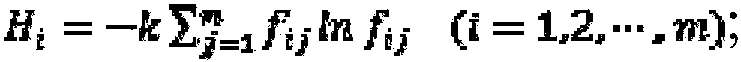Patents
Literature
106 results about "Priority Number" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
An integer designating the relative priority of events, activities, or entities of a similar type. Lower priority number signifies higher priority value.
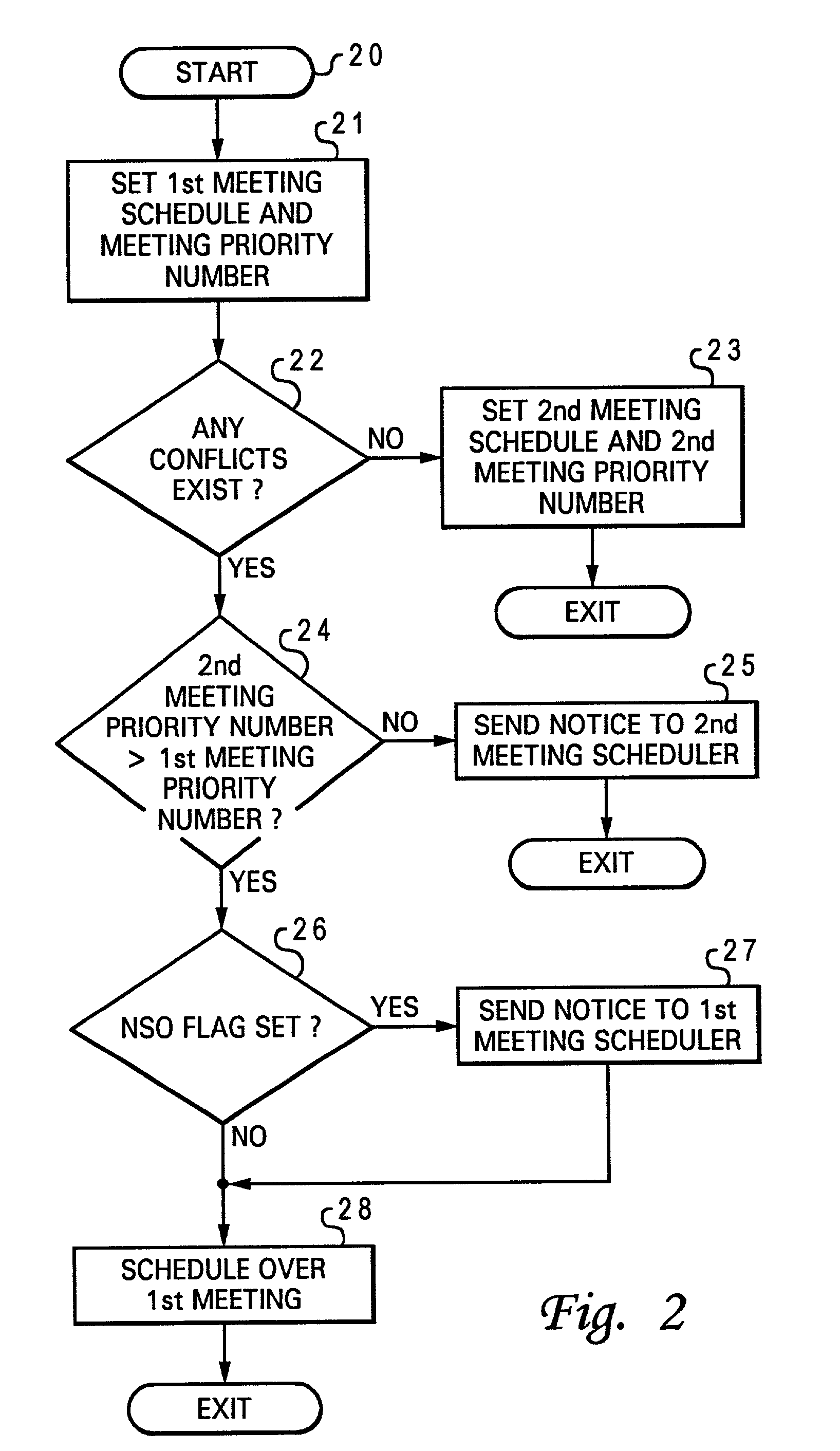
Method for resolving meeting conflicts within an electronic calendar application
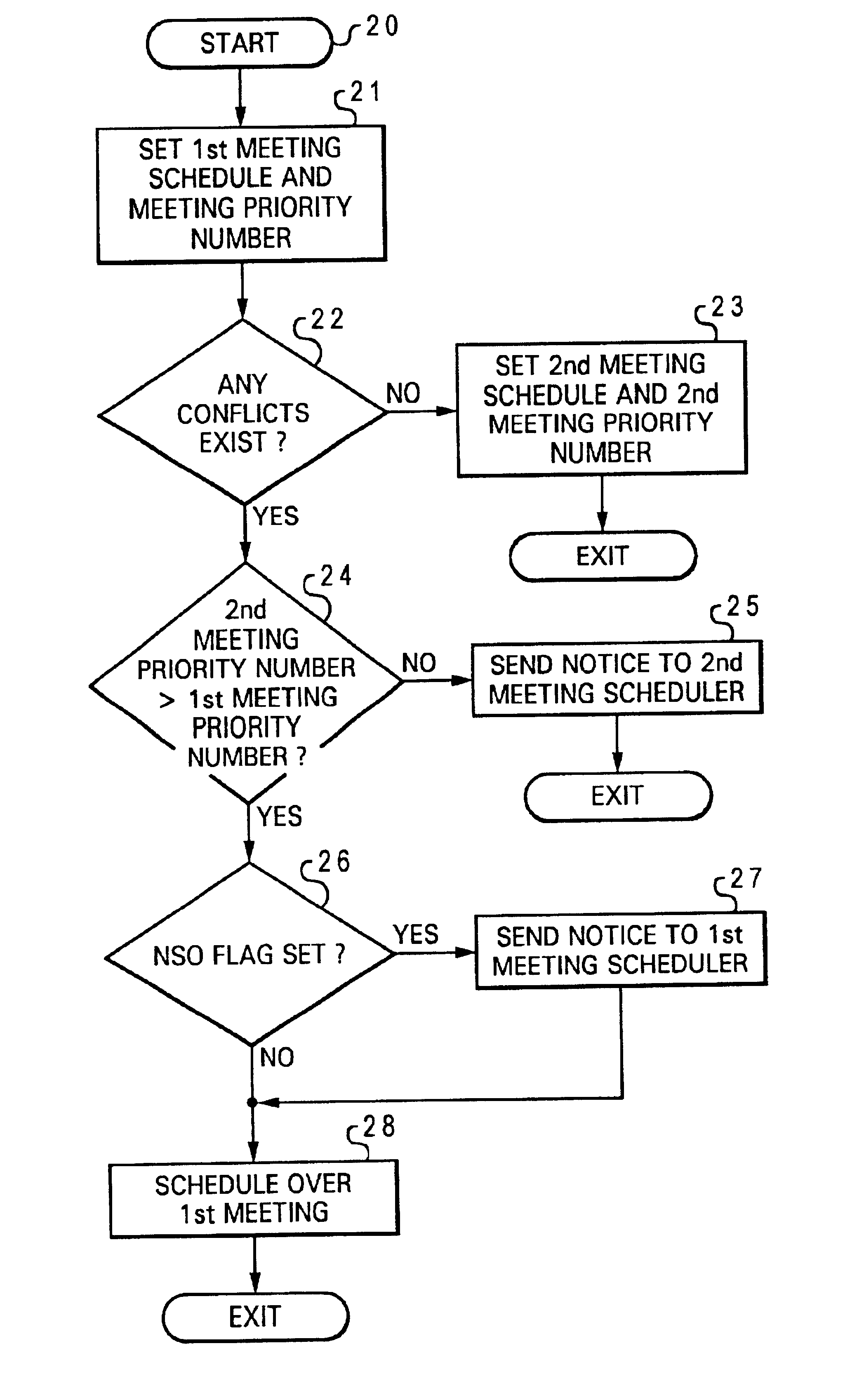
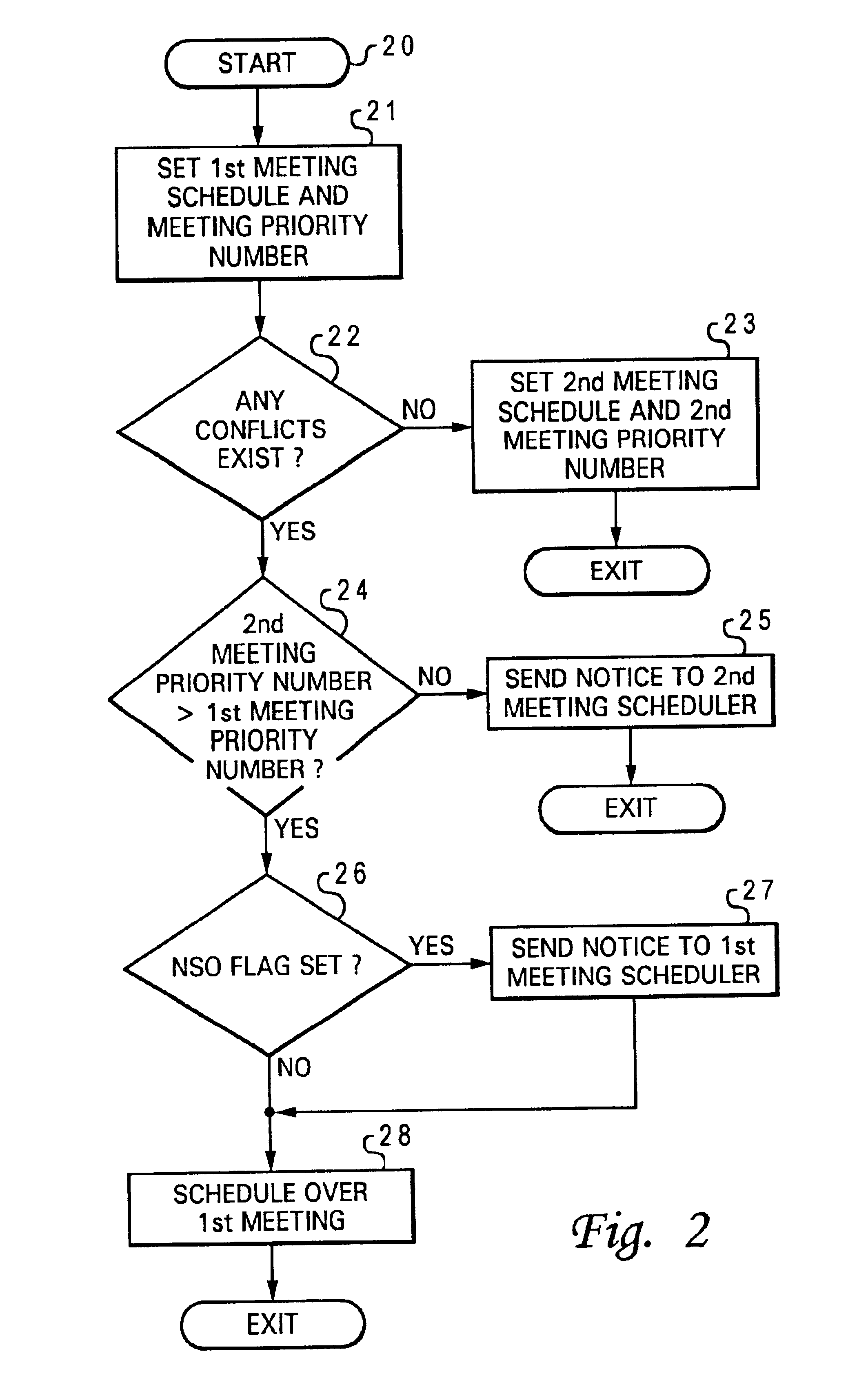
A method for resolving meeting conflicts for an electronic calendar application is disclosed. After receiving a request for setting a first meeting schedule for a first meeting, an electronic calendar application sets a first meeting schedule and a first meeting priority number associated with the first meeting. In response to a request to set a second meeting schedule for a second meeting, and the second meeting schedule conflicts with the first meeting schedule, the electronic calendar application determines whether a second meeting priority number associated with the second meeting is higher than the first meeting priority number associated with the first meeting. If the second meeting priority number is determined to be higher than the first meeting priority number, then the electronic calendar application overrides the first meeting schedule with the second meeting schedule. Next, the electronic calendar application informs a meeting scheduler of that first meeting that the first meeting has been overridden by the second meeting schedule.
Owner:IBM CORP
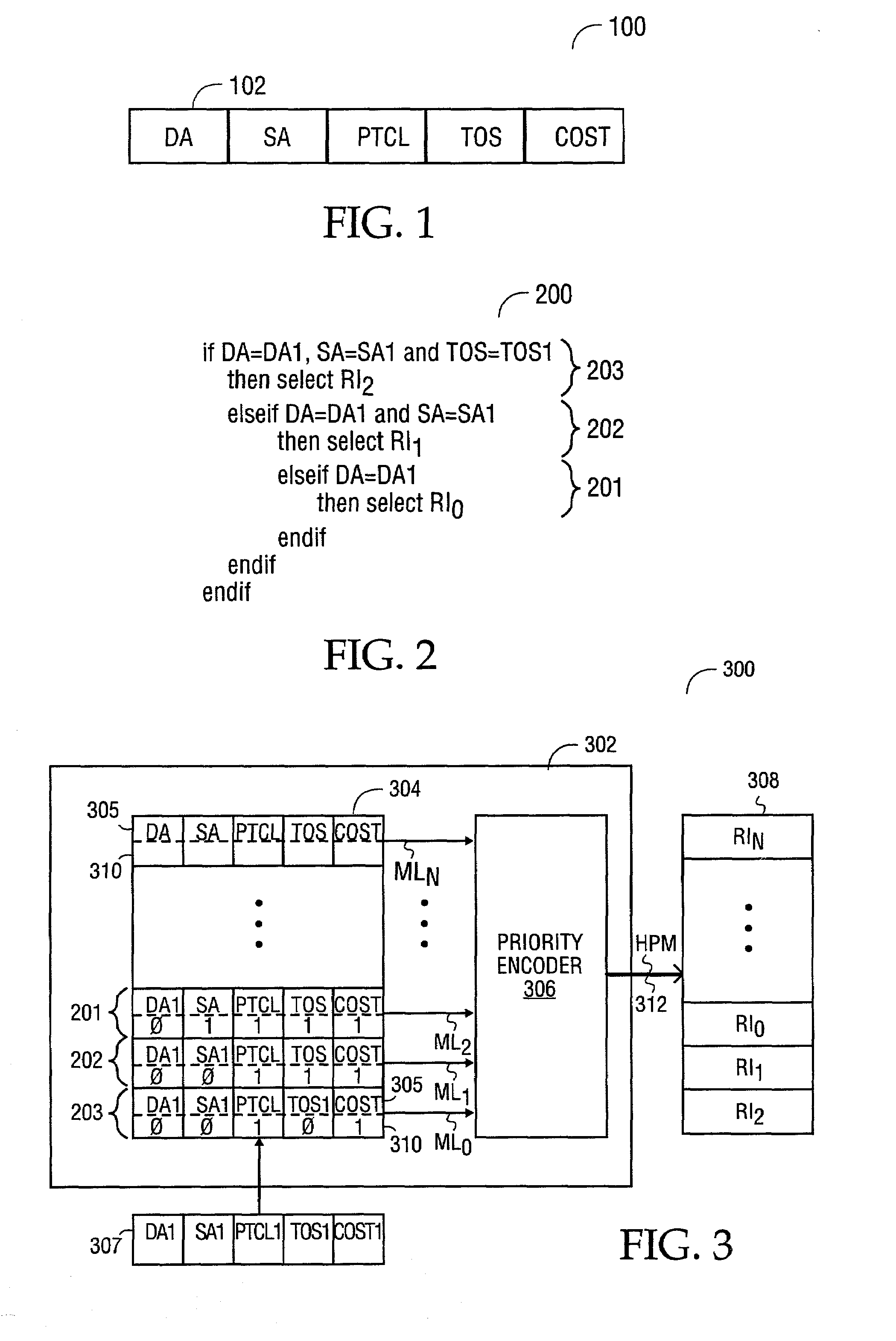
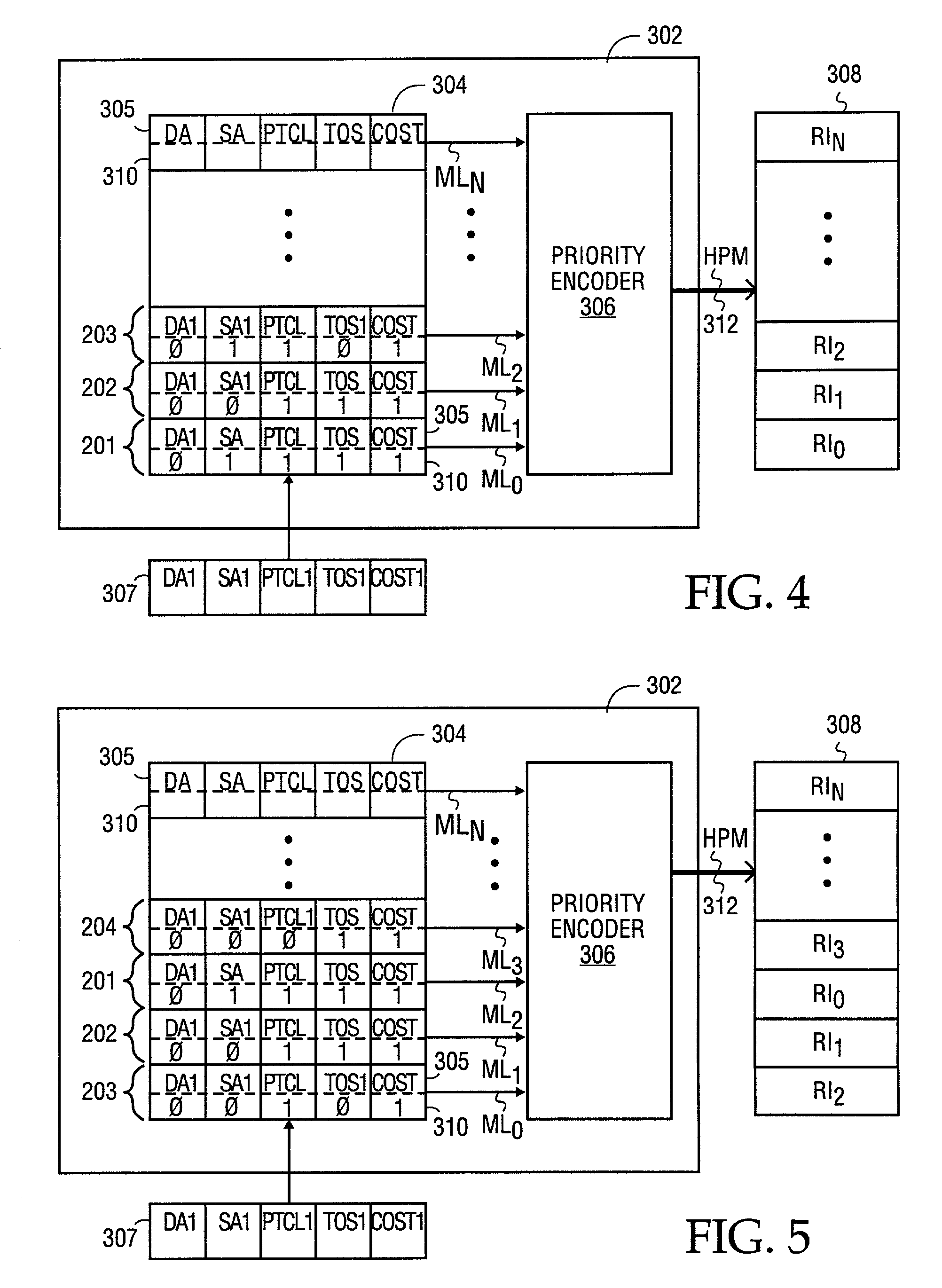
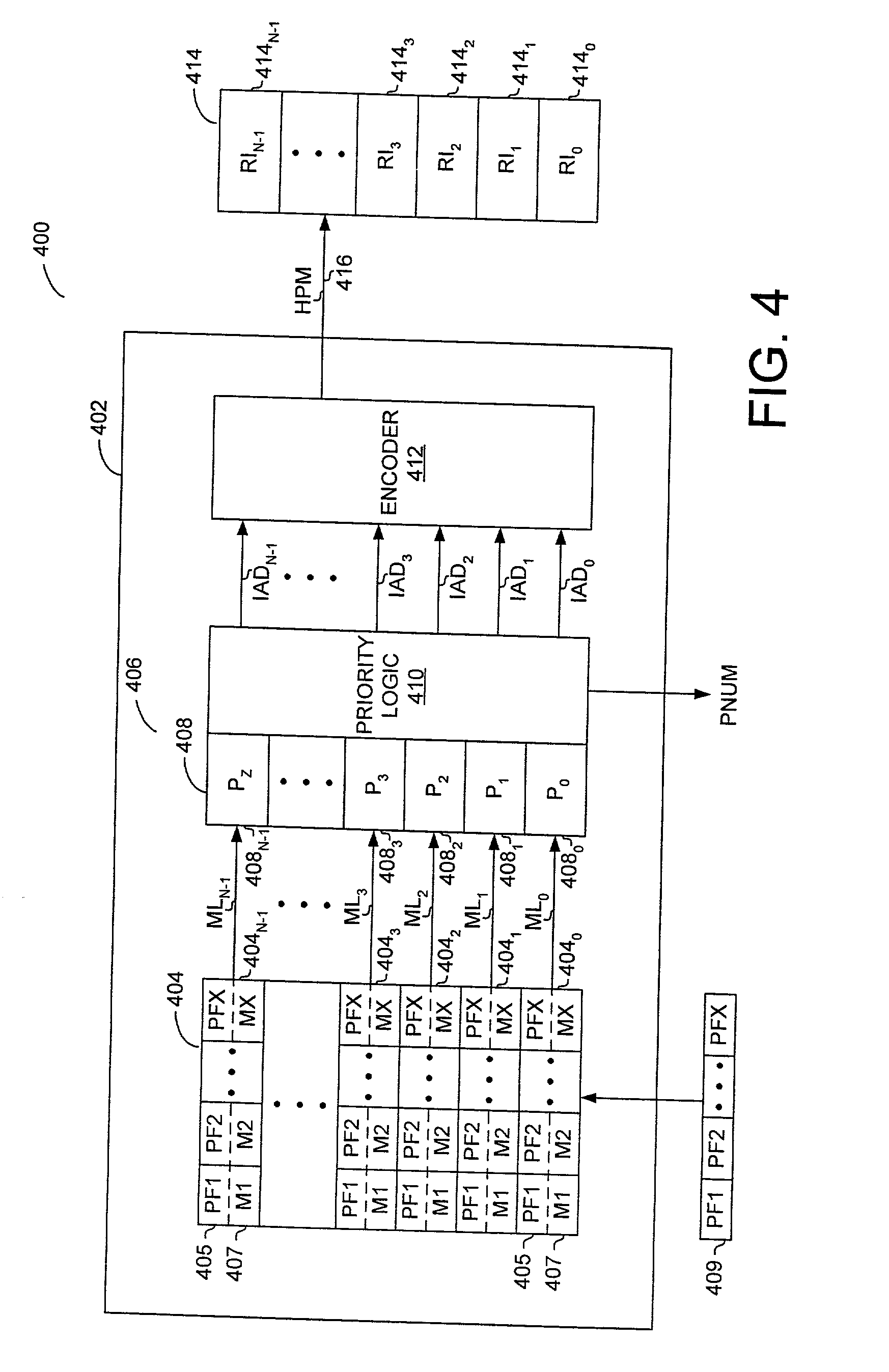
Method and apparatus for performing priority encoding in a segmented classification system using enable signals
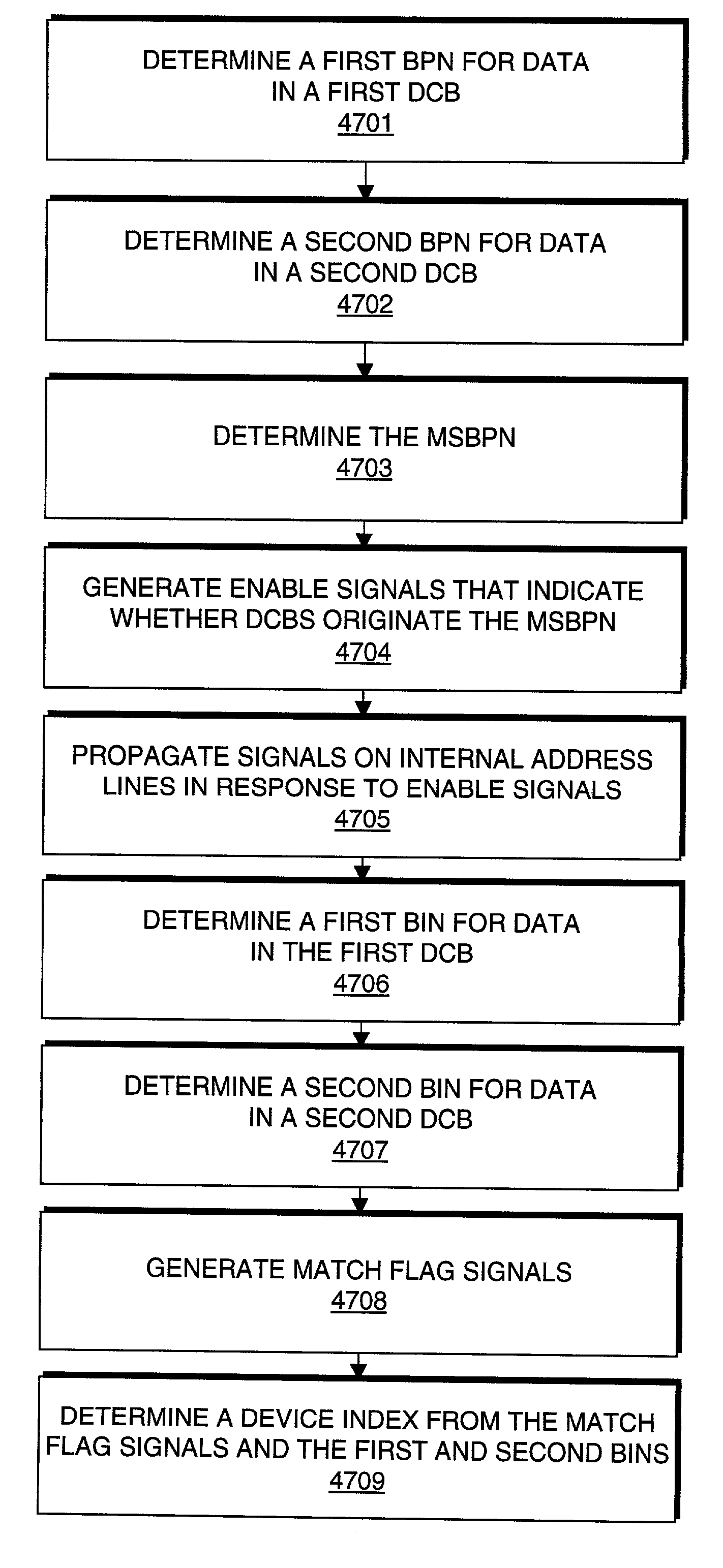
A digital signal processor. The digital signal processor includes a first data classification block. The first data classification block outputs a first block priority number associated with a first data stored in the first data classification block that matches a search key. The digital signal processor includes a second data classification block. The second data classification block outputs a second priority number associated with a second data stored in the second data classification block that matches the search key. The digital signal processor includes a device index processor. The device index processor selects a most significant block priority number from the first block priority number and the second block priority number.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
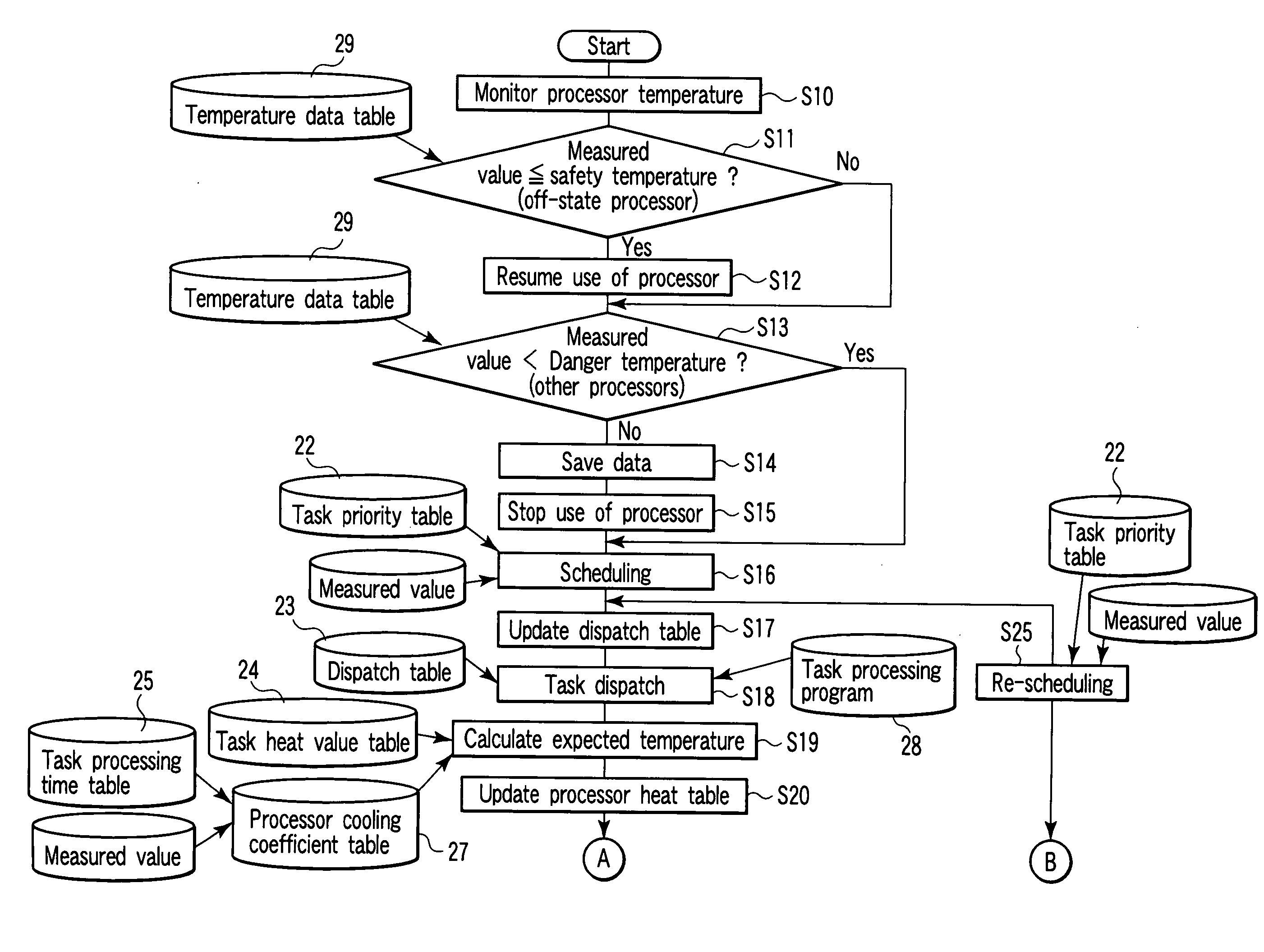
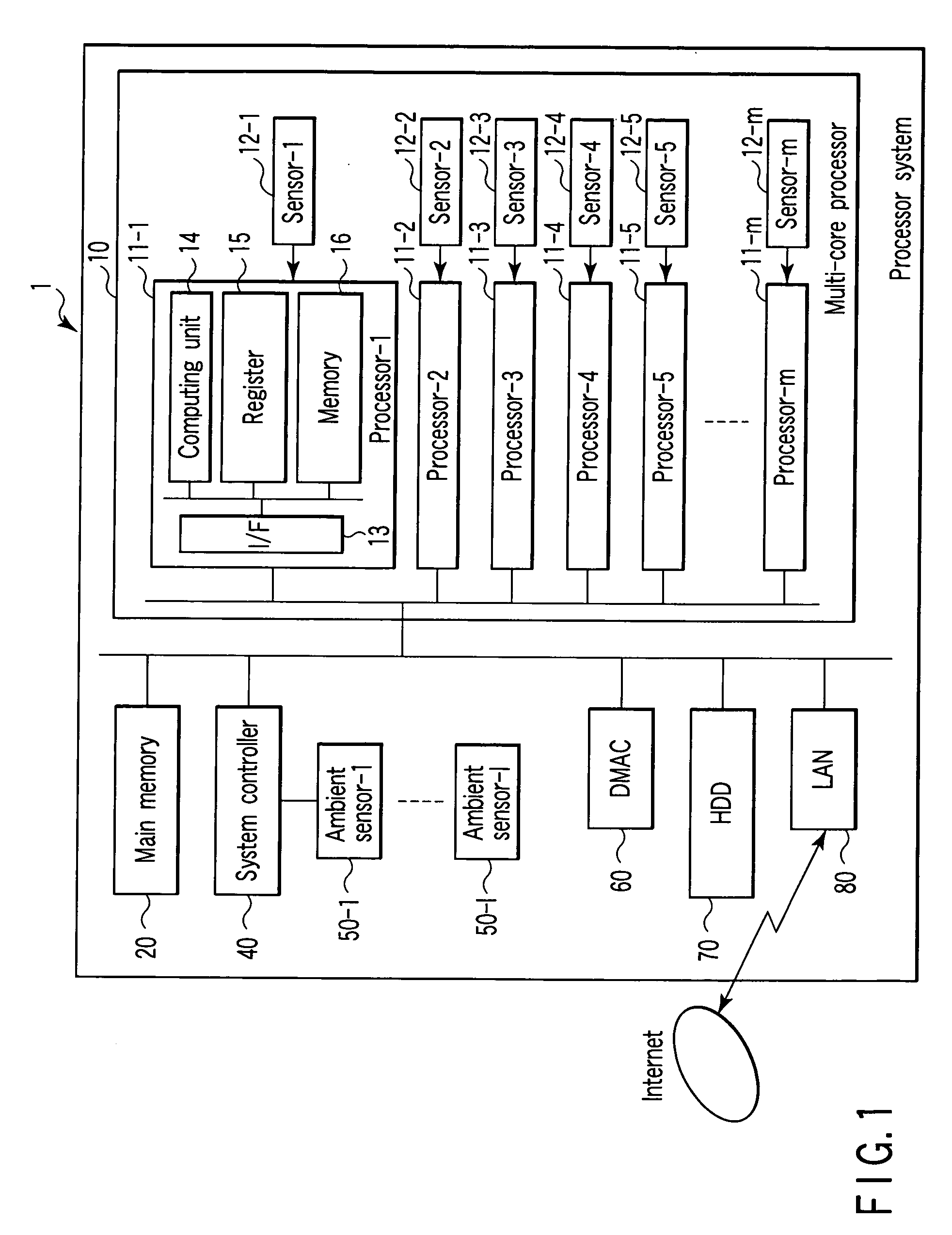
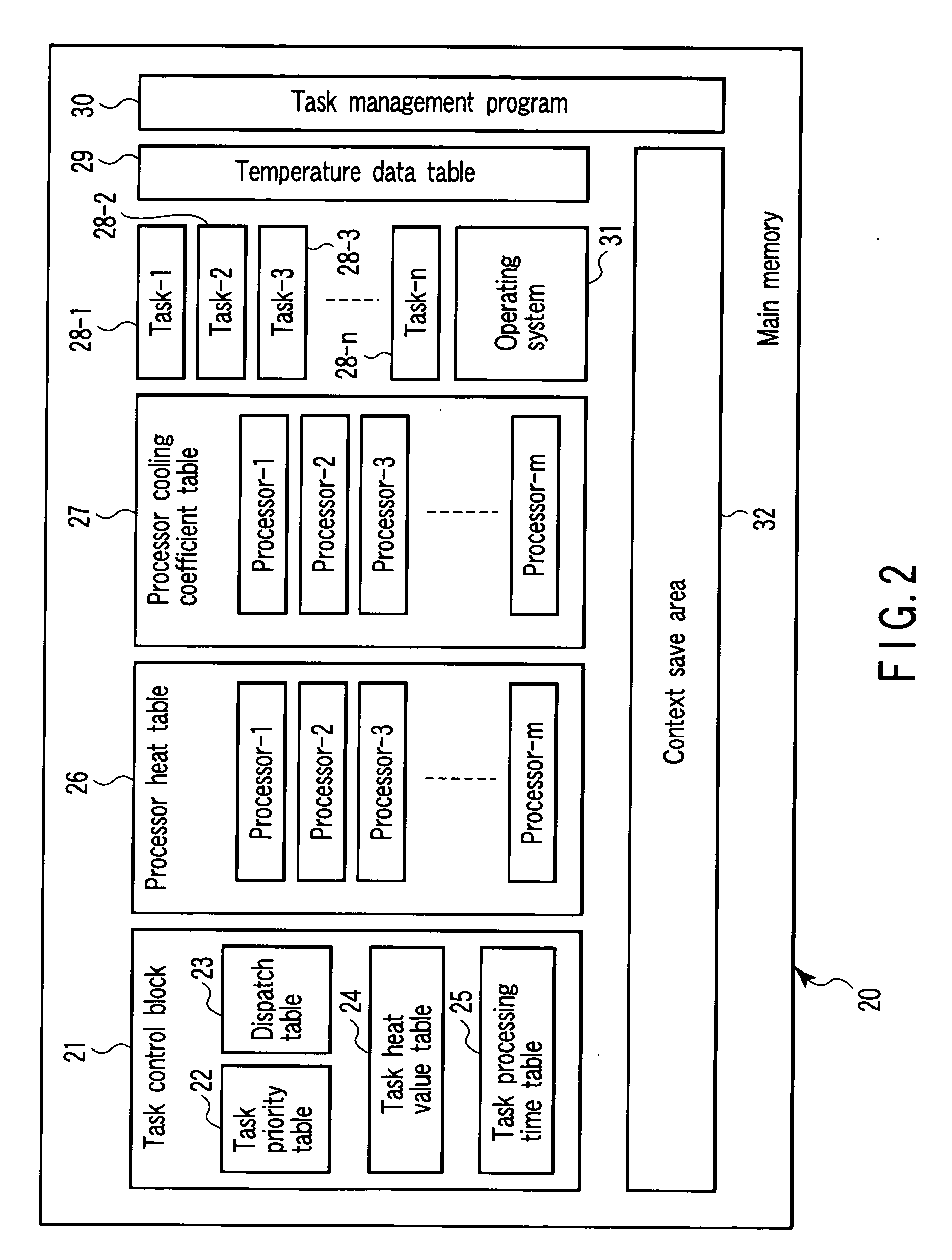
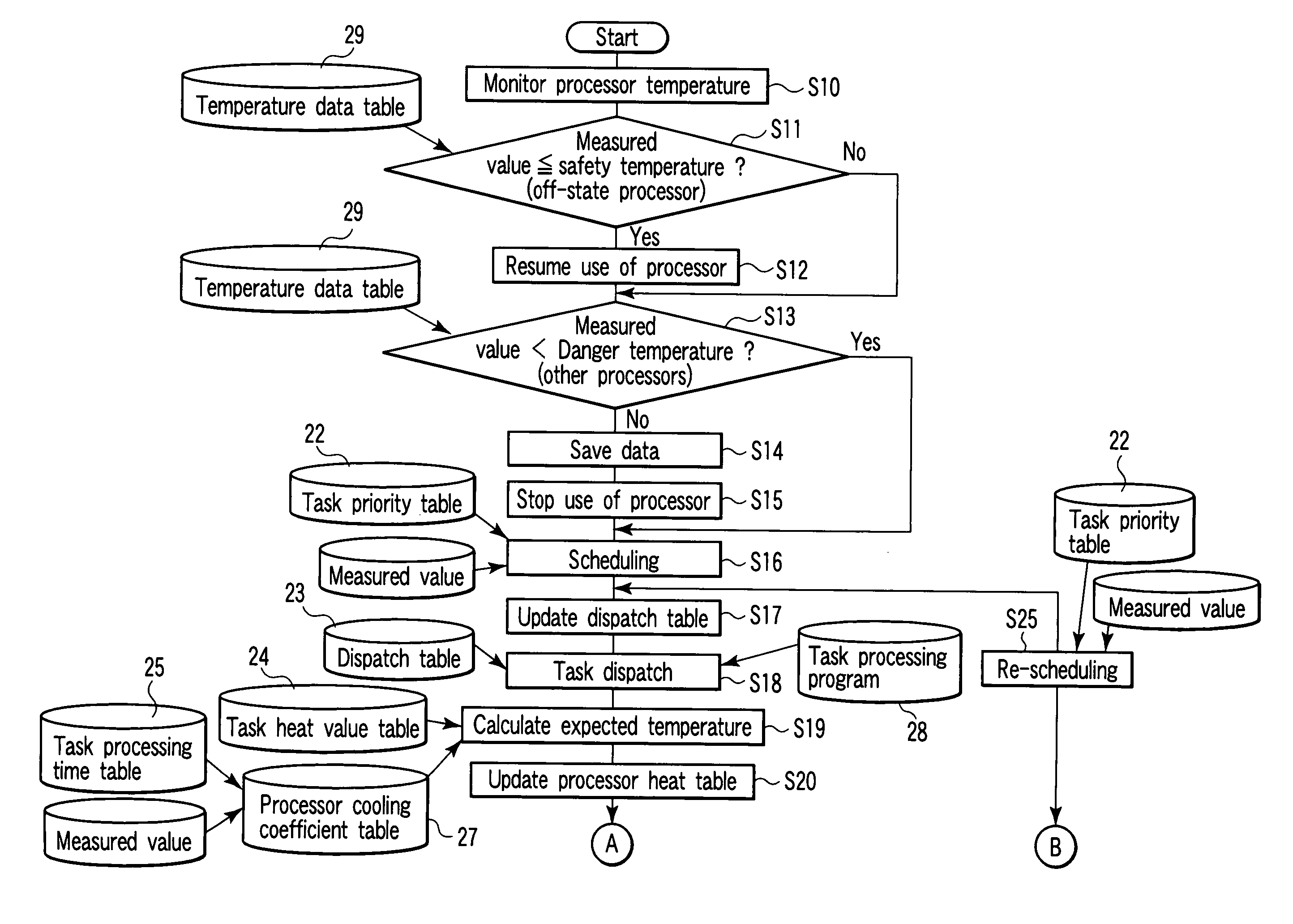
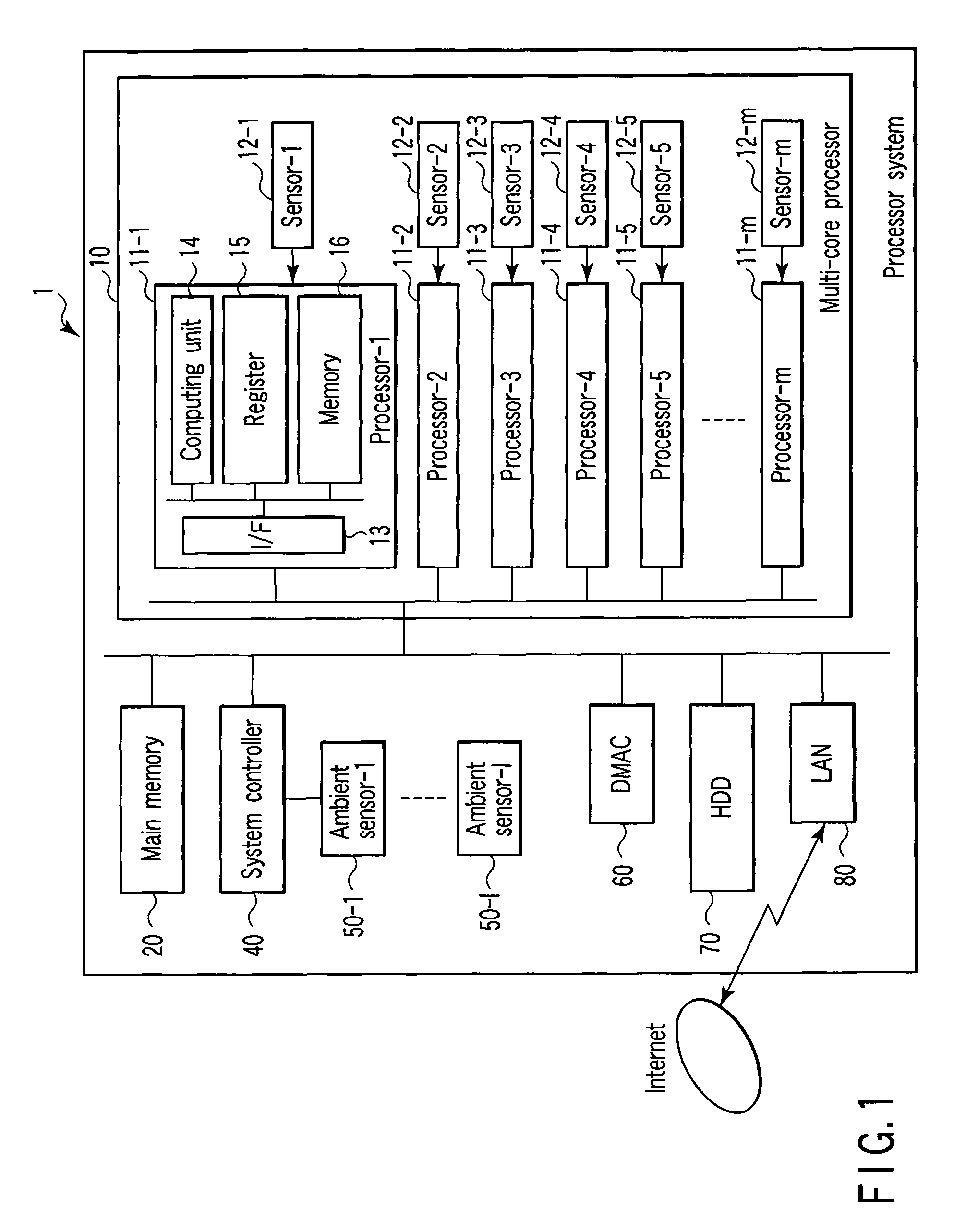
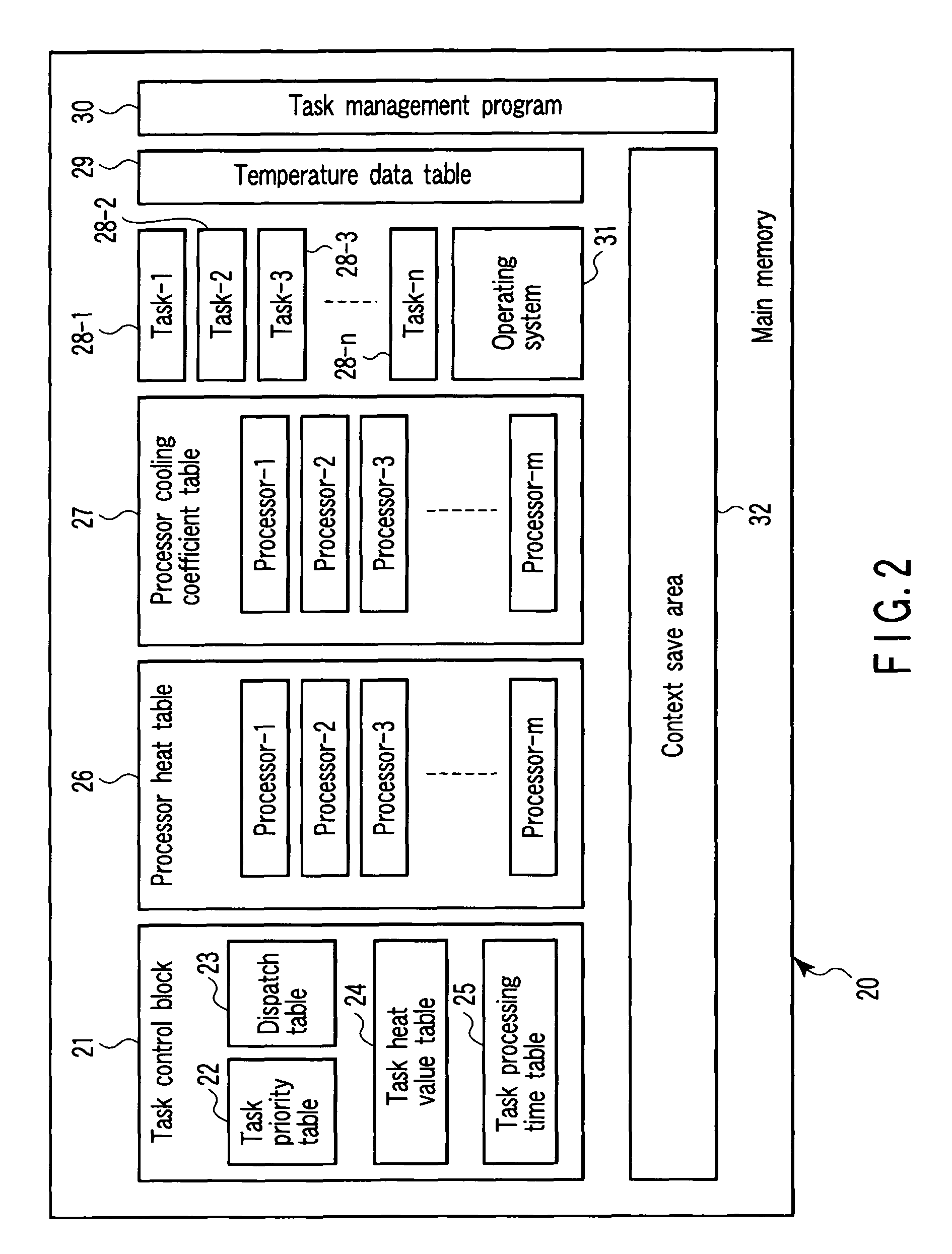
Processor system with temperature sensor and control method of the same
A processor system includes a plurality of first processors, a temperature sensor, a main memory, and a second processor. The first processors individually process tasks. The temperature sensor measures a temperature of each of the first processors. The main memory stores programs of the tasks processed by the first processors, and a task priority order table containing a relationship between the tasks and task priority numbers. The second processor assigns the tasks to the first processors on the basis of the task priority order table and the temperatures of the first processors measured by the temperature sensor.
