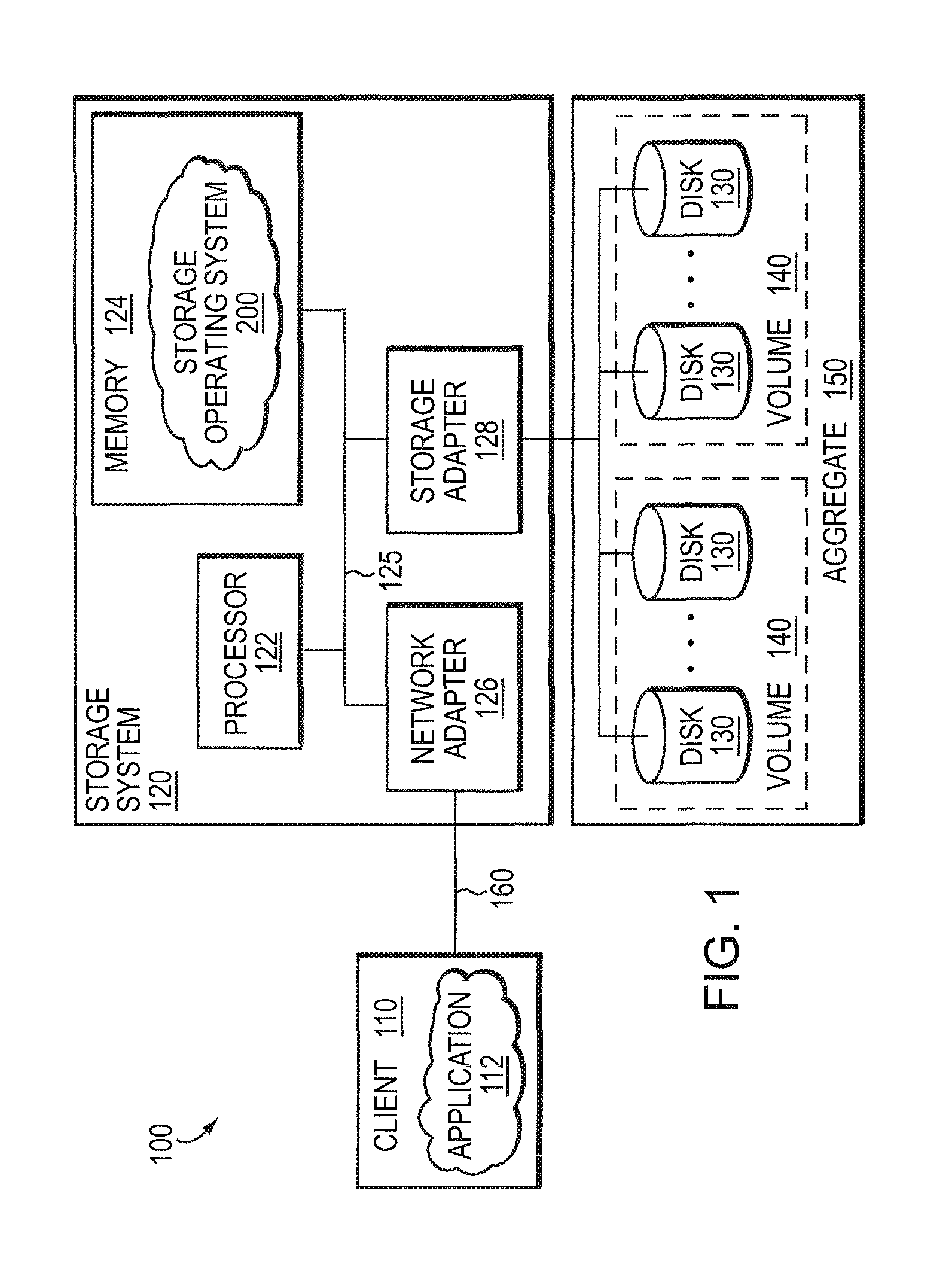
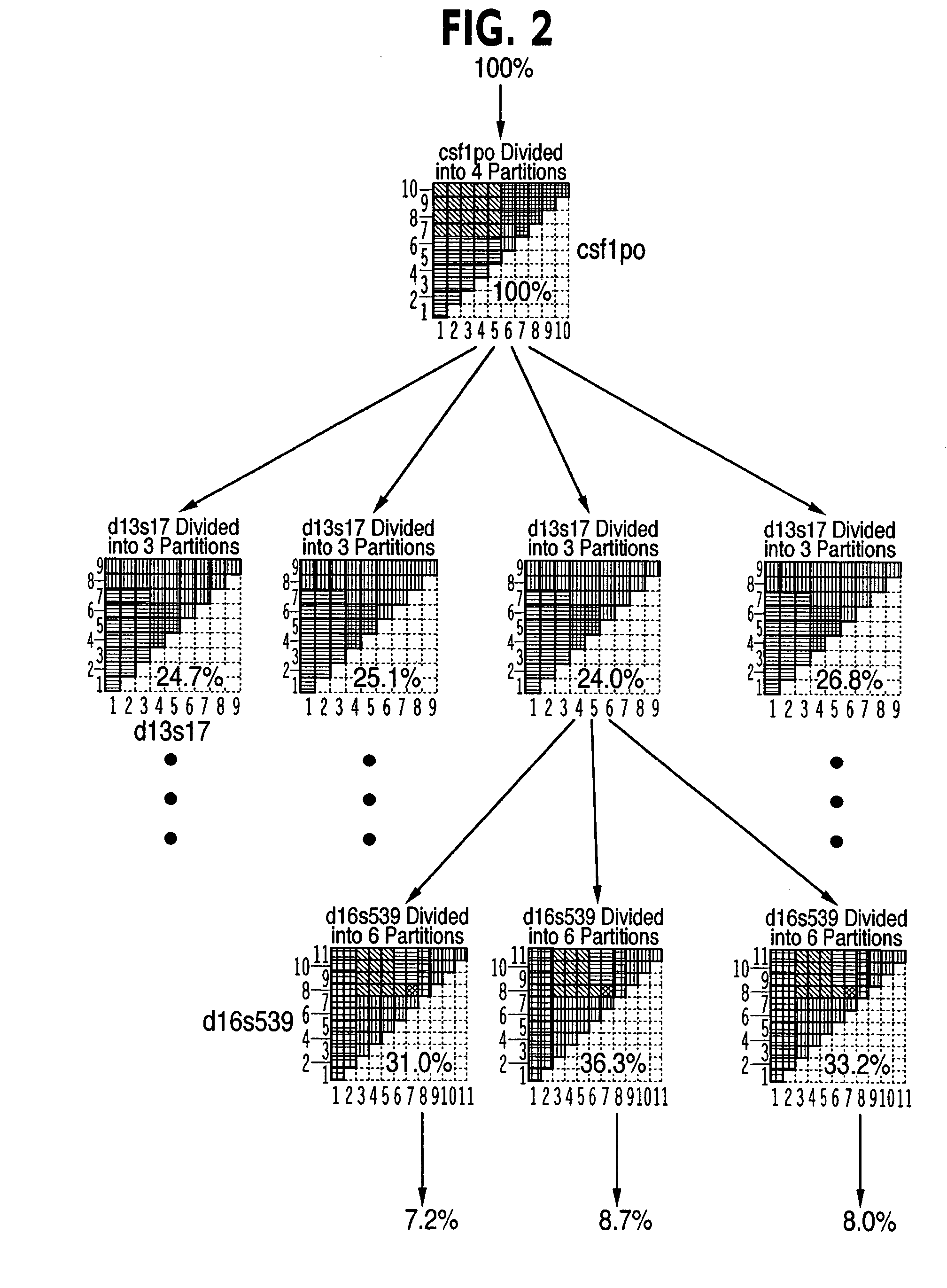
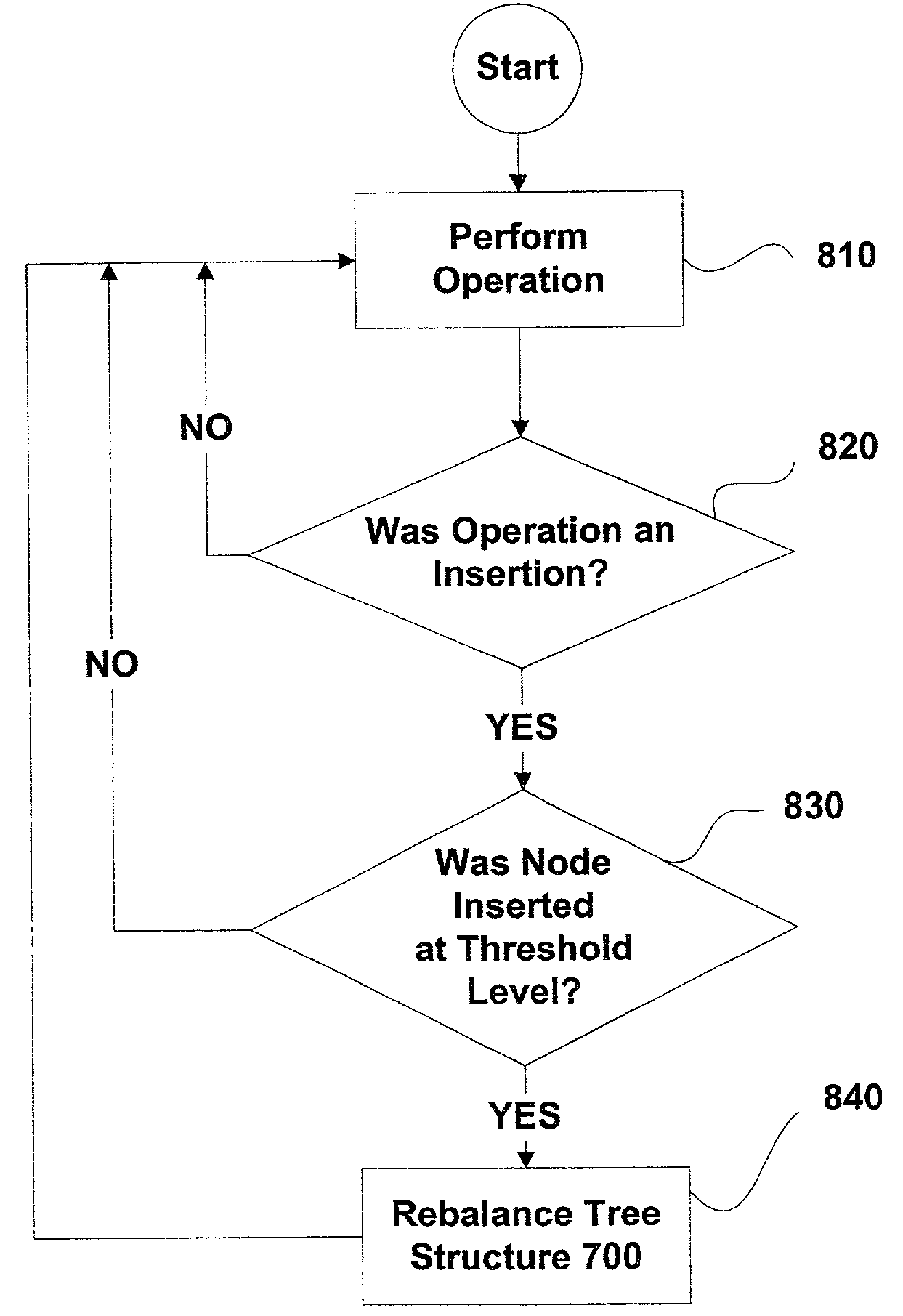
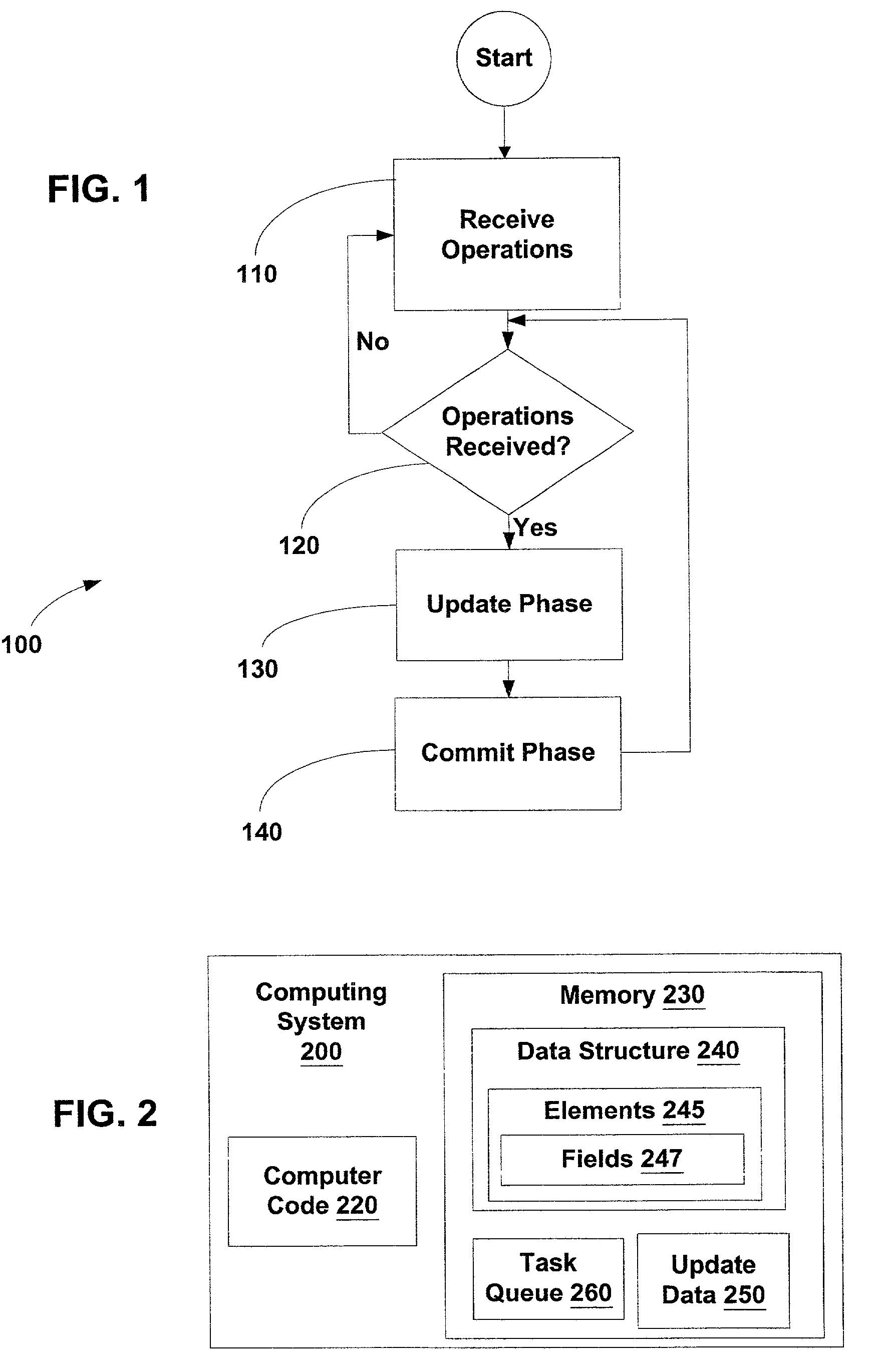
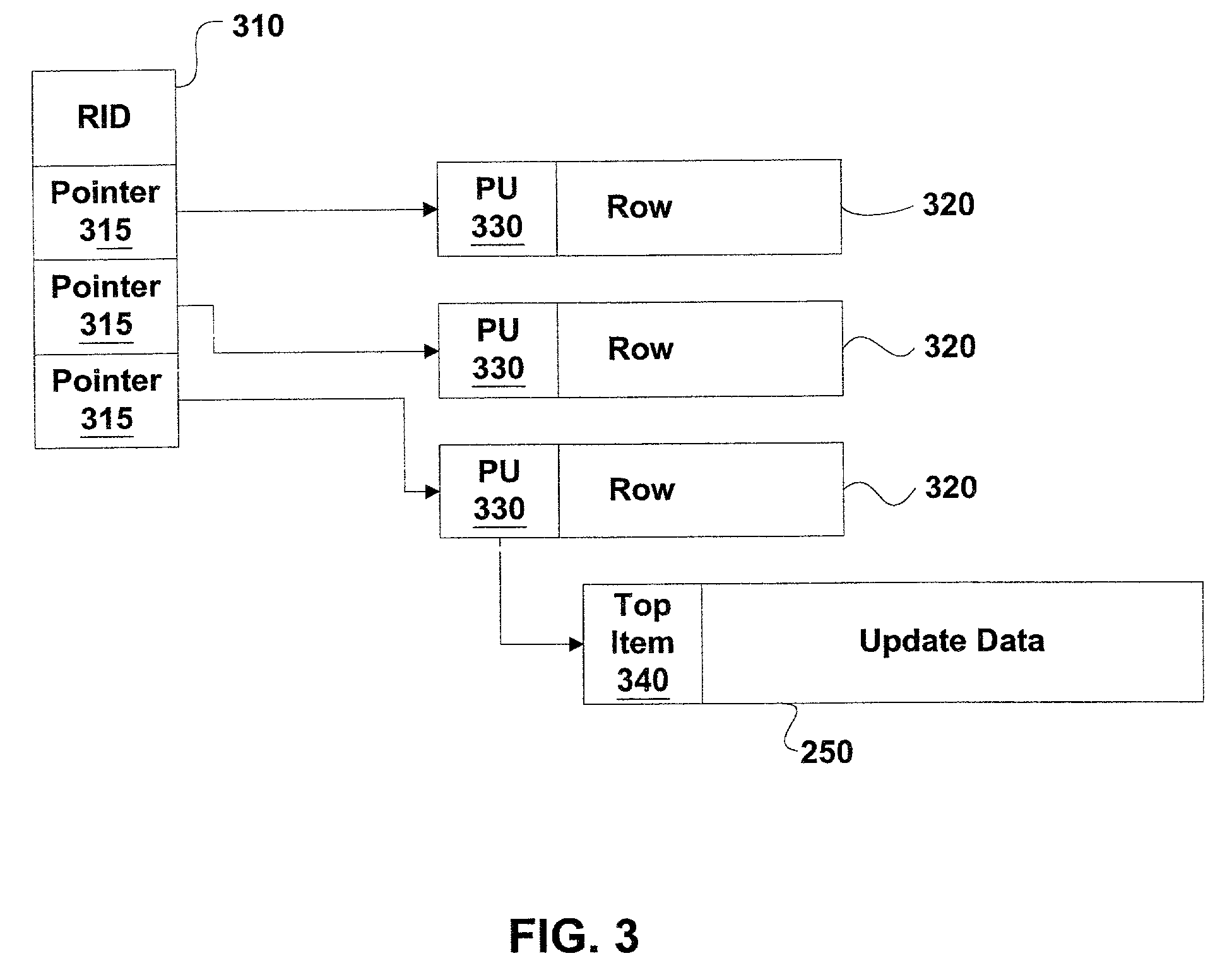
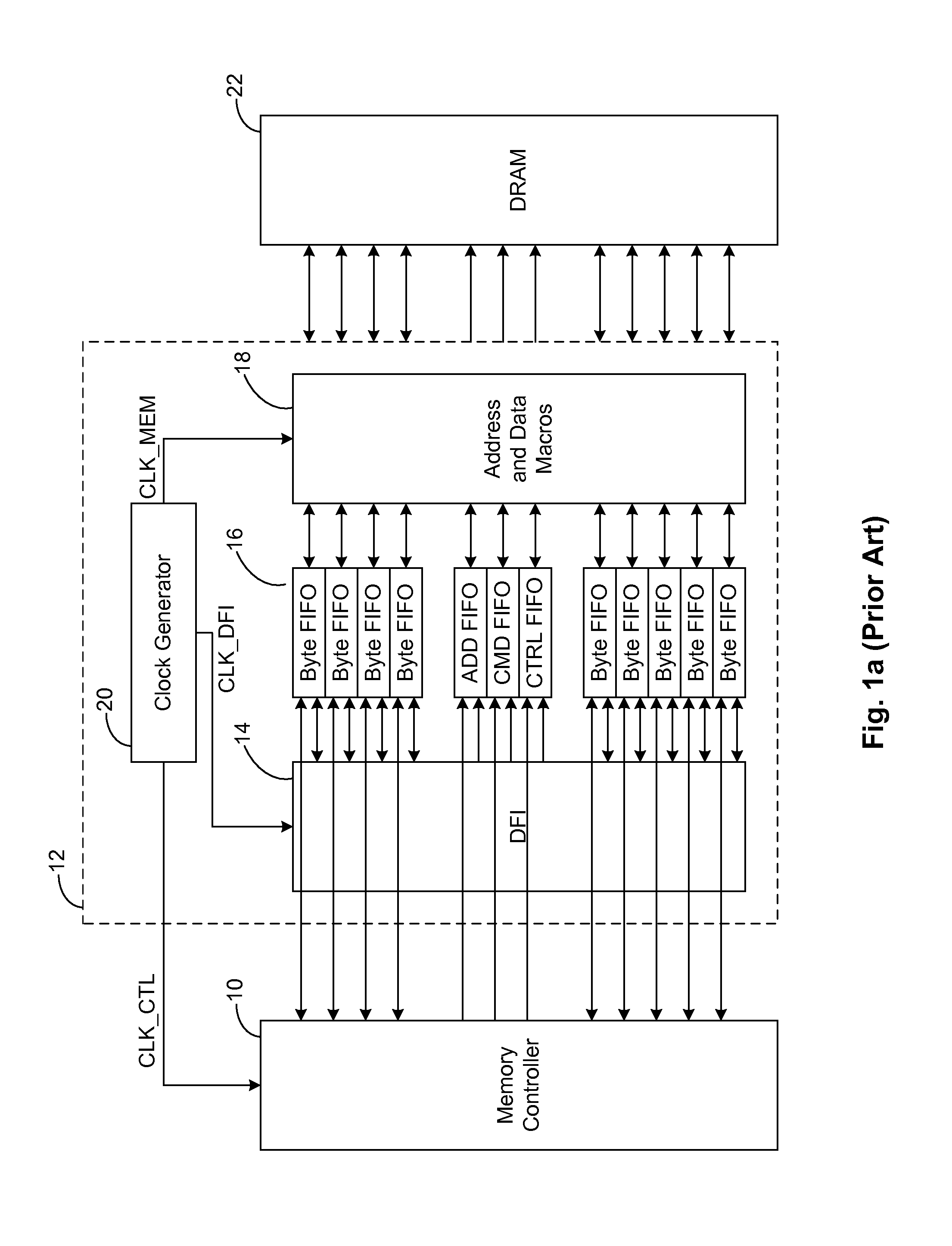
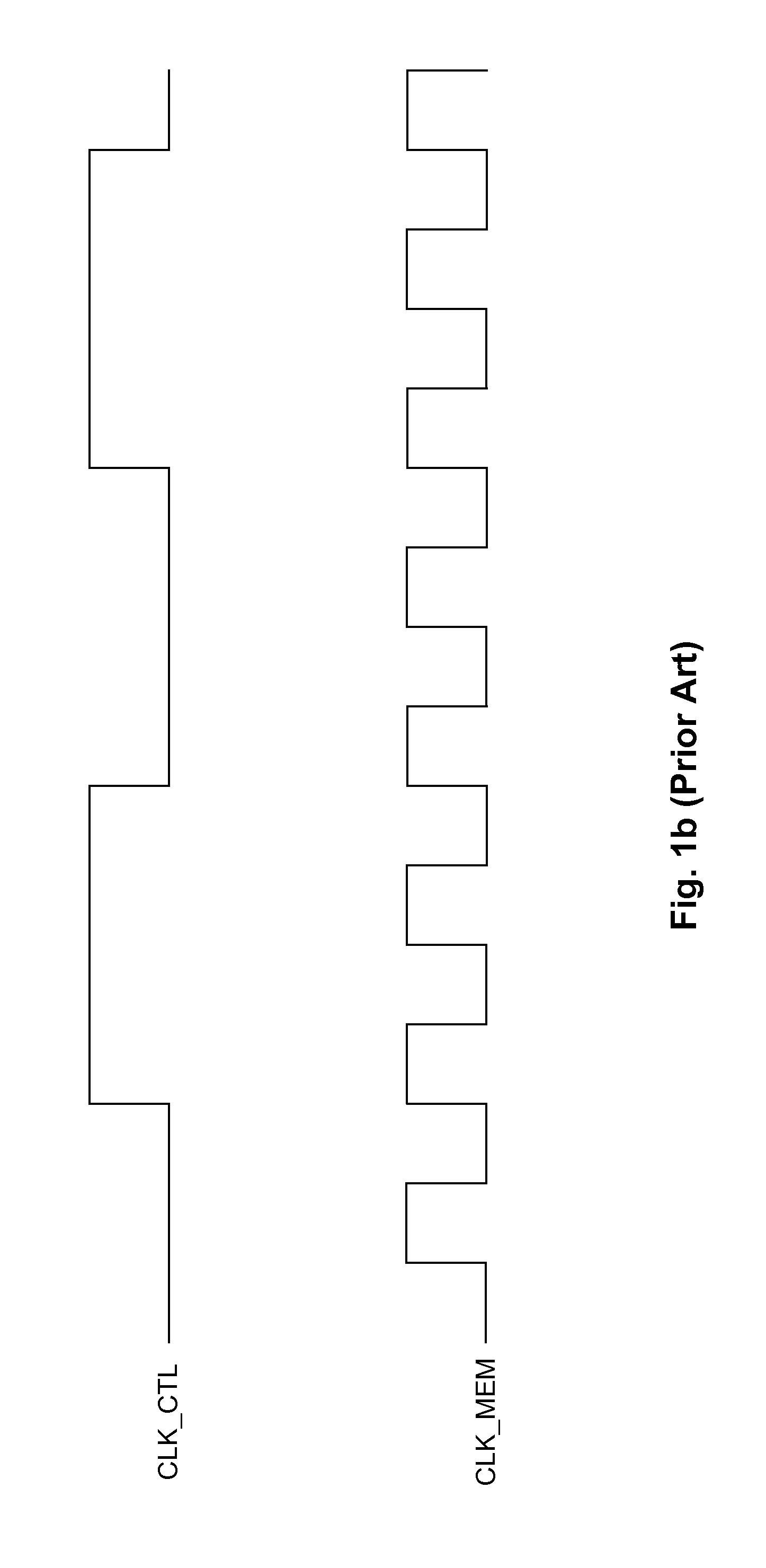
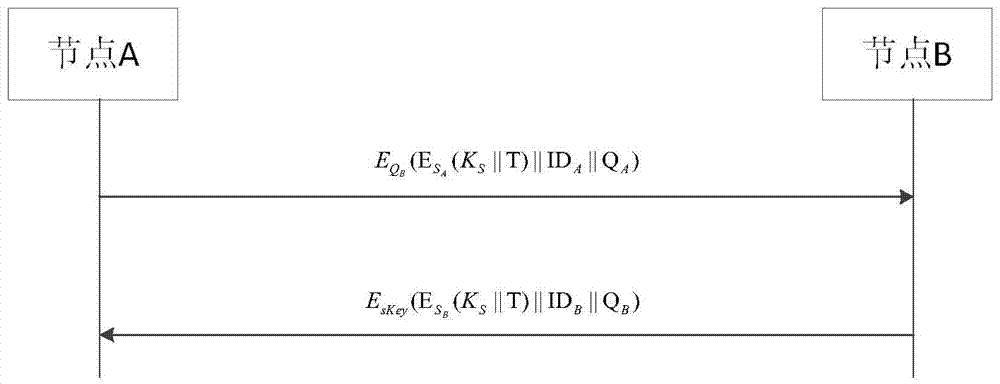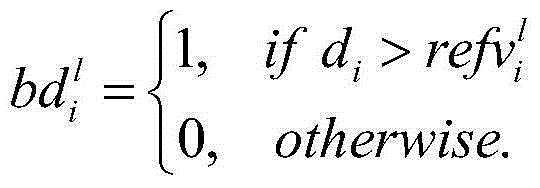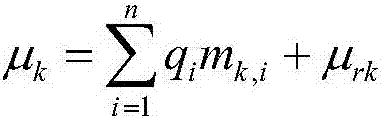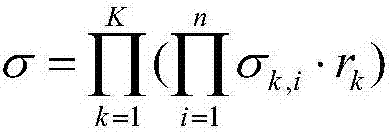Patents
Literature
52 results about "Self-balancing binary search tree" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
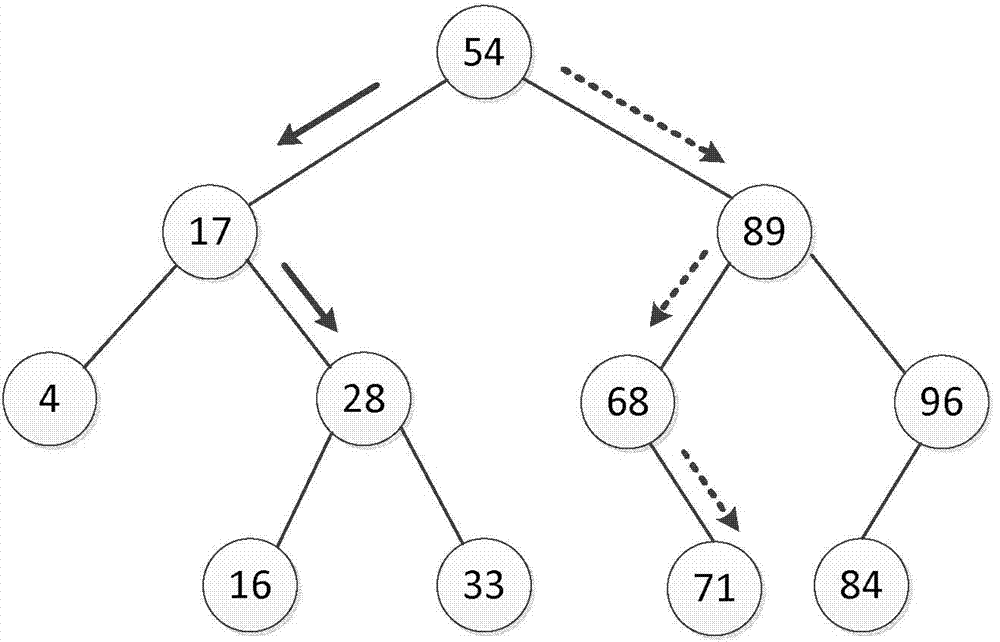
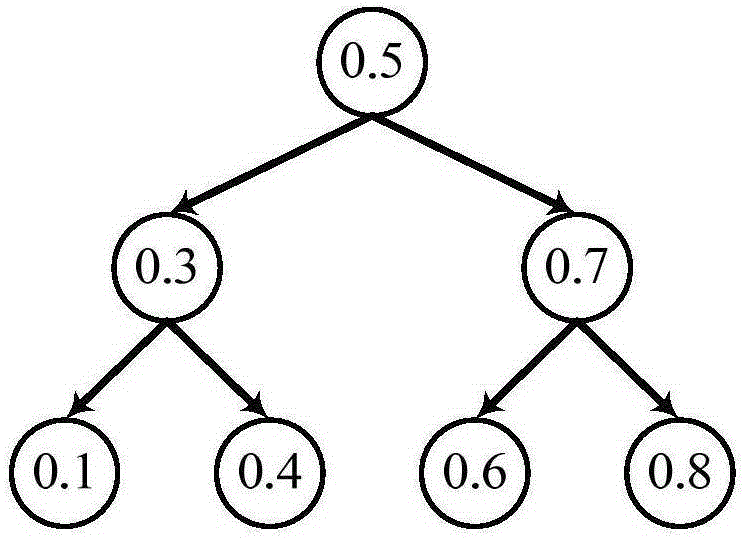
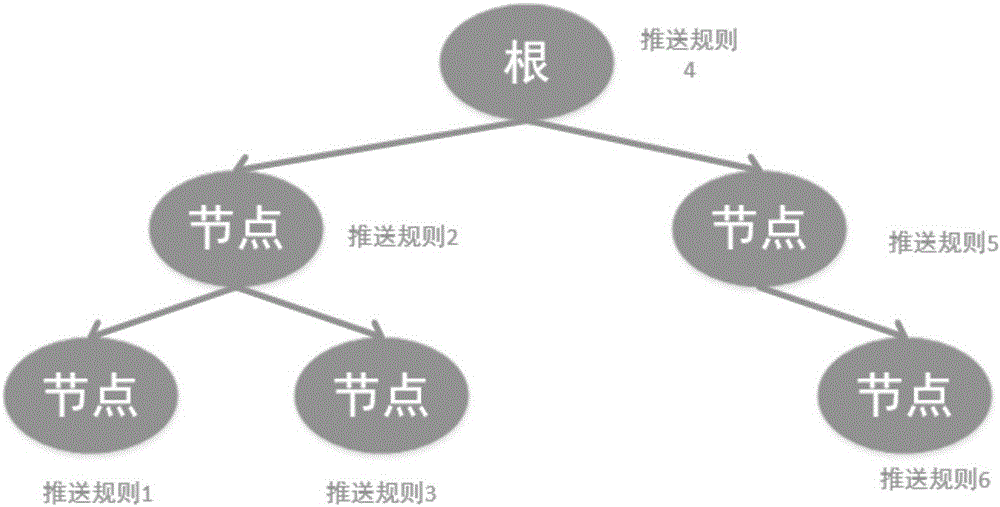
In computer science, a self-balancing (or height-balanced) binary search tree is any node-based binary search tree that automatically keeps its height (maximal number of levels below the root) small in the face of arbitrary item insertions and deletions.
