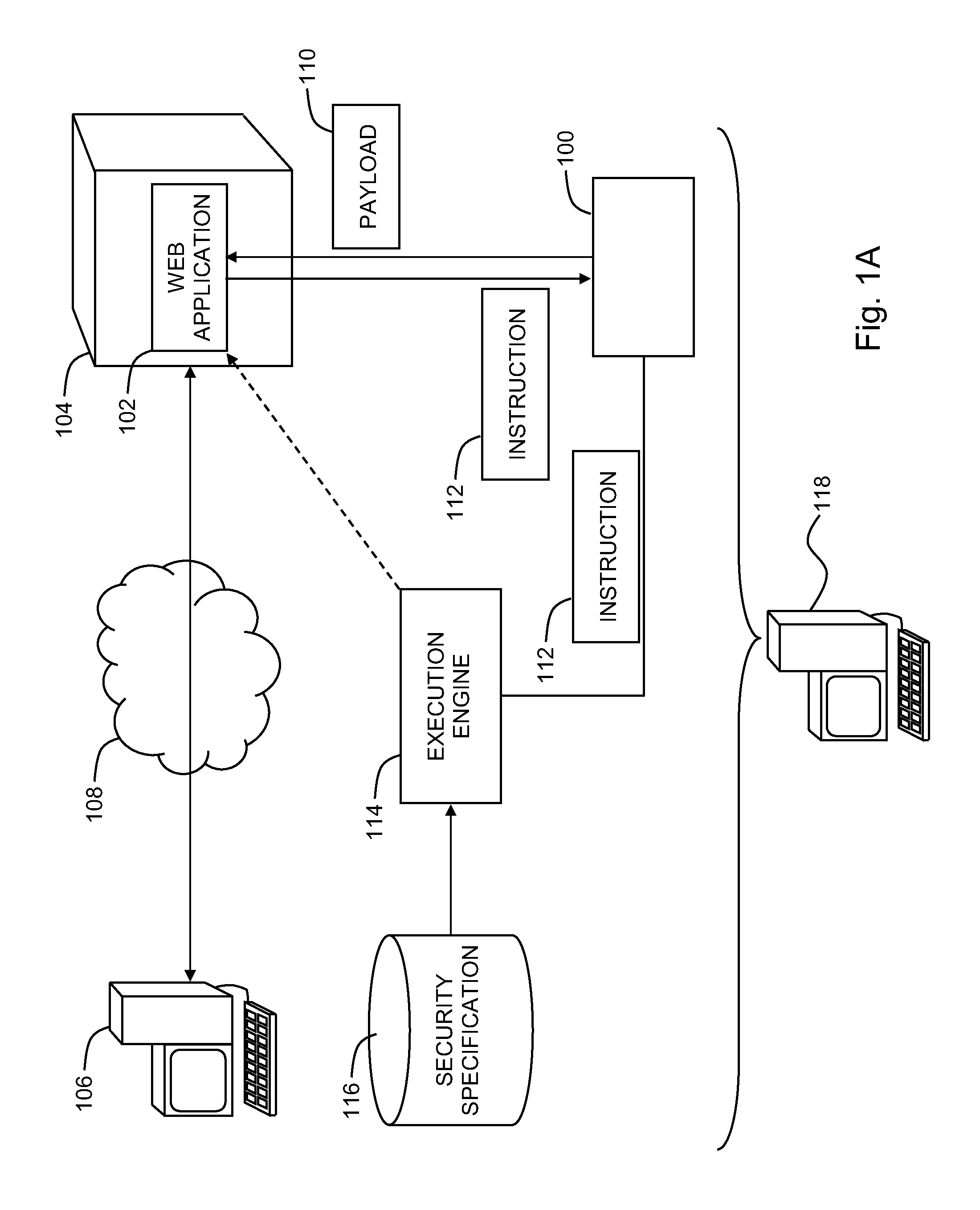
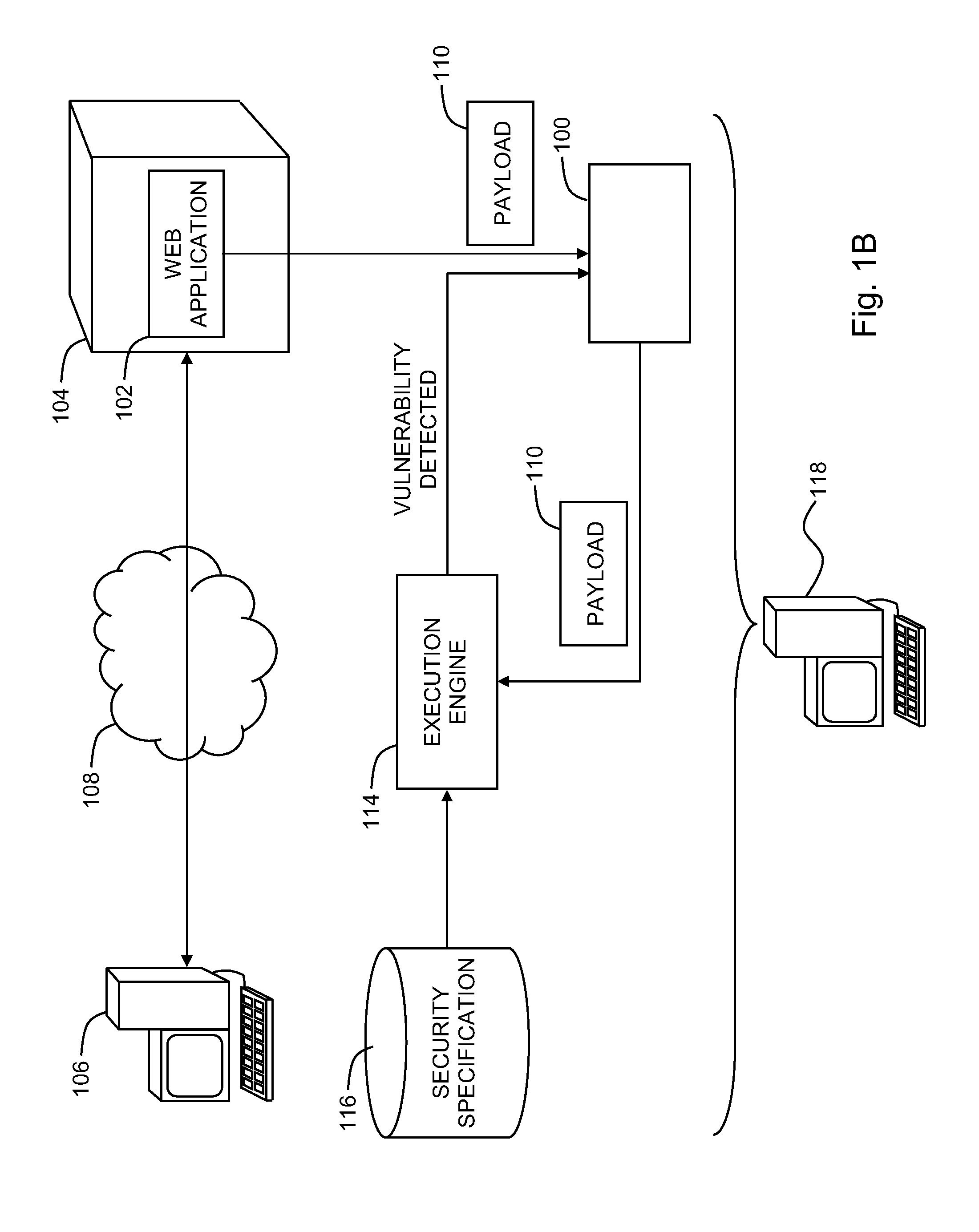
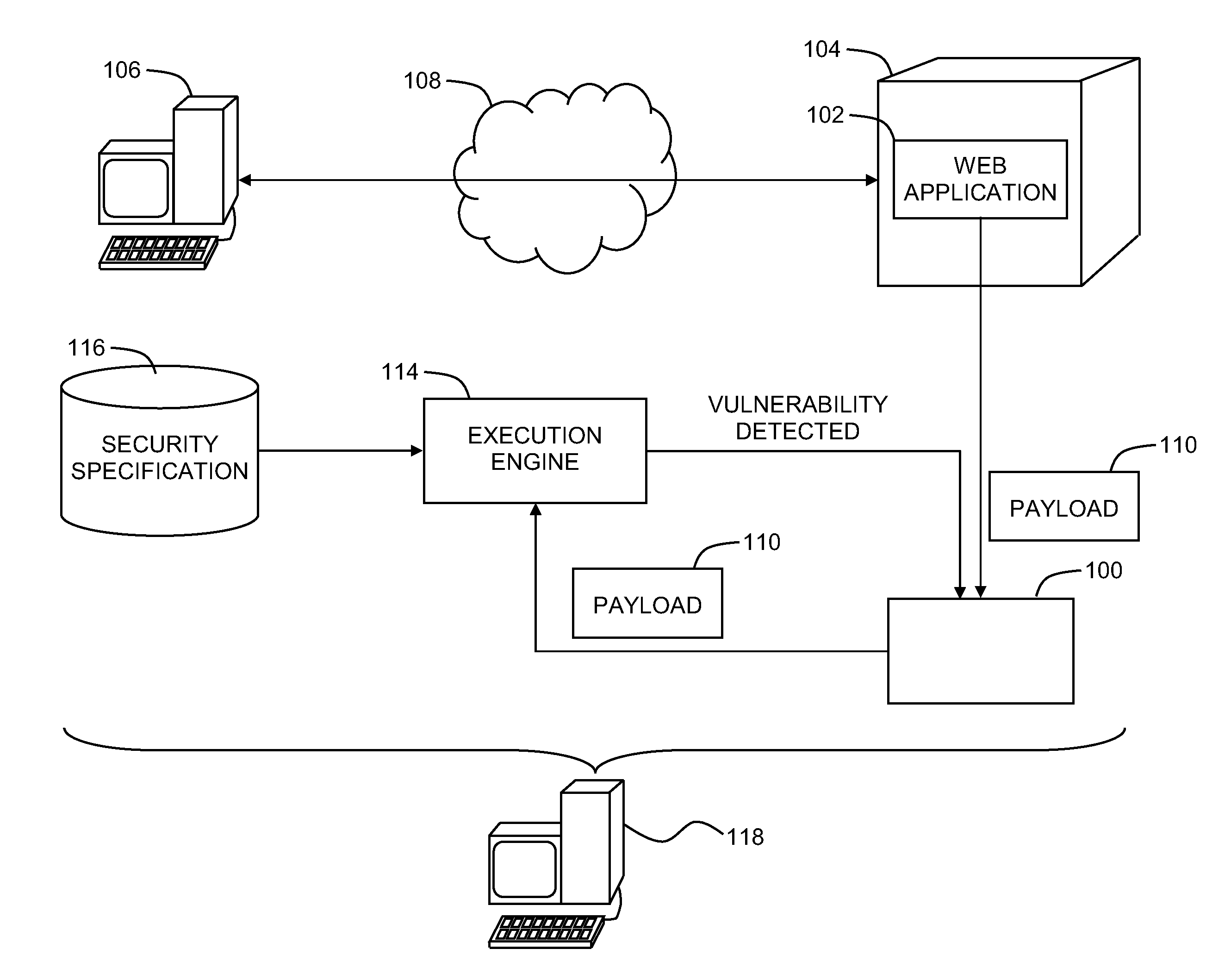
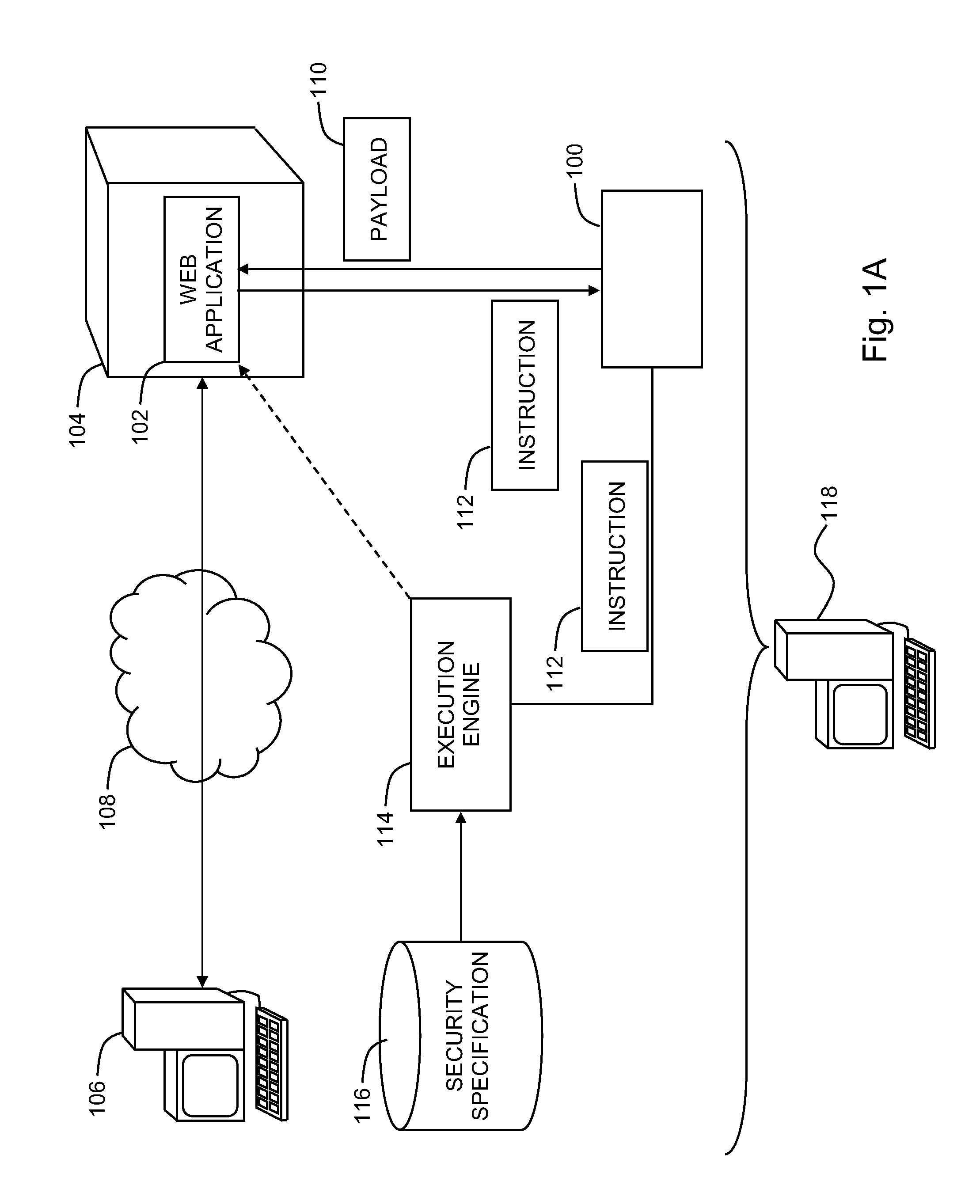
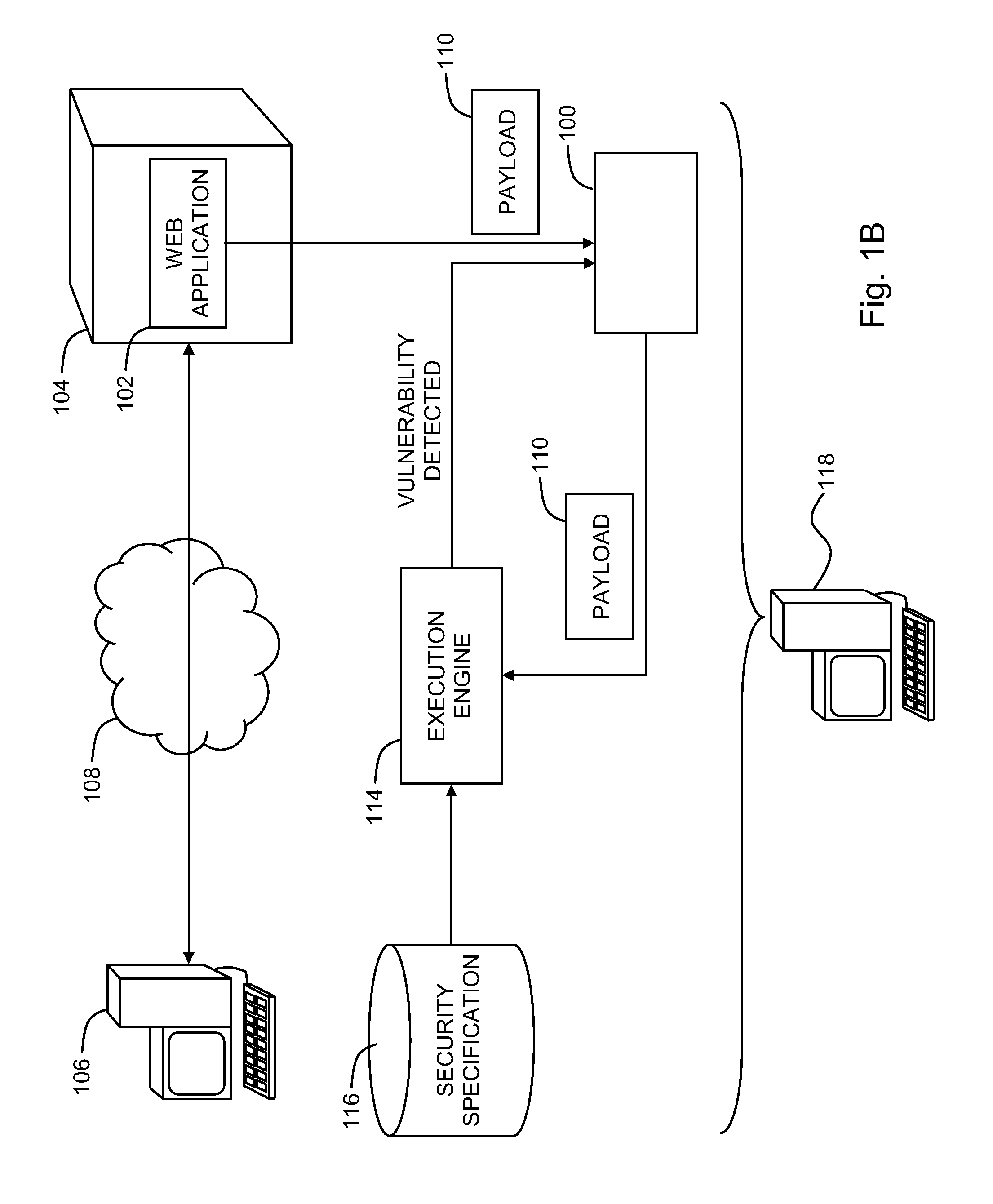
Detecting stored cross-site scripting vulnerabilities in web applications
A system for detecting security vulnerabilities in web applications, the system including, a black-box tester configured to provide a payload to a web application during a first interaction with the web application at a computer server, where the payload includes a payload instruction and an identifier, and an execution engine configured to detect the identifier within the payload received during an interaction with the web application subsequent to the first interaction, and determine, responsive to detecting the identifier within the payload, whether the payload instruction underwent a security check prior to execution of the payload instruction.
Owner:FINJAN BLUE INC
