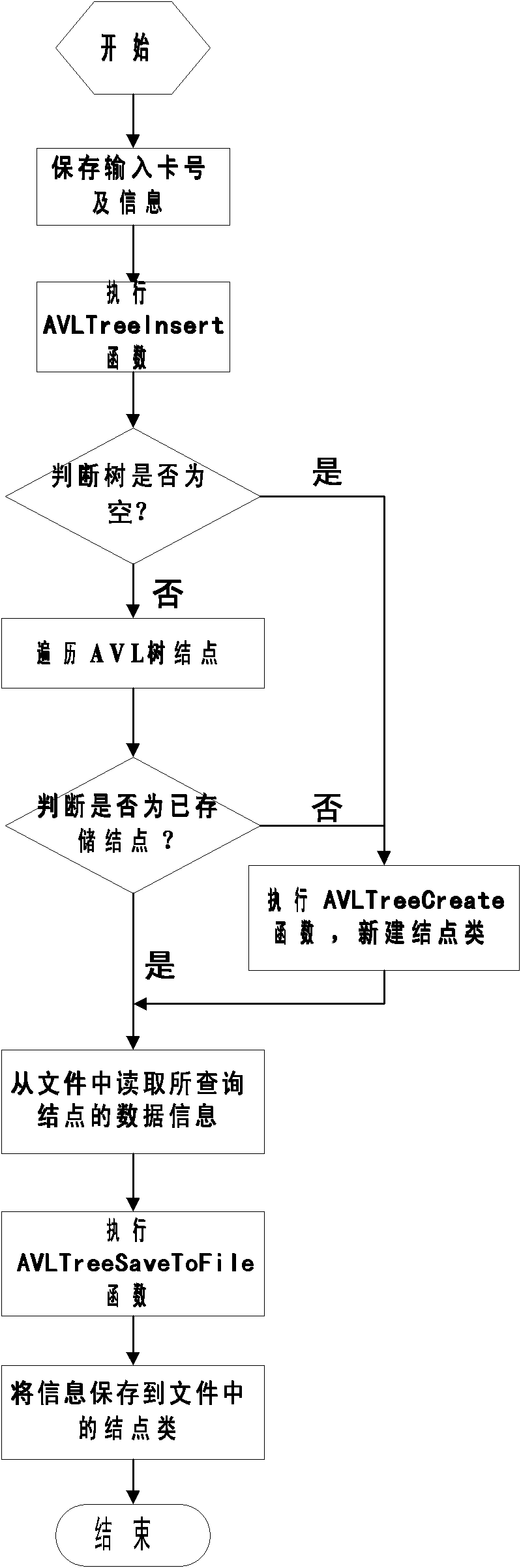
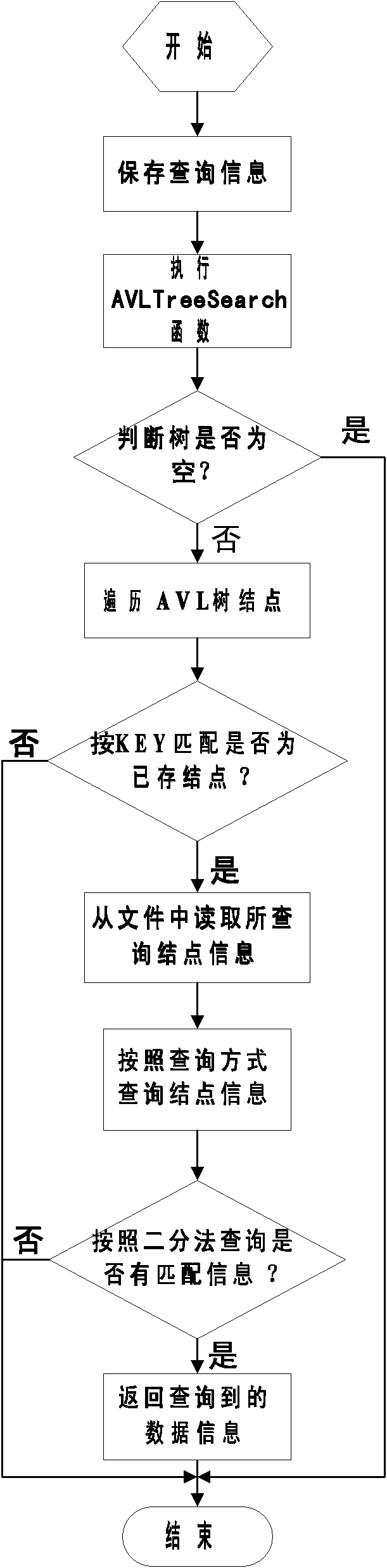
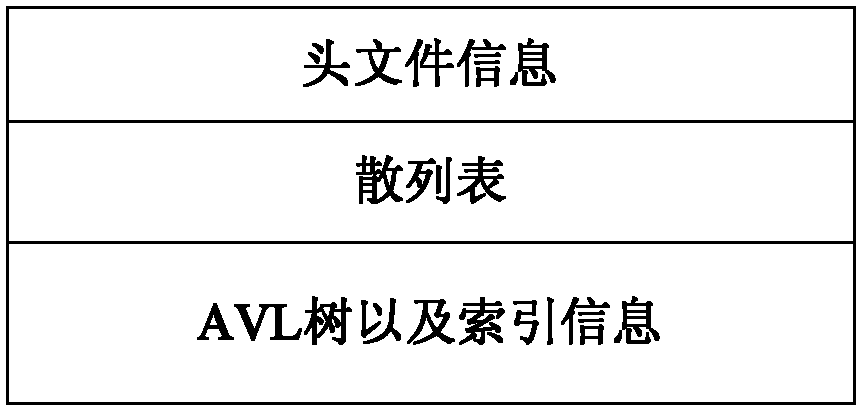
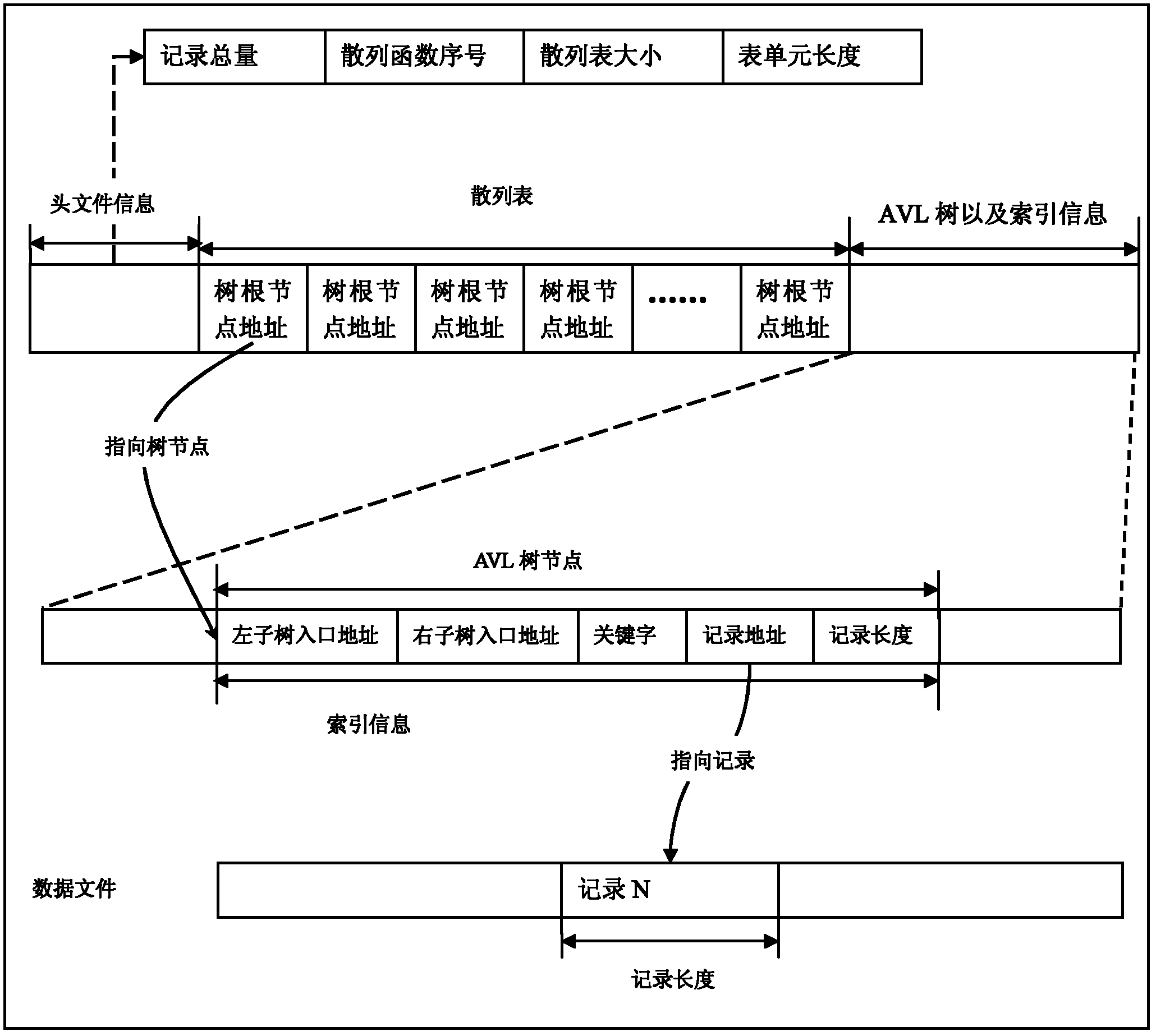
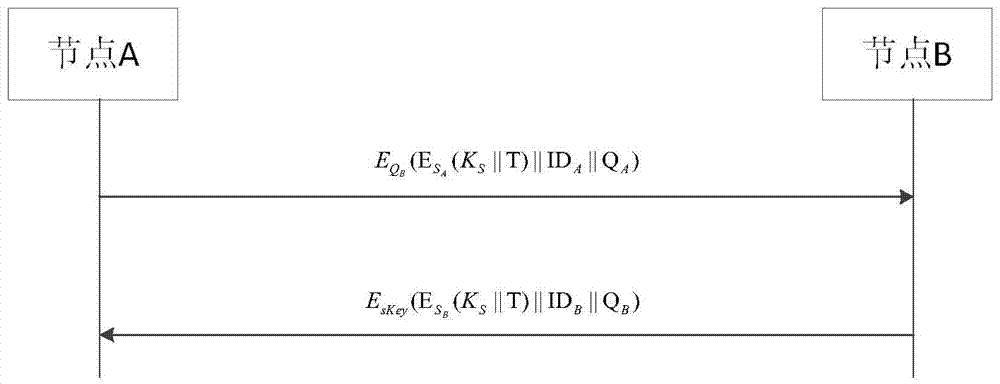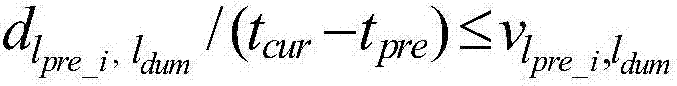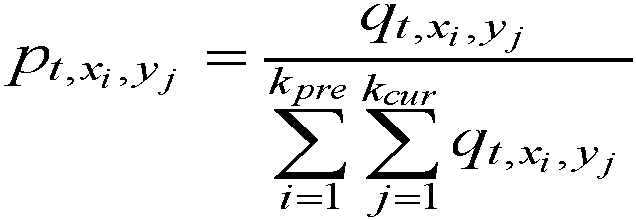Patents
Literature
40 results about "AVL tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
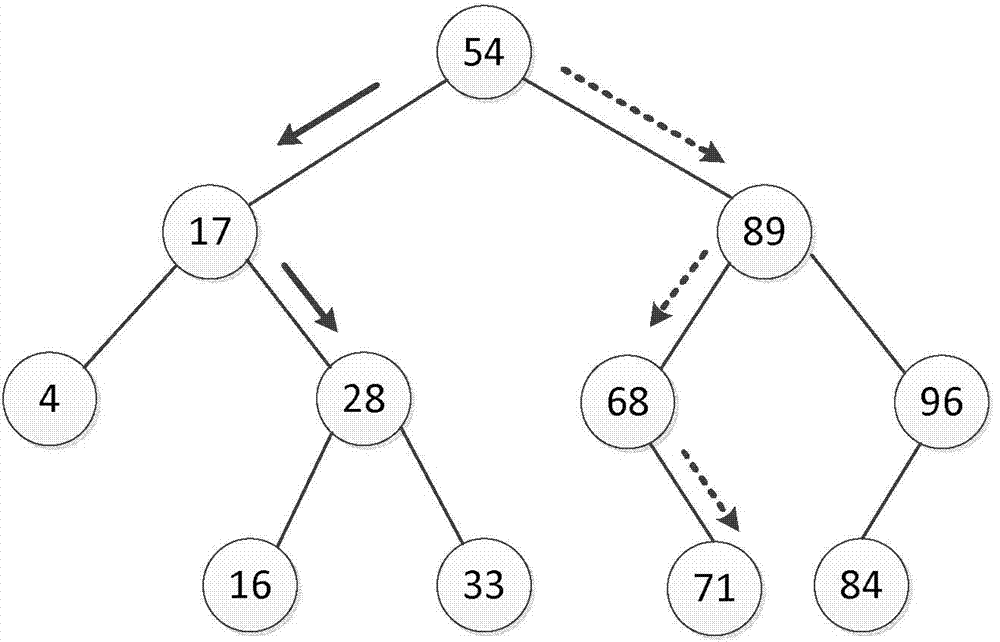
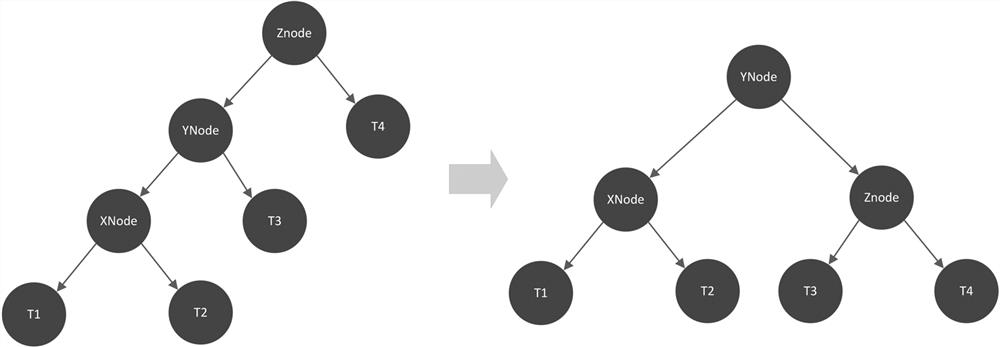
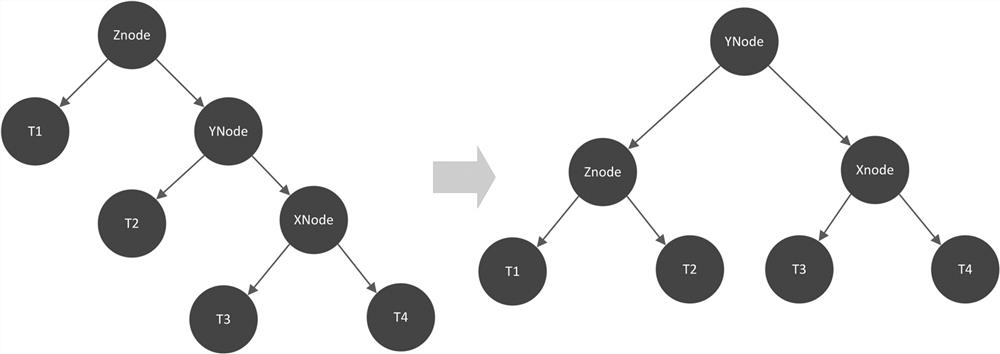
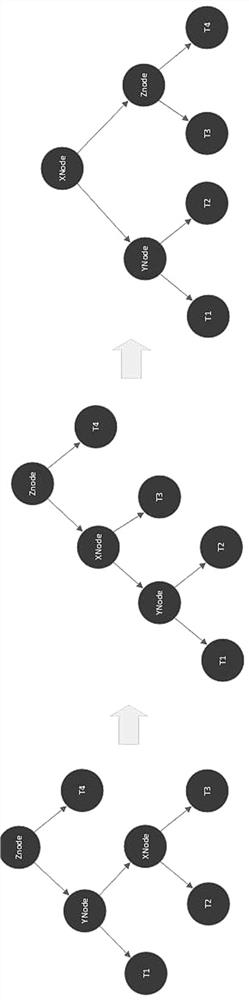
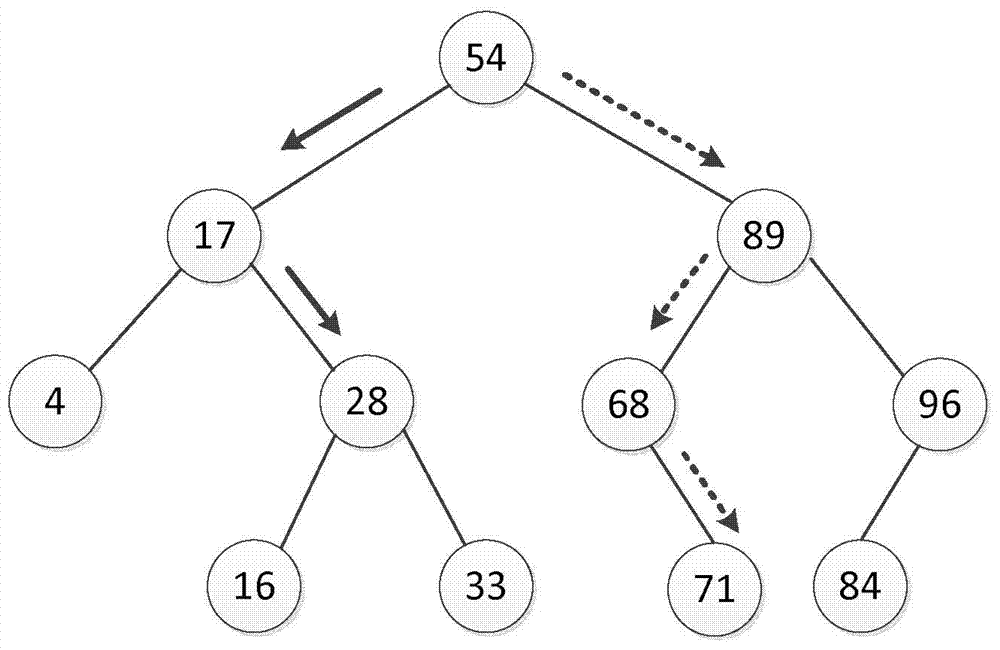
In computer science, an AVL tree (named after inventors Adelson-Velsky and Landis) is a self-balancing binary search tree. It was the first such data structure to be invented. In an AVL tree, the heights of the two child subtrees of any node differ by at most one; if at any time they differ by more than one, rebalancing is done to restore this property. Lookup, insertion, and deletion all take O(log n) time in both the average and worst cases, where n is the number of nodes in the tree prior to the operation.
