Patents
Literature
124results about How to "Not to be leaked" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Terminal data protecting method, system as well as mobile communication terminal
ActiveCN101252703ANot to be leakedTelemetry/telecontrol selection arrangementsRadio/inductive link selection arrangementsSecret codeData storing
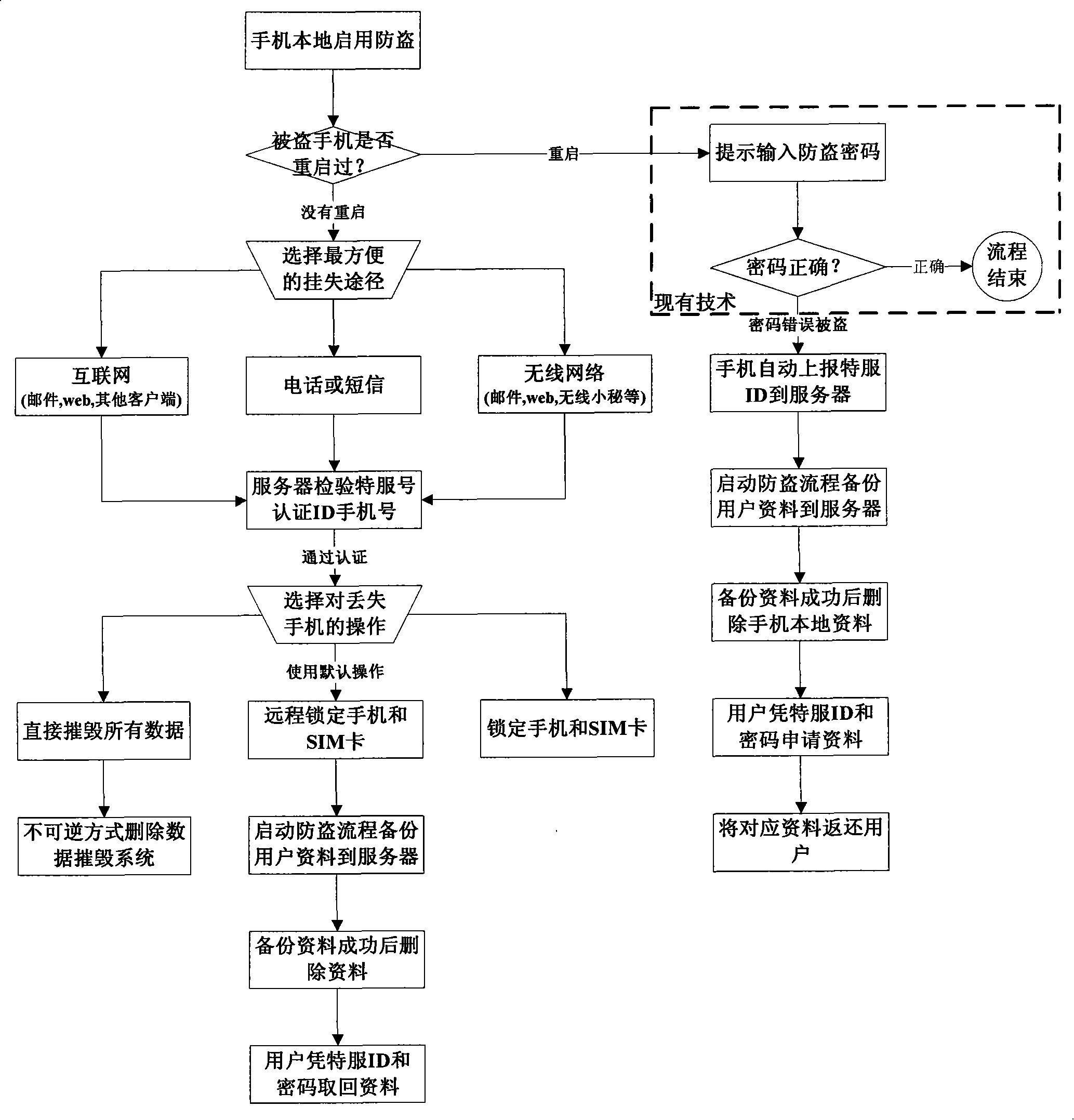
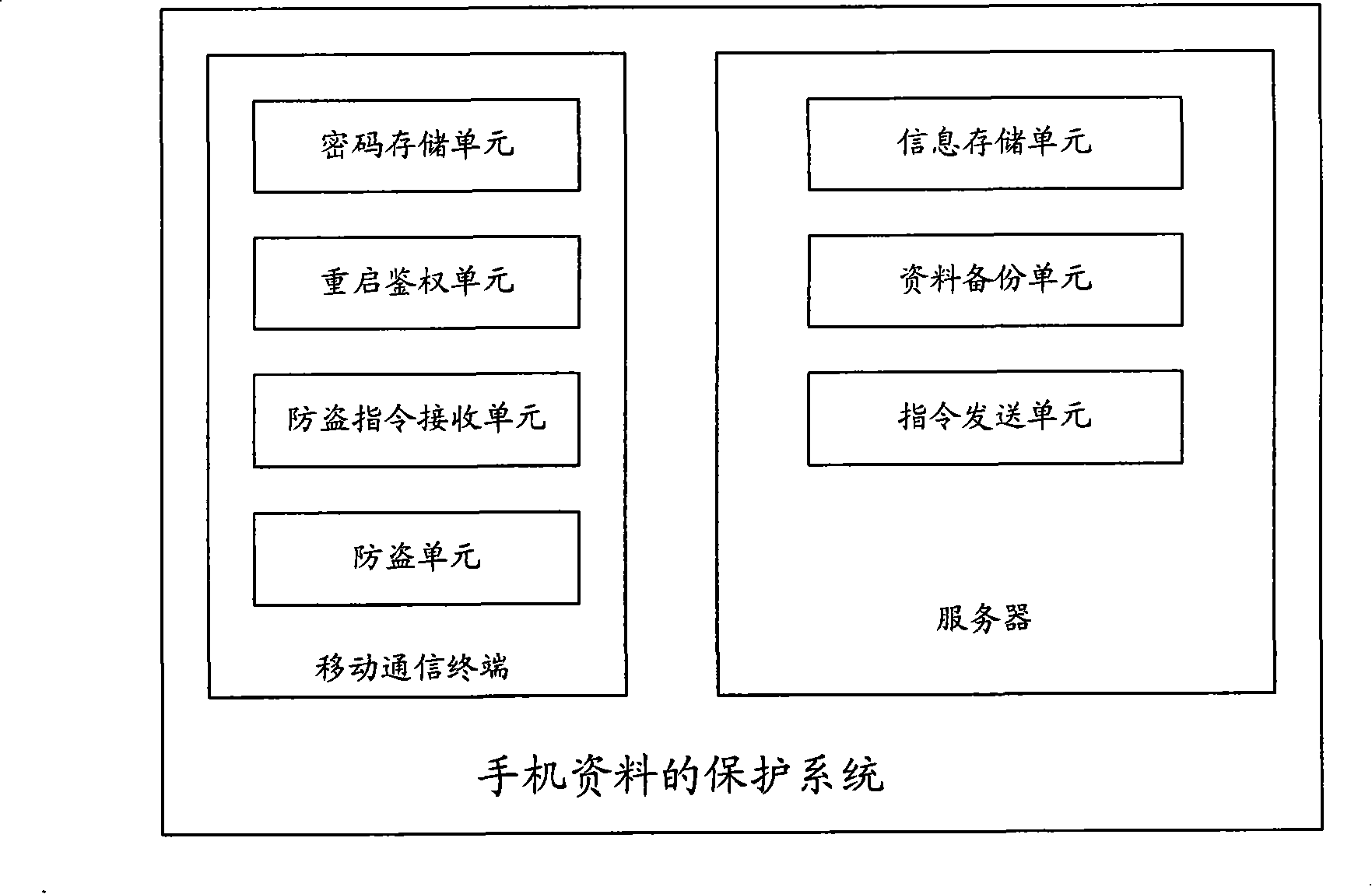
The invention relates to protection method and system and a mobile communication terminal for terminal data, and belongs to the wireless communication field. The method comprises the steps that the restarting code is verified if restarting occurs when the terminal is stolen, the terminal is recognized to be stolen and locked if the code is wrong; the user data stored at the stolen terminal is backed up; if restarting does not occur, operation instruction is remotely sent to the stolen terminal to back up the user data stored at the stolen terminal to a server. An identification authentication ID number issued simultaneously with the mobile communication terminal can be used for identifying the control right of the users to the mobile communication terminal and protect the control right; the users can perform anti-theft operation through logging in the server without setting the anti-theft function on the mobile communication terminal in advance; moreover, the adoption of the protection method and system and the mobile communication terminal can ensure the private data of the users to be protected and backed up immediately, thus protecting private data at the mobile communication terminal against leakage.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
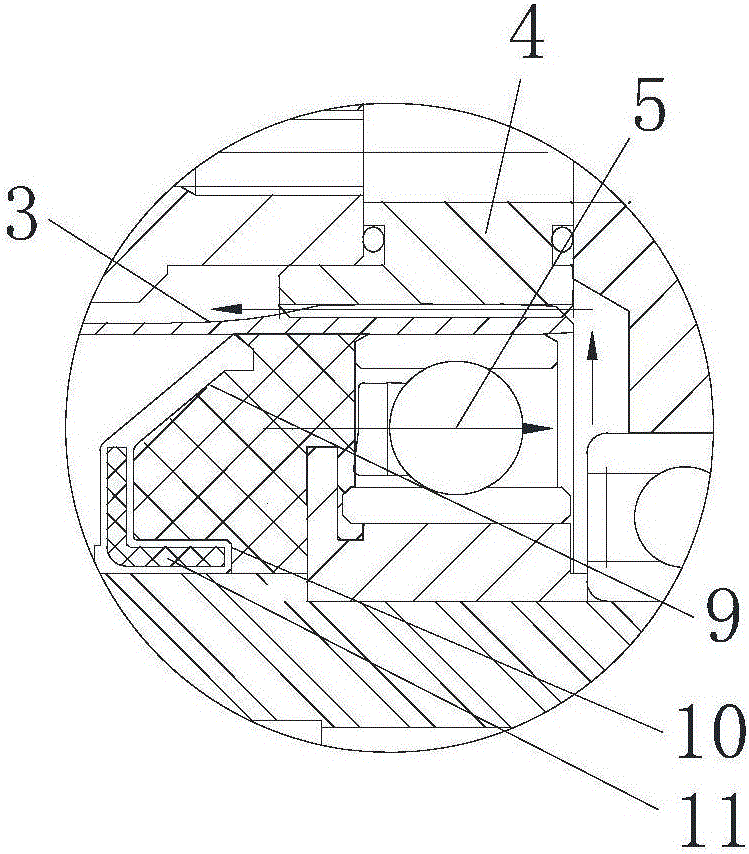
Self-lubricating harmonic reducer
ActiveCN105864365AReduce weightGuaranteed sealing performanceToothed gearingsGear lubrication/coolingHarmonicReduction drive
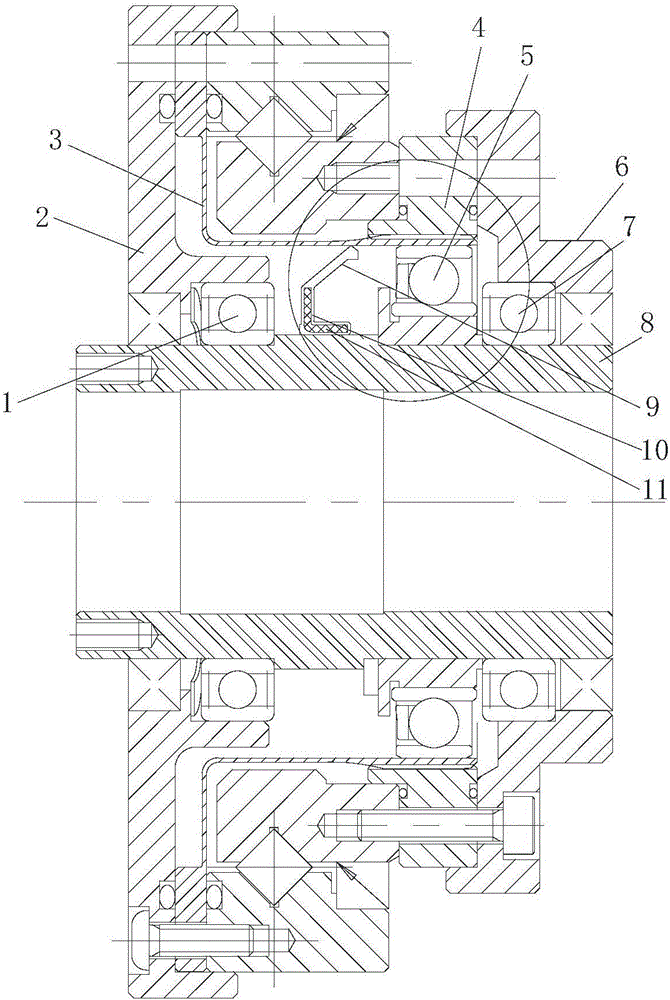
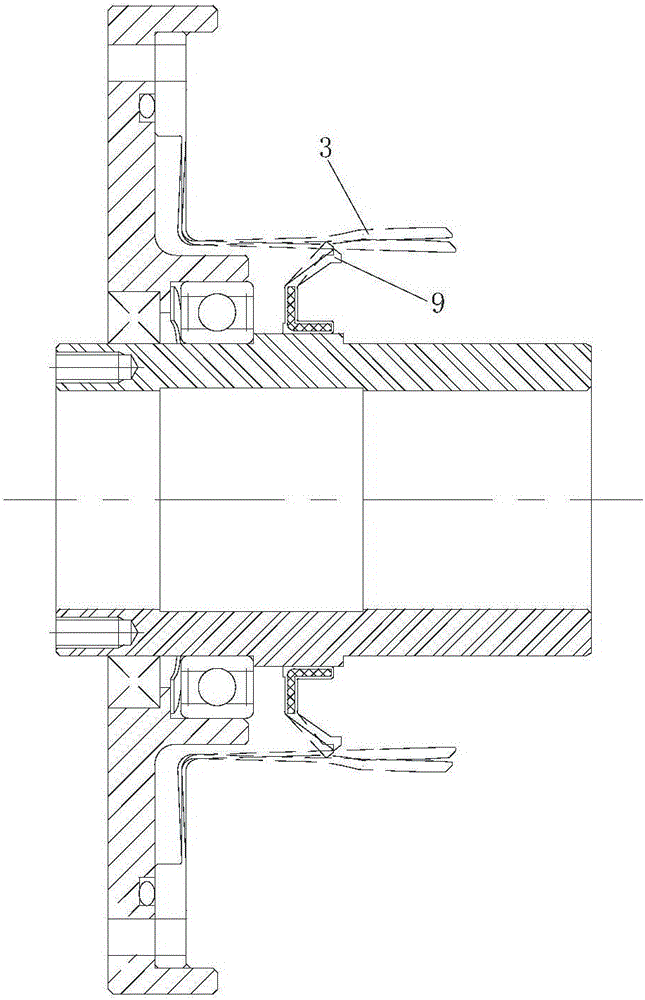
The invention discloses a self-lubricating harmonic reducer. The self-lubricating harmonic reducer comprises a wave generator, a rigid gear and a flexible gear, wherein the rigid gear is meshed with the flexible gear; the wave generator is in contact with the inner wall of the flexible gear; an oil seal is arranged on an input shaft of the wave generator or an output end of the reducer in a sealing manner; a lubricant cavity is formed among the oil sea, the wave generator and the flexible gear; the oil seal comprises a ring-shaped base part; an elastic lip edge overhangs outwards from the outer side wall of the base part; the elastic lip edge is slantly arranged toward the wave generator; the overhanging tail end of the elastic lip edge tightly presses against the inner wall of the flexible gear. According to the reducer disclosed in the invention, the lubricant cavity, rather than the whole cavity in the flexible gear, is filled with the lubricant, so that the weight of the lubricant is decreased; the lubricating supply for the rigid gear and the flexible gear can be completed, and the flowing direction of the lubricant is not influenced by the mounting direction of the harmonic reducer, so that the favorable lubrication for the rigid gear and the flexible gear is ensured, the torn-up scrap iron of the rigid gear and the flexible gear is prevented from flowing back to the flexible bearing along with the lubricant, and the service life of the reducer is prolonged.
