Shaping vulnerability detection method based on dynamic and static analysis
A vulnerability detection, dynamic and static technology, applied in the direction of platform integrity maintenance, instrumentation, electrical digital data processing, etc., can solve the problems affecting the detection of plastic vulnerability, the lack of dynamic detection tools for plastic vulnerability, and the lack of consideration of control flow dependencies, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
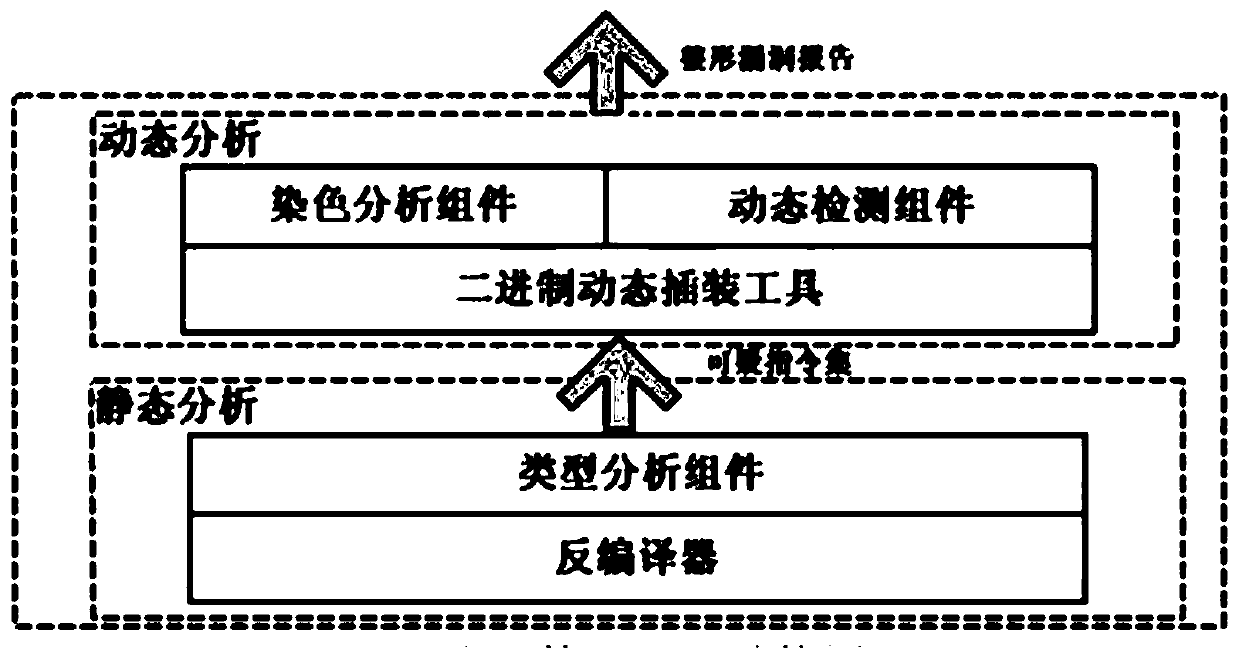
[0048] The method of the present invention proposes a binary tool consisting of static and dynamic analysis parts. First, the x86 binary program is converted into an intermediate language using LLVM. Then, by extending the type analysis system of LLVM, the complete type information is extracted, and the suspicious instruction set is constructed. Finally, combined with dynamic detection tools, the instructions related to vulnerabilities are determined in the suspicious instruction set.
[0049] like figure 2 Shown, in order to realize the above object, the present invention completes in three steps:
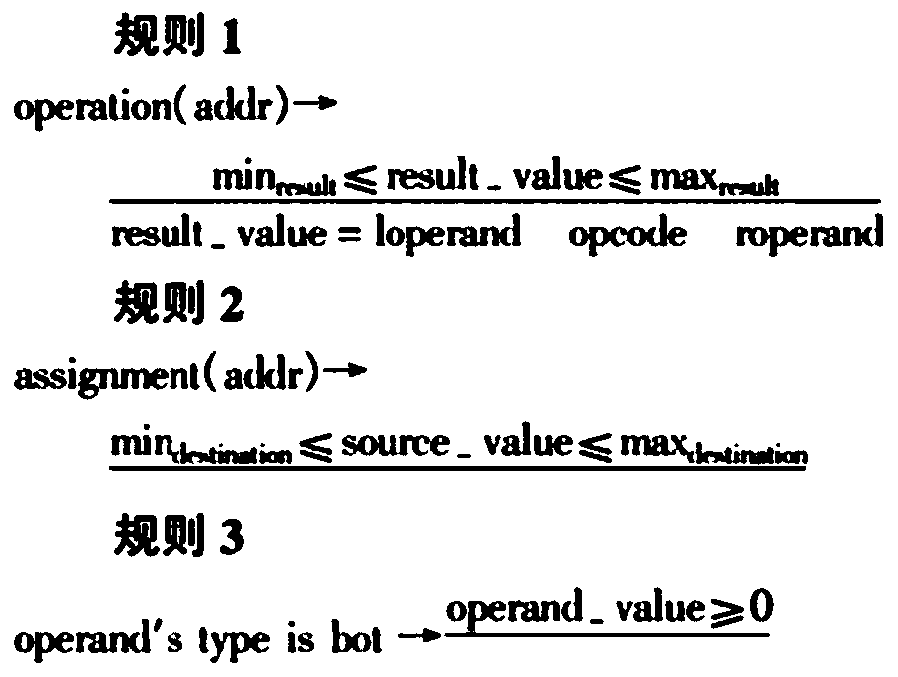
[0050] Step 1. Establish a plastic vulnerability model and describe the attributes related to the vulnerability;
[0051] Step 2, according to the vulnerability model, statically scan the code and analyze the suspicious instruction set;
[0052] Step 3, according to the vulnerability model, dynamically run the code to detect whether the instruction in the suspicious instructi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com