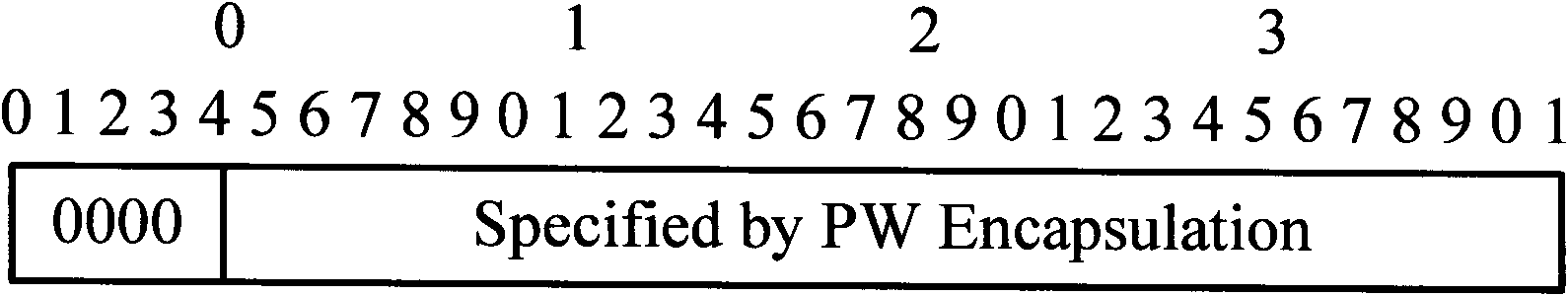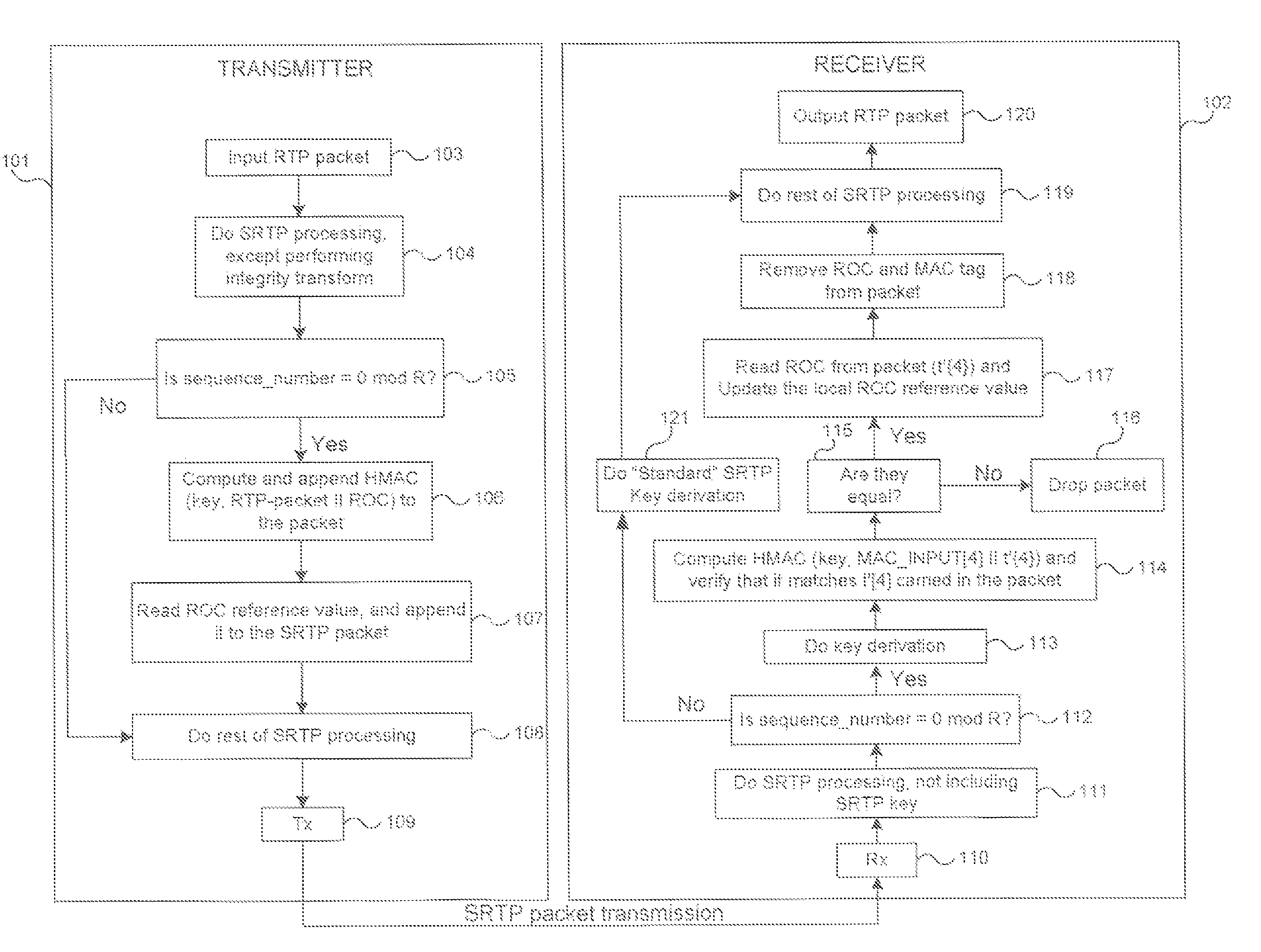Patents
Literature
37 results about "Request for Comments" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Request for Comments (RFC), in information and communications technology, is a type of text document from the technology community. An RFC document may come from many bodies including from the Internet Engineering Task Force (IETF), the Internet Research Task Force (IRTF), the Internet Architecture Board (IAB), or from independent authors. The RFC system is supported by the Internet Society (ISOC).
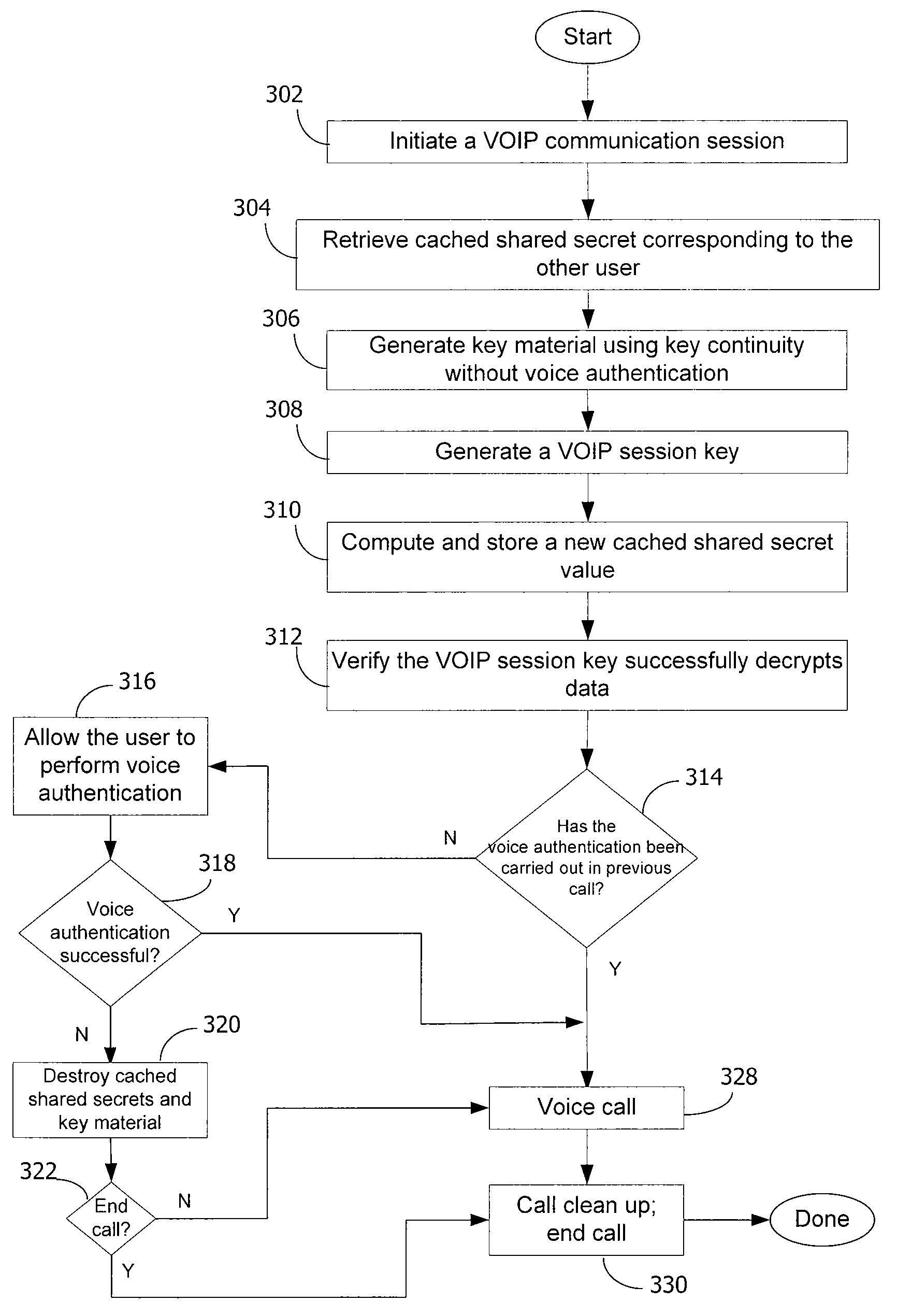
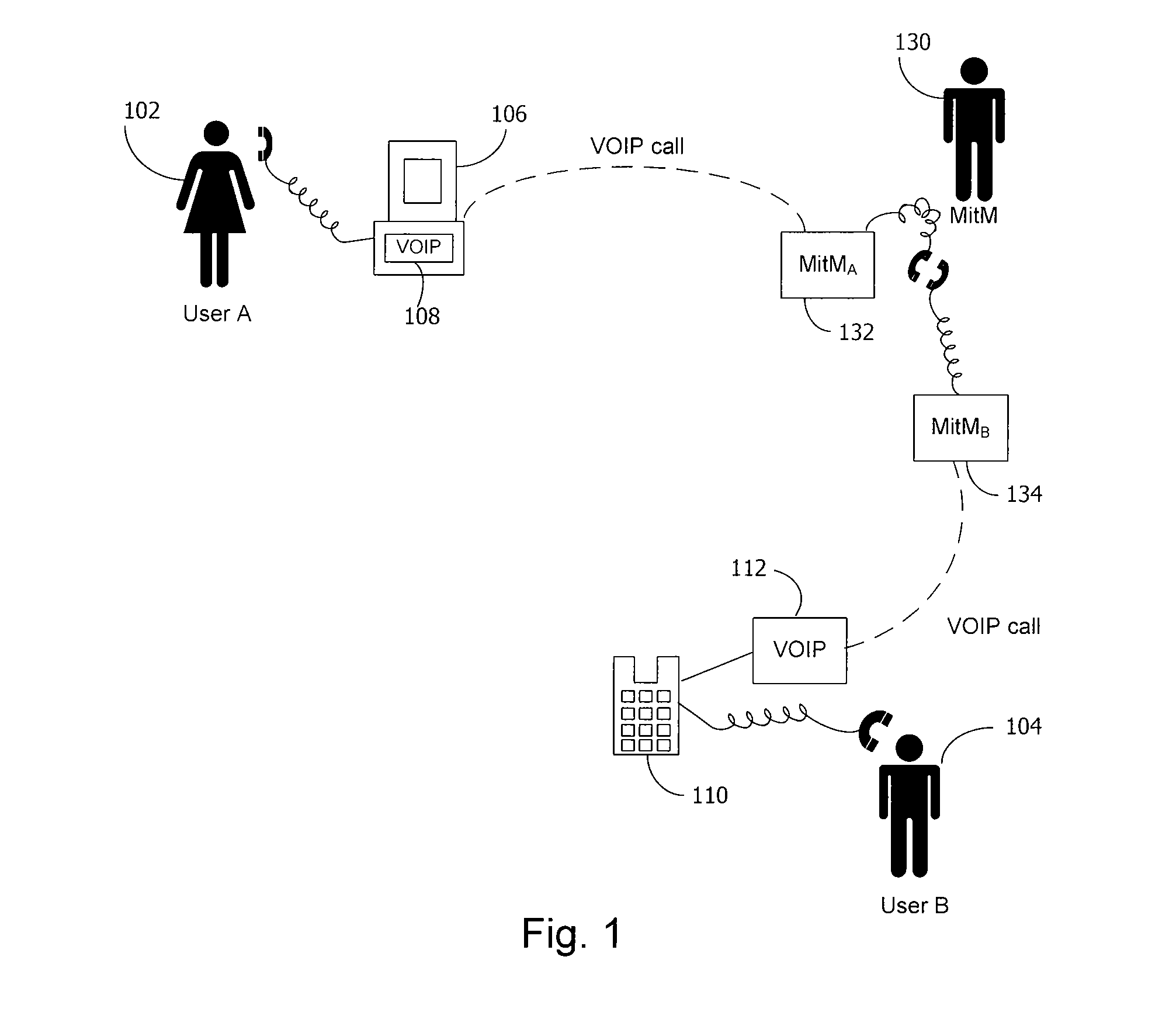
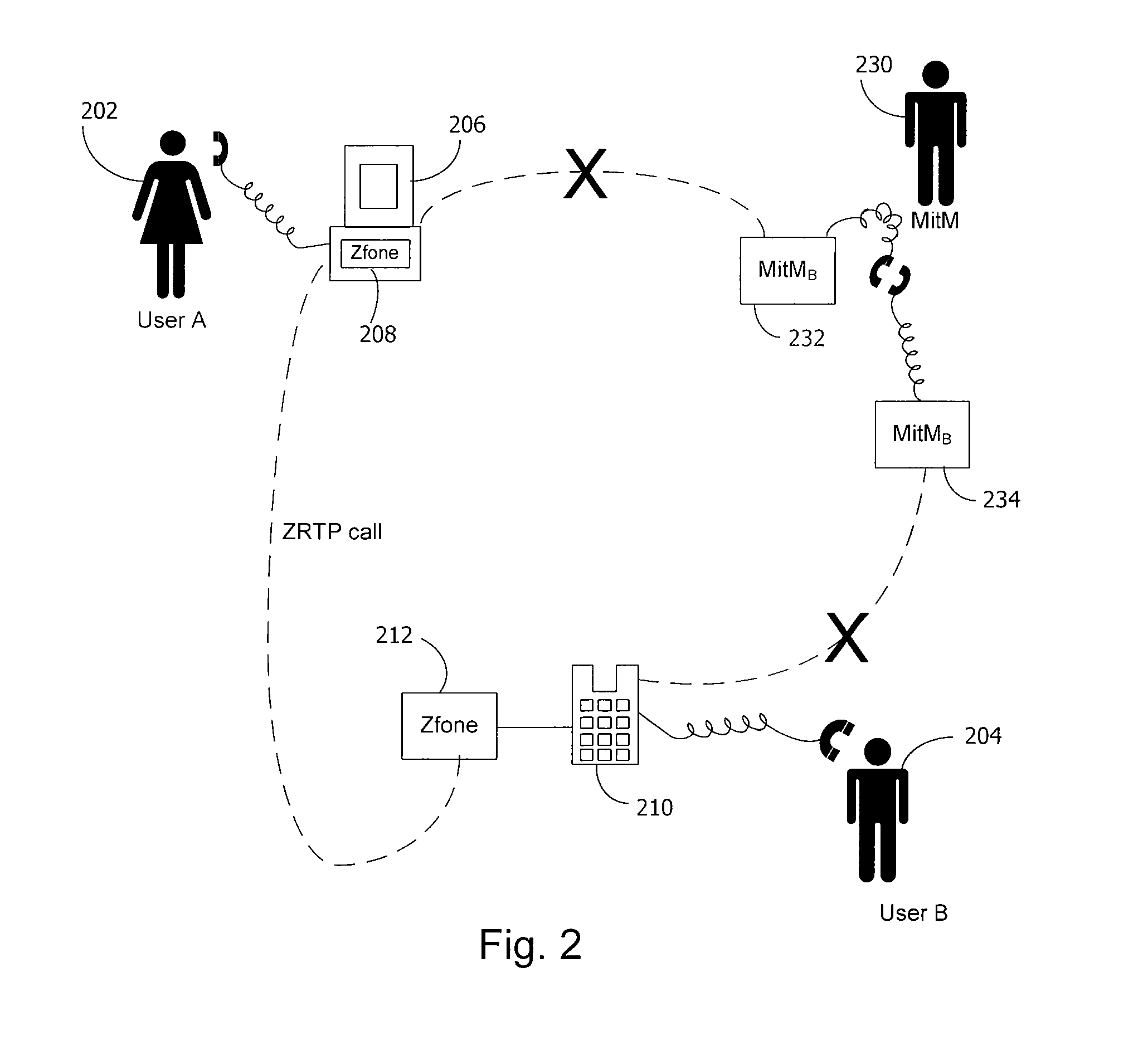
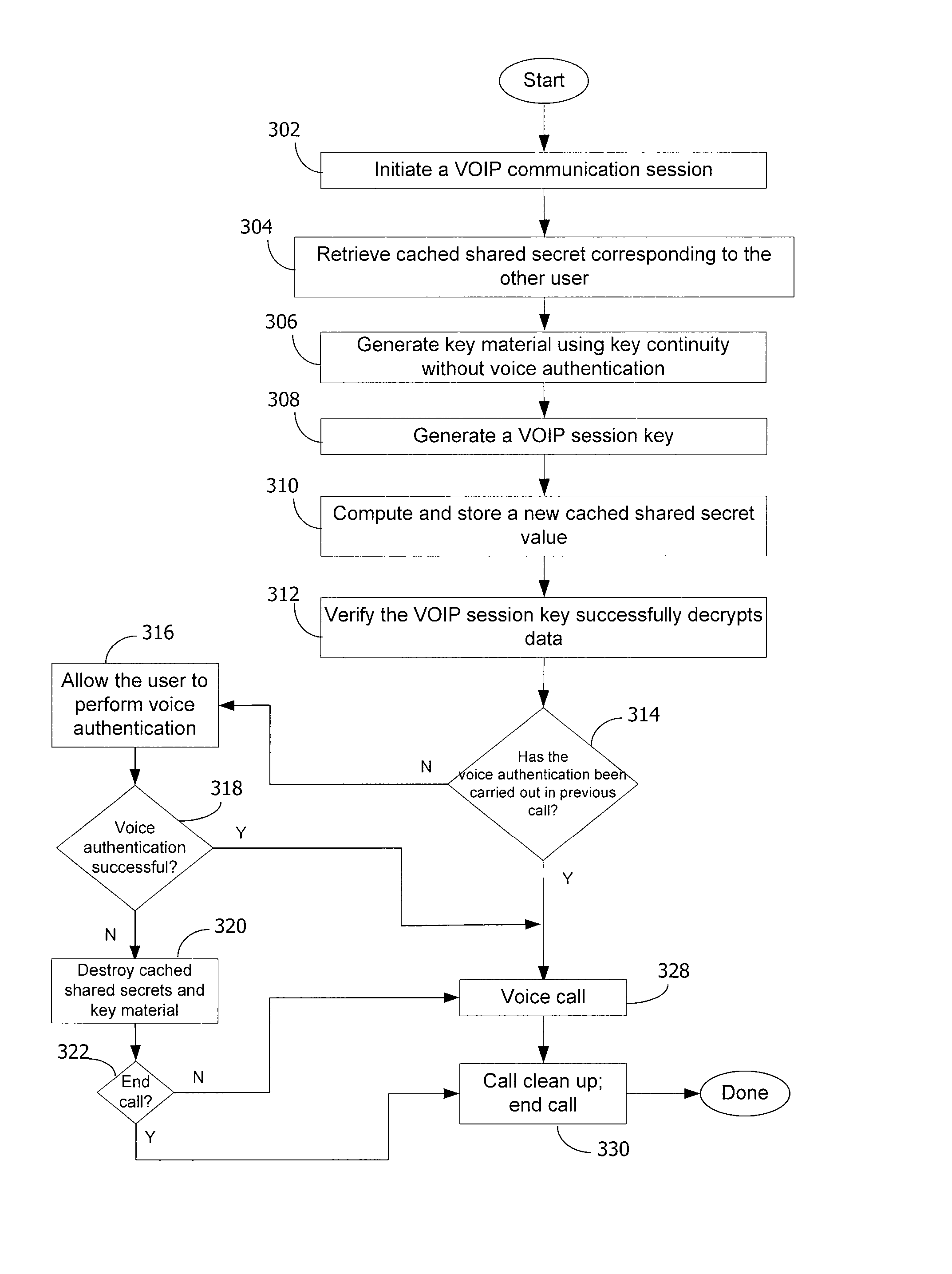
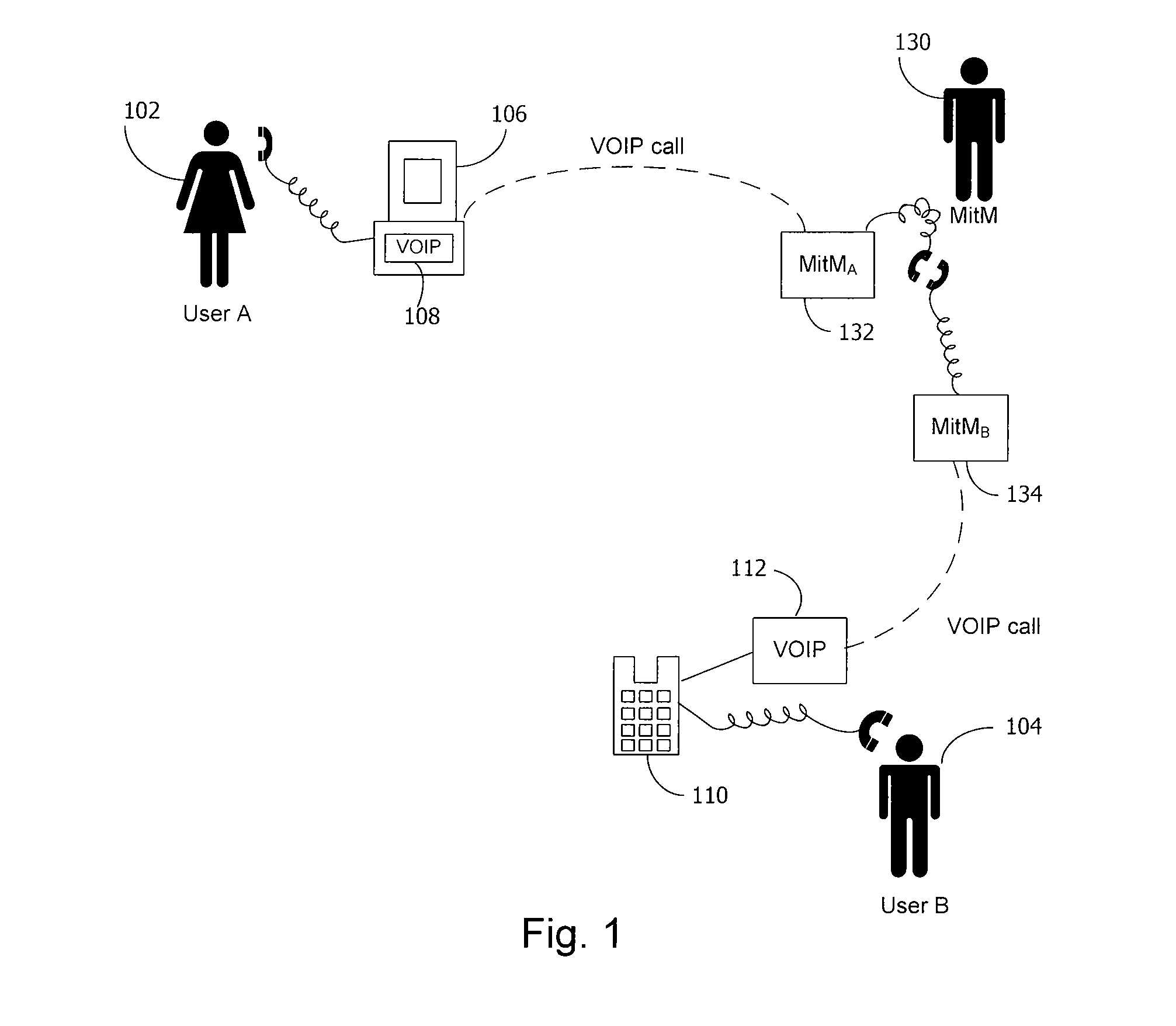
Method and system for key management in voice over internet protocol
InactiveUS7730309B2Eliminate needEasy to implementKey distribution for secure communicationUnauthorised/fraudulent call preventionSession Initiation ProtocolDiffie–Hellman key exchange
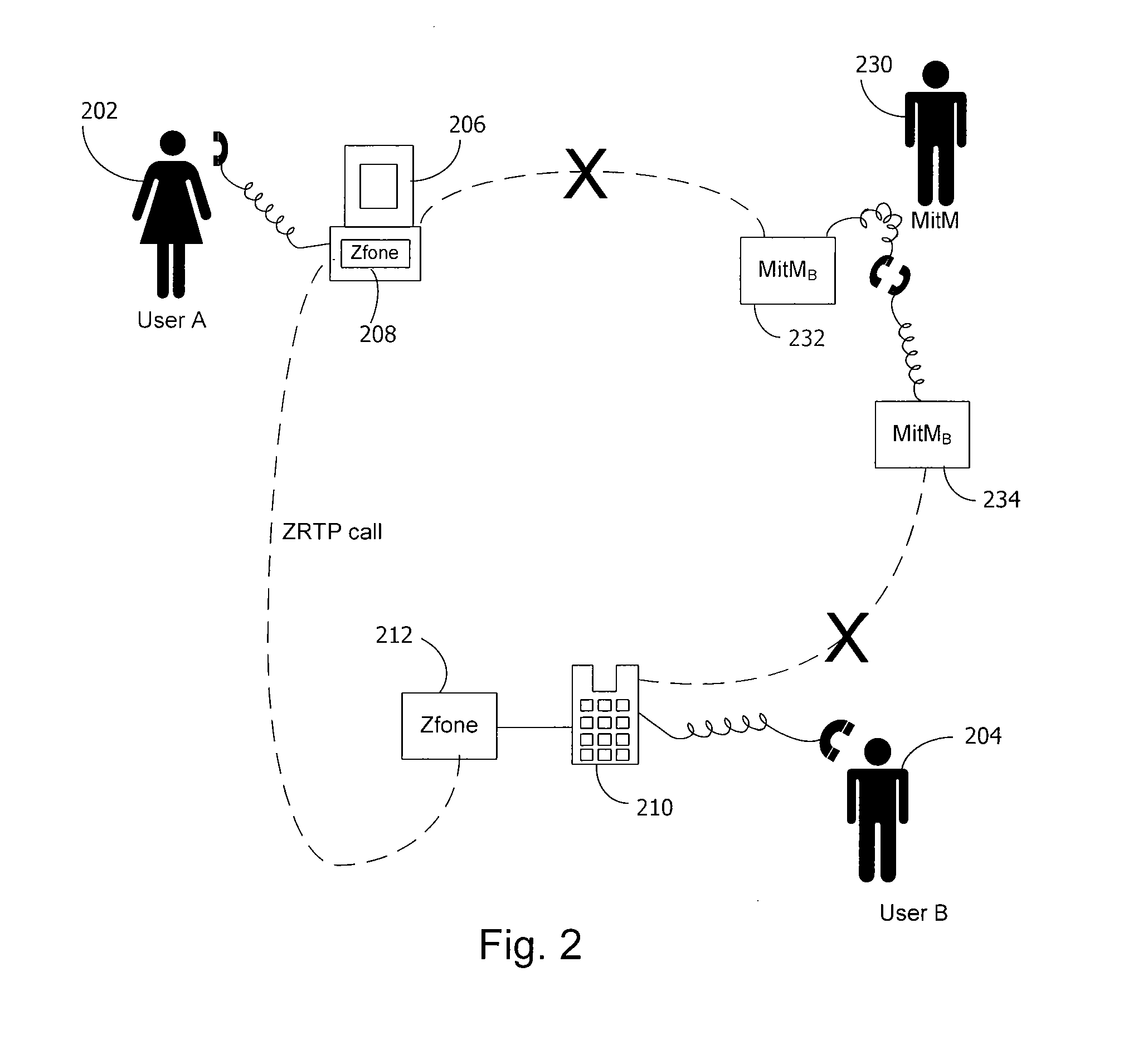
A method and system for a secure telephone protocol are disclosed, which can be implemented using current Voice over IP (VoIP) protocols, Session Initiation Protocol (SIP, as specified in the Request for Comment (RFC) 3261 from the Internet Engineering Task Force (IETF)), Real Time Transport Protocol (RTP, as specified in RFC 3550), and Secure RTP (SRTP, as specified in RFC 3711). The secure telephone protocol can include a shared secret value that is cached and then re-used later to authenticate a long series of session keys to be used for numerous separate secure phone calls over a long period of time, thereby providing cryptographic key continuity without the need for voice authentication. In an embodiment, the secure telephone protocol can utilize the Diffie-Hellman key exchange during call setup, and AES for encrypting the voice stream.