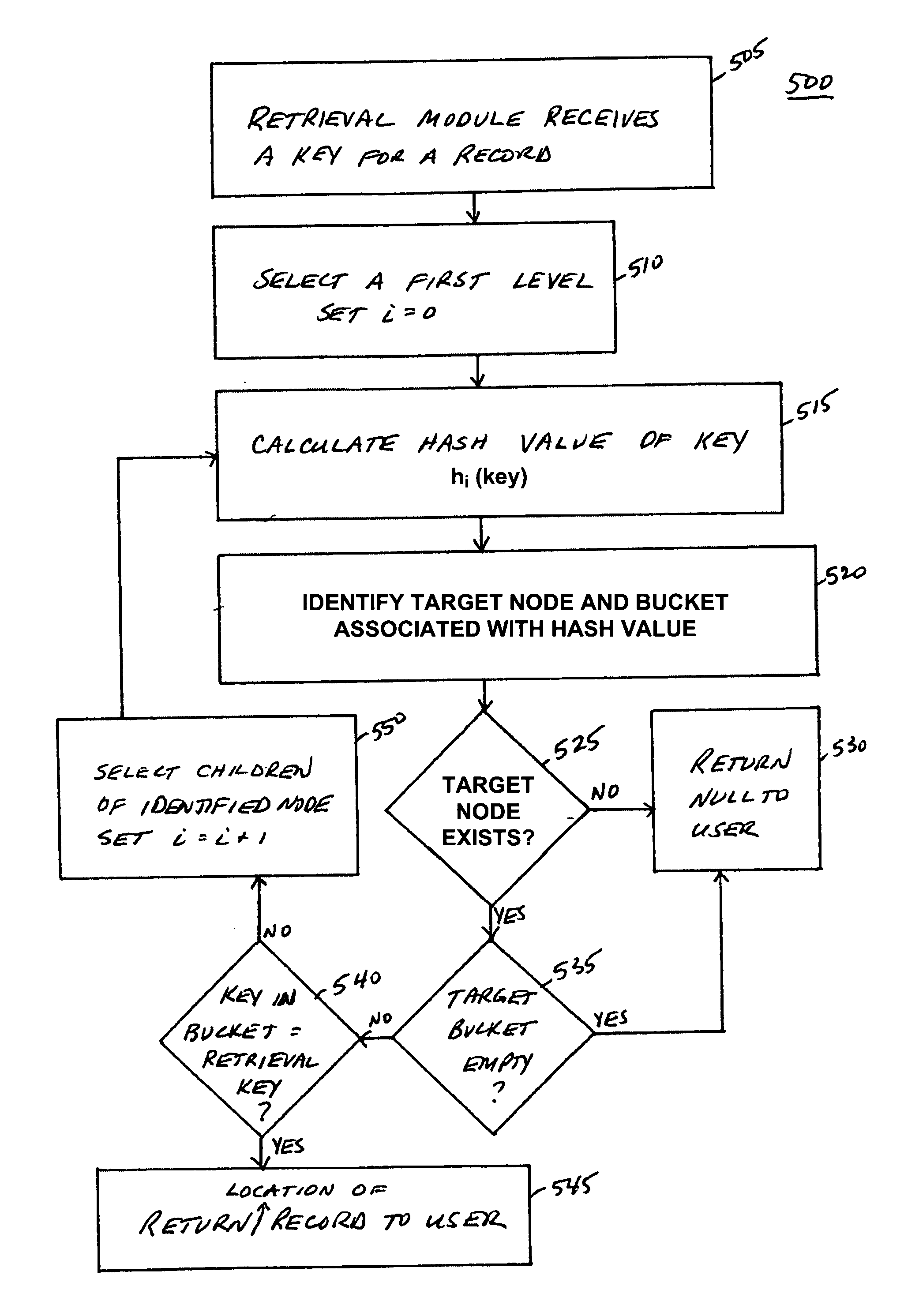
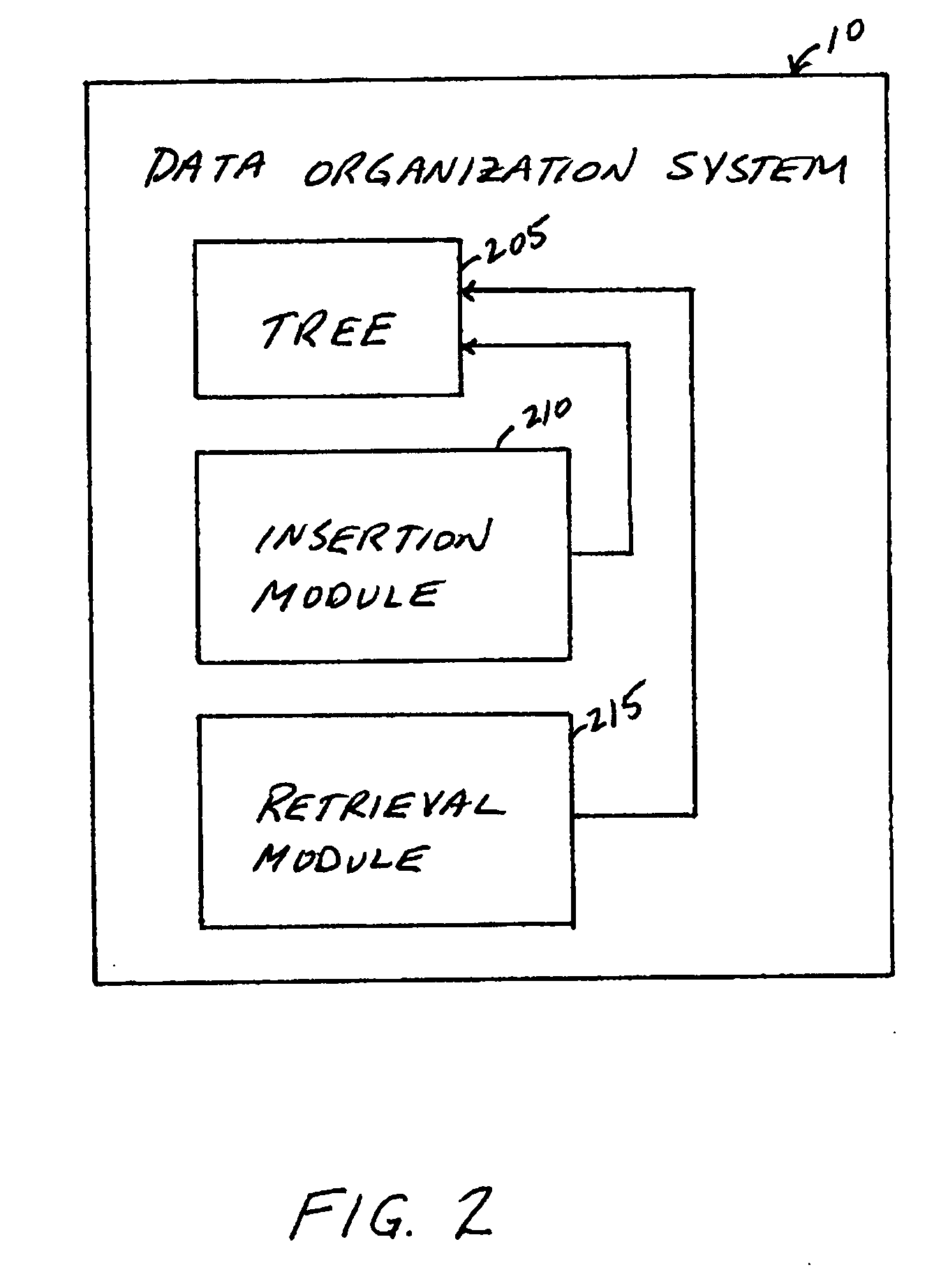
System, method, and service for organizing data for fast retrieval
InactiveUS20060218176A1Increase volumeDigital data information retrievalSpecial data processing applicationsUniversal hashingTheoretical computer science
A data organization system includes an index that offers fast retrieval of records and that protects records from logical modification. The index includes a balanced tree that grows from the root of the tree down to the leaves and requires no re-balancing. Each level in the tree includes a hash table. The hash table in each level in the tree can use a hash function that is different and independent from the hash function used in any other level in the tree. Alternatively, the hash table in each level in the tree can use a universal hash function. Possible locations of a record in the tree are fixed and determined by a hash function of a key of that record.
Owner:IBM CORP
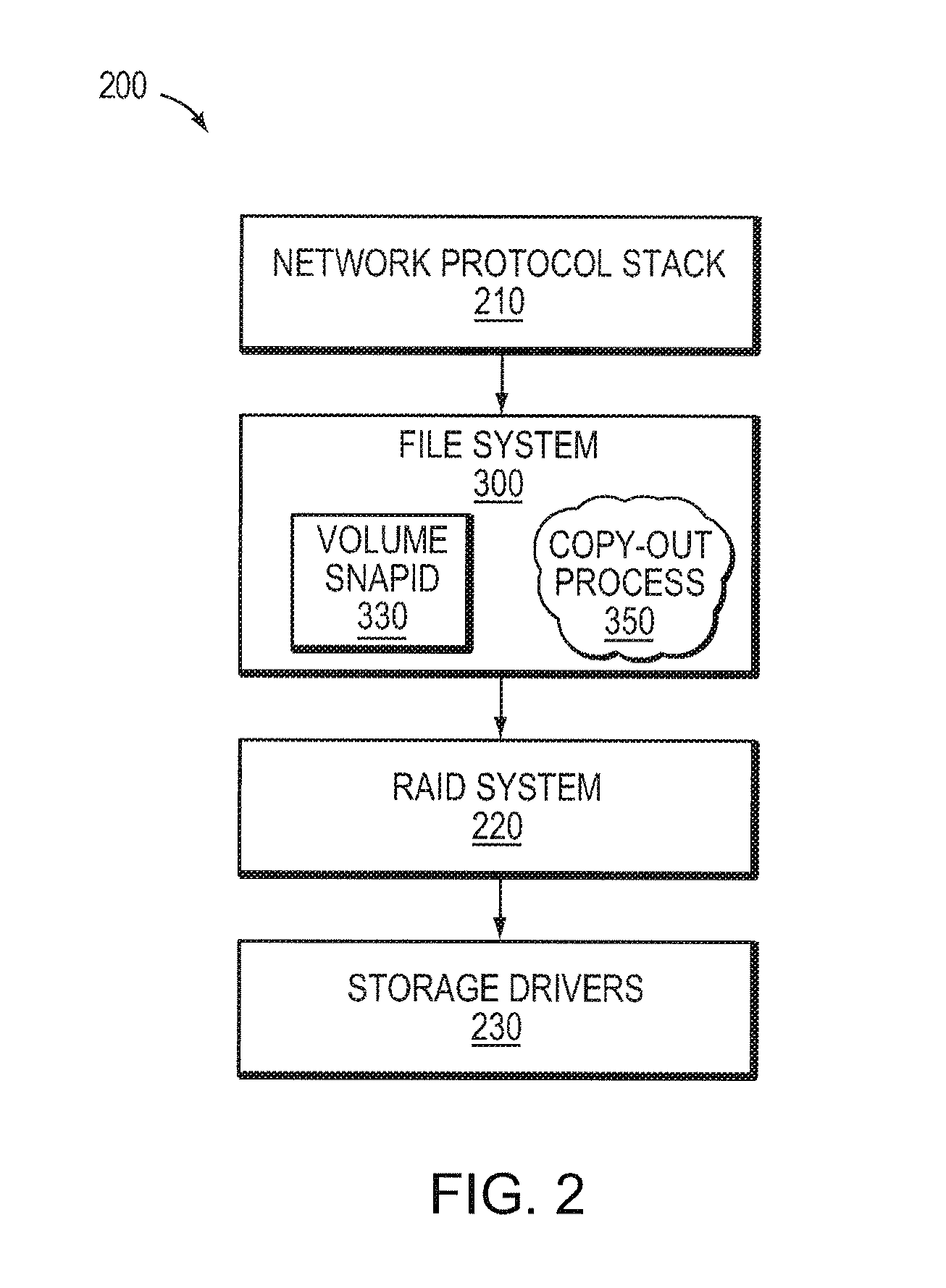
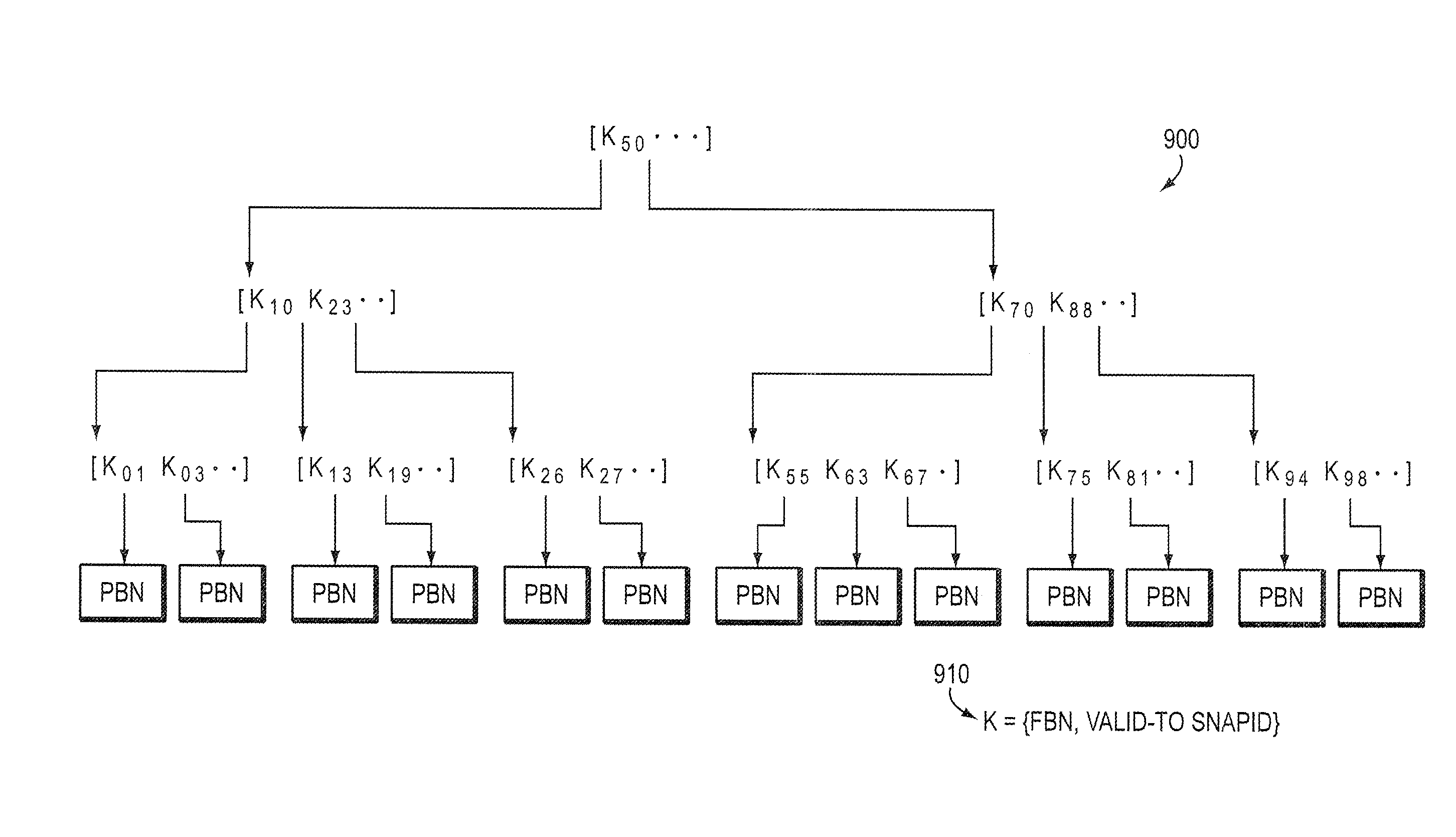
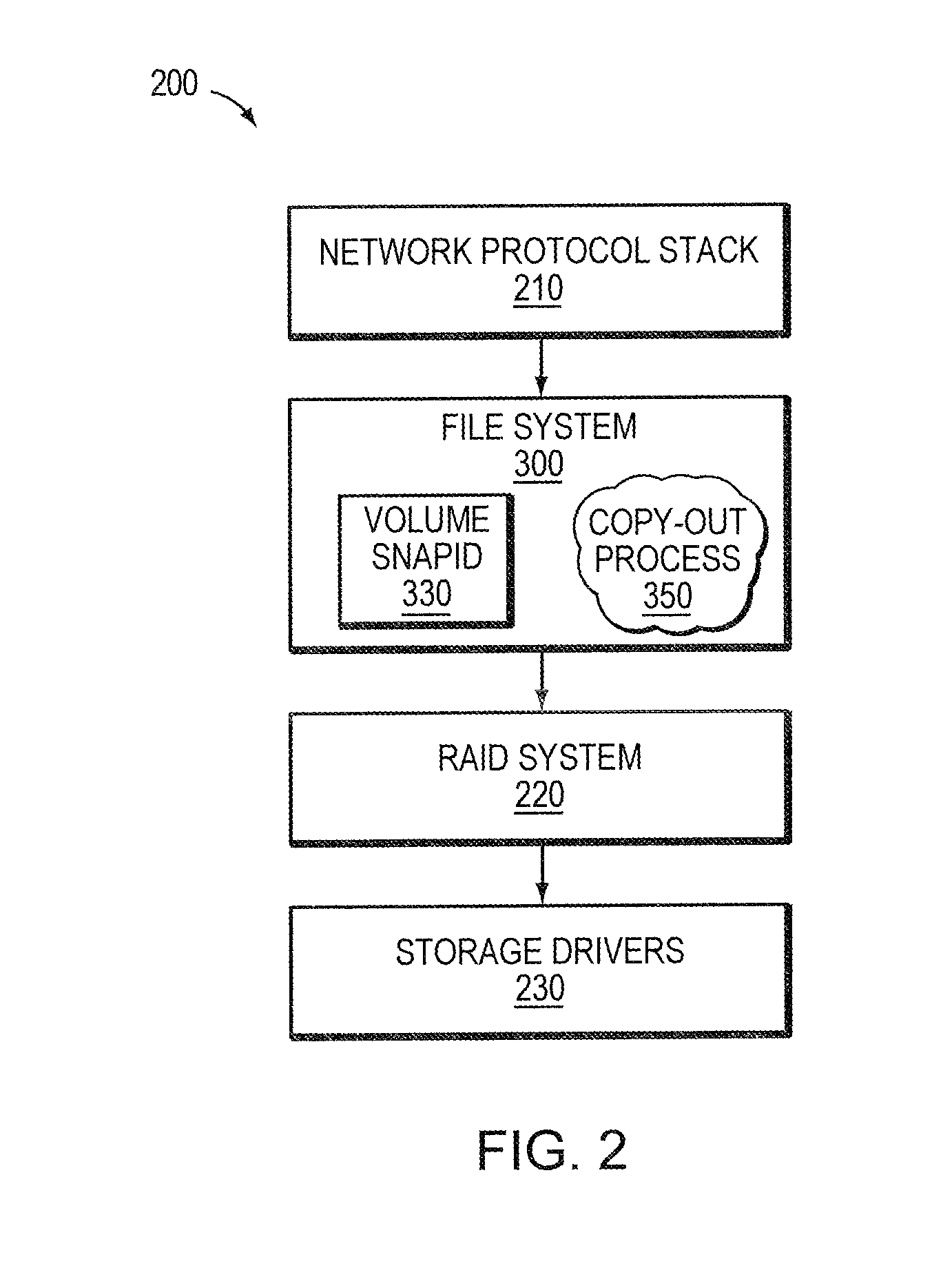
Identifying snapshot membership for blocks based on snapid
ActiveUS7849057B1Efficiently manage and organizeEasy to operateDigital data information retrievalDigital data processing detailsFile systemSelf-balancing binary search tree
An on-disk structure of a file system has the capability to efficiently manage and organize data containers, such as snapshots, stored on a storage system. A multi-bit, monotonically increasing, snapshot identifier (“snapid”) is provided that represents a snapshot and that increases every time a snapshot is generated for a volume of the storage system. The snapid facilitates organization of snapshot metadata within, e.g., a data structure used to organize metadata associated with snapshot data. In the illustrative embodiment, the data structure is a balanced tree structure configured to index the copy-out snapshot data blocks. The snapid is also used to determine which blocks belong to which snapshots. To that end, every block that is used in a snapshot has an associated “valid-to” snapid denoting the newest snapshot for which the block is valid. The oldest snapshot for which the block is valid is one greater than the valid-to field of the next older block at the same file block number.