Detecting stored cross-site scripting vulnerabilities in web applications
A method for detecting security vulnerabilities in web applications can include providing a payload to a web application during a first interaction with the web application at a computer server, where the payload includes a payload instruction and an identifier, detecting the identifier within the payload received during an interaction with the web application subsequent to the first interaction, and determining, responsive to detecting the identifier within the payload, whether the payload instruction underwent a security check prior to execution of the payload instruction.
Owner:FINJAN BLUE INC
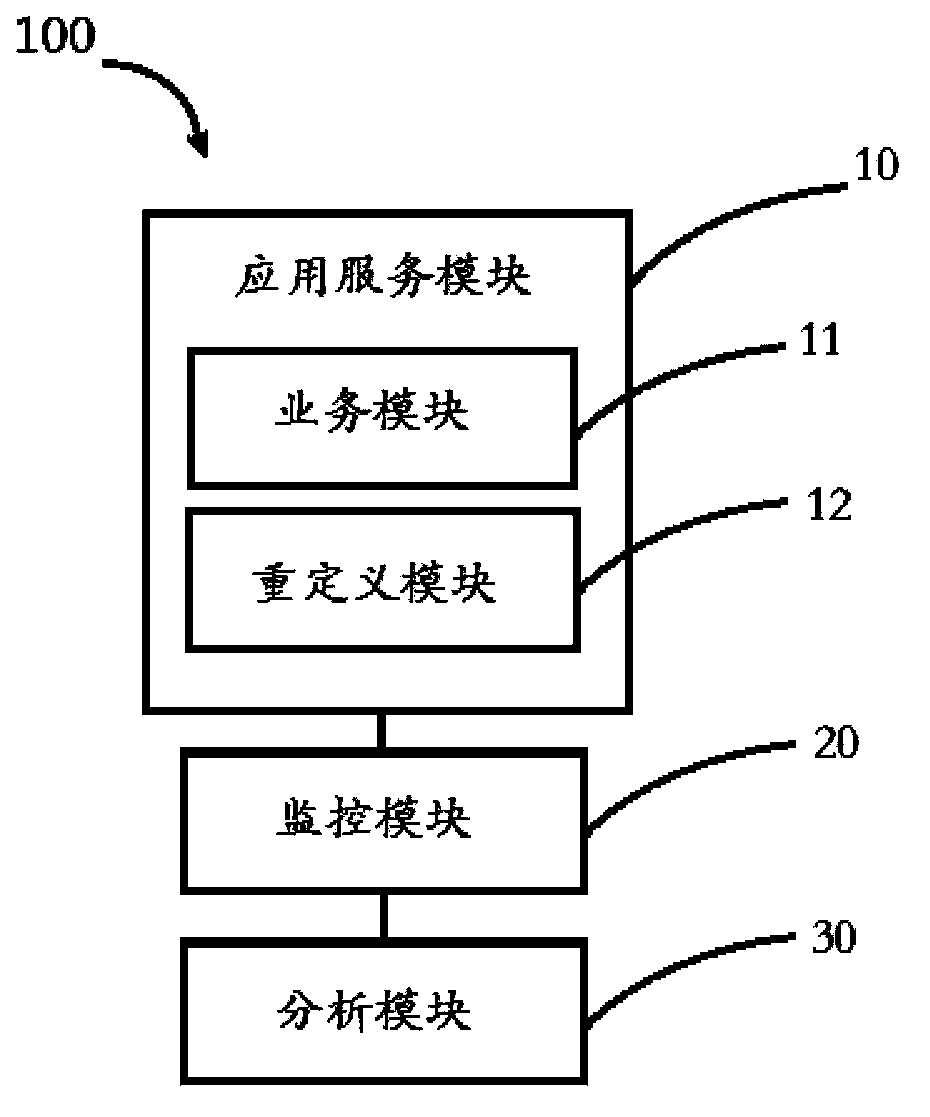
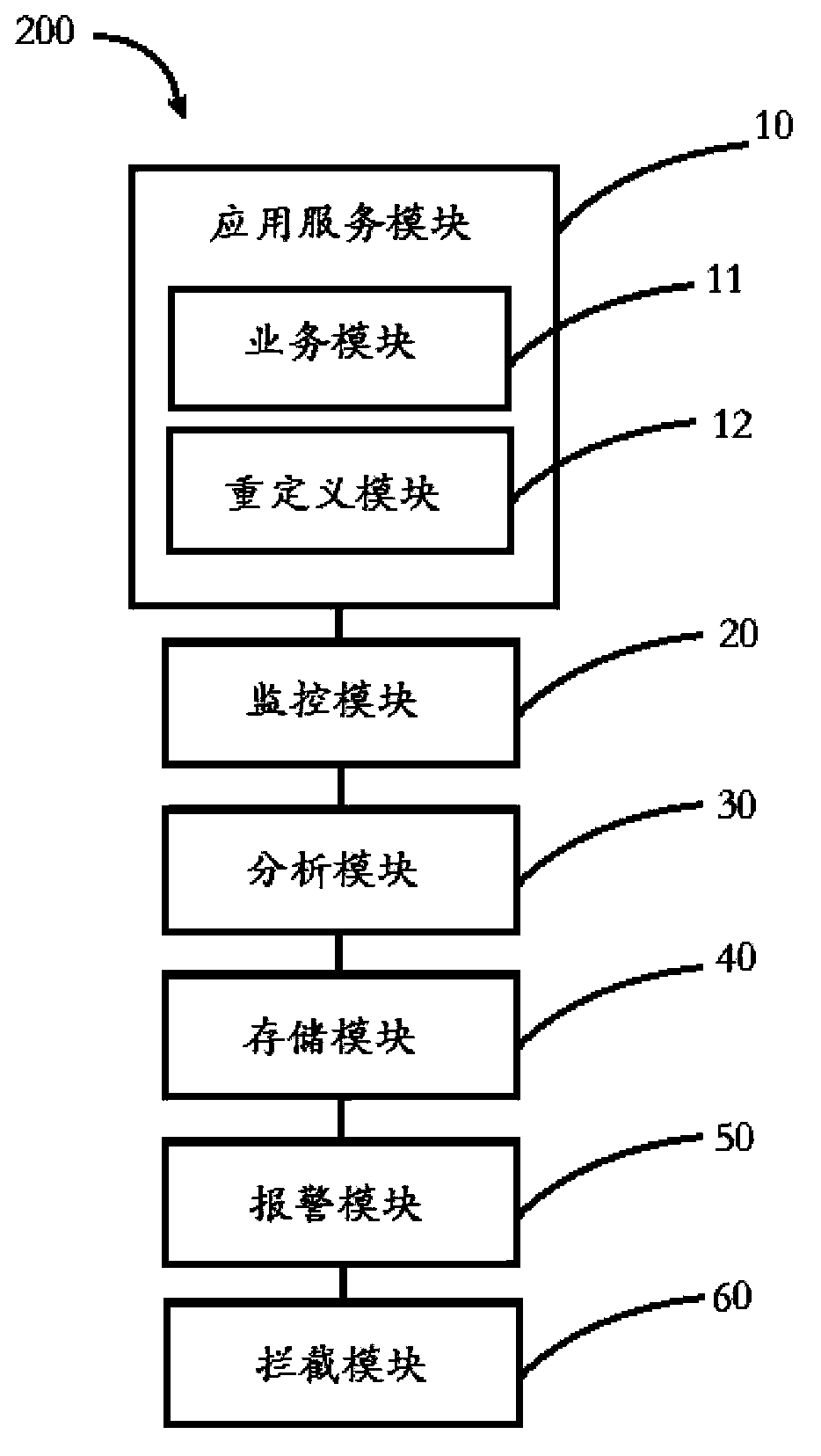
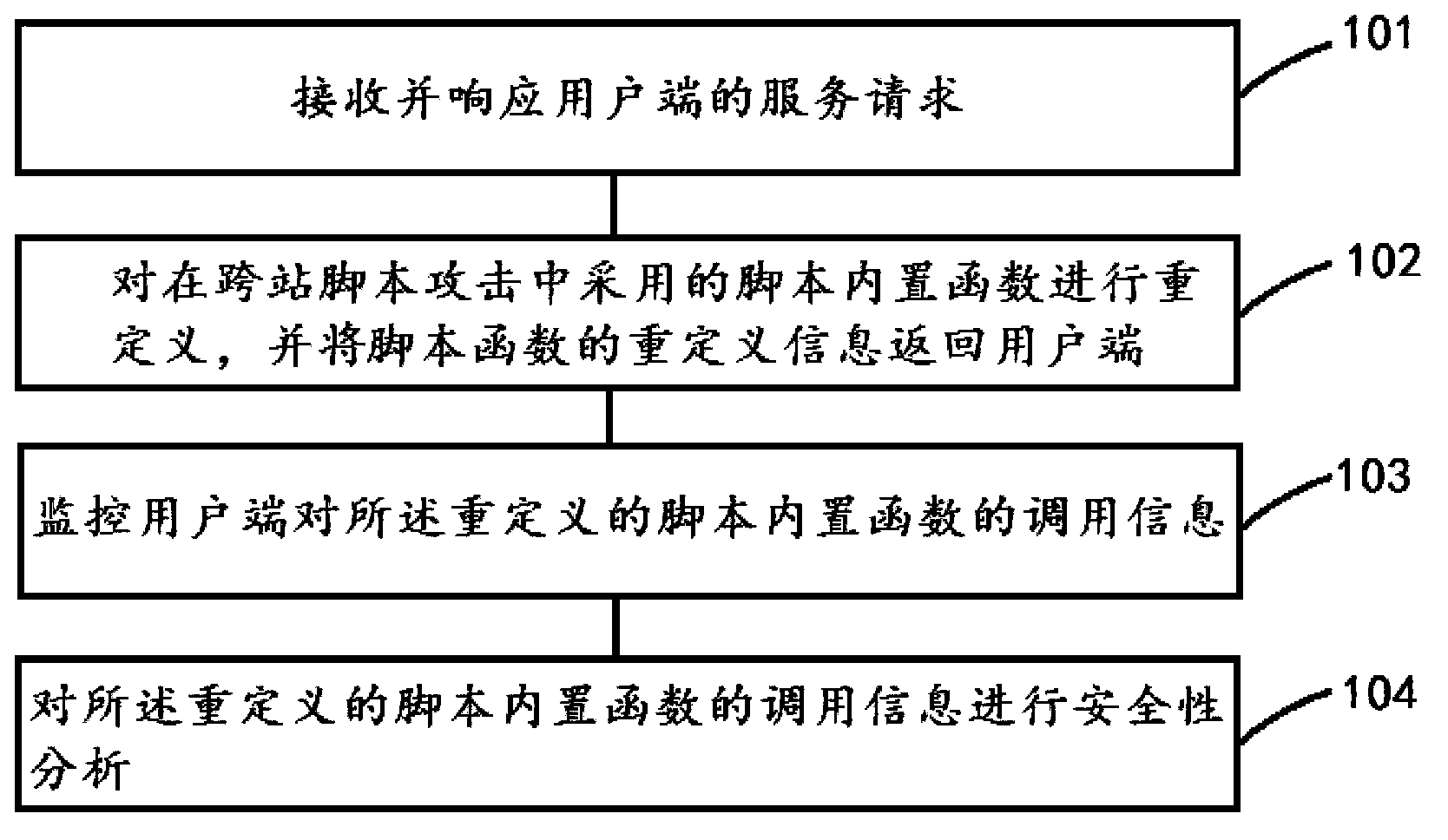
Cross-site scripting attack monitoring system and method
ActiveCN103856471AEfficient detectionIncrease reachPlatform integrity maintainanceTransmissionMonitoring systemService module
The invention relates to a cross-site scripting attack monitoring system. The cross-site scripting attack monitoring system comprises an application serving module, a monitoring module and an analyzing module. The application serving module comprises a service module and a redefining module. The service module receives and responds to a service request of a user side, and the redefining module redefines a script built-in function adopted in a cross-site scripting attack and returns redefining information of the script built-in function to the user side; the monitoring module monitors calling information of the user side to the redefined script built-in function; the analyzing module analyzes the safety of the calling information. The cross-site scripting attack monitoring system can realize accurate locating of the source of the cross-site scripting attack, the attacking time, leaked data, attacked vulnerability and the like. In addition, the invention further provides a cross-site scripting attack monitoring method.
