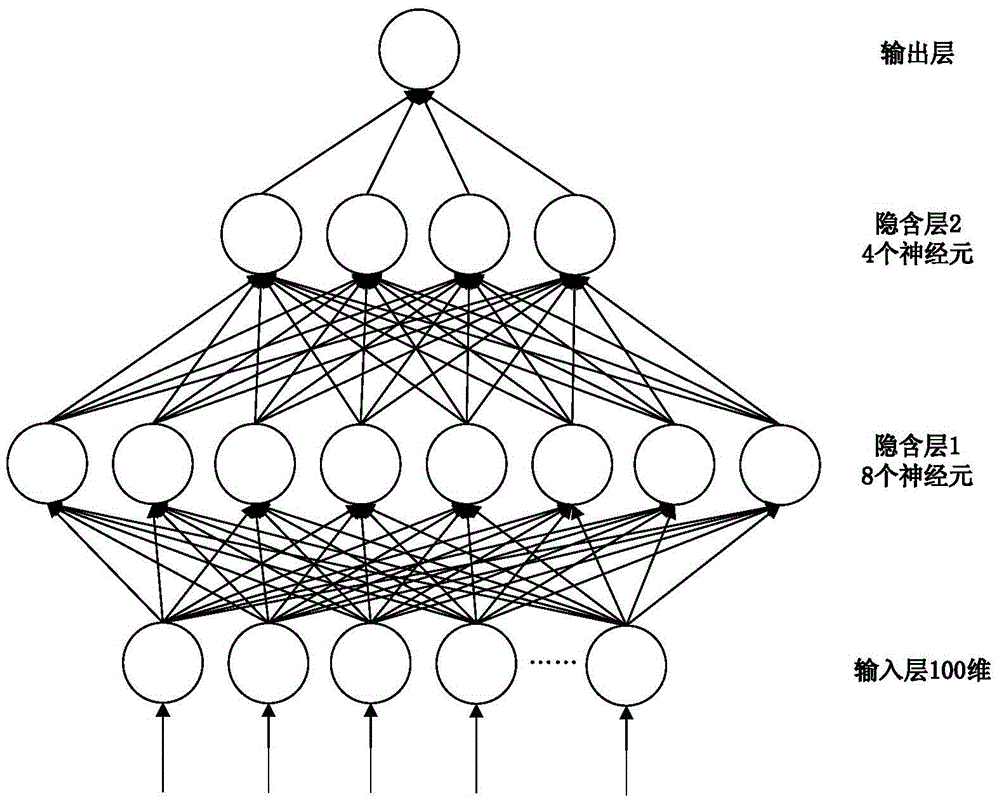
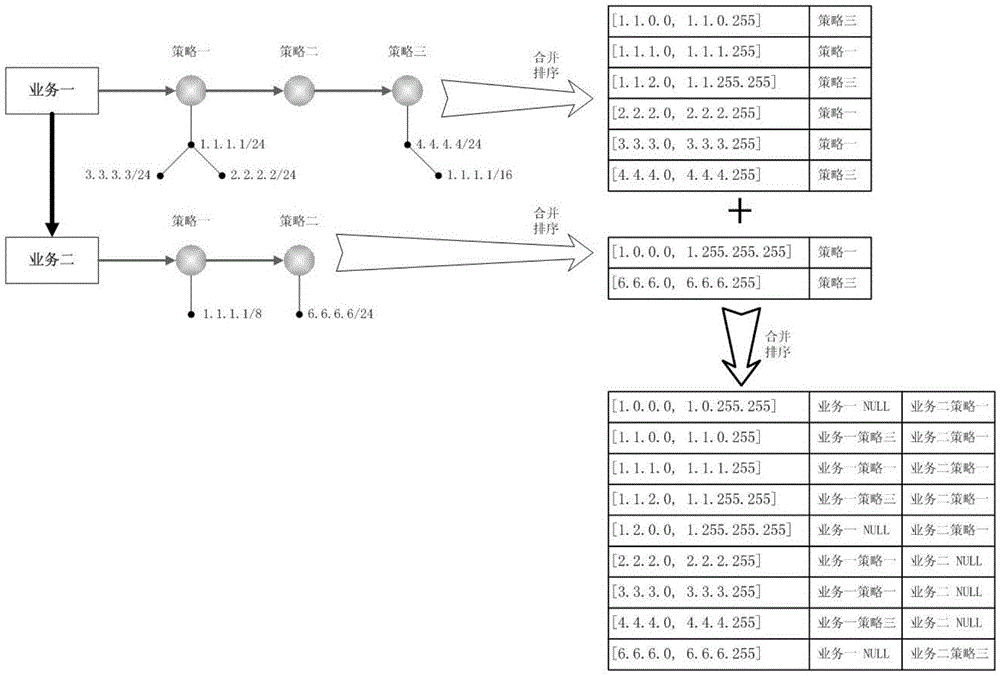
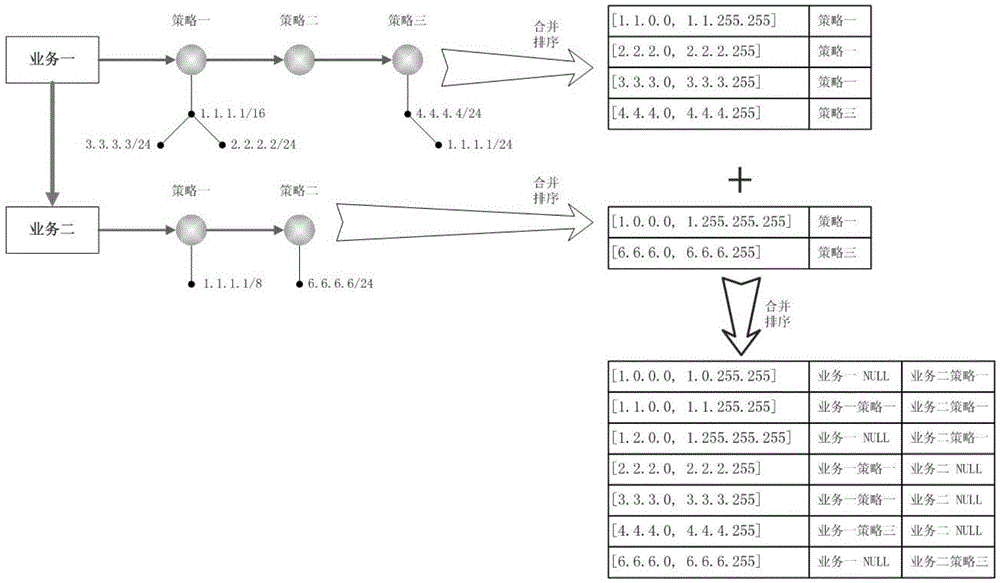
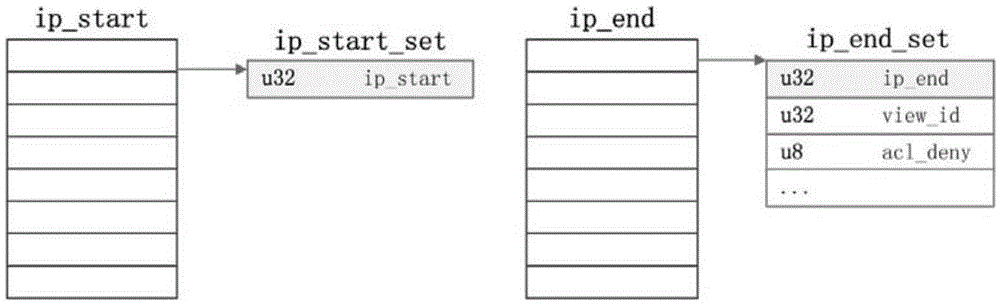
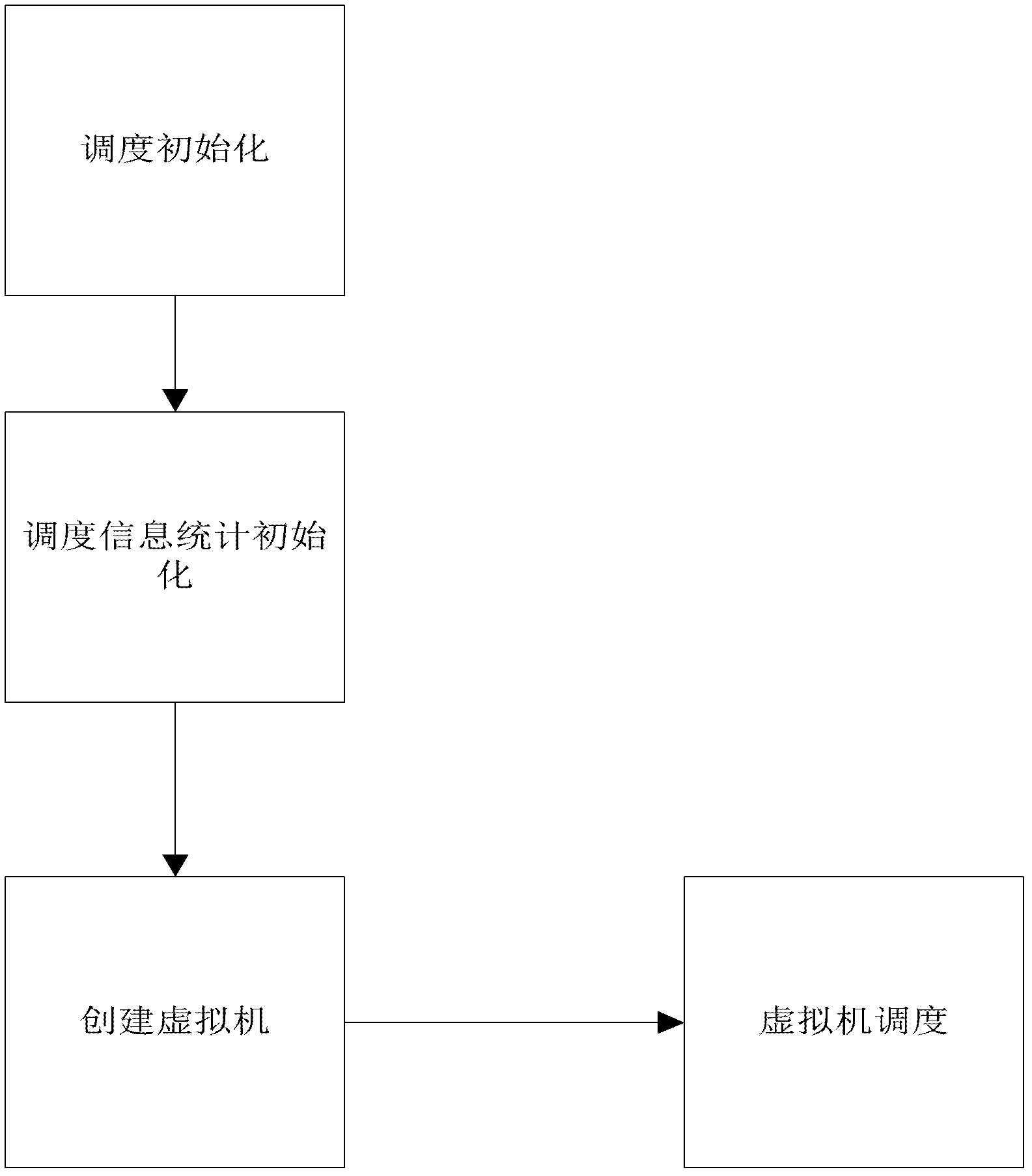Patents
Literature
112 results about "Red–black tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
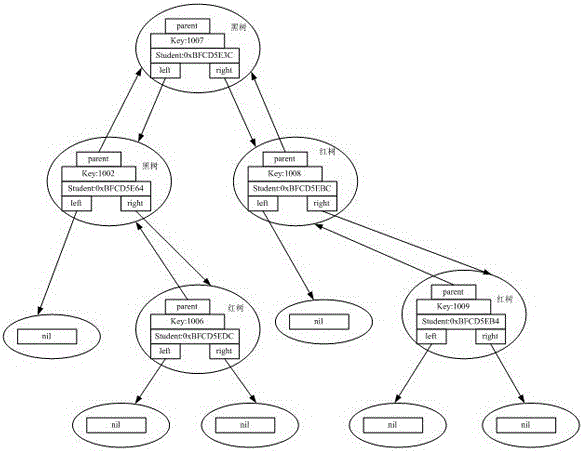
A red–black tree is a kind of self-balancing binary search tree in computer science. Each node of the binary tree has an extra bit, and that bit is often interpreted as the color (red or black) of the node. These color bits are used to ensure the tree remains approximately balanced during insertions and deletions.
Fine grit document and catalogs version management method based on snapshot
InactiveCN101162469AShort execution timeFlexible configuration version generation strategySpecial data processing applicationsGranularityUsability
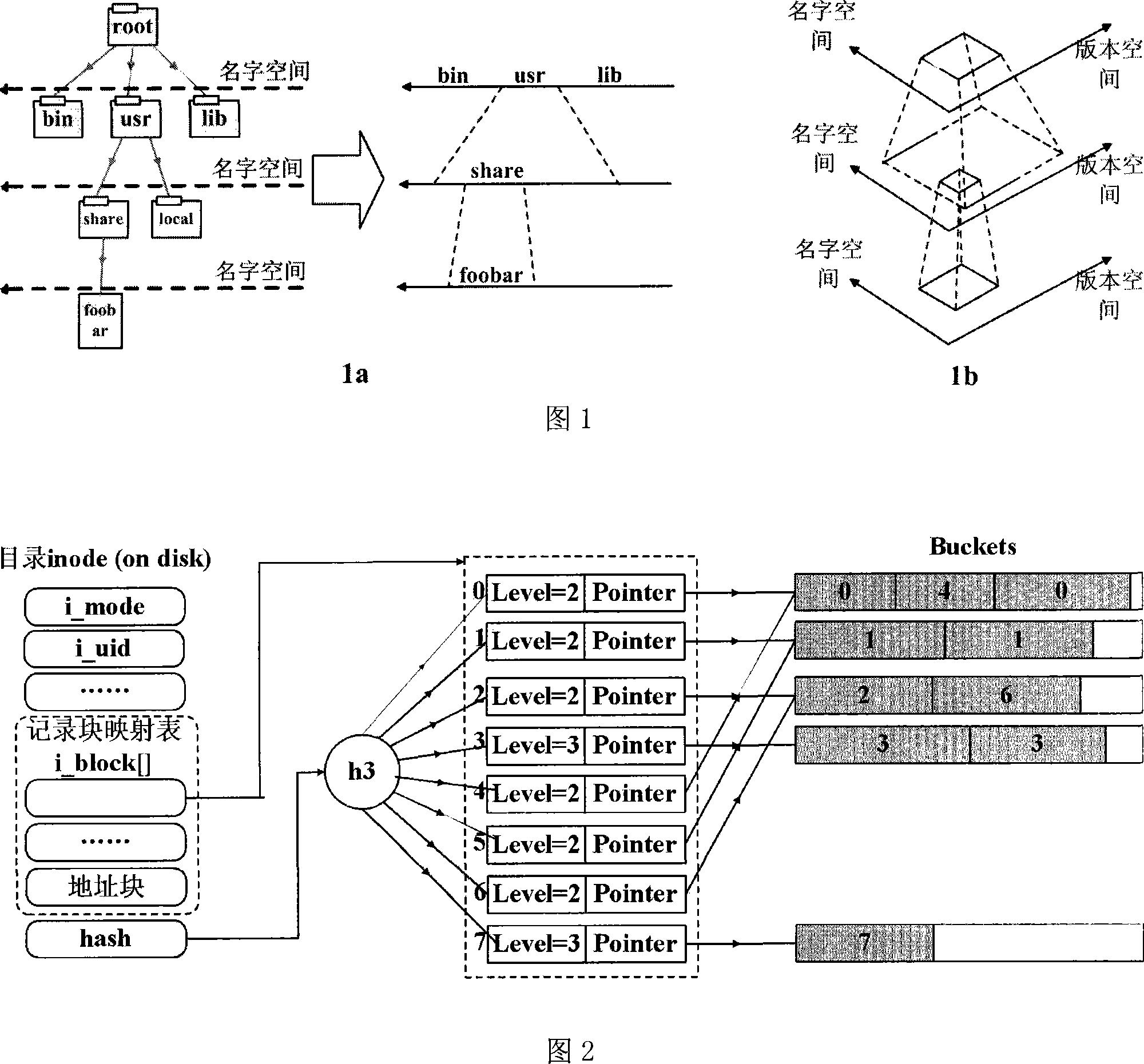
The present invention relates to a fine-granularity files and directory edition management method based on snapshots, belonging to the multi-version document system field. The present invention separates a name space consisting of files and dirnames in a whole file system from an edition space representing the generating periods of different editions, and adopts relatively independent strategies to execute management, forming a hierarchical two-dimensional structure, i.e. forming a hierarchical structure from a root directory to a file in the name space; in the edition space, the editions of files and directory are organized through an index structure chronologically, forming a hierarchical structure in the edition space. The retrieval of the name space adopts an index strategy based on dynamic hash. The retrieval of the edition space adopts an index strategy based on a red-black tree. The directory edition and file edition respectively adopt a red-black tree structure variant aiming at the respective characteristics. The present invention can greatly improve the usability and the performance of the system, and controls the amount of consumption of time and space resulting from the maintenance of historical editions in an acceptable scope.
Owner:TSINGHUA UNIV
Multi-level cache architecture and cache management method for peer-to-peer name resolution protocol
InactiveUS6912622B2Efficient solutionLess resourcesMemory adressing/allocation/relocationMultiple digital computer combinationsGranularityParallel computing
A peer-to-peer cache architecture stores peer address certificates in different cache segments according to the number of IDs being stored and their relative distance in the peer name space. The cache instantiates regions of decreased range and increased granularity as additional information from close peers is learned. In a large peer cloud where the number of instantiated IDs is not known, each succeeding cache region covers one tenth of the preceding cache region. For peers with multiple IDs registered locally, the segmented cache of the present invention combines overlapping segments of the same granularity to eliminate the duplication of information that would otherwise occur. A cache tree, an instantiated segment tree, and an uninstantiated segment tree are arranged in red-black trees to simplify the search and proper placement and instantiation of information.
Owner:MICROSOFT TECH LICENSING LLC
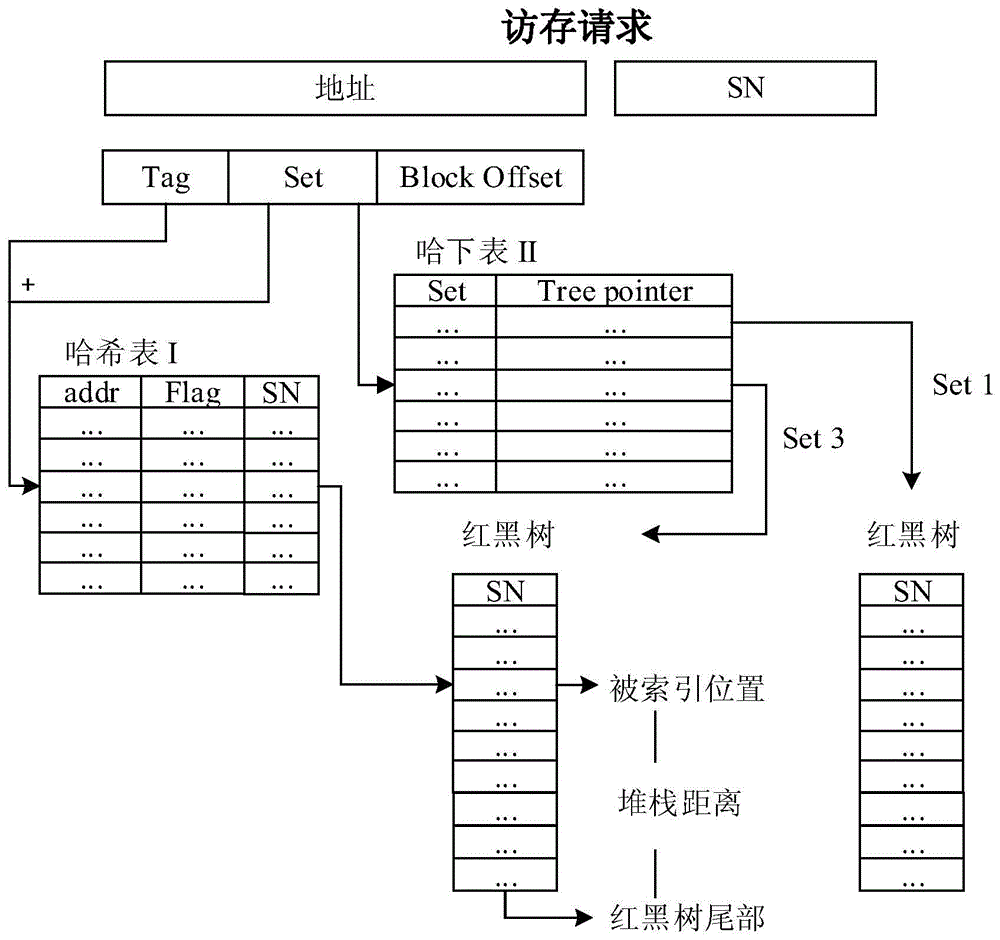
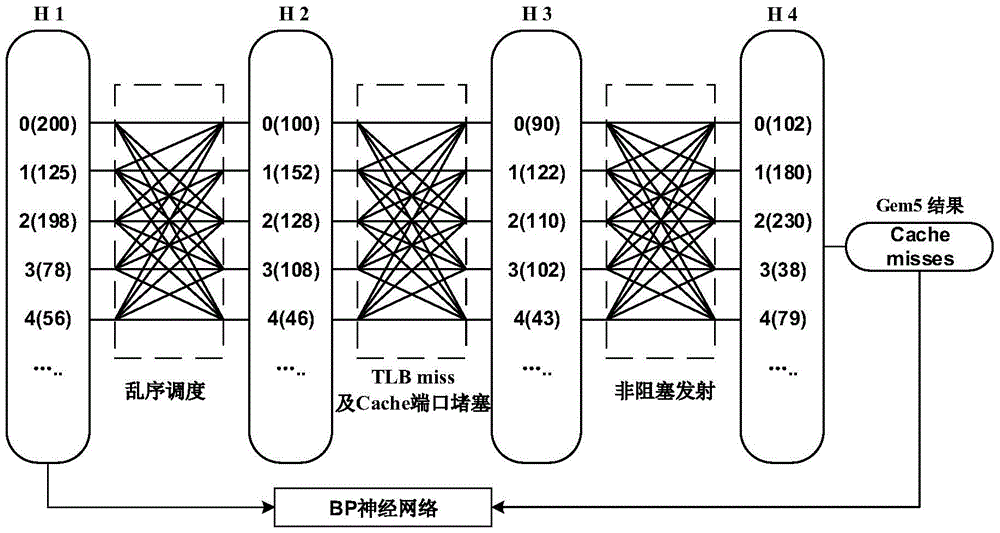
Artificial neural network-based out-of-order processor Cache memory access performance evaluation method
ActiveCN105653790AAccurately capture the full simulation processHigh speedNeural learning methodsSpecial data processing applicationsNerve networkStack distance
The invention discloses an artificial neural network-based out-of-order processor Cache memory access performance evaluation method, and aims at solving the problem that the memory access instructions are executed out of order so that the stacking distance distribution extracted by utilizing a binary execution tool during the prediction of LRU-Cache memory access behaviors is low in precision. The method comprises the following steps: combining a read-black tree and a hash table; designing a Cache group association architecture-based stacking distance extraction algorithm; respectively calculating a memory access sequence and the stacking distance distribution executed out of order; fitting the stacking distance distribution executed according to the memory access sequence and a memory access missing number by utilizing a BP neural network; and importing the stacking distance distributed extracted on the basis of the binary execution tool into the trained neural network so as to predict the Cache memory access behaviors with high precision. According to the method disclosed in the invention, the artificial neural network is adopted, so that the problem that the stacking distance distribution extracted by utilizing the binary execution tool during the prediction of the Cache memory access behaviors is low in precision is effectively solved.
