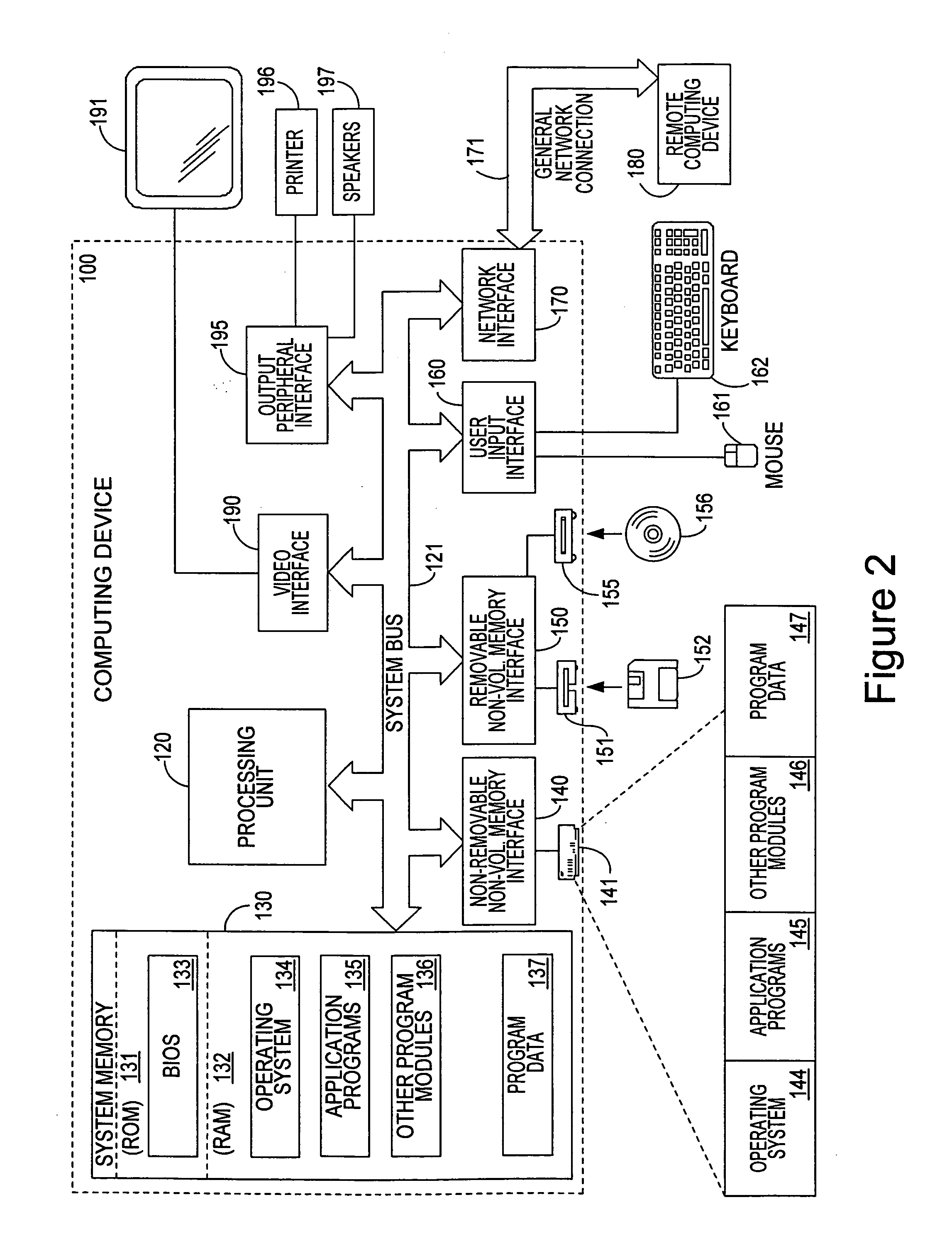
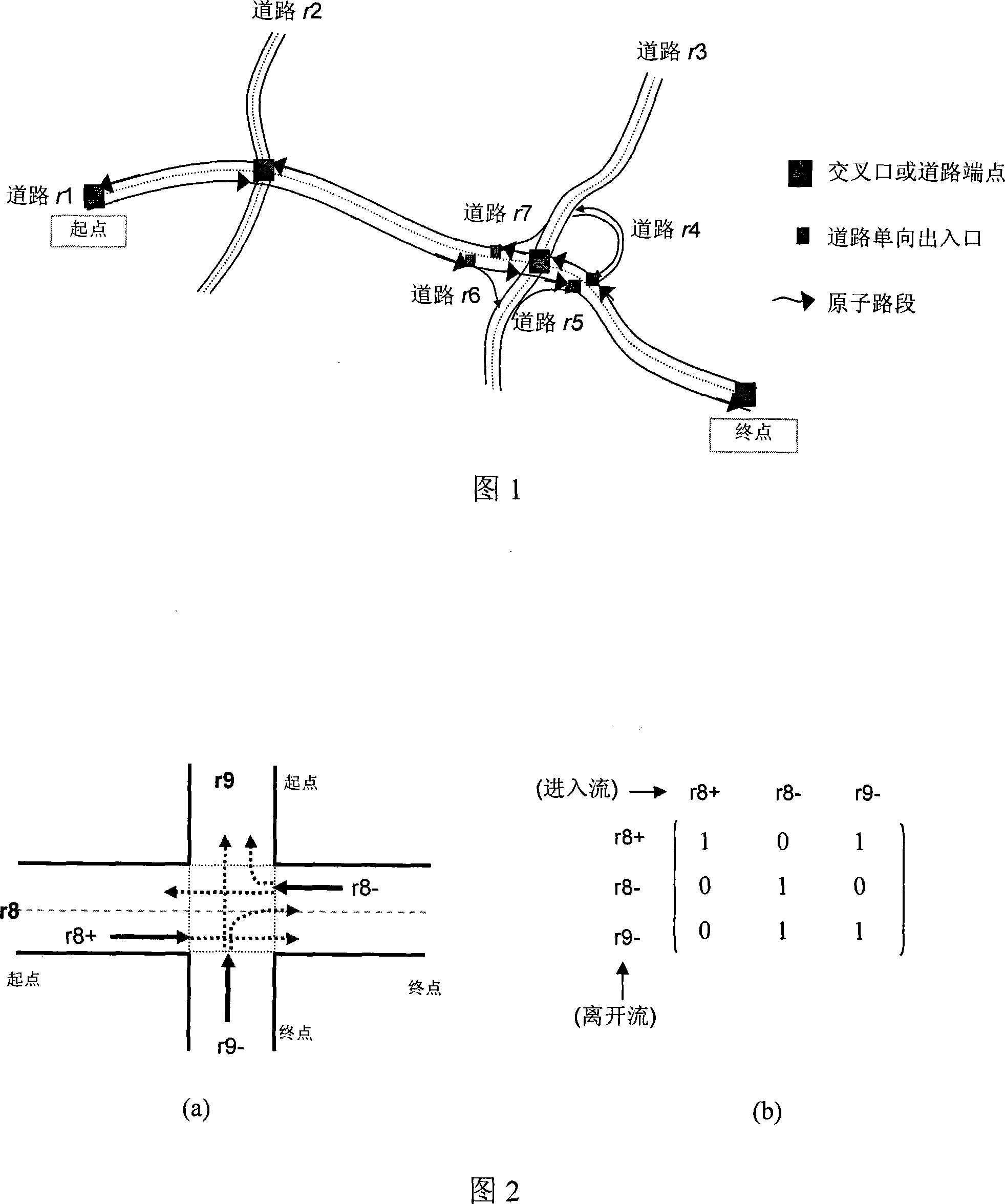
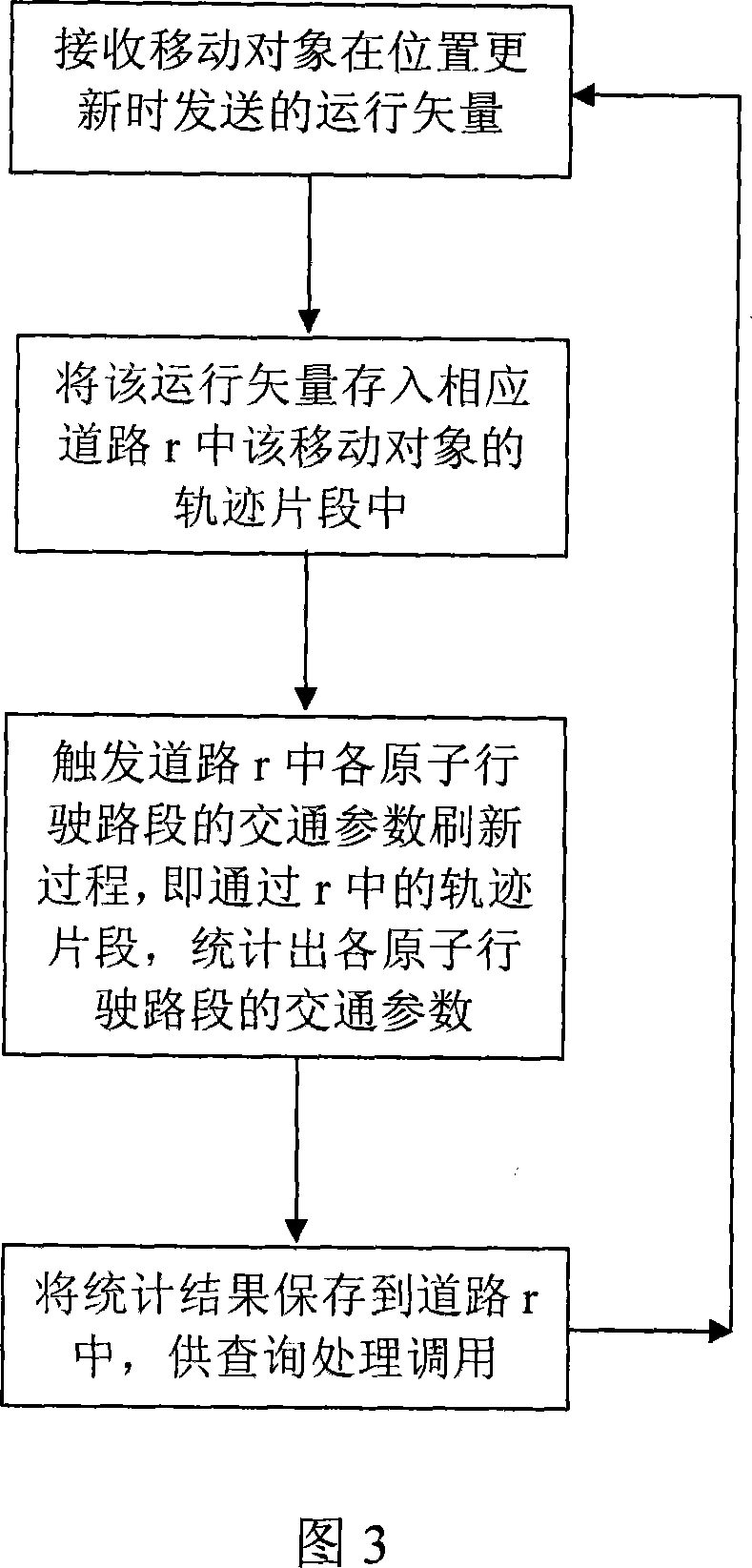
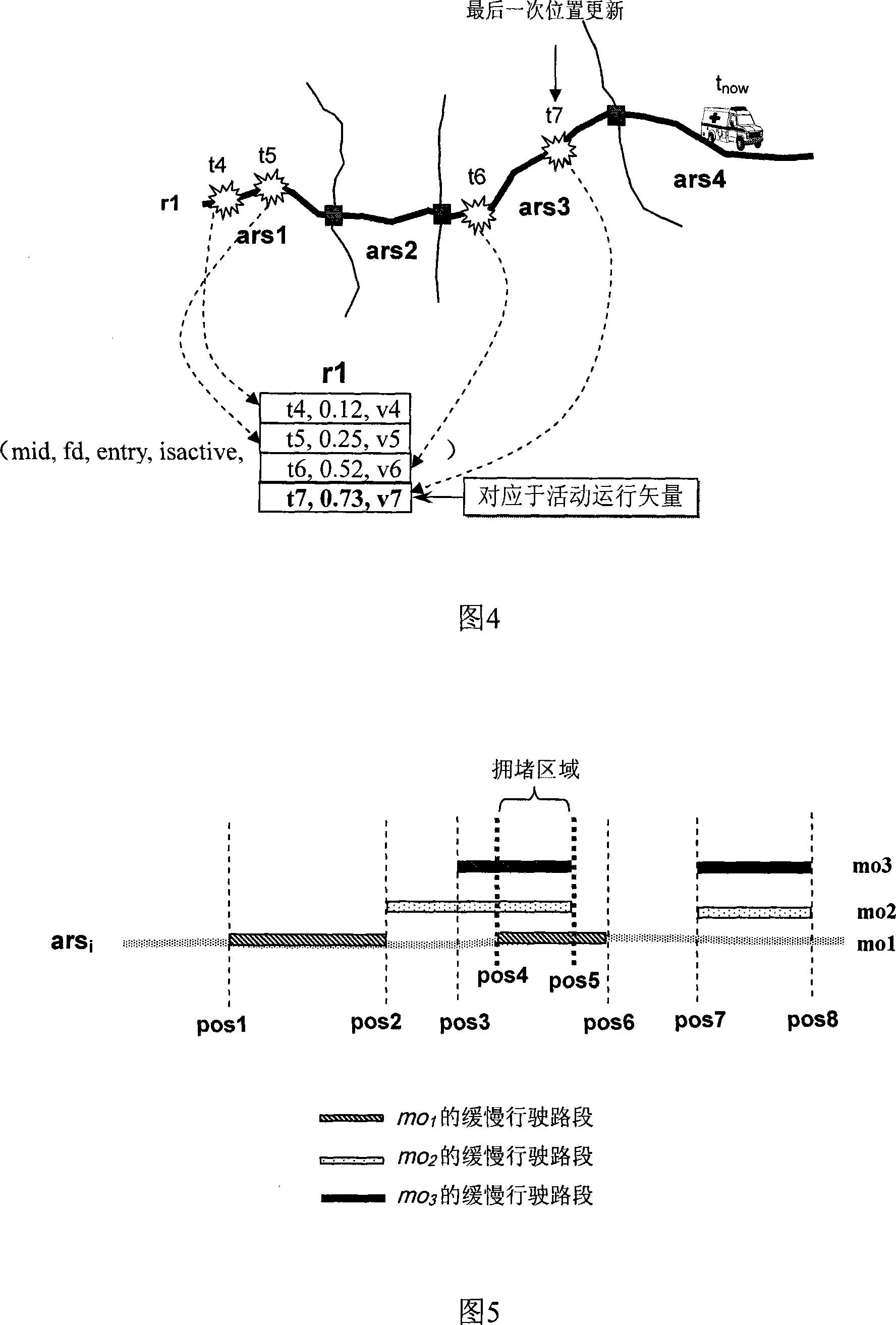
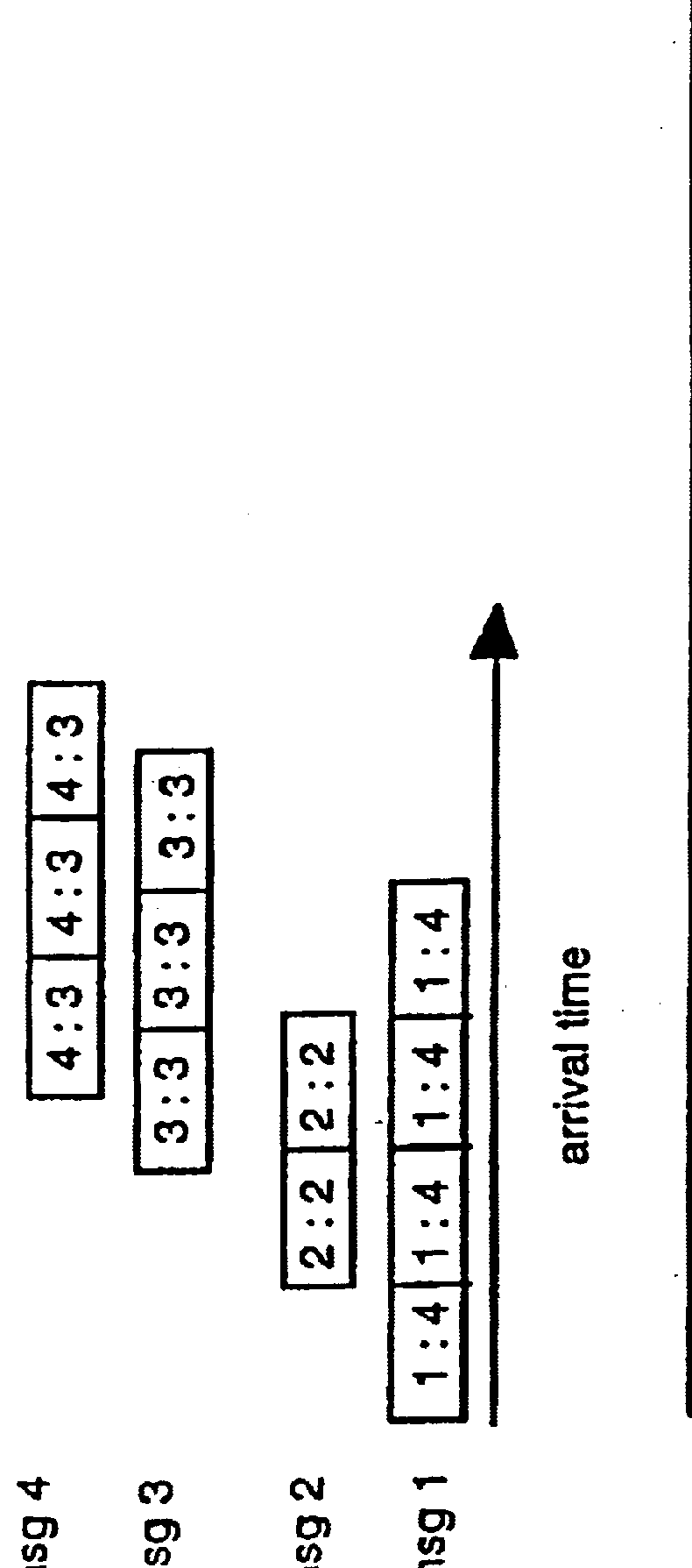
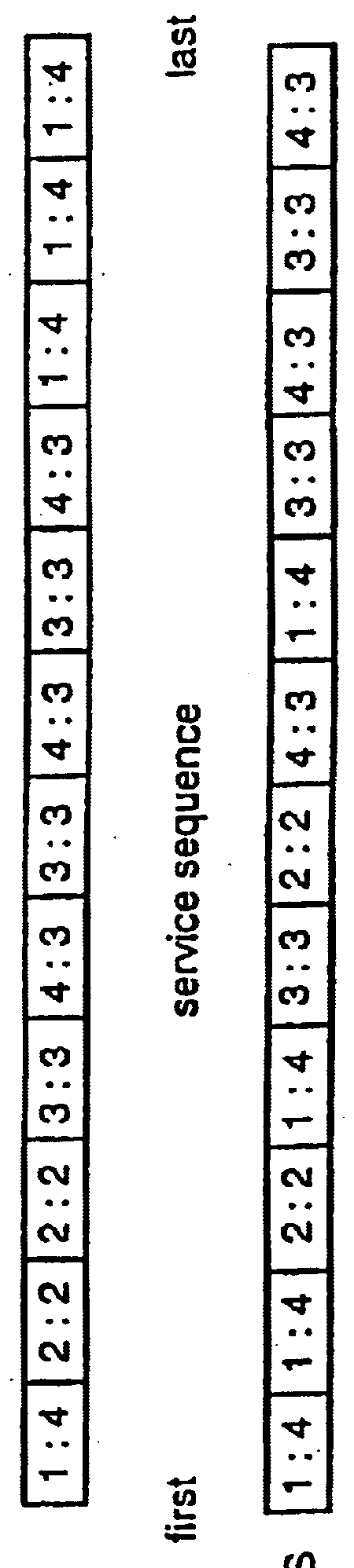
Patents
Literature
184 results about "Message delay" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
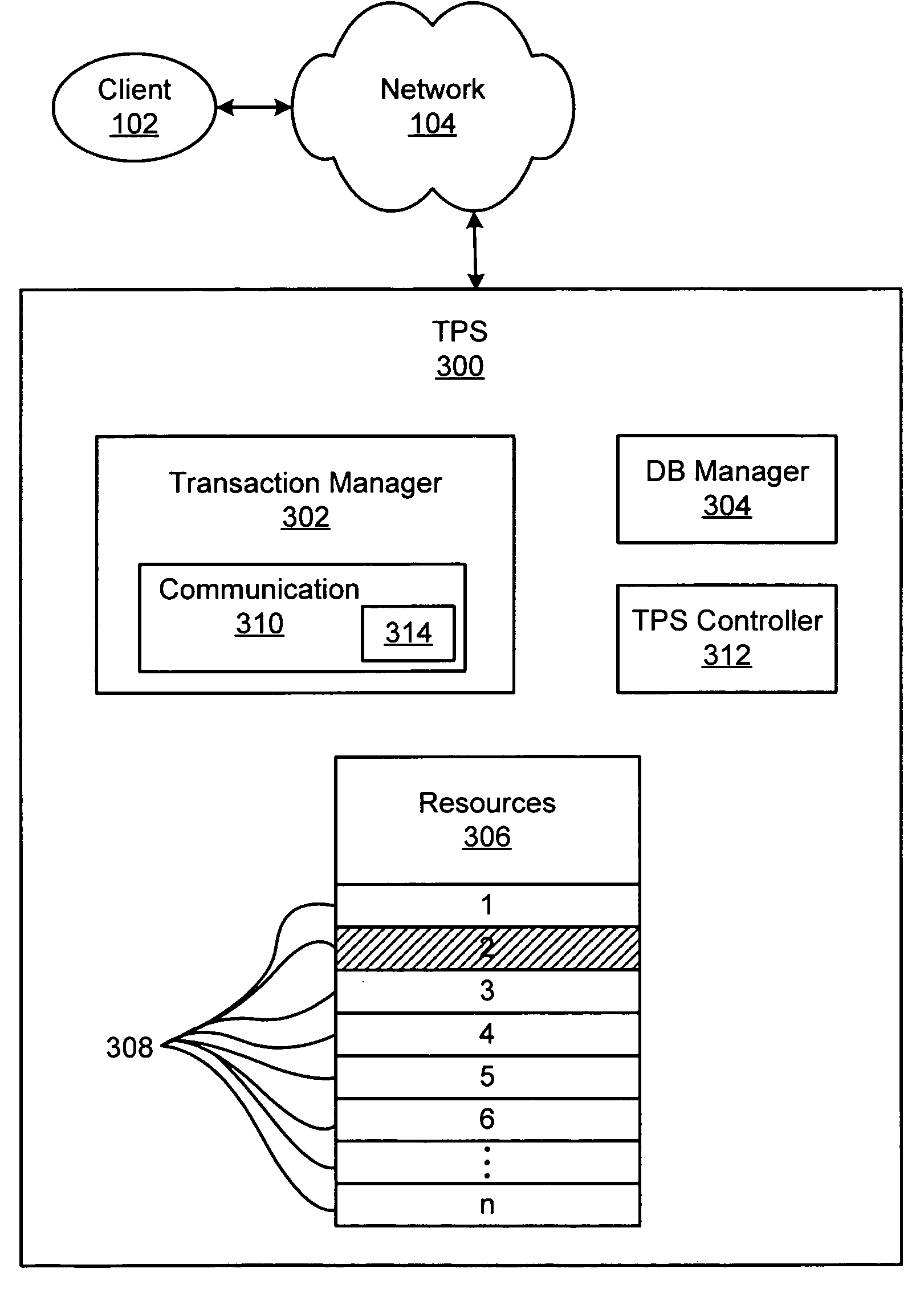
Fast transaction commit
InactiveUS7558883B1Few message delayMaintain consistencyError detection/correctionDatabase distribution/replicationClient-sideComputing systems
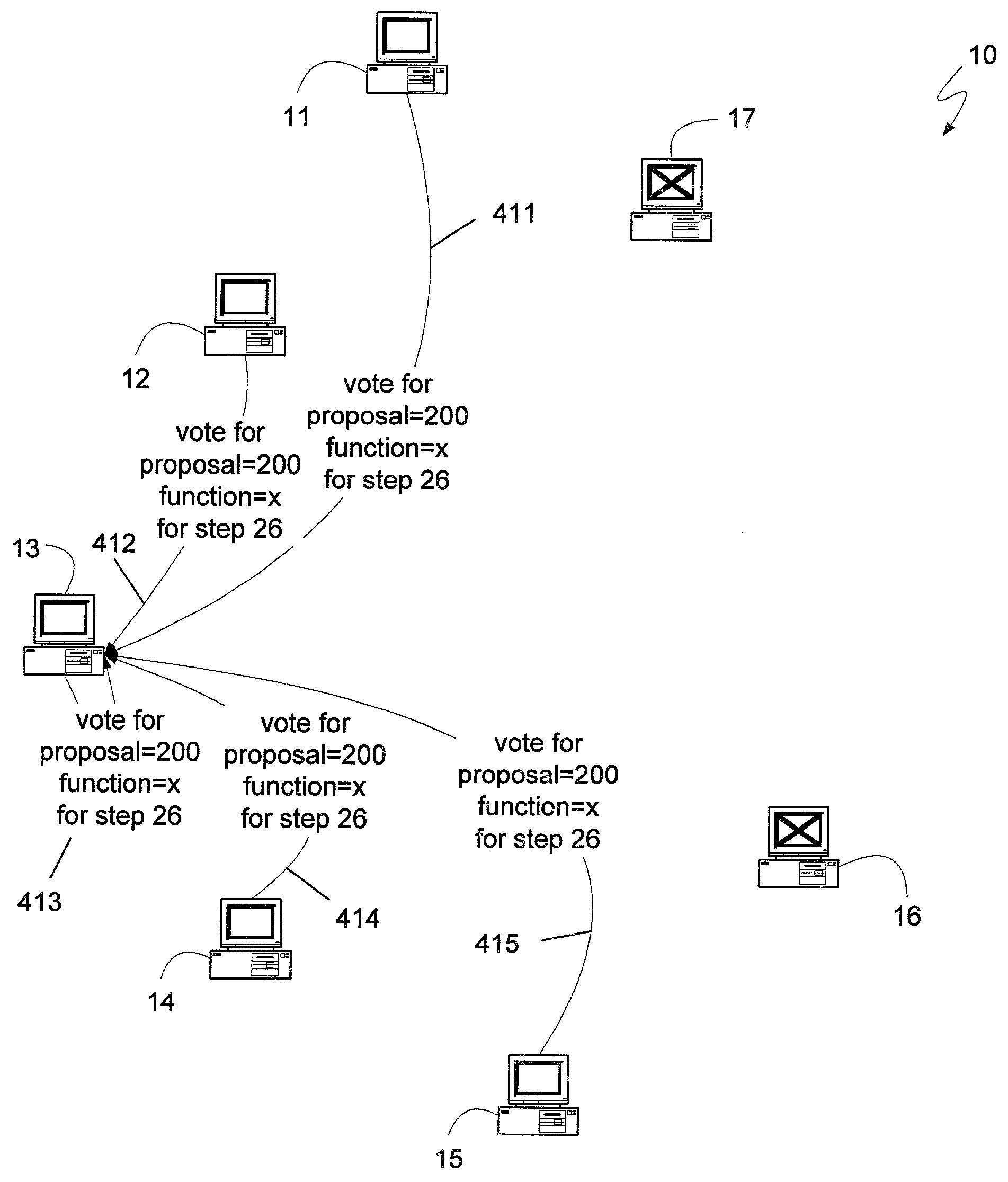
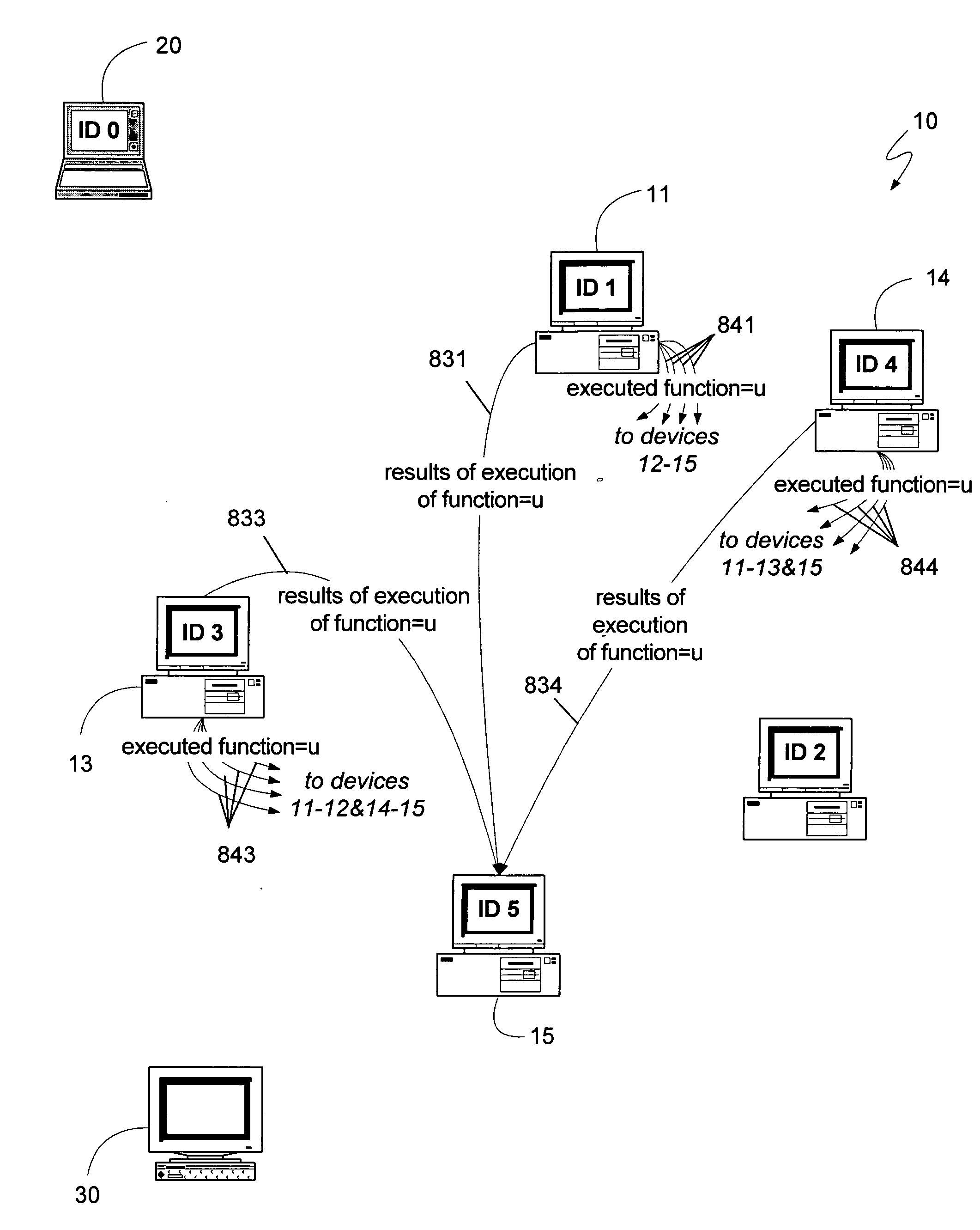
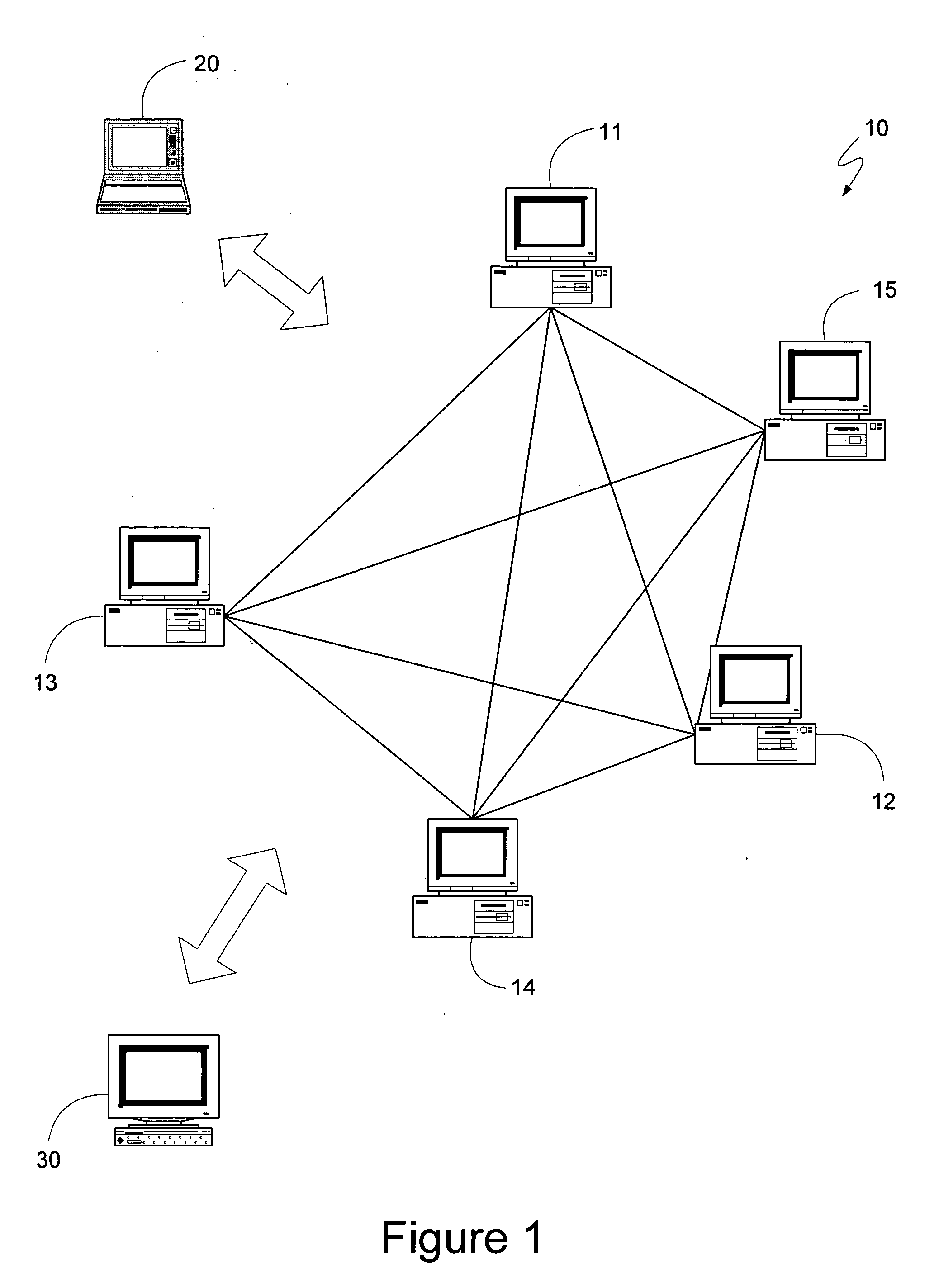
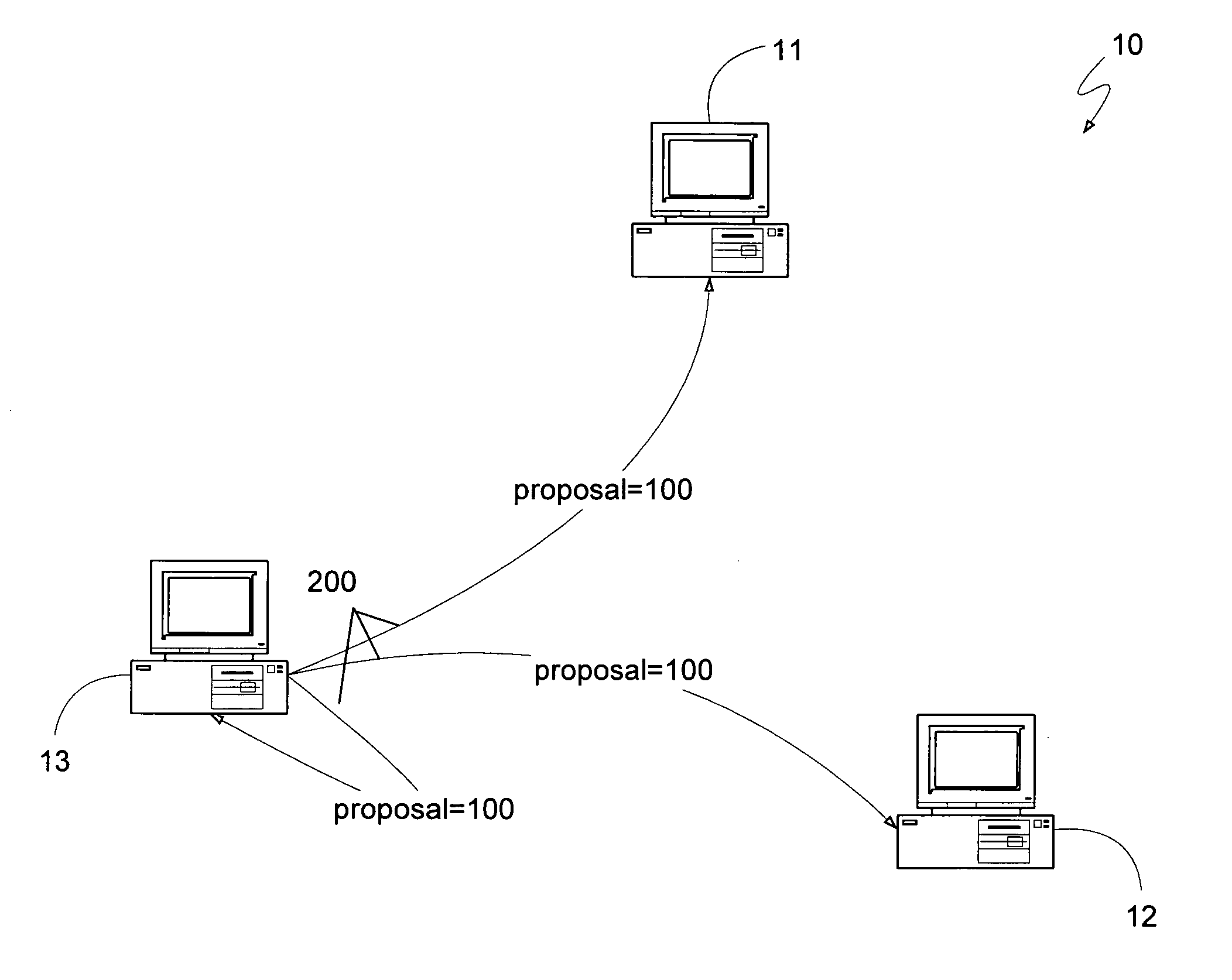
A distributed computing system, having a sufficient number of devices and requiring a sufficiently large number of devices to select any proposal, can maintain synchronization between its constituent devices and respond to client requests with as few as two message delays. A leader can synchronize the devices of the system and establish a safe proposal number for all current and future steps of the system. Devices can then receive client requests directly, treating the request as a proposal having the proposal number determined previously by the leader, and voting for the proposal. If the client receives an indication from a least a quorum of devices, where a quorum can be the minimum number of devices that can be operational at a given time, the client can know that the request was selected. If two or more clients attempt to request different functions at approximately the same time, the system may not select either request, in which case a leader can be requested to determine if any requests may have been selected, and to reestablish a safe proposal number. Systems with fewer devices can also implement the message-delay-reducing algorithm if they can also revert to the standard Paxos algorithm if an insufficient number of devices are operational. Such algorithms can be used to provide an efficient method for determining whether to commit or abort a client transaction.
Owner:MICROSOFT TECH LICENSING LLC
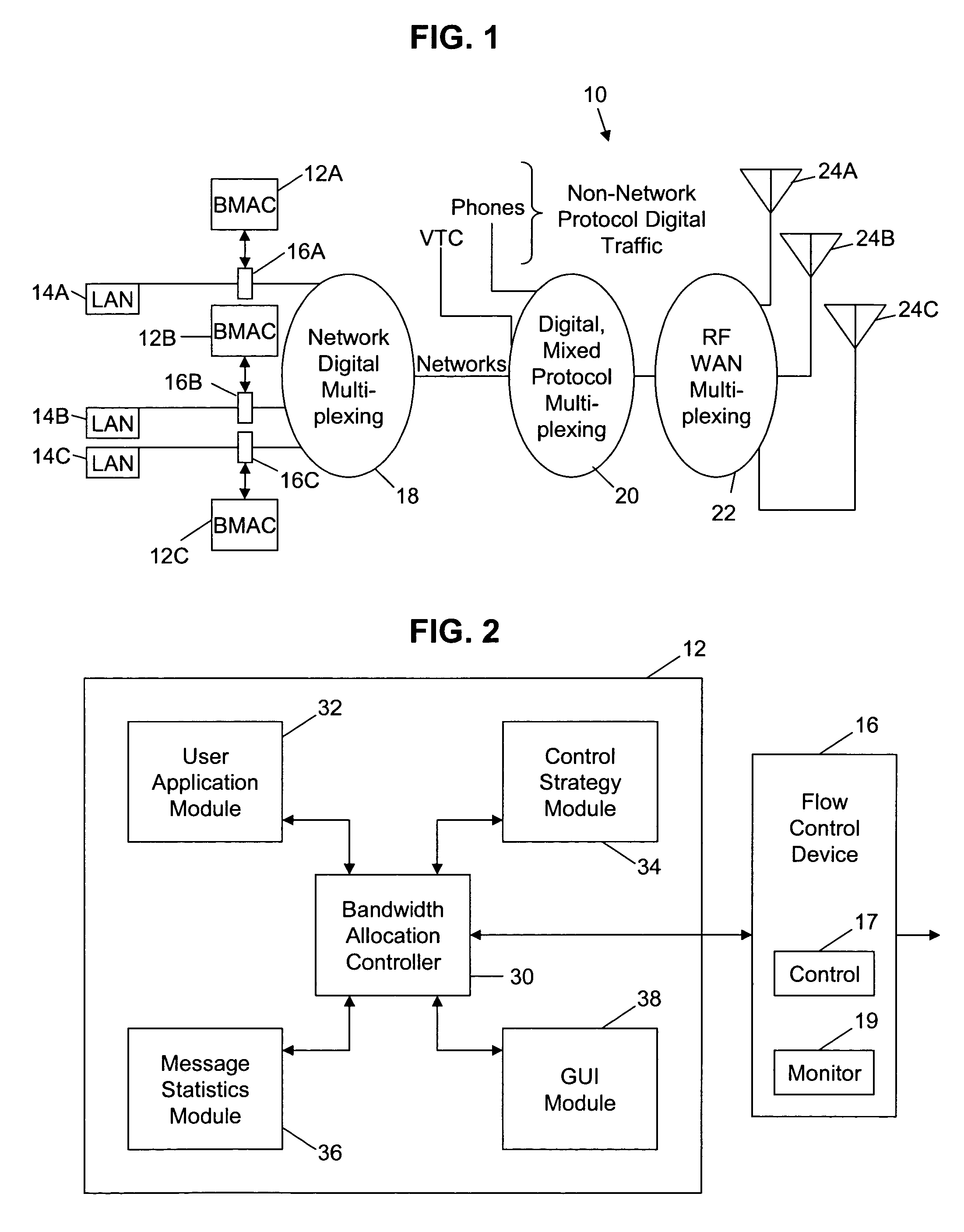
Method and apparatus for controlling the allocation of bandwidth of a network access point to an application having a message transmitted on the network
InactiveUS7493407B2Multiple digital computer combinationsData switching networksGraphicsGraphical user interface
An automated bandwidth monitoring and control method and system provides for real time, dynamic control of the allocation of bandwidth to selected applications in a communications network based on the selected operational context and the fixed bandwidth available at a network access point. A graphical user interface, using operational terms common to the overall enterprise in which and for which the network is implemented and understandable by an operator, displays the bandwidth allocation strategy, and in substantially real time displays statistics representative of actual bandwidth use at the access point, input functions for modifying the bandwidth allocation strategy in substantially real time and estimated message delay distributions for the applications of the strategy determined based on the actual bandwidth use statistics.