Owner:ALIBABA GRP HLDG LTD
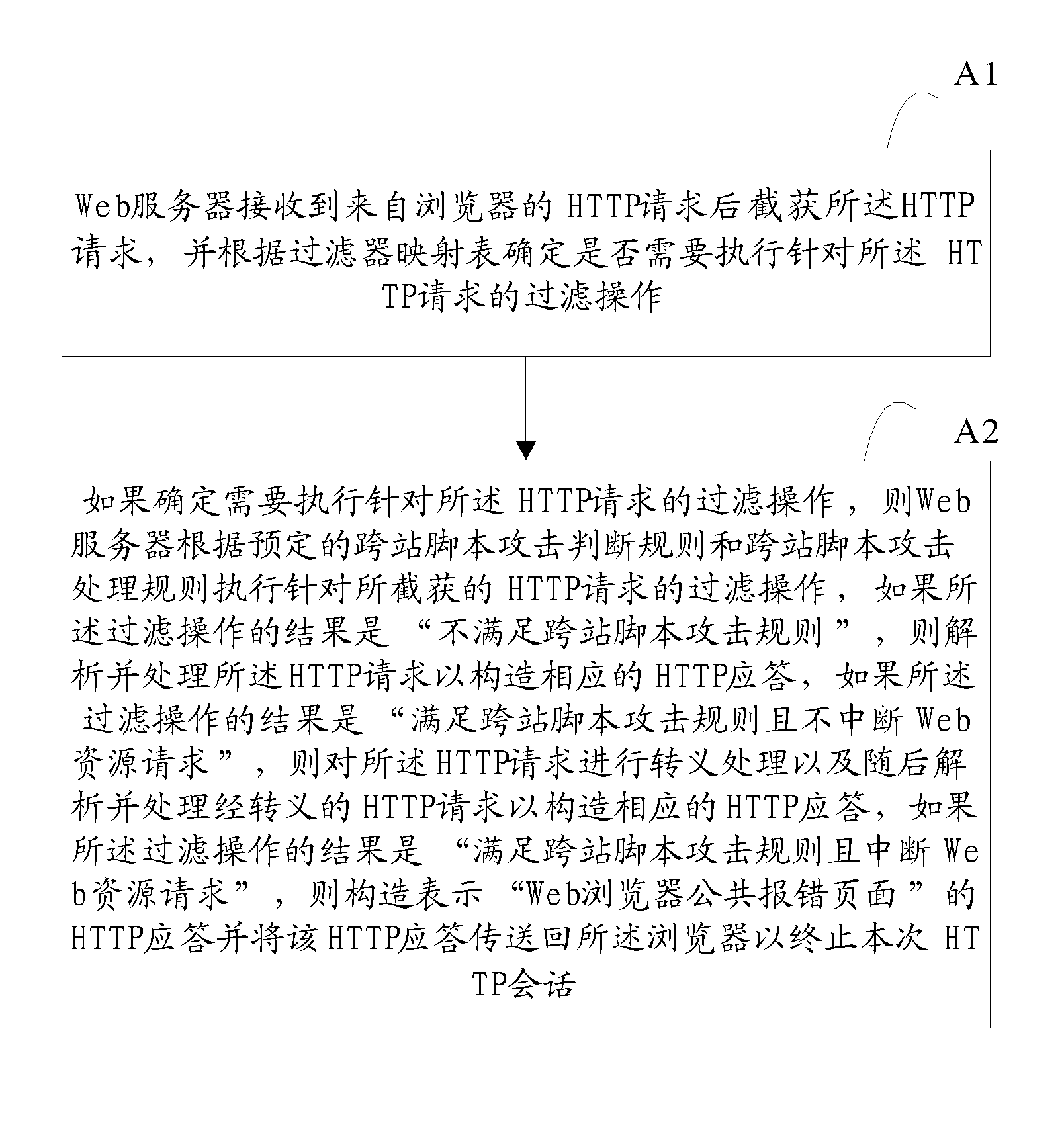
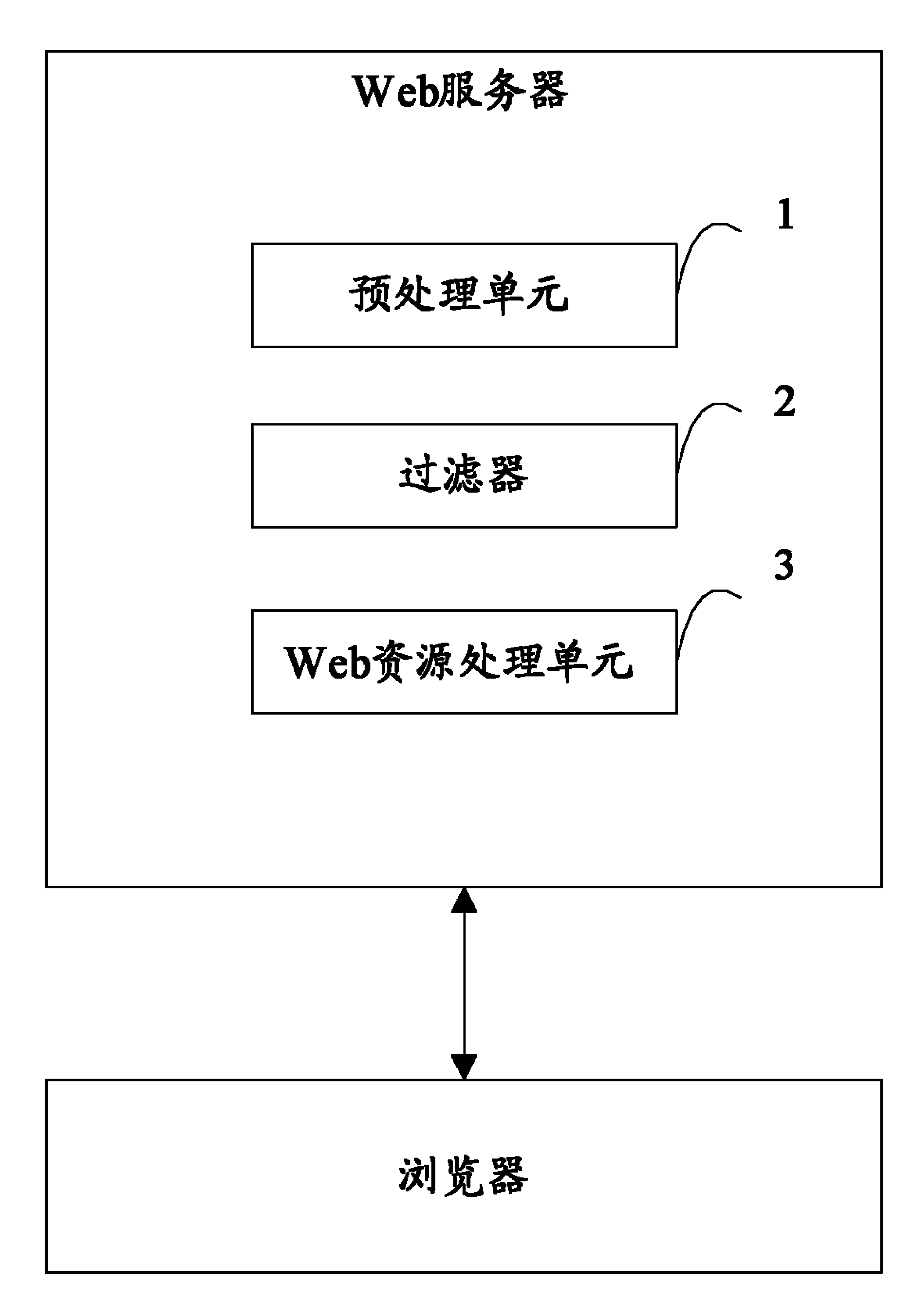
Web server and method for preventing cross-site scripting attack
The invention proposes a web server and a method for preventing cross-site scripting attack, wherein the method includes: after the Web server receives an HTTP request from a browser, intercepting the HTTP request, and determining, according to a filter mapping table, whether a filtering operation with respect to the HTTP request is to be executed; if it is determined that the filtering operation with respect to the HTTP request is needed to be executed, executing, by the Web server, the filtering operation with respect to the intercepted HTTP request according to a predetermined cross-site scripting attack judging rule and a cross-site scripting attack processing rule. The Web server and the method for preventing cross-site scripting attack disclosed in the invention can prevent effectively the cross-site scripting attack with respect to the browser and / or Web server.
Owner:CHINA UNIONPAY
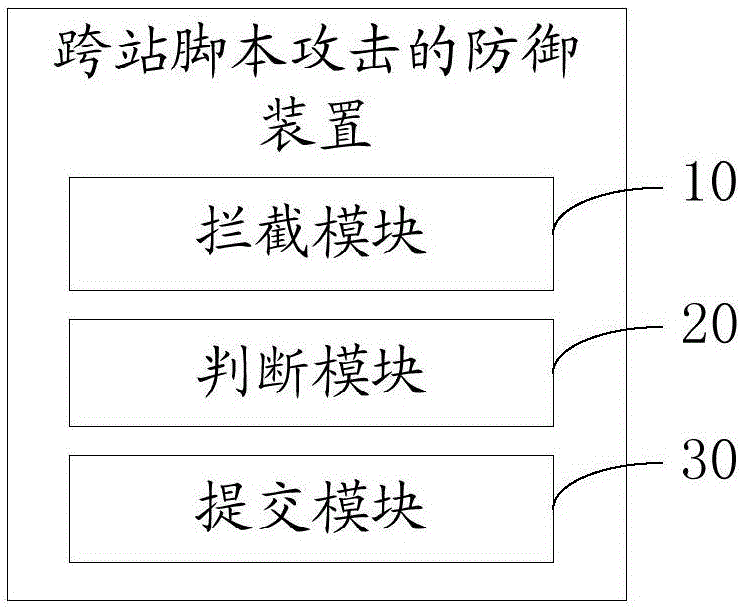
Defending device and method for cross-site scripting attack
The invention discloses a defending device for a cross-site scripting attack. The defending device comprises an intercepting module, a judging module and a submitting module, wherein the intercepting module is used for intercepting a request transmitted to an application in an application server through a cross-site scripting attack filter; the judging module is used for analyzing and processing the intercepted request, and judging whether the request includes malicious codes applied to the cross-site scripting attack; and the submitting module is used for submitting the request to an open-source project for escaping if the request includes the malicious codes applied to the cross-site scripting attack in order to submit the escaped request to the application in the application server. The invention also discloses a defending method for the cross-site scripting attack. Through adoption of the defending device and method, hard coding of Web pages can be avoided; the workload is lowered; and the efficiency in defending of the cross-site scripting attack is increased.
Owner:NUBIA TECHNOLOGY CO LTD
Cross domain communication
InactiveUS8250082B2Improve reliabilityDigital data processing detailsSpecial data processing applicationsA domainWeb page
Various embodiments utilize nested Iframes within a web page to allow cross domain communication. That is, various embodiments can create an embedded Iframe that shares the domain of an Iframe or web page with which communication is desired. Because the embedded Iframe shares the domain of the Iframe or web page with which communication is desired, restrictions on cross-site scripting do not inhibit communication or scripting between the domain-matched Iframe(s) and / or web page. This embedded Iframe can then provide a mechanism by which web pages or Iframes from other domains can communicate with the Iframe or web page with which the embedded Iframe shares a domain.
Owner:MICROSOFT TECH LICENSING LLC
Cross-site scripting attack defense method and device and application server
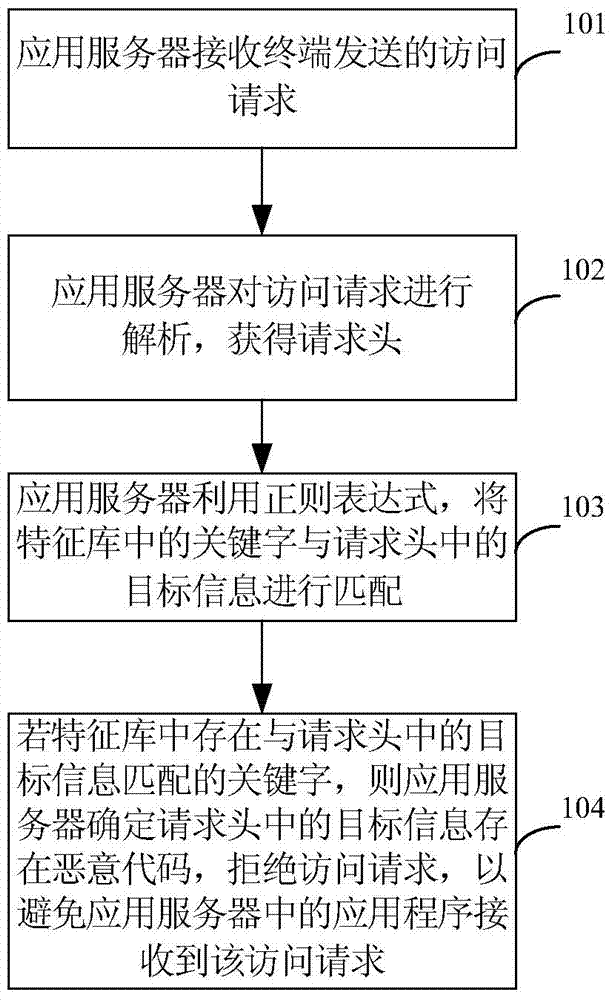
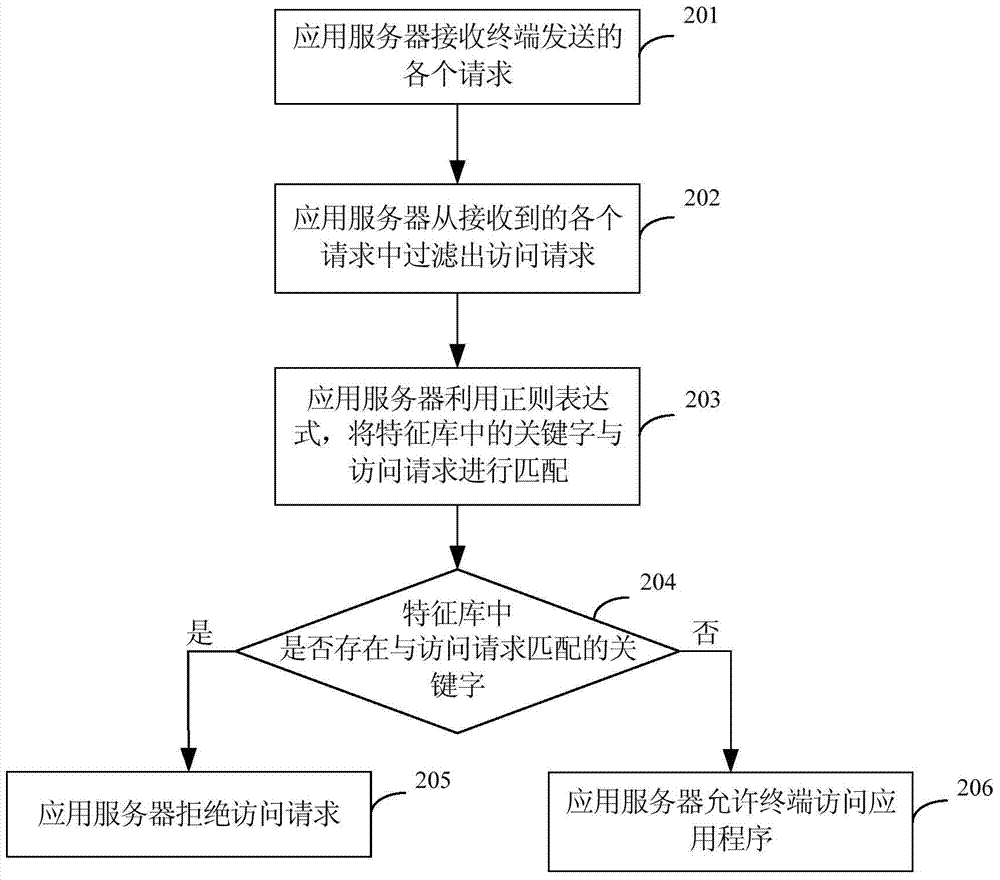
ActiveCN104519008AImprove attack efficiencyAvoid hardcodingTransmissionHard codingApplication server
The invention provides a cross-site scripting attack defense method and device and an application server. The method comprises the following steps: receiving an access request sent by a terminal through the application server; resolving the access request to obtain a request header; matching keywords in a feature library with target information in the request header by using a regular expression; and if keywords matched with the target information in the request header exist in the feature library, determining that a malicious code exists in the target information in the request header through the application server, and denying the access request through the application server in order to defense cross-site scripting attacks. Through uniform detection of the access requests sent by the terminal on the application server, hard coding of each Web page is avoided; the workload is lowered; and the cross-site scripting attack defense efficiency is increased.