Owner:RES INST OF SOUTHEAST UNIV IN SUZHOU
IP address list storage and query method applied to DNS query
ActiveCN105635343AReduce the number of queriesReduced impact on query timeTransmissionArray data structureIp address
The invention relates to an IP address list storage and query method applied to DNS query. The method comprises the following steps: firstly carrying out deduplication processing on the IP address list of each strategy, and storing by using modes of a red black tree, an array, a linked list and the like; and then combining the IP address lists of different strategies of each service to construct an IP address list+strategy form and storing, following an IP longest matching principle or a priority principle in the combination process; and continuously combining the IP address list+strategy storage structures of different services to construct and store an IP address list+service+strategy form; sorting the IP address list+service+strategy storage structures according to IP address list initial address sizes; and performing the DNS query by using dichotomy and the like query method while in query. Through the adoption of the method provided by the invention, the existing IP storage structure is improved, the operation is simple, the query time can be reduced, and the query efficiency is improved.
Owner:CHINA INTERNET NETWORK INFORMATION CENTER
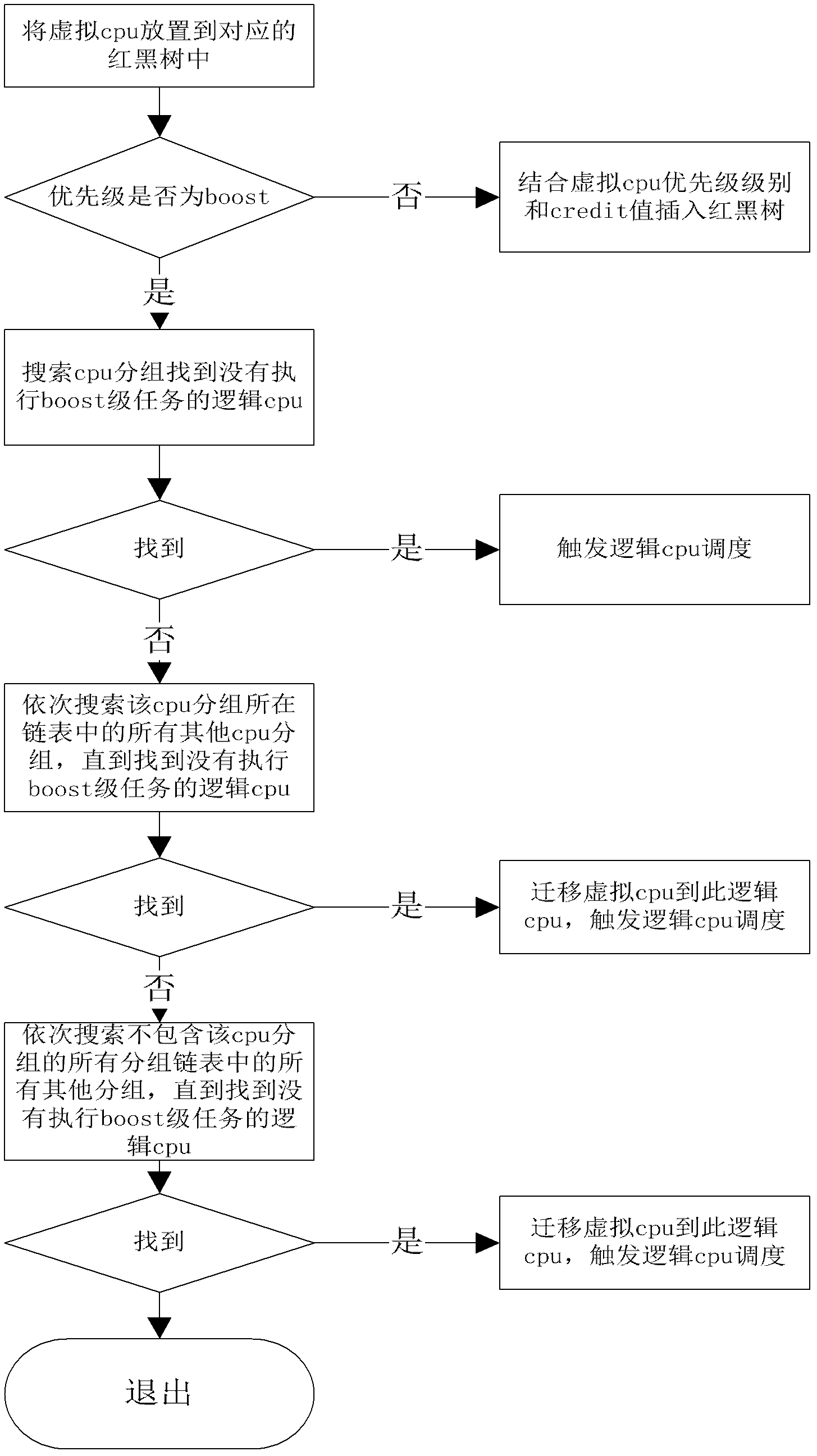
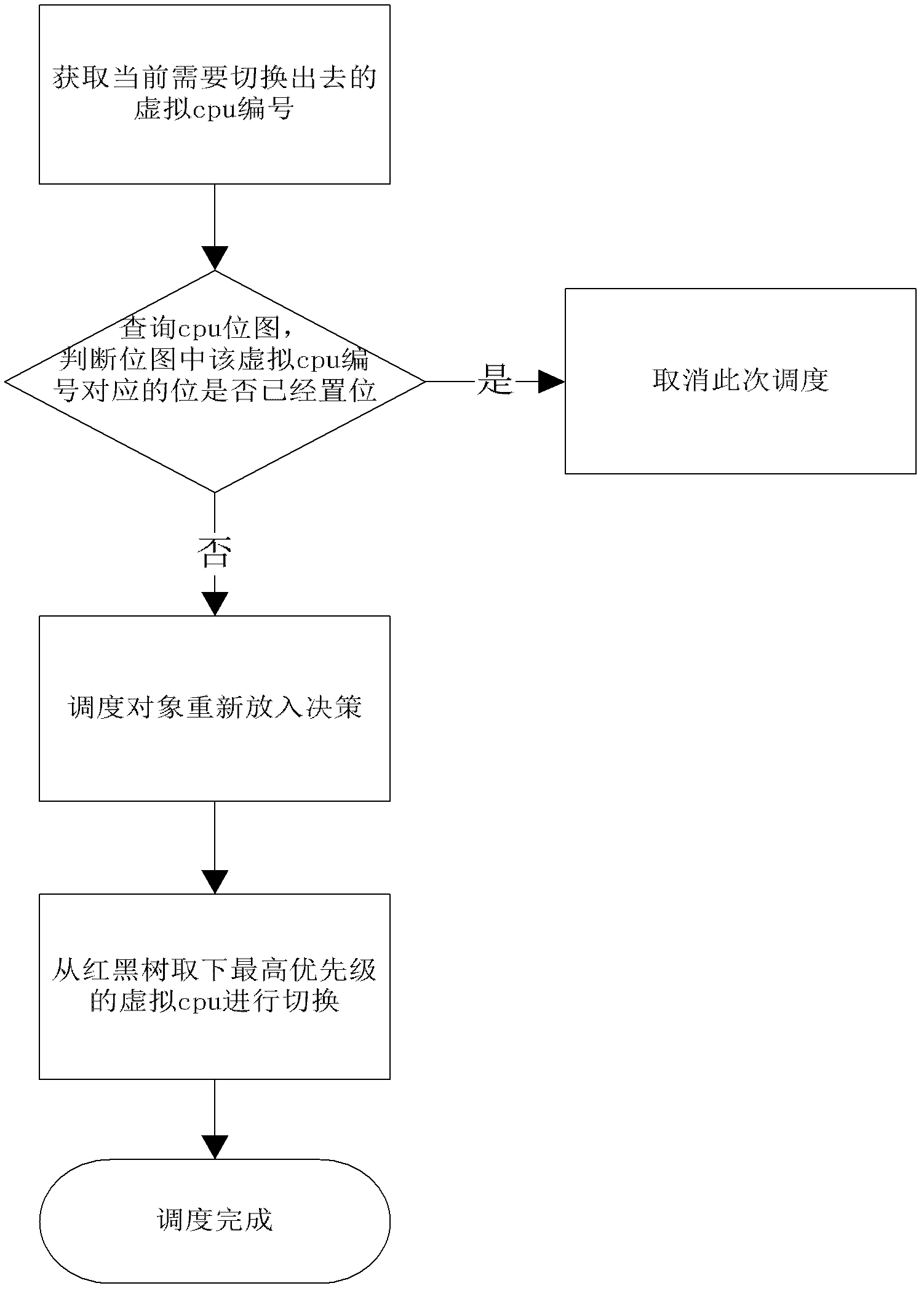
Xen virtual machine scheduling control method in multi-core environment
ActiveCN102253857AFast executionImprove performanceResource allocationSoftware simulation/interpretation/emulationMulticore architectureRed–black tree
The invention provides an Xen virtual machine scheduling control method in multi-core environment. The method comprises the following steps: (I) carrying out scheduling initialization; (II) carrying out initialization of scheduling information statistics, namely monitoring the virtual CPU (central processing unit) in a management domain 0, and sending the monitoring result to a VMM (virtual machine monitor) in real time; (III) creating a virtual machine, allocating the virtual CPU, storing the virtual CPU to a red black tree of a corresponding CPU group according to the priority level and a credit value, and starting all timers set in the initialization stage; and (IV) scheduling the virtual machine. According to the invention, the time slice executed by a logic CPU in the group can be dynamically adjusted, the time consumed by the scheduling method in the execution process is effectively reduced, relatively short response time for the IO (input / output) task is realized, and the method adapts to any type with relatively high requirement on time.
Owner:HUAZHONG UNIV OF SCI & TECH
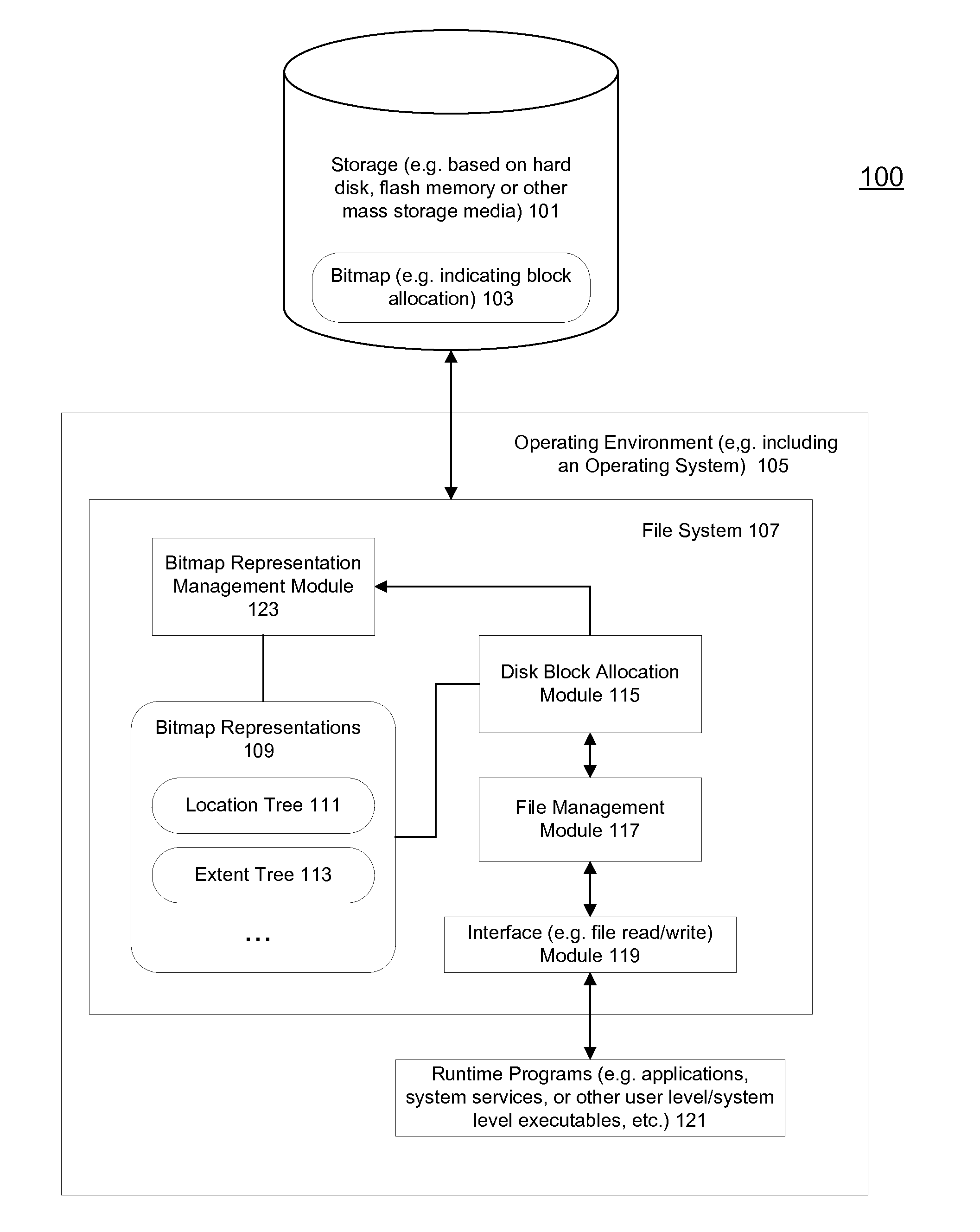
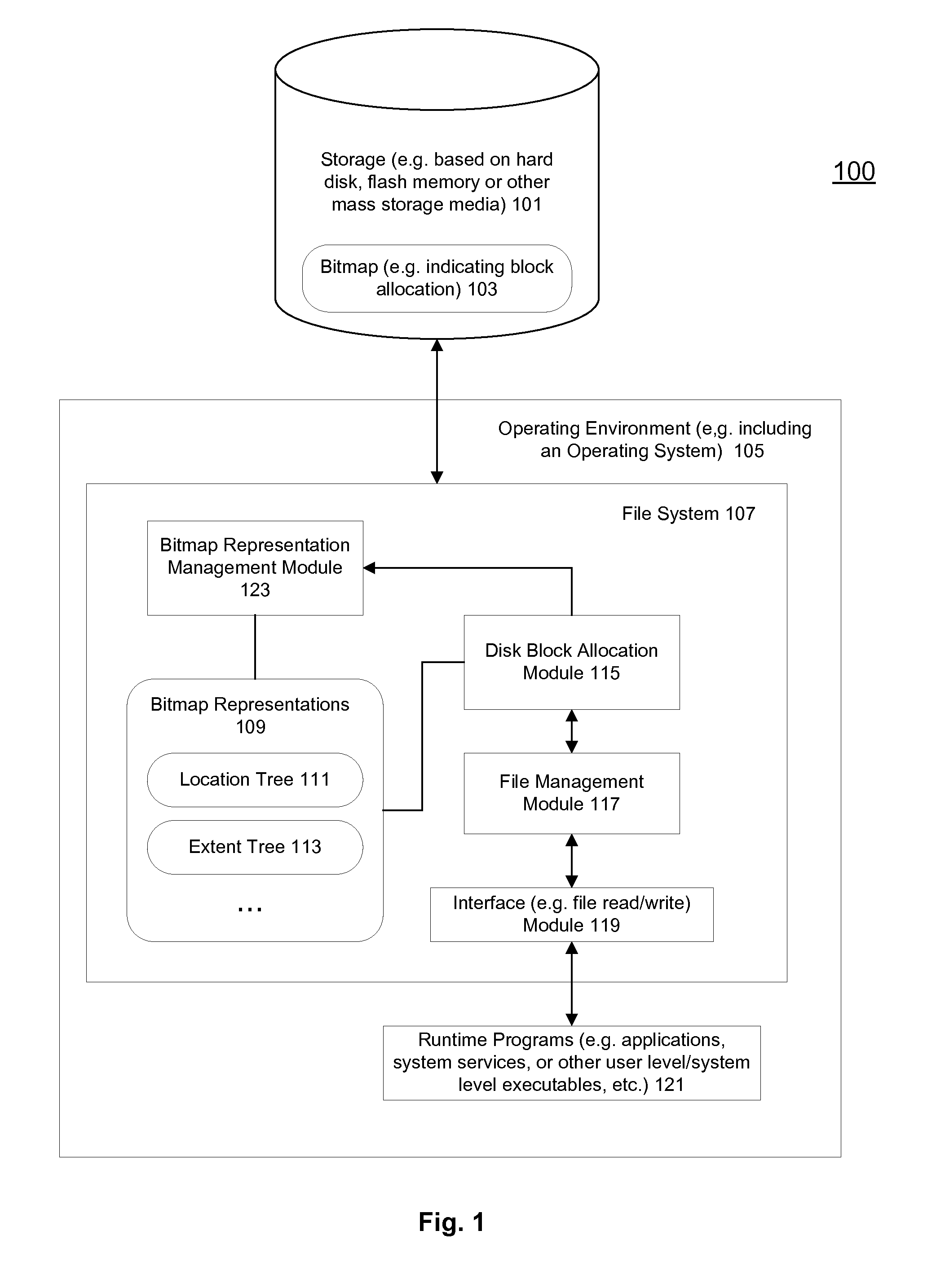
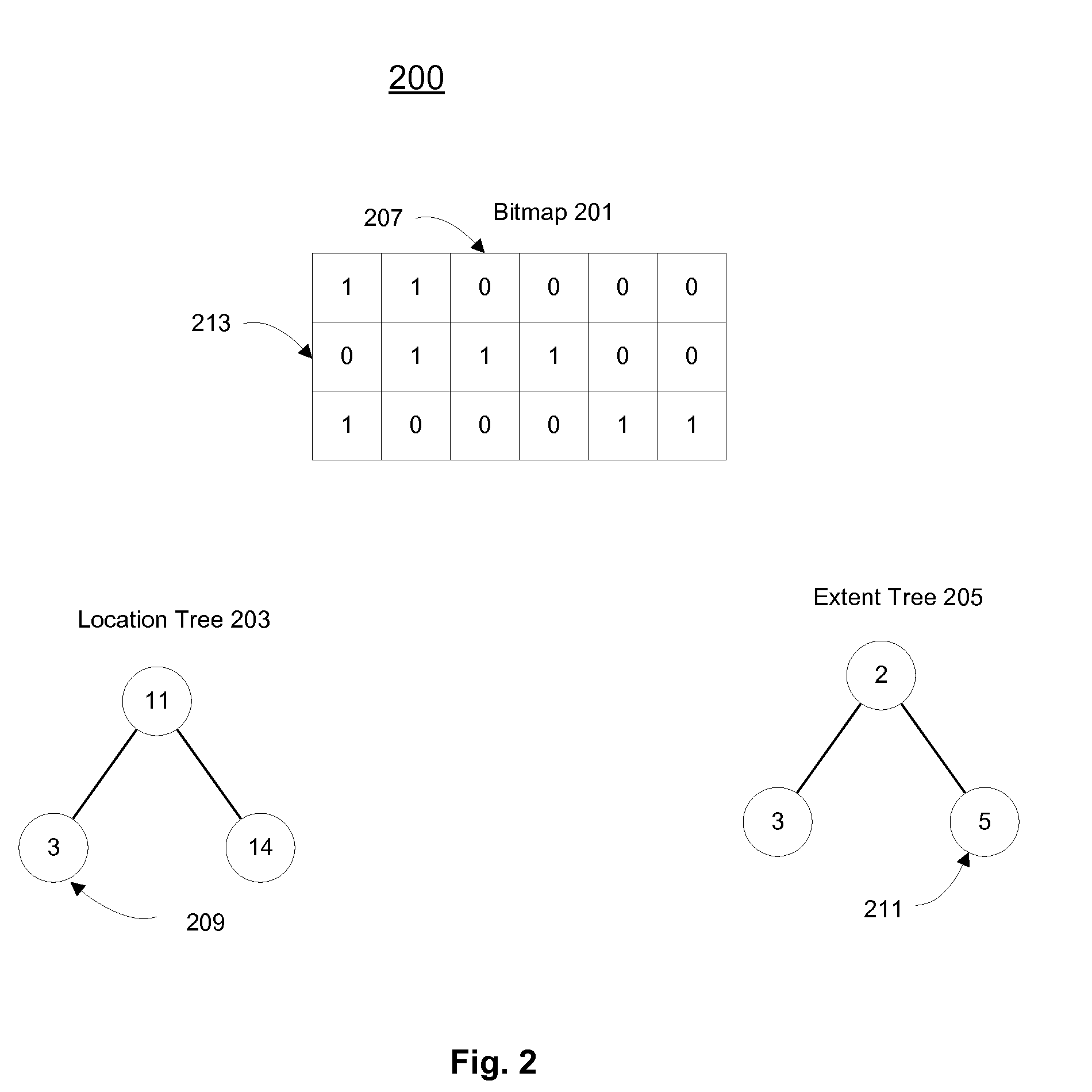
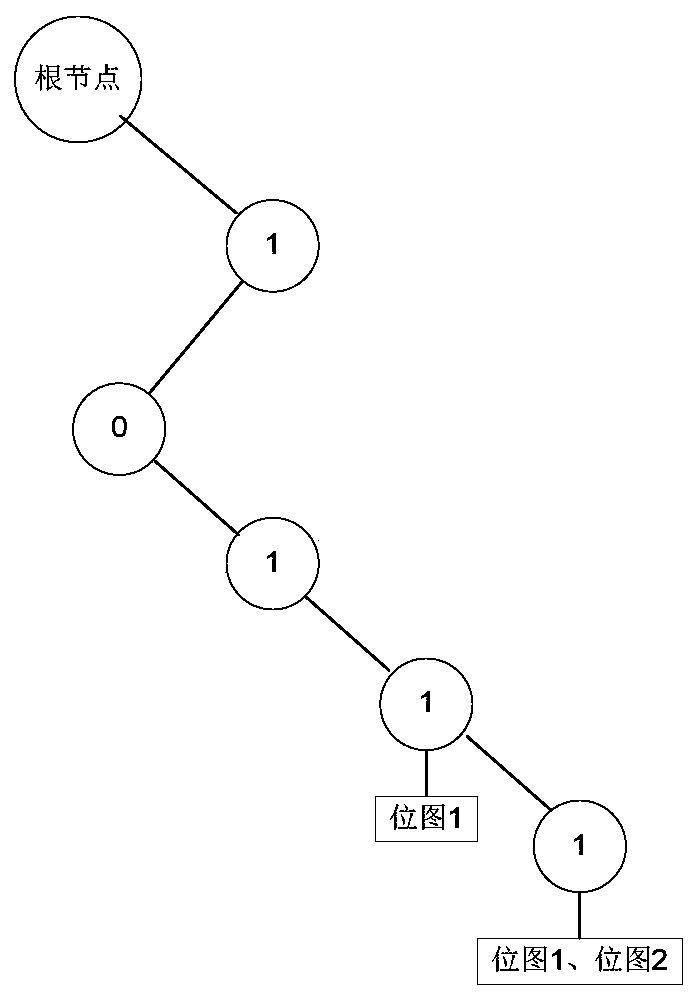
Methods and apparatuses to allocate file storage via tree representations of a bitmap
ActiveUS20110153976A1Digital data processing detailsMemory adressing/allocation/relocationBlock matchRed–black tree
Methods and apparatuses that search tree representations of a bitmap for available blocks to allocate in storage devices are described. An allocation request for a file may be received to initiate the search. In one embodiment, the bitmap may include an array of bits corresponding to blocks in the storage devices. Each bit may indicate whether one of the blocks is available. The tree representations may include at least one red-black tree having nodes corresponding to one or more consecutive bits in the bitmap indicating an extent of available blocks. One of the tree representations may be selected according to a file associated with an allocation request to identify an extent of available block matching the allocation request. The tree representations may be synchronized as the bitmap is updated with changes of block allocations in the storage devices.
