Patents
Literature
266 results about "Numbering scheme" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
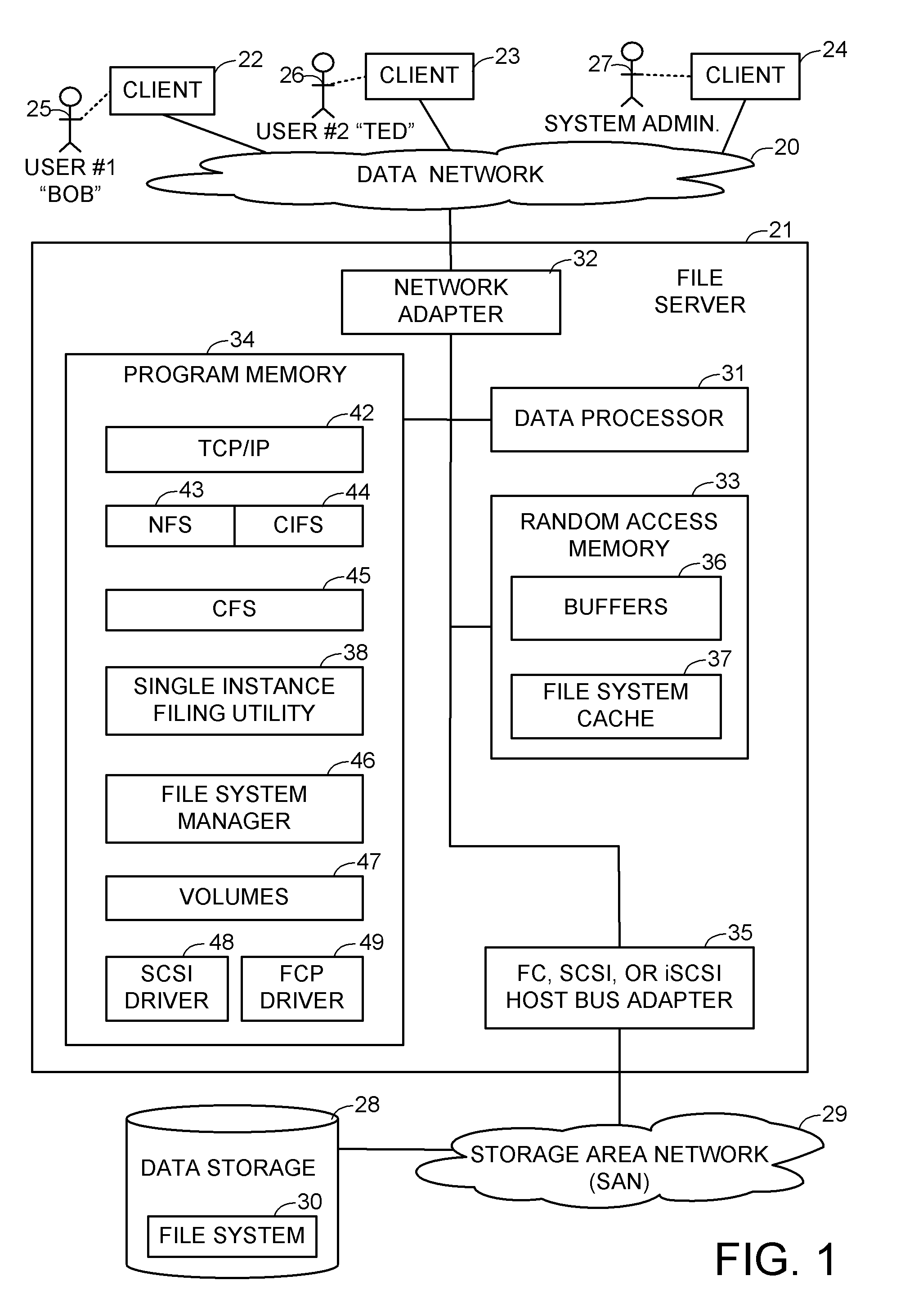
There are many different numbering schemes for assigning nominal numbers to entities. These generally require an agreed set of rules, or a central coordinator. The schemes can be considered to be examples of a primary key of a database management system table, whose table definitions require a database design.
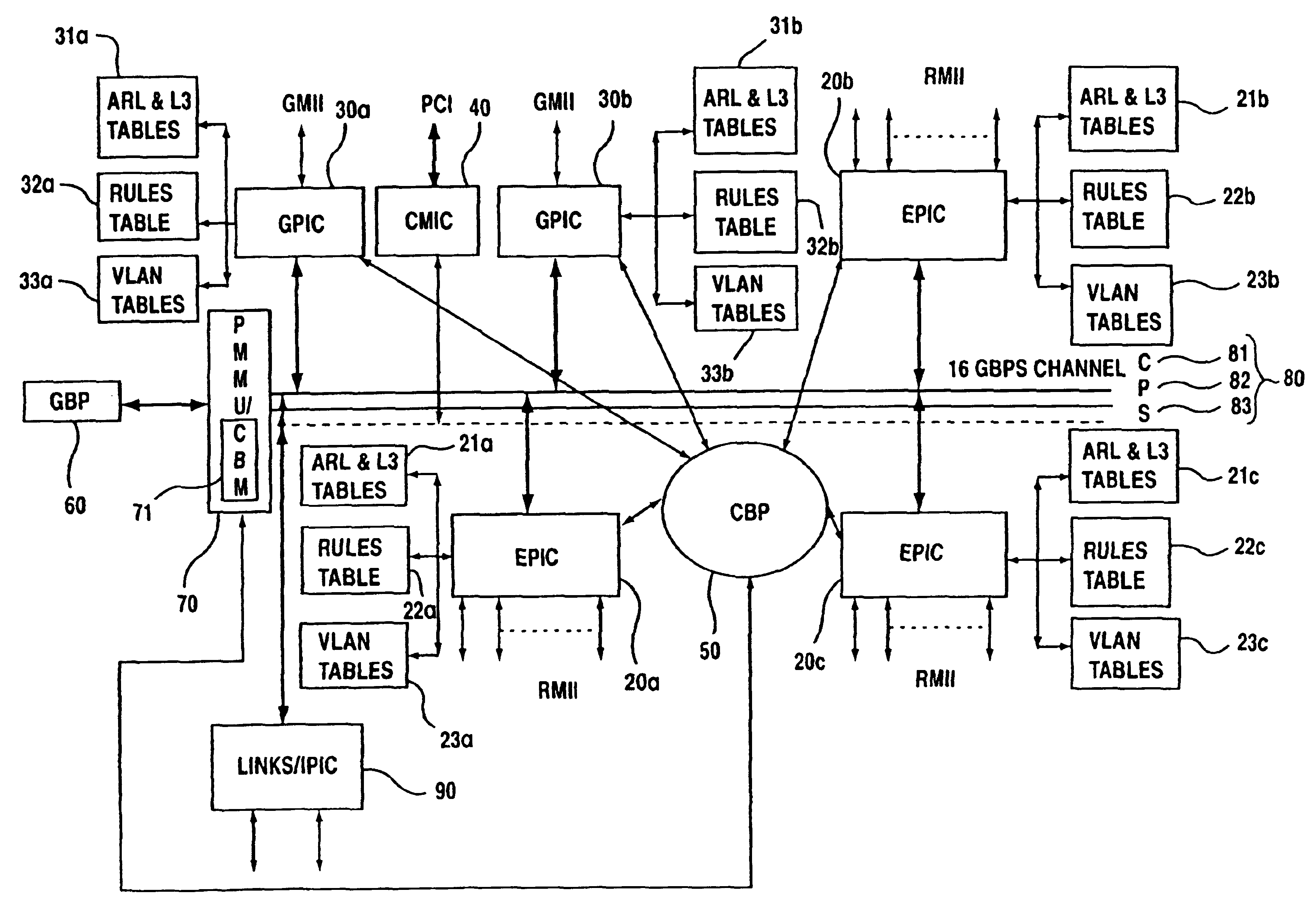
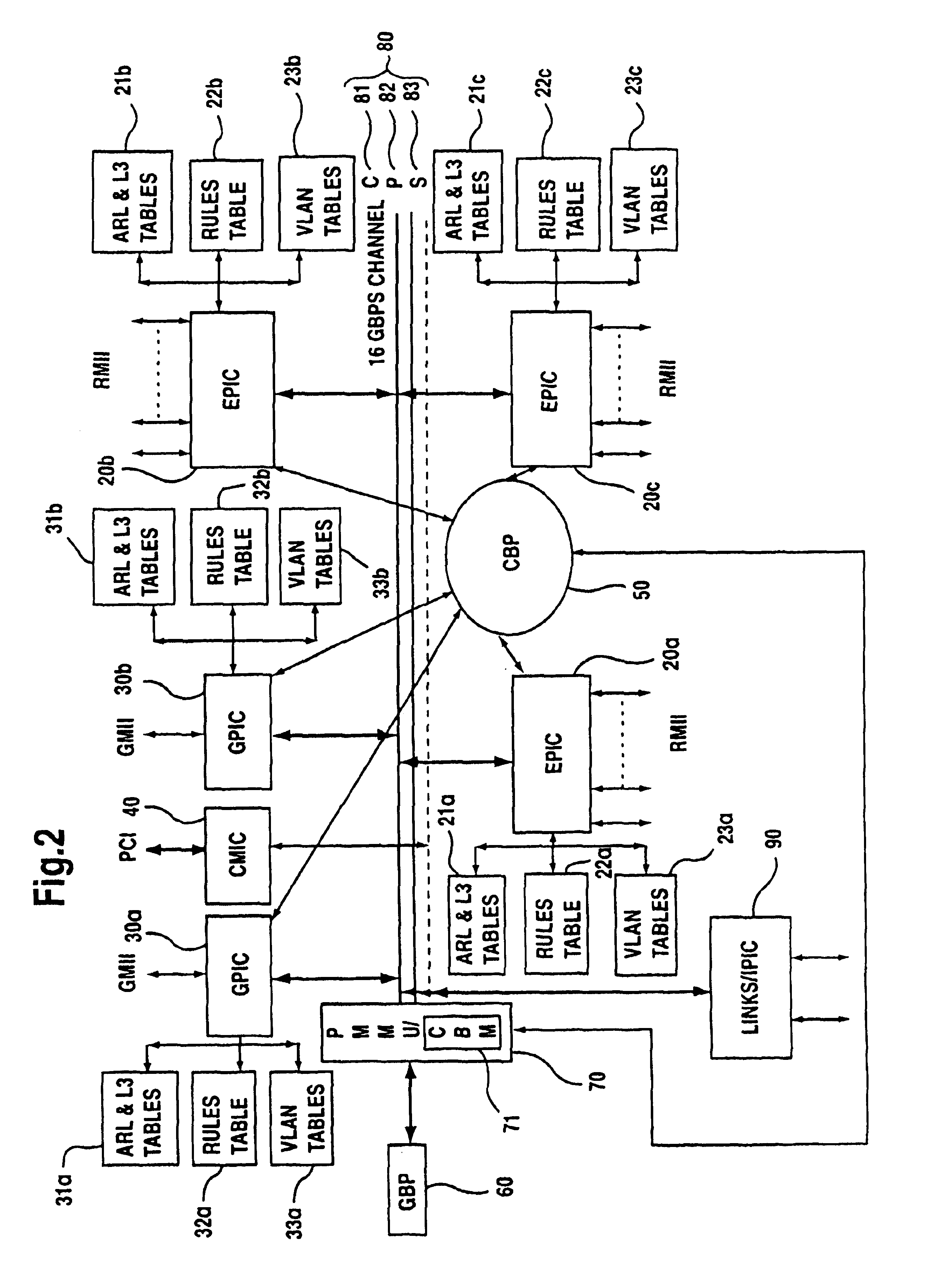
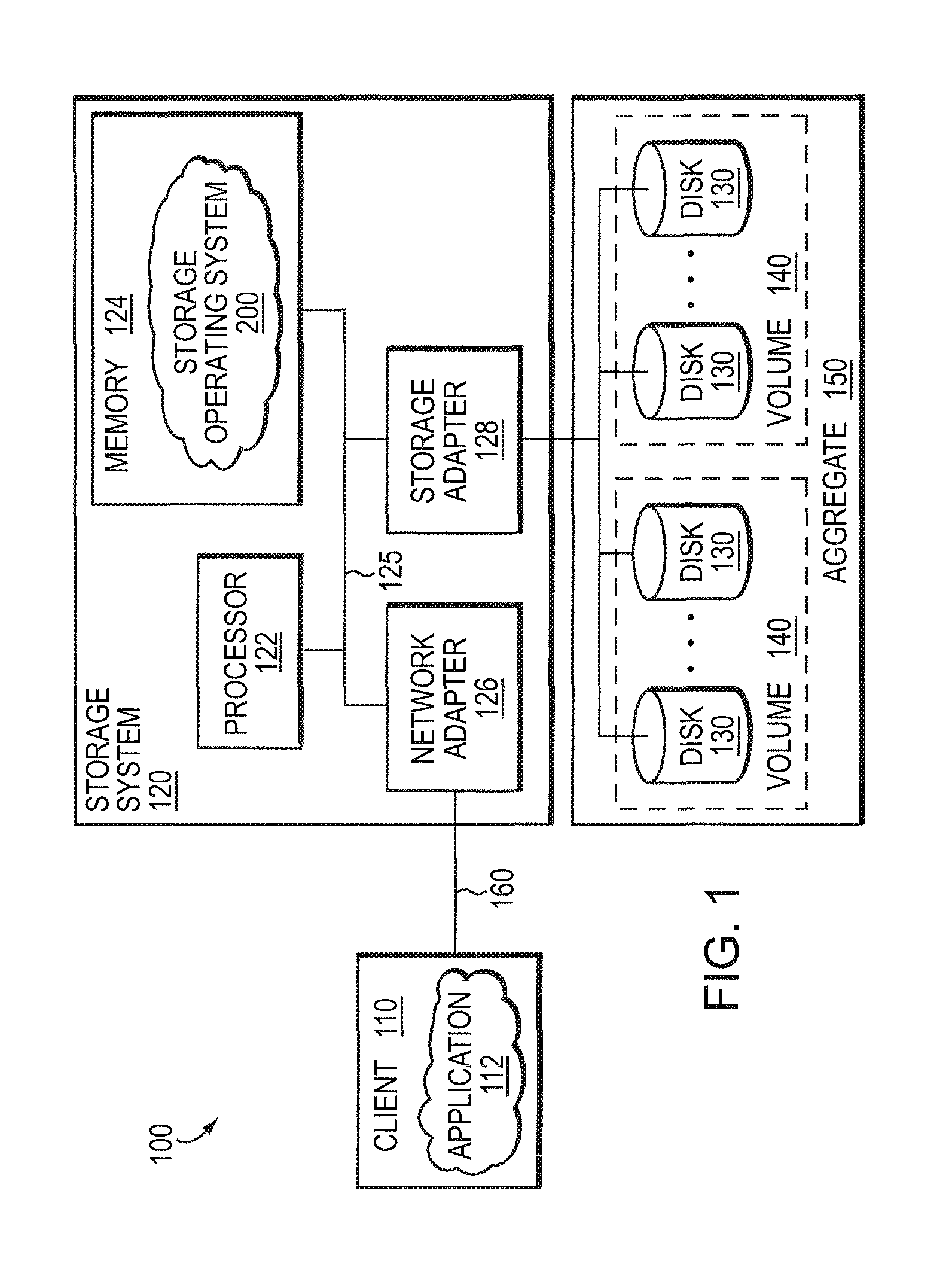
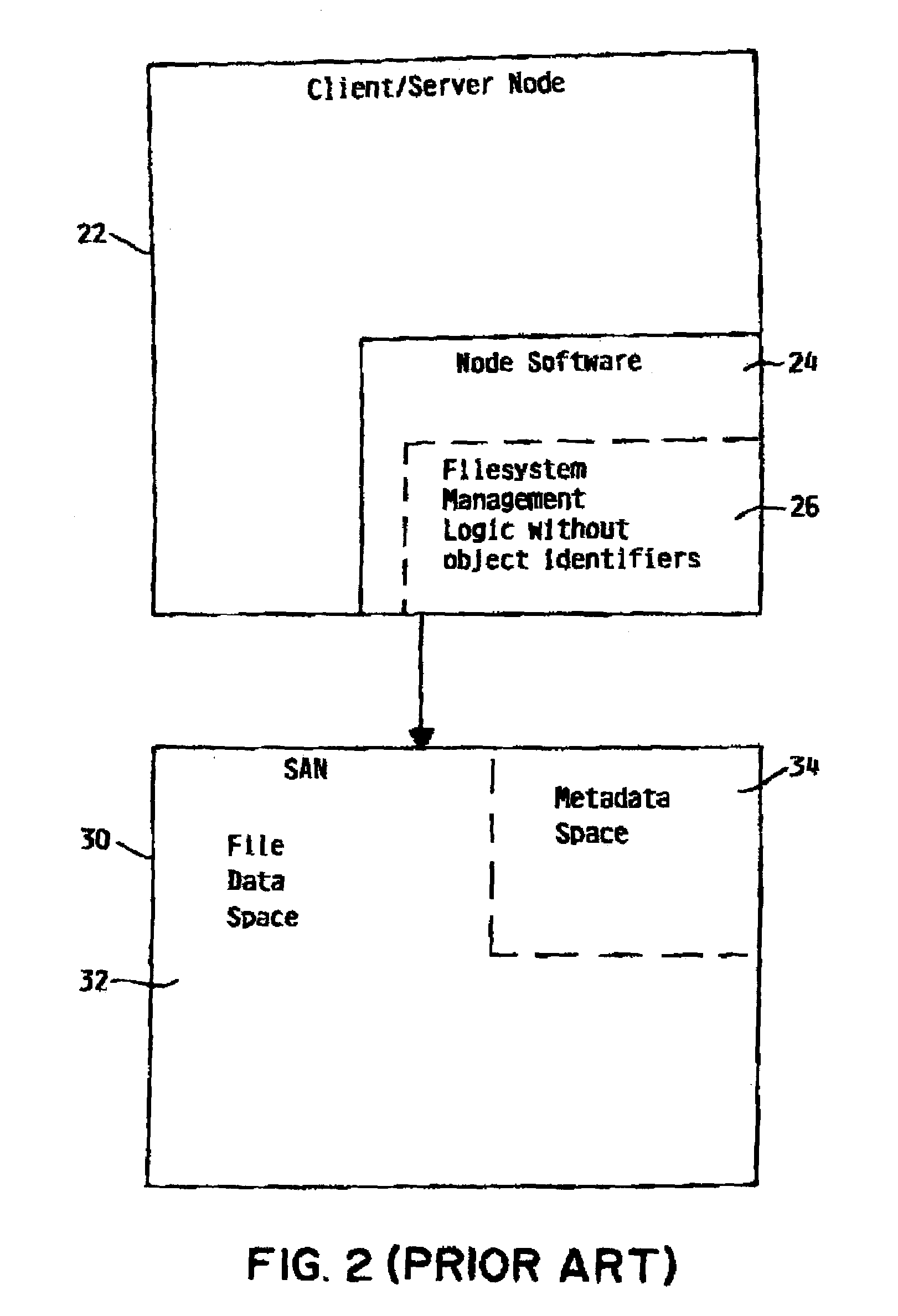
Linked network switch configuration
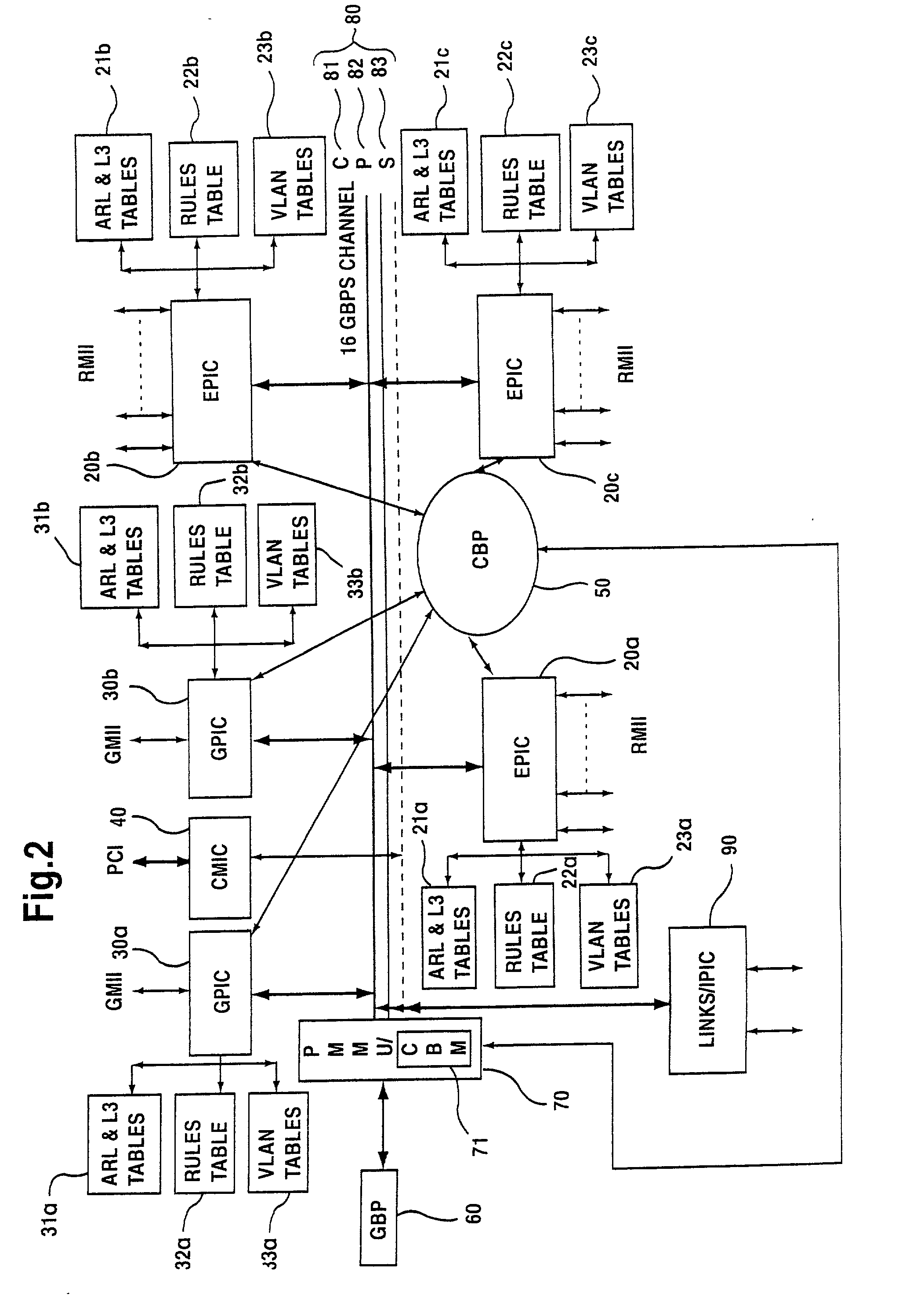
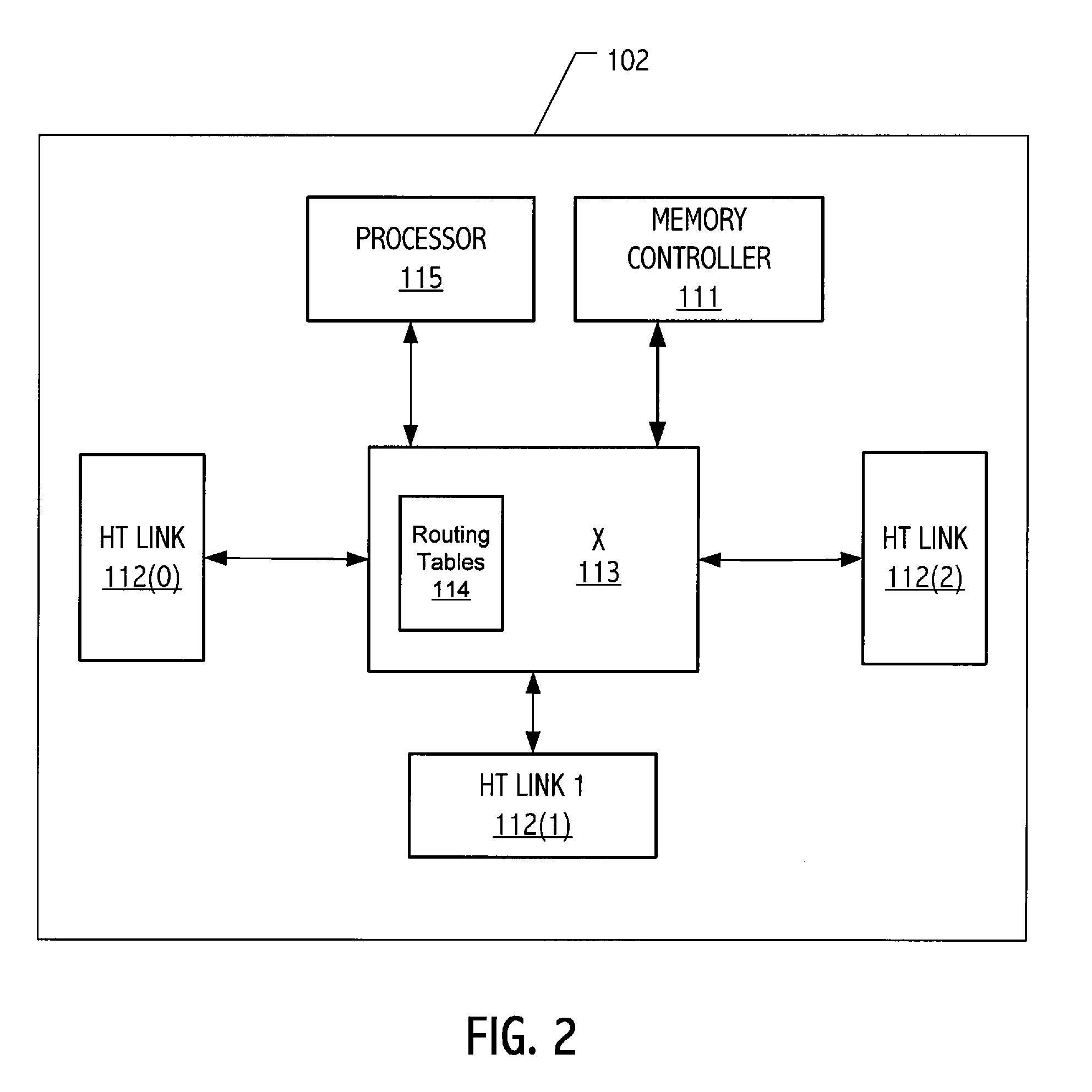
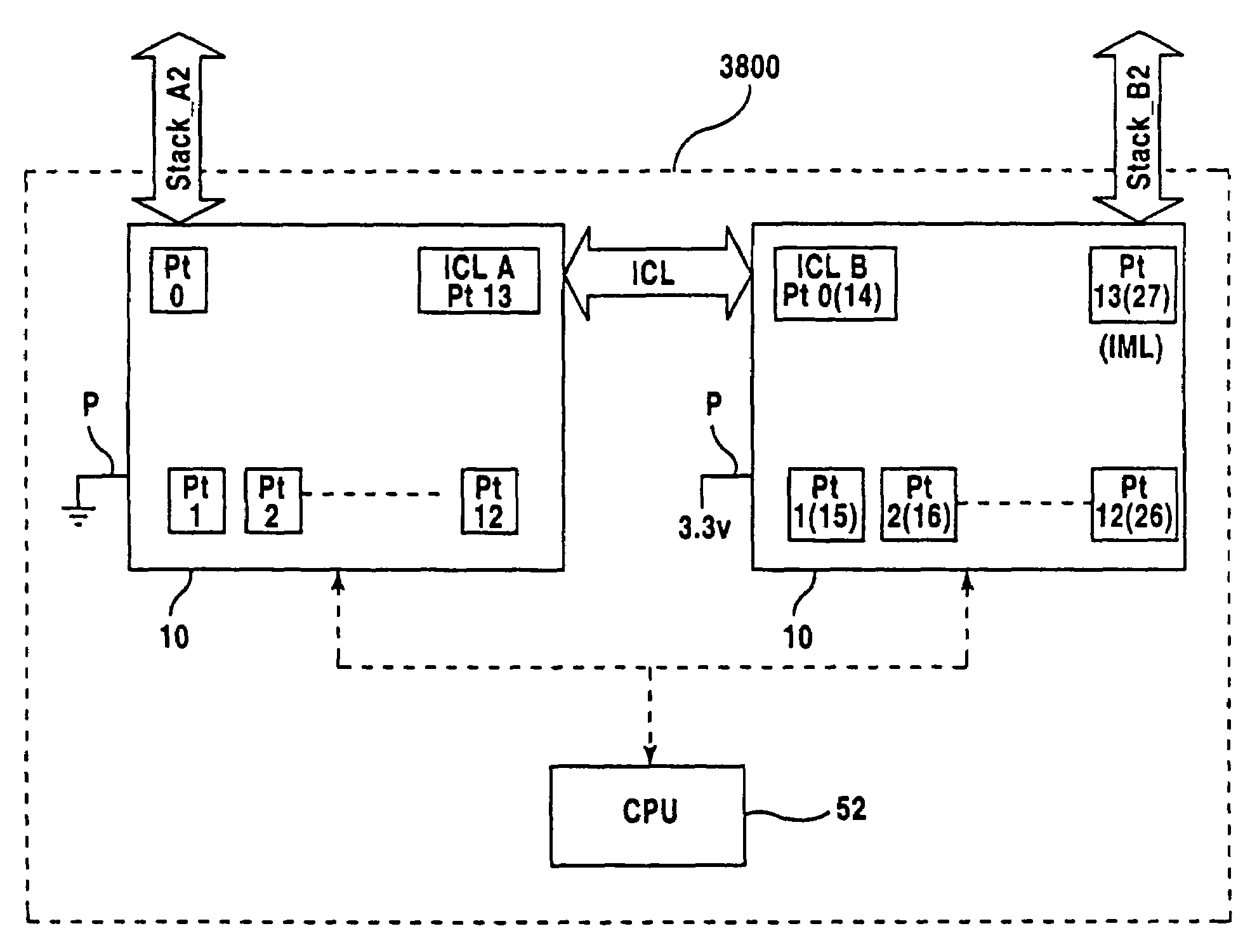
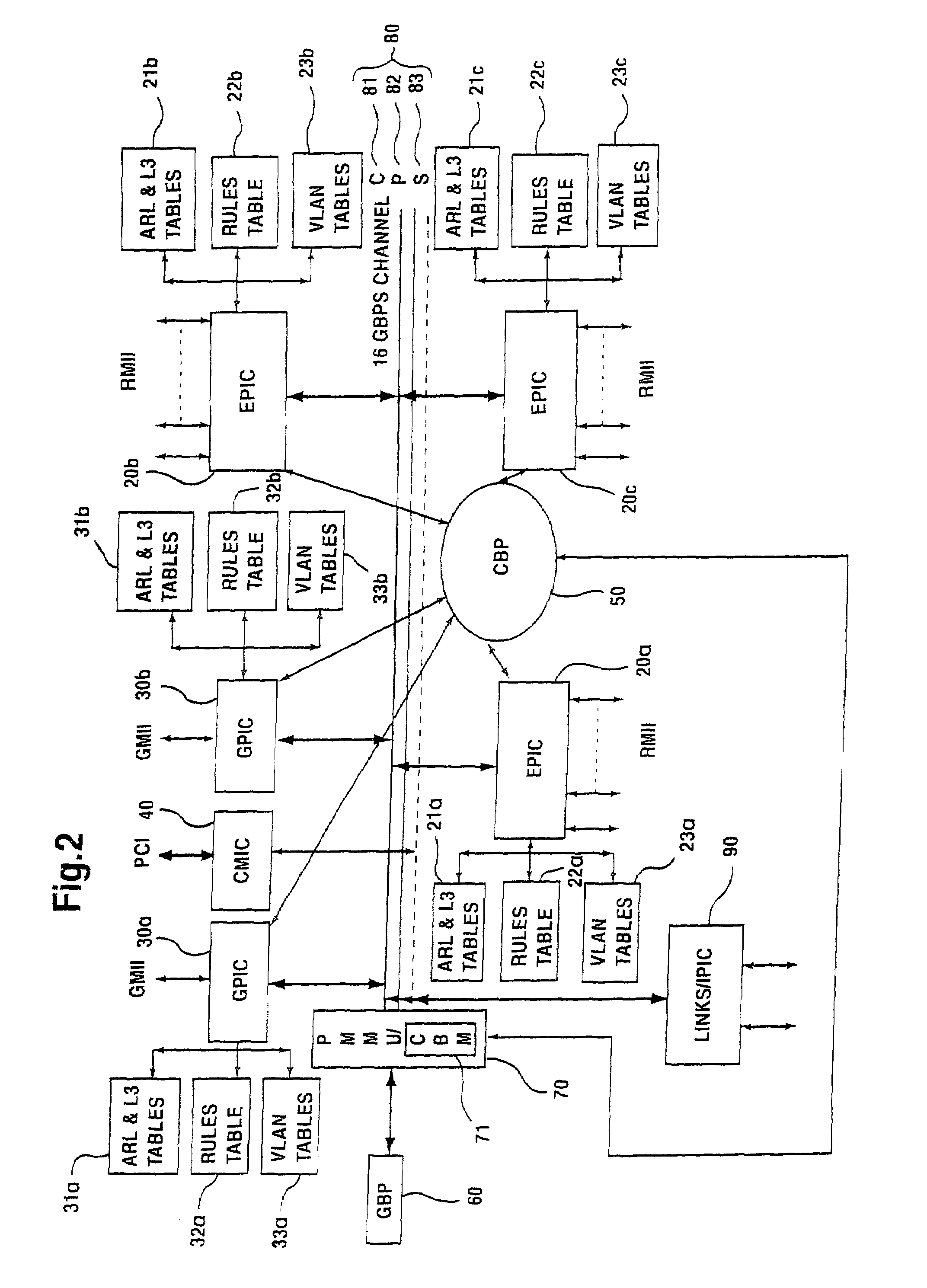
A network device includes a first switch, a second switch, address resolution logic (ARL), and a CPU. The first and second switch having a groups of ports which are a subset of the plurality of ports and are numbered by a different numbering schemes. The CPU coupled to the first switch and the second switch and configured to control the first switch, the second switch, and the ARL. A first link port of the first group of ports is coupled to a second link port of the second group of ports. The ARL is configured to perform address resolution based on the first and second numbering schemes such that when the first network port a data packet received at the first network port destined for the second network port is directly routed from the first network port to the second network port.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Fast transaction commit
InactiveUS7558883B1Few message delayMaintain consistencyError detection/correctionDatabase distribution/replicationClient-sideComputing systems
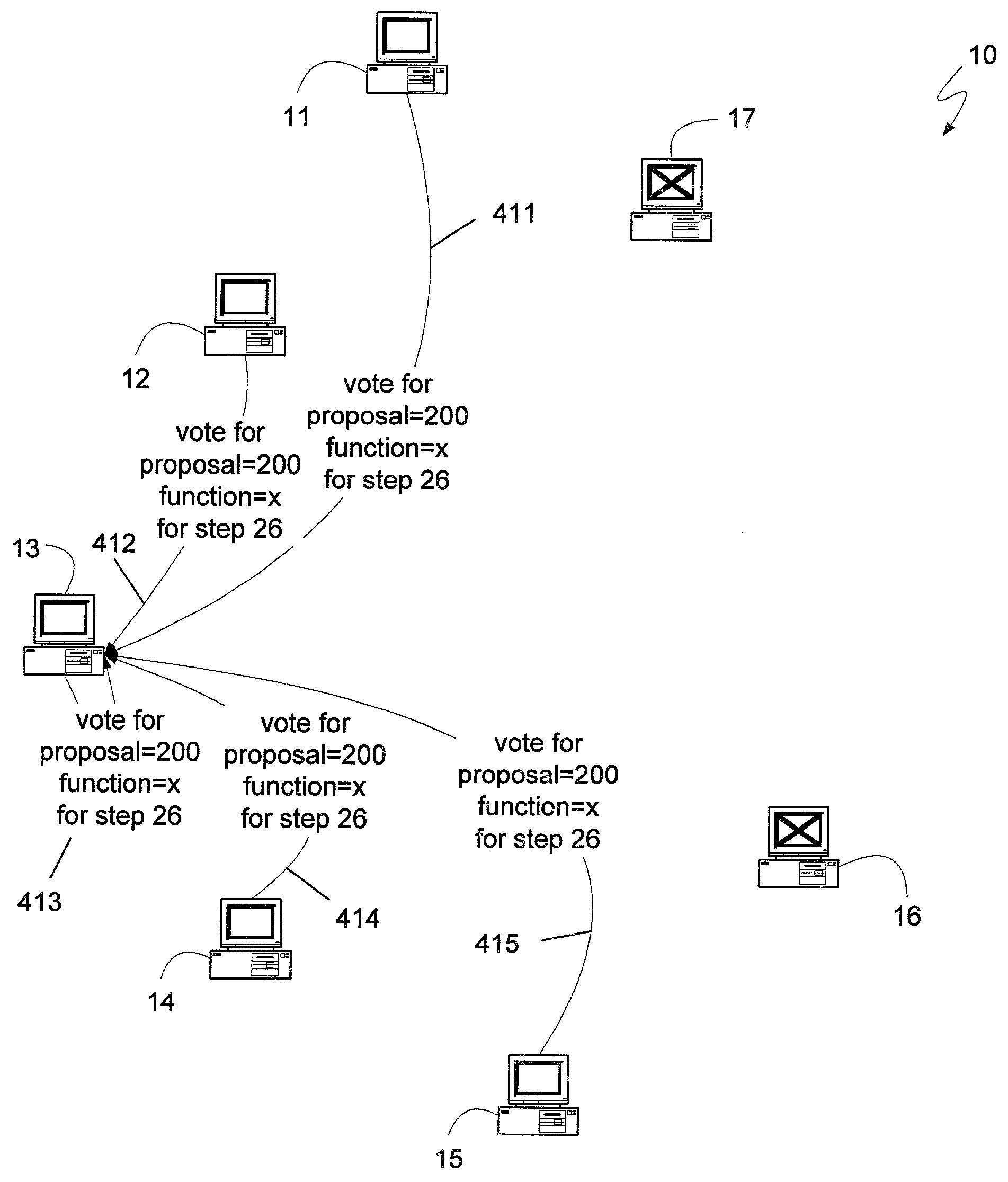
A distributed computing system, having a sufficient number of devices and requiring a sufficiently large number of devices to select any proposal, can maintain synchronization between its constituent devices and respond to client requests with as few as two message delays. A leader can synchronize the devices of the system and establish a safe proposal number for all current and future steps of the system. Devices can then receive client requests directly, treating the request as a proposal having the proposal number determined previously by the leader, and voting for the proposal. If the client receives an indication from a least a quorum of devices, where a quorum can be the minimum number of devices that can be operational at a given time, the client can know that the request was selected. If two or more clients attempt to request different functions at approximately the same time, the system may not select either request, in which case a leader can be requested to determine if any requests may have been selected, and to reestablish a safe proposal number. Systems with fewer devices can also implement the message-delay-reducing algorithm if they can also revert to the standard Paxos algorithm if an insufficient number of devices are operational. Such algorithms can be used to provide an efficient method for determining whether to commit or abort a client transaction.
Owner:MICROSOFT TECH LICENSING LLC
User-oriented cloud storage data integrity protection method
InactiveCN105320899ASave storage spaceAvoid Lost Security RisksDigital data protectionData integrityOriginal data
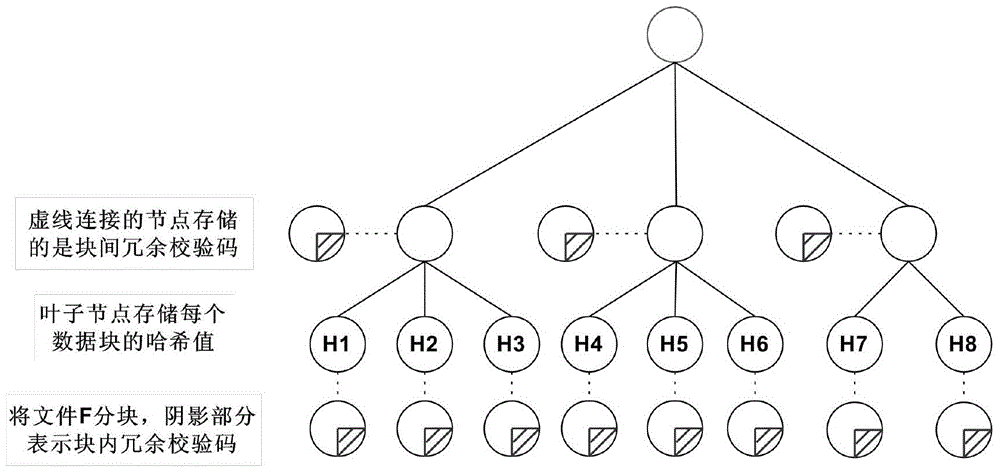
The invention discloses a user-oriented cloud storage data integrity protection method. The method includes the steps of 1, uploading, wherein a user side segments and numbers a file to generate intra-block redundancy check codes, the hash value of each file block is calculated and saved as a range-based 2-3 tree, the hash values are linked into one value and signed with private keys, and inter-block redundancy check codes are generated and encrypted with stream substitution secret keys; 2, verification, wherein a cloud management node sends a verification request to a corresponding cloud storage server, corresponding