Owner:NETWORK APPLIANCE INC
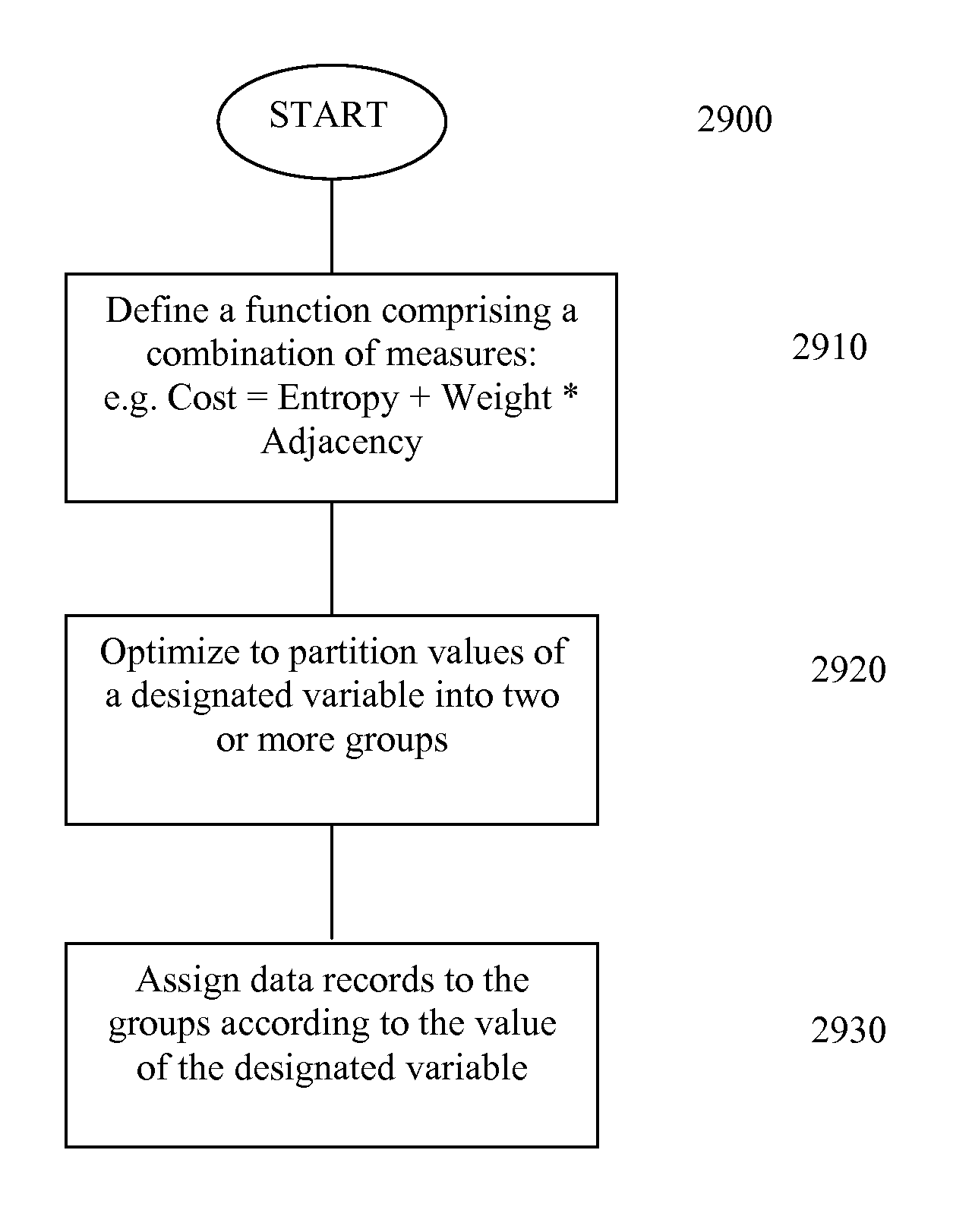
Method of partitioning data records
InactiveUS7272612B2Rapid and efficientMinimize timeData processing applicationsDigital data processing detailsSelf-balancing binary search treeMulti dimensional data
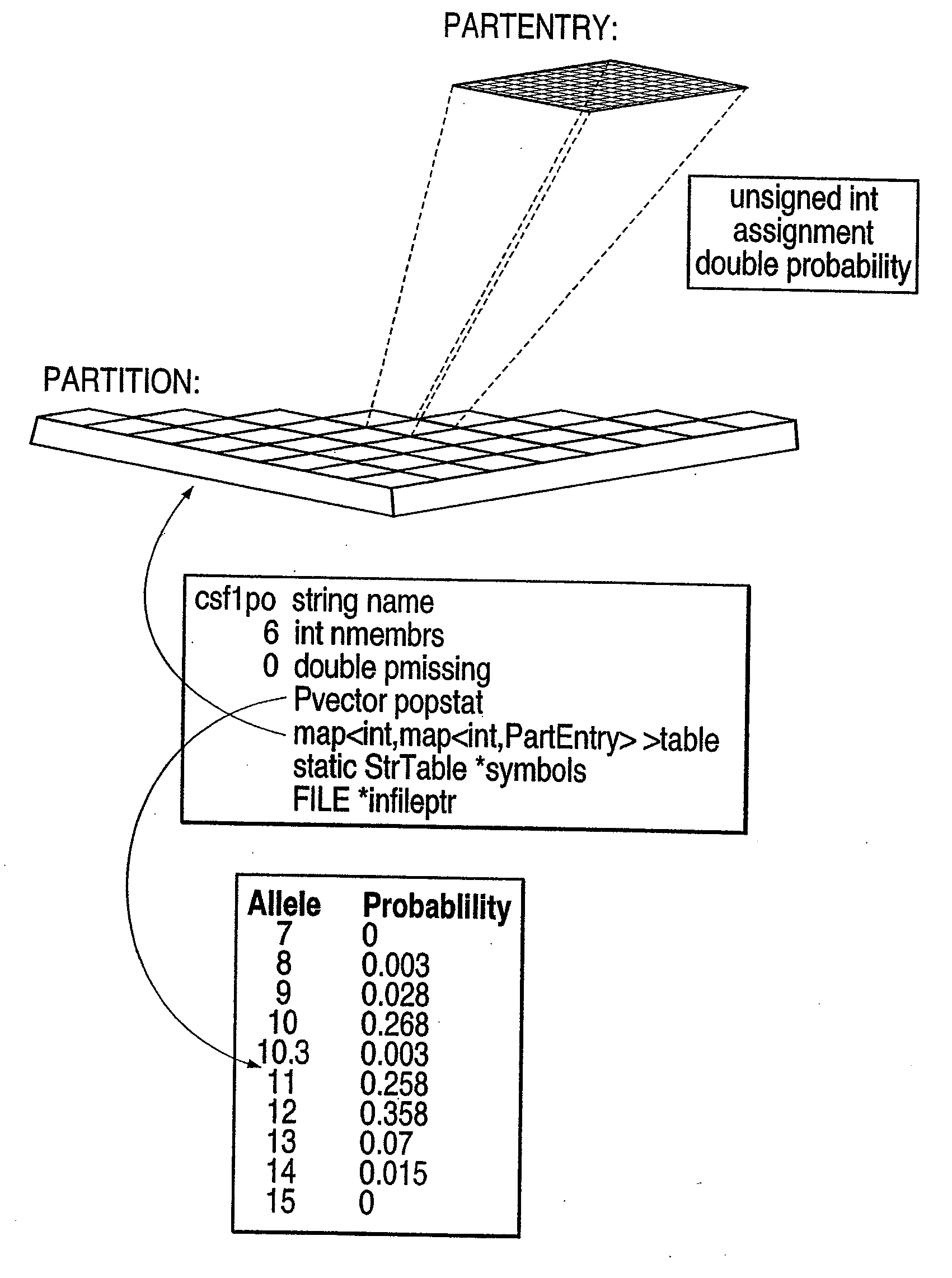
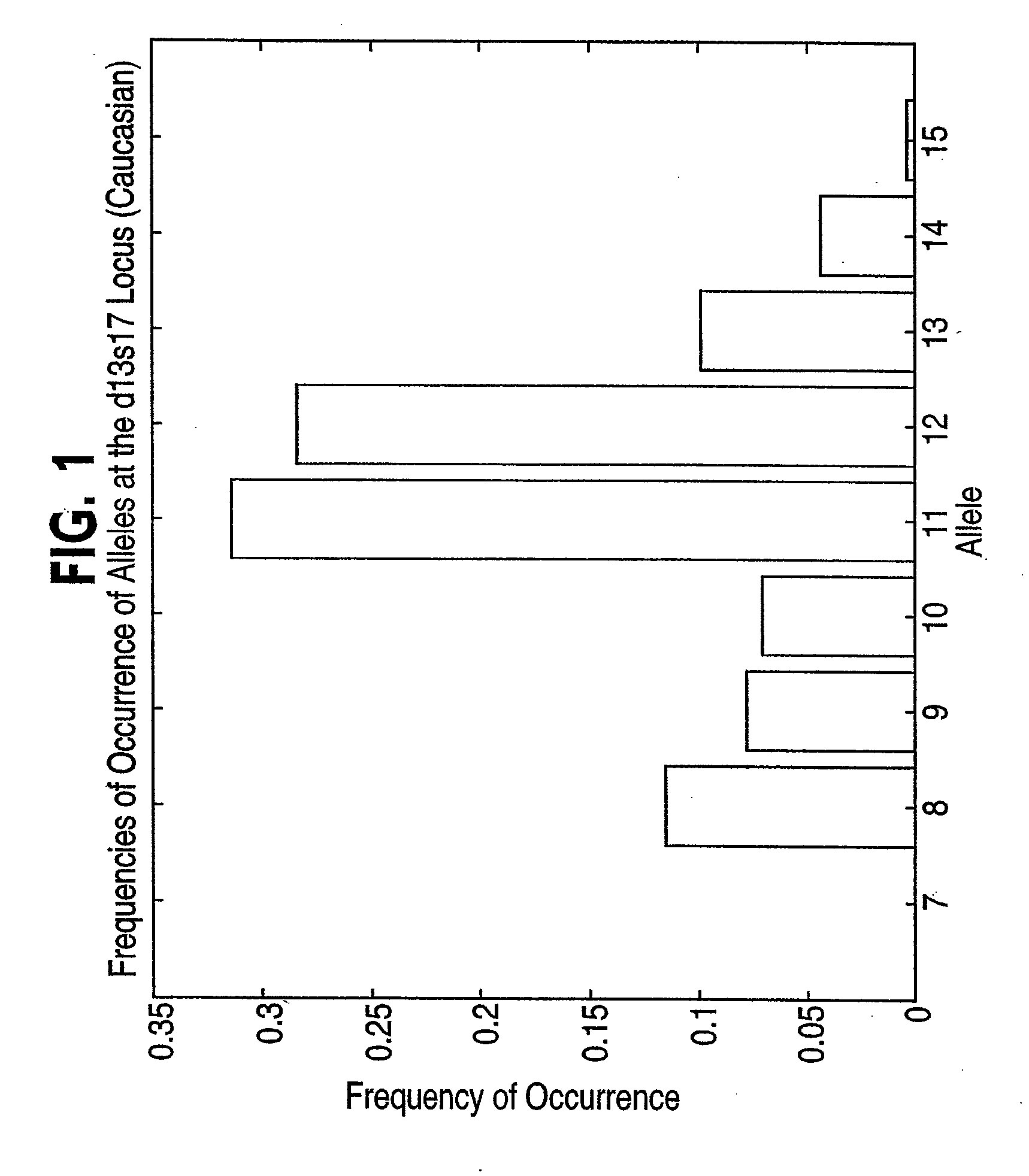
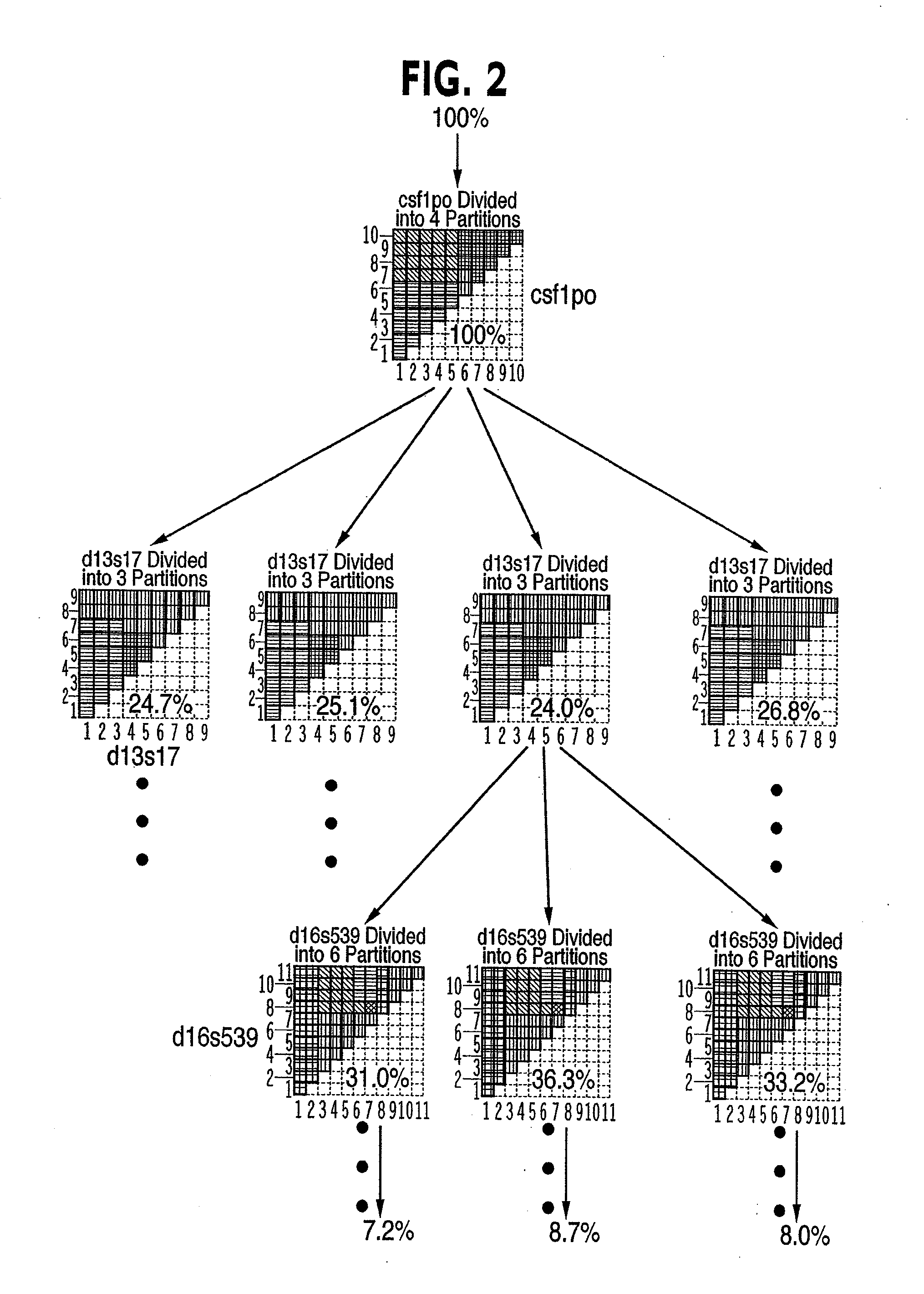
A tree-structured index to multidimensional data is created using occurring patterns and clusters within the data which permit efficient search and retrieval strategies in a database of DNA profiles. A search engine utilizes hierarchical decomposition of the database by identifying clusters of similar DNA profiles and maps to parallel computer architecture, allowing scale up past previously feasible limits. Key benefits of the new method are logarithmic scale up and parallelization. These benefits are achieved by identification and utilization of occurring patterns and clusters within stored data. The patterns and clusters enable the stored data to be partitioned into subsets of roughly equal size. The method can be applied recursively, resulting in a database tree that is balanced, meaning that all paths or branches through the tree have roughly the same length. The method achieves high performance by exploiting the natural structure of the data in a manner that maintains balanced trees. Implementation of the method maps to parallel computer architectures, allowing scale up to very large databases.
Owner:UNIV OF TENNESSEE RES FOUND
System and method for deferred rebalancing of a tree data structure
InactiveUS7539988B1Data processing applicationsDigital data information retrievalTheoretical computer scienceTree (data structure)
A method for executing operations upon a linked data structure having at least one element such that the time during which the linked data structure is locked is reduced. The method includes performing a first set of operation tasks in a first phase, the first set of operation tasks being operable to effect a first set of element state transitions. A second set of operation tasks is developed in the first phase, the second set of operation tasks being operable to effect a second set of element state transitions, the second set of element state transitions being distinct from the first set of element state transitions. The second set of operation tasks is performed in a second phase. The method finds particular implementation in the rebalancing of tree data structures.
Owner:FOUR JS DEV TOOLS
Data query method and device, storage medium and electronic equipment
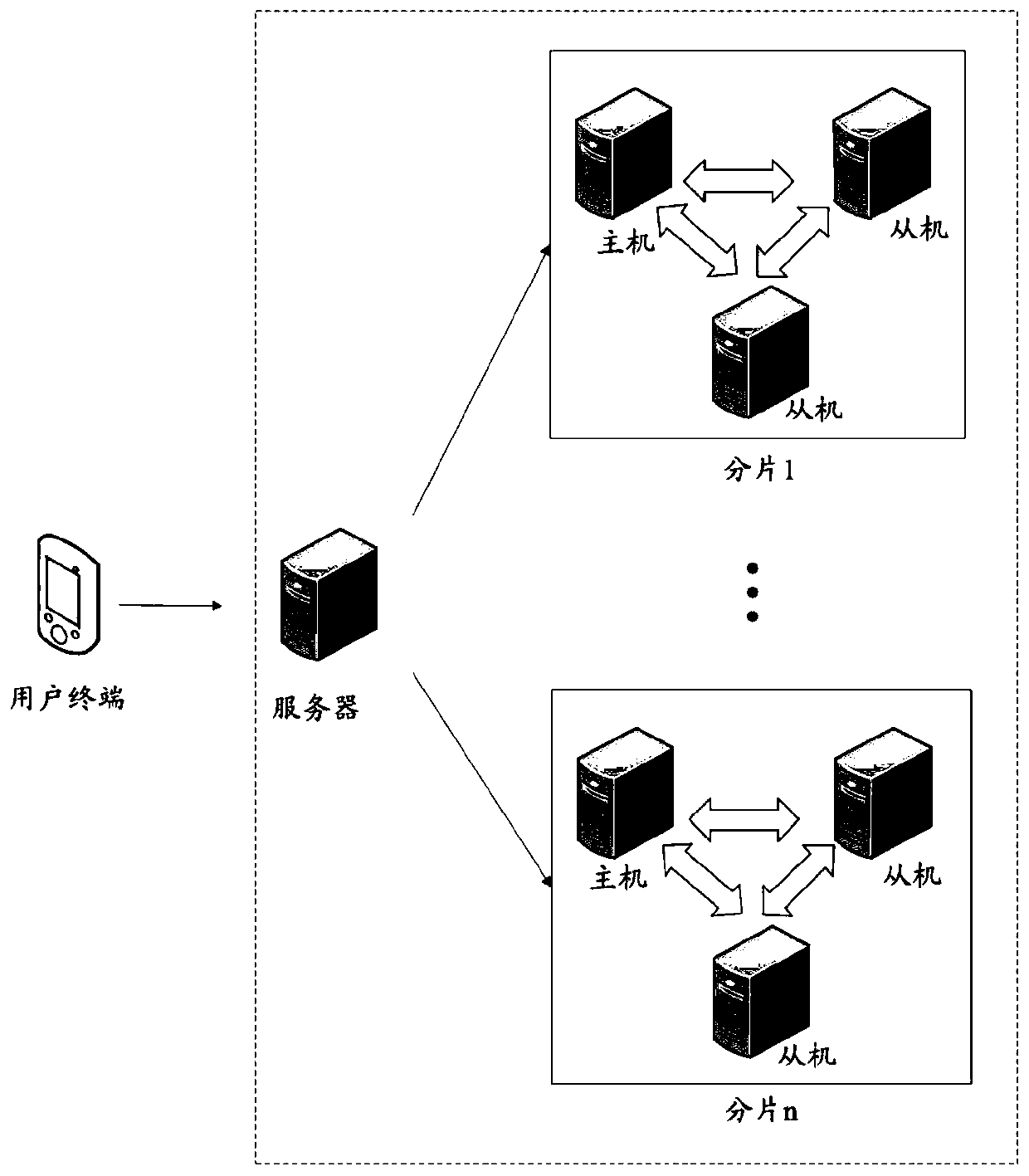
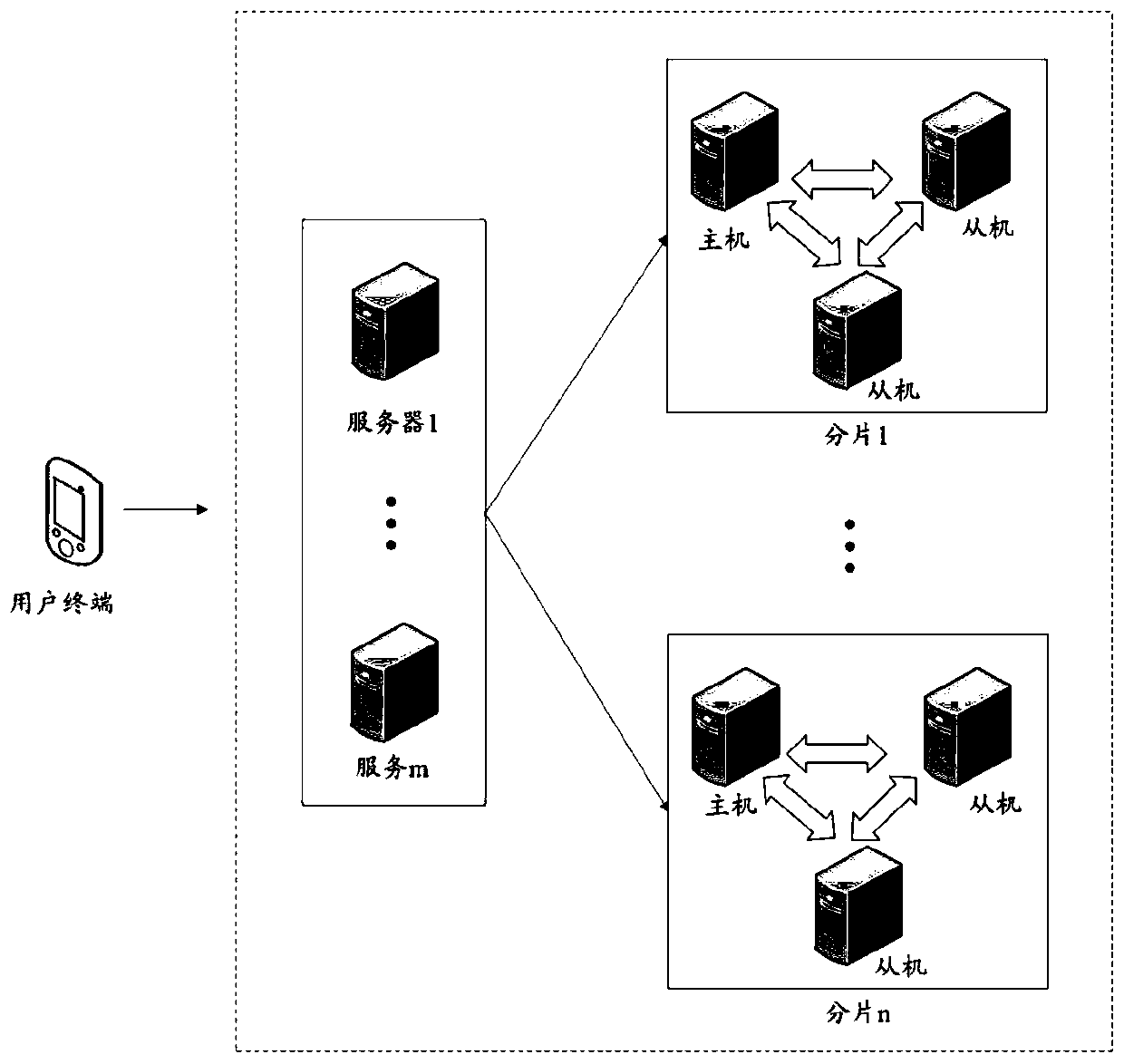
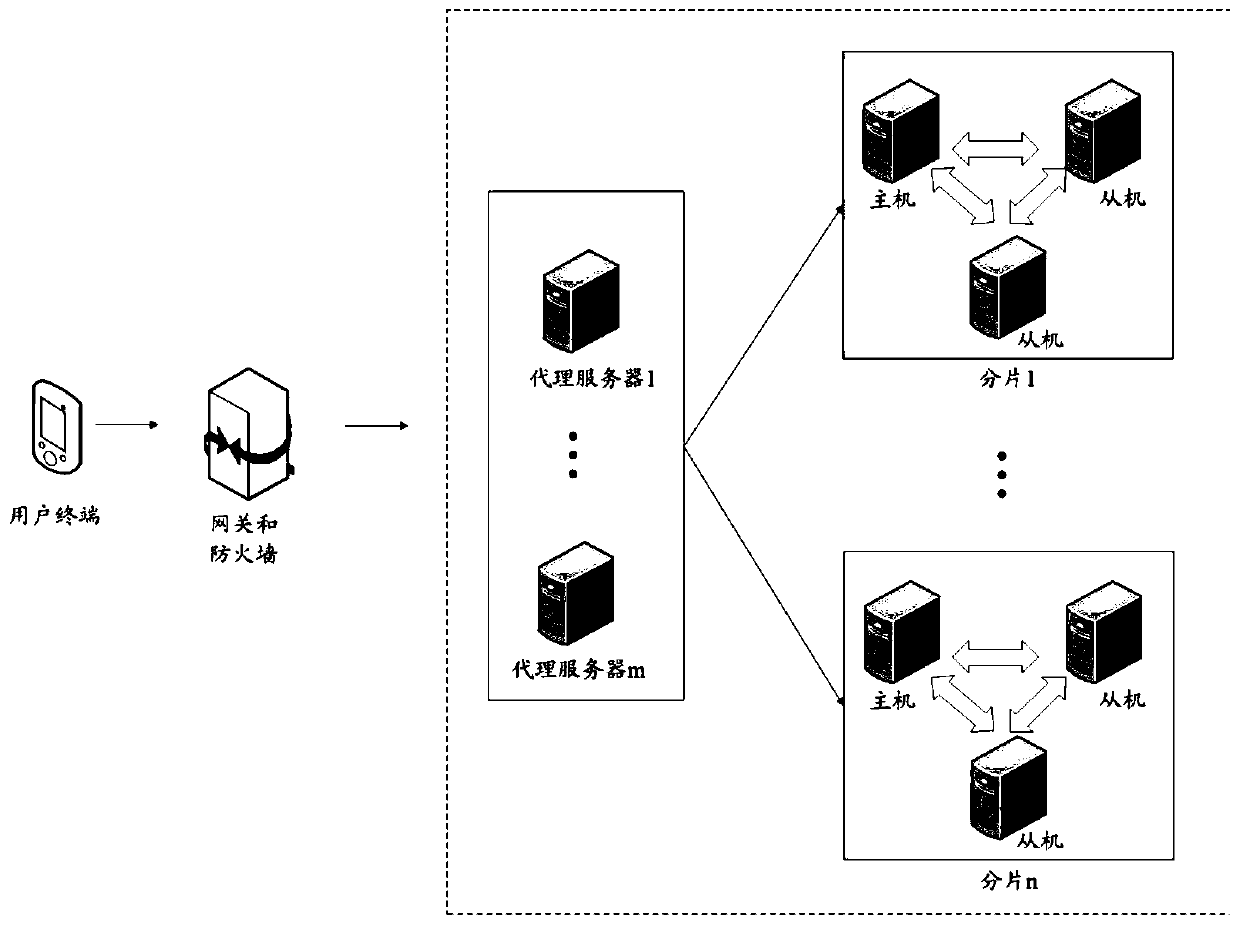
ActiveCN110704453AEfficient queryImprove query speedDatabase distribution/replicationSpecial data processing applicationsEngineeringTerm memory
The embodiment of the invention discloses a data query method and a device, a storage medium and electronic equipment. The data query method comprises the steps of when a data query request is received, determining a first sheet key and a query condition according to the data query request; determining a first fragment corresponding to the first fragment key from a fragment cluster, determining atarget balance tree matched with the query condition from a plurality of balance trees stored in the first fragment, and storing non-leaf nodes in a memory; searching the target balance tree layer bylayer to obtain a first index meeting a query condition and data record information associated with the first index from the leaf node; and obtaining first data corresponding to the first index from the first fragment according to the data record information, and responding to the data query request based on the first data to realize efficient query of the data.
Owner:TENCENT MUSIC ENTERTAINMENT TECH SHENZHEN CO LTD
Tree structured P2P overlay database system
InactiveUS20100250589A1Improve operating conditionsMinimize overheadDigital data processing detailsDatabase distribution/replicationSelf-healingCache algorithms
A system and methods to construct and maintain a balanced-tree overlay network are used to host distributed databases. As overlay nodes can detach from and re-attach to an overlay unpredictably, overlay protocols must maintain the overlay tree properly to minimize communication overheads associated with store and retrieval operations of the hosted databases. Unlike a DHT (distributed hash table) approach, the balanced-tree approach has the advantages of stabilizibility and provable correctness of the overlay protocols. Fast inquiry can be achieved by using a caching algorithm that allows each overlay node to keep track of data ranges stored in a neighboring set of nodes. Self-healing and load balancing protocols are also incorporated to enhance the performance and stability of the tree-structured overlay.