Owner:KK TOSHIBA
System and method for managing master-slave relationships within a network
InactiveUS20060221856A1Big advantageNetwork topologiesData switching by path configurationPriority NumberBluetooth networks
A system and method for managing the relationship between master devices and slave devices within a network such as a Bluetooth network. Each time that a master device connects to a slave device, the network topology is updated. This update is transmitted to each slave device, sending the node's properties for each slave device belonging to the network, as well as an update on the priority number given to each slave device. When a master device abruptly exits the network, a slave device with the highest priority configures itself as the master device. The new master device then attempts to connect to the other slave devices using previously-stored information.
Owner:NOKIA CORP
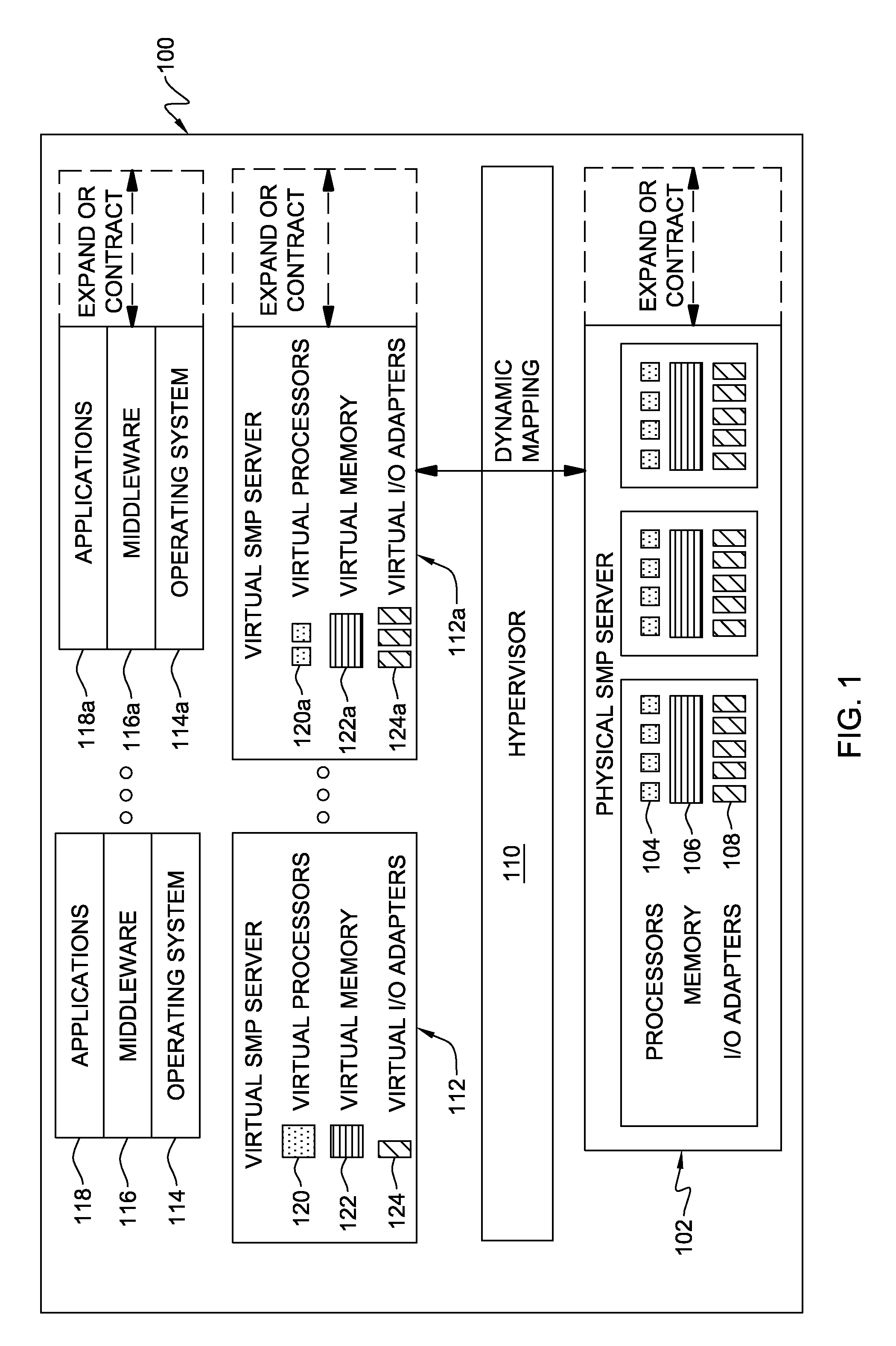
Managing Assignment of Partition Services to Virtual Input/Output Adapters
ActiveUS20090307690A1Multiprogramming arrangementsNon-redundant fault processingData processing systemService allocation
Automated management of partition service assignment to a virtual input / output (VIO) adapter is provided. Responsive to creation of a new partition service in a data processing system, a partition priority number is determined for the new partition service, and, for each VIO adapter, the partition priority numbers of the partition services currently assigned to that VIO adapter are summed. For a VIO adapter with a lowest sum of partition priority numbers, logic determines whether assigning the new partition service to that VIO adapter results in its summed partition priority number being above a predefined threshold, and the new partition service is assigned to a VIO adapter based, at least in part, on whether assigning the new partition service to the VIO adapter with the lowest sum of partition priority numbers results in that VIO adapter's summed partition priority number exceeding the predefined threshold.
Owner:IBM CORP
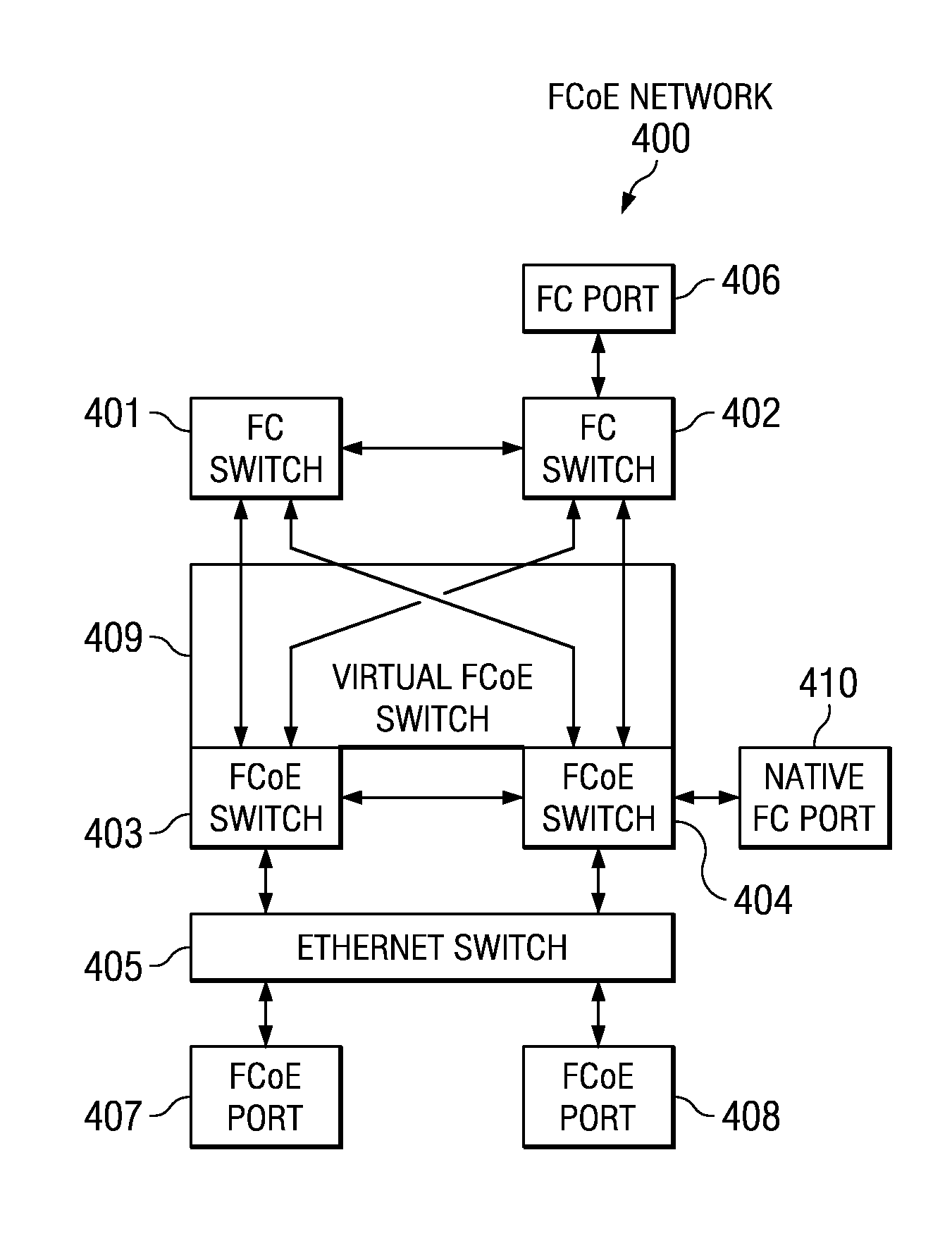
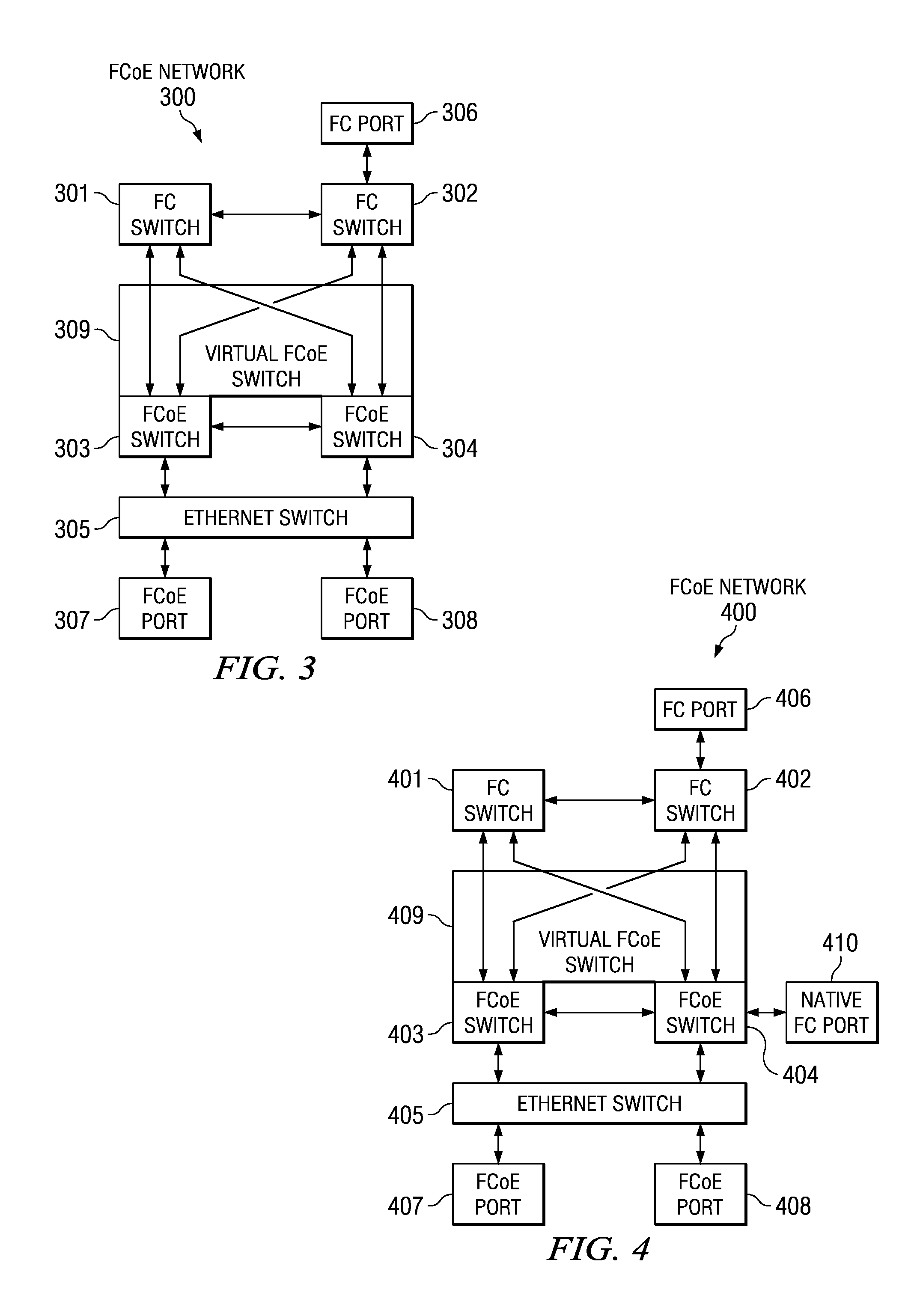
Virtual fibre channel over Ethernet switch
InactiveUS7792148B2Multiplex system selection arrangementsTime-division multiplexEngineeringFibre Channel over Ethernet
A system for using a virtual switch in a network. In response to a switch connecting to a network, network configuration data is read to determine whether the switch is part of a virtual switch. In response to determining that the switch is part of the virtual switch, a priority number for the switch is sent to other switches connected to the network. Priority numbers are received from the other switches. It is determined whether the switch has a highest priority number. In response to determining that the switch does have the highest priority number, the switch is selected to be a master switch for the virtual switch. Then, domain identification data for the virtual switch is sent to the other switches. Afterward, the switch and the other switches respond to requests over the network as one domain identified by the domain identification data.