Owner:NEW FOUNDER HLDG DEV LLC +1
Detection of DOM-based cross-site scripting vulnerabilities
ActiveUS20130111594A1Memory loss protectionUnauthorized memory use protectionUnique identifierApplication software
Testing a Web-based application for security vulnerabilities. At least one client request including a payload having a unique identifier can be communicated to the Web-based application. Response HTML and an associated Document Object Model (DOM) object can be received from the Web-based application. Content corresponding to the payload can be identified in the DOM object via the unique identifier. A section of the DOM object including the payload can be identified as un-trusted.
Owner:IBM CORP
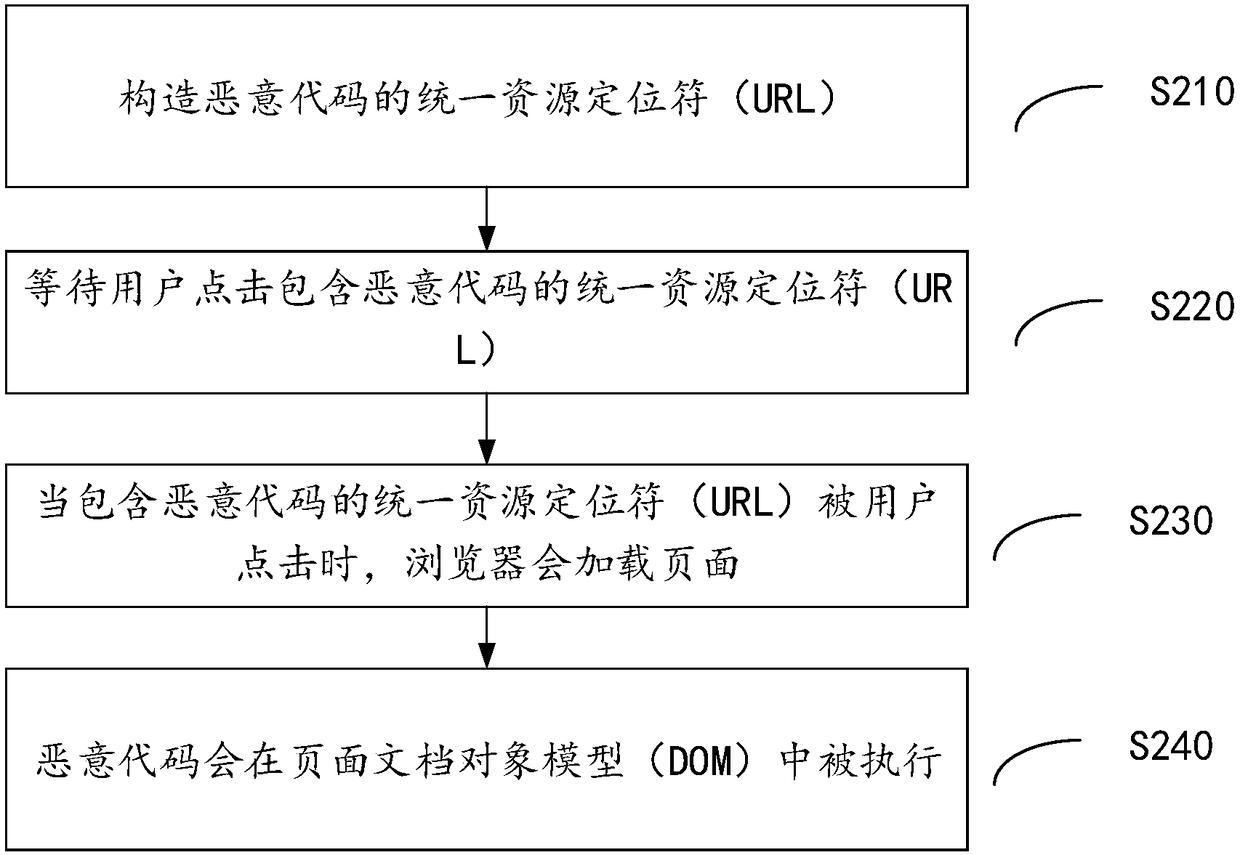
Method and device for defending DOM-Based-XSS vulnerability and client
ActiveCN108881101ARealize verificationHas the whole station defense effectTransmissionUniform resource locatorClient-side
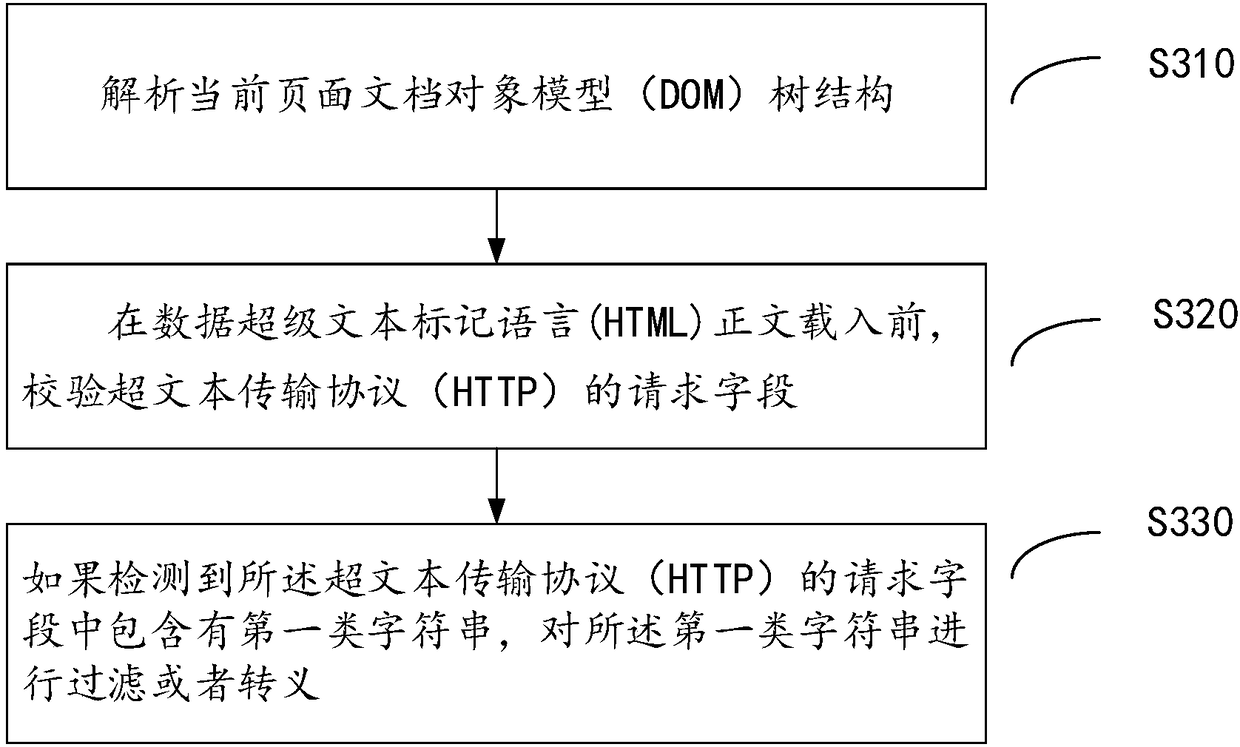
The invention provides a method and device for defending a document object model based cross site scripting (DOM-Based-XSS) vulnerability and a client. The method comprises the steps of: parsing a tree structure of a current page DOM; before a data hypertext markup language (HTML) text is loaded, checking a request field related to the DOM tree in a hypertext transfer protocol; and if the requestfield comprises a first category of character strings, carrying out filtering or escaping on the first category of character strings. According to the invention, at a moment before the data HTML textis loaded, the request field in the hypertext transfer protocol is verified, so that verification on a uniform resource locator (URL) can be comprehensively and efficiently implemented; the DOM-Based-XSS vulnerability is repaired; and the method and the device have a full-site defense effect and are helpful for controlling the online service increment DOM-Based-XSS vulnerability and preventing newDOM-Based-XSS vulnerability.