Owner:铂睿(山东)精密工业有限公司
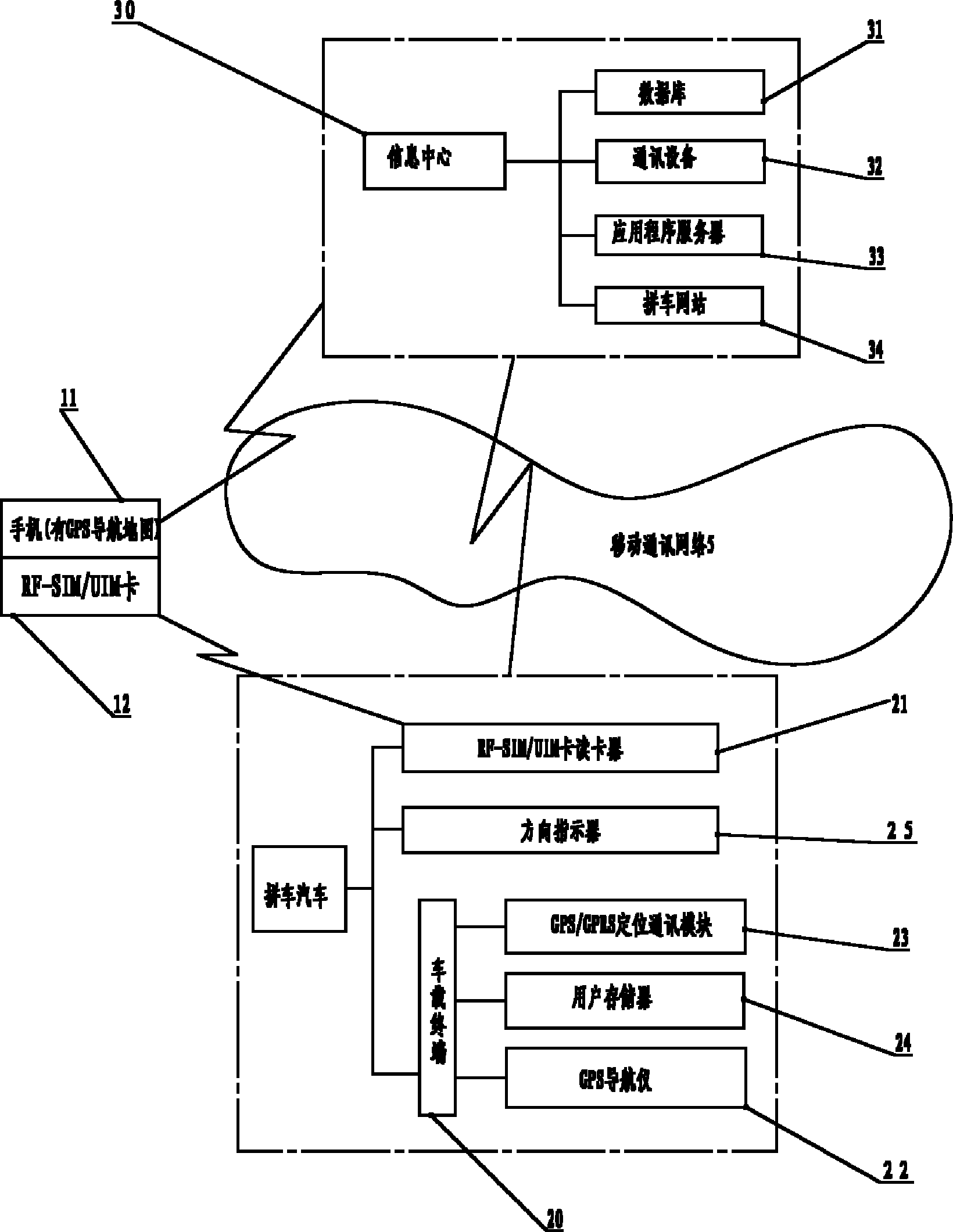
Urban convenient carpooling system and method thereof
InactiveCN102156941AEnsure safetyProtect interestsLocation information based serviceCommerceGps navigationReal-time computing
The invention provides an urban convenient carpooling system and method thereof. The system is provided with a mobile phone of a user, a carpooling car and an information center, wherein a vehicle-mounted terminal, a GPS (Global Positioning System) navigator, a non-contact radio frequency identification card reader and a user memory are arranged in the carpooling car; and the vehicle-mounted terminal is provided with a GPS / GPRS (General Packet Radio Service) positioning communication module. As a data communication passageway and a management platform are provided between a driver and a carpooling user by using the information center and the vehicle-mounted terminal, and the phone number of the user serves as main operation data for the appointment and the implementation of the carpooling, the purpose of independent carpooling between the driver and the carpooling user can be achieved conveniently and quickly. When the carpooling system and method are adopted, the safety, reliability and convenience of the carpooling operation can be ensured, meanwhile the calculation and sharing of the carpooling fee can be realized conveniently and quickly.
Owner:XIAMEN UNIV
Password storing and verifying method and password storing and verifying device
InactiveCN104281794AIncreased complexityReduce the probability of crackingDigital data protectionDigital data authenticationPasswordAuthentication information
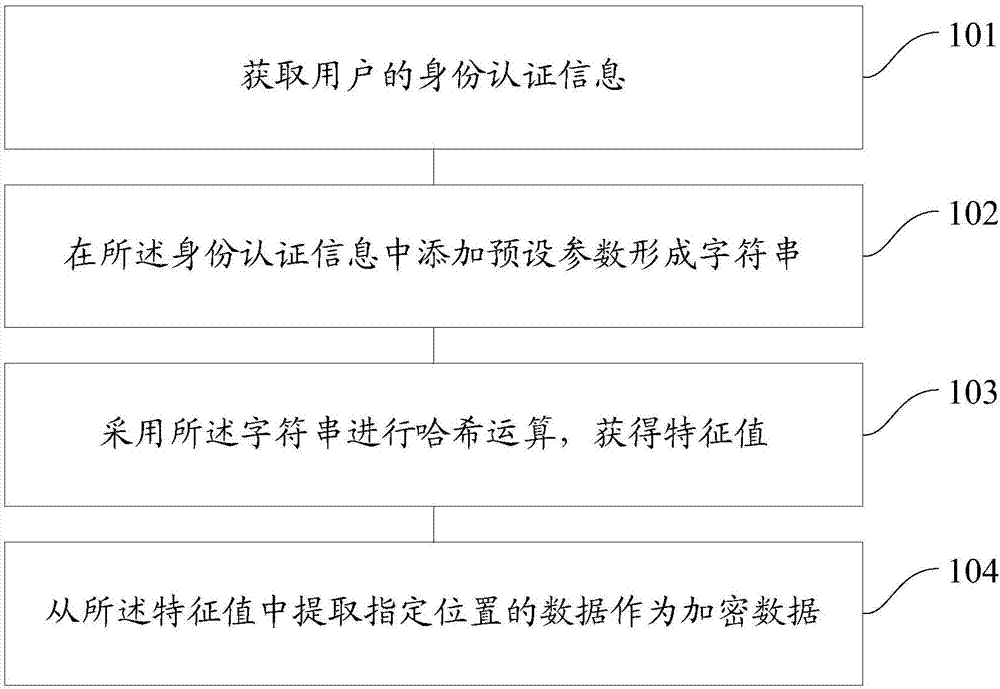
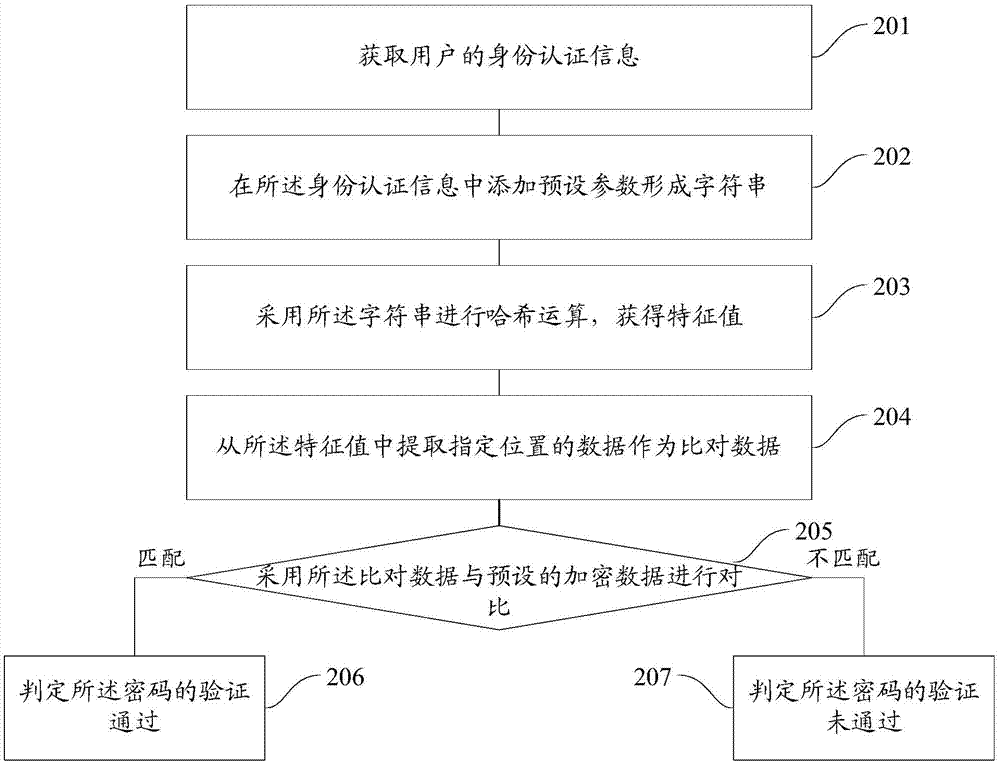
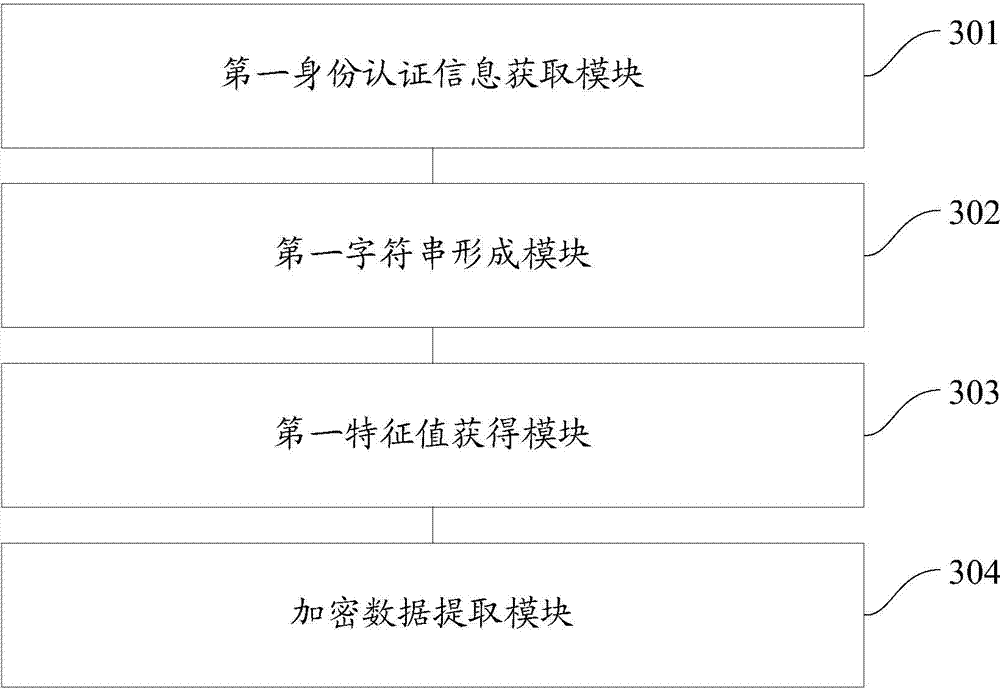
An embodiment of the invention provides a password storing and verifying method and a password storing and verifying device. The method comprises the following steps of acquiring identity authentication information of a user; adding preset parameters in the identity authentication information to obtain a character string; performing Hash operation by using the character string to obtain a characteristic value; and extracting data at an appointed position as enciphered data from the characteristic value. By the password storing and verifying method and the password storing and verifying device, the complexity of passwords of a user can be improved, the defense capability of the passwords of the user can also be improved, Hash collision is avoided or reduced, so that the crack probability of the passwords is reduced, and the passwords of the user are prevented from leaking.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Self-destruction system for memory data