Owner:DRS TECHN SERVICES
Failure detector with consensus protocol
InactiveUS6687847B1Emergency protective arrangements for automatic disconnectionNon-redundant fault processingStable storageComputing systems
New failure detector mechanisms particularly suitable for use in asynchronous distributed computing systems in which processes may crash and recover, and two crash-recovery consensus mechanisms, one requiring stable storage and the other not requiring it. Both consensus mechanisms tolerate link failures and are particularly efficient in the common runs with no failures or failure detector mistakes. Consensus is achieved in such runs within 3□ time and with 4n messages, where □ is the maximum message delay and n is the number of processes in the system.
Owner:CORNELL RES FOUNDATION INC
Fast byzantine paxos
ActiveUS7620680B1Accurate authenticationProvide securityMultiple digital computer combinationsTransmissionDigital signatureClient-side
A distributed computing system can operate in the face of malicious failures on the part of some of its constituent devices, and provide a minimum of message delays between receiving a client request and providing a response, when each device within the system verifies the sender of any message it receives, and the propriety of the message. The sender can be verified through message authentication schemes or digital signature schemes. The propriety of a message can be verified by receiving a sufficiently large number of equivalent, properly authenticated messages. If the number of malicious devices is represented by the variable “M”, a sufficient number of equivalent, properly authenticated messages to verify that the message is true can be any number of messages greater than M. Furthermore, to verify that a leader device is not maliciously submitting different proposals to different devices using the same proposal number, a quorum of devices can be required to select a proposal, where a quorum is a sufficiently large number of devices such that any other quorum has, as a majority of its devices, non-malicious devices from the first quorum. Therefore, the distributed computing system can operate properly with M number of malicious failures and F number of total failures, and with a minimum of message delays, if the number of constituent devices in the distributed computing system is greater than 3F+2M. Additionally, if the distributed computing system can revert to a more traditional algorithm if too many devices fail or become malicious, it can use a message-delay-reducing algorithm while having as few as 2Q+F+2M+1 constituent devices, where Q is the number of devices that can fail and still allow the system to use a message-delay-reducing algorithm.
