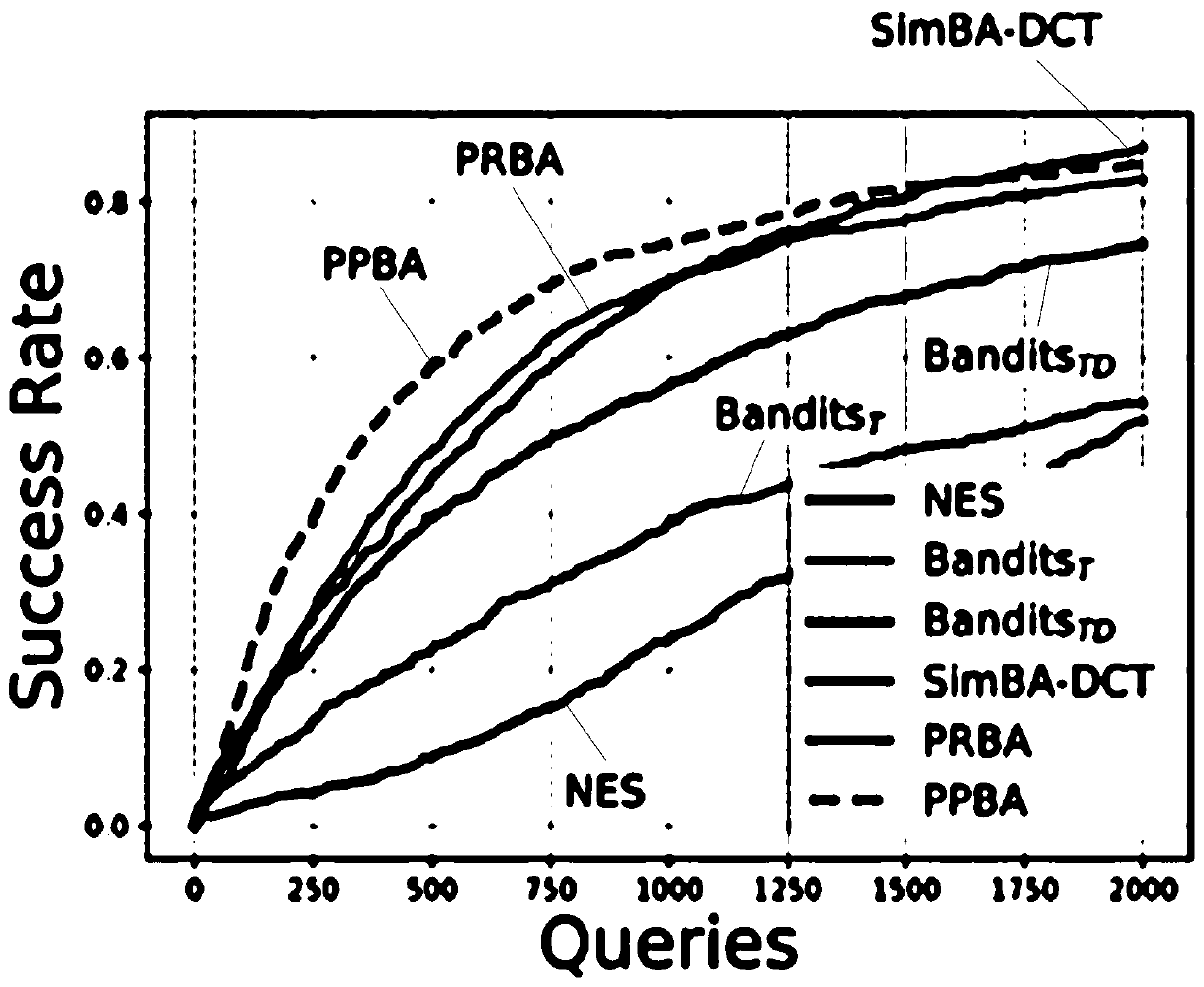
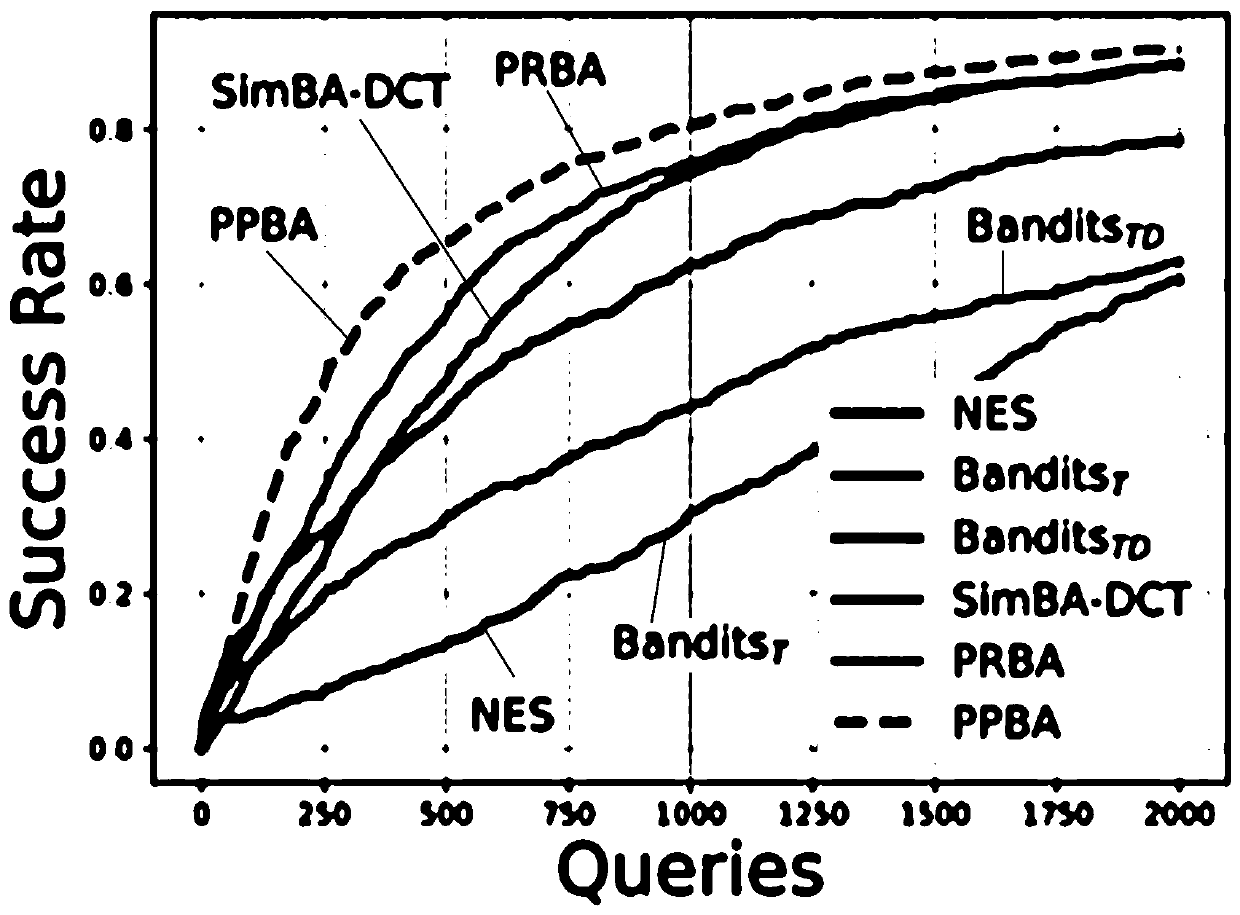
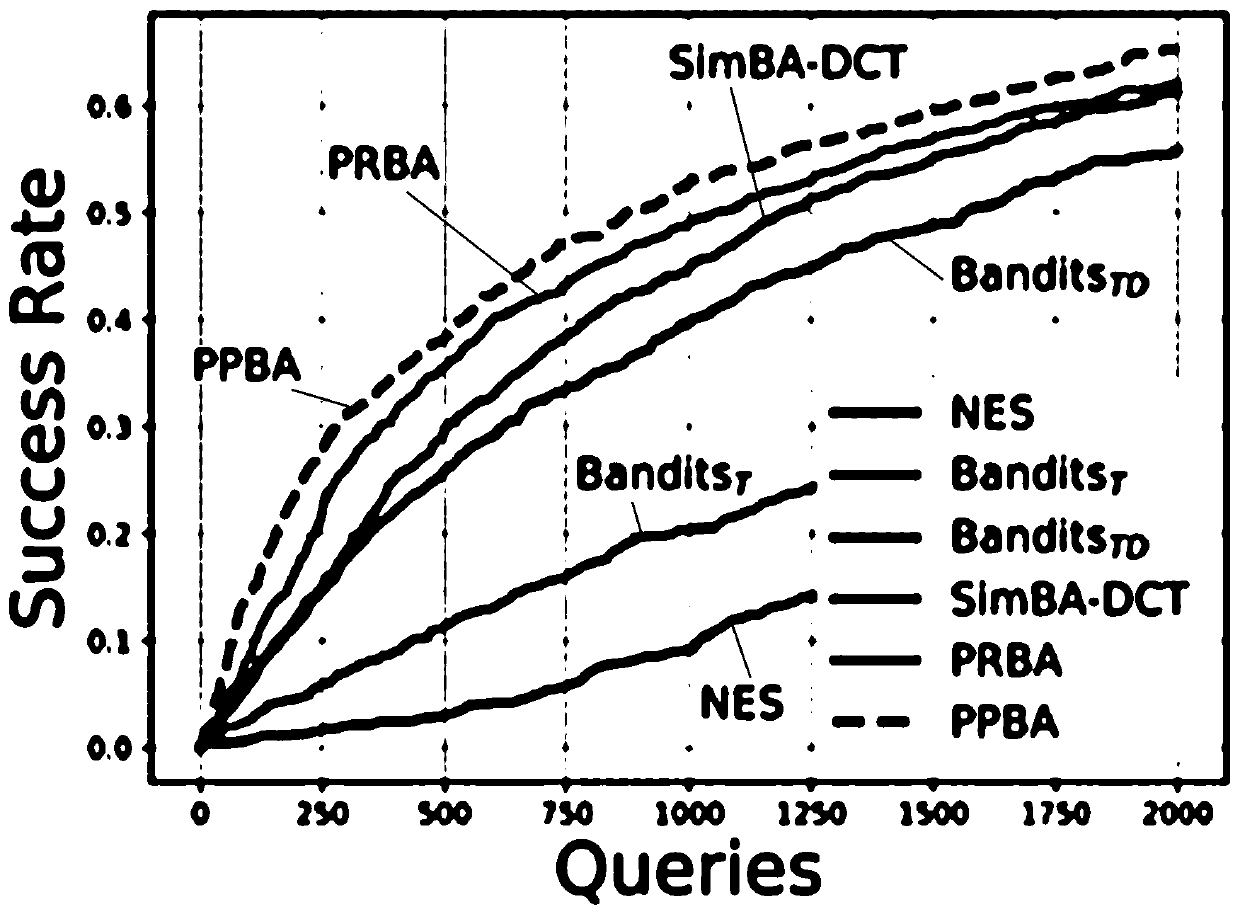
Black box depth model adversarial sample generation method
A deep model and adversarial sample technology, applied in neural learning methods, biological neural network models, character and pattern recognition, etc., can solve problems such as high overhead and achieve the effect of reducing the number of queries
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0048] In this embodiment, a black-box depth model adversarial sample generation method is as follows:
[0049] Step 1. Input the dimension d of the image x, set the number of frequencies m, the low frequency limit parameter r and the maximum number of queries max_iter;
[0050] Step 2. Construct a dimensionality reduction projection matrix W;
[0051] Step 2.1, initialize the dimensionality reduction projection matrix W with all zeros, and initialize the frequency j=0;
[0052] Step 2.2, if the frequency j is less than the number of frequencies m, from the matrix I r×d Randomly pick a base v from j , let W[j,:]=DCT(v j ), j=j+1;