original data and algebraic signatures of the inter-block redundancy check codes corresponding to the original data are calculated and returned to the user side for data integrity verification, and the step 3 is executed if data destruction is found; 3, recovery, wherein the user side acquires all the file blocks on corresponding branch trees from a cloud side according to tree information and performs error recovery on the file blocks through erasure codes of the file blocks. According to the method, integrity verification and recovery are performed on the dynamic data stored in the cloud side from the user perspective.
Owner:PEKING UNIV
International information search and delivery system providing search results personalized to a particular natural language
Documents containing information about product offerings in various natural languages are passed through transitional translation layers which convert the data to a single computer language using a universal character set encompassing the character sets used in all supported natural languages. The documents are stored in their original natural languages and in English with documents segmented into components which components are identified by search terms arranged in a taxonomy tree based on product types. The names of the products in the national languages are added to the English language documents enabling quick keyword searches when the product name or number is known. A bi-directional inverted index is provided for access by the keyword search terms so that keywords with the same meaning in different languages are accessible together when the keyword in one of the languages is queried.
Owner:IBM CORP
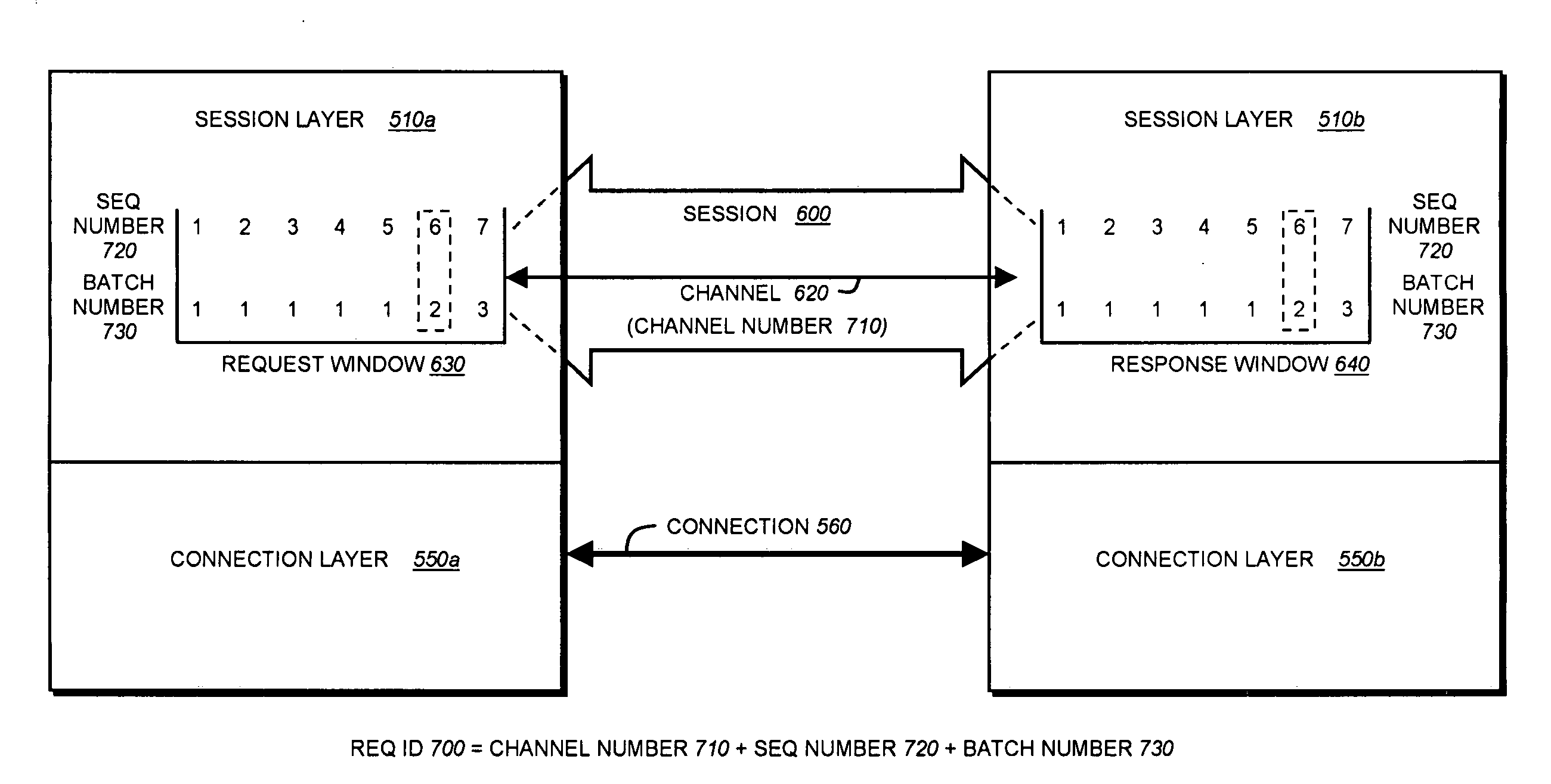
System and method for specifying batch execution ordering of requests in a storage system cluster
ActiveUS7657537B1Digital data processing detailsDigital computer detailsUnique identifierSerial code
A system and method specifies batch execution ordering of requests in a cluster of storage systems or nodes. Each node is generally organized as a network element and a disk element. One or more sessions are established between the elements in the cluster. Each session comprises a plurality of channels disposed over connections, wherein each channel enables multiple requests to be sent over a connection. Each request is identified by a unique identifier (“request id”) that is generally defined as the combination of a channel number and a sequence number. The request id is extended to include a batch number that provides an execution ordering directive within a channel. All requests with the same batch number in a channel can be executed in arbitrary order or concurrently. Ordering is imposed only when the batch number changes, e.g., increases. Although more than one request in a channel can have the same batch number, all requests with the same batch number are executed before any request with a higher batch number.
Owner:NETWORK APPLIANCE INC
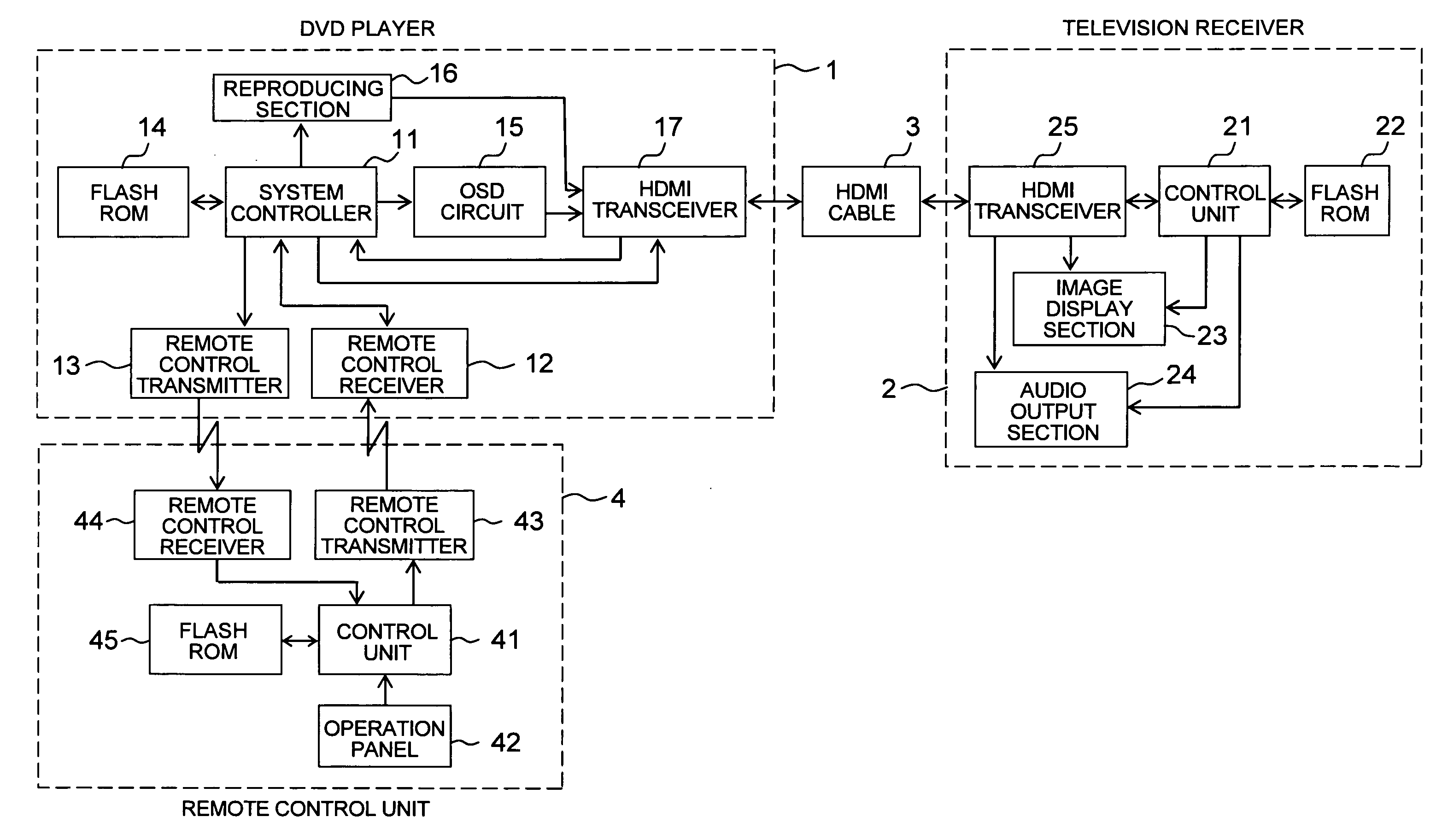
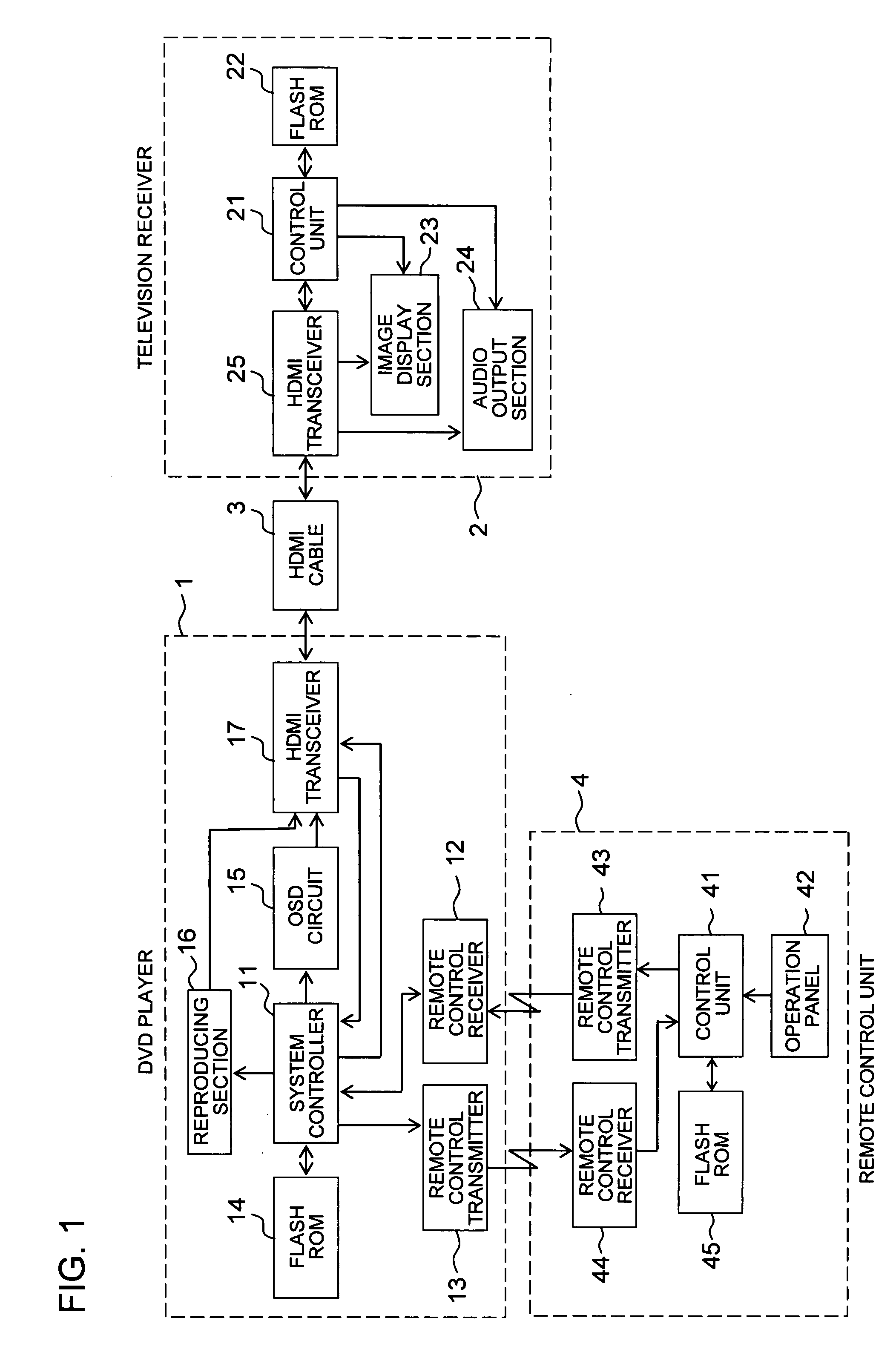
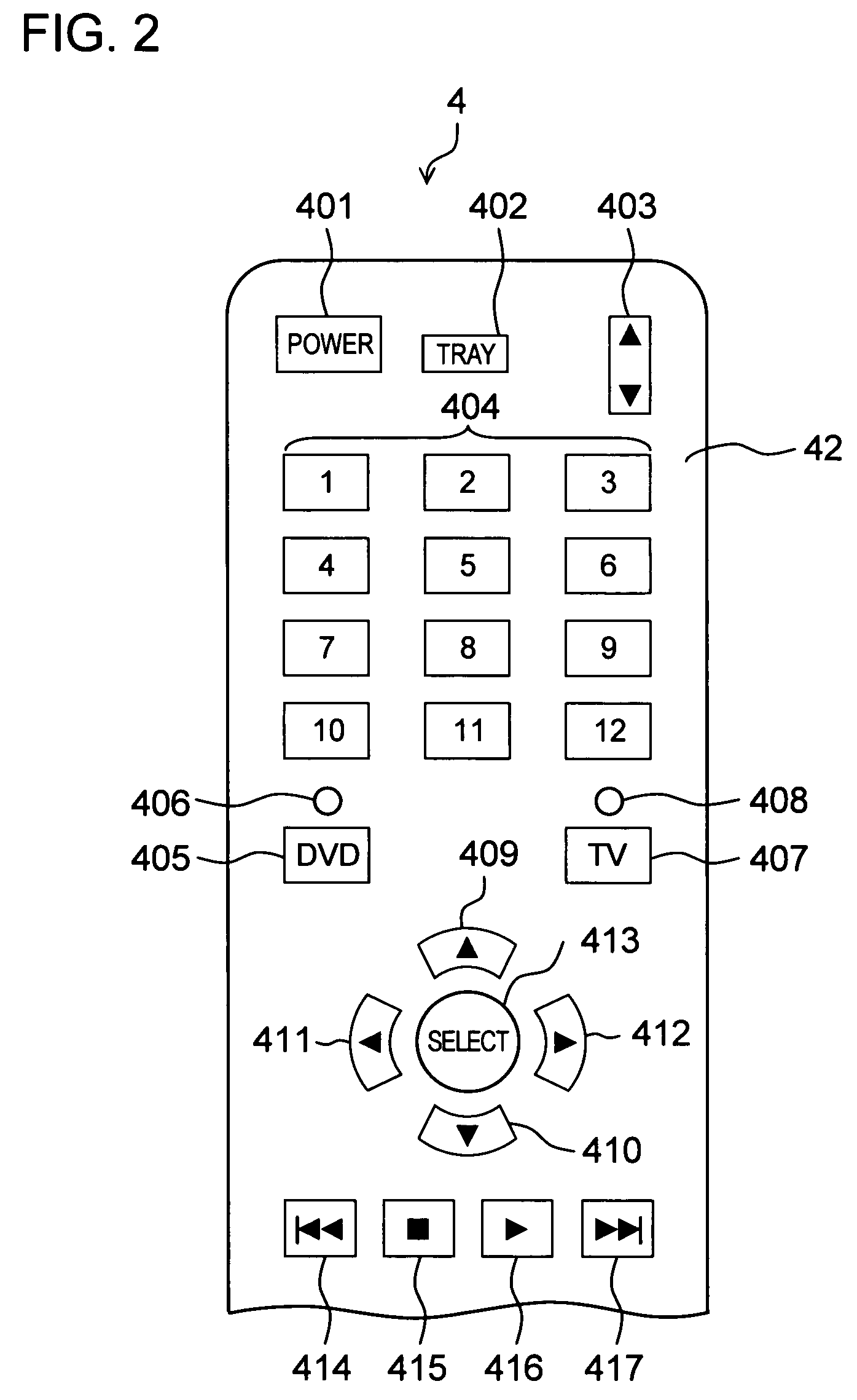
Remote operation system
InactiveUS20080088495A1Improve usabilityLow costInput/output for user-computer interactionTelevision system detailsOperational systemTelevision receivers
When a television receiver is connected to a DVD player via an HDMI cable, HDMI authentication is carried out. EDID data is then acquired from the television receiver and a manufacturer name is determined. When the manufacturer name is determined to be, for example, “company A”, a table indicating a correspondence relationship of manufacturer names and remote control codes is referred to and remote control codes corresponding to the determined company A are selected. The selected remote control codes are then transmitted after selection of remote control codes of the company A is carried out. Remote control codes corresponding to the manufacturer name of the company A received from the DVD player are then stored in a memory in a manner corresponding to operation key numbers allocated in advance to a plurality of operation keys at a remote control unit.
