Safety neighbor discovering method, network appliance and mobile station
A neighbor discovery and network equipment technology, applied in the field of communication, can solve the problems of excessive occupation of network transmission resources, low efficiency of neighbor discovery, waste of air interface resources, etc., to achieve the effect of saving air interface resources, improving efficiency, and reducing transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
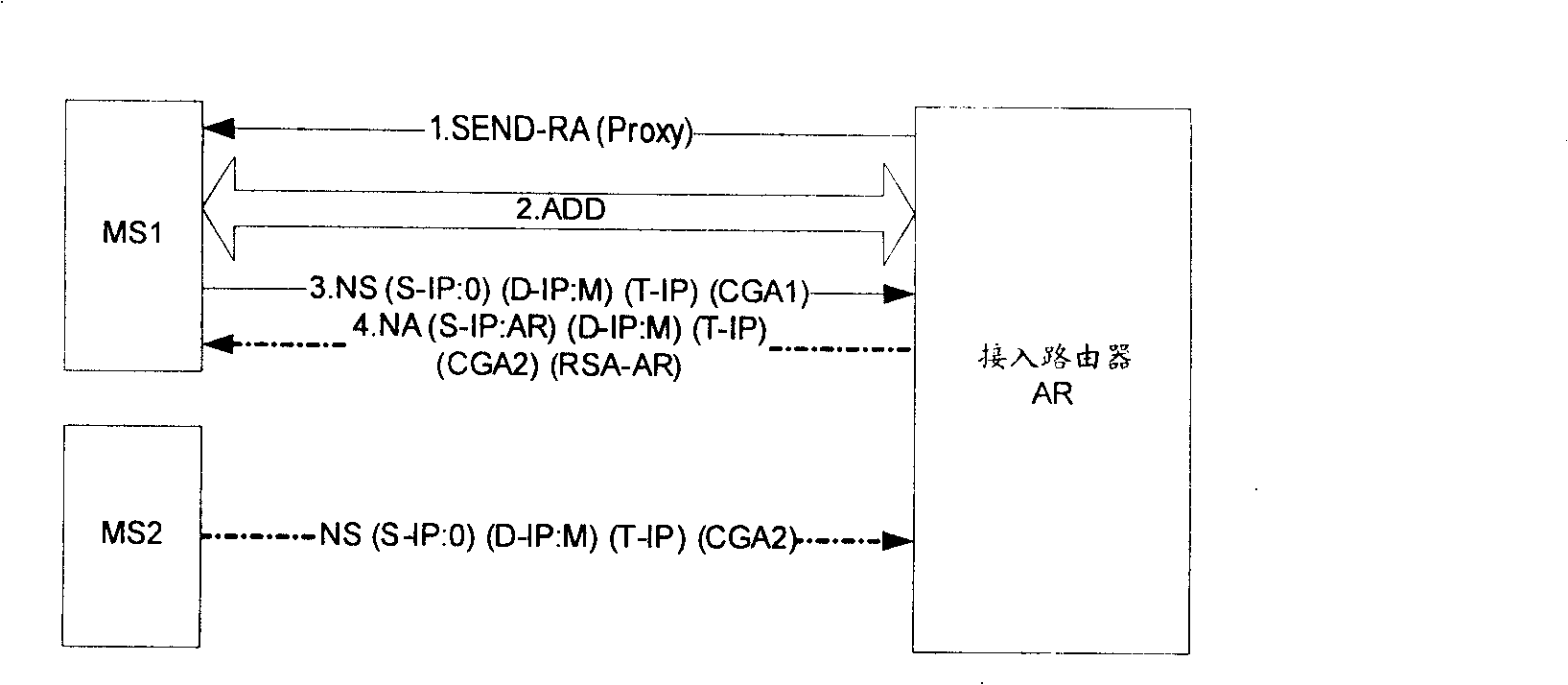
[0036] Implementation mode 1. The access router AR uses its own private key to reply to the NA message as an agent. The specific implementation process is as follows: figure 1 shown.
[0037] exist figure 1 In step 1, the access router AR sends an RA (Router Advertisement) message, and the RA message carries indication information that the security agent of the access router AR replies to the NA message.