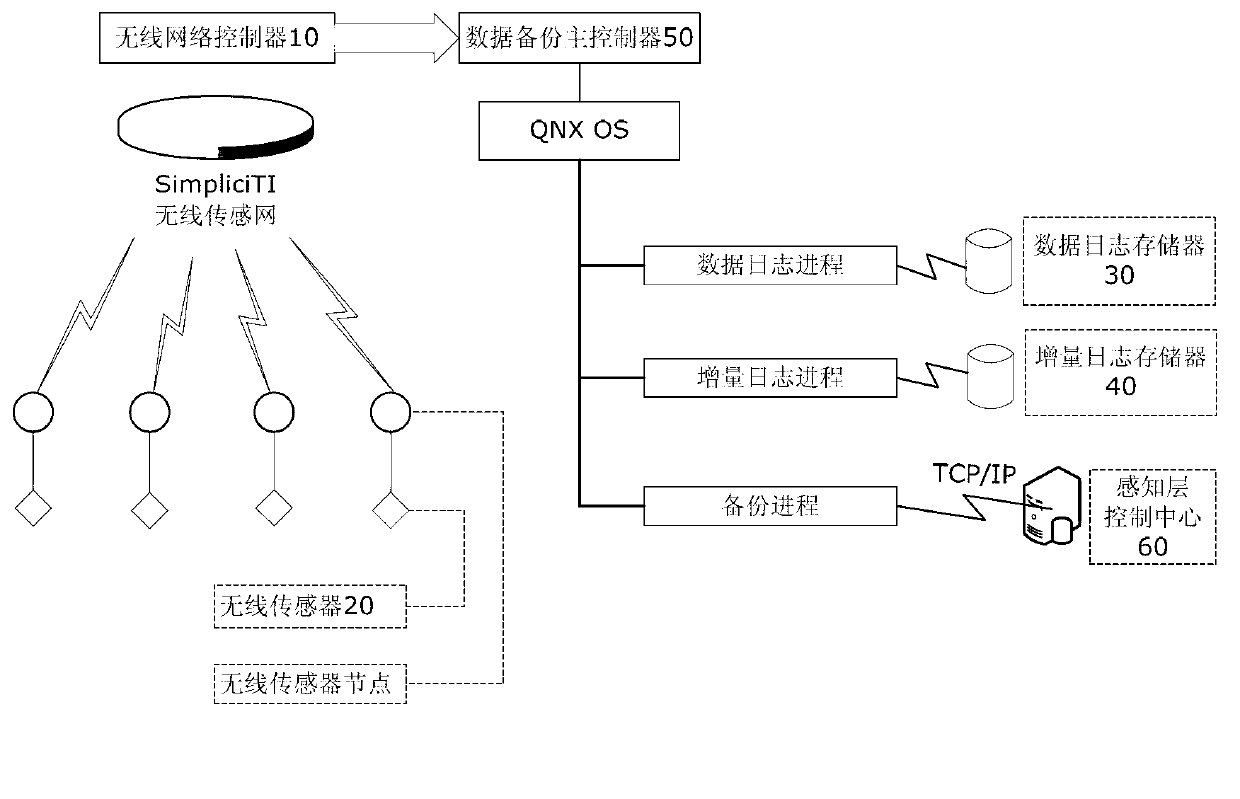
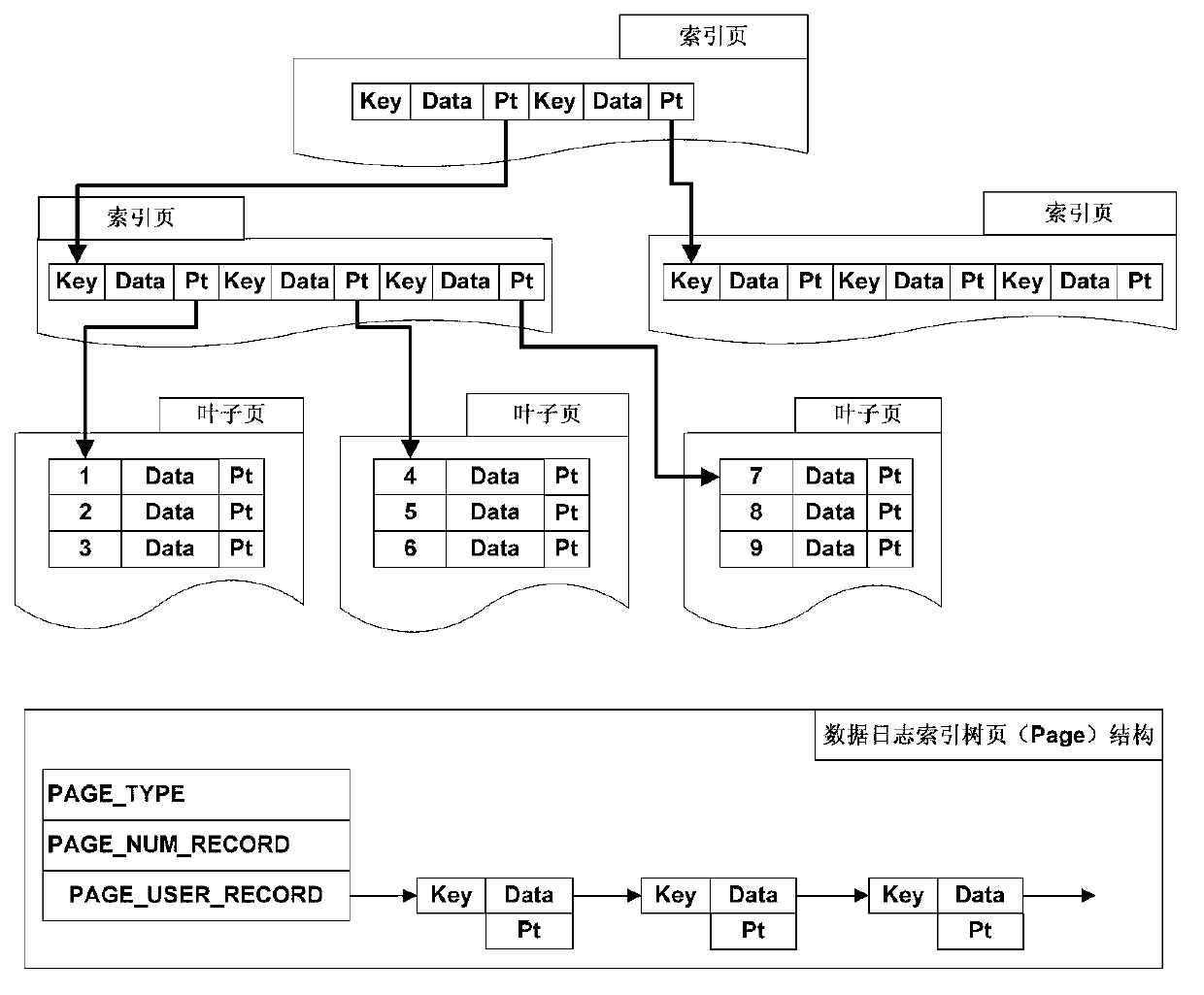
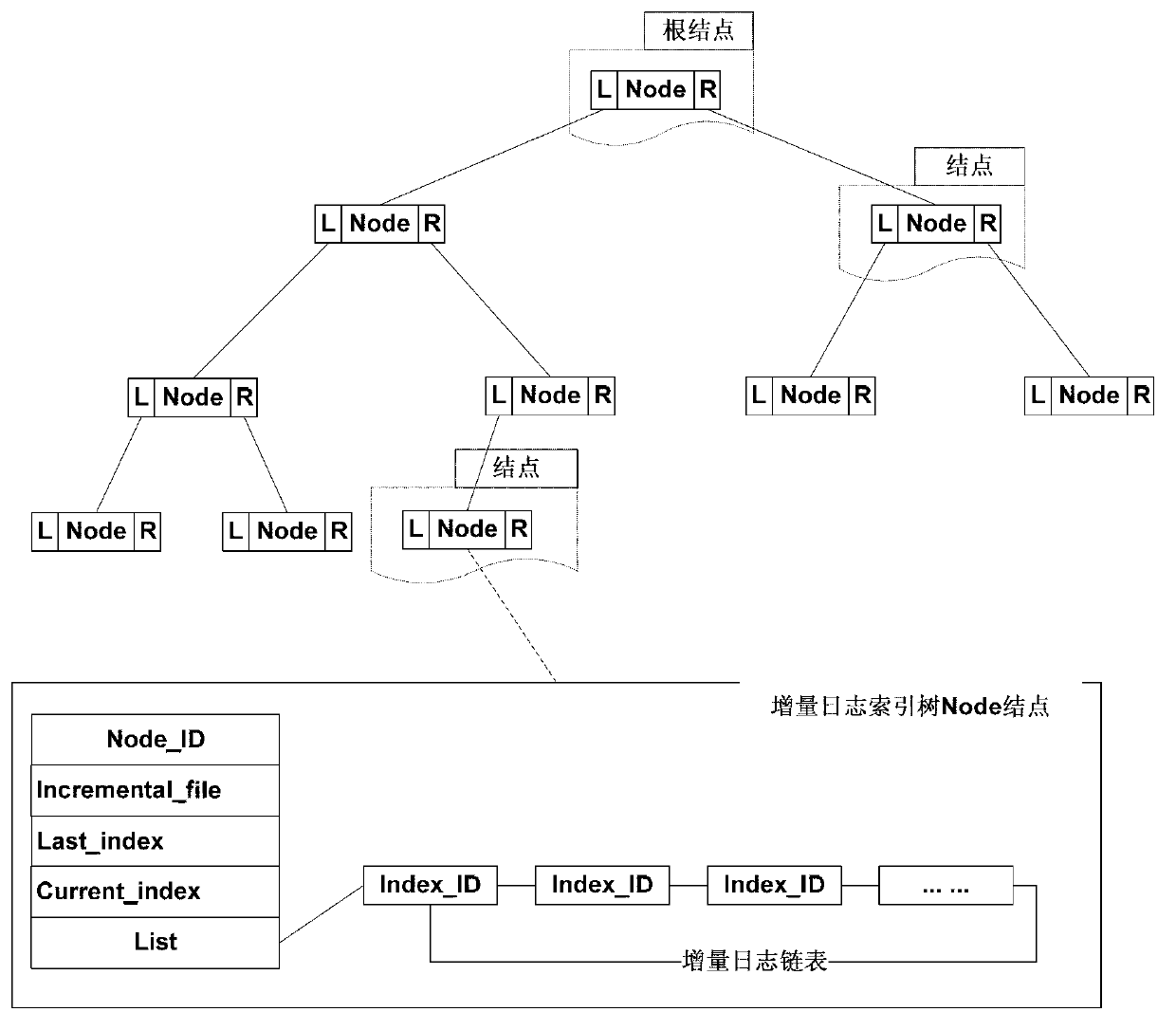
Method and system for data increment backup of sensing layer of Internet of Things
ActiveCN102981933AGuaranteed uptimeAccurate recordData switching networksRedundant operation error correctionNode clusteringThe Internet
The invention discloses a method and a system for data increment backup of a sensing layer of the Internet of Things. The method comprises the following steps of: distributing a unique node clustered index Node_ID to every sensor, and automatically distributing a unique data clustered index Index_ID during detection data generation of every sensor; searching an incremental log index tree with the node clustered index Node_ID as a key to obtain a node of the corresponding sensor on the incremental log index tree, and updating according to the comparison results of two groups of recent detection data of every node, wherein an AVL (approve vendor list) structure is adopted by the incremental log index tree; searching a data log index tree with the data clustered index Index_ID as a key to obtain a node of the corresponding sensor on the data log index tree, and writing detection data into a data log file, wherein a B plus structure is adopted by the data log index tree. Online backup can be performed during operation, continuous operation of the Internet of Things can be ensured, and the speed of inquiry of data increments can be improved greatly.
Owner:WUHAN POST & TELECOMM RES INST CO LTD
Data storage and query method based on classification characteristics and balanced binary tree
InactiveCN102521334AReduce complexityEasy to implementEnergy efficient computingSpecial data processing applicationsTheoretical computer scienceThe Internet
The invention discloses a data storage and query method based on classification characteristics and balanced binary tree. The method comprises the following steps: constructing a balanced binary tree to create nodes; dynamically classifying and storing data information in corresponding nodes according to the sequence of inorder traversal, preorder traversal and postorder traversal; and inputting an enquired content, dynamically traversing the AVL tree to obtain the desired data information. The method provided by the invention can lower the time complexity of dynamic query to static query level, thereby greatly improving storage and query efficiency. The method has the advantages of high speed, low energy consumption, less memory usage, and simple algorithm, and can be implemented by a plurality of languages. The method is widely suitable for data management in the communication field, in particular to massive data storage and query in communication of the internet of things.
Owner:GUANGDONG UNIV OF TECH
Searching and storing method for embedded database
InactiveCN102629269AIncrease profitImprove retrieval efficiencySpecial data processing applicationsLimited resourcesEmbedded database
The invention discloses a searching and storing method for an embedded database. When an embedded system is under an off-line mode, the method comprises the following steps: external high-speed equipment is used for data organization and storage, a data file is set up and the recording is kept, an index file is kept, index information is kept in an AVL tree node, and finally, a database file is downloaded to embedded equipment for use. When the embedded system is under the off-line mode, the method comprises the following steps: searching AVL tree in the index file through keywords, obtaining the index information, so as to obtain the recording of the date file, or insert newly built tree node into an AVL tree, and keep the index information and the recording. The method provided by the invention fully uses optimization process of the external high-speed equipment according to the characteristics of the resource of date and uses the technologies such as a hash table and AVL three for data organization and storage, and the method provided by the invention has the benefits of less resource consumption and high searching efficiency, and can be used in embedded systems with limited resources.
Owner:SHENZHEN MINDE ELECTRONICS TECH
Method for updating distributed cipher key based on AVL tree
ActiveCN101257382AReduce consumptionLow number of stored keysSpecial service provision for substationKey distribution for secure communicationTheoretical computer scienceOne-way function
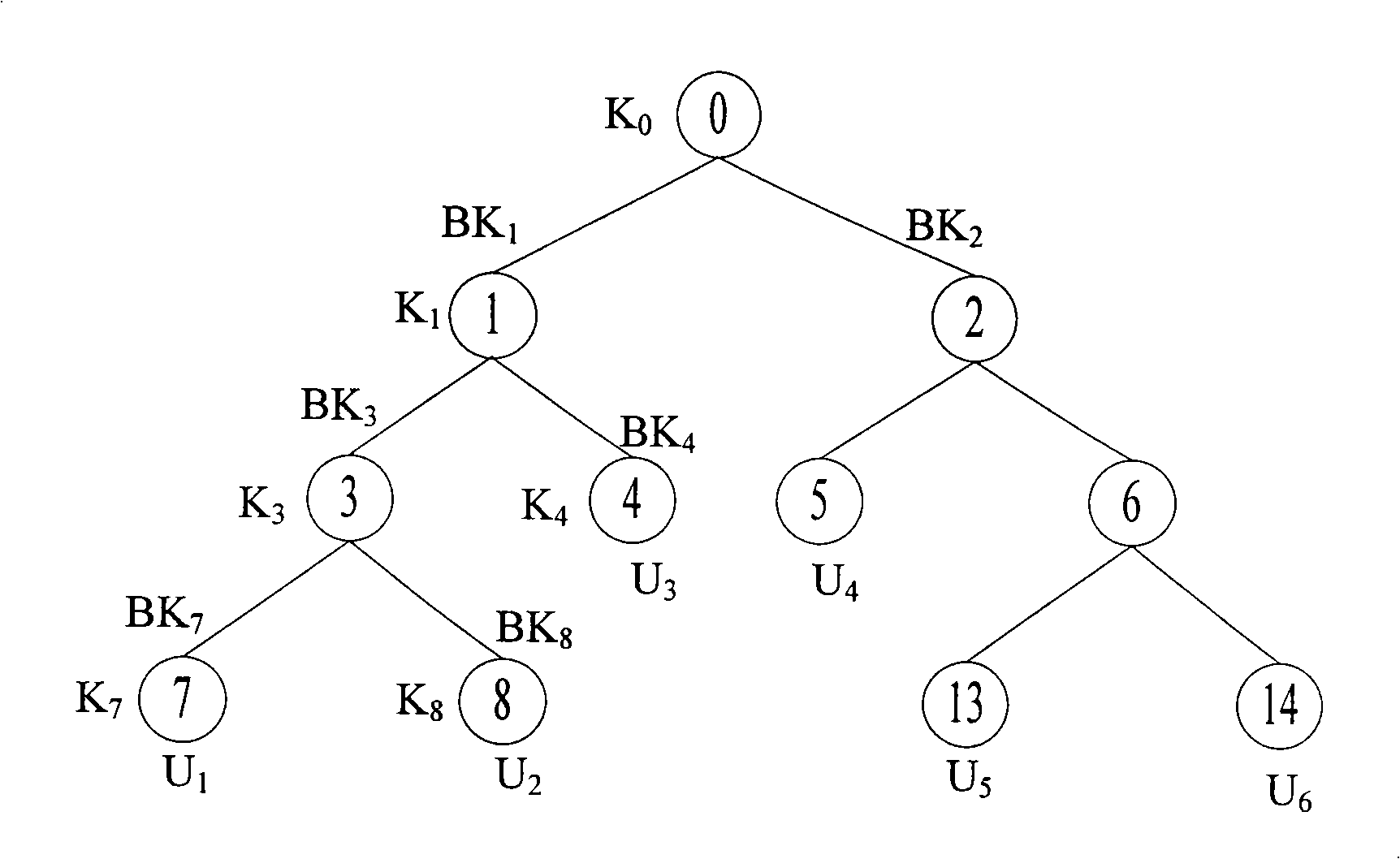
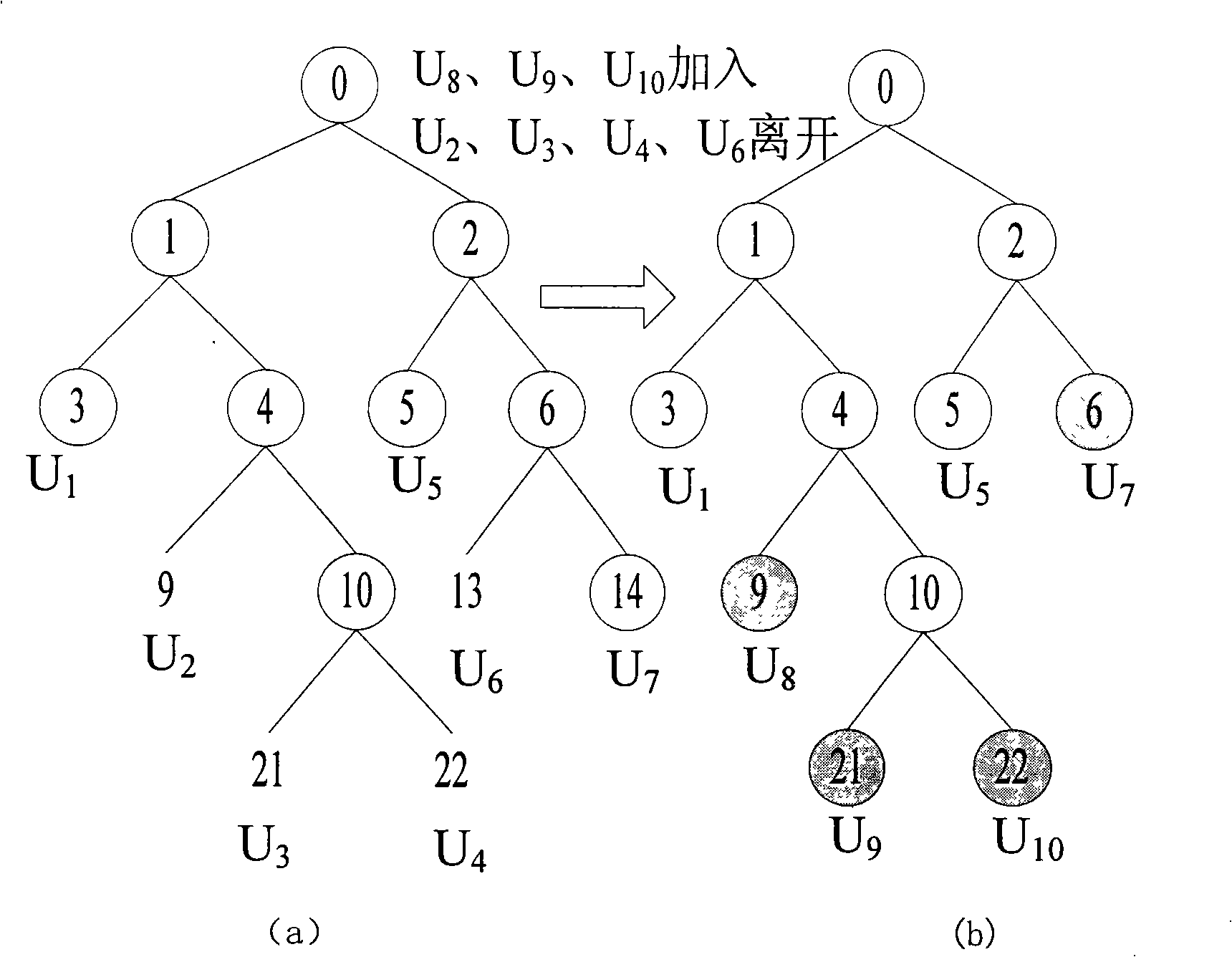
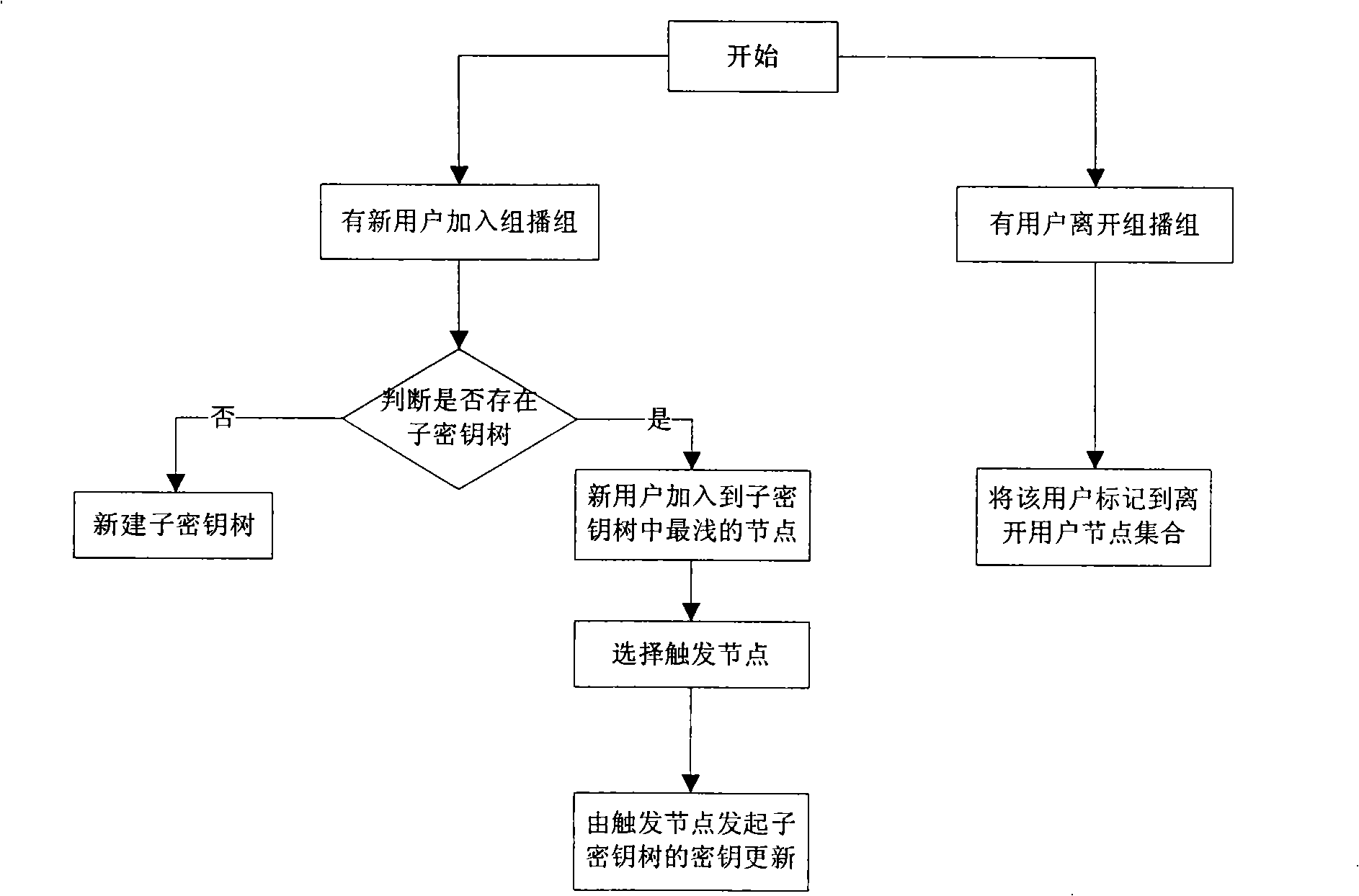
The invention relates to a distributed group key updating method based on the AVL tree, belonging to the computer network security field. The method comprises: subkey tree forming step, subkey tree combining step, AVL rotating step; if newly formed key tree is loss of balance, rotating the new key tree in the AVL mode until recovering the balance; selecting the leaf nodes at the far left of the subtree whose all of the leaf nodes are newly jointed nodes of the new key tree as the triggering node; initiating the key updating process of the whole key tree. The invention effectively solves key tree unbalance problem in the key management plan completely based on the one-way function tree due to the perfect balance ability of AVL tree and reduces the storage spending of the users.