InactiveCN101615235AErase in timeNot to be leakedInternal/peripheral component protectionElectrical resistance and conductanceMicrocontroller
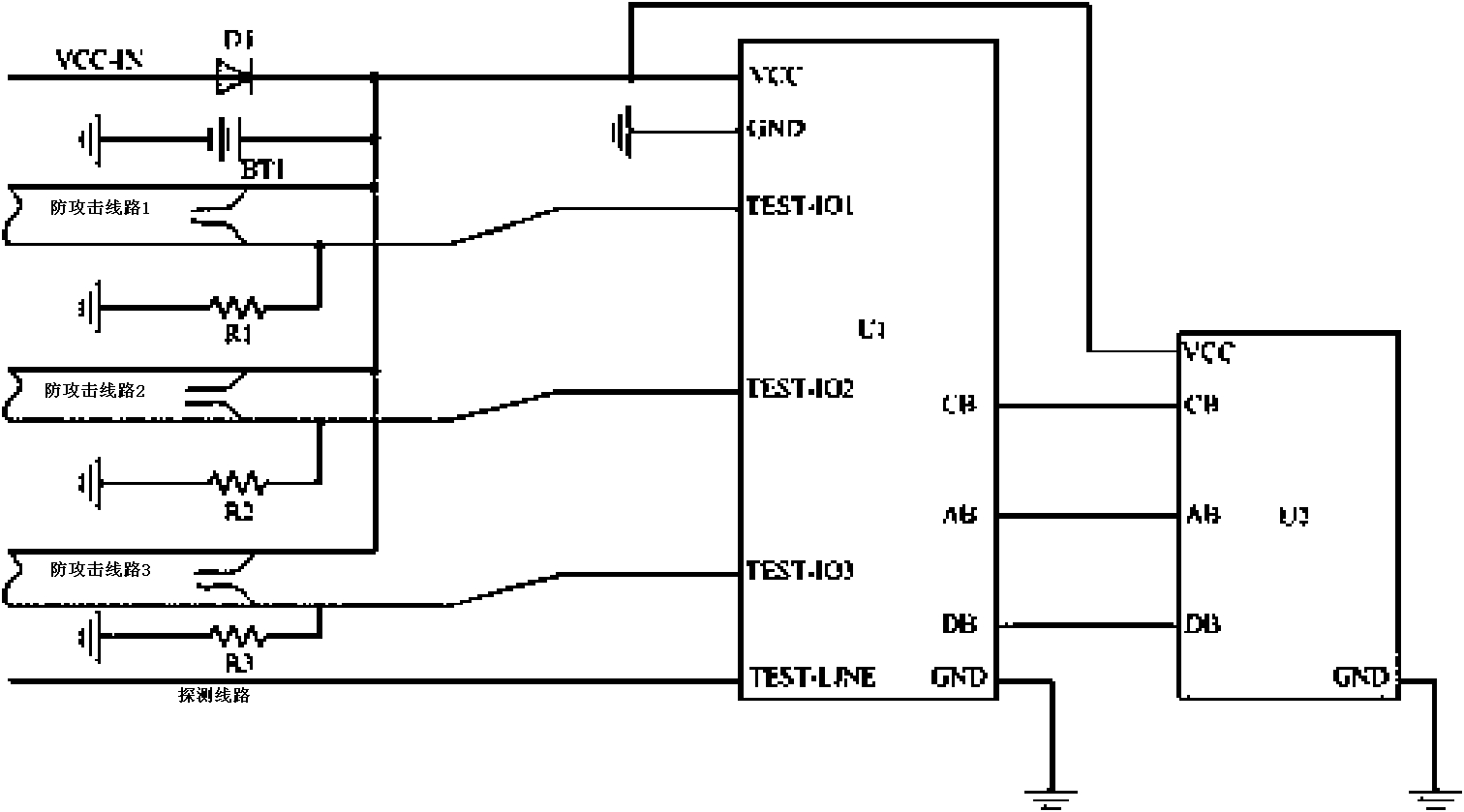
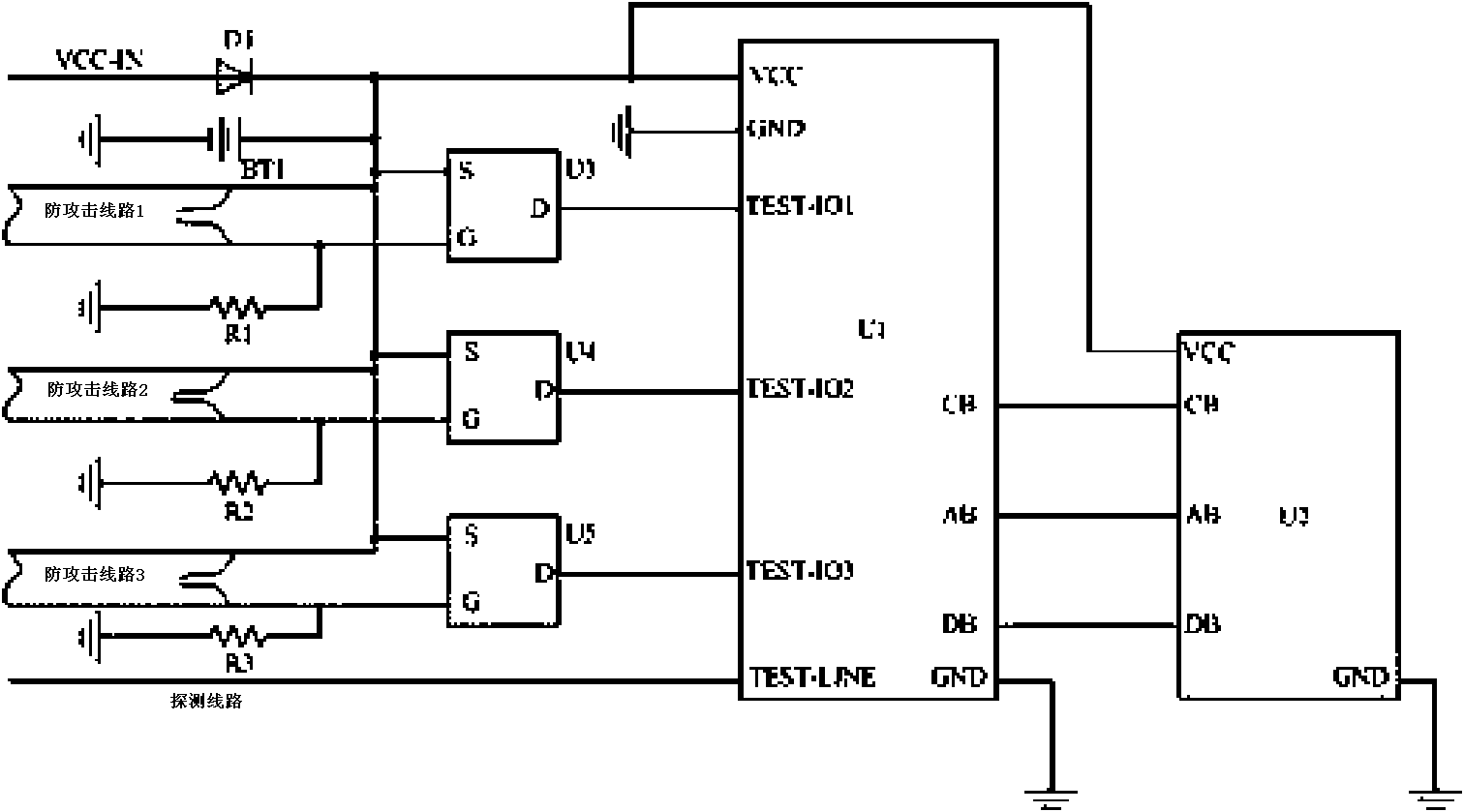
The invention discloses a self-destruction system for memory data, which comprises a mask body, an attack preventing line, a microcontroller and a memory, wherein the mask body is used for physically sealing the memory and the microcontroller; the attack preventing line is wound on the mask body to form a serpentine routing arrangement; one end of the attack preventing line is connected with a power supply, and the other end of the attack preventing line is connected with the microcontroller and is grounded through a resistor; the microcontroller is used for detecting the level change of the other end of the attack preventing line, and erasing at least part of data stored in the memory if the level changes; and the memory is used for storing the data, connecting the microcontroller, and carrying out erasing operation on the data under the control of the microcontroller. In the self-destruction system, the microcontroller detects the level on the attack preventing line and erases the data in the memory if the level changes, so the self-destruction system can accurately learn whether the data are destructed by an external force, erase the data in the memory in time, and ensures that the important data are not divulged.
Owner:HISENSE INTELLIGENT COMML SYST CO LTD
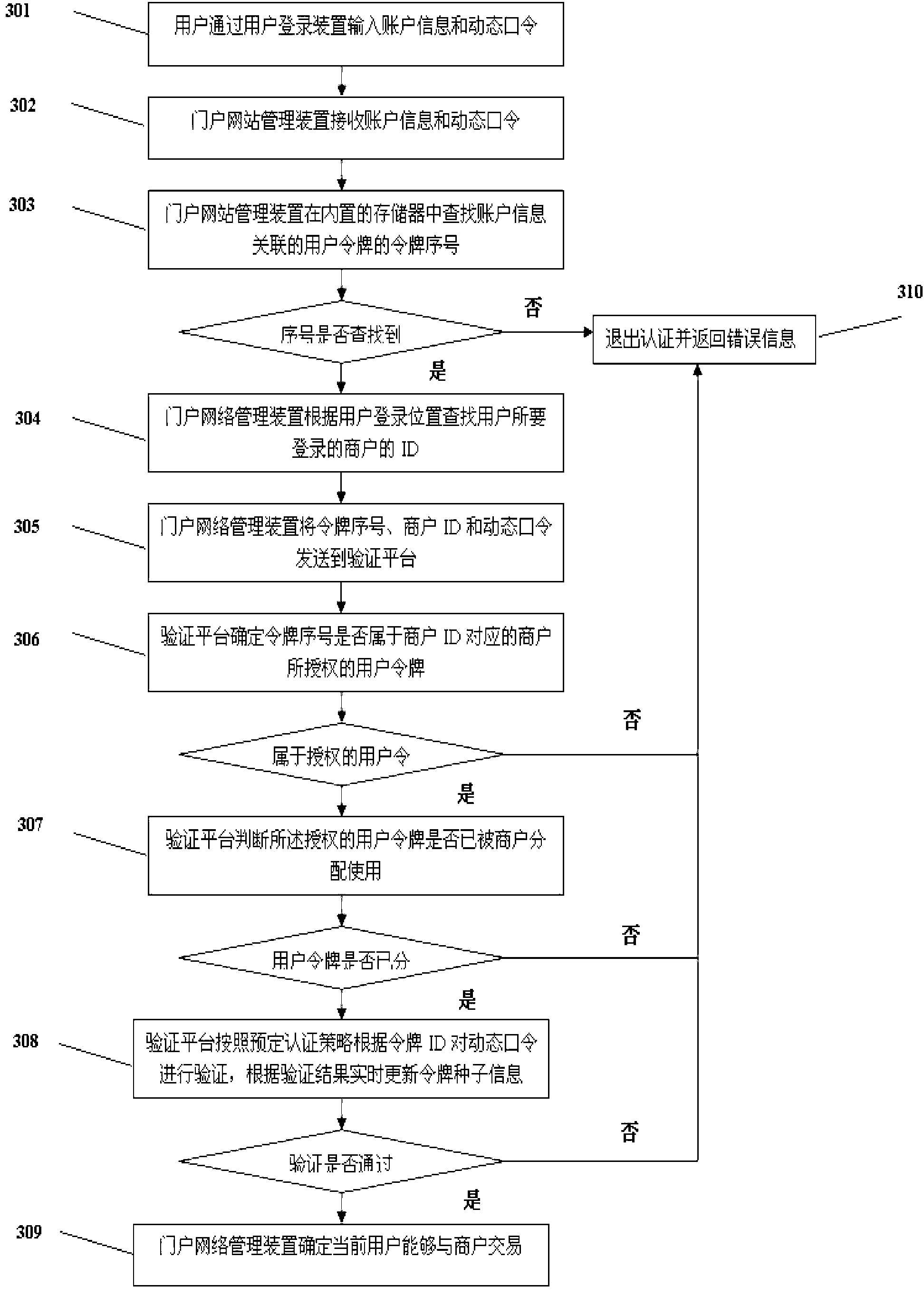
Independent account seamless access dynamic password login system and method
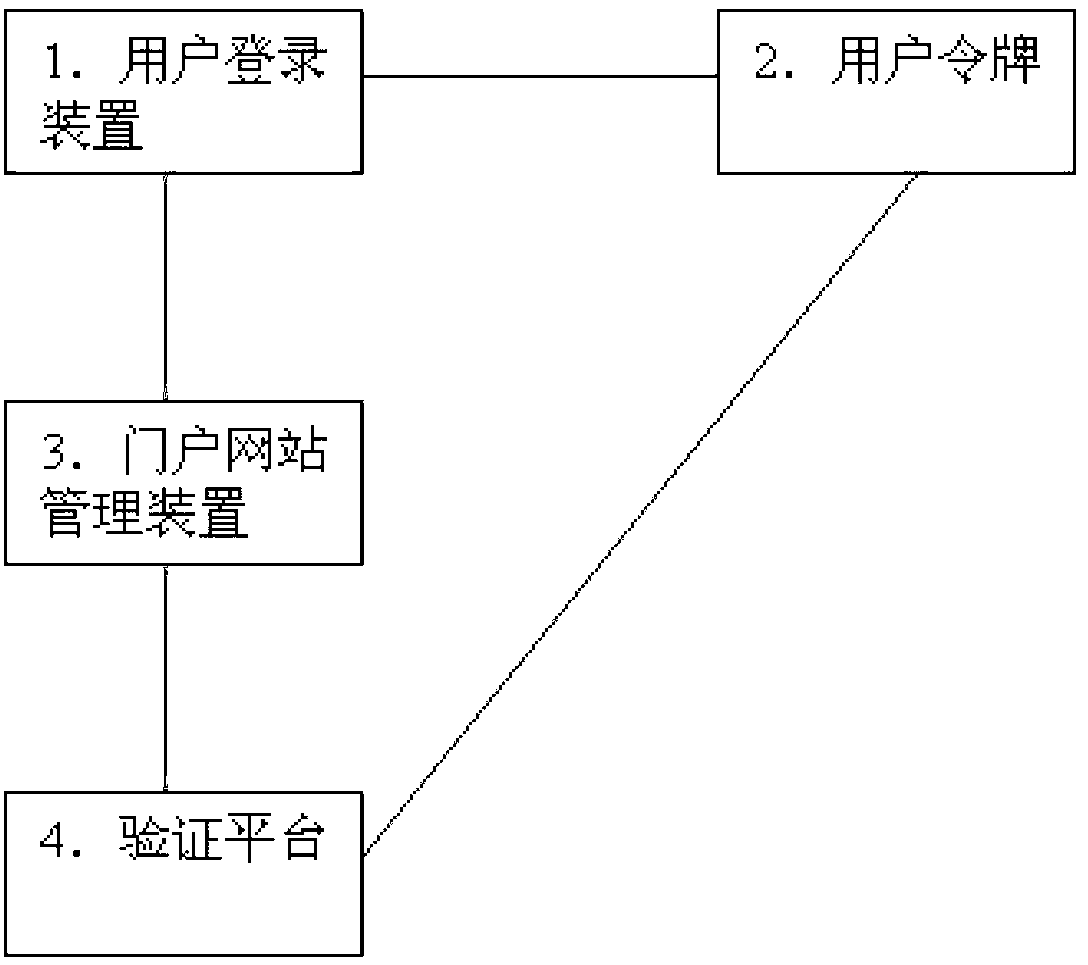
The invention provides an independent account seamless access dynamic password login system and method. The system comprises a user login device, a user token, a user website management device and a verification platform, wherein the user login device is connected with the user website management device, and the user website management device is connected with the verification platform; and the verification platform is connected with the user token. According to the independent account seamless access dynamic password login system and method provided by the invention, the user token and the user account maintenance are arranged at the portal website management device side, thereby avoiding the leakage of client information on a portal website, ensuring the economic interests of a portal website operator, and improving the security of dynamic password login.