Owner:GRASSTELL NETWORKS
Radio frequency recognizing privacy authentication method for dynamic cryptographic key update based on rarefaction tree
InactiveCN101256615AReduce overheadReduce storage overheadDigital data authenticationSensing record carriersRfid authenticationSystem maintenance
The invention relates to a radio frequency identification technology and discloses a method for privacy authentication of radio frequency identification based on dynamic key update of sparse tree, which comprises the following steps that: system initialization step, a read-write machine generates the key of each label stored by the sparse key tree; label identification step, the read-write machine sends an authentication request to the label, the label computes and sends the authentication information to the read-write machine, and the read-write machine identifies the label after receiving the authentication information; key updating step, after the label identification is finished, the read-write machine updates the key tree and sends the synchronous updating authentication information to the label which updates the stored keys; system maintenance step, once the label joins in or level RFID system, the read-write machine maintains the system sparse key tress. The invention is able to efficiently resist various passive and active attacks at present, and in contrast with the RFID authentication method based on the balance tree structure, greatly reduces the storage expense at the label end.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
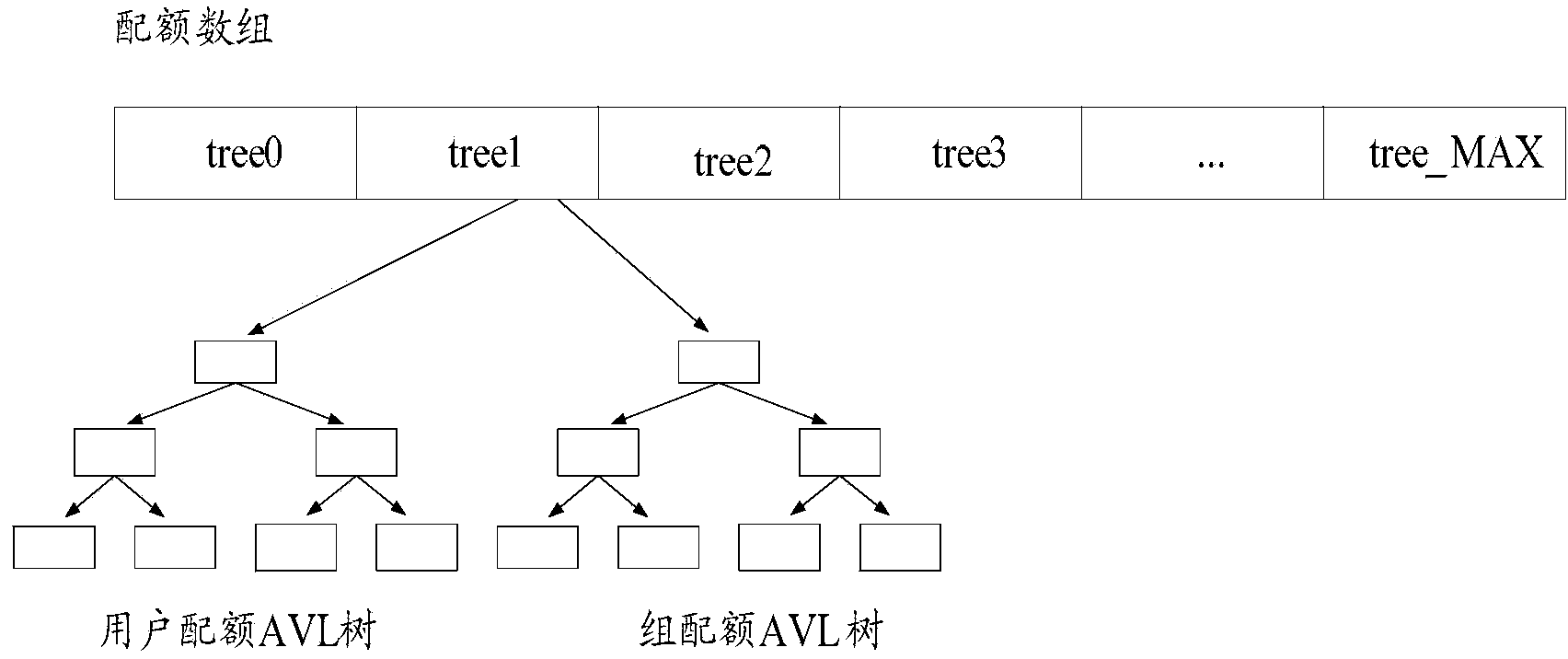
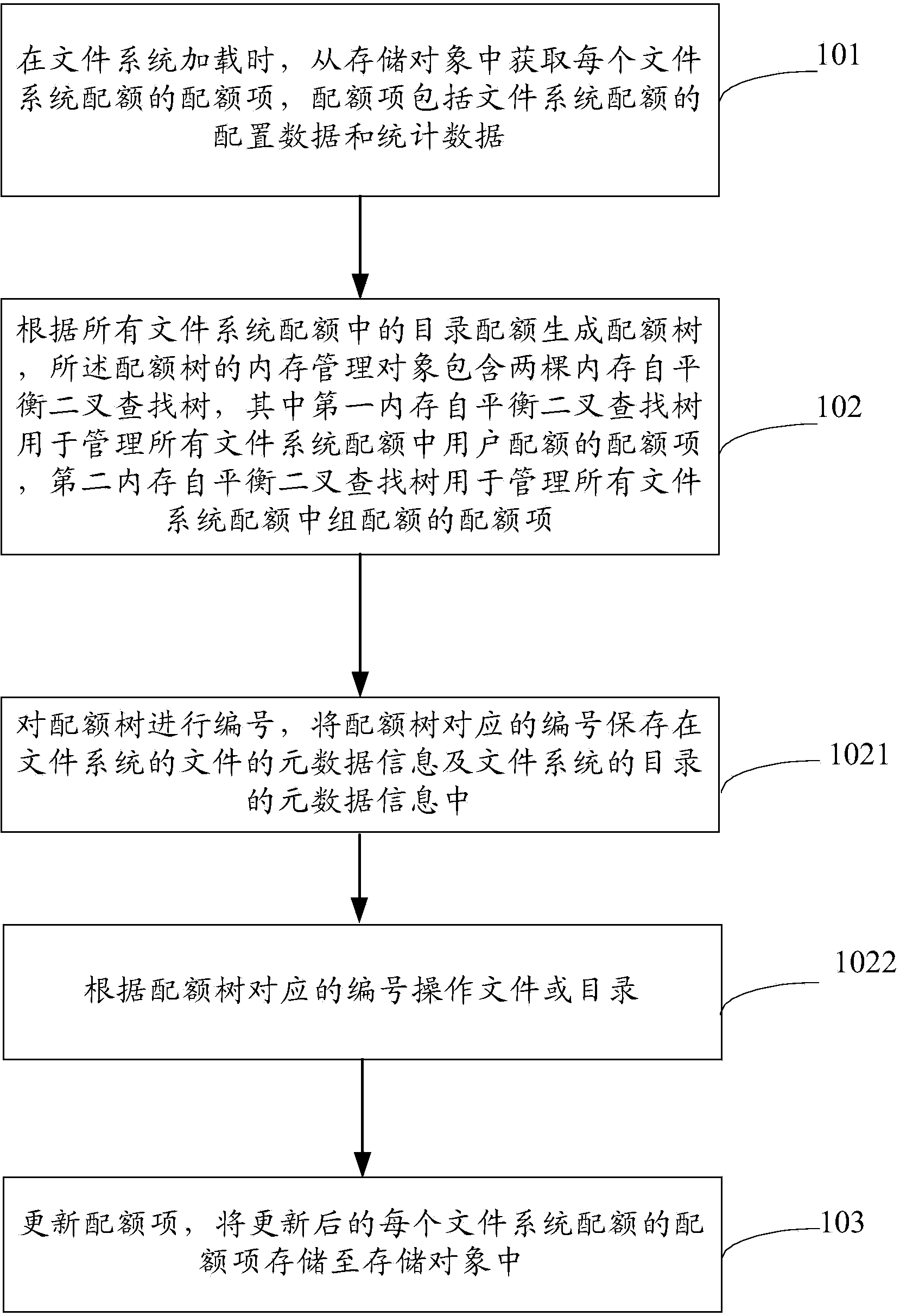
File system quota managing method, device and system
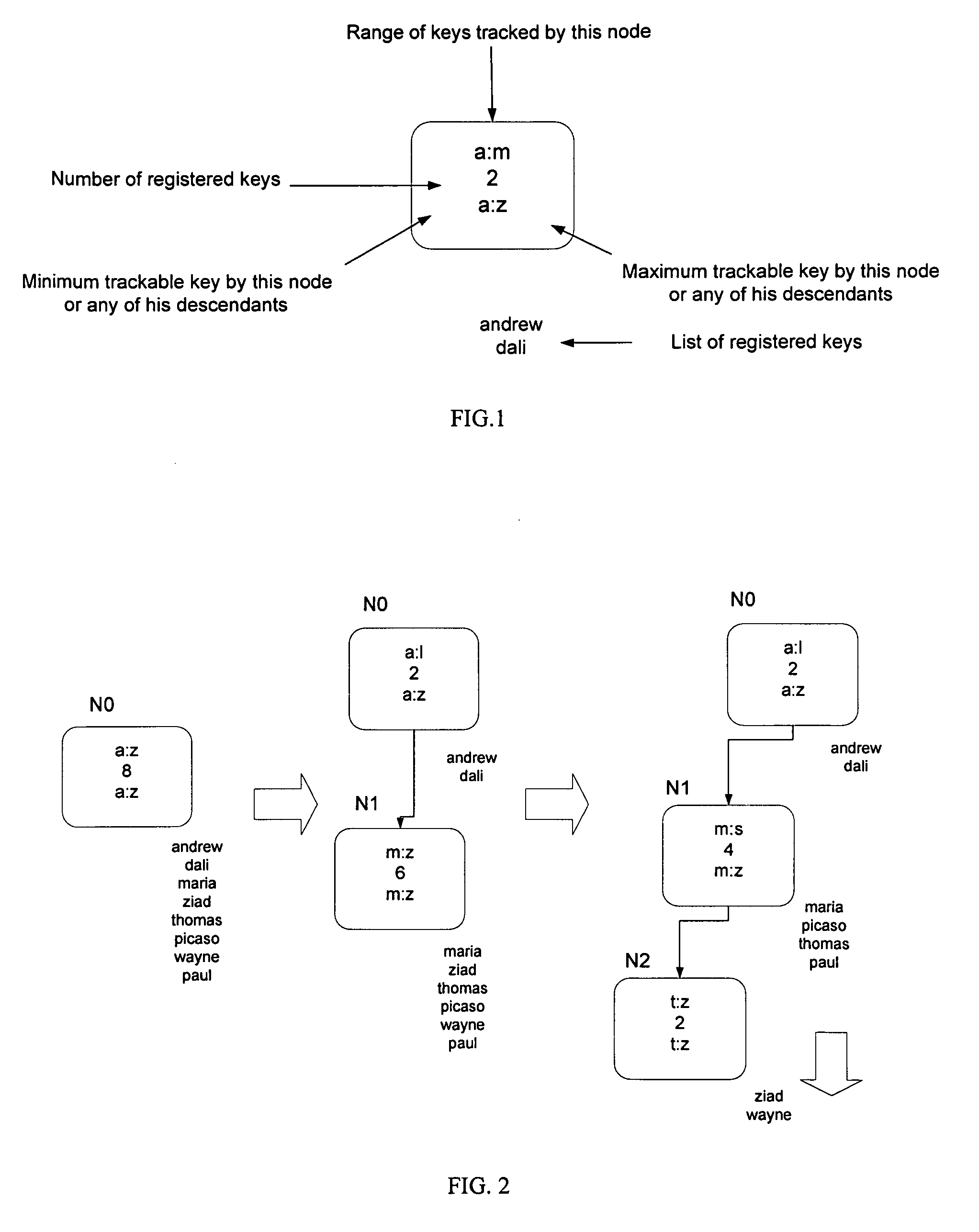
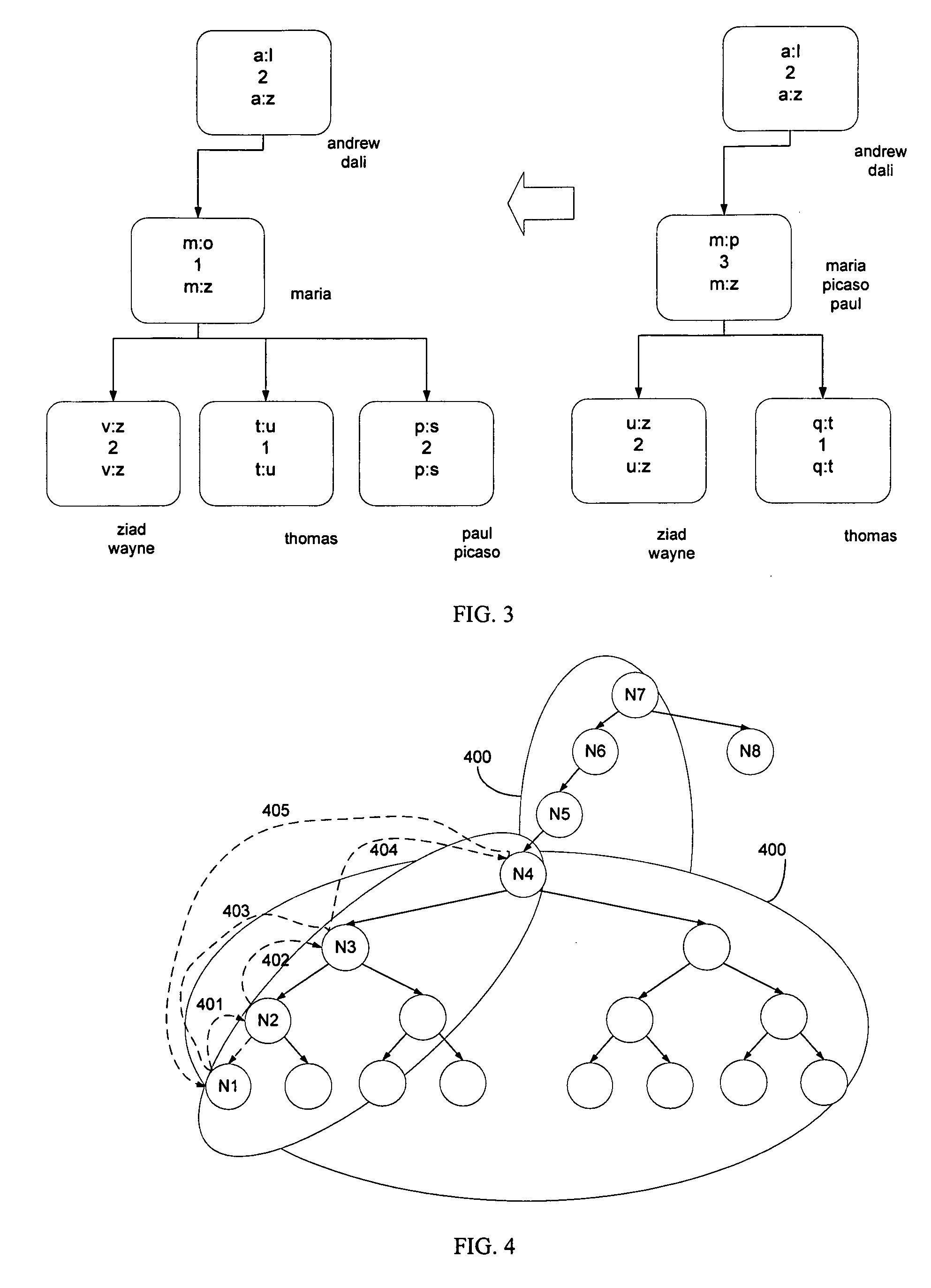
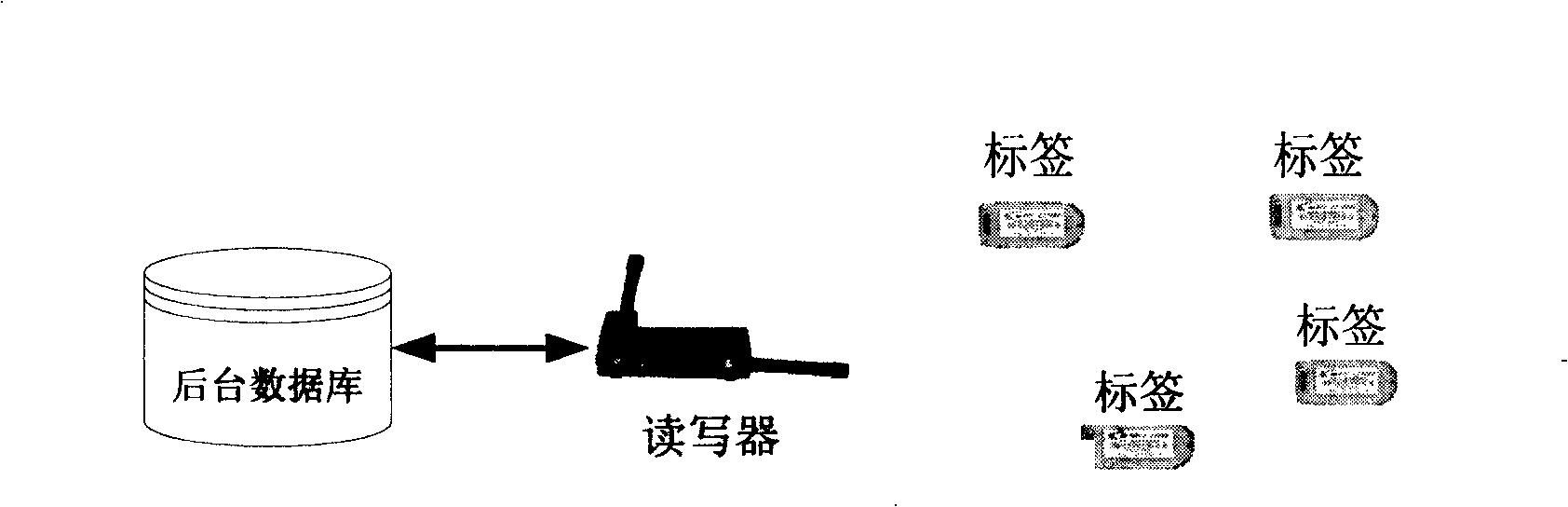
ActiveCN103559231AImprove operational efficiencyQuota management is easyMemory loss protectionFile system functionsFile systemSelf-balancing binary search tree
The embodiment of the invention discloses a file system quota managing method, device and system, is applied to the field of computers and is used for solving the defect of low quota operation efficiency in the prior art. The method comprises, when a file system is loaded, obtaining the quota entry of every file system quota from a storage object, wherein every quota entry contains the configuration data and the statistical data of the corresponding file system quota; generating a quota tree according to the lists of all the file system quotas, the memory management object of the quota tree comprises two memory self-balancing binary search trees, wherein the first memory self-balancing binary search tree serves for management of the quota entries of user quotas of all the file system quota, and the second memory self-balancing binary search tree serves for management of the quota entries of group quotas of all the file system quotas; updating the quota entries, and storing the updated quota entry of every file system quota in the storage object. The file system quota managing method, device and system is applicable to file system quota management.
Owner:HUAWEI TECH CO LTD
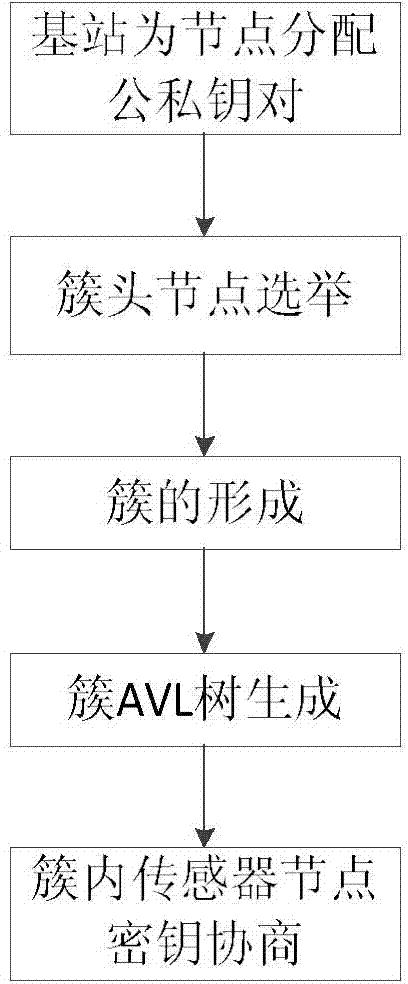
Wireless sensor network key management method
ActiveCN103929744AImprove securityAllow to addNetwork topologiesSecurity arrangementPasswordWireless sensor networking
The invention discloses a wireless sensor network key management method. The method comprises the steps that a base station distributes public and private key pairs to all sensor nodes according to set parameters, cluster head nodes are elected from all the sensor nodes, the elected cluster head nodes send information to the surrounding sensor nodes, the surrounding sensor nodes select the cluster head nodes of their own according to the information so that clusters can be formed, the base station generates a self-balancing binary search tree (AVL tree) of the in-cluster sensor nodes for all the clusters to generate the in-cluster sensor nodes, and the in-cluster sensor nodes inquire the information of the other sensor nodes according to the AVL tree, exchange information, mutually authenticate the legality of the public keys, and share the session keys after the authenticating is successful. According to the method, the AVL tree mode is utilized for storing the public keys and the identity information, the searching time is shortened, and the consumption is reduced; an elliptical curve password system is utilized for achieving key distribution and management, the higher safety of the network can be ensured, and the calculation expenditure can be reduced to the greatest extent.
Owner:SOUTHEAST UNIV
Mass toll-ticket fast cross rearrangement based on memory
ActiveCN1897629AEfficient methodEfficient designTelephonic communicationSelection arrangementsAVL treeTheoretical computer science
The invention uses the memory multi level storage mechanism, the index technique of the digital search tree based on the binary balance tree (AVL tree)and the process of combining the compression technique based on the BCD code and the RLC(Run-Length Coding) algorithm with the cross and rearrange approach based on the time slice. Said multi level storage mechanism uses three -levels storage mechanism comprising a first level used as the widow of working set, a second level used as the compression and rearrange information and a third level used as the storage disc; the exchange between the first level and the second level is for encoding and decoding, and the data saving in first and second level is implemented using memory mapping approach; the index approach of the digital search tree based on the binary balance tree (AVL tree) is used for the cross and rearrangement.
Owner:LINKAGE SYST INTEGRATION
General and automatic approach to incrementally computing sliding window aggregates in streaming applications
InactiveUS20160012110A1Digital data information retrievalDigital data processing detailsSlide windowTheoretical computer science
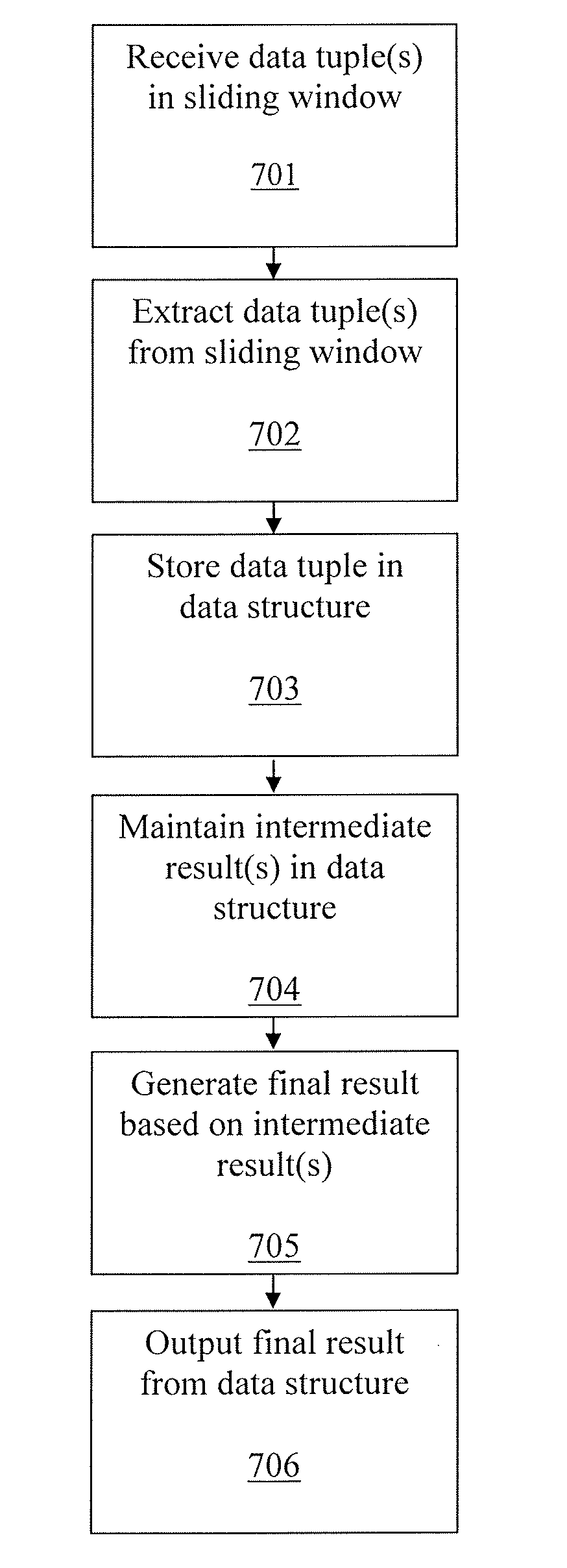
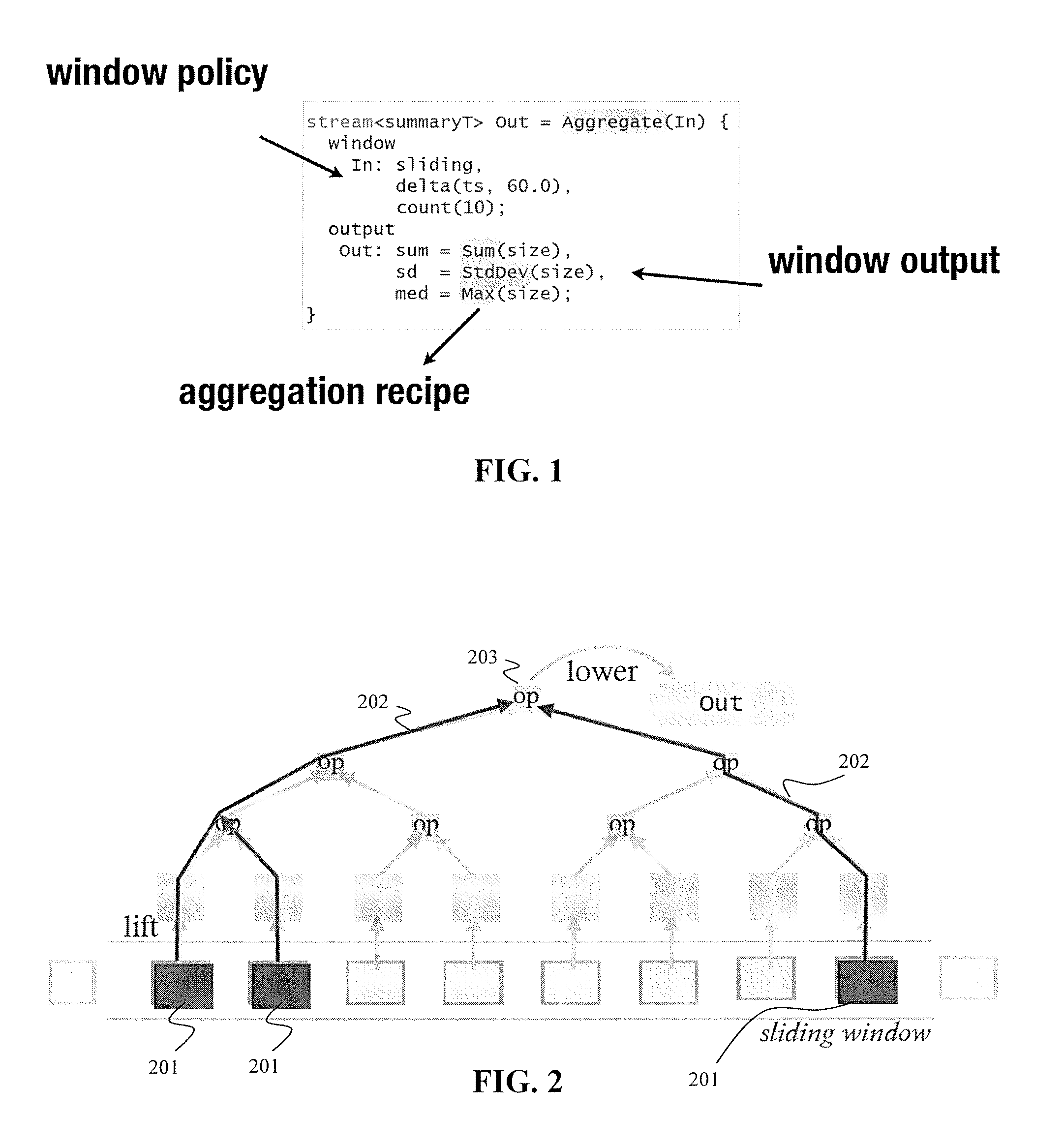
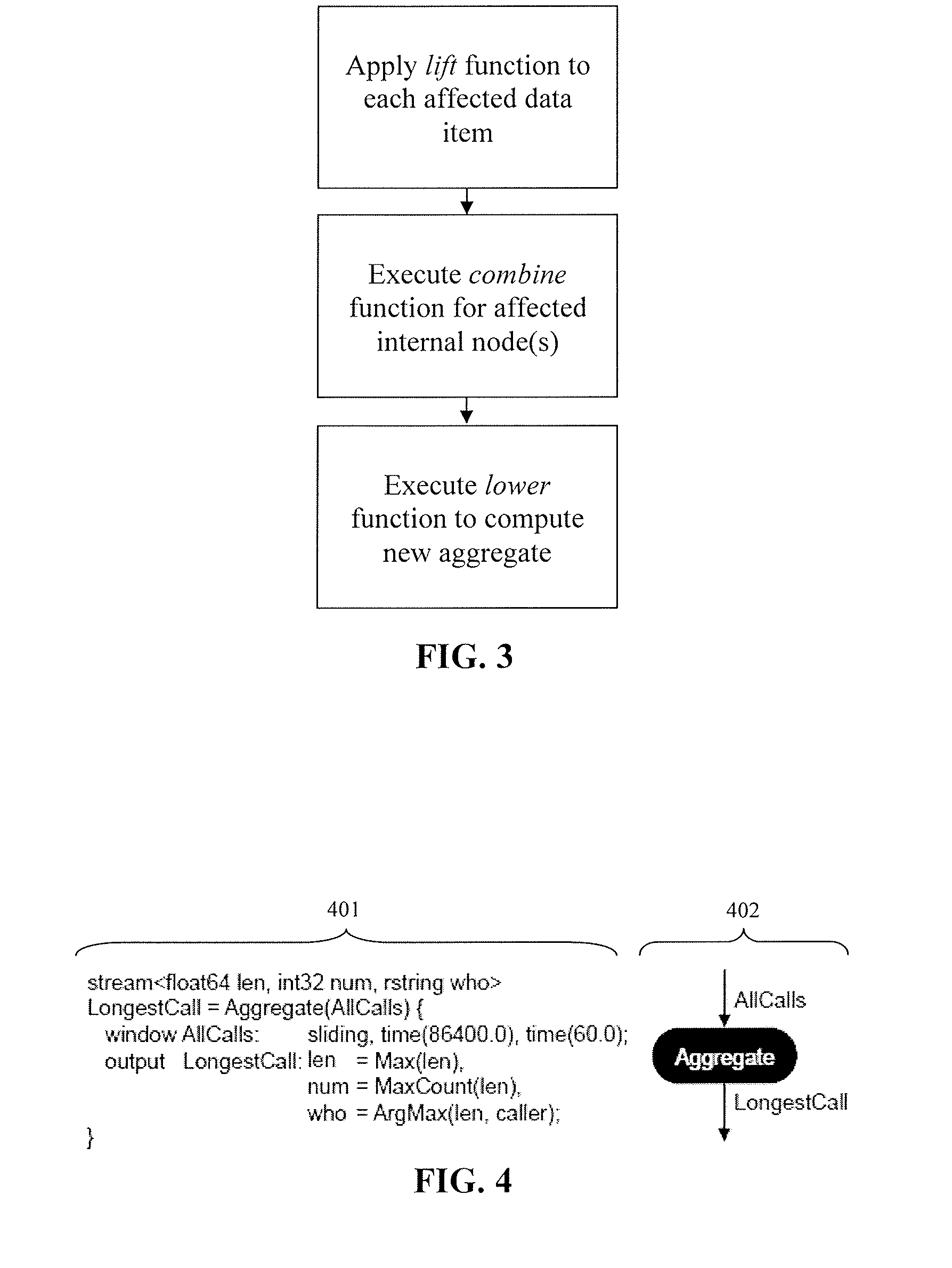
A method of incrementally computing an aggregate function of a sliding window in a streaming application includes receiving a plurality of data tuples in the sliding window, extracting at least one data tuple from the sliding window, and storing the at least one extracted data tuple in a data structure in a memory. The data structure is a balanced tree and the at least one data tuple is stored in leaf nodes of the balanced tree. The method further includes maintaining at least one intermediate result in at least one internal node of the balanced tree. The at least one intermediate result corresponds to a partial window aggregation. The method further includes generating a final result in the balanced tree based on the at least one intermediate result, and outputting the final result from the balanced tree. The final result corresponds to a final window aggregation.