Owner:TSINGHUA UNIV
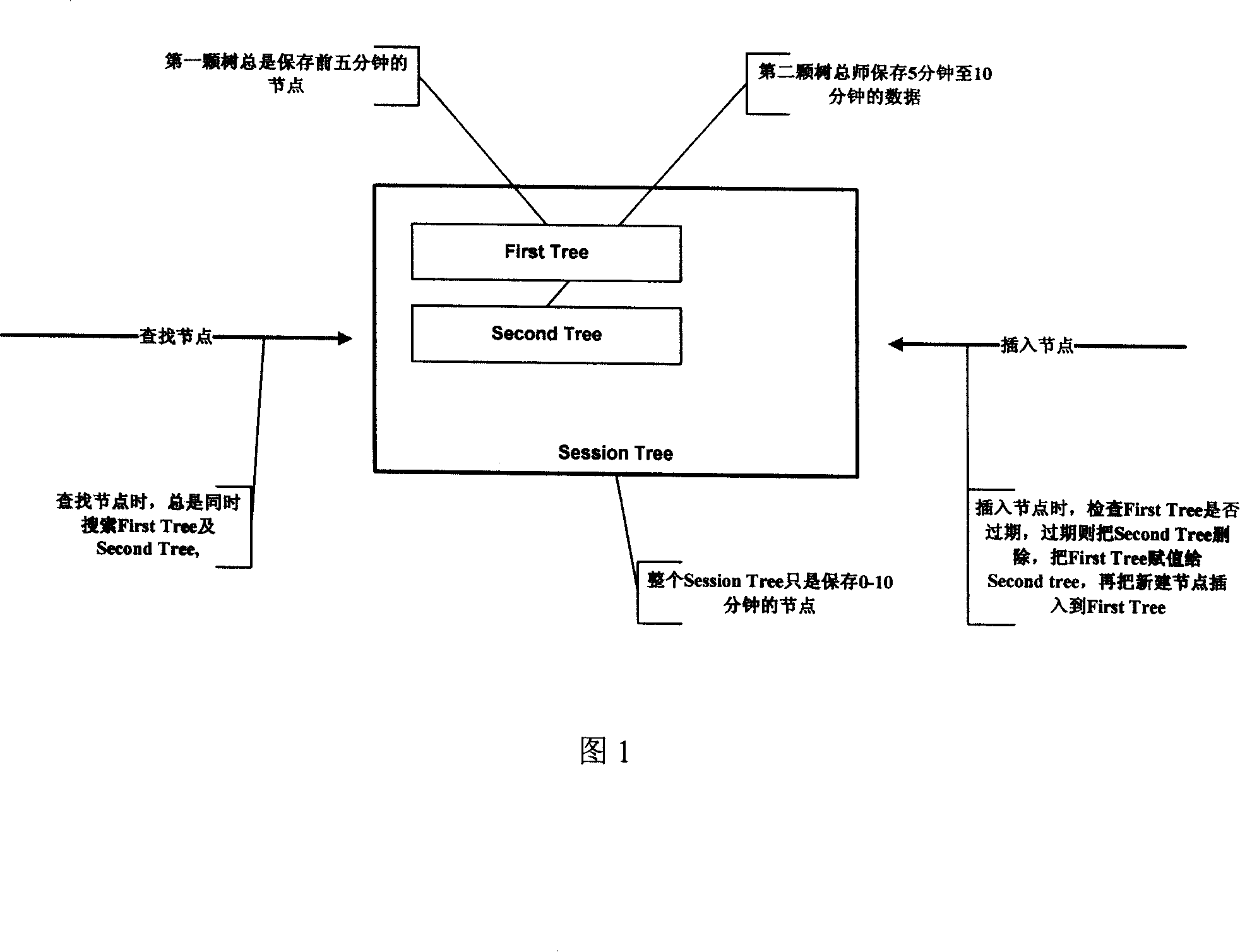
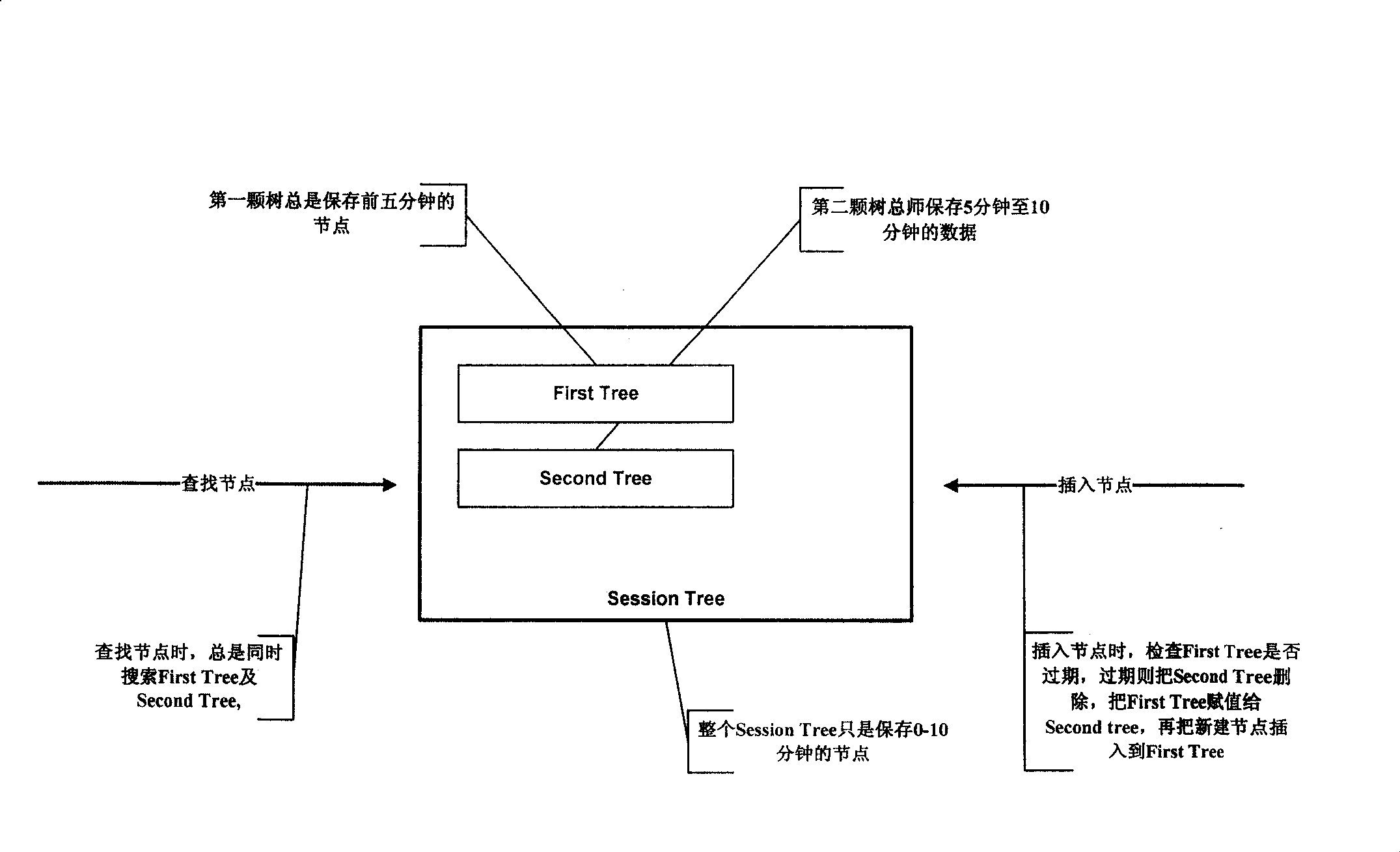
Session cache method based on binary balance tree
ActiveCN101089810ASave memorySpecial data processing applicationsSpecific program execution arrangementsTheoretical computer scienceBinary tree
A Session Cache method based on binary balance tree includes using front tree to store all nodes generated at former time slot and using back tree to store all nodes generated at later time slot, judging whether all nodes stored on said tree are expired or not by comparing ratio of said nodes setting-up time to their current time when node is searched and deleting off node stored on the tree if node stored on the tree is expired.
Owner:苏州海加网络科技股份有限公司
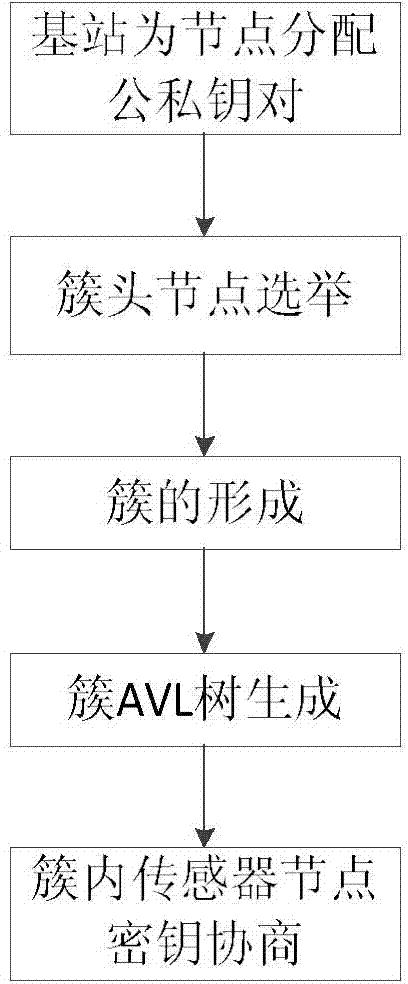
Wireless sensor network key management method
ActiveCN103929744AImprove securityAllow to addNetwork topologiesSecurity arrangementPasswordWireless sensor networking
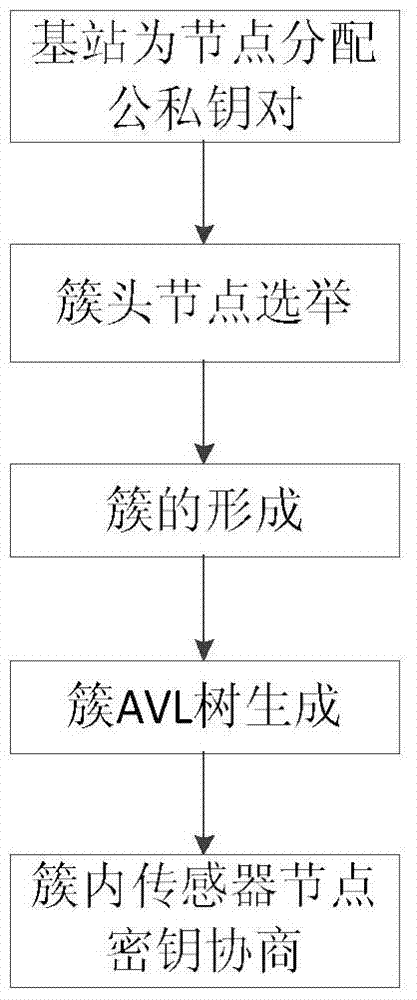
The invention discloses a wireless sensor network key management method. The method comprises the steps that a base station distributes public and private key pairs to all sensor nodes according to set parameters, cluster head nodes are elected from all the sensor nodes, the elected cluster head nodes send information to the surrounding sensor nodes, the surrounding sensor nodes select the cluster head nodes of their own according to the information so that clusters can be formed, the base station generates a self-balancing binary search tree (AVL tree) of the in-cluster sensor nodes for all the clusters to generate the in-cluster sensor nodes, and the in-cluster sensor nodes inquire the information of the other sensor nodes according to the AVL tree, exchange information, mutually authenticate the legality of the public keys, and share the session keys after the authenticating is successful. According to the method, the AVL tree mode is utilized for storing the public keys and the identity information, the searching time is shortened, and the consumption is reduced; an elliptical curve password system is utilized for achieving key distribution and management, the higher safety of the network can be ensured, and the calculation expenditure can be reduced to the greatest extent.
Owner:SOUTHEAST UNIV
Mass toll-ticket fast cross rearrangement based on memory
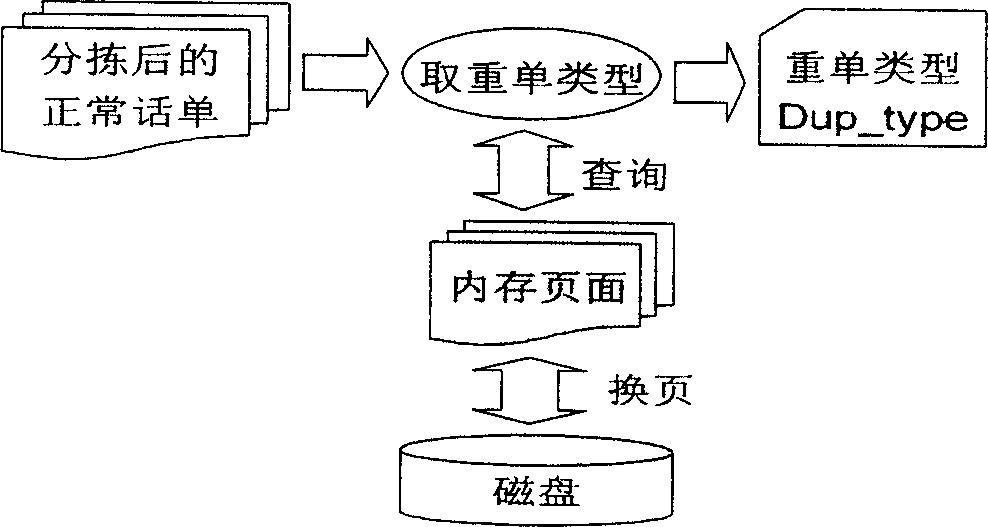
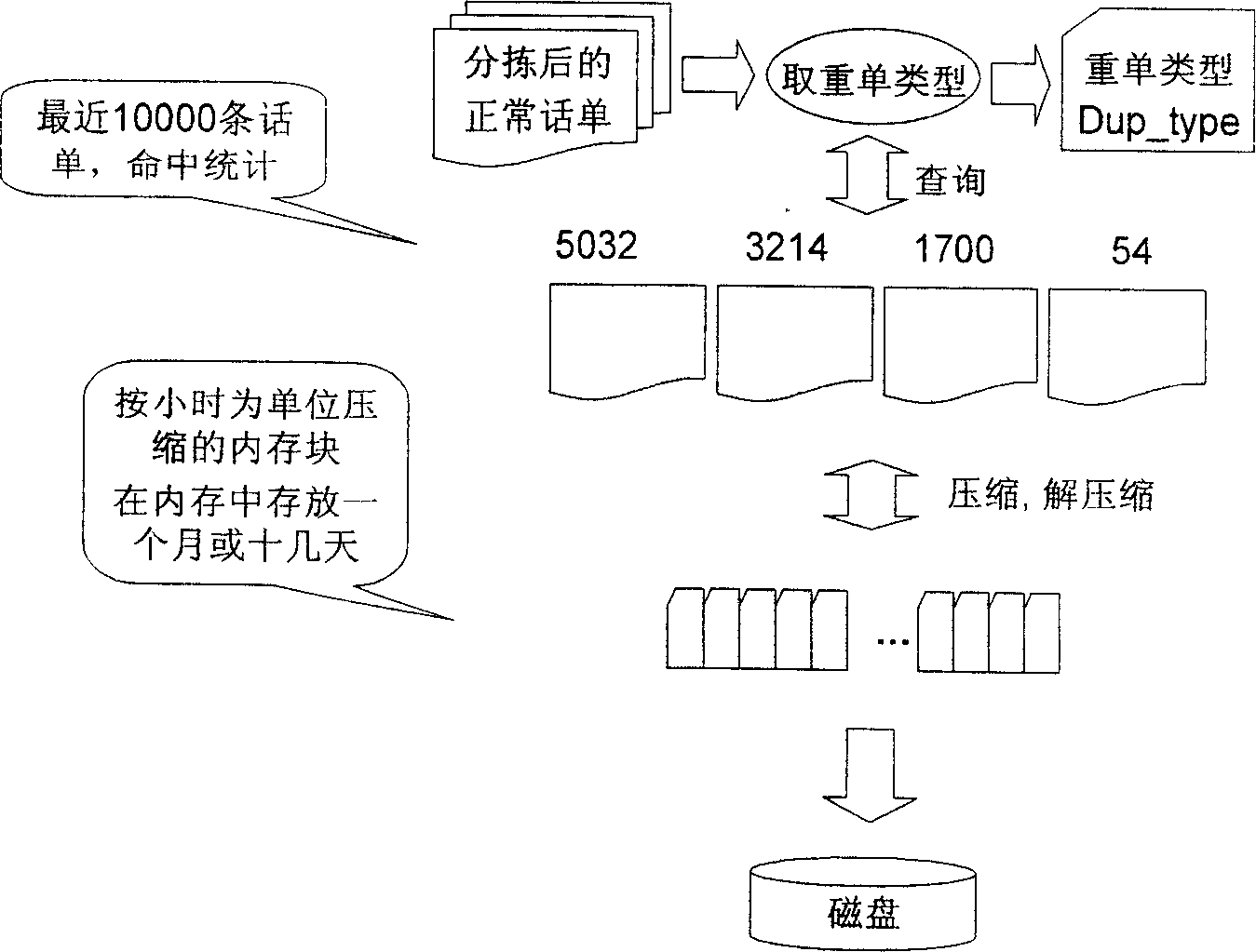
ActiveCN1897629AEfficient methodEfficient designTelephonic communicationSelection arrangementsAVL treeTheoretical computer science
The invention uses the memory multi level storage mechanism, the index technique of the digital search tree based on the binary balance tree (AVL tree)and the process of combining the compression technique based on the BCD code and the RLC(Run-Length Coding) algorithm with the cross and rearrange approach based on the time slice. Said multi level storage mechanism uses three -levels storage mechanism comprising a first level used as the widow of working set, a second level used as the compression and rearrange information and a third level used as the storage disc; the exchange between the first level and the second level is for encoding and decoding, and the data saving in first and second level is implemented using memory mapping approach; the index approach of the digital search tree based on the binary balance tree (AVL tree) is used for the cross and rearrangement.