[0053] Step 2.3, repeating step 2.2 until the frequency j is equal to the number of frequencies m; at this time, the dimensionality reduction projection matrix W is output;
[0054] Step 3, optimize the amplitude α;
[0055] Step 3.1, initializing the amplitude α=0, query times t=0;
[0056] Step 3.2. Randomly sample the vector Δα within a ce...
Embodiment 2
[0060] On the basis of the first embodiment, when optimizing the amplitude, the amplitude is constrained to a discrete three-valued space. In this embodiment, a black-box depth model adversarial sample generation method is as follows:
[0061] Step 1. Input the dimension d of the image x, set the number of frequencies m, the low frequency limit parameter r and the maximum number of queries max_iter;
[0062] Step 2. Construct a dimensionality reduction projection matrix W;
[0063] Step 2.1, initialize the dimensionality reduction projection matrix W with all zeros, and initialize the frequency j=0;
[0064] Step 2.2, if the frequency j is less than the number of frequencies m, from I r×d Randomly pick a base v from j , let W[j,:]=DCT(v j ), j=j+1;
[0065] Step 2.3, repeating step 2.2 until the frequency j is equal to the number of frequencies m; at this time, the dimensionality reduction projection matrix W is output;
[0066] Step 3, optimize the amplitude α;
[0067...
Embodiment 3
[0072] In this embodiment, on the basis of the first embodiment, when optimizing the amplitude, the amplitude is constrained to a discrete three-valued space, and a probability-driven optimal sampling method is adopted. A black-box depth model adversarial sample generation method in this embodiment is specifically as follows:
[0073] Step 1. Input the dimension d of the image x, set the number of frequencies m, the low frequency limit parameter r and the maximum number of queries max_iter;
[0074] Step 2. Construct a dimensionality reduction projection matrix W;
[0075] Step 2.1, initialize the dimensionality reduction projection matrix W with all zeros, and initialize the frequency j=0;
[0076] Step 2.2, if the frequency j is less than the number of frequencies m, from I r×d Randomly pick a base v from j , let W[j,:]=DCT(vj), j=j+1;
[0077] Step 2.3, repeating step 2.2 until the frequency j is equal to the number of frequencies m; at this time, the dimensionality red...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com