Owner:APPLE INC
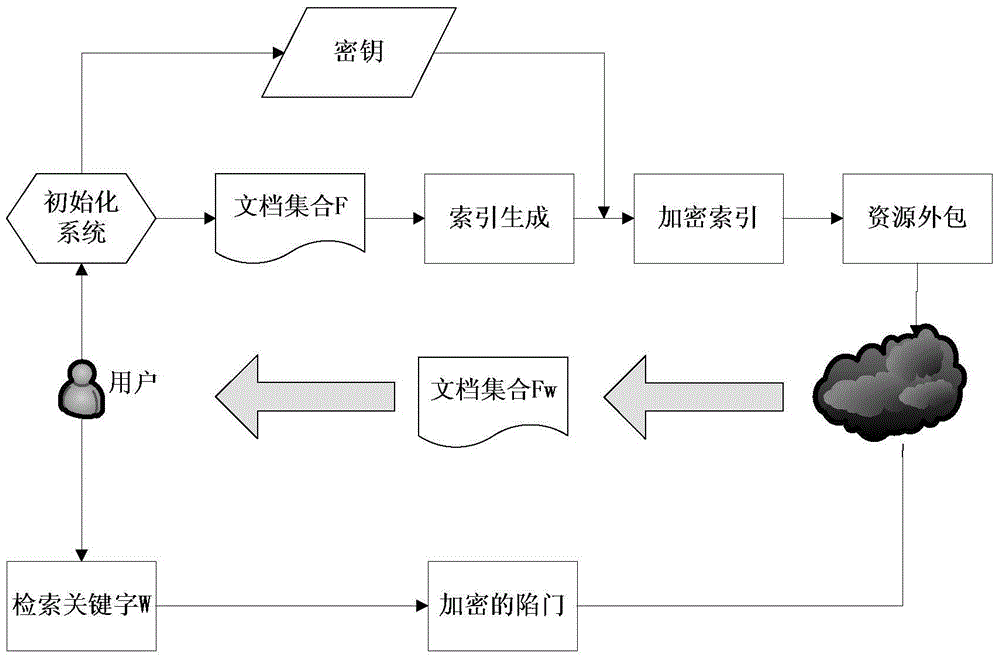
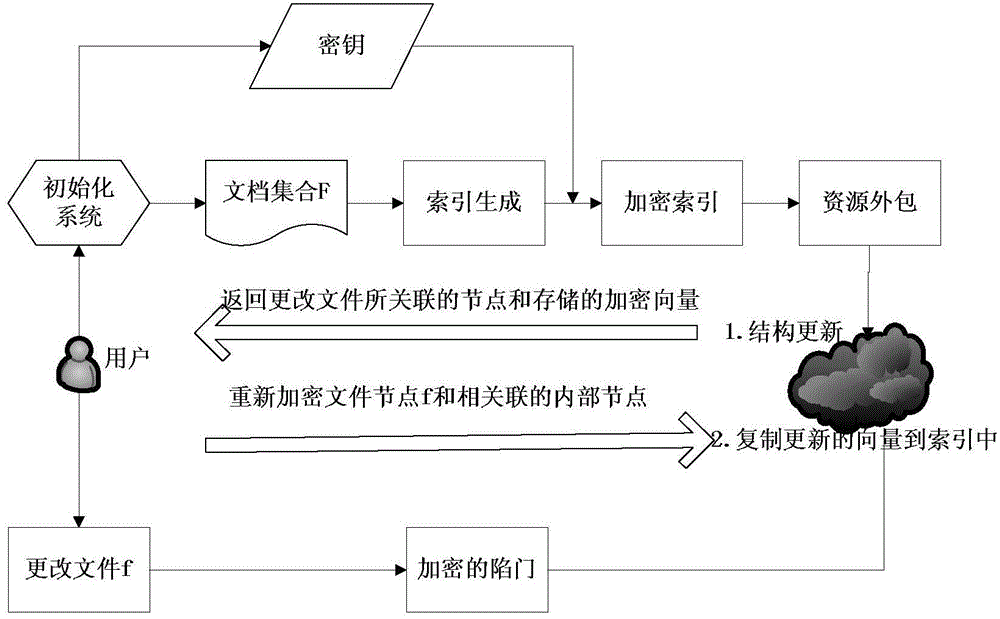
Search encryption method supporting dynamic updating and multi-keyword safe ranking
ActiveCN104615692ATroubleshoot dynamic update issuesStructural updateFile access structuresSpecial data processing applicationsRankingClient-side
The invention discloses a search encryption method supporting dynamic updating and multi-keyword searching and achieving safe ranking. According to the search encryption method, a red-black tree serves as an index structure, an unencrypted index is generated for a file set, file vectors are stored in leaf nodes, and a union result of child nodes is stored in an internal node. Vectors of all the nodes in the tree are encrypted through an asymmetrical scalar product. During keyword searching, a client side generates a trap door matched with the child nodes of the red-black tree. Calculation is conducted according to the word frequency stored by the leaf nodes, and a top-k file can be returned during searching. When a file is added or canceled, the client side sends a file name and operation, a server returns relevant nodes, and structure updating is achieved in the server. The client side conducts data decrypting and updating and sends decrypted and updated date to the server. Partial updating of the index is achieved through the server. By means of the search encryption method, the dynamic updating purpose of cloud storage data can be achieved, and the user experience can be improved through multi-keyword searching and safe ranking.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
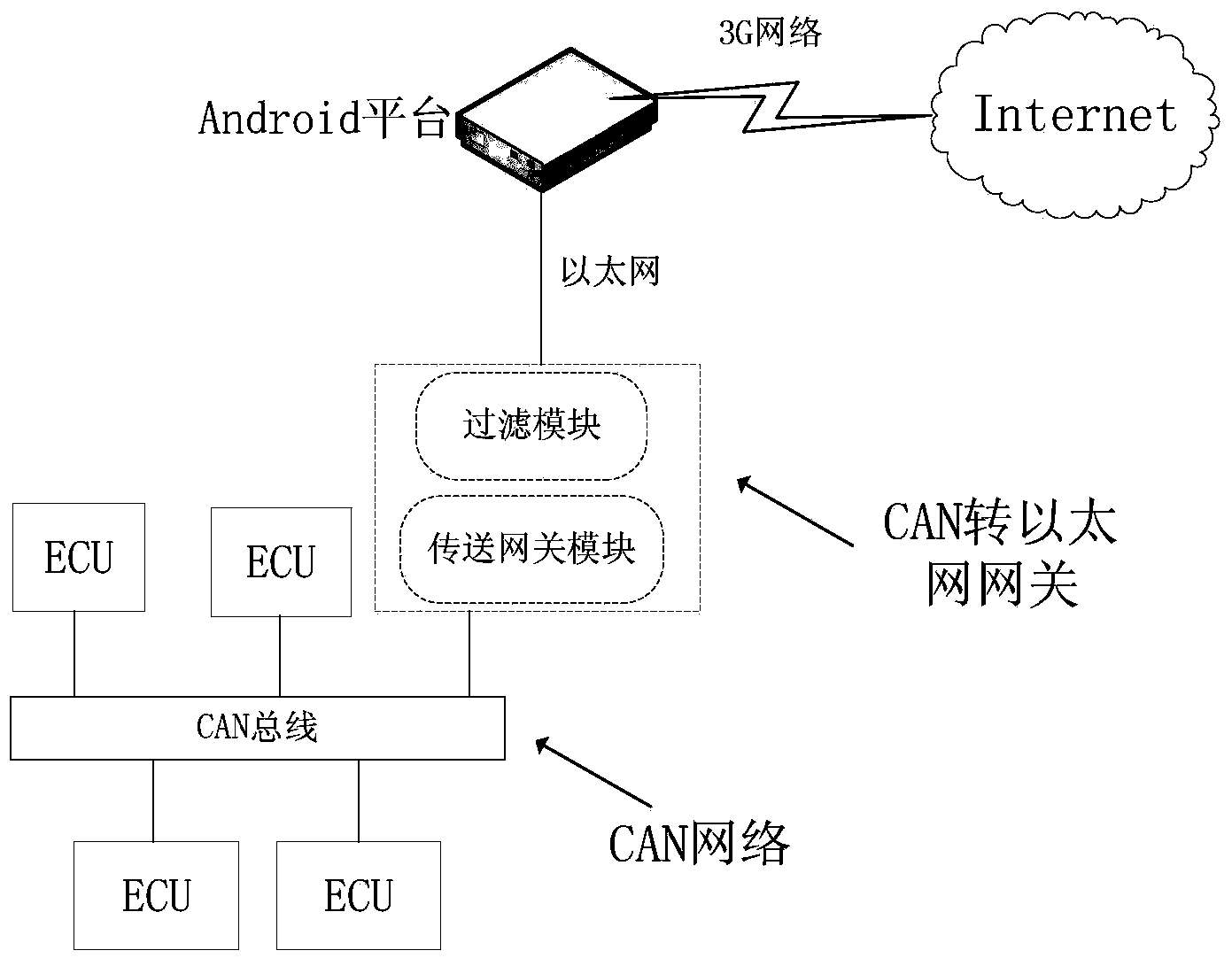
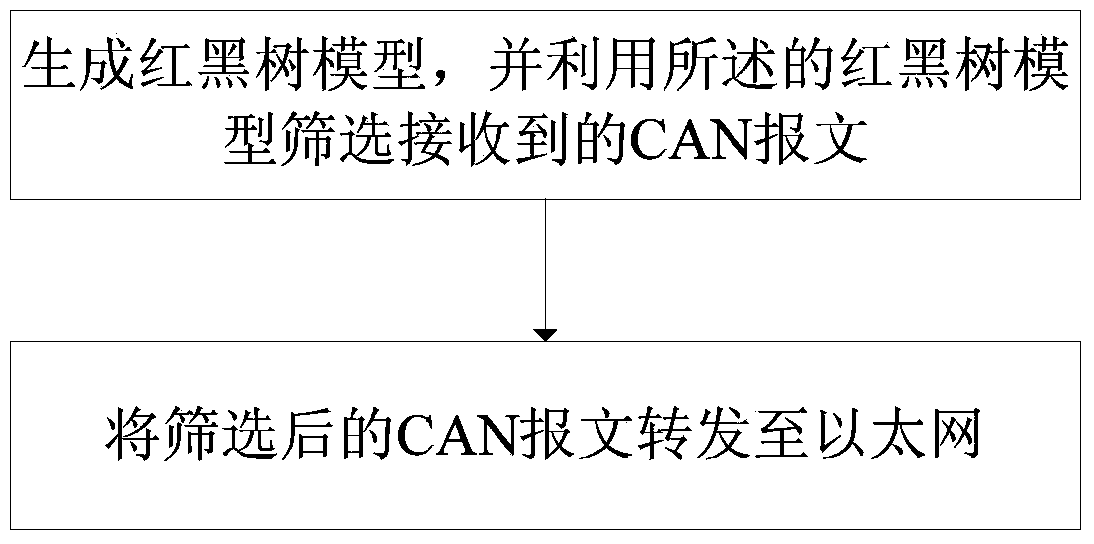
CAN (Controller Area Network) to Ethernet gateway with filtering function and data transmission method based on gateway
ActiveCN103812765AIncrease forwarding rateReduce consumptionNetwork connectionsTraffic capacitySearch data structure
The invention discloses a CAN (Controller Area Network) to Ethernet gateway with a filtering function and a data transmission method based on the gateway. The CAN to Ethernet gateway with the filtering function comprises a filtering module for generating a red-black tree model according to the configuration of a host, and screening received CAN messages by using a red-black tree, and a transmission gateway module for forwarding the screened CAN messages to the Ethernet. The gateway is provided with the filtering module, the filtering module is used for screening the received CAN messages, and the transmission gateway module is used for only forwarding the screened CAN messages, thereby lowering the flow consumption. Moreover, by organizing a searched data structure through the red-black tree model, a judgment on whether received CAN messages have matched configuration or not can be made rapidly by searching the red-black tree to finish screening.
Owner:ZHEJIANG UNIV
Memory algorithm facing real-time system
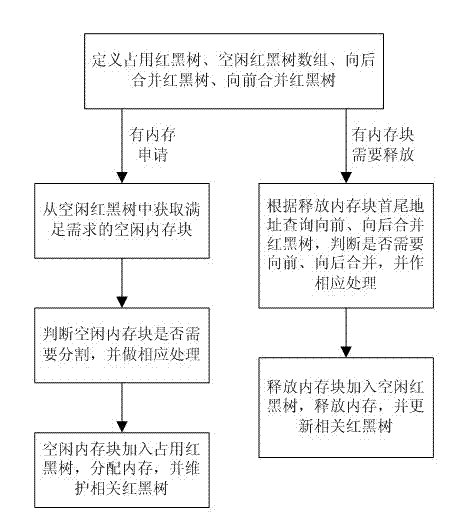
InactiveCN102880555ATime and Efficiency ImprovementsImprove recovery rateMemory adressing/allocation/relocationArray data structureParallel computing
The invention relates to a memory algorithm facing a real-time system. A red-black tree data structure is adopted for quickly looking up a required memory block. An algorithm is used for defining an occupied red-black tree, an idle red-black tree array, a backward integration red-black tree and a forward integration red-black tree; when a memory application is in the presence, an idle memory block which meets the requirement is obtained from the idle red-black tree; whether the idle memory block needs to be cut is judged; corresponding processing is carried out; then, the idle memory block is added into the occupied red-black tree; the memory is distributed, and a relevant red-black tree is maintained; when the memory block needs to be released, the forward integration red-black tree and the backward integration red-black tree are inquired according to the head-tail address of a release memory block so as to judge whether backward integration and forward integration are required; the corresponding processing is carried out; then, the release memory block is added into the idle red-black tree; the memory is resealed; and the relevant red-black tree is updated. The algorithm is favorable for improving the memory distribution time efficiency.
Owner:FUZHOU UNIV
System and method for implementing dynamic set operations on data stored in a sorted array
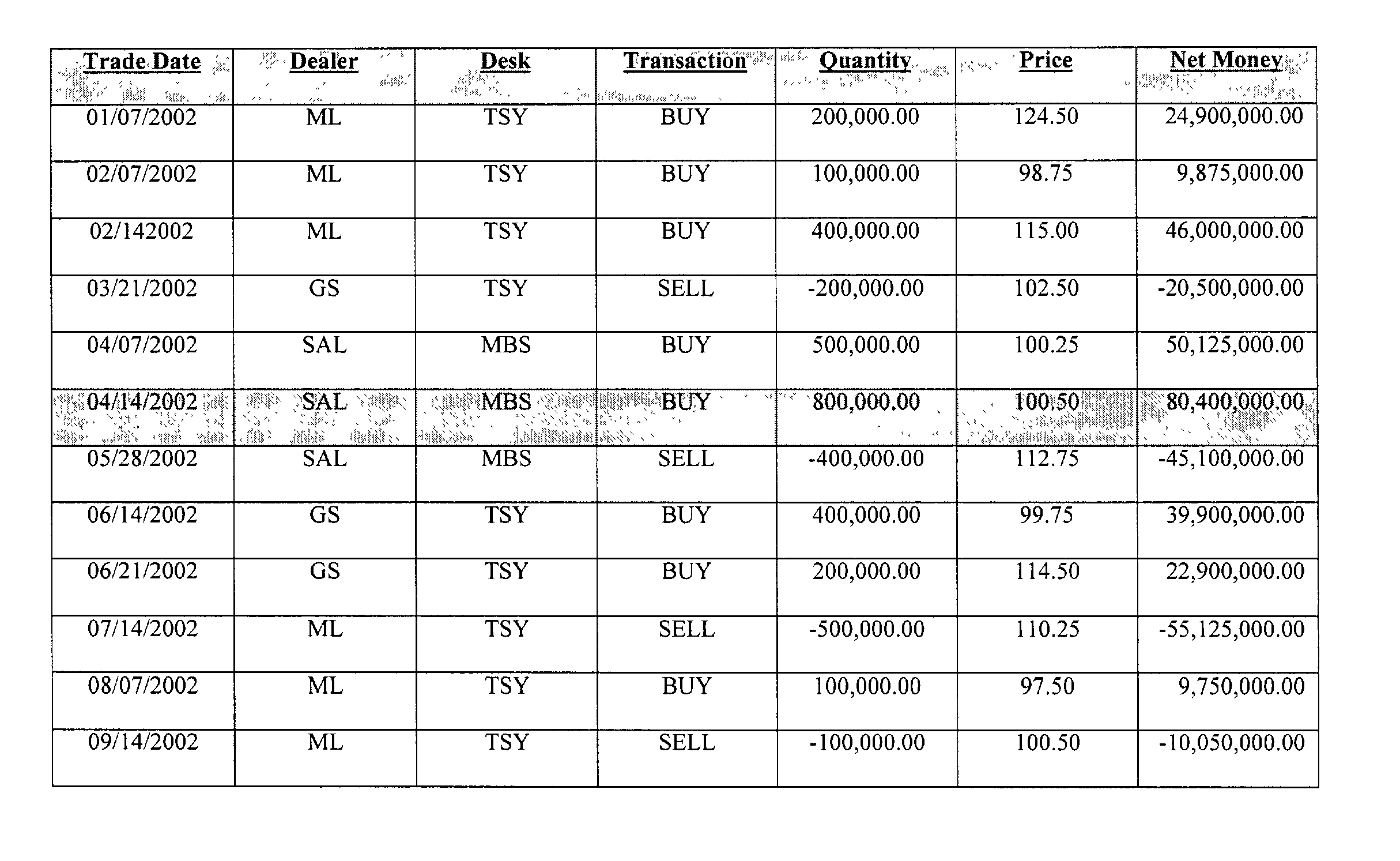
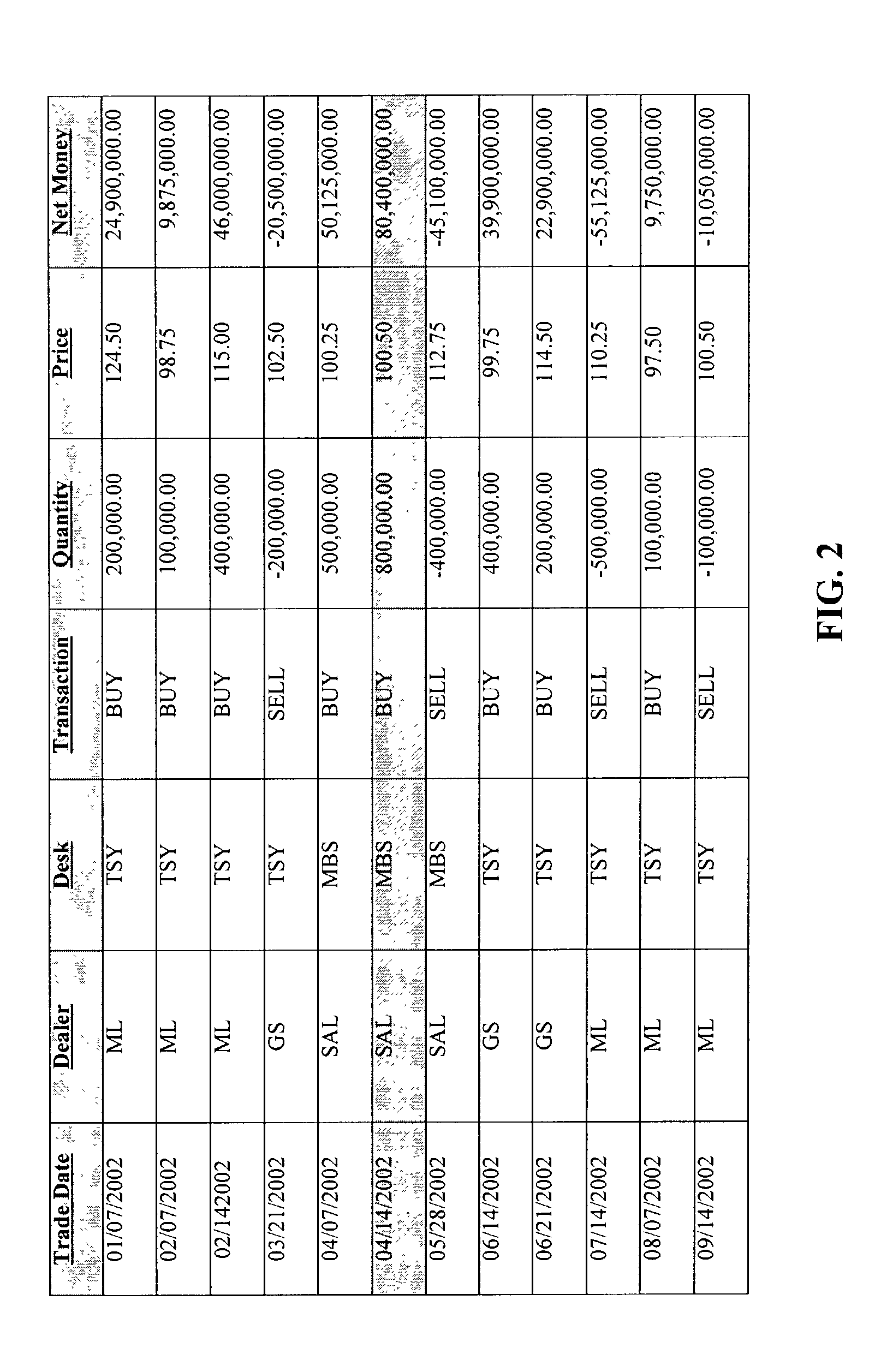
A system and method are disclosed for implementing dynamic set operations on data stored in a sorted array using a hybrid red-black binary search tree as a data structure. More particularly, the subject invention facilitates the implementation of a binary search to access data items stored in a sorted array by position, rather than by key value, as in conventional red-black trees. This is accomplished by generating a balanced red-black binary search tree for a sorted array of data items wherein the information stored at each node of the tree includes: a key value; a color; a left pointer to indicate the presence of a child to the left of the node; a right pointer to indicate the presence of a child to the right of the node; a count of descendents along a branch to the left of the node; and a count of descendants along a branch to the right of the node.