Owner:LINKAGE SYST INTEGRATION
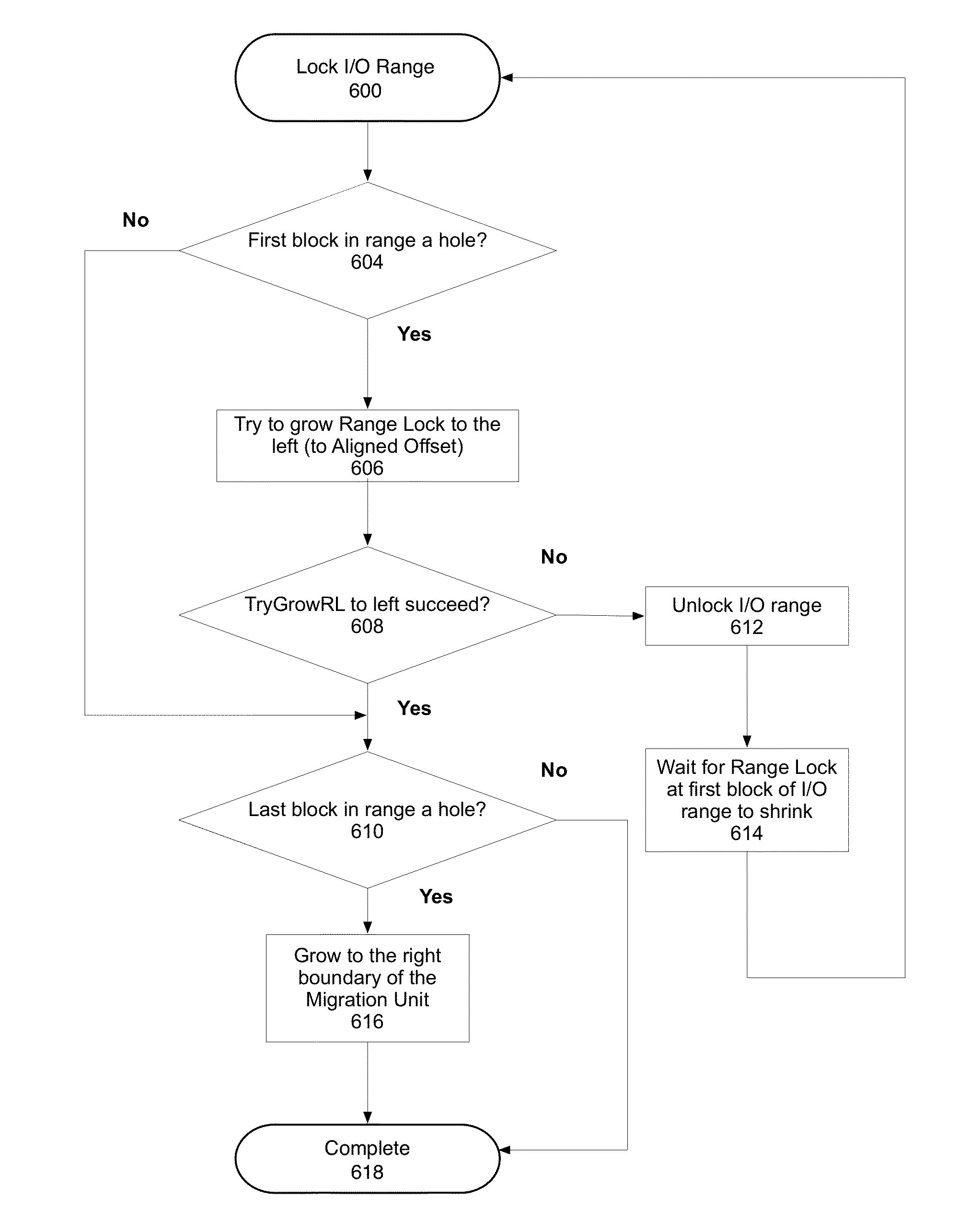
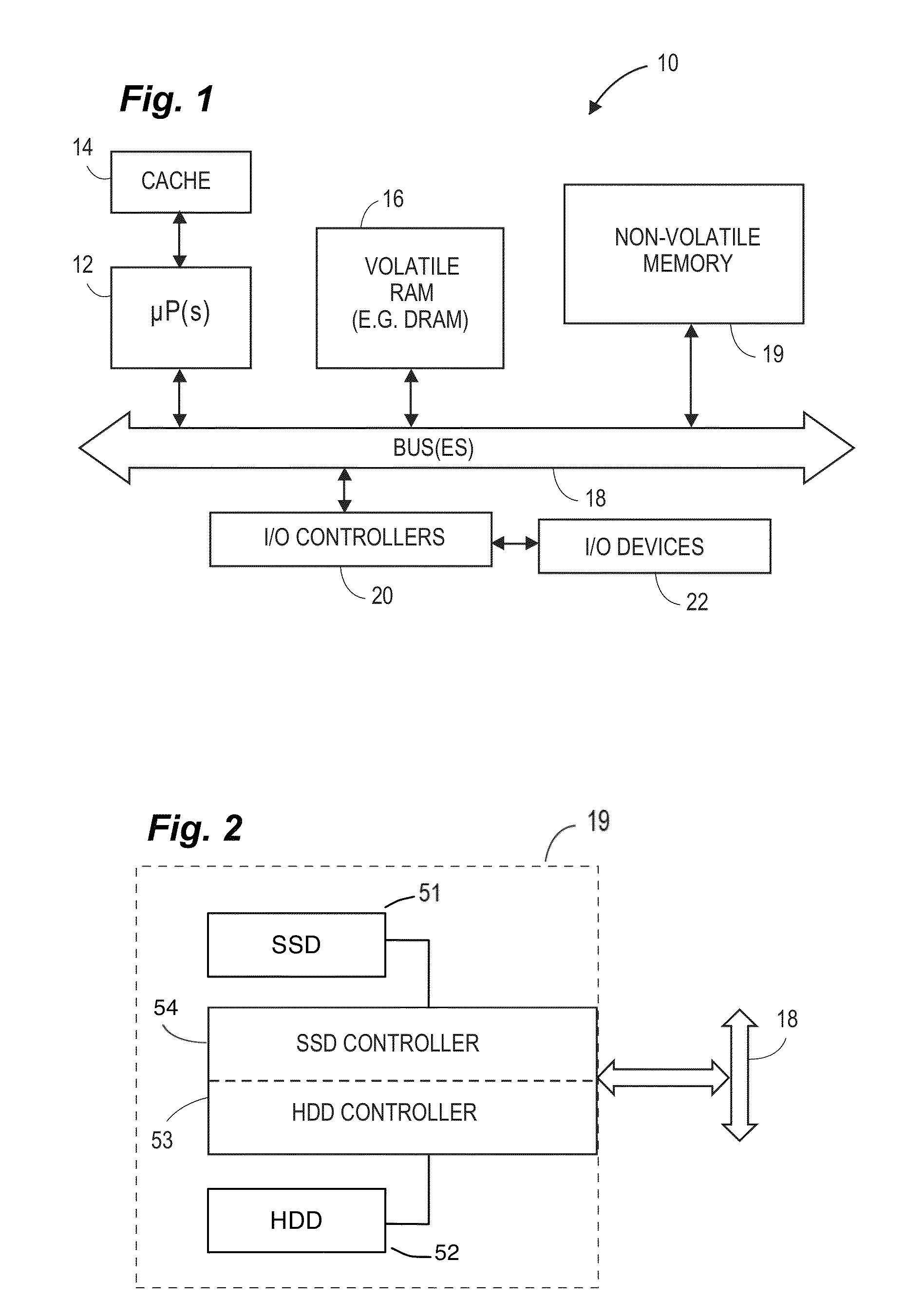
Methods and systems for maintaining a storage volume with holes and filling holes
ActiveUS20130219139A1Improve the level ofMemory loss protectionUnauthorized memory use protectionHard disc driveTheoretical computer science
In one embodiment, a method for managing access to a fast non-volatile storage device, such as a solid state device, and a slower non-volatile storage device, such as a magnetic hard drive, can include a method of managing a sparse logical volume in which unmapped blocks of the logical volume are not allocated until use. In one embodiment, a method of sparse hole filling operates in which range locks are dynamically adjusted to perform allocations for sparse hole filling, and then re-adjusted to perform standard operations using a byte range lock. In one embodiment, a high level data structure can be used in the range lock service in the form of an ordered search tree, which could use any search tree algorithm, such as red-black tree, AVL tree, splay tree, etc.
Owner:APPLE INC
Validity detection method of memory block
ActiveCN102789407AEfficient detectionShorten the timeDetecting faulty computer hardwareMemory adressing/allocation/relocationArray data structurePoor memory
The invention provides a validity detection method of a memory block, which mainly comprises the following steps of: obtaining a start address and an end address of a memory pool in a memory management system; retrieving AVL (Automatic Vehicle Location) trees of free memory blocks in the memory management system, collecting the information of all the free memory blocks, storing in an array manner and sequencing according to the addresses of the memory blocks from low to high; judging whether a free block exists, detecting the validity of the current free block if the free block exists and finishing detection if the free block does not exist; and taking the memory block as a poor block if the memory block can not pass the validity test, prompting the position and the detailed information of the poor block and obtaining the circle detection of a next free block. The memory block validity detection method has the beneficial effects that on the basis that the existing organization structure of the memory block is not expanded, and any mark consumption additional memory is not required to be increased, the poor memory block existing in the memory management system can be effectively detected, and the position and the information of the poor block are prompted to facilitate a developer to position the existing reason of the poor block.
Owner:PHICOMM (SHANGHAI) CO LTD
File access method
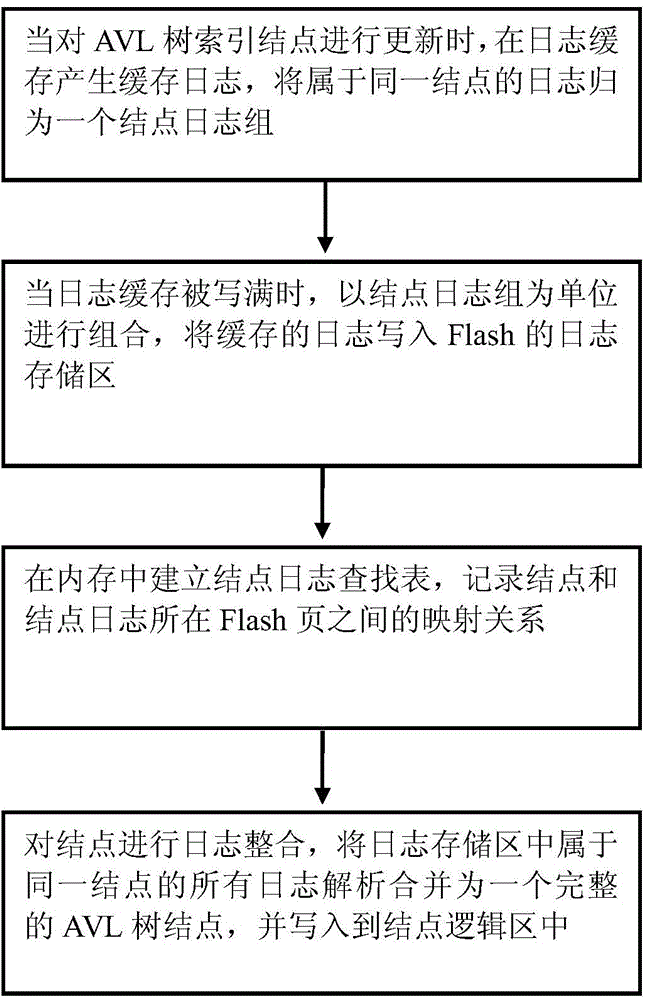
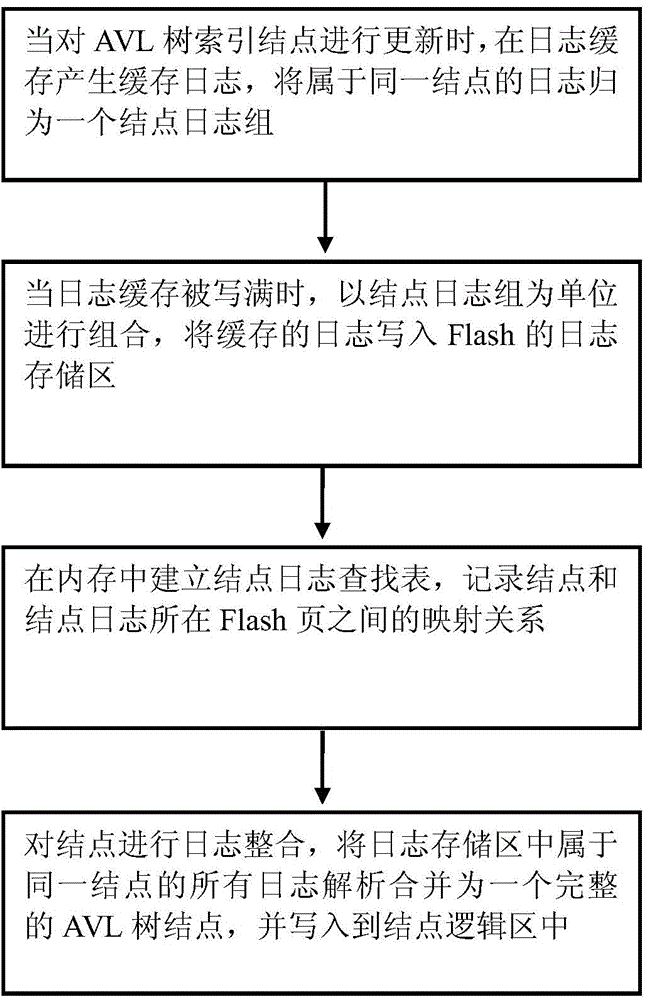
InactiveCN104156432AGuaranteed retrieval performanceGuaranteed update efficiencyMemory adressing/allocation/relocationFile access structuresAccess methodLookup table
The invention provides a file access method used for carrying out indexing in a Flash database. The method comprises the steps that when AVL tree indexing nodes are upgraded, cached logs are generated in a log cache; when the log cache is fully written, the cached logs are combined with the node log set as an unit and written into a log storage area; a node log lookup table is set up, and the mapping relation between the nodes and a Flash page where the logs are located is recorded; log integration is carried out on the nodes and written into a node logic area. According to the method, the number of times for writing NANA Flash is reduced in the database upgrading process, and the upgrading efficiency of the index is ensured.
Owner:CHENGDU DINGZHIHUI TECH
BitMap high-speed fuzzy search method
ActiveCN110442570ASave logic resourcesIncrease logic processing rateSpecial data processing applicationsDatabase indexingTheoretical computer scienceLookup table
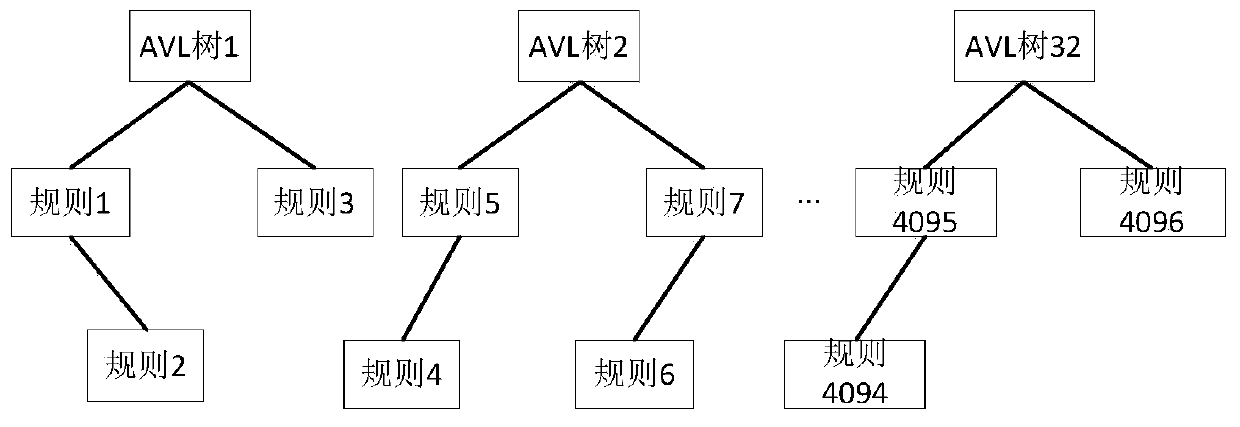
The invention relates to a BitMap high-speed fuzzy search method, which comprises the following steps: establishing and issuing rule table entries by software, namely dividing a required quintuple combination into an AVL tree; each AVL tree storing rule nodes according to the principle that the accurate matching priority is the highest, the higher the fuzzy matching precision being, the higher thepriority being, and linearly arranging the intra-blocks and the inter-blocks according to the priority; carrying out linear arrangement according to priorities, establishing a Bitmap lookup table, and carrying out quintuple information segmentation to establish a lookup index; when the Bitmap is updated, a plurality of combinations needing to be matched according to the mask; generating an indexKey based on the rule table entry information, and then segmenting the index Key into a plurality of sub-Keys; and looking up the quintuple of the IP network message according to the index key. According to the method, the table writing and looking-up mode of a content fuzzy looking-up mode is improved, logic resources are saved, the logic processing rate is increased, meanwhile, multiple instantiation extensions are conducted in a modular mode, resources can be estimated, convenience and rapidness are achieved, and the design risk is reduced.
Owner:BEIJING ZUOJIANG TECH
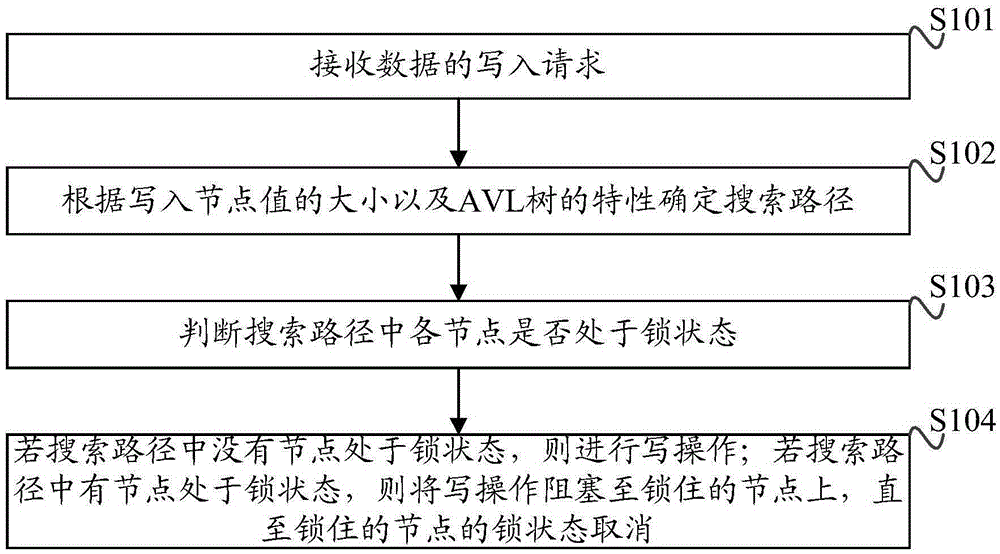
AVL tree-based data writing method and apparatus
InactiveCN105389360AImprove write performanceSpecial data processing applicationsConcurrency controlParallel processing
The present invention discloses an AVL tree-based data writing method and apparatus, which use a read-write lock for performing concurrency control on data writing. The method comprises: receiving a data write request; determining a search path according to sizes of written node value and characteristics of an AVL tree; determining whether each node in the search path is in a lock state, wherein the lock state is that when a first node in a currently concurrent write operation is a root node of a subtree locally adjusted, the first node is set into a locked state; If no node in the search path is in the lock state, performing the write operation; and if a certain node in the search path is in the lock state, blocking the write operation up to the locked node until the lock state of the locked node is canceled. According to the AVL tree-based data writing method and apparatus provided by the present invention, parallel processing is allowed to be performed on the write operation without a conflict in the local of the AVL tree, thereby improving data writing performance.
Owner:INSPUR BEIJING ELECTRONICS INFORMATION IND
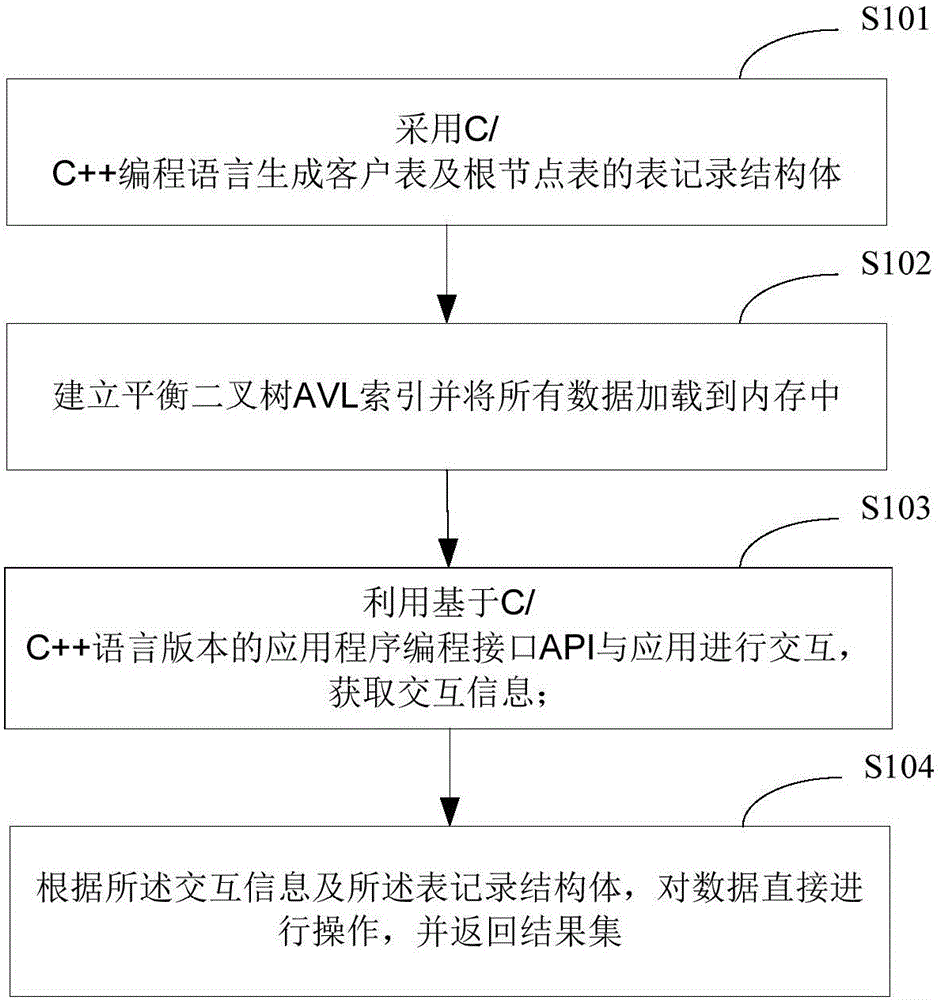
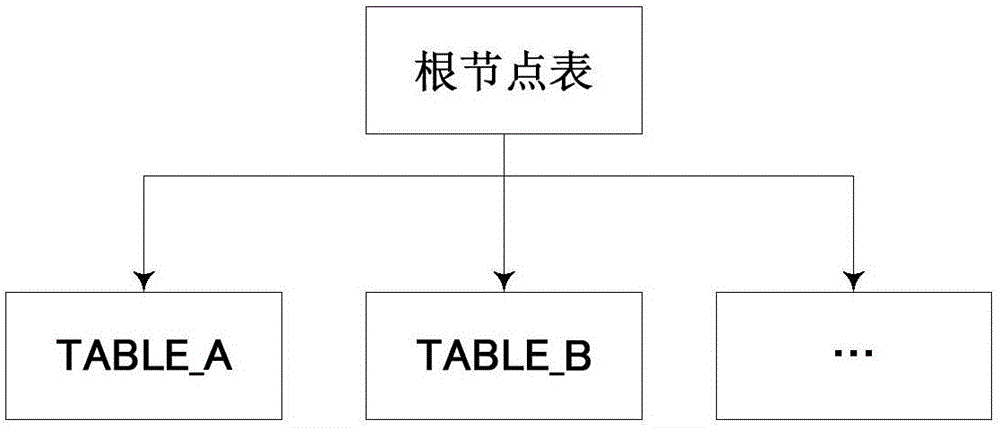
Database implementation method and database
InactiveCN106570056AImprove real-time response performanceImprove processing efficiencySpecial data processing applicationsStructure of Management InformationApplication software
The invention is applied to the technical field of information, and provides a database implementation method and a database. The database implementation method comprises the following steps of: generating table recording structural bodies of a client table and a root node table by adopting C / C++ programming language; establishing a balanced binary tree AVL index, and loading all data in a memory; performing interaction with an application by utilizing an application programming interface API based on the C / C++ language version, so that interaction information is obtained; and, according to the interaction information and the table recording structural bodies, directly operating the data, and returning a result set. In the embodiment of the invention, due to adoption of the C / C++ programming language, the table recording structural bodies are generated and the corresponding API is provided; therefore, when the database receives the interaction information of the development application based on the C / C++ language, the data can be managed without any conversion; the processing efficiency is increased; the AVL tree index is established; therefore, the data query complexity is reduced; because the data processing is completed in the memory, limitation of the I / O speed of the traditional database magnetic disk is broken through; and the real-time response capability of the database system is improved.