Owner:FUNAI ELECTRIC CO LTD
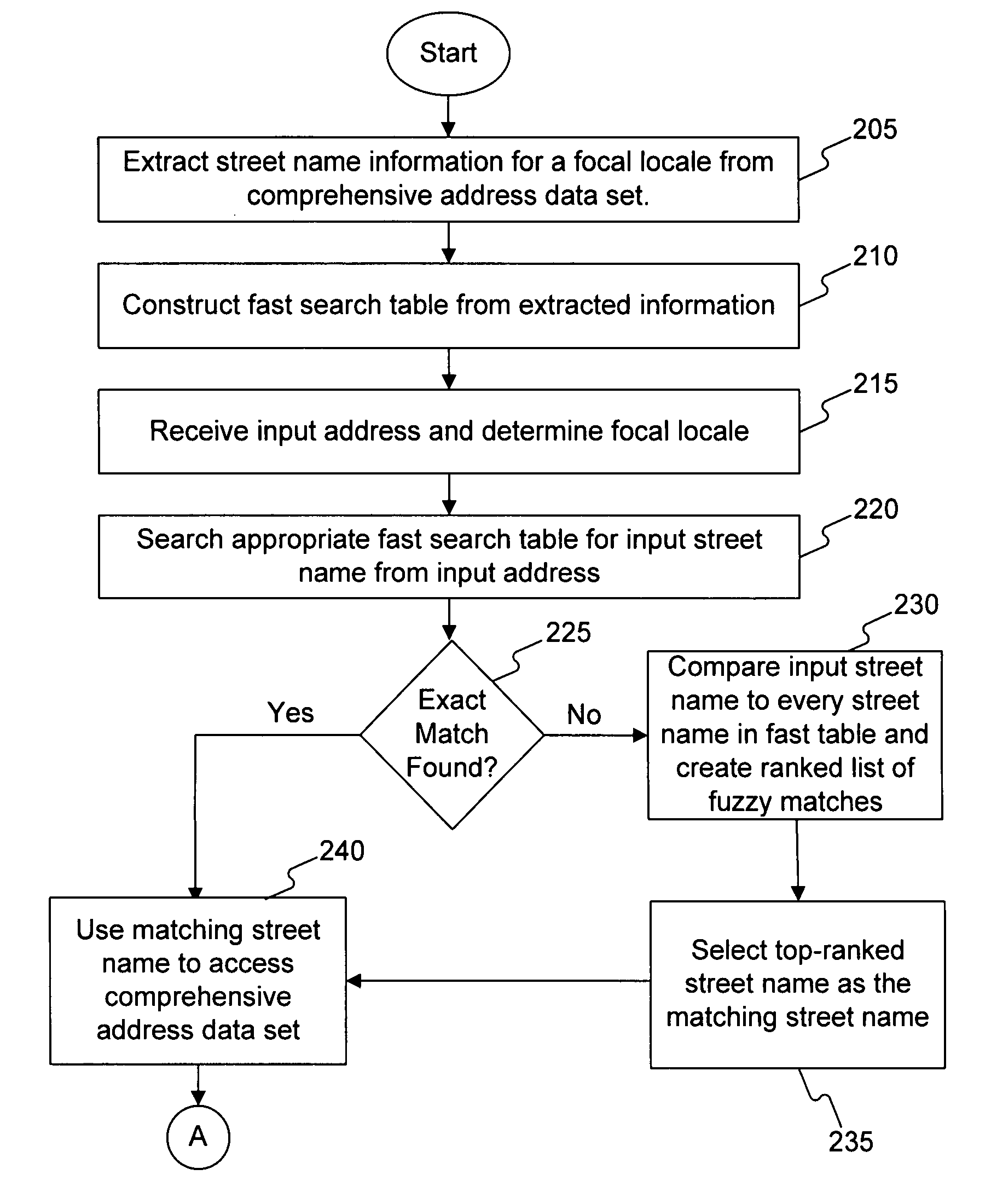
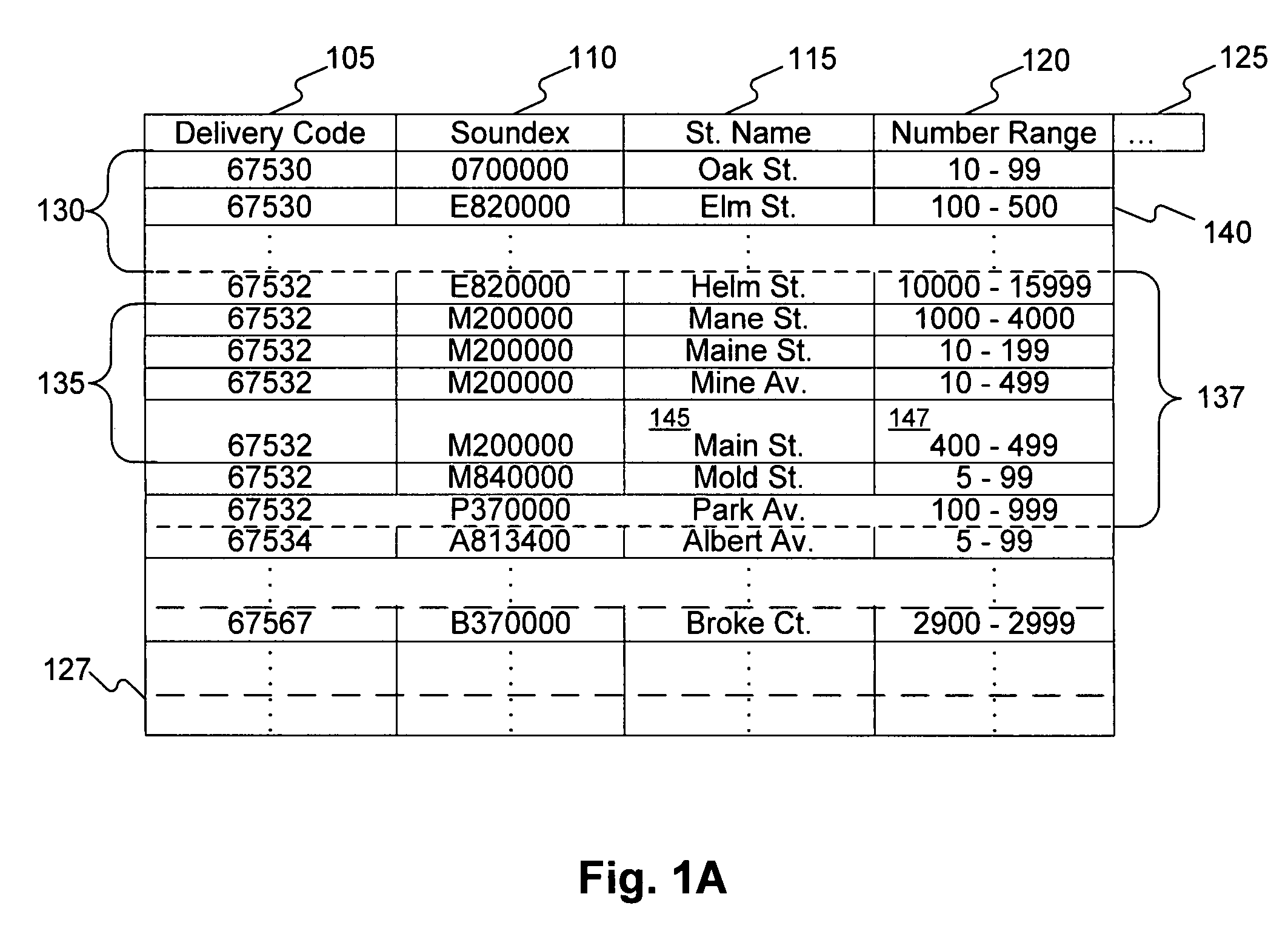
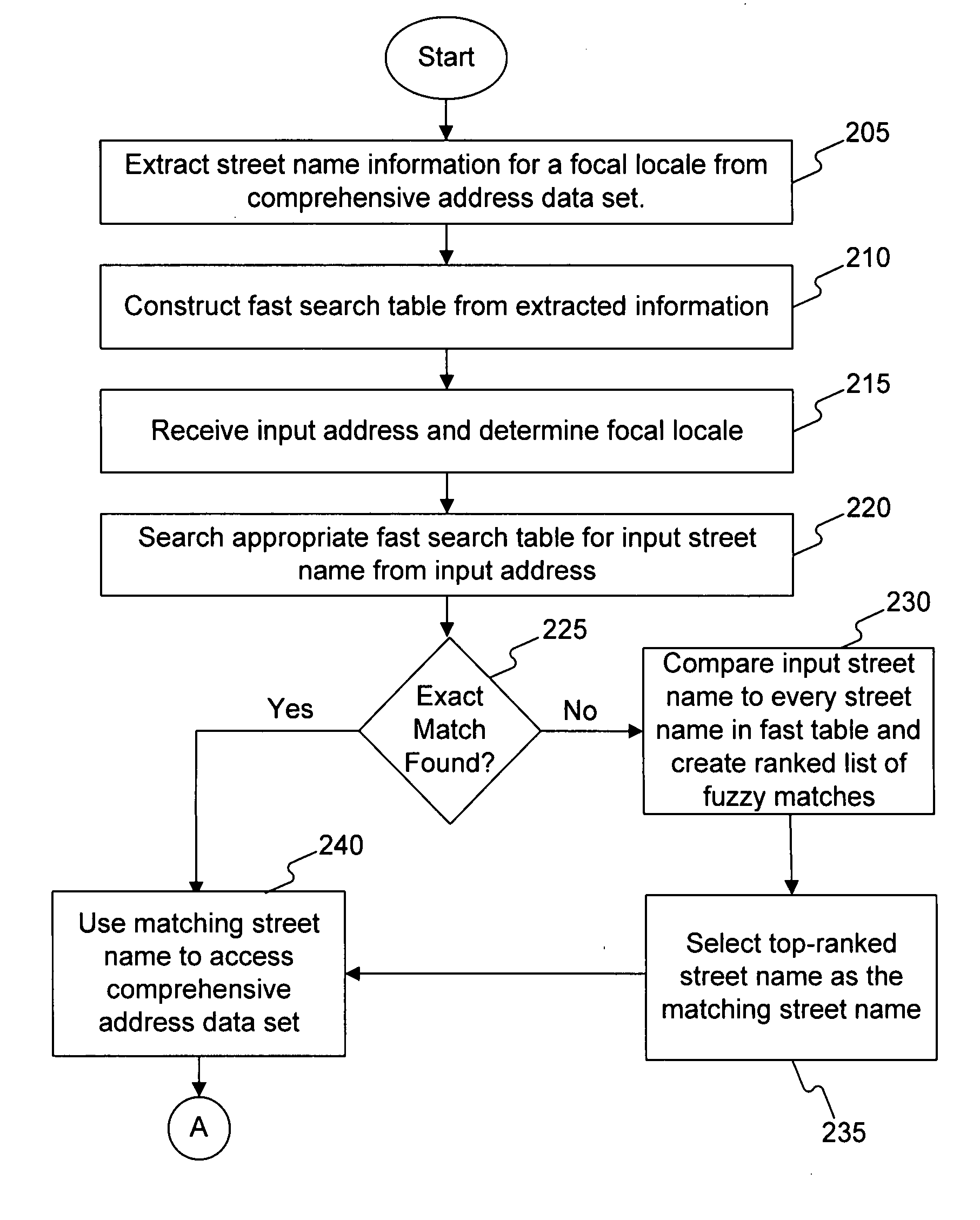
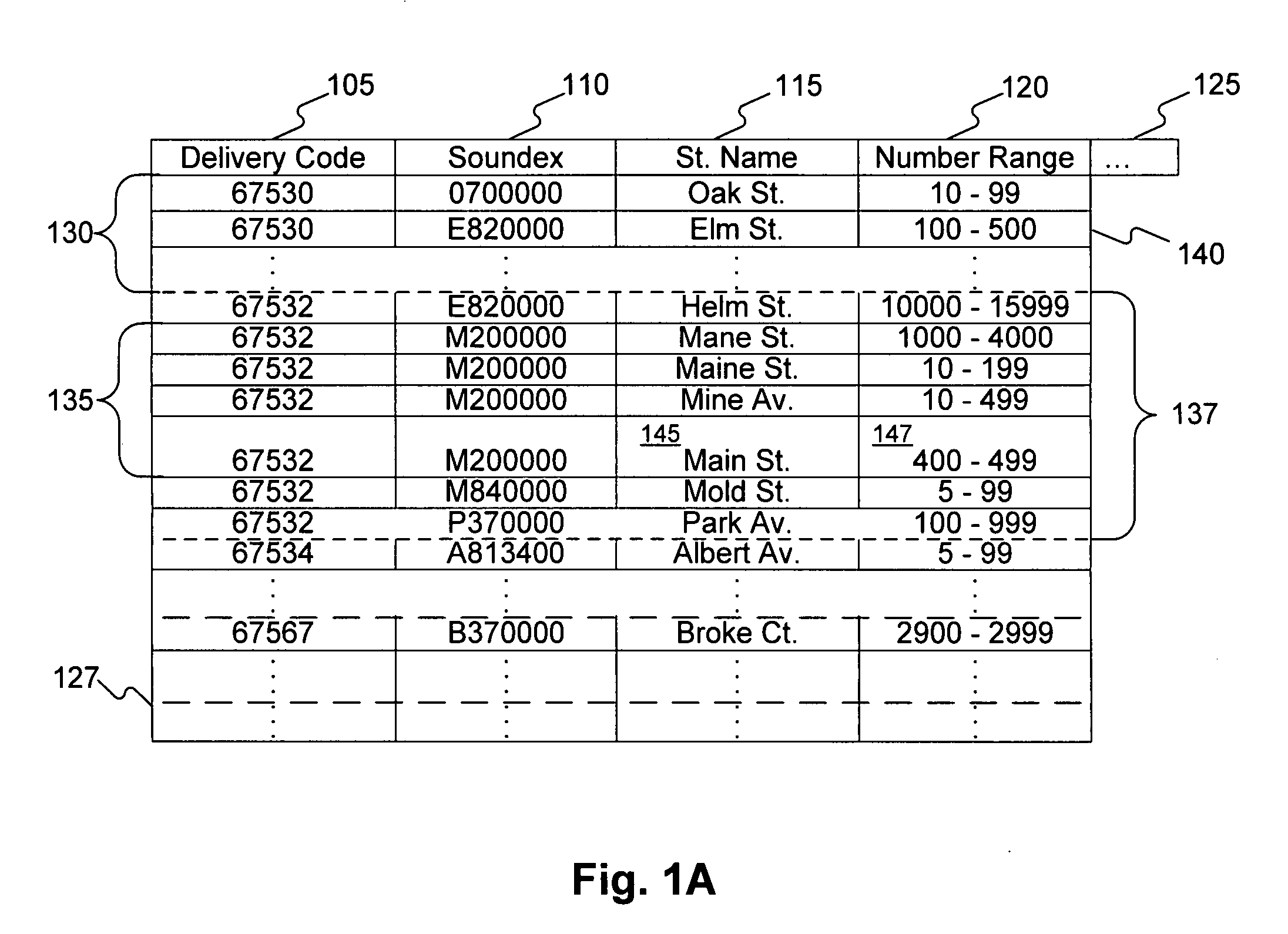
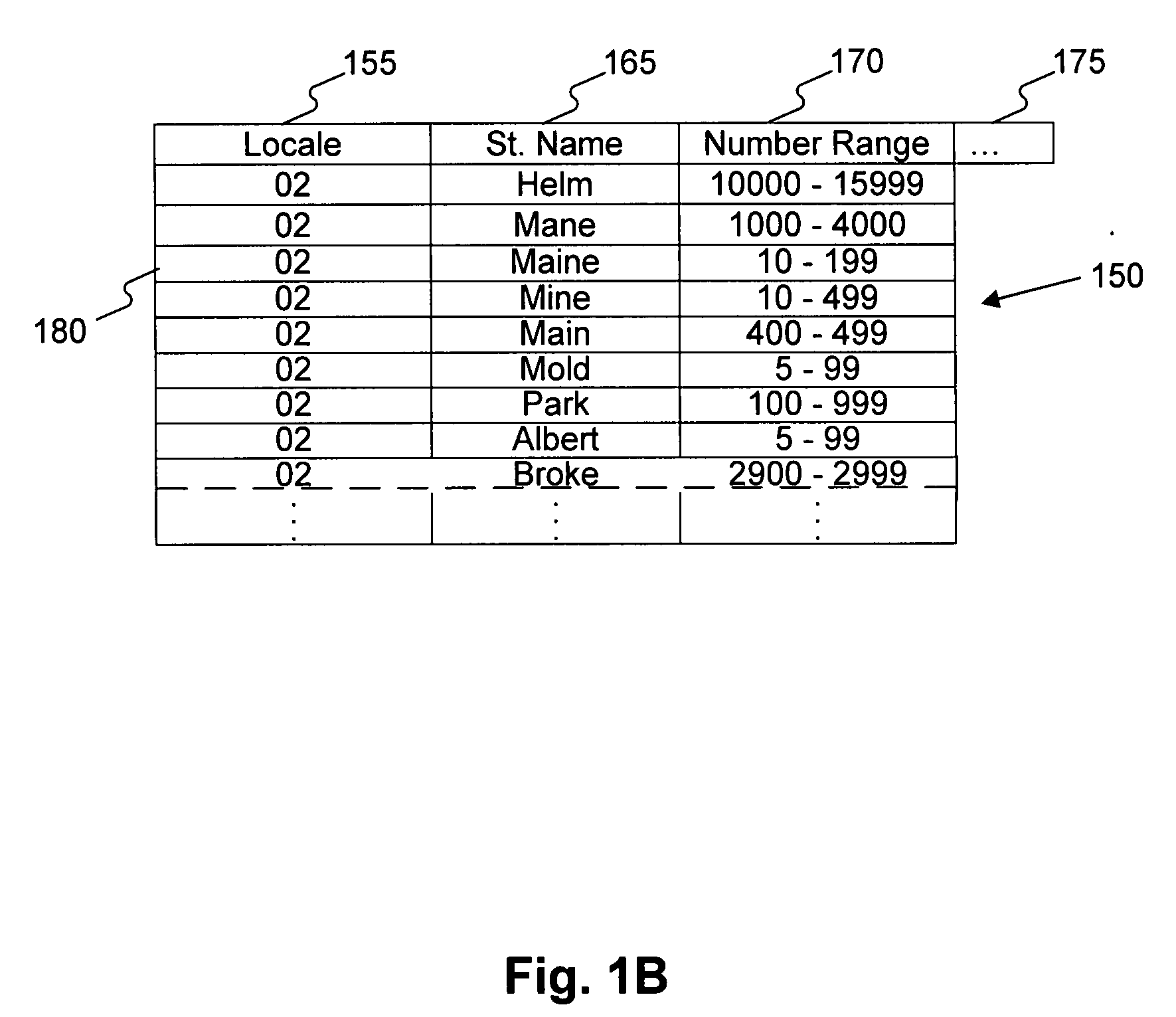
Systems and methods for validating an address
Systems, methods, and software determine whether a field of an input digital representation of information, such as the street name field in an address, is correct by quickly comparing the field to a list of valid choices for that field. The list of valid choices is generated based on information from the input digital representation, such as a character string. If an exact match is not found, a fuzzy match comparison determines the most closely matching valid choice. If a suitable fuzzy match is not found, then the input information is invalid. Otherwise, another field of the input information, such as the building number field of an address, is tested for validity. If the second field passes the validity check, then the fuzzy match (or exact match) for the field is valid. A fuzzy matching field may replace the input field, thereby correcting the input information.
Owner:US POSTAL SERVICE
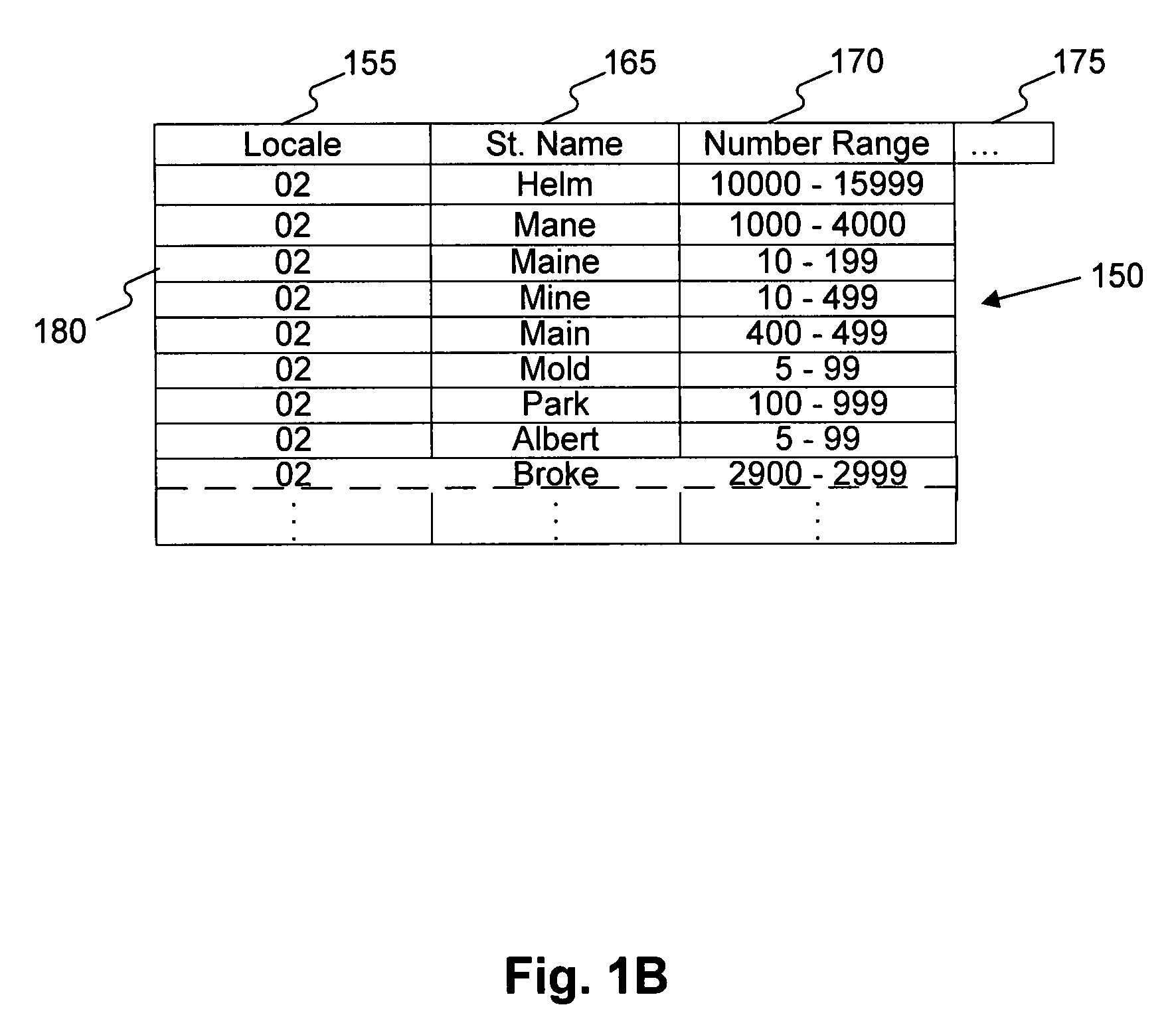
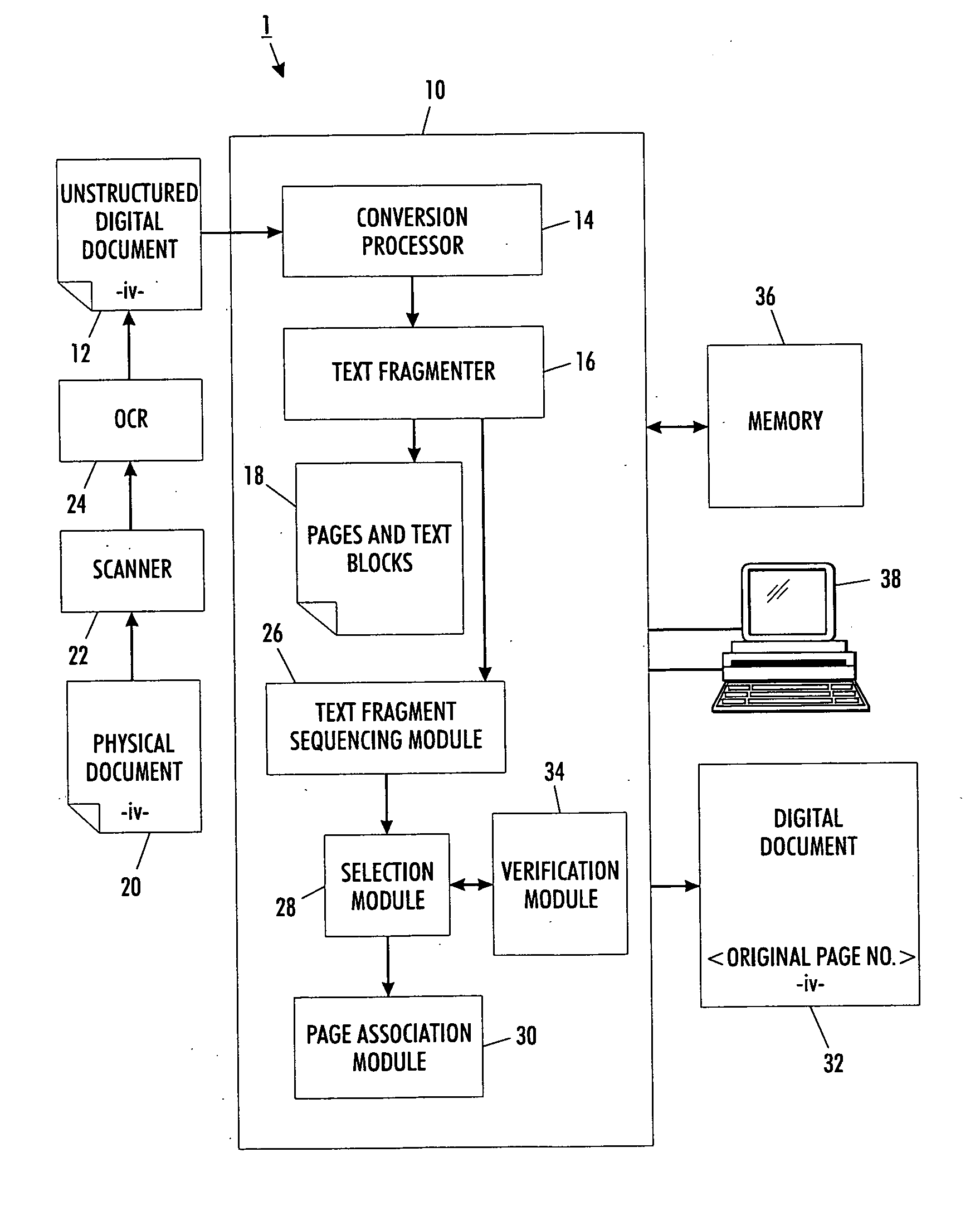
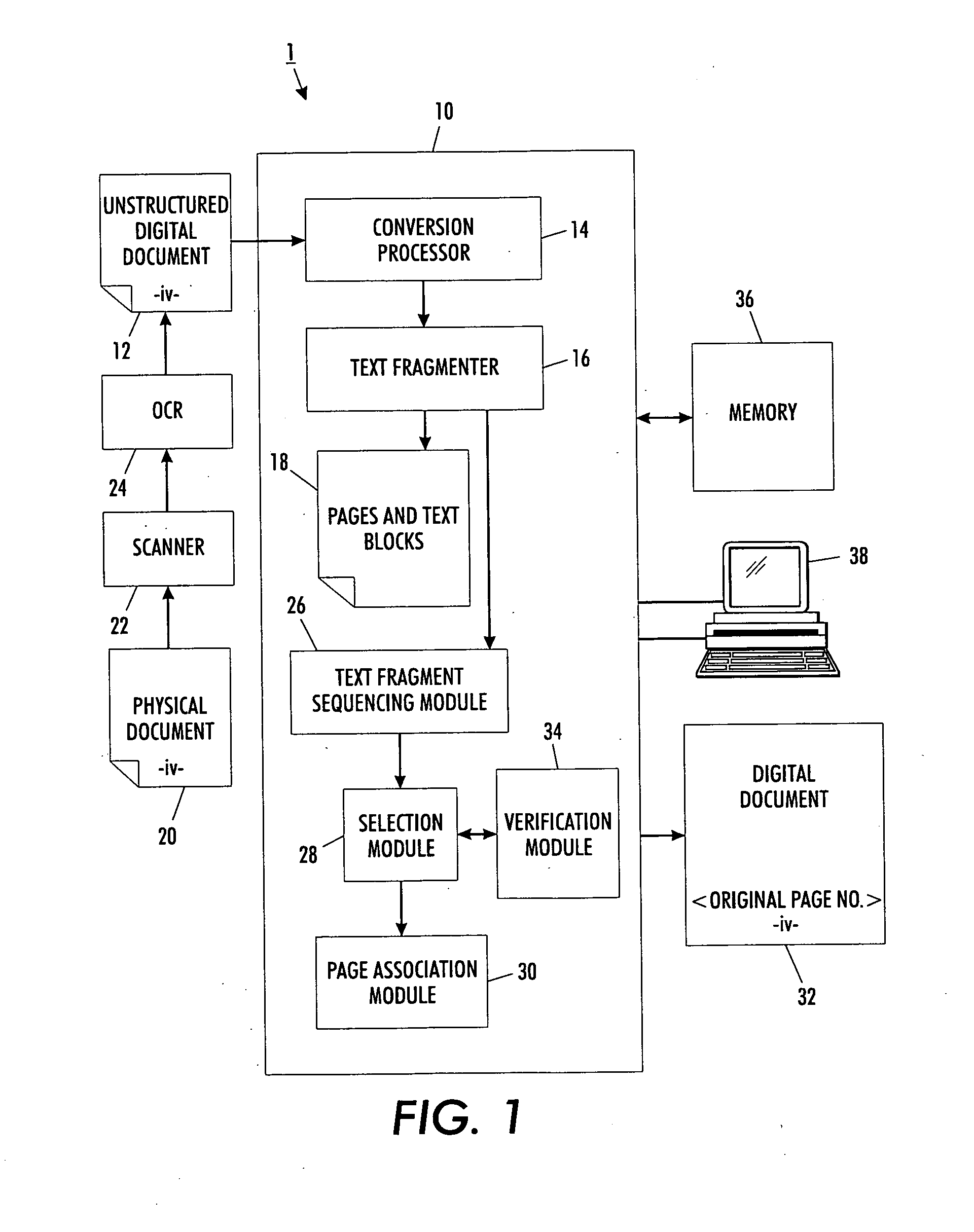
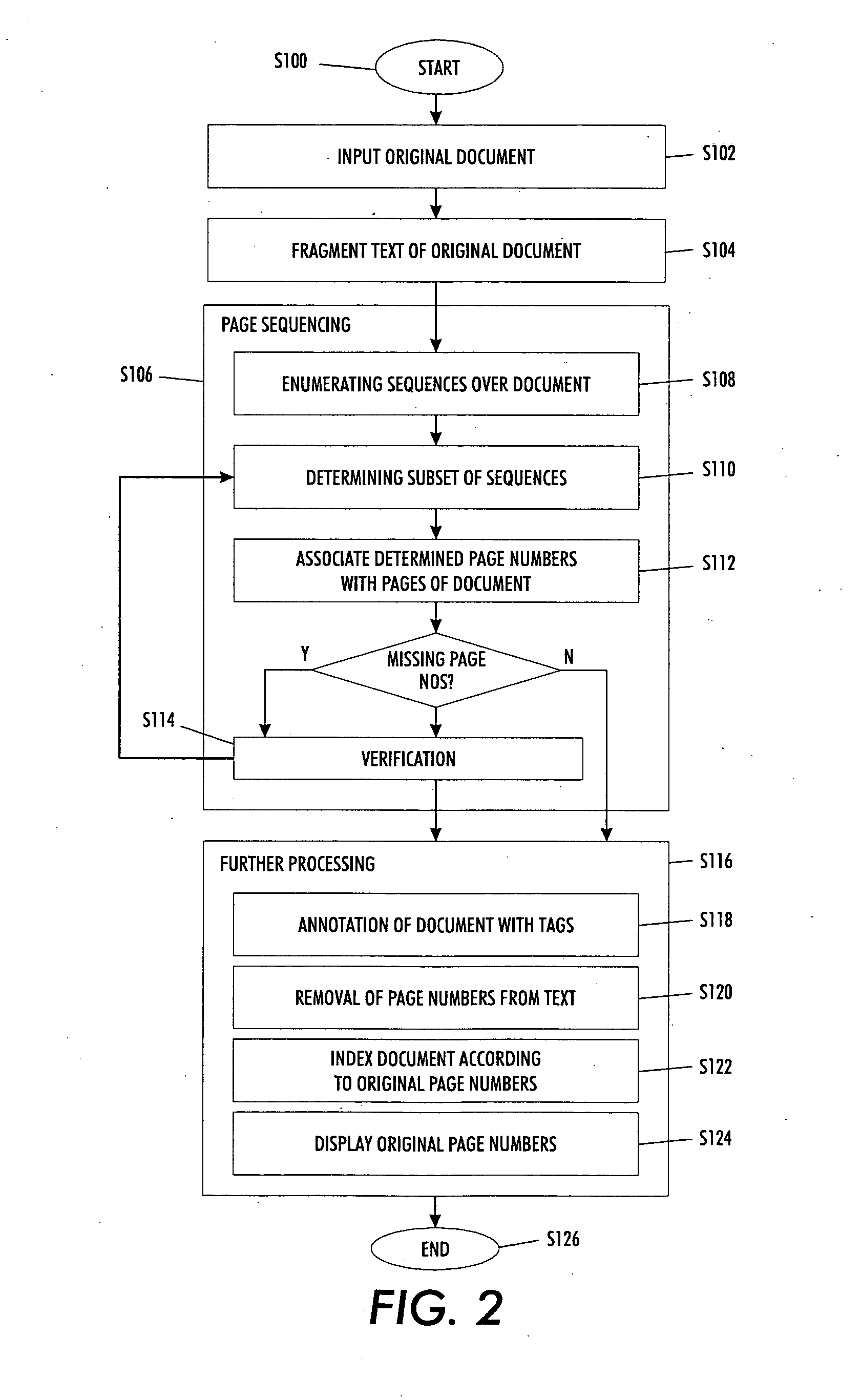
Versatile page number detector
InactiveUS20080114757A1Digital data information retrievalCharacter and pattern recognitionRecognition sequenceDocument preparation
A method for detection of page numbers in a document includes identifying a plurality of text fragments associated with a plurality of pages of a document. From the identified text fragments, at least one sequence is identified. Each identified sequence includes a plurality of terms. Each term of the sequence is derived from a text fragment selected from the plurality text fragments. The terms of an identified sequence comply with at least one predefined numbering scheme which defines a form and an incremental state of the terms in a sequence. A subset of the identified sequences which cover at least some of the pages of the document is computed. Terms of at least some of the subset of the identified sequences are construed as page numbers of pages of the document. Additional page numbers may be identified by considering one or more features of the terms in the subset of identified sequences.