Owner:SHANGHAI PEOPLENET SECURITY TECH
Narrow pulse driver of insulation bar power tube
The invention relates to field of MOSFET,IGBT drive circuit, specially a kind of MOSFET,IGBT narrow pulse driver which is electricity separated and without separating power source, the driver includes three parts: Signal transforming and drive, pulse transformer, electronic switch. The signal transforming circuit transforms the high or low level of input signal to high narrow pulse or low narrow pulse with definite frequency, the input signal is modulated by the high frequency narrow pulse signal, the power tube drives the pulse transformer, and charges the gate of the power tube under the control of electronic switch to form positive pressure or negative pressure. When the narrow pulse signal is generated, the electronic switch is opened, when it is diminished, the electronic switch is closed. It uses the gate capacitance to maintain gate pressure, because it adopts the narrow pulse drive, the capacity of the pulse transformer is small, without separating power source, and can maintain the dredge or cut off of the power tube.
Owner:满会生
Simple and easy express waybill and rapid express sorting and delivery method
InactiveCN105741157ANot to be leakedBuying/selling/leasing transactionsLogisticsPCI ExpressComputer science
The invention relates to a simple and easy express waybill and a rapid express sorting and delivery method. The simple and easy express waybill comprises six areas and seven information sources, wherein the seven information sources are generated by an express management center system, and is used for obtaining information in the whole express service process. Through the first information source, the expresses are rapidly classified according to intra-city, district, intra-province and other provinces, so that the intra-city expresses are distributed to the customers in the shortest time; and in the whole express delivery process, express information is provided through the simple and easy express waybills and the background express management center system, so that the personal information of the customers is protected from disclosure.
Owner:NINGXIA XIBULANGQUN GREEN TECH CO LTD
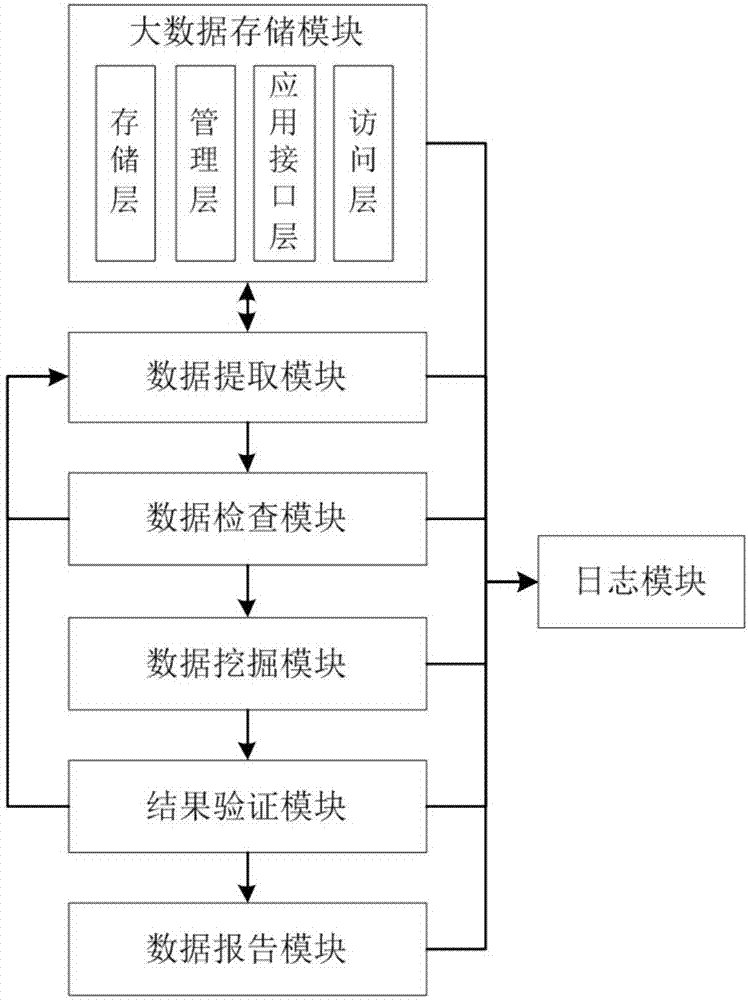
Big data mining system
ActiveCN107577771APowerful load balancing functionImprove management efficiencySpecial data processing applicationsData ingestionData set
The invention relates to a big data mining system which comprises a big data storing module, a data extracting module, a data checking module, a data mining module, a result verifying module, a data reporting module and a log module. The data extracting module extracts a data set meeting user requirements from the big data storing module and sends the data set to the data checking module. The datachecking module checks the integrity of the data set, filters the data set, removes wrong or inconsistent data in the data set to ensure the effectiveness of the effective data set and sends the filtered effective data set to the data mining module. The data mining module mines and analyzes the effective data set by means of various mining algorithms, the big data mining accuracy can be improved,and user private information can be protected from leakage. The result verifying module verifies the accuracy of the data mining result. The data reporting module generates a data report according tothe data mining result. The log module records the log data generated in the data mining process.
Owner:北京海融兴通信息安全技术有限公司
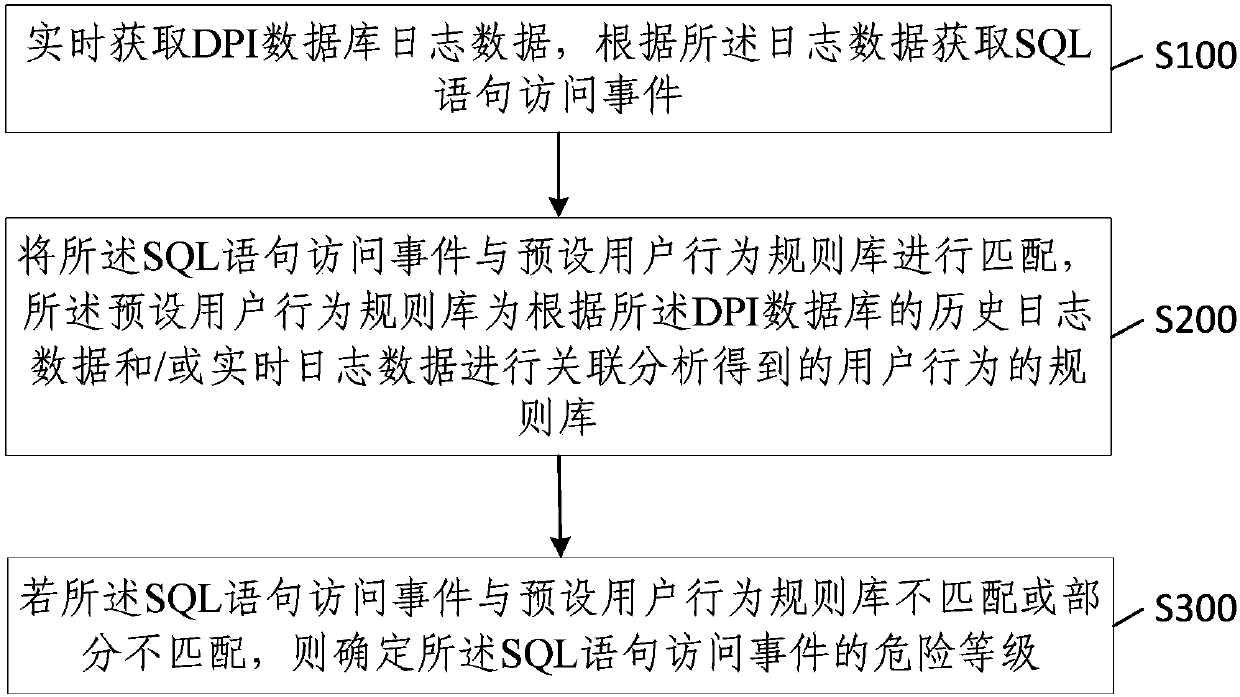
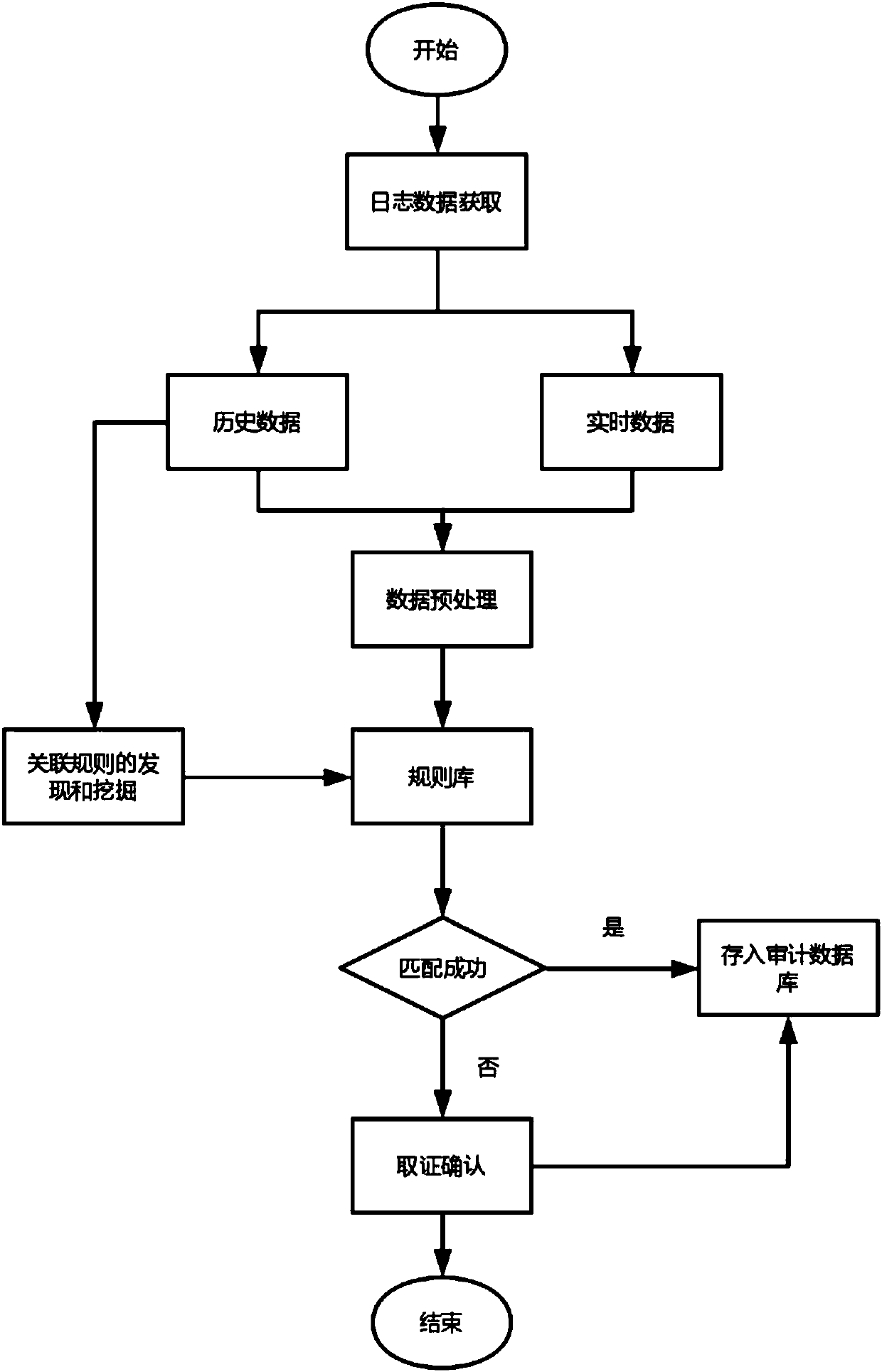
Database security auditing method and device and electronic equipment
ActiveCN109977689ANot to be leakedEffective reasoningDigital data protectionDatabase securityData mining
The invention provides a database security auditing method and device and electronic equipment. The method comprises the steps of obtaining DPI database log data in real time, and obtaining an SQL statement access event according to the log data; matching the SQL statement access event with a preset user behavior rule base, wherein the preset user behavior rule base is a rule base of user behaviors obtained by performing association analysis according to historical log data and / or real-time log data of the DPI database; and if the SQL statement access event is not matched with a preset user behavior rule base or partially not matched with the preset user behavior rule base, determining the danger level of the SQL statement access event. According to the method, the association rule can beadjusted according to the structural change of the database and the new behavior of the user, the user behavior is dynamically discovered, and the auditing strategy is adjusted, so that the method adapts to different application scenarios and novel user behaviors, and an effective database security guarantee can be provided.
