Anti-interference and anti-attack traffic monitoring system and method capable of customizing privacy protection
A privacy-preserving and customized technology, applied in the fields of anonymous authentication and Internet of Vehicles, it can solve the problems of location privacy leakage, interference attack, and lack of consideration, and achieve the effect of protecting identity information, protecting it from being leaked, and realizing location privacy protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
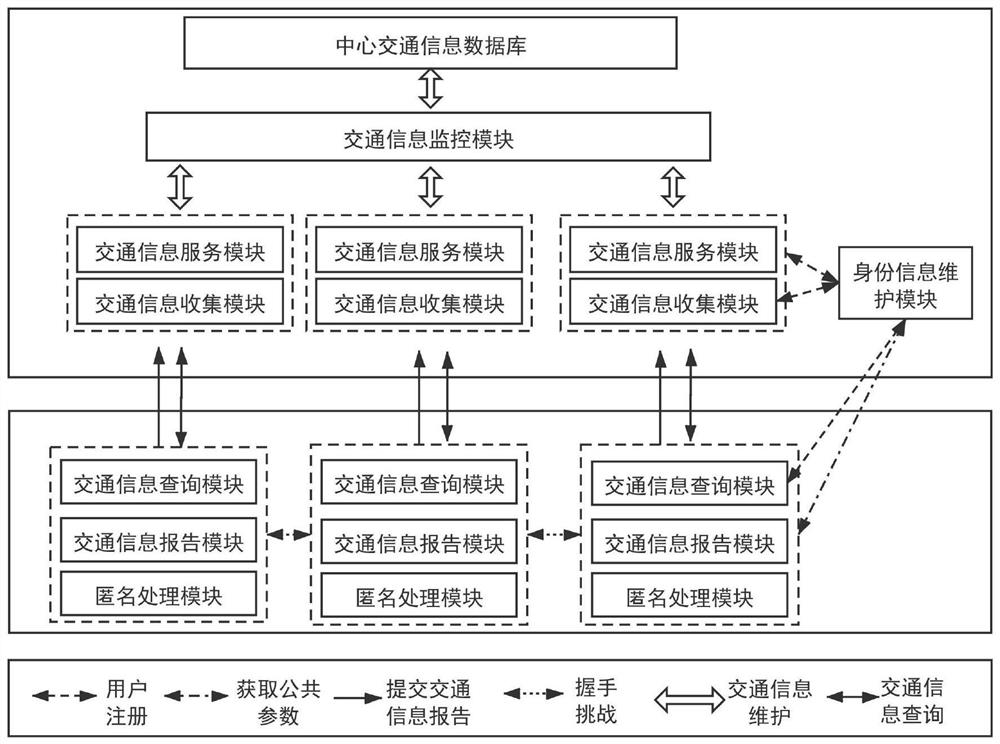
[0078] In this embodiment, a traffic monitoring system that supports self-defined privacy protection against interference attacks, such as figure 1 As shown, it includes identity information maintenance module, anonymous processing module, traffic information monitoring module, several traffic information processing combination modules and several traffic information access combination modules, each traffic information processing combination module includes: traffic information service module, traffic information Information collection module, each traffic information access combination module includes: traffic information query module, traffic information report module;
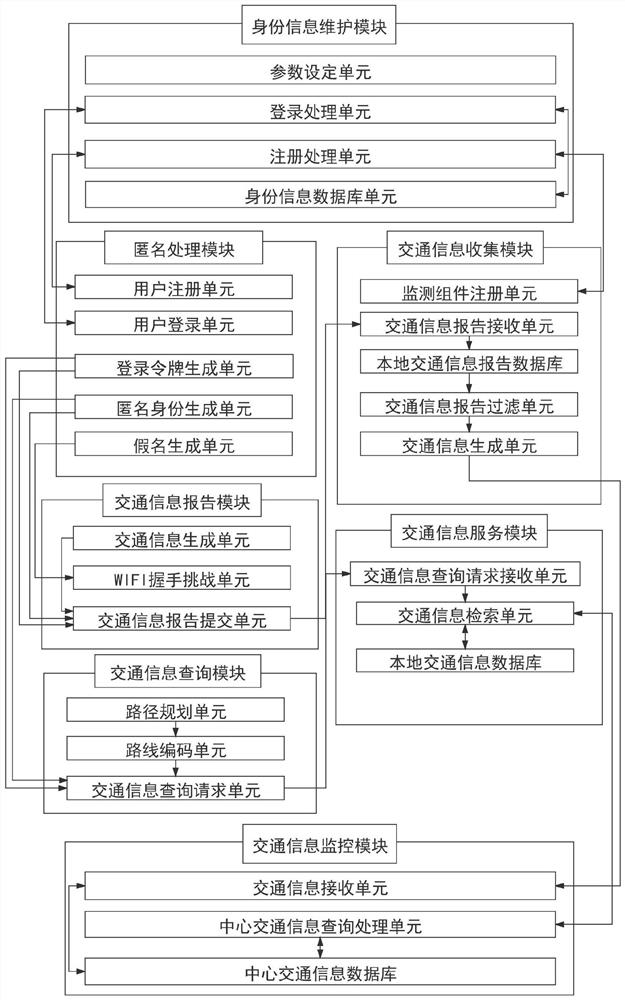
[0079] Such as figure 2 As shown, the identity information maintenance module includes: a parameter setting unit, a registration processing unit, a login processing unit, and an identity information database;
[0080] The anonymous processing module includes: user registration unit, user login unit, login ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com