Owner:XEROX CORP
Stability Site for VPLS Multi-Homing
ActiveUS20140056125A1Reduce lossesError preventionFrequency-division multiplex detailsFailoverService provision
Novel tools and techniques are described for mitigating data loss during failover in a VPLS multi-homed network. In one aspect, a primary link might be established between a lowest numbered provider edge (“PE”) router in the service provider network and a lowest numbered physical site at customer premises outside the service provider network. A stability site might be established within the service provider network, communicatively coupled to at least the lowest numbered PE router via a primary virtual circuit. The stability site might be designated as the lowest numbered virtual site, which might have a site ID number lower than the lowest numbered physical site. In response to the primary link failing or becoming broken, one or more backup virtual circuits might be established between a plurality of ingress PE routers and a plurality of egress PE routers in the service provider network, without destroying the primary virtual circuit.
Owner:CENTURYLINK INTPROP
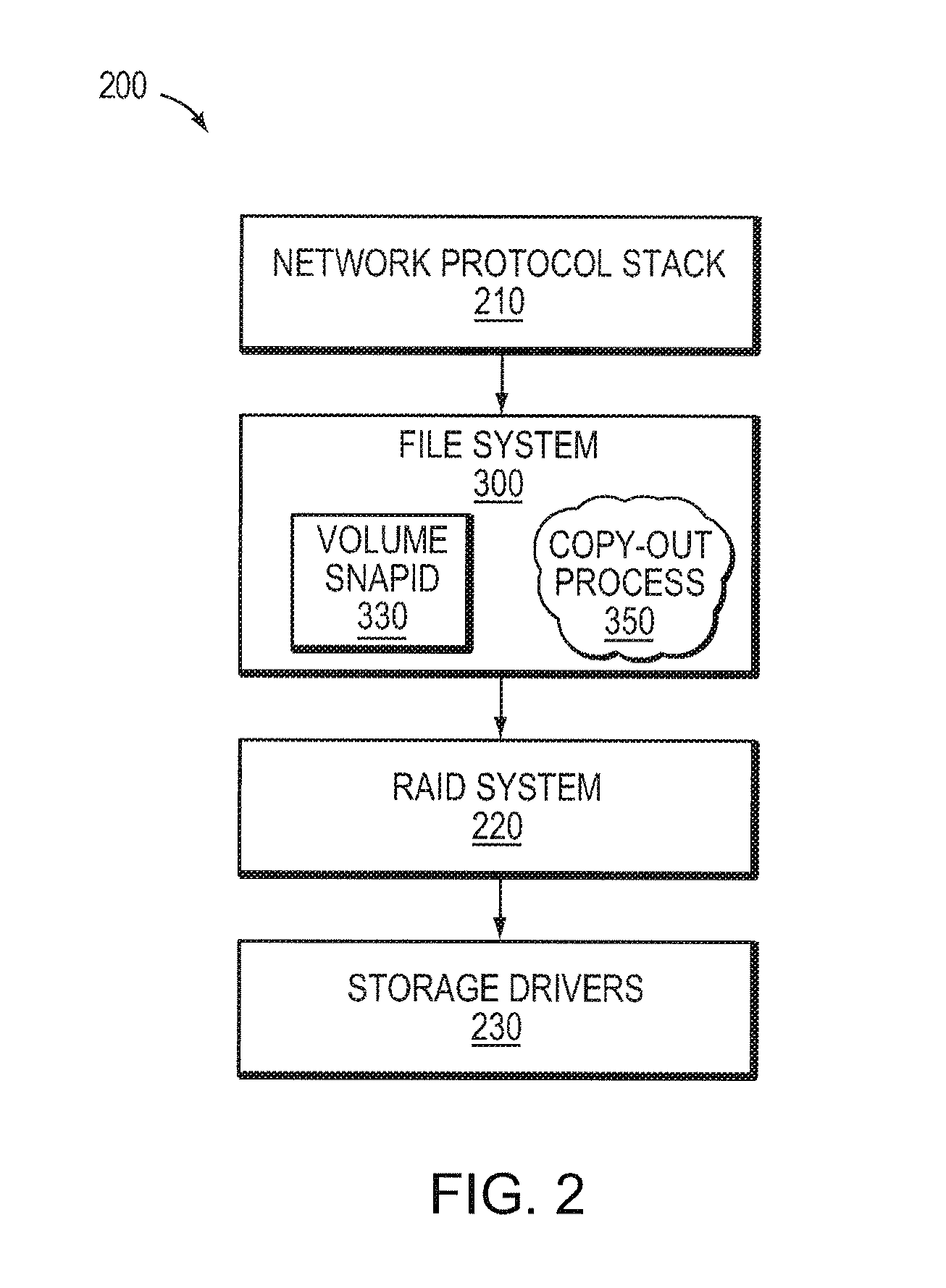
Identifying snapshot membership for blocks based on snapid
ActiveUS7849057B1Efficiently manage and organizeEasy to operateDigital data information retrievalDigital data processing detailsFile systemSelf-balancing binary search tree
An on-disk structure of a file system has the capability to efficiently manage and organize data containers, such as snapshots, stored on a storage system. A multi-bit, monotonically increasing, snapshot identifier (“snapid”) is provided that represents a snapshot and that increases every time a snapshot is generated for a volume of the storage system. The snapid facilitates organization of snapshot metadata within, e.g., a data structure used to organize metadata associated with snapshot data. In the illustrative embodiment, the data structure is a balanced tree structure configured to index the copy-out snapshot data blocks. The snapid is also used to determine which blocks belong to which snapshots. To that end, every block that is used in a snapshot has an associated “valid-to” snapid denoting the newest snapshot for which the block is valid. The oldest snapshot for which the block is valid is one greater than the valid-to field of the next older block at the same file block number.
Owner:NETWORK APPLIANCE INC
Linked network switch configuration
A network device having a plurality of ports including address resolution logic (ARl), a first switch, a second switch, and a CPU. The first and second switches include groups of ports which are a subset of the plurality of ports and are numbered by different numbering schemes, rate control logic for performing rate control functions related to switching data packets between the network ports, and local communications channels for transmitting messages between the groups of ports and the rate control logic. The first switch is configured to generate a rate control message and relay the rate control message to the second switch, and the second switch is configured to generate a second rate control message based on the first rate control message, where the second rate control message is different than the first message.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Efficient support of consistent cyclic search with read-copy-update
InactiveUS7426511B2Data processing applicationsDigital data information retrievalQuiescent stateRead-copy-update
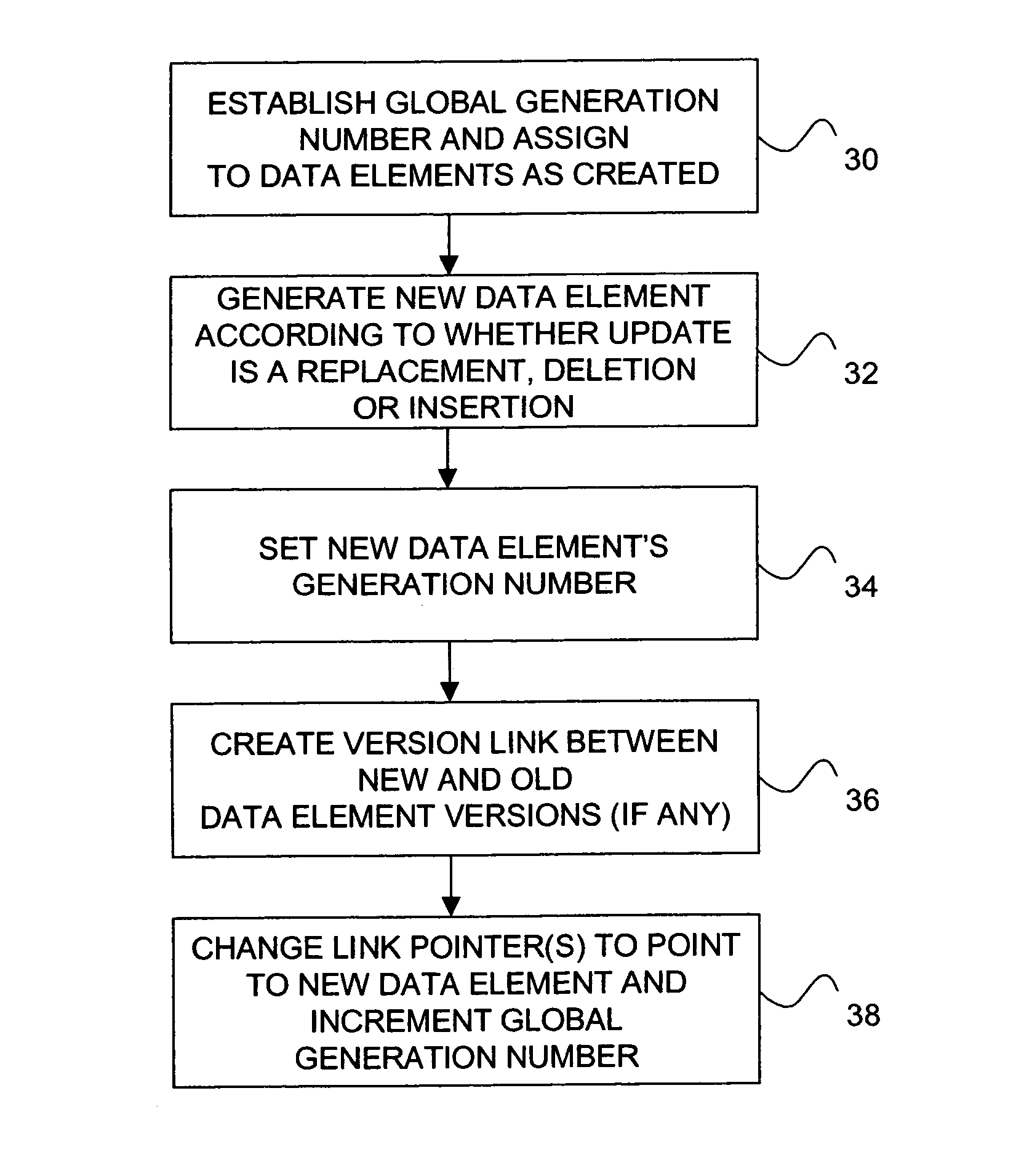
A method, system and computer program product for modifying data elements in a shared data element group that must be updated atomically for the benefit of readers requiring group integrity. A global generation number is associated with the data element group and each member receives a copy of this number when it is created. Each time an update is performed, the global generation number is incremented and the updated element's copy of this number is set to the same value. For each updated data element, a link is maintained from the new version to the pre-update version thereof, either directly or using pointer-forwarding entities. When a search is initiated, the current global generation number is referenced at the commencement of the search. As data elements in the group are traversed, the reader traverses the links between new and old data element versions to find a version having a matching generation number, if any. Following the occurrence of a grace period in which all readers have passed through quiescent states, all old data element versions are freed.
Owner:INT BUSINESS MASCH CORP
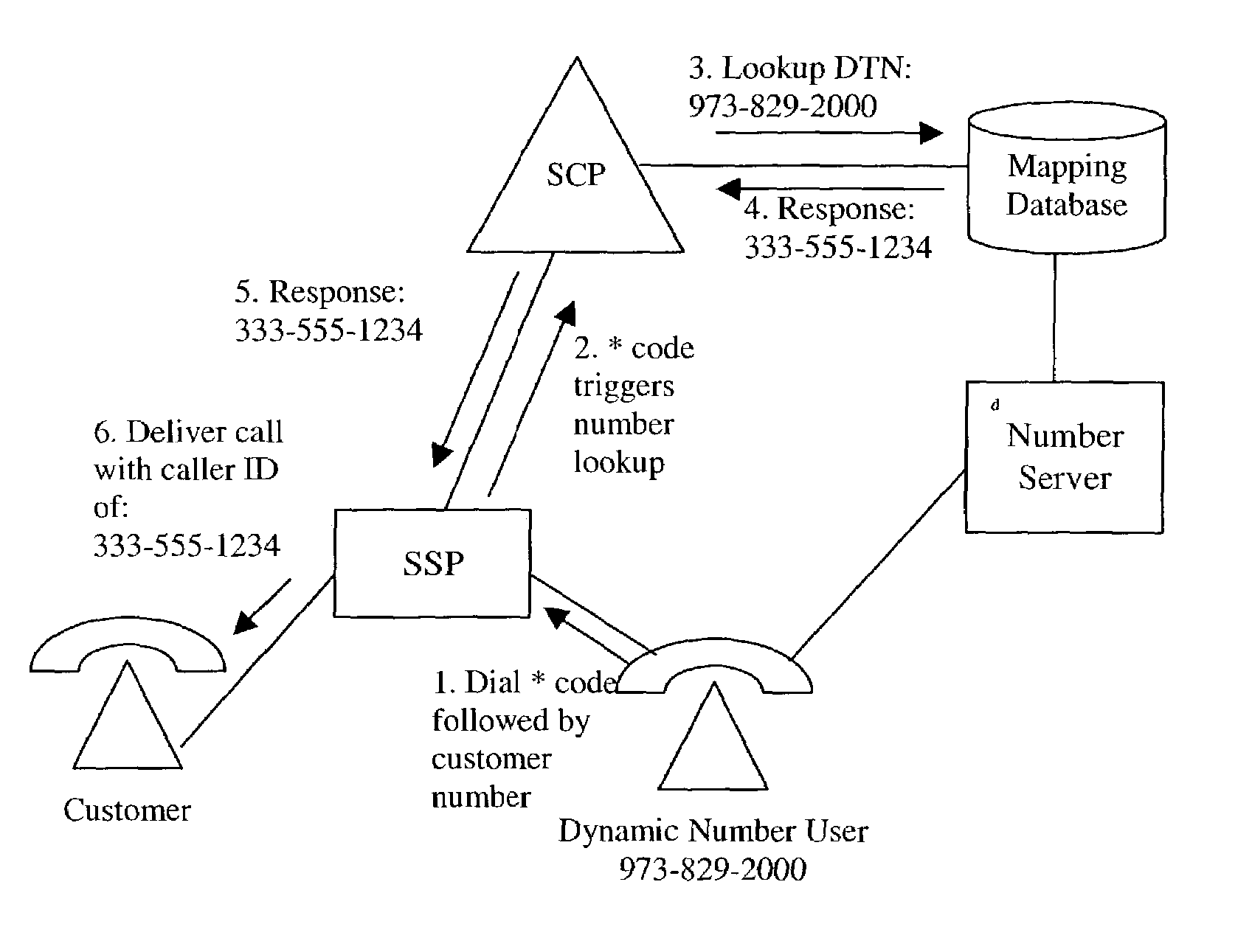
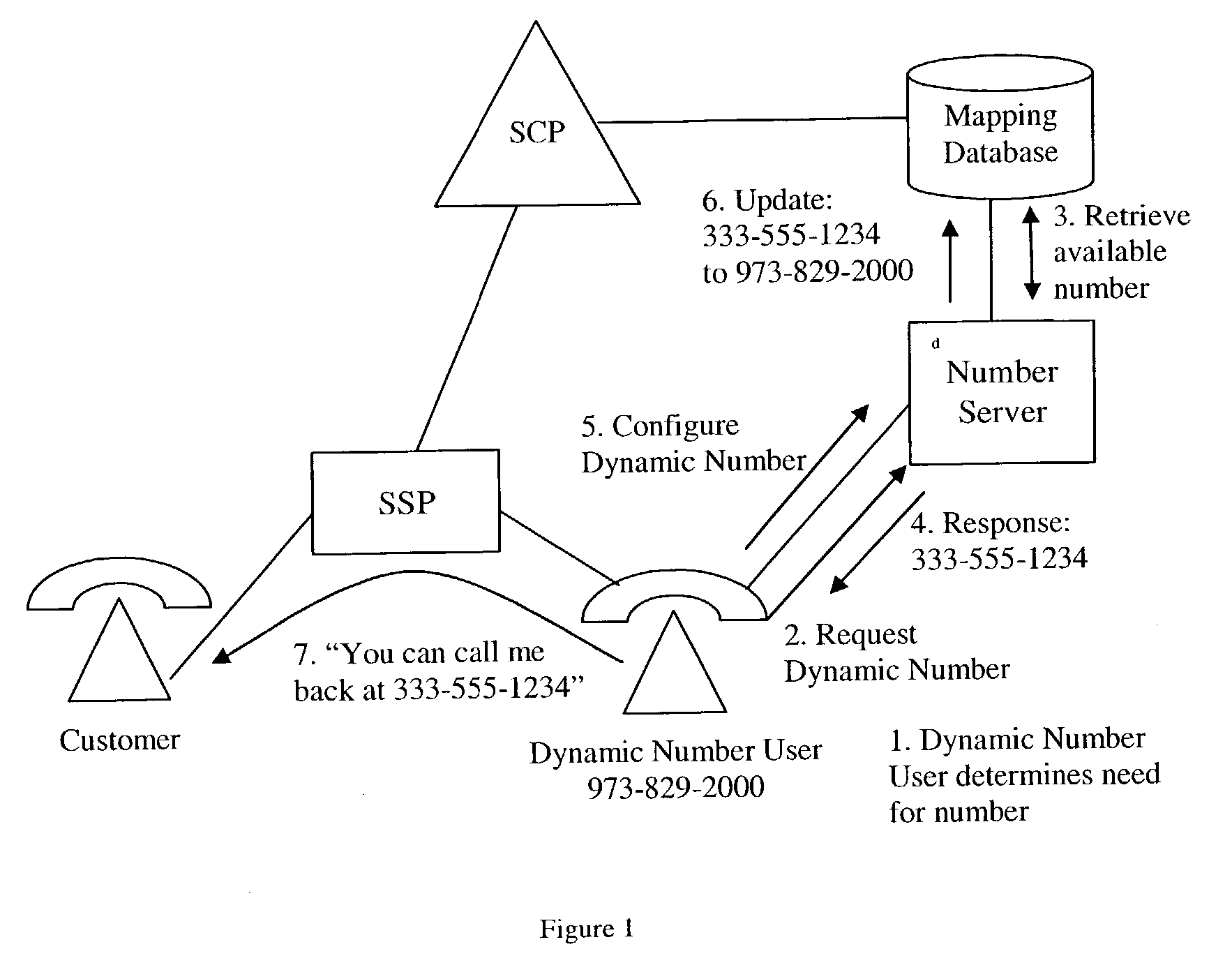
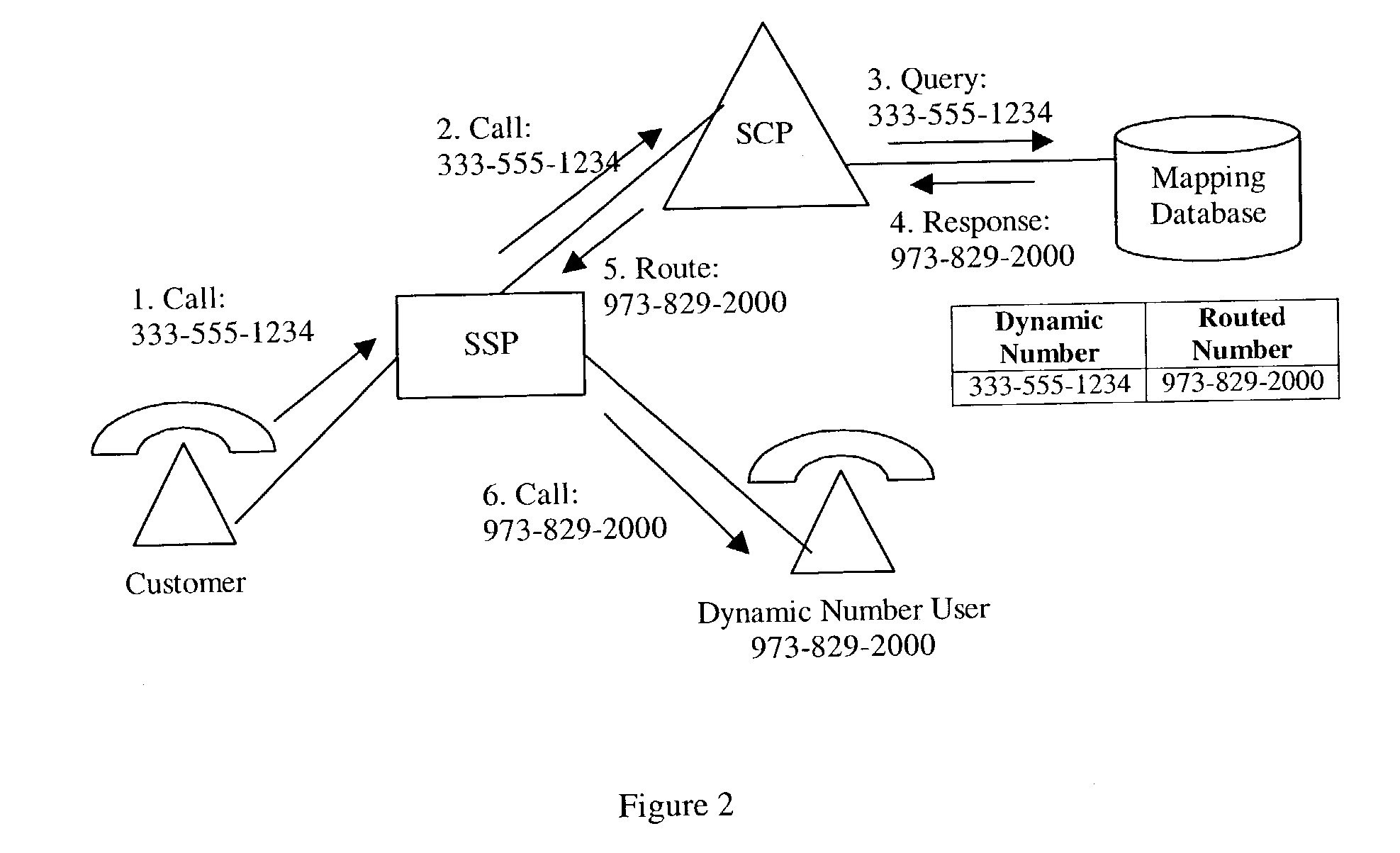
Dynamic telephone numbering system
ActiveUS7020256B2Avoid the needIntelligent networksSpecial service for subscribersNumbering systemTime segment
The present invention relates generally to logical telephone numbers. In particular, dynamic number users are able to obtain dynamic numbers and to map those numbers to routable numbers of their choosing. The present invention provides a tool for protecting privacy while sharing and / or publicizing a number for public purposes. The present invention relates to a Dynamic Telephone Number Service (DTNS.) wherein users are provided with a logical temporary telephone number that is mapped dynamically to a physically addressable number. The use of the DTNS allows a dynamic number user to publish the logical number, thus avoiding the need to publish private information and phone numbers for public purposes. Further, the logical number is not permanently assigned, but rather is temporary and provided to the dynamic number user for a relatively short period of time.