Owner:BLACKROCK FINANCIAL MANAGEMENT
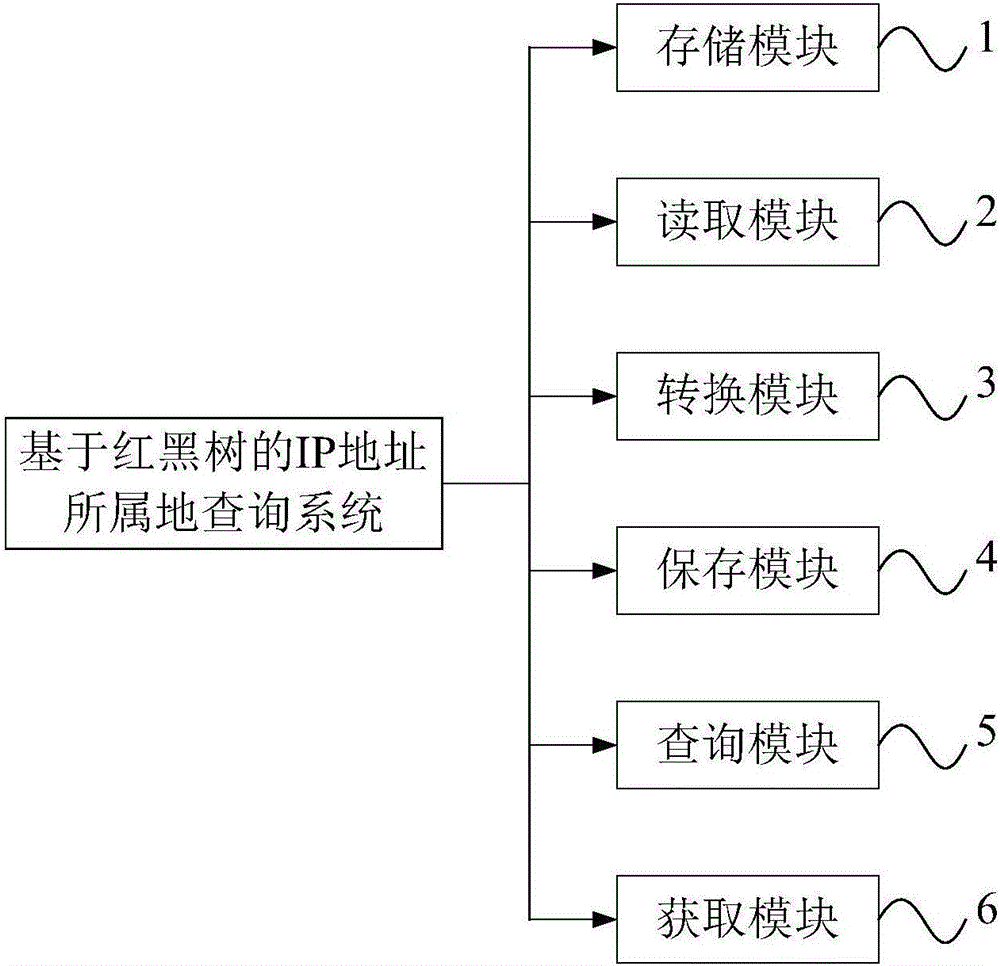
IP address subordinated region inquiring method and system based on red-black tree
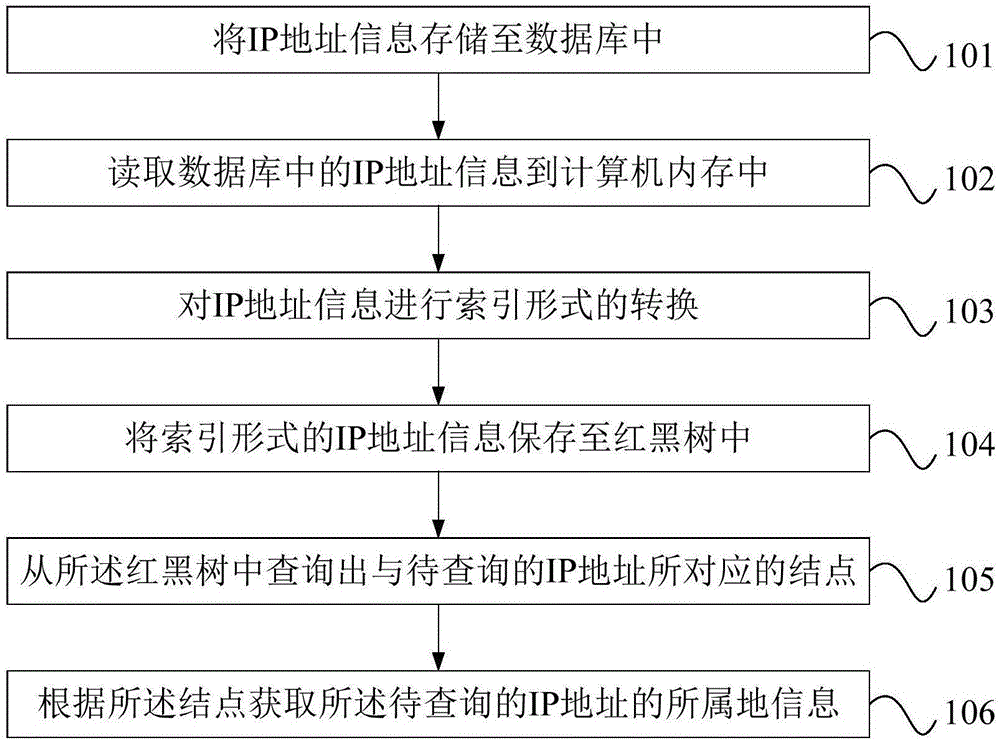
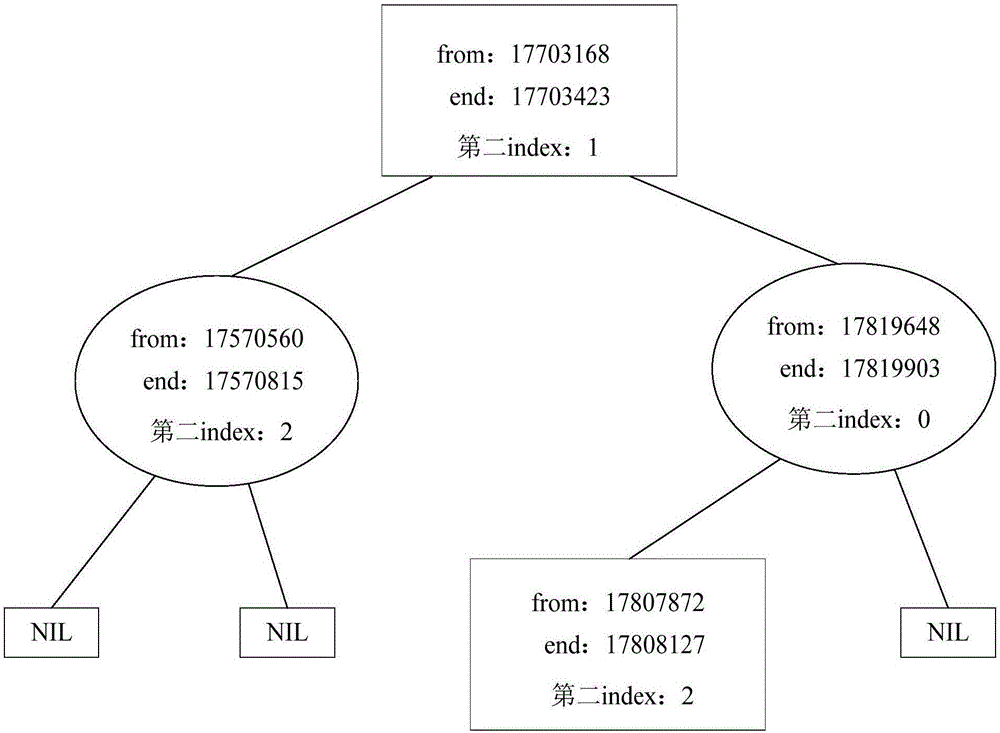
ActiveCN106777163AScalable and strongImprove scalabilitySpecial data processing applicationsIp addressRelational database
The invention discloses an IP address subordinated region inquiring method and system based on a red-black tree. The IP address subordinated region inquiring method based on the red-black tree comprises the following steps: S1, storing IP address information in a database; S2, reading the IP address information in the database to a computer memory; S3, executing the index mode conversion to the IP address information; S4, storing the IP address information of the index mode in the red-black tree; S5, inquiring a node corresponding to the IP address to be inquired from the red-black tree; and S6, according to the node, obtaining the subordinated region information of the IP address to be inquired. The method is based on the computer memory, the red-black algorithm and the relational database, and has the good extensible, real-time and high concurrent performances.
Owner:CTRIP TRAVEL NETWORK TECH SHANGHAI0
IP address matching method and device
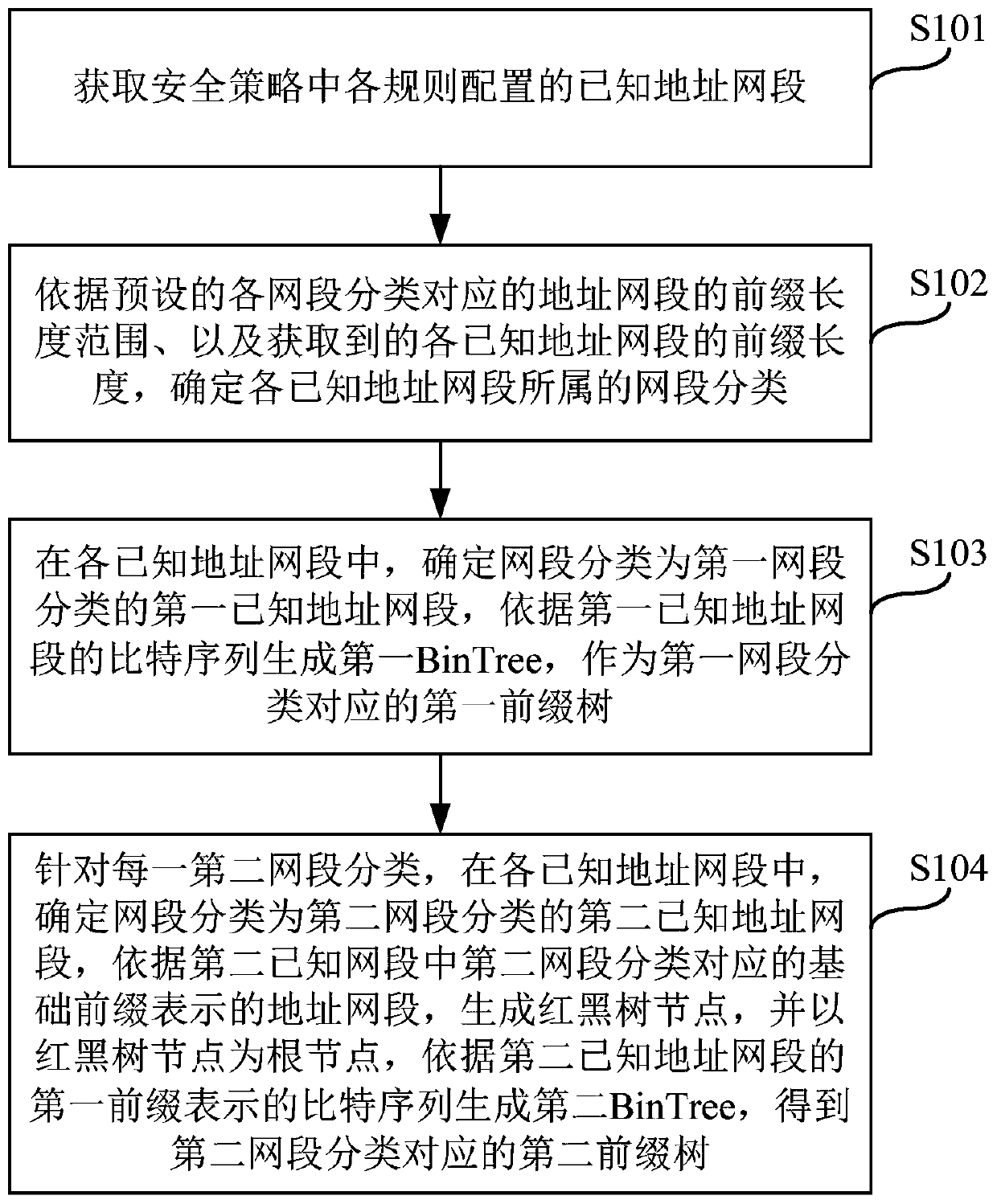
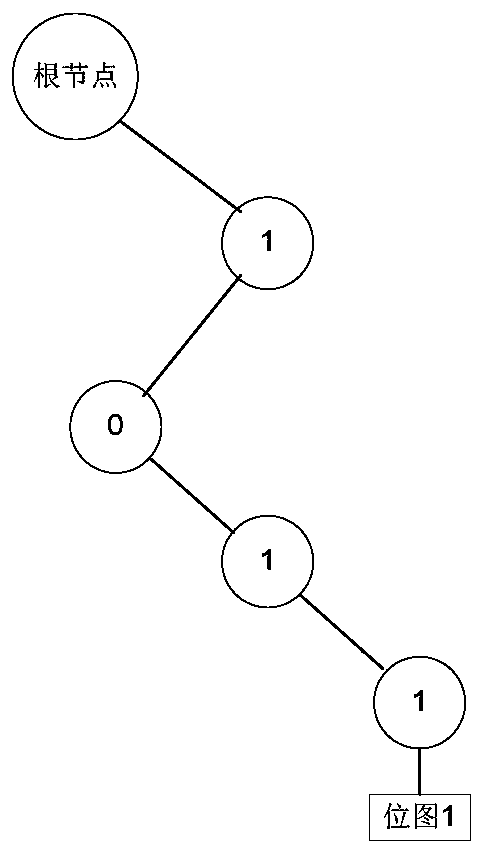
ActiveCN110290117AImprove matching efficiencyImprove the efficiency of matching IP addressesTransmissionIp addressData mining
The embodiment of the invention provides an IP address matching method and device, and relates to the technical field of network security, and the method is applied to network equipment, and comprises the steps: obtaining a to-be-matched target IP address and a target basic prefix of each second network segment classification corresponding to the target IP address; in the first prefix tree, searching whether a first sub-node matched with the target IP address exists or not according to a longest matching principle, and obtaining a first matching result; searching whether a second sub-node matched with the target IP address exists in the red-black tree node of each second prefix tree or not, and if yes, searching whether a third sub-node matched with the target IP address exists or not in a second BinTree with the second sub-node as a root node so as to obtain a second matching result; and determining a final matching result of the target IP address according to the first matching result and the second matching result. By adopting the method and the device, the IP address matching efficiency can be improved.
Owner:NEW H3C SECURITY TECH CO LTD
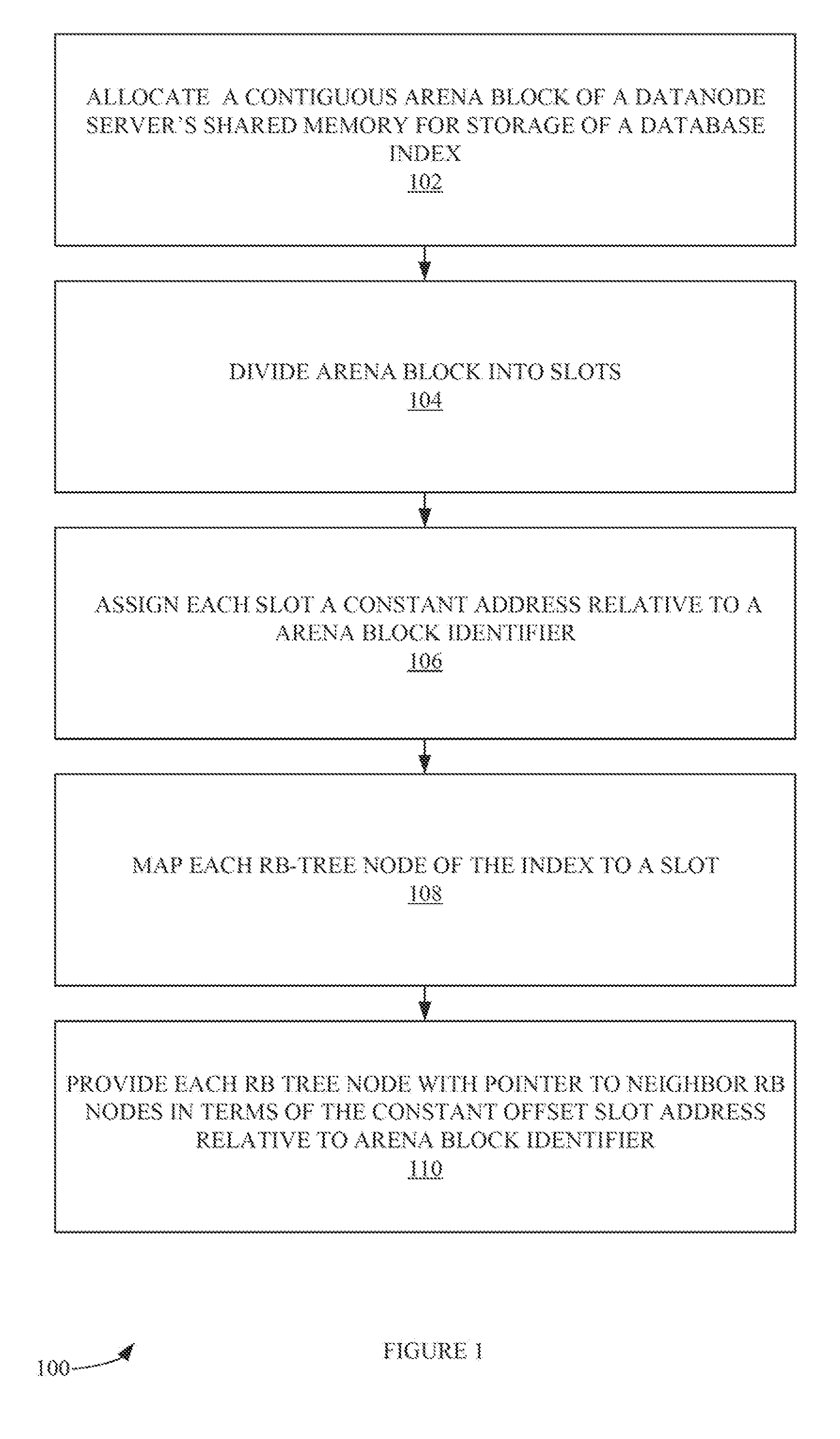
Method and system of implementing a database index in shared memory
InactiveUS20140344530A1Input/output to record carriersSpecial data processing applicationsMemory addressDatabase index
In one exemplary embodiment, a method includes allocating an arena block of a shared memory of a database node server. The arena block is divided into one or more slots. The one or more slots include a discreet and constant area of memory within the arena block. Each slot is assigned a constant-memory address relative to an arena-block's shared memory address. The index is implemented as a red-black tree data structure. Each red-black tree node is mapped to a slot. Each red-black-tree node is provided a pointer to one or more neighbor nodes. The index stored in shared memory can be used during a ‘warm’ rebooting process.