Owner:ZIMMERMANN PHILIP R
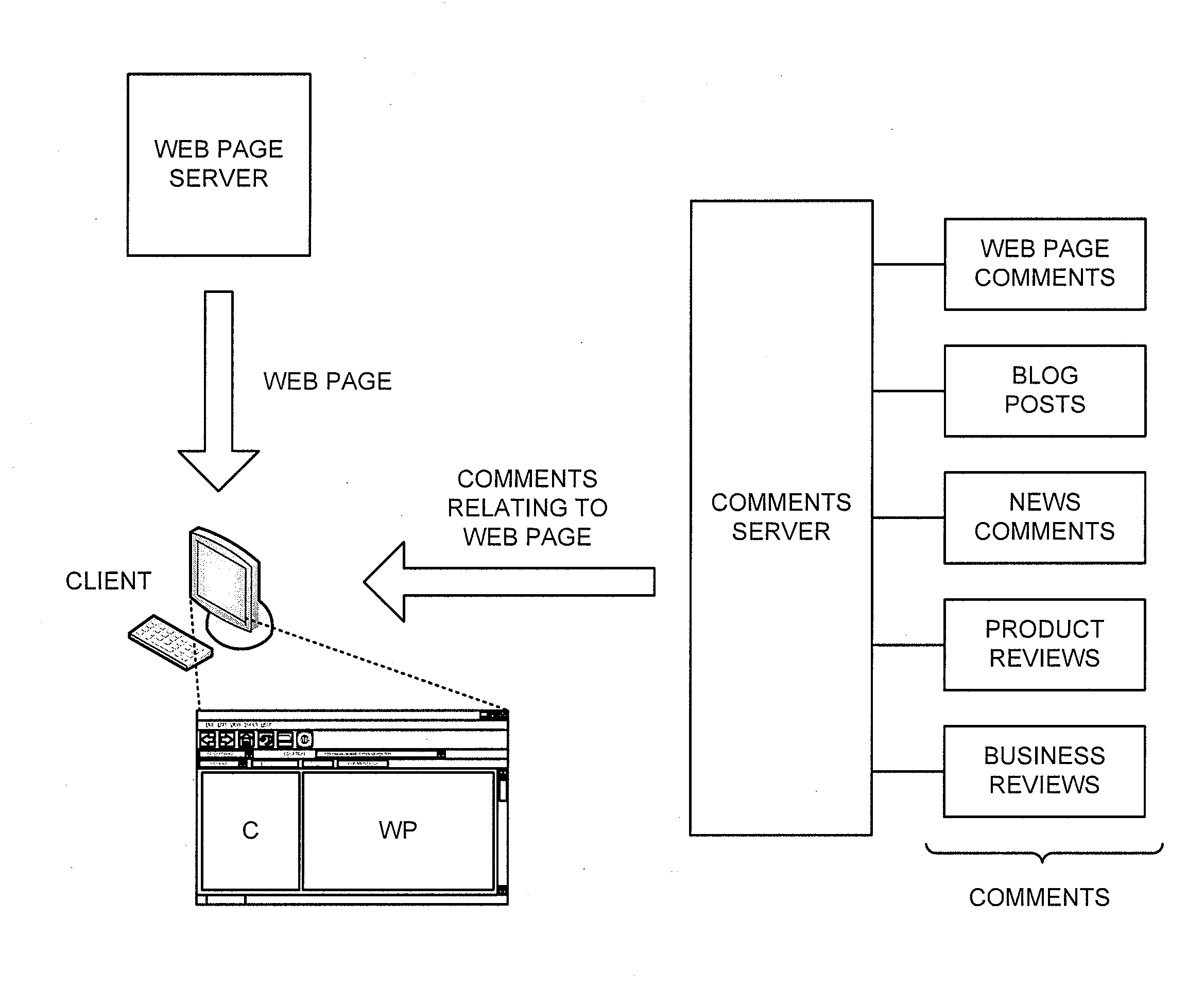
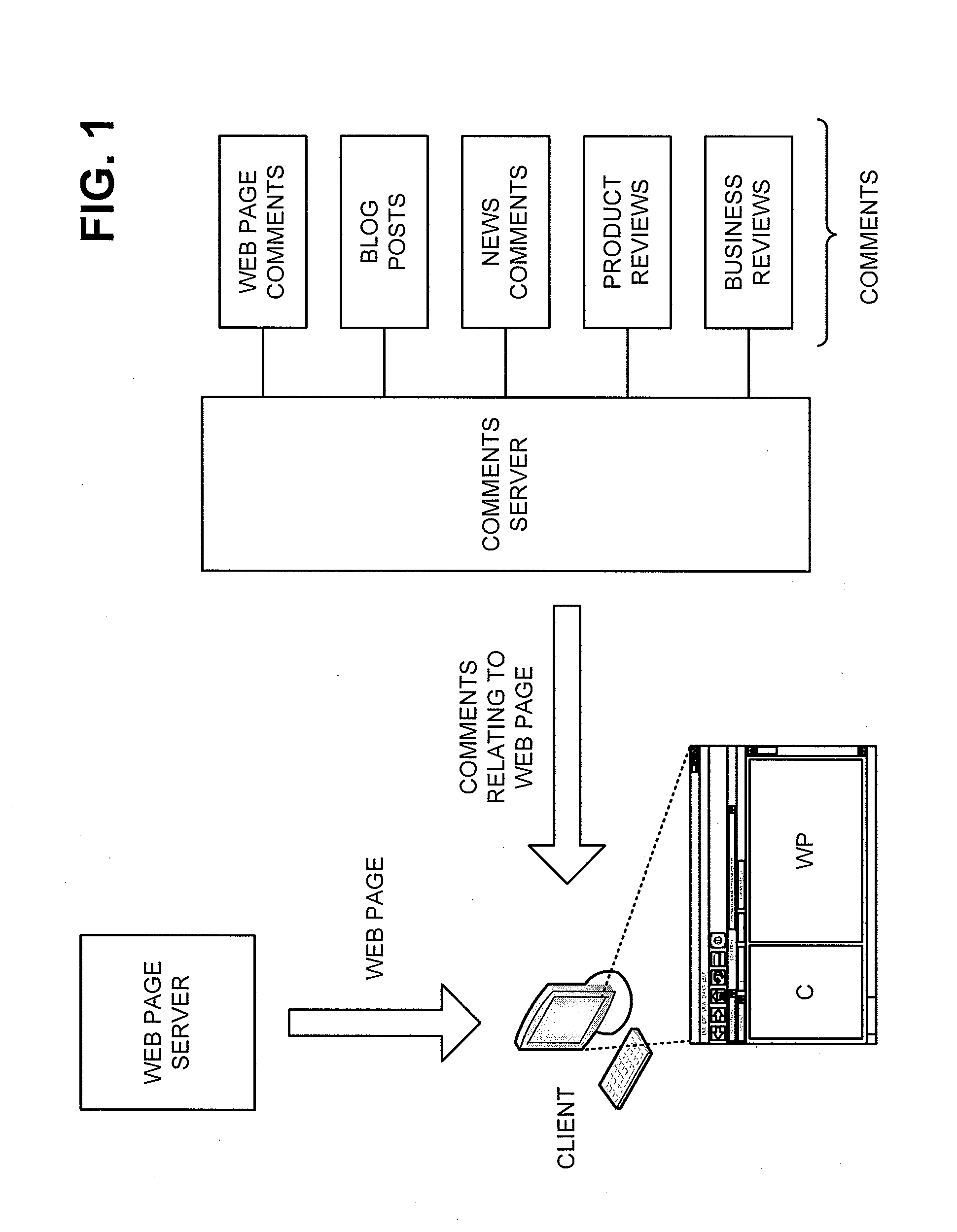
Presenting comments from various sources
InactiveUS20110040787A1Web data indexingDigital data processing detailsDocumentation procedureServer appliance
A system may include one or more databases to store comments relating to documents, the comments originating from first and second sources, where the comments from the first source include comments received from users via commenting functionality associated with browsers installed on client devices, and the comments from the second source include comments received from users independent of the commenting functionality associated with the browsers installed on the client devices. The system may also include one or more server devices to receive a request for comments relating to a particular document, search at least one of the one or more databases to identify comments relating to the particular document, and provide the identified comments for presentation in connection with the particular document.
Owner:GOOGLE LLC
Method and system for key management in voice over internet protocol
InactiveUS20070157026A1Eliminate needEasy to implementKey distribution for secure communicationUnauthorised/fraudulent call preventionSession Initiation ProtocolDiffie–Hellman key exchange
A method and system for a secure telephone protocol are disclosed, which can be implemented using current Voice over IP (VoIP) protocols, Session Initiation Protocol (SIP, as specified in the Request for Comment (RFC) 3261 from the Internet Engineering Task Force (IETF)), Real Time Transport Protocol (RTP, as specified in RFC 3550), and Secure RTP (SRTP, as specified in RFC 3711). The secure telephone protocol can include a shared secret value that is cached and then re-used later to authenticate a long series of session keys to be used for numerous separate secure phone calls over a long period of time, thereby providing cryptographic key continuity without the need for voice authentication. In an embodiment, the secure telephone protocol can utilize the Diffie-Hellman key exchange during call setup, and AES for encrypting the voice stream.
Owner:ZIMMERMANN PHILIP R
Communication switching method among different networks and terminal equipment thereof
InactiveCN101801055AFix switching issuesReduce loadWireless communicationInternational standardService experience
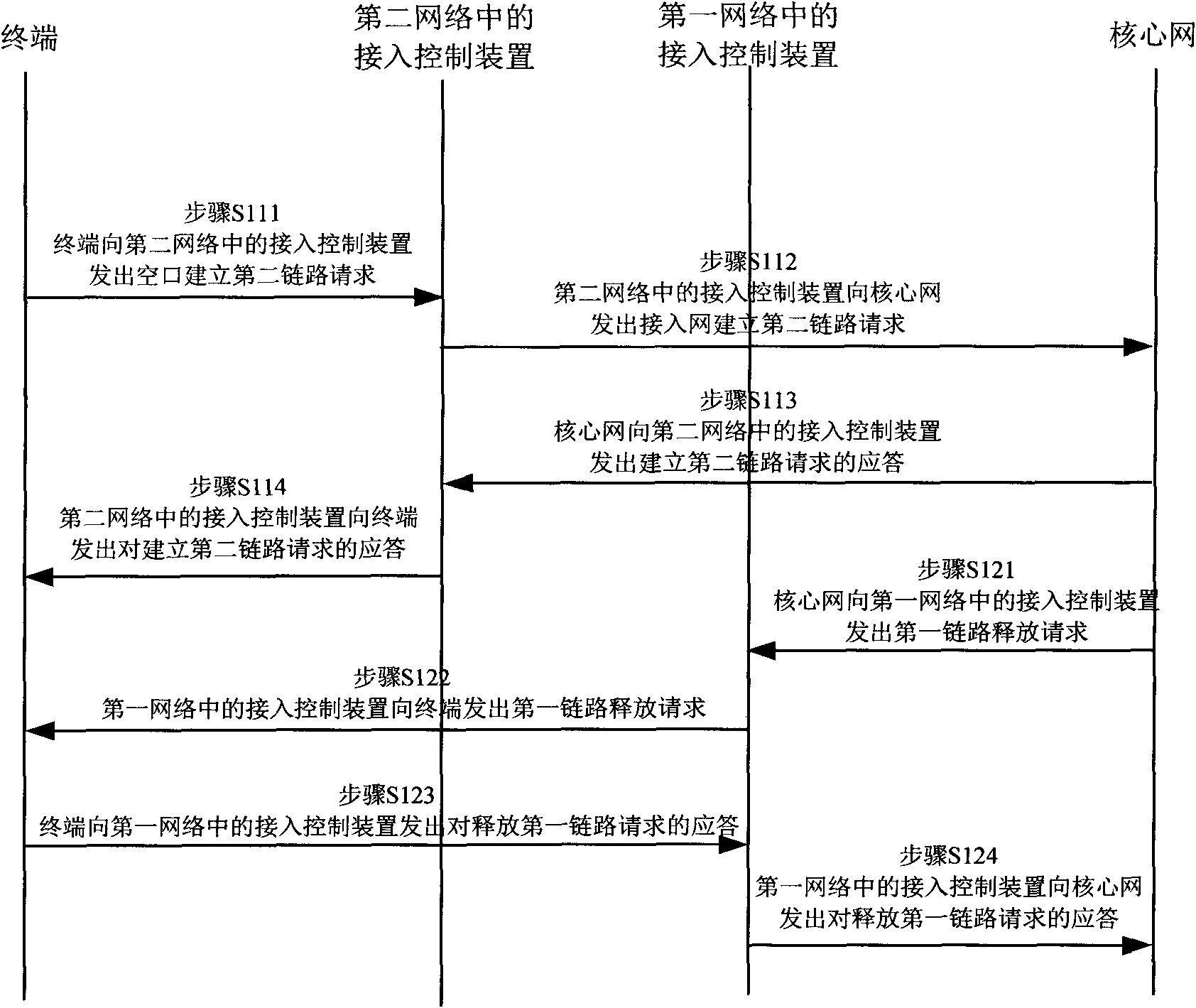
The invention relates to a communication switching method among different networks, which comprises the following steps of: sending a request for establishing a second link to a core network by a terminal through an access control device of a second network; and after completing the establishment of the second link, sending a request for releasing a first link to the terminal by the core network through an access control device in a first network. The invention has the advantages of providing and solving the technical problem of the processing of seamless switching of a multi-mode terminal between a WLAN (Wirele Local Area Network) network and a mobile wireless network in the prior art, and guarantees service quality and service experience of users during roaming. The invention provides a novel implementation system and method according to international standards of 3GPP (The 3rd Generation Partnership Project), 3GPP2, RFC (Request for Comments) and the like, which have easy implementation and capability of scale commercial popularization.
Owner:SHANGHAI DINGZHU COMM TECH
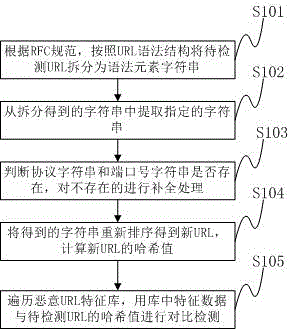
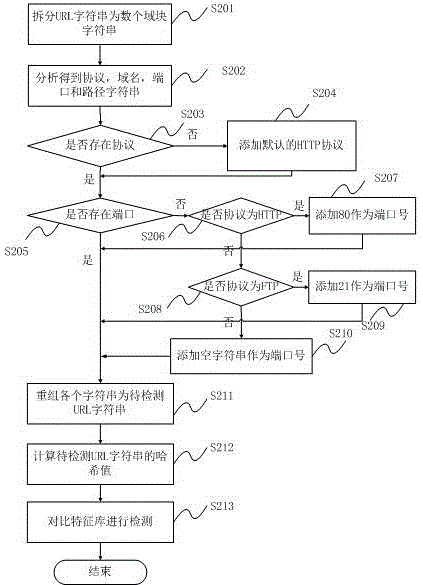
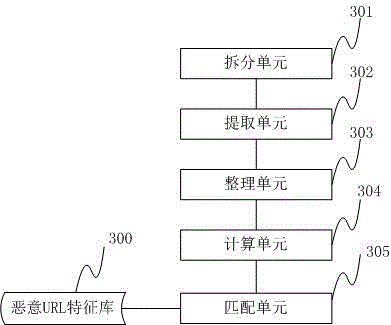
Formalization detection method and system for malicious URL (uniform resource locator)
ActiveCN102843271AImprove the detection rateGood detection rateData switching networksSoftware engineeringFeature data
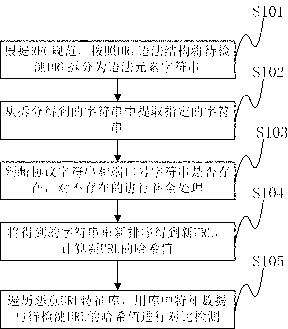
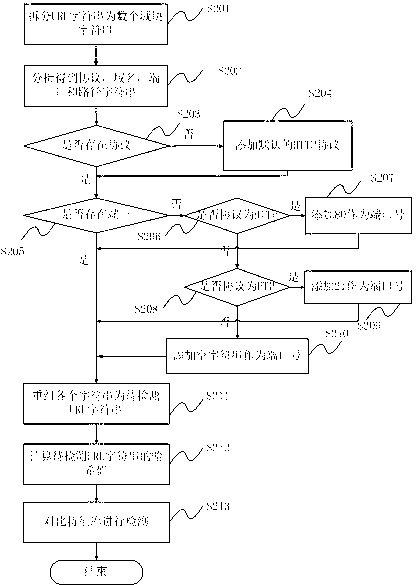
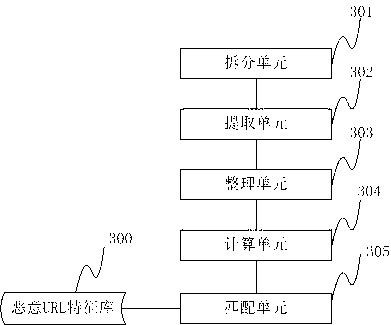
The invention discloses a formalization detection method for a malicious URL (uniform resource locator). The formalization detection method comprises the following steps of: splitting the URL to be detected into syntactic element character strings according to a URL syntactic structure on the basis of the standard of RFC (request for comments); extracting designated character strings from the character strings obtained by splitting; performing completing treatment on the non-existent character strings; reordering the character strings obtained after completing treatment to obtain a new URL, and calculating the hash value of the new URL; and traversing a malicious URL feature library, and performing contrast detection on feature data in the malicious URL feature library and the hash value of the URL to be detected. The invention further discloses a formalization detection system for the malicious URL. The technical scheme disclosed by the invention can be effectively used against the variability in the formats of the URL; and compared with the traditional URL detection method, the detection rate against the malicious URL which often changes the format is higher, and a single feature can also be adopted for corresponding to multiple format variants of the malicious URL, so that the volume of a virus feature library required for the detection method is smaller, and the space of a memory and a magnetic disk can be further saved.
Owner:HARBIN ANTIY TECH
Multi-stage hierarchical bandwidth management method
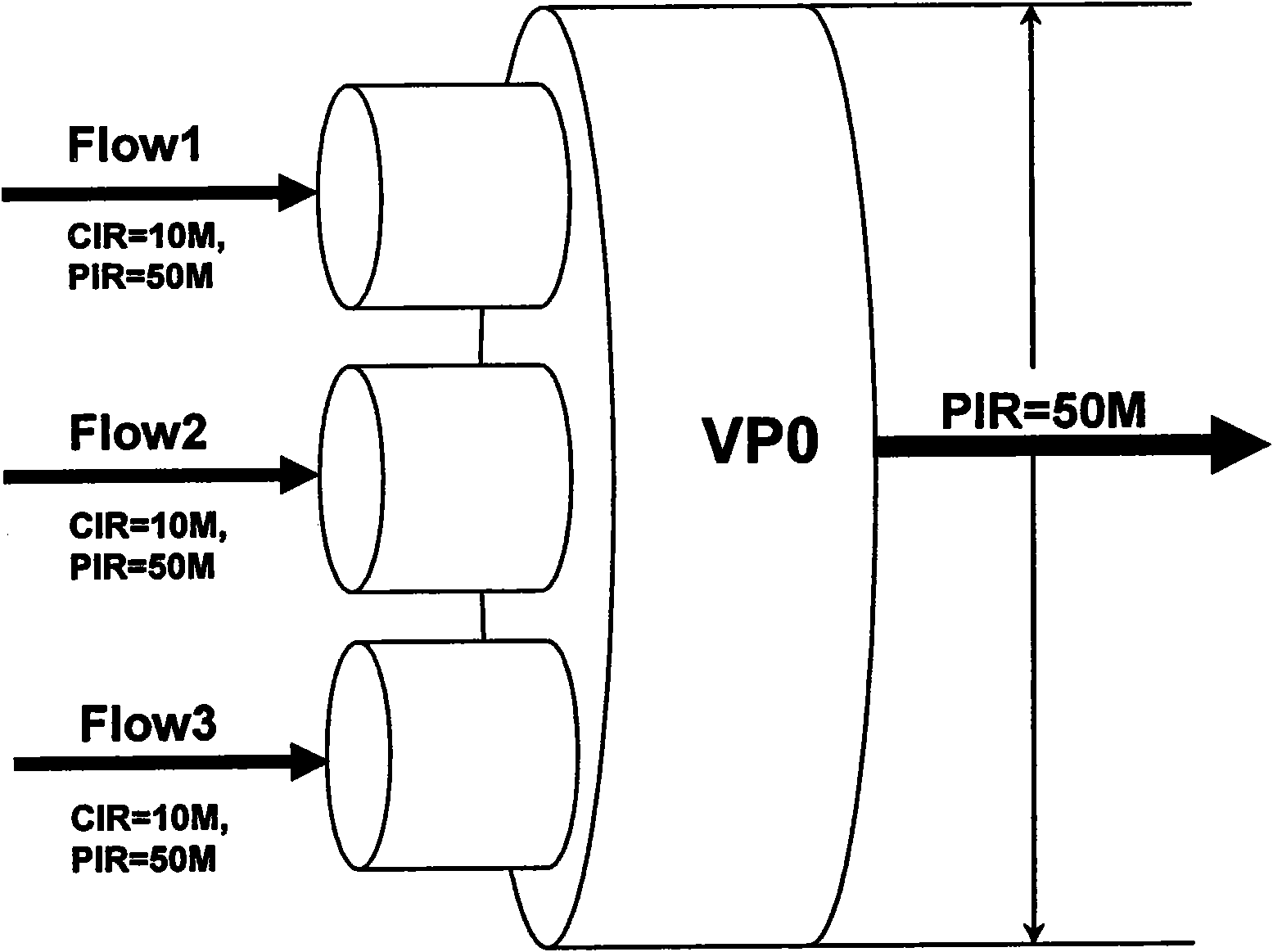
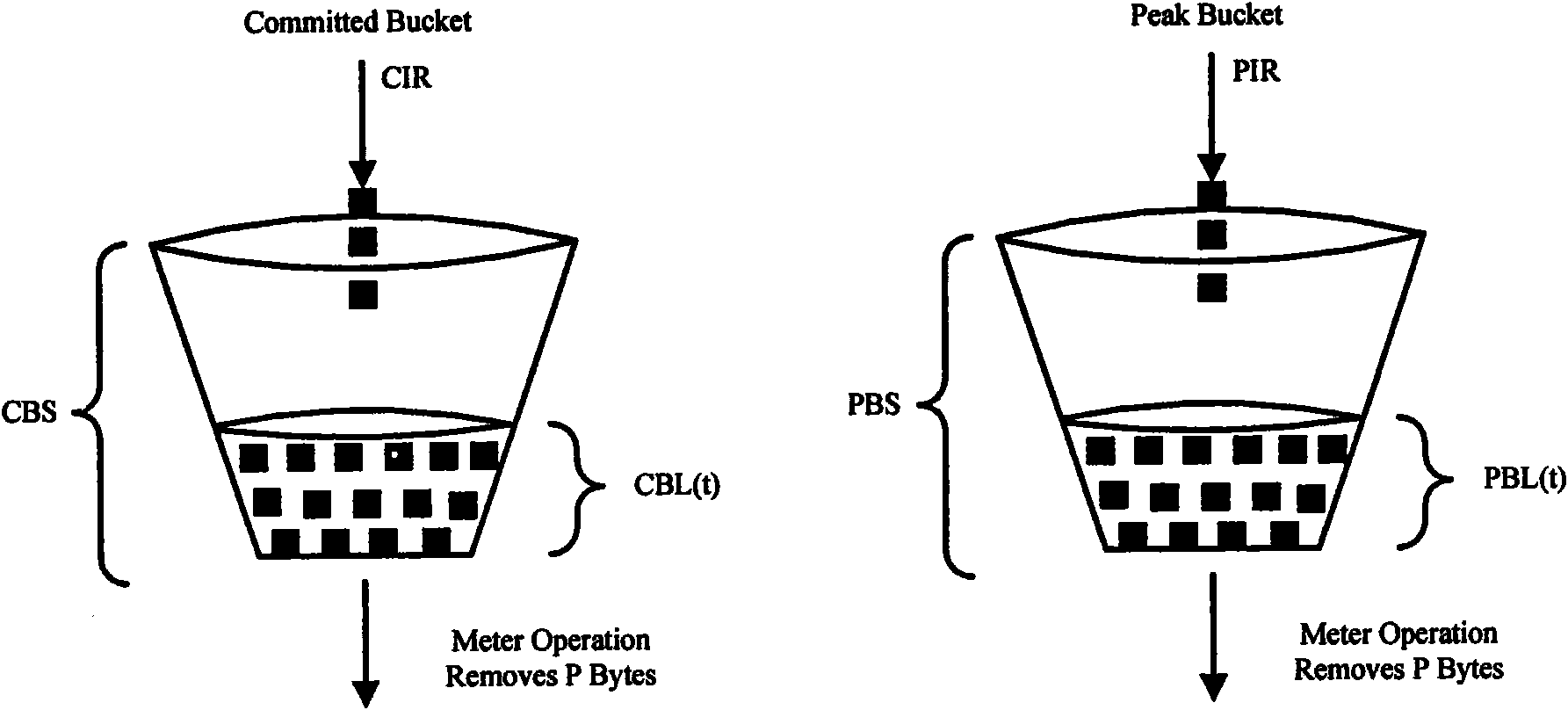
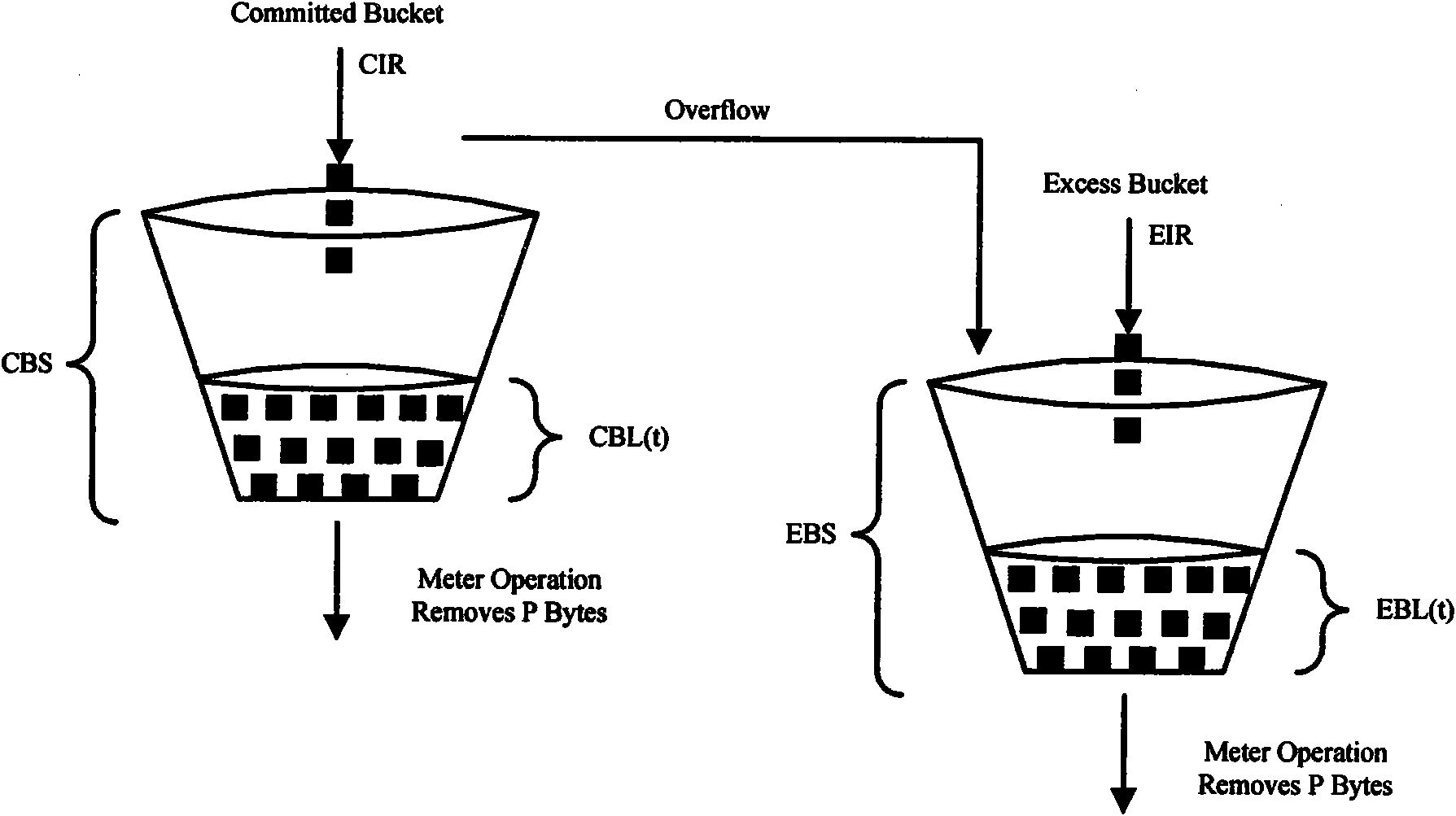
The invention discloses a multi-stage hierarchical bandwidth management method, which comprises the following steps of: A10, configuring CIR (Committed Information Rate) and PIR (peak Information Rate) (or EIR (Excess Information Rate)) of each stage of scheduling node according to a business model, wherein the CIR of the node is set according to the bandwidth purchased by a user in the first stage, the bandwidth distribution principle of each node from the second stage of scheduling is shown in the description, EIRni=PIRni-CIRni, and n is not less than 2; and A20, respectively marking messages as green, yellow or red by using MEF (Managed Extensibility Framework), RFC2697 (Request for Comments 2697) or RFC2698 algorithms in the first stage, configuring each node into a color sensitive mode and a coupling mode from the second stage, and shaping the traffic according to the MEF algorithm. By using the invention, the multi-stage hierarchical bandwidth management is realized on an exchanging chip supporting the MEF Traffic Shaping algorithm without need of special ASIC (Application Specific Integrated Circuits) or hardware; and the requirements are satisfied through updating software under the situation of changing or updating the business so that considerable hardware cost is saved; and the bandwidth distribution algorithm of the hierarchical business model is simple and convenient for web masters to configure.