Owner:MICROSOFT TECH LICENSING LLC
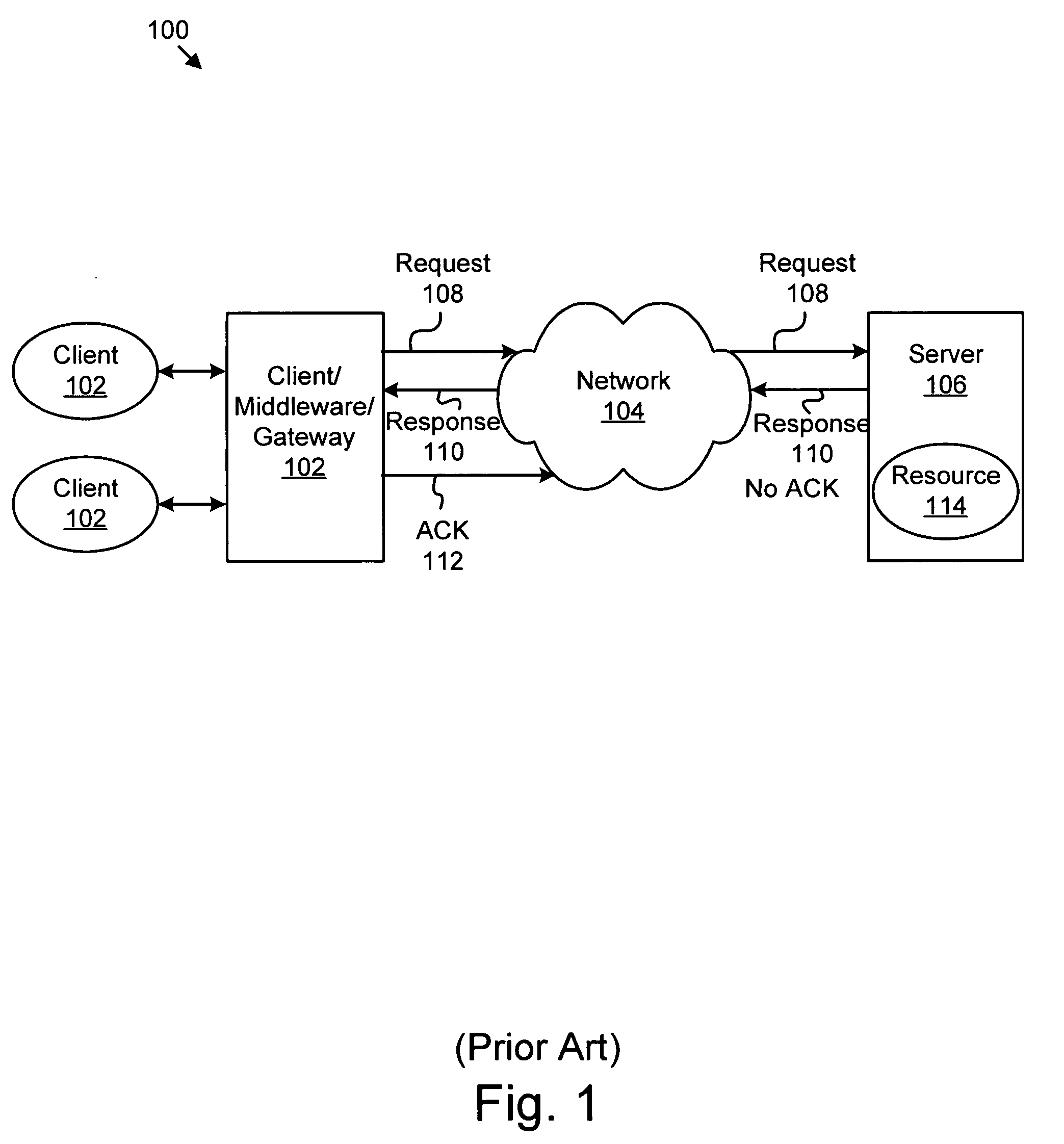
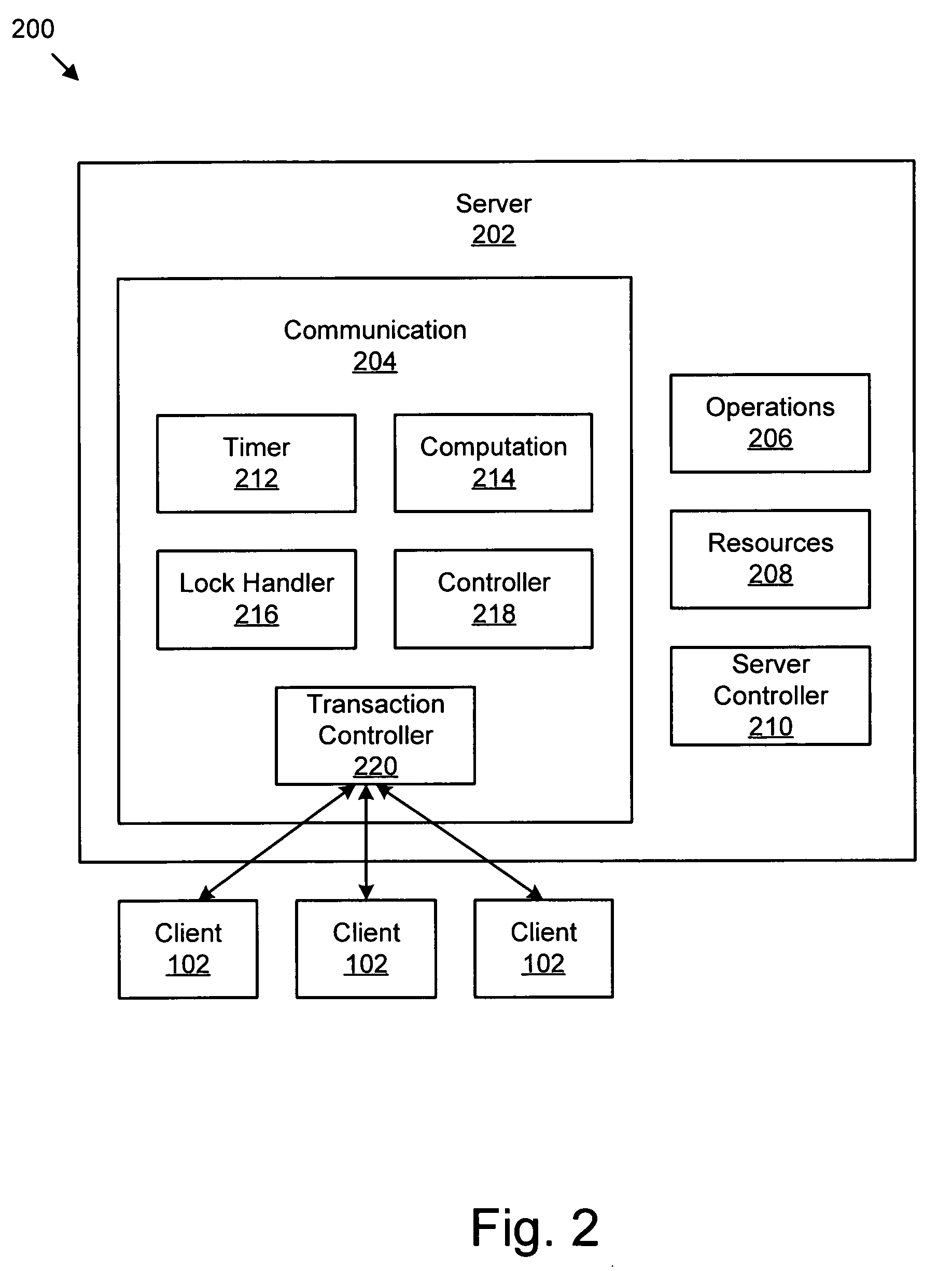
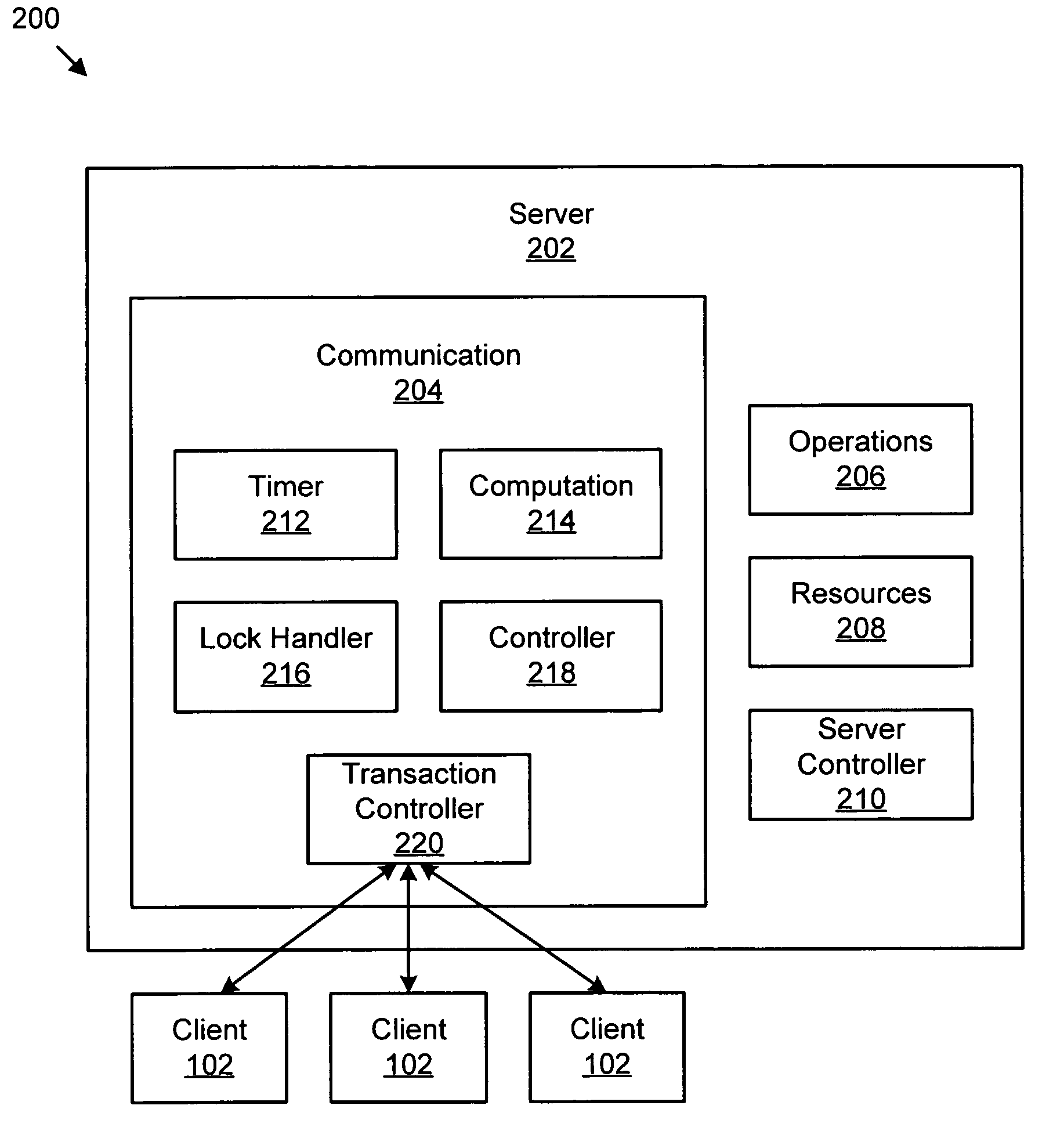
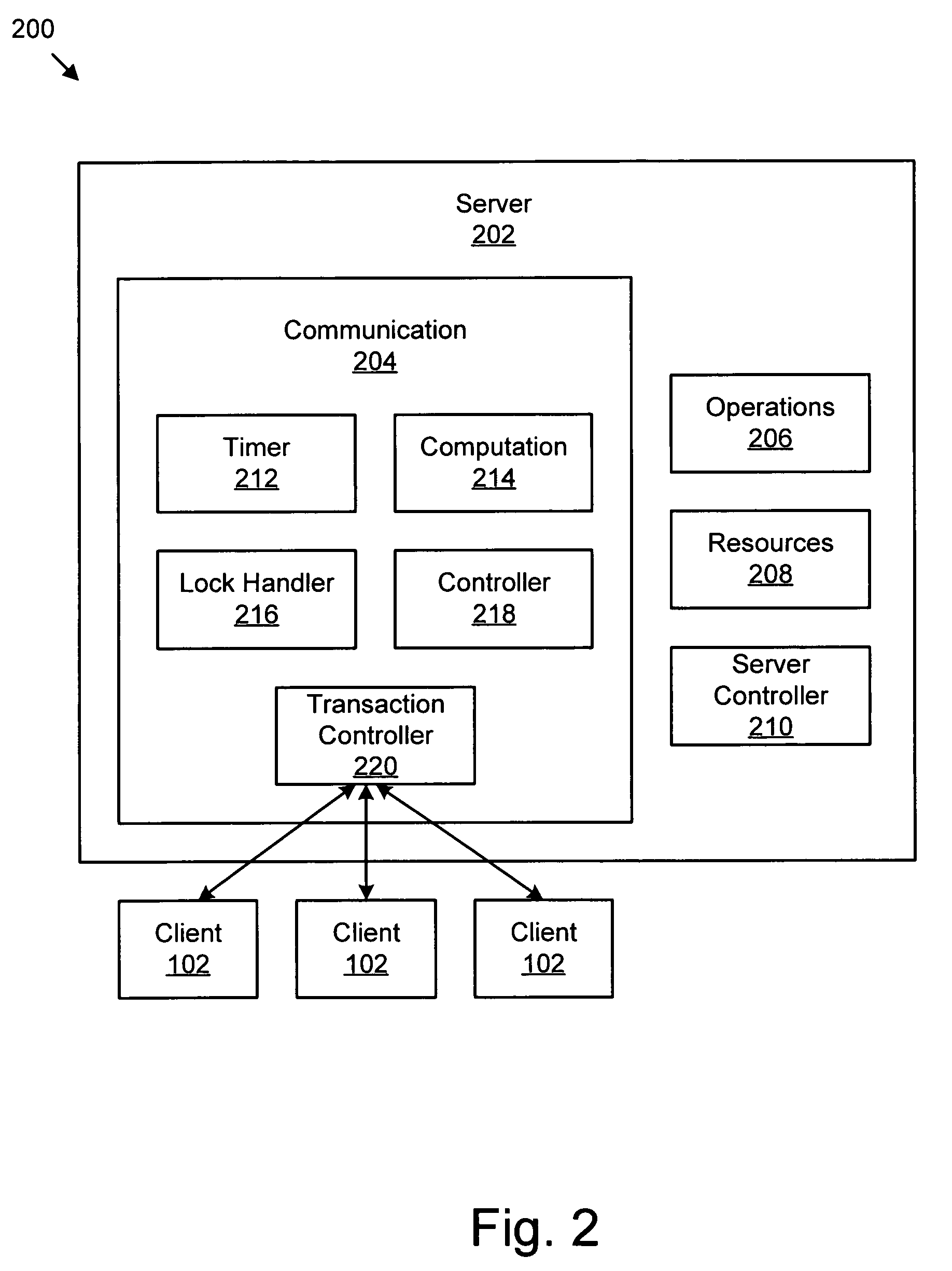
Apparatus, system, and method for automatically freeing a server resource locked awaiting a failed acknowledgement from a client
An apparatus, system, and method are provided for automatically freeing locked server resources using a timeout value closely related to actual real-time message delays plus a delta value that can be adjusted at a plurality of levels. The levels include default, server, connection, and transaction. The apparatus includes a timer, a communication module, a computation module, and a lock handler. The timer determines a timeout value for communications from a client to a server. The communication module sends an output message to the client and locks a server resource in anticipation of an acknowledgement (ACK) message from the client. The computation module, which calculates an ACK timer, includes a difference between a send time and a current time. If no ACK message has been received from the client and the ACK timer exceeds the timeout value, the lock handler may free the locked server resource.
Owner:IBM CORP
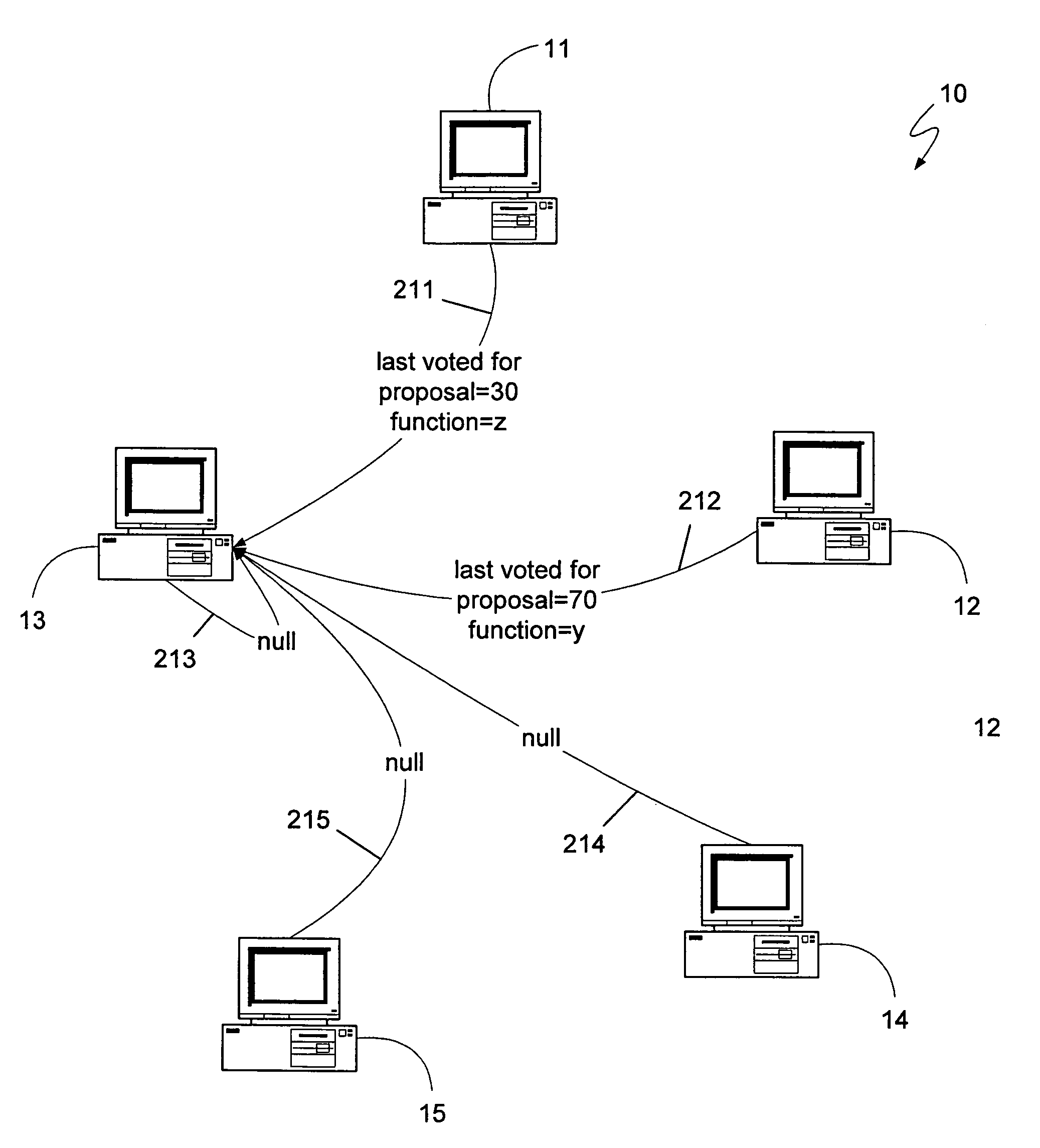
Fast Paxos recovery
ActiveUS7555516B2Error detection/correctionMultiple digital computer combinationsClient-sideMessage delay
A distributed computing system can achieve consensus while introducing fewer message delays by using an algorithm that allows the constituent devices to vote on functions received directly from one or more clients. If a conflict occurs, a leader device from among the devices can be selected such that the leader device already knows of the other devices' previous votes, and can determine an appropriate function to propose, using an immediately subsequent proposal number, without performing the first phase of the Paxos algorithm. Alternatively, each device can independently determine, by using the same repeatable mechanism used by a leader device, what function the leader device would propose, and can then vote for that function using the immediately subsequent proposal number. If the devices' votes again result in a conflict, the Paxos algorithm can be used, or additional iterations can be performed prior to resorting to the Paxos algorithm.
Owner:MICROSOFT TECH LICENSING LLC
Fast paxos recovery
ActiveUS20060168011A1Error detection/correctionMultiple digital computer combinationsClient-sideComputer science
A distributed computing system can achieve consensus while introducing fewer message delays by using an algorithm that allows the constituent devices to vote on functions received directly from one or more clients. If a conflict occurs, a leader device from among the devices can be selected such that the leader device already knows of the other devices' previous votes, and can determine an appropriate function to propose, using an immediately subsequent proposal number, without performing the first phase of the Paxos algorithm. Alternatively, each device can independently determine, by using the same repeatable mechanism used by a leader device, what function the leader device would propose, and can then vote for that function using the immediately subsequent proposal number. If the devices' votes again result in a conflict, the Paxos algorithm can be used, or additional iterations can be performed prior to resorting to the Paxos algorithm.
Owner:MICROSOFT TECH LICENSING LLC
Traffic flow data sampling and analysis based on network limited moving object database
ActiveCN101127159AGuaranteed collectionInstruments for road network navigationDetection of traffic movementStatistical analysisData acquisition
Owner:WUXI ZHONGKE IOT BASIC SOFTWARE R & D CENT CO LTD
Conflict fast consensus
InactiveUS20050149609A1Multiple digital computer combinationsProgram controlClient-sideDirect response
A conflict tolerant message delay reducing consensus algorithm is presented for operating a distributed computing system. The devices of the distributed computing system can directly receive client requests, and can execute the requests and respond directly to the clients, saving message delays. If there is a conflict, the ultimately selected request can be the request submitted by the client with the highest client identifier. A device can change its vote, and execute a different request, if it is made by a client having a more dominant client identifier. All but one of the clients can also be a device implementing the system. A device that has executed a requested function may no longer submit a request in the same step. Consequently, a request is executed by the system when all devices have executed the request. If one or more devices fails, any fault tolerant consensus algorithm can be used.
