Cross-site scripting attack monitoring system and method
A cross-site scripting attack and monitoring system technology, applied in transmission systems, instruments, electrical digital data processing, etc., can solve the problems of account security collapse, high implementation costs, and inability to automatically prevent attacks, achieving good monitoring effects and high coverage. , apply the effect of high matching degree
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The specific embodiments of the present application will be described in further detail below based on the accompanying drawings. It should be understood that the specific embodiments described here are merely examples, and are not intended to limit the protection scope of the present application.
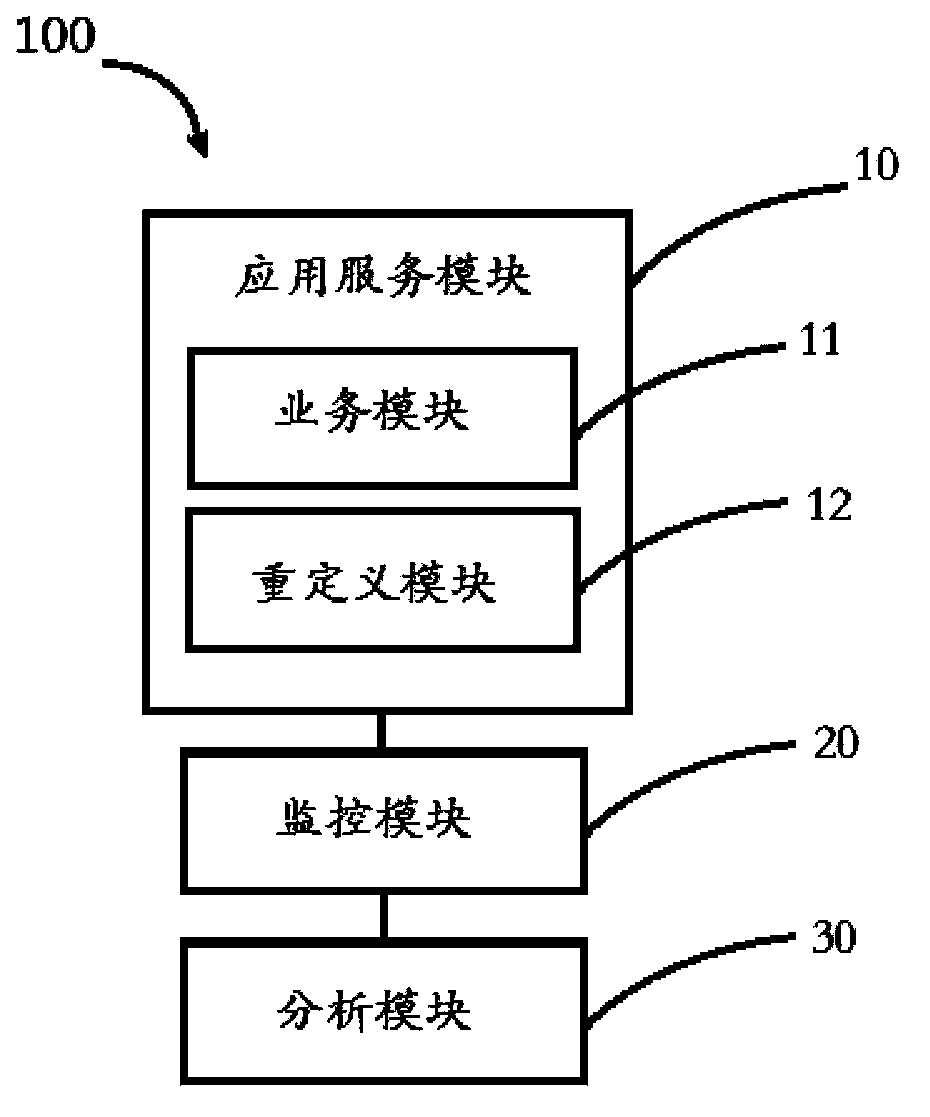
[0027] see figure 1 , is the cross-site scripting attack monitoring system 100 provided in the embodiment of the present application.