Owner:AEROSPIKE INC
Method for extracting binary image quick skeleton based on sequential refining
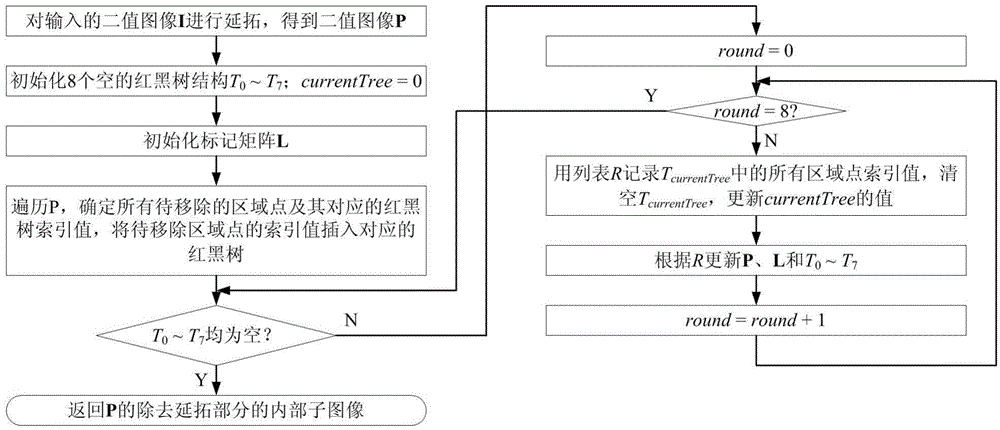
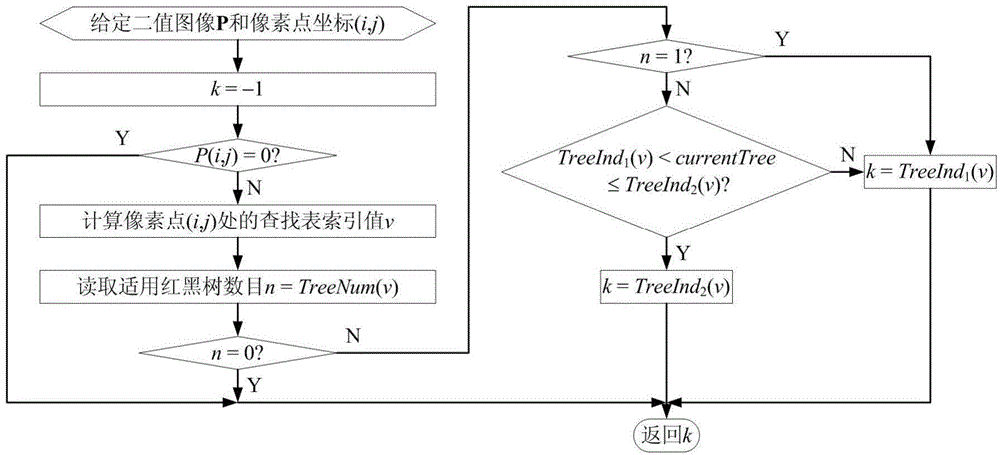
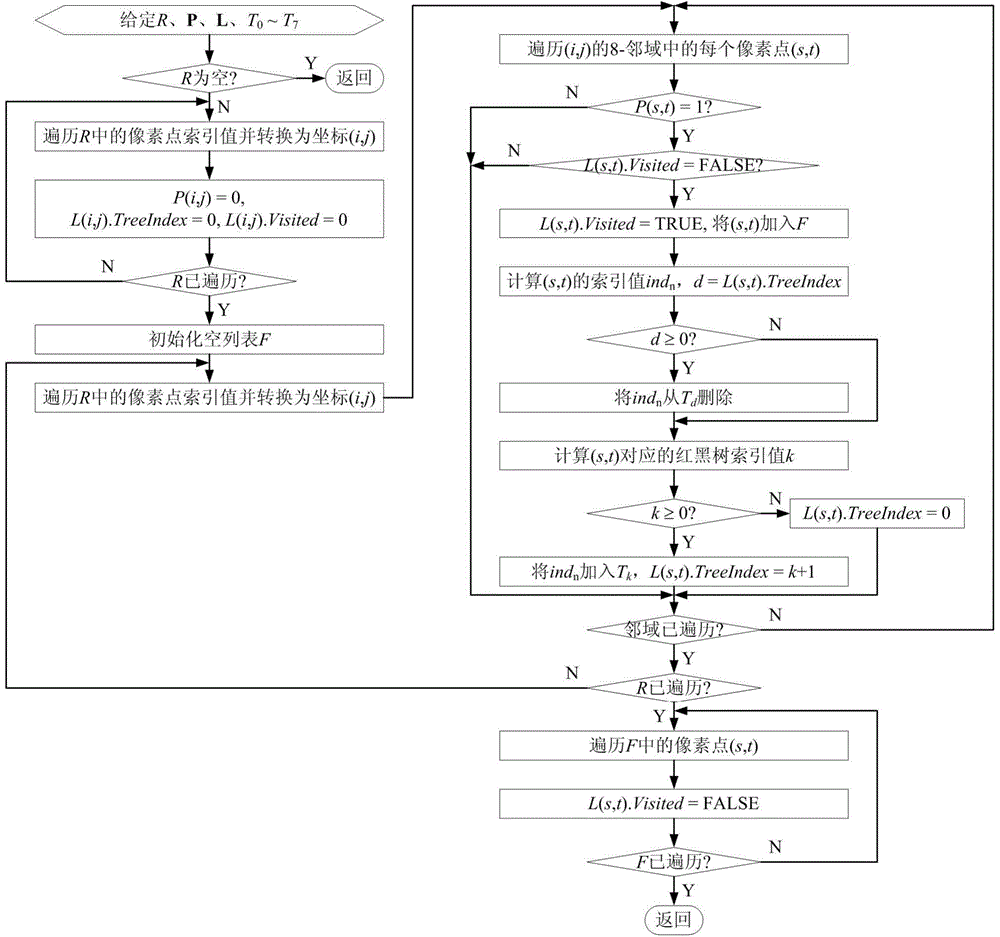
ActiveCN104637066AFast extractionReduce repetitive operationsImage analysisTree (data structure)Computer vision
The invention discloses a method for extracting a binary image quick skeleton based on sequential refining operation. The method comprises the following steps of in the sequential refining process of a binary image area, utilizing a red and black tree data structure to record and manage the removed area points caused by the refining operation in each step; after refining operation in each step, according to the recorded information of the removed area points, inspecting other pixels in 8 adjacent areas of each removed area point, and determining the to-be-removed area point required by the subsequent refining operation. The method has the advantages that the repeated operation is furthest reduced when the removed area points caused by the refining operation are determined, the searching time required by the management of the to-be-removed area point is reduced, and the running speed of the skeleton extracting method based on the sequential refining is obviously improved.
Owner:HUNAN UNIV
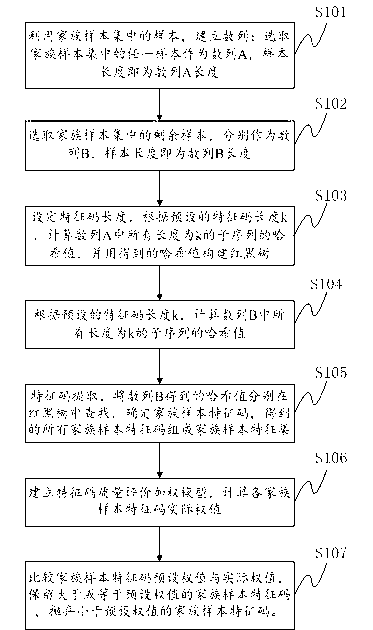
Method and system for automatically extracting virus characteristics based on family samples
ActiveCN103324888AImprove efficiencyIncrease the number ofPlatform integrity maintainancePattern recognitionLongest common subsequence problem
The invention provides a method and a system for automatically extracting virus characteristics based on family samples. According to the method and the system, a longest public subsequence algorithm is modified, a sequence A and a sequence B are established by using samples in the family samples, Hash values of subsequences with lengths equal to preset values in the sequence A and the sequence B are calculated respectively through preset feature code lengths, and the Hash values of the subsequences in the sequence A and the sequence B are matched through a red black tree manner, if the Hash values are same, the subsequences corresponding to the Hash values are public subsequences of the sequence A and the sequence B, and the public subsequences are feature codes of the family samples; and when surplus samples are taken as the sequence B and searched in a red black tree, feature codes of all family samples are obtained and combined into a feature set of the family samples, a weighting model is evaluated according to qualities of the established feature codes, the qualities of the established feature codes are judged, and the feature codes of the family samples are determined. According to the method, the time complexity of the algorithm is simplified, and the extraction efficiency and the accuracy of the feature codes are improved.
Owner:HARBIN ANTIY TECH
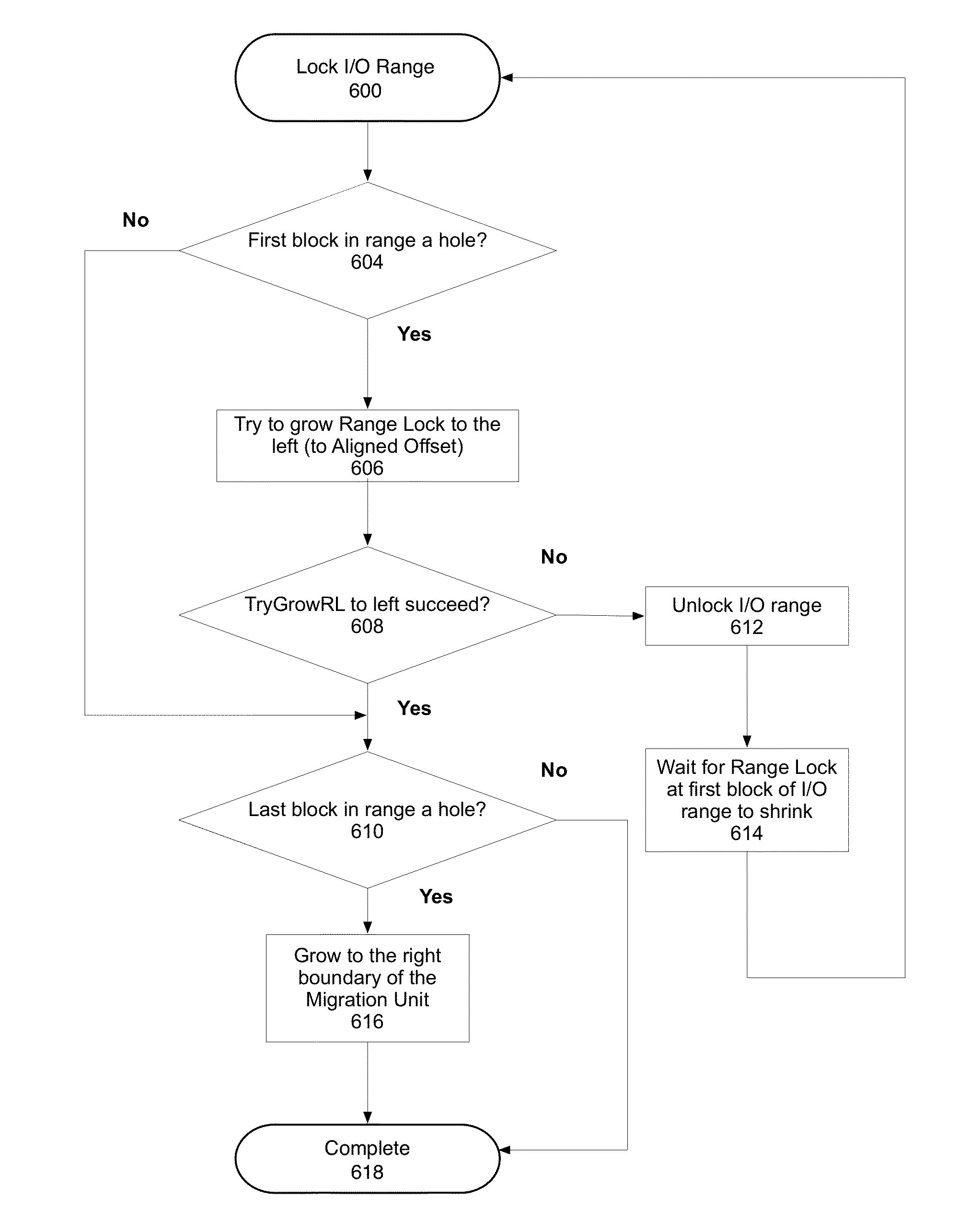
Methods and systems for maintaining a storage volume with holes and filling holes
ActiveUS20130219139A1Improve the level ofMemory loss protectionUnauthorized memory use protectionHard disc driveTheoretical computer science
In one embodiment, a method for managing access to a fast non-volatile storage device, such as a solid state device, and a slower non-volatile storage device, such as a magnetic hard drive, can include a method of managing a sparse logical volume in which unmapped blocks of the logical volume are not allocated until use. In one embodiment, a method of sparse hole filling operates in which range locks are dynamically adjusted to perform allocations for sparse hole filling, and then re-adjusted to perform standard operations using a byte range lock. In one embodiment, a high level data structure can be used in the range lock service in the form of an ordered search tree, which could use any search tree algorithm, such as red-black tree, AVL tree, splay tree, etc.
Owner:APPLE INC
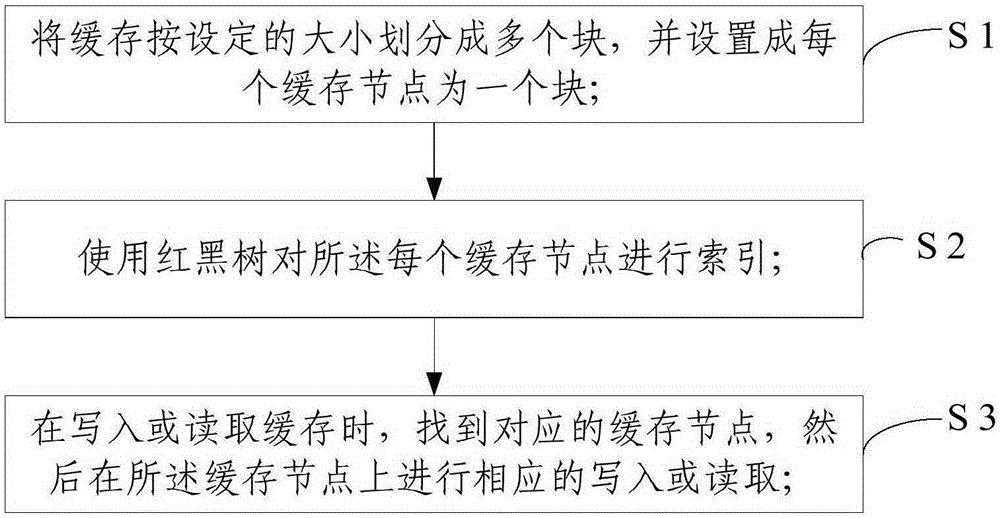
Adaptive cache mixed reading/writing method
InactiveCN105183378AEnsure read and write consistencyFast searchInput/output to record carriersParallel computingRed–black tree
The invention relates to an adaptive cache mixed reading / writing method and system. The method comprises: S1, dividing a cache of a memory into a plurality of blocks according to a set size, and setting each cache node to be a block; S2, indexing each cache node by using a red black tree; and S3, during cache writing or reading, finding the corresponding cache node and then performing corresponding writing or reading on the cache node, wherein during cache writing or reading, the reading or writing state and ratio of the cache are subjected to statistics, and the cache writing or reading ratio is adjusted. According to the method, the cache reading or writing ratio is adaptively adjusted by controlling cache reading or writing size.
Owner:深圳神州数码云科数据技术有限公司
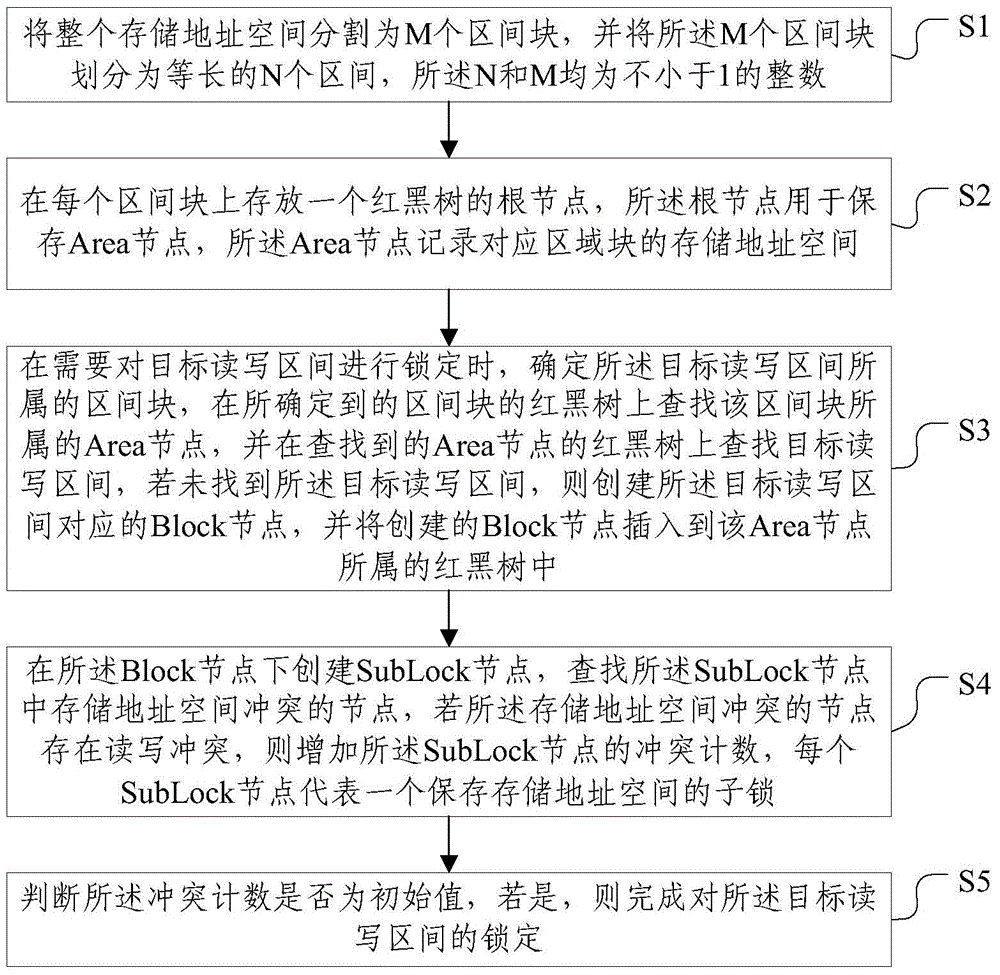
Double-controller-based read-write locking method and device
ActiveCN105808155AAccurate processingReduce communicationInput/output to record carriersMemory adressing/allocation/relocationMemory addressRed–black tree
The invention discloses a double-controller-based read-write locking method and device, and relates to the technical field of disk data read-write. The method comprises the following steps: determining an interval block, to which a target read-write interval belongs; searching an Area node, to which the interval block belongs, on a read-black tree of the determined interval block; searching the target read-write interval on a red-black tree of the searched Area node; if the target read-write interval is not searched, creating a Block node corresponding to the target read-write interval and inserting the created Block node into the red-black tree of the Area node; creating a SubLlock node under the Block node; searching nodes, the memory address spaces of which have conflict, in the SubLock node; adding conflict count of the SubLock node if the nodes, the memory address spaces of which have conflict, have read-write conflict; judging whether the conflict count is an initial value; if the conflict count is an initial value, completing the locking of the target read-write interval. Through the coordination of the steps, the communication can be decreased and the locking conflict can be processed more accurately.
Owner:武汉神州数码云科网络技术有限公司 +1
Method for organizing and accessing metadata file log
ActiveCN102541982AReduce sync operationsReduce processing timeSpecial data processing applicationsDependabilityRed–black tree
The invention provides a method for organizing and accessing a metadata file log. The method comprises the following steps of: organizing all files related to a consistency operation of a log system by utilizing a red-black tree, and selecting a file name of a log file as a keyword of the red-black tree. According to the method for organizing and accessing the metadata file log, provided by the invention, the files related to a reliable operation are managed by guiding the red-black tree so that operation times of the files in the reliable operation are reduced and performance of the reliable operation is improved; and simultaneously, an operation of writing a plurality of metadata into a disc is subjected to convergence management so that a sync operation of the files is largely reduced and the processing time of the reliable operation is shortened.