Owner:MICROSOFT TECH LICENSING LLC
Simplified Paxos
ActiveUS7711825B2To overcome the large delayFast learningMultiple digital computer combinationsSpecial data processing applicationsClient-sideMessage delay
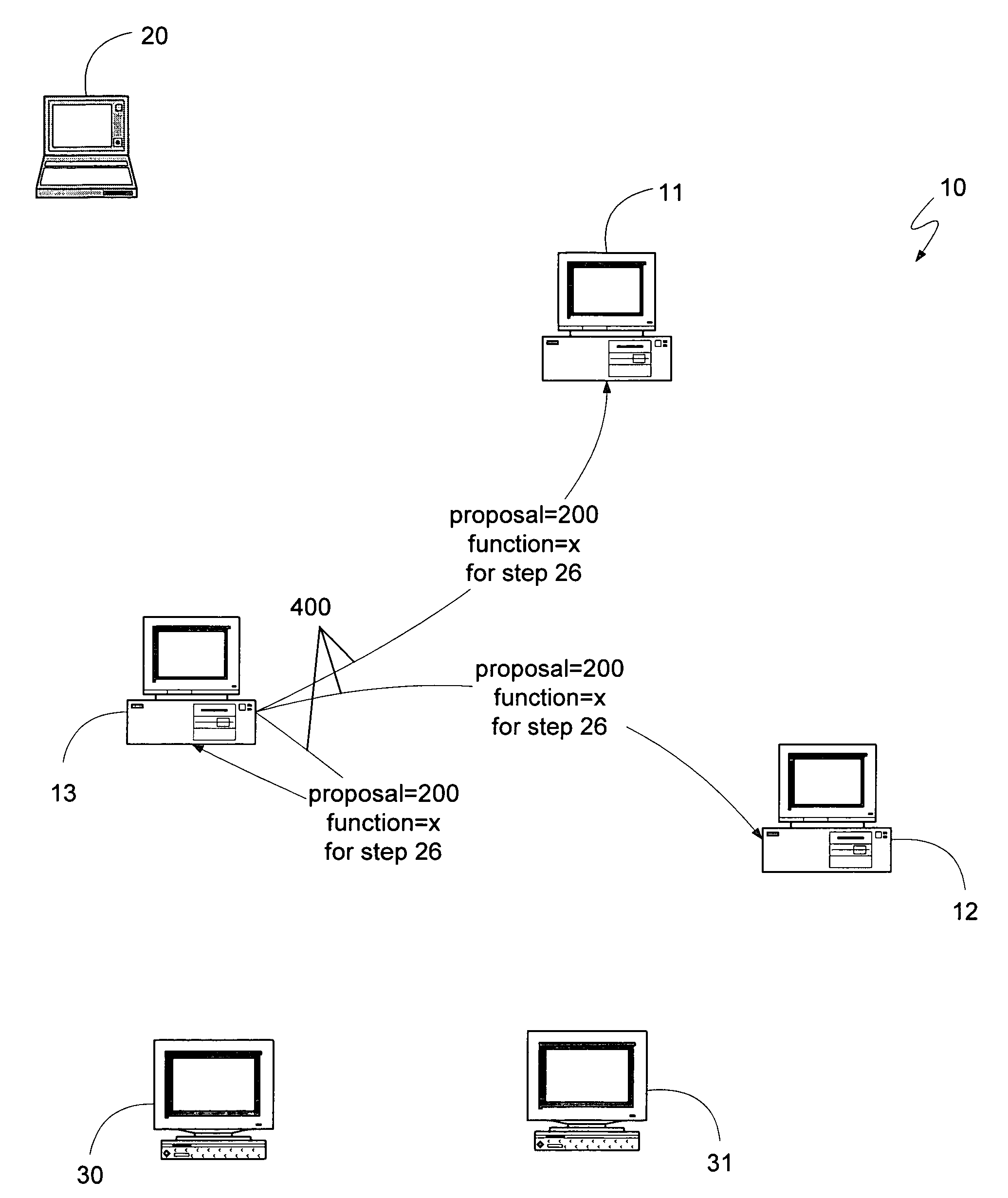
A simplified fault tolerant algorithm is presented for operating a distributed computing system in a fault tolerant manner. A system comprising three computing devices need only have two devices agree to perform any proposed function. Thus, when soliciting a vote for a proposed function, a leader device can also send its vote for the proposed function. This allows any recipient device to complete the quorum with its own vote. Consequently, any recipient device can, without any further messages, determine whether to execute the proposed function. Furthermore, if the device executes the proposed function, it can transmit the results directly to the client that requested the function, saving a message delay. If the quorum of devices used to select and execute proposed functions is itself selected by a quorum, then one of the devices of the system can be an inexpensive device having limited computational ability or storage capacity.
Owner:MICROSOFT TECH LICENSING LLC
Method and device for selecting time synchronization sources
ActiveCN102957488AImprove rationalityIncrease flexibilityTime-division multiplexQuality levelProtection mechanism
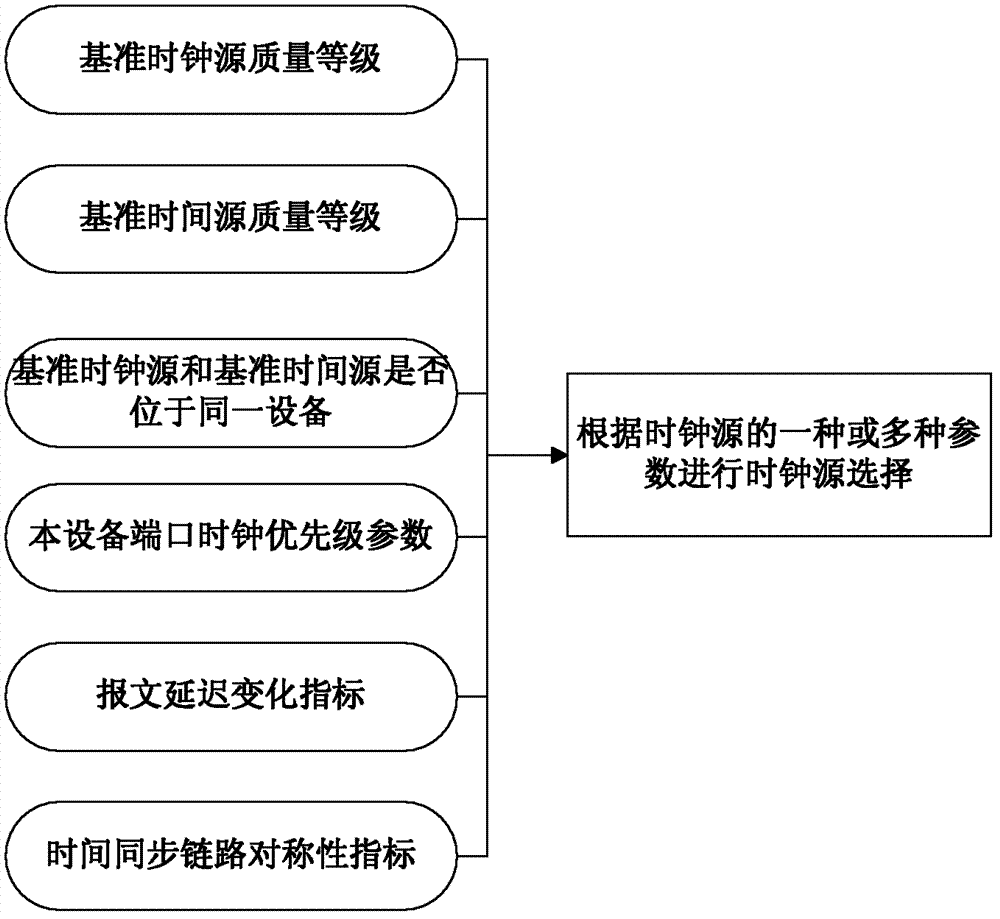
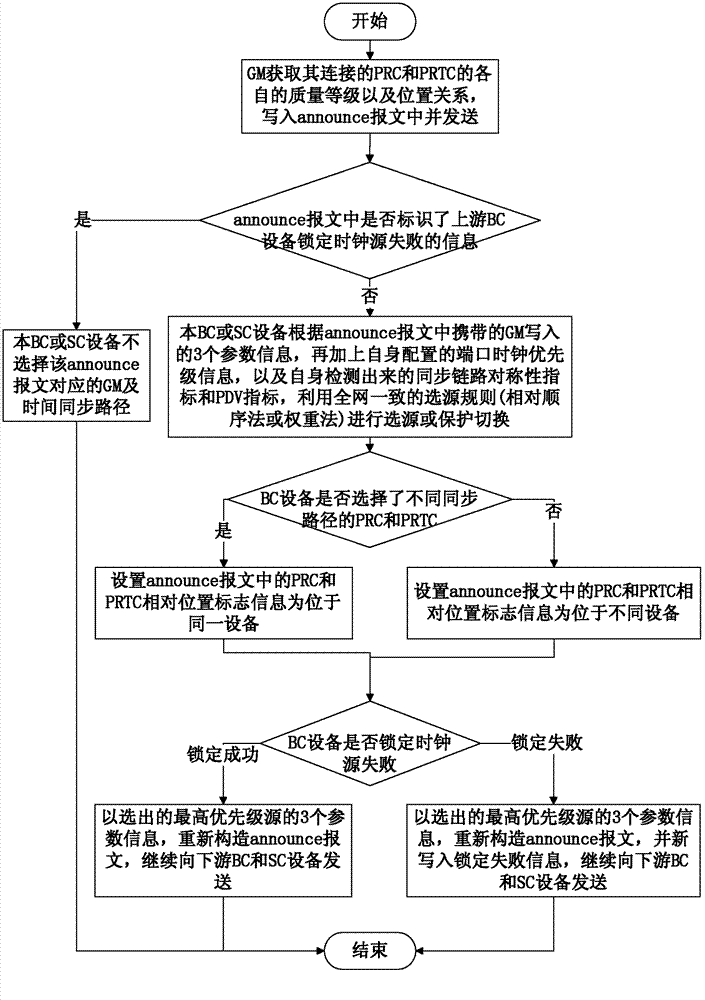
The invention discloses a method and a device for selecting time synchronization sources. The method includes: allowing a boundary clock device or a slave clock device to select sources according to any parameters of clock sources, such as primary reference clock source quality level, primary reference time source quality level, co-existence or no co-existence of primary reference clock sources and primary reference time sources in a device, device port clock priority parameter, message delay change indicator, and time synchronization link symmetry indicator. The method and device are applicable to time-synchronized source selection schemes, multiple relevant parameters can be fully utilized to select sources, and accordingly source selection reasonability is improved. A protection mechanism is also achieved for a time synchronization network and used for protecting switching, certain special faults of the time synchronization network can be timely sensed and treated, interaction between a clock synchronization network and the time synchronization network is supported, flexibly in switching the time synchronization network is improved and time synchronization performance is protected from influence.
Owner:ZTE CORP
Fast Byzantine Paxos
InactiveUS20100017495A1Avoid excessive delayCorrect behaviorMultiple digital computer combinationsTransmissionClient-sideComputing systems
A distributed computing system can operate in the face of malicious failures on the part of some of its constituent devices, and provide a minimum of message delays between receiving a client request and providing a response, when each device within the system verifies the sender of any message it receives, and the propriety of the message.
Owner:MICROSOFT TECH LICENSING LLC
Time-triggered based airborne optical network simulation system
ActiveCN105245301AHigh simulationObserve performanceTransmission monitoringNetwork generationComputer module
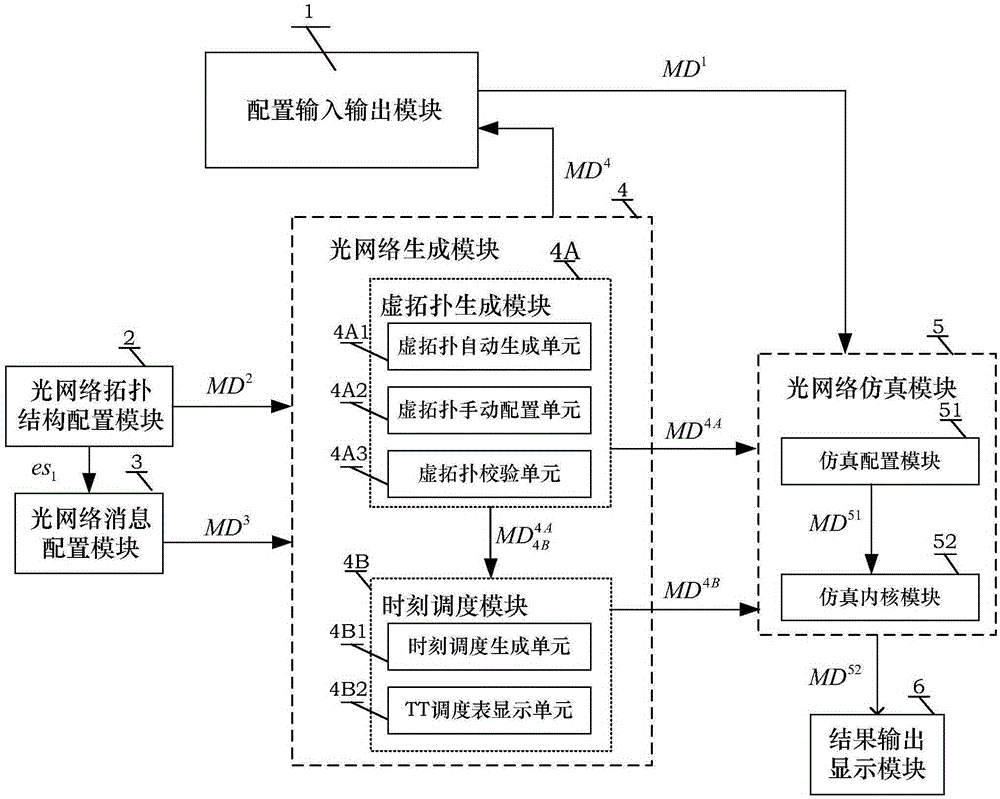
The invention discloses a time-triggered based airborne optical network simulation system. The system comprises a configuration input and output module (1), an optical network topology configuration module (2), an optical network message configuration module (3), an optical network generation module (4), an optical network simulation module (5) and a result output display module (6). By simulating the generation of communication tasks and a running process in the airborne optical network, the airborne optical network simulation system provided by the invention solves the technical problem in the existing airborne optical network that time certainty is not provided for messages transmitted in real time in a transmission mechanism. The airborne optical network simulation system provided by the invention can add a Time-Triggered in the airborne optical network, and can make the airborne optical network have certain timeliness and can more efficiently use network bandwidth resource, so as to realize a technical effect that the airborne optical network has time certainty in transmitting message delay.
Owner:北京国科天迅科技股份有限公司
Packet scheduling based on message length
InactiveUSH2103H1Reduce transmission delayReduce delaysError preventionTransmission systemsMessage lengthFirst principle
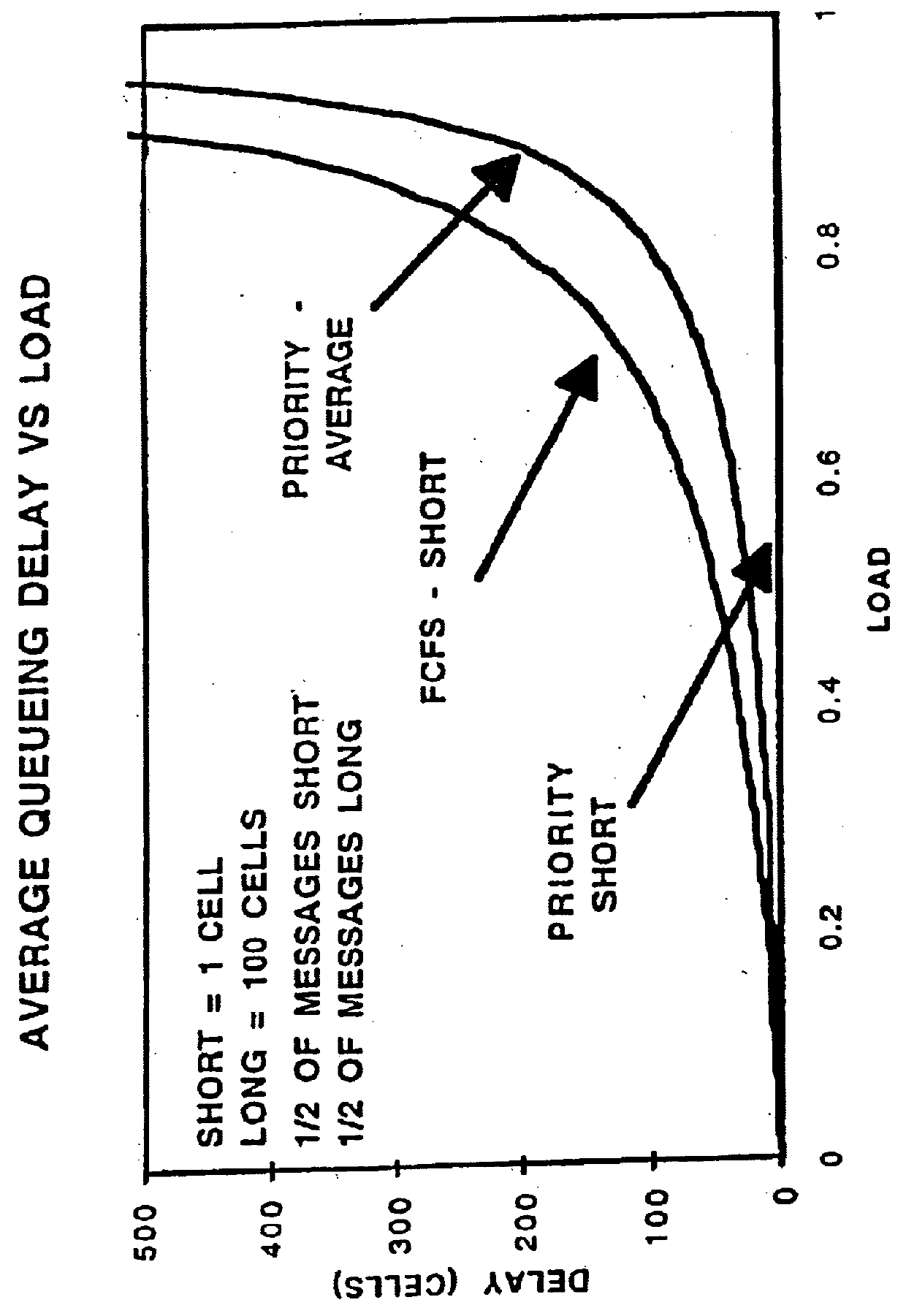
A system using two algorithms for scheduling packets in a multi-hop network. The objective of the algorithms is to reduce end-to-end message (not packet) transmission delays. Both algorithms schedule packet transmissions based on the length of the original message to which the package belongs. The first algorithm is preemptive and is based on the shortest-message-first principle and the second is based on the shortest-remaining-transmit-time principle. We develop simulation models for analyzing the algorithms. The simulations show that when message sizes vary widely, these algorithms can significantly reduce average end-to-end message delays compared to the First-Come-First-Serve scheduling.
Owner:AIR FORCE UNITED STATES
Conflict fast consensus
A conflict tolerant message delay reducing consensus algorithm is presented for operating a distributed computing system. The devices of the distributed computing system can directly receive client requests, and can execute the requests and respond directly to the clients, saving message delays. If there is a conflict, the ultimately selected request can be the request submitted by the client with the highest client identifier. A device can change its vote, and execute a different request, if it is made by a client having a more dominant client identifier. All but one of the clients can also be a device implementing the system. A device that has executed a requested function may no longer submit a request in the same step. Consequently, a request is executed by the system when all devices have executed the request. If one or more devices fails, any fault tolerant consensus algorithm can be used.
Owner:MICROSOFT TECH LICENSING LLC
Simplified Paxos
ActiveUS20050198106A1To overcome the large delayFast learningMultiple digital computer combinationsSpecial data processing applicationsClient-sideComputer science
A simplified fault tolerant algorithm is presented for operating a distributed computing system in a fault tolerant manner. A system comprising three computing devices need only have two devices agree to perform any proposed function. Thus, when soliciting a vote for a proposed function, a leader device can also send its vote for the proposed function. This allows any recipient device to complete the quorum with its own vote. Consequently, any recipient device can, without any further messages, determine whether to execute the proposed function. Furthermore, if the device executes the proposed function, it can transmit the results directly to the client that requested the function, saving a message delay. If the quorum of devices used to select and execute proposed functions is itself selected by a quorum, then one of the devices of the system can be an inexpensive device having limited computational ability or storage capacity.