Owner:IBM CORP
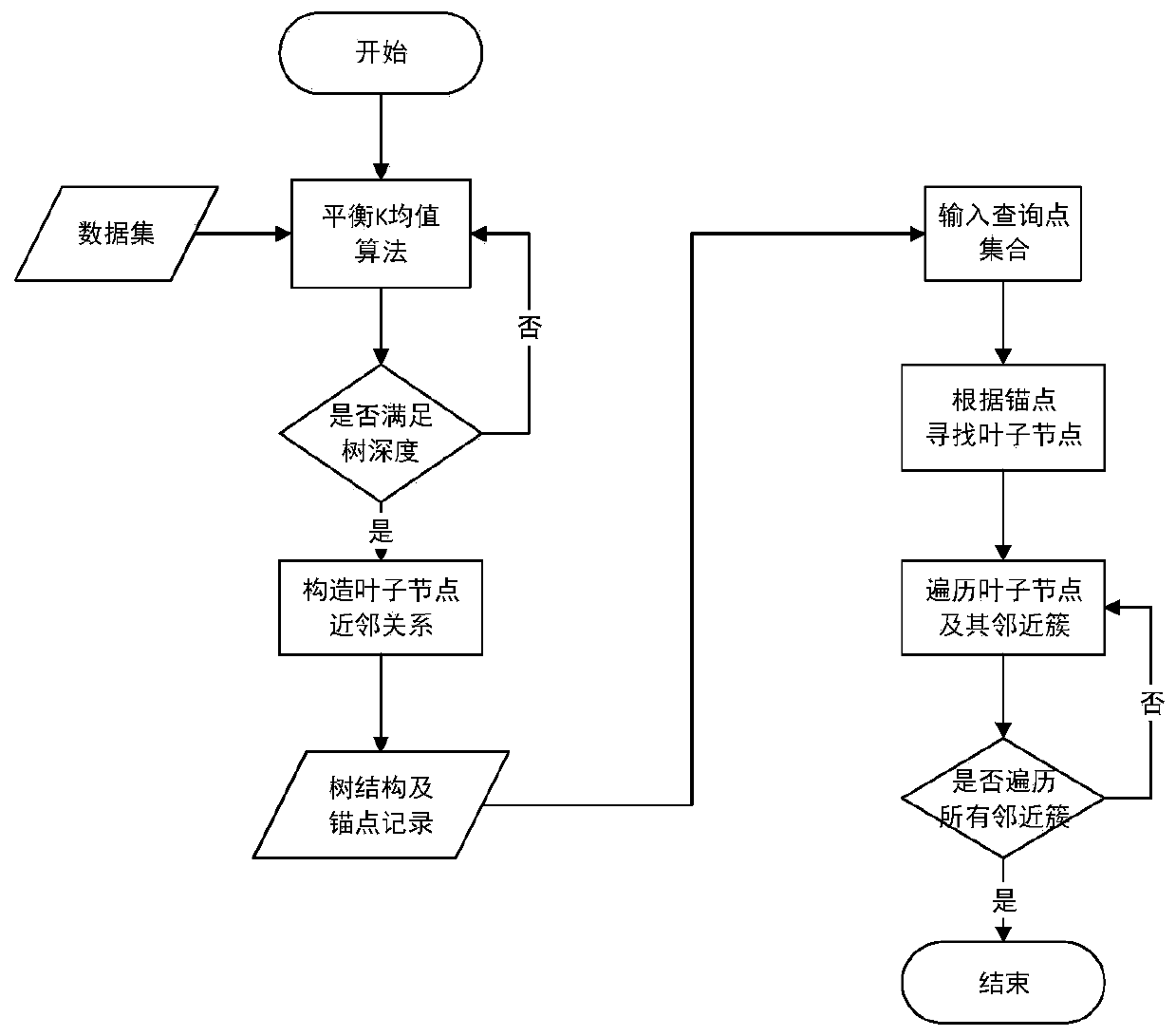
Fast approximate K neighbor method based on tree strategy and balanced K-means clustering
ActiveCN110070121AGuaranteed reliabilityGuaranteed reasonablenessCharacter and pattern recognitionData compressionSelf-balancing binary search tree
The invention provides a fast approximate K neighbor method based on a tree strategy and balanced K-means clustering, so as to improve the performance and speed of approximate K neighbor retrieval. The method comprises the following steps: firstly, constructing a balanced K-means tree through a balanced K-means clustering method, enabling data to be organized in a tree-shaped structure efficientlyand orderly, and realizing rapid positioning of any new sample data; then, utilizing an anchor positioning method and a neighbor cluster idea, and quickly finding a plurality of approximate neighborpoints, namely K neighbor points, of the new data sample through a balance tree. According to the method, the advantages of a tree-based K-nearest neighbor algorithm and a balanced K-means algorithm are taken into account at the same time, and the method can be applied to the fields of image recognition, data compression, mode recognition and classification, machine learning, document retrieval systems, statistics, data analysis and the like.
Owner:NORTHWESTERN POLYTECHNICAL UNIV
A non-structural grid nearest wall distance solving method based on a balanced KD tree
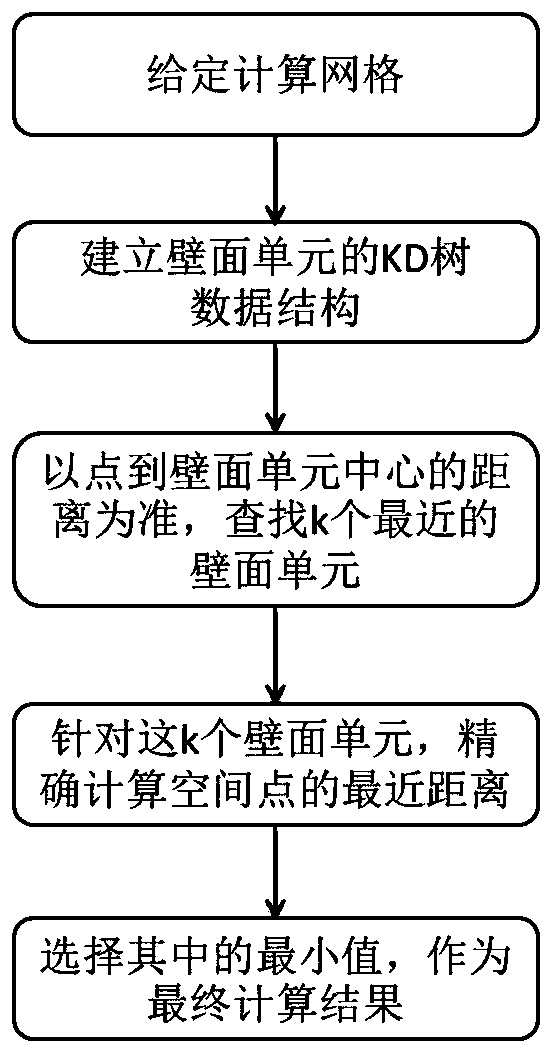
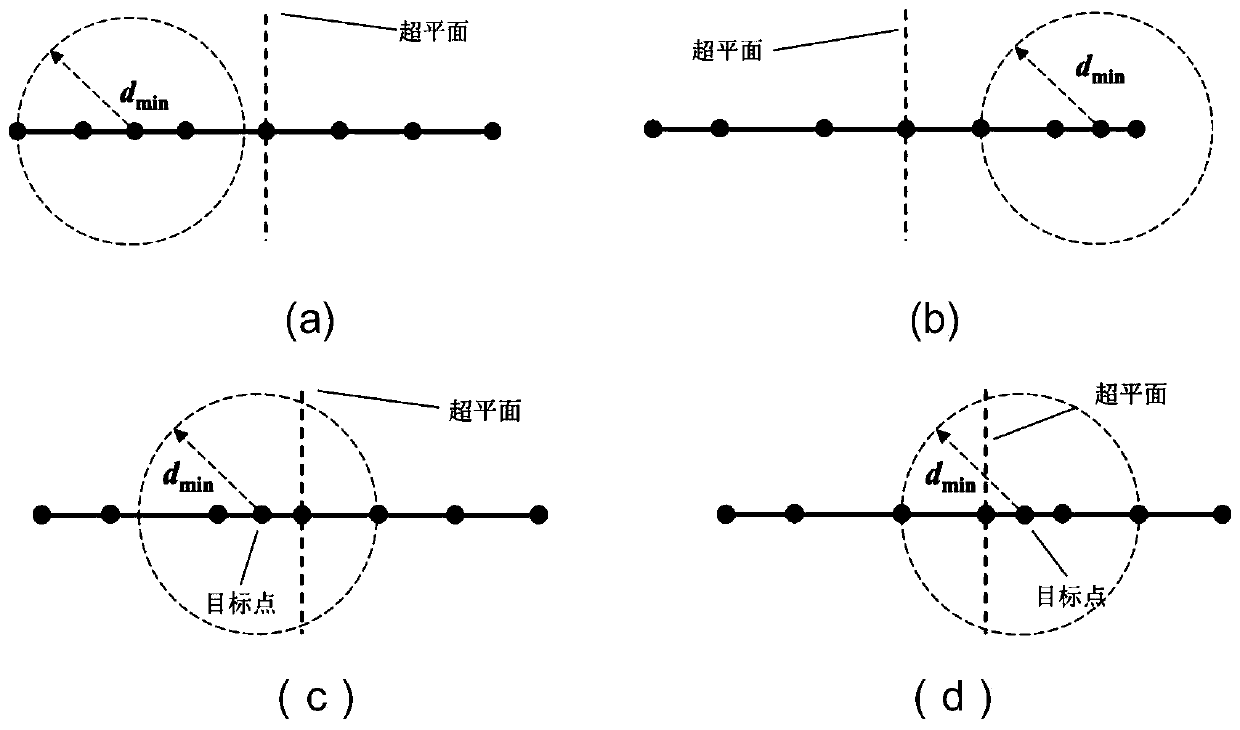
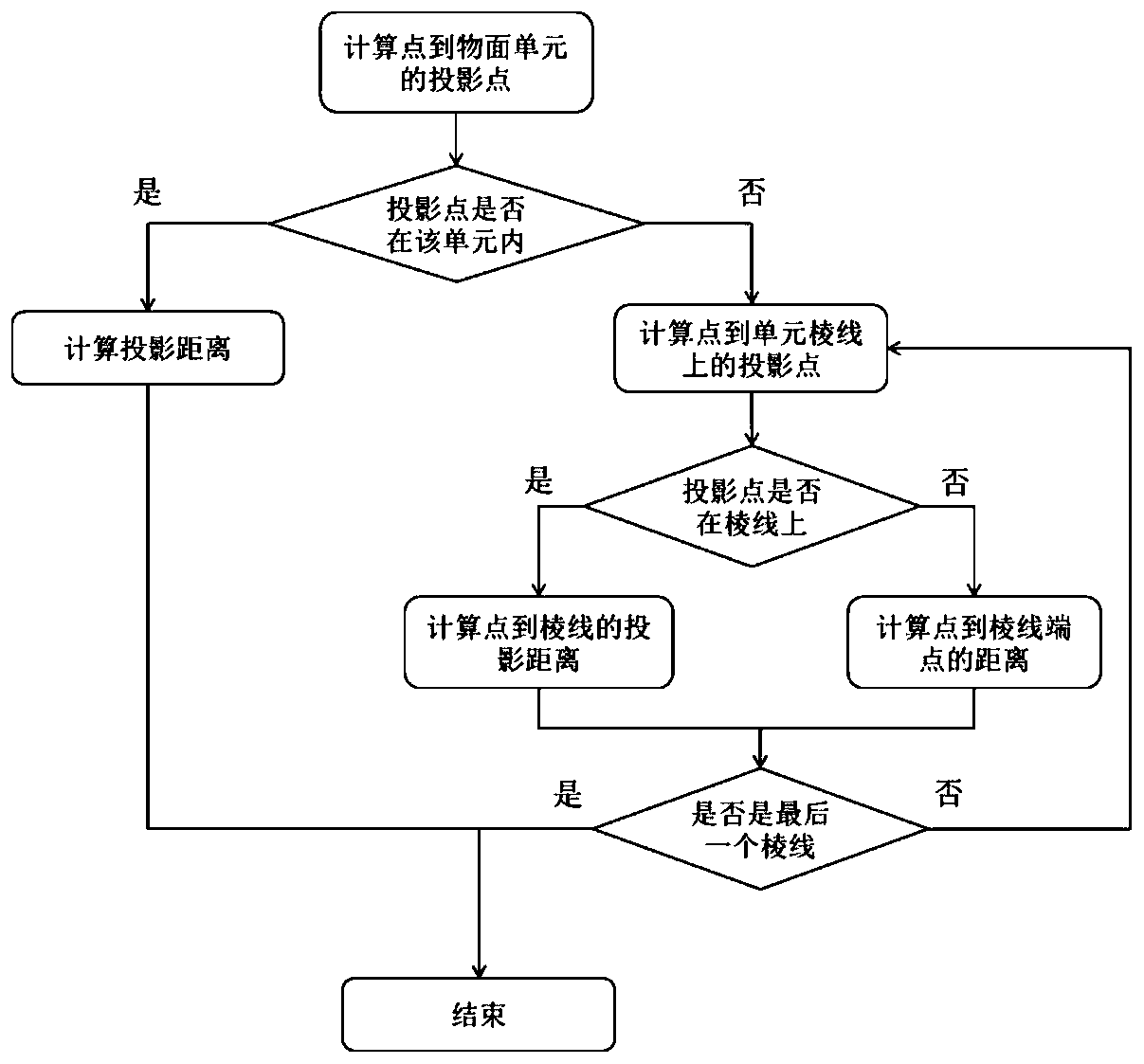
PendingCN109948002AGuaranteed solution accuracyImprove solution efficiencyOther databases indexingOther databases queryingTree (data structure)Time complexity
The invention discloses a non-structural grid nearest wall surface distance solving method based on a balanced KD tree. The method comprises the following steps: 1) establishing a balanced KD tree structure according to a central point of a wall surface unit; 2) for a certain target point in the space, searching k nearest wall surface units from the KD tree structure by taking the distance from the target point to the central point of the wall surface unit as an approximate nearest distance; and 3) aiming at the k wall surface units, accurately calculating the nearest distance between the target point and the k wall surface units, and selecting the minimum value as a calculation result. According to the method, the KD tree data structure of the object plane unit is established, and an optimized searching path and wall surface distance solving algorithm is adopted, so that the time complexity and the calculation amount of query are greatly reduced. According to the method, the calculation efficiency can be greatly improved on the premise of fully ensuring the calculation precision, and parallel calculation is easy to realize. Test results for thousands of thousands of magnitudes ofcalculation grids show that compared with a direct method, the method can shorten the calculation time by more than two orders of magnitudes.
Owner:AERODYNAMICS NAT KEY LAB
Method for realizing image retrieval by mining distinguishing features from multiple relevant pictures
InactiveCN105183746AImprove efficiencyEasy to digCharacter and pattern recognitionSpecial data processing applicationsImaging FeatureImage retrieval
The invention discloses a method for realizing image retrieval by mining distinguishing features from multiple relevant pictures. The method is characterized in that the method is finished by the generation of a flexible binary descriptor and feature matching on the basis of the binary descriptor. The flexible binary descriptor compares each dimension of an original floating-point type image feature with a corresponding reference value of each knot of a binary balance tree so as to convert the original floating-point type image feature into a binary form; and the feature matching firstly calculates similarity among features on the basis of the binary descriptor and then carries out normalization on the similarity scores of the features to successively select optimal-matching feature pairs, and the distinguishing features in the multiple relevant pictures can be found through the optimal-matching feature pairs. Although an amount of the distinguishing features is small, the distinguishing features represent the important visual content of the picture, the geometrical information of the picture is combined for retrieval, and therefore, a good retrieval result can be obtained.
Owner:XI AN JIAOTONG UNIV
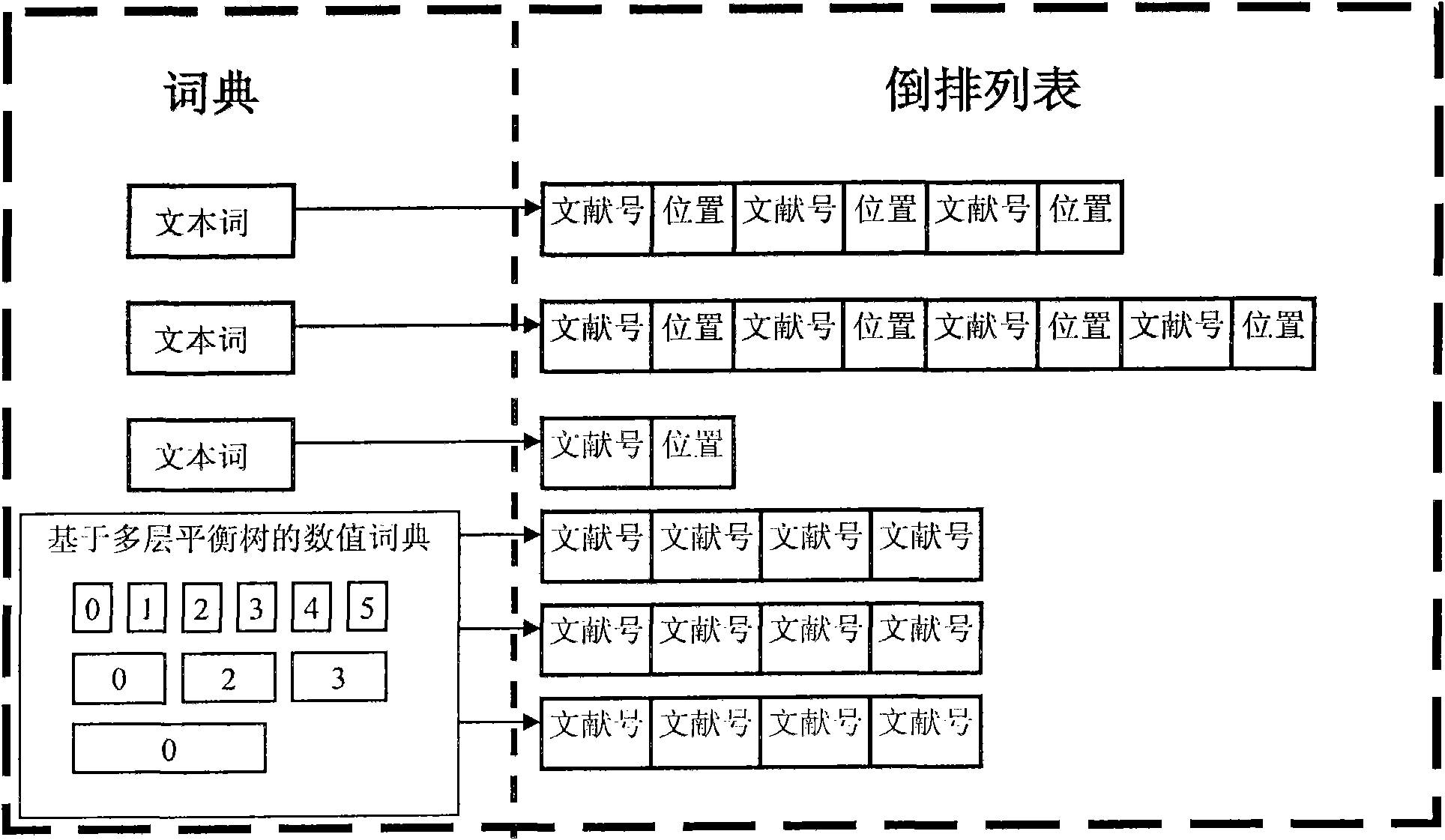
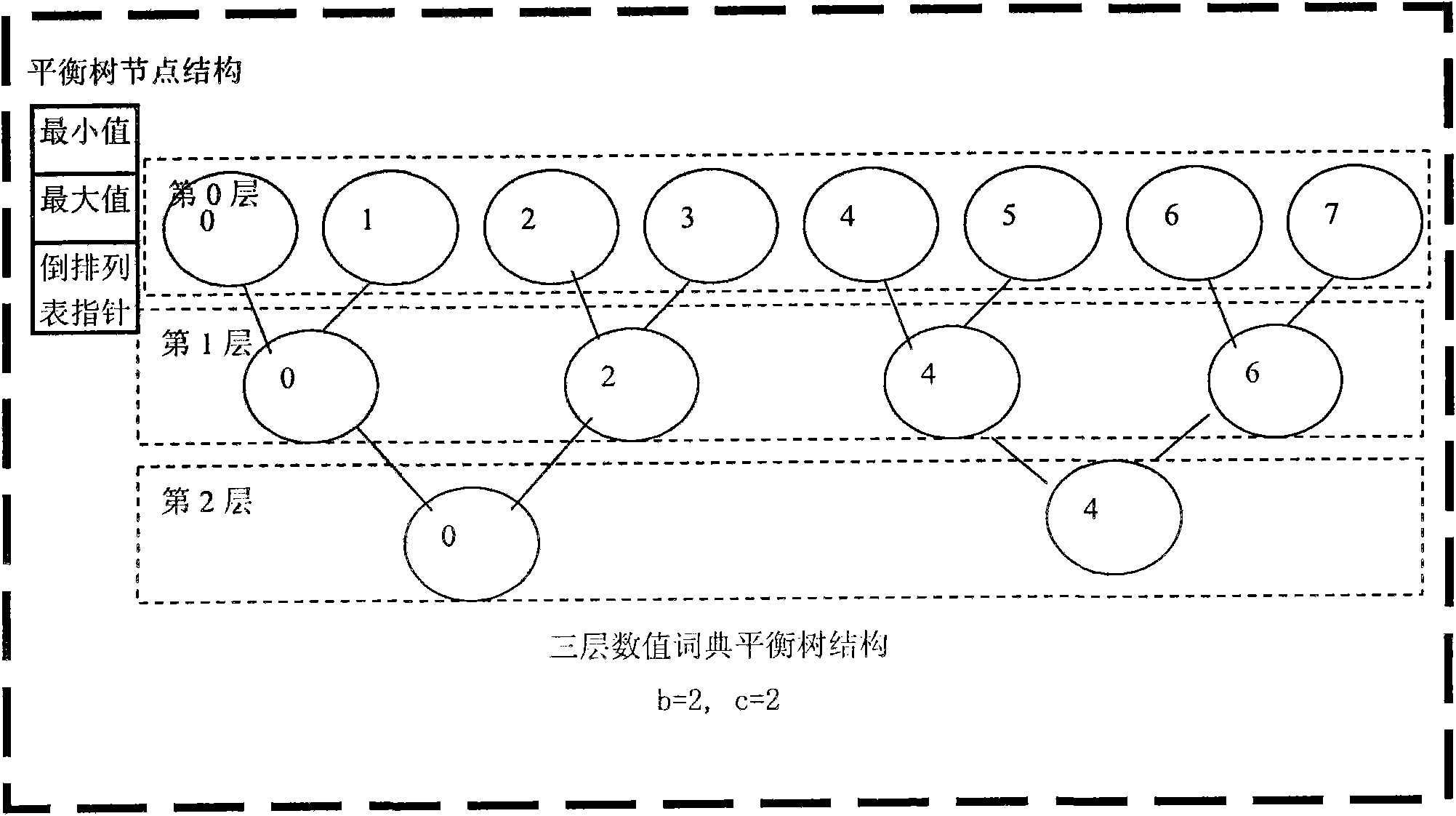
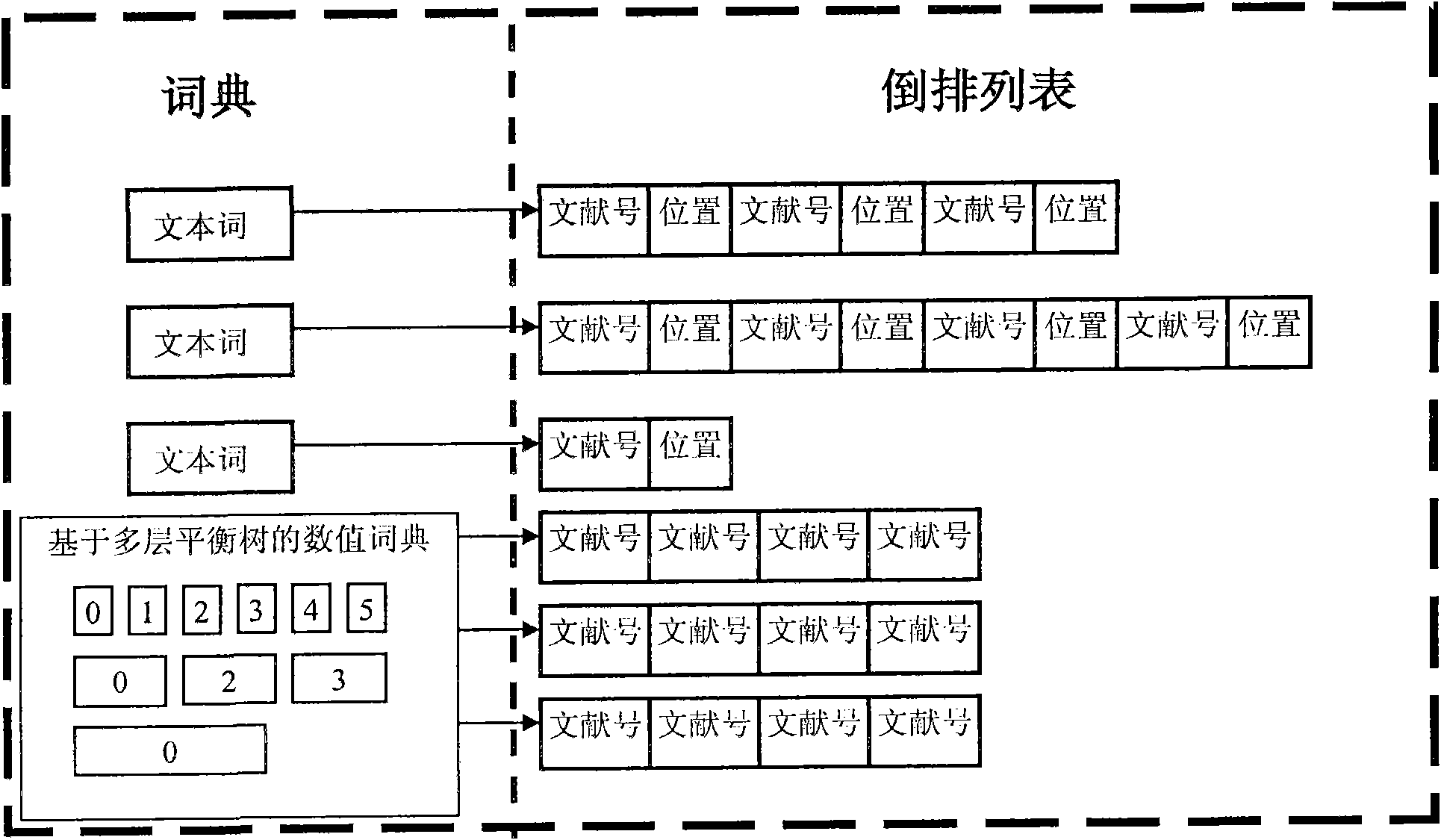
Numerical value and text mixed inverted index algorithm based on multilayer-optimization balanced tree
InactiveCN102402540AImprove performanceOptimal parameter valueSpecial data processing applicationsHybrid typeData management
The invention discloses a numerical value and text mixed inverted index algorithm based on a multilayer-optimization balanced tree. The traditional text inverted index only supports indexing on free texts, wherein the content of a numerical value is generally converted into a text, and then an inverted index is established according to the content of the text. According to the invention, the traditional text inverted index algorithm is optimized and expanded so as to be capable of supporting the indexing on numerical value and text mixed data, and a reasonable balance is realized in the aspects of query performance, index space and establishing performance. The index algorithm disclosed by the invention is suitable for being used in a mixed type data management engine and can be used for increasing the composite query performance of the numerical value and text mixed type data.
Owner:ZHEJIANG TIANYU INFORMATION TECH
Identifying snapshot membership for blocks based on snapid
ActiveUS8832026B1Efficiently manage and organizeEasy to operateDigital data processing detailsSpecial data processing applicationsFile systemSelf-balancing binary search tree
An on-disk structure of a file system has the capability to efficiently manage and organize data containers, such as snapshots, stored on a storage system. A multi-bit, monotonically increasing, snapshot identifier (“snapid”) is provided that represents a snapshot and that increases every time a snapshot is generated for a volume of the storage system. The snapid facilitates organization of snapshot metadata within, e.g., a data structure used to organize metadata associated with snapshot data. In the illustrative embodiment, the data structure is a balanced tree structure configured to index the copy-out snapshot data blocks. The snapid is also used to determine which blocks belong to which snapshots. To that end, every block that is used in a snapshot has an associated “valid-to” snapid denoting the newest snapshot for which the block is valid. The oldest snapshot for which the block is valid is one greater than the valid-to field of the next older block at the same file block number.
