Formal detection method and system for malicious url
A detection method and detection system technology, which can be applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as missed reports of antivirus software, and achieve the effect of high detection rate and good detection rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] In order to enable those skilled in the art to better understand the technical solutions in the embodiments of the present invention, and to make the above-mentioned purposes, features and advantages of the present invention more obvious and easy to understand, the technical solutions in the present invention will be further detailed below in conjunction with the accompanying drawings illustrate.
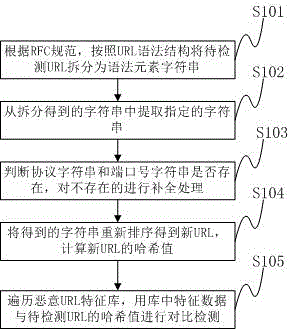
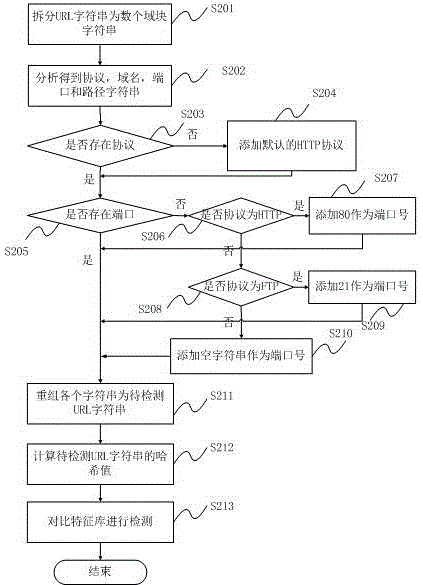
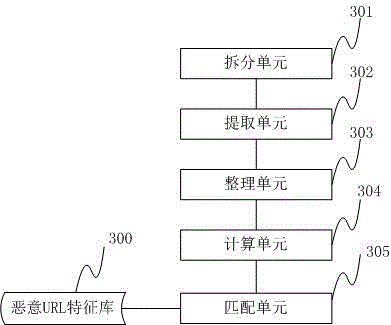
[0036] The present invention aims at the variability of the character string format of the malicious URL link address, and regularizes the character string format, abandons the part that is changeable and meaningless to detection, supplements the part that is omitted by default, and forms a composition that contains enough Informative data to be detected. The string format of the regularized URL address is "scheme: / / domain:port / path", which retains the protocol, domain name, port, and path. These data can completely determine the address information pointed to by a URL, so th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com