Owner:CHINA MOBILE GRP GUANGDONG CO LTD +1
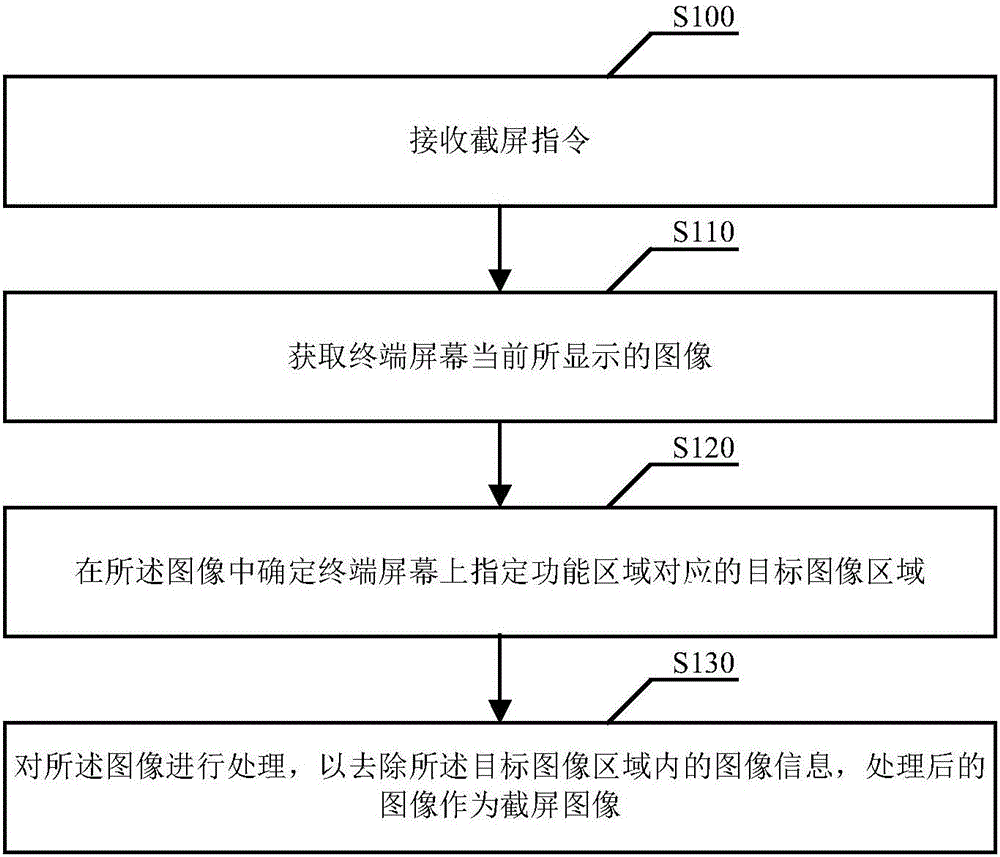
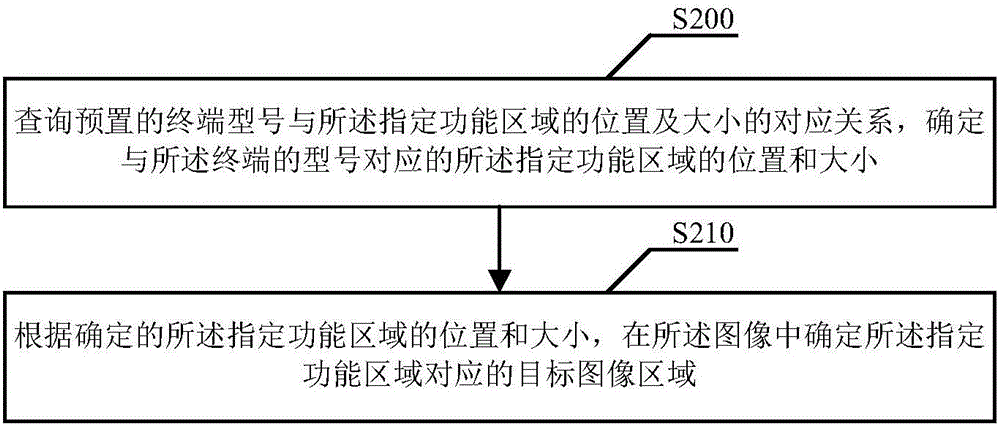
Screen-shooting method and device
InactiveCN106775333ANot to be leakedGuaranteed privacy and securityImage enhancementImage analysisSpecific functionImage display
The invention discloses a screen-shooting method and device. The method comprises the steps of receiving a screen-shooting command; obtaining an image displayed currently on a terminal screen; determining a target image area corresponding to a specific function area on the terminal screen in the image; processing the image to remove image information in the target image area, and adopting the processed image as a screen-shooting image. As can be seen, after the image displayed currently on the terminal screen is screen-shot, the target image area corresponding to the specified function area on the terminal screen is determined in the image, instead of directly adopting the image as a screen-shooting image, the image information in the target image area is further removed, and the processed image is adopted as the screen-shot image. According to the screen-shooting method and device, it is guaranteed that the image information in the specific function area is not leaked, and the privacy safety of a user is guaranteed.
Owner:SHENZHEN IPANEL TECH LTD
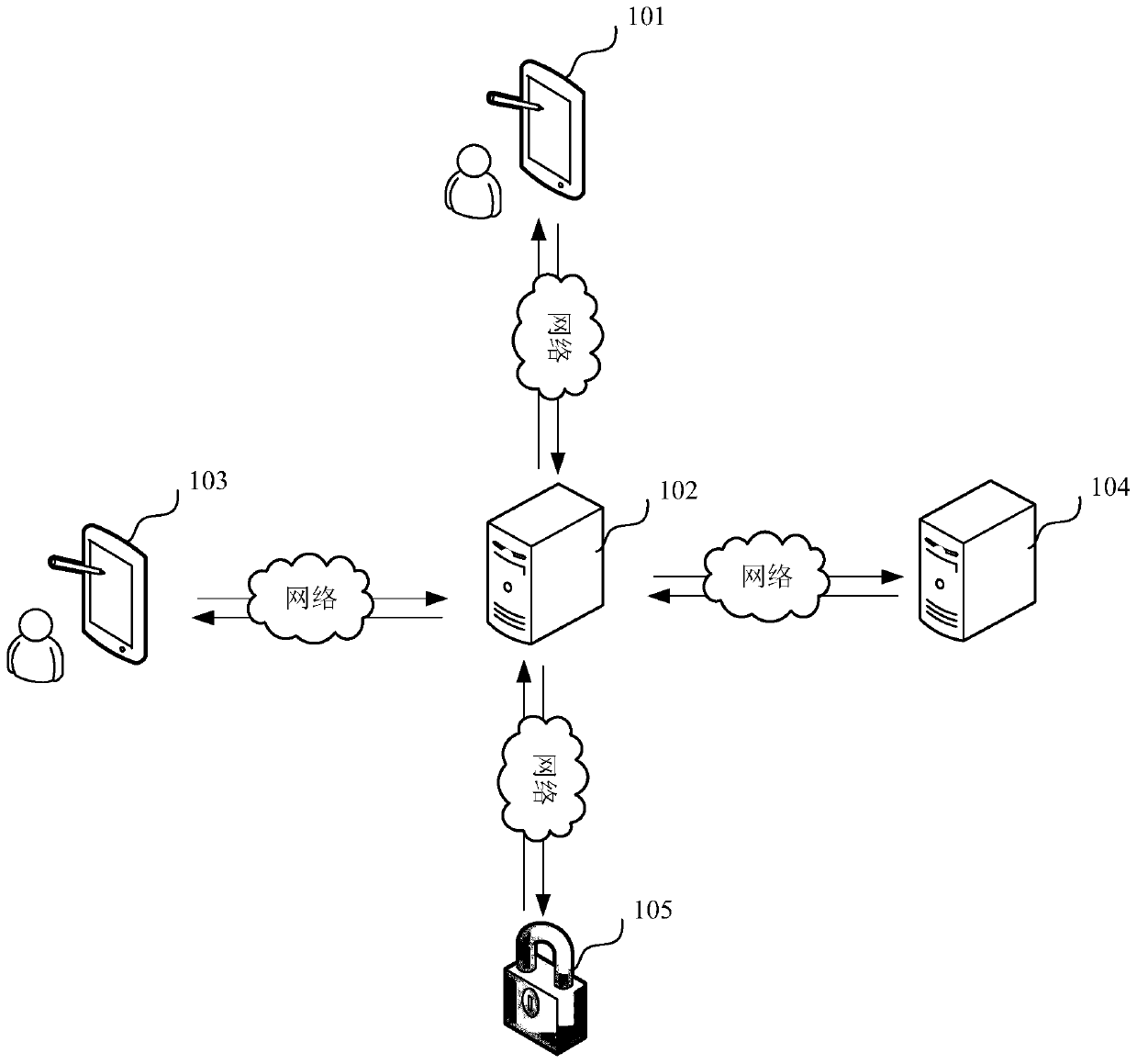
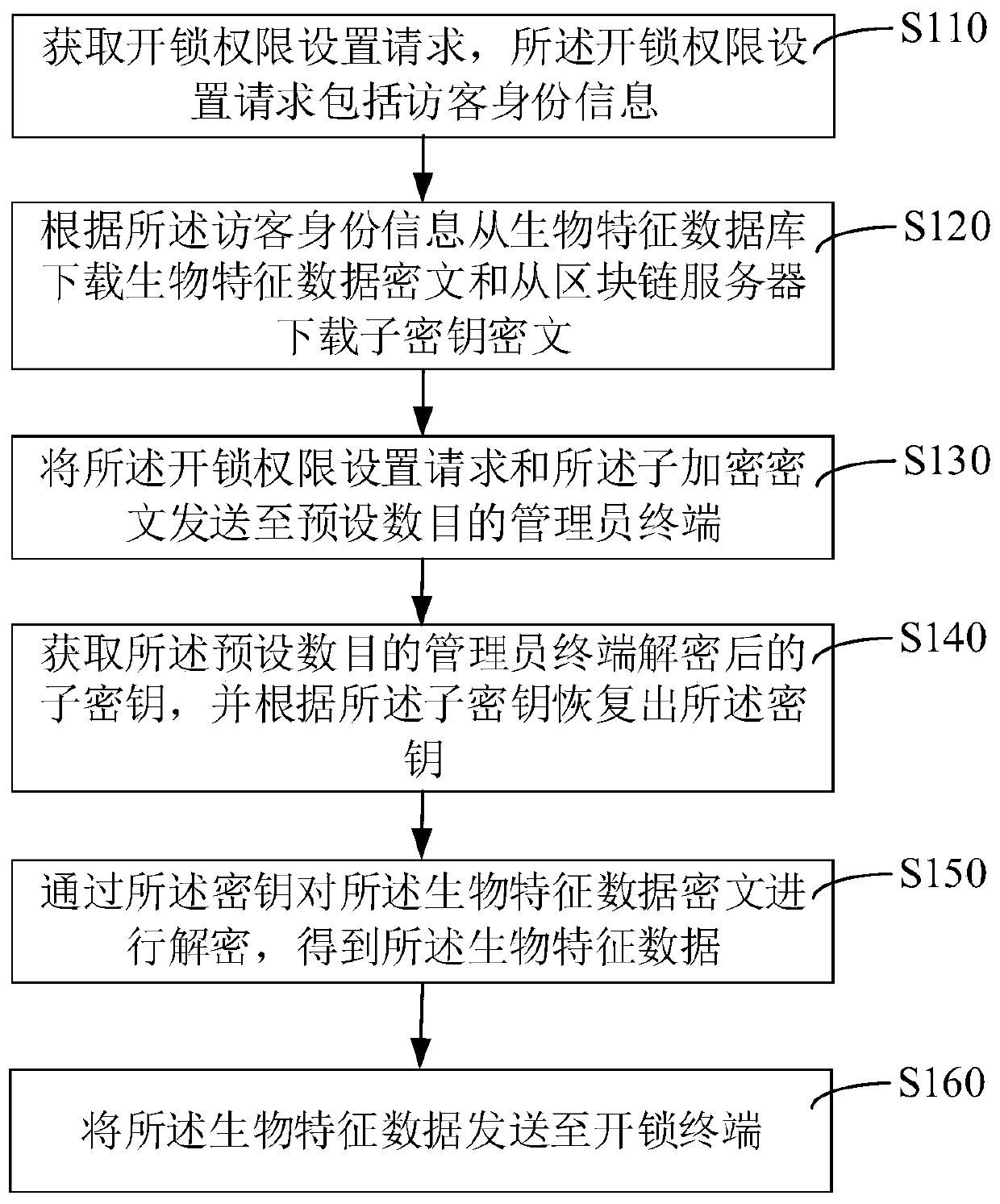
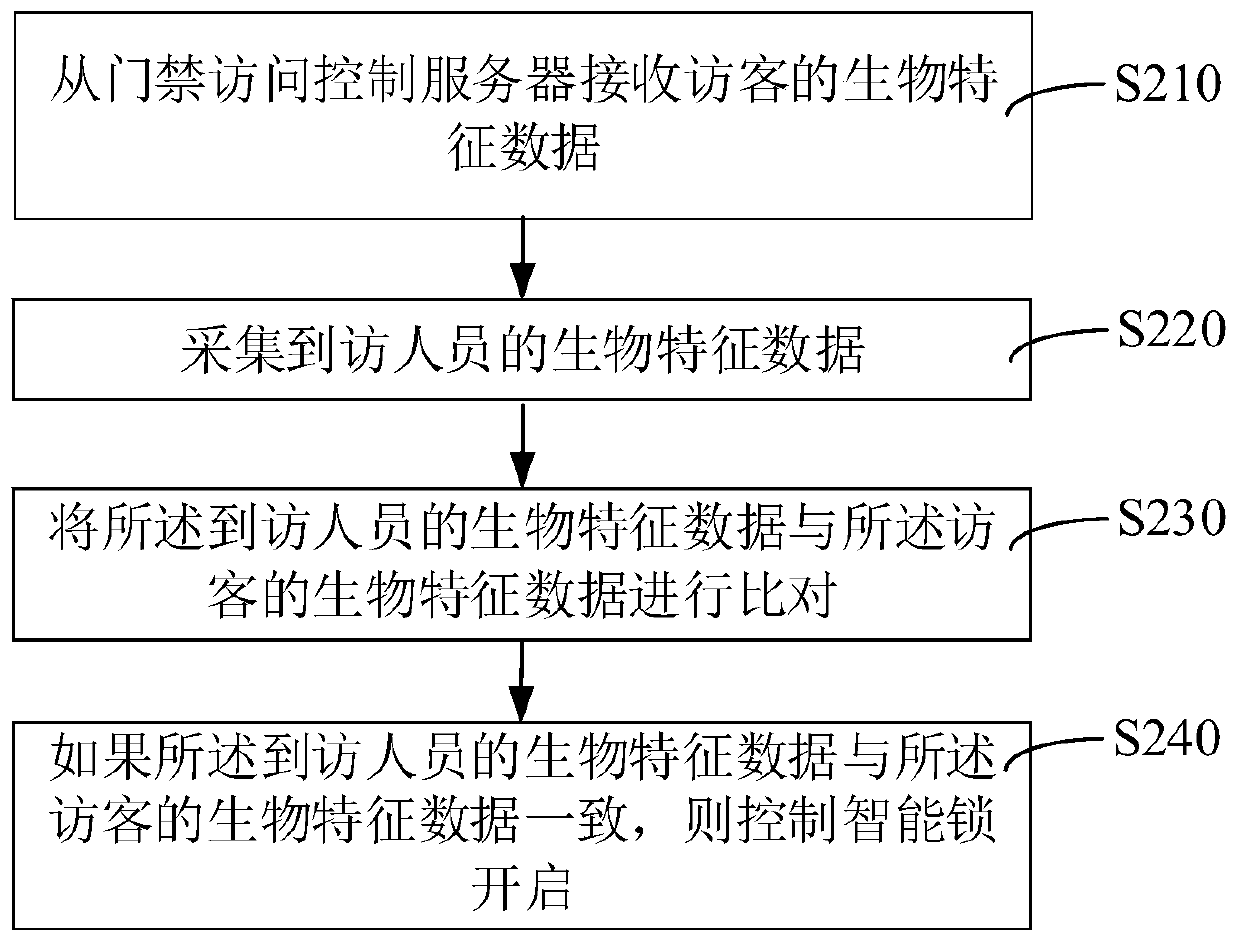
Blockchain-based access control method and device
ActiveCN110706379AImprove securityNot to be leakedKey distribution for secure communicationIndividual entry/exit registersCiphertextInternet privacy
The invention relates to a blockchain-based access control method and device. The method comprises the steps of: obtaining an unlocking permission setting request, wherein the unlocking permission setting request comprises visitor identity information; downloading a biological feature data ciphertext from a biological feature database and downloading a subkey ciphertext from a blockchain server according to the visitor identity information; sending the unlocking permission setting request and the subkey ciphertext to a preset number of administrator terminals; obtaining subkeys decrypted by the preset number of administrator terminals, and restoring the key according to the subkeys; decrypting the biological feature data ciphertext via the key to obtain biological feature data, wherein thekey is destroyed after the biological feature data are obtained; and sending the biological feature data to an unlocking terminal, wherein the unlocking terminal performs unlocking according to the biological feature data. By adopting the method, the safety of the biological feature data for smart locks can be improved.