Owner:IBM CORP
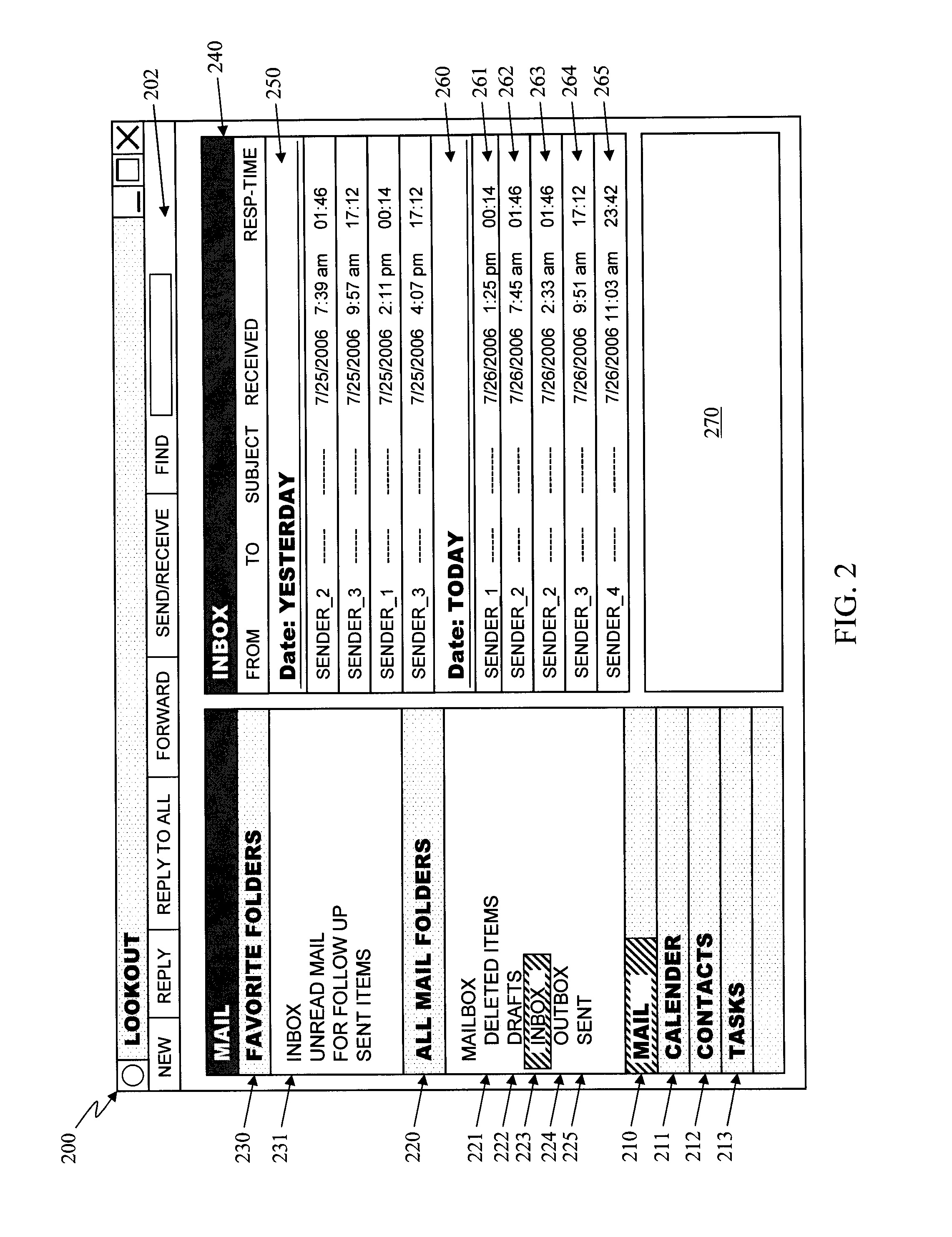
System and method for managing emails based on user response time
InactiveUS20080065736A1Quick identificationRespond quicklyMultiple digital computer combinationsTime managementDisplay Order
An email management method including the steps of determining a user response interval for a plurality of emails, generating an attribute priority number for one or more attributes associated with the plurality of emails, and automatically ranking new emails based on the attribute priority numbers associated with the first plurality of emails. The attribute priority numbers may, therefore, be used to infer the relevance of new emails based on the recipient's response time and then display those new emails from the most relevant to least relevant. In the preferred embodiment, the primary email attribute upon which emails are automatically ranked is the sender's name or identity, although various other properties of an email may be used to determine a suitable display order for new emails.
Owner:GROSS WILLIAM
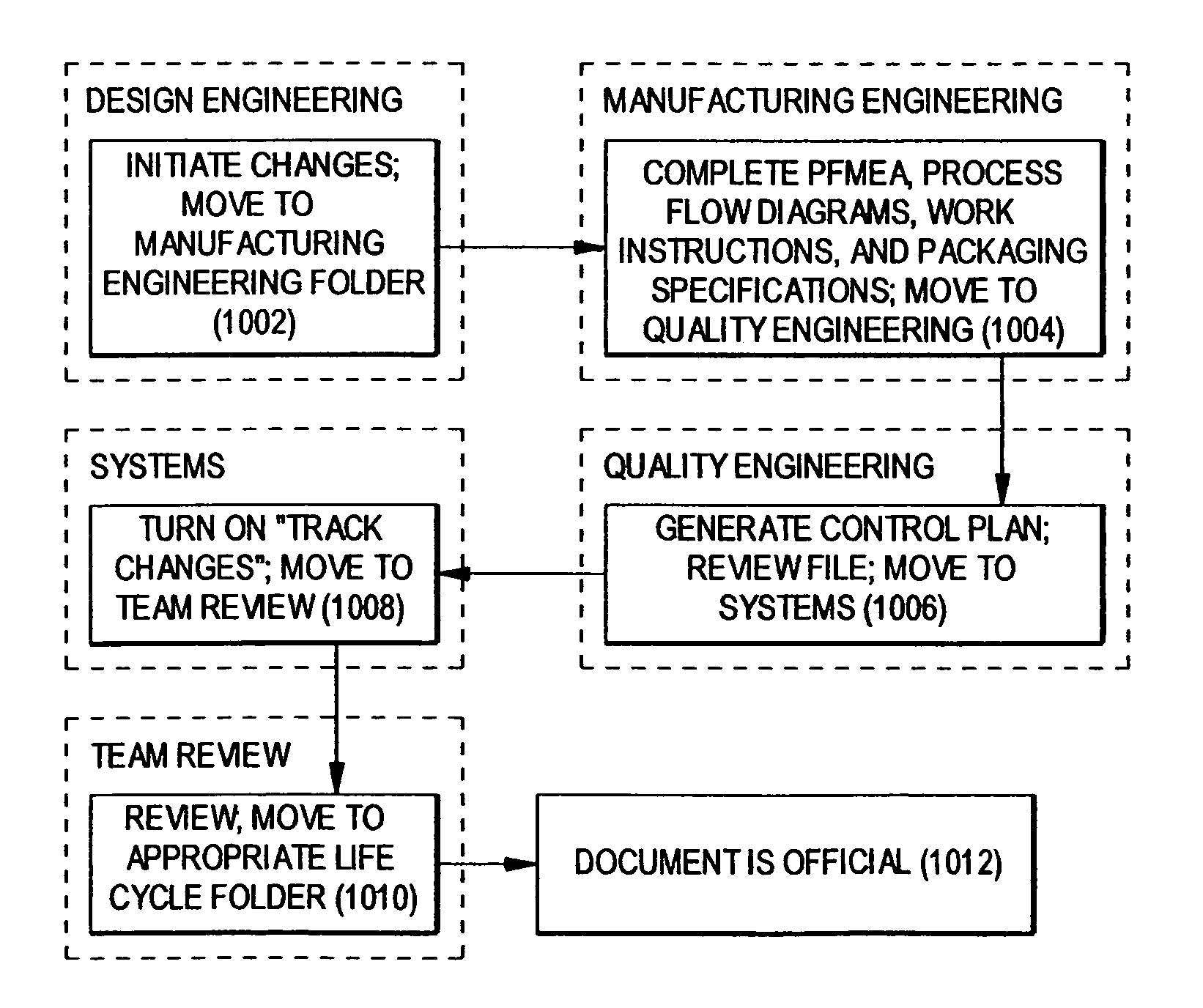
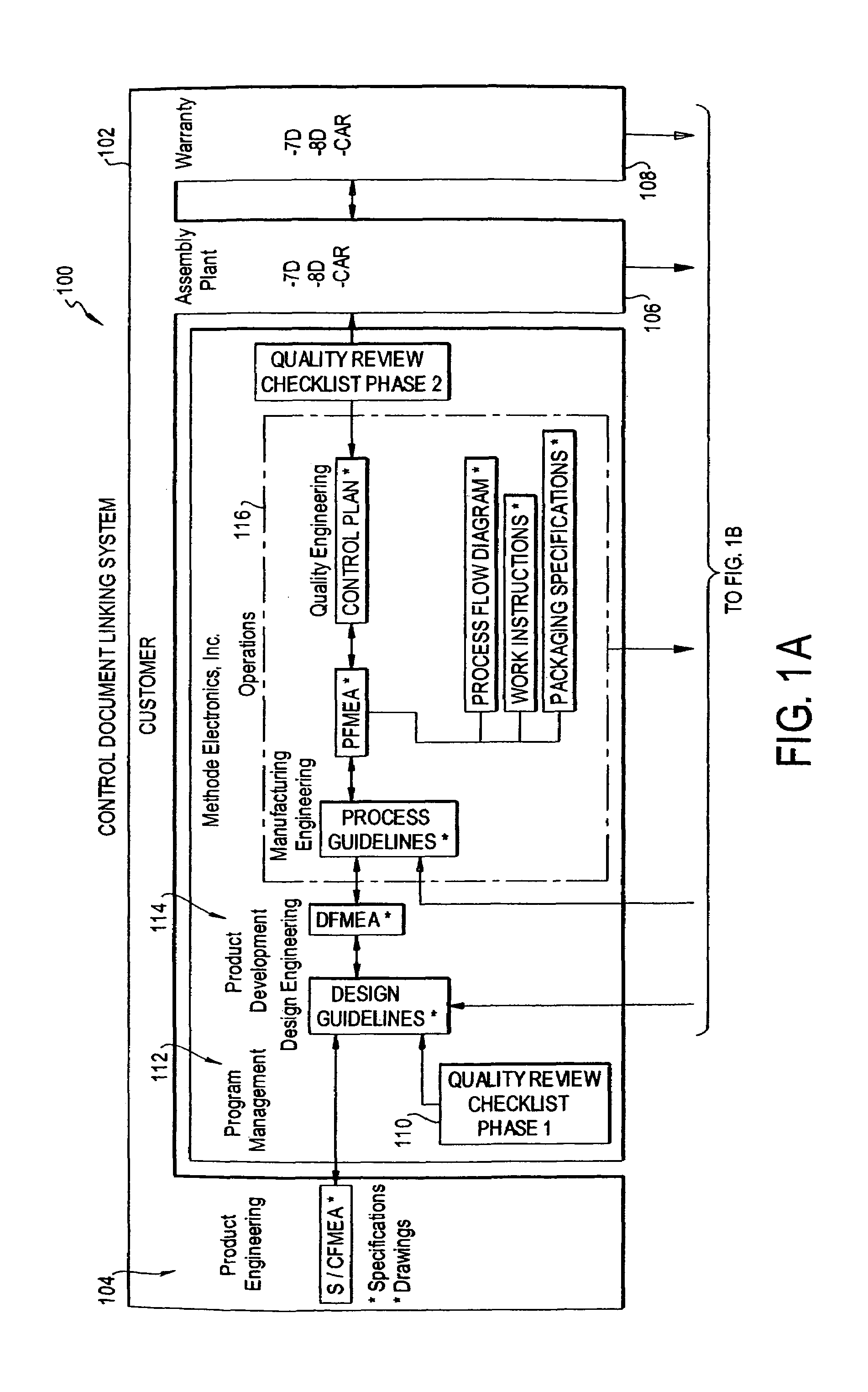
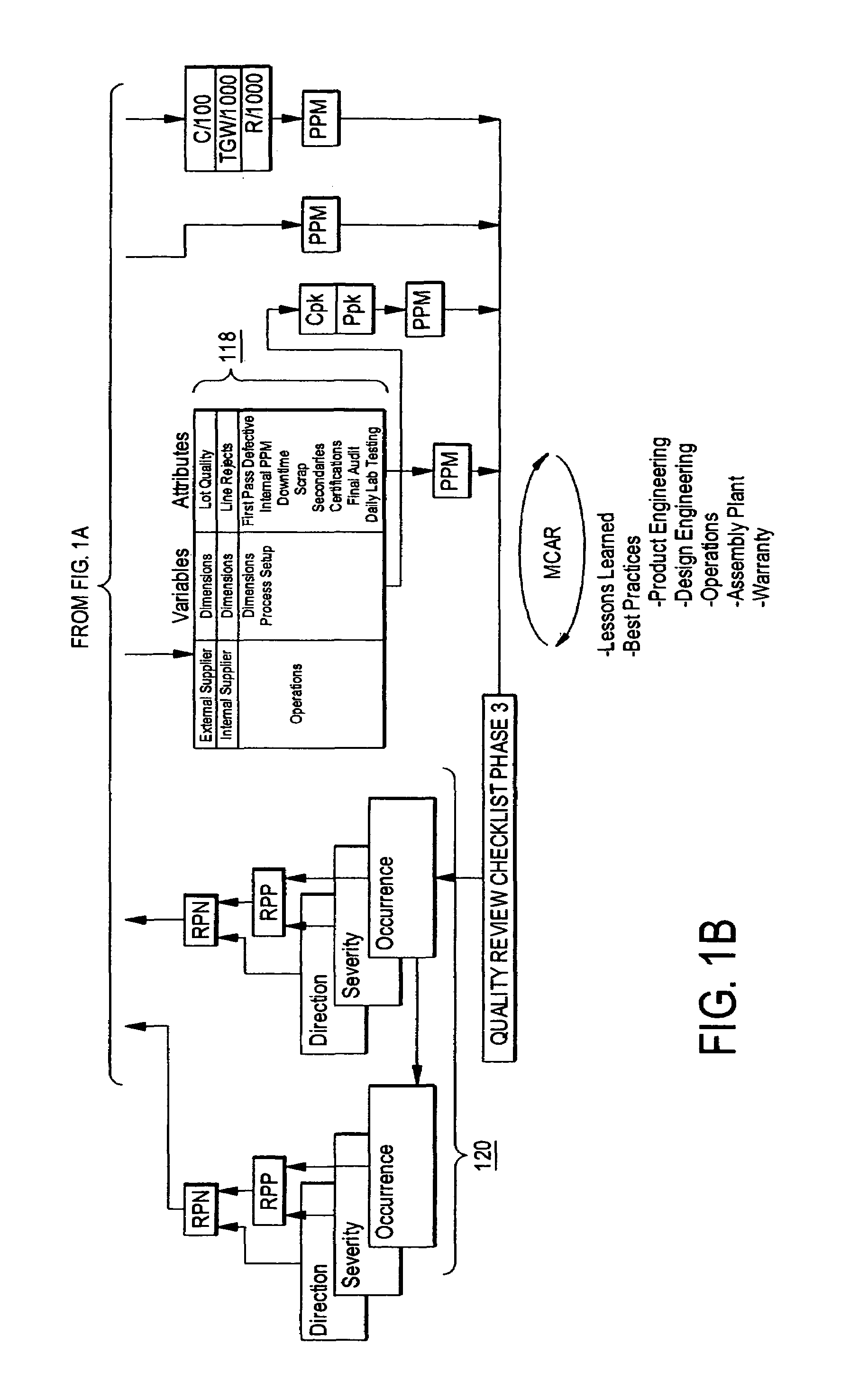
Design control document linking template
InactiveUS7096082B1Facilitate consistent entryWork lessFinanceAnimal feeding devicesOriginal dataElectronic form
A control document template streamlines the creation of control documents and facilitates consistent entry of data. A multi-page spreadsheet file incorporates the design and process failure mode effects analysis pages, the control plan, tools for forming the process flow diagram, the work instructions, and the packaging specifications. A macro sorts the failure mode effects analysis pages by risk priority number without overwriting the original data.
Owner:METHODE ELETRONICS INC
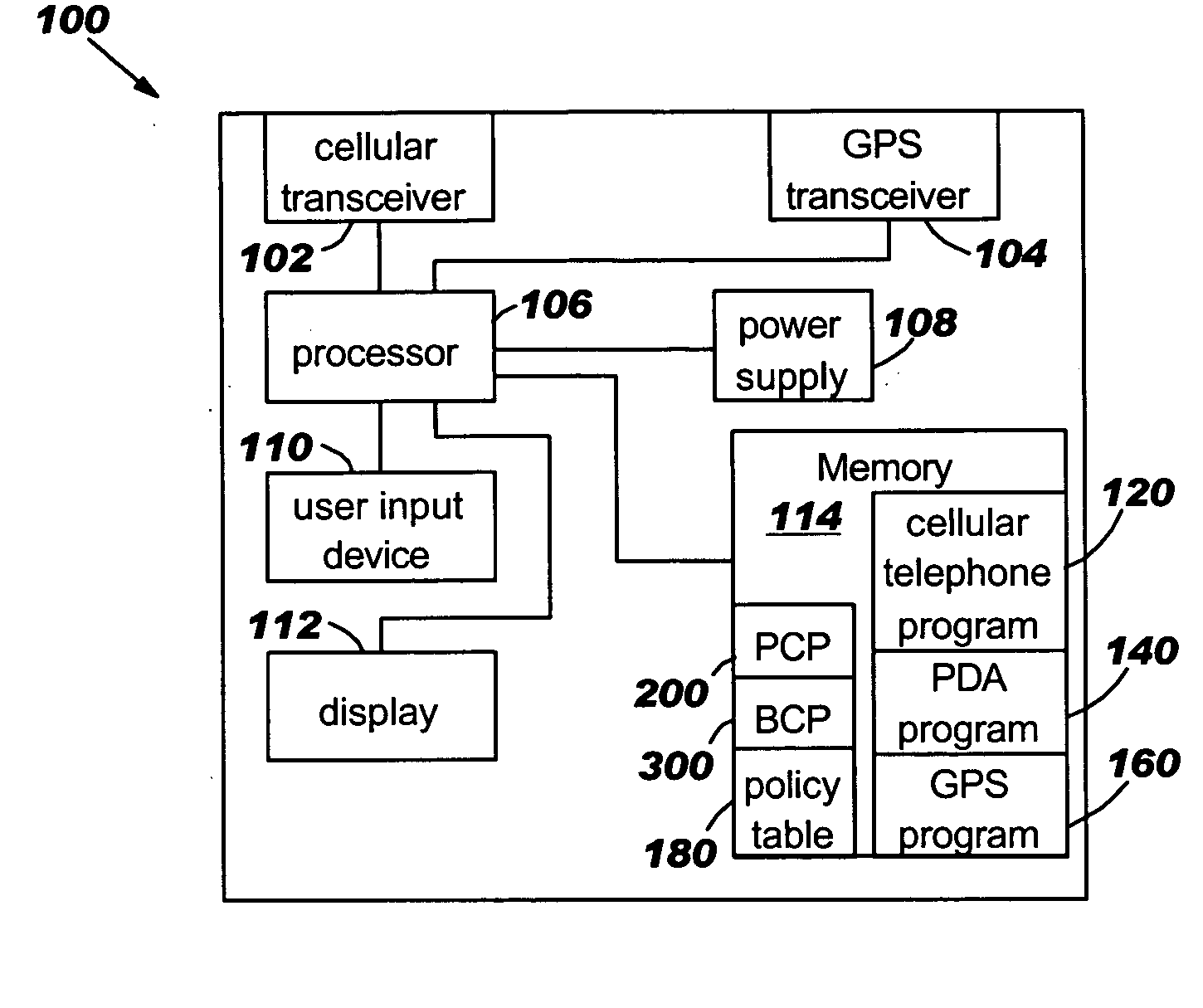
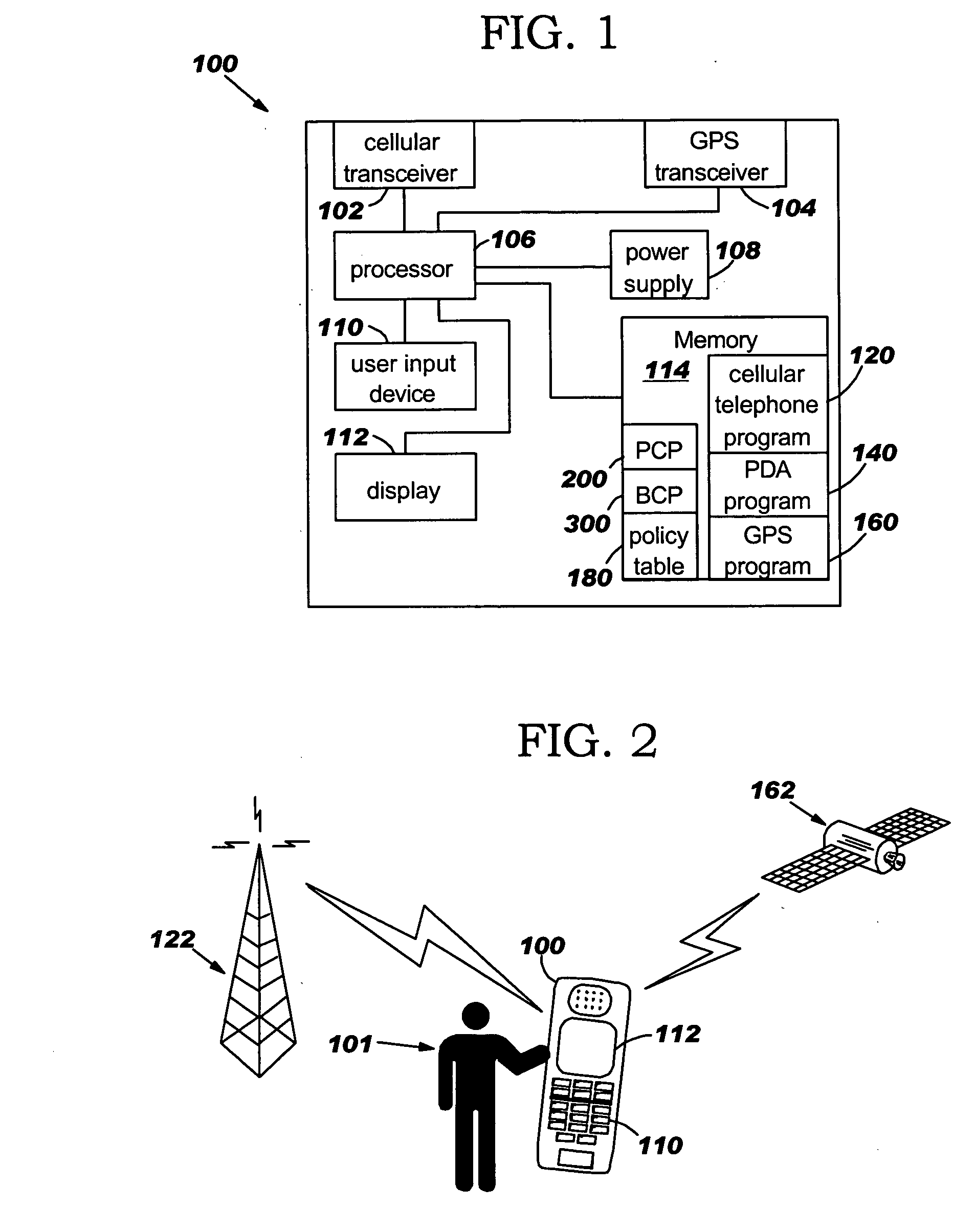
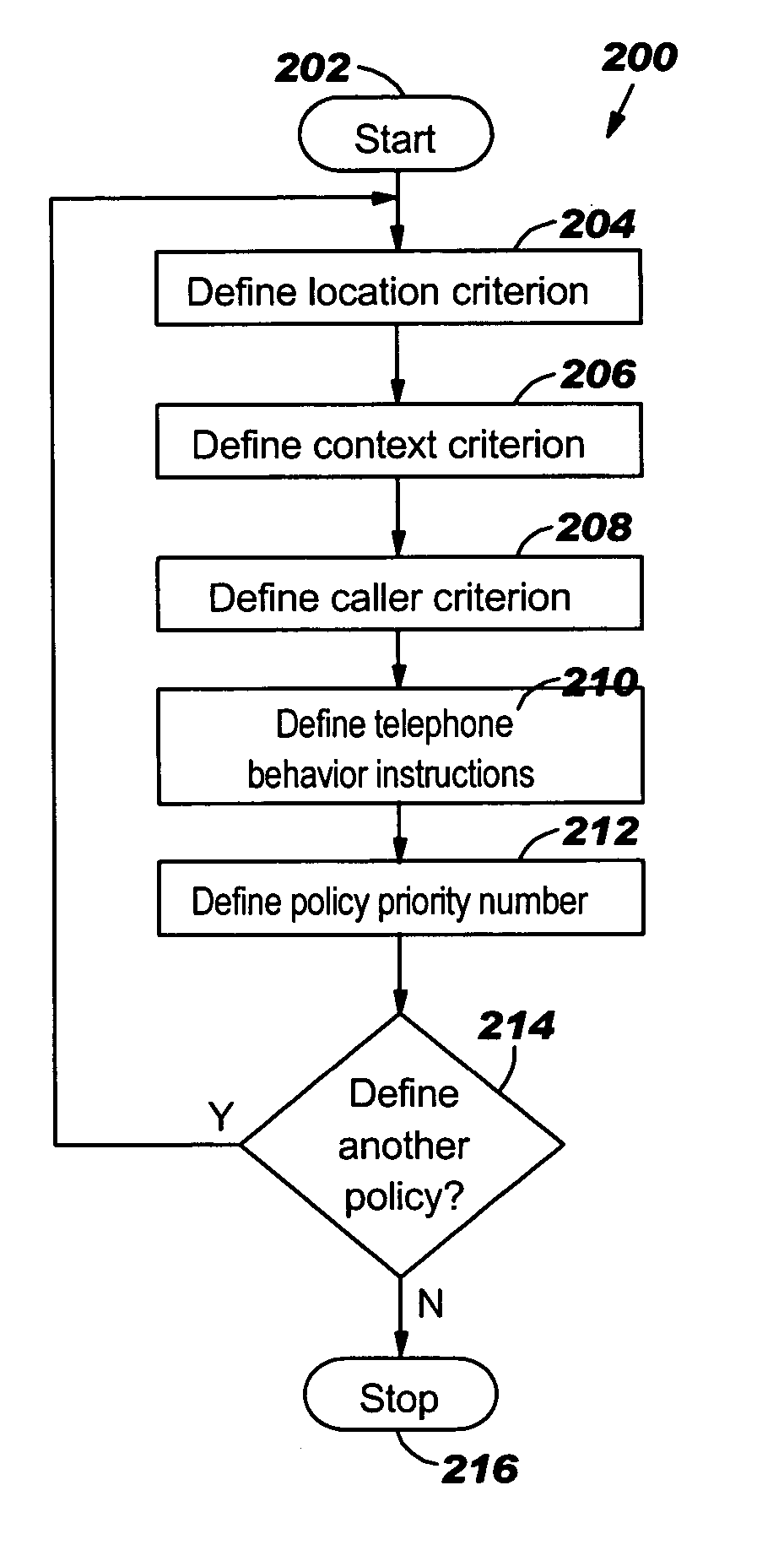
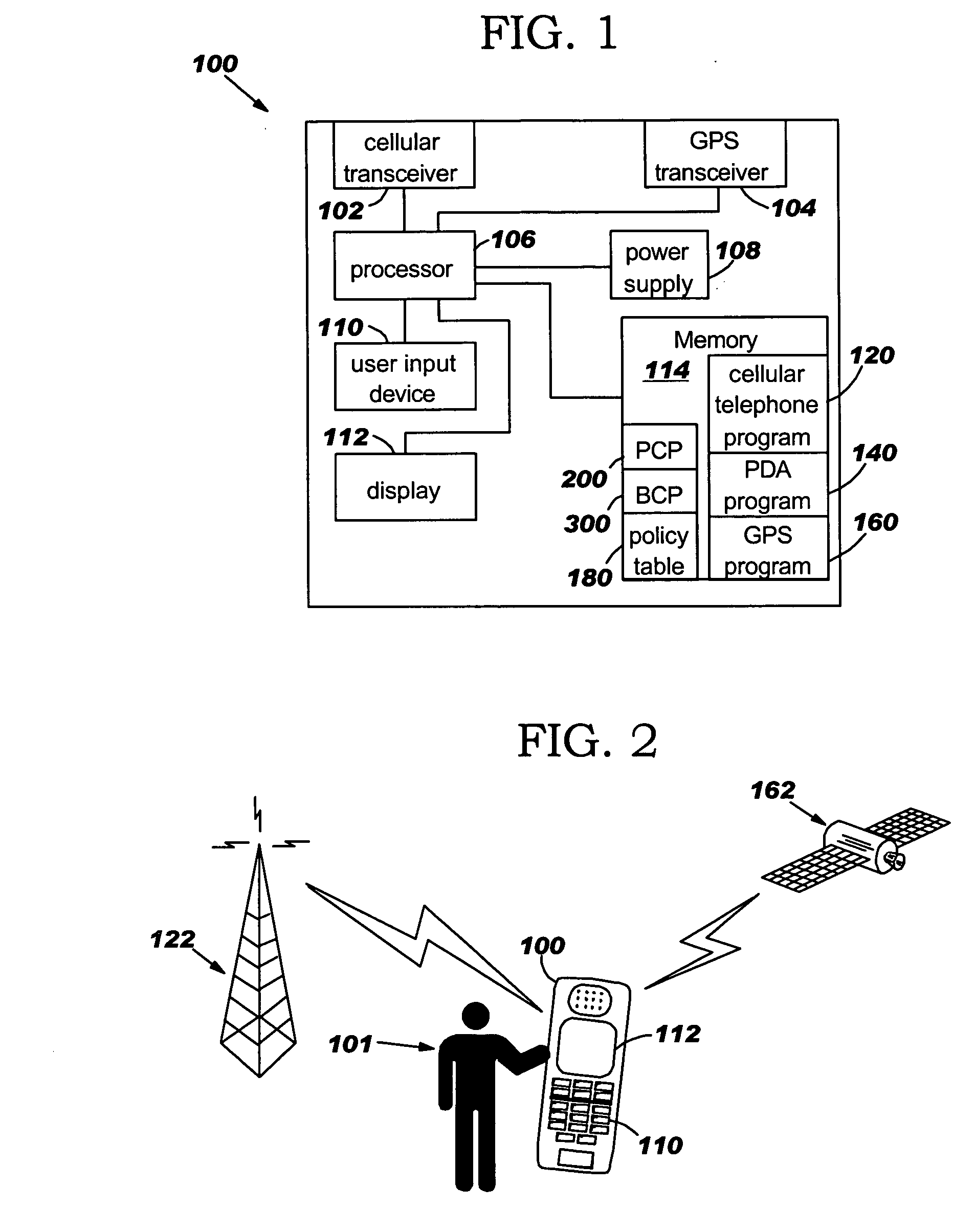
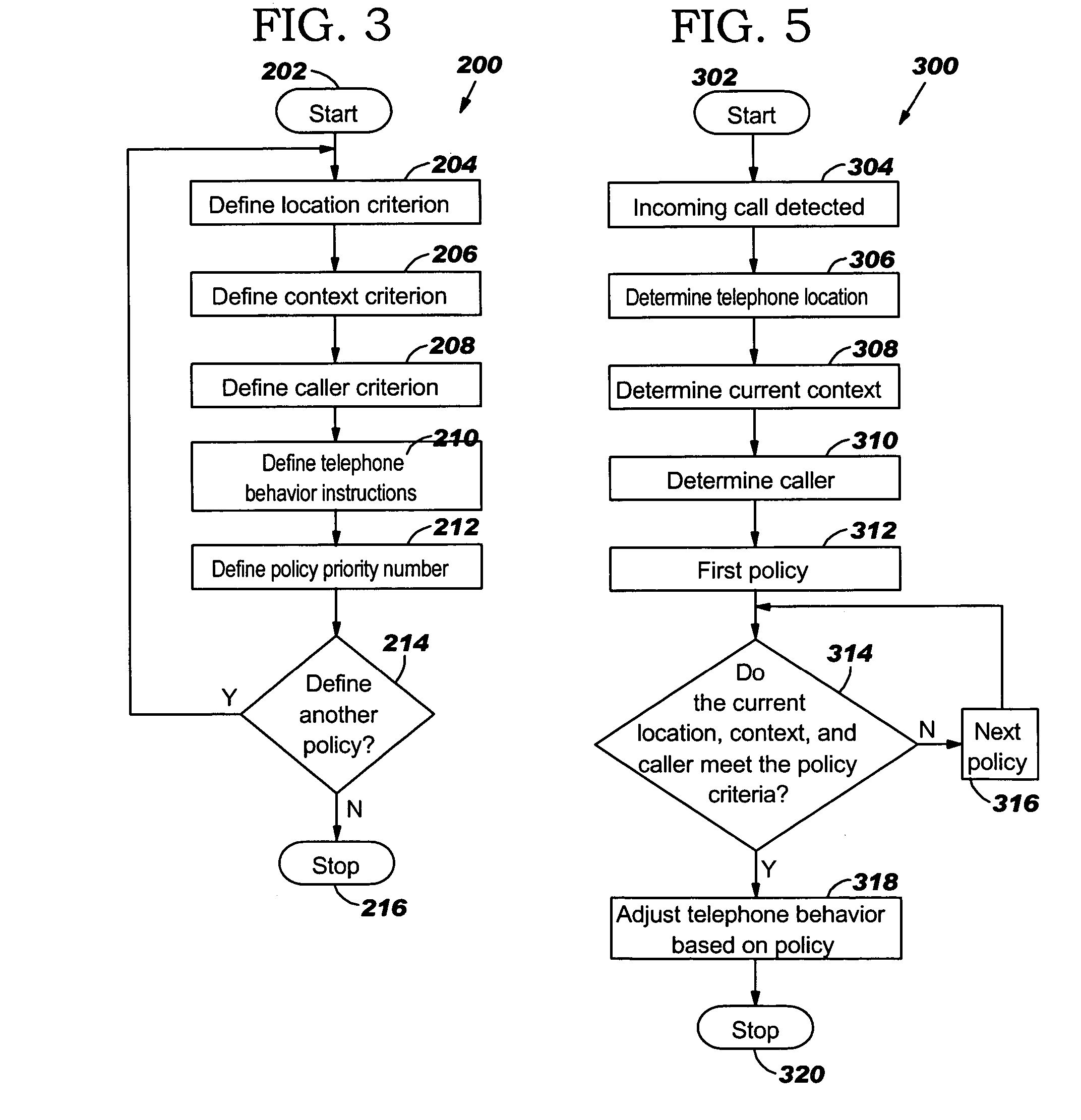
Environmentally driven phone behavior
InactiveUS20050197138A1Current supply arrangementsCalling susbscriber number recording/indicationBehavior controlOperating system
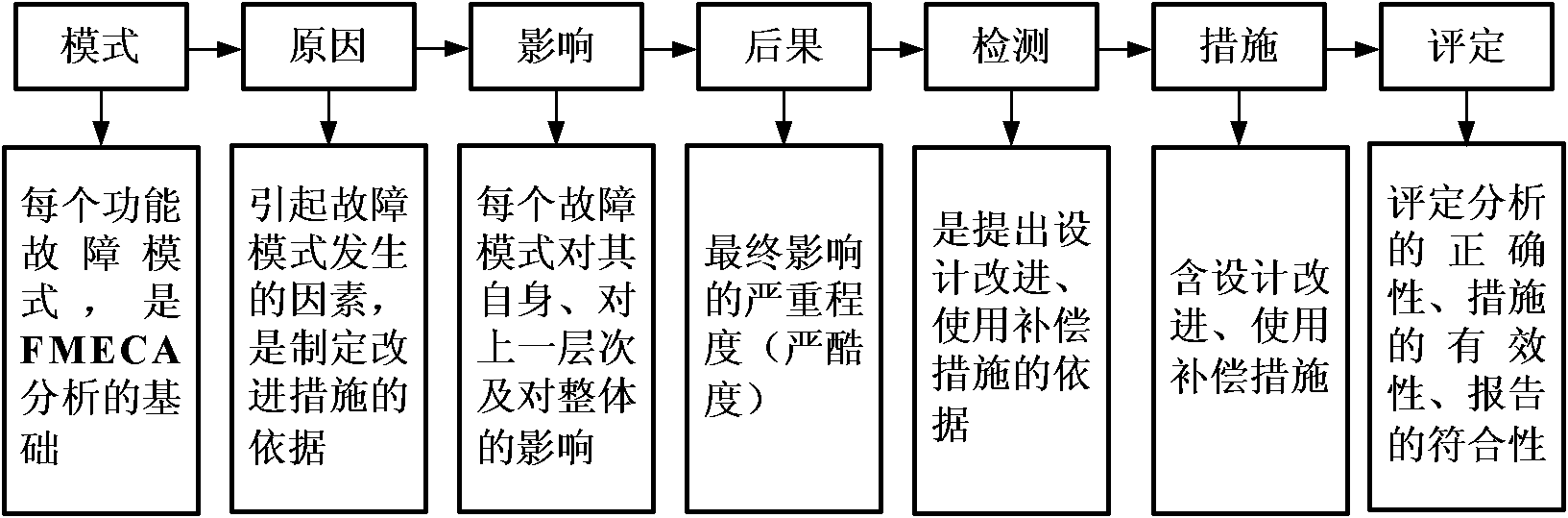
A method for controlling the behavior of a telephone using policies, the method comprising a Policy Creation Program (PCP) and a Behavior Control Program (BCP). The policies comprise telephone behavior instructions and three criteria conditions: location criteria, context criteria, and caller criteria. Each policy is also assigned a policy priority number based on the importance of the policy, which is used to resolve conflicts between the policies. The PCP allows the user to create the policies and stores the policies in a policy table based on the policy priority numbers. The BCP detects an incoming telephone call and determines the location, context, and caller conditions. The BCP compares the location, context, and caller conditions to a plurality of the policies and determines the policy that matches the conditions. The BCP then controls the telephone's behavior according to the telephone behavior instructions in the policy.
Owner:IBM CORP
Failure mode effects and criticality analysis method adopting two RPNs
InactiveCN103186708ASpecial data processing applicationsDesign improvementFailure mode, effects, and criticality analysis
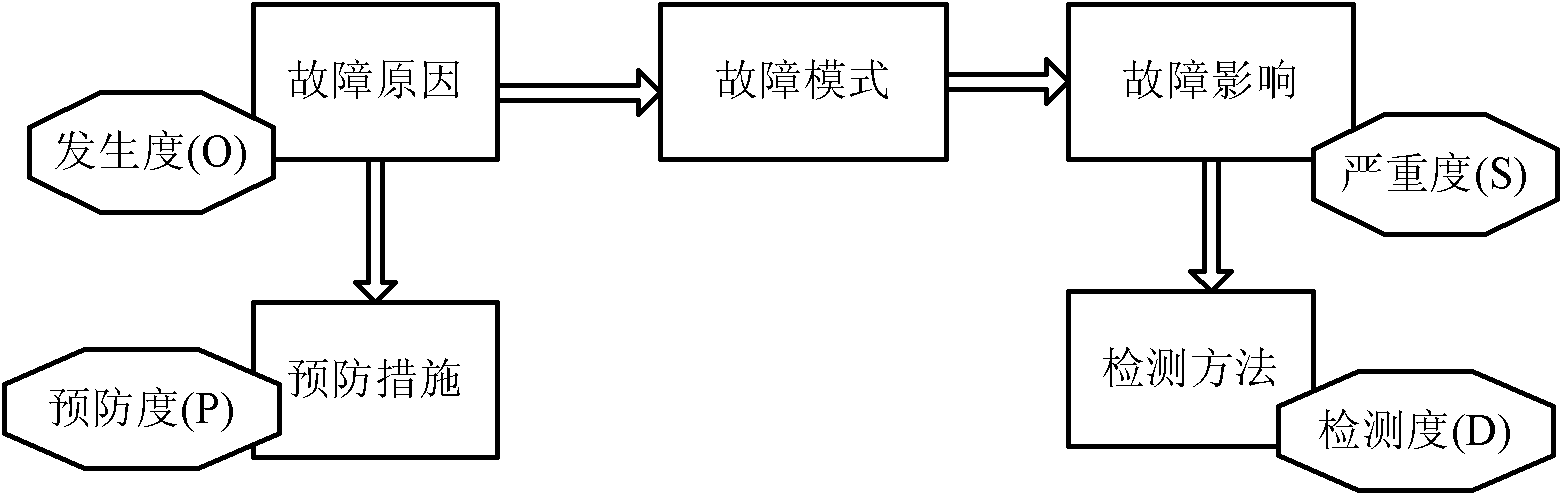
The invention discloses a failure mode effects and criticality analysis method adopting two RPNs (risk priority numbers). The method particularly comprises the steps as follows: grading according to the prevention level and the detection difficulty respectively to obtain failure mode severity and occurrence quantitative indexes, namely an RPN 1 and an RPN 2, wherein the RPN 1 is O*S*P, the RPN 2 is O*S*D, P is the prevention level, O is the failure mode occurrence rank, S is the severity level, and D is the detection difficulty level; and comparing the RPN 1 with the RPN 2 according to the numerical sizes of the two RPNs to obtain failure mode sorting and selection modes. According to the method, the detection difficulty level of failure modes and the prevention level of design improvement to the failure modes are considered when the RPNs are calculated, so that the failure modes are sorted from the aspects of prevention and detection by the obtained two RPNs, the situation of neglection of design improvement due to good detection measure is avoided, and a more comprehensive basis is provided for product design improvement.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Environmentally driven phone behavior