Owner:INTELLECTUAL VENTURES II
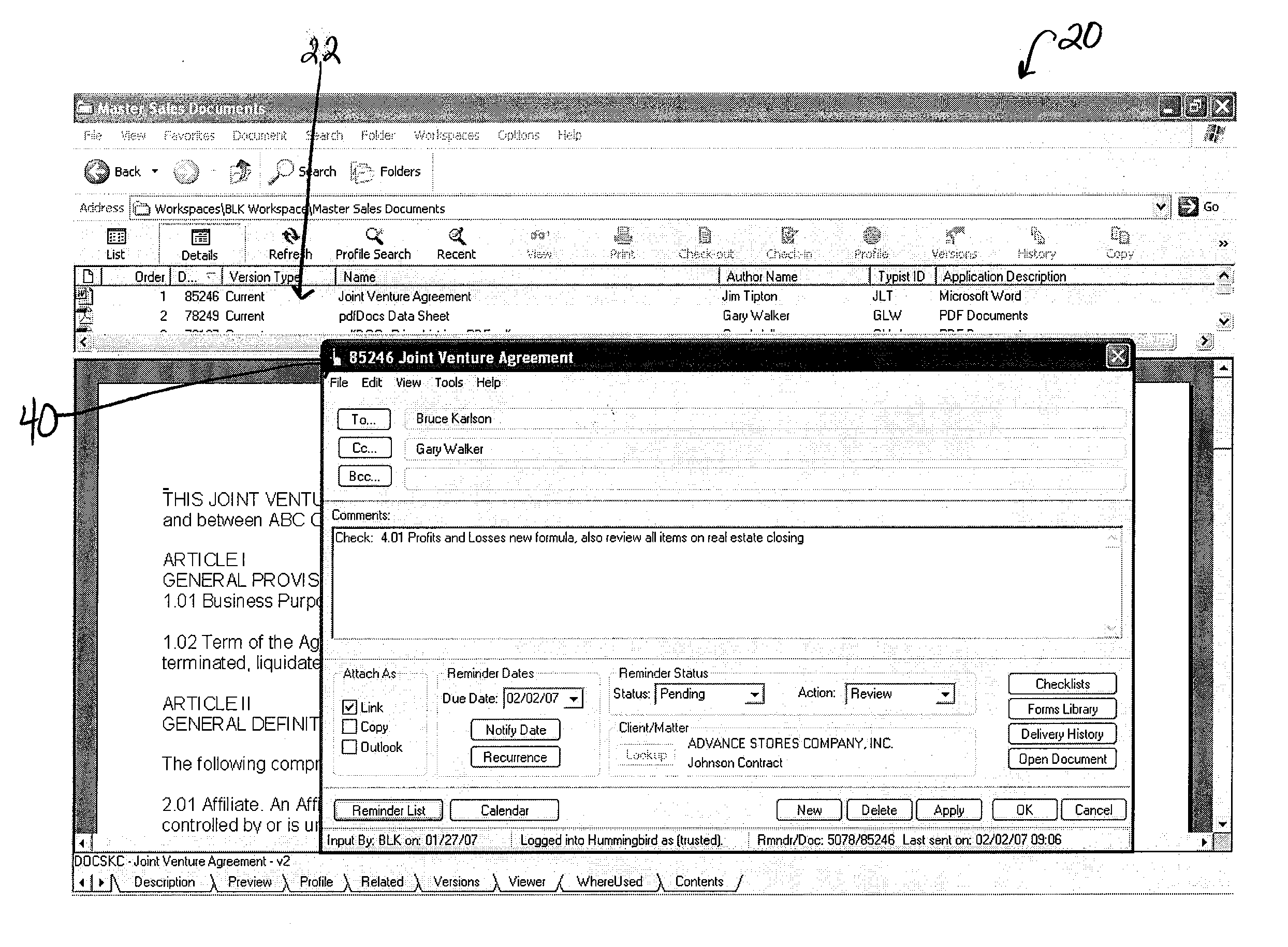
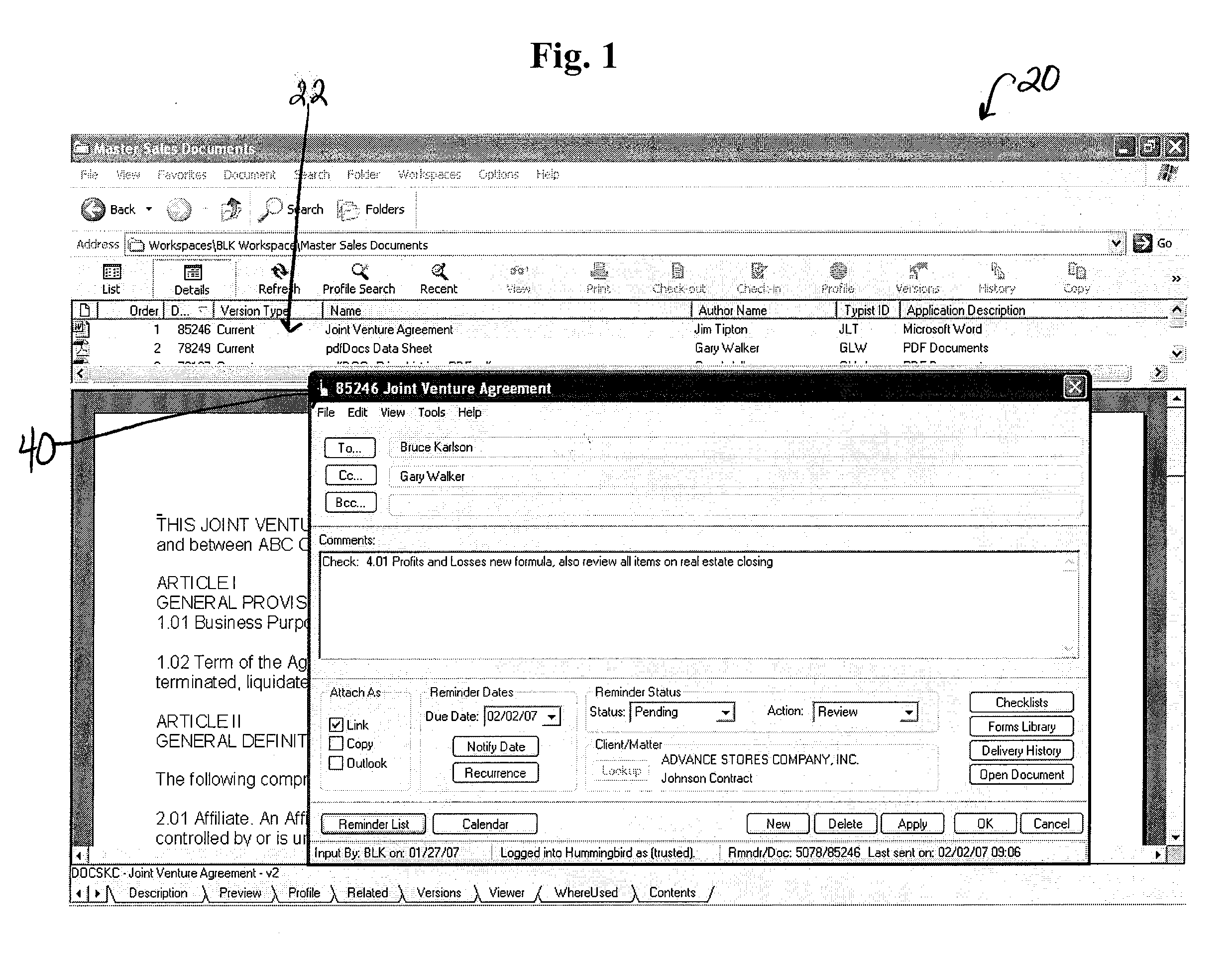
Reminder system
ActiveUS20130212197A1Easy to useImprove usabilityData switching networksSpecial data processing applicationsCourse of actionWorkload
A reminder system is provided. The system provides a user-friendly interface to a user's existing email, and in some embodiments to the user's document management, calendar and other systems, in order to ensure that an appropriate user is notified when action should be taken, and also provides notation to the user indicating the appropriate course of action to be taken. The system provides a calendaring feature where a supervisor or manager can determine the workload of a group of workers for an upcoming time period. The system provides an easily accessible and traceable database of information pertaining to a project checklist, document, a client name, a client matter number, a document type, or other customizable fields in order for a user to search and sort the information for their own use.
Owner:DOCSOF
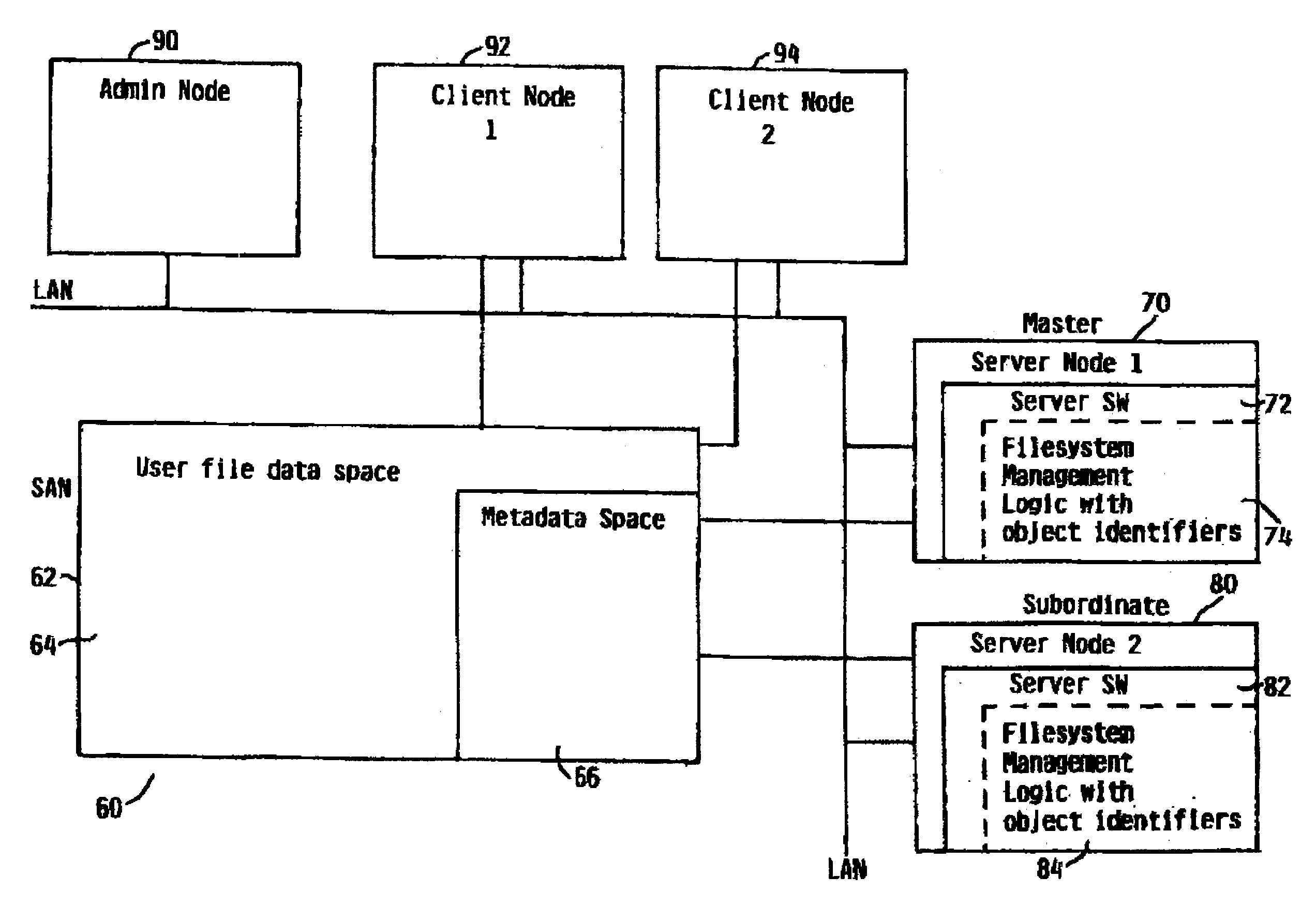
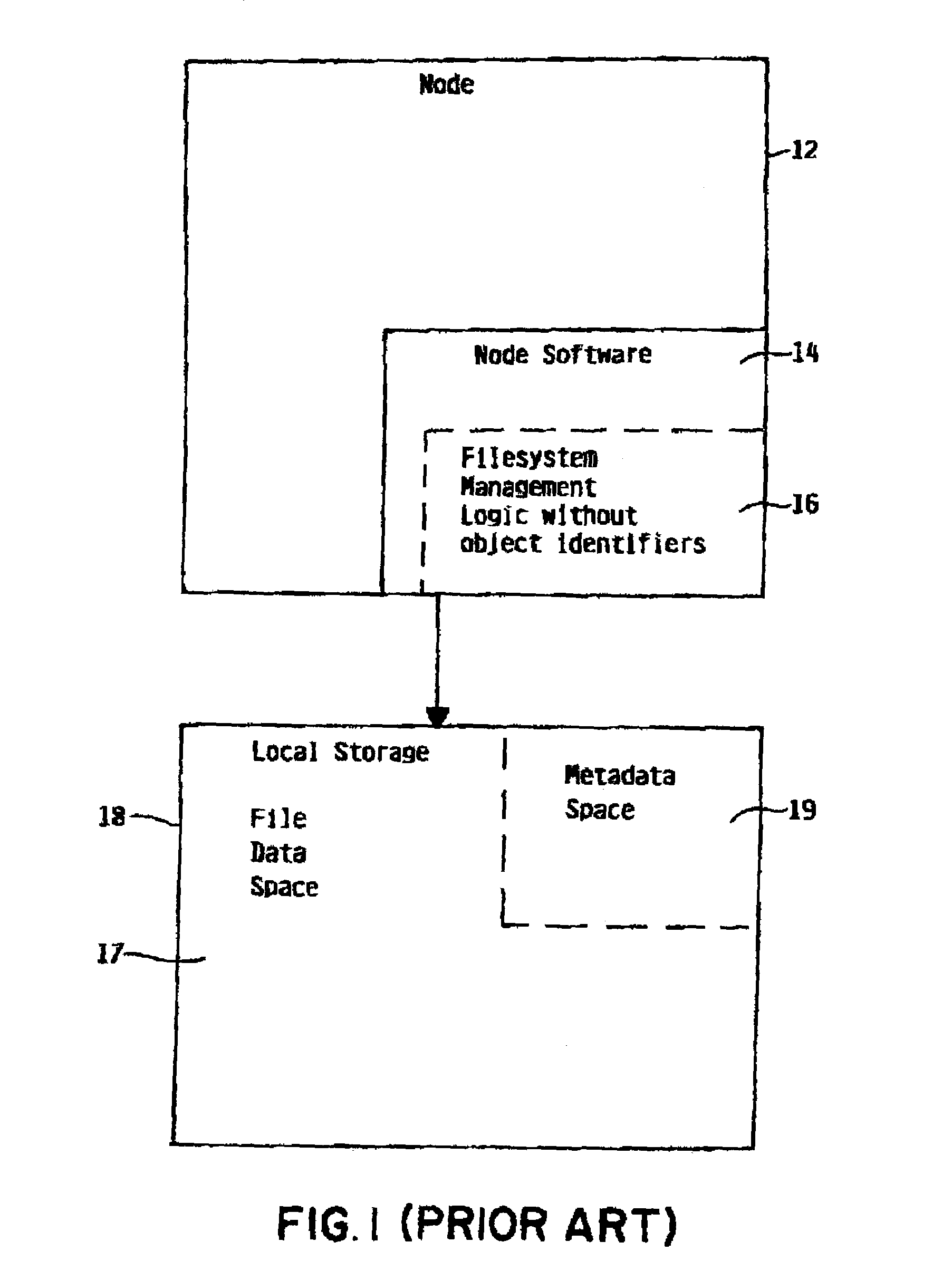
Managing filesystem versions
InactiveUS7139781B2Data processing applicationsDigital data processing detailsFile systemParallel computing
A system and method for managing logical versions of a filesystem made through a near-instantaneous copy process is provided. Each logical version of the filesystem, including the primary version, is assigned a unique epoch number or other identifying value, and each filesystem object is assigned two epoch numbers that define the space of logical versions for which the object exists. A list of all valid epoch numbers are maintained in a version table. The near-instantaneous creation of a logical version of the filesystem requires inserting a unique epoch number entry in the version table (106) and the next epoch number to the new logical version. An original state of the system is preserved through the use of a copy-on-write procedure for filesystem objects that are reference by that logical filesystem version (120). Accordingly, filesystem versions are maintained and original states of previous states of the logical filesystem versions are preserved.
Owner:IBM CORP
Mapping between part numbers that are based on different part numbering schemes
InactiveUS6988111B2Accurate item priceReduce complexityComputer security arrangementsBuying/selling/leasing transactionsComputer scienceNumbering scheme
A computer-implemented method for mapping between part numbers that are based on different part numbering schemes includes receiving a first part number associated with an item, the first part number associated with the item being defined according to a first part numbering scheme. A database is searched for one or more second part numbers that are associated with the item and also cross-referenced to the first part number associated with the item, the one or more second part numbers associated with the item being defined according to one or more corresponding second part numbering schemes. In response to identifying the one or more second part numbers associated with the item, a database is searched for a third part number that is associated with the item and also cross-referenced to at least one second part number associated with the item, the third part number associated with the item being defined according to a third part numbering scheme, the first part number associated with the item being mapped to the third part number associated with the item through the at least one second part number associated with the item.
Owner:BLUE YONDER GRP INC
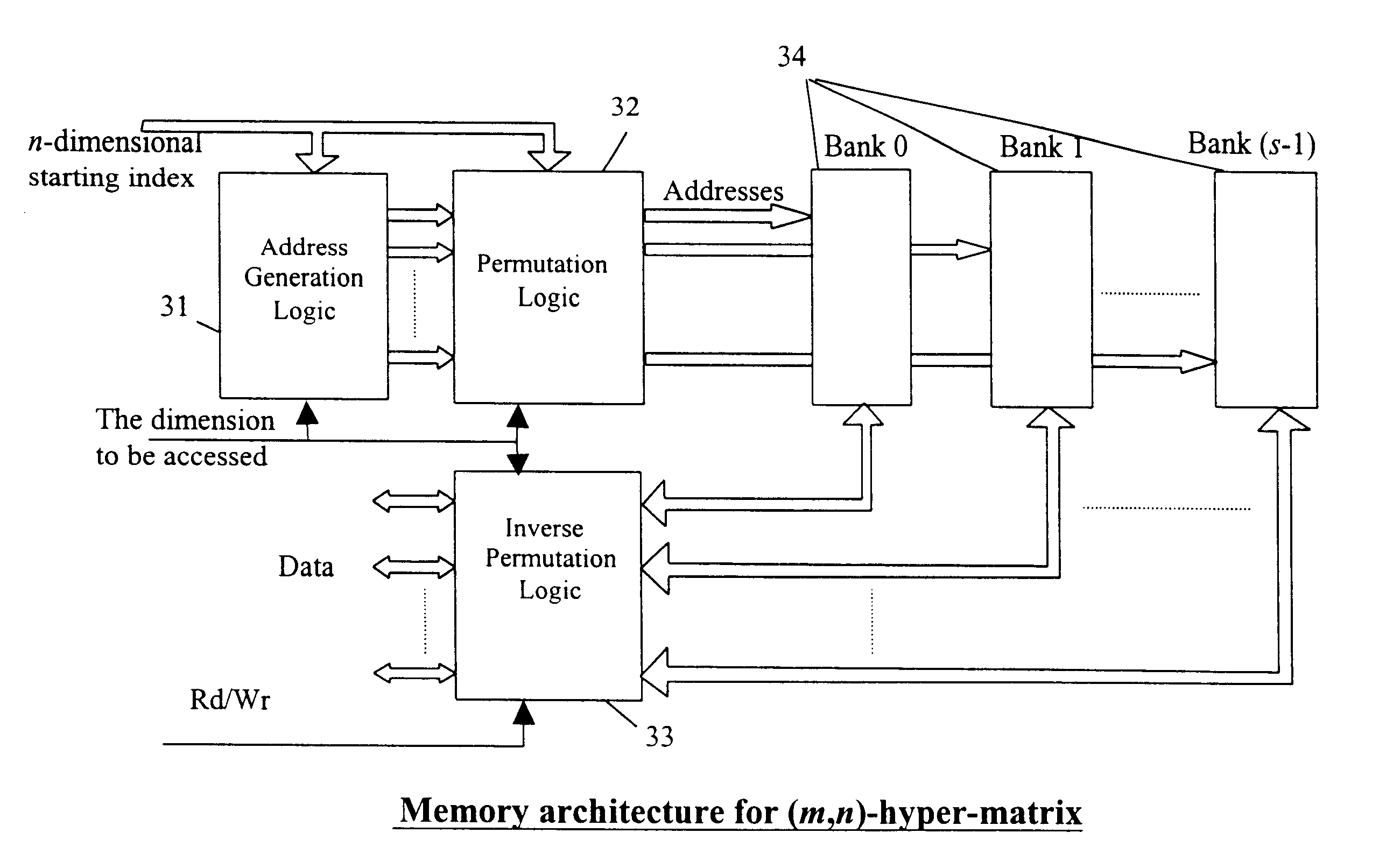
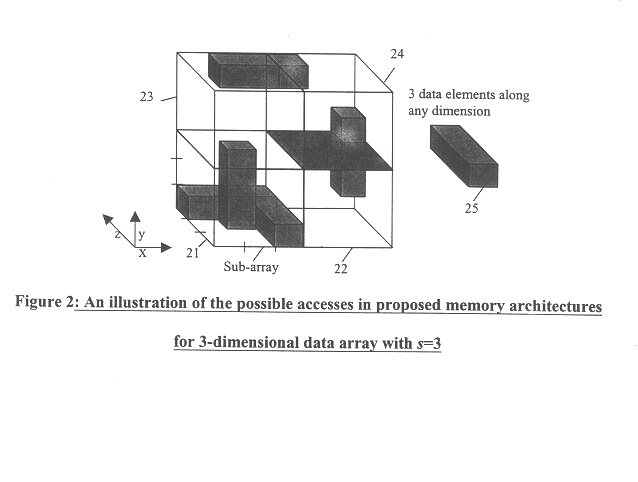
Memory architecture for parallel data access along any given dimension of an n-dimensional rectangular data array
InactiveUS6604166B1Less complexThe process is simple and effectiveMemory adressing/allocation/relocationMicro-instruction address formationMemory bankData access
A memory architecture is provided to enable parallel access along any dimension of an n-dimensional data array. To enable parallel access of s data elements along any dimension, the data elements of n-dimensional data array are mapped to s parallel memory banks in such a way that consecutive s data elements along any dimension are mapped to different memory banks. This mapping is defined by two functions, which define the memory bank number and location within a memory bank for each data element in n-dimensional data array. The necessary and sufficient conditions, which the mapping functions should satisfy in order to enable parallel data access, are described. These generic function pairs are described for all combinations of (n, s). Two particular instances of the mapping, namely circular permutation (rotation) along 0th dimension and dyadic permutation along 0th dimension have been discussed in detail. The mapping defined as dyadic permutation along 0th dimension holds only for values of s, which is integer power of 2. The mapping defined as circular rotation holds for any integer value of s. For these mappings, the basic architecture as well as its extensions are discussed. The basic architecture is for n-dimensional data array which has only s data elements along each dimension, whereas the extensions are for data arrays with m data elements along each dimension under the constraint that m is an integer multiple of s.
Owner:SHARP KK
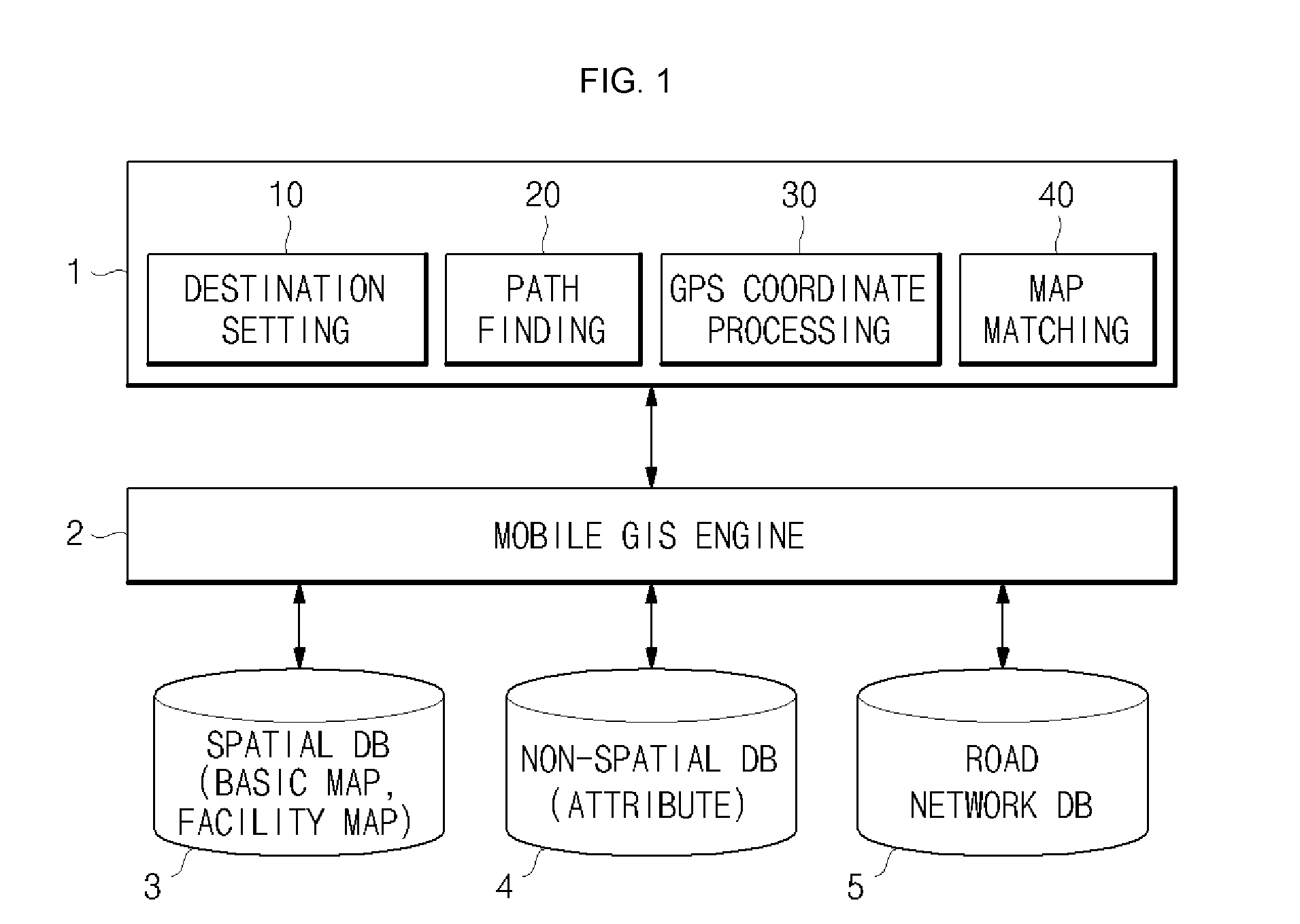
System for power facility navigation
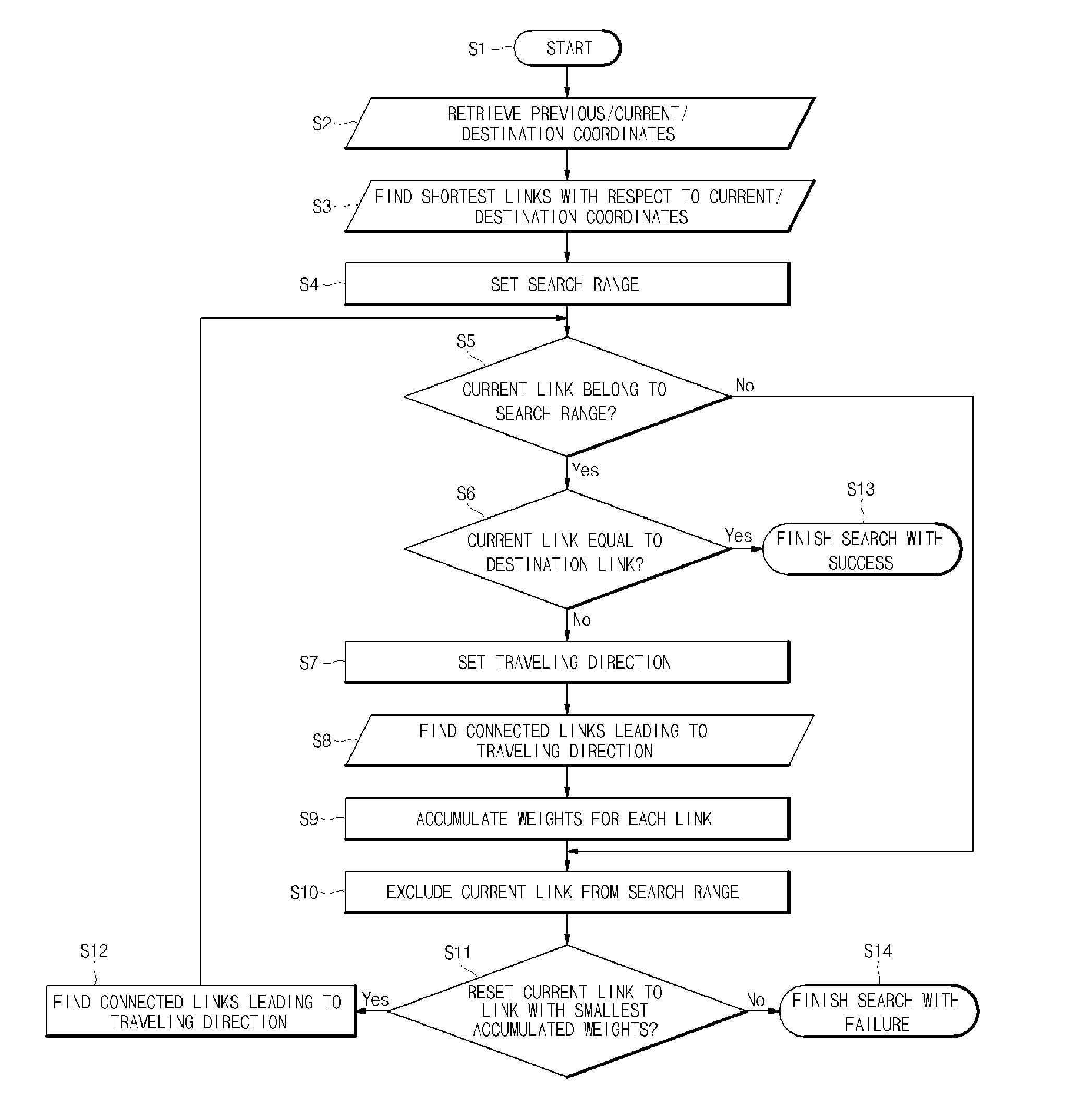
InactiveUS20100114475A1Reduce failure recovery timeGood serviceInstruments for road network navigationRoad vehicles traffic controlEngineeringNavigation system
A system for power facility navigation is disclosed. For rapid dispatch in the field service including power failure recovery and maintenance, the destination location can be set using various items such as pole numbers, computerization codes, customer names, trade names, equipment numbers and GIS coordinates. Destination location setting and path finding can be performed in order of priorities assigned to these items and in consideration of characteristics of field service activities. Location coordinates are received through a GPS receiver, coordinate conversion is performed according to a facility GIS coordinate system, and map matching is processed when GPS coordinates do not match facility GIS coordinates. The road network database is composed of linear array structures and the structure of a link is configured to include information regarding all other links connected to the start node and end node in a manner that link information and node attributes are integrated together.