Owner:SHENZHEN IBOX INFORMATION TECH CO LTD
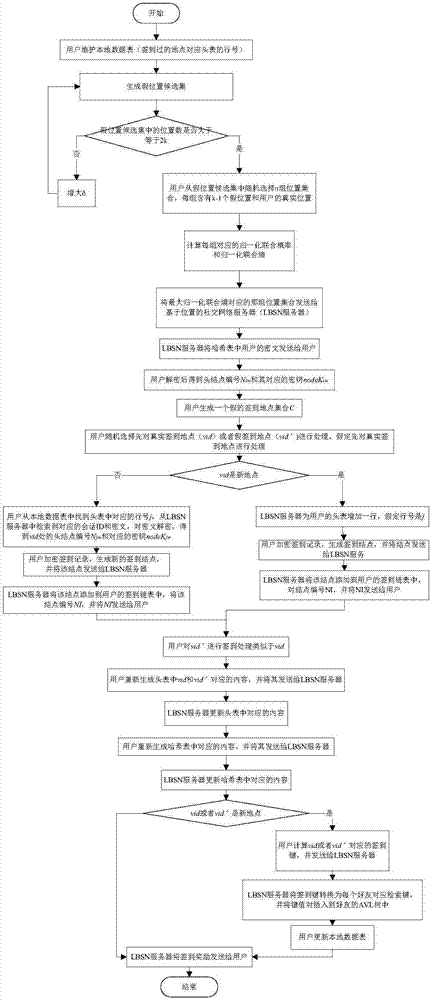
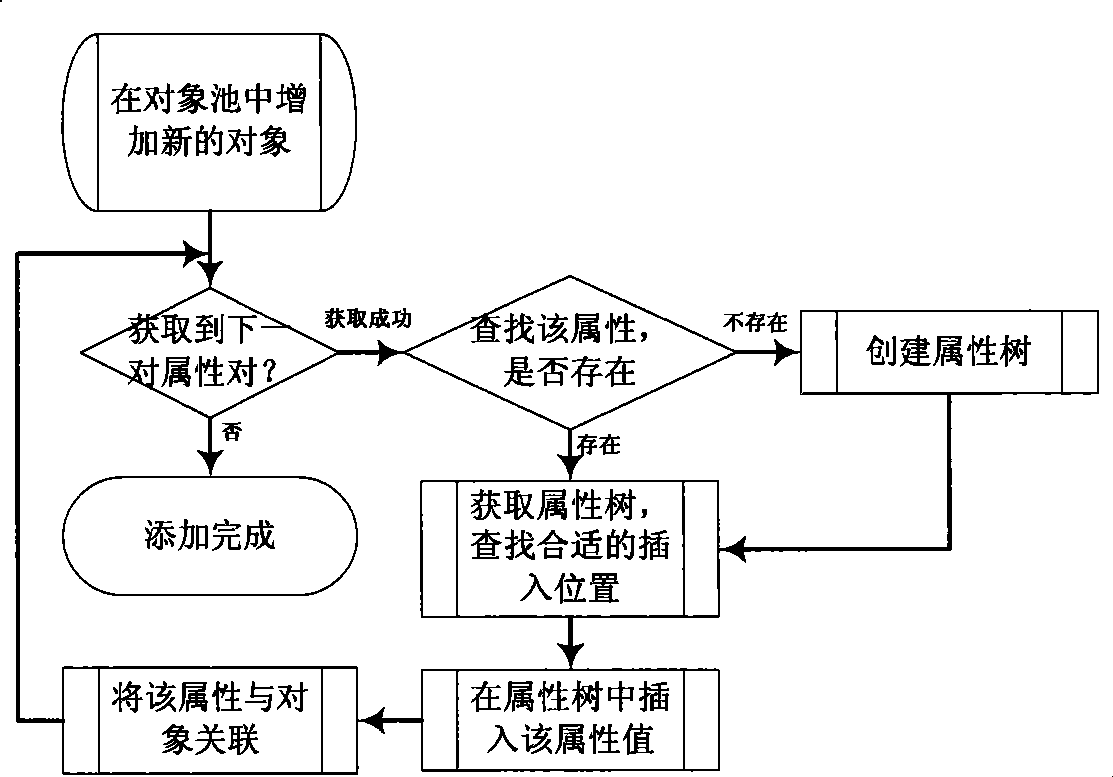
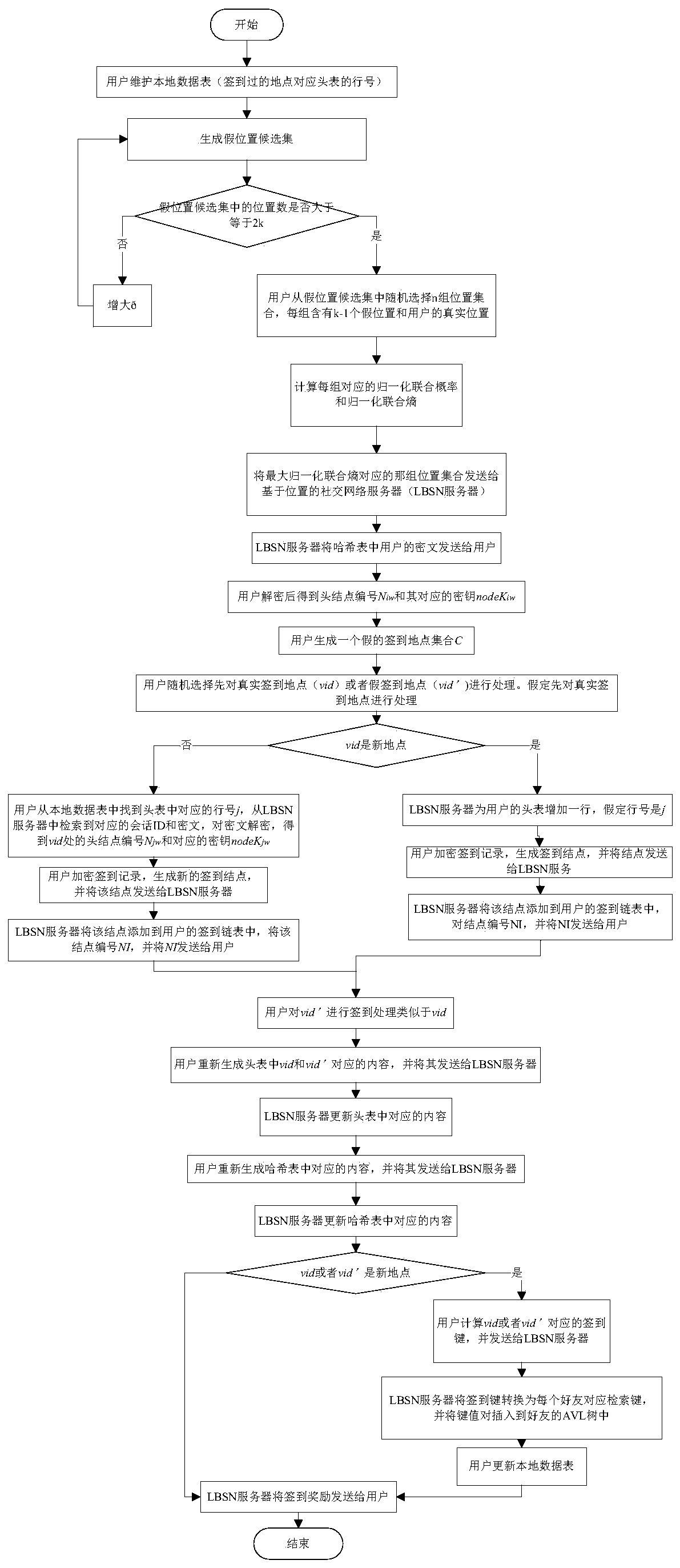
Location privacy protection method in check-in service
ActiveCN106961386ARealize k-anonymityImplement location privacy protectionData switching networksCiphertextPrivacy protection
The invention discloses a location privacy protection method in a check-in service. Check-in records of each user are encrypted and each check-in node is numbered via a location set generated by K-anoymity for achieving the purpose of maintaining a check-in chain for the user and protecting location privacy; meanwhile, the location privacy protection is increased by adding a false check-in node, the true check-in node and the false check-in node are distinguished via a zone bit corresponding to a check-in record ciphertext, and in addition, a header table and a Hash table are maintained for the user, so that node numbers included in the header table and the Hash table are the number of the node that the user checks in latest and a corresponding decryption key; therefore, all the check-in records of friends can be acquired by directly decrypting the ciphertext in the Hash table, meanwhile, all the friends checked in at a specific site and corresponding header table line numbers can be acquired by searching an AVL tree, the check-in records of all the specific sites can be acquired by decrypting the header table, and thus the location privacy protection can also be improved in the case of providing two search modes.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
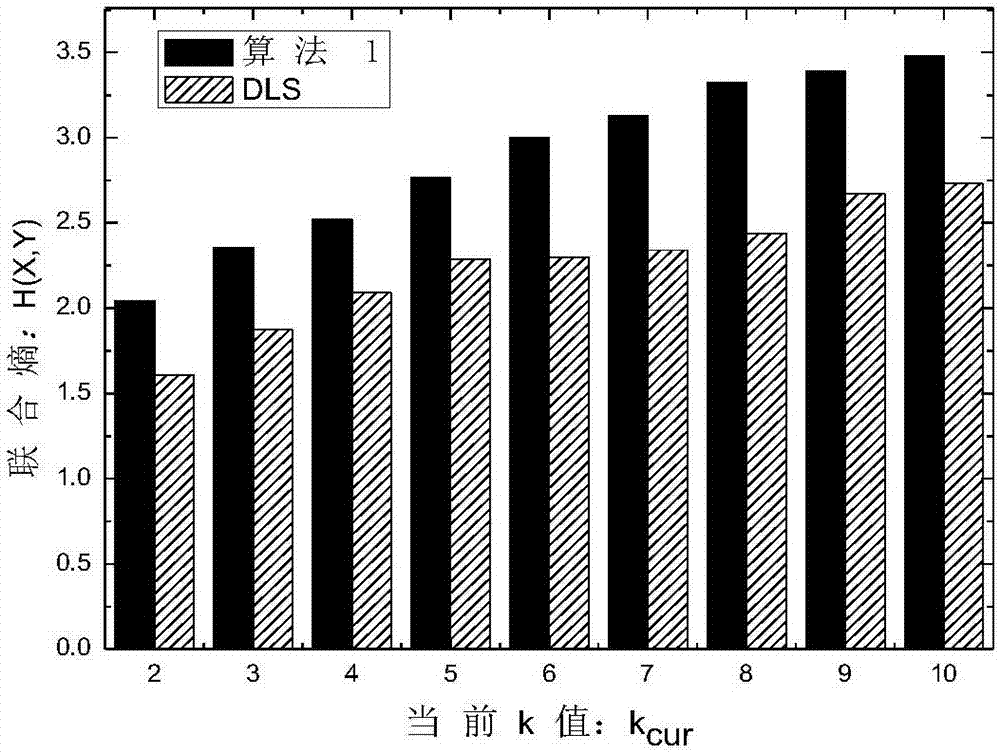
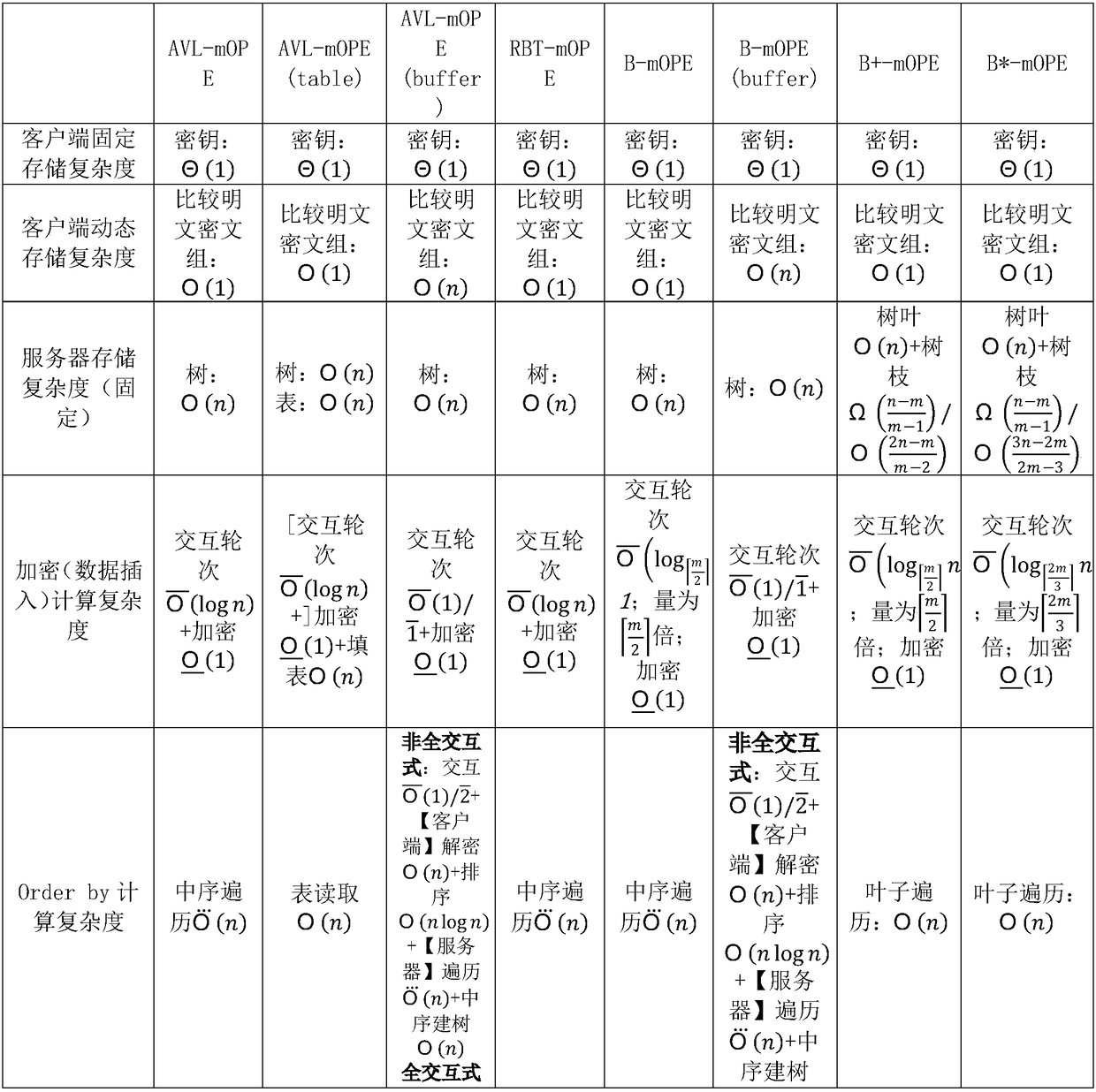
Order-preserving encryption algorithm based on balanced sort tree storage structure
ActiveCN109495446AEncryption apparatus with shift registers/memoriesDigital data protectionSorting algorithmPassword
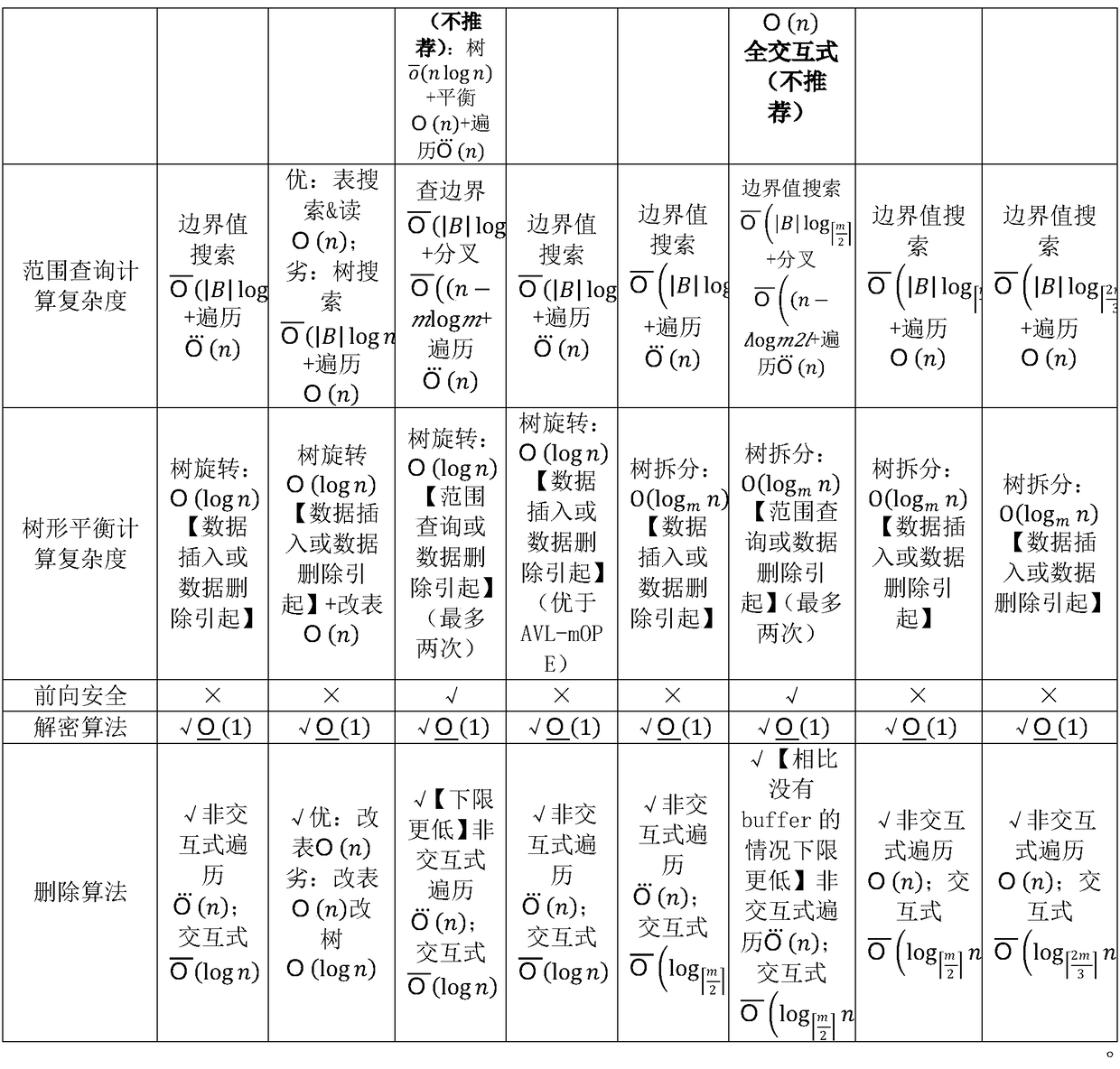
The invention belongs to the technical field of passwords, and specifically relates to an order-preserving encryption algorithm based on a balanced sort tree storage structure. In the order-preservingencryption algorithm, a data storage basic structure comprises an AVL tree, a red-black tree, a B tree, a B+ tree or a B* tree; and different data storage structures have slightly different algorithmexpressions. The algorithm takes an AVL tree structure as an example, and comprises a basic AVL tree-based ideal secure order-preserving encryption algorithm and some improved order-preserving encryption algorithms. Various algorithms are described from a tree structure, an initialization algorithm, an encryption algorithm, a decryption algorithm, an orderby sort algorithm, a range query algorithm, a deletion algorithm, a balancing algorithm and an interactive query algorithm. Compared with most order-preserving encryptions that cannot achieve the ideal secure effect, the algorithm security provided by the invention has absolute advantages, the algorithm provided by the invention also performs all-directional comparison, and the algorithm is suitable for most systems and is especially suitable for a system with relatively high security requirements and sufficient bandwidth configuration.
