Method for updating distributed cipher key based on AVL tree
An AVL tree and update method technology, which is applied to key distribution, can solve the problems of unbalanced one-way function tree and reduce system storage overhead, etc., and achieve the effect of small update resource consumption and small number of stored keys
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
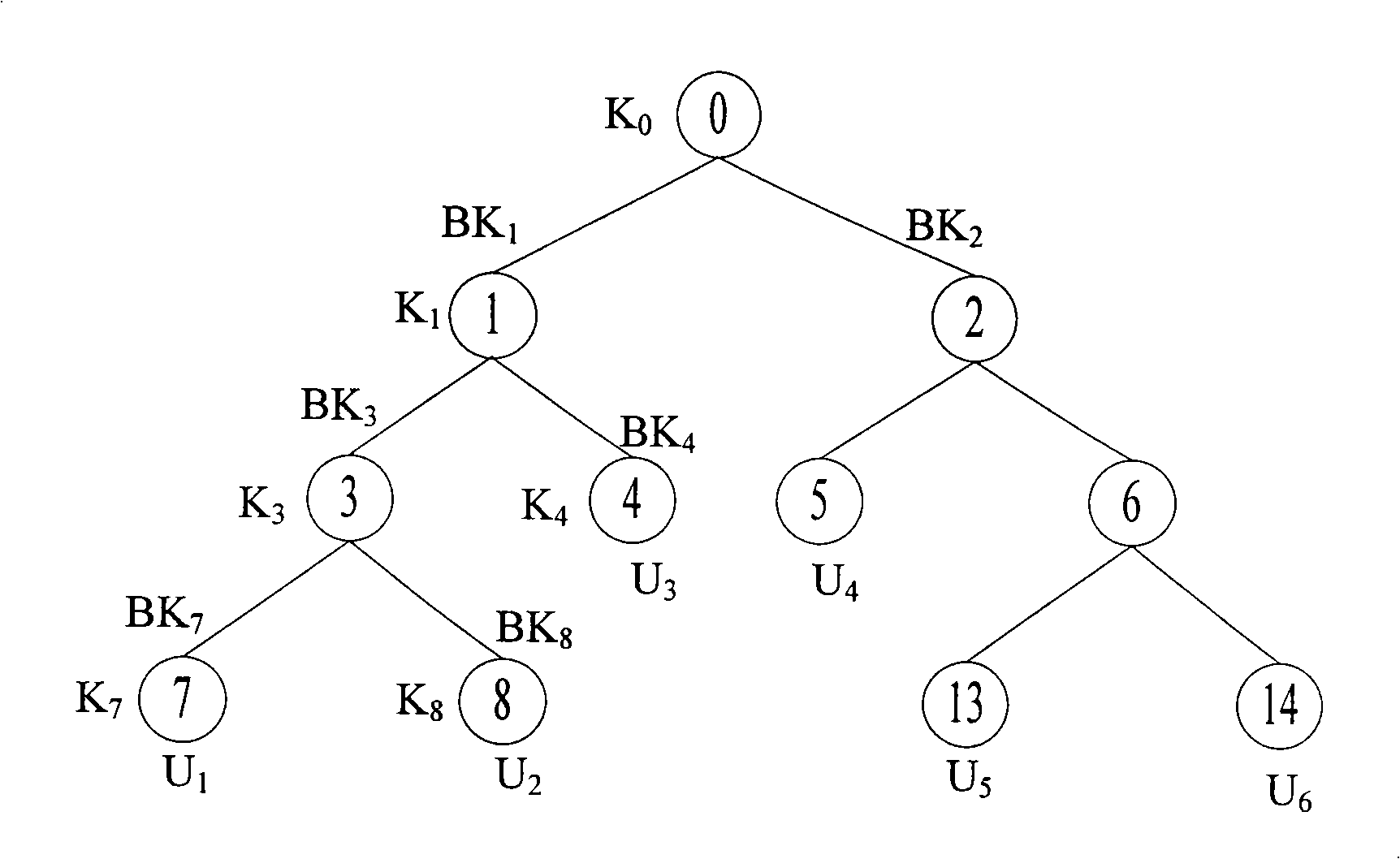
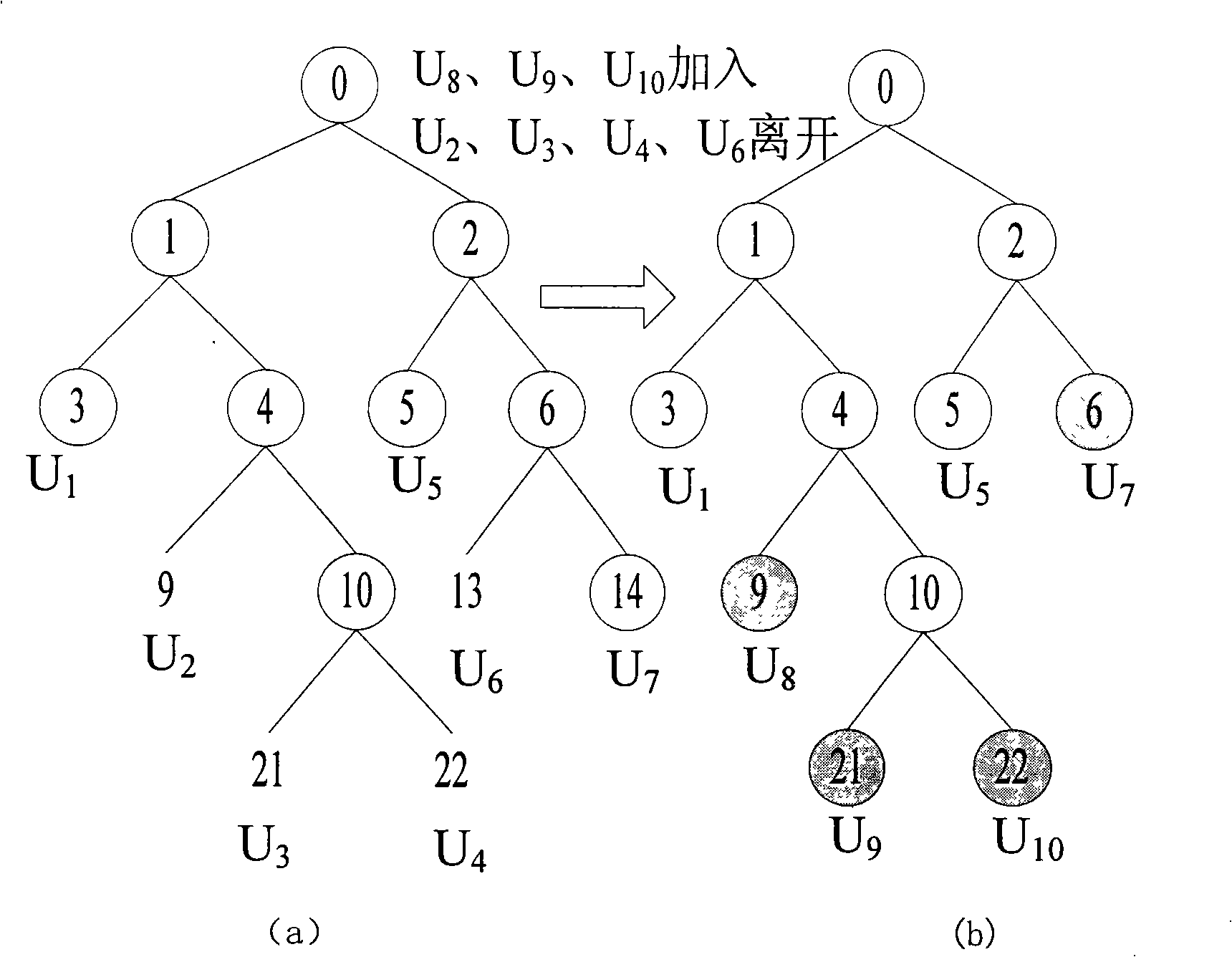
[0061] The update method of embodiment 1 is as Figure 7 to Figure 11 As shown, this example shows in detail figure 2 The key tree on the left in the center is out of balance during the update process, and the balance is restored by the method of the present invention, and finally the key update process of the entire key tree is completed.