InactiveUS7496352B2Current supply arrangementsCalling susbscriber number recording/indicationOperating systemPriority Number
A method for controlling the behavior of a telephone using policies, the method comprising a Policy Creation Program (PCP) and a Behavior Control Program (BCP). The policies comprise telephone behavior instructions and three criteria conditions: location criteria, context criteria, and caller criteria. Each policy is also assigned a policy priority number based on the importance of the policy, which is used to resolve conflicts between the policies. The PCP allows the user to create the policies and stores the policies in a policy table based on the policy priority numbers. The BCP detects an incoming telephone call and determines the location, context, and caller conditions. The BCP compares the location, context, and caller conditions to a plurality of the policies and determines the policy that matches the conditions. The BCP then controls the telephone's behavior according to the telephone behavior instructions in the policy.
Owner:IBM CORP
System and method for co-operative thermal management of electronic devices within a common housing
InactiveUS6934864B2Energy efficient ICTVolume/mass flow measurementCo operativeReliability engineering
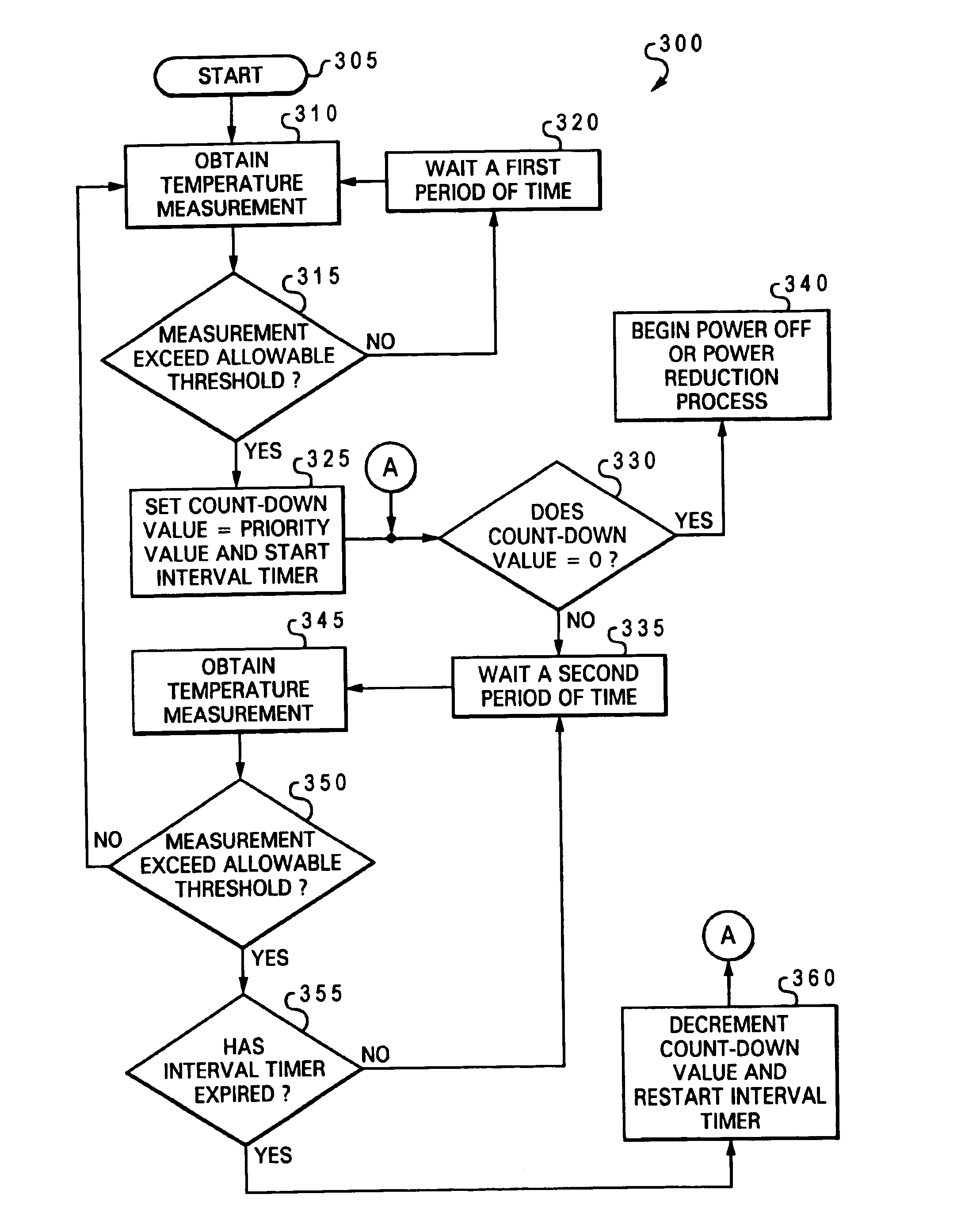
A method for co-operative thermal management of a number of independent electronic devices housed within a common enclosure that includes designating a priority number and measuring a temperature for each of the independent electronic devices. Next, for each of the independent electronic devices, the measured temperature is evaluated to determine if it exceeds a threshold value for the independent electronic device. If the measured temperature exceeds a threshold value, a count-down value is initialize to the designated priority number of the independent electronic device. Following which, the count-down value is evaluated to determine if it is equal to zero. If the count-down value is equal to zero, the independent electronic device is powered down. However, if the count-down value is not equal to zero, a specified time interval is allowed to expire before the count-down value is decremented and re-evaluated to determine if it is equal to zero.
Owner:IBM CORP
Method and system for limiting speed of token bucket based on priority
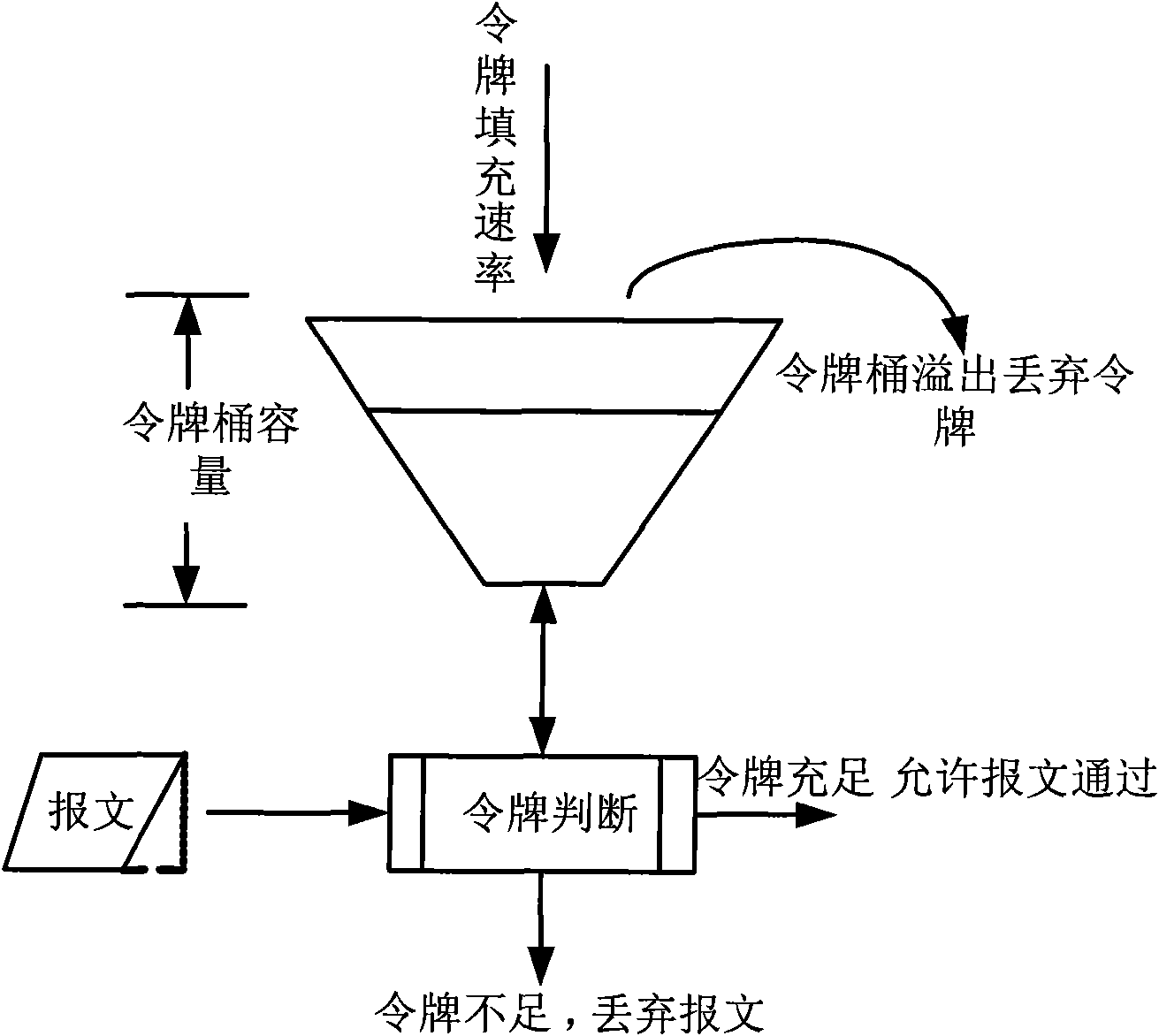
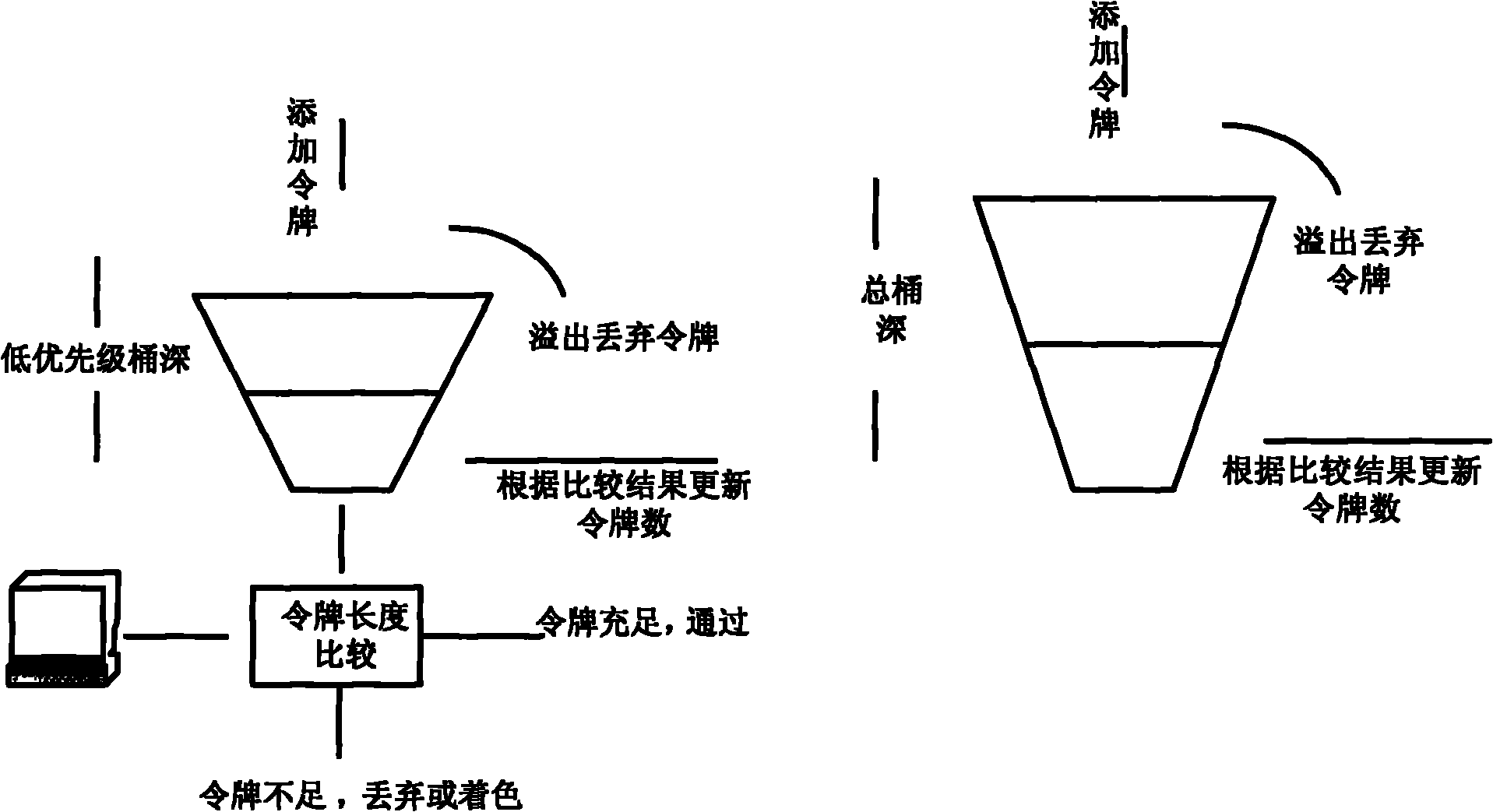
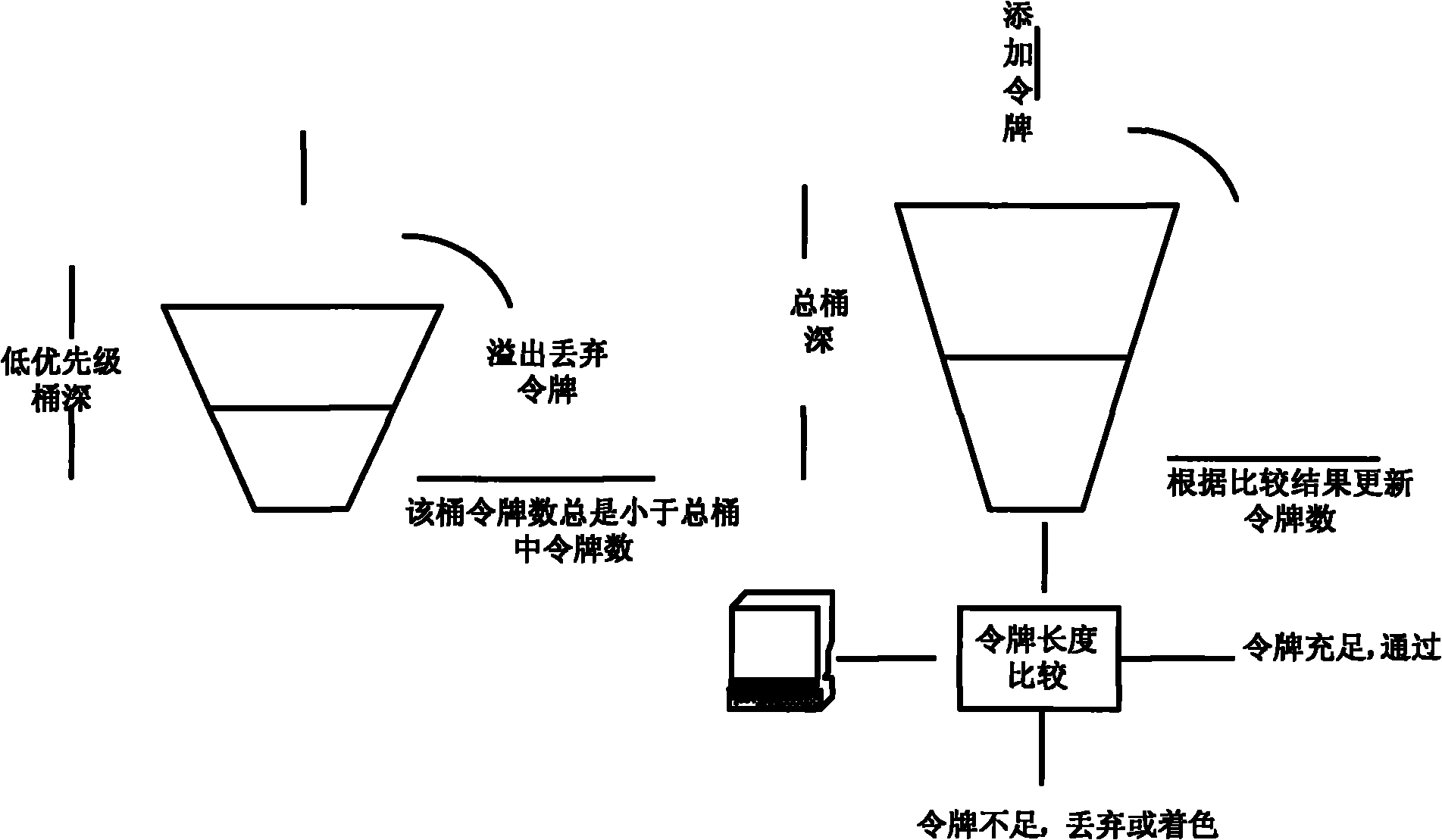
ActiveCN101997766AHigh probability of discardingAvoid the problem of random dropData switching networksDistributed computingSpeed limit
The invention discloses a method and a system for limiting speed of a token bucket based on priority. The method comprises the following steps of: configuring speed limiting parameters of a message according to the attribute of the message, wherein the speed limiting parameters comprise a speed limiting value and gradually decreased depths of token buckets at different stages, and ensuring that the token number in the token bucket at the highest stage is greater than or equal to sum of the token numbers in the token buckets at the rest stages of the token buckets; calculating the token number to be added after receiving the message; limiting the speed of the current message by using the token bucket at the highest stage when determining that priority speed limiting is not needed; limiting the speed of the current message by using the token bucket corresponding to the number of stages of the current message for the messages with the same priority number of the message as the speed limiting stage number when determining that priority speed limiting is needed; and limiting the speed of the current message for the messages with different priority stage of the message from the speed limiting stage number by using the token bucket at the highest stage. Through the method and the system, different messages have different discard probabilities under the condition of the same speed limiting condition, and the service quality of a network is improved.