Owner:KOREA ELECTRIC POWER CORP
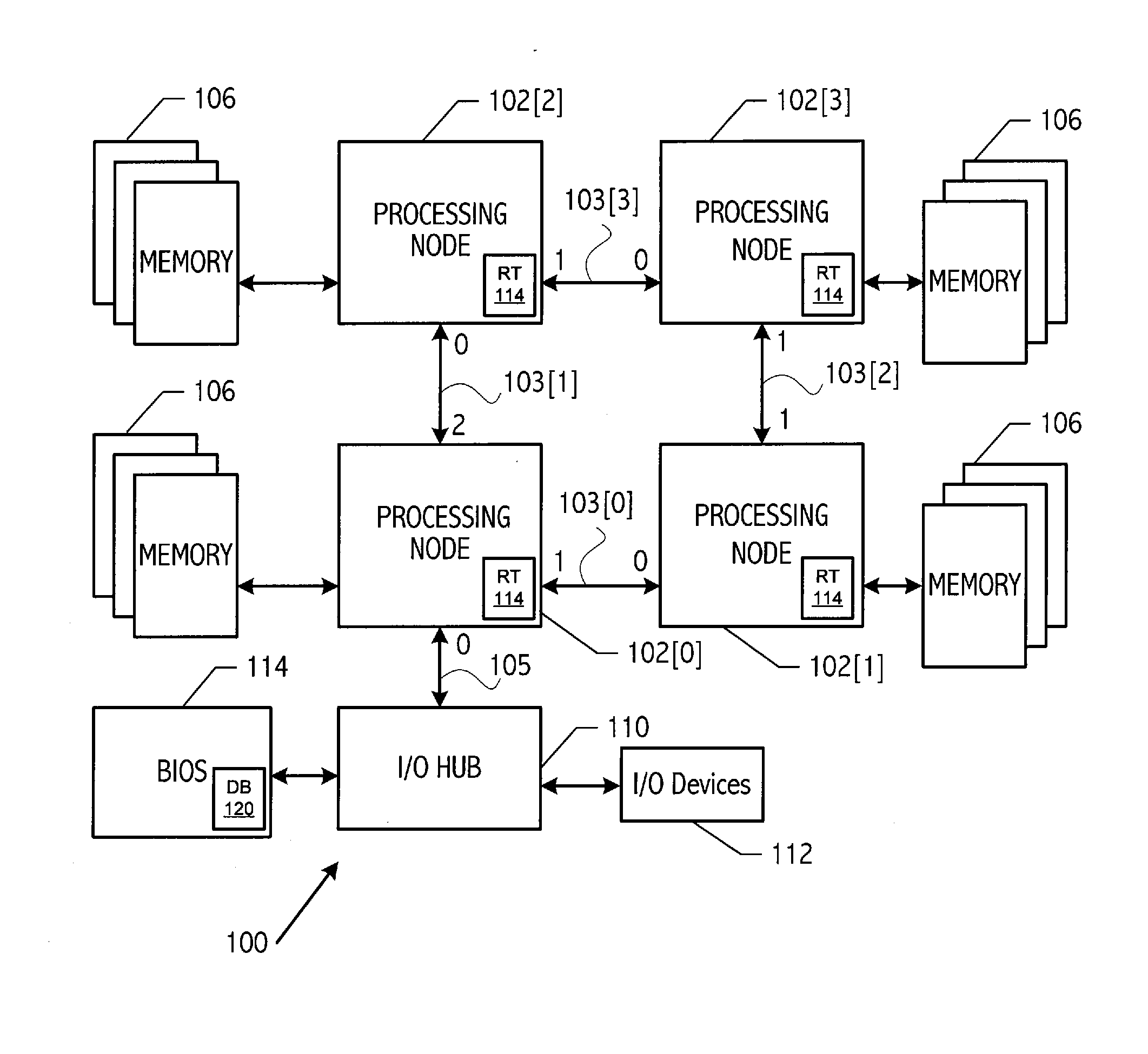
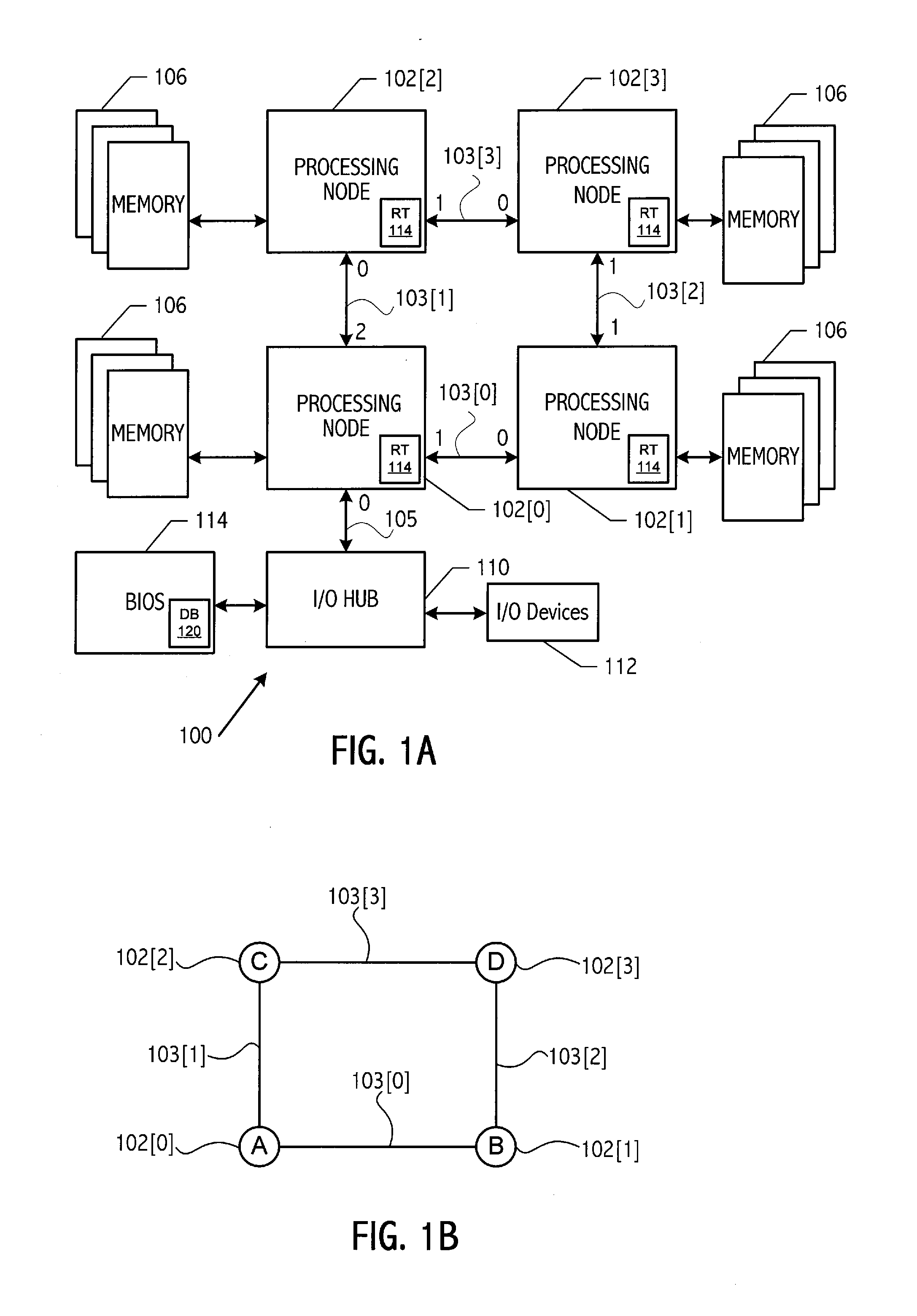
Communication network initialization using graph isomorphism
InactiveUS20090016355A1Reduce effortImprove robustnessData switching by path configurationTelecommunications linkCommunications system
A communication system, such as a computer system, with a plurality of processing nodes coupled by communication links stores a database of abstract topologies that provides a node adjacency matrix and abstract routing between nodes. A breadth-first discovery of the actual communication fabric is performed starting from an arbitrary root node to discover the actual topography. A graph isomorphism algorithm finds a match between the discovered topology and one of the stored abstract topologies. The graph isomorphism algorithm provides a mapping between the ‘abstract’ node numbers and the discovered node numbers. That mapping may be used to rework the stored routing tables into the specific format needed. The computed routing tables are loaded into the fabric starting at the leaf nodes, working back towards the root node (i.e., start loading from the highest node number and work back to the lowest numbered node).
Owner:ADVANCED MICRO DEVICES INC
Banking system with enhanced identification of financial accounts
A computer based banking system is provided in which at least selected clients termed participating system members have access to a remote device adapted to communicate with the computer base banking system such that financial transactions can be conducted by remote operation of the remote device by the participating system member to result in the debiting of a financial data base record associated with an instructing participating system member and in the crediting of a different financial data base record. Each data base record is identified by a conventional account number generated to conform to banking numbering standards as well as a linked communication number different from the relevant bank account number and composed of at least two component strings of numbers and / or letters, one of which is a number regionally unique to the participating system member, and the other of which is a bank identifying number unique to the particular bank at least on a regional basis. The communication number preferably also includes the two digit international dialing code; the telecommunications area code or the mobile operator code; and a check digit.
Owner:FUNDAMO
Multi- nuclear DSP system self-adapting task scheduling method
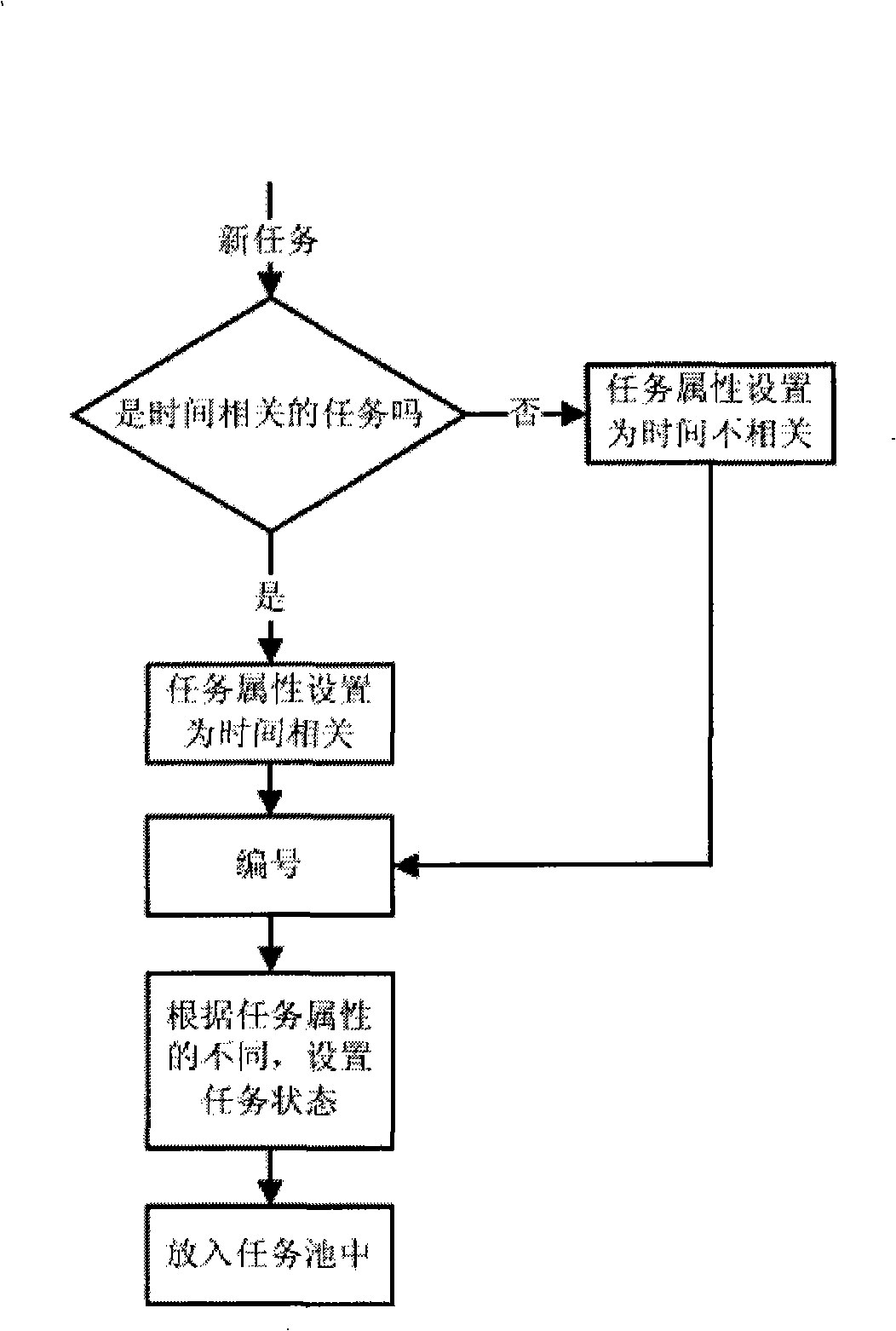
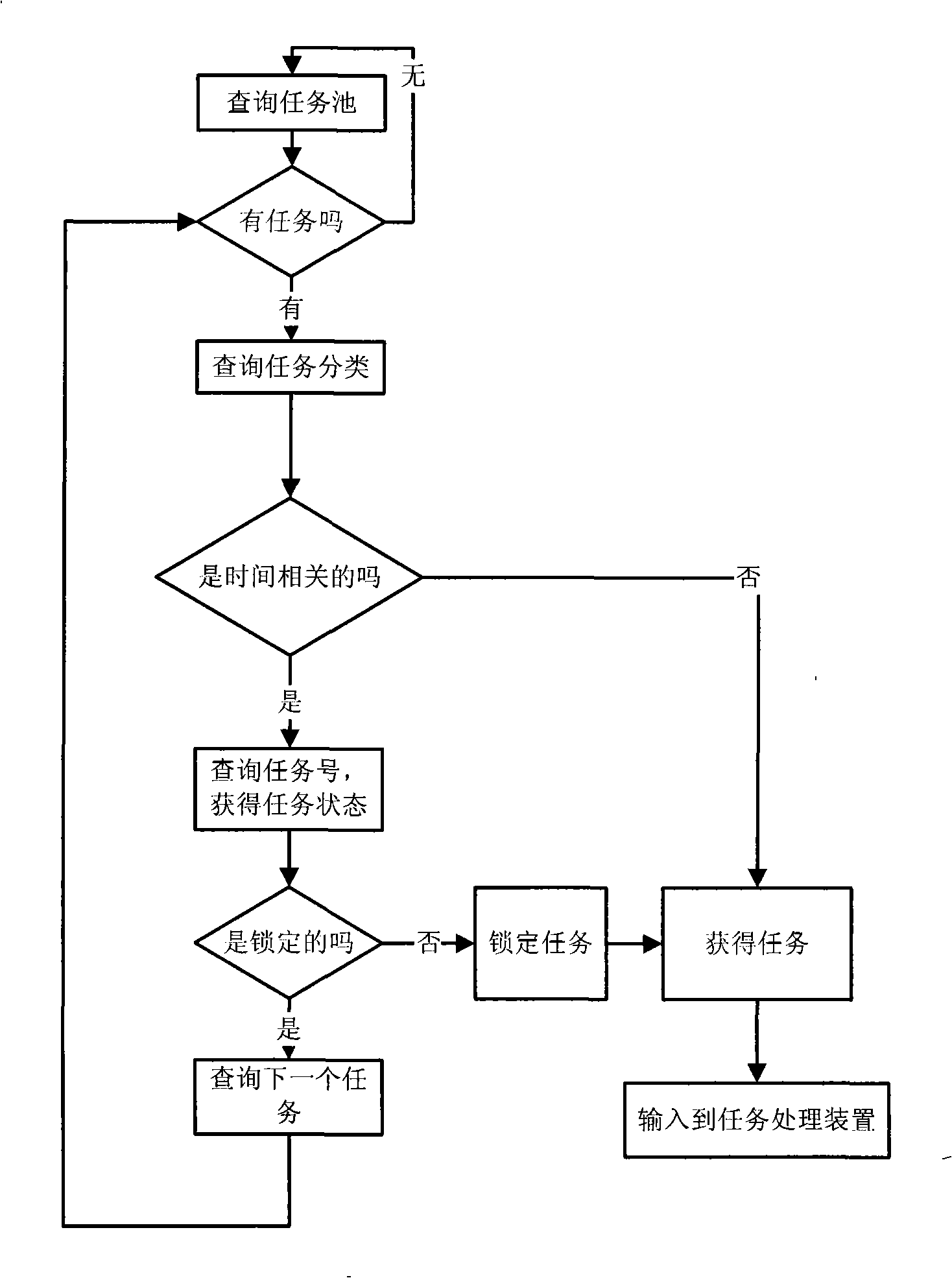
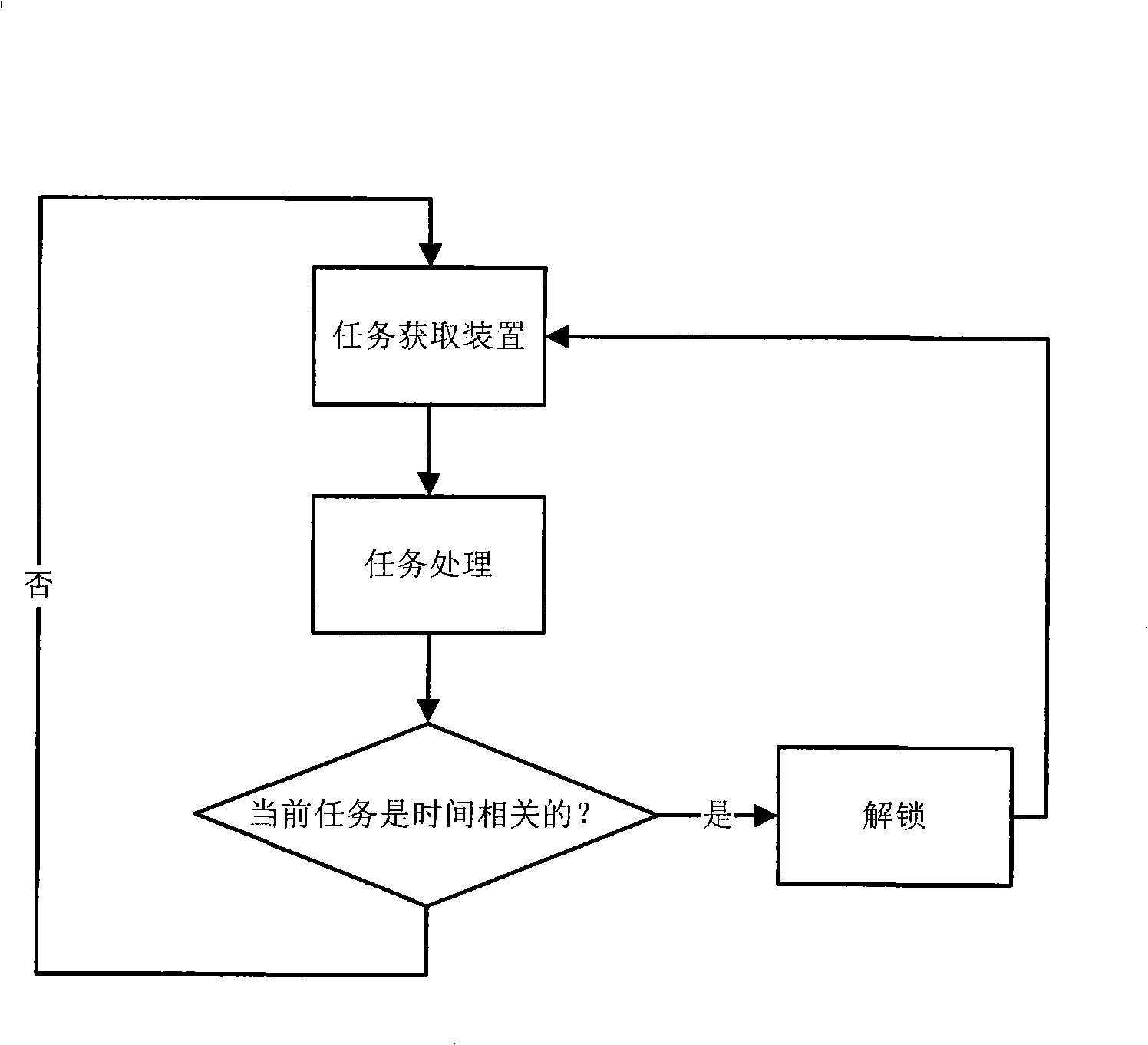
InactiveCN101261591ATo achieve load balancingReal-time processingProgram initiation/switchingIdle timeComputer architecture
The invention relates to a task scheduling method in a multi-core DSP system. A shared task pool is established in a shared memory in the multi-core DSP system, tasks are input into the task pool, the tasks are firstly classified into two categories of time-related and non-time-related, then each task is carried out the numbering, the time-related tasks have the same serial number, the non-time-related tasks are independently carried out the numbering, the initial states of the tasks with the different serial numbers are set as the non-locked states; and a task obtaining device of each idle slave core carries out the inquiry to the shared task pool and carries out the processing of the task after obtaining the task. The task scheduling method changes the technical proposal of using a main core for distributing tasks by the traditional multi-core DSP system and adopts the method of using the slave cores to actively obtain the tasks during the idle time, which can effectively reduce the requirements on the reliability of priori knowledge and reduce the load balance of the multi-core system.
Owner:AVONACO COMM SYST SUZHOU
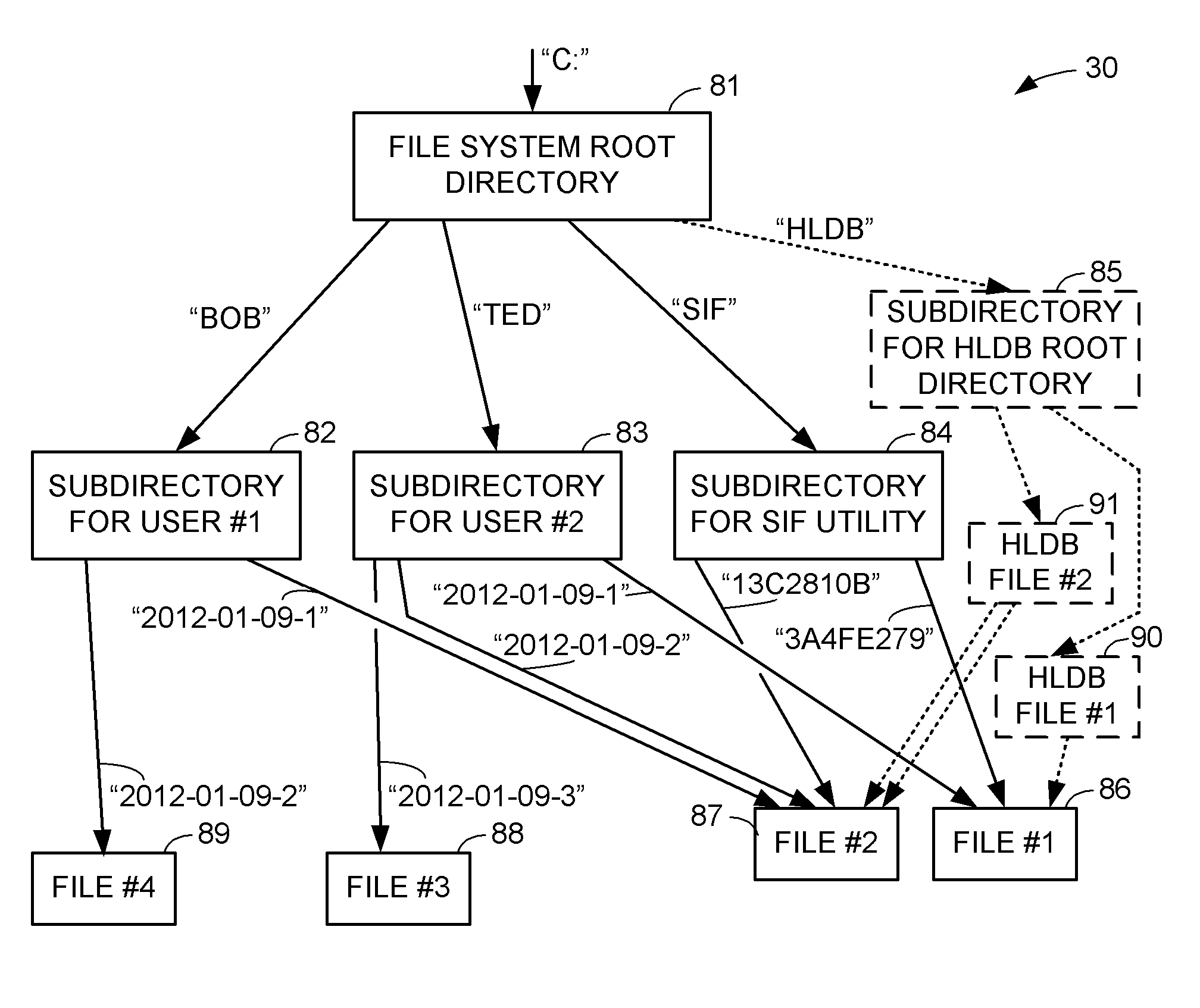
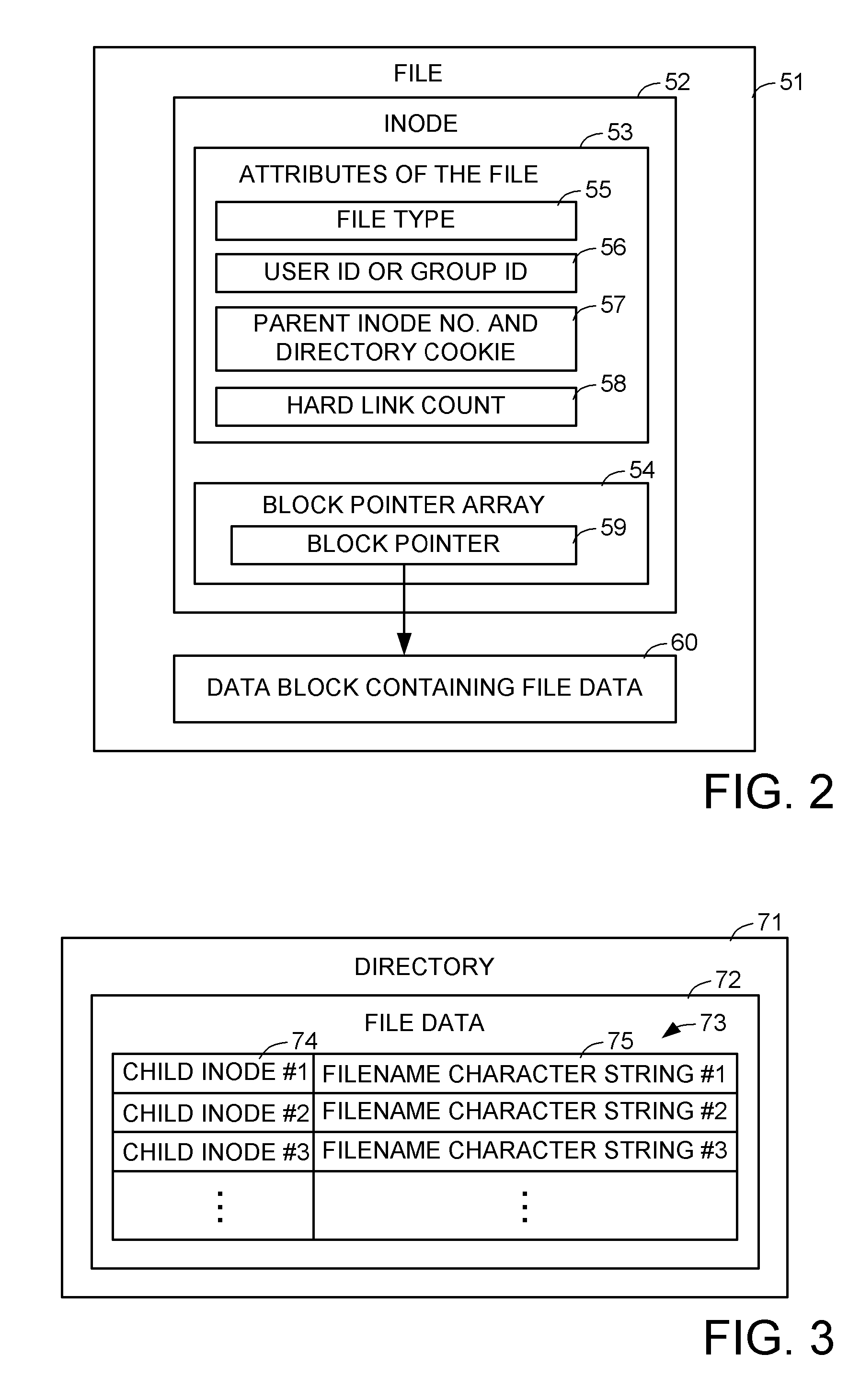
Inode to pathname support with a hard link database
For enabling a fast reverse lookup of parent directories storing records of hard links to a specified regular file, a file system manager maintains a hard link database (HLDB) storing information for addressing hard links to the regular files having multiple hard links. The HLDB contains a corresponding HLDB file for each regular file having multiple hard links. In a preferred implementation, the inode of each regular file stores the addressing information for one hard link to the regular file, a corresponding HLDB file stores the addressing information for other hard links to the regular file, each HLDB file is a directory accessed by invoking file system manager directory access routines, and the HLDB has a directory tree providing a multi-level hash index for searching the HLDB given the inode number of a regular file.