Owner:DAWNING INFORMATION IND BEIJING +1
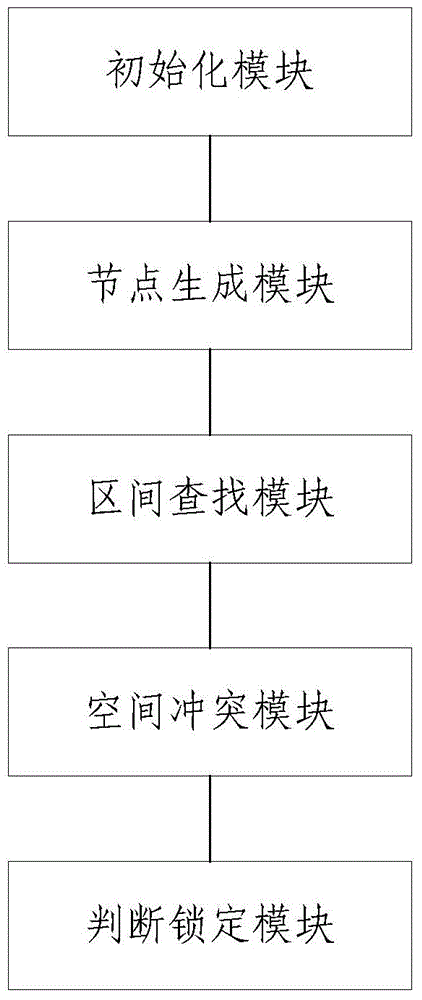
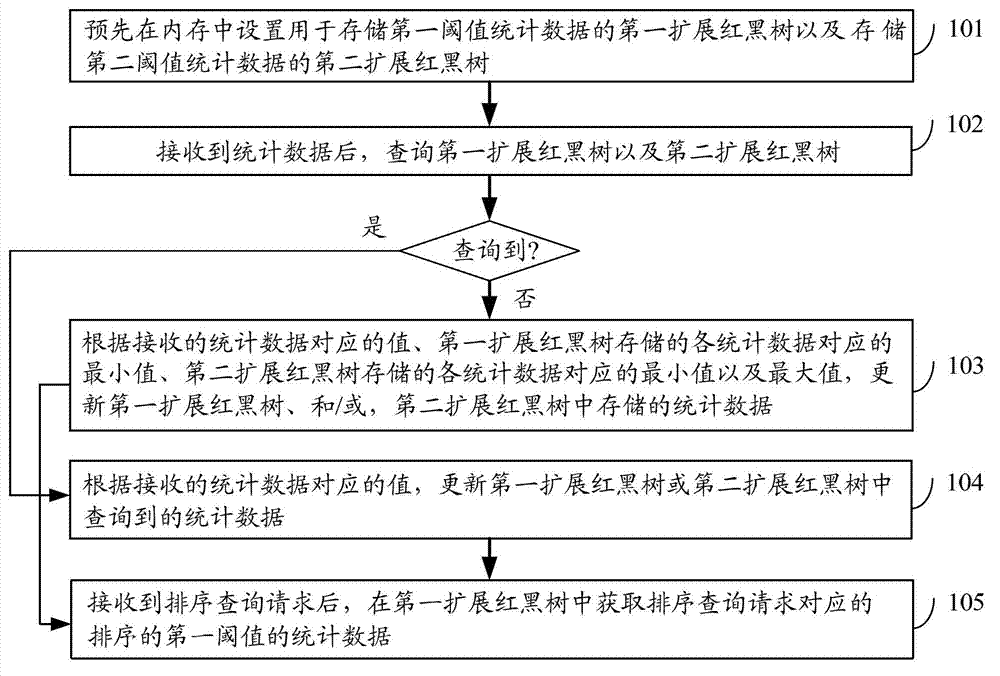
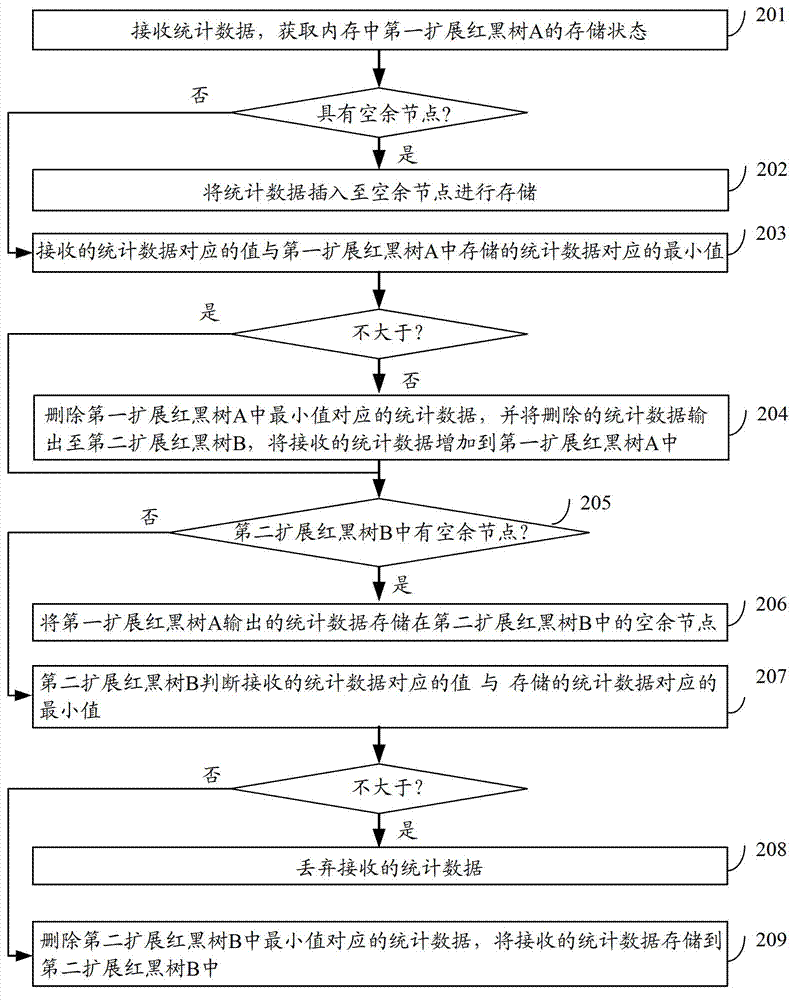
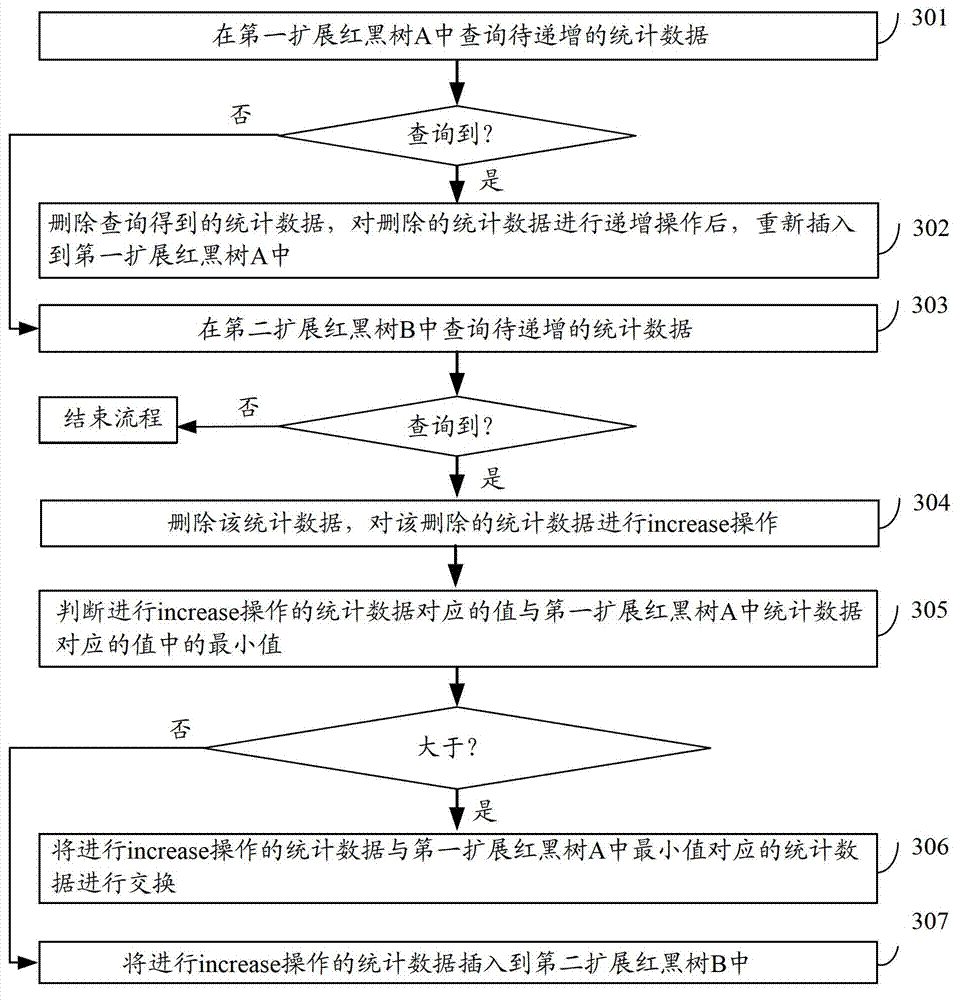
Acquisition method of ordering statistical data and ordering device
ActiveCN103116641AShorten the timeImprove sorting efficiencySpecial data processing applicationsData queryData mining
Owner:新浪技术(中国)有限公司
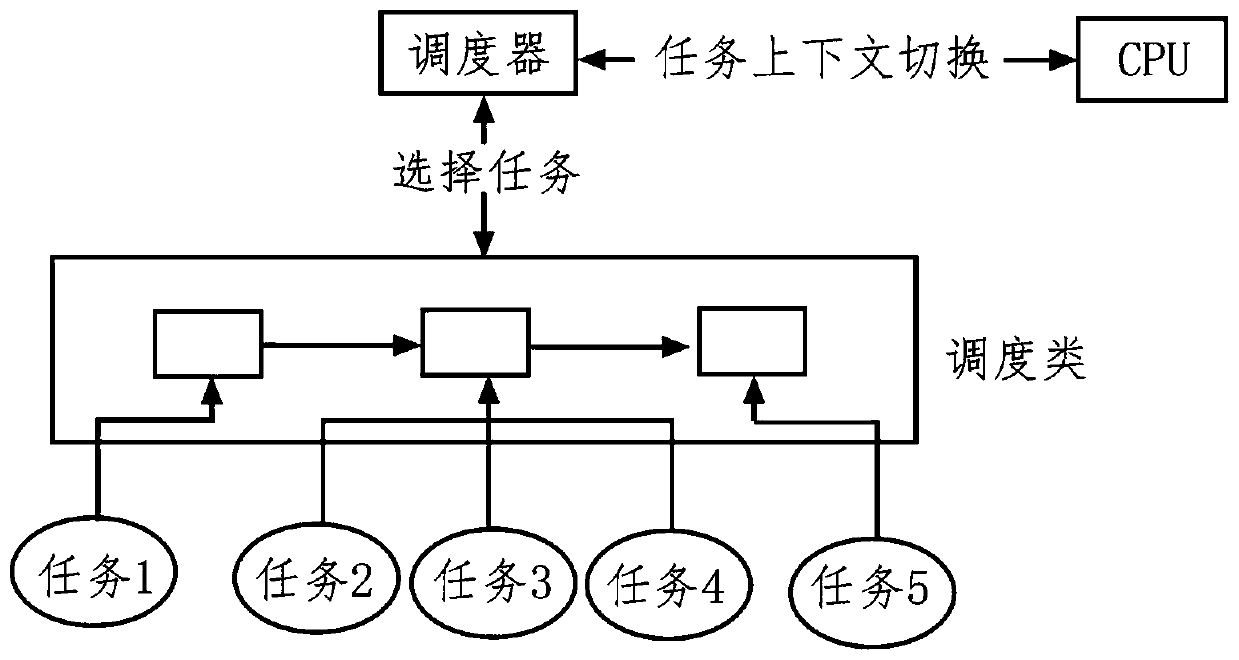
Task scheduling method and device for embedded operating system and storage medium
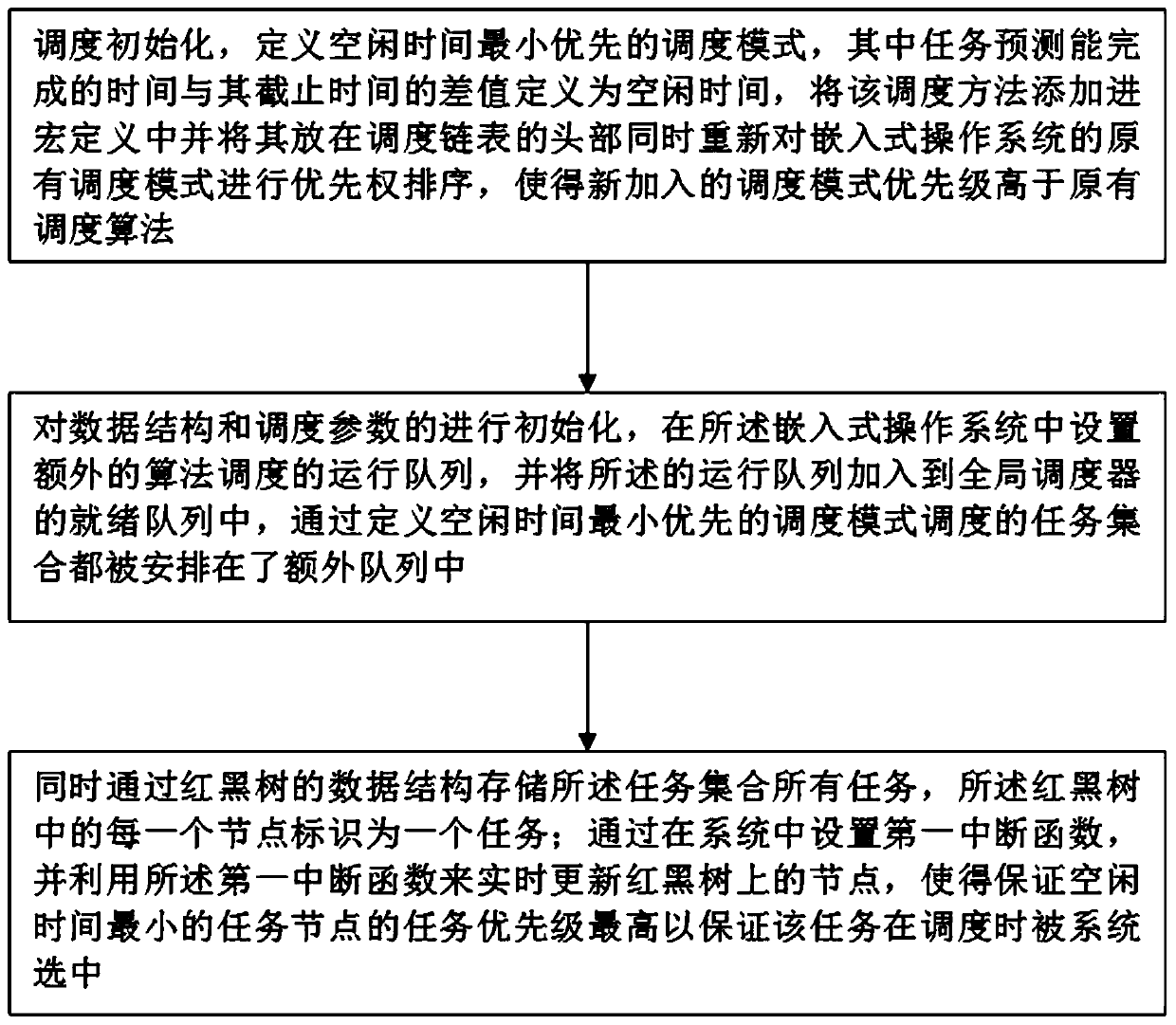
PendingCN110825506AImproved task distribution balanceSelf-aware affinityProgram initiation/switchingGlobal schedulingOperational system
The invention discloses a task scheduling method of an embedded operating system. The method comprises steps of carrying out scheduling initialization, defining a scheduling mode with minimum idle time priority; wherein the difference between the task prediction completion time and the deadline is defined as idle time; adding the scheduling method into macro definition and placing at the head of ascheduling linked list, and performing priority ranking on the original scheduling mode of the embedded operating system again, so that the priority of the newly added scheduling mode is higher thanthat of the original scheduling algorithm; initializing a data structure and scheduling parameters, setting an additional algorithm scheduling running queue in the embedded operating system, and adding the running queue into a ready queue of a global scheduler; wherein all the task sets scheduled by defining the scheduling mode with the minimum idle time priority are arranged in an additional queue; and storing all tasks of the task set through a data structure of a red-black tree.
Owner:湖南智领通信科技有限公司
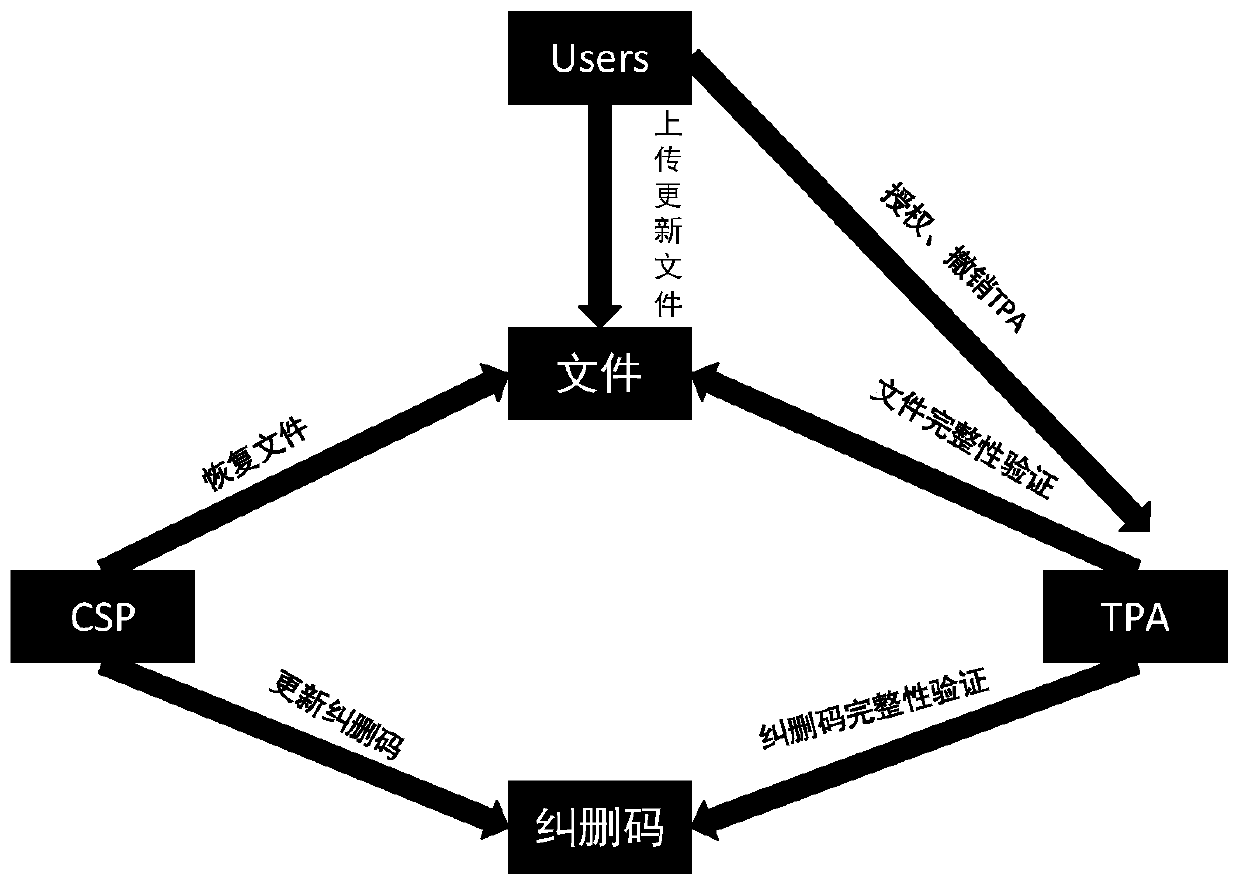
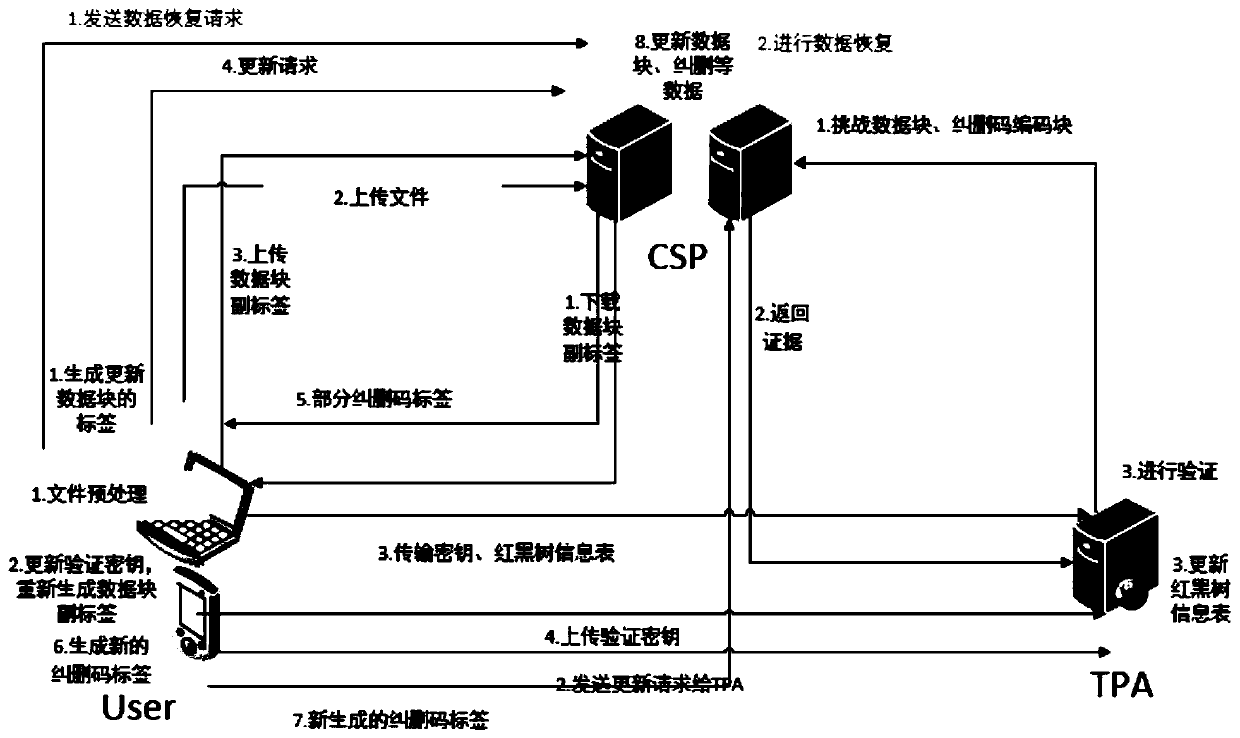
Cloud storage revocable dynamic data integrity verification system and method
PendingCN110008755ADynamic Update EfficientRealize privacy protectionDigital data protectionData integrityCloud storage system
The invention discloses a cloud storage revocable dynamic data integrity verification system and method. A red and black tree information table and an erasure code caching technology are utilized to reduce the overhead of dynamically updating data, and a new signature technology is utilized to reduce the calculation overhead when the data block label is generated, so that the file preprocessing speed is higher, and meanwhile, the canceling of a verifier is also supported. The method is used for safe storage of the cloud storage system.