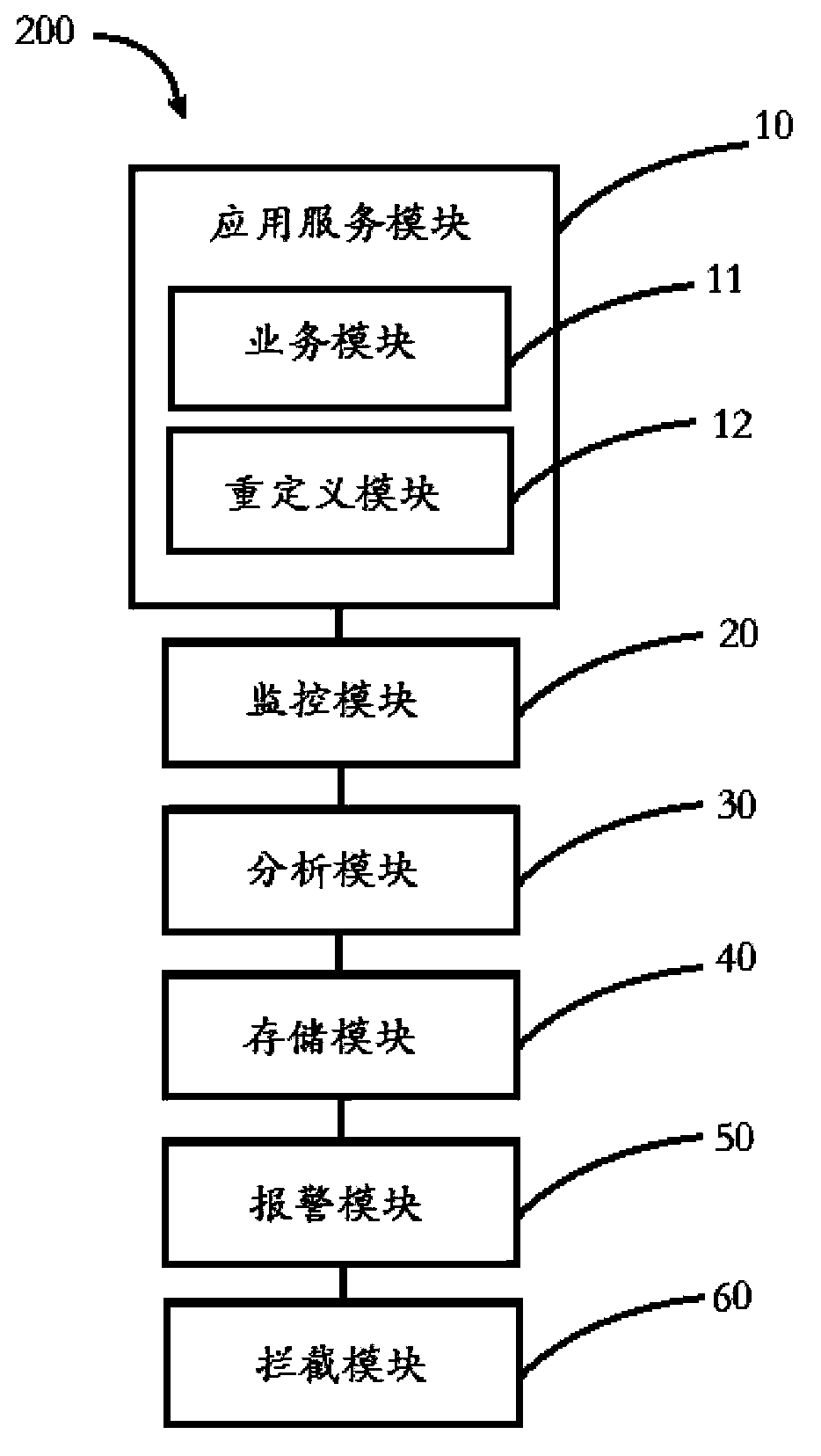
[0028] The cross-site scripting attack monitoring system 100 includes an application service module 10 , a monitoring module 20 and an analysis module 30 .