[0038] The RA message in step 1 can be constructed according to the description of RFC (Request For Comments, request for comments), and of course it can also be constructed using other protocols. When constructing the RA message described in the RFC, it is necessary to extend the RA message so that the RA message carries the indication information of the NA message replied by the AR security agent of the access router.
[0039] The RA message sent by the access router AR may not carry the above indication information, and the AR may carry the above indication information ...
Embodiment approach 2
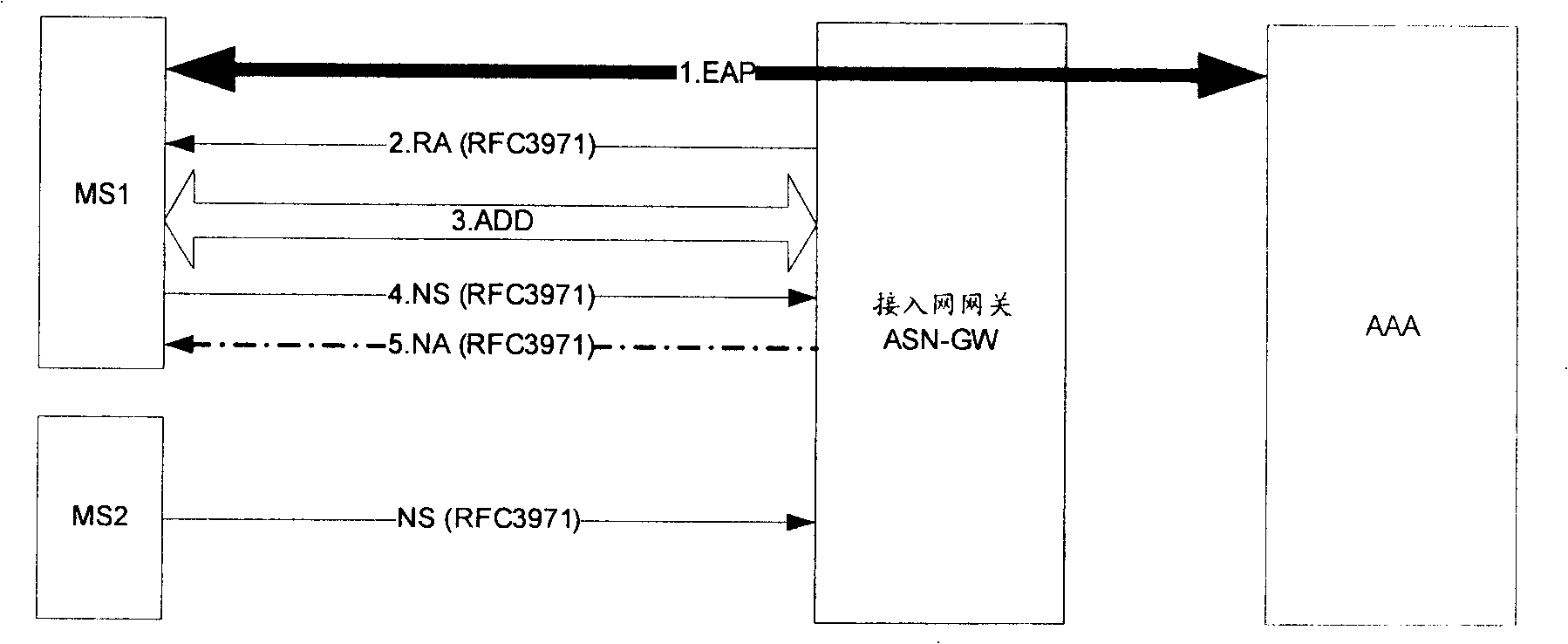
[0051] Embodiment 2. The access router AR uses the public key and private key of other mobile stations to send NA messages, and the MS uses the public keys of other mobile stations carried in the NA messages to verify the NA messages. The specific implementation process is as follows: figure 2 shown.