Owner:MICROSOFT TECH LICENSING LLC
Routing control method based on big-scale WSN (wireless sensor network) emergency monitoring
InactiveCN102665171AAvoid lossAvoid excessive wear and tearNetwork topologiesBroadcast service distributionWireless mesh networkMulti hop relay
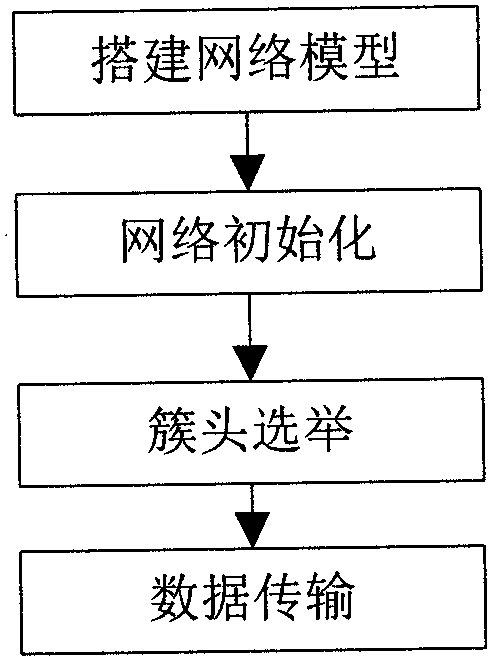
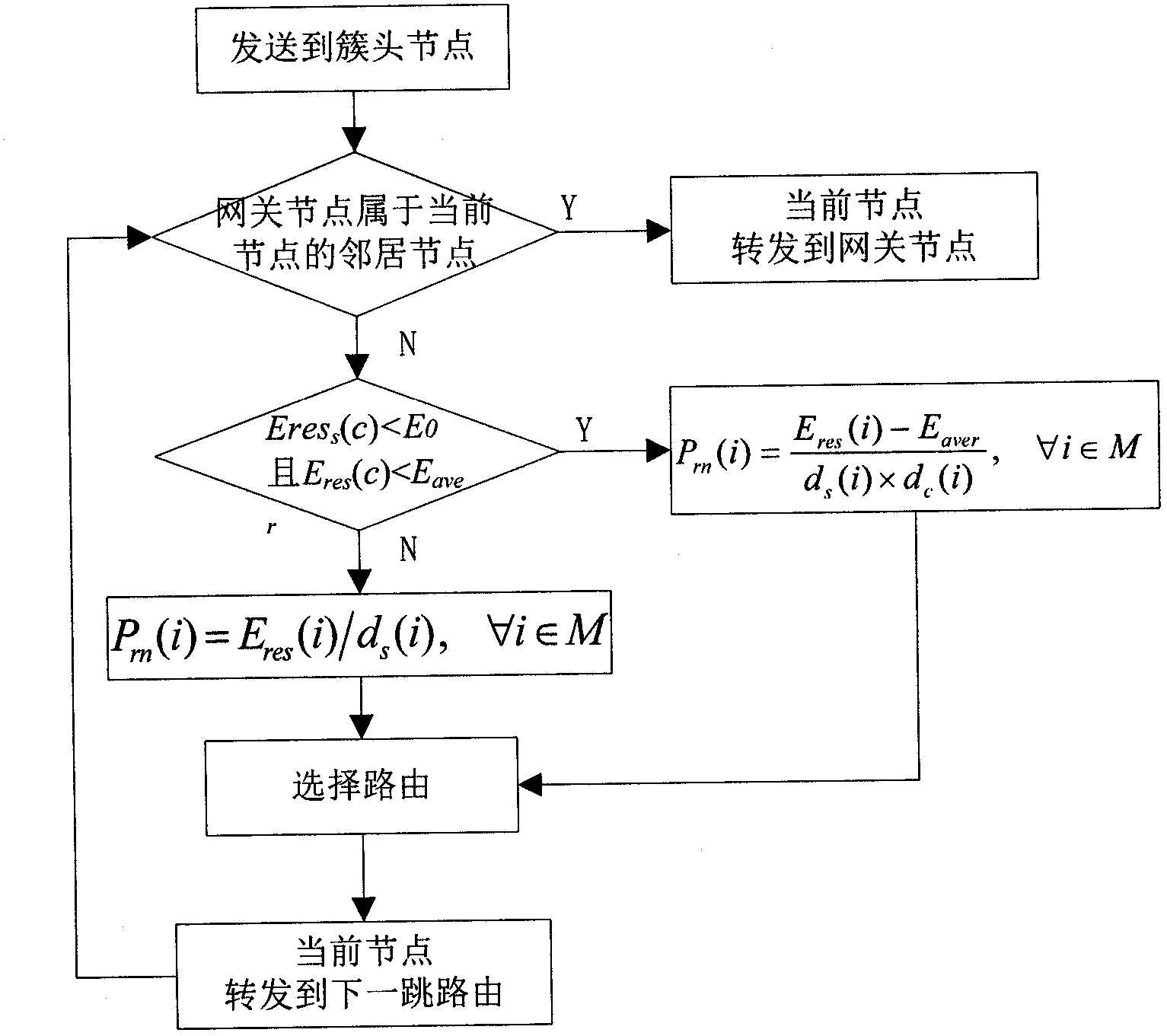
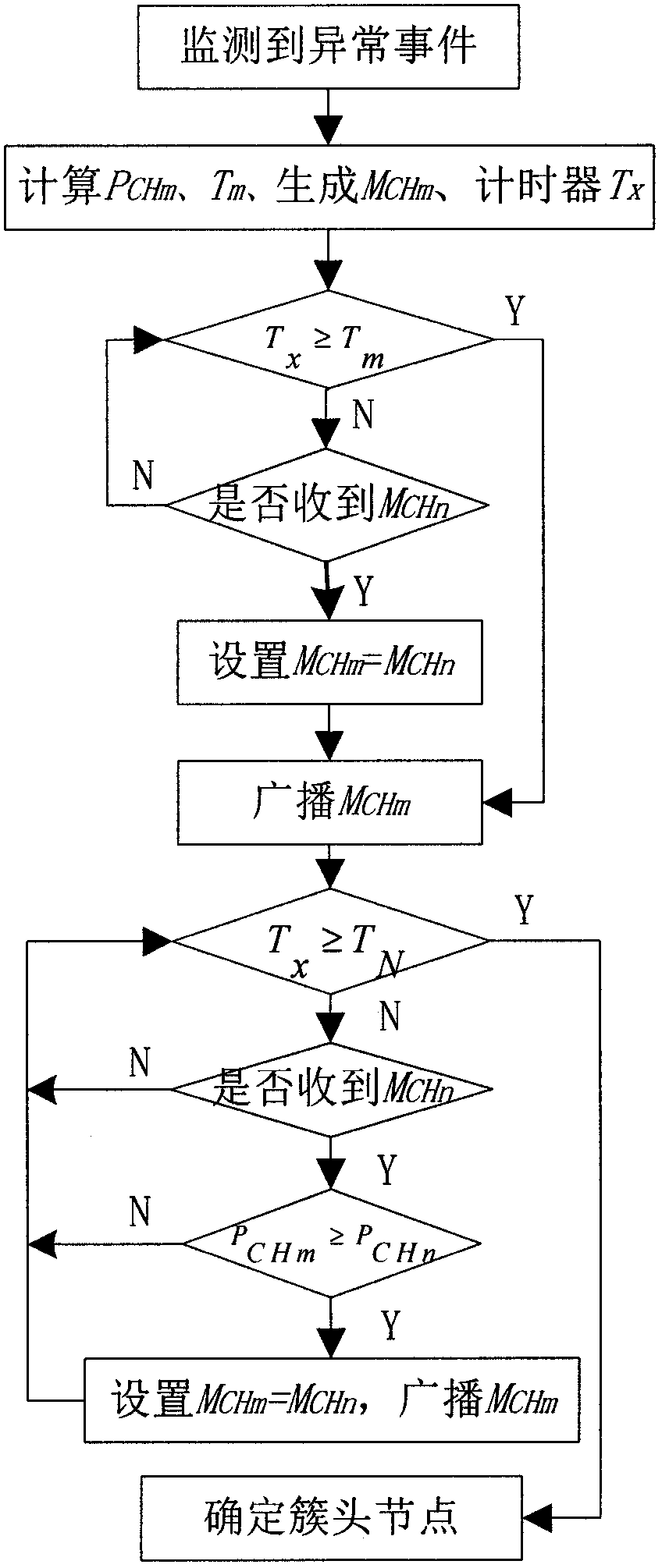
The invention discloses a routing control method based on big-scale WSN (wireless sensor network) emergency monitoring, which comprises four steps of building a network model, initializing a network, electing a cluster and transmitting data, wherein in the data transmission process, a cluster node selects a trunking mode of one hop or multiple hops to send effective monitoring data back to a gateway node according to the fact whether the gateway node is in a self 'neighbor node log sheet'; and in the trunking mode of multiple hops, the current node selects different algorithms to find a next-hop route node according to the self residual energy situation. The routing control method has the outstanding effects that the cluster node and the gateway node are communicated in the trunking mode of one hop or multiple hops to avoid excessive energy loss caused by long-distance transmission. According to the mechanisms of a cluster node and relay node election method, self-adaption power regulation, message delay forwarding control and the like, network energy consumption is saved and balanced so as to delay the time of the first dead node and improve the network performance.
Owner:CHONGQING UNIV
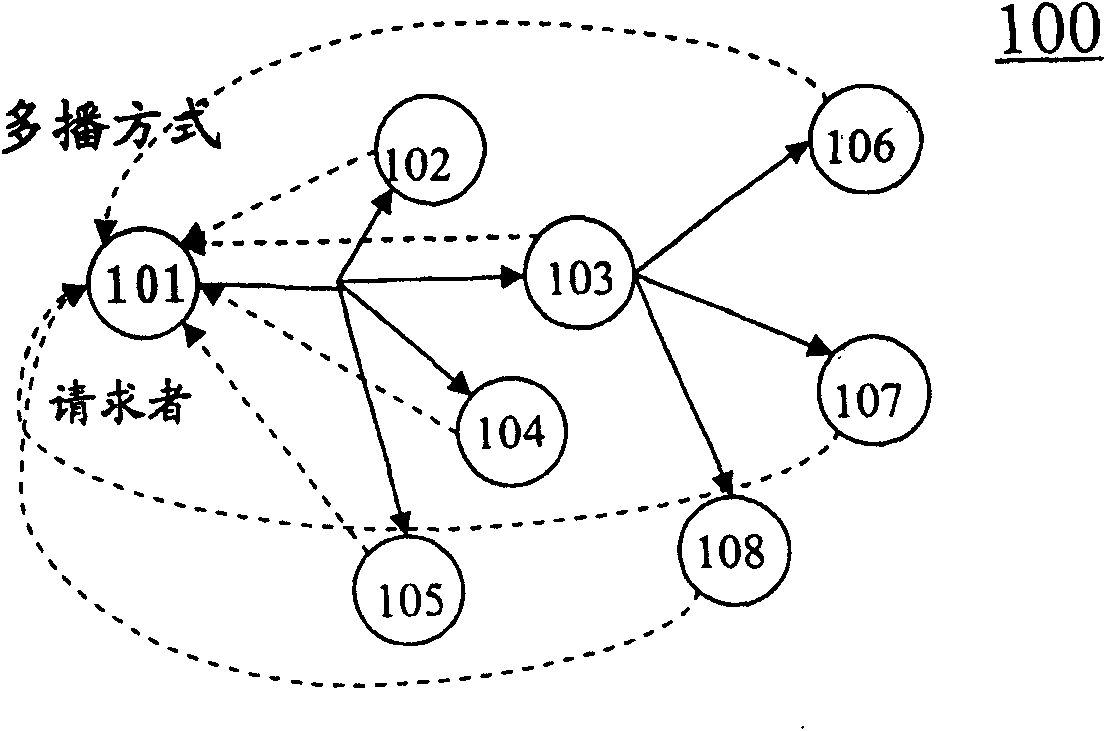
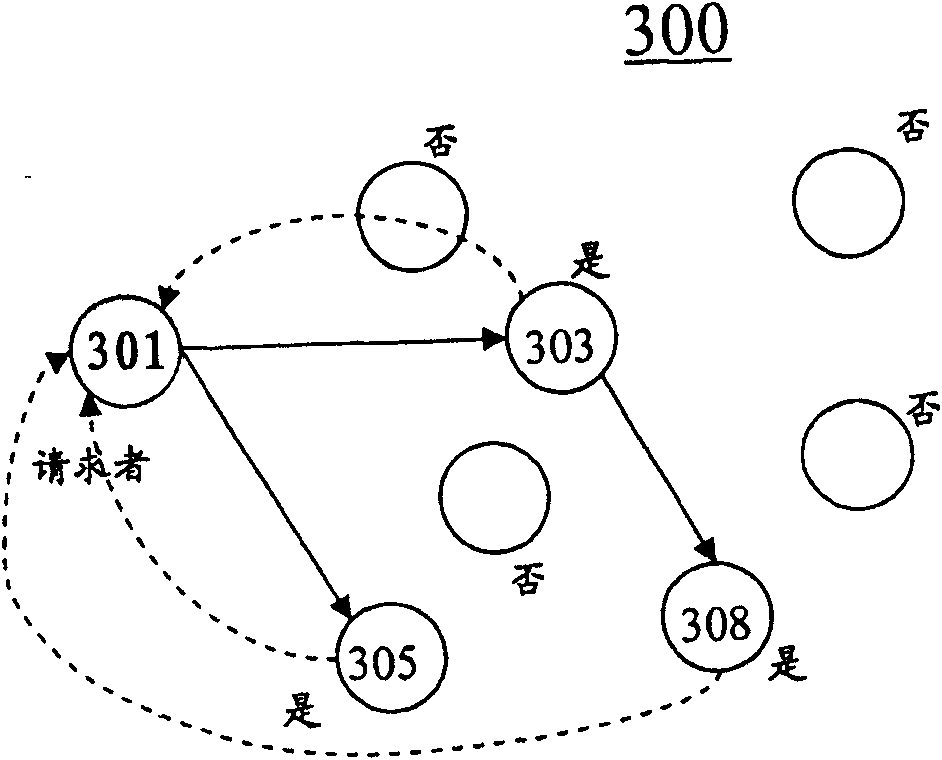
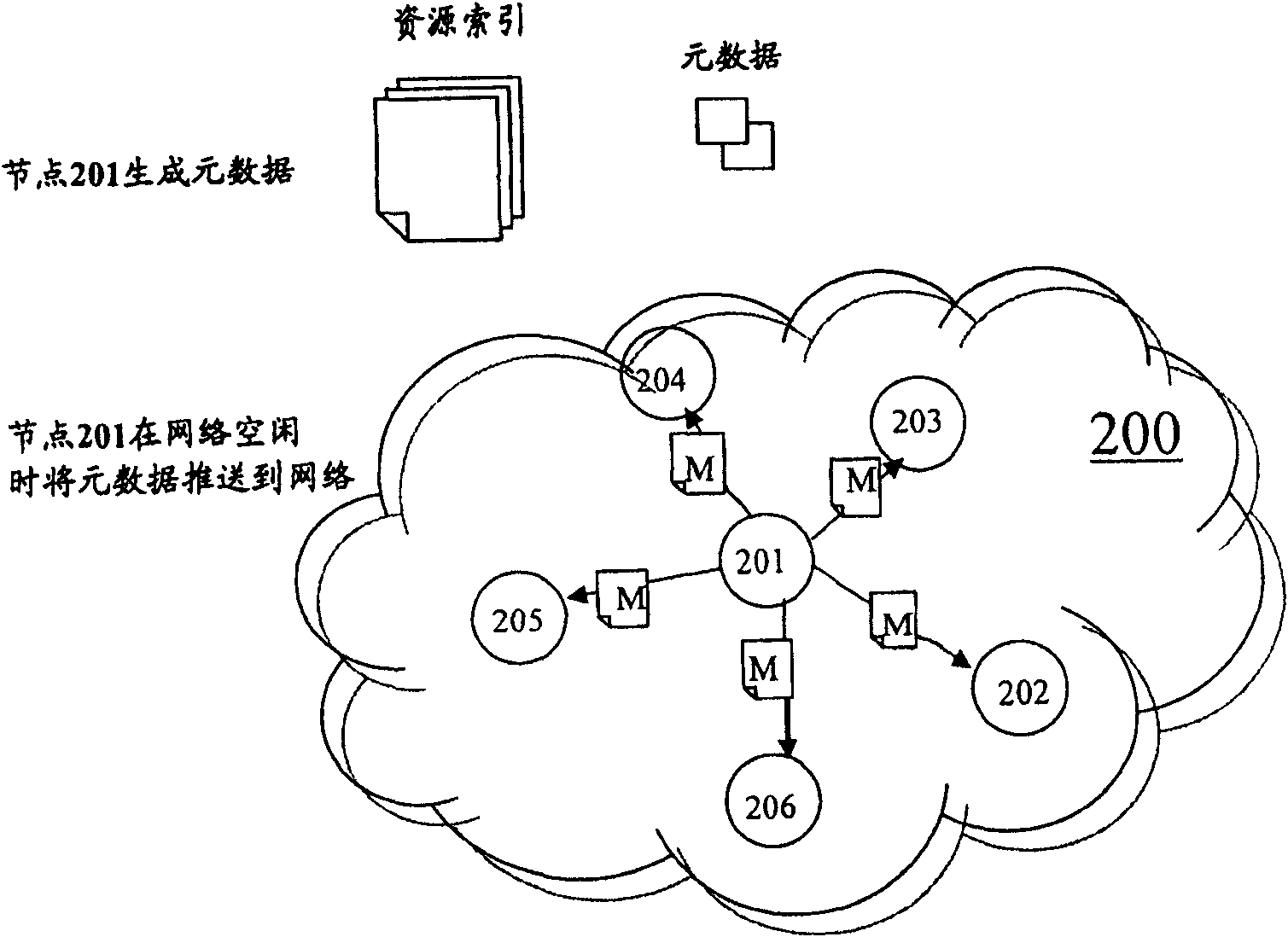
Method and equipment for searching resource in peer-to-peer network
The invention discloses a method for searching resource in P2P network, which comprises the following steps: receiving metadata from other peer-to-peer nodes in advance, wherein the metadata of each node comprises shared file information in the peer-to-peer node; responding to a requirement for requesting specific resource from other peer-to-peer nodes; judging which peer-to-peer node claims to have the specific resource according to the received metadata; and transmitting the request to the peer-to-peer node which claims to have the specific resource. By using the method, the traffic in the P2P network can be remarkably reduced, and the phenomenon of message delay and message explosion in the network traffic peaks can be reduced or avoided.
Owner:IBM CORP
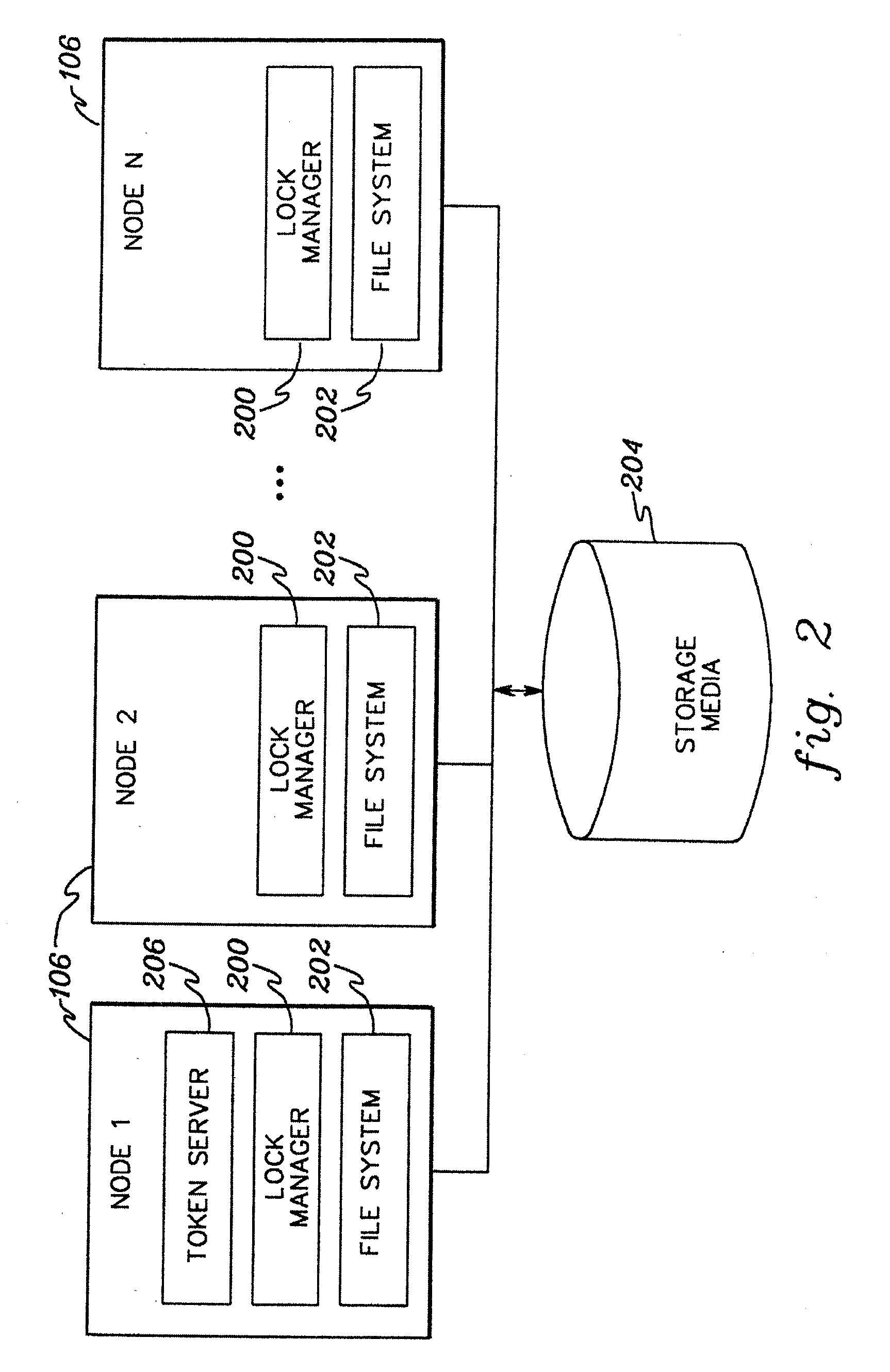
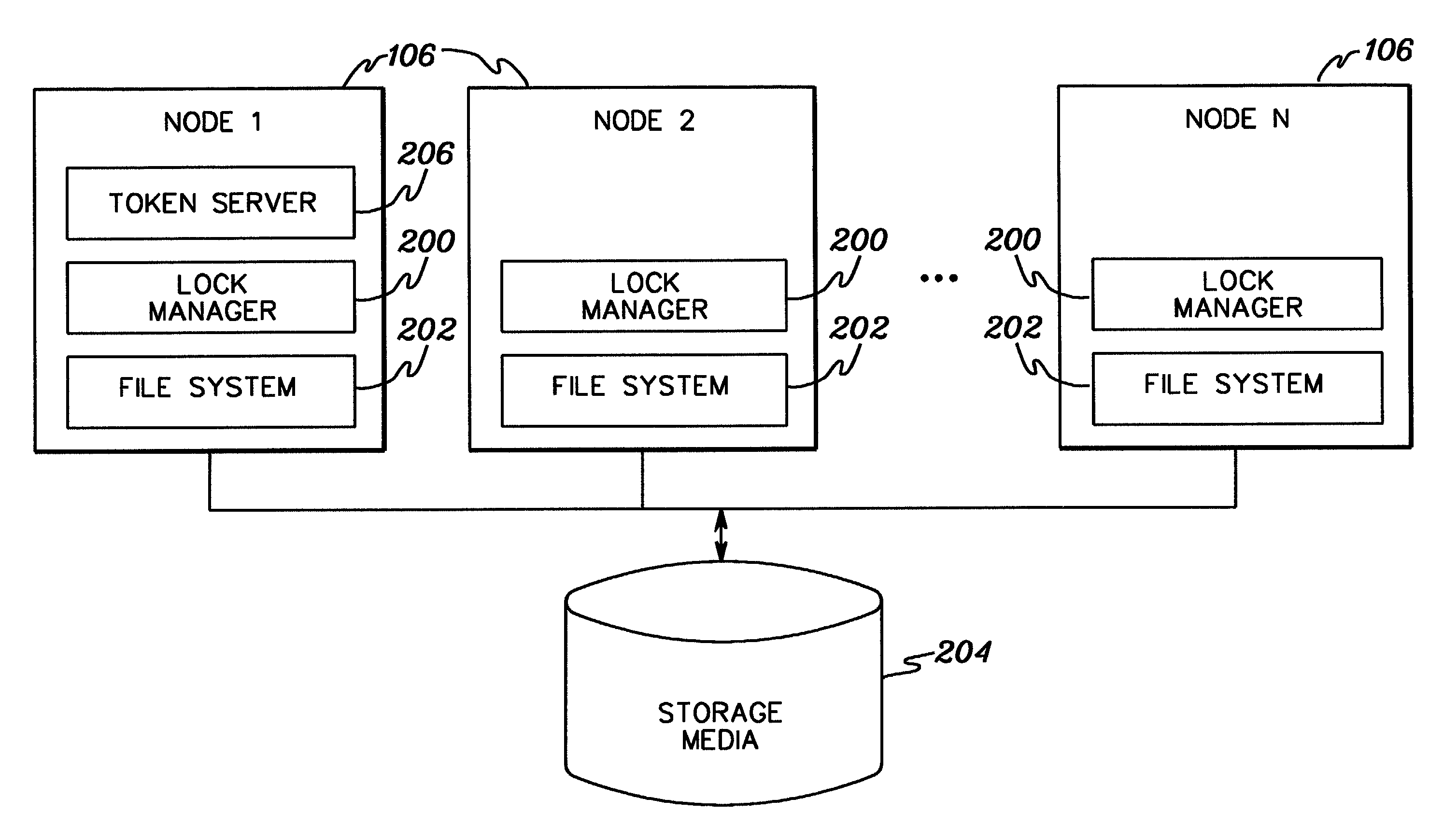
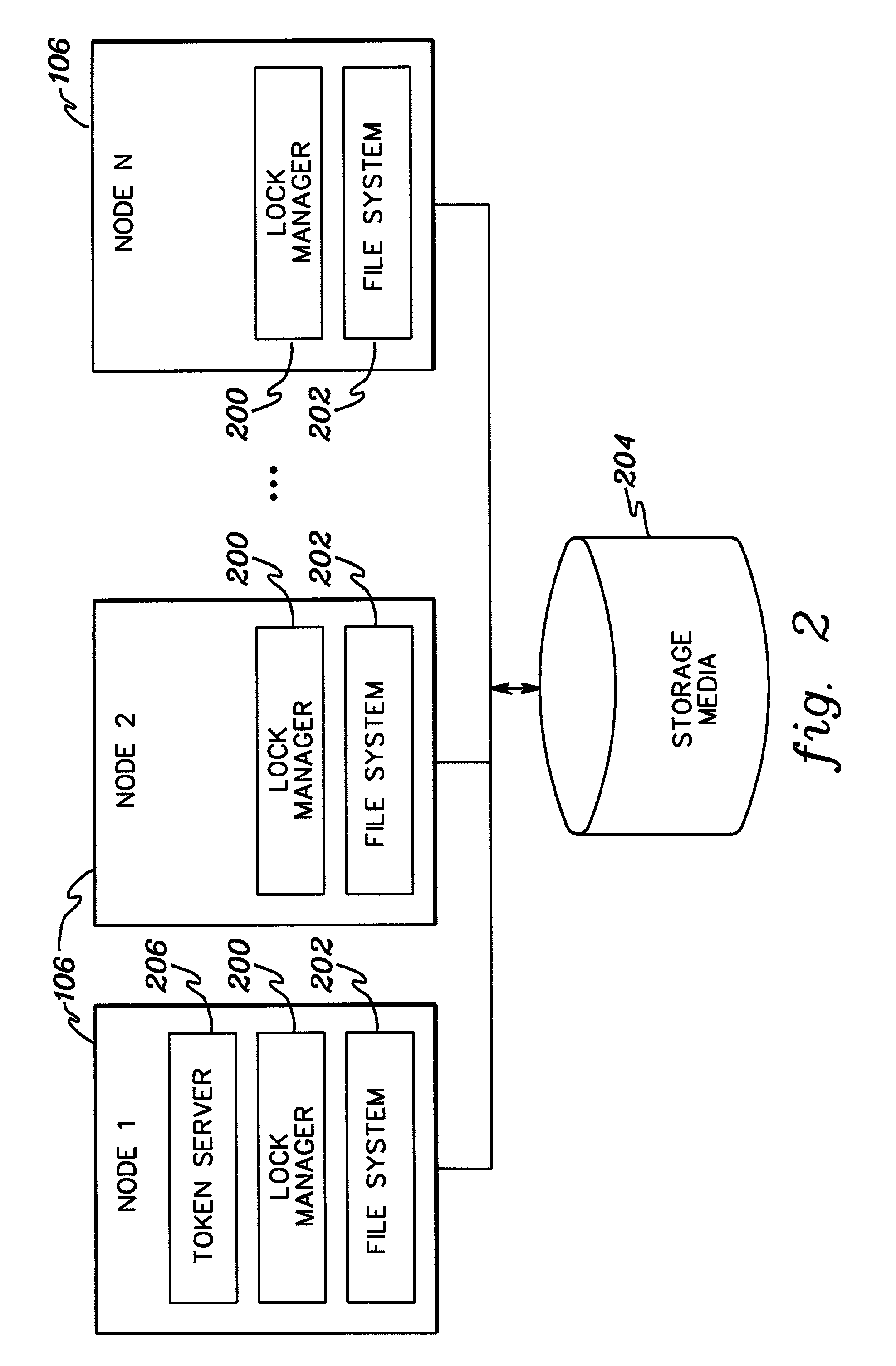
Distributed locking protocol with asynchronous token prefetch and relinquish
InactiveUS20080091680A1Message being delayedReduce overheadDigital data processing detailsMultiple digital computer combinationsComputer scienceShared resource
Asynchronous messages are used to prefetch and / or relinquish tokens used in providing locking of shared resources. A message is sent to prefetch one or more tokens, and prior to receiving a reply for the message, another message (e.g., an acquire) is sent for at least one of those tokens. Similarly, a message is sent indicating a voluntary relinquish of one or more tokens and without having acknowledgment that the relinquish request was processed, a further message (e.g., an acquire) is sent for at least one of the tokens. Multiple tokens may be acquired and / or relinquished in a single message to the token server. This reduces message delays and overall message traffic.