Owner:FUDAN UNIV
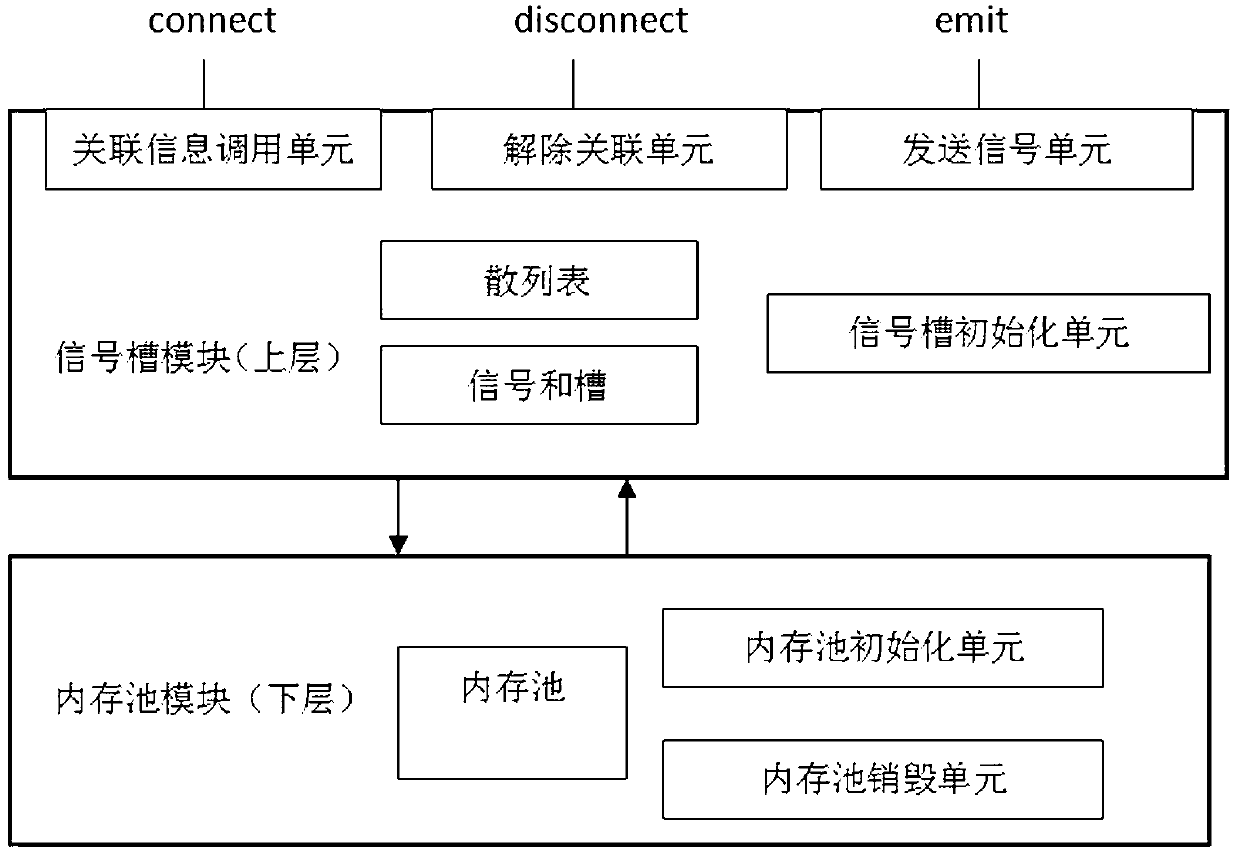
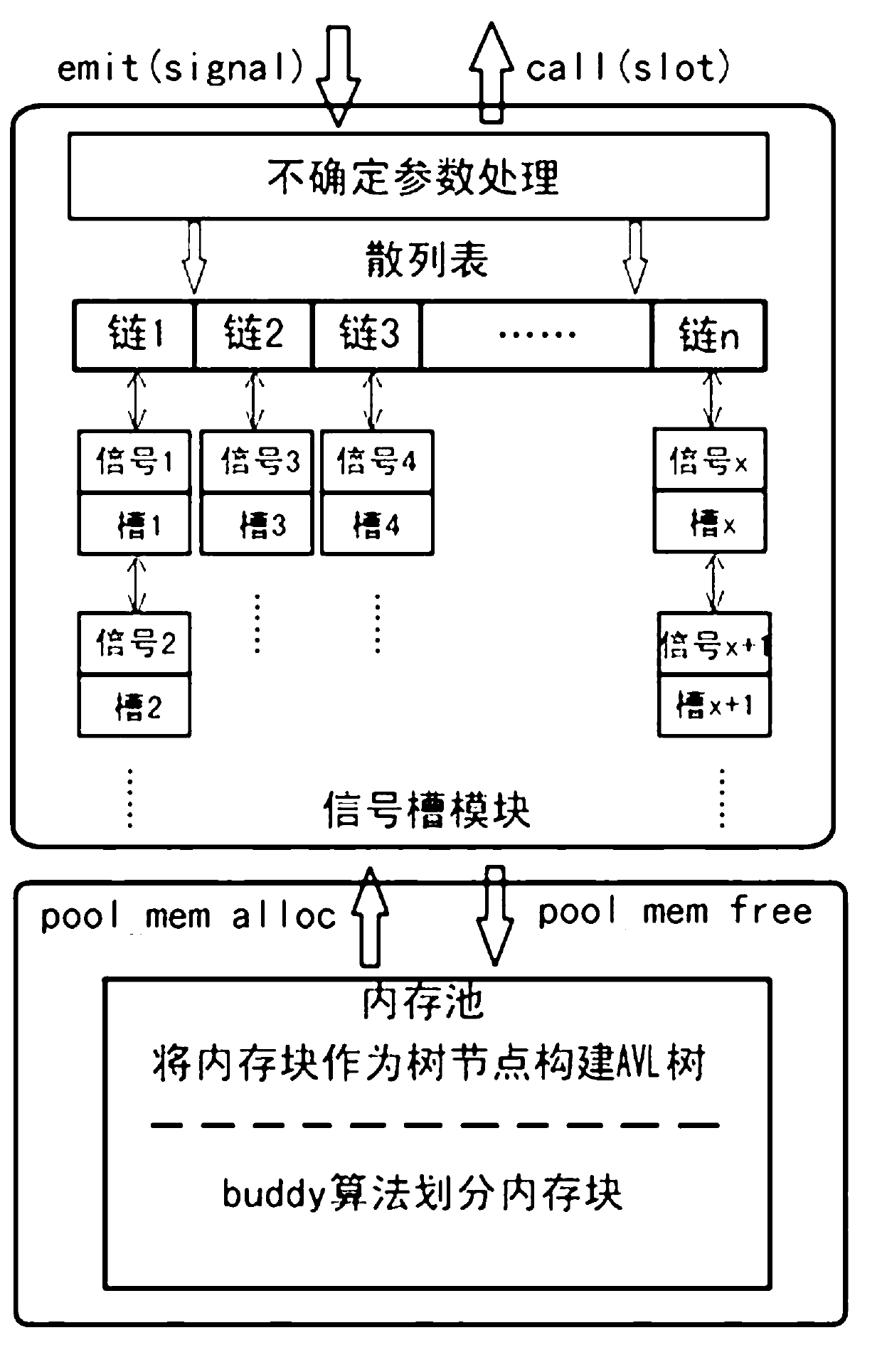
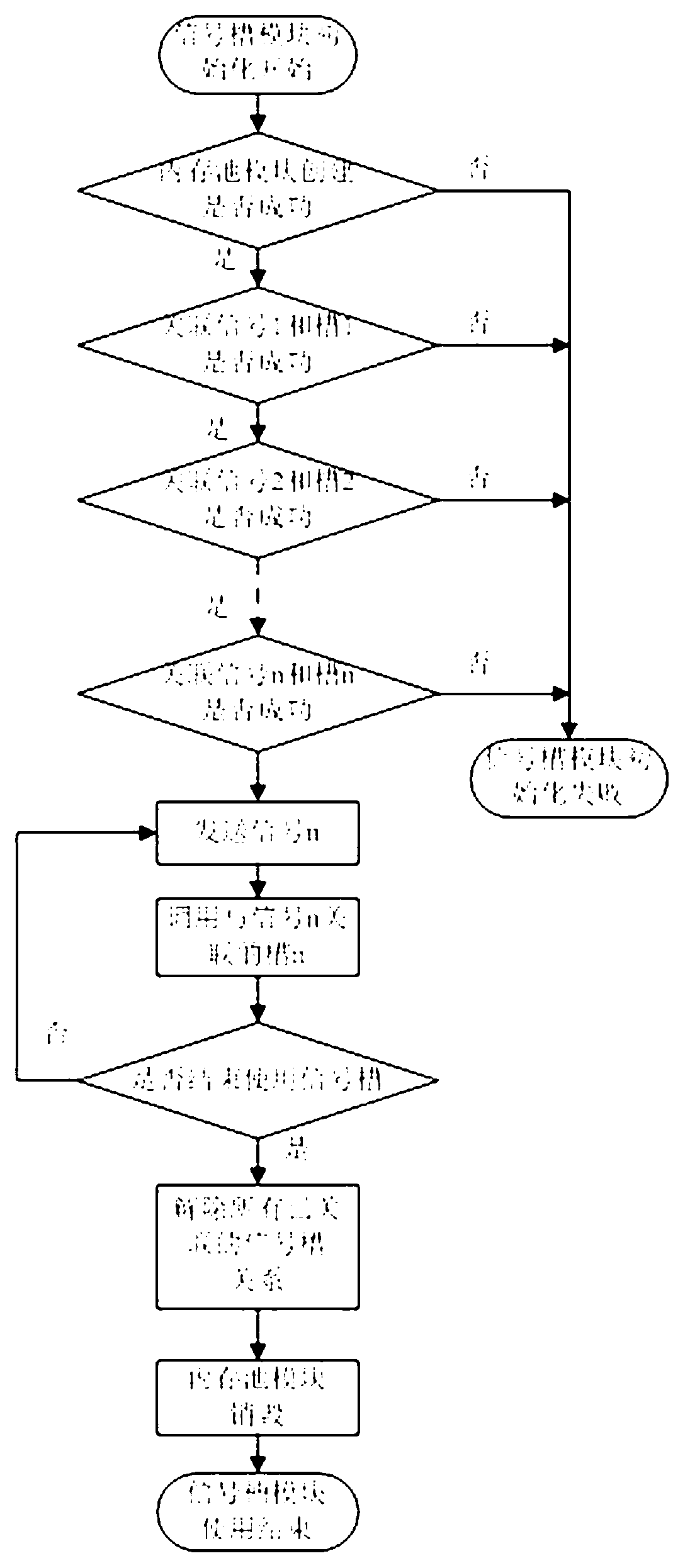
Signal-slot structure for embedded system
InactiveCN102945163AEffective organizationEfficient managementSpecific program execution arrangementsSignals and slotsTime complexity
The invention discloses a signal-slot structure for an embedded system. The signal-slot structure is divided into an upper layer and a lower layer, wherein a signal-slot module is arranged on the upper layer and a memory cell module is arranged on the lower layer; the signal-slot module uses a hash table to manage signals and slots; the memory cell module is used for creating a memory cell, providing necessary memory for the signal-slot module to store related data of the signals and the slots, and recovering the occupied memory when the signals are disassociated from the slots; and the memory cell module manages a memory block through establishing a balanced binary (AVL) tree, and distributes and recovers the memory on the basis of a buddy algorithm. When the signal-slot structure is applied to the embedded system, the signals and the slots can be effectively organized and managed, the time complexity of searching the slots corresponding to the signals is low, and an objective function does not need to be searched by traversing the whole function list like in a traditional method, so that the calling efficiency of the function is improved, componential programing of a system can be realized and the communication efficiency among components can be improved.
Owner:GUILIN UNIV OF ELECTRONIC TECH +1
Non-recursive high-performance construction method of balanced binary tree
InactiveCN113326271ASolve highSolve deleteSpecial data processing applicationsDatabase indexingTheoretical computer scienceBinary tree
The invention discloses a non-recursive high-performance construction method of a balanced binary tree, which belongs to the technical field of computer basic algorithms, and comprises the following steps: establishing a database server, a node adding server, a node deleting server and a balanced binary tree construction server; in constructing an AVL tree, the imbalance adjustment of the AVL tree comprises right-handed rotation adjustment, left-handed rotation adjustment, left-handed rotation and right-handed rotation adjustment and right-handed rotation and left-handed rotation adjustment, and the technical problem that the operation of adding, deleting and querying the AVL tree is achieved through a non-recursive method is solved. According to the method, for the querying occasion in which the AVL tree is required, the AVL tree can be generated with the efficiency similar to that of red-black tree generation, data query is carried out with the query efficiency about 10% higher than that of the red-black tree, the tree generation efficiency has no great advantage compared with a red-black tree algorithm, the method can be applied to occasions which are slightly insensitive to data generation time but have high requirements for query speed, and the algorithm time consumption is greatly reduced compared with a recursive algorithm.
Owner:江苏未来智慧信息科技有限公司
Program execution method
InactiveCN104156212AGuaranteed retrieval performanceGuaranteed update efficiencySpecific program execution arrangementsLookup tableAVL tree
The invention provides a program execution method which is used for indexing in a Flash database. The method comprises the steps that when AVL tree index nodes are updated, a cache log is generated in log cache; when the log cache is full, combination is conducted with a node log group as a unit, and the cached log is written into a log storage region; a node log lookup table is built, and the mapping relation between the nodes and the Flash page where the log is located is recorded; log integration is conducted on the nodes, and the result is written into a node logic region. By means of the program execution method, the times of writing NAND Flash when the database is updated is reduced, and updating efficiency of indexing is guaranteed.
Owner:CHENGDU DINGZHIHUI TECH
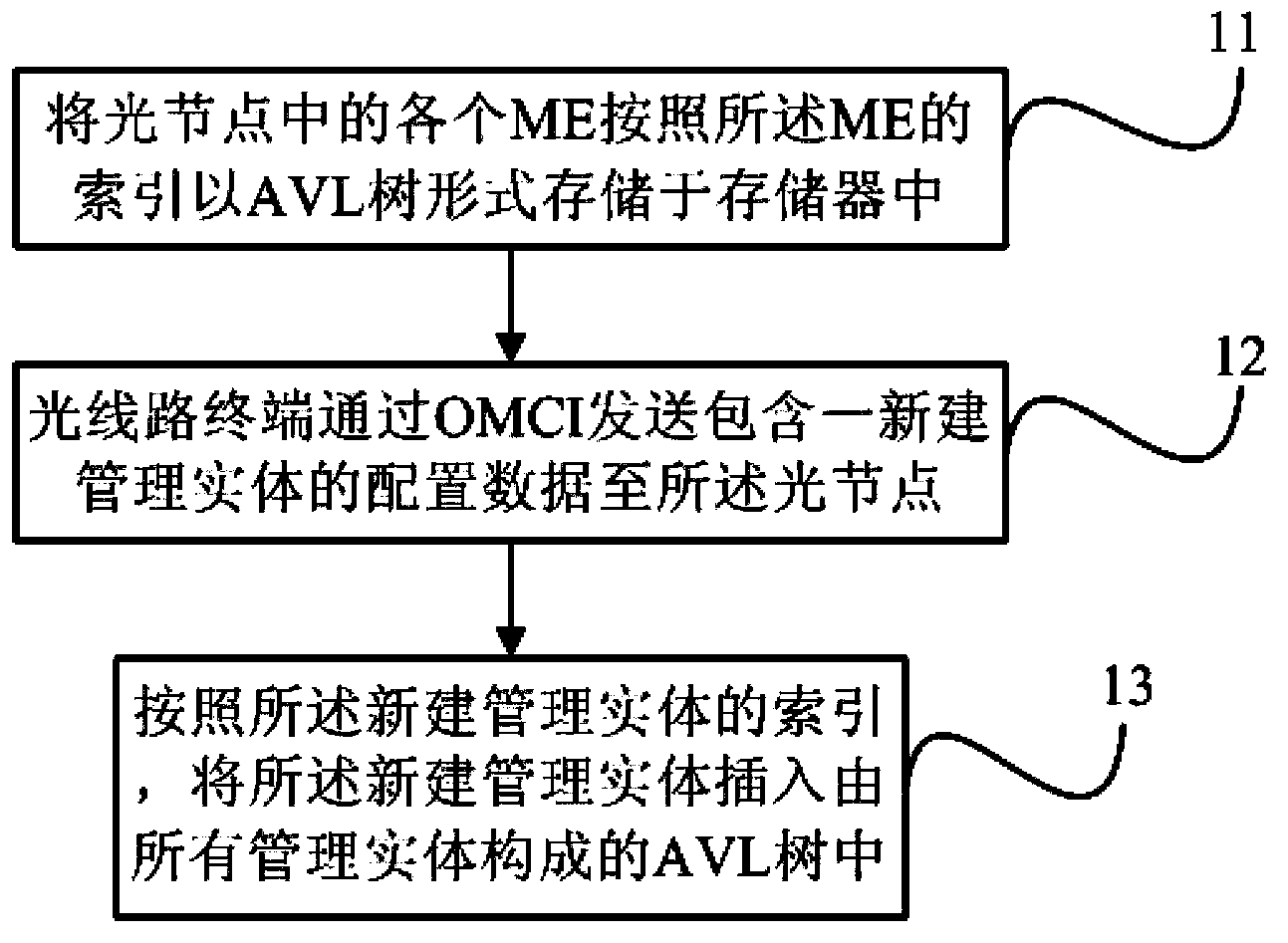
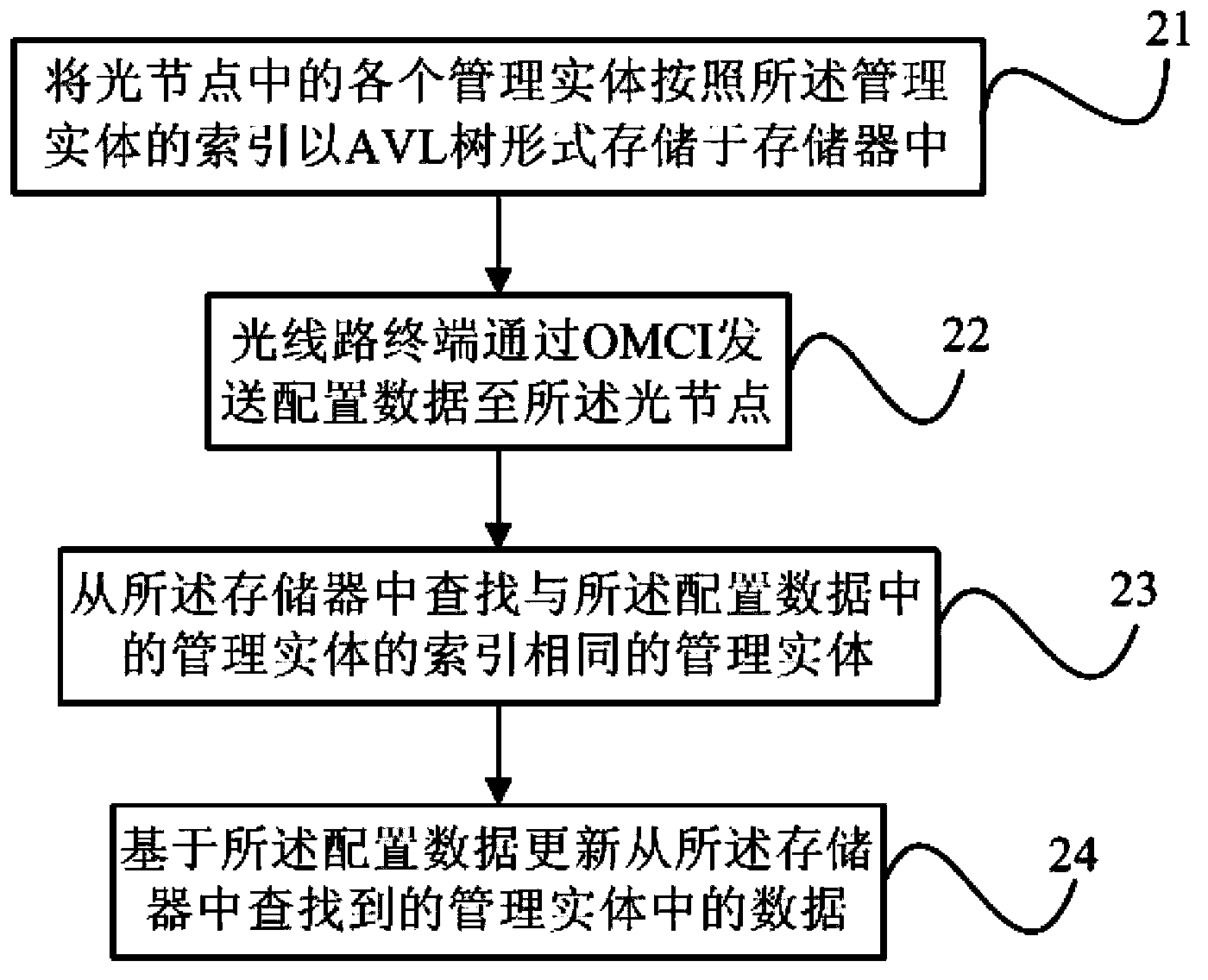
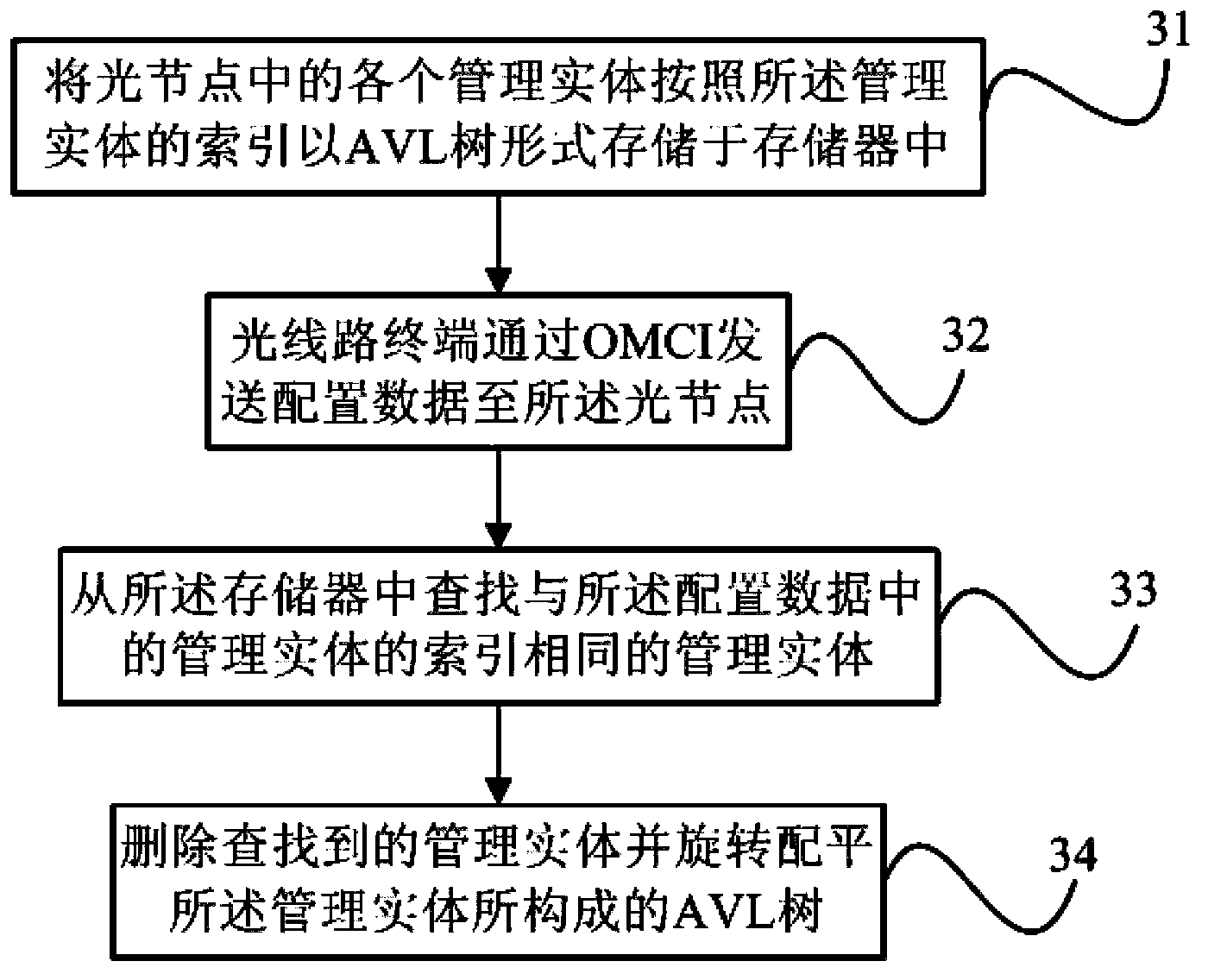
Operation method for light node management entity, and GPON system
InactiveCN103580882AEfficient use ofGuaranteed operating efficiencyTransmission monitoring/testing/fault-measurement systemsData switching networksAVL treeStorage efficiency
The invention discloses an operation method for a light node management entity and, a GPON system. The operation method comprises steps that: S11, each management entity in one light node is stored in a memory in an AVL tree mode according to identification data of the management entities; S12, configuration data including a newly-established management entity is sent to the light node by a light line terminal through an OMCI; and S13, the newly-established management entity is stored in the memory based on the configuration data, and the newly-established management entity is inserted in an AVL tree formed by all the management entities in the memory according to the identification data of the newly-established management entity. According to the operation method for the light node management entity, and the GPON system, ME data is stored by utilizing the AVL tree, and thereby storage efficiency and a searching rate are improved.