Owner:广东优世联合控股集团股份有限公司
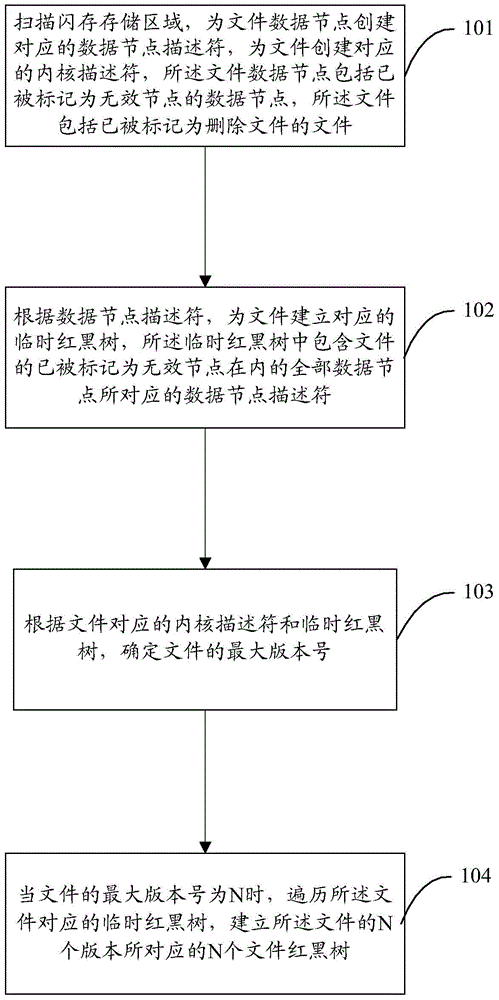
Flash memory file data recovery method and apparatus
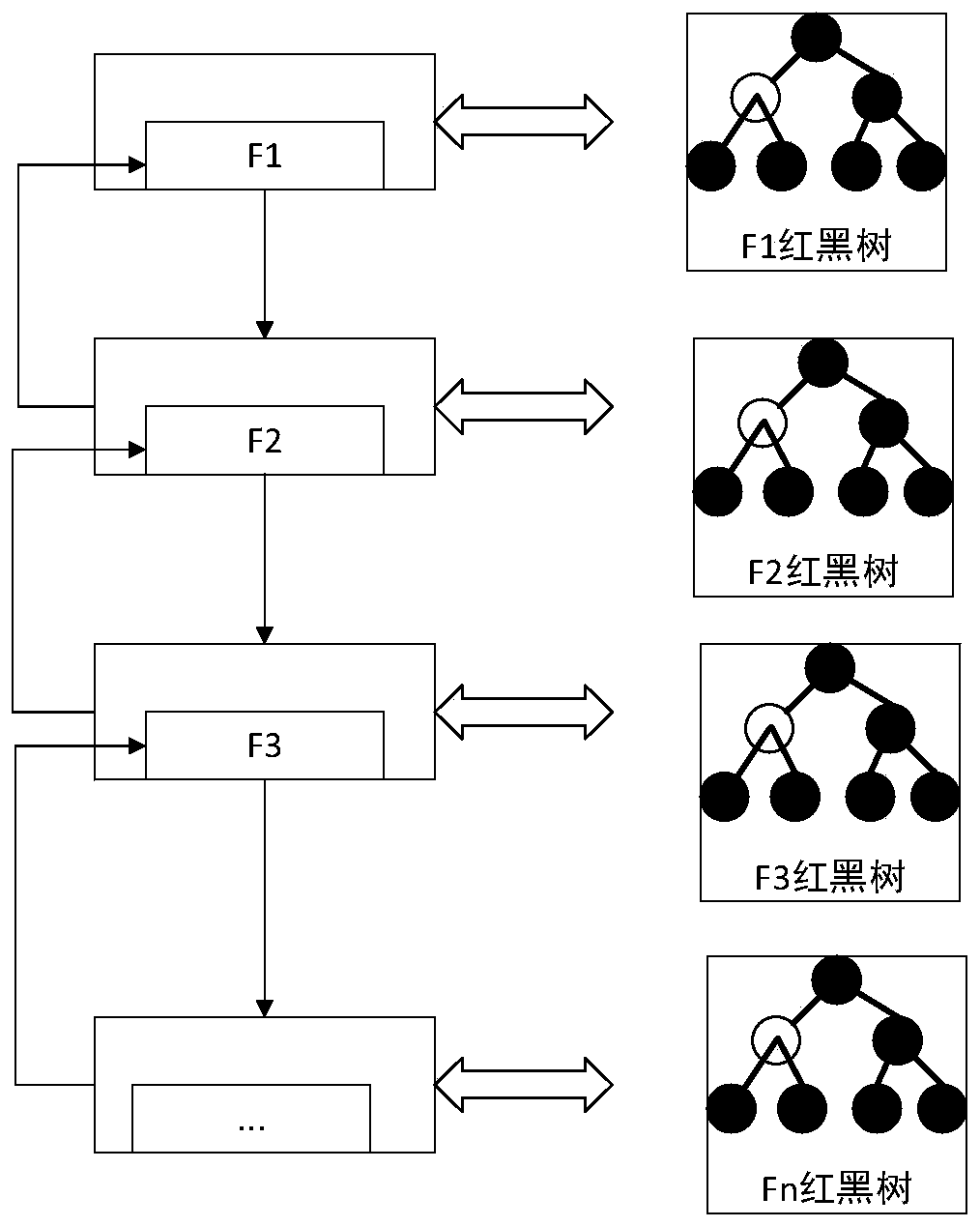
InactiveCN105487939ARedundant operation error correctionSpecial data processing applicationsData nodeRed–black tree
The invention discloses a flash memory file data recovery method. The method comprises: scanning a storage region of a flash memory, creating corresponding data node descriptors for file data nodes, and creating corresponding kernel descriptors for files, wherein the file data nodes include a data node that has been marked as an invalid node, and the files include a file that has been marked as a deletion file; according to the data node descriptors, establishing corresponding temporary red black trees for the files, wherein the temporary red black trees contain data node descriptors corresponding to all data nodes, including the data node that has been marked as the invalid node, of the files; according to the kernel descriptors and the temporary red black trees corresponding to the files, determining a maximum version number of the files; and when the maximum version number of the files is N, traversing the temporary red black trees corresponding to the files, and establishing N file red black trees corresponding to N versions of the files, wherein N is a positive integer. The invention furthermore discloses a flash memory file data recovery apparatus.
Owner:ZTE CORP
Indoor positioning method based on UWB technology
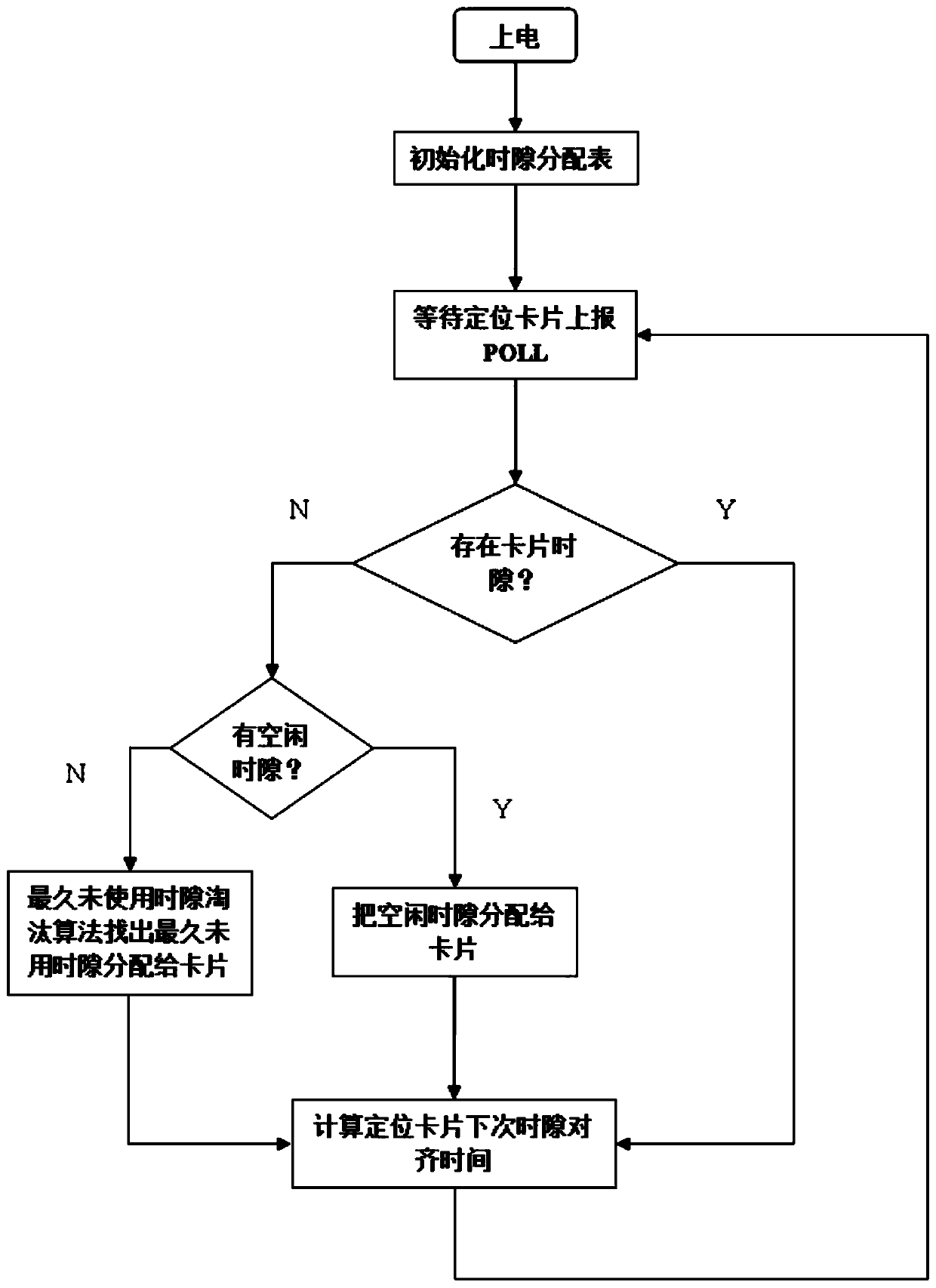
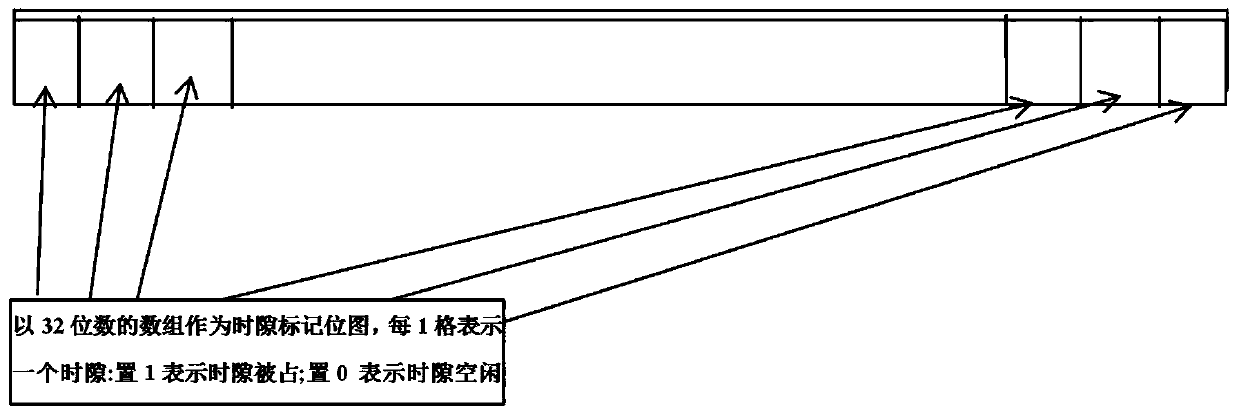
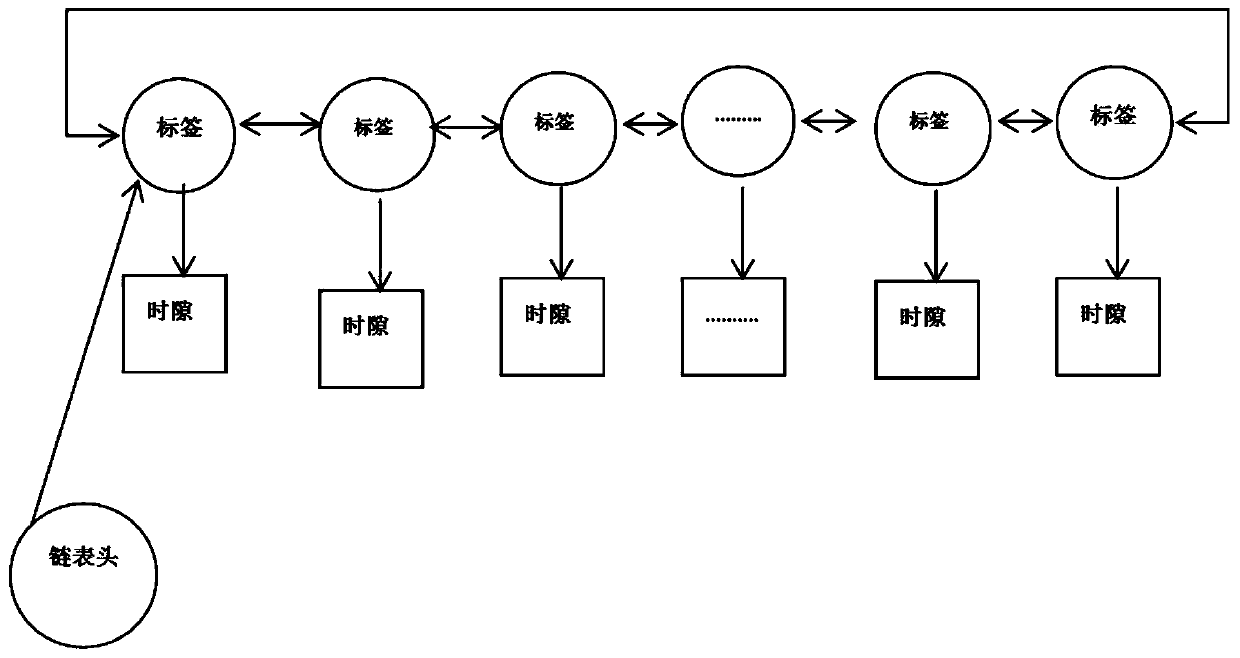
ActiveCN110225461AEfficient managementEffective distributionParticular environment based servicesLocation information based serviceTime domainIdle time
The invention provides an indoor positioning method based on a UWB technology, and mainly solves the problem of communication collision of UWB multi-positioning tags in the prior art. According to thepositioning method, a time division multiplexing technology is adopted in a time domain, time slots of positioning tags are managed and distributed in a unified mode by setting reference base stations, time slot occupation conditions are marked by adopting a bitmap algorithm, and idle time slots are quickly found; a corresponding relation between the positioning tag and the use time slot is recorded by adopting red-black tree index; and the time slot is recovered by adopting the longest non-use elimination algorithm. According to the method, the time slot searching and distribution of the positioning base station end are optimized, the time slot distribution time is shortened to the maximum extent, the probability of communication collision can be effectively reduced, the positioning precision is ensured, and the requirements of different positioning modes can be met.
Owner:GUODIAN LONGYUAN ELECTRICAL +1
Fault storage method and apparatus and fault search method and apparatus
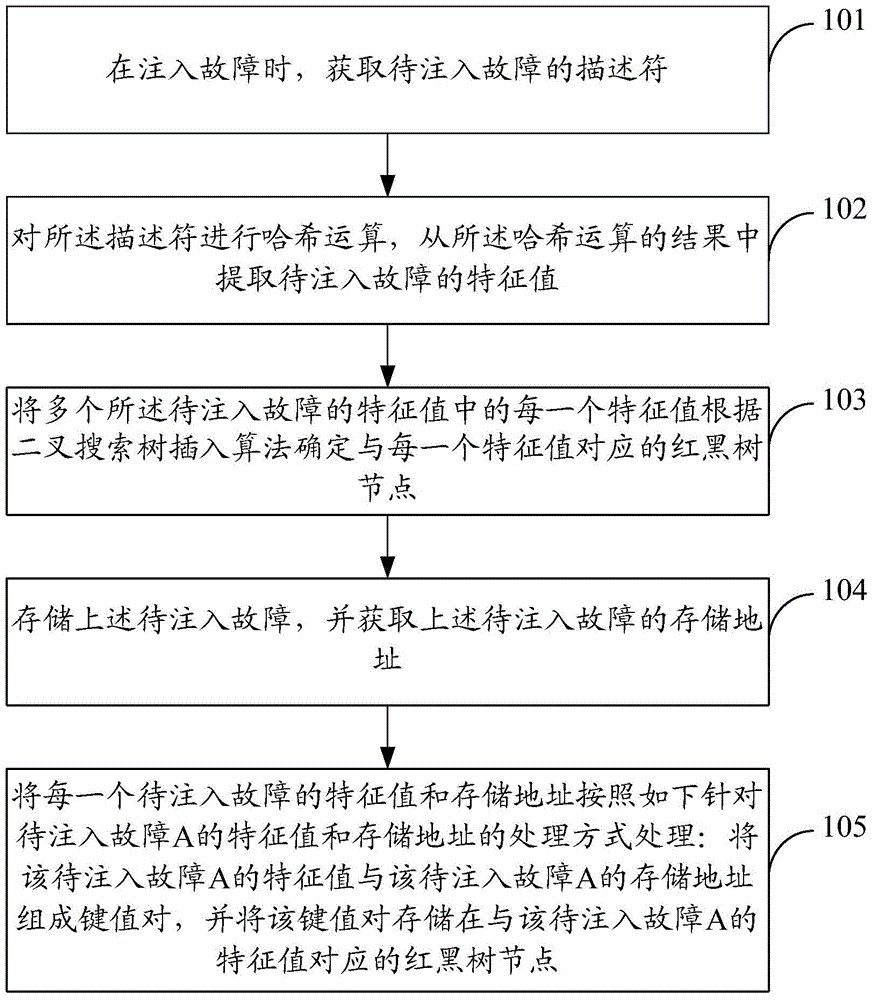
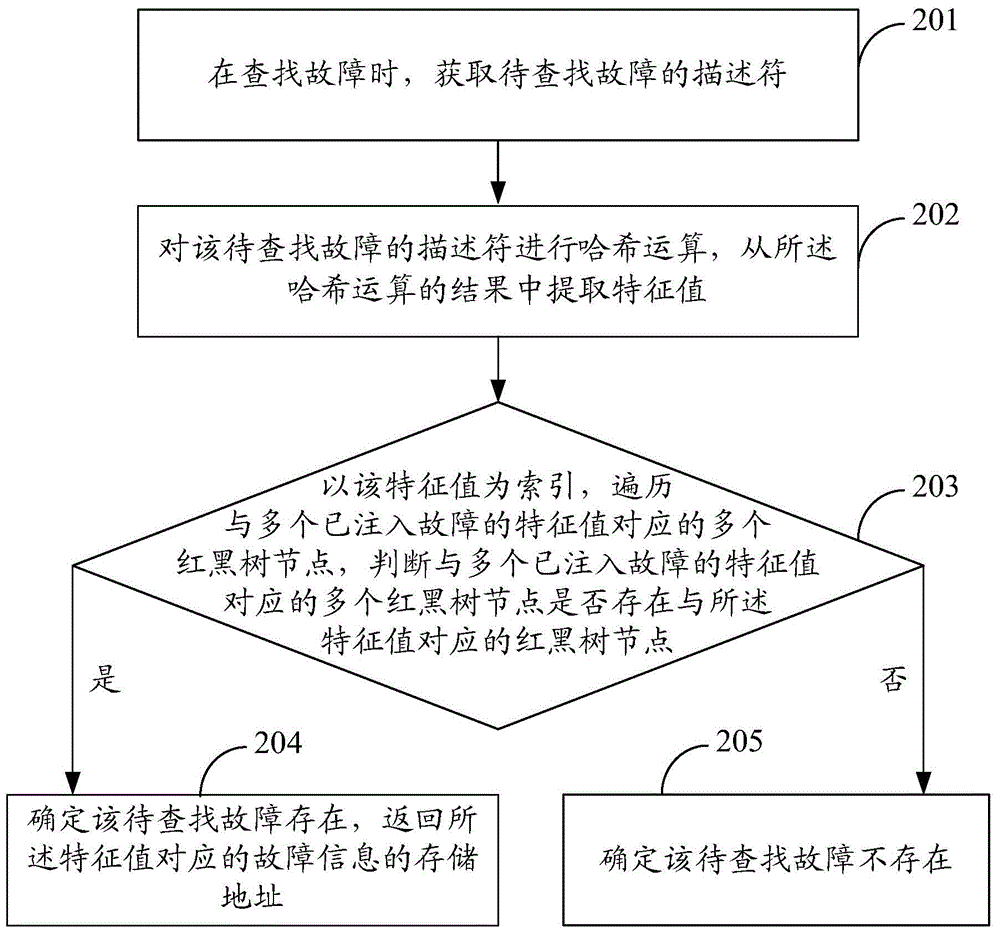
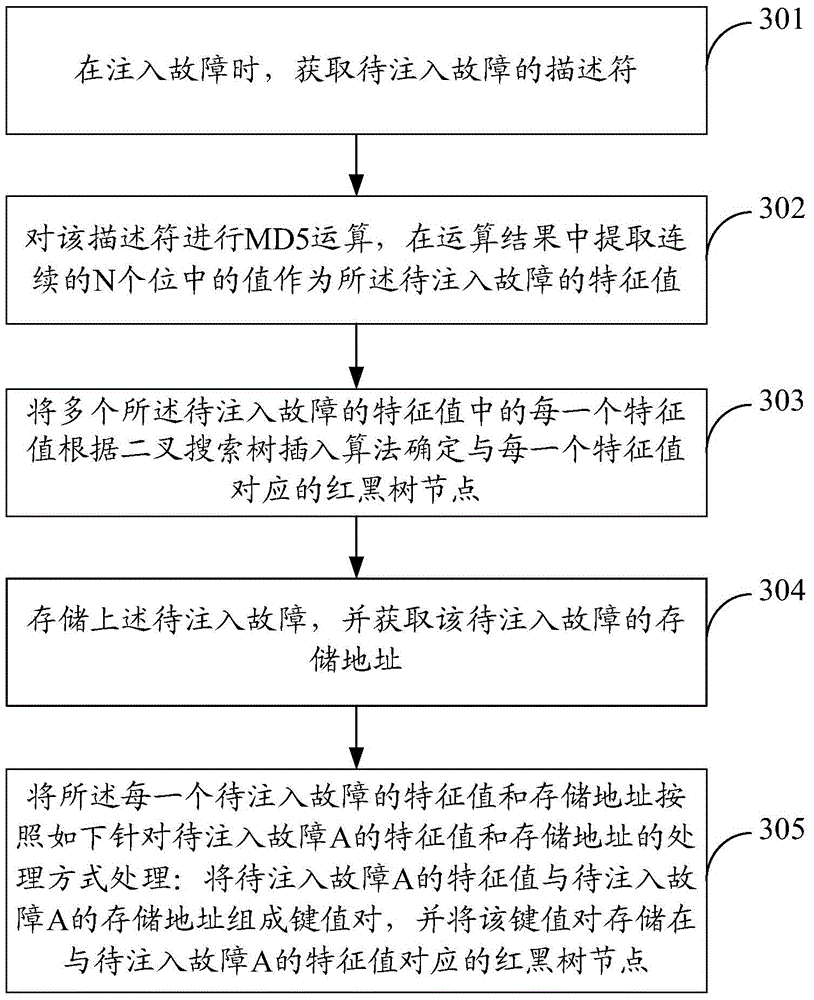
The invention discloses a fault storage method and apparatus and a fault search method and apparatus, and belongs to the field of fault injection. The fault storage method comprises: obtaining descriptors of to-be-injected faults to perform Hash operation during fault injection, and extracting feature values of the to-be-injected faults from a result; determining a corresponding red black tree node according to a binary search tree insertion algorithm for each feature value in the feature values of the to-be-injected faults; storing the to-be-injected faults and obtaining a storage address; and forming a key value pair by the feature value of each to-be-injected fault and the storage address, and storing the key value pair in the red black tree node. The fault search method comprises: obtaining descriptors of to-be-searched faults to perform Hash operation during fault search, extracting feature values from a result, traversing red black tree nodes by taking the feature values as indexes, judging whether the feature values exist or not, if so, determining that the faults exist, and returning a storage address of fault information corresponding to the feature values; otherwise, determining that the faults do not exist. According to the fault storage method and apparatus and the fault search method and apparatus, the fault search efficiency of a fault injection system is effectively improved.