Owner:NETWORK APPLIANCE INC
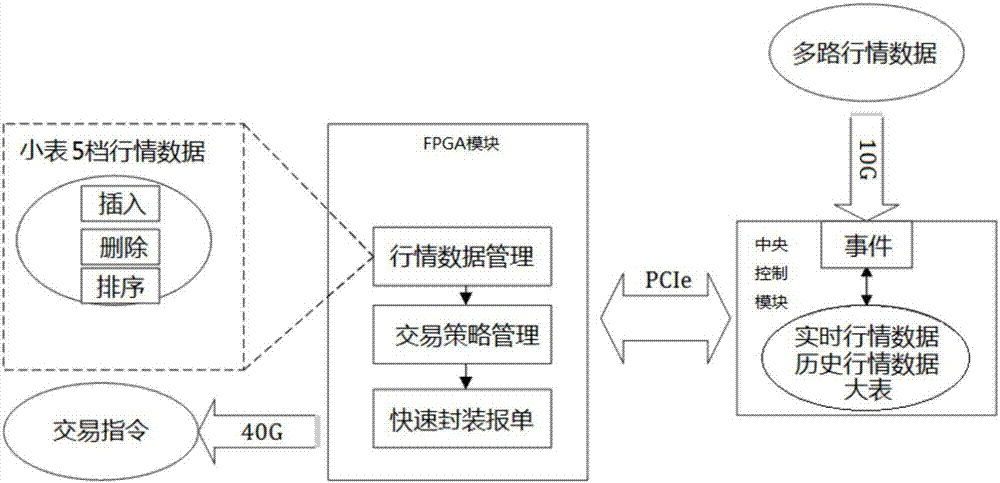
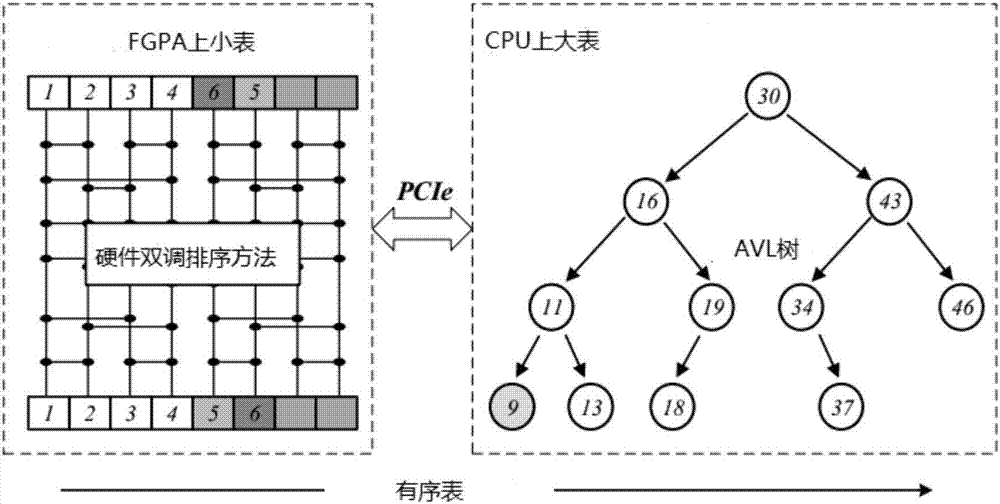
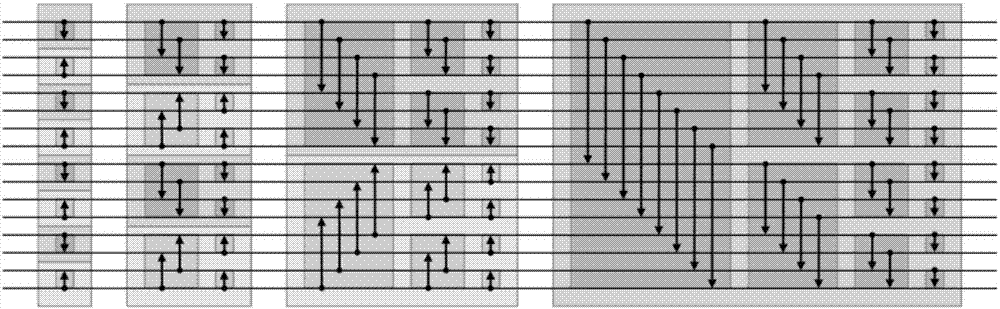
High-speed information interaction system based on FPGA-CPU mixed architecture
InactiveCN107451091AImprove processing efficiencyReduce the number of communication bytesFinanceDigital computer detailsInteraction systemsReal-time data
Disclosed is a high-speed information interaction system based on an FPGA-CPU mixed architecture. The system comprises an FPGA module, a central control module and an interaction terminal, wherein the FPGA module is in data communication with the central control module through a PCIe interface, the central control module receives multi-path TCP demand data for external selection, stores historical demand data and generates and maintain a historical data pricing table; the FPGA manages and maintains a real-time data pricing table generated according to the real-time demand data, the historical data pricing table and the real-time data pricing table are called according to the trigger of the interaction terminal to execute corresponding operation instructions to conduct quick decision-making and order combination, an interaction instruction is generated, and information interaction is achieved through the interaction terminal; the content of the real-time data pricing table is sorted through the adoption of a hardware bitonic sorting method, and the content of the historical data pricing table is sorted through the adoption of a balanced tree method. According to the high-speed information interaction system based on the FPGA-CPU mixed architecture, the delay of interaction between the FPGA and the CPU is controlled within a better delay range, a flexible and effective communication mode is adopted, the respective processing characteristics of the FPGA and the CPU take effects, and the speedup ratio of the mixed architecture system is increased.
Owner:上海金融期货信息技术有限公司
Data processing method and device, data access method and device and computer equipment
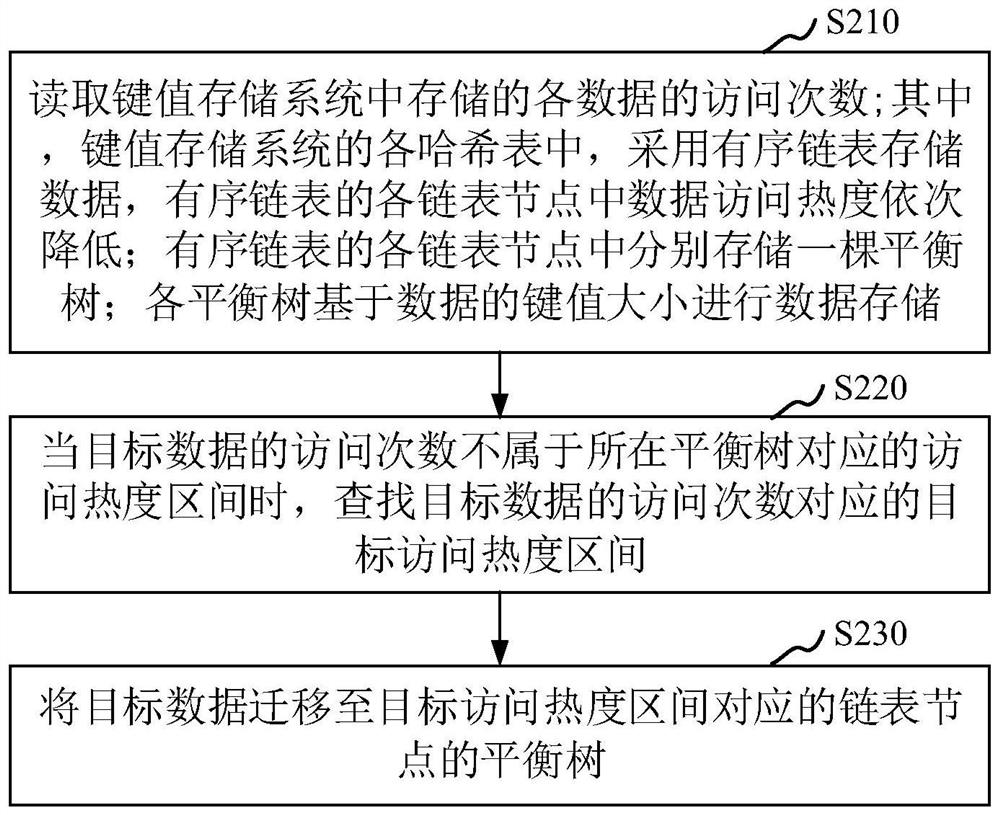
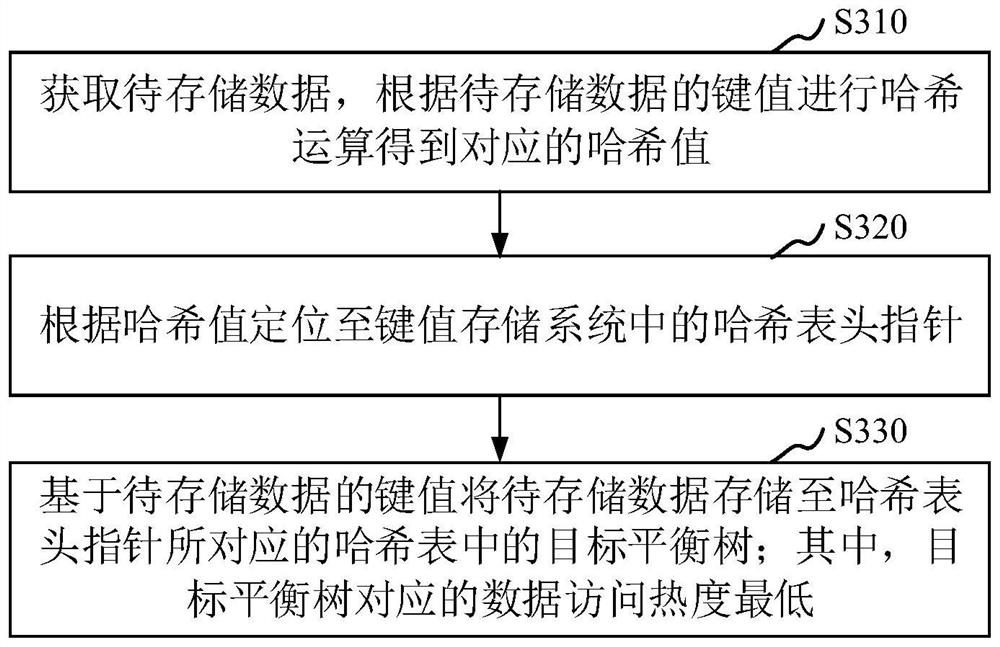
PendingCN112100293AImprove read and write performanceShorten the timeRelational databasesSpecial data processing applicationsData accessAccess frequency
The invention discloses a data processing method, a data access method, a data access device and computer equipment. The data processing method comprises the following steps: reading the access frequency of each piece of data stored in a key value storage system, wherein in each hash table of the key value storage system, an ordered linked list is adopted to store data, the data access popularityin each linked list node of the ordered linked list is sequentially reduced, and a balance tree is stored in each linked list node of the ordered linked list, performing data storage in each balance tree based on the key value size of the data; when the access frequency of the target data does not belong to an access popularity interval corresponding to the balance tree, searching a target accesspopularity interval corresponding to the access frequency of the target data; and migrating the target data to the balance tree of the linked list node corresponding to the target access popularity interval. According to the method, all the data does not need to be traversed during data access, so the read-write performance of the data can be improved; and the higher the access popularity is, theshorter the search time required for accessing of the data is.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Methods and Systems for Distributing Clock and Reset Signals
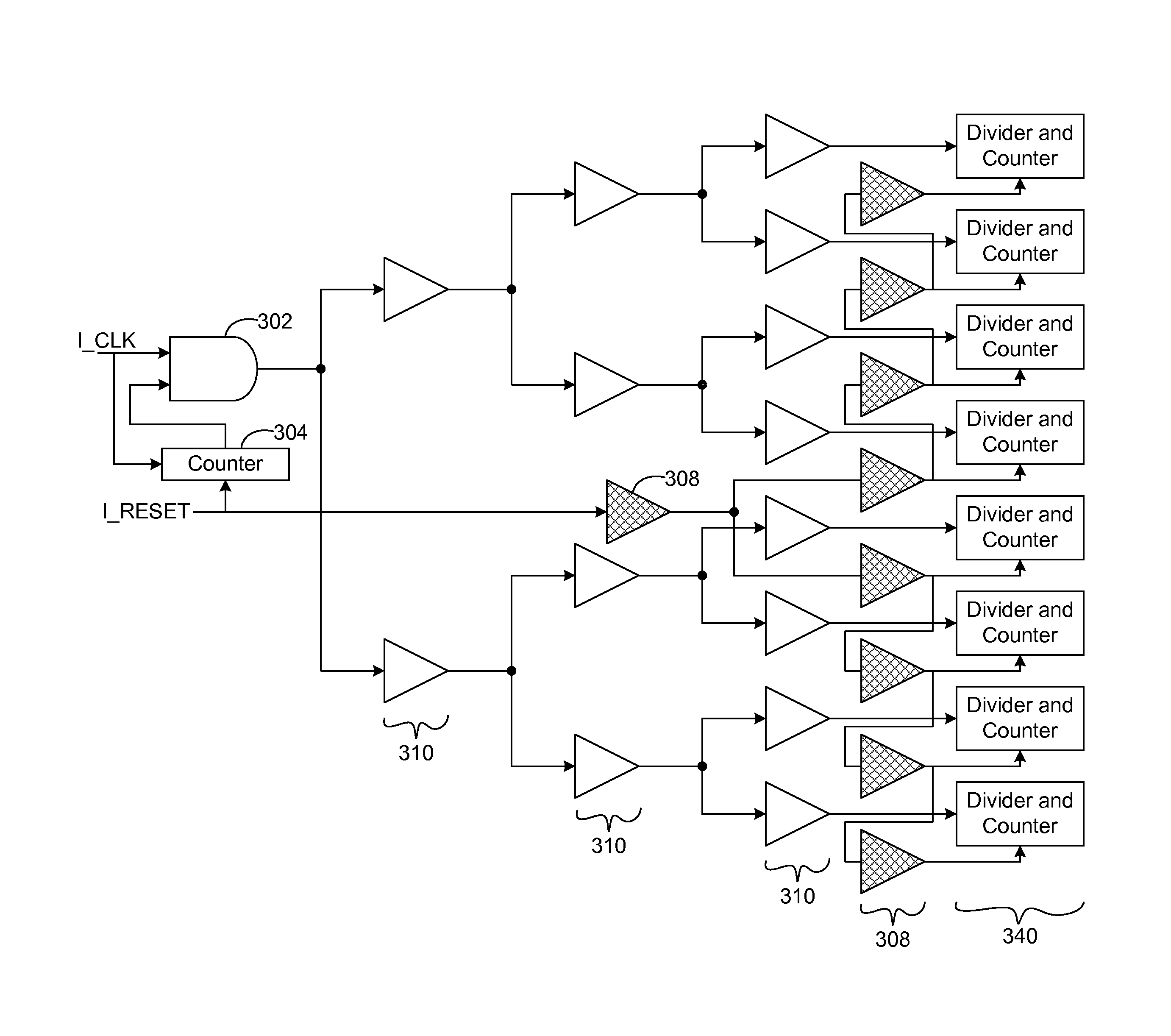
ActiveUS20140317434A1Reduce chip area usageReduce power consumptionSynchronisation information channelsPulse automatic controlSelf-balancing binary search treeComputer science
A distribution network, comprises: circuit blocks having counters, wherein the counters are synchronized relative to an input signal; drivers connected in a balanced tree for distributing the input signal synchronously to the circuit blocks; and drivers connected in an unbalanced tree for distributing a reset signal to the circuit blocks, wherein the input signal is distributed via the balanced tree as a function of the reset signal.
Owner:SYNOPSYS INC
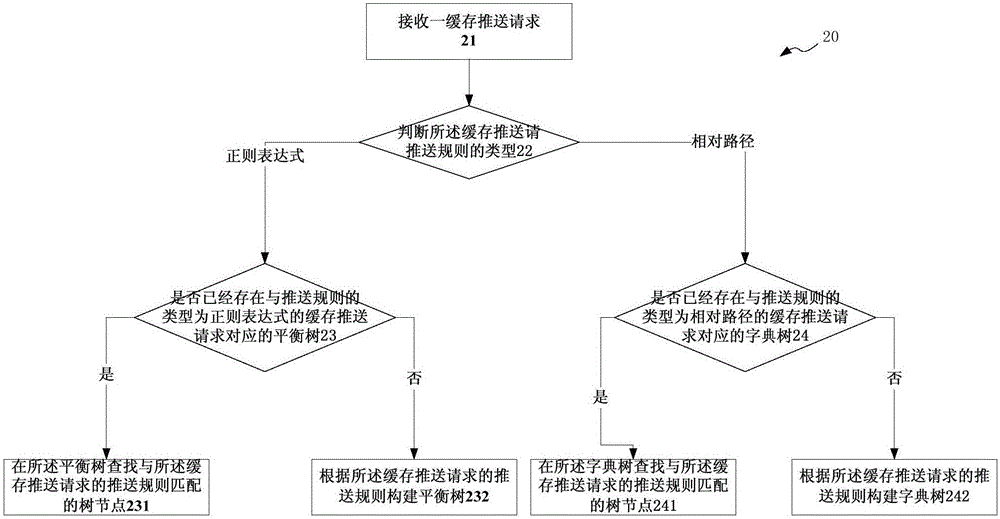
Communication system, cache server and cache content pushing and finding method and system
ActiveCN106446246AReduce time complexityImprove accuracySpecial data processing applicationsCommunications systemCache server
The invention provides a communication system, a cache server and a cache content pushing and finding method and system. The cache server establishes a balance tree and a dictionary tree according to the type of a cache pushing request and judges the type of the received cache pushing request, a matched tree node is found according to the balance tree when the type is a regular expression type, a matched tree node is found according to the dictionary tree when the type is a relative path type, and after the matched node is found, the cache content corresponding to the node is updated. The cache content is flexibly stored and found in different modes according to the type of a pushing rule of the cache pushing request, the complexity of time for finding is low, and accuracy is high.
Owner:CHINANETCENT TECH
Data monitoring method based on cloud computing
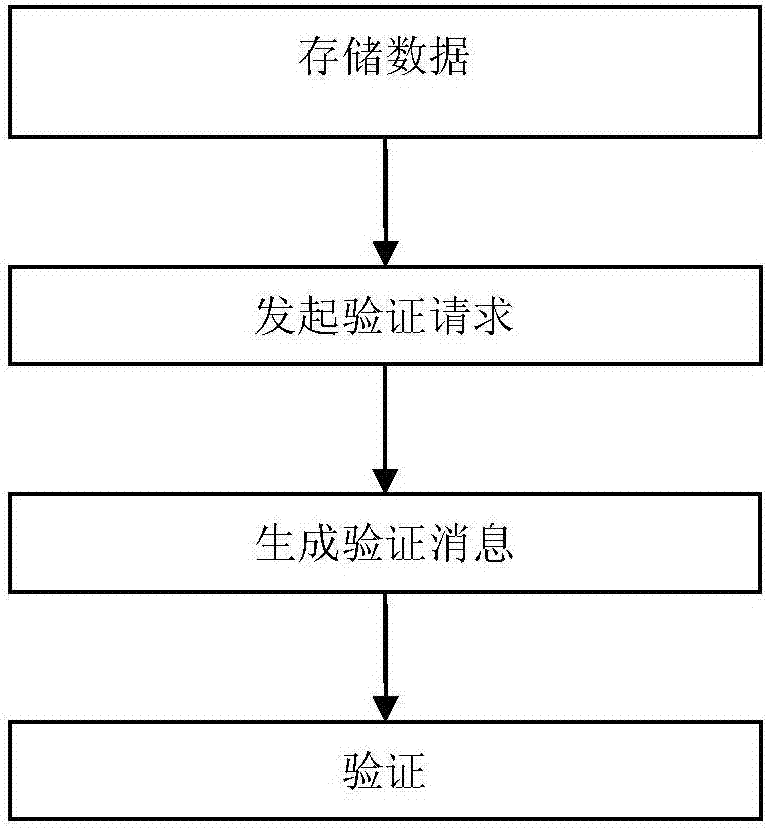
InactiveCN107231370AImprove processing efficiencySave storage spaceKey distribution for secure communicationDigital data protectionSelf-balancing binary search treeOptimal binary search tree
The invention provides a data monitoring method based on cloud computing. A user file is verified through adoption of a full storage tree. The full storage tree specifically comprises the fact that the full storage tree is established by taking a balance binary search tree as a basic structure; each node of the full storage tree stores the following content: 1), a file block m at the node; 2), a hash value H=H(m) of the file block of the node; 3), a joint hash value H<sum>(i), wherein if the i is a leaf sub-node, the H<sum>(i) is equal to the Hi, otherwise, the hash value of a father node is solved according to the hash value of the ith sub-node of the node, iterative calculation is carried out until the hash value of a root node of the full storage three, namely the hash value H(Root) of the whole full storage tree, is obtained. The method comprises the steps of (1), storing data; (2), initiating a verification request; (3), generating a verification message; and (4), carrying out verification. According to the method provided by the invention, the data processing efficiency is improved and the occupied storage space is reduced.
Owner:CHENGDU DINGZHIHUI TECH
Parallel data processing architecture
InactiveUS20080109461A1Minimize timeBalance workloadData processing applicationsBiostatisticsConfigfsSelf-balancing binary search tree
A tree-structured index to multidimensional data is created using naturally occurring patterns and clusters within the data which permit efficient search and retrieval strategies in a database of DNA profiles. A search engine utilizes hierarchical decomposition of the database by identifying clusters of similar DNA profiles and maps to parallel computer architecture, allowing scale up past to previously feasible limits. Key benefits of the new method are logarithmic scale up and parallelization. These benefits are achieved by identification and utilization of naturally occurring patterns and clusters within stored data. The patterns and clusters enable the stored data to be partitioned into subsets of roughly equal size. The method can be applied recursively, resulting in a database tree that is balanced, meaning that all paths or branches through the tree have roughly the same length. The method achieves high performance by exploiting the natural structure of the data in a manner that maintains balanced trees. Implementation of the method maps naturally to parallel computer architectures, allowing scale up to very large databases.
Owner:UNIV OF TENNESSEE RES FOUND
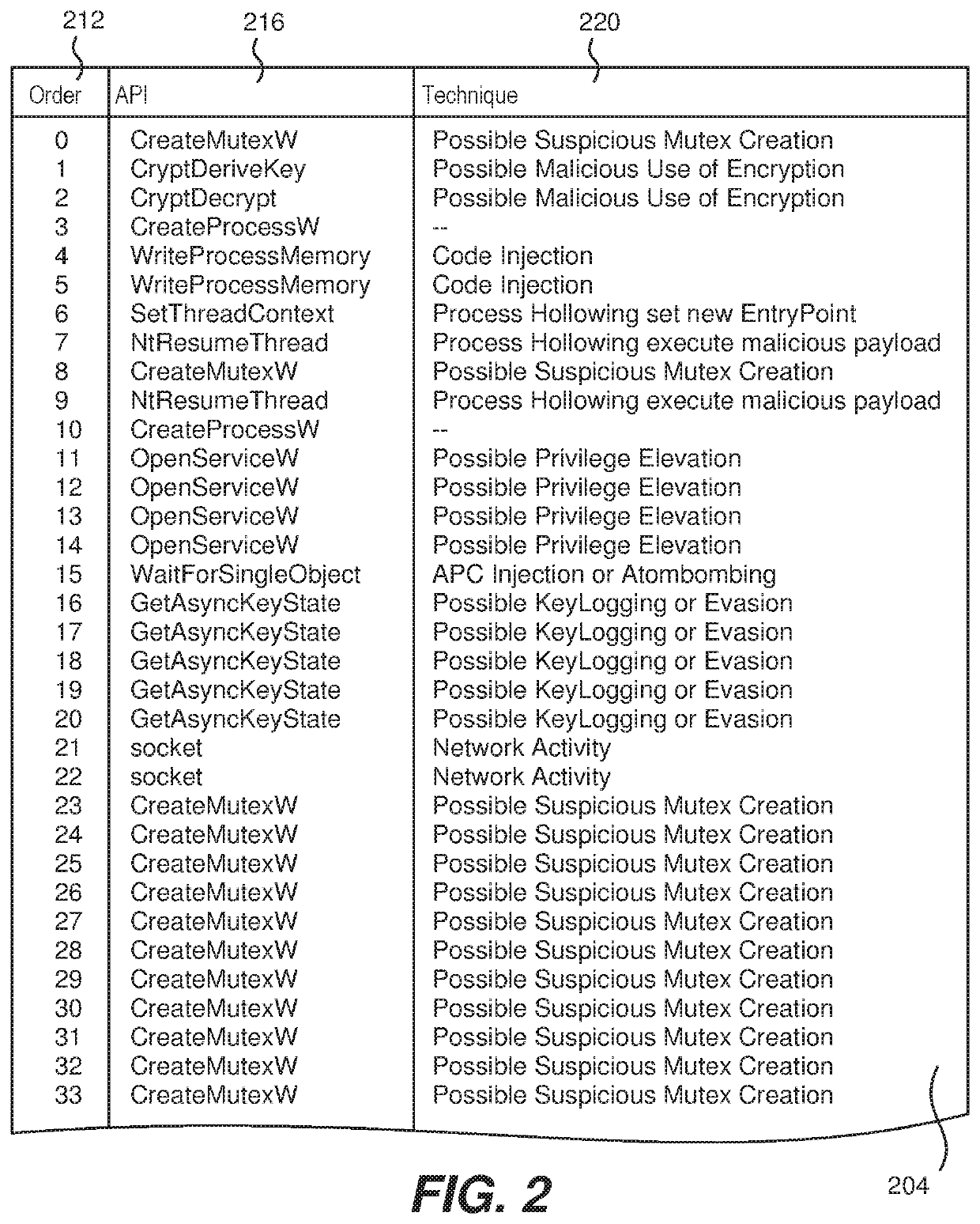
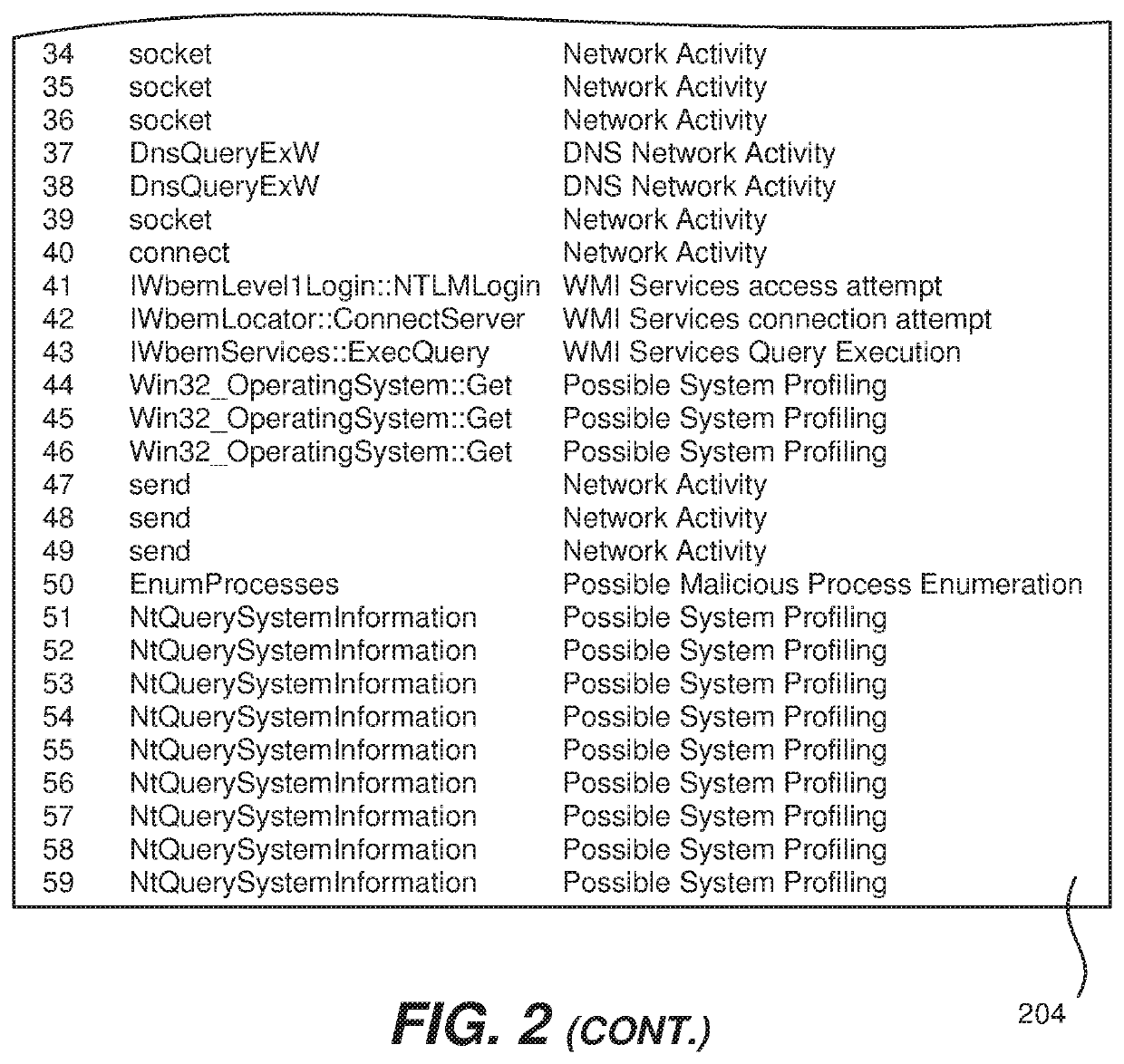
Malware detection using locality sensitive hashing of API call sequences
ActiveUS11354409B1Fast computerQuick calculationInterprogram communicationPlatform integrity maintainanceTheoretical computer scienceEngineering
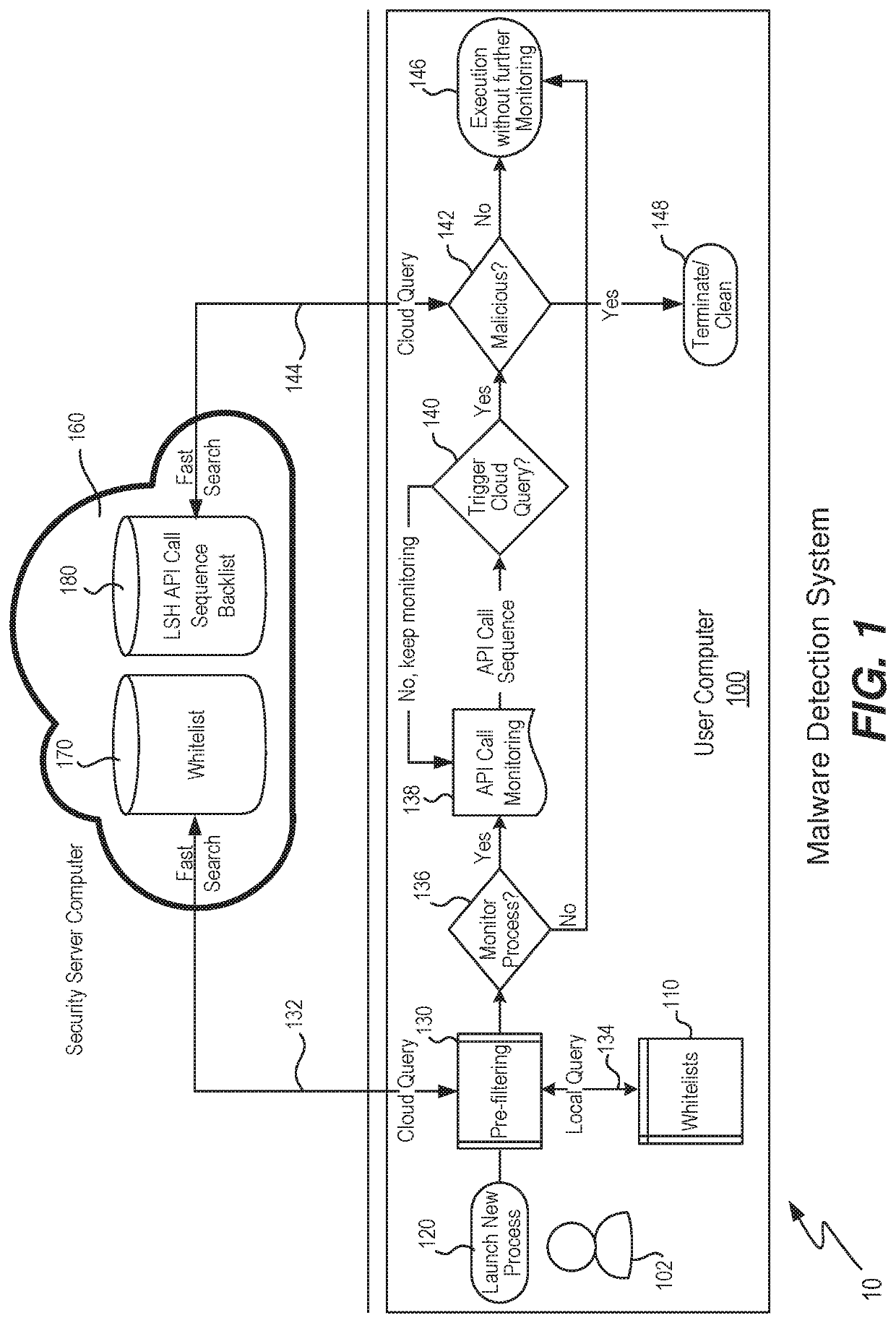
An agent on an endpoint computer computes a locality-sensitive hash value for an API call sequence of an executing process. This value is sent to a cloud computer which includes an API call sequence blacklist database of locality-sensitive hash values. A search is performed using a balanced tree structure of the database using the received hash value and a match is determined based upon whether or not a metric distance is under or above a distance threshold. The received value may also be compared to a white list of locality-sensitive hash values. Attribute values of the executing process are also received from the endpoint computer and may be used to inform whether or not the executing process is deemed to be malicious. An indication of malicious or not is returned to the endpoint computer and if malicious, the process may be terminated and its subject file deleted.