Owner:GRG BAKING EQUIP CO LTD +1
A method for protecting privacy information of users and a terminal
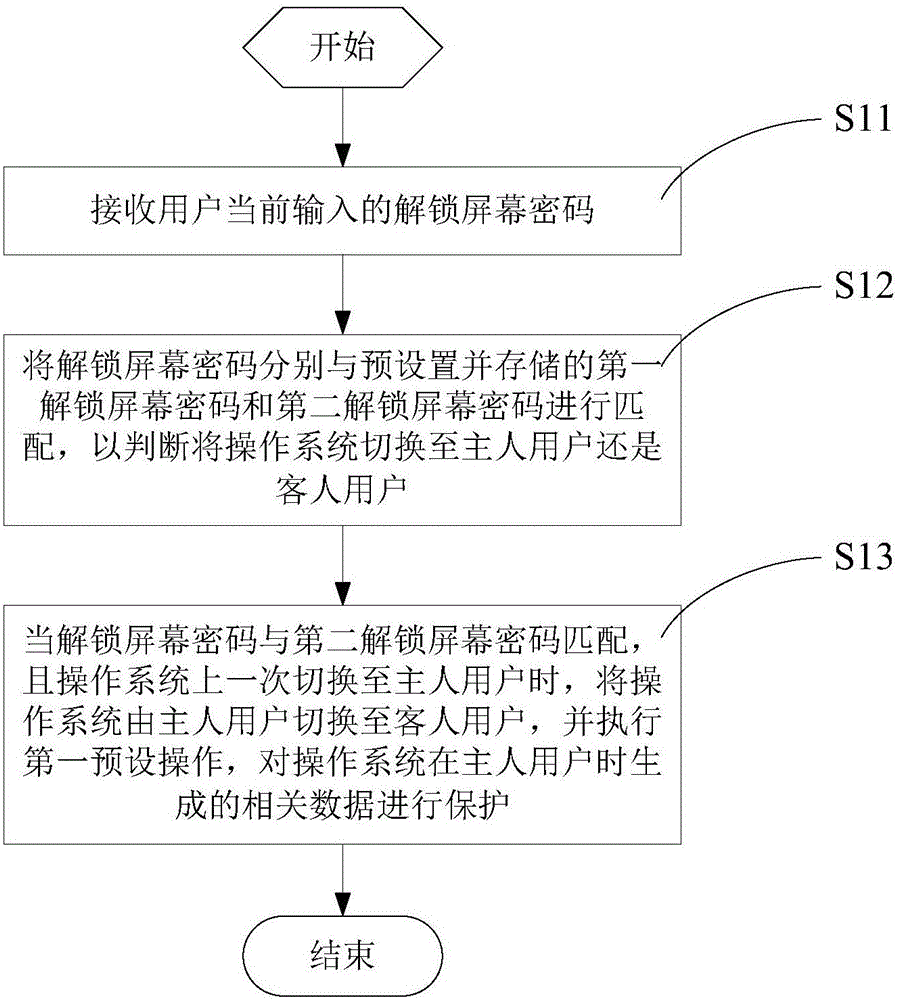
ActiveCN106127077AImplement encryptionNot to be leakedDigital data protectionSubstation equipmentOperational systemUser input
The invention provides a method for protecting privacy information of users and a terminal. The method comprises the steps of setting different screen unlocking passwords for different using users of a terminal; by matching a screen unlocking password input by a user and the screen unlocking passwords corresponding to owner users and guest users, judging whether an operating system is switched to the owner user mode or guest user mode; when it is needed to switch the operating system from the owner user mode to the guest user mode, performing a first presetting operation including setting file reading / writing permission on related data generated when the operating system is in the owner user mode, hiding database files of to-be-protected applications, and backing up system setting data to encrypt the privacy information of a user. Therefore, when a terminal is operated by others, by performing the first operation, the others cannot visit information in the terminal and modify some information freely, so that the privacy information of a user in the terminal can be protected against leakage.
Owner:THUNDER SOFTWARE TECH
Method and device for website account login, verification and verification information processing and system
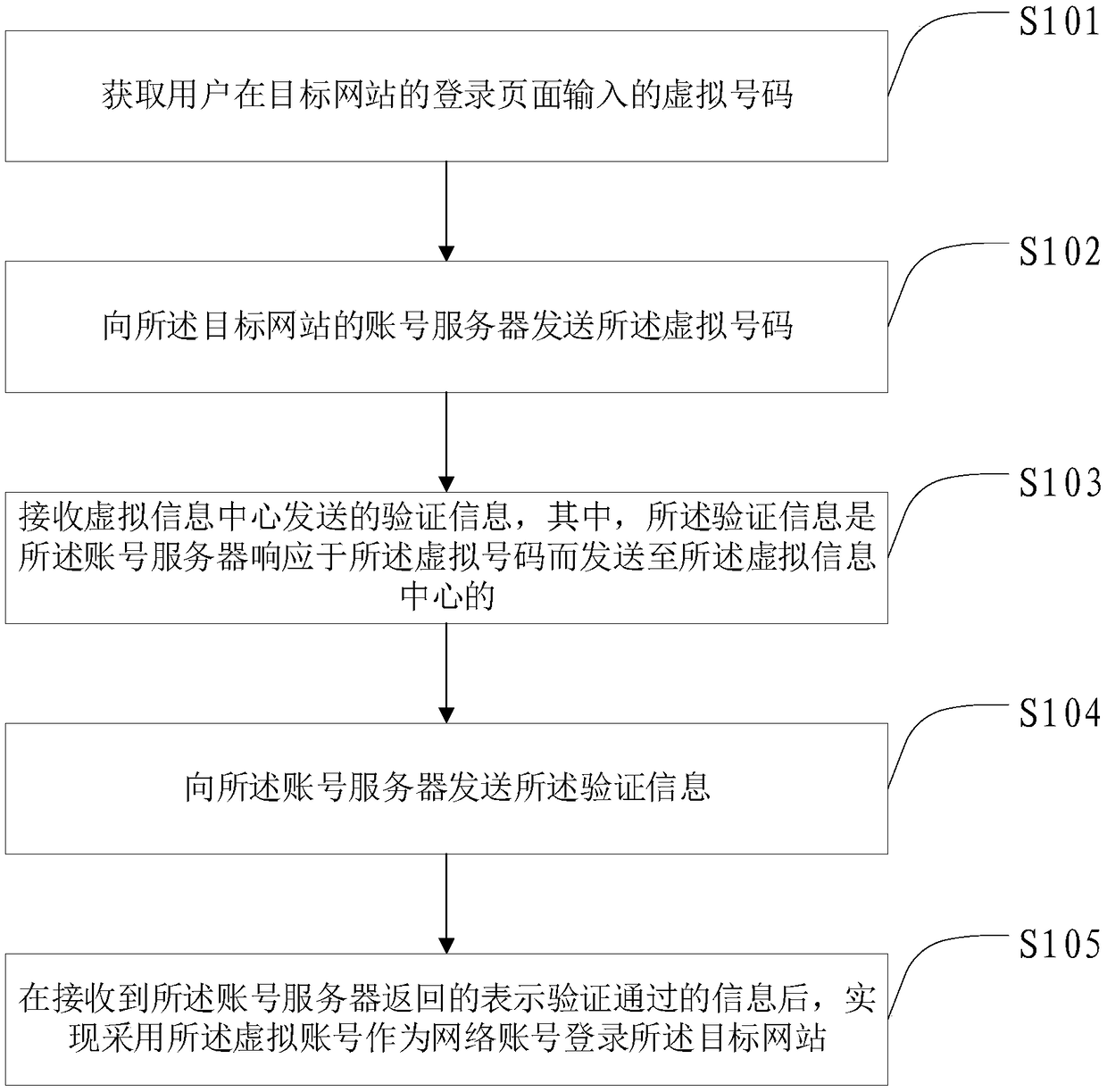
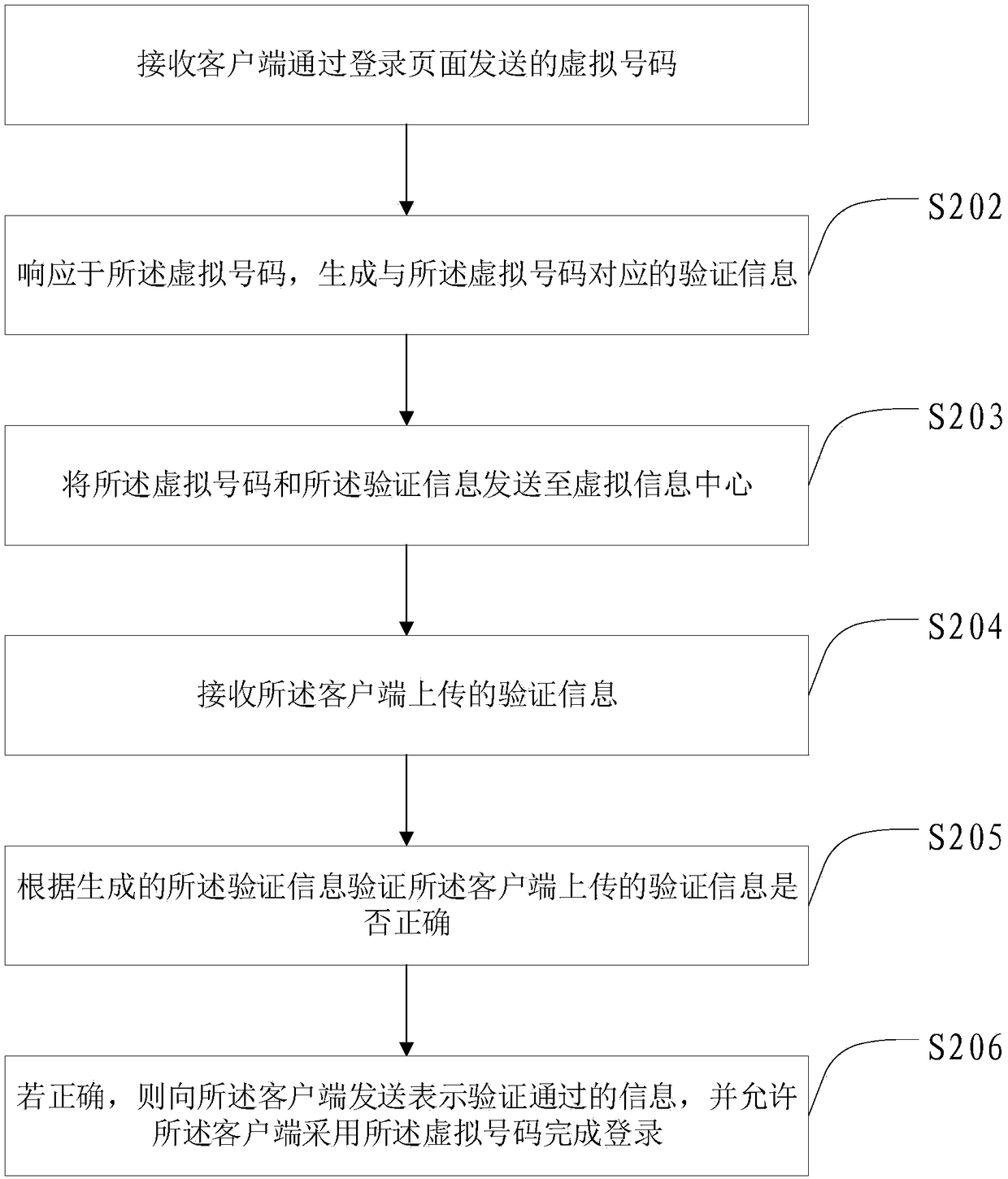
The invention provides a method and device for website account login, a method and device for login verification, a method and device for verification information processing and a website account login system. The website account login method comprises the steps that a virtual number input in a login page of a target website by a user is acquired; the virtual number is sent to an account server ofthe target website; verification information sent by a virtual information center is received; the verification information is sent to the account server; after information which represents that theverification is valid and is returned by the account server is received, it is achieved that a virtual account is adopted to serve as a network account to login the target website. Compared with the prior art, the virtual number is adopted to replace a phone number to login the website, so that it is avoided that the phone number is known by the website, thereby being capable of ensuring that thephone number of the user is not disclosed by the website.
