Software security loophole prediction method based on assembly dependence diagram
A technology for software security and prediction methods, applied in computer security devices, instruments, electrical digital data processing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
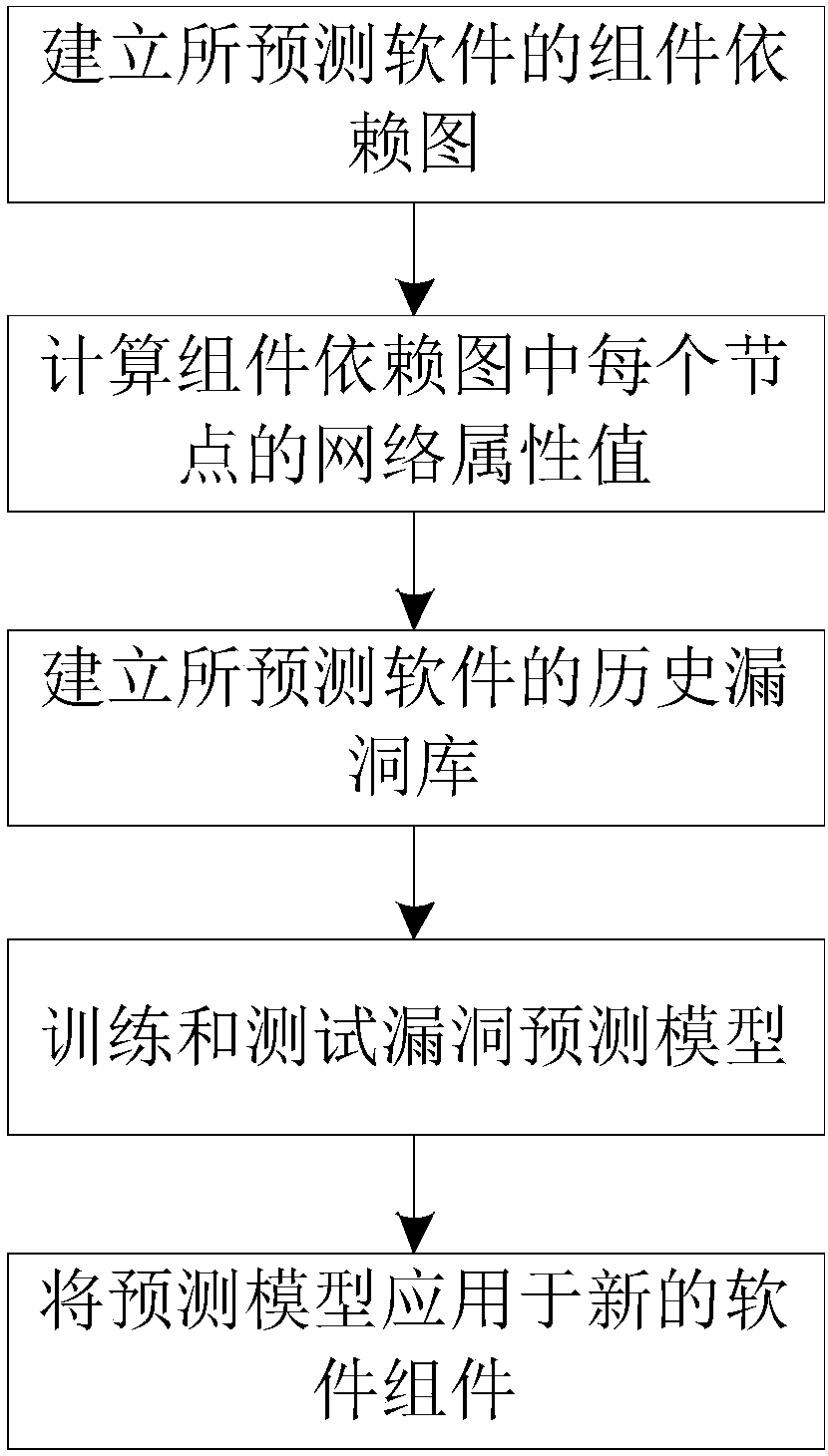
[0027] Taking the vulnerability prediction of the open source software project Firefox as an example, the vulnerability prediction process is given in detail below.