Owner:TENCENT TECH (SHENZHEN) CO LTD
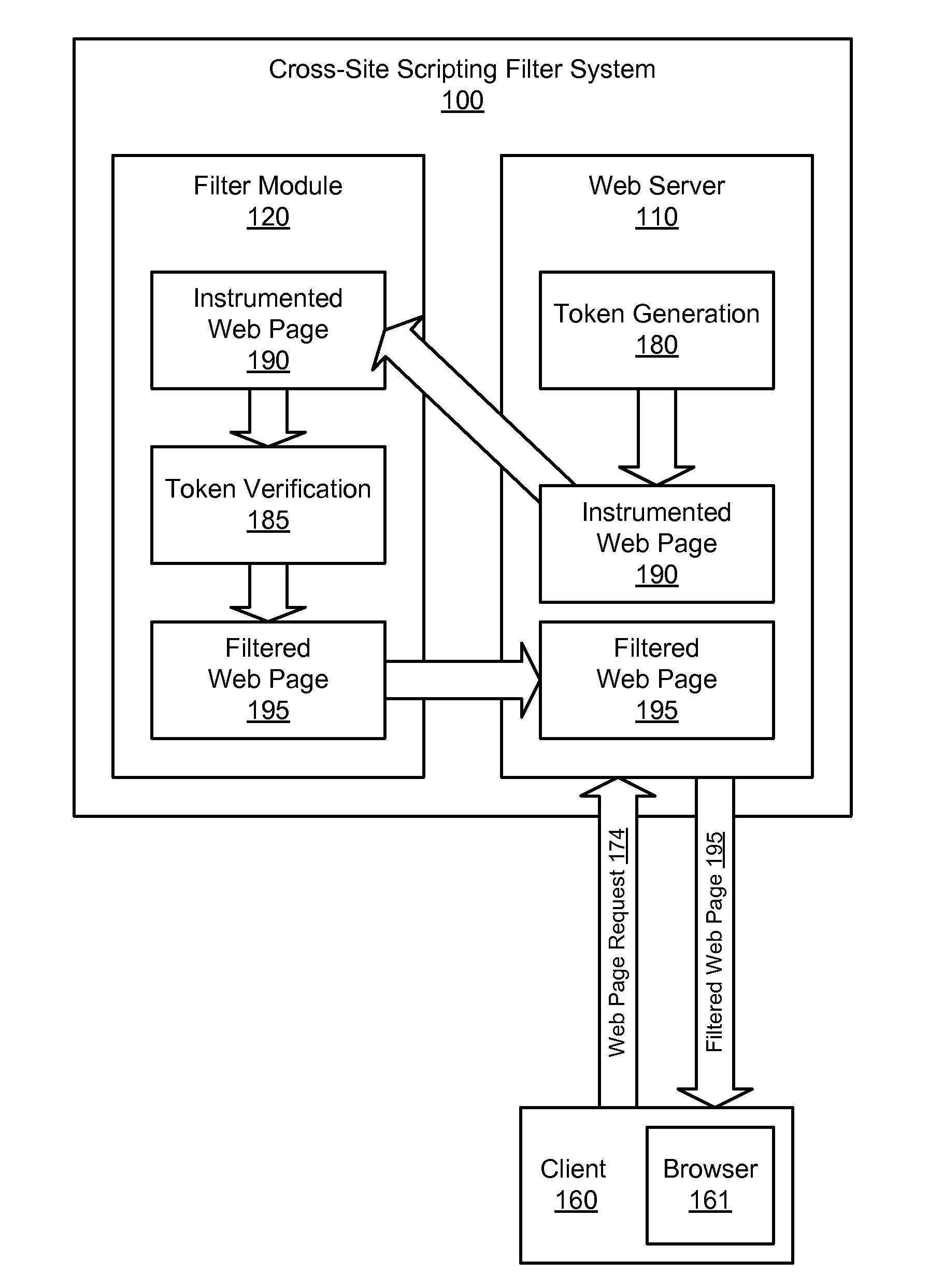
Protecting websites from cross-site scripting
Methods and systems for protecting websites from cross-site scripting are disclosed. A request for a web page comprising a web page element is received from a client. It is determined if the web page comprises a data integrity token for the web page element. It is also determined if a value of the data integrity token matches an expected value. If the web page comprises the data integrity token and if the value matches the expected value, the web page comprising the web page element is sent to the client. If the web page does not comprise the data integrity token or if the value does not match the expected value, a protective operation is performed.
Owner:AMAZON TECH INC
Method for generating cross-site scripting attack
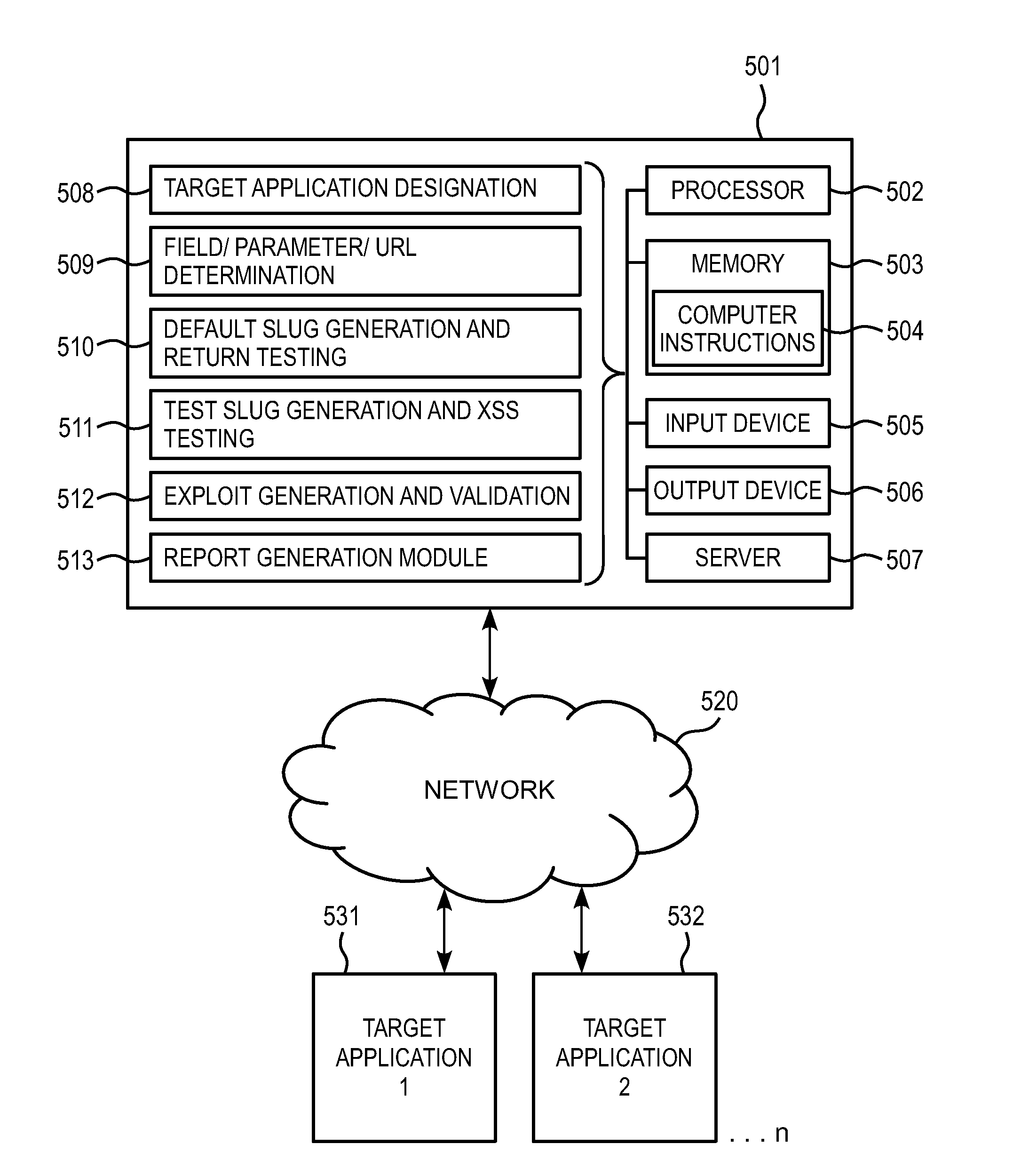
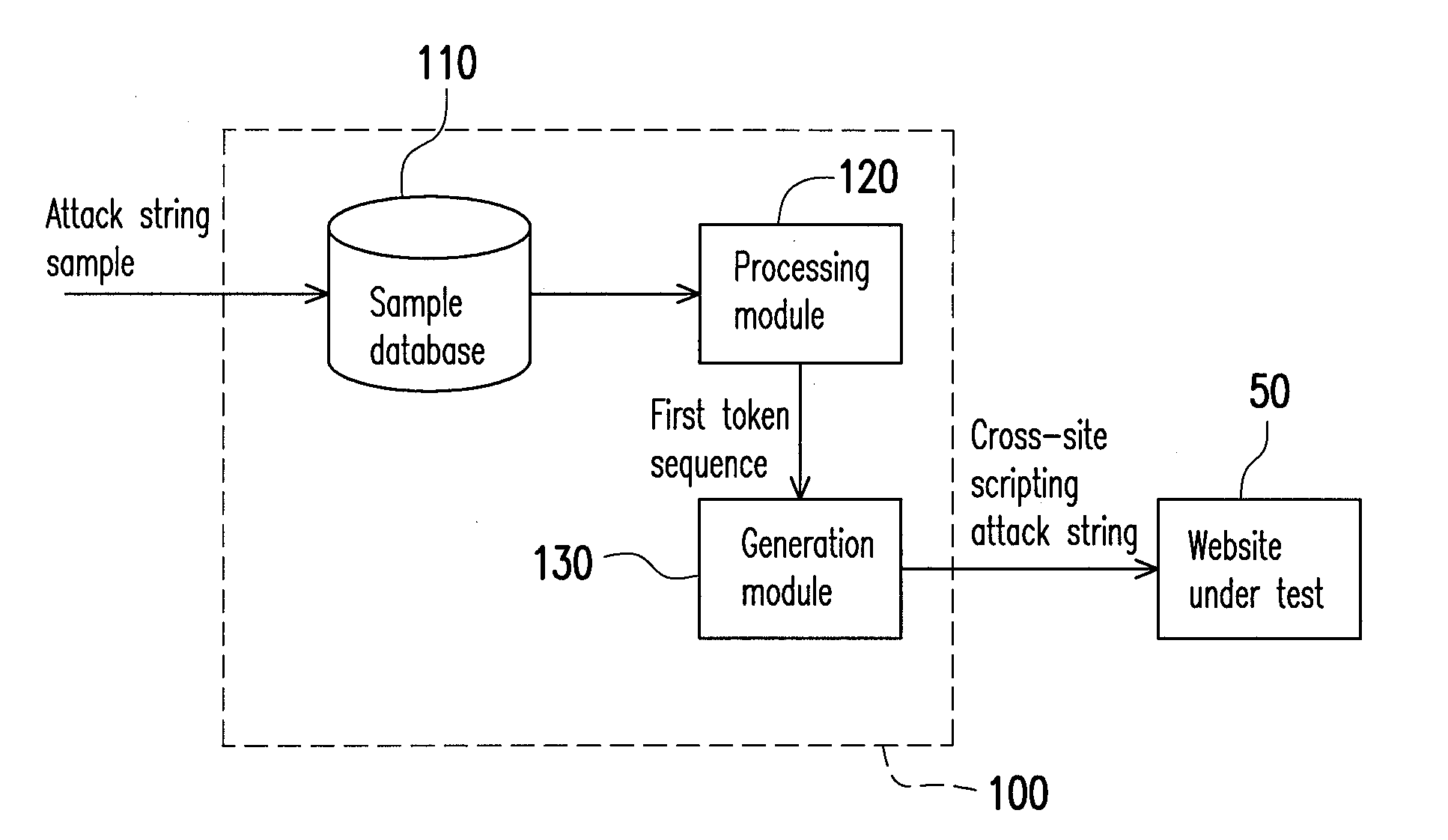
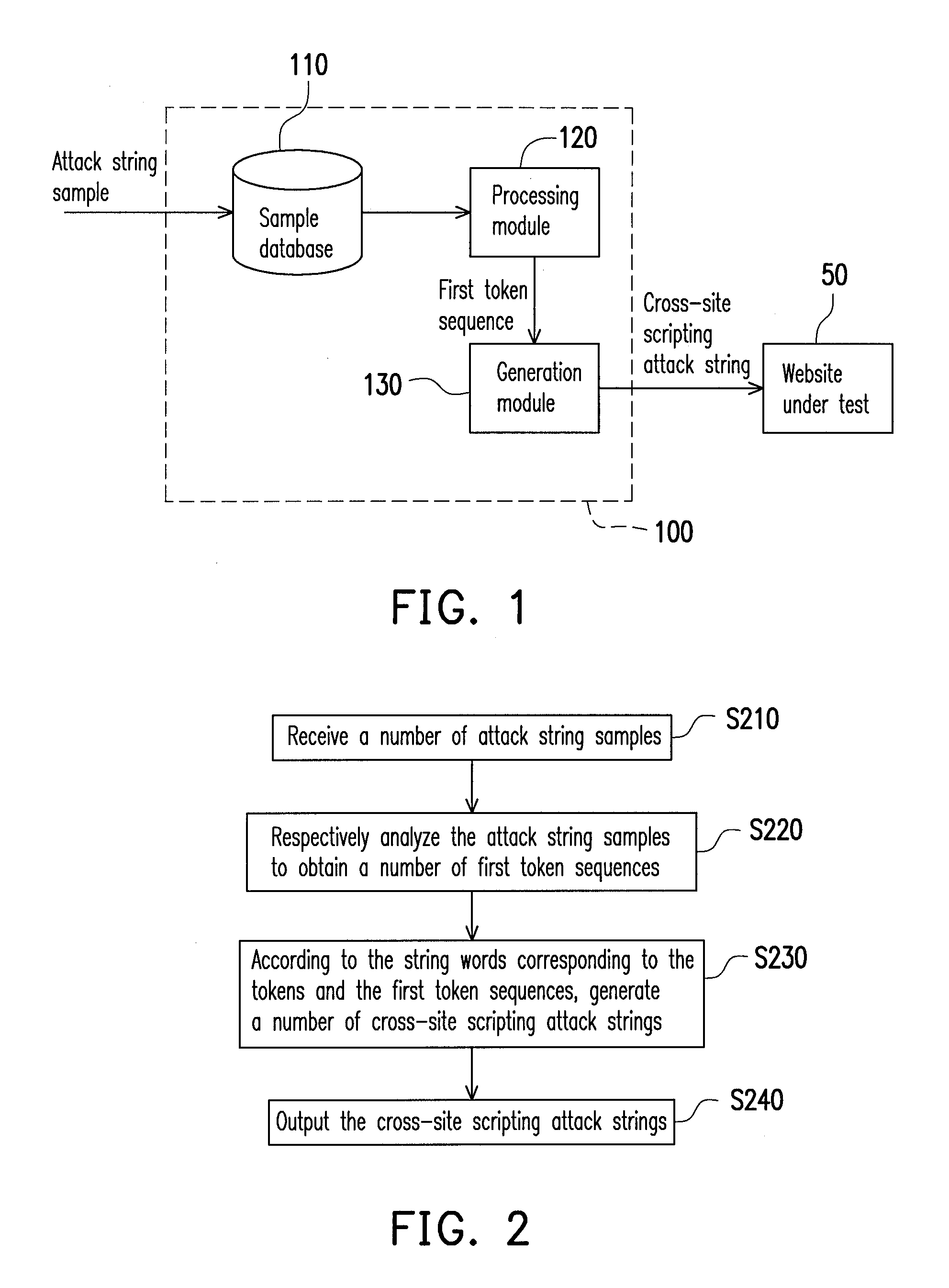
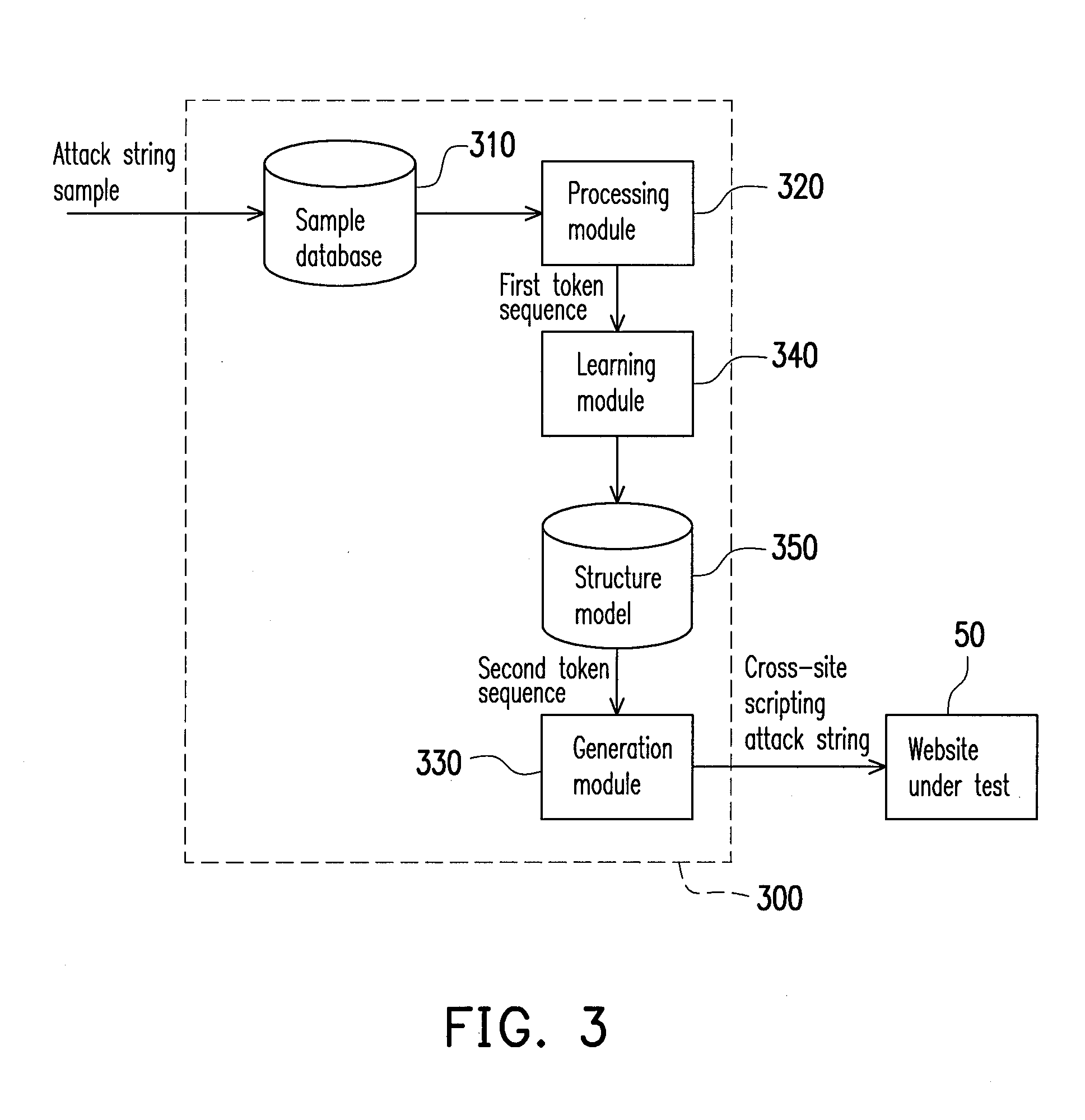
InactiveUS20130055400A1Improve abilitiesDetection technologyMemory loss protectionDigital data processing detailsPenetration testComputer security
A method for generating a cross-site scripting attack is provided. An attack string sample is analyzed for obtaining a token sequence. A string word corresponding to each token is used to replace the token for generating a cross-site scripting attack string. Accordingly, a large number of cross-site scripting attacks are generated automatically, so as to execute a penetration test for a website.
Owner:NAT TAIWAN UNIV OF SCI & TECH
Method and Apparatus for Serving Content Elements of a Markup Language Document Protected Against Cross-Site Scripting Attack