Owner:EMC IP HLDG CO LLC
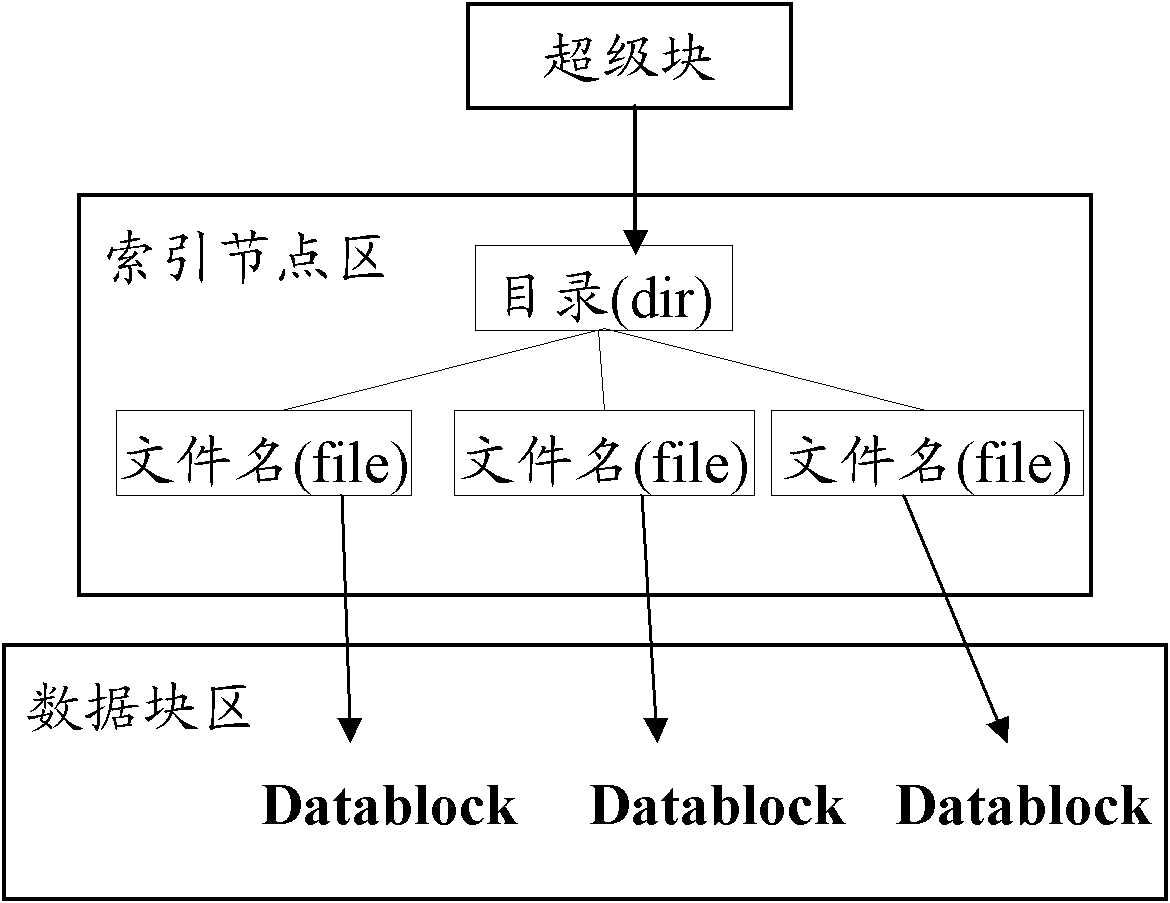
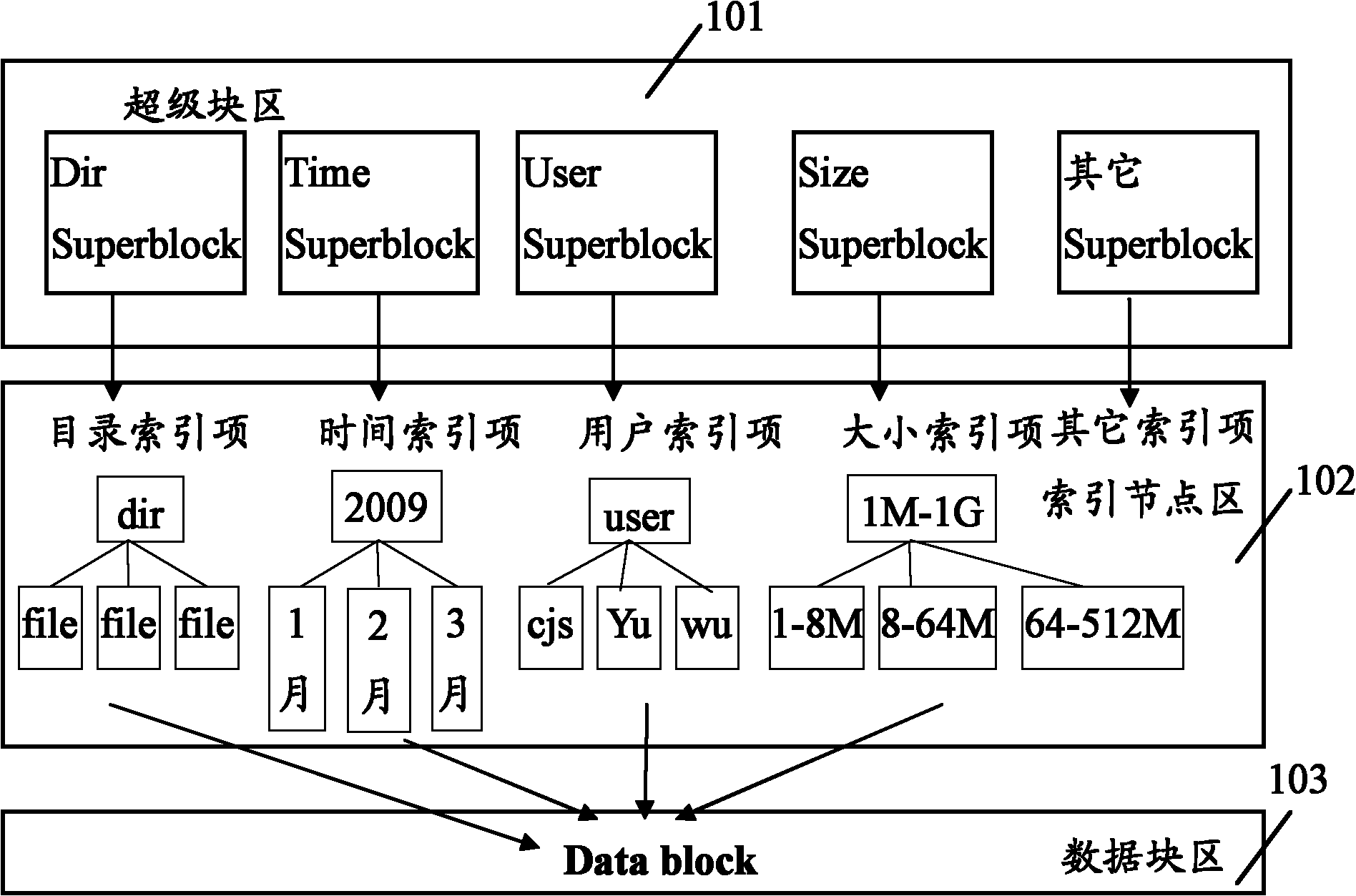
File system, and method and device for retrieving, writing, modifying or deleting file
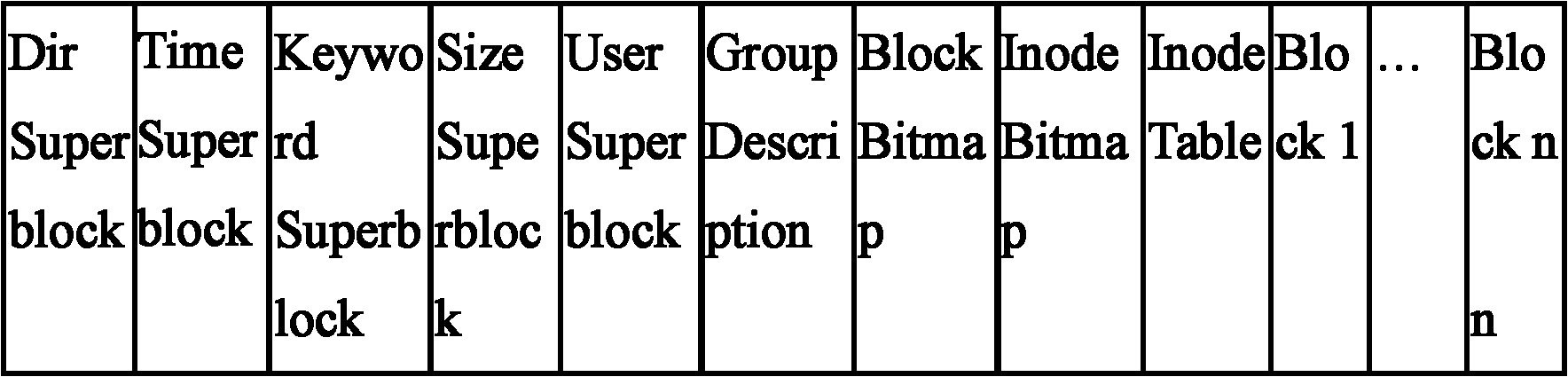
ActiveCN102184211ASolve problems with search methodsFile access structuresSpecial data processing applicationsInodeSerial code
The embodiment of the invention discloses a file system. The file system comprises a superblock region, an index node region and a data block region, wherein the superblock region comprises at least two superblocks serving as search entrances of different attributes of a file; the index node region comprises attribute index entry lists corresponding to each superblock, and index nodes corresponding to each file stored in the data block region, wherein each attribute index entry list stores a corresponding relationship between file attributes and index node serial numbers; the index nodes store the file attributes and storage addresses; and each storage address points to a data block, storing the file, of the data block region. The invention also provides a method and a device for retrieving, writing, modifying or deleting the file. By using the file system provided by the invention, the problem that the file system in the prior art cannot provide a single retrieving mode of retrieving by taking a file name as an attribute is solved by providing different retrieving modes through the superblocks and the attribute index entry lists of the different attributes of corresponding file.
Owner:CHENGDU HUAWEI TECH
Linked network switch configuration
InactiveUS7035255B2Time-division multiplexData switching by path configurationNetwork switchComputer science
A network device includes a first switch, a second switch, and a CPU. The first and second switches each include a group of ports numbered by a numbering scheme, a rate control logic for performing rate control functions related to switching data packets between the network ports, and a local communications channel for transmitting messages between the group of ports and the rate control logic. Each switch is configured to generate rate control messages based on data packet traffic to its group of ports. The CPU is coupled to the first switch and the second switch and configured to control the first switch and the second switch. A first link port of the first switch is coupled to a second link port of the second switch, and the first link port and the second link port are configured to relay the rate control messages to each other.
Owner:AVAGO TECH INT SALES PTE LTD
Systems and methods for validating an address
Systems, methods, and software determine whether a field of an input digital representation of information, such as the street name field in an address, is correct by quickly comparing the field to a list of valid choices for that field. The list of valid choices is generated based on information from the input digital representation, such as a character string. If an exact match is not found, a fuzzy match comparison determines the most closely matching valid choice. If a suitable fuzzy match is not found, then the input information is invalid. Otherwise, another field of the input information, such as the building number field of an address, is tested for validity. If the second field passes the validity check, then the fuzzy match (or exact match) for the field is valid. A fuzzy matching field may replace the input field, thereby correcting the input information.
Owner:US POSTAL SERVICE
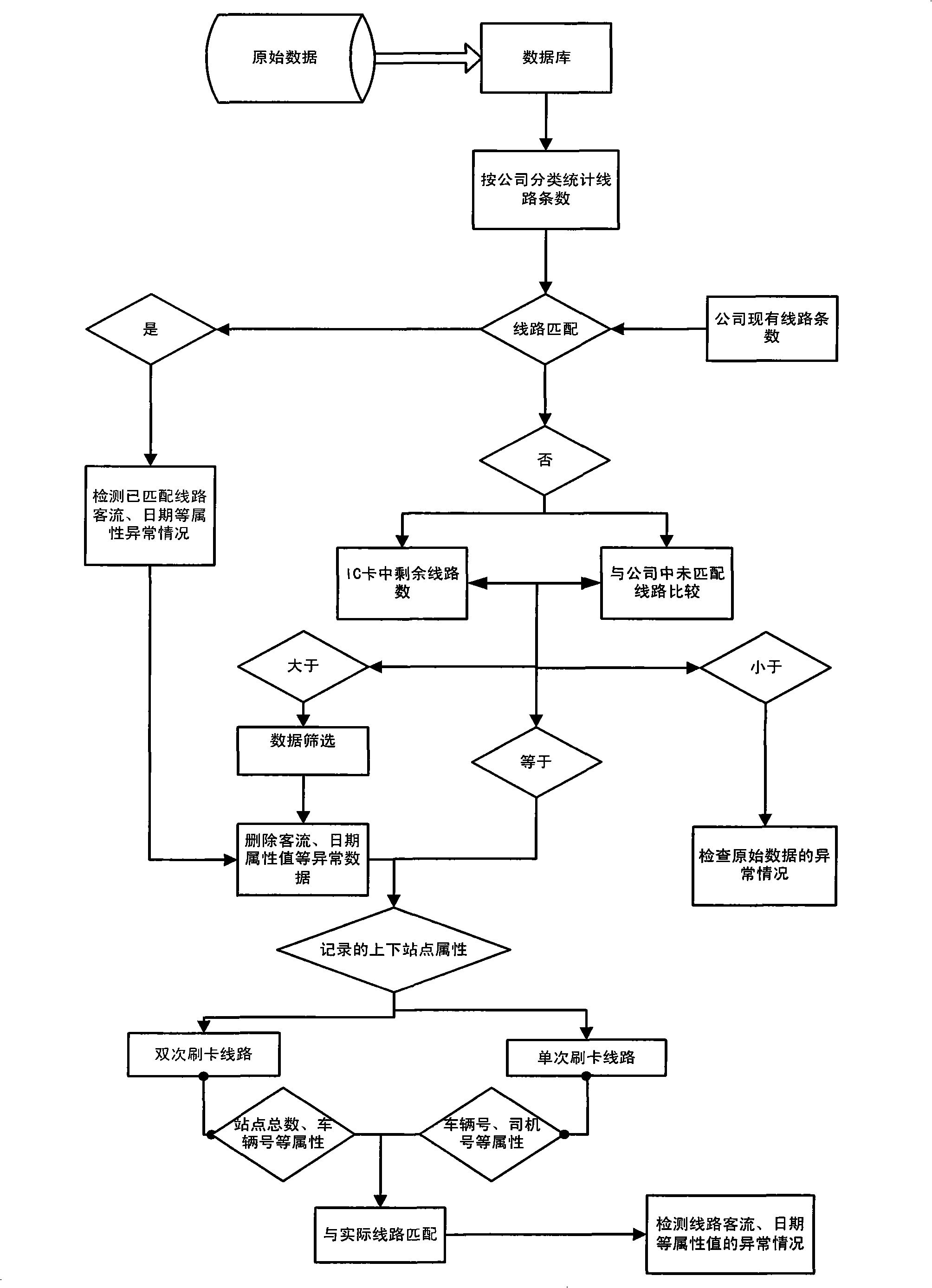
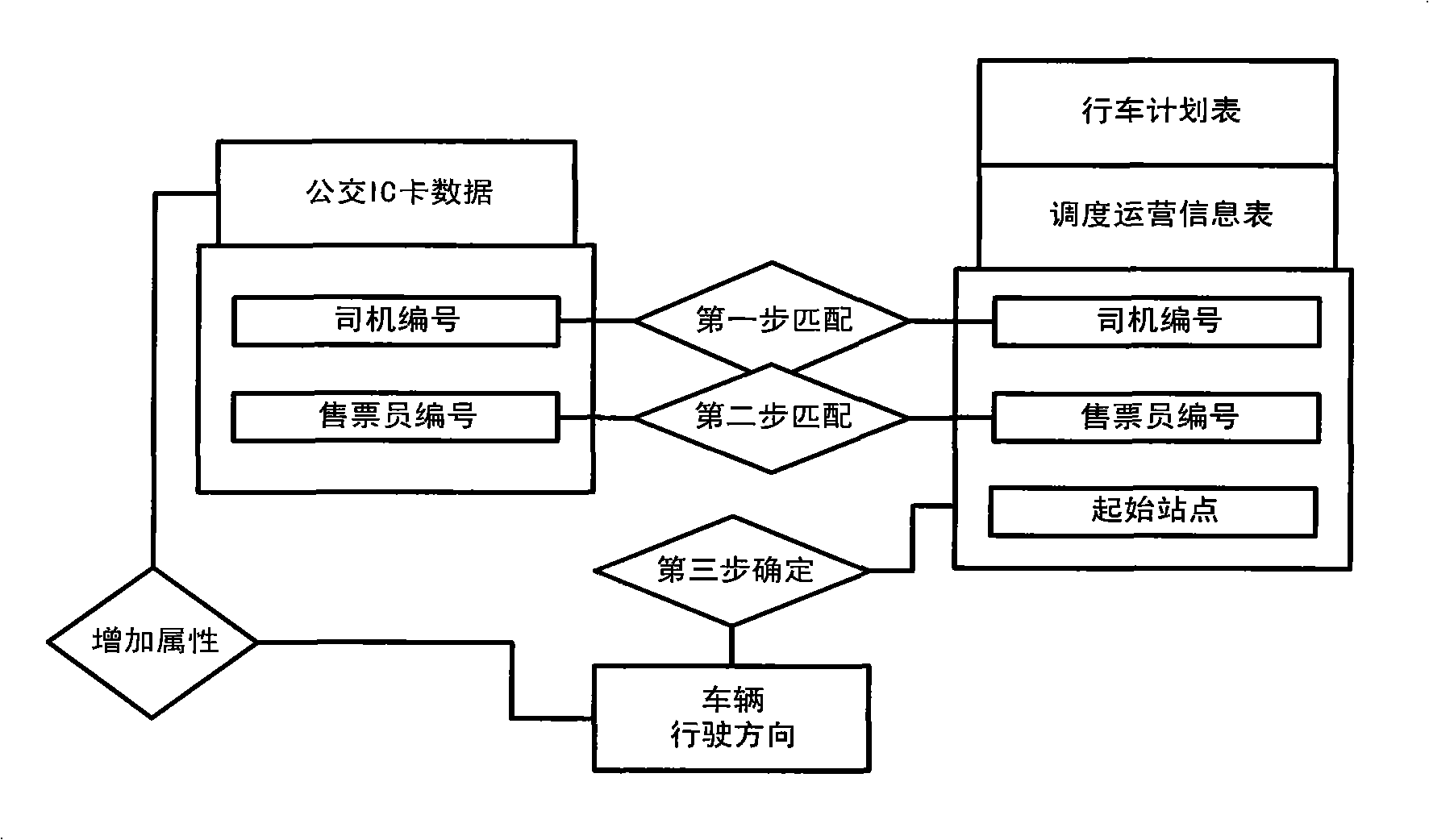
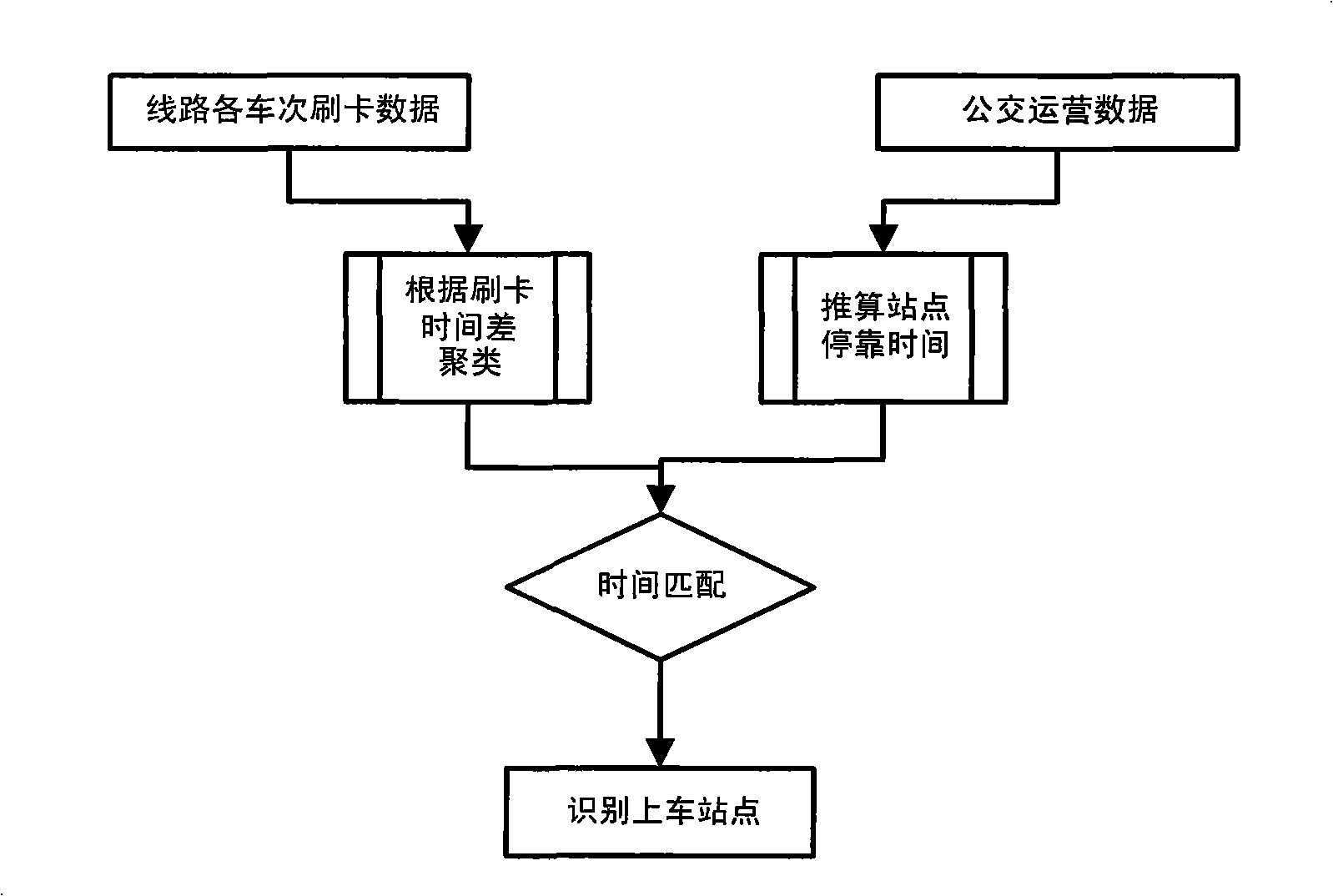
Matching method based on public transport IC card lines
The invention discloses a matching method based on public transport IC card lines, and belongs to the field of public transport information treatment and integration. The method comprises the steps of matching public transport IC card line numbers, matching vehicle running directions, and judging bus getting-on station platforms based on cluster analysis; matching the non-matched lines for many times according to the public transport IC card station platform attribute, vehicle number and attribute of driver number; associating the line serial number with the vehicle serial number and the public transport scheduling information list in a many-to-one manner according to the card swiping time records of the data of a universal public transport card; performing cluster analysis for the card swiping data according to the card swiping time difference of different station platforms, and selecting a proper time difference threshold value; and identifying the bus getting-on station platforms according to the selection of time difference threshold value. The invention performs pre-treatment including filtration, integration and convention for IC card data, deeply excavates the data, and finally obtains the station platform passenger number of the line. The invention provides planning evidence for public transport designers and provides evidence of public transport operation policy for public transport managers.
Owner:BEIJING UNIV OF TECH
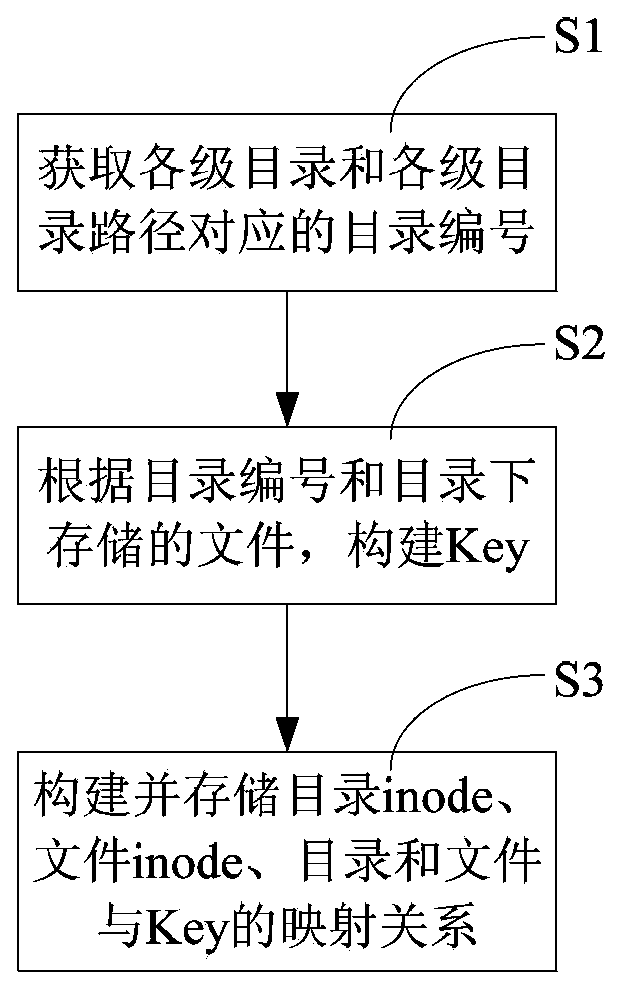
File system building method and device in key-value storage system, and electronic device
InactiveCN103902632ASmall footprintSave storage spaceDigital data protectionSemi-structured data mapping/conversionFile systemDatabase
The present invention relates to the field of data storage, and more particularly to a method, an apparatus, and an electronic device for building a file system in a key value storage system. In the method for building a file system in a key value storage system disclosed by the present invention, first directory sequence numbers corresponding to directory paths of all levels of directories are acquired, and keys corresponding to directories and files are then built according to the directory sequence numbers and files stored in all levels of directories; in this case, the directory sequence numbers in the Keys occupy small space, and each directory sequence number is unique without a phenomenon of any repetition, thereby effectively saving storage space; in addition, a directory Key corresponding to a directory is built according to the directory sequence number, and when a directory needs to be operated, the directory to be operated can be directly acquired according to the Key of the directory, so that the operation process is simplified.