[0052] figure 2 In step 1, when MS1 accesses the network, an EAP (Extensible Authentication Protocol) process is required. During the EAP process, both MS1 and the access network gateway can obtain the public key used by MS1 for SEND (Secure Neighbor Discovery) and private key. For convenience of description, the public key used by MS1 for SEND is denoted as SEND-PuK, and the private key used by MS1 for SEND is denoted as SEND-PrK.
[0053] In step 1, there are many ways for MS1 and the access network gateway to obtain the public key and private key of MS1, and two methods for obtaining the public key and private key of MS1 are briefly introduced below.
[0054] Method 1....
Embodiment approach 3
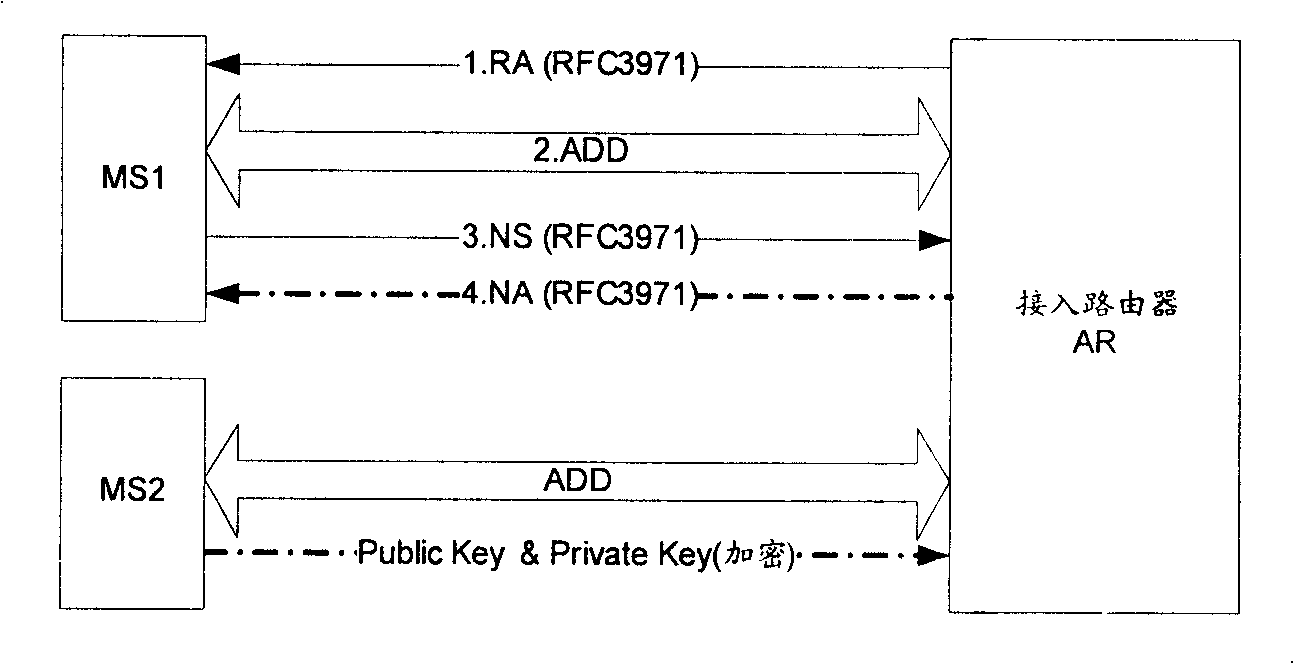
[0067] Embodiment 3: After the MS performs secure neighbor discovery, the MS sends its public key and private key to the access router AR. The access router AR obtains the public key and private key of each MS. In the process of secure neighbor discovery for a certain MS, if it needs to send NA message, it uses the public key and private key of the corresponding mobile station to send the NA message, and the MS uses Its public key authenticates NA messages. The specific implementation process is attached image 3 shown.
[0068] image 3 In step 1, the AR sends an RA message, and the RA message can be constructed according to the description of RFC3971.
[0069] In step 2, MS1 performs ADD verification after receiving the RA message, and the ADD verification process can be performed according to the description of the RFC.
[0070] In step 3, MS1 processes the RA message sent by the access router AR after passing the ADD verification of the access router AR. MS1 can refer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com