Owner:FENGHUO COMM SCI & TECH CO LTD
Consultation method of control word ability and pseudowire establishing equipment
InactiveCN101924676AResolve configurationSolving Consistency IssuesHybrid transportNetworks interconnectionTerminal equipmentOperations research
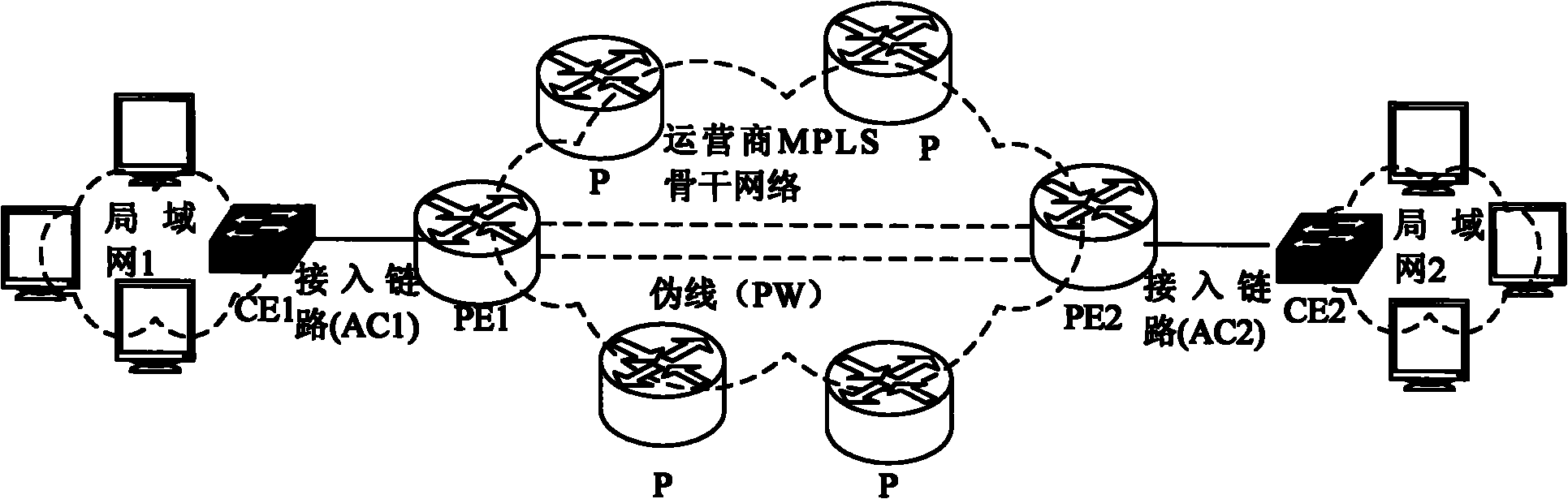
The invention discloses a consultation method of control word ability and pseudowire establishing equipment. The consultation method comprises the steps of: configuring attributes of control word ability on local equipment and opposite terminal equipment, informing the attributes of the configured control word ability to an opposite side; and comparing by the opposite side according to the obtained attributes of the control word ability. CBit information in an Mapping message fully reflects the configuration of the control word ability of the local equipment to PW (Pocket Writing); during the consultation, and operation is carried out on an identification bit of the local control word ability and an identification bit of the remote end control word ability to obtain a result which is used as a final consultation result of the control word ability of the PW for guiding the forwarding. The invention solves the problem of inconsistency of control word ability configuration and the consultation result existing in rules defined in the present RFC4447 (Request for Comments), and optimizes the process of consulting the control word ability.
Owner:ZTE CORP
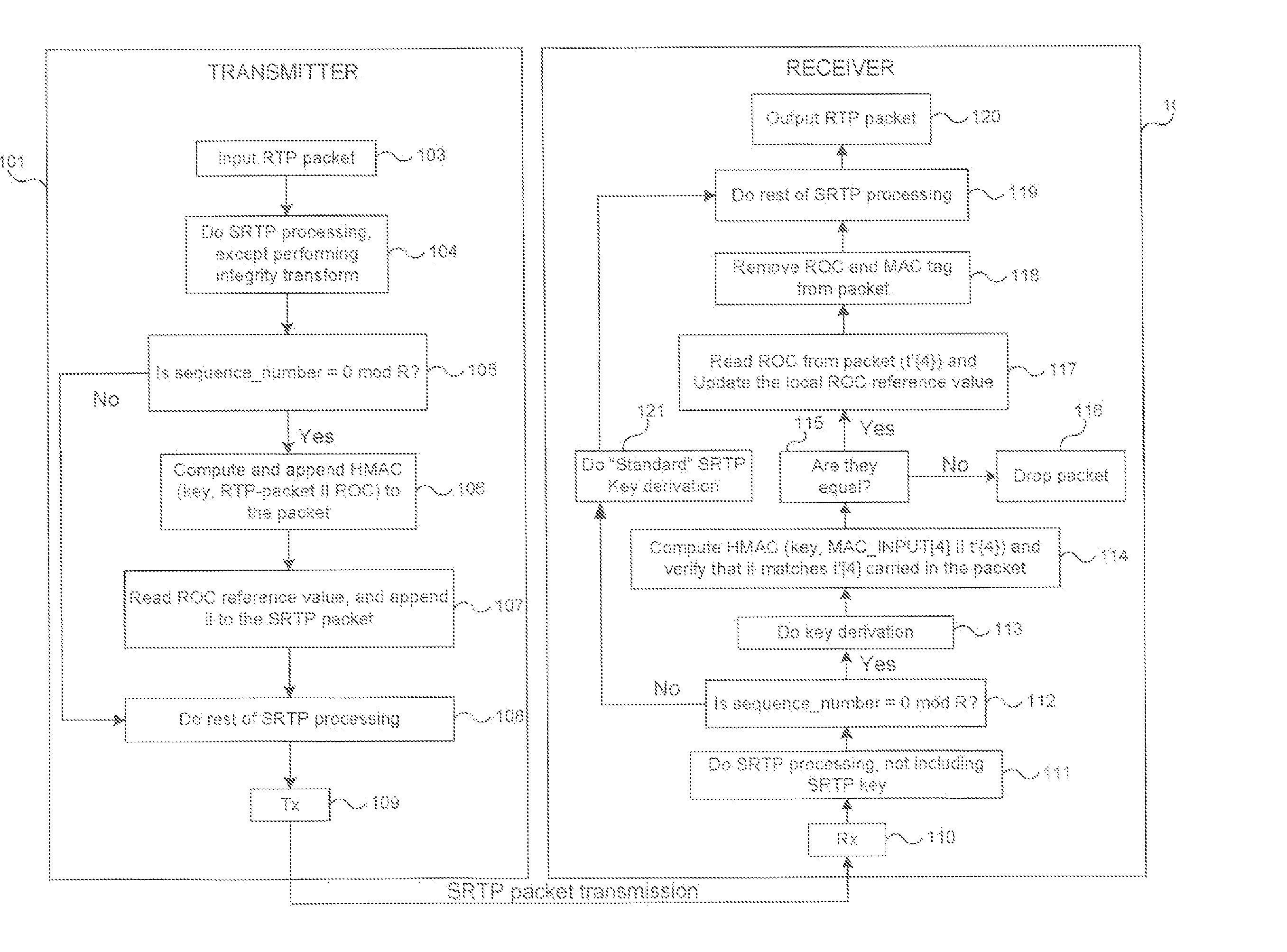
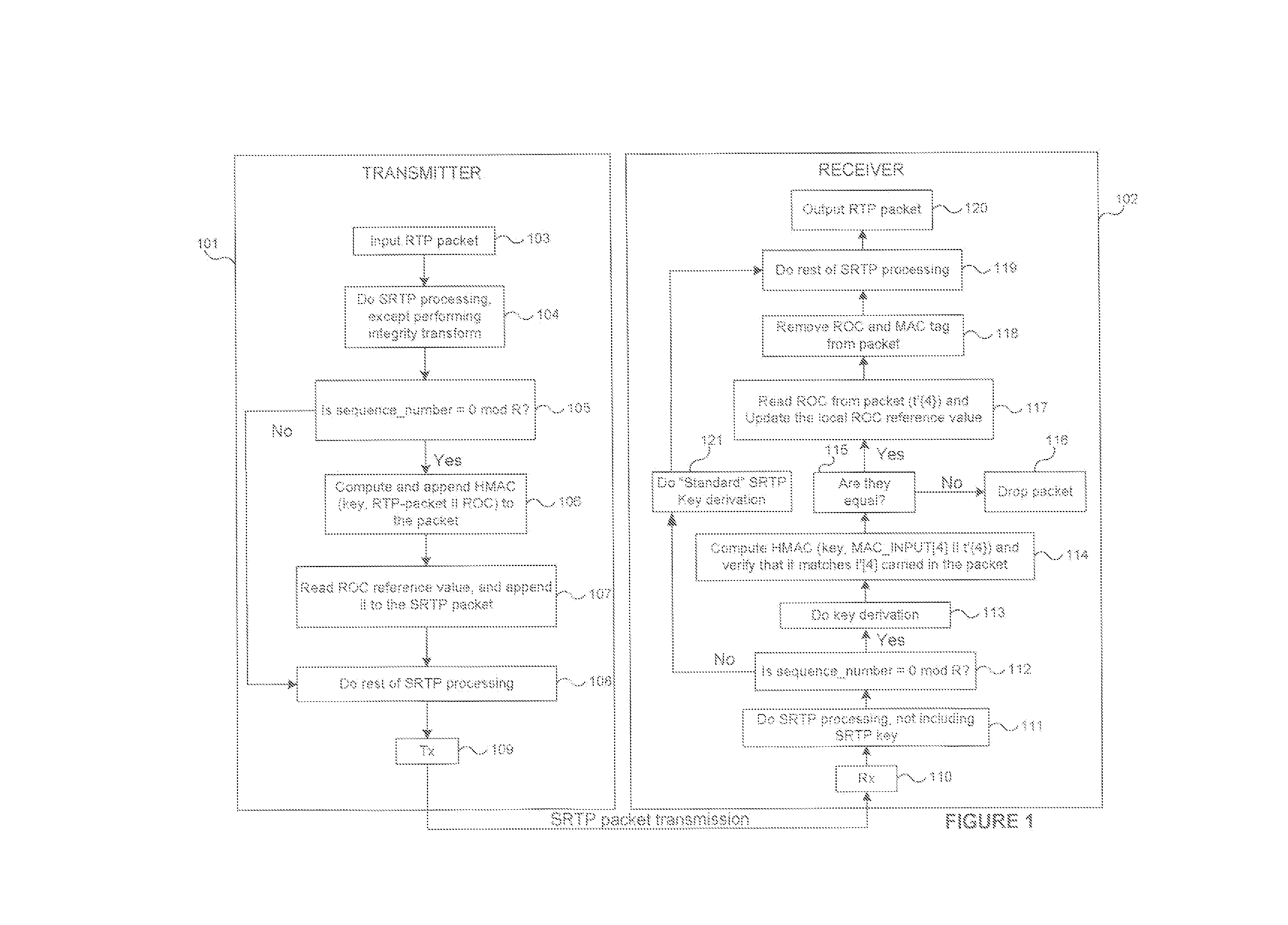
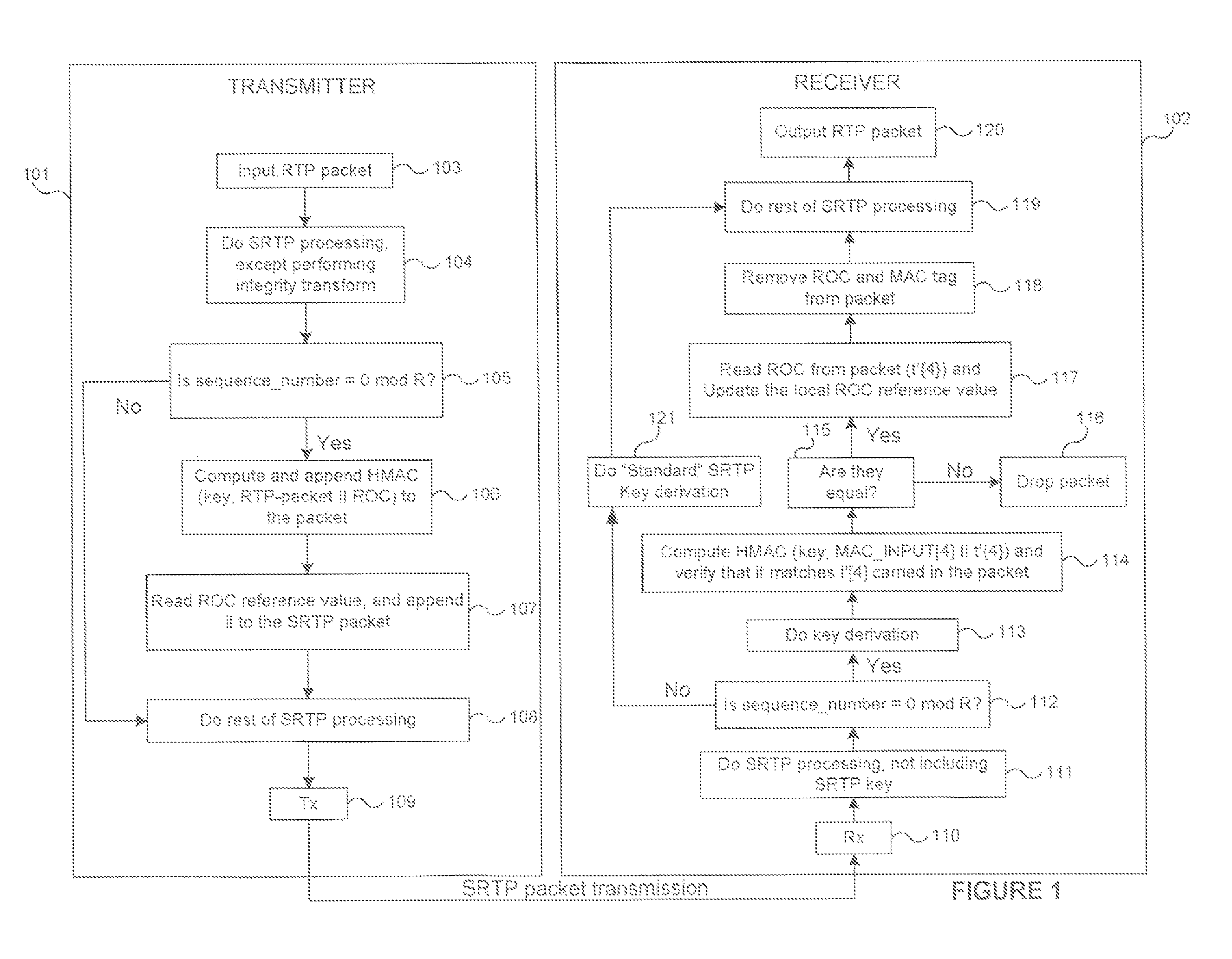
Methods for secure and bandwidth efficient cryptographic synchronization
ActiveUS20070113085A1Efficient use of bandwidthEasy to useSynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageTransmission protocolSecure Real-time Transport Protocol
Methods for cryptographic synchronization of data packets. A roll-over counter (ROC) value is periodically appended to and transmitted with a data packet when a function of the packet sequence number equals a predetermined value. The ROC effectively synchronizes the cryptographic transformation of the data packets. Although the disclosed methods are generally applicable to many transmission protocols, they are particularly adaptable for use in systems wherein the data packets are transmitted to a receiver using the Secure Real-Time Transport Protocol (SRTP) as defined in Internet Engineering Task Force (IETF) Request for Comments (RFC) 3711.
Owner:TELEFON AB LM ERICSSON (PUBL)
Apparatus and method for implementing instruction support for the camellia cipher algorithm
A processor including instruction support for implementing the Camellia block cipher algorithm may issue, for execution, programmer-selectable instructions from a defined instruction set architecture (ISA). The processor may include a cryptographic unit that may receive instructions for execution. The instructions include one or more Camellia instructions defined within the ISA. In addition, the Camellia instructions may be executable by the cryptographic unit to implement portions of a Camellia cipher that is compliant with Internet Engineering Task Force (IETF) Request For Comments (RFC) 3713. In response to receiving a Camellia F( )-operation instruction defined within the ISA, the cryptographic unit may perform an F( ) operation, as defined by the Camellia cipher, upon a data input operand and a subkey operand, in which the data input operand and subkey operand may be specified by the Camellia F( )-operation instruction.
Owner:SUN MICROSYSTEMS INC
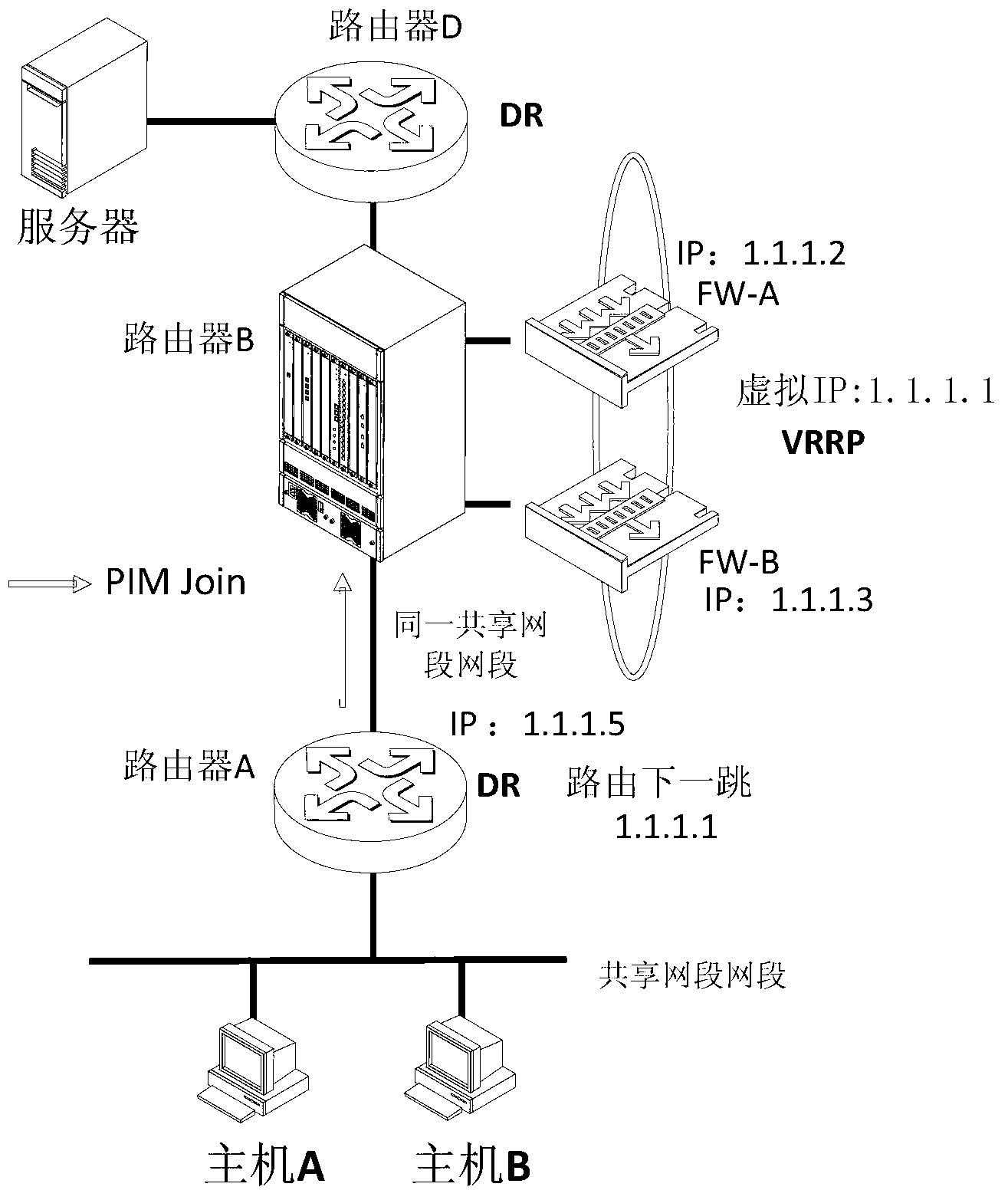
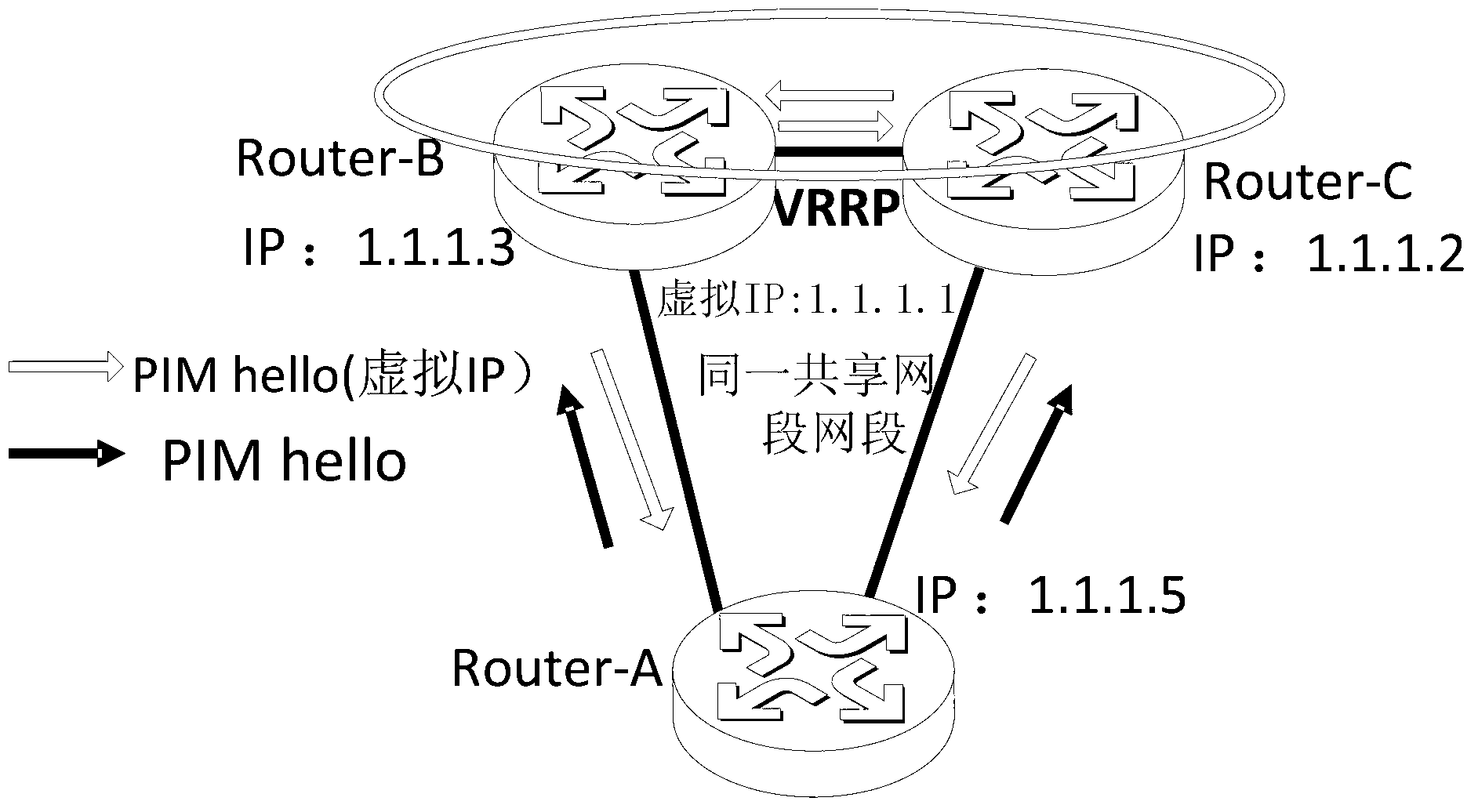
Method and device for realizing PIM multicast in VRRP network environment
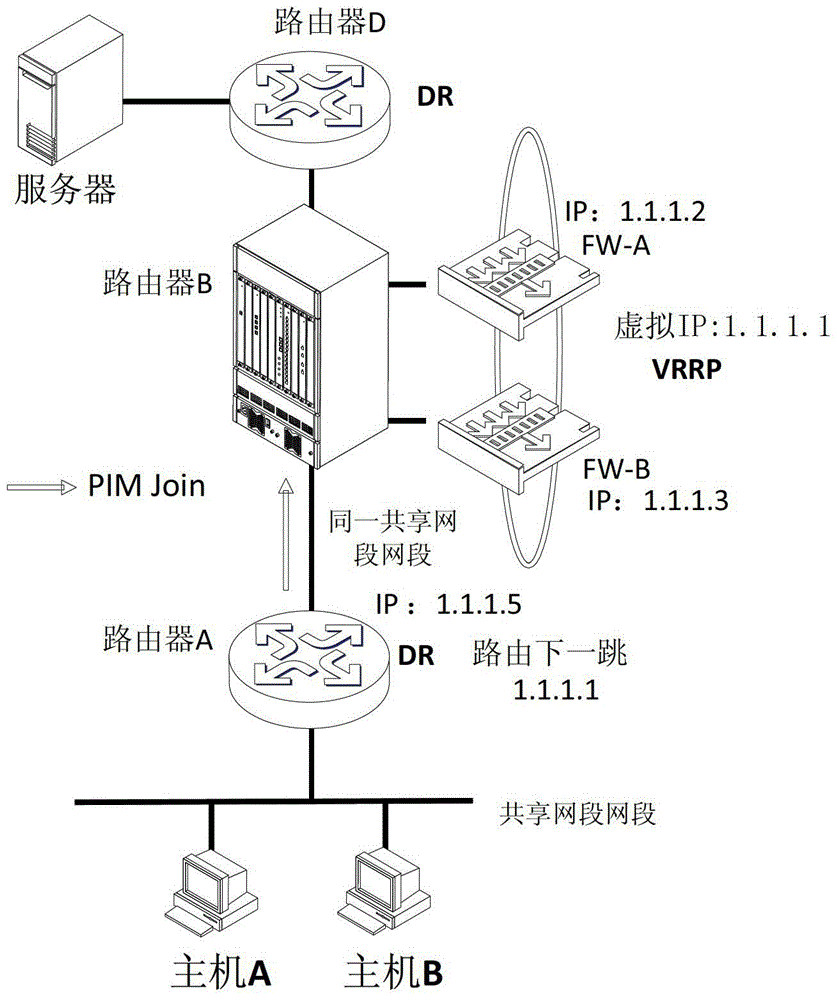
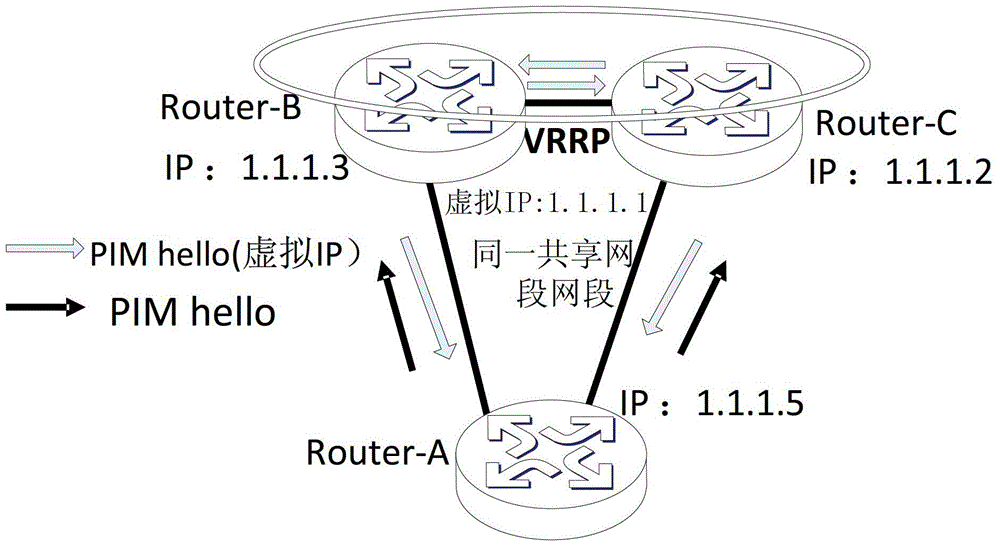
ActiveCN103227724AEnable co-deploymentSolve the problem that multicast cannot be deployed at the same timeSpecial service provision for substationIP multicastProtocol Independent Multicast
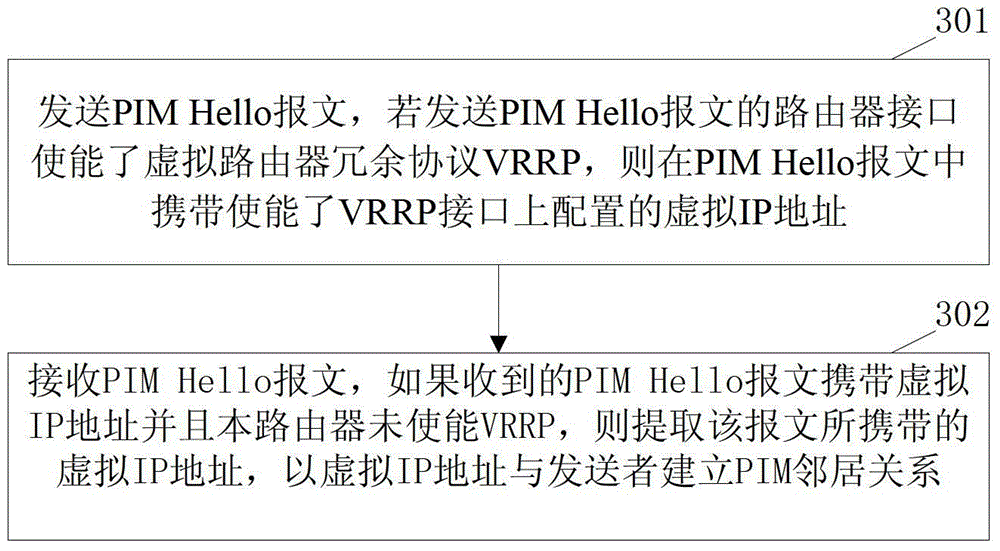
The invention discloses a method for realizing PIM (Protocol Independent Multicast) in a VRRP (Virtual Router Redundancy Protocol) network environment. A virtual IP (Internet Protocol) address is carried when a PIM Hello message is transmitted to an interface for enabling the VRRP; when the PIM Hello message is received, the virtual IP address of the VRRP is used for establishing a PIM neighbor, so that unicast and multicast services can be simultaneously used as a host and a backup in the VRRP network environment. Meanwhile, the virtual IP address of the VRRP is completely compatible with a current RFC (Request for Comments) protocol, and so that the problem that the VRRP and the multicast cannot be deployed simultaneously at present is solved. The invention also discloses a device for realizing the PIM multicast in the VRRP network environment. The device comprises a transmitting module and a receiving module, wherein the transmitting module is used for transmitting the PIM Hello message carrying the virtual IP address; and the receiving module is used for receiving the PIM Hello message and selecting and transmitting a router of the PIM Hello message to establish the PIM neighbor by using a real address or the virtual IP address. The method and the device disclosed by the invention have the characteristics that the protocol is simple and the deployment is flexible; common deployment of the VRRP and the multicast can be realized; and the host and backup of the unicast and the multicast can be allowed at the same time.