Owner:PHICOMM (SHANGHAI) CO LTD
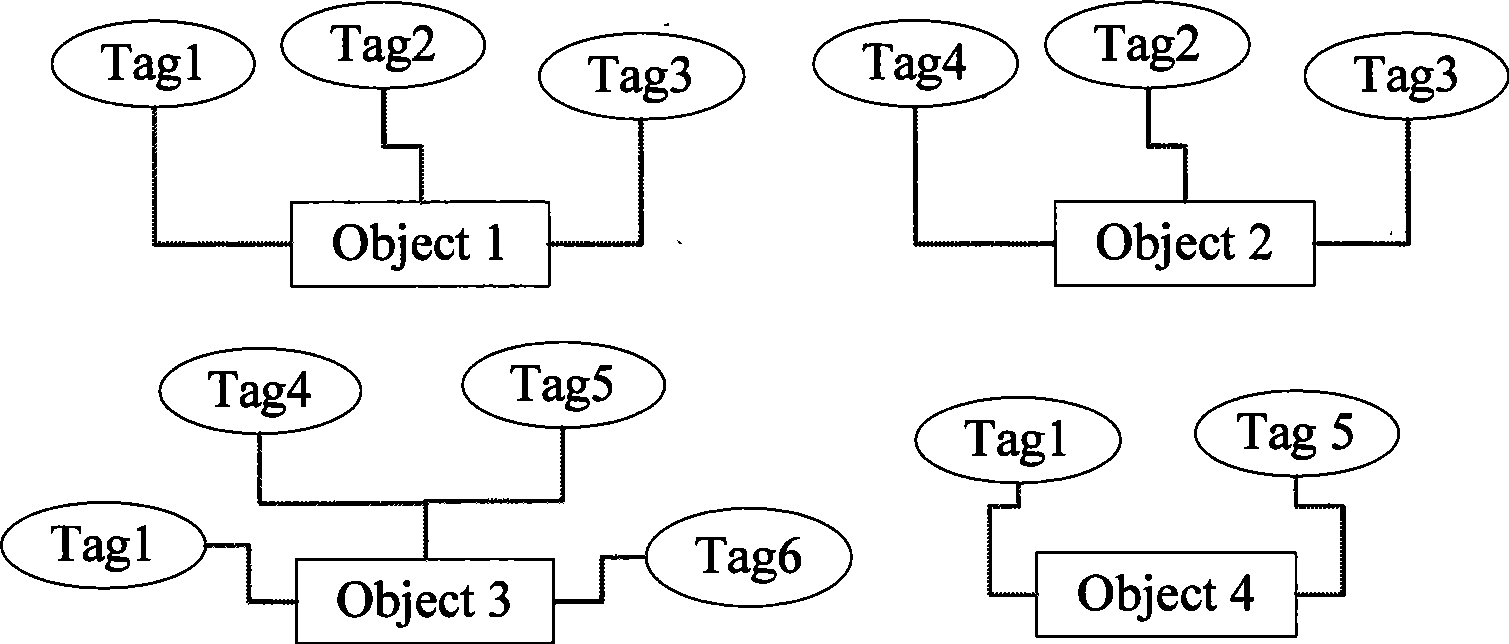
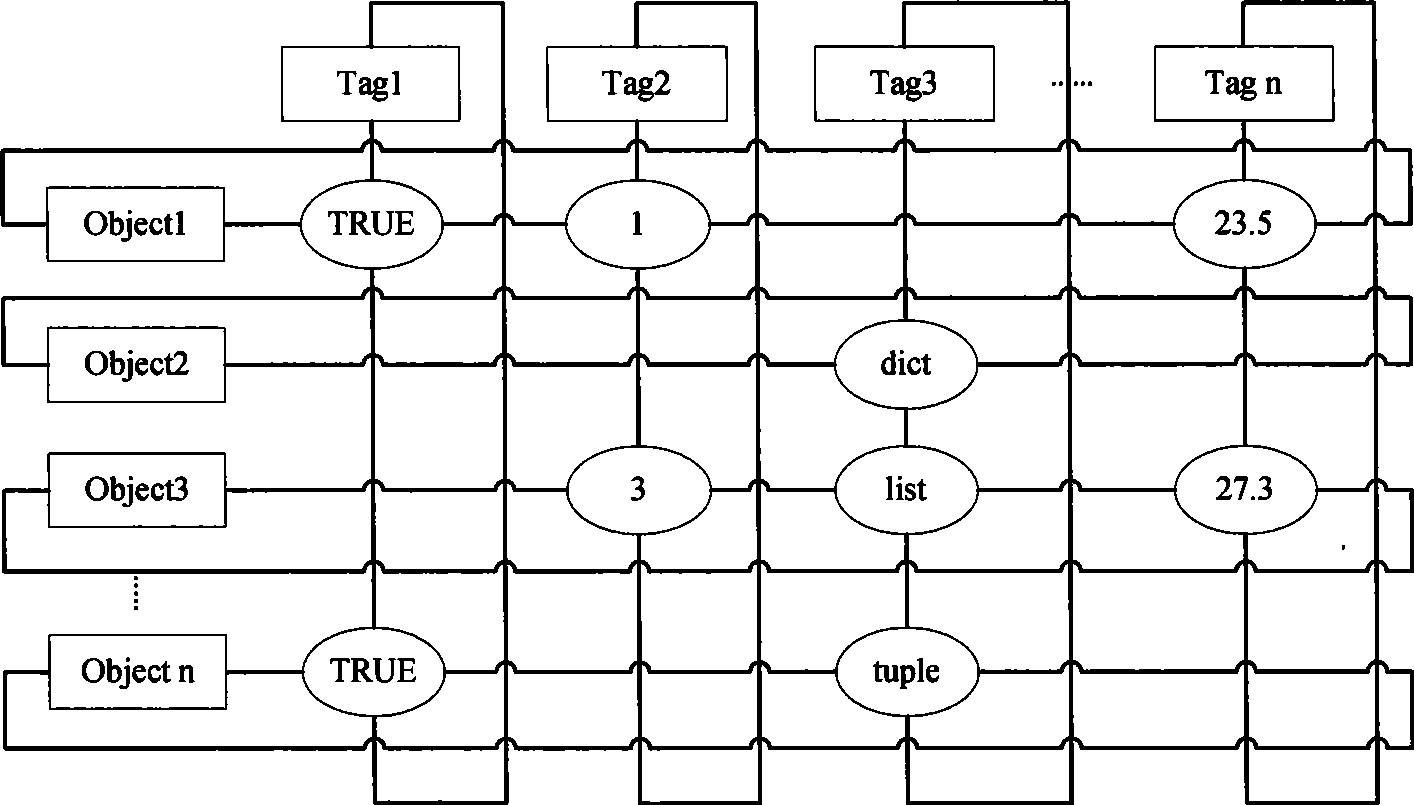
High-efficiency data search method based on expanded Tag cloud
InactiveCN101430713AFlexible and Efficient Sorting CapabilitiesSpecial data processing applicationsAVL treeHash list
The invention discloses a method for searching data efficiently based on expending Tag cloud. In the method, an orthogonal list is adopted based on a sparse matrix realization algorithm, as the orthogonal list can only contain data and can not provide functions of retrieving or positioning, the orthogonal list is modified in a mode of combining a hash list and an AVL tree, so that quick positioning of data is supported, and retrieving support is provided. The invention transforms the Tag from a common label to an assignable container. Therefore, the label not only provides the function of classification, but also contains certain information, and provides more particular function of positioning by the information.
Owner:NANJING UNIV
Session cache method based on binary balance tree
ActiveCN100485611CSave memorySpecific program execution arrangementsSpecial data processing applicationsTheoretical computer scienceBinary tree
A Session Cache method based on binary balance tree includes using front tree to store all nodes generated at former time slot and using back tree to store all nodes generated at later time slot, judging whether all nodes stored on said tree are expired or not by comparing ratio of said nodes setting-up time to their current time when node is searched and deleting off node stored on the tree if node stored on the tree is expired.
Owner:苏州海加网络科技股份有限公司
A location privacy protection method in sign-in service
ActiveCN106961386BRealize k-anonymityImplement location privacy protectionData switching networksComputer networkCiphertext
The invention discloses a position privacy protection method in a sign-in service, which encrypts each user's sign-in record and numbers each sign-in node through k-anonymously generated position sets, so as to maintain the sign-in chain and protect position privacy for users ; At the same time, increase location privacy protection by adding fake sign-in nodes, and distinguish real sign-in nodes from fake sign-in nodes through the sign bits corresponding to sign-in record ciphertexts. In addition, a header table and Hash table, so that the node numbers contained in the header table and the hash table are the latest node numbers signed by the user and their corresponding decryption keys; in this way, by directly decrypting the ciphertext in the hash table, you can get all Check-in records, and at the same time, by searching the AVL tree, you can get all the friends who have checked in at a specific place and their corresponding head table line numbers, and decrypt the head table to get all the check-in records at a specific place. Therefore, it is also possible to provide two retrieval methods Improve location privacy protection requirements.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Routing information compression and retrieval method and system
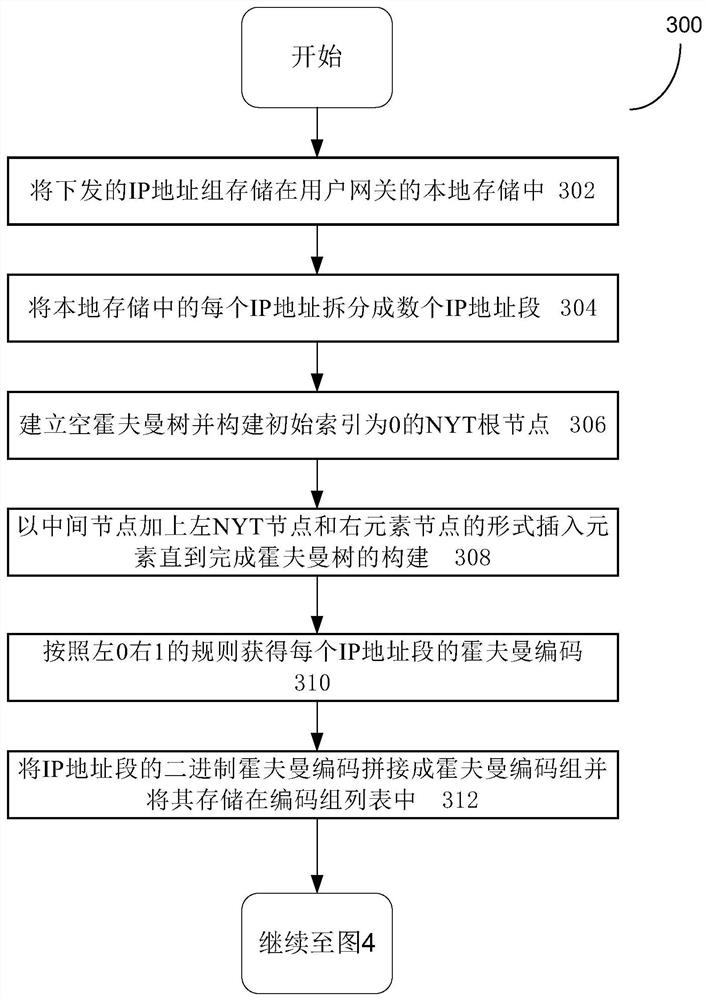
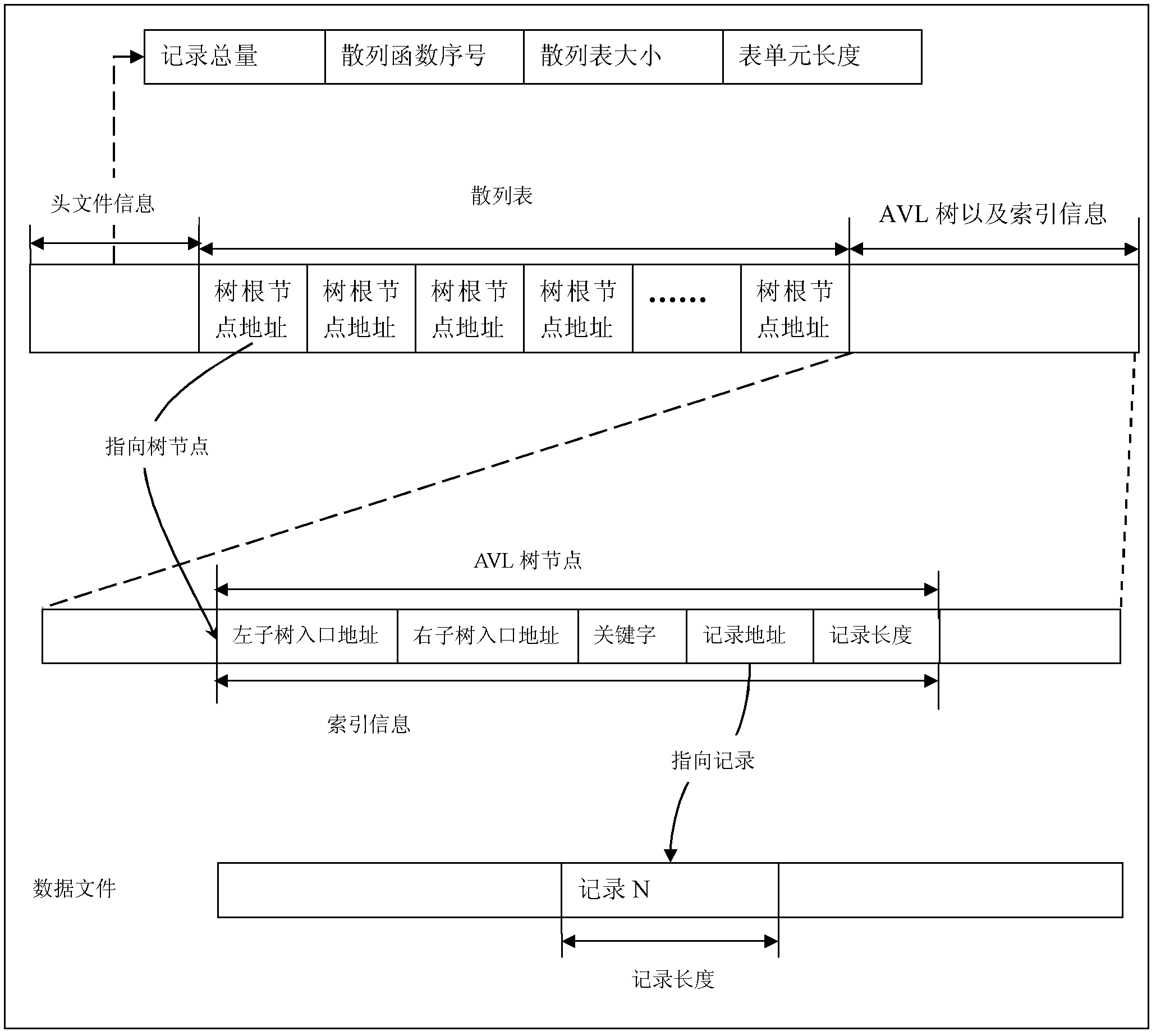
ActiveCN113852556AShorten the lengthIncrease the number ofData switching networksAlgorithmIp address
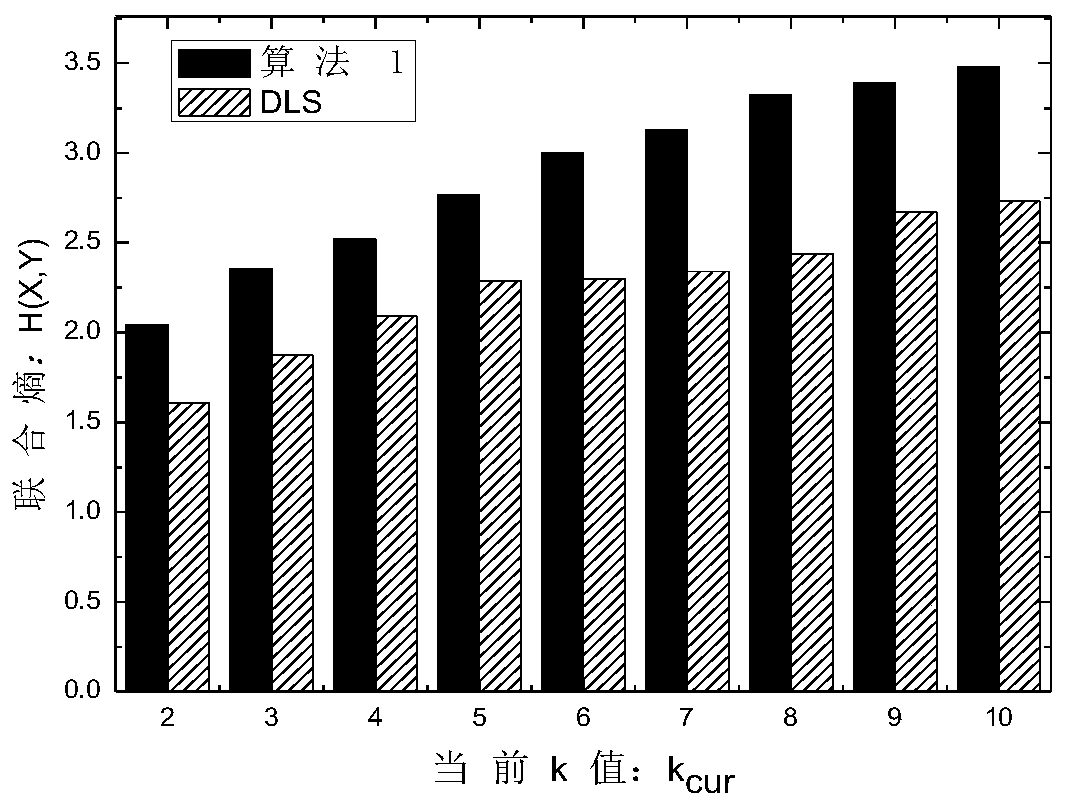
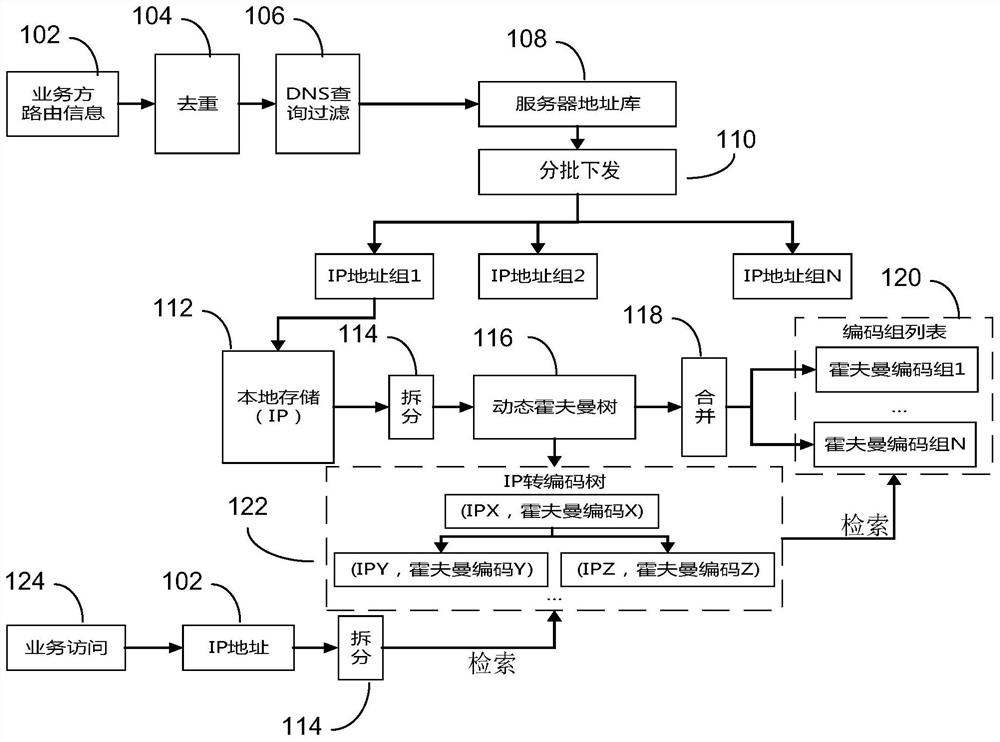
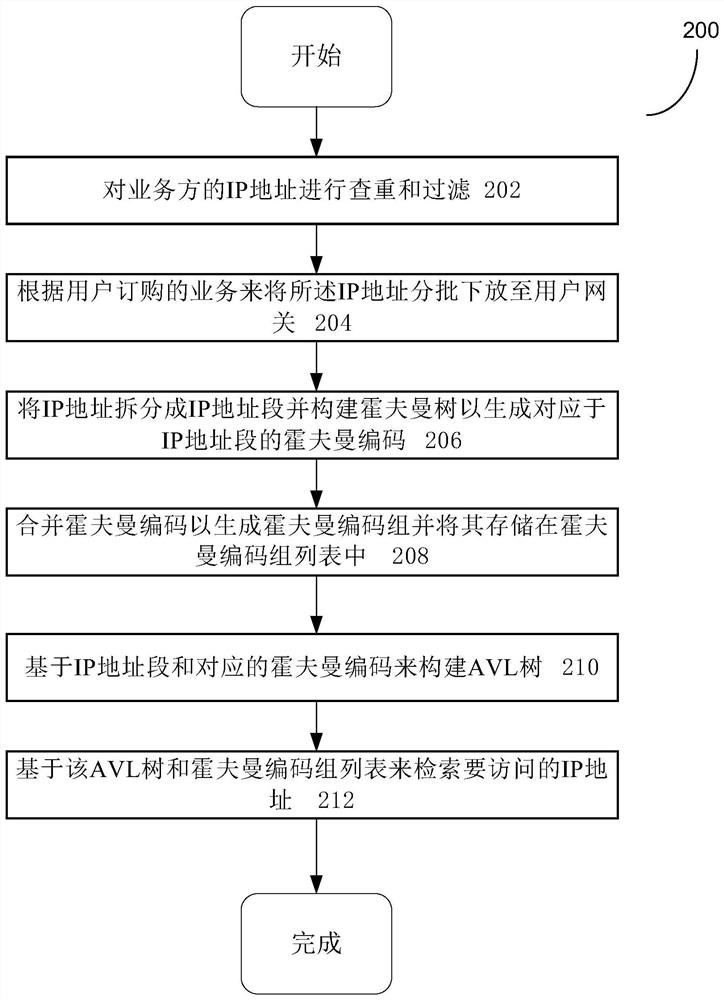
The invention relates to a routing information compression and retrieval method based on Huffman coding and an AVL tree. The method comprises the steps of performing duplicate checking and filtering on an IP address of a service party, issuing the IP address to a user gateway in batches according to a service ordered by a user, splitting the IP address into an IP address field and constructing a Huffman tree to generate Huffman codes corresponding to the IP address field, merging the Huffman codes and storing the Huffman codes in a Huffman code group list, constructing an AVL tree based on the IP address field and the corresponding Huffman code, and retrieving the IP address to be accessed based on the AVL tree and the Huffman code group list.
