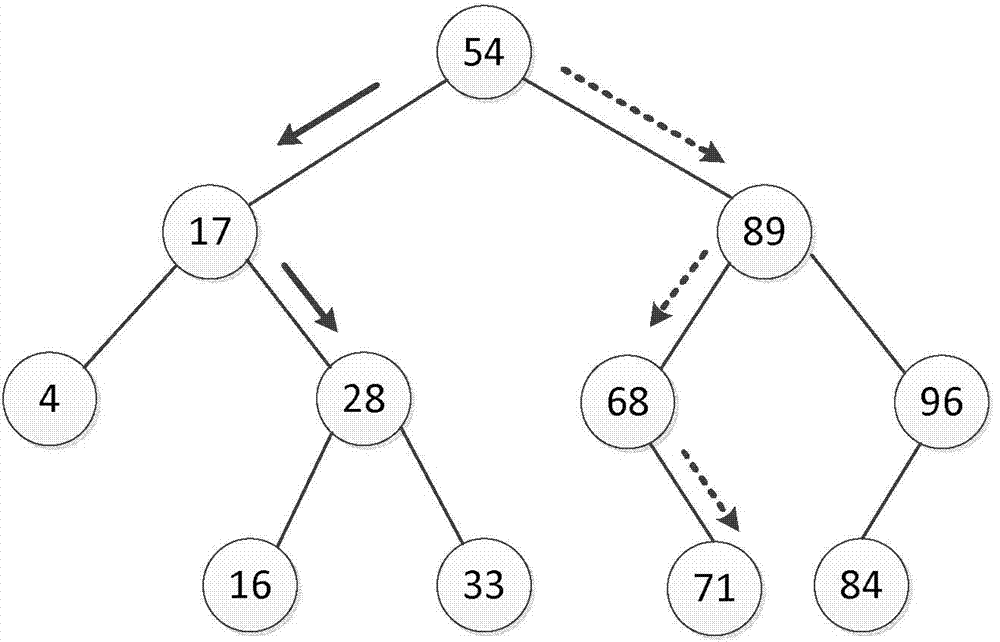
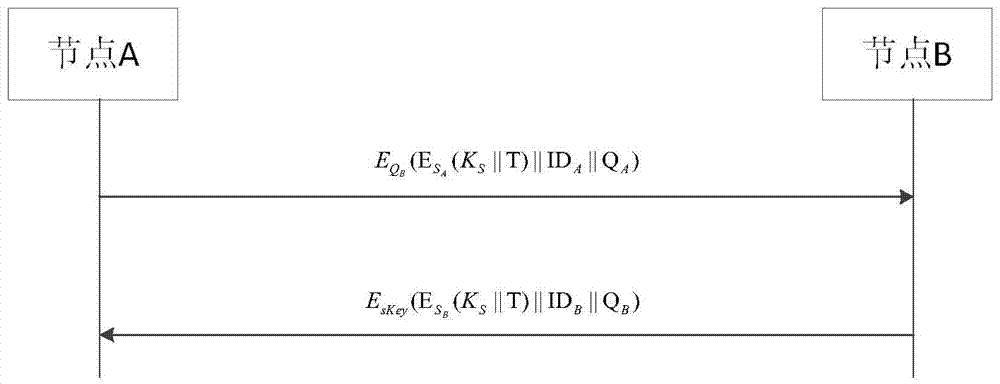Wireless sensor network key management method
A wireless sensor and network key technology, which is applied in the field of wireless sensor network key management, can solve problems such as limited computing power and storage capacity, insufficient communication bandwidth, and dynamic changes in network topology, so as to reduce search time and consumption, and achieve strong reliability. Scalability and the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The invention will be described in further detail below in conjunction with the accompanying drawings.
[0018] 1. Network formation stage:
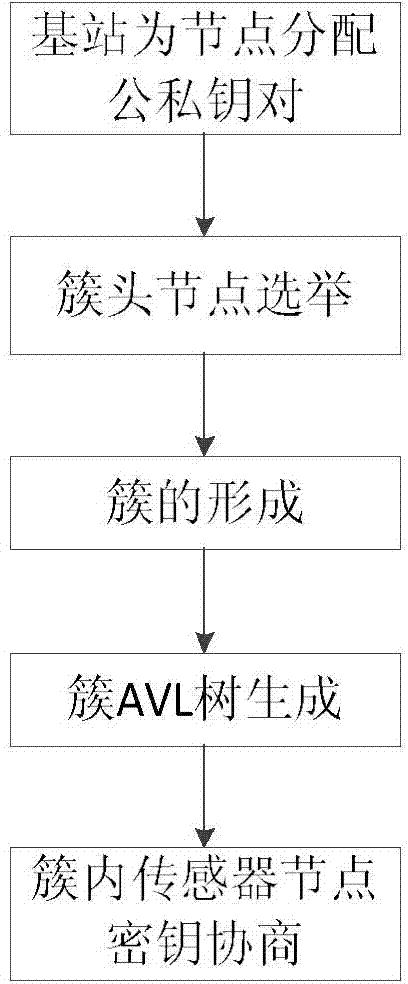
[0019] see figure 1 , the present invention is divided into 5 steps in the network formation stage.
[0020] (1-1) Key pre-distribution:
[0021] The base station sets certain parameters and distributes the public key Q to all nodes (including all cluster head nodes and sensor nodes) i and private key S i , and exist in the node. The base station generates the initial shared key K i , preset in all nodes.
[0022] (1-2) Cluster head node election:
[0023] In order to ensure that the high energy consumption cost of data transmission is evenly allocated to all sensor nodes, we use the LEACH algorithm to elect cluster head nodes from all sensor nodes. The specific method is: each sensor node sequentially generates a random number between 0 and 1, and the first sensor node smaller than the threshold T(n) becomes the cluster h...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com