Owner:北京华三通信技术有限公司
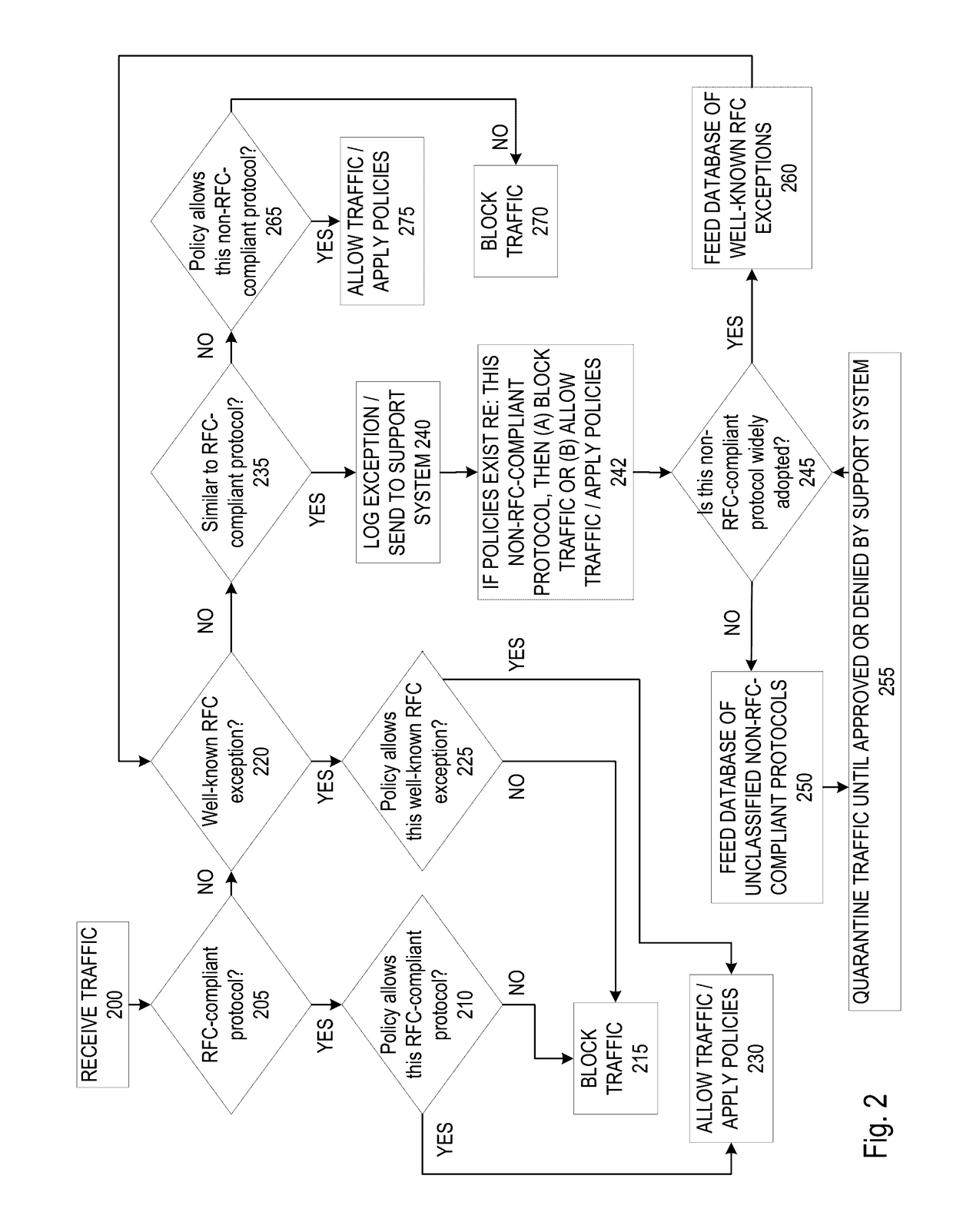
Non RFC-compliant protocol classification based on real use
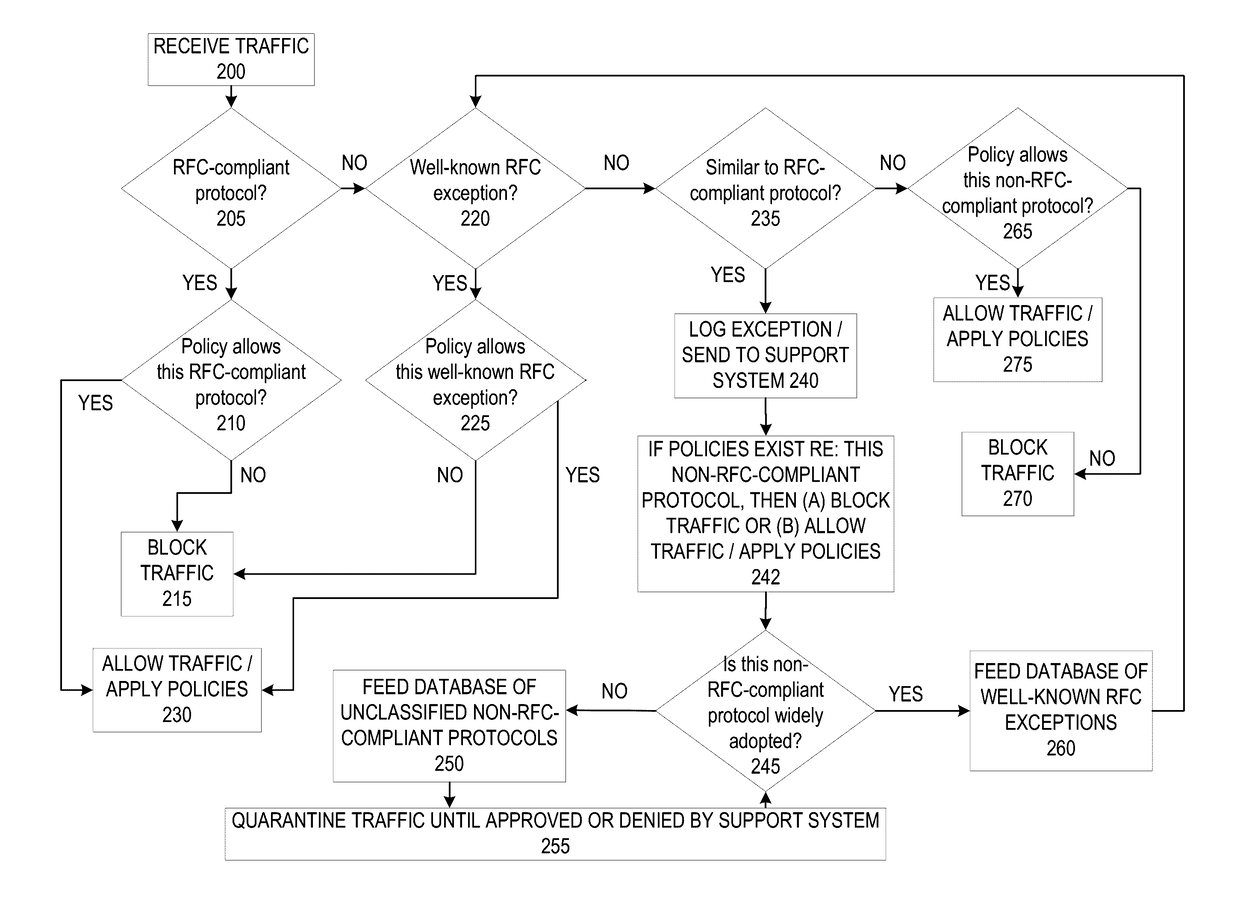
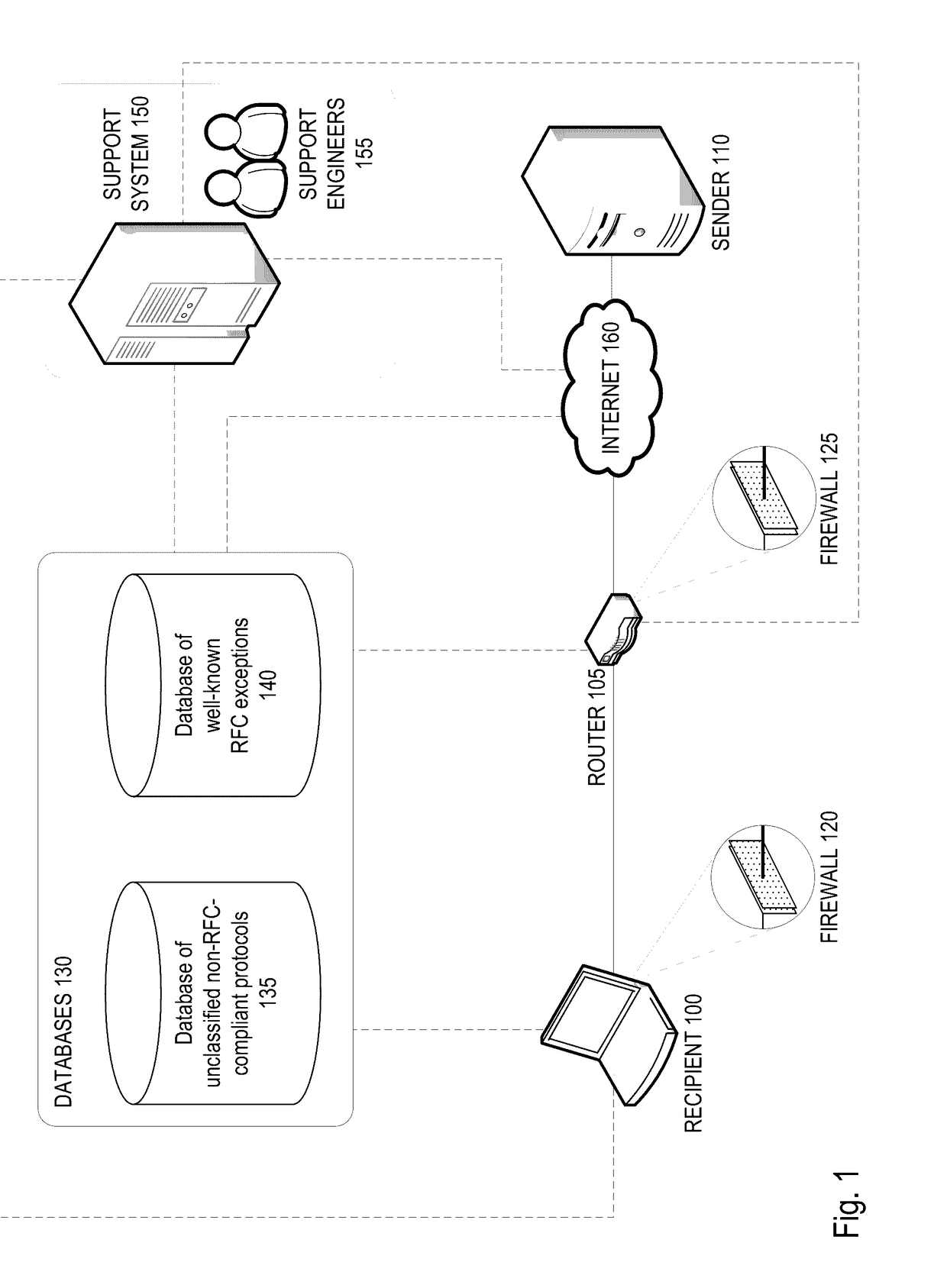
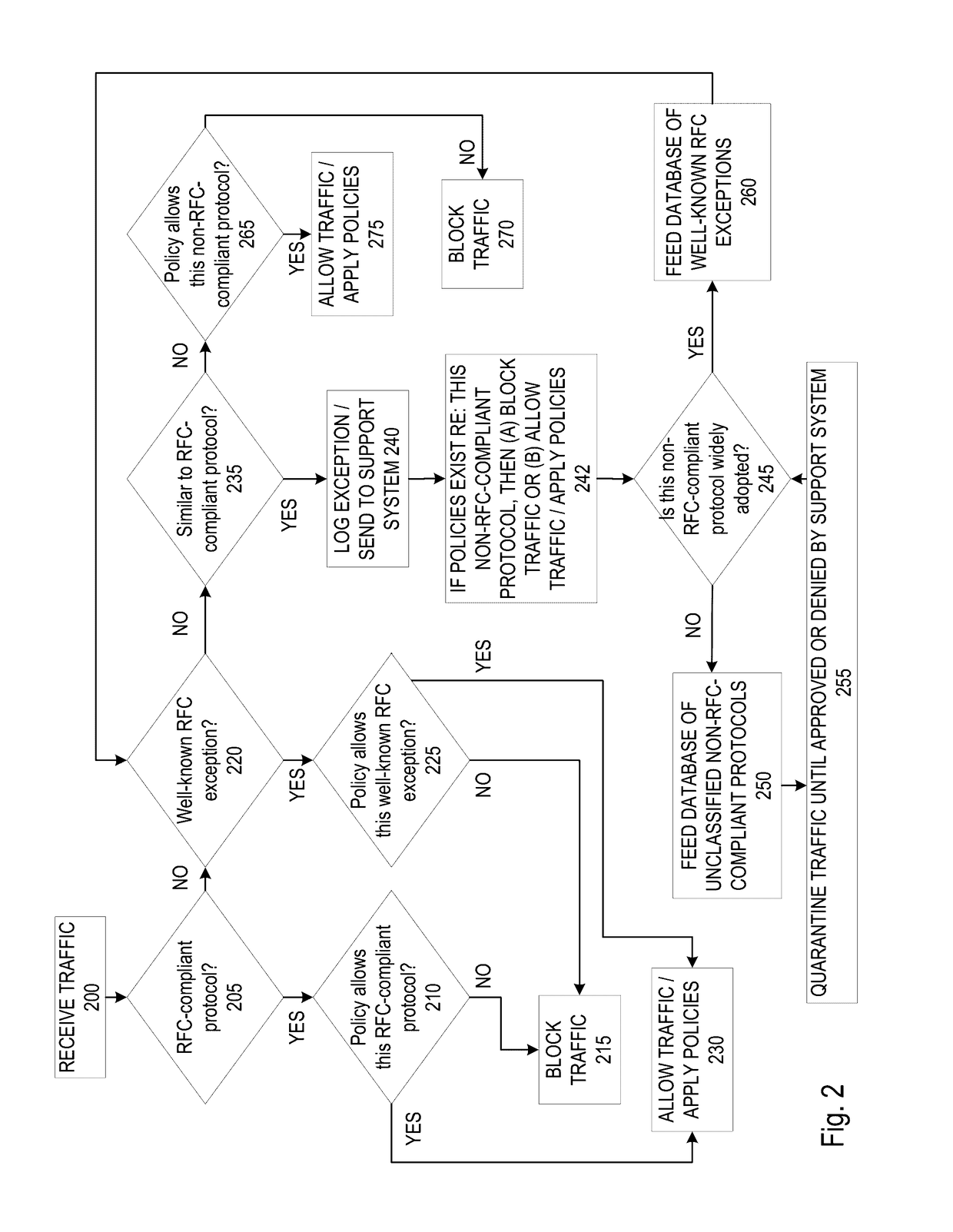
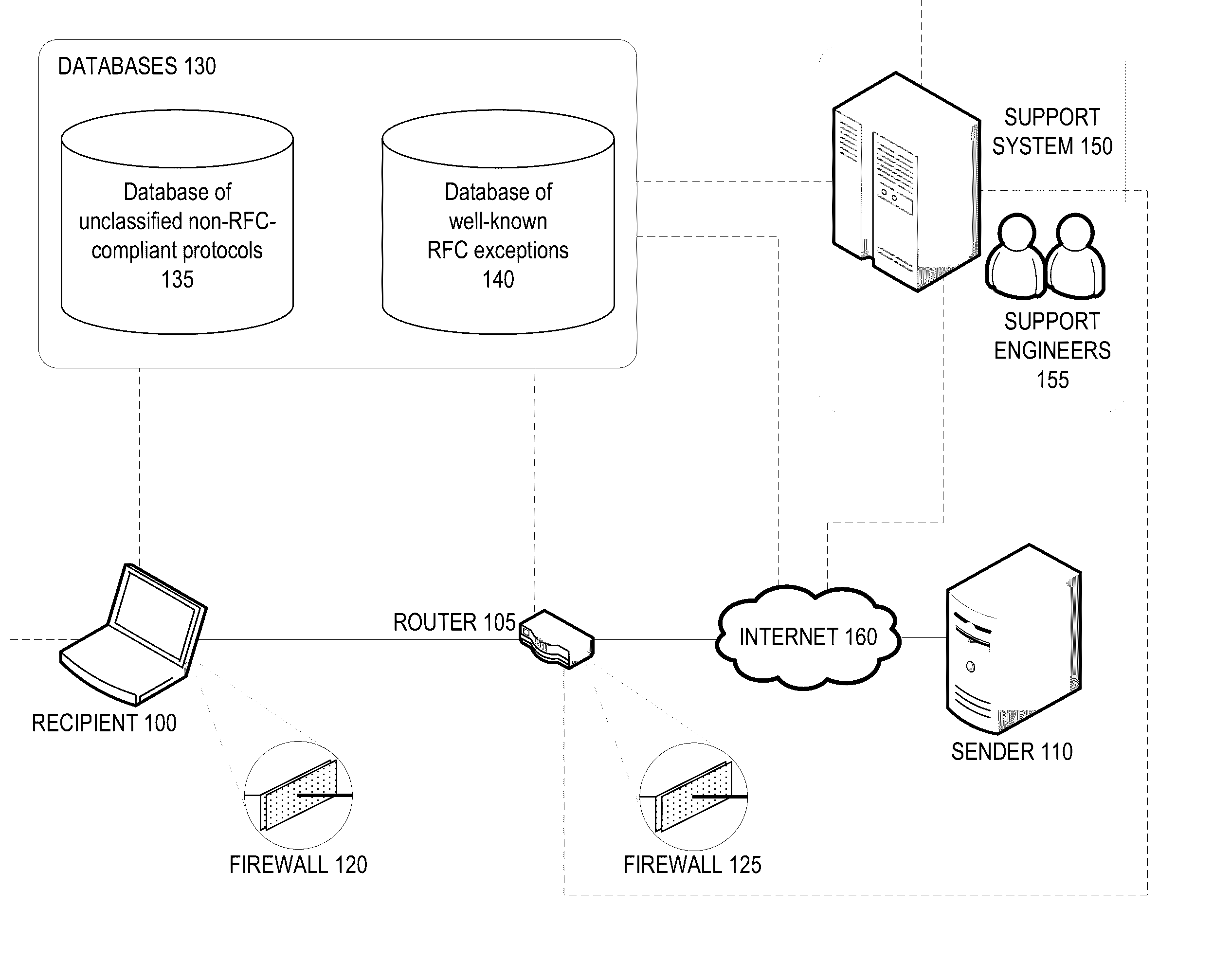
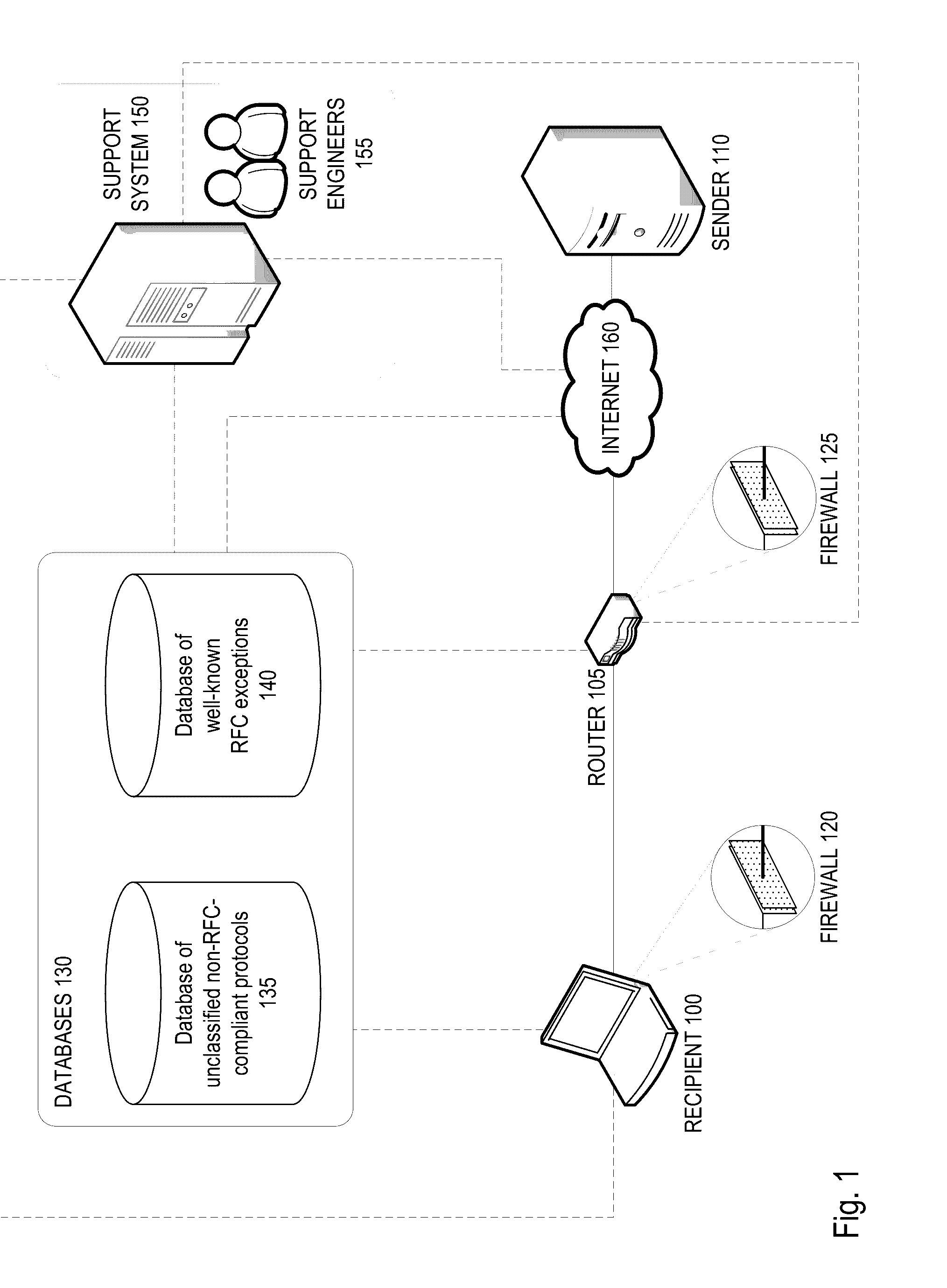
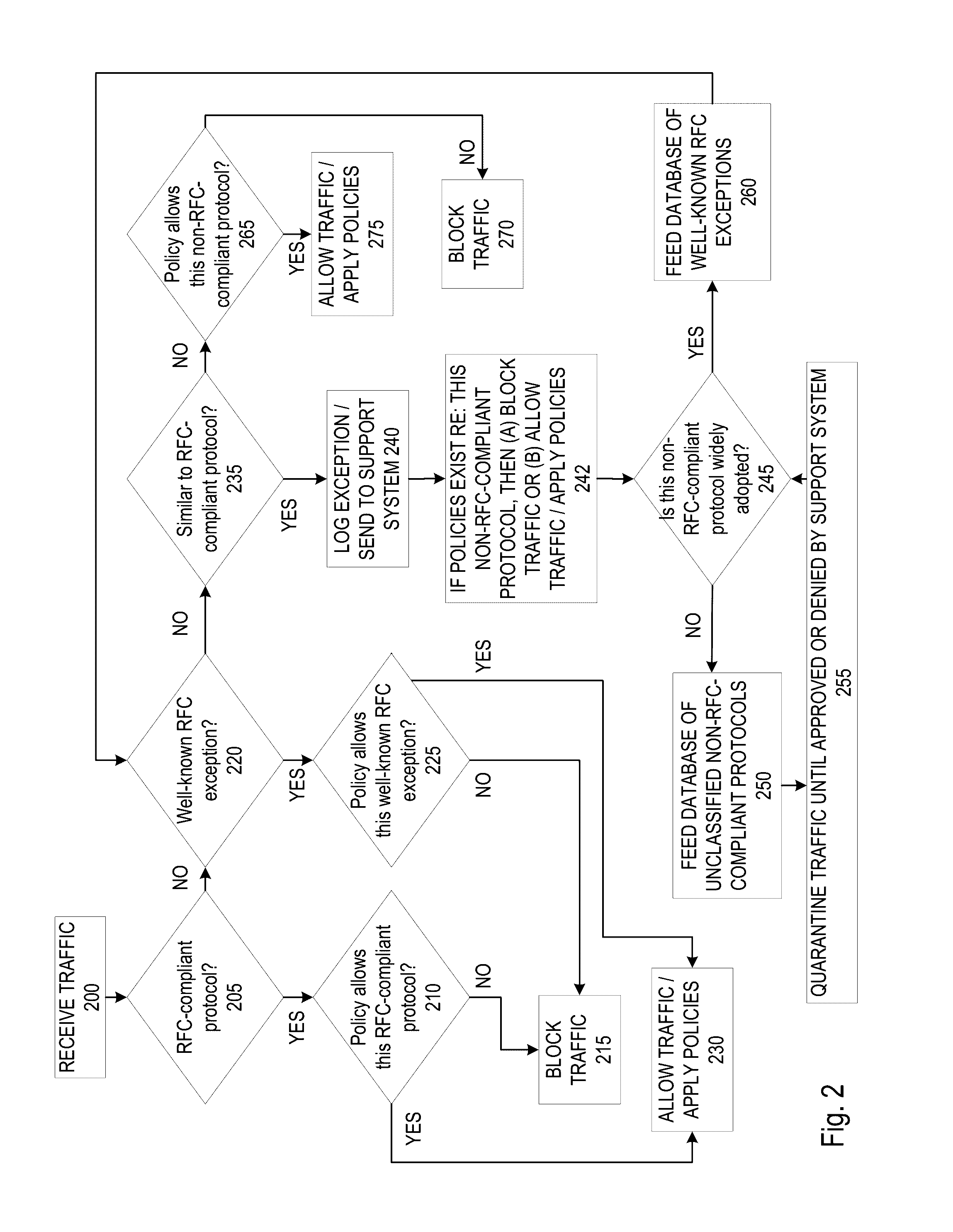
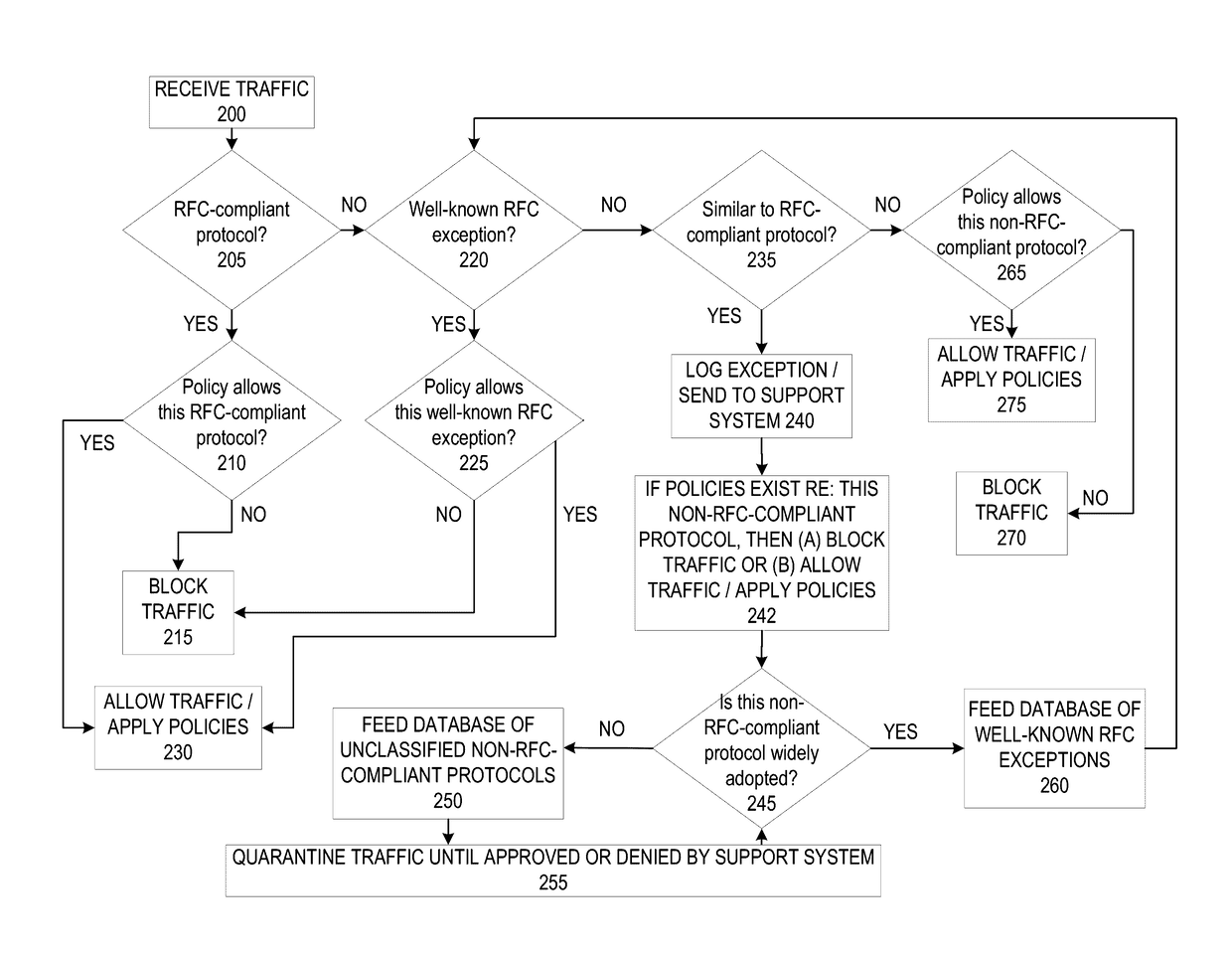
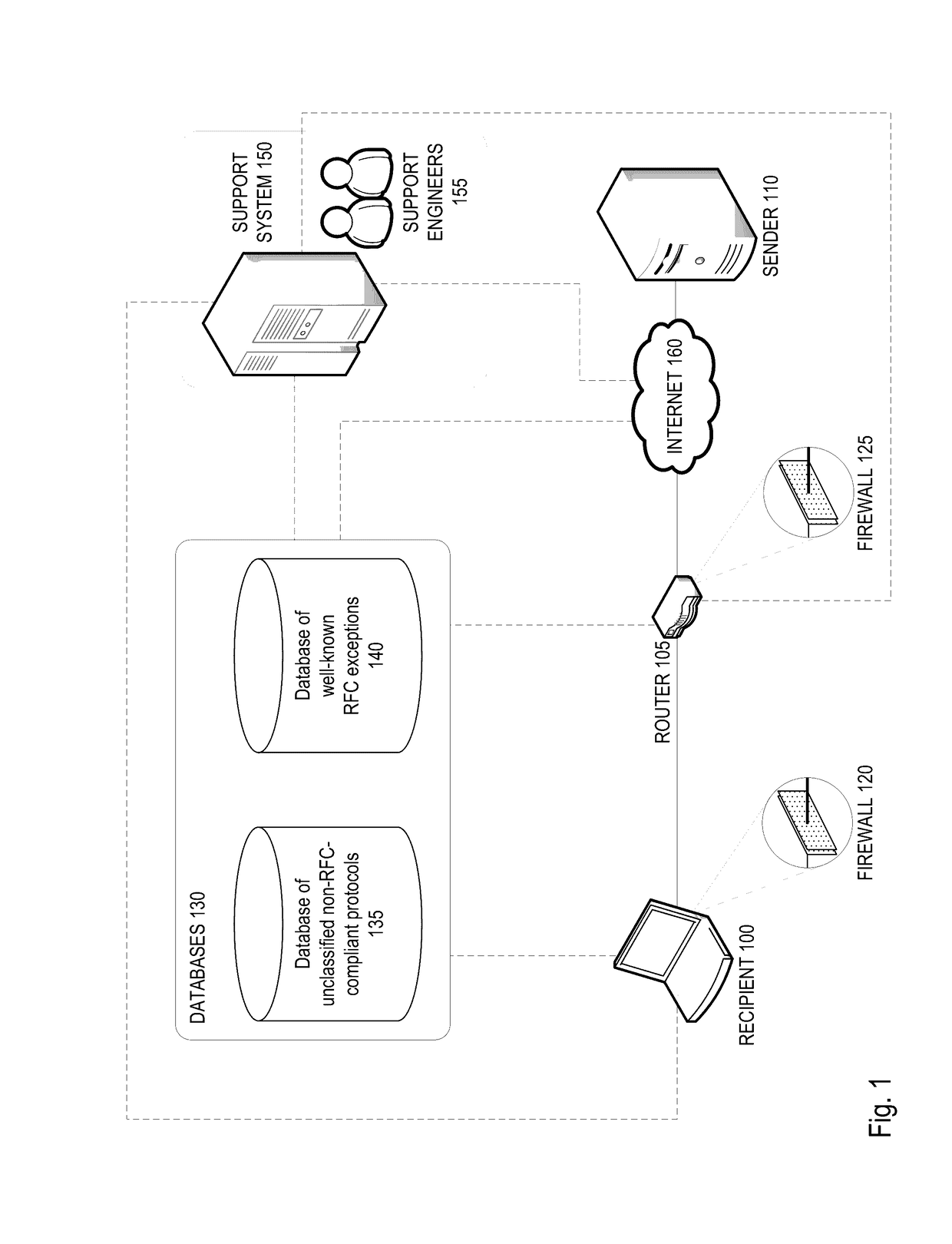
A firewall system determines whether a protocol used by an incoming data packet is a standard protocol compliant with Request For Comment (RFC) standards. In the event the protocol is RFC compliant, the firewall transmits the packet to the recipient according to firewall policies regarding the standard protocol. If the protocol is not that of an RFC standard, the firewall determines whether the protocol matches an RFC-exception protocol in a RFC-exception protocol database. If the protocol does match an RFC-exception, the firewall may transmit the packet to the recipient according to firewall policies regarding the RFC-exception protocol. If it does not match an RFC-exception, the firewall may transmit the packet or protocol to a support system where it may be quarantined until it is approved based on a decision that the protocol is safe and / or widely adopted.
Owner:SONICWALL US HLDG INC
Non rfc-compliant protocol classification based on real use
A firewall system determines whether a protocol used by an incoming data packet is a standard protocol compliant with Request For Comment (RFC) standards. In the event the protocol is RFC compliant, the firewall transmits the packet to the recipient according to firewall policies regarding the standard protocol. If the protocol is not that of an RFC standard, the firewall determines whether the protocol matches an RFC-exception protocol in a RFC-exception protocol database. If the protocol does match an RFC-exception, the firewall may transmit the packet to the recipient according to firewall policies regarding the RFC-exception protocol. If it does not match an RFC-exception, the firewall may transmit the packet or protocol to a support system where it may be quarantined until it is approved based on a decision that the protocol is safe and / or widely adopted.
Owner:SONICWALL US HLDG INC
Non rfc-compliant protocol classification based on real use
InactiveUS20170163687A1Computer security arrangementsTransmissionSupporting systemRequest for Comments
A firewall system determines whether a protocol used by an incoming data packet is a standard protocol compliant with Request For Comment (RFC) standards. In the event the protocol is RFC compliant, the firewall transmits the packet to the recipient according to firewall policies regarding the standard protocol. If the protocol is not that of an RFC standard, the firewall determines whether the protocol matches an RFC-exception protocol in a RFC-exception protocol database. If the protocol does match an RFC-exception, the firewall may transmit the packet to the recipient according to firewall policies regarding the RFC-exception protocol. If it does not match an RFC-exception, the firewall may transmit the packet or protocol to a support system where it may be quarantined until it is approved based on a decision that the protocol is safe and / or widely adopted.