Owner:E-SURFING DIGITAL LIFE TECH CO LTD
Searching and storing method for embedded database
InactiveCN102629269BIncrease profitImprove retrieval efficiencySpecial data processing applicationsLimited resourcesEmbedded database
The invention discloses a searching and storing method for an embedded database. When an embedded system is under an off-line mode, the method comprises the following steps: external high-speed equipment is used for data organization and storage, a data file is set up and the recording is kept, an index file is kept, index information is kept in an AVL tree node, and finally, a database file is downloaded to embedded equipment for use. When the embedded system is under the off-line mode, the method comprises the following steps: searching AVL tree in the index file through keywords, obtaining the index information, so as to obtain the recording of the date file, or insert newly built tree node into an AVL tree, and keep the index information and the recording. The method provided by the invention fully uses optimization process of the external high-speed equipment according to the characteristics of the resource of date and uses the technologies such as a hash table and AVL three for data organization and storage, and the method provided by the invention has the benefits of less resource consumption and high searching efficiency, and can be used in embedded systems with limited resources.
Owner:SHENZHEN MINDE ELECTRONICS TECH
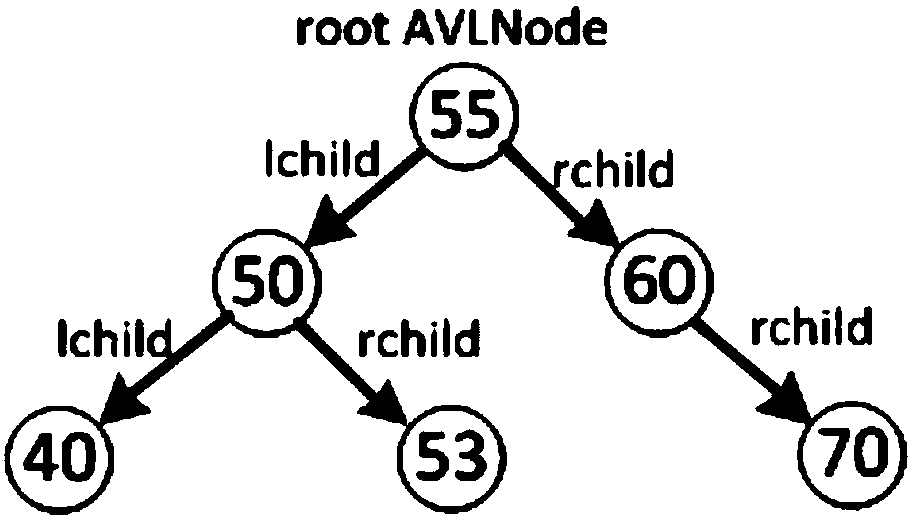
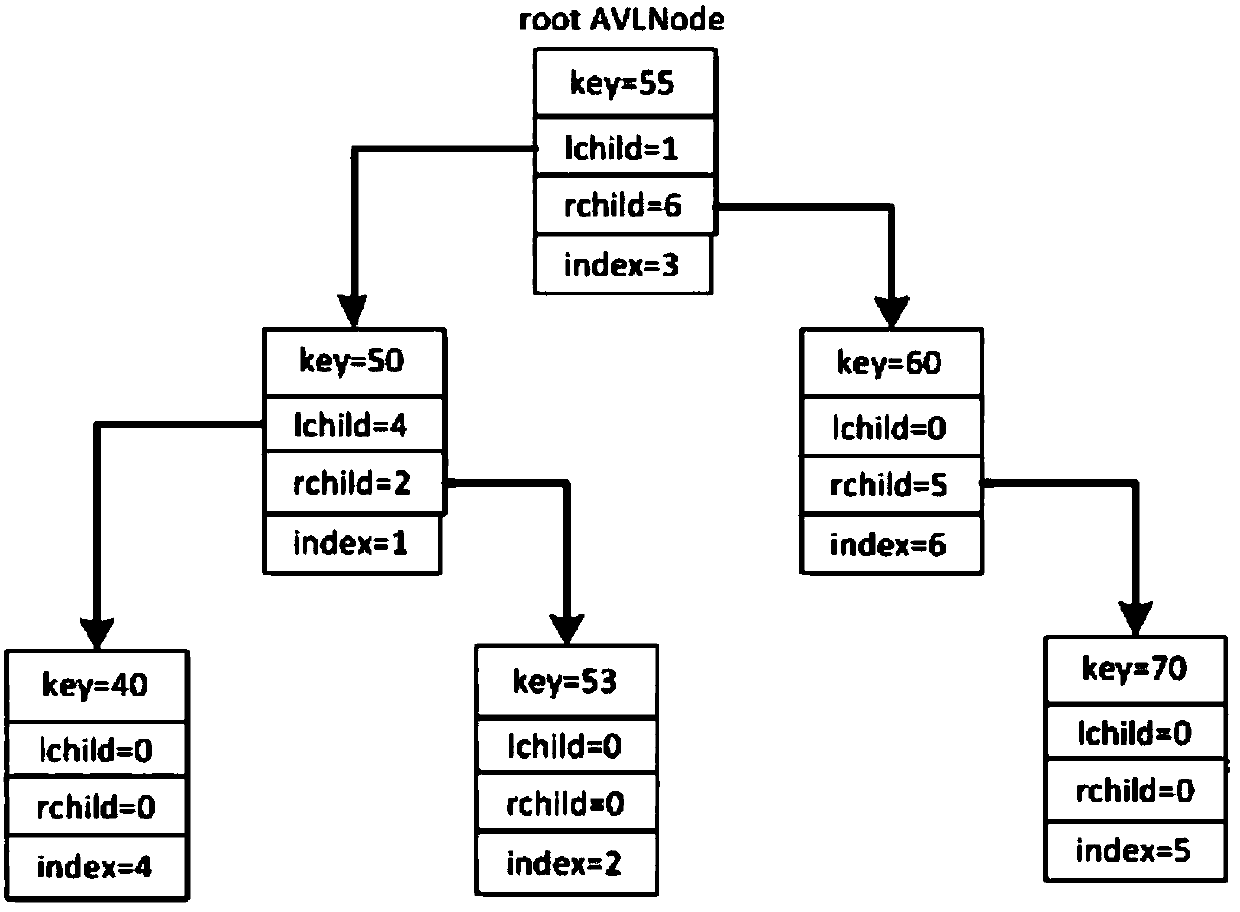
Method and system for realizing use of interprocess AVL (Self-Balancing Binary Search Tree) tree
InactiveCN107656993ASpecial data processing applicationsDatabase indexingOperational systemSelf-balancing binary search tree
The invention discloses a method and a system for realizing the use of an interprocess AVL (Self-Balancing Binary Search Tree) tree, and is used for solving the problem that an existing AVL tree operating system can not be used among processes. The method comprises the following steps that: S1: distributing the value of an interprocess AVL tree node in sequence; S2: according to the sequence, determining the index value of the interprocess AVL tree node; S3: according to the value and the index value of the interprocess AVL tree node, establishing shared memory; and S4: mapping the shared memory to the local process address space of each process. By use of the method, the index value of the shared memory is used for managing a left subnode and a right subnode to replace a situation that atraditional pointer manages the left subnode and the right subnode, and each node is managed by the AVL tree among the processes.
Owner:杭州吉吉知识产权运营有限公司
A wireless sensor network key management method
ActiveCN103929744BImprove securityReduce search timeNetwork topologiesSecurity arrangementPasswordWireless sensor networking
Owner:SOUTHEAST UNIV
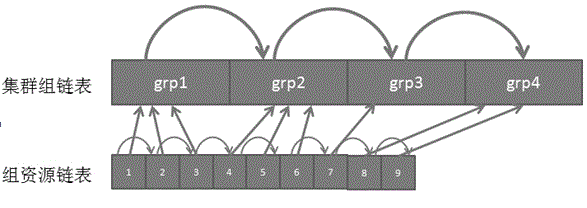
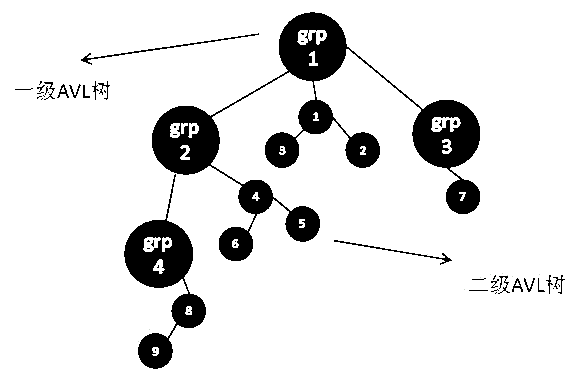
High-availability cluster resource management method
InactiveCN104679877AImprove search speedReduce downtimeProgram controlSpecial data processing applicationsResource managementAVL tree
The invention discloses a high-availability cluster resource management method and relates to the field of high-availability cluster software. The high-availability cluster resource management method comprises the following steps: in high-availability cluster resource management, managing groups and group resources in a cluster by a two-stage AVL tree to replace an original chain table management mode; establishing a correlation relationship between the groups and group resources by the two-stage AVL tree to make the correlation relationship between the groups and group resources clear. According to the high-availability cluster resource management method, the resources are managed through the AVL tree, so that the resource switchover time is reduced, the service interruption time is shortened and the competitive power of high-availability cluster products is improved.
Owner:INSPUR GROUP CO LTD
Information query method and device, electronic equipment and medium
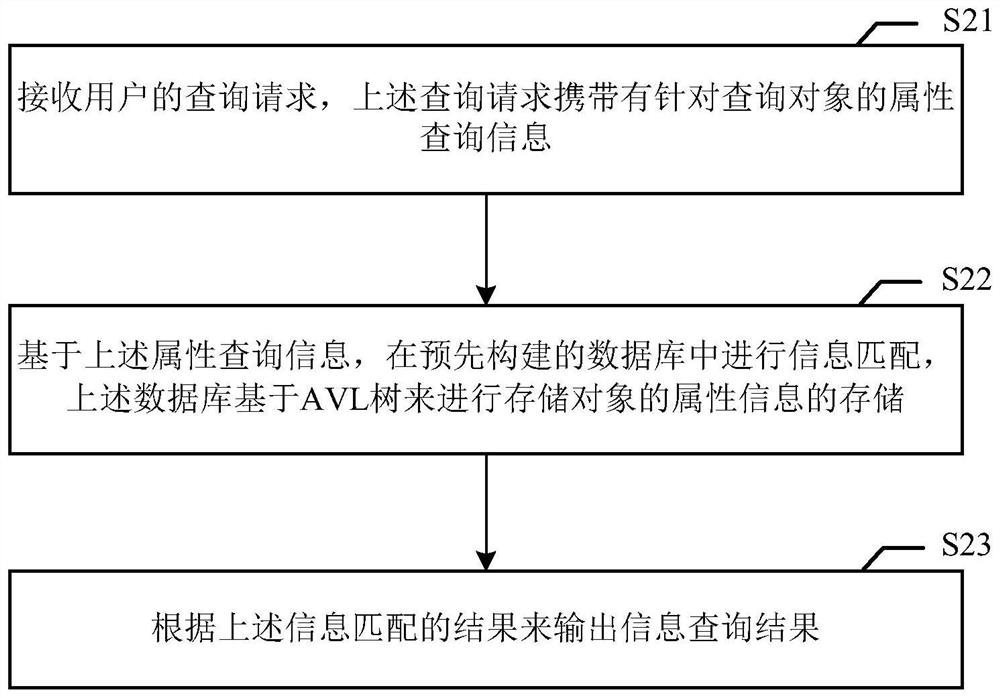
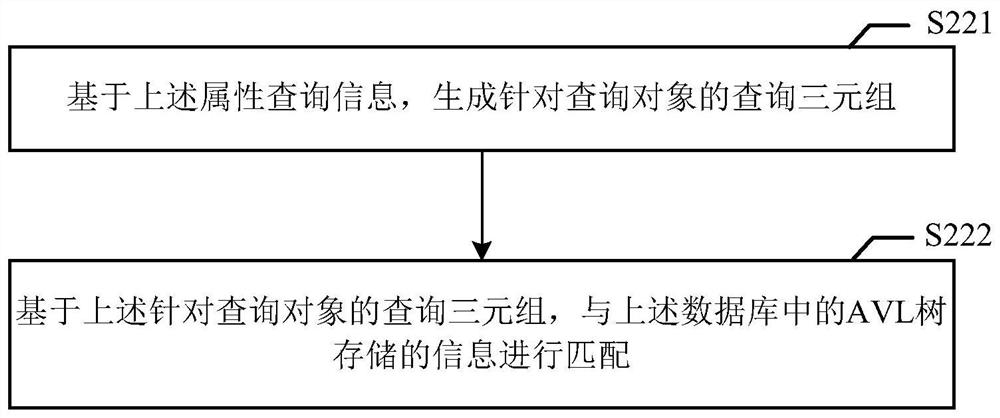
PendingCN113449003AEfficient queryQuick responseDatabase updatingSpecial data processing applicationsEngineeringData mining
The invention relates to an information query method and device, electronic equipment and a medium, and the information query method comprises the steps of: receiving a query request of a user, wherein the query request carries attribute query information for a query object; performing information matching in a pre-constructed database based on the attribute query information, the database storing attribute information of a storage object based on an AVL tree; and outputting an information query result according to an information matching result.
Owner:JINGDONG TECH HLDG CO LTD
Organization and management method and system for personalized service requirements
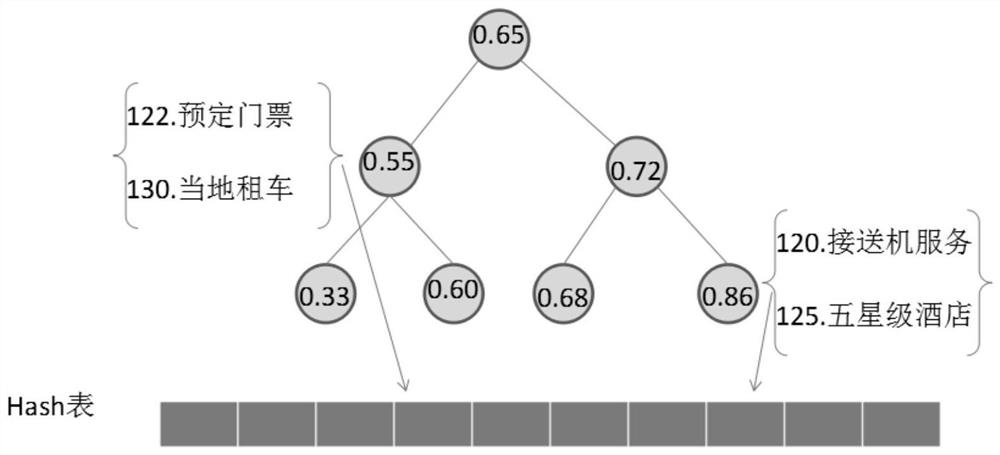
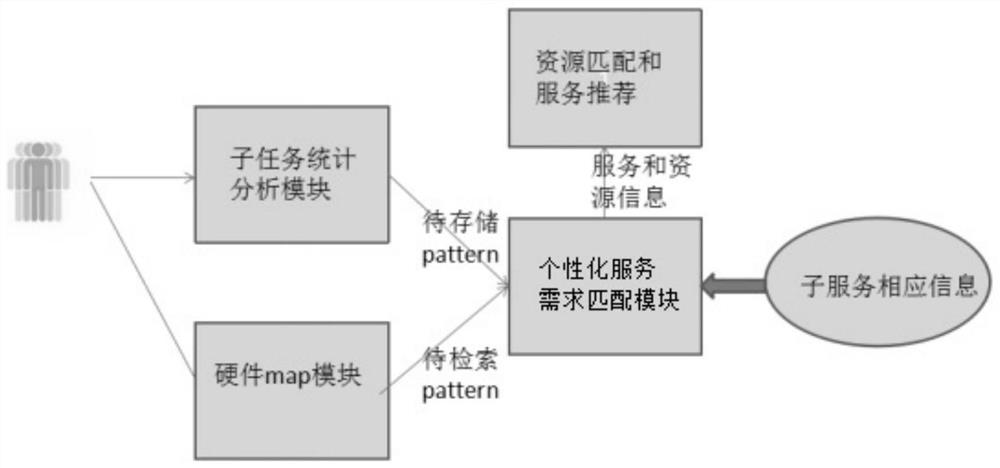
PendingCN111898779AAchieve the role of personalized recommendationEfficient and orderly dynamic resource matching effectReservationsSpecial data processing applicationsService modeData mining
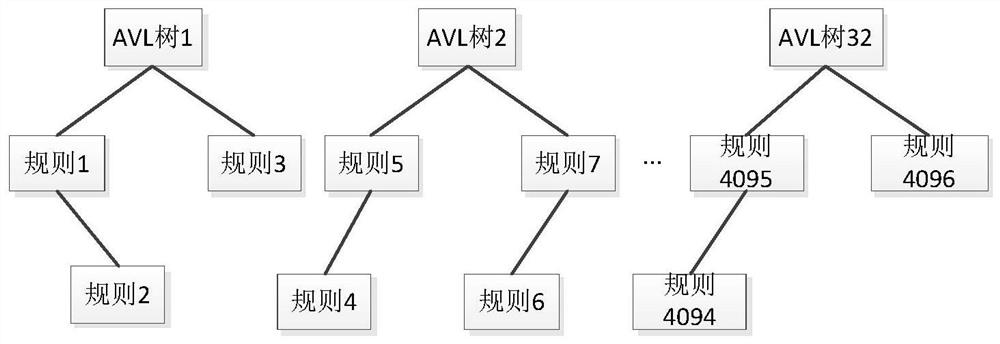
The invention provides an organization and management method and system for personalized service requirements. Counting and analyzing entropies of personalized sub-services in a large number of cloudservices; entropy is used as a key value code, a large number of personalized service modes are built into an AVL tree, repeated key codes are stored in a hash table, and when a user initiates a service request on a cloud platform, the specific content, characteristics, associated requirements, comprehensive recommendation and the like of personalized requirements of the user can be quickly indexed through the data structure and method. According to the invention, a dynamic link integration model for personalized services can be established, so that the compatibility of resources and servicesis improved, and the matching efficiency and integration efficiency of demands and resources are improved.
Owner:SOUTHEAST UNIV
A high-speed fuzzy search method for bitmap
ActiveCN110442570BSave logic resourcesIncrease logic processing rateSpecial data processing applicationsDatabase indexingExact matchAlgorithm
The present invention relates to a BitMap high-speed fuzzy search method, which includes: software establishment and distribution of rule entries: the required five-tuple combination is divided into AVL trees; each AVL tree has the highest priority according to the exact matching, and the fuzzy matching accuracy is higher The higher the priority, the higher the principle of storing rule nodes, and the blocks are arranged linearly according to the priority; according to the priority, the Bitmap lookup table is established, and the five-tuple information is divided to establish a search index; when updating the Bitmap, it needs to be matched according to the mask Various combinations; generate an index key based on the rule entry information, and then divide it into multiple sub-keys; look up the table based on the index key for the five-tuple of IP network packets. The invention improves the table writing and table lookup mode of the content fuzzy lookup mode, saves logic resources, improves logic processing speed, and simultaneously expands multiple instantiations in a modularized manner, resources can be estimated, is convenient and quick, and reduces design risks.
Owner:BEIJING ZUOJIANG TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com