Owner:IBM CORP
Secure time communication system
InactiveUS20190342101A1Synchronising transmission/receiving encryption devicesUser identity/authority verificationCommunications systemMessage delay
Methods and apparatus for a Secure Time Communication System (10) are disclosed. One embodiment of the invention provides secure and non-interactive communication of clock information over an unsecured communications channel. This communication provides perfect forward secrecy, while detecting and blocking message spoofing, message replay, denial of service and cryptographic performance attacks. This mechanism also bounds the effect of message delay manipulation. The mechanism consists of two components, a filtered time encryptor (16) and a filtered time decryptor (28). The filtered time encryptor (16) produces a message in two parts; a time token followed by an encrypted message body. The time token is used as a filter to detect most attacks and to determine the message key.
Owner:BLUE ARMOR TECH LLC
Apparatus, system, and method for automatically freeing a server resource locked awaiting a failed acknowledgement from a client
An apparatus, system, and method are provided for automatically freeing locked server resources using a timeout value closely related to actual real-time message delays plus a delta value that can be adjusted at a plurality of levels. The levels include default, server, connection, and transaction. The apparatus includes a timer, a communication module, a computation module, and a lock handler. The timer determines a timeout value for communications from a client to a server. The communication module sends an output message to the client and locks a server resource in anticipation of an acknowledgement (ACK) message from the client. The computation module, which calculates an ACK timer, includes a difference between a send time and a current time. If no ACK message has been received from the client and the ACK timer exceeds the timeout value, the lock handler may free the locked server resource.
Owner:IBM CORP
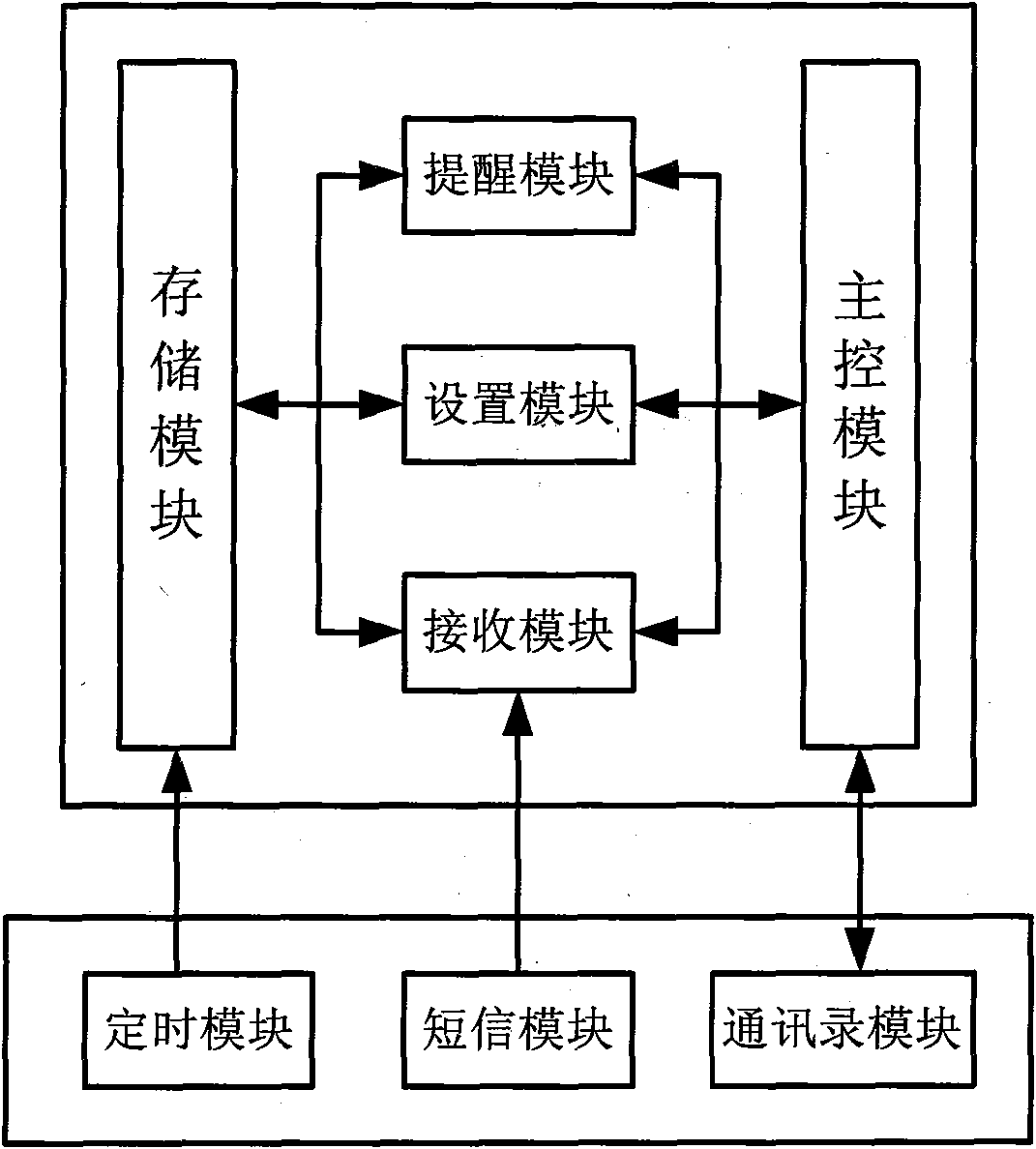
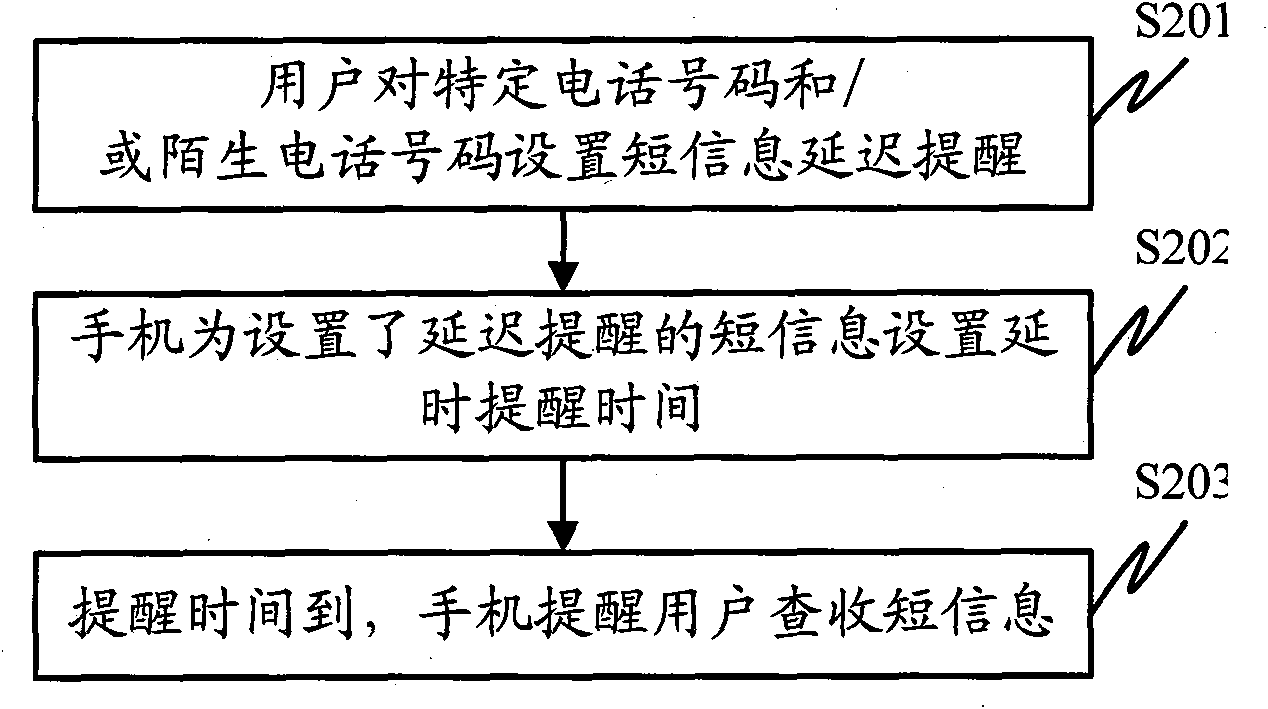
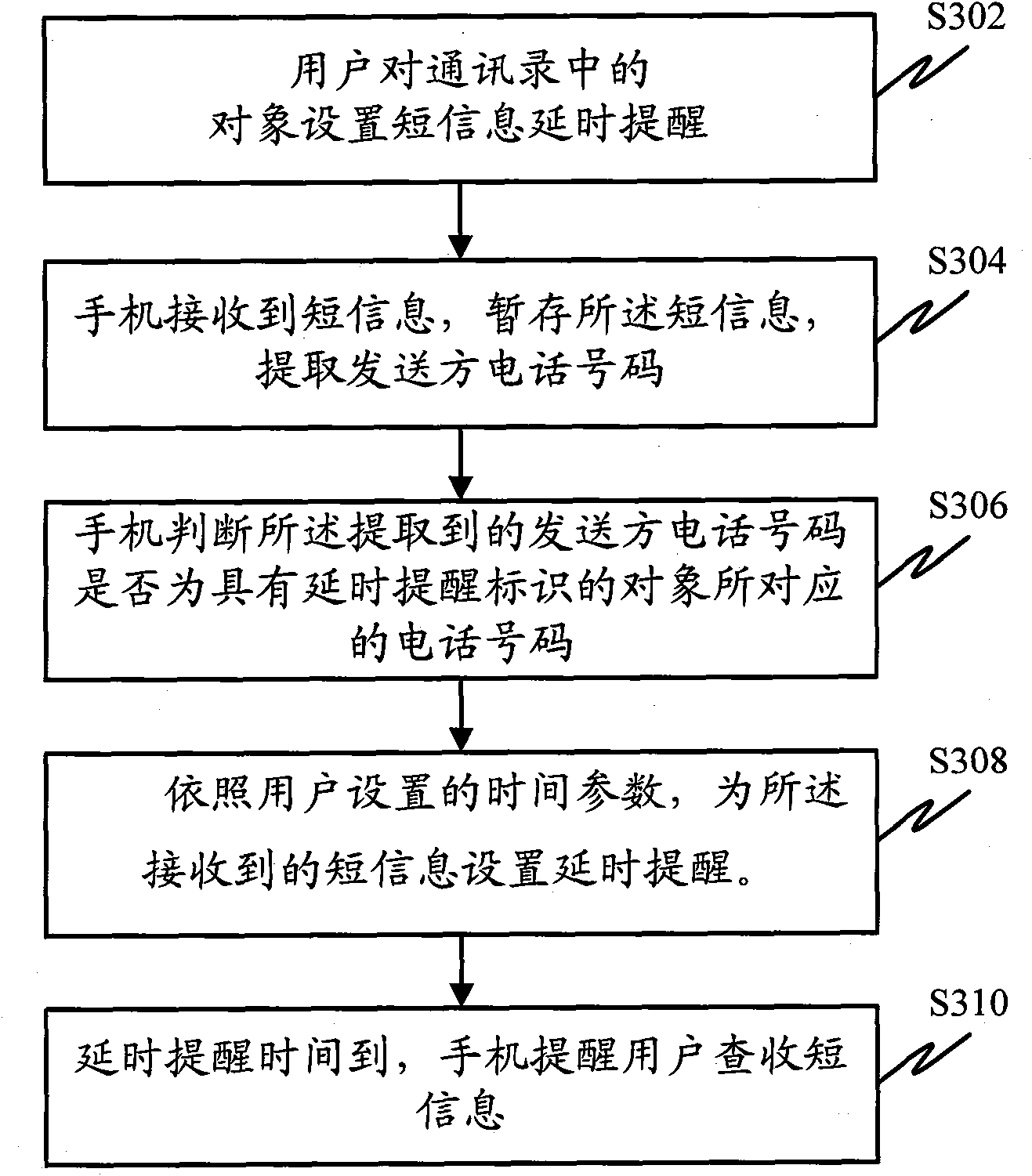
Short message delay reminding terminal and method
InactiveCN101841596AAvoid disturbanceAffect timely reviewSubstation equipmentTime managementMemory module
The invention discloses a short message delay reminding terminal and a method, which belong to the communication field. The terminal comprises a main control module, a memory module, a setup module and a reminding module, wherein the main control module is used for receiving operation order of the user; the memory module is used for storing the short message received by the cell phone and for managing the delay reminding time; the setup module is used for setting the delay reminding of the short message; and the reminding module is used for reminding the user to check and accept the short message after the delay time is ended. The method comprises the following steps that: user can set up the short message delay reminding for particular phone number and / or strange phone number; a delay reminding time is set up on the cell phone for the short message with the delay reminding; and when the reminding time is up, the cell phone reminds the user to check and accept the short message. By utilizing the short message delay reminding terminal, not only the disturbing of the strange short message can be avoided within a given period of time, but also the useful short message can be avoided to miss.