Owner:BEIJING GZT NETWORK TECH
Automatic destruction structure for information of electronic equipment
InactiveCN104200174AImprove stability and reliabilityAutomatic prompt destructionDigital data protectionInternal/peripheral component protectionElectrical batteryEngineering
The invention provides an automatic destruction structure for information of electronic equipment. The automatic destruction structure comprises a chassis of the electronic equipment, a key destruction switch module arranged on the inner side of the wall of the chassis and a secrete key storage plate in the chassis. The secrete key storage plate comprises a key destruction switch plug, a storage chip and a battery, and an information erasing program is set in the storage chip. The key destruction switch module comprises a key destruction switch, the key destruction switch is provided with a switch head, and the key destruction switch module forms an information destruction circuit with the secrete key storage plate and the battery through the key destruction switch plug, wherein the information destruction circuit can be closed. A normal working state is determined for the switch head in advance, after the normal working state is changed, the information destruction circuit formed by the key destruction switch module, the battery and the storage chip is closed, the battery supplies power to the storage chip, an information erasing program is started, and secrete key information on the storage chip is destructed. The automatic destruction structure for the information of the electronic equipment has the advantages of having an automatic destruction function and a manual destruction function and being good in device concealing performance and high in device stability and reliability.
Owner:成都卫士通信息产业股份有限公司
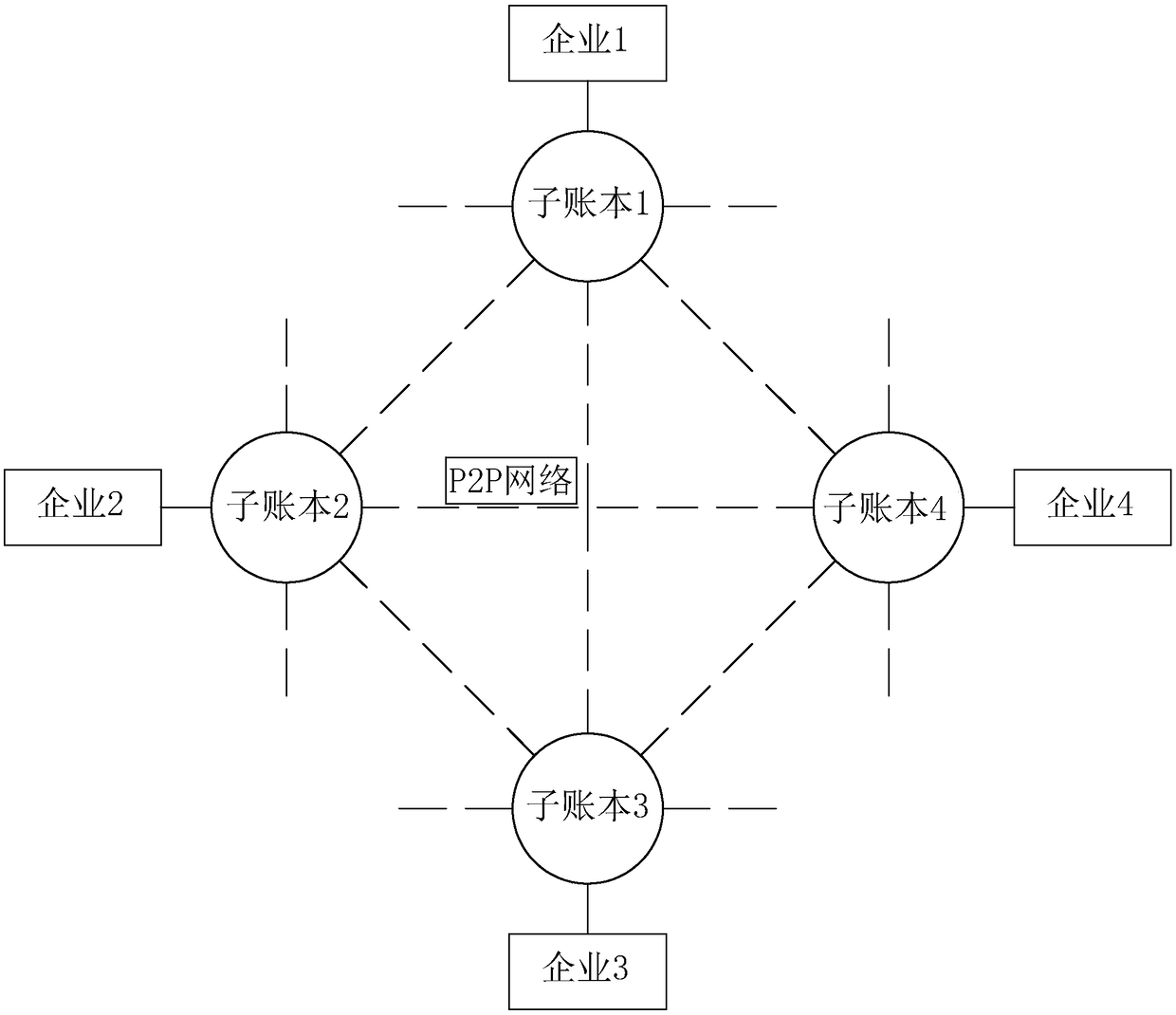
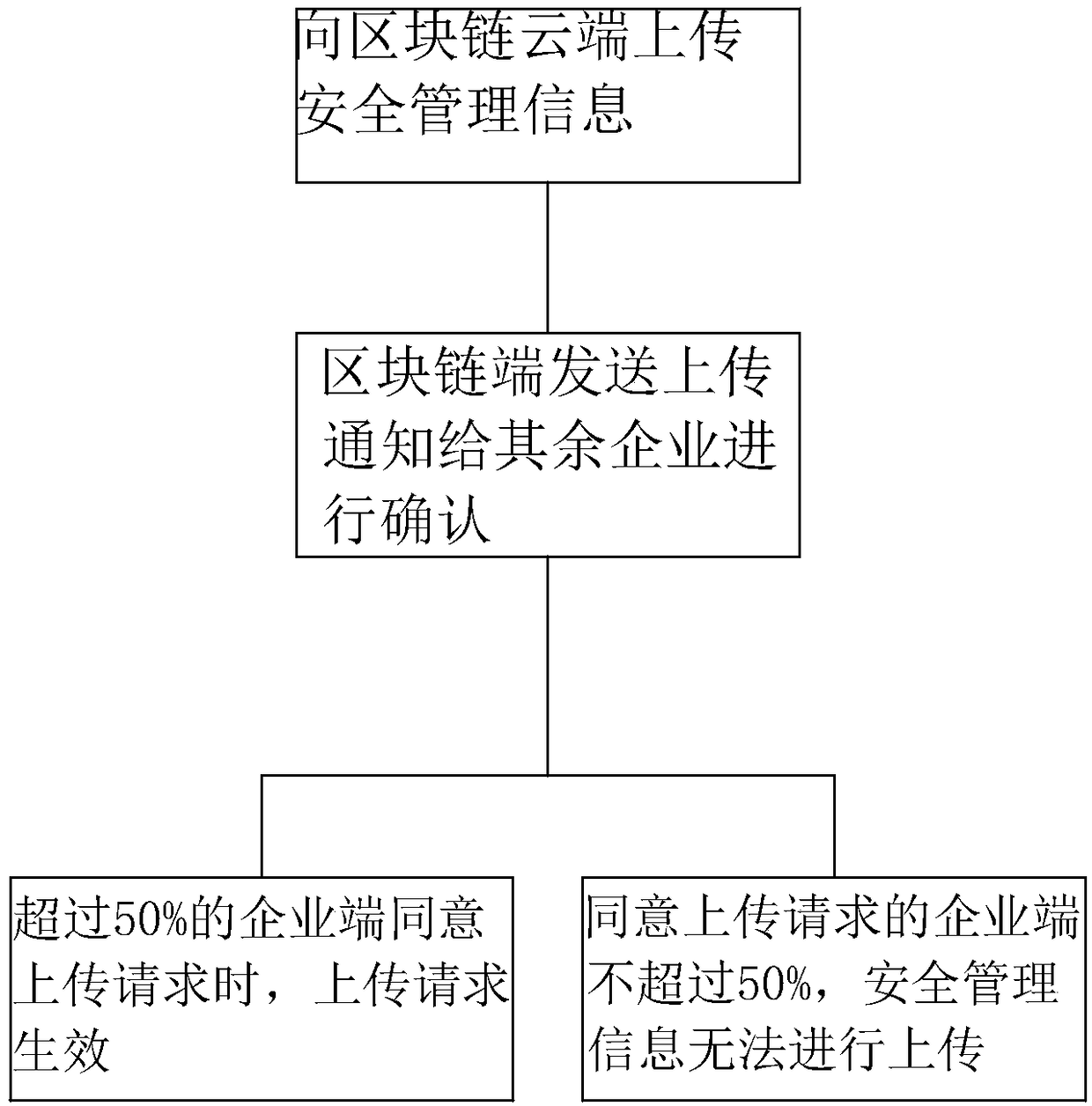
Safety production information sharing method based on block chain technology
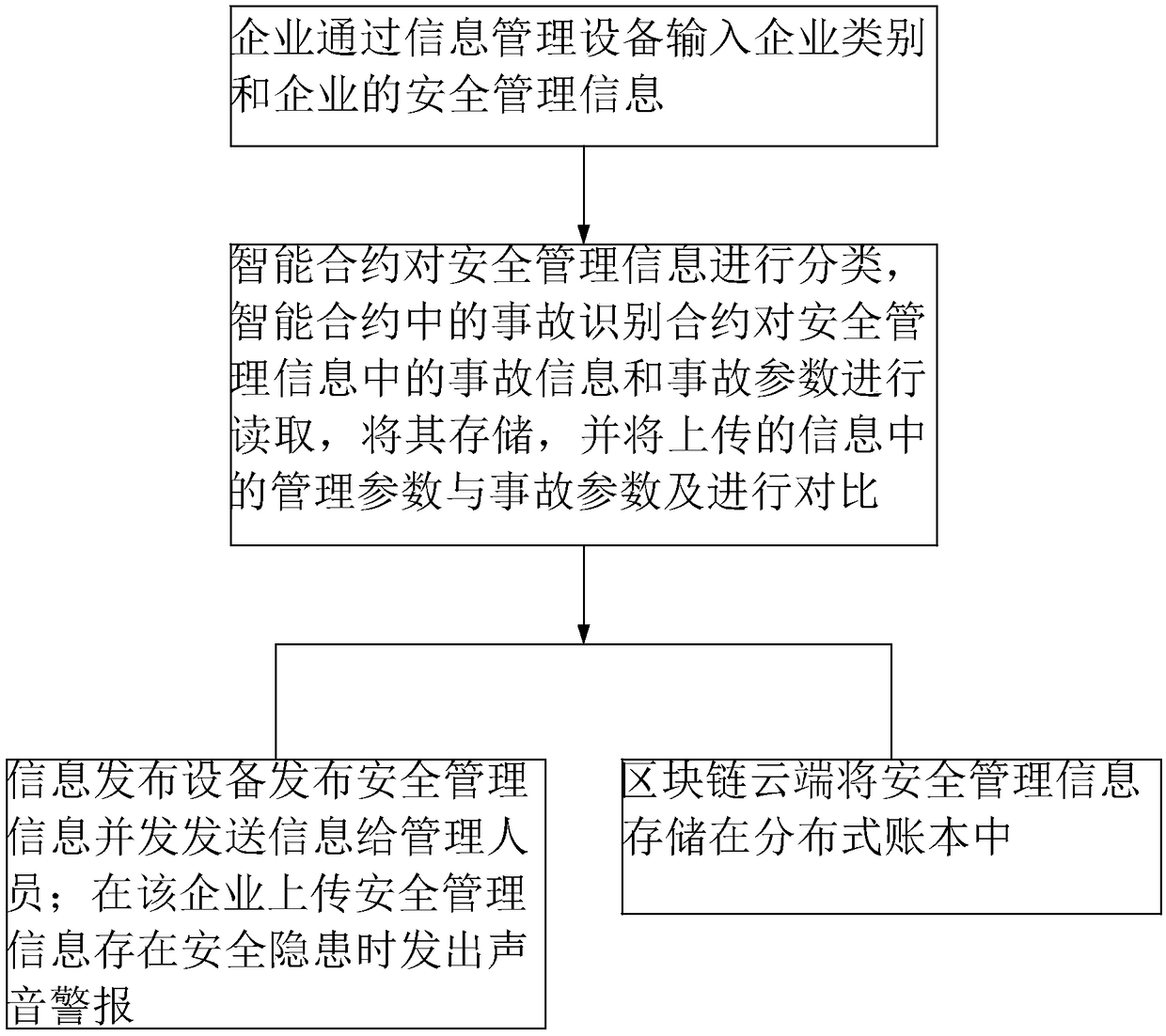
ActiveCN108920978ANot to be leakedAvoid lossDigital data protectionResourcesInformation sharingEnterprise integration
The invention discloses a safety production information sharing method based on a block chain technology, and belongs to the technical field of safety production information sharing. The safety production information sharing method is characterized in that an enterprise end is provided with information managing equipment and information publishing equipment; through the information managing equipment, the type and safety management information of an enterprise are input, and the information managing equipment uploads the safety management information to a block chain module; through an intelligent contract of the block chain, the uploaded safety management information is classified, the safety management information of the corresponding type is sent to the information publishing equipmentof the enterprise of the corresponding type, and the safety management information is publicized; the block chain module saves the safety management information uploaded through a distributed information account book. The problems are solved that in transmission sharing of existing production safety information, resource enterprise information easily leaks, and the transmission information has asymmetric lag; the enterprise can timely receive the safety management information in the field, and the leakage of the enterprise information in the information sharing process is reduced.