Owner:SONICWALL US HLDG INC
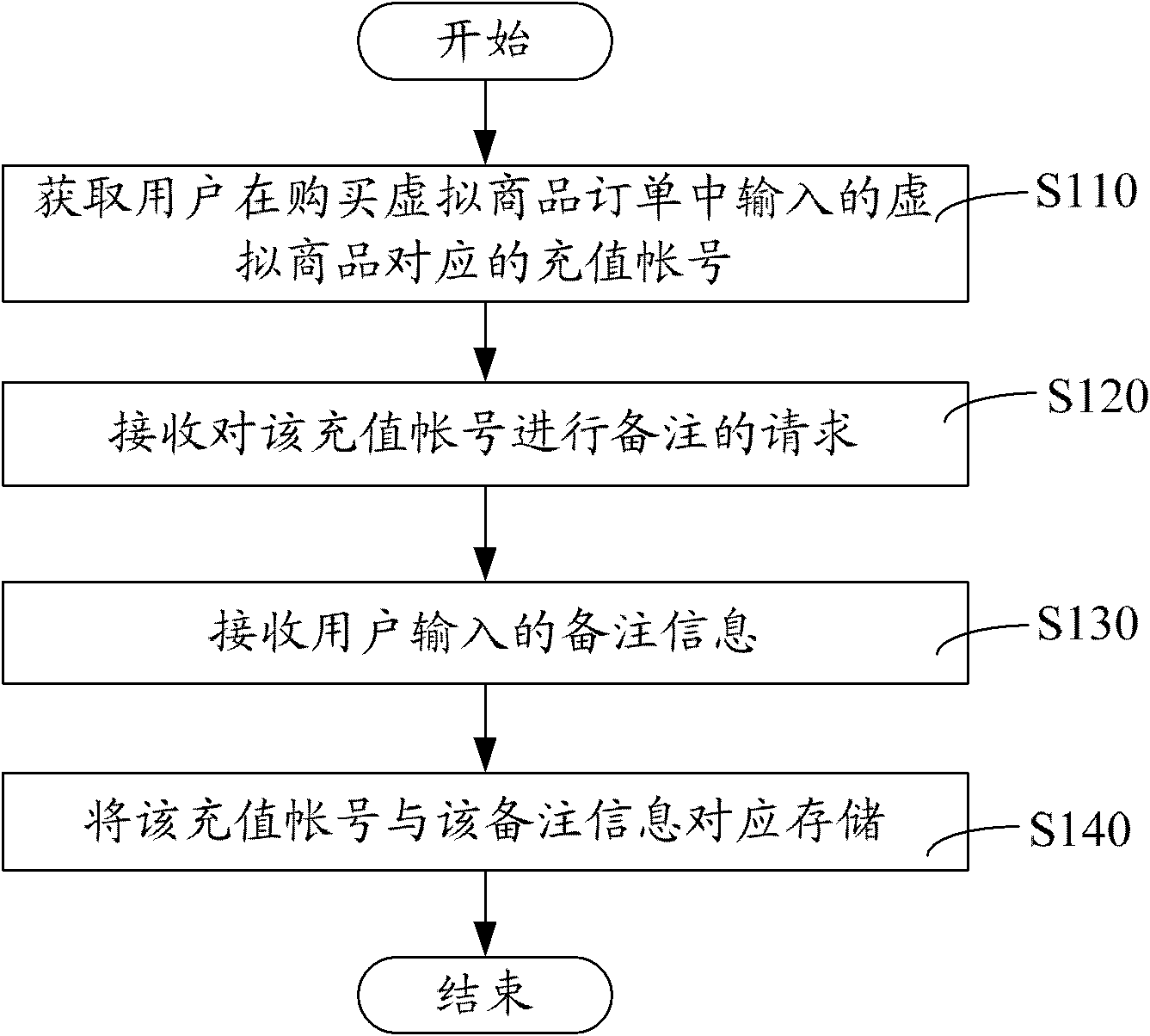
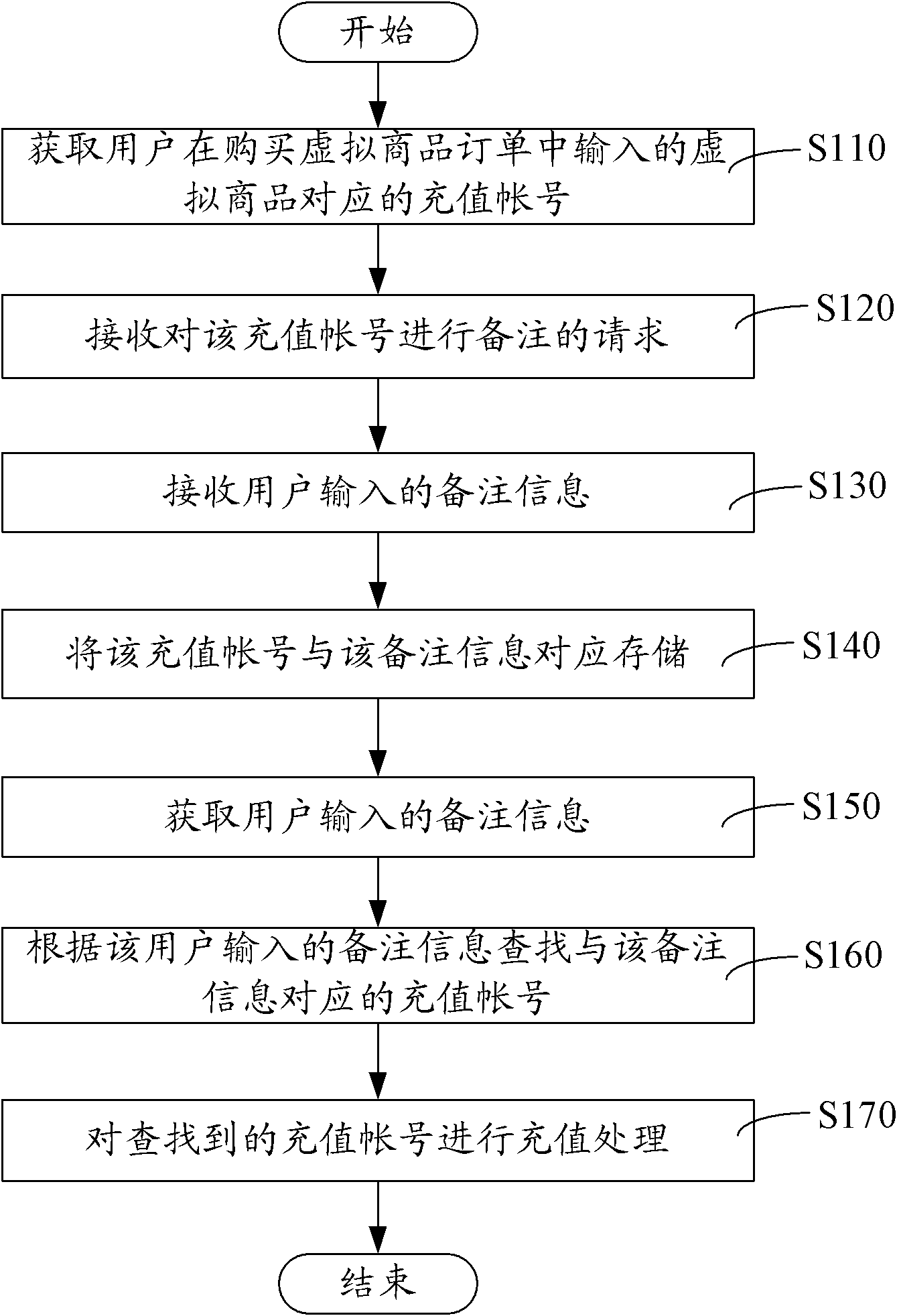
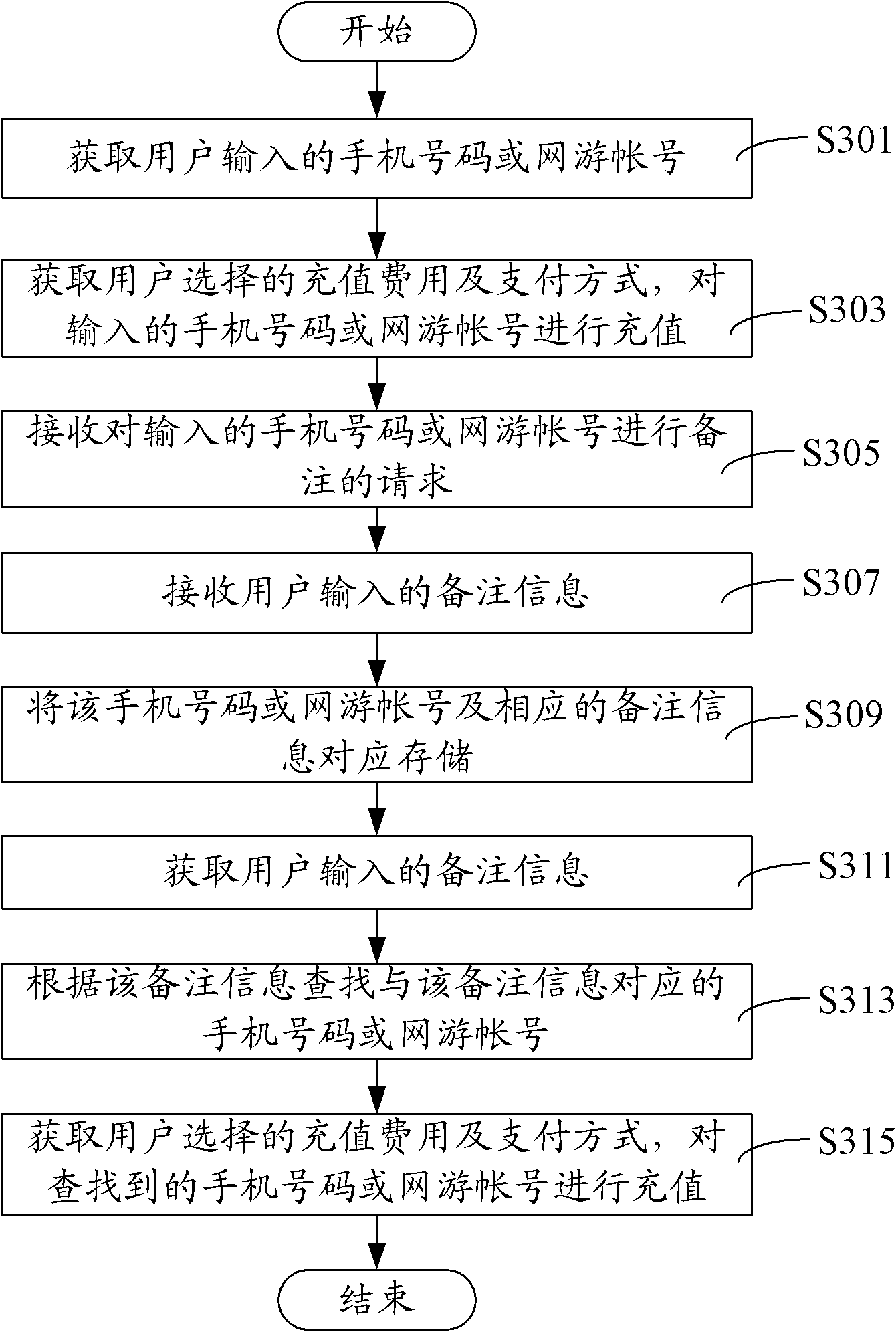
Method and system for virtual goods order comments
InactiveCN102915499AEasy to findEasy to operateCommercePrepayment telephone systemsUser inputOrder form
The invention relates to a method and a system for virtual goods order comments. The method includes the steps: acquiring a recharge account corresponding to virtual goods inputted into a virtual goods purchase order by a user; receiving a request for commenting the recharge account; receiving comment information inputted by the user; and correspondingly storing the recharge account and the comment information. By the method and the system for virtual goods order comments, the comment information inputted by the user is received according to the comment request after the recharge account corresponding to the virtual goods is acquired, the recharge account and the comment information are correspondingly stored, the comment information is added to the recharge account, the user searches the needed recharge account conveniently and rapidly according to the comment information without checking a mobile recharge account, operation is convenient, and misoperation is reduced.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Group creation method and server
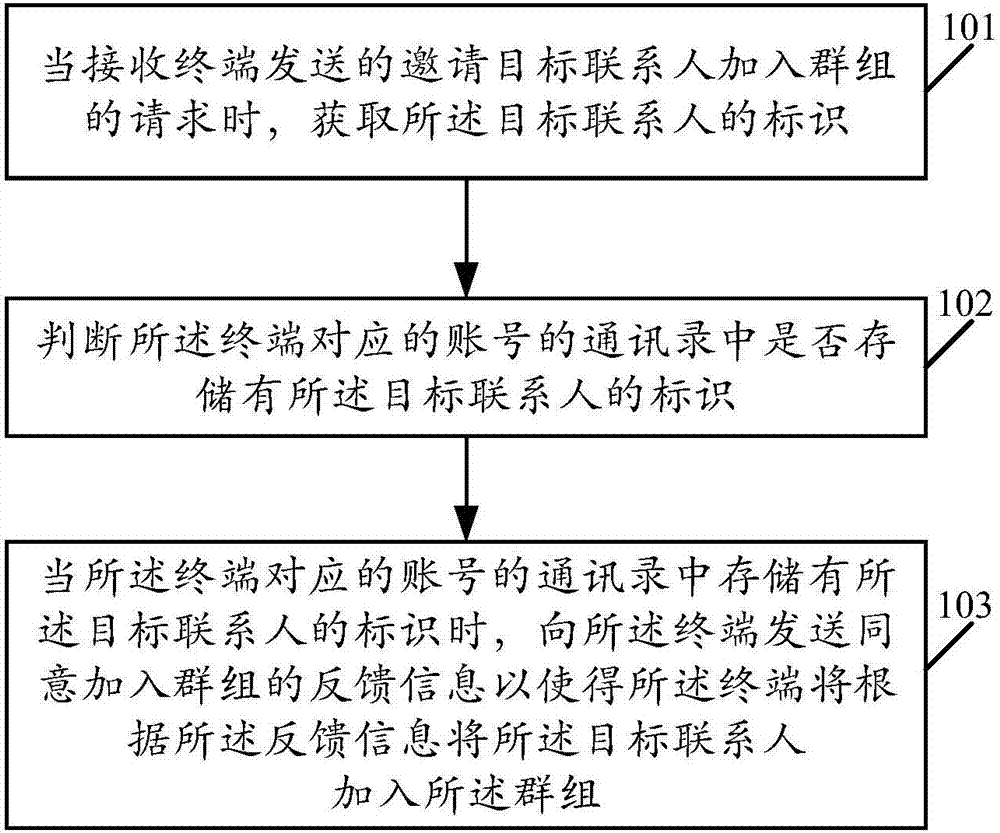
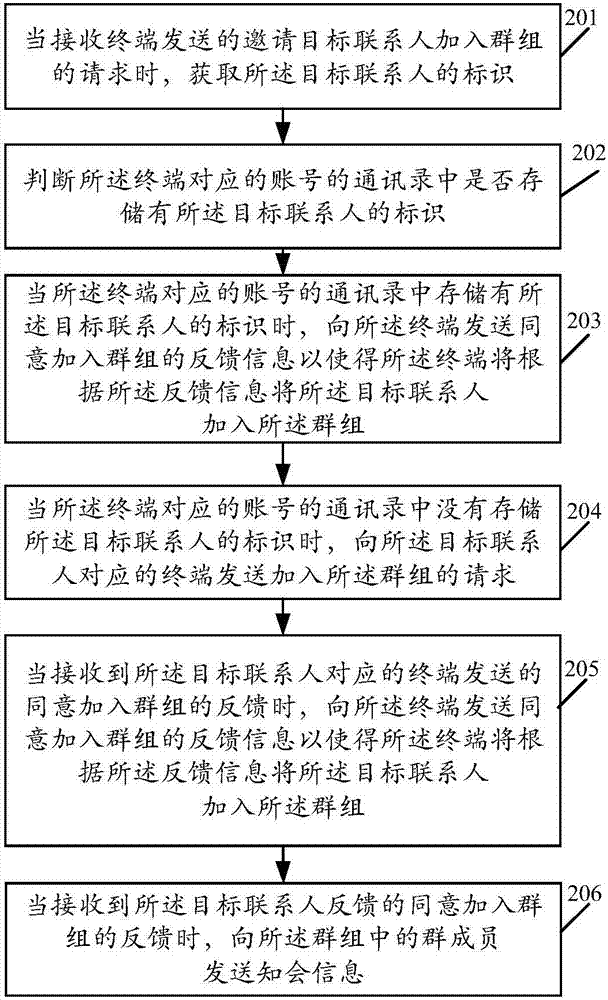
The invention provides the field of the Internet, and discloses a group creation method and a server. The method comprises the following steps: when a request of inviting a target contact to join a group sent by a terminal, obtaining an identifier of the target contact; judging whether the identifier of the target contact is stored in an address book of an account corresponding to the terminal; and if the identifier of the target contact is stored in the address book of the account corresponding to the terminal, sending feedback information of accepting the target contact to join the group to the terminal, wherein the feedback information is used for indicating the terminal to join the target contact in the group. By adoption of the above technical scheme, whether consultation is sent can be determined according to the identity of the invitee, when the invitee and the inviter are contacts of each other, the consultation is not generated, and the invitee is directly added to the chat group, thereby greatly improving the efficiency of group creation.