Owner:SANECHIPS TECH CO LTD
Data center network transmission layer stream data transmission method based on priority
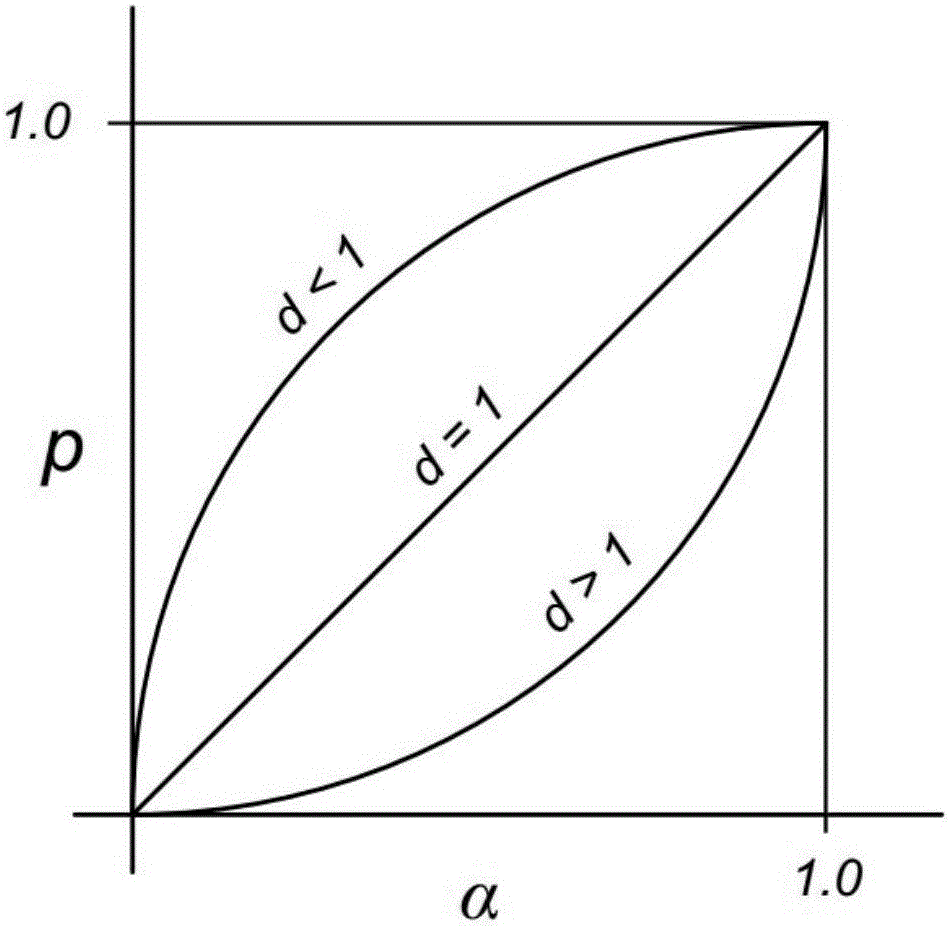
InactiveCN105827540AImprove throughputReduce transmission delayData switching networksData streamData center
The invention discloses a data center network transmission layer stream data transmission method based on priority. The method comprises steps that S1, data flows transmitted by a data center network are classified into small data flows and large data flows; S2, the priority number pri of the small data flows is calculated; S3, weight w of the small data flows is calculated; S4, a congestion degree alpha of the present network is calculated; S5, whether the present network is in a congestion state is determined, if yes, a step S6 is actuated; if not, a step S7 is actuated; S6, results of the steps S2, S3 and S4 are substituted into a Gamma function formula to reduce the size of a data flow congestion degree window; S7, the result of the step S3 is substituted into the formula to enlarge the size of the data flow congestion degree window; and S8, the data flows are sent according to the updated window. Through the method, transmission delay of the small data flows can be not reduced on the condition that an application level is not required to prompt parameters such as the volume of the data flows, and the integral high throughput of the network can be further maintained.
Owner:SHENZHEN GRADUATE SCHOOL TSINGHUA UNIV
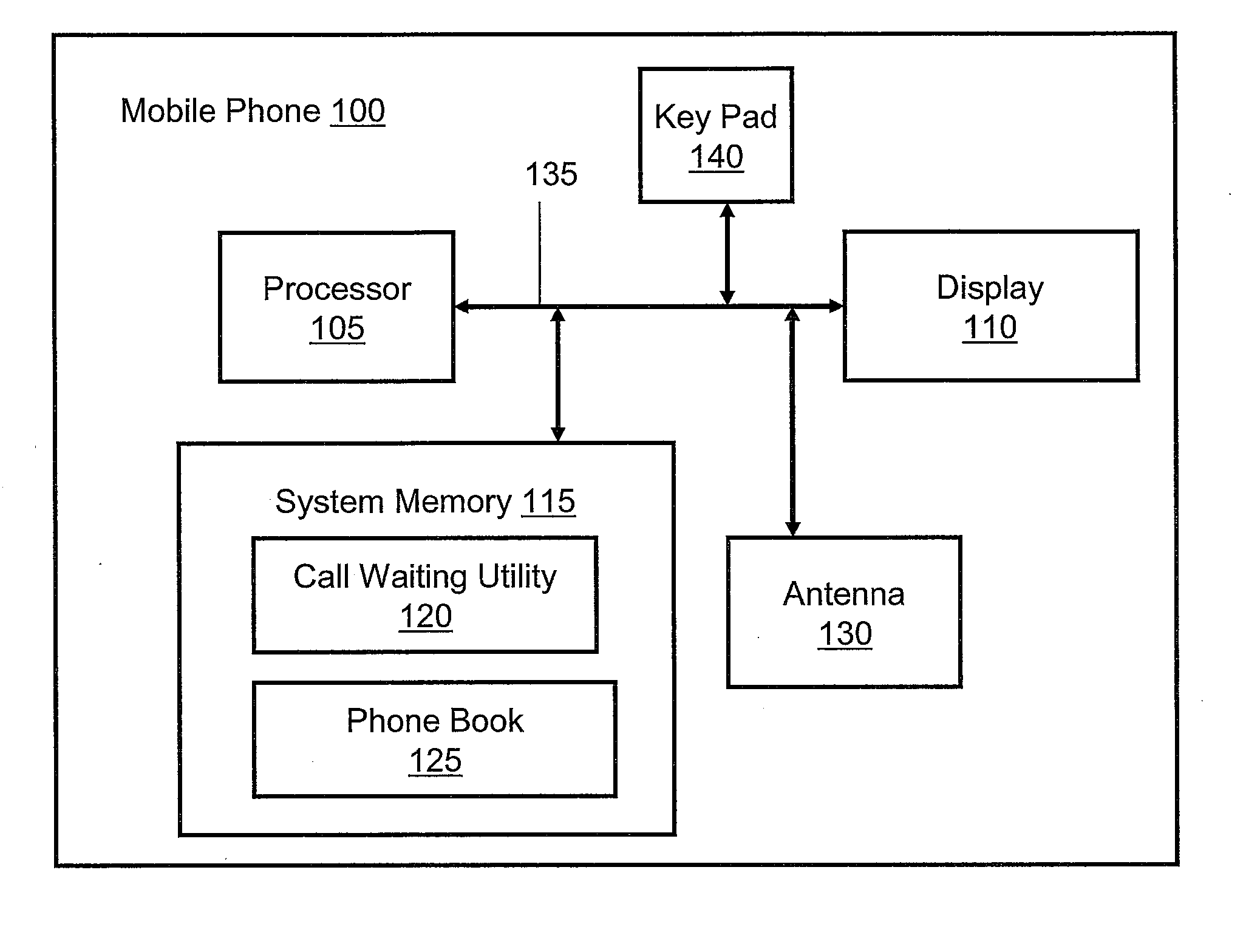
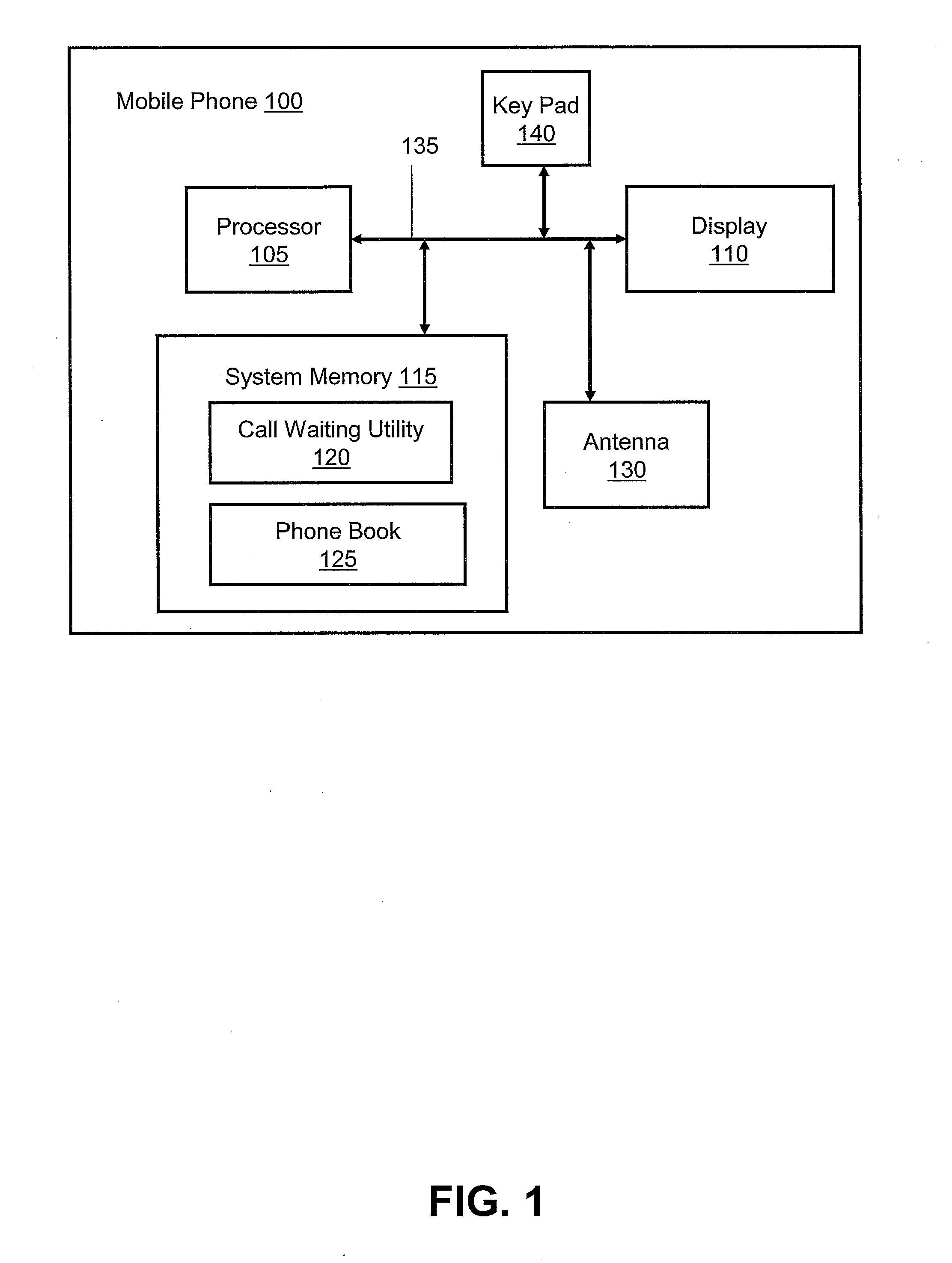
Method and system for assigning call waiting priorities to phone numbers
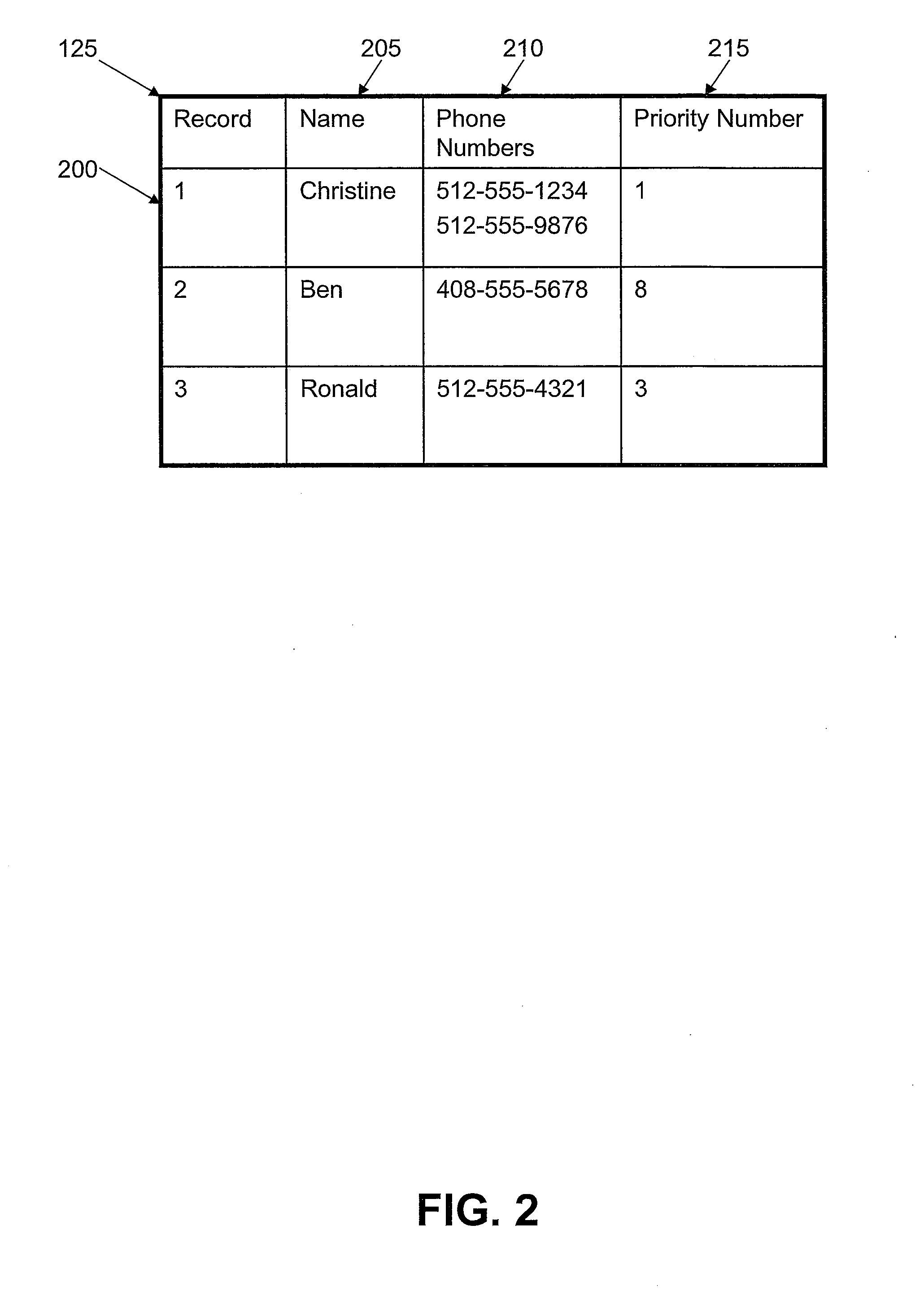
A method for enabling a mobile phone to control the automatic activation / deactivation of the call waiting feature in real time through the use of customized pre-set user preferences. The mobile phone contains a database with multiple records for people and / or businesses known to the user. Within each record, the user may define a priority number. Each priority number is a scaled integer value, with low priority numbers representing a high priority record and high priority numbers representing low priority records. If the mobile phone detects an incoming call while a call is already in progress, a call waiting utility notifies the user of the incoming call if the incoming call corresponds to a preset priority number that is less than or equal to the priority number of the current call. Otherwise, the incoming call is directed to the user's voicemail system without interrupting the current call.
Owner:IBM CORP
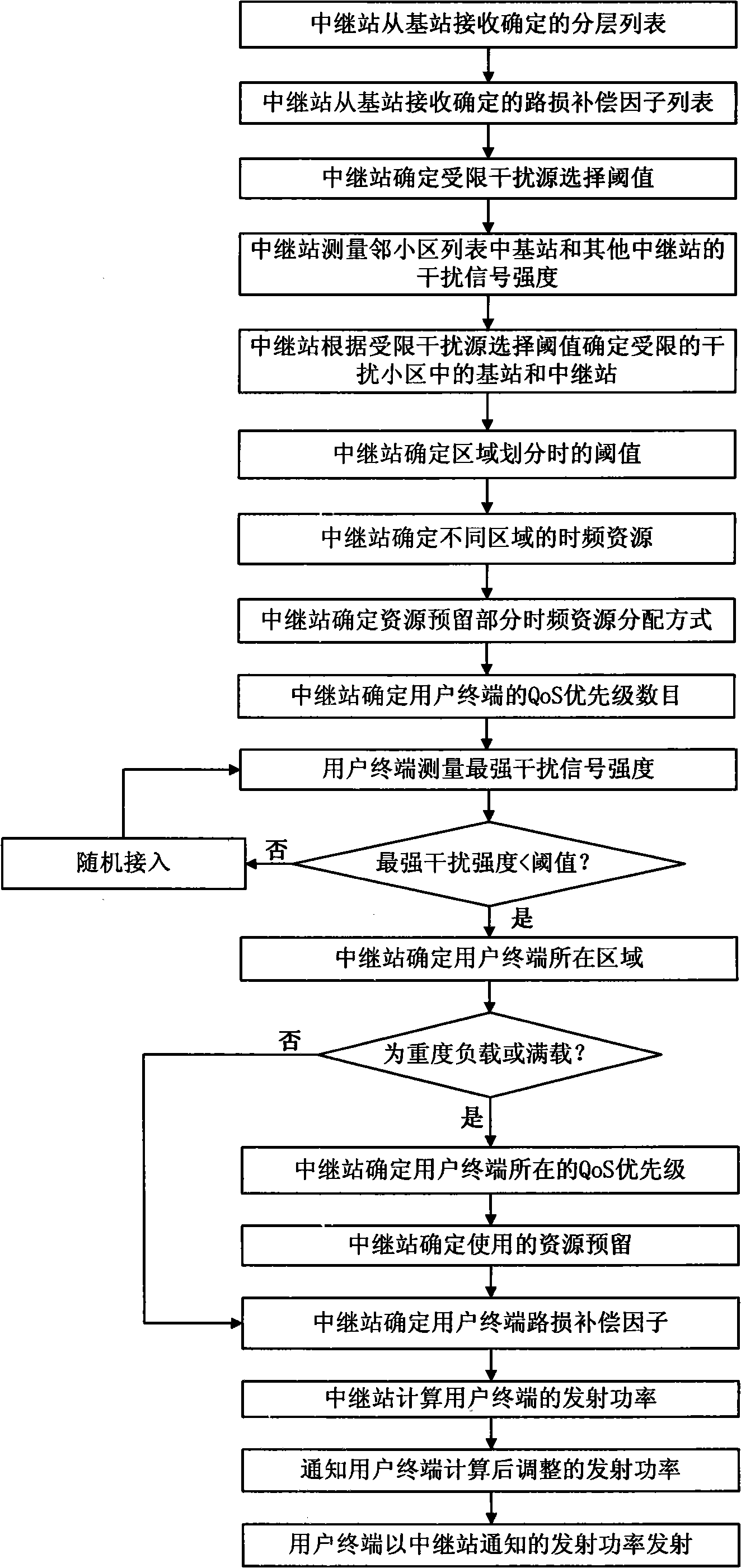
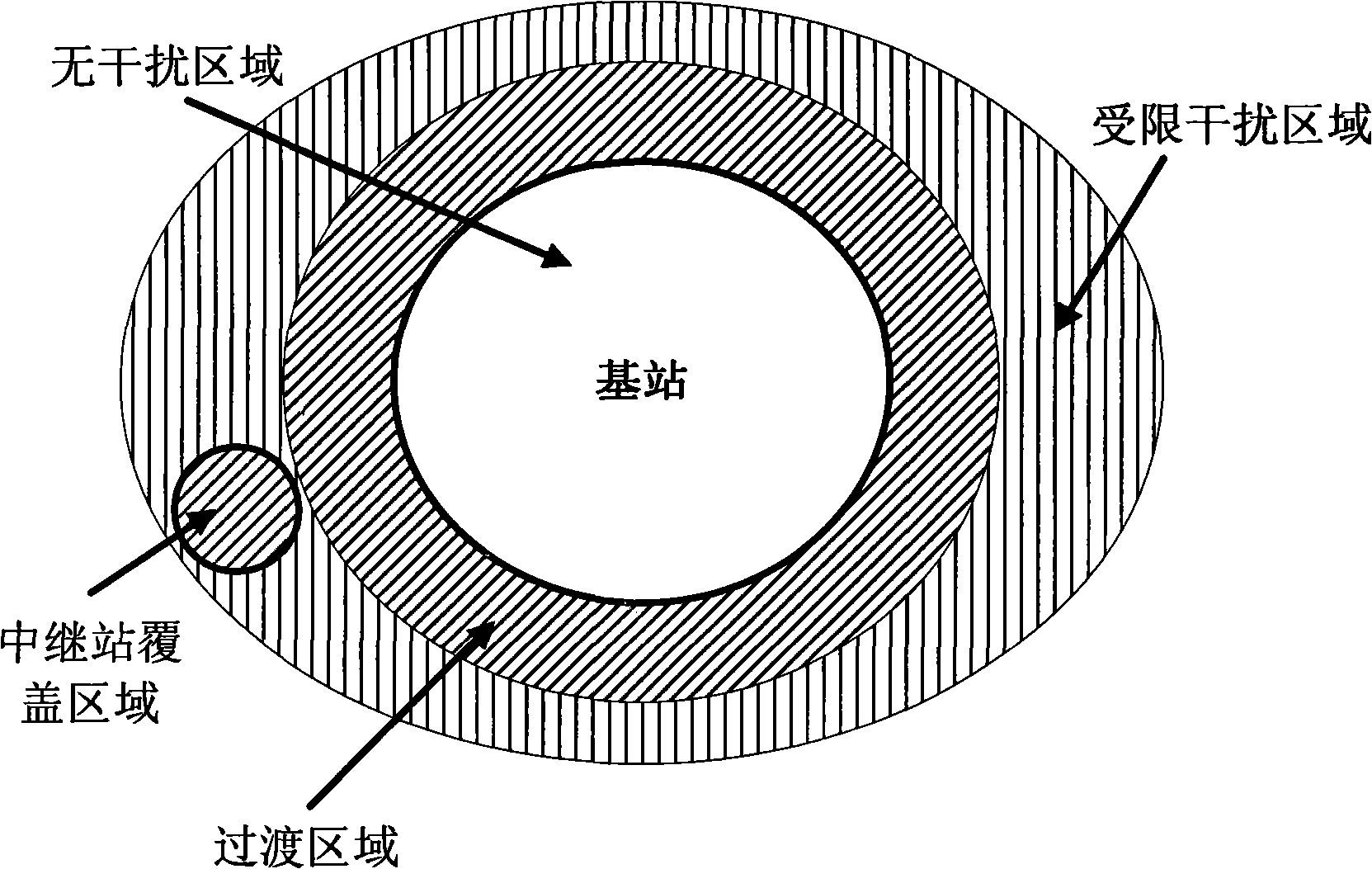
Method for coordinating interference between districts of relay wireless communication network
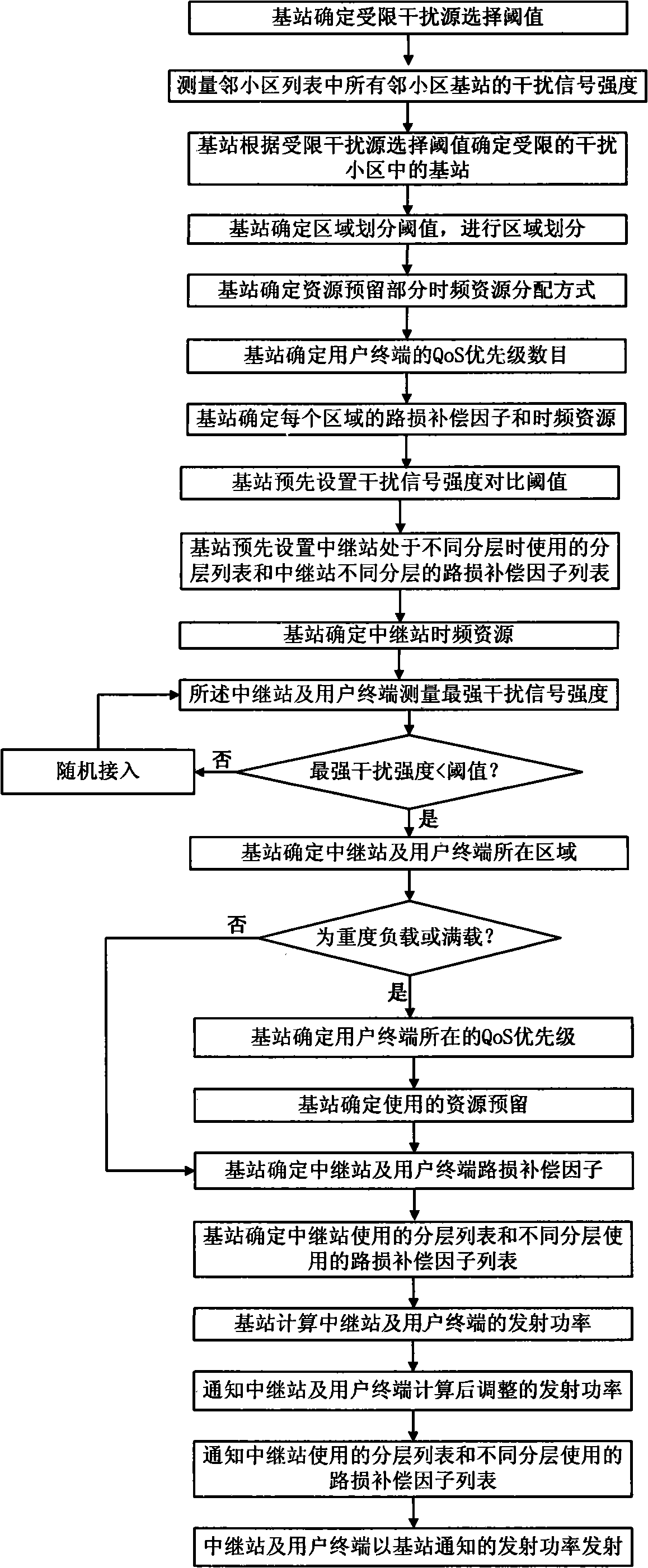
InactiveCN101494899AImprove throughputAverage throughputPower managementTransmission control/equalisingQuality of serviceFlexible scheduling
The invention relates to an inter-cell interference coordination method in radio communication network with relay station, including the interference coordination to base station covering area and relay station covering area. The method comprises: firstly, selecting limited interference source; then, dividing the cell including the limited interference source into several layers, and setting resources reservation distribution mode, service quality priority number and link loss compensation factor; finally, determining to start the random accessing process or the power adjusting process according to interference signal intensity. When the time frequency resource in the limited interference source distributed area is in heavy load or full load, and the flexible scheduling and separating of the time frequency resource is different from that of the time frequency resource of the limited interference source, The limited interference source selection, area dividing and time frequency resource distribution mode in the invention are beneficial to ensure the time frequency resource orthogonal, reduce inter-cell interference, and guarantees service quality while meets the minimum service quality.