Owner:ZTE CORP
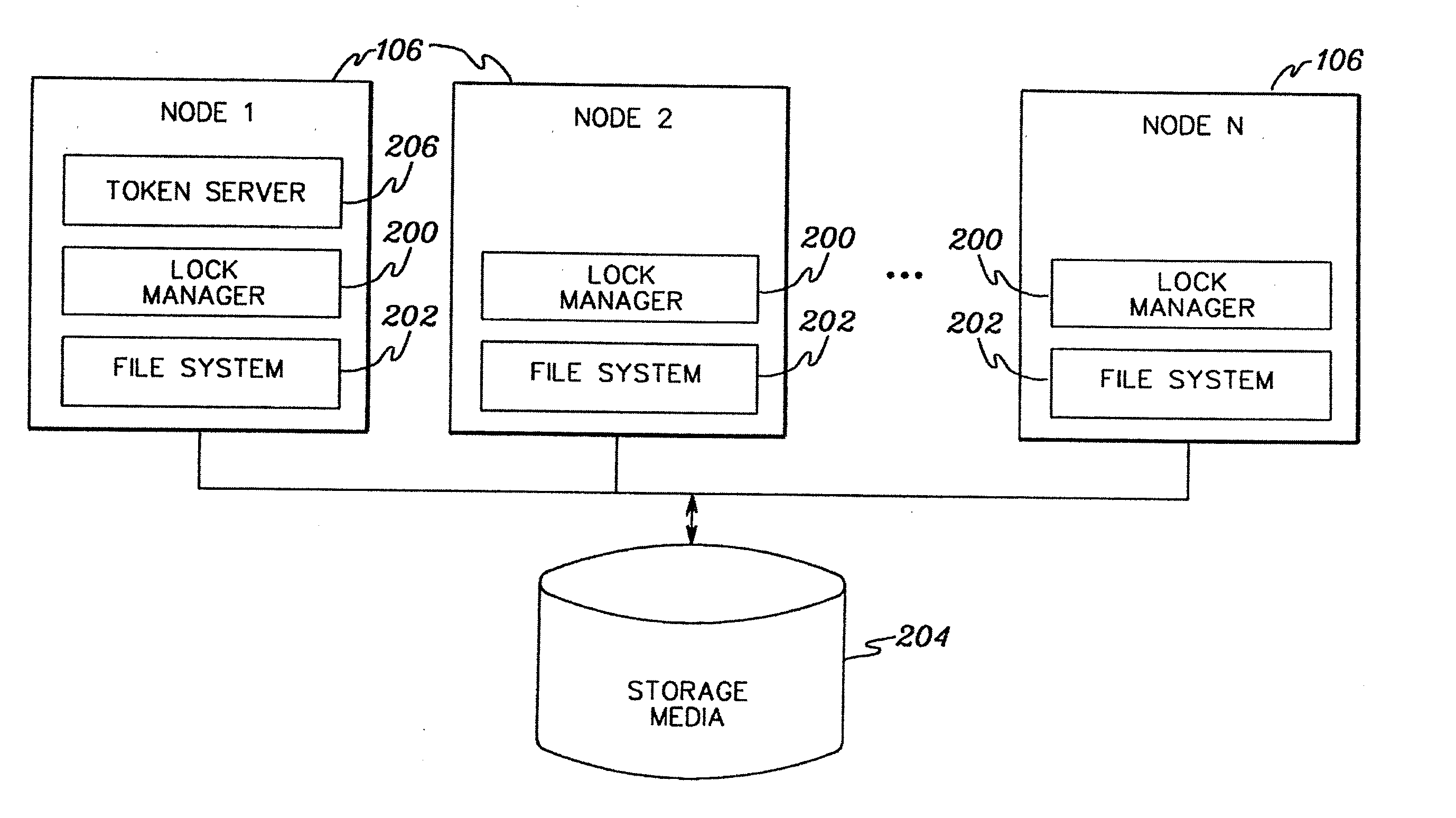
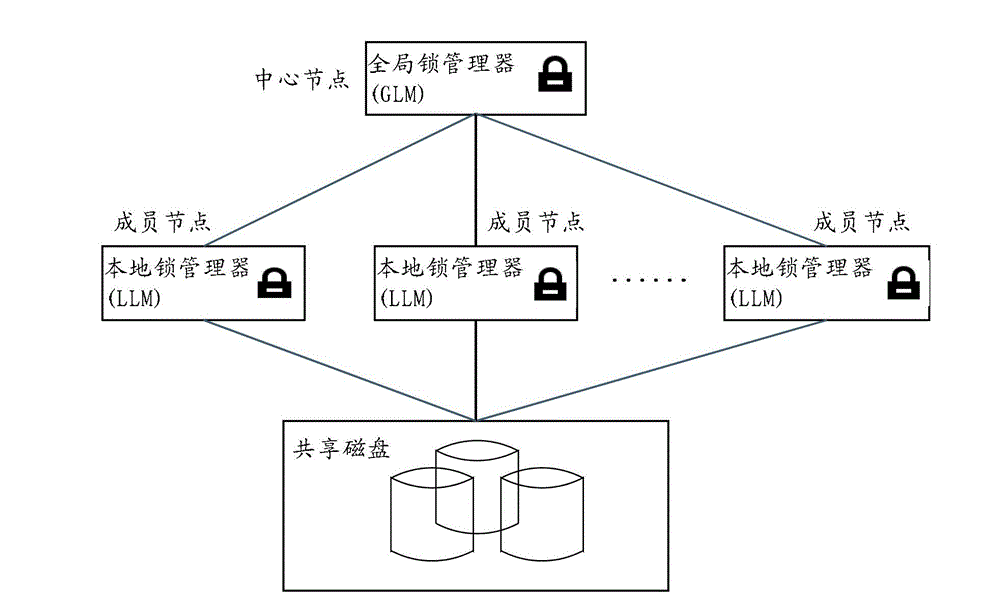
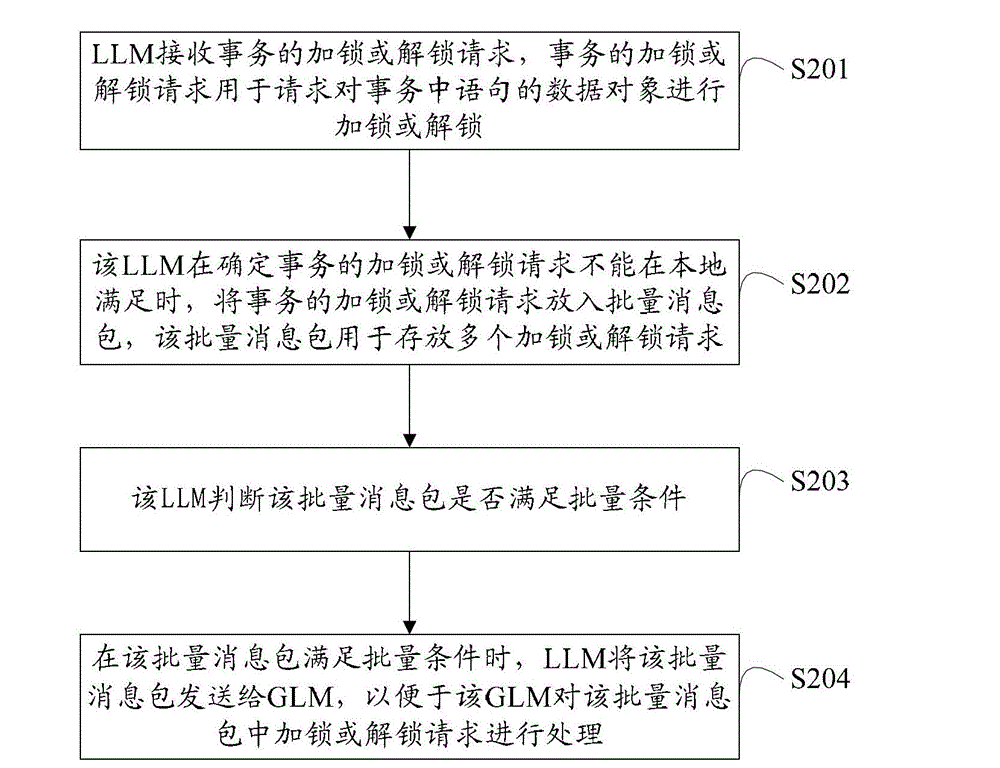
Business locking and unlocking method and device
ActiveCN103064898AReduce in quantityLower latencySpecial data processing applicationsLock managerDatabase clustering
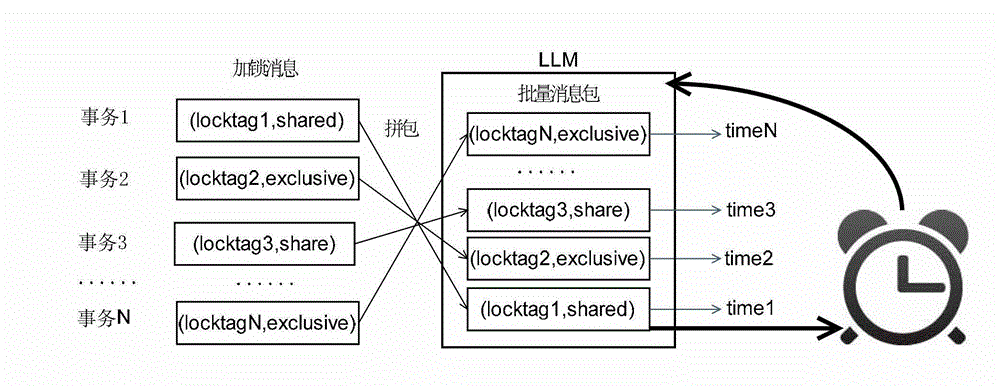
The invention provides a business locking and unlocking method and device which are applied to the technical field of data clusters. The business locking and unlocking method includes that: a local lock manager (LLM) receives a locking or unlocking request of a business; the LLM places the locking or unlocking request of the business into a batch message packet when determining that the locking or unlocking request of the business cannot be met locally, wherein the batch message packet is used for storing a plurality of locking or unlocking requests; and the LLM transmits the batch message packet to a general lock manger (GLM) when judging that batch messages meet batch conditions, so that the GLM can process the locking or unlocking request in the batch message packet conveniently. By adopting the business locking and unlocking method and device, the quantity of the locking or unlocking requests transmitted to the GLM by the LLM in a short time can be reduced, pressure of a channel between the LLM and the GLM is reduced, message delay is reduced, and linear scalability of the database clusters is improved.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
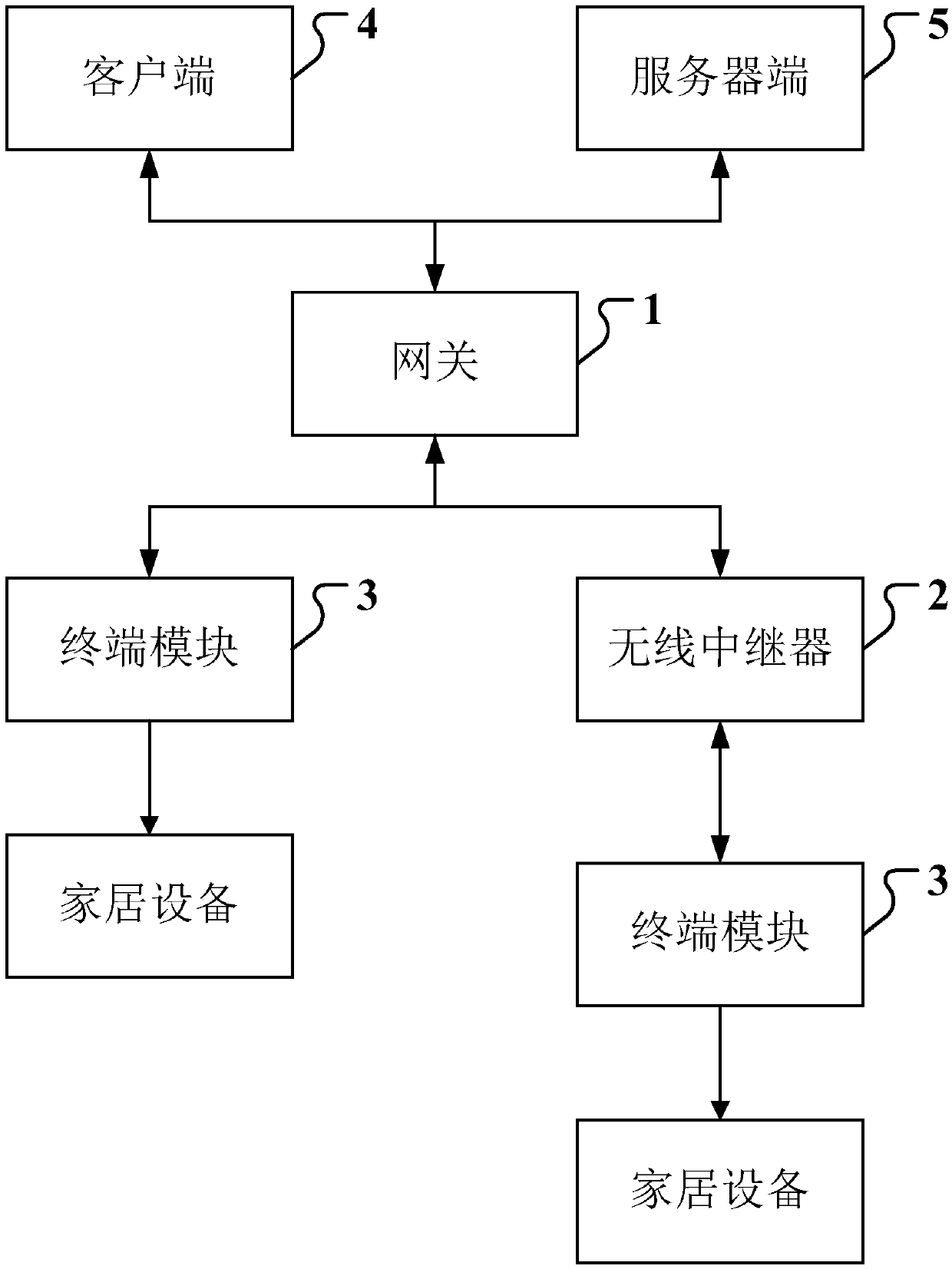
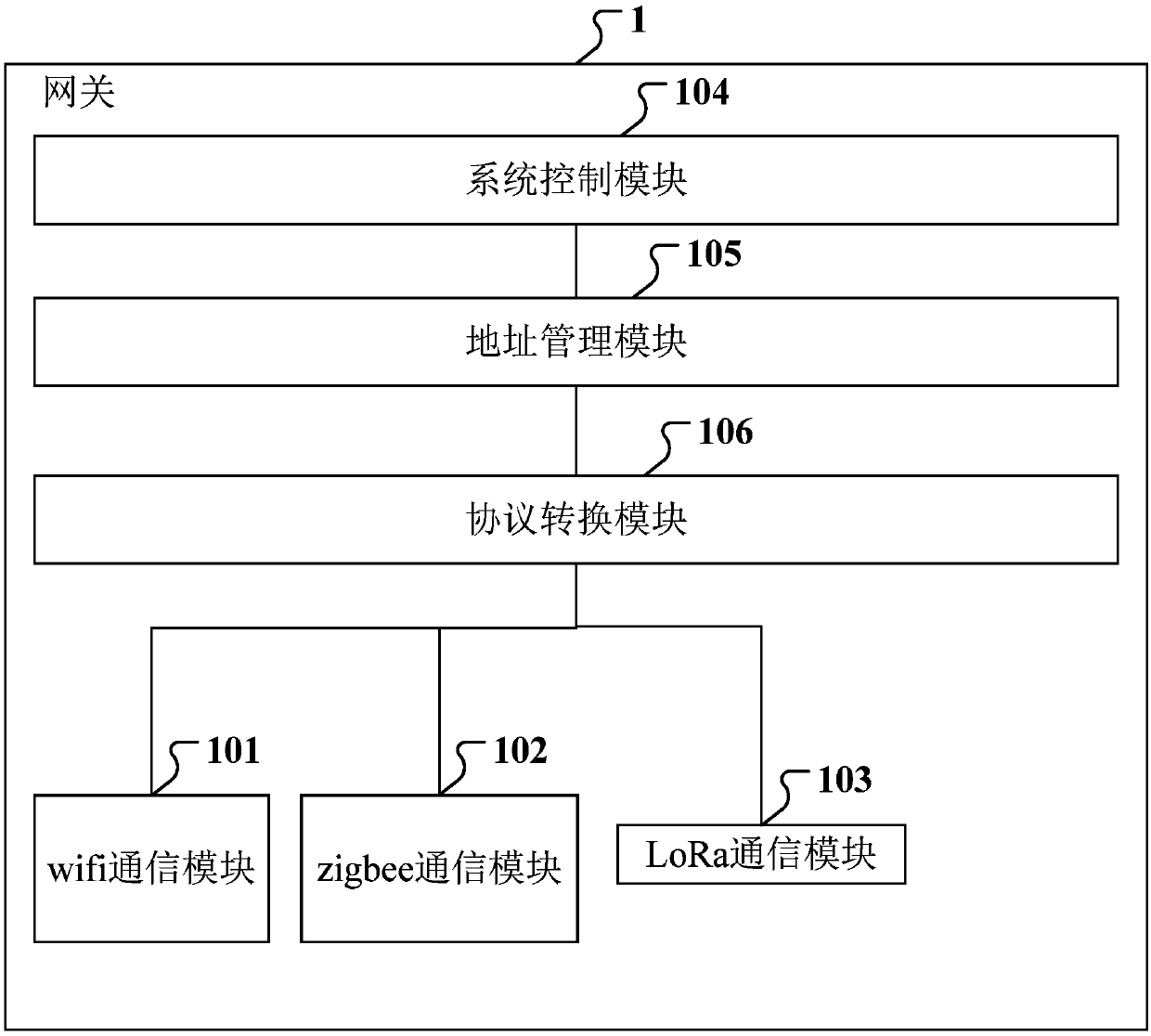
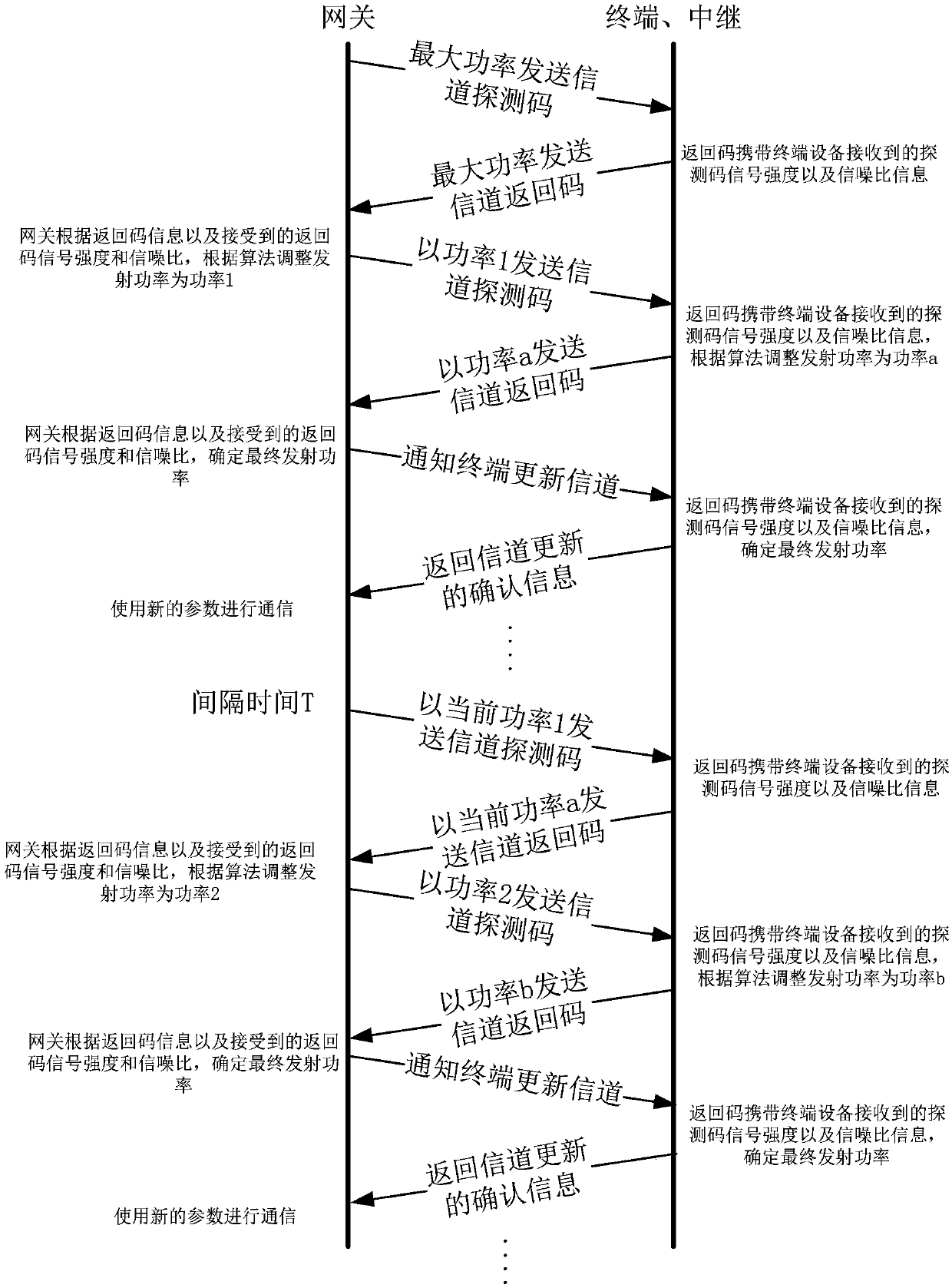
Smart home communication system based on dual-mode communication
ActiveCN108683576AAvoid interferenceReduced Power RequirementsShort range communication serviceHigh level techniquesCommunications systemDual mode
The invention discloses a smart home communication system based on dual-mode communication. A Lora communication module is added in a gateway, and a Lora communication module is also added in a terminal module. Based on the above, the communication modes of the two modes are merged. The communication signal strength of the Lora network is set to the lowest signal strength to meet the communicationstability, so as to avoid interference with the zigbee network system and the physically adjacent lora communication system. Meanwhile, the smart home communication system preferentially uses the zigbee link for communication. When the zigbee link fails, the LoRa link is used for re-delivery to ensure reliable communication. When the gateway broadcasts a message, the message is sent by the LoRa link, and the message delay is short to avoid the zigbee broadcast storm. The system has the beneficial effects that the smart home communication system can be stable and reliable, the device respondsin time, and the requirements of low power consumption of the device can be met.
Owner:天津白泽技术有限公司
Centralized internet of vehicle MAC layer combination and collision predicting and preventing method
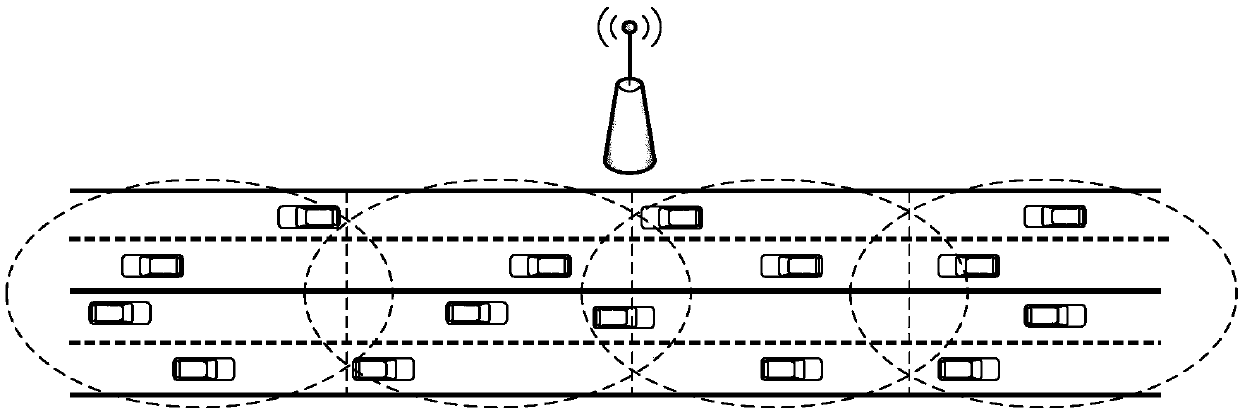
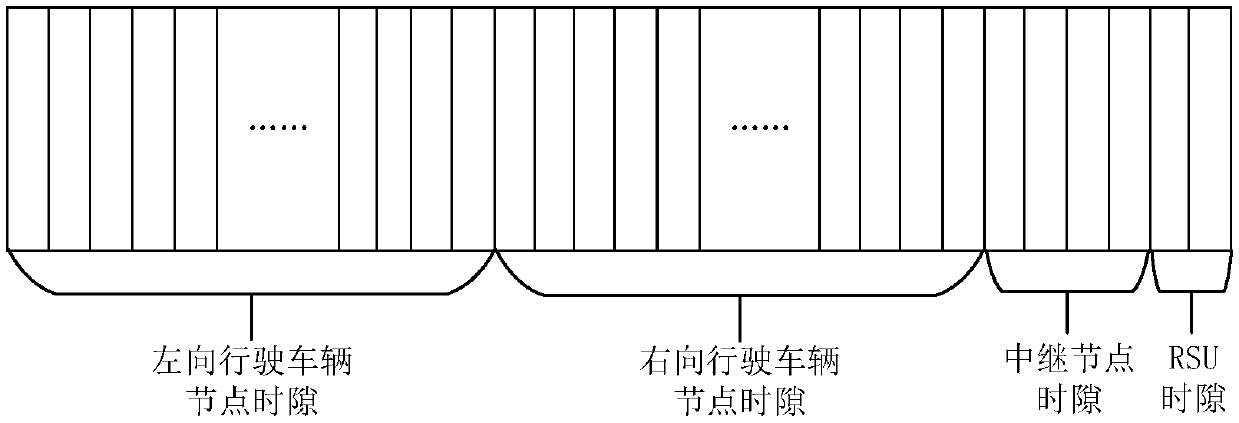
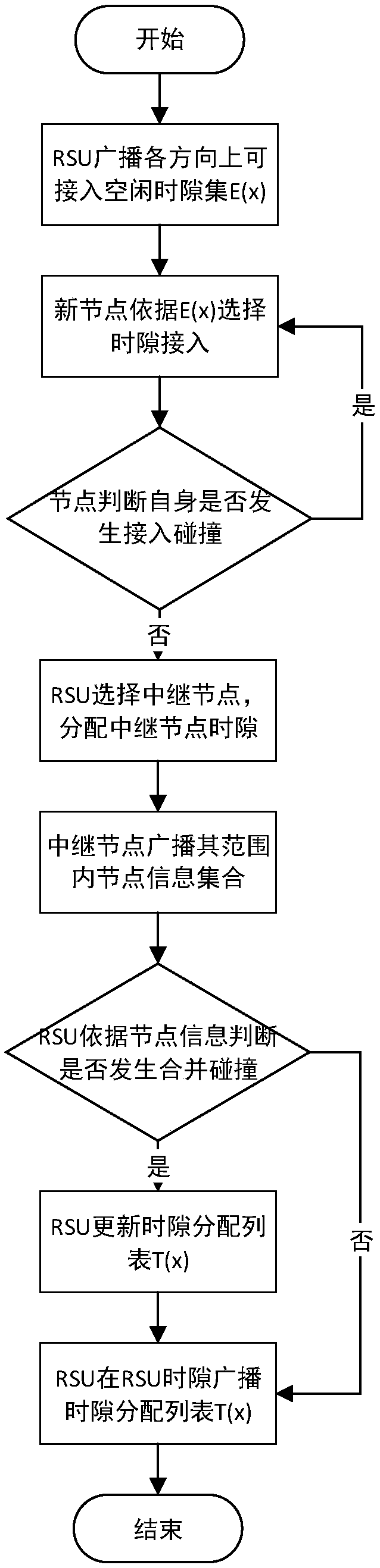
ActiveCN107343024AImprove efficiencyMeet node density statusWireless commuication servicesTransmissionThe InternetSelf-organizing network
The invention discloses a centralized internet of vehicle MAC layer combination and collision predicting and preventing method, belonging to the field of VANET. The method permits reuse of a node timeslot beyond two hops, thereby making the timeslot resource more efficient. First, a road side unit (RSU) can access an idle timeslot set in an RSU timeslot broadcast node in each timeslot period, and a new node selects a timeslot to access randomly according to the timeslot set; then the RSU acquires a position, a speed and timeslot use condition of a vehicle in a range through a relay node, so as to predict the possibility that combination and collision occur; and finally, the RSU adjusts timeslot allocation and broadcasts an adjustment result, so as to prevent combination and collision effectively. In the method, timeslot reuse and assistance of RSU help lower the possibility of combination and collision, so as to shorten message delay of the MAC layer and increase throughput. The method can be used as an MAC layer protocol for sending a broadcast message by a node in the VANET.