Owner:HUAWEI TECH CO LTD
CFS dispatcher
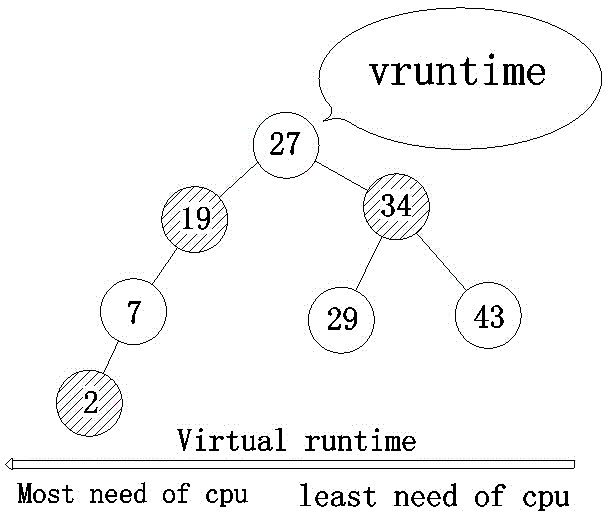
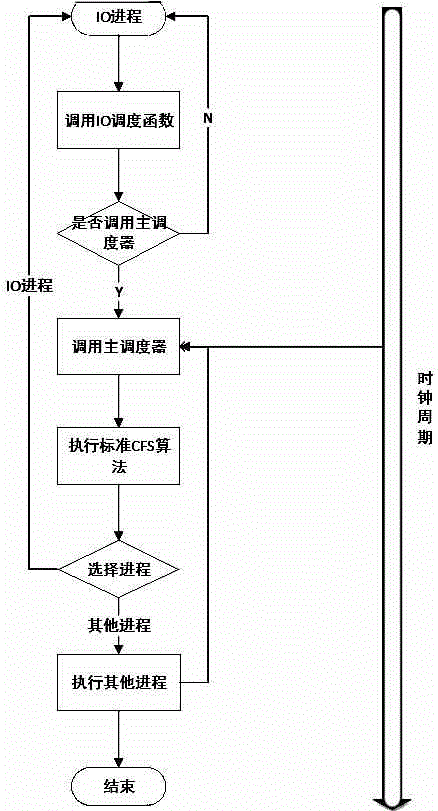
ActiveCN104375883AProcess Scheduling OptimizationComprehensive treatmentProgram initiation/switchingVirtual timeLinux kernel
The invention provides a CFS dispatcher and belongs to the field of linux kernel process scheduling algorithm design. The CFS dispatcher comprises a weight conversion module (1), a time slice distributing module (2), a virtual time module (3), a red-black tree maintaining module (4) and a process selecting module (5). When IO operation is conducted, an IO special dispatching function is called each time the operation is over; when the IO dispatching function is called, the virtual operation time of the process is modified; when the function is called the first time, the virtual operation time is set to be an initial state, and a main dispatcher is called; in next two times of calling, the main dispatcher is normally called; back-and-forth switching is conducted; a next program for operating is selected through the main dispatcher. The CPU time distributed for the IO process by the CFS algorithm can be effectively prolonged, and therefore the IO speed is increased.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
Linear data structure query efficiency improving method
InactiveCN105843750AImprove query efficiencyMemory adressing/allocation/relocationData domainTheoretical computer science
The present invention relates to a linear data structure query efficiency improving method. The method comprises the following steps: taking an ID of a linear storage data object as a KEY of a red-black tree node, and taking an address of the data object in a storage medium as a data domain of the red-black tree node, so as to construct a red-black tree; and inquiring the KEY of the red-black tree in the red-black tree, and when the key corresponding to the ID of the same data object is inquired, obtaining a to-be-searched object from data directing storage addresses. Thus, query in linear storage elements is converted into query in the red-black tree, so that search time is significantly saved.
Owner:SHENZHEN SUNGREAT COMM CO LTD
Order-preserving encryption algorithm based on balanced sort tree storage structure
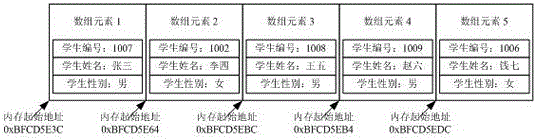
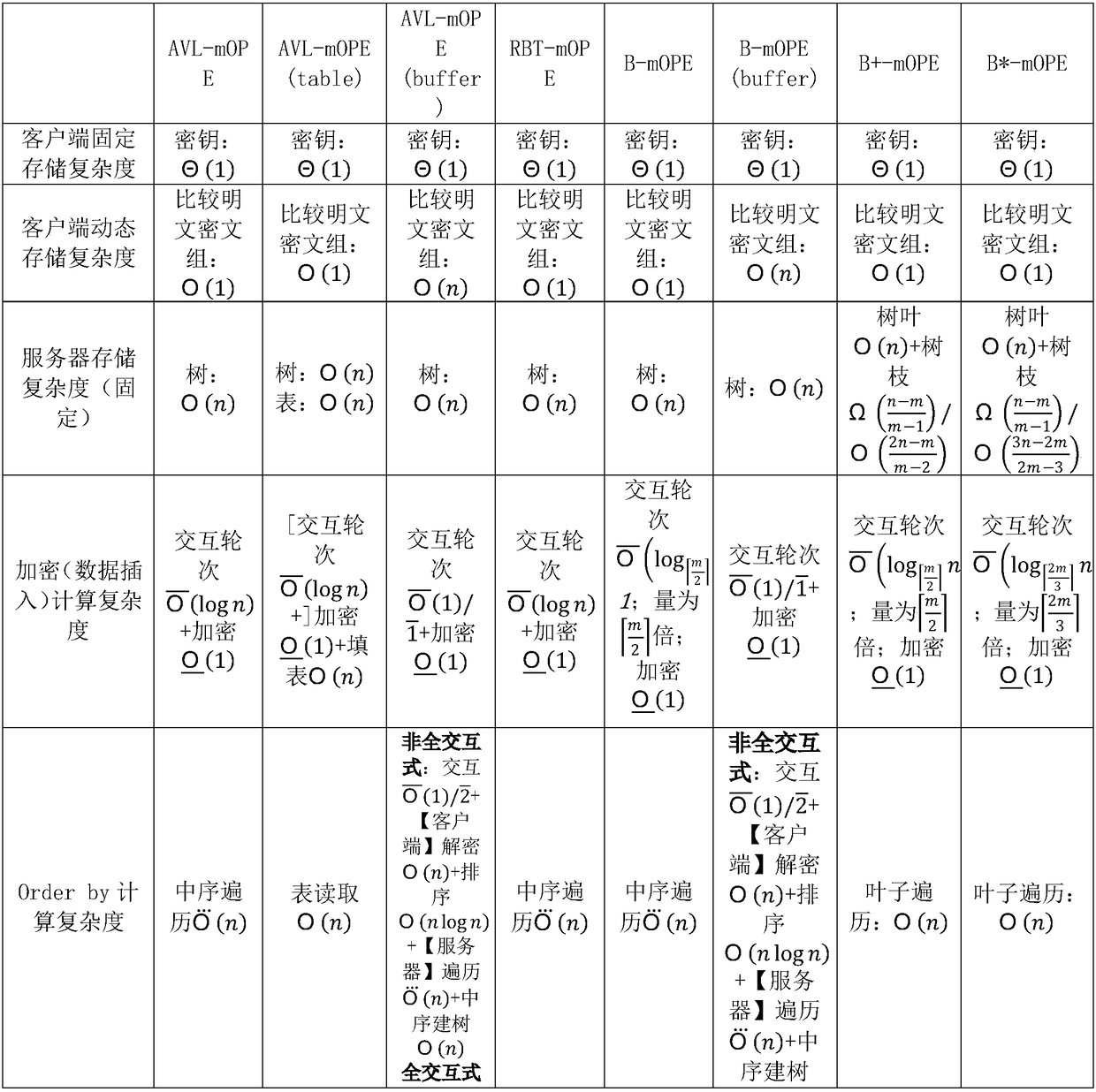
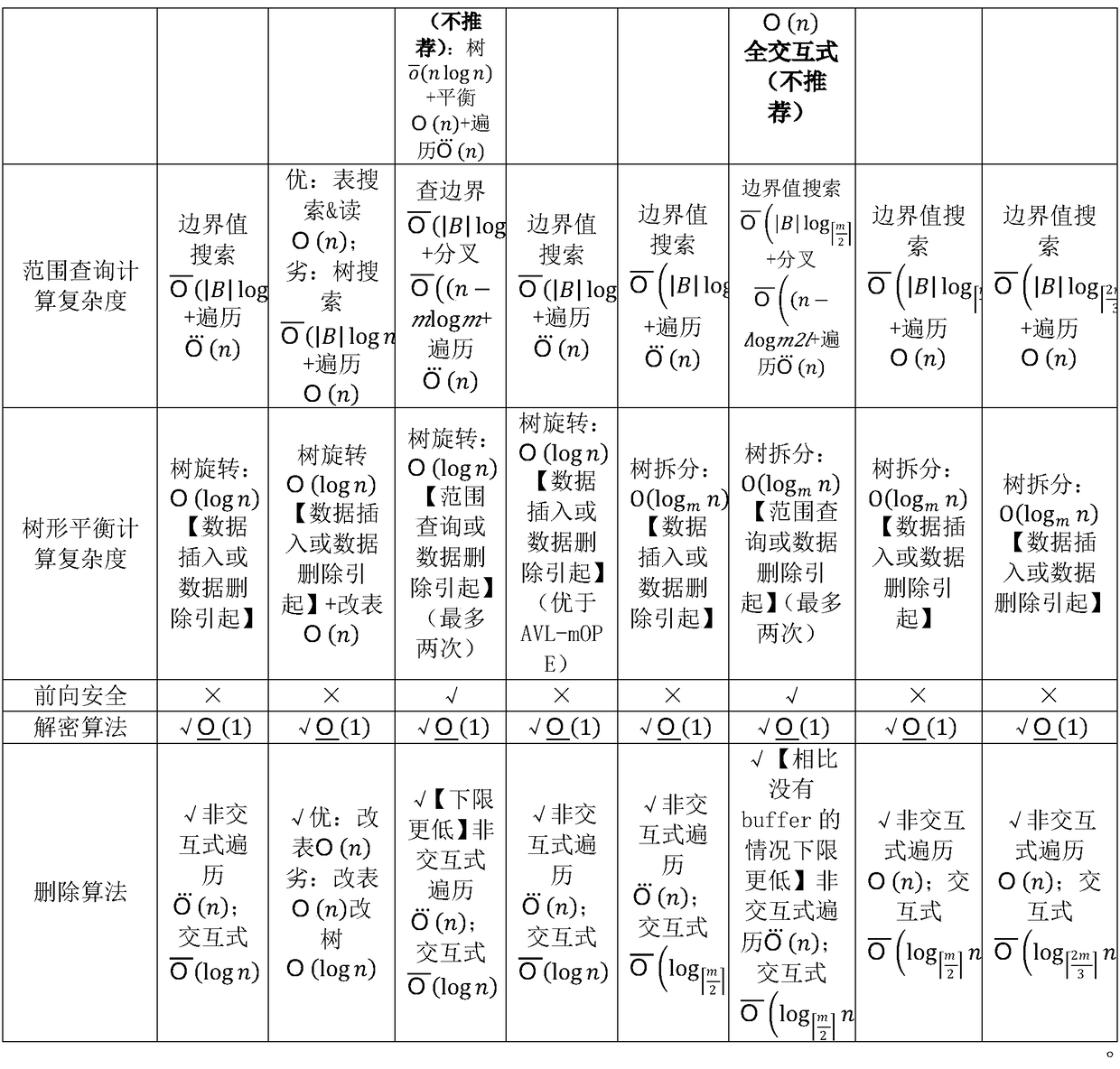
ActiveCN109495446AEncryption apparatus with shift registers/memoriesDigital data protectionSorting algorithmPassword
The invention belongs to the technical field of passwords, and specifically relates to an order-preserving encryption algorithm based on a balanced sort tree storage structure. In the order-preservingencryption algorithm, a data storage basic structure comprises an AVL tree, a red-black tree, a B tree, a B+ tree or a B* tree; and different data storage structures have slightly different algorithmexpressions. The algorithm takes an AVL tree structure as an example, and comprises a basic AVL tree-based ideal secure order-preserving encryption algorithm and some improved order-preserving encryption algorithms. Various algorithms are described from a tree structure, an initialization algorithm, an encryption algorithm, a decryption algorithm, an orderby sort algorithm, a range query algorithm, a deletion algorithm, a balancing algorithm and an interactive query algorithm. Compared with most order-preserving encryptions that cannot achieve the ideal secure effect, the algorithm security provided by the invention has absolute advantages, the algorithm provided by the invention also performs all-directional comparison, and the algorithm is suitable for most systems and is especially suitable for a system with relatively high security requirements and sufficient bandwidth configuration.
Owner:FUDAN UNIV
Open computing language (OpenCL)-based red-black tree acceleration algorithm
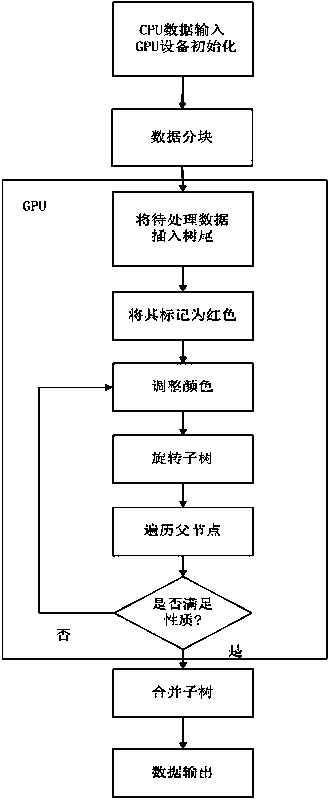
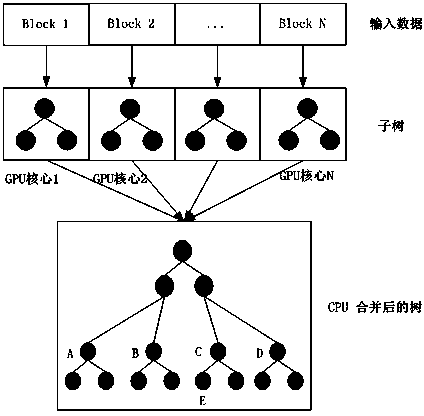
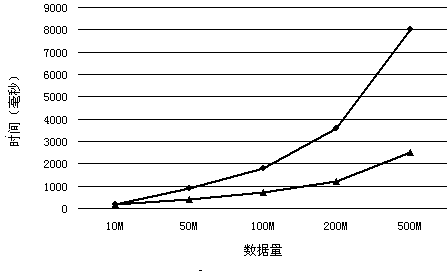
InactiveCN104036141AQuick buildTree building time shortenedSpecial data processing applicationsTheoretical computer scienceRed–black tree
The invention discloses an open computing language (OpenCL)-based red-black tree acceleration algorithm. The method includes that according to the characteristic that multiple calculations are capable of being parallel processed during establishing the red-black tree, an OpenCL heterogeneous platform is adopted to rapidly establish a red-black tree model on the basis of big data; with an idea of employing graphics processing unit (GPU) acceleration, to-be-operated data are divided into multiple data blocks, and multiple cores enter a data insertion operation at the same time by the GPU; and after operations of all GPUs are synchronized, by means of a merge operation, the whole red-black tree is established. The OpenCL-based red-black tree acceleration algorithm has the advantages that in the situation of the big data, the red-black tree is rapid to be established within a short time.
Owner:SHANGHAI UNIV
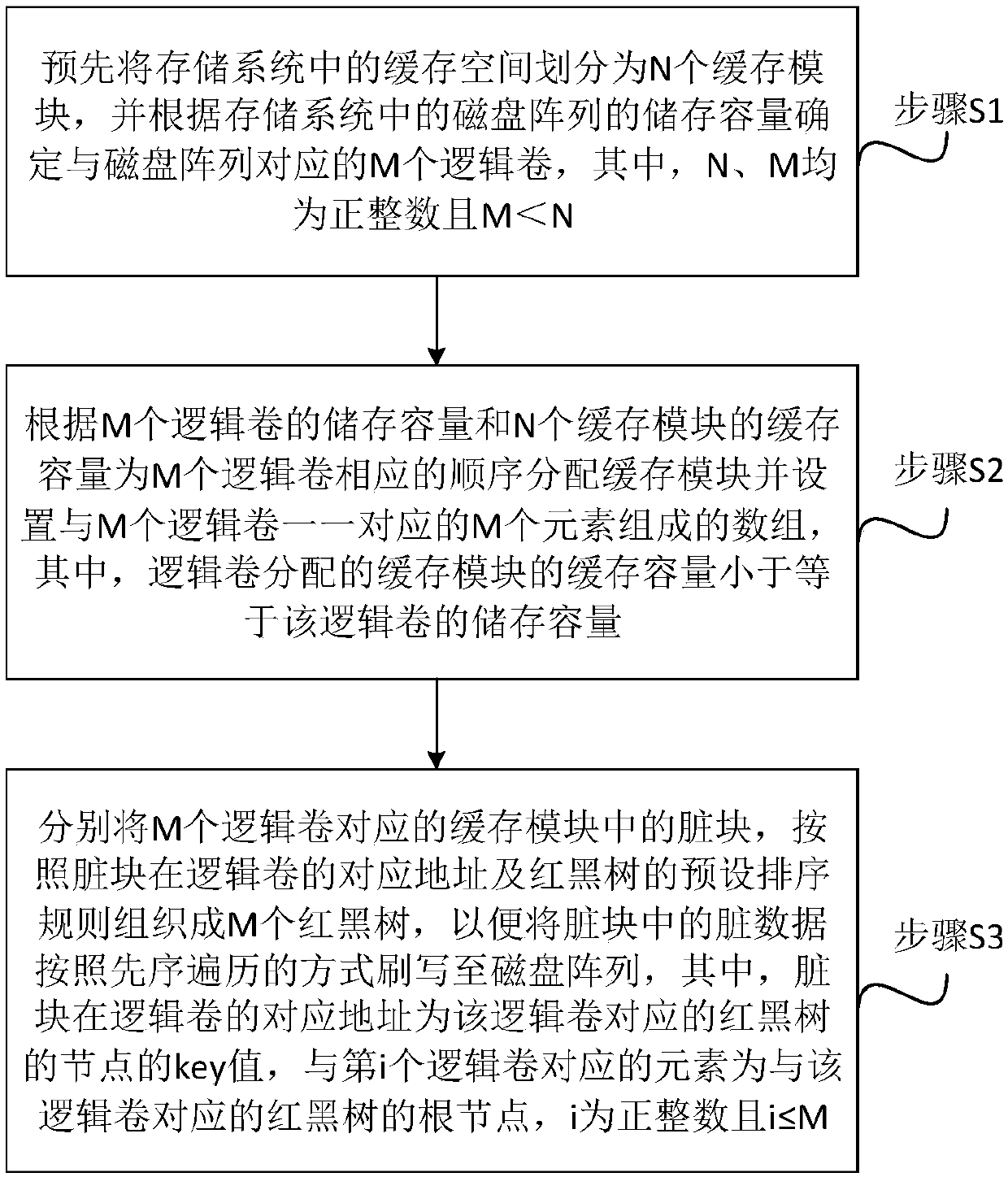
Organizing management method and system of dirty data in cache and storage system
ActiveCN107844436AImprove the writing speedReduce latencyMemory systemsArray data structureDirty data
The invention discloses an organizing management method and system of dirty data in a cache and a storage system. According to the method, cache space is divided into multiple cache modules, and multiple logical volumes are determined according to the storage capacity of a disk array; the cache modules are distributed for the logical volumes, arrays corresponding to the logical volumes in a one-to-one mode are further arranged, and elements in the arrays serve as root nodes of a red-black tree respectively. According to the organizing management method and system of the dirty data in the cacheand the storage system, the address of a dirty block corresponding to any logical volume in the cache modules can also be determined, accordingly the corresponding address of the dirty block in the corresponding logical volume is determined, and the corresponding address serves as a key value of the node of the red-black tree corresponding to the logical volume. Then, the dirty blocks can be organized into the red-black trees according to a preset red-black tree ranking rule, the dirty data in the dirty blocks is written according to a preorder traversal mode when written to the disk array, which is equal to conducting ordered access on the disk array, the writing speed is improved, the writing time is shortened, and the accessing efficiency of the system is improved.
Owner:ZHENGZHOU YUNHAI INFORMATION TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com