Owner:GUANGDONG OPPO MOBILE TELECOMM CORP LTD
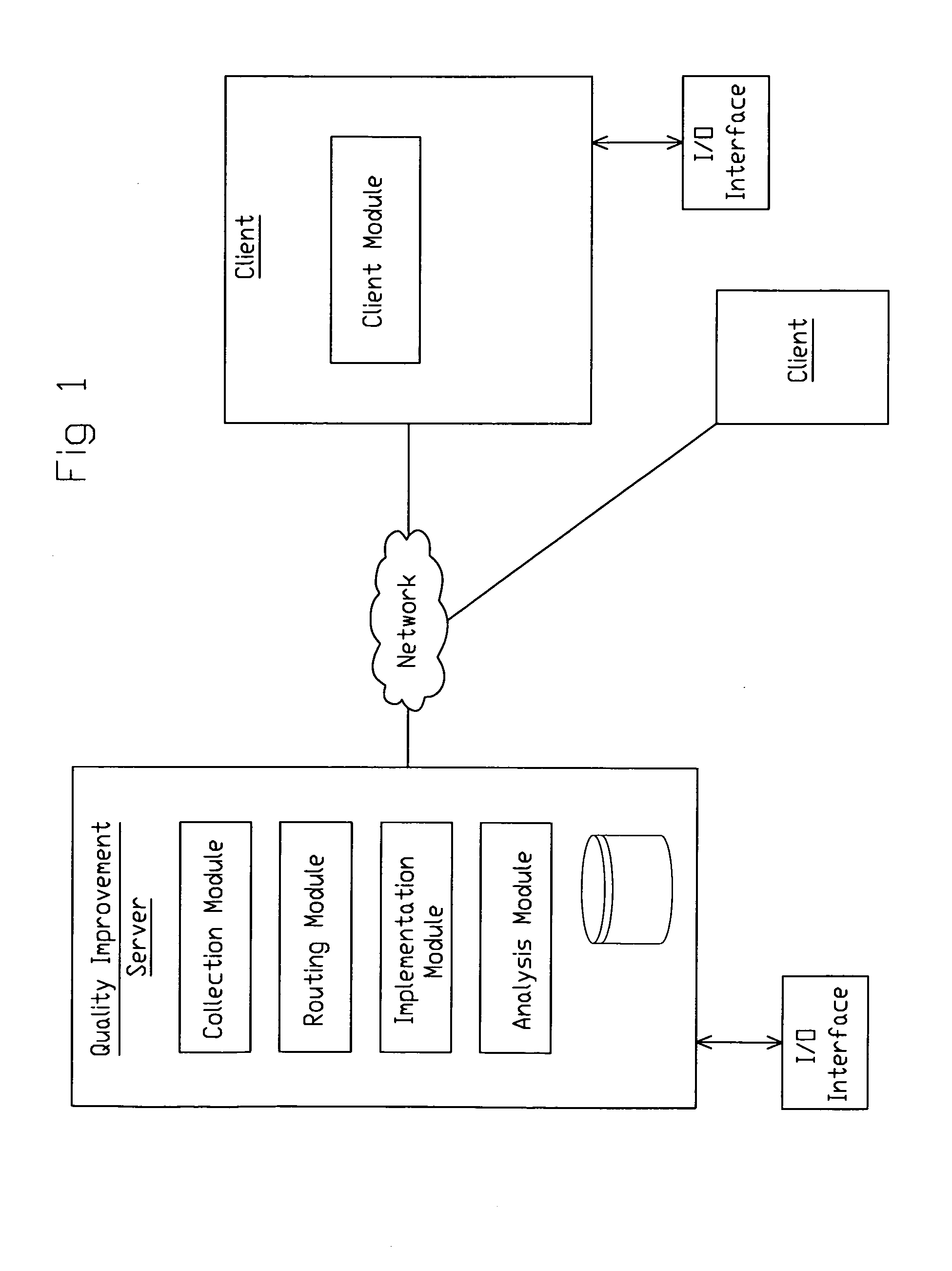
System and method for facilitating continous quality improvement
InactiveUS20120095799A1Facilitating continuous quality improvementQuality improvementResourcesKnowledge managementRequest for Comments
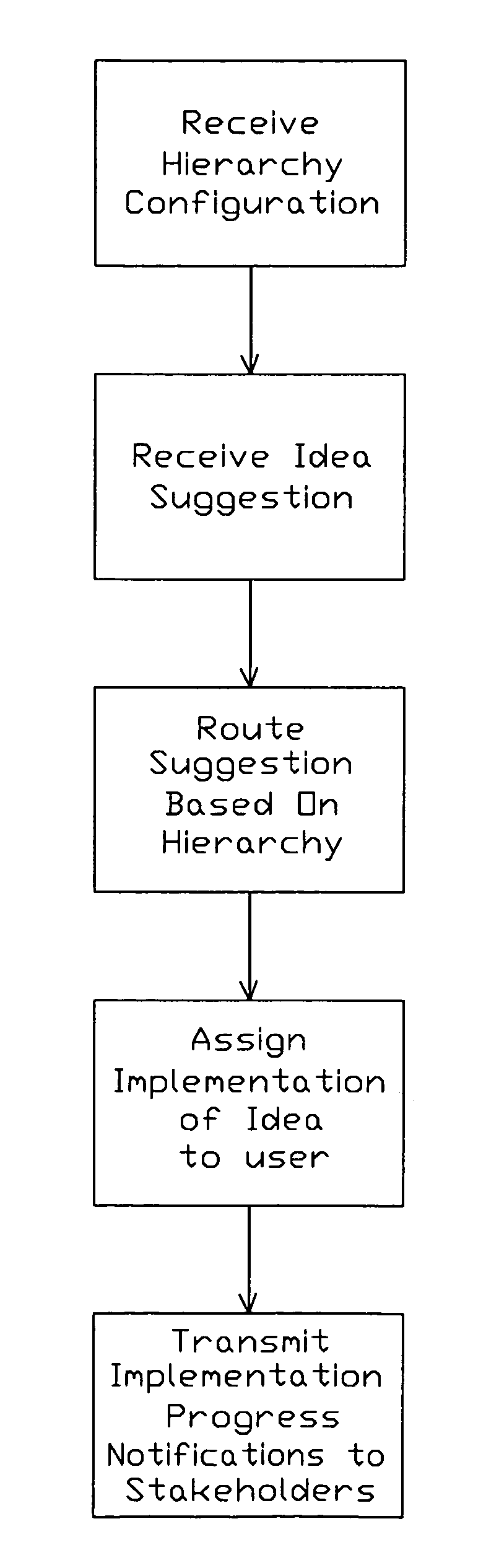
A quality improvement system and associated methods are contemplated. The quality improvement system is configured to collect and route ideas from and between users of the system. The routing of ideas may be based on a user hierarchy that is adaptable and scalable to support any organization desiring to utilize the contemplated system. The system may also be configured to assist users in evaluating and implementing collected ideas and to report on the impact of any implemented ideas. To facilitate and encourage the submission of ideas a process of challenging employees to provide ideas may also be provided. The process may be used by management to solicit ideas from employees and may be an incentive-based process.
Owner:JACOBSON GREGORY +1
Methods for secure and bandwidth efficient cryptographic synchronization
ActiveUS7725709B2Efficient synchronizationSynchronising transmission/receiving encryption devicesMultiple keys/algorithms usageTransmission protocolNetwork packet
Methods for cryptographic synchronization of data packets. A roll-over counter (ROC) value is periodically appended to and transmitted with a data packet when a function of the packet sequence number equals a predetermined value. The ROC effectively synchronizes the cryptographic transformation of the data packets. Although the disclosed methods are generally applicable to many transmission protocols, they are particularly adaptable for use in systems wherein the data packets are transmitted to a receiver using the Secure Real-Time Transport Protocol (SRTP) as defined in Internet Engineering Task Force (IETF) Request for Comments (RFC) 3711.
Owner:TELEFON AB LM ERICSSON (PUBL)
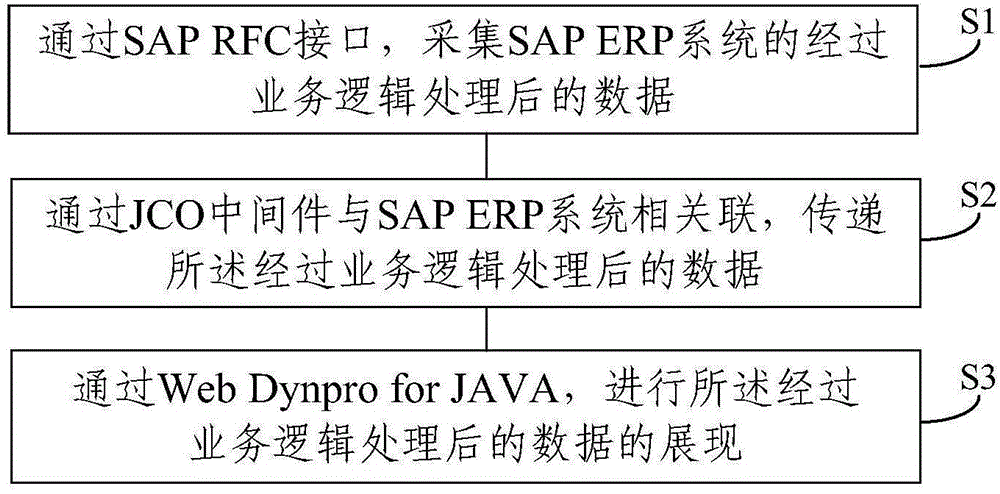
Method and system for processing data in an ERP (Enterprise Resource Planning) environment
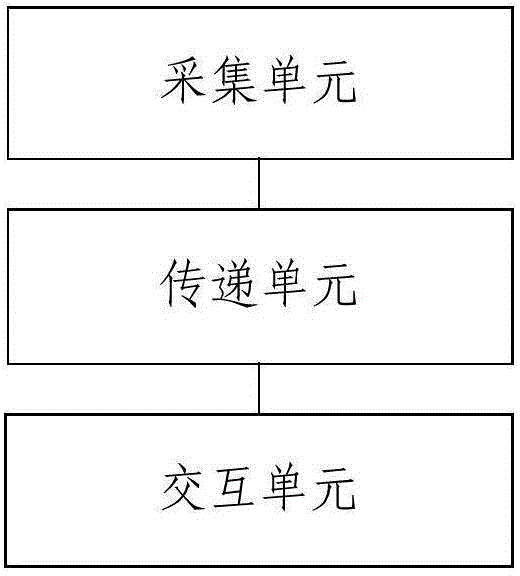
InactiveCN104484164AReal-time controlReal-time monitoringResourcesSpecific program execution arrangementsEnterprise resource planningMiddleware
The invention discloses a method and a system for processing data in an ERP environment; the method comprises the steps: acquiring data, subjected to business logical processing, of an SAP (Service Access point) ERP system by using an SAP RFC (Request For Comments) interface; correlating with the SAP ERP system by a JCO middleware and transferring the data subjected to the business logical processing; and exhibiting the data subjected to the business logical processing by using Web Dynpro for Java. The system comprises an acquisition unit for acquiring data, subjected to the business logical processing, of the SAP (Service Access point) ERP system by using the SAP RFC (Request For Comments) interface; a transfer unit for correlating with the SAP ERP system by a JCO middleware and transferring the data subjected to the business logical processing; and an interaction unit for interacting with users and exhibiting the data subjected to the business logical processing by using Web Dynpro for Java. The method and the system for processing data in the ERP environment are capable of managing, controlling and supervising engineering projects in real time.
Owner:朱敏
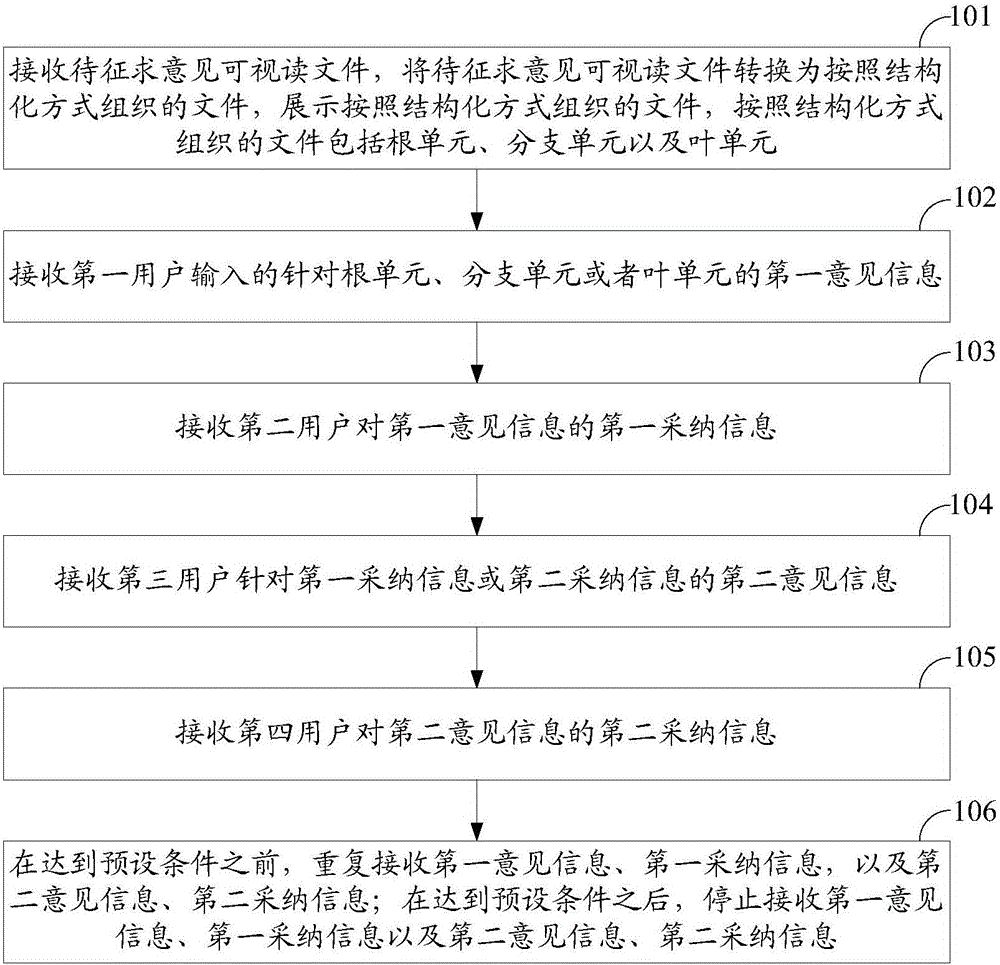
File processing method and device
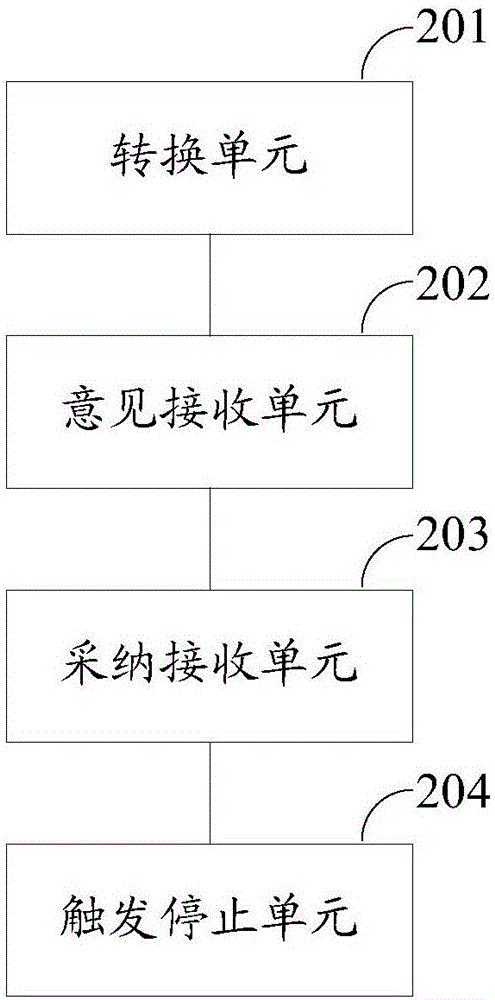
ActiveCN106599328ASeek advice comprehensivelyAvoid changeOffice automationFile access structuresUser inputSecond opinion
The invention discloses a file processing method and device, which can be used for increasing the efficiency of opinion collection and adoption of files and preventing from changing the working process of the opinion collection and adoption without authorization. The method comprises the following steps: receiving a file to be consulted, converting the visual and readable file to be consulted to a file which is organized based on a structured way, and displaying the file which is organized based on the structured way, wherein the the file which is organized based on the structured way comprises a root unit, a branch unit and a leaf unit; receiving the first opinion information which is input by a first user and aims at the root unit, the branch unit or the leaf unit; receiving the first adoption information of a second user to the first opinion information; receiving the second opinion information of a third user to the adoption information; receiving the second adoption information of a fourth user to the second opinion information, and returning to receive the second opinion information of the third user to the adoption information; and after achieving the preset conditions, stopping receiving the first opinion information, the first adoption information, the second opinion information and the second adoption information.
Owner:AGRICULTURAL BANK OF CHINA
Method for querying hierarchical node data
ActiveCN103744989ADoes not affect normal useImprove versatilityOther databases queryingSpecial data processing applicationsData retrievalData acquisition
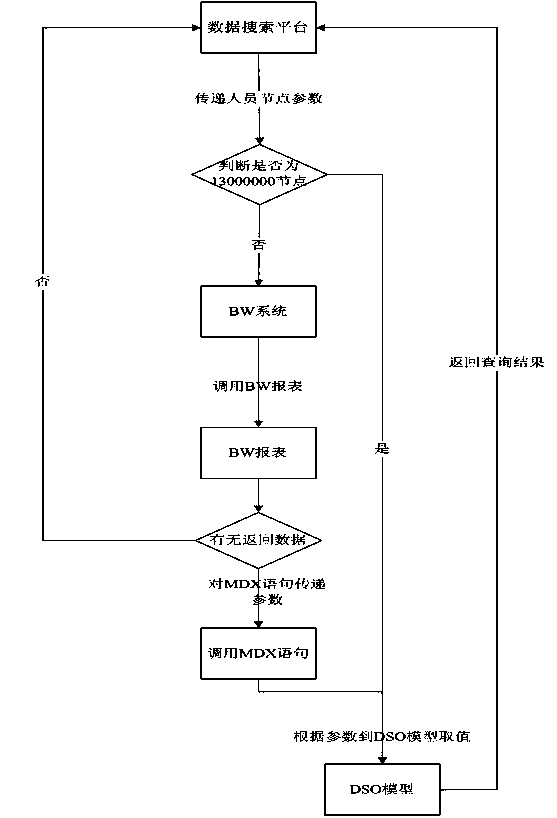
The invention discloses a method for querying hierarchical node data. By using the method, MDX (multidimensional expressions) statements, BWETL (band width extract transform and load) data extracting and RFC (request for comment) remote functions are invoked integrally, the hierarchical node data are queried, hierarchical nodes are inputted, and queried nodes are inputted on a data retrieval platform. The method for querying hierarchical node data comprises the following steps of examination on authorization: verifying authorization of inputted nodes and personnel using the method; parameter transmitting: transmitting parameters to a function if verification passes and performing specific data extracting operation; executing on a node report: invoking a BWQUERY node report according to the parameters after the parameters are received by the function; invoking of the MDX statements: invoking the MDX statements if data of the inputted nodes exist, transmitting the running result of the report to an inner table of the function and maintaining the running result as a queried parameter; and returning of the result: reading data from a DSO (digital storage oscilloscope) model according to the node parameters and limiting conditions of the function, and returning the result to the data retrieval platform to obtain the hierarchical node data. By using the method, the data acquisition efficiency is improved, and data uploading is stable.