Owner:SOUTH CHINA UNIV OF TECH
Method and system for realizing delay message queue
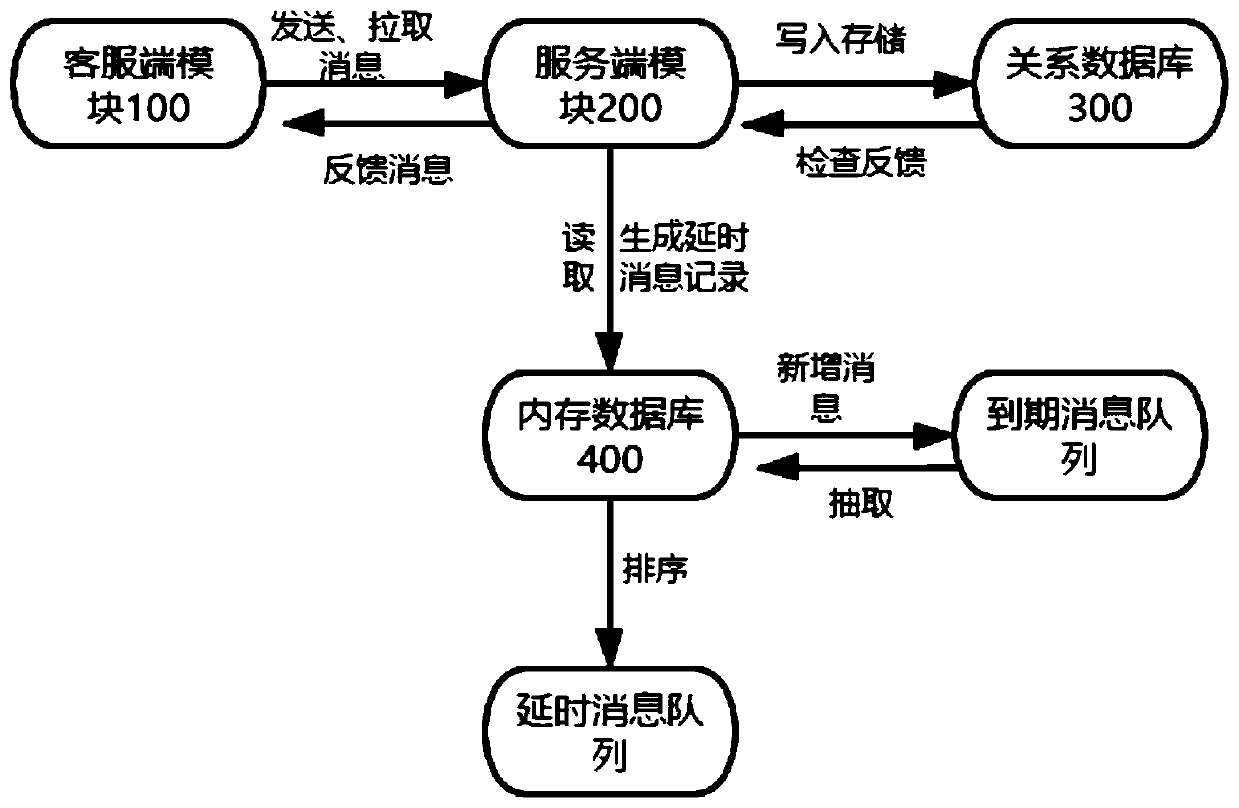
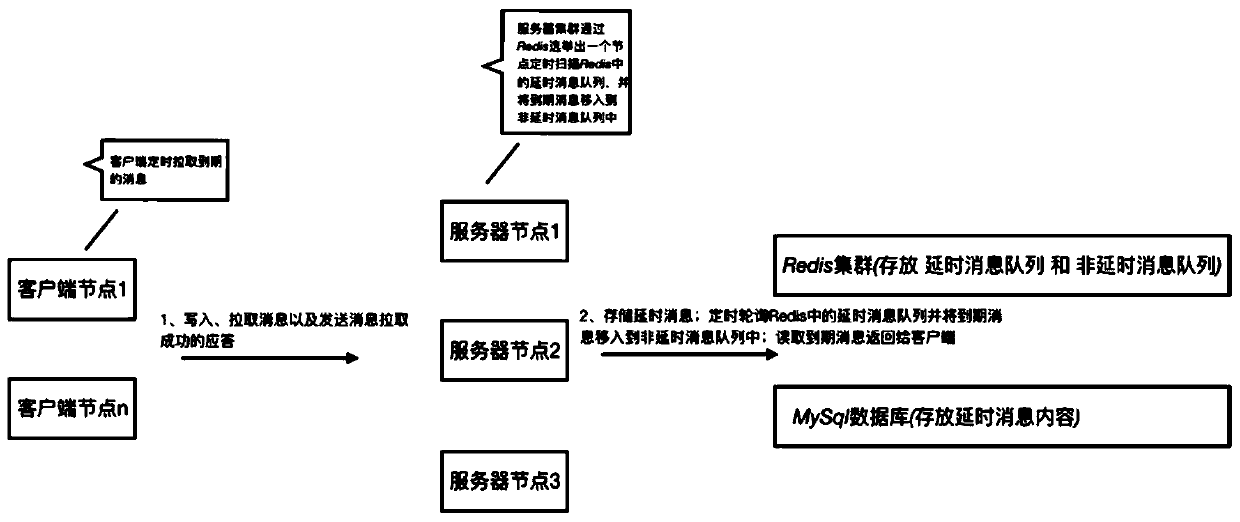
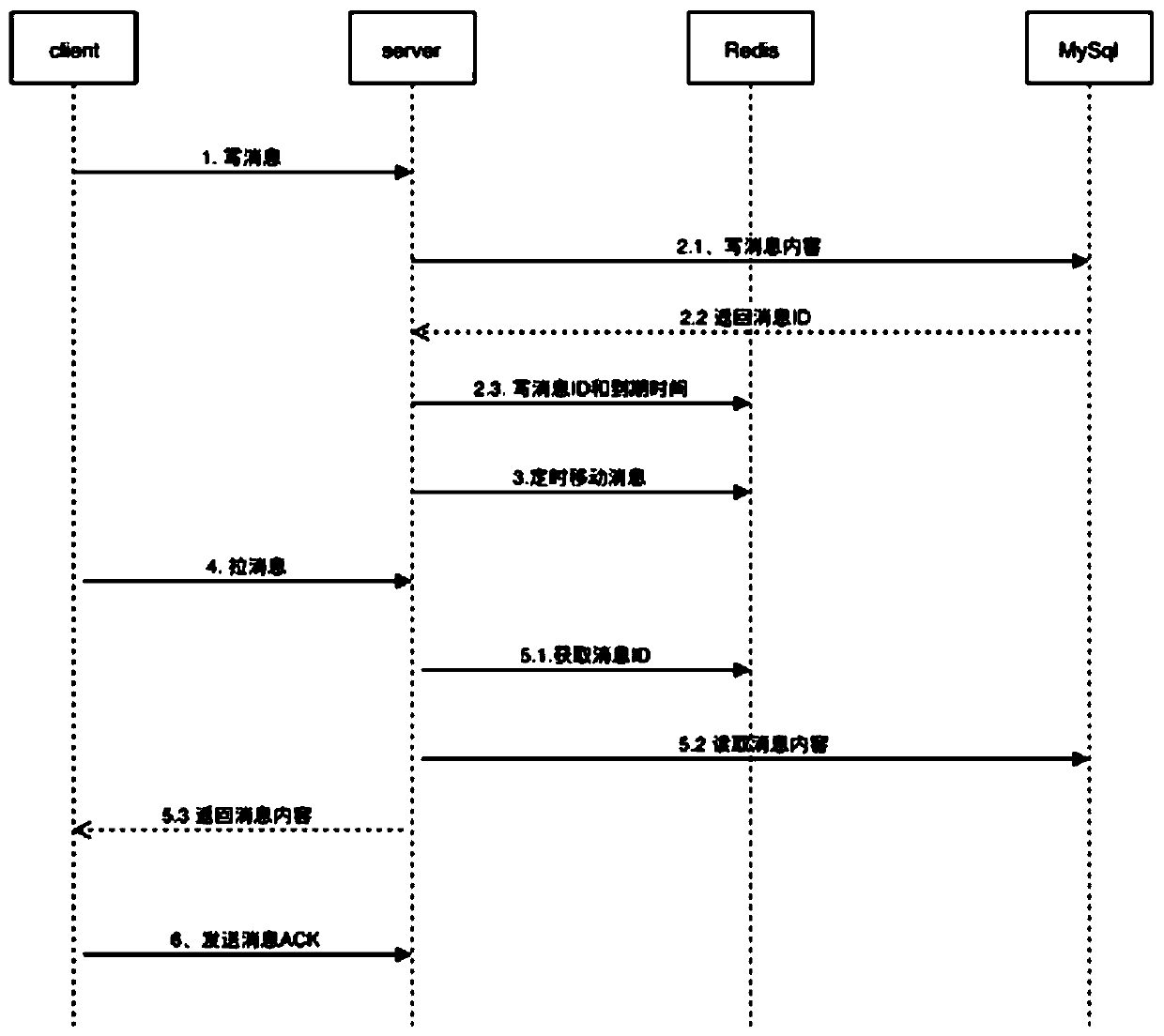
ActiveCN111225041AAddressing slow performanceReduce riskInterprogram communicationTransmissionExpiration TimeIn-memory database
The invention discloses a method and system for realizing a delay message queue, and the method comprises the steps that a client module transmits a message to a server module, and the server module writes the message into a relational database for storage; the server module judges that the expiration time of the message is greater than the time of the current server, and generates a delay messagerecord; the server module writes the delay message record into a delay message queue in a memory database, and periodically polls the delay message queue; the client module pulls a delay message record to the server module, and the server module checks the delay message queue, reads the message content in the relational database and feeds back the message content to the client module; and the client module receives the message content, sends ACK to the server module, and displays that the message is successfully received. According to the method, an extension strategy is adopted, various service scenes needing message delay are supported, functions of an existing message queue system are fully utilized to achieve zero invasion, and risks caused by modification of an original message queuesystem are avoided.
Owner:西藏宁算科技集团有限公司
Pushed message delay processing method and system, intelligent receiving terminal and mobile terminal
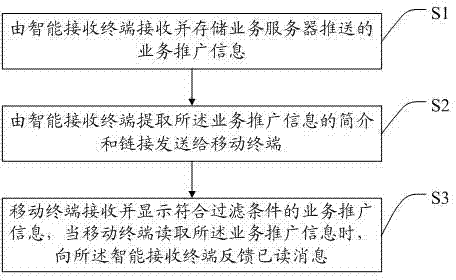
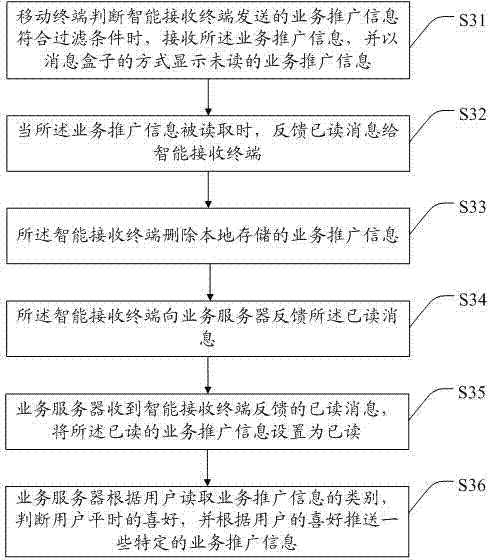
ActiveCN104270656AIncrease valueEasy to operateSelective content distributionHandling systemCable television
The invention discloses a pushed message delay processing method and system, an intelligent receiving terminal and a mobile terminal. The pushed message delay processing system comprises a service server, the intelligent receiving terminal and the mobile terminal, wherein service popularization information pushed by the service server is received and stored through the intelligent receiving terminal, the intelligent receiving terminal extracts the abstract and link of the service popularization information and sends the abstract and link to the mobile terminal, and the mobile terminal can display and operate the service popularization information originally stored on the intelligent receiving terminal, so that the situation that a user misses the interested service popularization information when not using the intelligent receiving terminal is avoided. In addition, when watching movie and television programs of the intelligent receiving terminal, the user can browse and operate the service popularization information through the mobile terminal, playing of the movie and television programs by the intelligent receiving terminal is not interrupted, and therefore the marketing value of the existing service popularization information like television advertisements and television shopping is improved.
Owner:SHENZHEN SKYWORTH RGB ELECTRONICS CO LTD
Wireless Message Collision Avoidance with High Throughput
ActiveUS20200205199A1Well formedError prevention/detection by using return channelWireless communicationWireless trafficEngineering
Improved protocols for wireless networking are disclosed. At low / zero marginal cost, embodiments enable increased throughput and reduced delays at high traffic density, while greatly reducing message collisions and ensuring that each user is able to transmit in order. By providing a sequencing advantage to nodes that have already been delayed, embodiments can eliminate the “blocked node” problem in which some nodes are suppressed indefinitely while other nodes are allowed to dominate a communication channel with multiple transmissions. As the wireless traffic density soars in the coming years, embodiments can improve system utility while enhancing user satisfaction by providing higher message success rates, reducing user frustration, minimizing message delays and message collisions, and eliminating node blocking. An array of embodiments can be implemented on existing and planned equipment with appropriate programming. And of vital importance in emergencies, the likelihood of a blocked 911 call can be significantly reduced.
Owner:ULTRALOGIC 6G LLC
Distributed locking protocol with asynchronous token prefetch and relinquish
InactiveUS7325064B2Reduce message overheadReduce message trafficMultiple digital computer combinationsData switching networksTraffic capacityComputer science
Asynchronous messages are used to prefetch and / or relinquish tokens used in providing locking of shared resources. A message is sent to prefetch one or more tokens, and prior to receiving a reply for the message, another message (e.g., an acquire) is sent for at least one of those tokens. Similarly, a message is sent indicating a voluntary relinquish of one or more tokens and without having acknowledgment that the relinquish request was processed, a further message (e.g., an acquire) is sent for at least one of the tokens. Multiple tokens may be acquired and / or relinquished in a single message to the token server. This reduces message delays and overall message traffic.
Owner:IBM CORP
Method for securely transmitting control data from a secure network
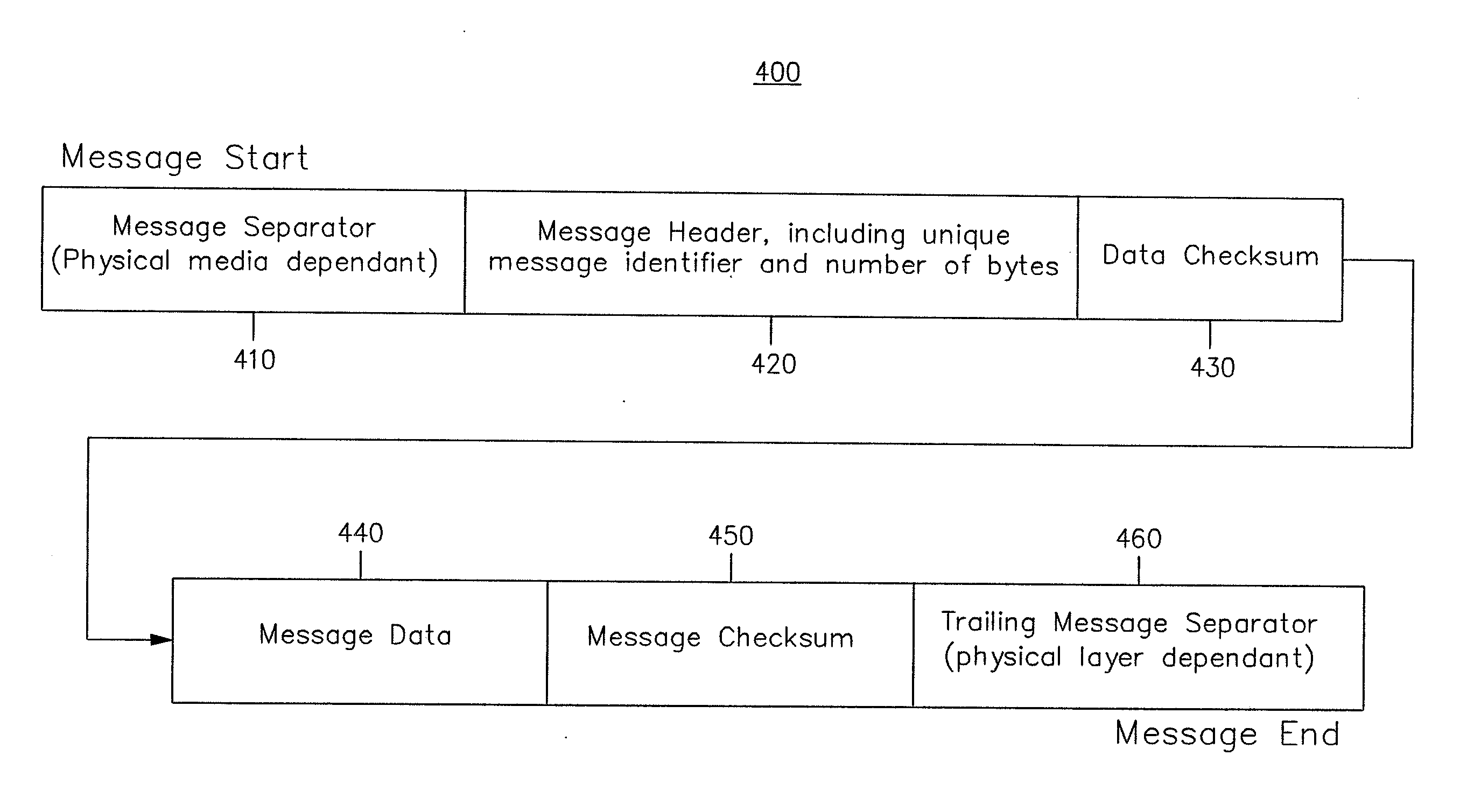
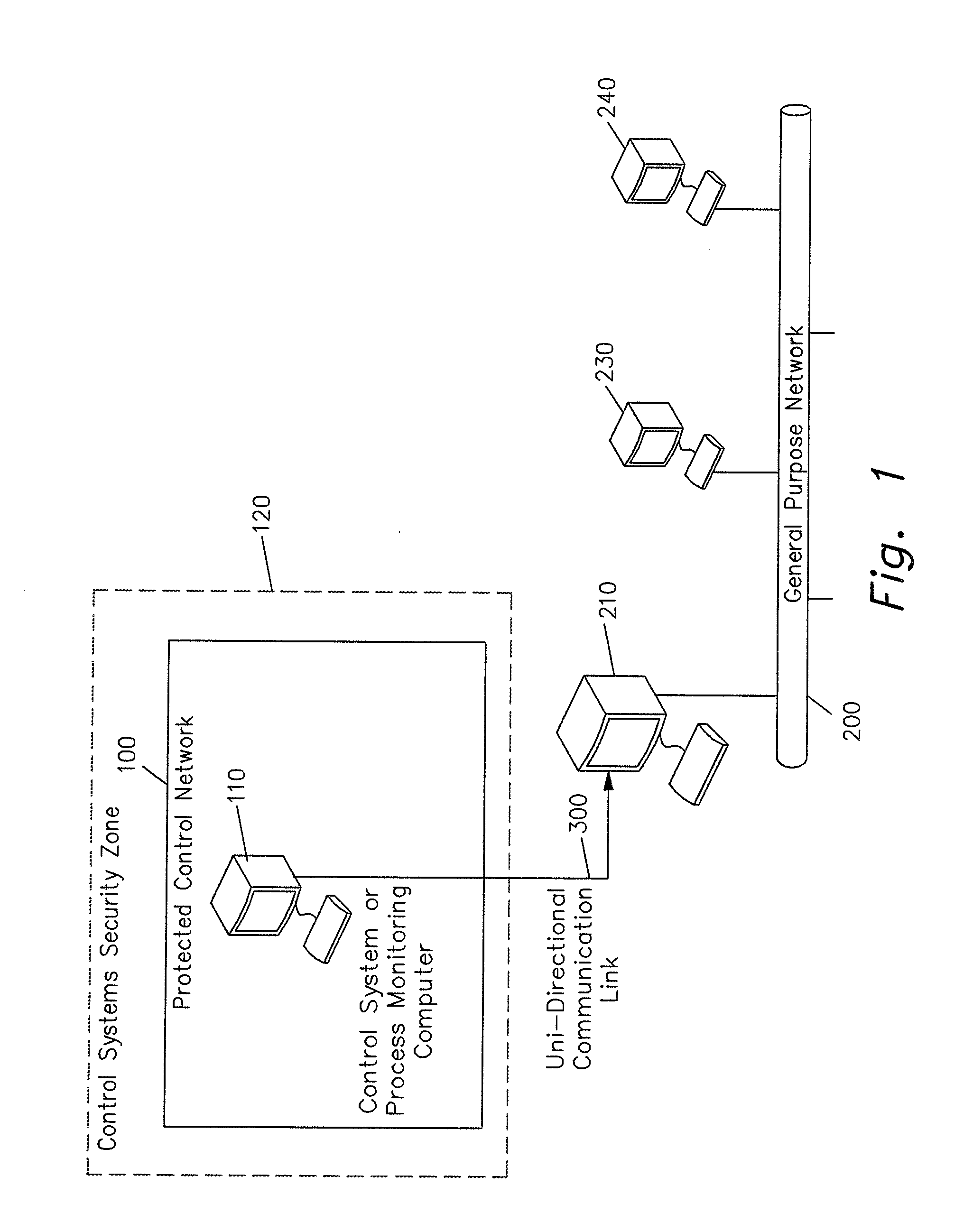
ActiveUS20100275031A1Risk minimizationReliable data transmissionUser identity/authority verificationCyber-attackTransfer system
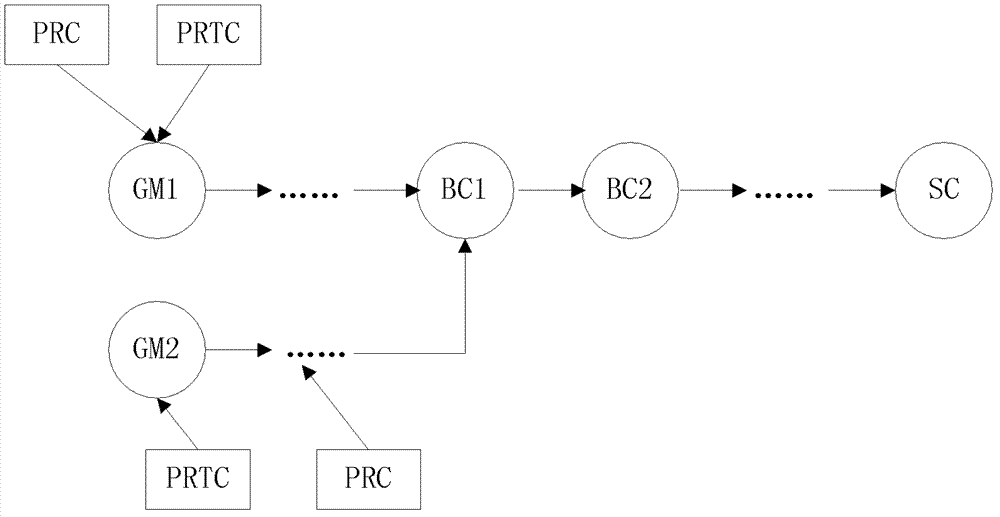
This method securely transmits data from a secure control system [110] located on an isolated computer network [100] to a separate computer [210] outside the isolated control network [100]. The method includes several features designed to minimize the risk of outside cyber attack on the control system [110] while ensuring that the data is transmitted correctly and promptly. The system uses a non-routable unidirectional physical data link [300]. Messages [400] are redundantly transmitted to computer [210] without acknowledgement along with checksums [430,450]. The checksum information is used to validate that the message header [420] and the message data [440] have been received correctly. Redundant information contained in repeated message data blocks [440] is discarded after the transmitted message [400] is correctly received and decoded. An ordered transmission sequence is used to minimize the message delay if an individual message [400] was not received correctly on its first transmission.
Owner:GENERAL ELECTRIC TECH GMBH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com