Owner:TREND MICRO INC
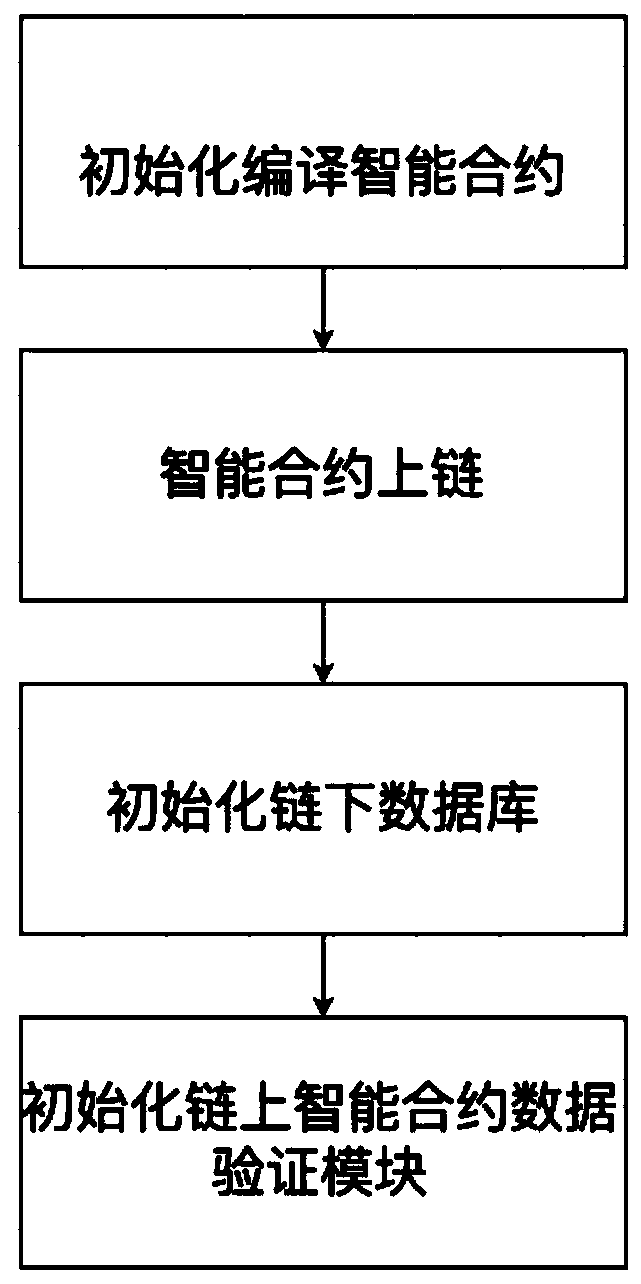
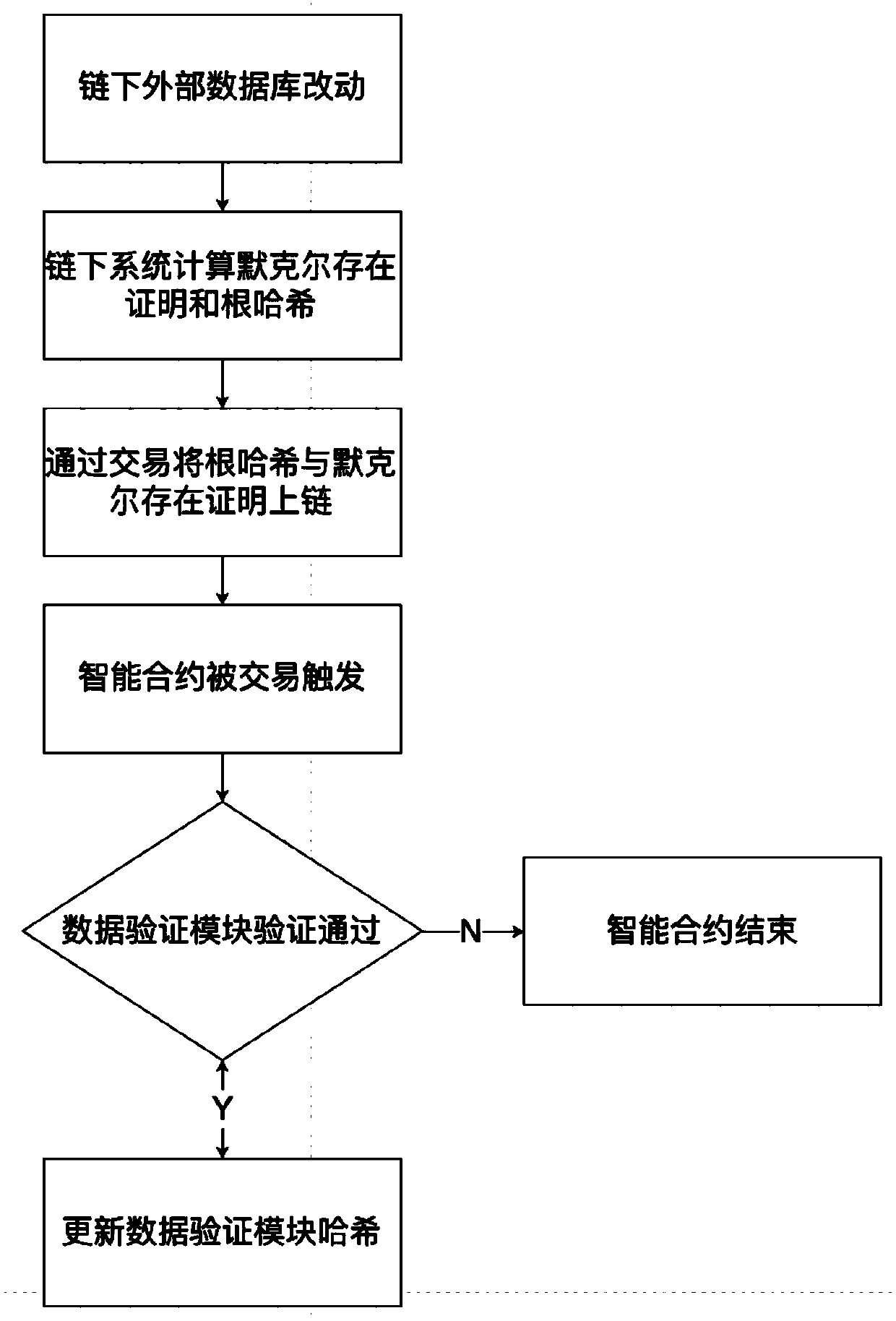
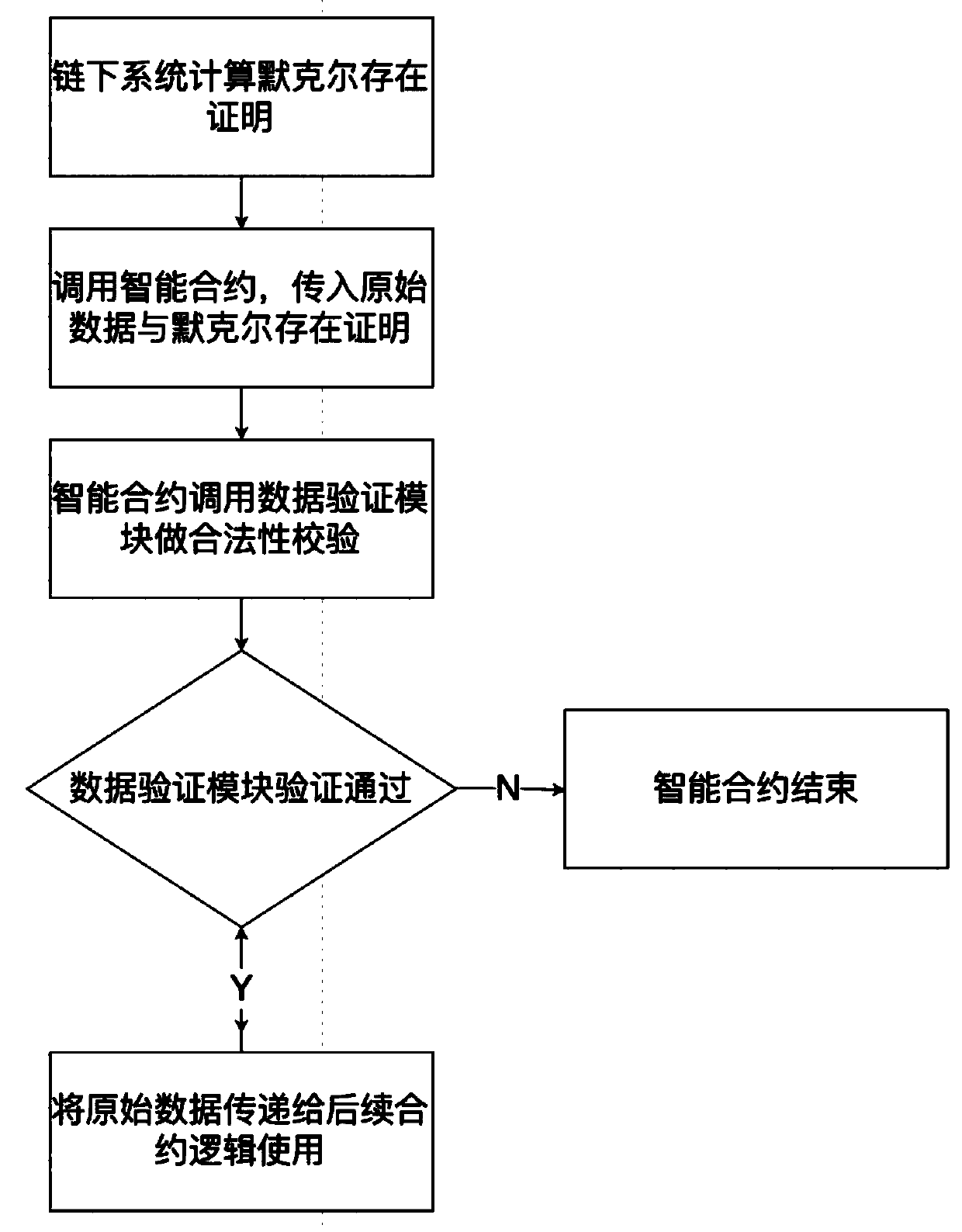
Method and system for anchoring trustable external database by blockchain intelligent contract
The invention discloses a method and system for anchoring a trustable external database by a blockchain intelligent contract, and the method comprises the steps: peeling the data of the intelligent contract from the storage space of the intelligent contract, and storing the data in a database under any type of chain; adding a fixed-length hash to a continuous storage layer of the smart contract torepresent Merkel tree root hash of the under-chain external database mapped by the smart contract; if the data need to be inserted into the smart contract or the data need to be deleted from the smart contract or the data needs to be called; according to the invention, the Merkel tree, which is a data structure, is utilized to compress the infinite data set into the Hash with a certain length tooptimize the virtual space of the continuous storage of the intelligent contract; in the process of adding, deleting, modifying and checking external data, the verification overhead of the smart contract is always kept within a reasonable range by utilizing the characteristics of the balance tree, and block chain node CPU resources within the reasonable range are fully utilized to replace storageresources under a trusted chain which is nearly free of an upper limit.
Owner:杭州时戳信息科技有限公司
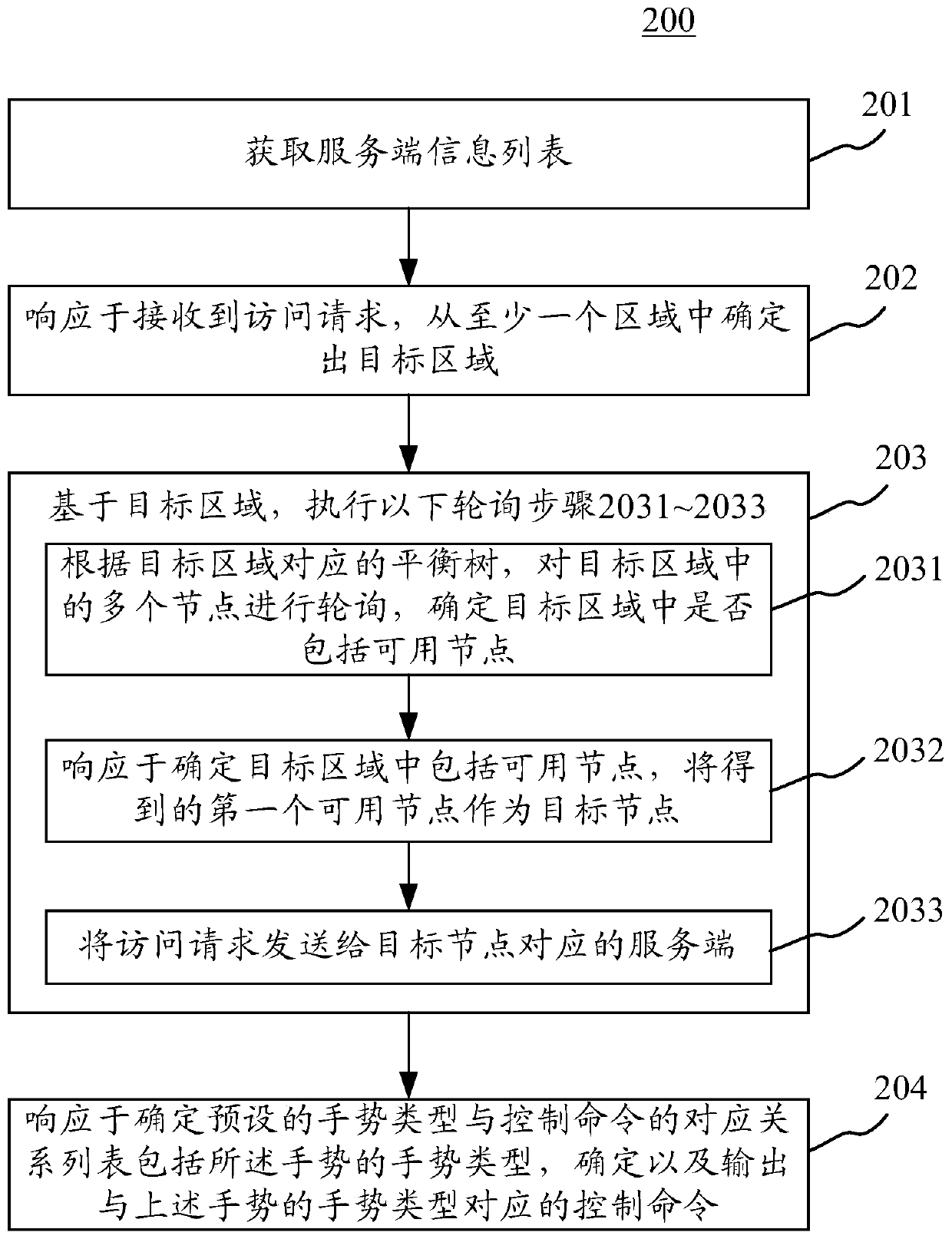
Method and device for realizing load balancing
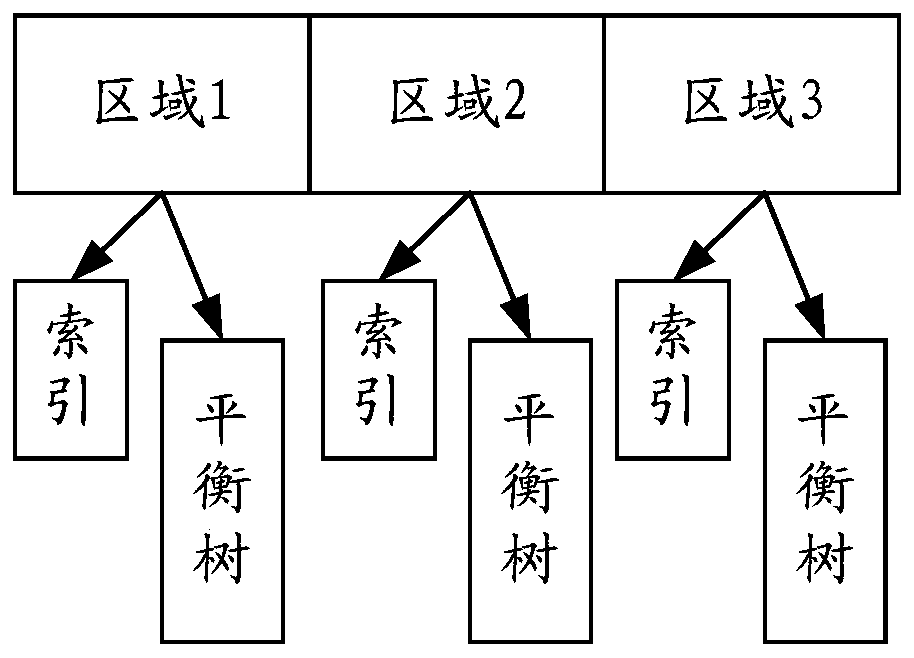
ActiveCN110650209AReduce forwarding delayImprove forwarding efficiencyTransmissionEngineeringPolling
The embodiment of the invention discloses a method and a device for realizing load balancing. A specific embodiment of the method comprises the following steps: acquiring a server information list; responding to the received access request, and determining a target area from the at least one area; based on the target area, executing the following polling steps: polling a plurality of nodes in thetarget area according to a balance tree corresponding to the target area, and determining whether the target area comprises available nodes or not; in response to determining that the target area comprises available nodes, taking the obtained first available node as a target node; sending the access request to a server corresponding to the target node; and in response to determining that the target area does not include the available node, determining a new target area according to the server information list, and continuing to execute the polling step. According to the embodiment, the forwarding delay is reduced, and the forwarding efficiency is improved.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
Efficient communication method and system applied to blockchain
PendingCN113709203APrevent centralizationSolve the problem of easily occupying network bandwidth and even causing floodingTransmissionTree rootComputer network
The invention provides an efficient communication method and system applied to a blockchain. Nodes of a blockchain network are divided into a plurality of node sets which are organized through a balance tree structure, a new node is added to a balance tree at random and taken as a leaf node of the balance tree, and the newly generated balance tree is broadcasted to other nodes in the balance tree. A root node can generate a new balance tree at random according to the balance tree at regular time, and sends the addresses of other root nodes in the blockchain network stored by the original root node to the root node of the newly generated balance tree. Only a parent node and a child node in the balance tree directly communicate, so that the problem that p2p communication used by the blockchain occupies too much bandwidth is solved. Meanwhile, the number of balance tree nodes is limited, and the blockchain is prevented from tending to be centralized.
Owner:曾春峰
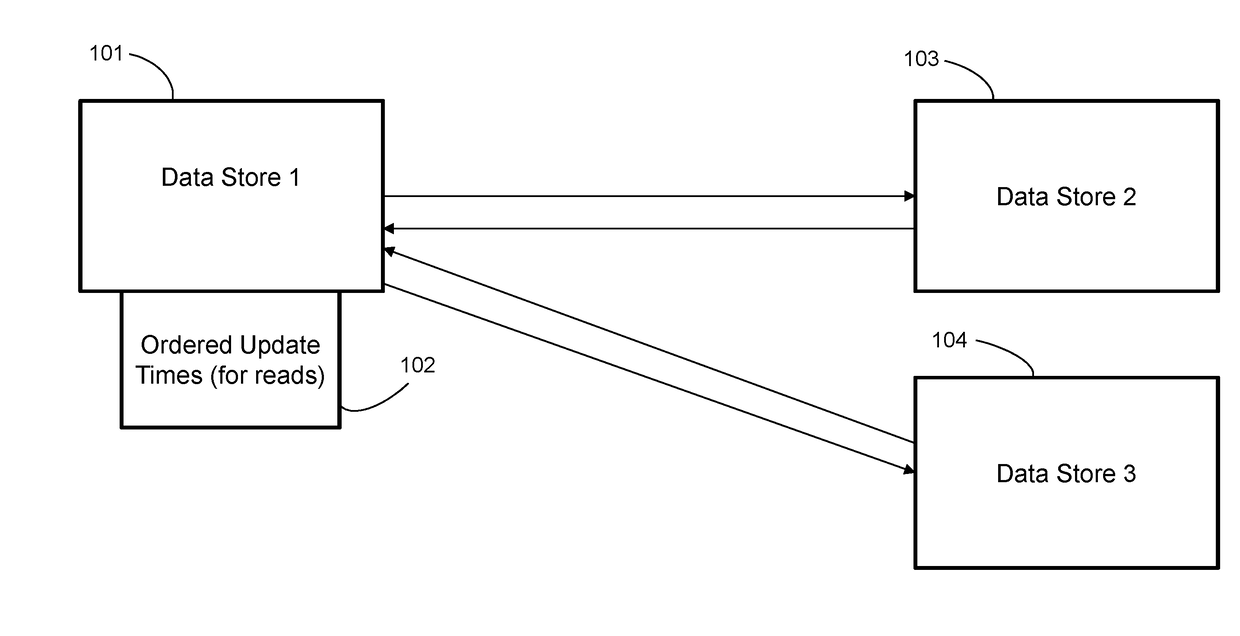
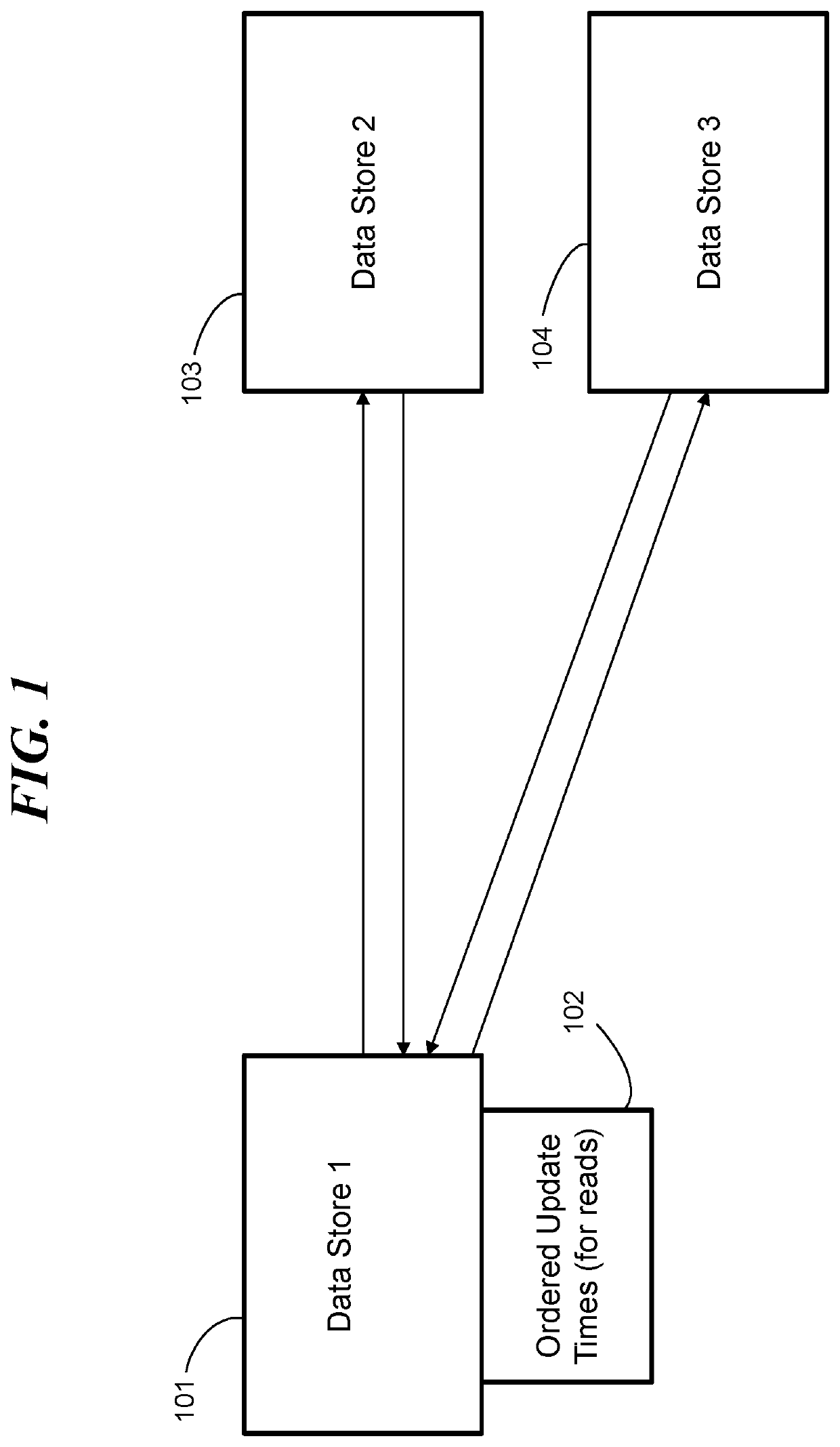
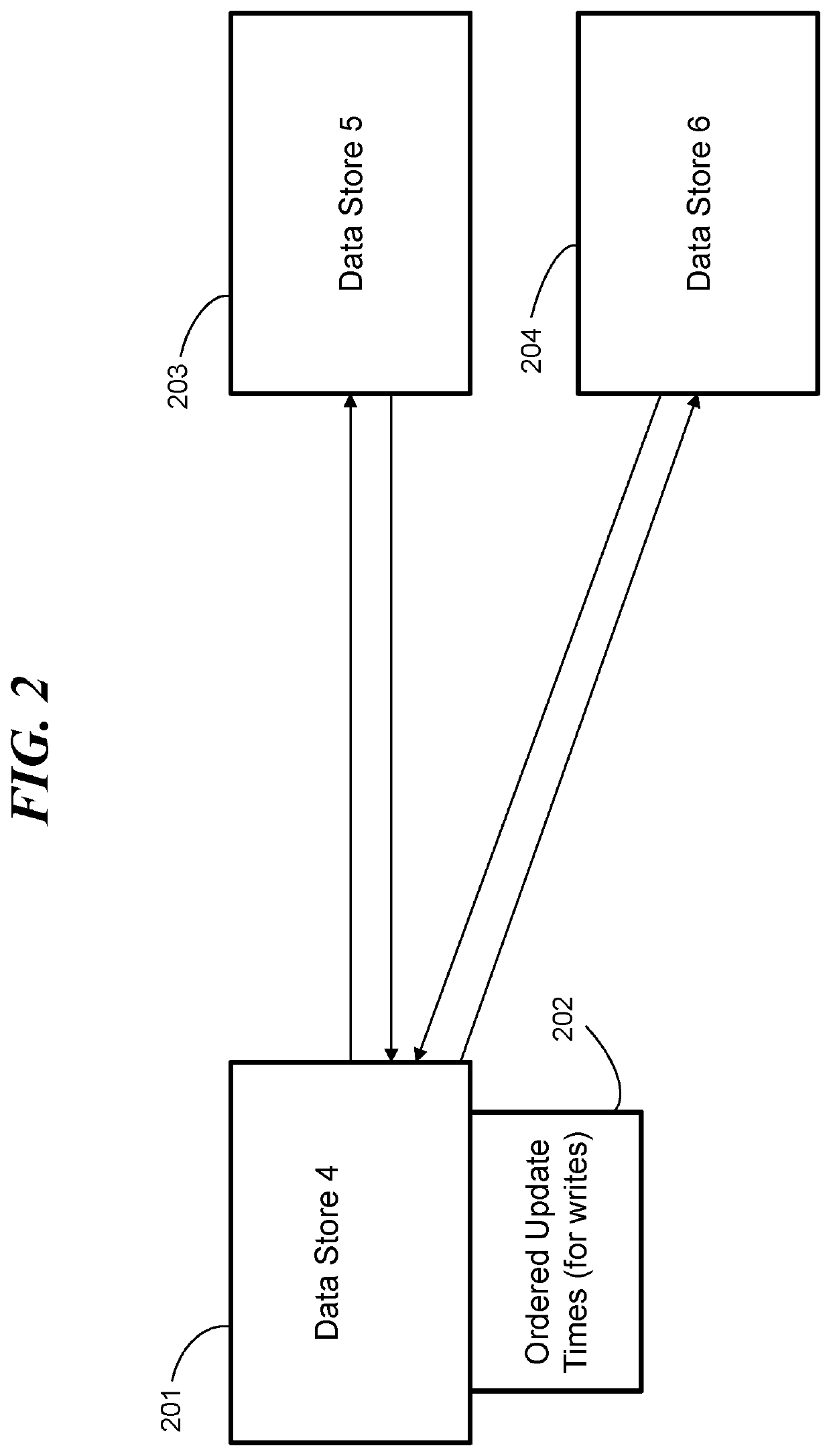
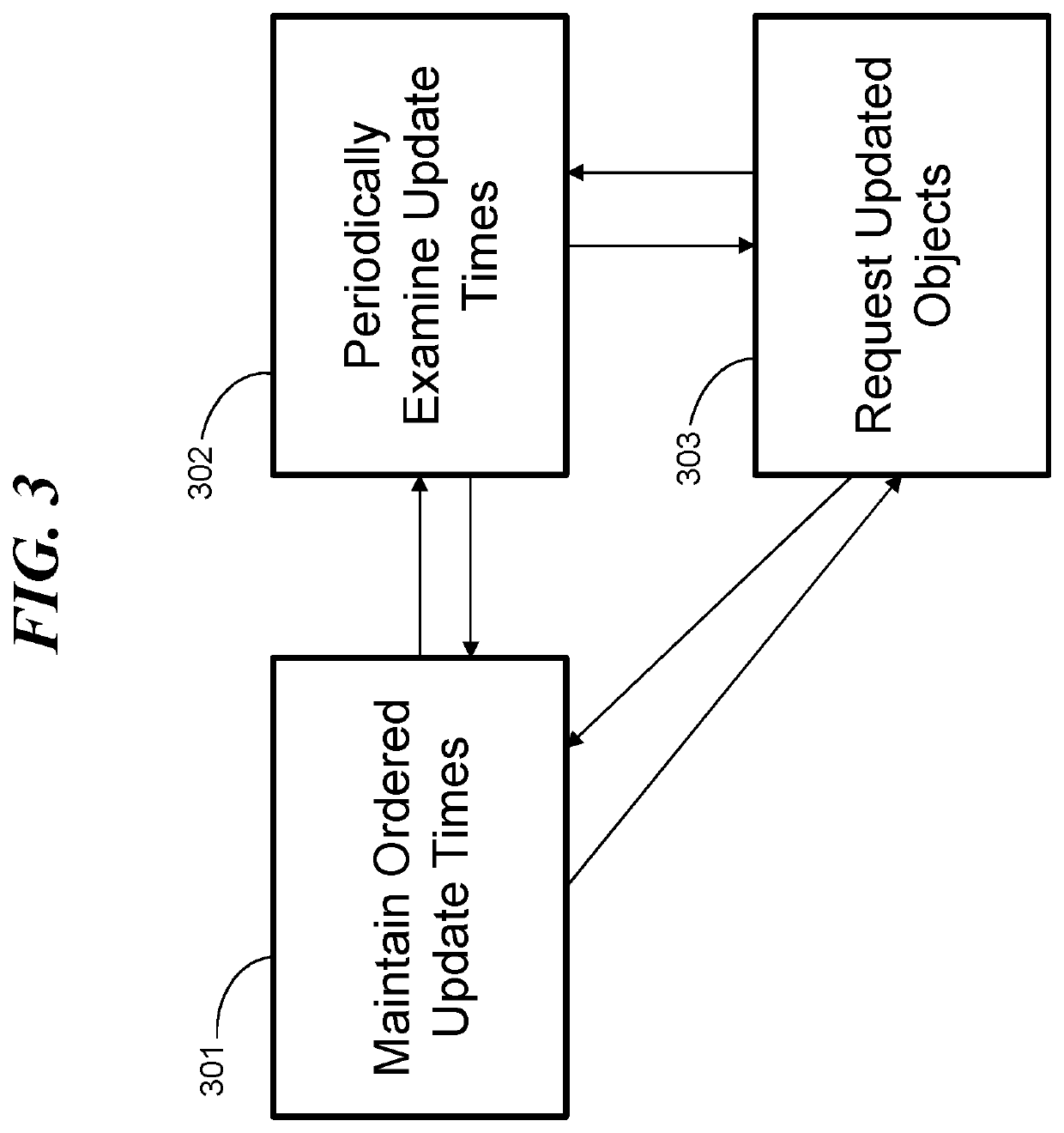
Synchronizing data values by requesting updates