Owner:HUAWEI TECH CO LTD +1
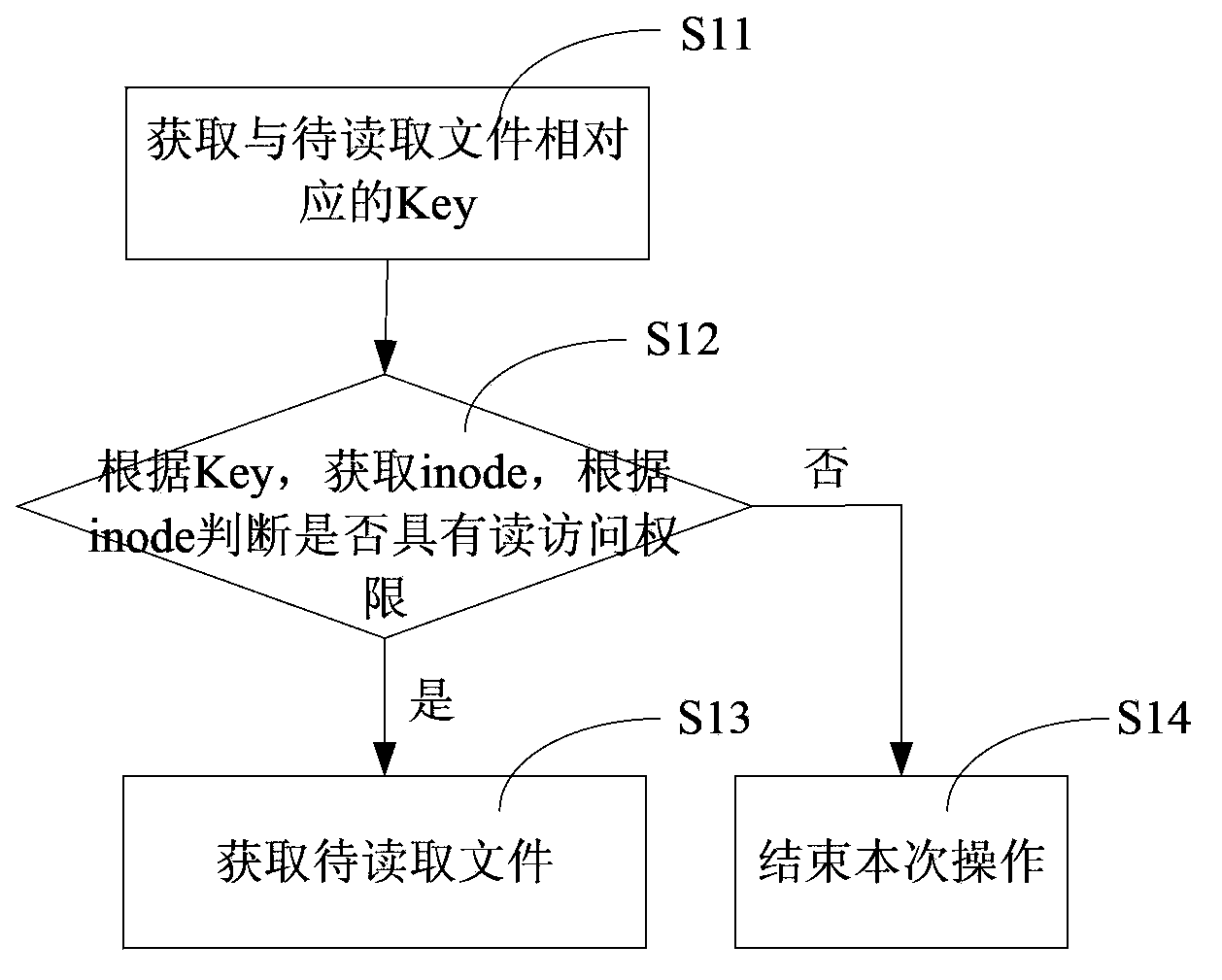
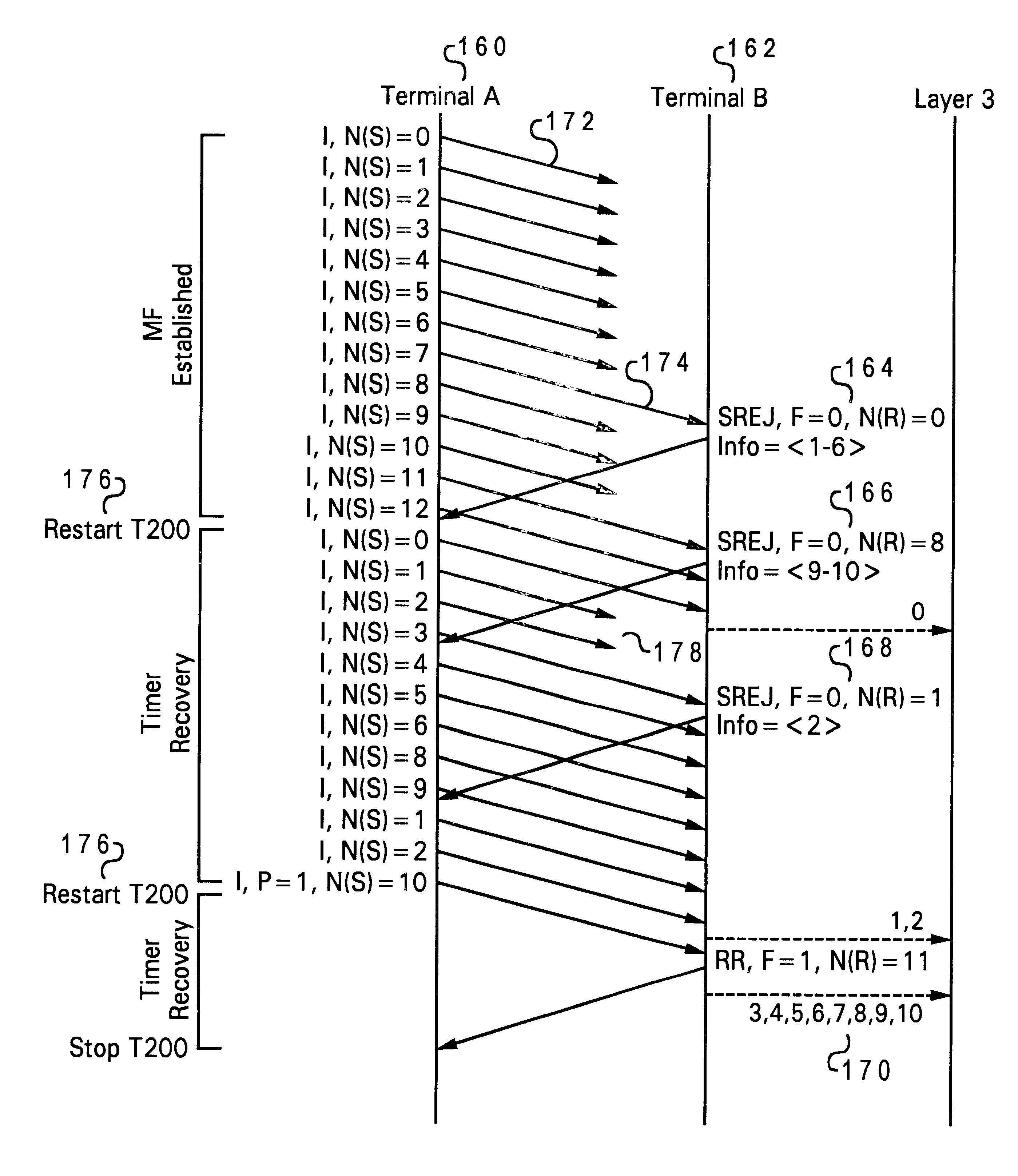
Method and system for sequential ordering of missing sequence numbers in SREJ frames in a telecommunication system
InactiveUS6434147B1Minimize effortError prevention/detection by using return channelTransmission systemsComputer hardwareNumbering scheme
A method and system for sequential ordering of missing sequence numbered information frames within a telecommunication system using selective reject (SREJ) frames is disclosed. Upon receiving a sequence numbered information frame from a transmit terminal, a receive terminal determines if it is out of sequence. If the sequence numbered information frame is out of sequence, the receive terminal further checks the sequence numbered information frame to see if a poll bit has been set. If the poll bit is not set, the sequence numbered information frame further checks to see if the sequence numbered information frame is new or retransmitted. If the sequence numbered information frame is new, a list of missing sequence numbers is constructed in ascending sequential order beginning with the missing sequence number one greater than the largest number in the receive queue and ending with N(S)-1. If the sequence numbered information frame is retransmitted, a list of missing sequence numbers is constructed in ascending sequential order beginning with the next smaller missing sequence number in the receive queue plus one and ending with N(S)-1. In either case the ascending sequential order is constructed with respect to the transmit window and the modulo 128 sequence numbering scheme of the LAPD protocol. Thereafter, a select reject frame (SREJ) is sent to the transmit terminal containing a list of the out-of-sequence numbered information frame(s) for re-transmittal.
Owner:APPLE INC
Environmentally driven phone behavior
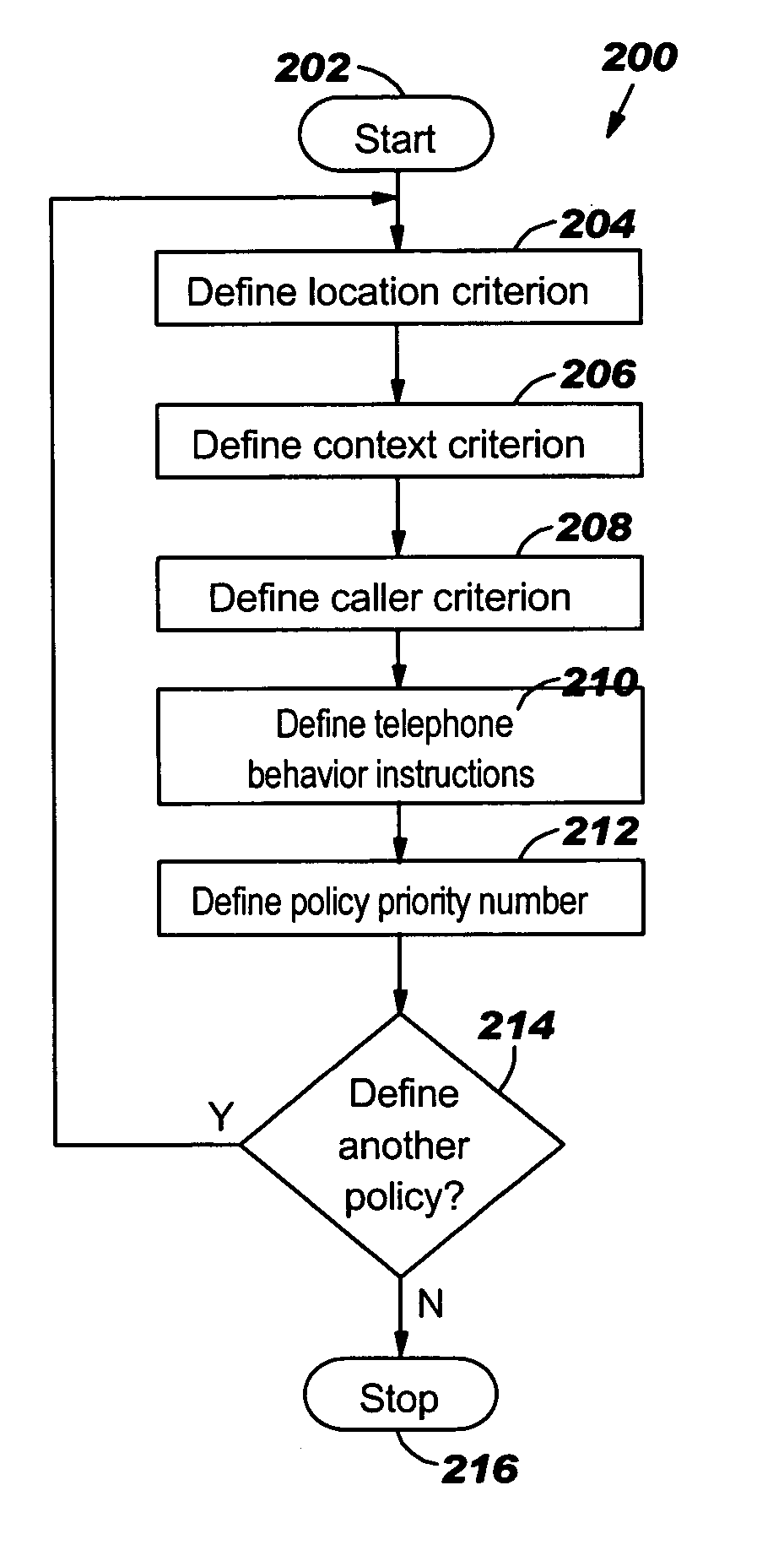
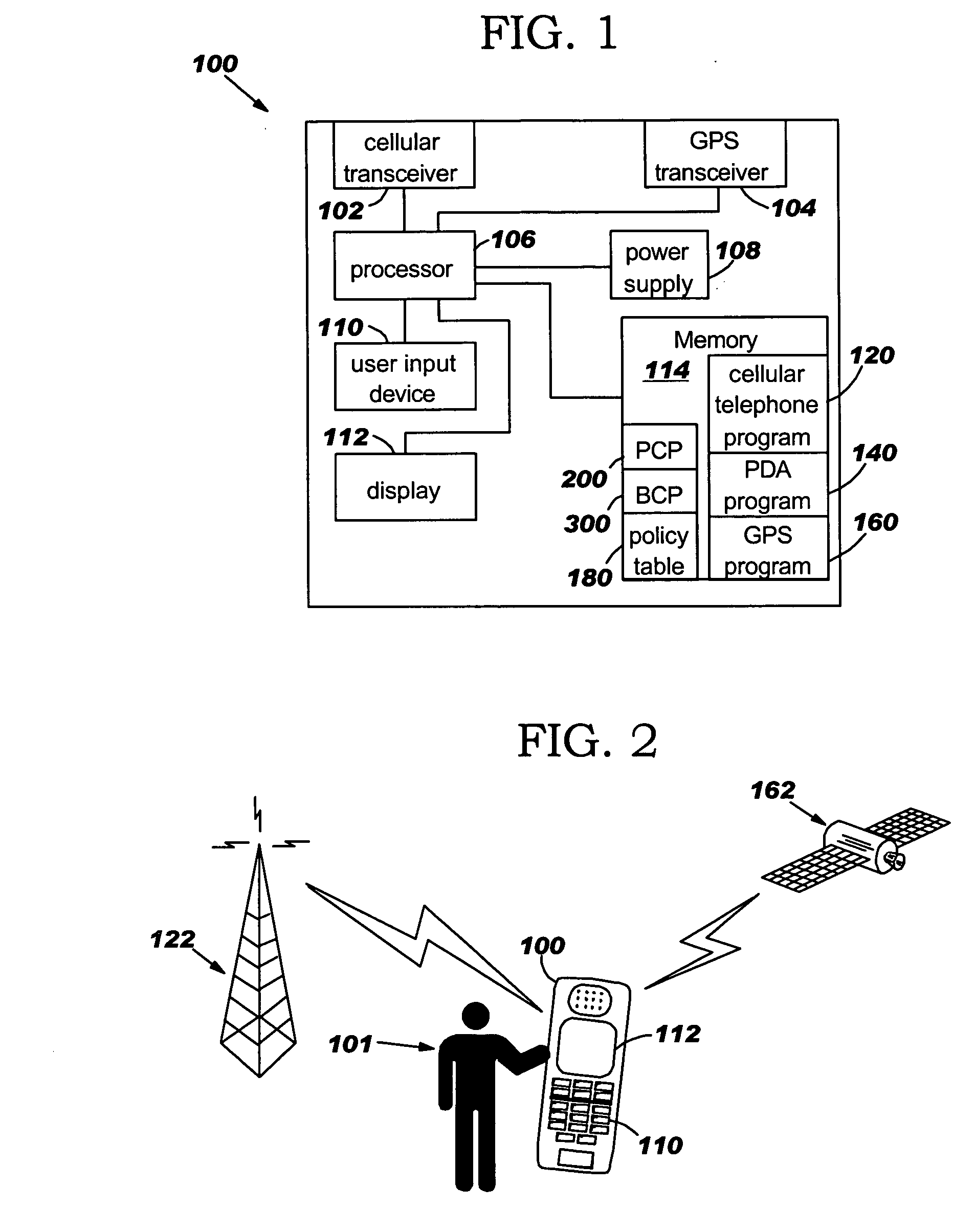
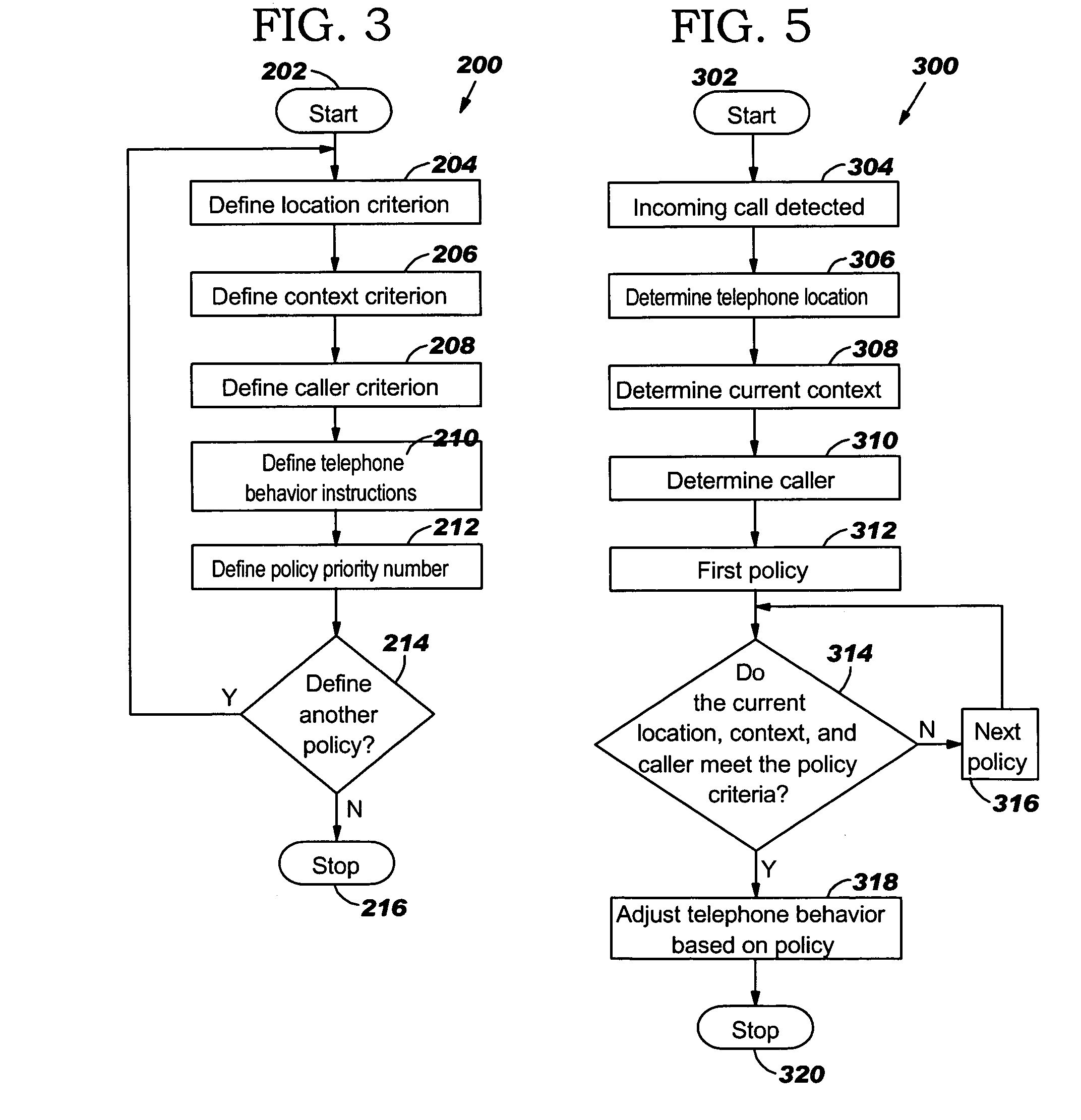
InactiveUS7496352B2Current supply arrangementsCalling susbscriber number recording/indicationOperating systemPriority Number
A method for controlling the behavior of a telephone using policies, the method comprising a Policy Creation Program (PCP) and a Behavior Control Program (BCP). The policies comprise telephone behavior instructions and three criteria conditions: location criteria, context criteria, and caller criteria. Each policy is also assigned a policy priority number based on the importance of the policy, which is used to resolve conflicts between the policies. The PCP allows the user to create the policies and stores the policies in a policy table based on the policy priority numbers. The BCP detects an incoming telephone call and determines the location, context, and caller conditions. The BCP compares the location, context, and caller conditions to a plurality of the policies and determines the policy that matches the conditions. The BCP then controls the telephone's behavior according to the telephone behavior instructions in the policy.
Owner:IBM CORP
Systems and methods for lottery-style games
InactiveUS20100019453A1Facilitate more efficient and more entertaining implementationBoard gamesApparatus for meter-controlled dispensingUnique identifierNumbering scheme
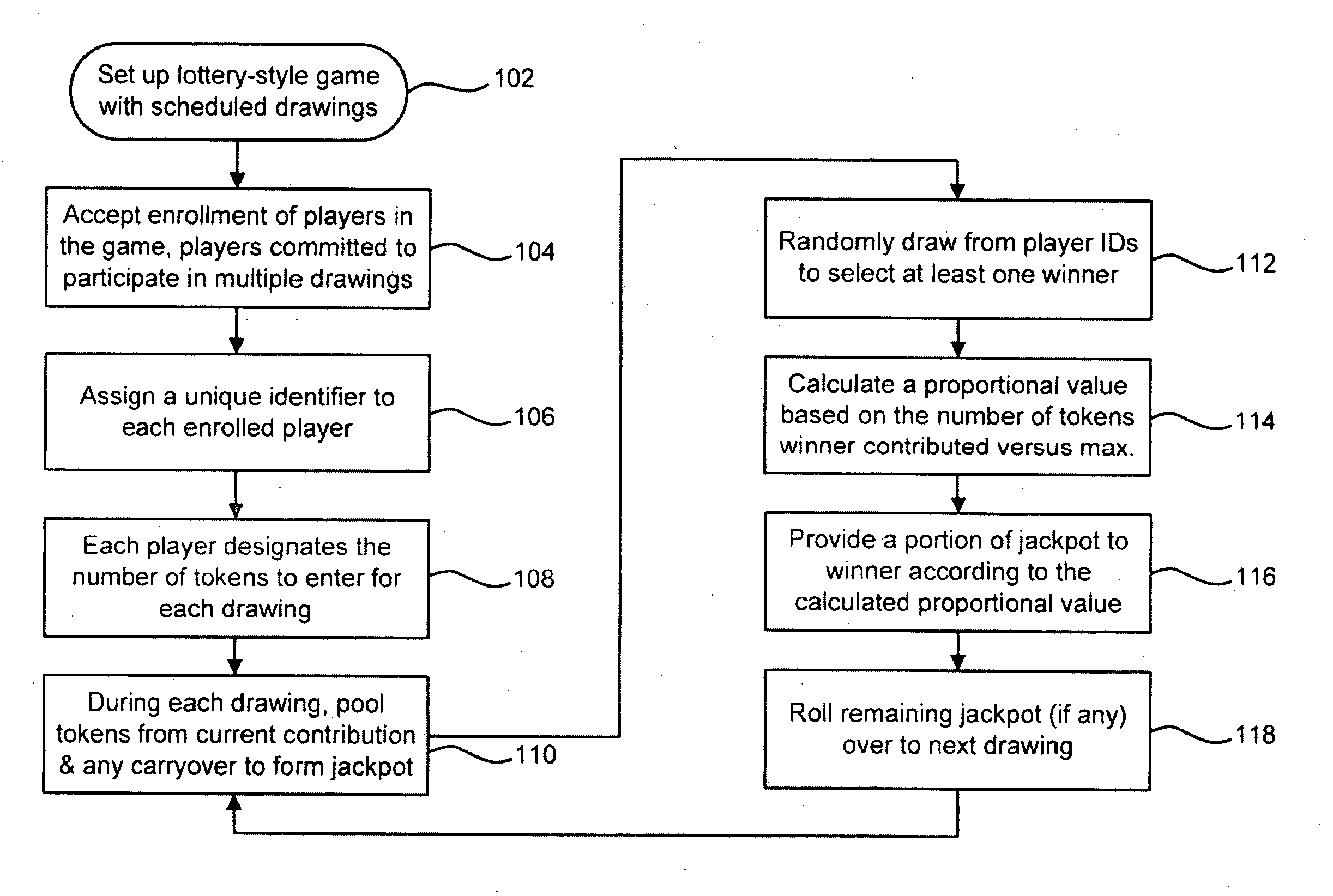
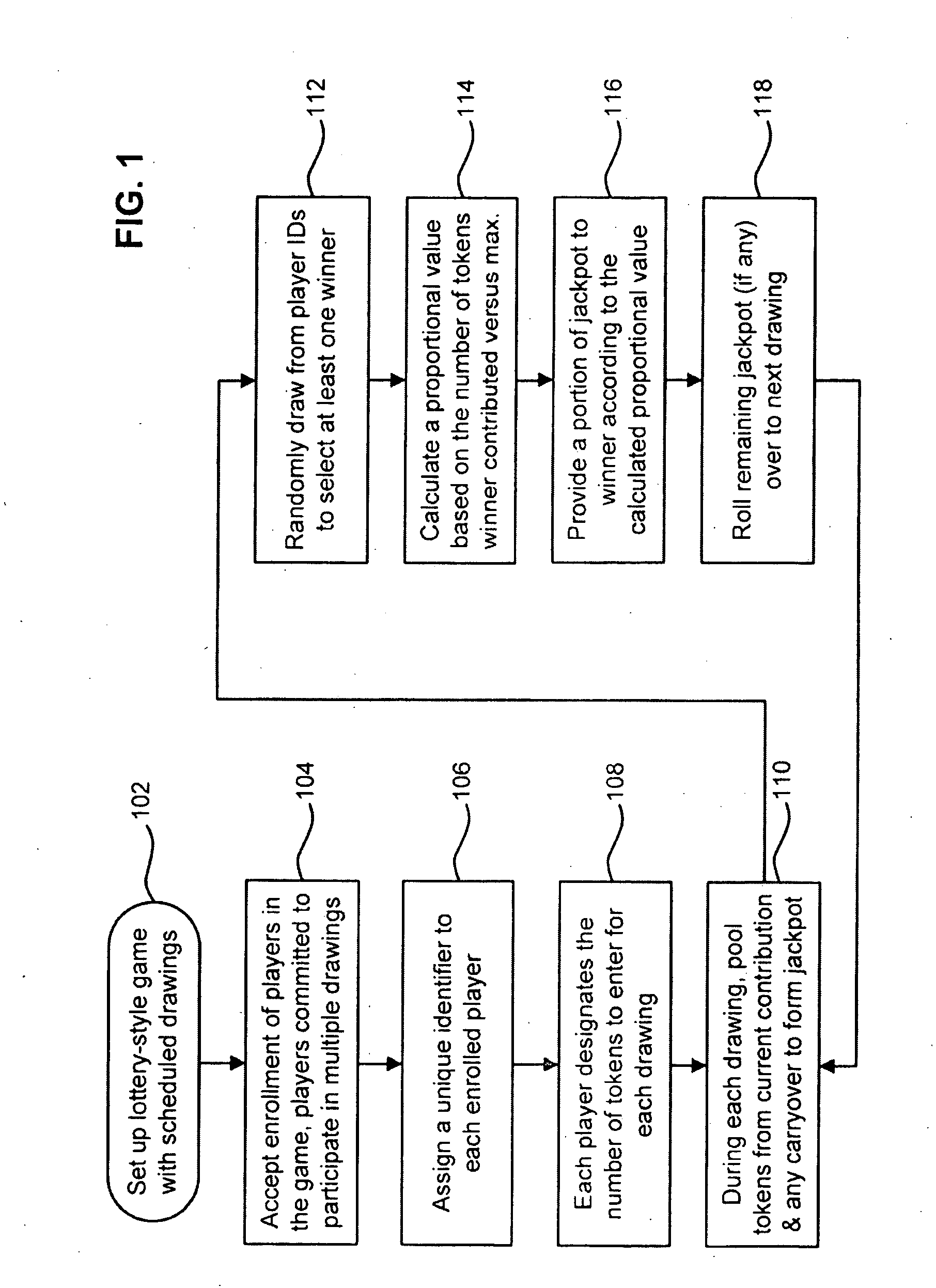
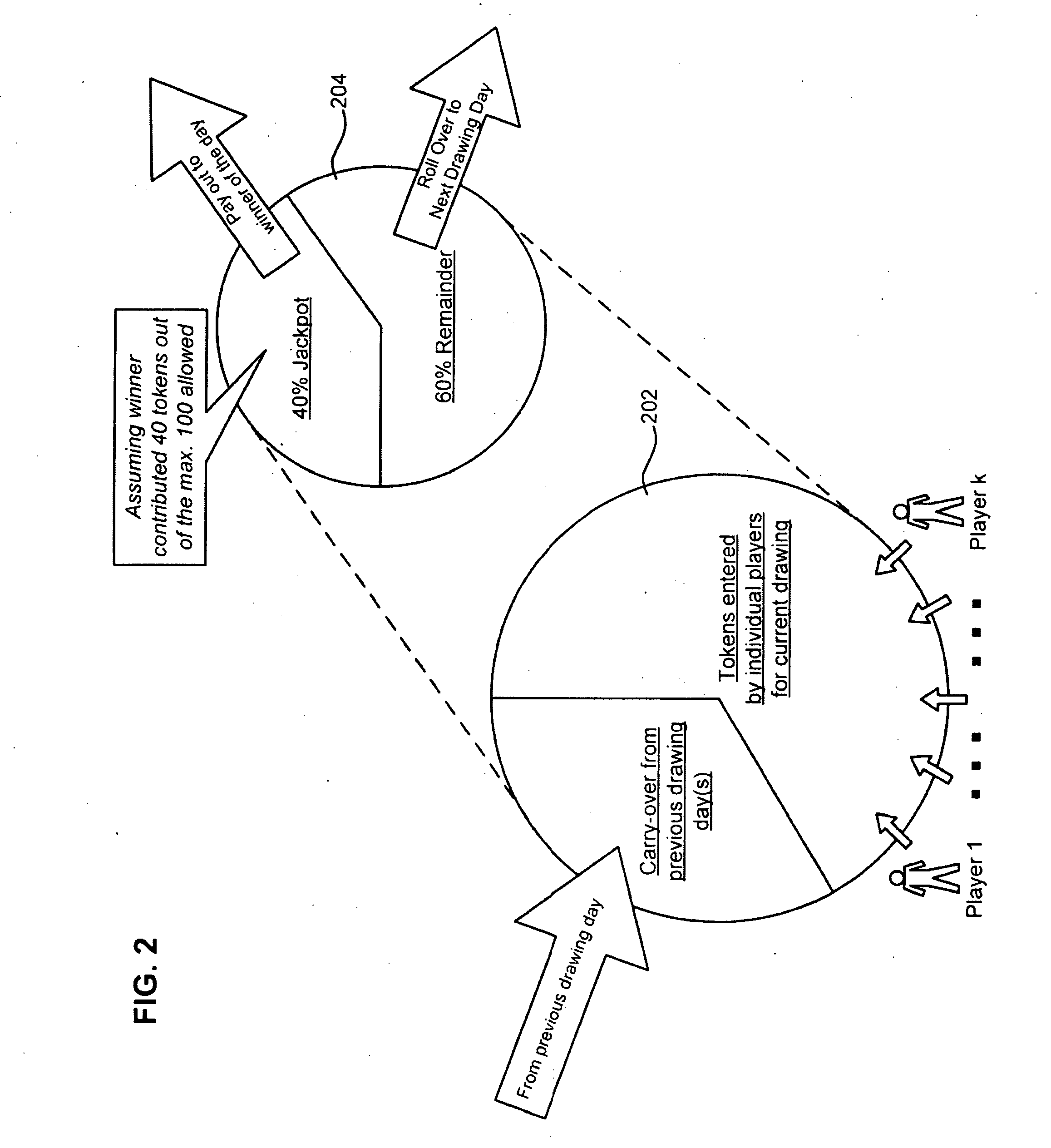
Systems and methods for lottery-style games are disclosed. In one particular exemplary embodiment, a computer-implemented method may comprise: establishing an online game that is scheduled to have lottery drawings on a number of drawing days; accepting enrollment of a plurality of players in the online game, each player being assigned at least one unique identifier and being committed to participate in a plurality of the lottery drawings; receiving, from each player, a designated number of tokens to be entered for each unique identifier in each lottery drawing said player is committed to participate in, each designated number being at least one and up to a predetermined maximum; and executing the online game on each drawing day by conducting a drawing, from unique identifiers of the participating players, to select one winner and by providing a fraction of a jackpot to the selected winner based on a calculated proportional value.
Owner:GEONOMICS GLOBAL GAMES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com