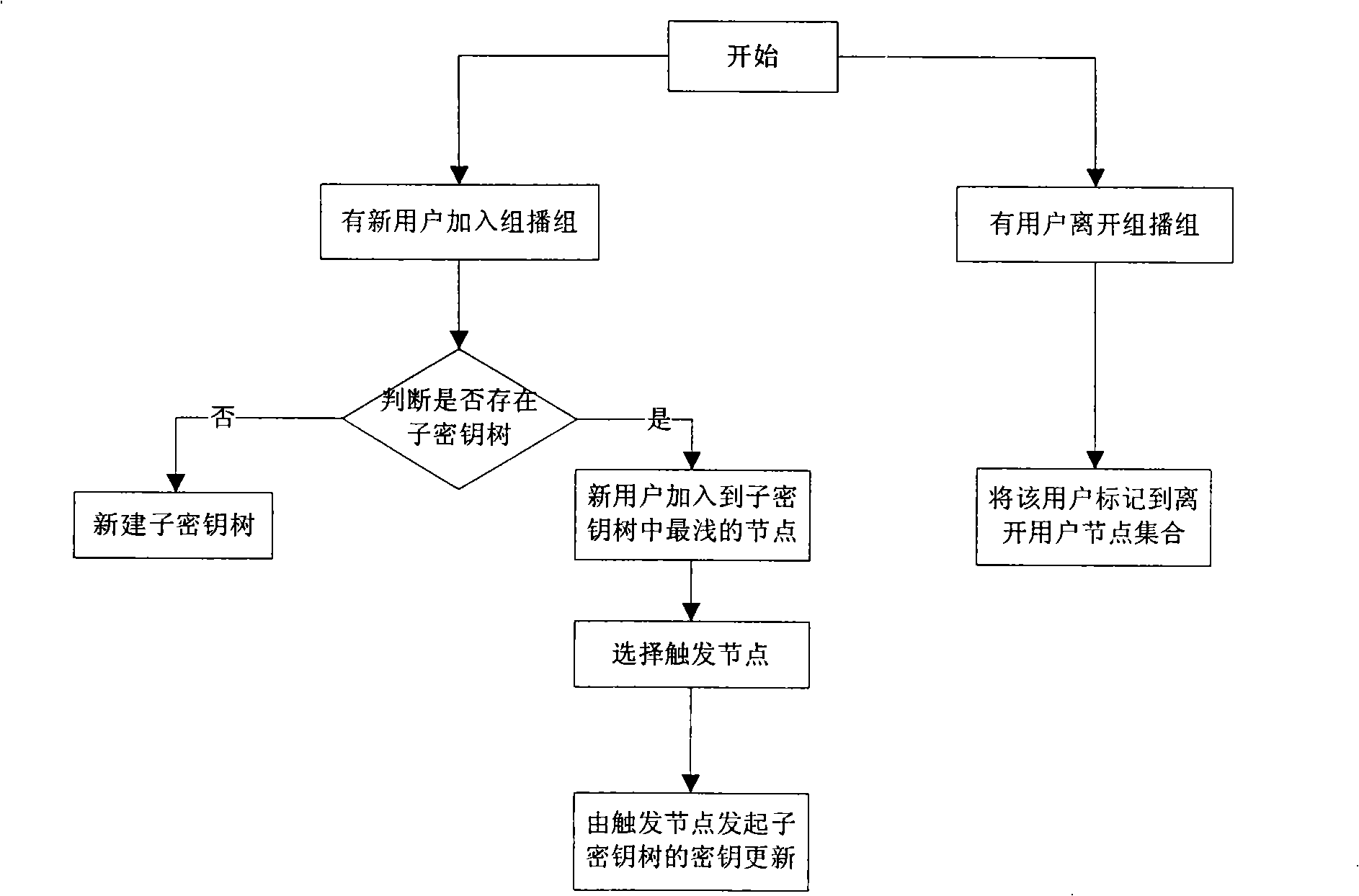
[0062] The key update process of this embodiment includes the following steps:
[0063] 1) The user node U to be newly added 8 , U 9 , U 10 Form a subkey tree; such as Figure 7 shown;
[0064] 2) Will figure 2 The leaving user node U in 2 , U 3 , U 4 , U 6 mark-to-leave user node set, figure 2 The node indicated by the dotted line in the middle;
[0065] 3) There are nodes to leave in the user node set, so first insert the subkey tree into the original key tree, such as Figure 8 As shown, the subkey tree is inserted into the shallowest node 3 of the original key tree to form a new key tree;
[0066] 4) Put U 2 , U 3 , ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com