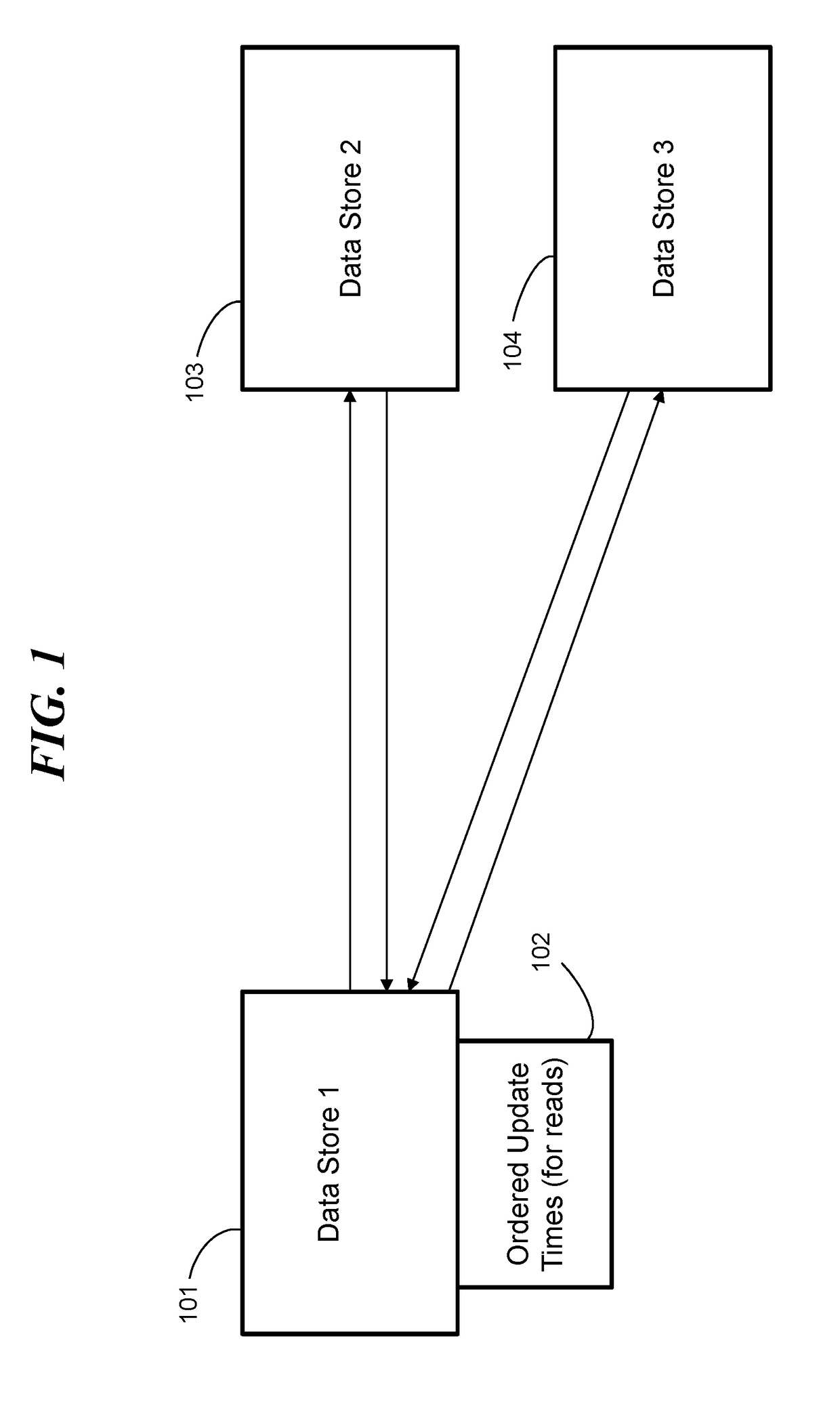
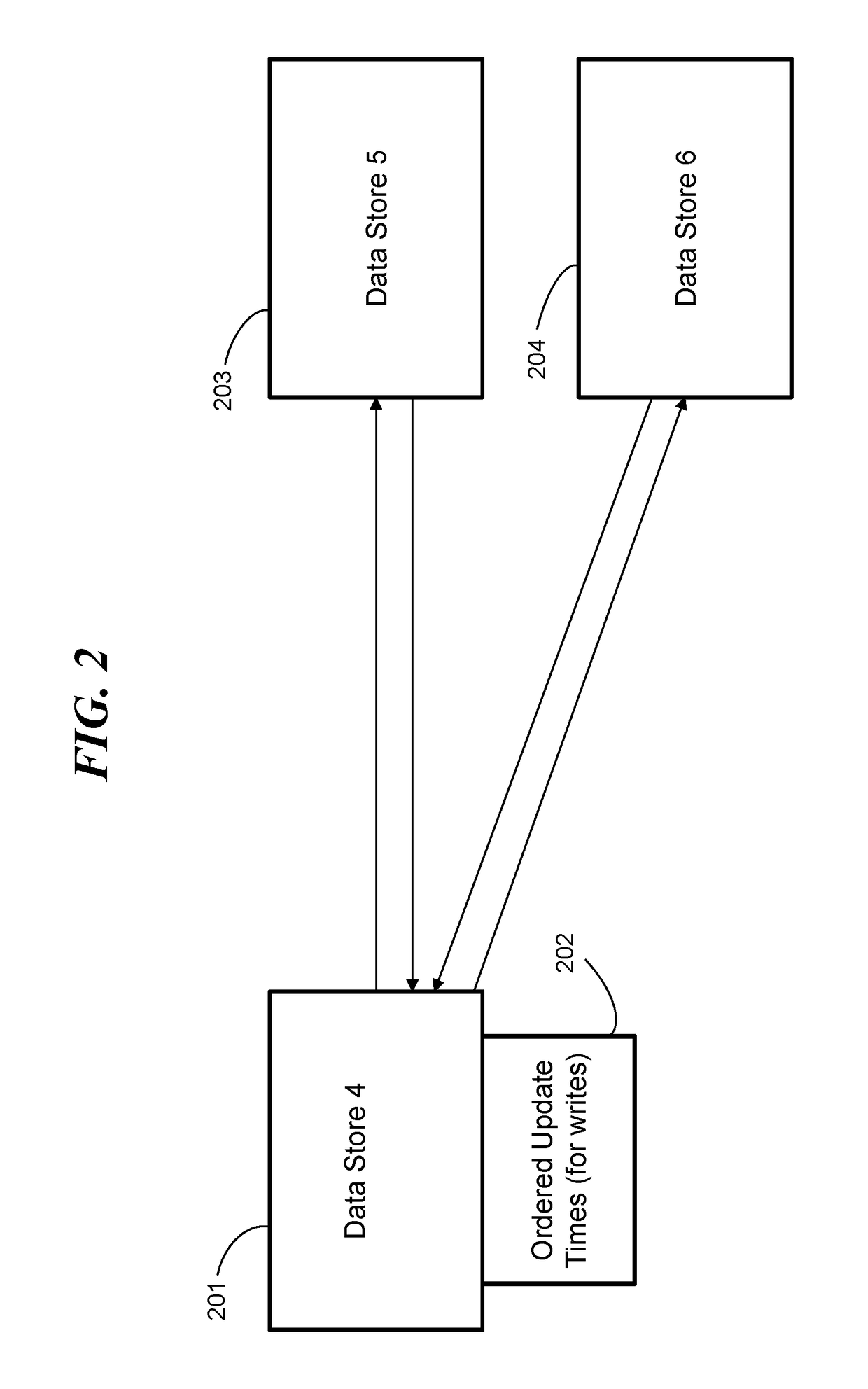
ActiveUS20180329938A1Object oriented databasesSpecial data processing applicationsObject basedData memory
A processing system, computer program product, and methods for maintaining consistent values of objects in two or more stores. A method includes a data store associating an update time for each object of a plurality of objects, where each object of the plurality of objects resides on a respective another data store. The data store maintains a data structure ordering the plurality of objects by update times. The data store periodically examines the data structure to read update times. The data store makes a decision to request an updated version of an object belonging to the plurality of objects based on an update time of the object. The data structure can be a balanced tree.
Owner:IBM CORP
Front-end interface generation method and device
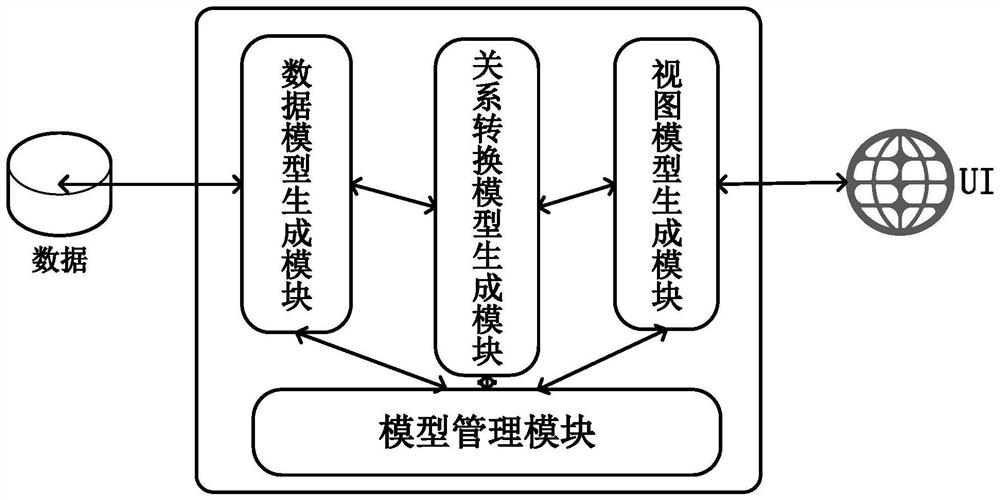
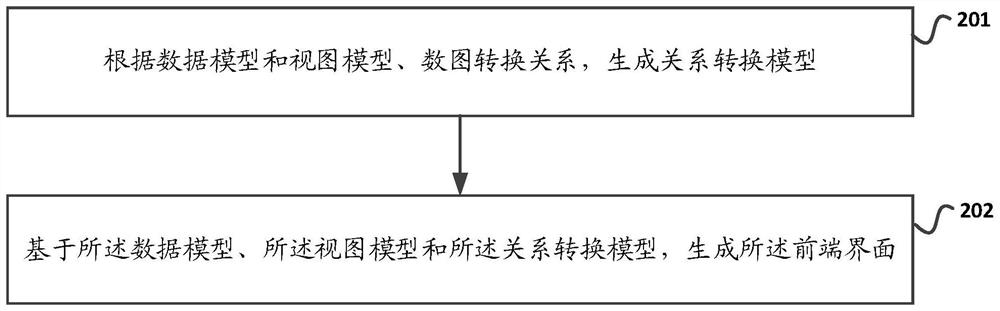
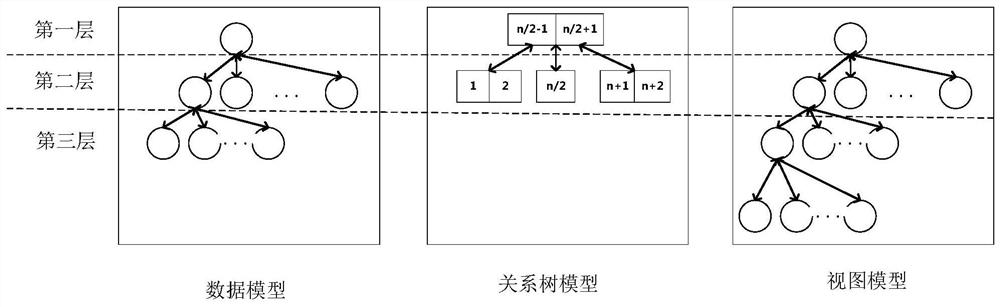
PendingCN111880795ASoftware engineeringExecution for user interfacesTheoretical computer scienceTree (data structure)
The invention discloses a front-end interface generation method and device, and the method comprises the steps: generating a relation conversion model according to a data model, a view model and a digital-to-image conversion relation, wherein the data model is used for defining interface parameters and parameter attributes of a front-end interface, the view model is used for defining an interfaceview and view attributes of the front-end interface, the digital graph conversion relationship is a preset conversion relationship between the interface parameters of the front-end interface and the interface view of the front-end interface, the data structures of the data model and the view model are multi-way trees, the data structure of the relation conversion model is a multi-way balance tree;and a relationship node of a multi-way balance tree of the relationship conversion model indicates a corresponding relationship between a data node of the data model and a view node of the view model; and generating the front-end interface based on the data model, the view model and the relationship conversion model.
Owner:CHINA UNIONPAY
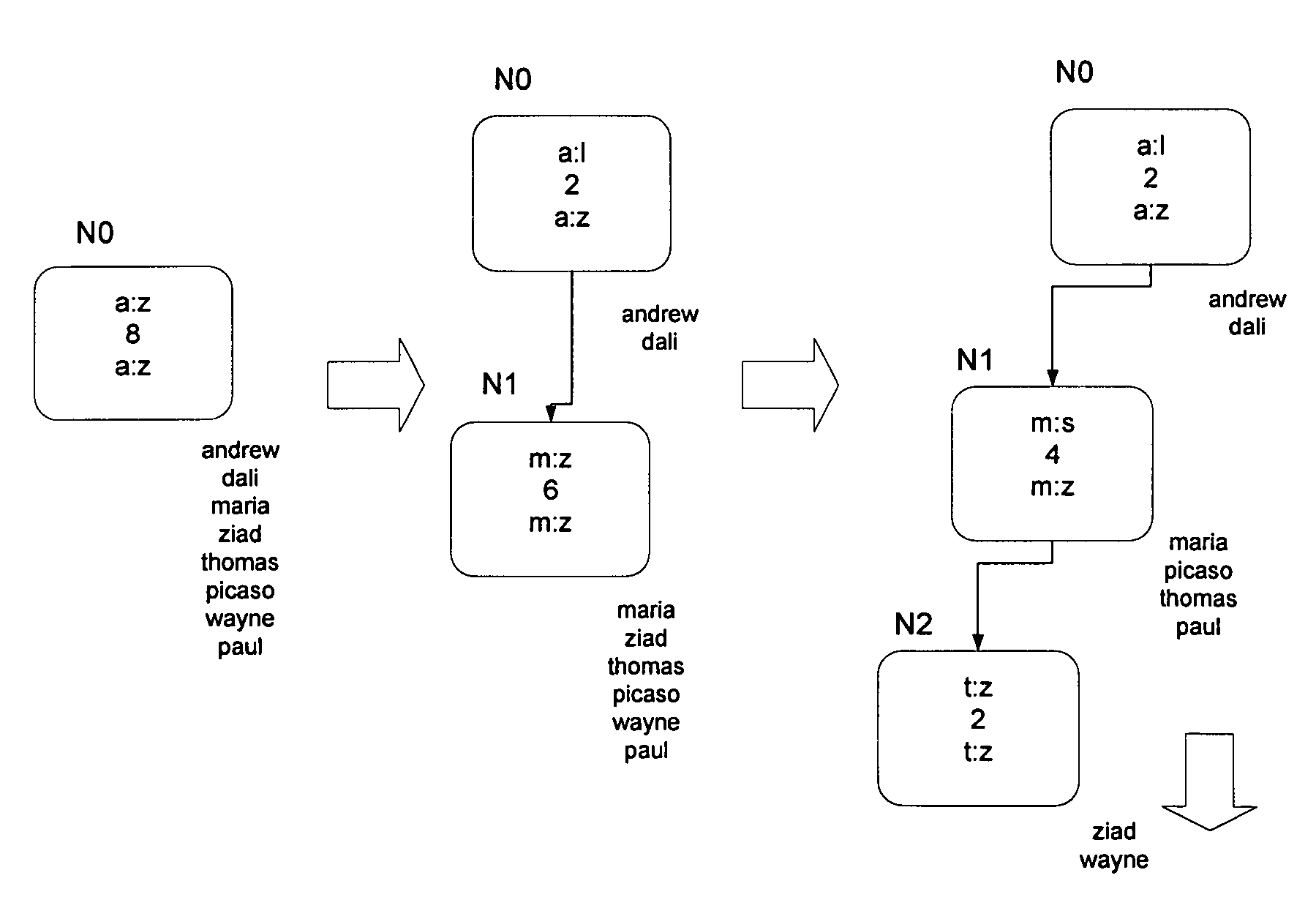
Concurrent updating method of balance tree and read-write system
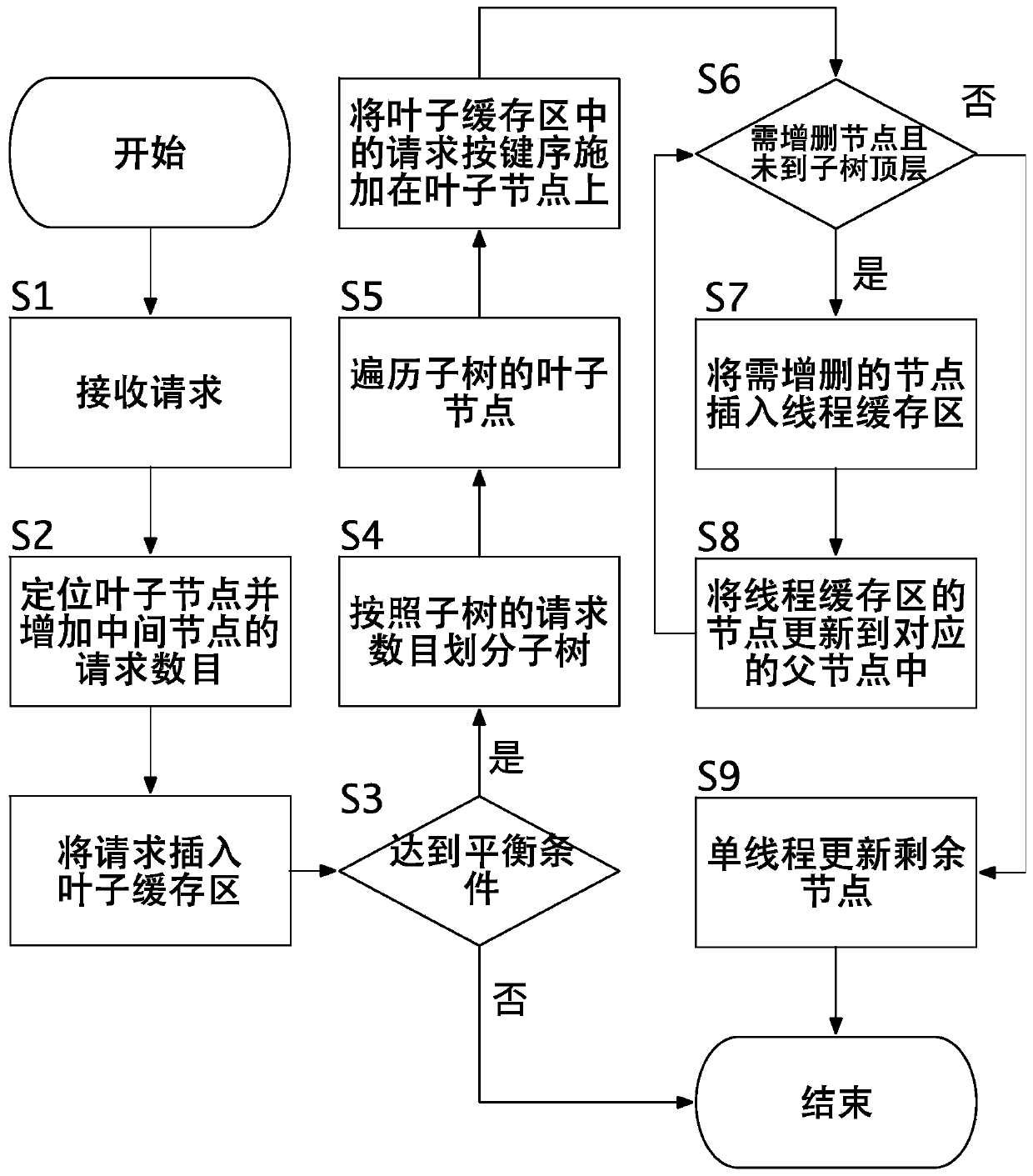
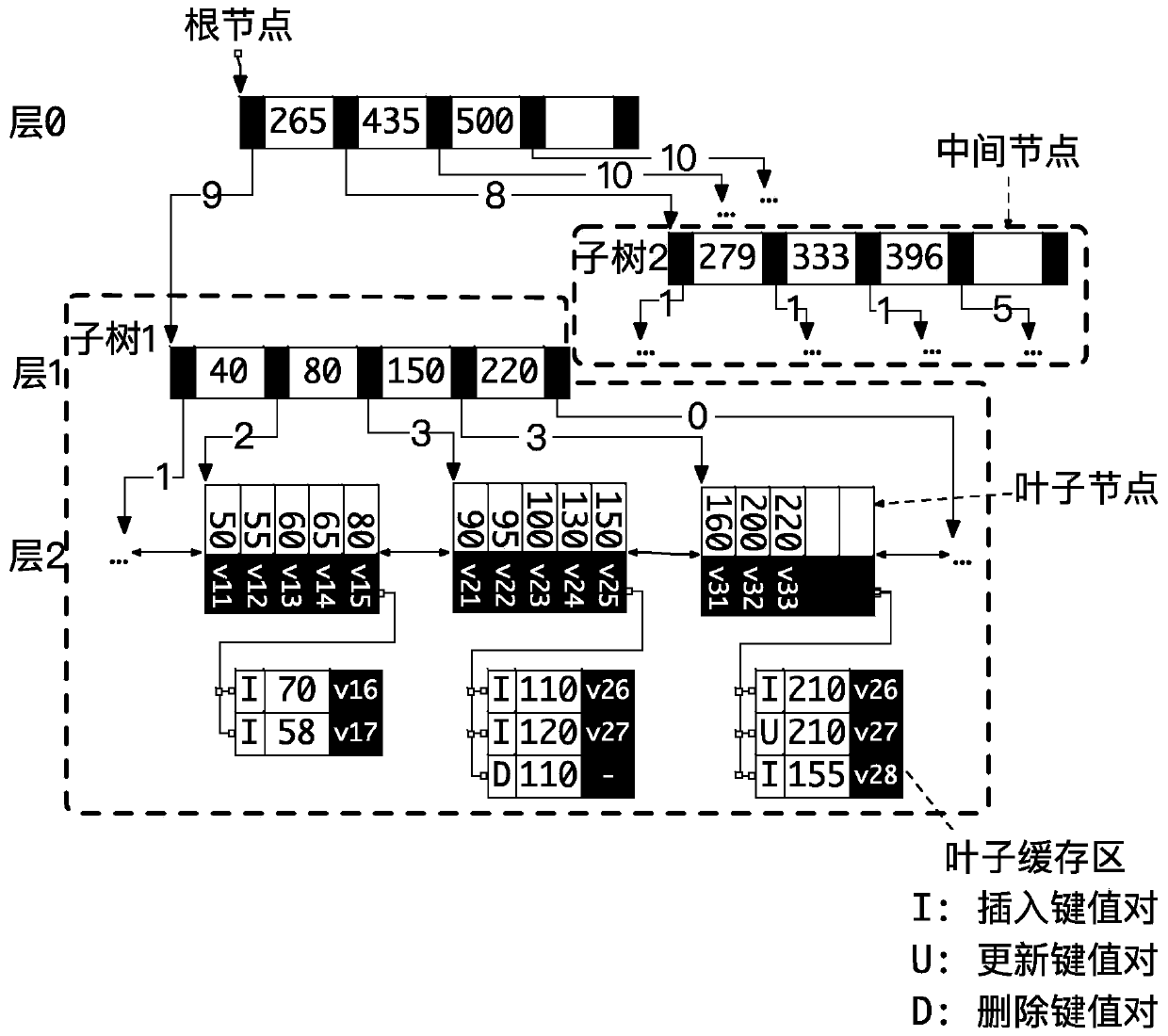
ActiveCN110825734AEasy to operateReduce redundant requestsDatabase updatingResource allocationTheoretical computer scienceSelf-balancing binary search tree
The invention provides a balance tree concurrent updating method and a read-write system, and the method comprises the steps: caching a request for updating a balance tree at a leaf node in a positioning stage, then delaying the structure adjustment of the balance tree to a balance stage, and enabling a task to be divided to different working threads for execution. According to the method, redundant time-consuming operations and requests can be reduced to save CPU resources, task parallelism and data parallelism are fully utilized to improve the performance of updating the balance tree, and the performance of updating the balance tree under the condition of concurrent updating and the performance of querying the balance tree under the condition of reading and writing concurrency are improved.
Owner:SHANGHAI JIAO TONG UNIV
Synchronizing data values by requesting updates
A processing system, computer program product, and methods for maintaining consistent values of objects in two or more stores. A method includes a data store associating an update time for each object of a plurality of objects, where each object of the plurality of objects resides on a respective another data store. The data store maintains a data structure ordering the plurality of objects by update times. The data store periodically examines the data structure to read update times. The data store makes a decision to request an updated version of an object belonging to the plurality of objects based on an update time of the object. The data structure can be a balanced tree.
Owner:INT BUSINESS MASCH CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com