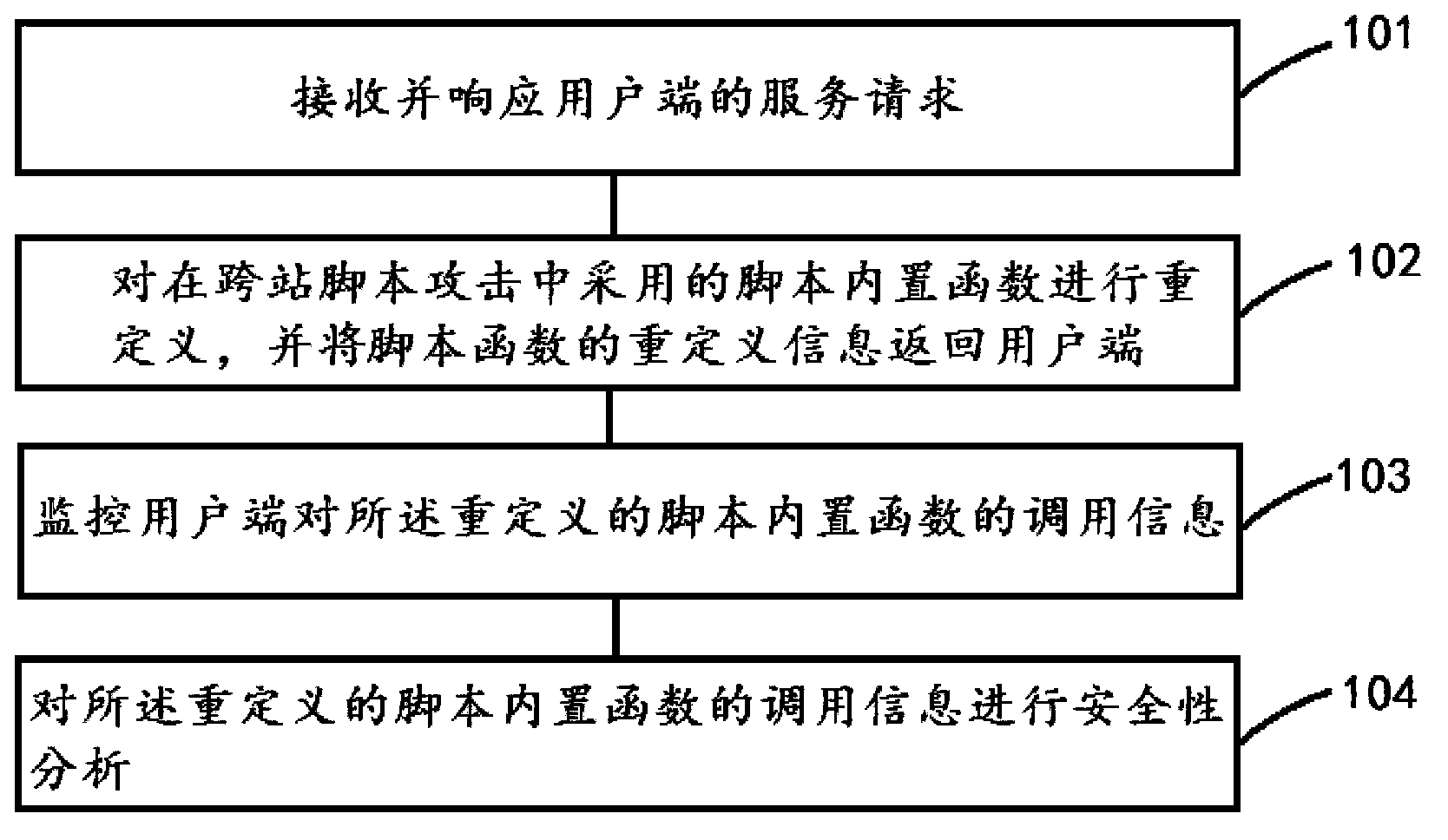
[0029] The application service module 10 includes a business module 11 and a redefinition module 12 . The service module 11 receives the service request from the client 60 and responds to the service request. The redefinition module 12 determines script built-in functions commonly used in cross-site scripting attacks, and redefines them.
[0030] The script built-in functions are bu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com