Owner:ZTE CORP
Content addressable memory with block-programmable mask write mode, word width and priority
InactiveUS20020129198A1Counting chain synchronous pulse countersDigital storageCamTernary content addressable memory
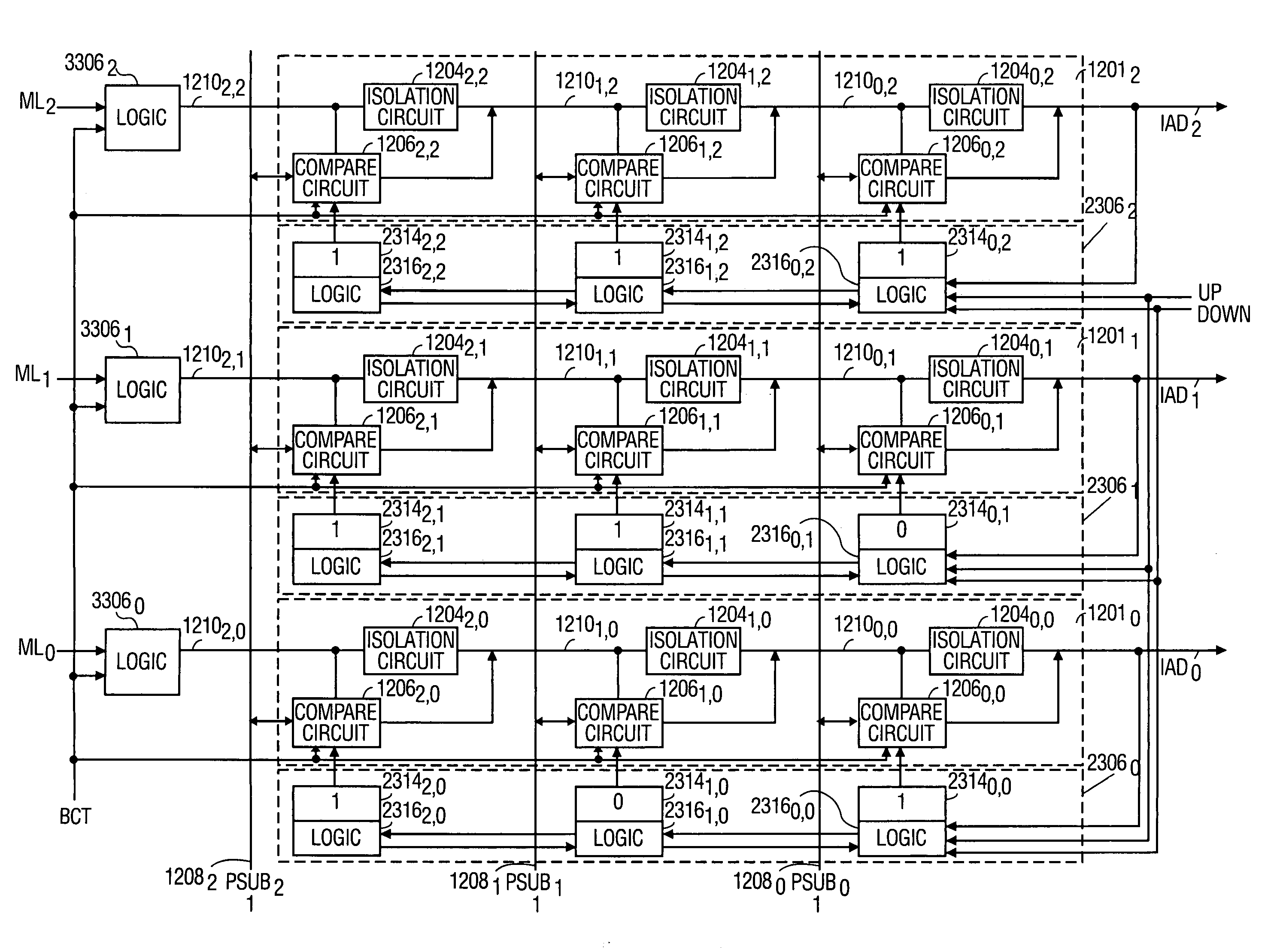
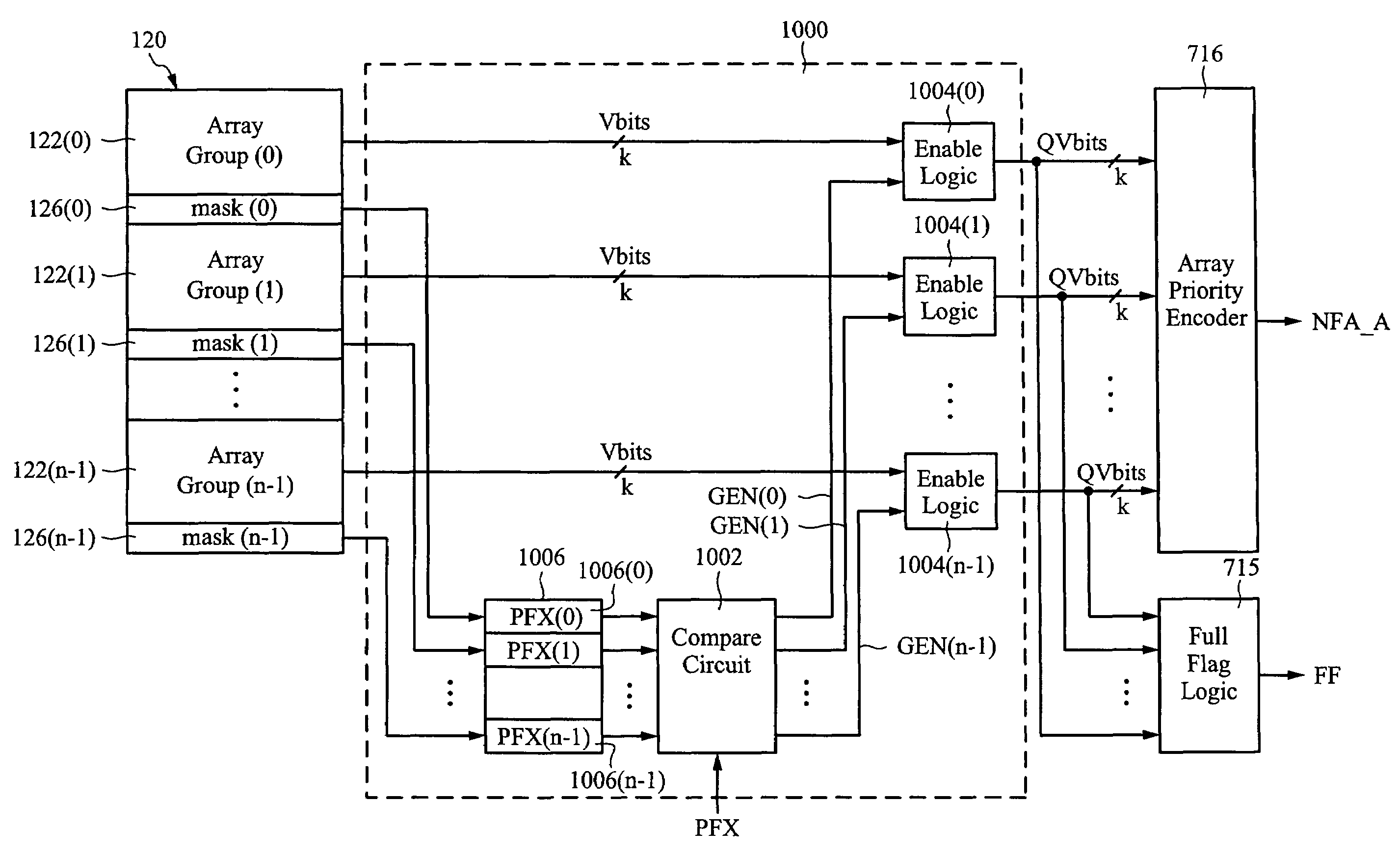
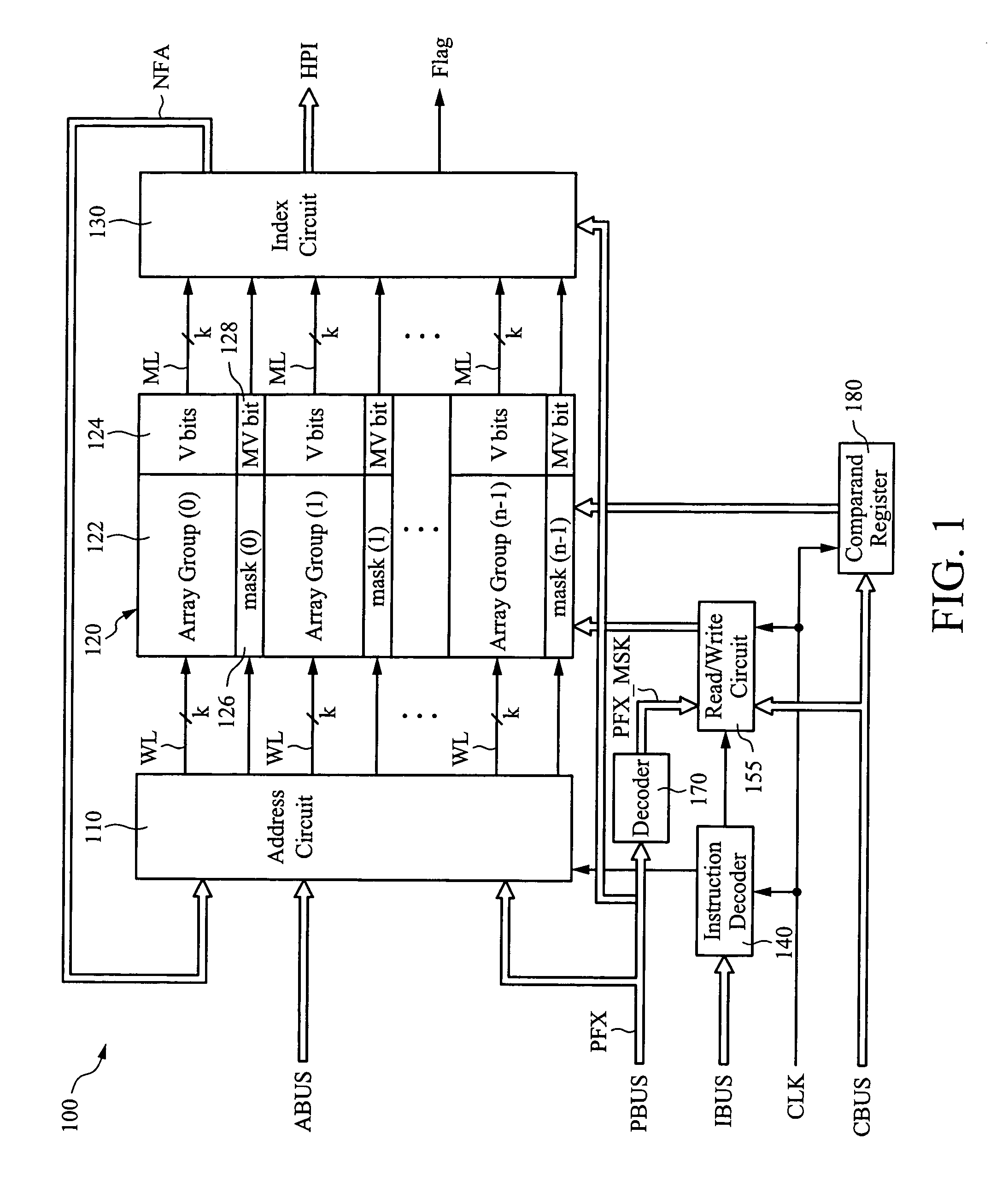
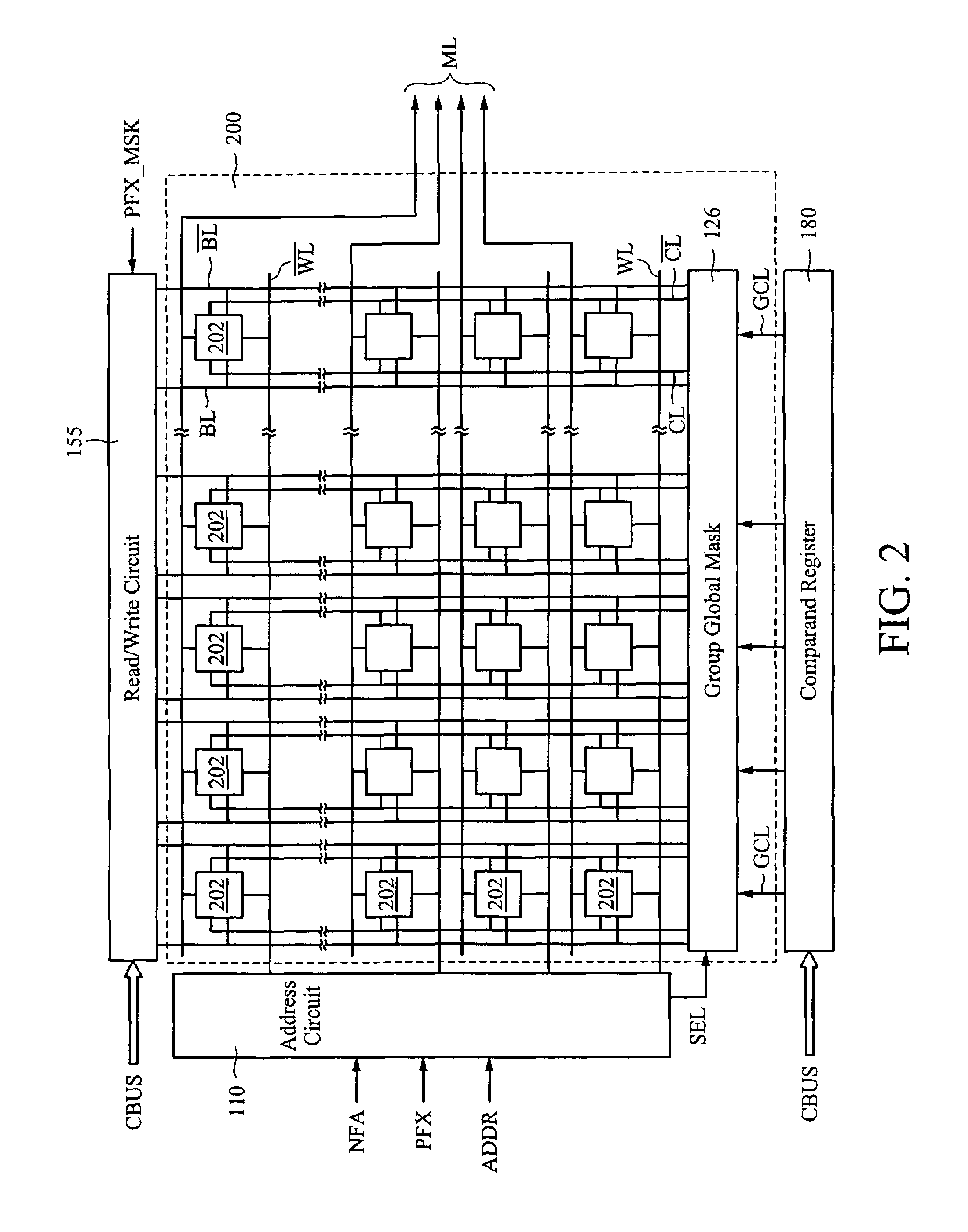
A content addressable memory (CAM) device comprising a plurality of CAM blocks and a block control circuit. The plurality of CAM blocks each includes an array of CAM cells to store data words and an array of priority number storage circuits to store priority numbers. Each priority number indicates a priority of a respective one of the data words relative to others of the data words. The block control circuit has an input to receive a class code and circuitry to output a plurality of select signals to the plurality of CAM blocks. Each select signal selectively disables a respective one of the plurality of CAM blocks from participating in a compare operation according to the class code.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Self-adapting binary tree multi- label collision intermediation method for RFID system
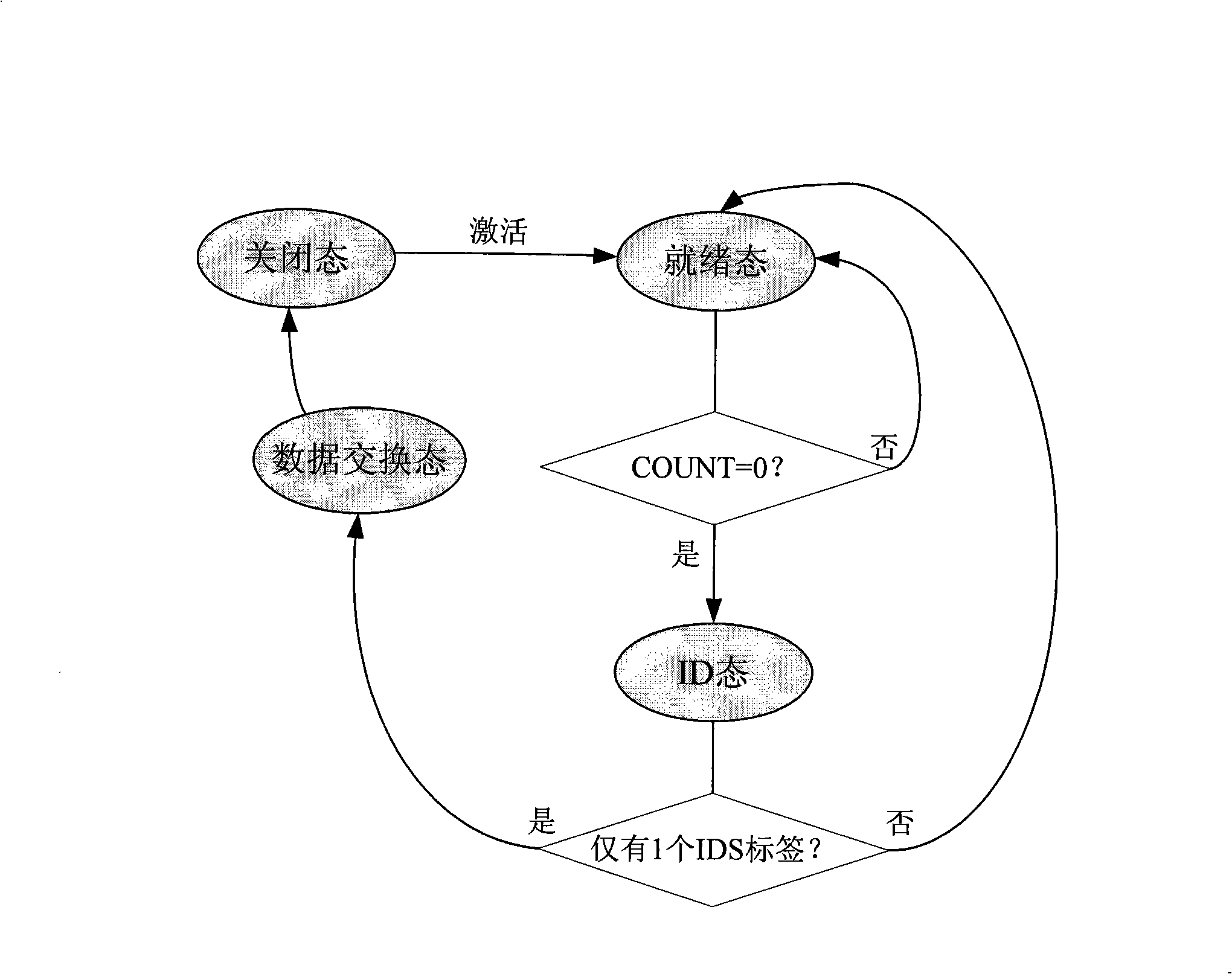
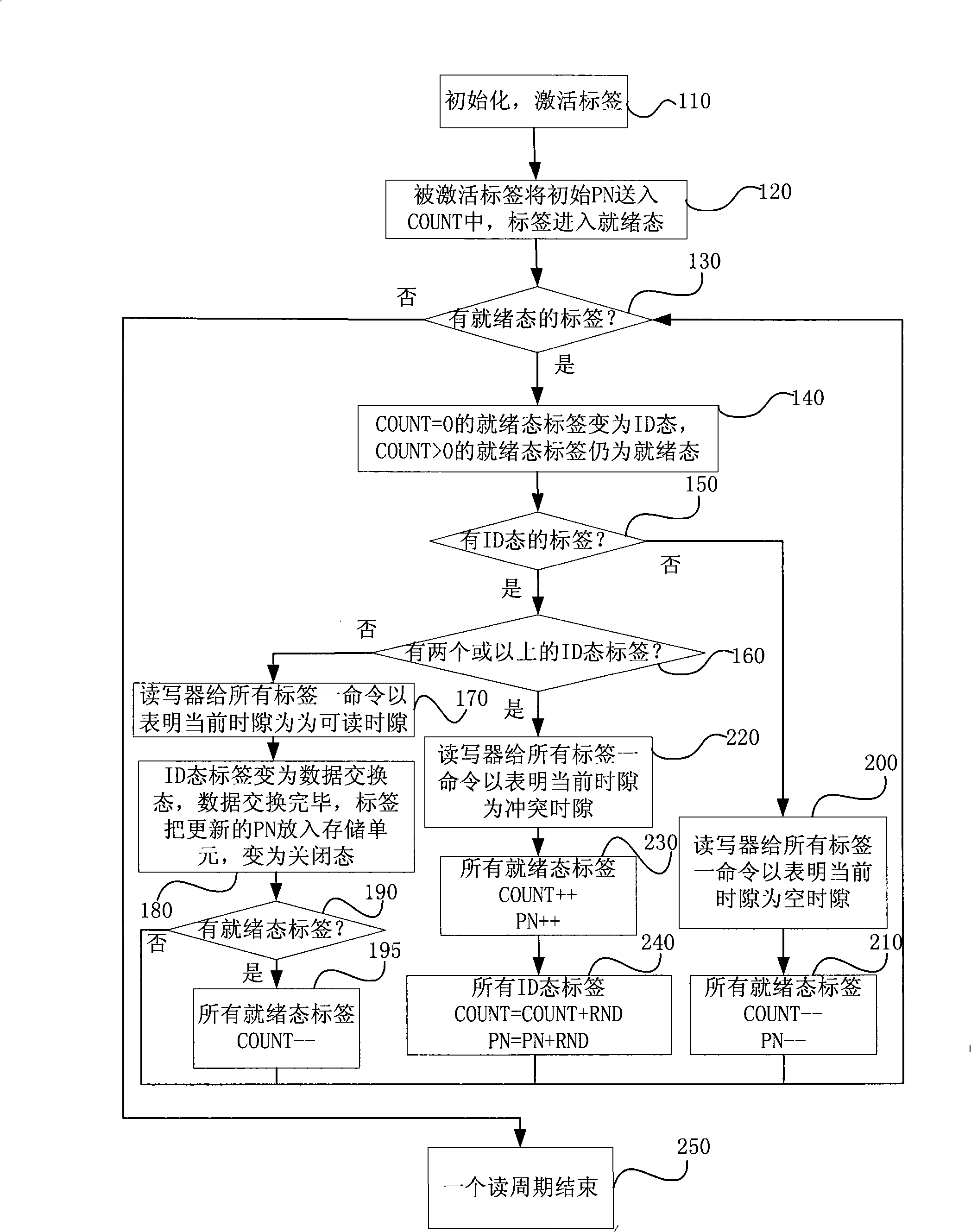
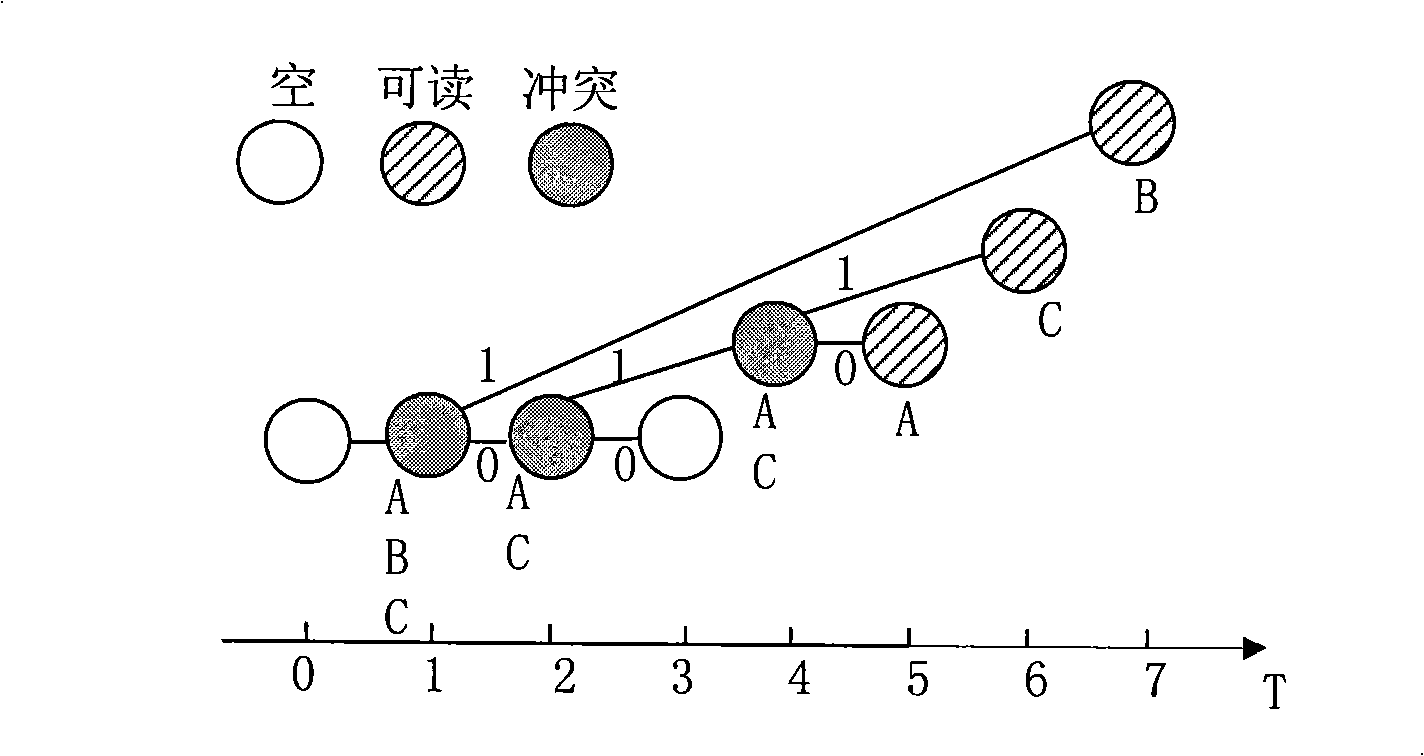
ActiveCN101334830AReduce the number of conflictsReduce conflictSensing record carriersIdle timeBinary tree
The invention discloses a self-adaptive binary tree multi-label conflict arbitration method used for a RFID system comprising a reader and at least two labels in the coverage area of the reader. The reader sends out an instruction and the labels execute corresponding operation after receiving the instruction. The labels are provided with four states, i.e. close, ready, ID and data exchanging and can adopt a counter and a random number generator to execute the state shifting according to the present time slot state to realize the binary tree method so as to avoid the conflict between labels. The storage of each label stores a priority number which can determine when the label can be communicated with the reader in a reading circle and the priority number in each reading circle can make self-adaptive adjustment according to the present time slot state so as to reduce conflict and idle time slot. The application of the invention to the RFID multi-label conflict can largely reduce conflict arbitration time and avoid the problems of label reading leakage and unlimited extension of the reading circle.
Owner:YUNNAN KUNMING SHIPBUILDING DESIGN & RESEARCH INSTITUTE
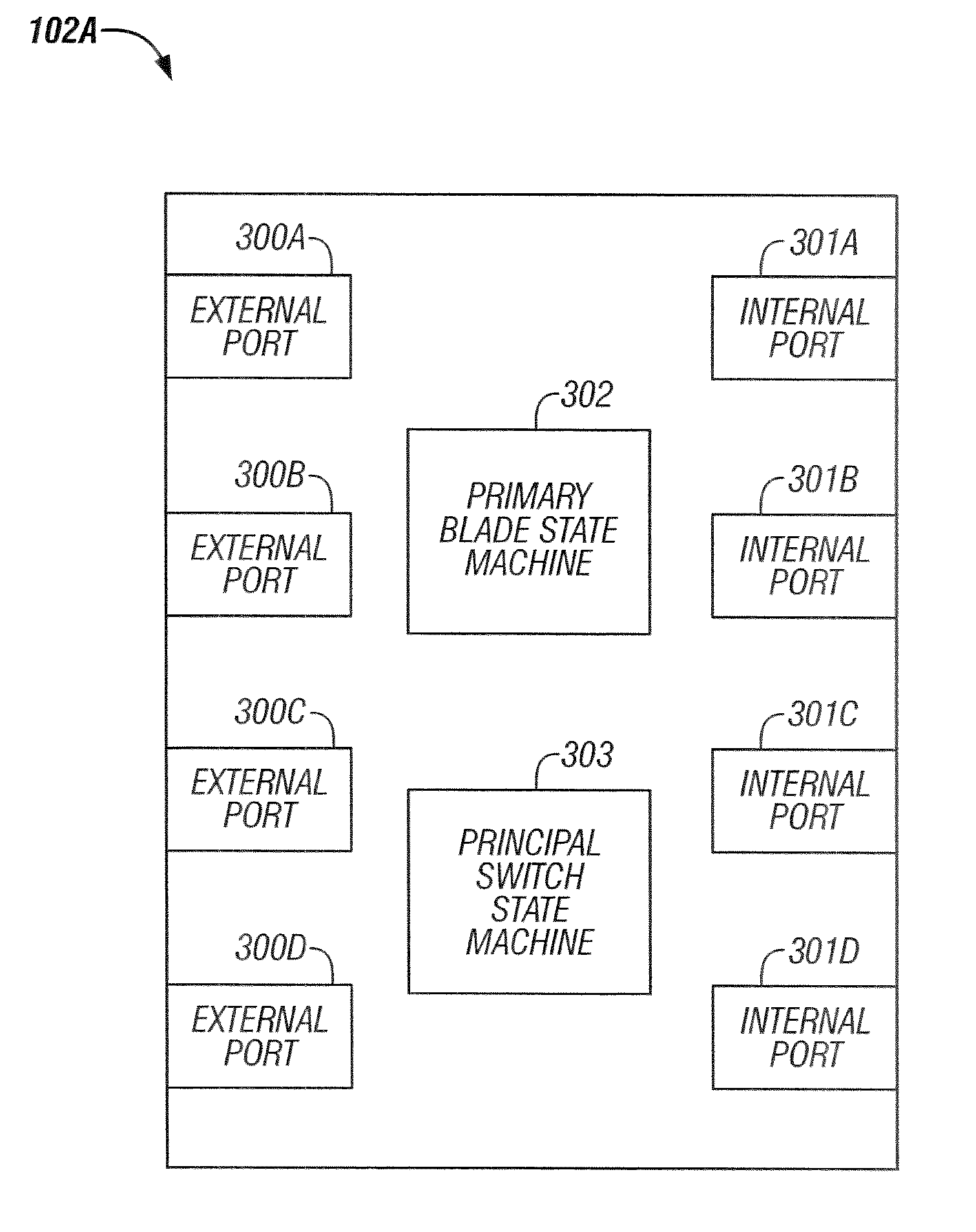
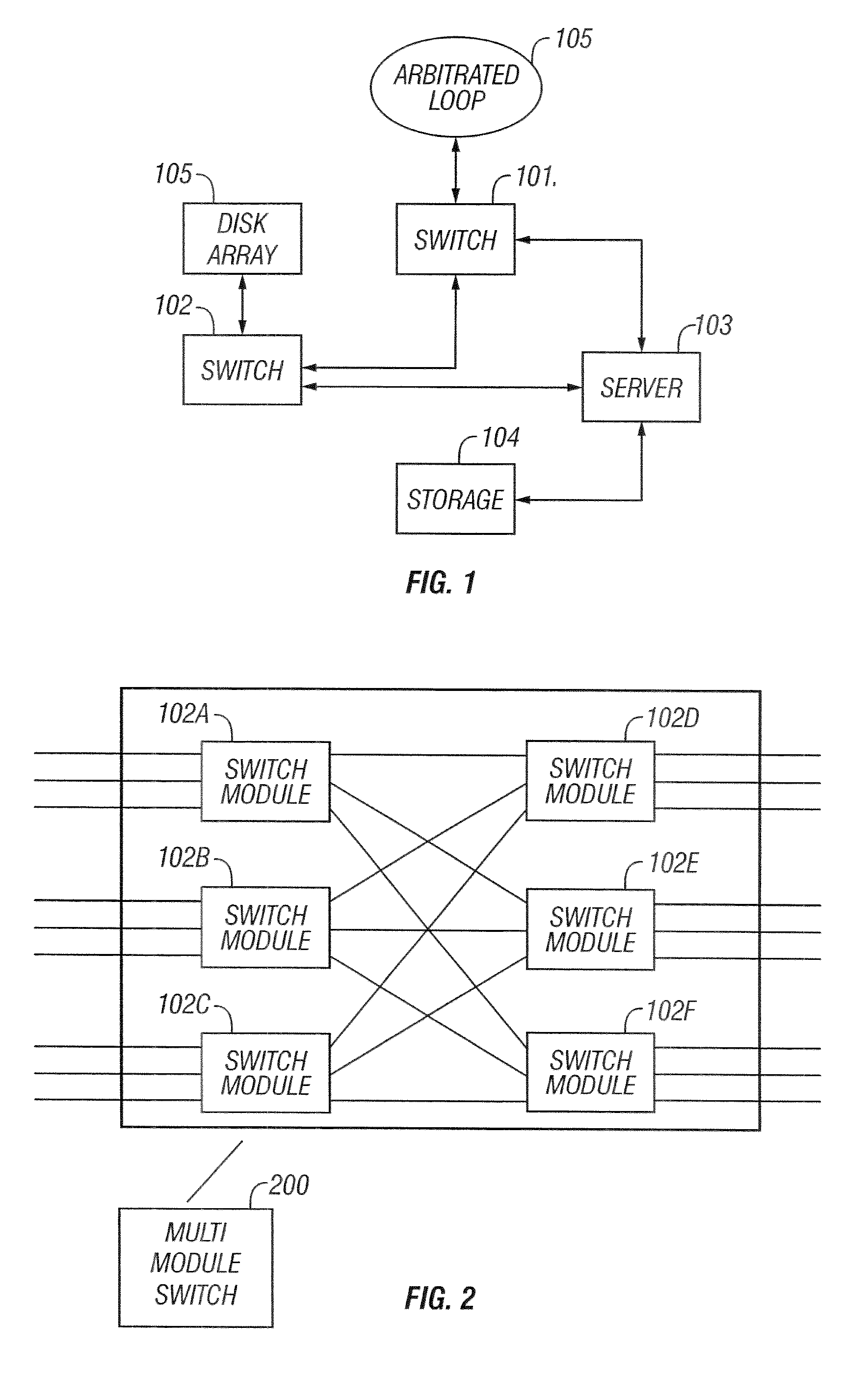
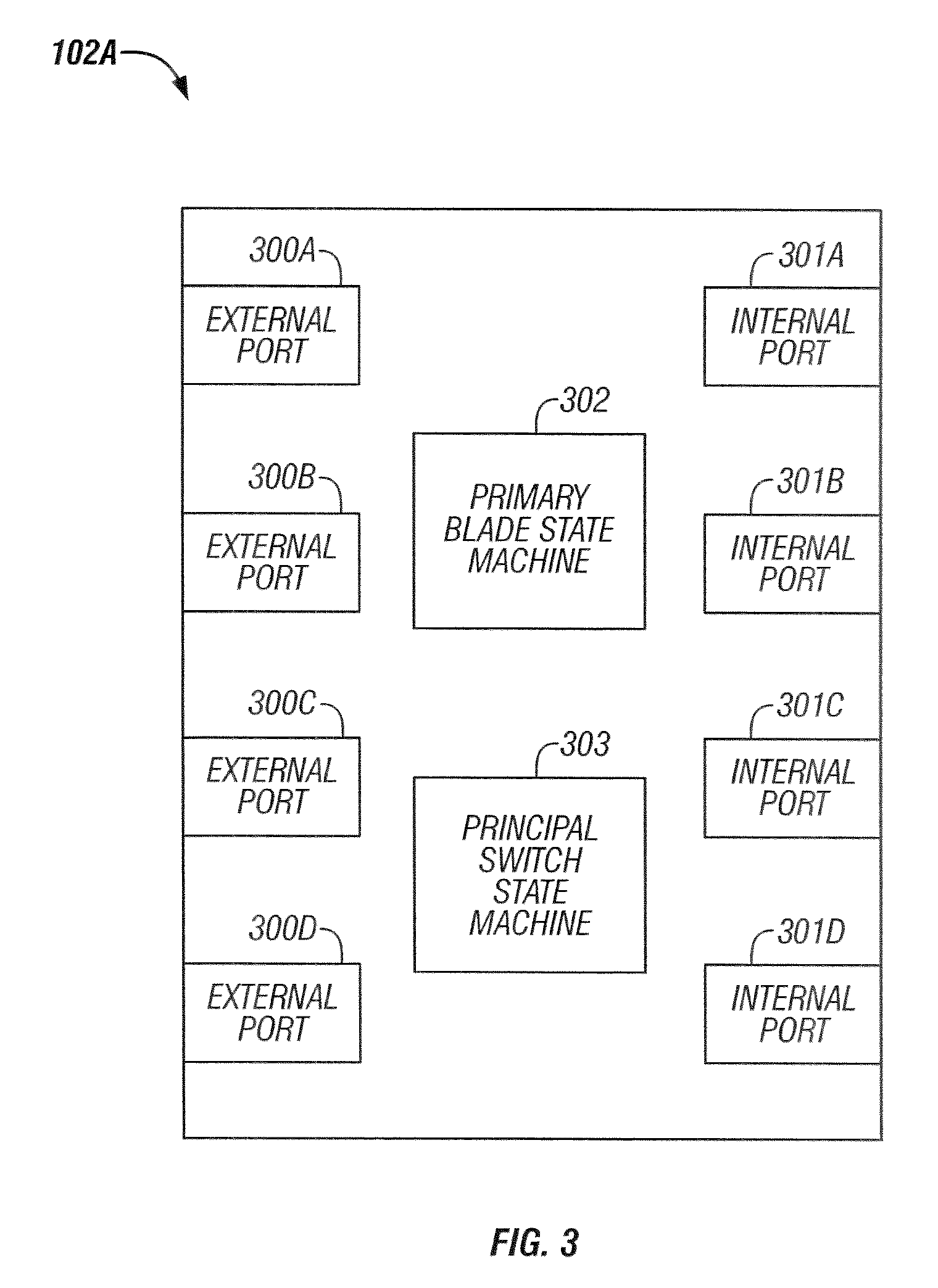
Method and system for primary blade selection in a multi-module fibre channel switch
InactiveUS20070081527A1Multiplex system selection arrangementsData switching by path configurationEngineeringFibre Channel switch
A system and method for selecting a primary blade in a multi-module fibre channel switch with plural blades is provided The system includes a state machine for sending exchangeable blade parameter(s) (“EBP”) to the plural blades; and determining if a primary blade flag is set. If the primary blade flag is set, selecting the blade with the EBP priority number. If the primary blade flag is not selected, then selecting a blade with an EBP priority number if the EBP priority number is less than a retained priority number.
