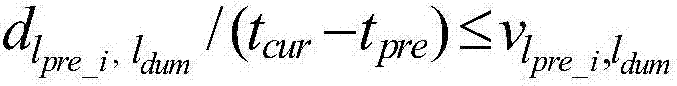Location privacy protection method in check-in service
A privacy protection and false location technology, applied in the field of social network services, can solve the problems that social network servers cannot obtain user location information, do not consider the needs of all user sign-in records, and cannot issue user sign-in rewards to users, etc., to achieve high applicability Sex, good location privacy protection, good applicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
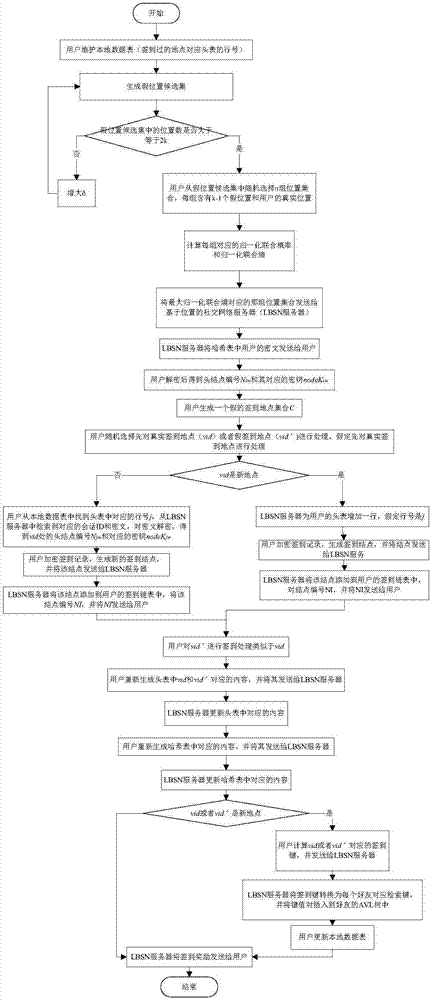
[0045] figure 1 It is a flowchart of a location privacy protection method in a sign-in service of the present invention.
[0046] In this example, if figure 1 As shown, a location privacy protection method in a check-in service of the present invention comprises the following steps:
[0047] S1. The user maintains a local data table, which is used to store the places the user has checked in and the corresponding header table row number.
[0048] S2. Generate a false location candidate set
[0049] Let the number of locations sent to the social network server LBSN by the user's last check-in be k pre , and l real is the real position of the user at the current moment, therefore, there are k pre joint probabilities, respectively q(l pre_1 , l real ),...,q(l pre_kpre , l real ). Among them, l pre_1 ,...,l pre_kpre They are the k sent by the user to the LBSN during the last check-in pre locations. We find all positions satisfying the following two conditions, except ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com