Owner:STATE GRID CORP OF CHINA +3
Method, device and system for filtering content
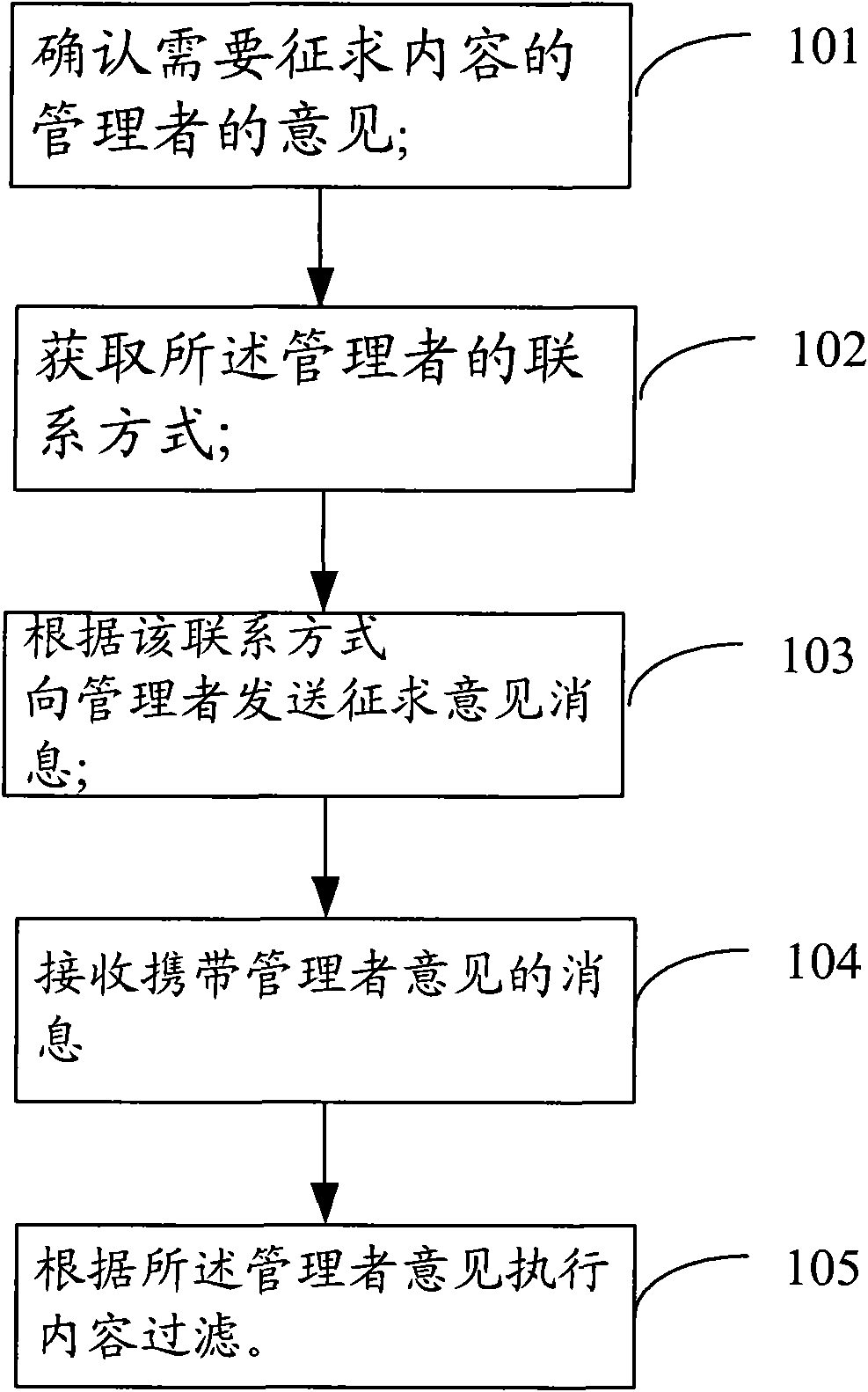
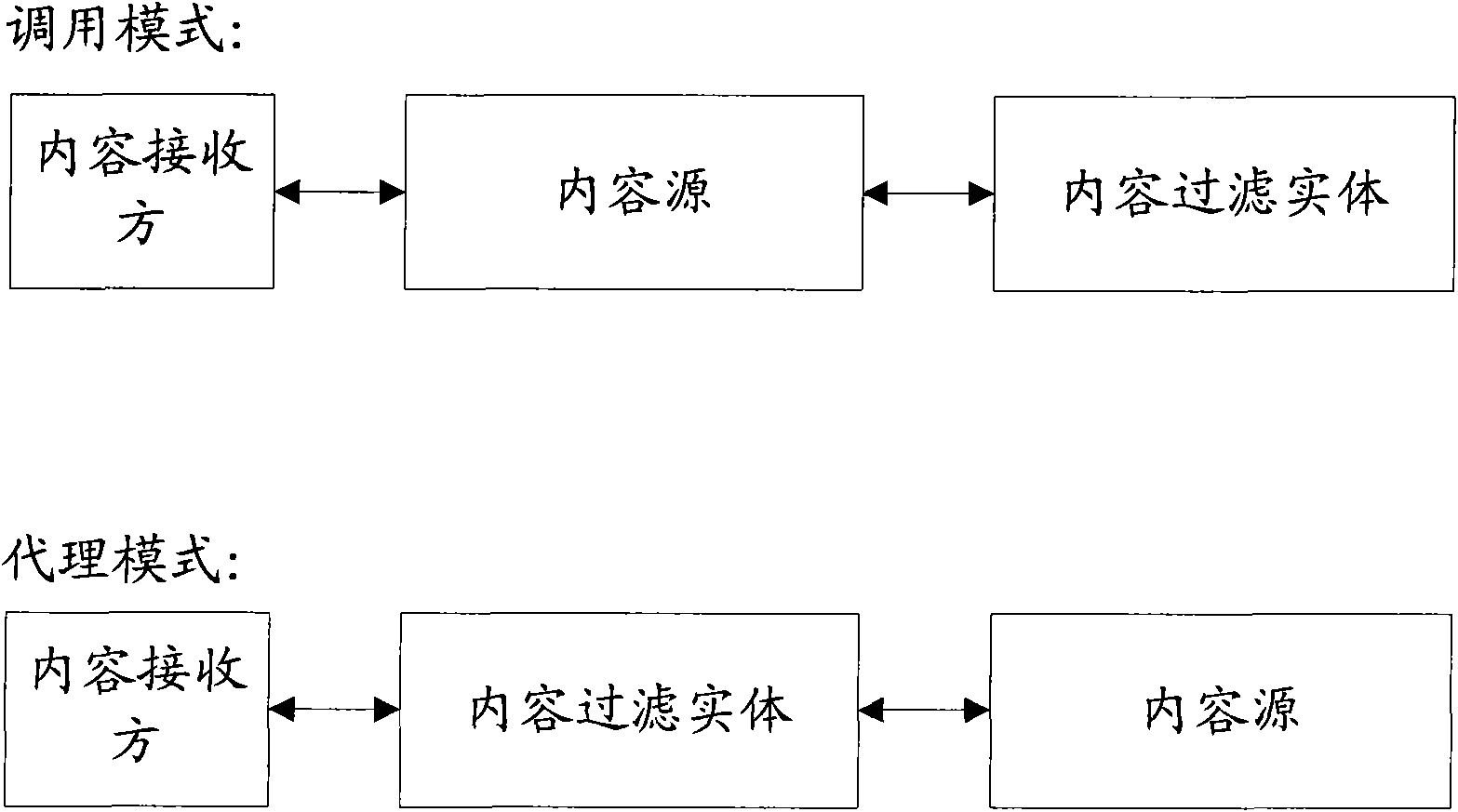
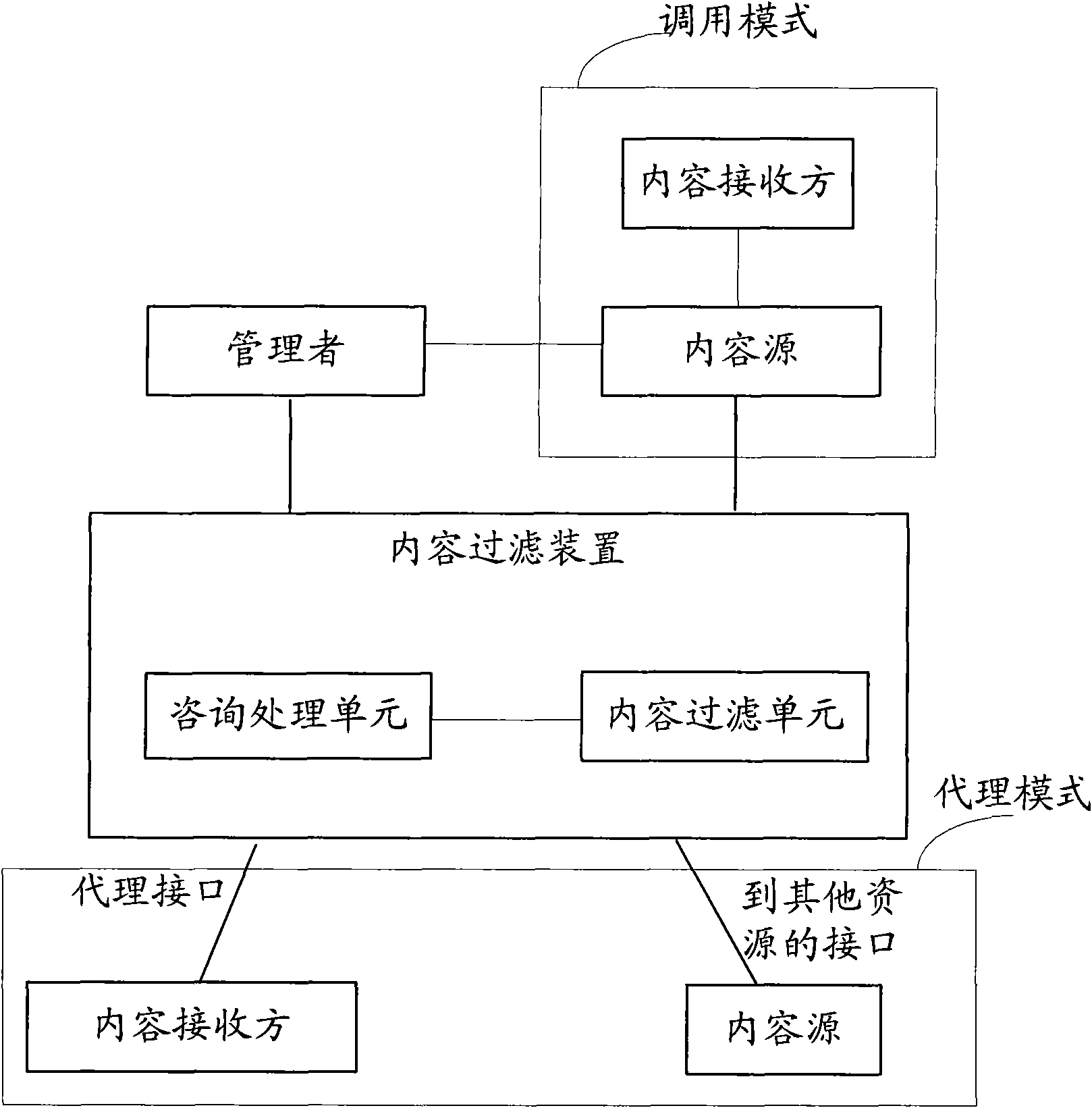
InactiveCN101674294AMeet the needs of personalized filteringData switching networksSpecial data processing applicationsPersonalizationFiltering rules
The invention provides a method for filtering content as well as a corresponding content filtering device, a content source and a system which are capable of using the method. The method comprises thefollowing steps: confirming comments of an administrator needing to ask for content according to filtering rules or a processing mode of the content filtering device; acquiring a contact way of the administrator; sending information for asking for comments to the administrator according to the contact way of the administrator, wherein the comments relate to filtering according to the condition ofthe content; receiving information which is sent by the administrator and carries the comments of the administrator; and filtering the content according to the comments of the administrator. By the method and the related device, the content filtering at a network side can be processed according to the comments of the administrator more flexibly, and therefore, demands of users for the personalized filtering of the content at the network side can be met.
Owner:HUAWEI TECH CO LTD
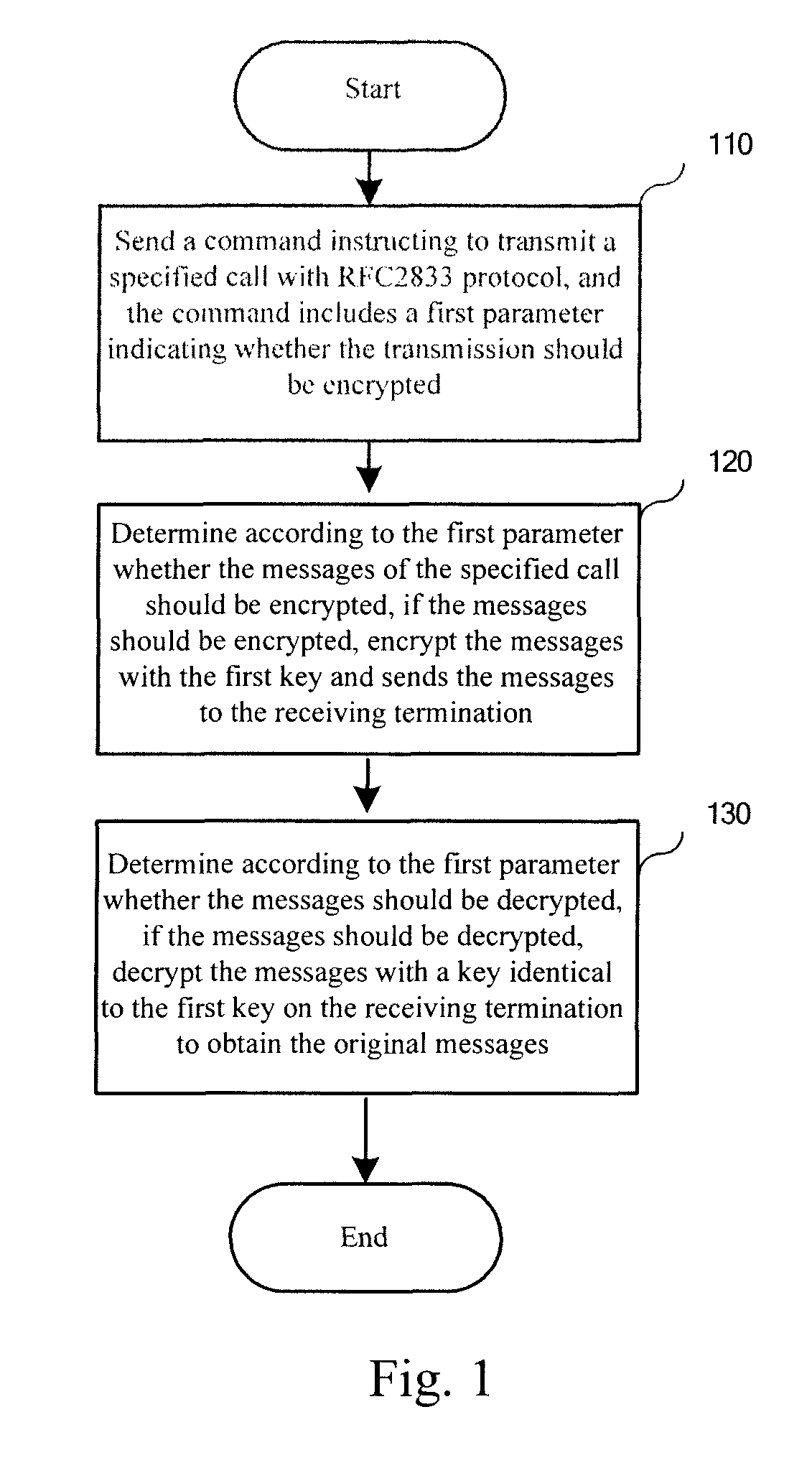
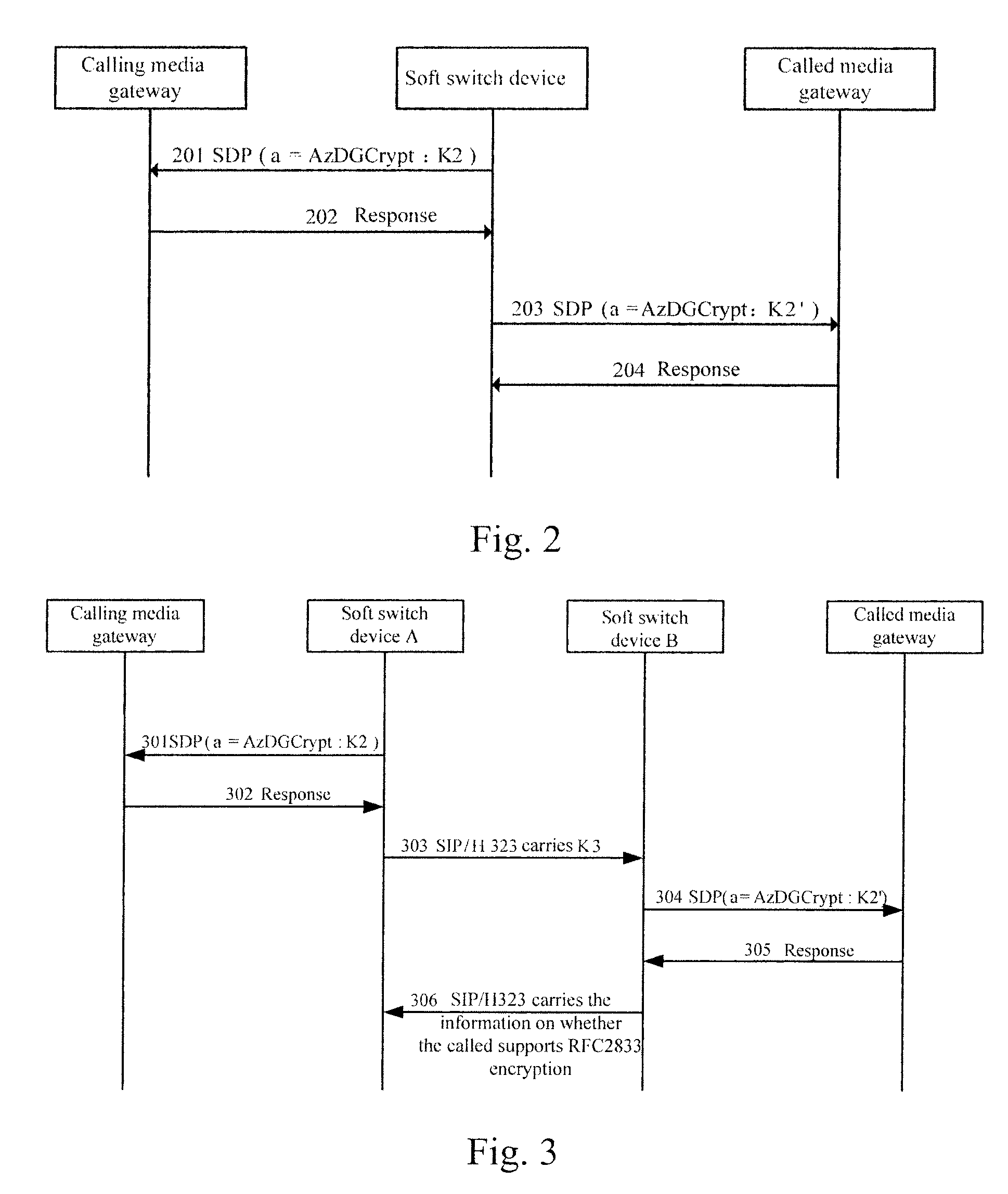
Method, media gateway and system for transmitting content in call established via media gateway control protocol
ActiveUS8181013B2Keep Content SafeImprove securitySecuring communicationSelection arrangementsPlaintextSoftswitch
Owner:HUAWEI TECH CO LTD
Formal detection method and system for malicious url
ActiveCN102843271BImprove the detection rateGood detection rateData switching networksSoftware engineeringFeature data
The invention discloses a formalization detection method for a malicious URL (uniform resource locator). The formalization detection method comprises the following steps of: splitting the URL to be detected into syntactic element character strings according to a URL syntactic structure on the basis of the standard of RFC (request for comments); extracting designated character strings from the character strings obtained by splitting; performing completing treatment on the non-existent character strings; reordering the character strings obtained after completing treatment to obtain a new URL, and calculating the hash value of the new URL; and traversing a malicious URL feature library, and performing contrast detection on feature data in the malicious URL feature library and the hash value of the URL to be detected. The invention further discloses a formalization detection system for the malicious URL. The technical scheme disclosed by the invention can be effectively used against the variability in the formats of the URL; and compared with the traditional URL detection method, the detection rate against the malicious URL which often changes the format is higher, and a single feature can also be adopted for corresponding to multiple format variants of the malicious URL, so that the volume of a virus feature library required for the detection method is smaller, and the space of a memory and a magnetic disk can be further saved.
Owner:HARBIN ANTIY TECH
A method and device for realizing pim multicast in VRRP network environment
ActiveCN103227724BEnable co-deploymentSolve the problem that multicast cannot be deployed at the same timeSpecial service provision for substationProtocol Independent MulticastVirtual Router Redundancy Protocol
The invention discloses a method for realizing PIM multicast in a VRRP network environment, by carrying a virtual IP address when sending a PIM Hello message on an interface enabled with VRRP, and using VRRP when receiving the PIM Hello message The establishment of PIM neighbors with virtual IP addresses can enable unicast and multicast services to be active and standby at the same time in the VRRP network environment. At the same time, it is fully compatible with the current RFC protocol, which solves the problem that VRRP and multicast cannot be deployed at the same time. At the same time, it also discloses a device for realizing PIM multicast in a VRRP network environment, including a sending module and a receiving module. The router of the packet establishes a PIM neighbor relationship with a real address or a virtual IP address. The invention has simple protocol and flexible deployment, can realize the co-deployment of VRRP and multicast, and allows active and standby of unicast and multicast at the same time.
Owner:北京华三通信技术有限公司
Information transmission method, media gateway and base station controller
InactiveCN103888985ASolve the problem of failure of some operation and maintenance functionsSolve the problem of failure of operation and maintenance functionsWireless communicationInformation transmissionMultiple frequency
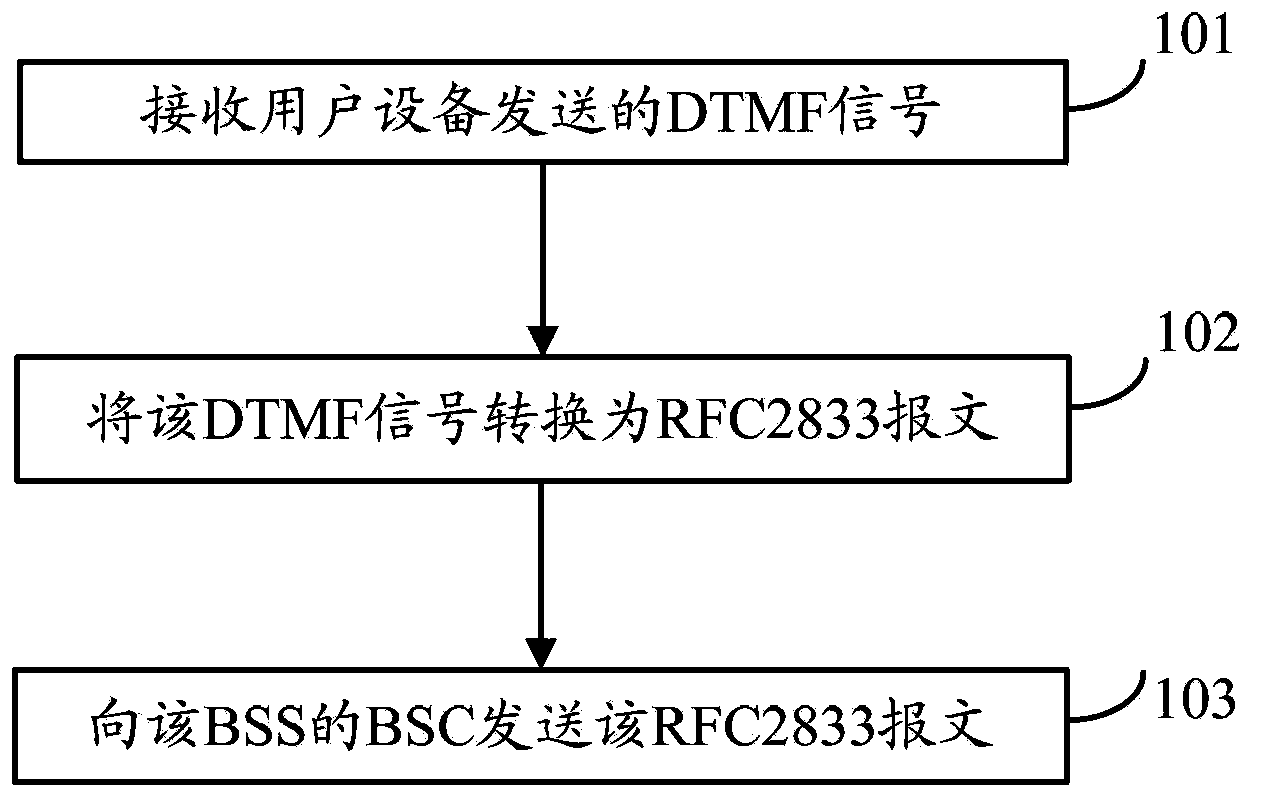
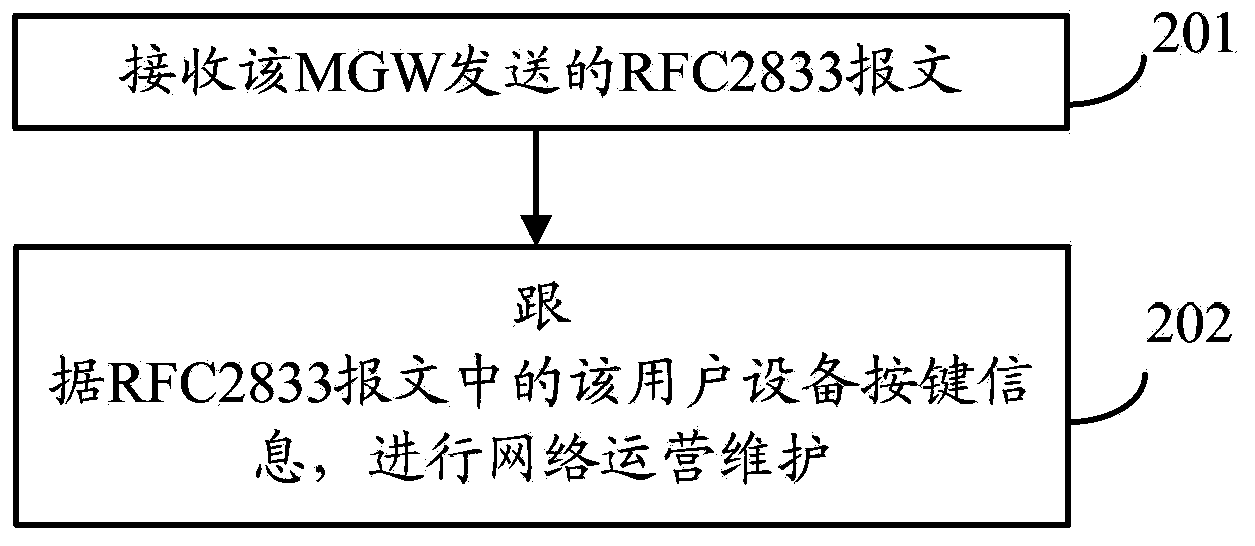
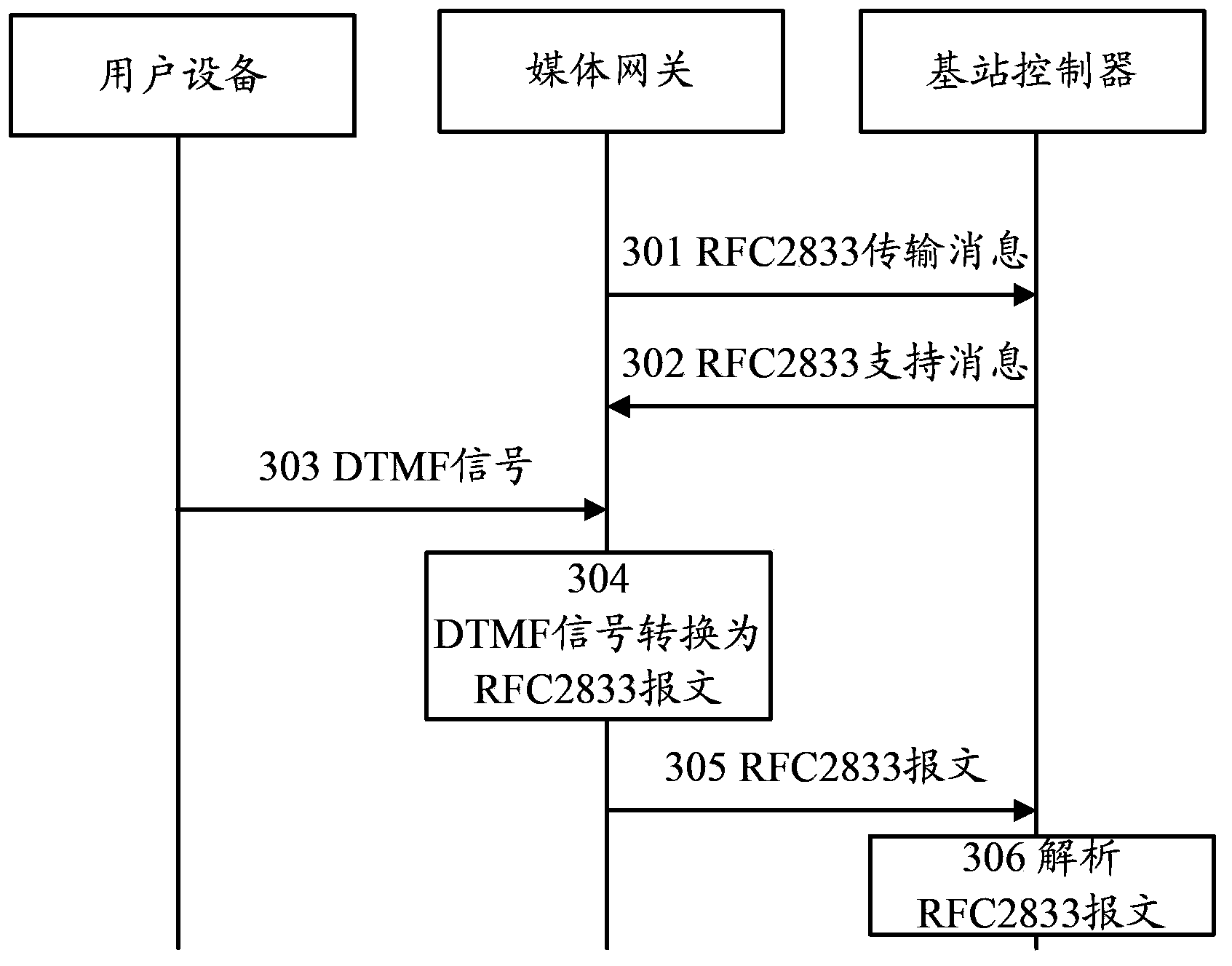
The invention provides an information transmission method, a media gateway and a base station controller. The method comprises: under the condition of IP (internet protocol) conversion of an A interface, receiving DTMF (dual tone multiple frequency) signals sent by user equipment, the DTMF signals comprising button information of the UE (user equipment); converting the DTMF signals into RFC2833 (request for comment 2833) messages, the RFC2833 messages comprising the button information of the use equipment; and sending the RFC2833 messages to the BSC (base station controller) of a BSS (base station subsystem). Since the DTMF signals comprising the button information of the UE are converted into the RFC2833 messages comprising the button information of the user equipment, in the BSS, the button information of the user equipment can be obtained by directly using the BSC to parse the RFC2833 messages, and the operation maintenance of a network is carried out according to the button information of the user equipment, so that the problem of partially failed operation maintenance functions caused by the lack of a transcoder (TC) in the BSS after the conversion of the A interface is solved.
