System for detecting software bug triggered during practical running of computer program
A computer program and actual operation technology, applied in the field of detection systems that trigger software vulnerabilities, can solve problems such as failure to detect vulnerabilities, inability to directly analyze binary codes, large time and system resource overhead, etc., to improve software vulnerabilities and vulnerabilities Possibility, high program executable path coverage, and the effect of reducing resource and time overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] The embodiments of the present invention will be described in detail below with reference to the accompanying drawings. This embodiment is implemented on the premise of the technical solution of the present invention. Detailed implementation modes and specific operation procedures are given, but the protection scope of the present invention is not limited to the following Mentioned examples.
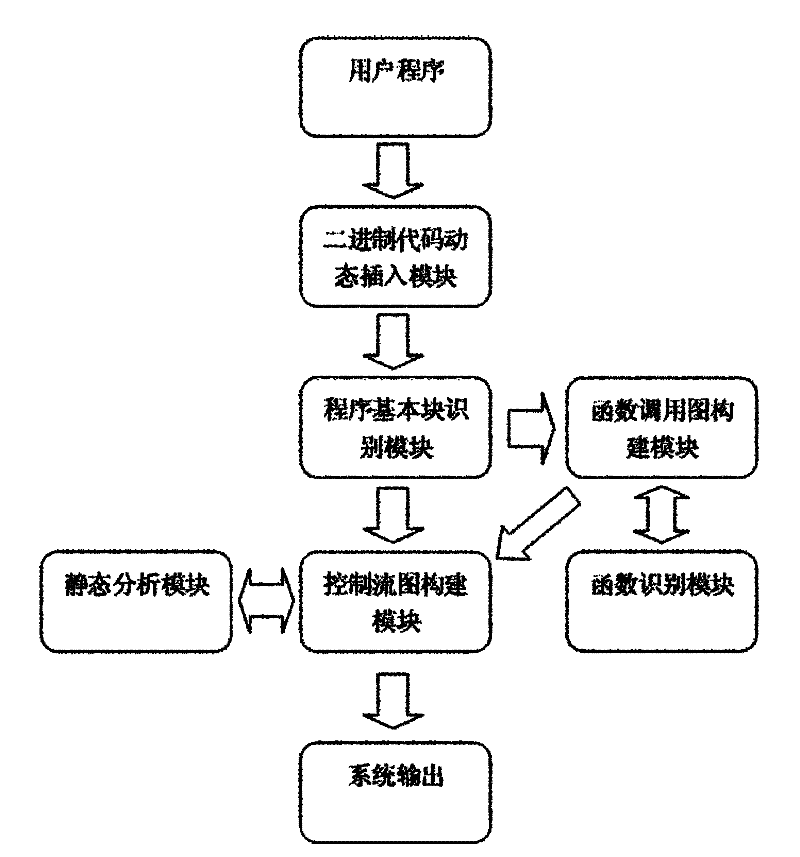
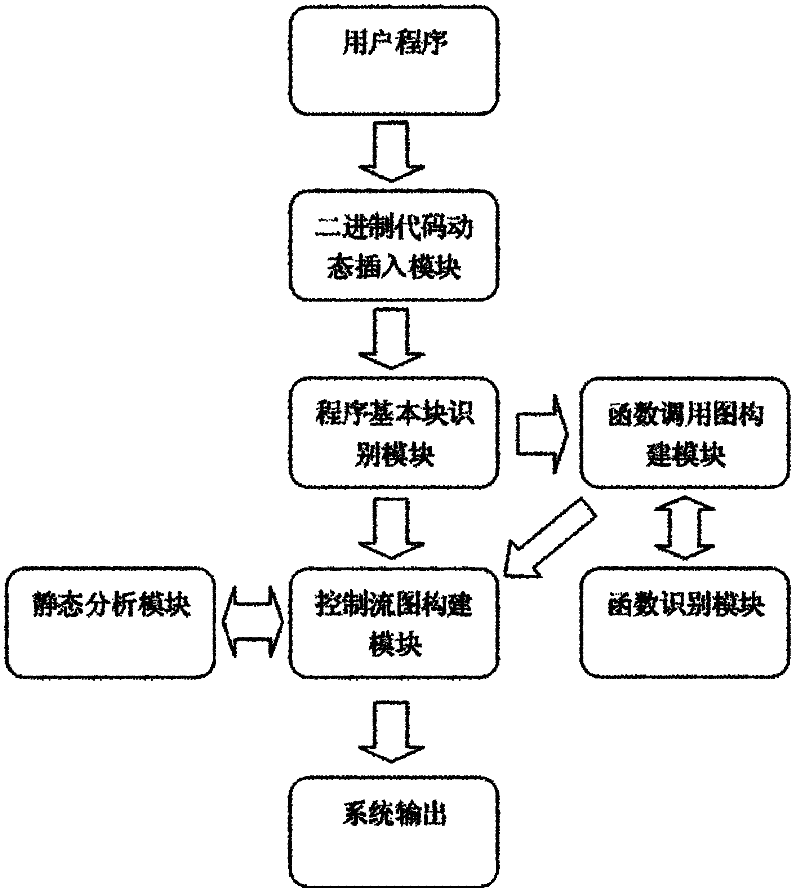
[0020] Such as figure 1 As shown, this embodiment includes: a binary code dynamic insertion module, a program basic block identification module, a function call graph building module, a control flow graph building module, a function identification module, and a static analysis module. The binary code dynamic insertion module can insert the user-defined analysis code into any position of the program, and track the system API called by the program, and finally return the analysis result through the callback function provided by the custom program analysis file and pass it to the program...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com