ActiveUS20110289556A1Protected contentDigital data processing detailsMultiple digital computer combinationsDomain nameWeb application
A web application decomposed into one or more domain sandboxes ensures that the contents of each sandbox are protected from attacks on the web application outside that sandbox. Sandboxing is achieved on a per-element basis by identifying content that should be put under protection, generating a secure domain name for the identified content, and replacing the identified content with a unique reference (e.g., an iframe) to the generated secure domain. The identified content is then served only from the generated secure domain using a content handler.
Owner:IBM CORP
Methods and systems for scripting defense
ActiveUS8931084B1Avoid loopholesKey distribution for secure communicationMemory loss protectionWorld Wide WebIntegrity check
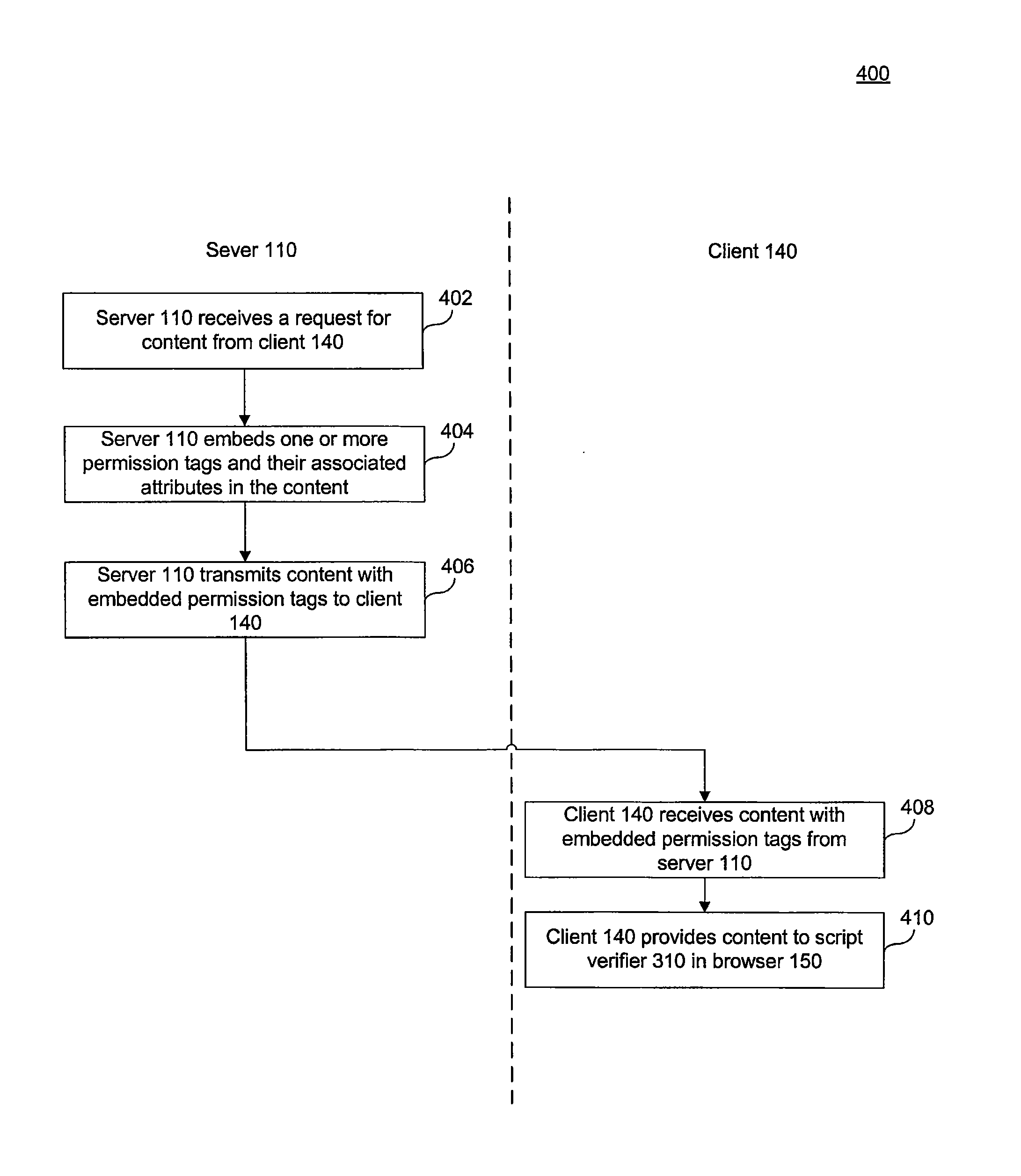
Methods and systems for cross-site scripting (XSS) defense are described herein. An embodiment includes, embedding one or more tags in content at a server to identify executable and non-executable regions in the content and transmitting the content with the tags to a client based on a request from the client. Another embodiment includes receiving content embedded with one or more permission tags from a server, processing the content and the permission tags, and granting permission to a browser to execute executable content in the content based on the permission tags. A method embodiment also includes receiving content embedded with one or more verify tags from a server, performing an integrity check using the verify tags and granting permission to a browser to execute executable content in the content based on the integrity check.