[0028] Step 1. Build the component dependency graph of the predicted software
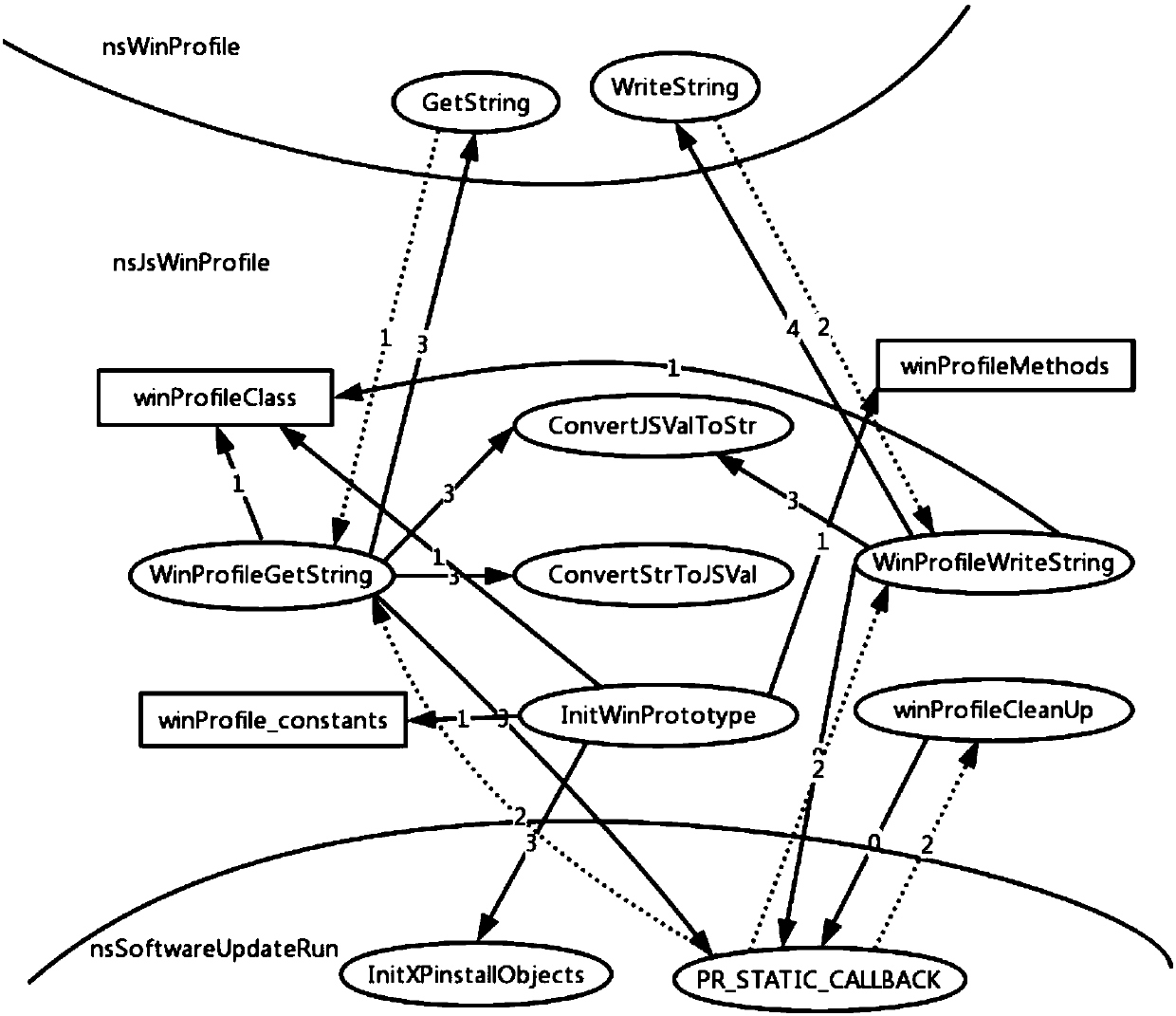
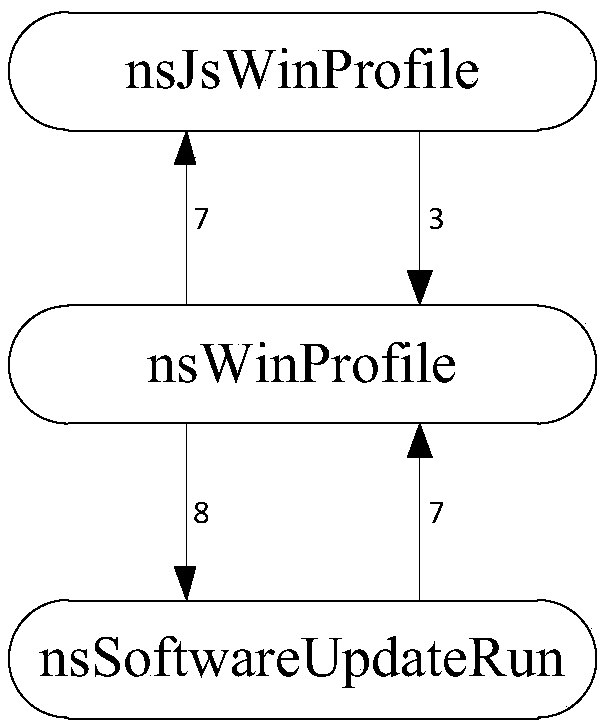
[0029] A software system can be viewed as a collection of components and their relationships. The connection between components is actually the connection between the members in the components, so the relationship between components is determined by the relationship between the members in the components. From a static point of view, a component's members include executable code and data items. The relationship between executable code and data items includes data reading and data writing, and the relationship between executable code and executable code includes function calling and function returning.
[0030] A component is a triplet CC , M C , R C >, where D C is a collection of shared variables or data members, M C is a collec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com