Owner:MARVELL ASIA PTE LTD
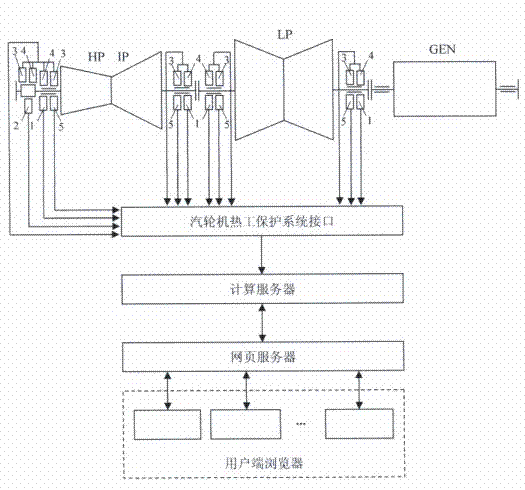
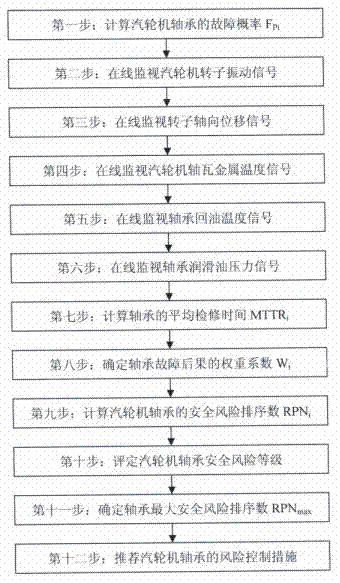
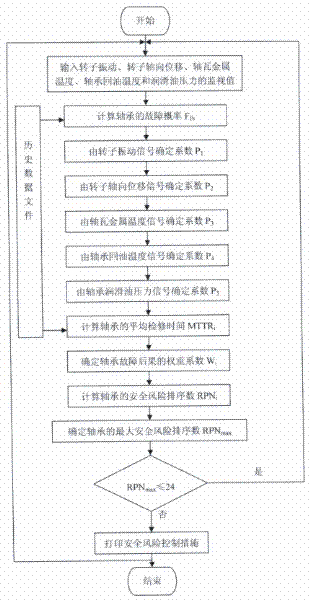
Device and method for monitoring and controlling security risk of turbine bearing in on-line manner
ActiveCN102213116AEasy to controlMachines/enginesSafety/regulatory devicesAxial displacementMean time to repair
The invention relates to a device and method for monitoring and controlling the security risk of a turbine bearing in an on-line manner. The method comprises steps of: calculating a fault probability FPi of the turbine bearing; on-line monitoring a rotor vibration signal, a rotor axial displacement signal of the turbine, a bearing bush metal temperature signal and a bearing oil back signal as well as a bearing lubricating oil pressure signal of the turbine; calculating a mean time to repair MTTRi of the bearing, determining a weight coefficient Wi of bearing fault result; calculating a risk priority number RPNi of the turbine bearing; evaluating the turbine bearing security rank; determining the max risk priority number RPNmax of the turbine bearing; and recommending risk control measures of the turbine bearing. The invention provides the on-line monitoring and control method of the security risk of the turbine bearing, and realizes the on-line calculation and control of the security risk of the turbine bearing.
Owner:SHANGHAI POWER EQUIP RES INST
Automobile operation risk evaluation system and method
InactiveCN107153914AHigh real-time status correlationMeet the safety needs of vehiclesResourcesPriority NumberAutomobile safety
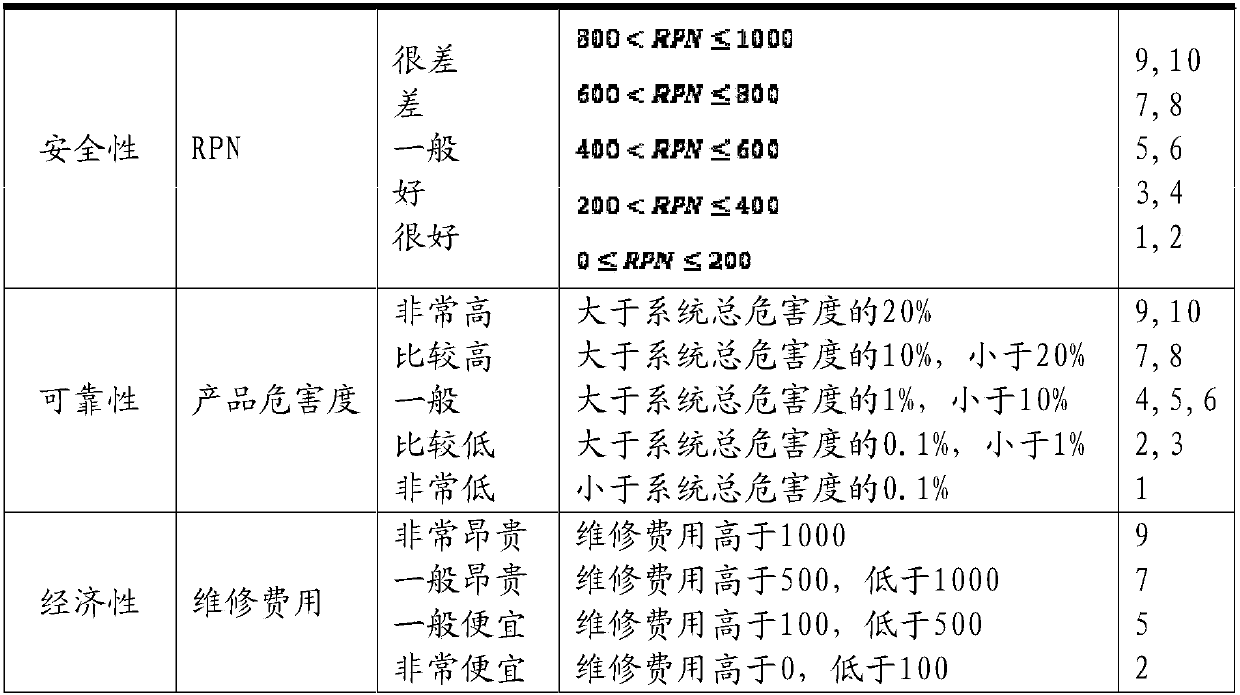
The invention belongs to the automobile safety technology field and discloses an automobile operation risk evaluation system and method. The method comprises steps that a to-be-evaluated automobile model is determined, and statistics data of all the automobiles having models same as the to-be-evaluated automobile model is acquired; according to generation probability of a fault type, a harshness degree after generation of the fault type and a detection degree of the fault type, the risk priority number of a part corresponding to the fault type is determined; three evaluation indexes of each part are acquired, including the risk priority, a hazard degree and maintenance cost; entropy weights of the three evaluation indexes of each part are determined according to an entropy weight algorithm; according to the three evaluation indexes of each part and the entropy weights of the three indexes, a final risk index of the part is determined; an early warning priority of the part is determined according to the final risk index of the part; and objective and accurate automobile risk evaluation can be carried out.
Owner:RES INST OF HIGHWAY MINIST OF TRANSPORT
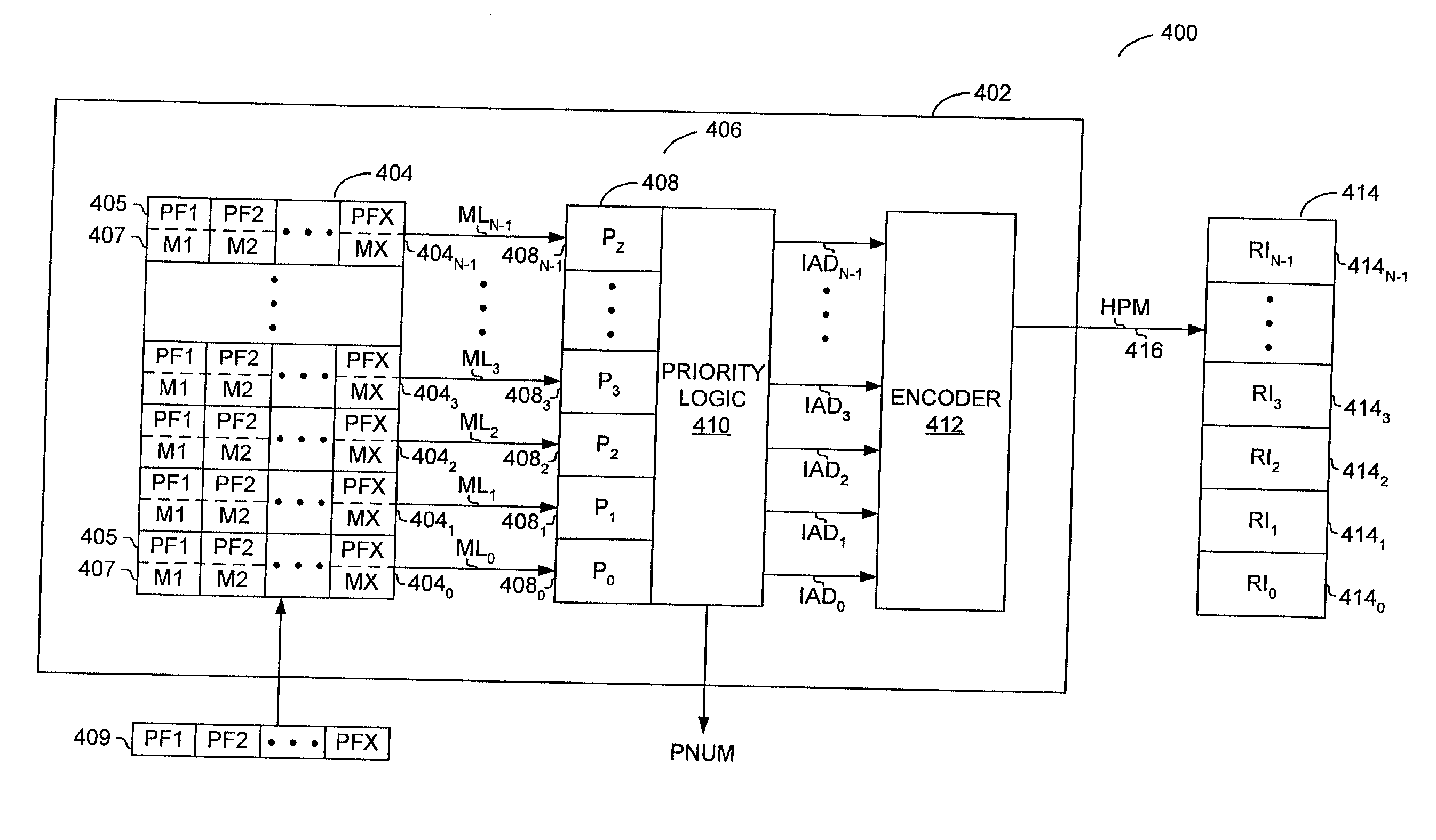
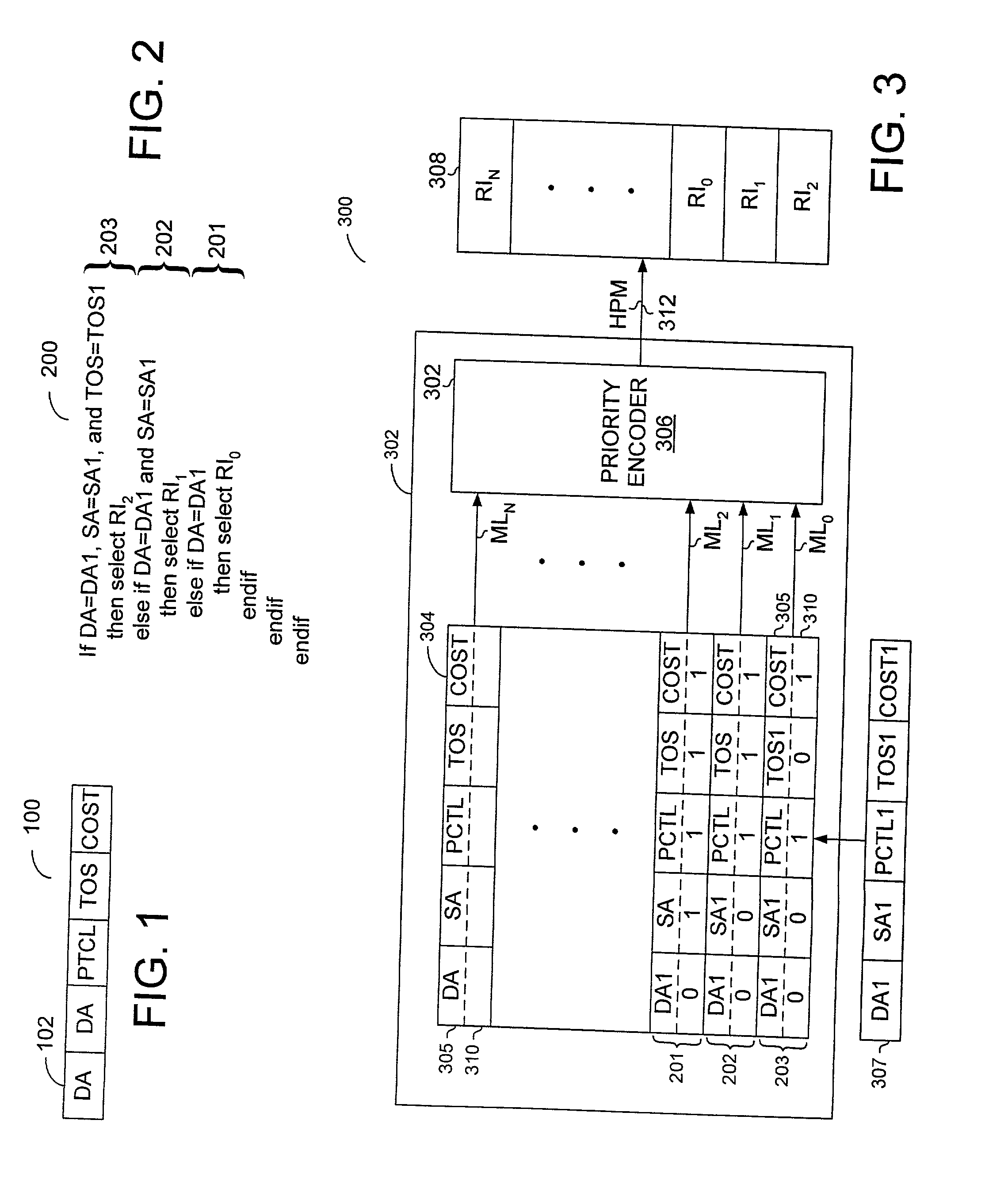
Method and apparatus for performing packet classification for policy-based packet routing
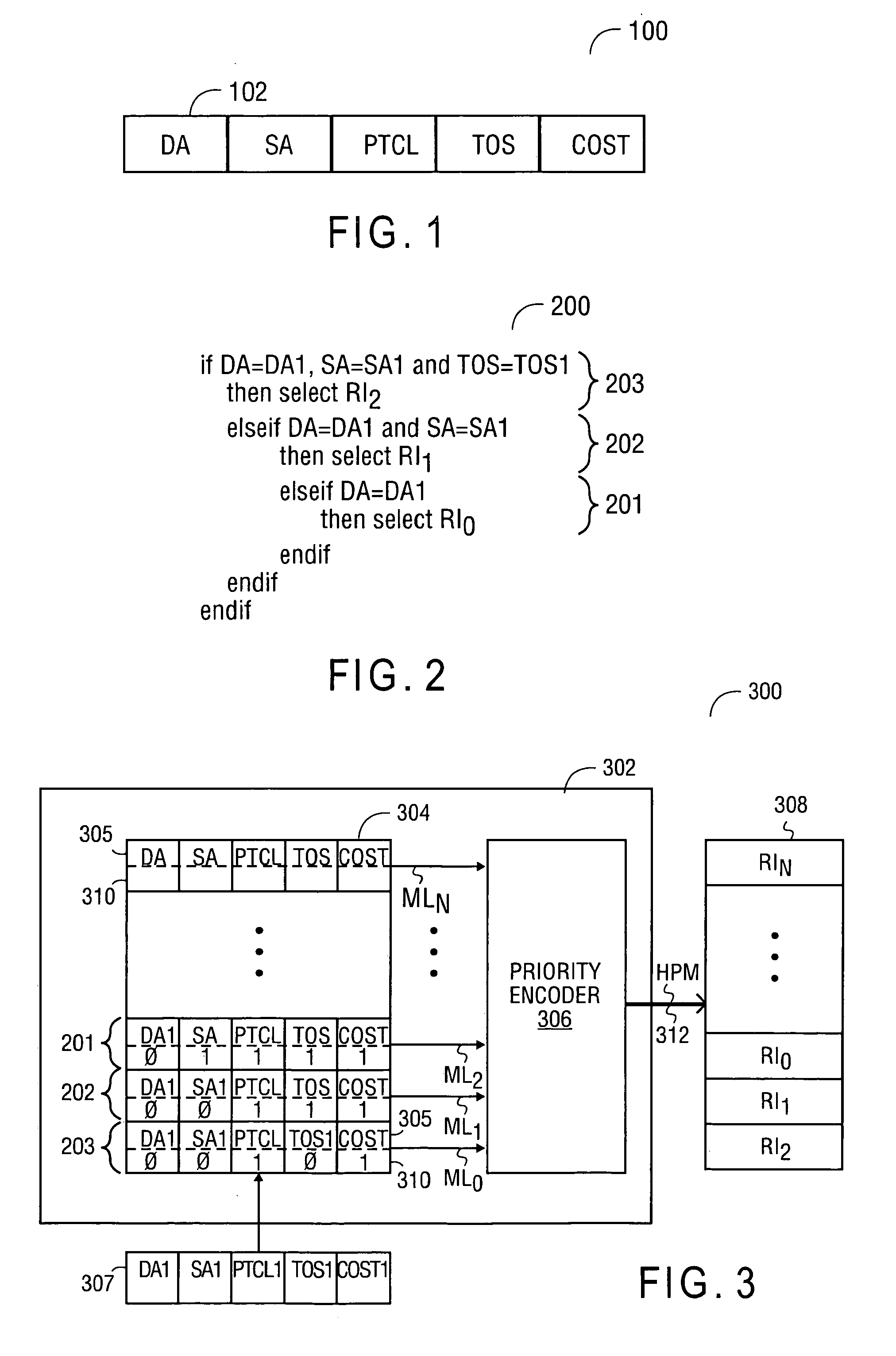
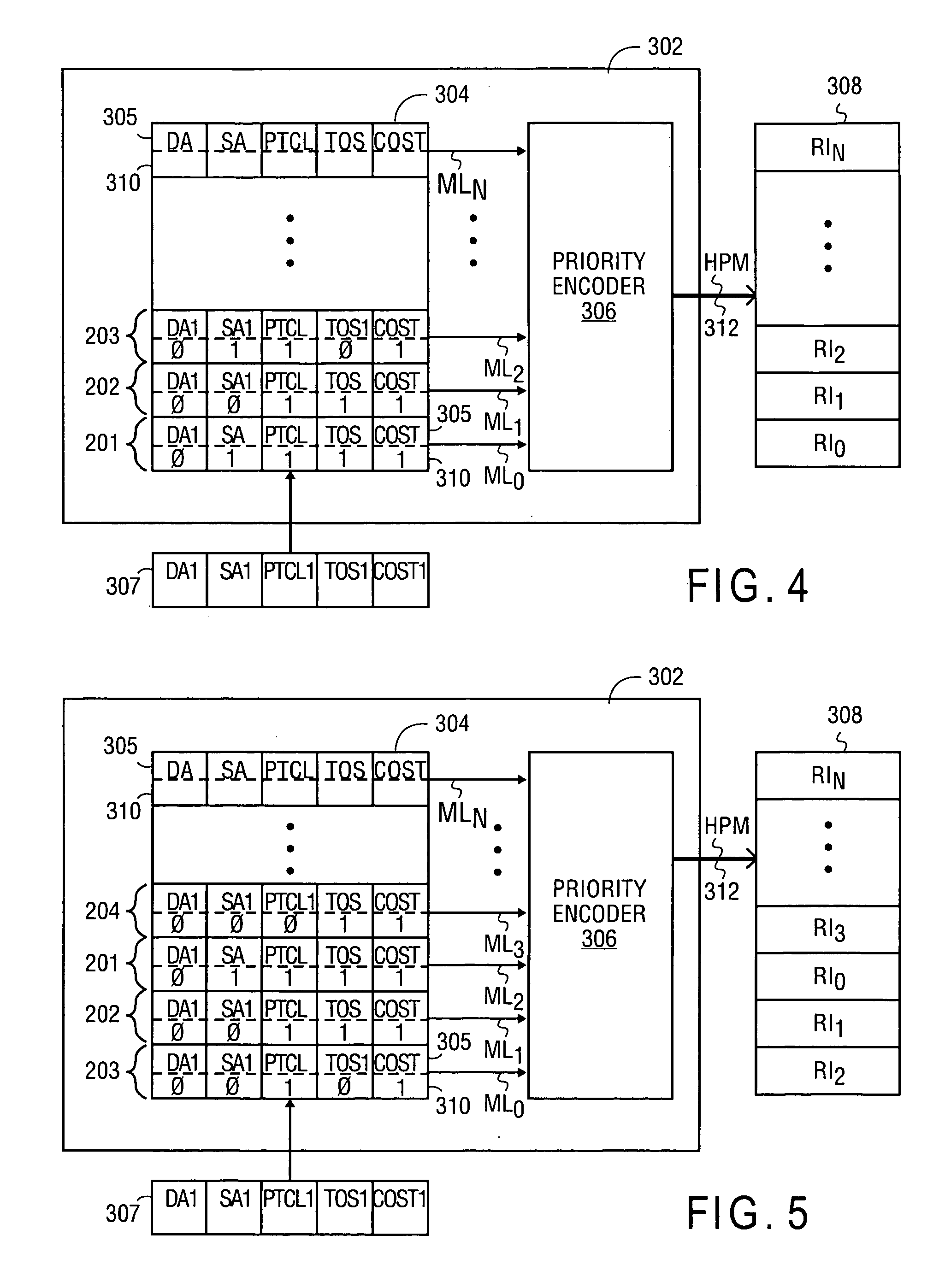
InactiveUS7143231B1Reduce hardwareReduce softwareDigital data processing detailsCounting chain synchronous pulse countersComputer sciencePacket routing
A method and apparatus for performing packet classification in a digital signal processor for policy-based packet routing. For one embodiment, the digital signal processor includes a policy statement table for storing policy statements. Each policy statement has associated with it a priority number that indicates the priority of the policy statement relative to other policy statements. The priority numbers are separately stored in a priority index table. The priority index table includes priority logic that determines the most significant priority number from among the policy statements that match an incoming packet during a classification of filter operation. The priority logic also identifies the location in the priority index table of the most significant priority number. The identified location in the priority index table can be used to access associated route information or other information stored in a route memory array. New policy statements can be added at any location in the policy statement table, and the associated priority numbers loaded into corresponding locations in the priority index table. Priority numbers of previously stored priority policy statements may be updated such that the new policy statement does not have the same priority number as the previously stored policy statements.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
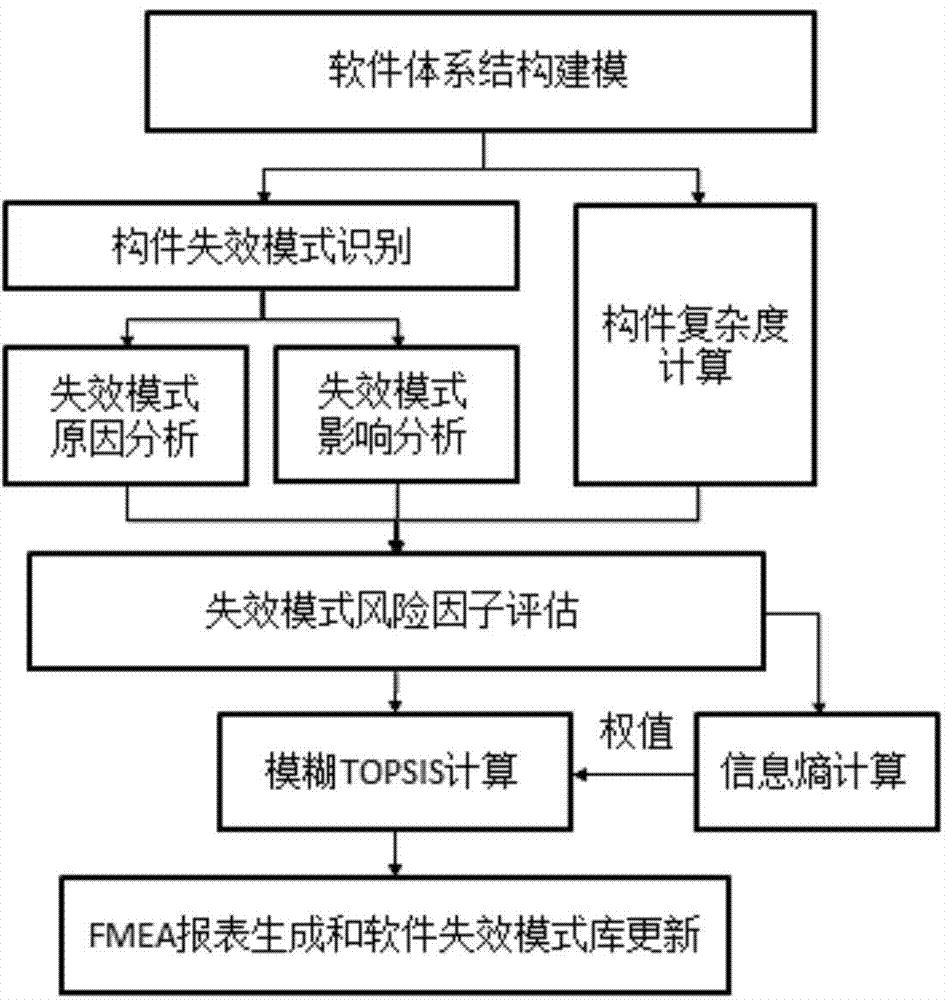
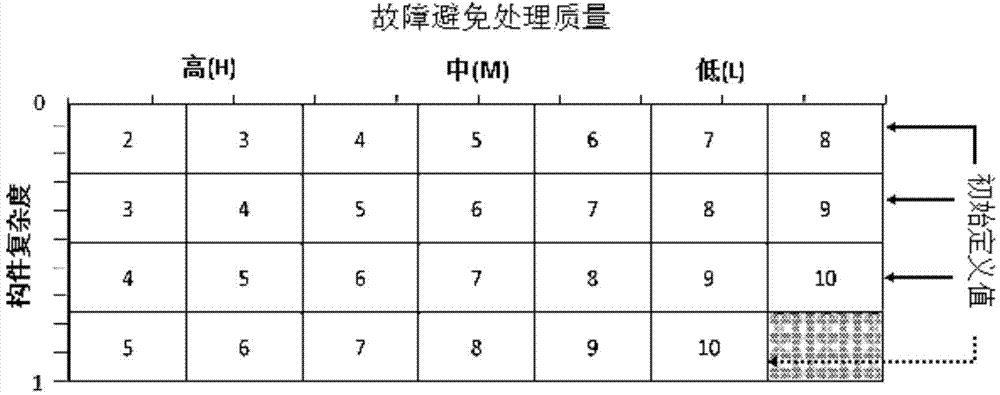
Comprehensive risk priority number calculating method for architecture
ActiveCN104750979AAccurate and reliable assessment resultsAvoid the problem of inaccurate subjective semantic description boundariesSpecial data processing applicationsCOLA (software architecture)Computing Methodologies
The invention provides a comprehensive risk priority number calculating method for architecture. Three risk factors (the appearance frequency, the severity degree and the discovery index) in FMEA are evaluated in the mode that fuzzy numbers are utilized in software architecture in a leveled mode; the appearance frequency and the discovery index are determined through component complexity and expertise, and the weights of different risk factors are distinguished through the conception of information entropy; through the conceptions of a positive ideal solution and a negative ideal solution in a TOPSIS method, a more reasonable and accurate risk priority number rank is obtained; in this way, a comprehensive software-failing mode risk factor evaluation technology for the architecture is achieved. By means of the comprehensive risk priority number calculating method, at the initial software design stage, developers are helped to find out potential design defects in a system, and therefore the subsequent software development quality is guaranteed.