Owner:GOOGLE LLC
Method and system for detecting cross-site scripting attack injection
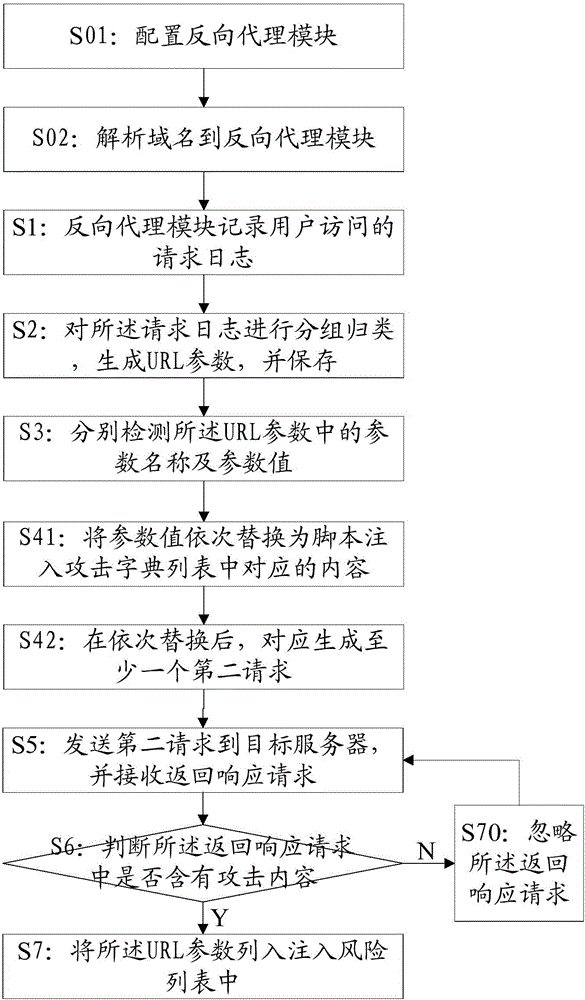
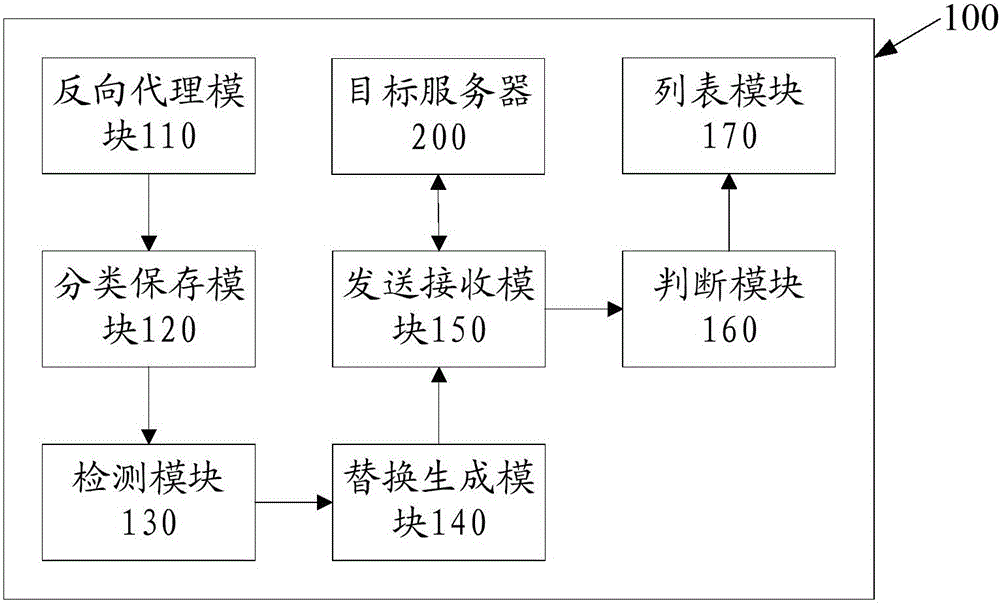
ActiveCN105049440AComprehensive detectionReduce the risk of being attackedTransmissionReverse proxyUniform resource locator
The invention discloses a method and a system for detecting cross-site scripting attack injection. The method comprises the following steps: recording request logs of user access by a reverse proxy module; grouping and classifying the request logs, and generate and saving a URL parameter; detecting a parameter name and a parameter value in the URL parameter, respectively; replacing the parameter value with corresponding content in a scripting injection attack dictionary list and generating a second request; sending a second request to a target server and receiving a response return request; judging whether the response return request contains attack content, and if so, adding the URL parameter to an injection risk list. In the way, the method for detecting the cross-site scripting attack injection is capable of detecting XSS bugs in a website more comprehensively, reducing the risk of attacks to users and improving the security of the website; besides, the URL detected by use of the method is more complete than the URL detected in a crawler way.
Owner:FUJIAN TQ DIGITAL
Cross-site scripting vulnerability detection method and device based on file object model
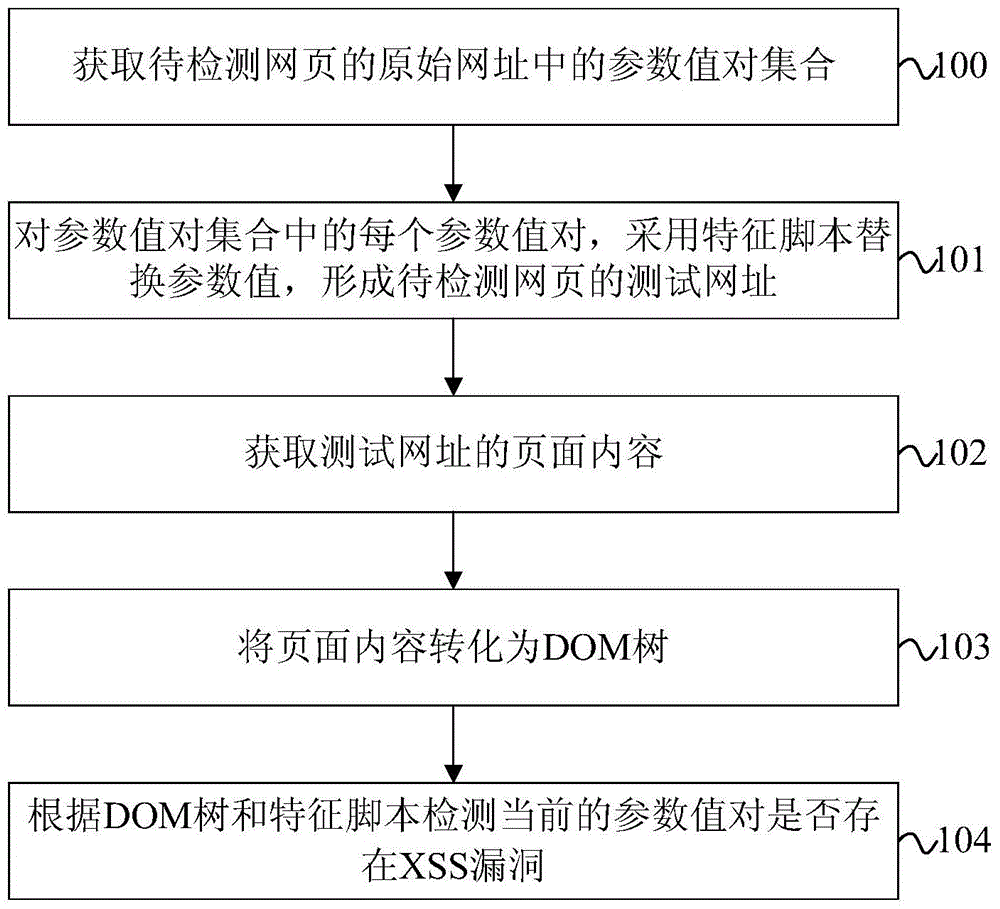
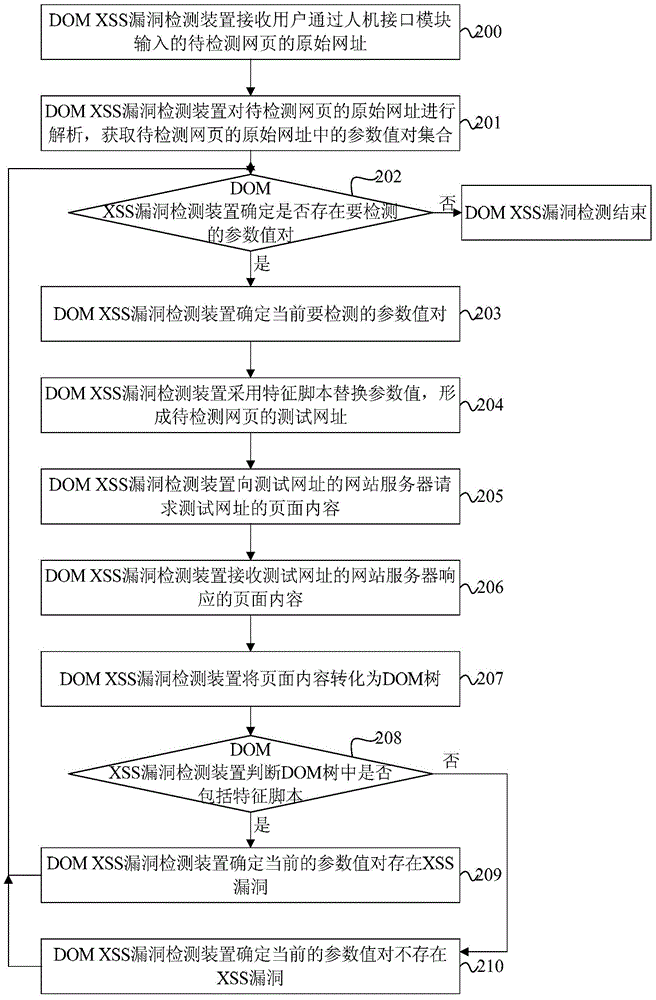
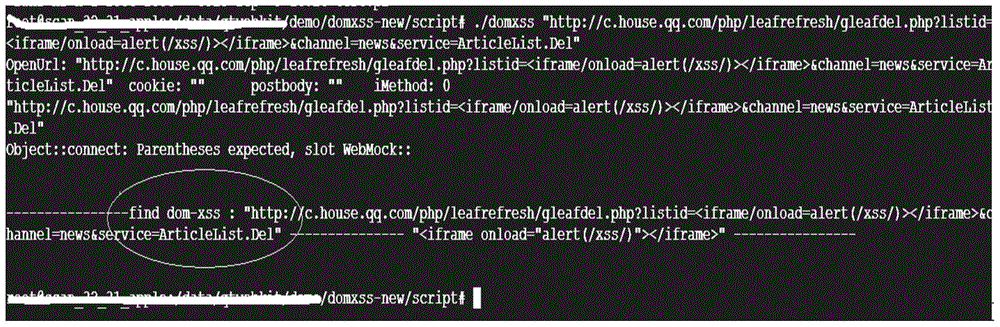
ActiveCN104636664AEfficient discoveryImprove vulnerability discovery capabilitiesPlatform integrity maintainancePattern recognitionDocumentation
Disclosed are a method, apparatus, and terminal for detecting a document object model-based cross-site scripting attack vulnerability. The method comprises: obtaining a set of parameter value pairs in the original URL of a webpage, the set of parameter value pairs including at least one parameter value pair; replacing parameter values of the parameter pairs with a feature script to form a test URL of the webpage, the feature script being malicious codes that contain malicious characters and can be uniquely identified in a document object model tree of the webpage; obtaining the page content corresponding to the test URL; converting the page content into the document object model tree; and detecting whether the cross-site scripting attack vulnerabilities are in the parameter value pairs according to the document object model tree and the feature script. By using the above solution, DOM XSS vulnerabilities can be effectively found only through searching the inserted feature script in the converted DOM tree and without triggering the execution of the feature script, thus greatly improving the ability of vulnerability discovery and the detection efficiency.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com