Owner:HUAWEI TECH CO LTD
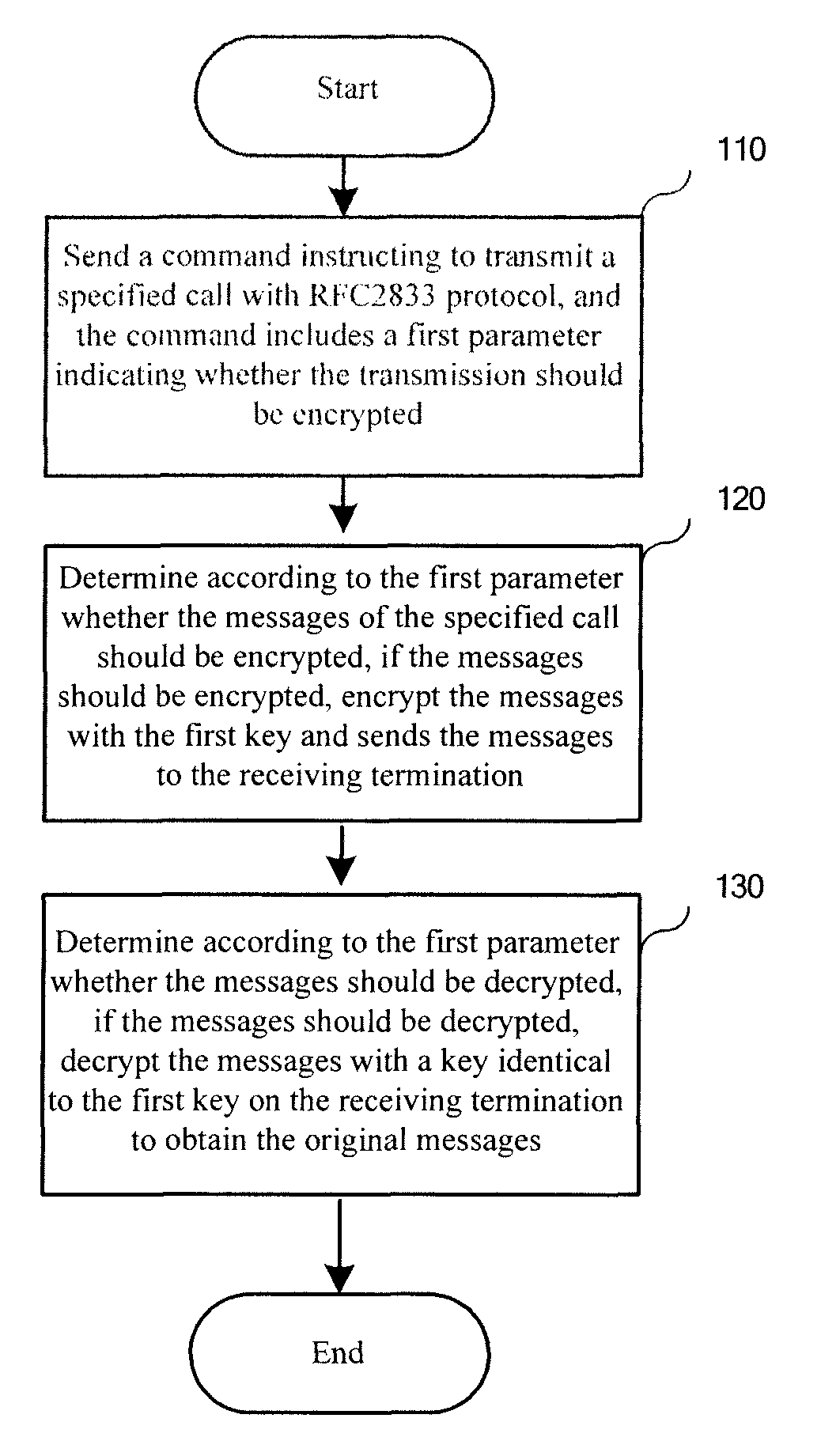
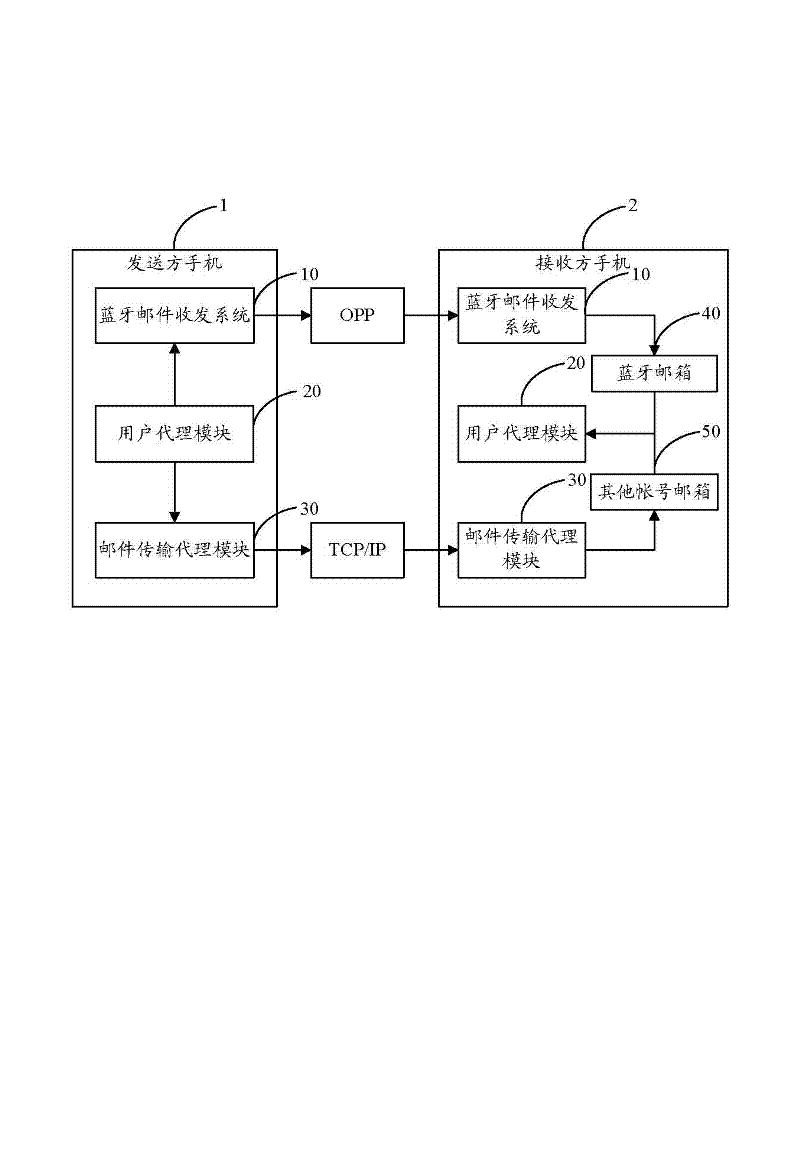
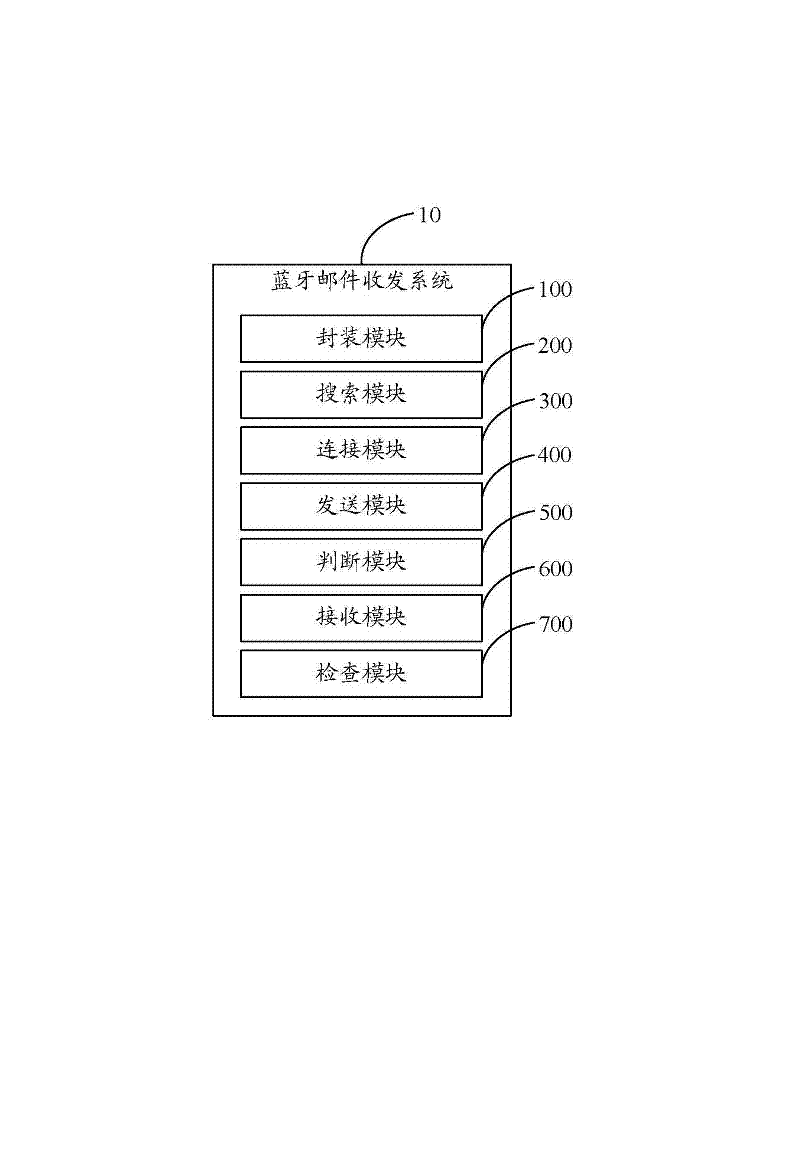
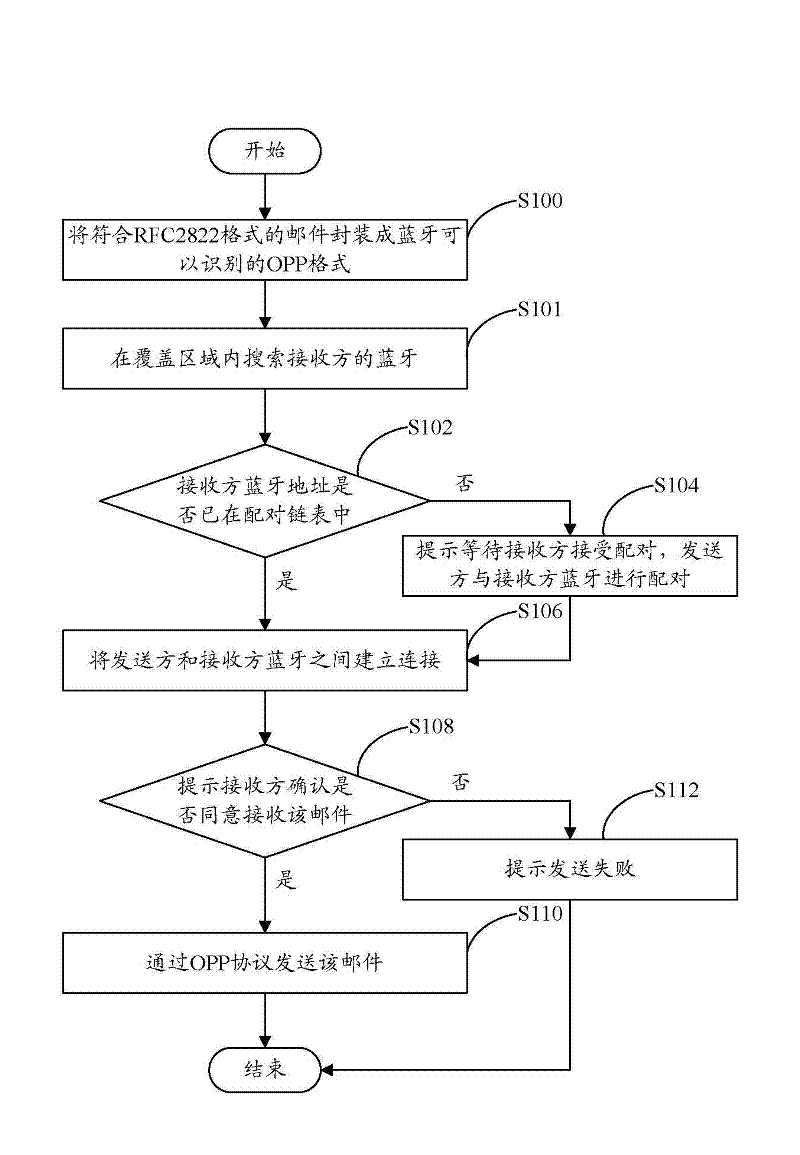
Email receiving and sending system and method implemented by using Bluetooth
InactiveCN102684749ANo traffic feeNear-field transmissionNetwork topologiesTraffic capacityBluetooth
The invention discloses an email receiving and sending system implemented by using Bluetooth. The system comprises a packaging module, a search module, a connection module and a sending module, wherein the packaging module is used for packaging emails conforming to an RFC2822 (request for comments) format into an OPP (object push profile) format which can be identified by Bluetooth; the search module is used for searching the Bluetooth of a receiving party in a coverage area; the connection module is used for reading a Bluetooth matching chain list of a sending party, and establishing a connection between the Bluetooth of the sending party and the Bluetooth of the receiving party; and the sending module is used for prompting the receiving party to confirm whether to agree to receive the email, when the receiving party refuses to receive the email, prompting a situation of failing to send the email and ending the operation, and when the receiving party agrees to receive the email, sending the email through an OPP protocol. The invention also provides an email receiving and sending method implemented by using Bluetooth. According to the invention, an effect of sending and receiving emails by using Bluetooth in a mobile phone can be achieved, operations of email sending and receiving are convenient and quick, and no flow fee is required to be paid.
Owner:SHENZHEN FUTAIHONG PRECISION IND CO LTD +1
Method for realizing communication of enterprise switchboard
ActiveCN102427565ARelieve pressureImprove operational efficiencySpecial service for subscribersSelection arrangementsComputer hardwareNetwork packet
The invention discloses a method for realizing communication of an enterprise switchboard. The method comprises the following steps: DTMF (Dual-Tone Multi-Frequency) data formed into a data packet according to the set rule and format so that the data is sent in an extended RFC (Request for Comments) format; after a user and the switchboard establish connection, the data packet in the extended RFC format is sent to the switchboard through a client side, and then the switchboard receives the data packet in the extended RFC format and analyzes the data packet to obtain personal information of the user; a menu drive unit drives a menu to be automatically displayed on a display unit of the client side when the user dials the number of the switchboard, and then the user can select the needed functions according to the menu; the client side sets conversation information and operation information in the data packet in the extended RFC format sent to the switchboard; and the switchboard receives the data packet in the extended RFC format and analyzes the data packet to obtain the conversation information and the operation information so as to further perform subsequent operation according to the obtained information. The method disclosed by the invention has the beneficial effects that the standard RFC format is extended, and the personal information of the user, the conversation information and the operation information are set in the newly added field add, which can reduce pressure on a background server of the switchboard and improve the operating efficiency.
Owner:杭州世导通讯有限公司
Multi-stage hierarchical bandwidth management method
ActiveCN102185777BLow costConsiderable cost savingsData switching networksExtensibilityPeak information rate
The invention discloses a multi-stage hierarchical bandwidth management method, which comprises the following steps of: A10, configuring CIR (Committed Information Rate) and PIR (peak Information Rate) (or EIR (Excess Information Rate)) of each stage of scheduling node according to a business model, wherein the CIR of the node is set according to the bandwidth purchased by a user in the first stage, the bandwidth distribution principle of each node from the second stage of scheduling is shown in the description, EIRni=PIRni-CIRni, and n is not less than 2; and A20, respectively marking messages as green, yellow or red by using MEF (Managed Extensibility Framework), RFC2697 (Request for Comments 2697) or RFC2698 algorithms in the first stage, configuring each node into a color sensitive mode and a coupling mode from the second stage, and shaping the traffic according to the MEF algorithm. By using the invention, the multi-stage hierarchical bandwidth management is realized on an exchanging chip supporting the MEF Traffic Shaping algorithm without need of special ASIC (Application Specific Integrated Circuits) or hardware; and the requirements are satisfied through updating software under the situation of changing or updating the business so that considerable hardware cost is saved; and the bandwidth distribution algorithm of the hierarchical business model is simple and convenient for web masters to configure.
Owner:FENGHUO COMM SCI & TECH CO LTD
Interaction method and user equipment
Owner:BEIJING ZHIGU RUI TUO TECH
Fault-tolerant mechanism optimised for peer to peer network
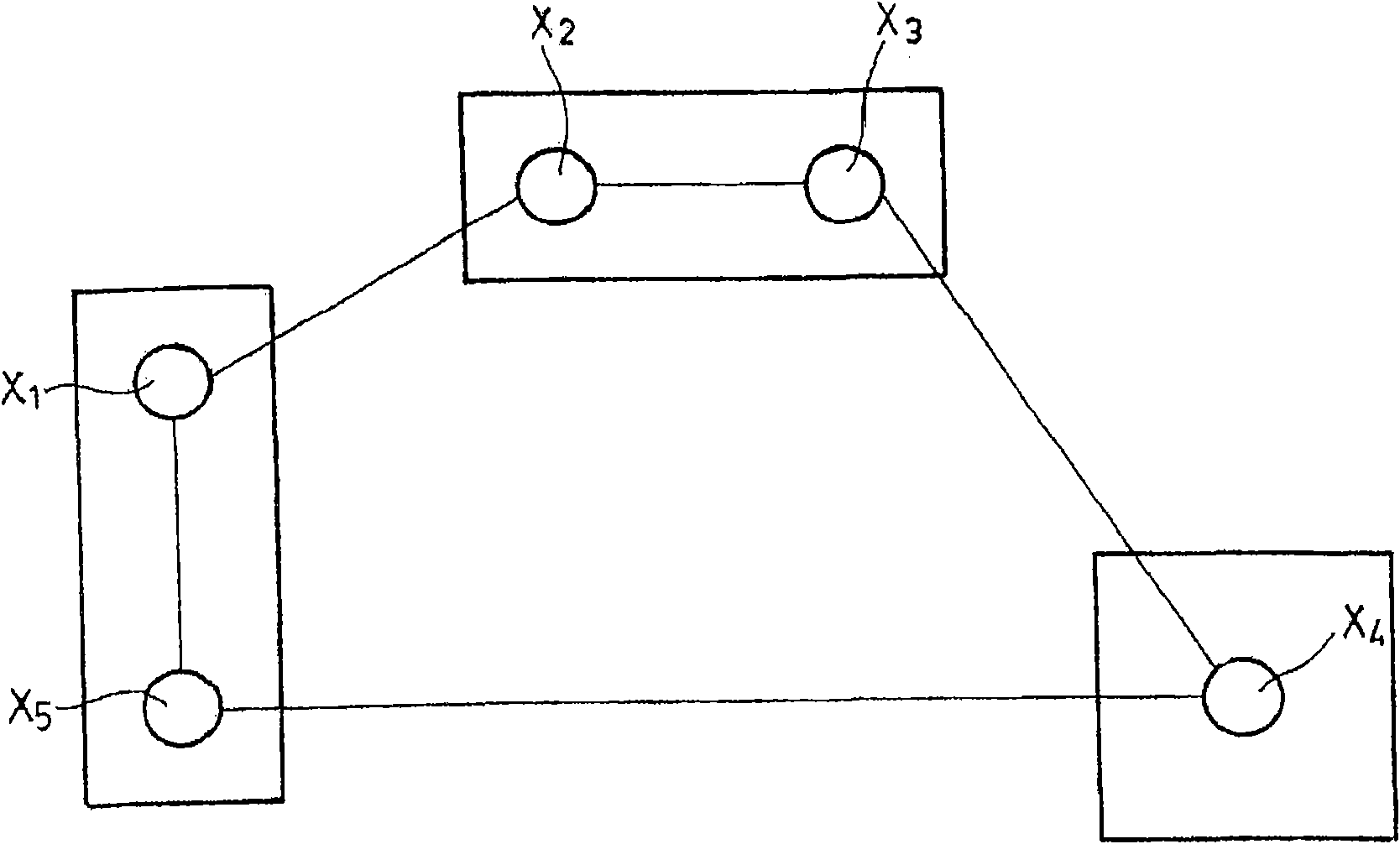
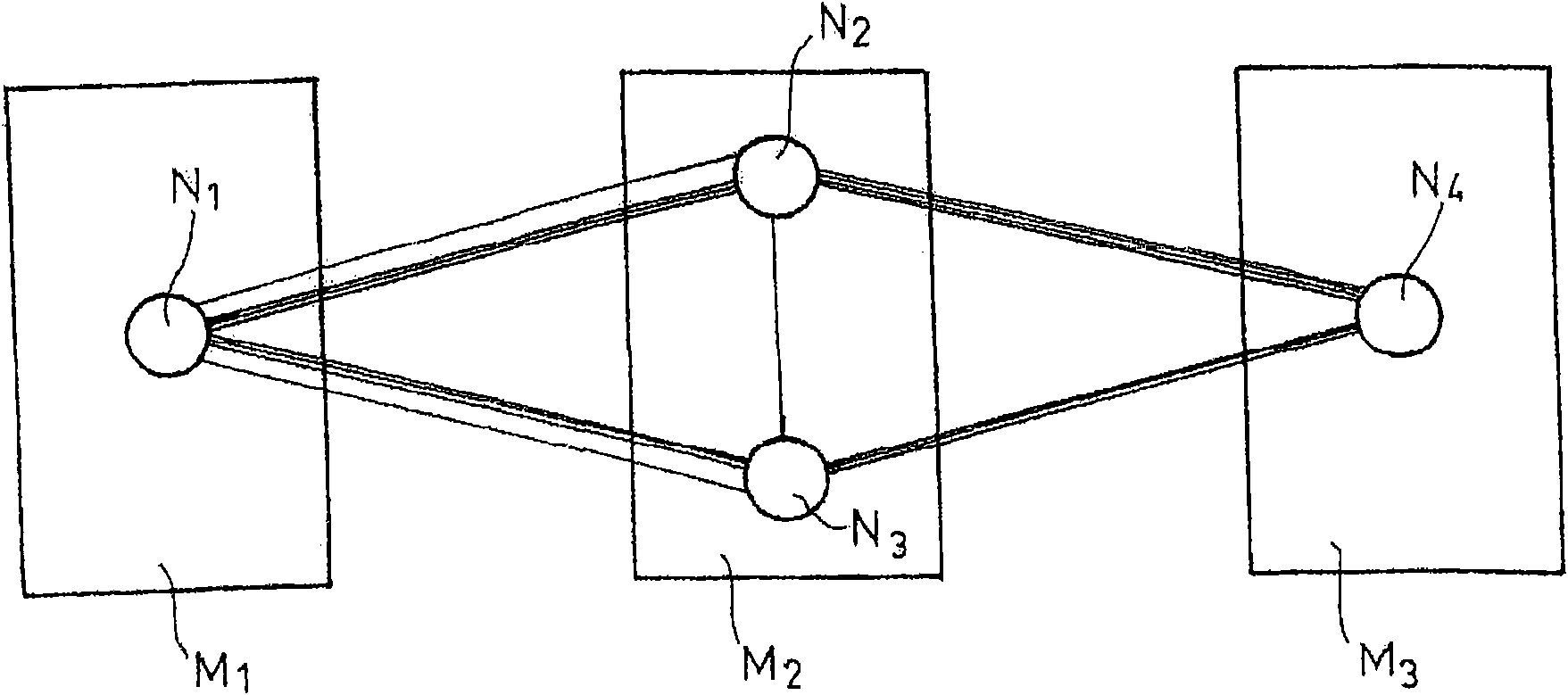
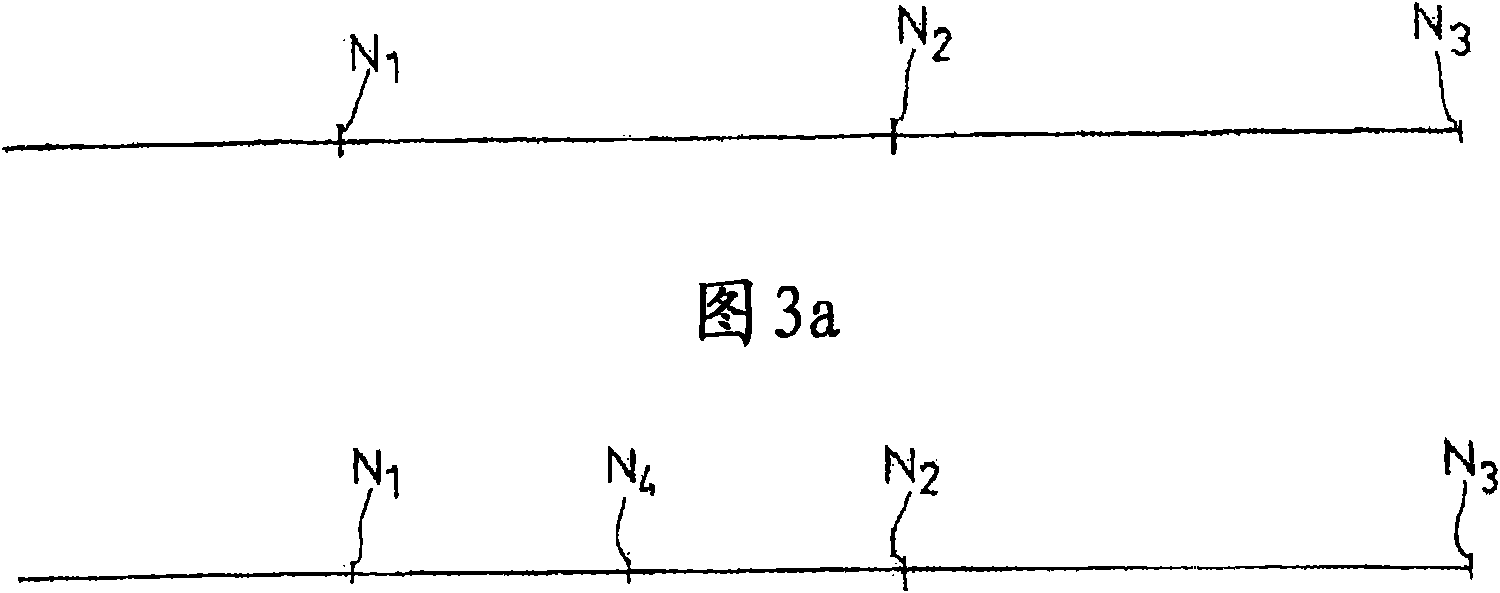
#CMT# # / CMT# The device has an admission unit i.e. admission component, for inserting a new node within a peer-to-peer network (Np2p) of a communication element (E1) e.g. application server in a communication architecture, where the network is composed of nodes (N1-N5). The admission unit determines the adjacent nodes deployed on a same processing equipment, and inserts the new node between the nodes. The nodes (N1-N5) are arranged in circular form such that each node possesses a single successor node and a single predecessor node. #CMT# : # / CMT# An independent claim is also included for a communication element comprising a peer-to-peer network. #CMT#USE : # / CMT# Device for managing a peer-to-peer network of a communication element (claimed) e.g. application server in a communication architecture i.e. Internet protocol multimedia subsystem architecture, or signaling element e.g. proxy conforming to a session initiation protocol defined by Request for Comments (RFC) 3261 of Internet Engineering Task Force (IETF), or call session control function within the architecture. #CMT#ADVANTAGE : # / CMT# The device is configured such that two of the nodes are not present in the same processing equipment, thus limiting the simultaneous failure of the nodes, while eliminating the need for changing fault-tolerant mechanisms. #CMT#DESCRIPTION OF DRAWINGS : # / CMT# The drawing shows a schematic view of a communication element. E1, E2 : Communication equipments LB : Load distribution module Np2p : Peer-to-peer network N-TEL : Communication network N1-N5 : Nodes.
Owner:ALCATEL LUCENT SAS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com