Owner:SHANGHAI JIAO TONG UNIV
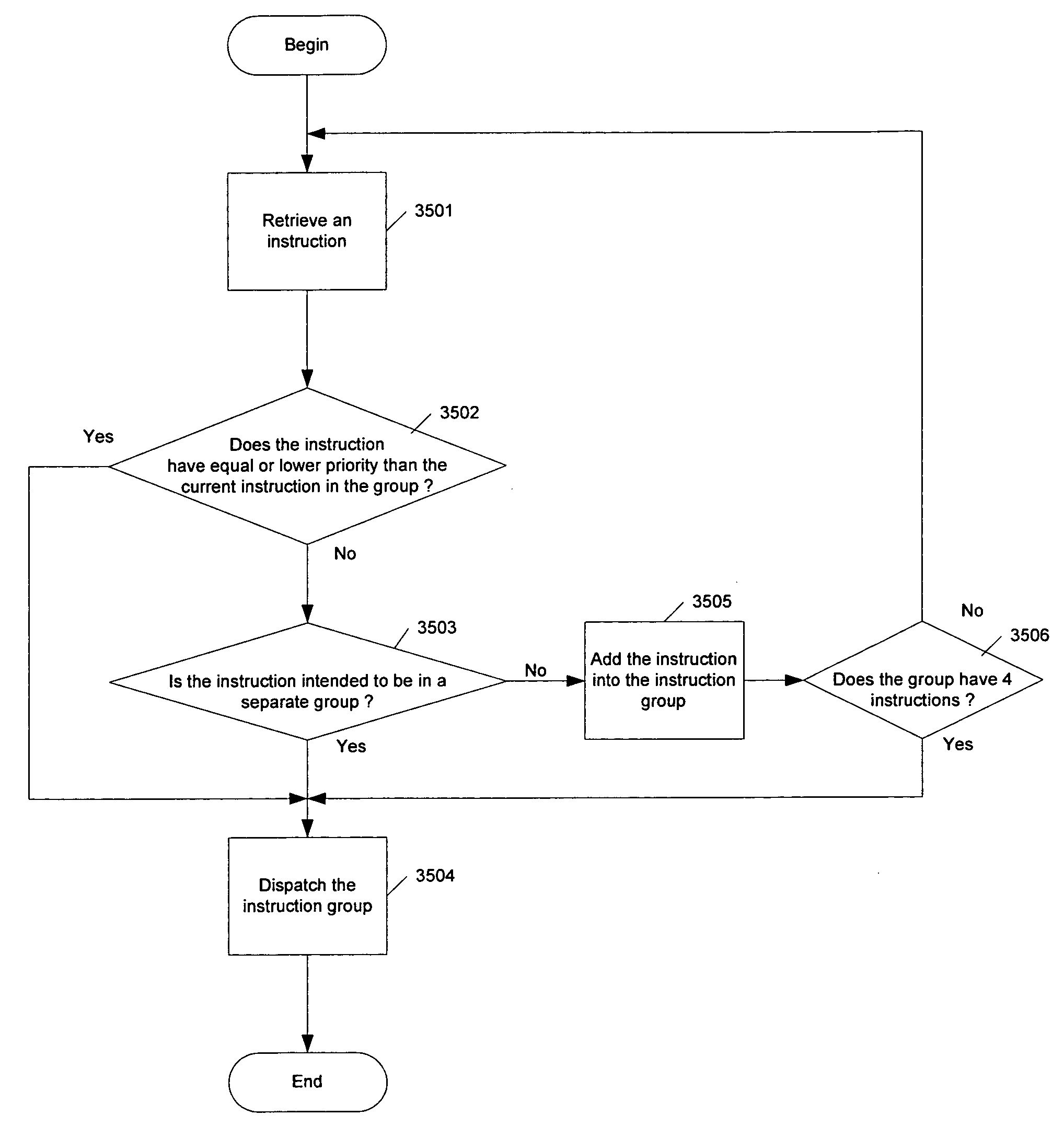
Method and apparatus for forming and dispatching instruction groups based on priority comparisons
Methods and apparatuses for dispatching instructions executed by at least one functional unit of a data processor, each one of the instructions having a corresponding priority number, in a data processing system having at least one host processor with host processor cache and host memory are described herein. In one aspect of the invention, an exemplary method includes receiving a next instruction from an instruction stream, examining a current instruction group to determine if the current instruction group is completed, adding the next instruction to the current instruction group if the current instruction group is not completed, and dispatching the current instruction group if the current instruction group is completed.
Owner:APPLE INC
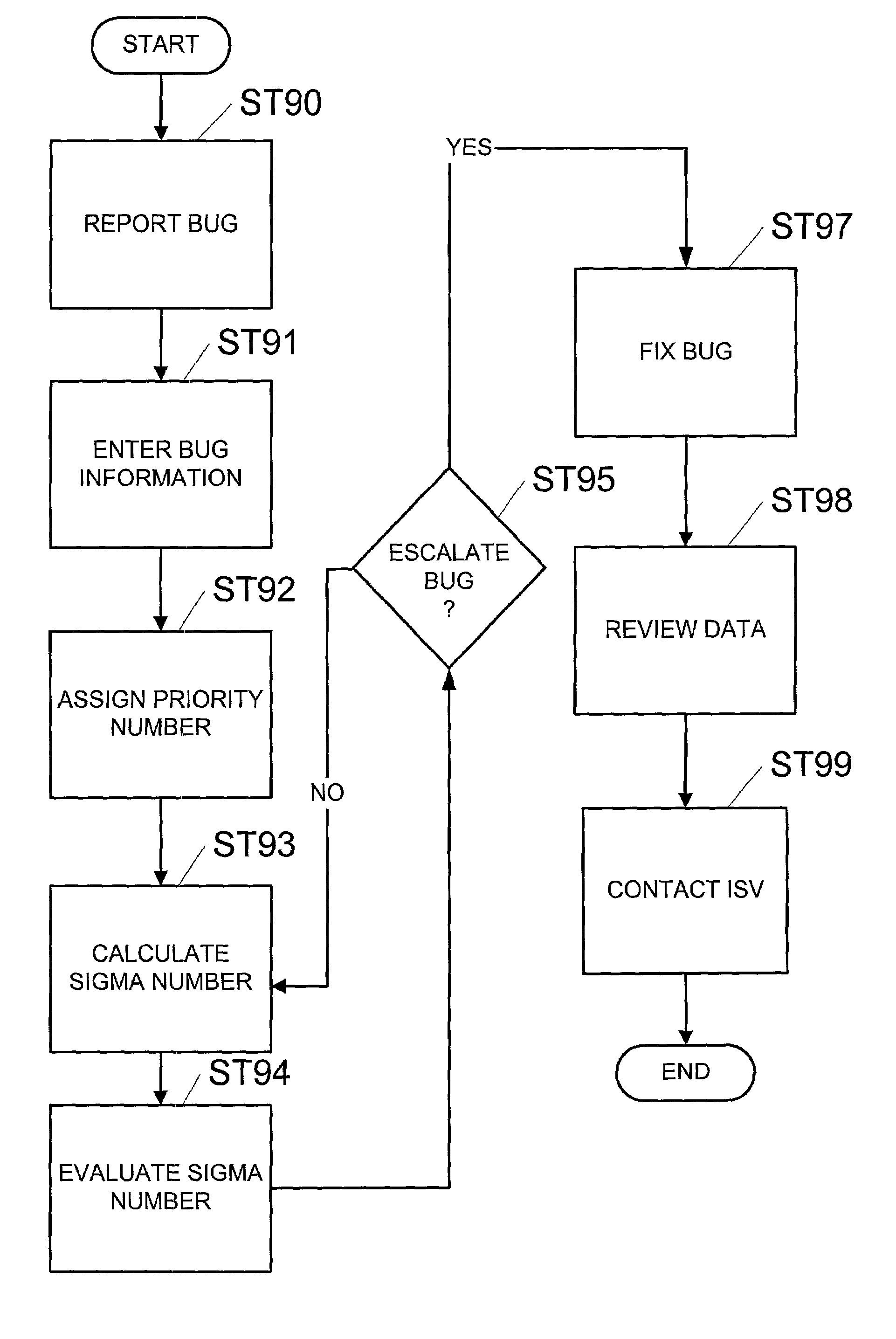
Rating apparatus and method for evaluating bugs
ActiveUS6978441B2Reduce reproductionSoftware testing/debuggingSpecific program execution arrangementsGraphicsGraphical user interface
A method of rating a bug, including reporting the bug to a business entity by an interested party, entering information regarding the bug into a database, assigning a priority number for the bug, calculating a sigma number for the bug using the priority number, evaluating the bug to be fixed using the sigma number, and escalating the bug. A bug council rating apparatus, including a database to store the information entered using a graphical user interface, a priority number module configured to generate a priority number, and a sigma number module configured to generate a sigma number.
Owner:ORACLE INT CORP
Ternary content addressable memory device
InactiveUS7054993B1Multiplex system selection arrangementsData switching by path configurationComputer hardwareTernary content addressable memory
A ternary content addressable memory device. The device includes a ternary CAM array segmented into a plurality of array groups, each of which includes a number of rows of ternary CAM cells. Each array group is assigned to a particular priority by storing the priority number for each array group in an associated storage element. Data entries are then stored in array groups according to priority.
Owner:AVAGO TECH INT SALES PTE LTD
Method for time synchronization between nodes in self-organizing network
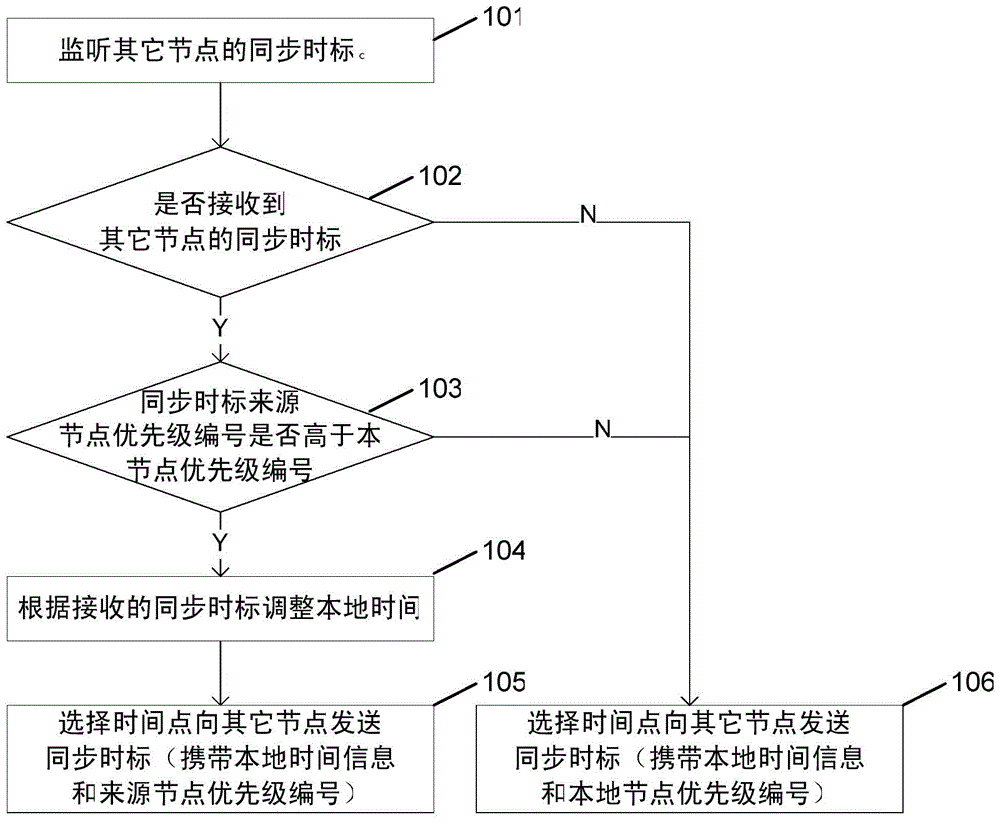
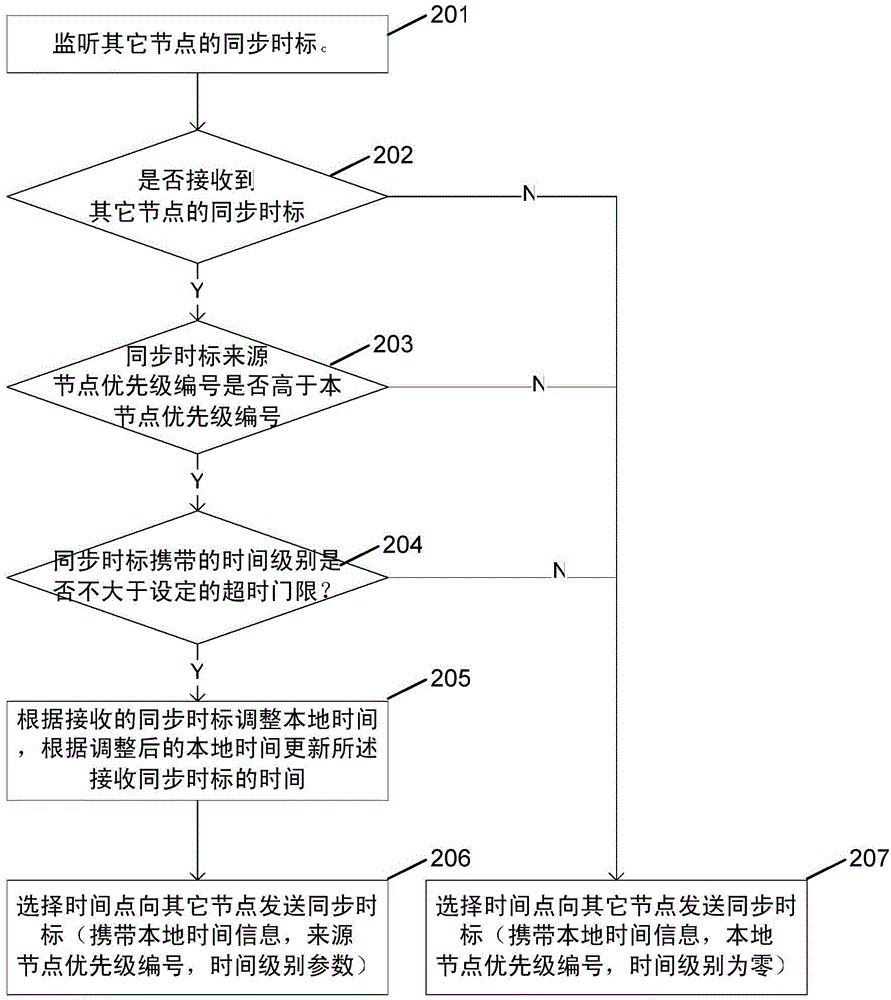
InactiveCN104427607AGuaranteed Priority ExperienceSynchronize node timeSynchronisation arrangementNetwork topologiesTemporal informationTime mark
The invention provides a method for time synchronization between nodes in a self-organizing network. All nodes have unique priority numbers. The method comprises: step 1, any node A in the network monitors synchronous time marks sent by other nodes during the silence period; and if one synchronous time mark is received, the step 2 is carried out; otherwise, the step 3 is carried out after the end of the silence period; step 2, if the priority of the priority number of the source node of the received synchronous time mark is superior to the priority number of the local node, the node A adjusts local time according to the received synchronous time mark and the step 3 is carried out; and otherwise, the step 3 is carried out directly; and step 3, the node A selects a time point to send a synchronous time mark to other nodes, wherein the synchronous time mark carries the node local time information as well as the node priority number. With the method, time synchronization of all nodes can be realized without the unified coordination of a central control node, thereby improving the efficiency of the time synchronization between the nodes and guaranteeing the user priority experience.
Owner:BEIJING XINWEI TELECOM TECH
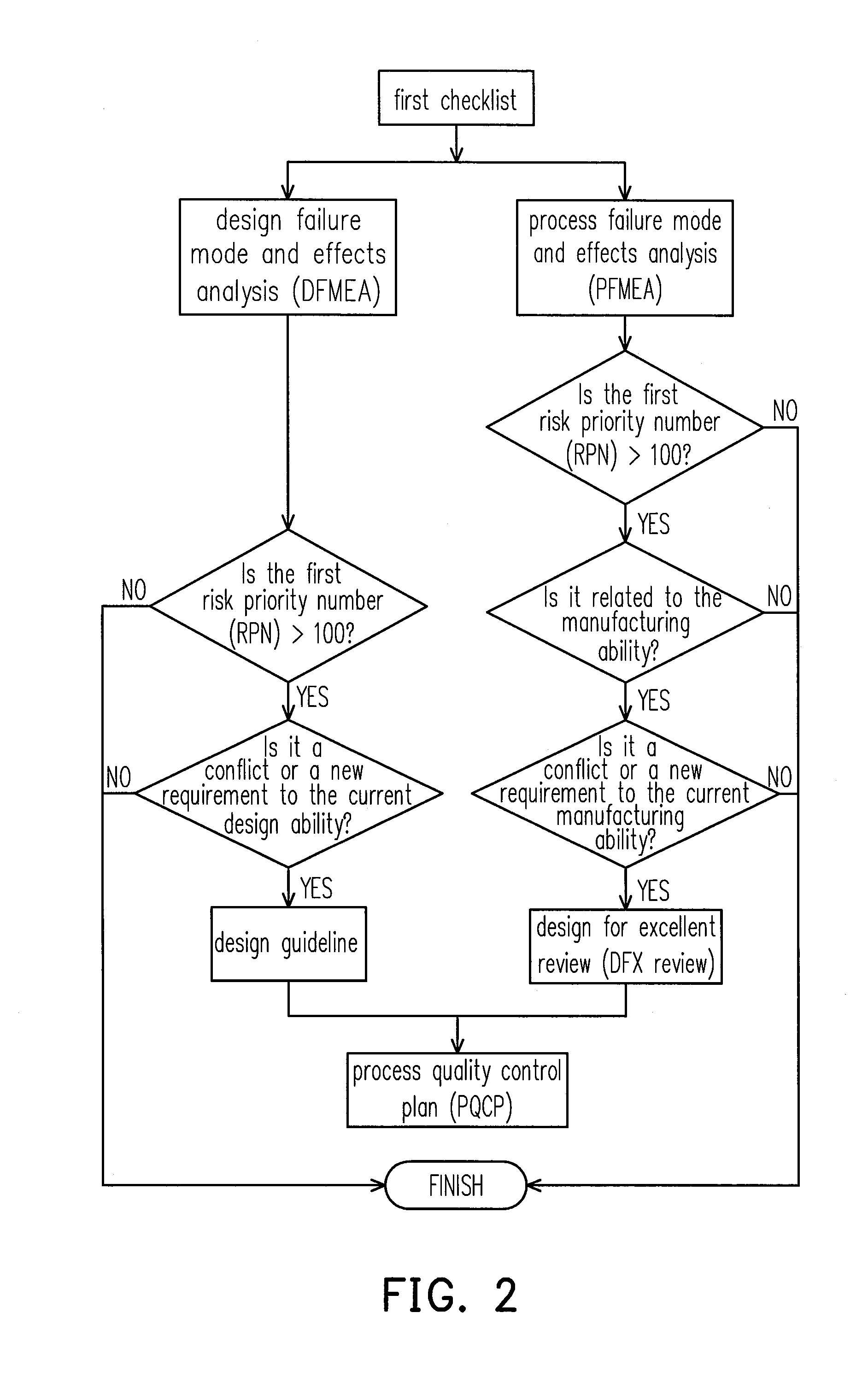
Product quality improvement feedback method
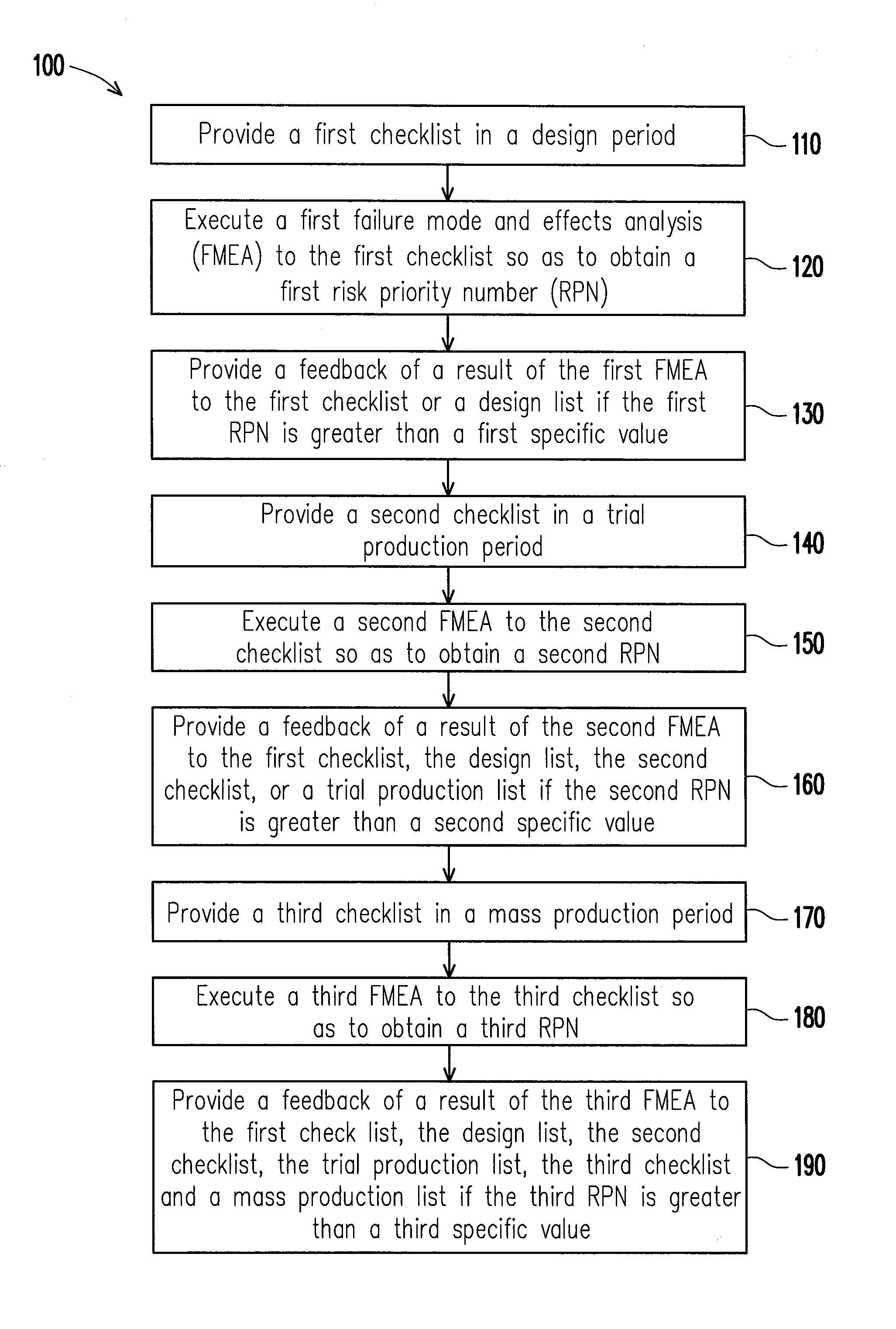
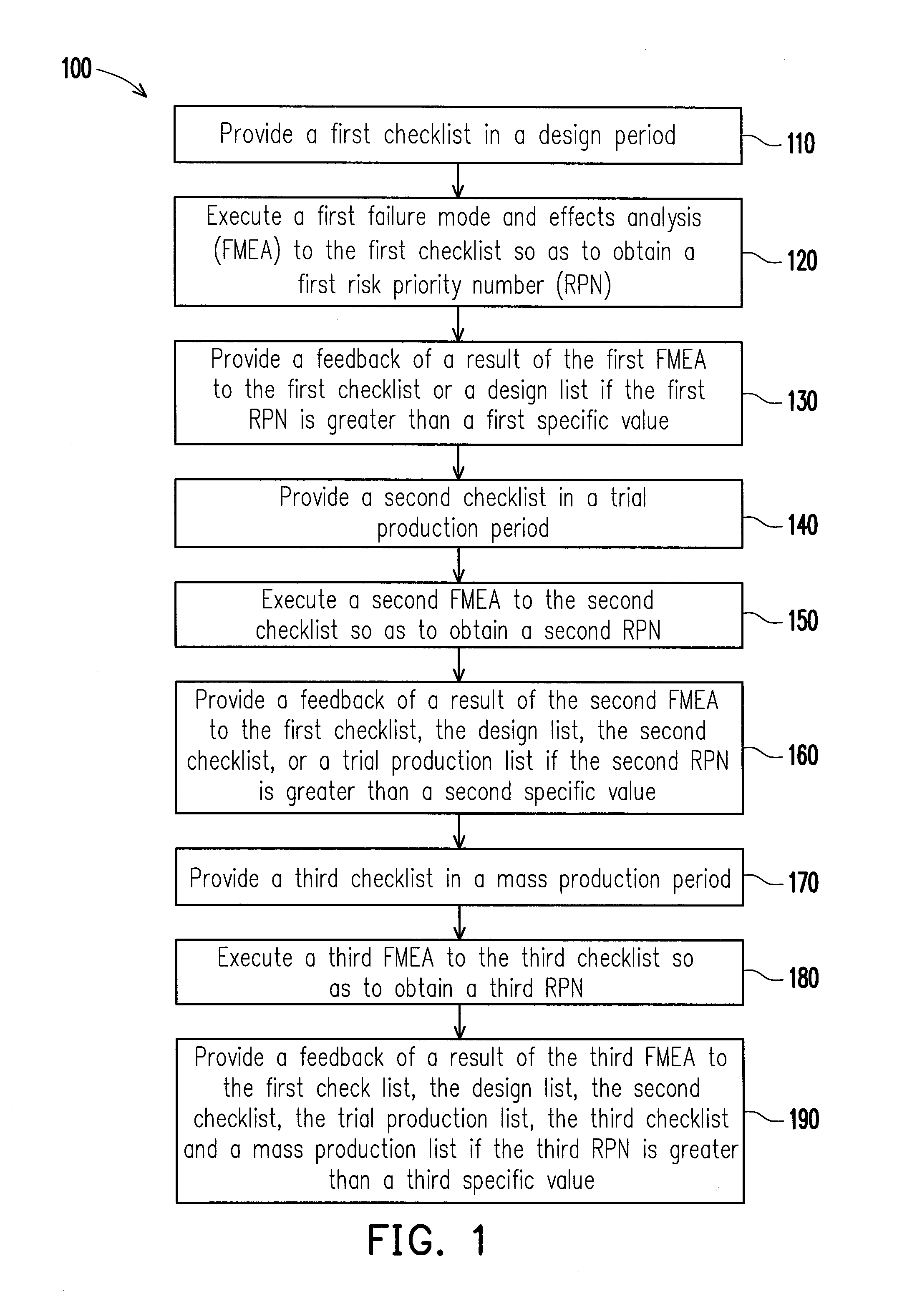
InactiveUS20140081442A1Avoid problemsSolve the real problemSpecial data processing applicationsInfluence analysisEffect analysis
A product quality improvement feedback method is provided. The method includes the following steps. Provide a first checklist, a second checklist, and a third checklist in a design period, a trial production period, and a mass production period respectively. Execute a failure mode and effects analysis to the first checklist, the second checklist, and the third checklist so as to obtain a risk priority number respectively. When the first risk priority number is greater than a specific value, feedback each result of the failure mode and effects analyses to the first checklist, the second checklist, the third checklist, a design list, a trial production list or a mass production list.
Owner:ASKEY COMP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com