Owner:赛飞特工程技术集团有限公司
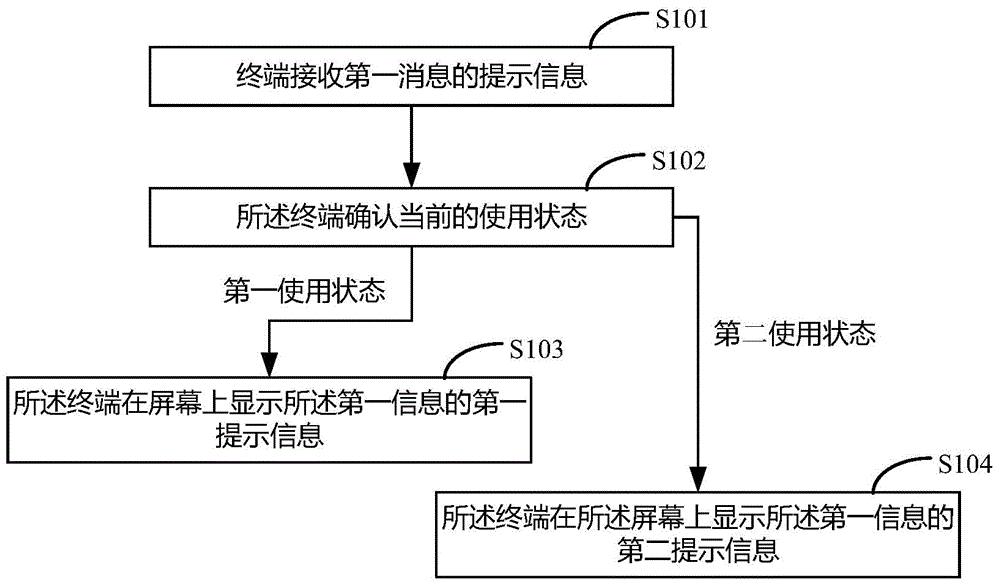
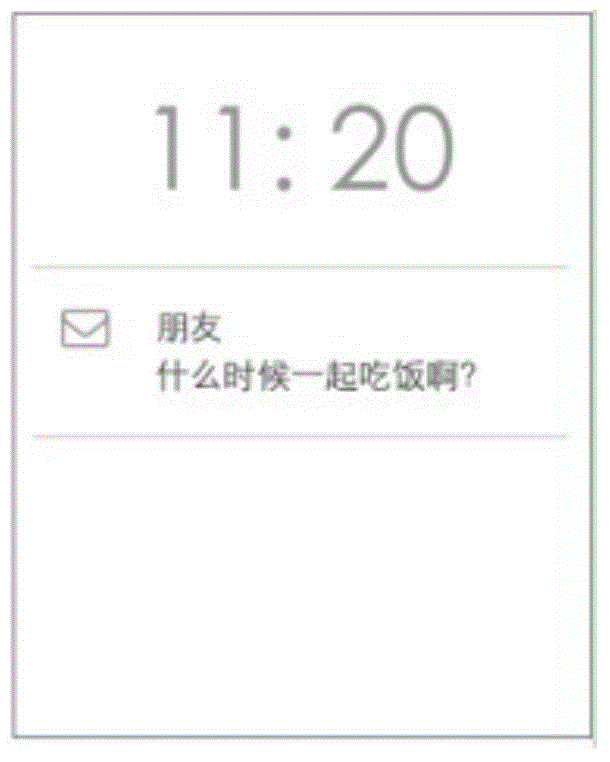
Display method and apparatus of reminding messages
InactiveCN105824588ANot to be leakedImprove securitySubstation equipmentMessaging/mailboxes/announcementsComputer terminalComputer science
Owner:ALIBABA GRP HLDG LTD
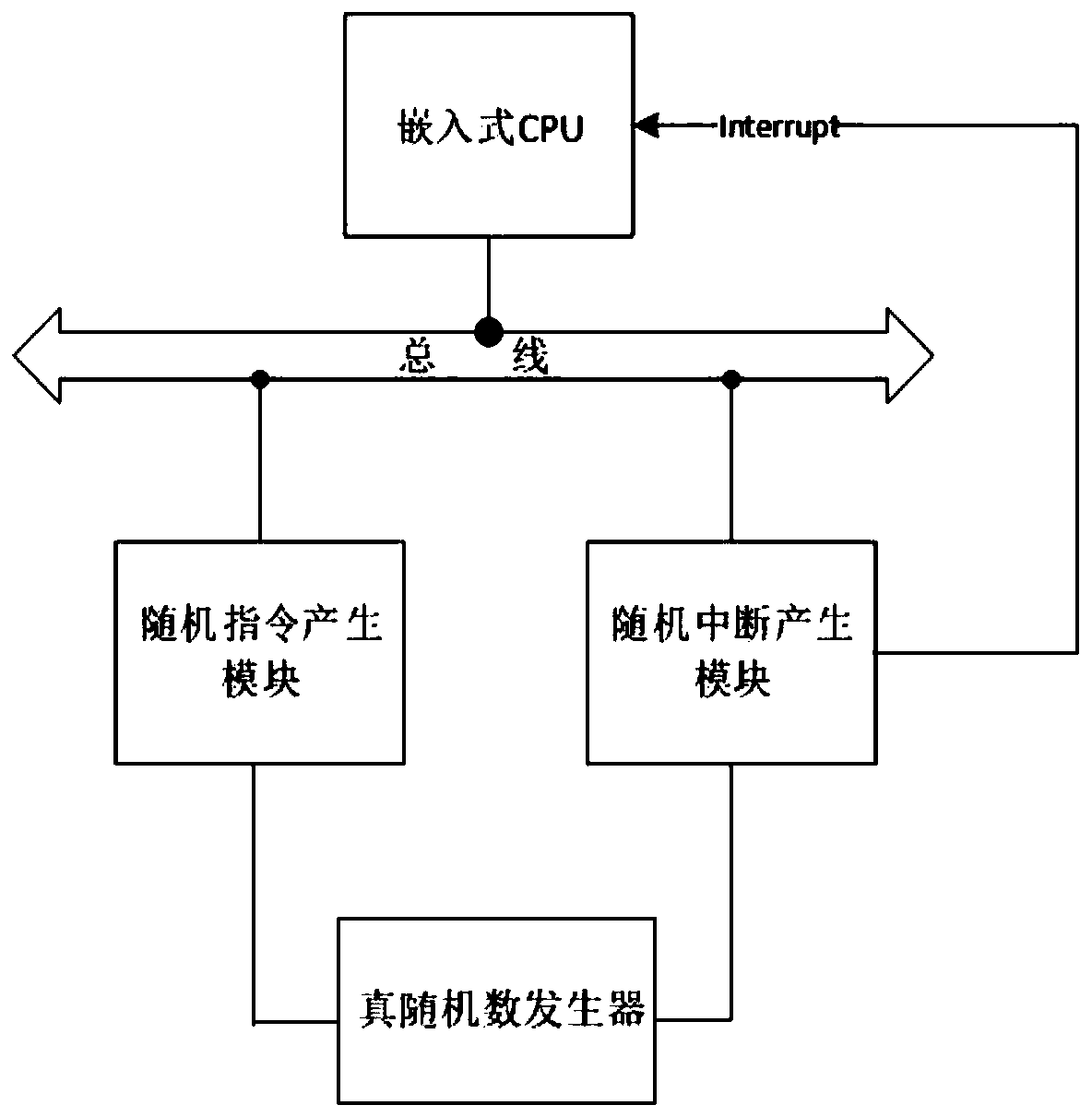
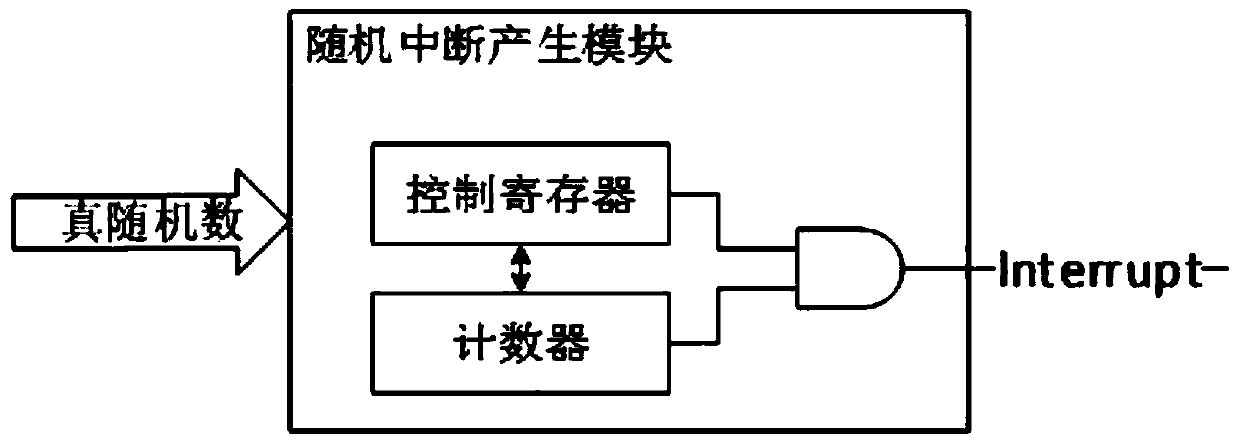
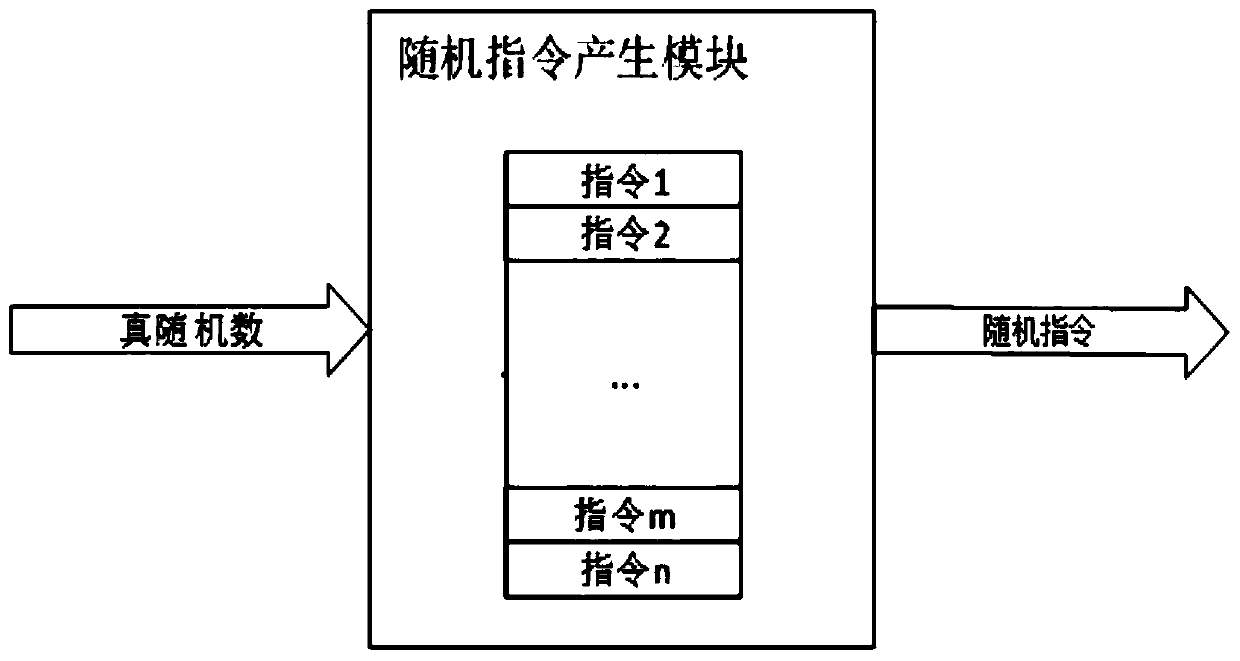
Embedded CPU anti-differential power consumption analysis device and method
InactiveCN111046381ANot to be leakedGuaranteed preservationPlatform integrity maintainanceComputer hardwareComputer architecture
The invention discloses an embedded CPU anti-differential power consumption analysis device and method. The device comprises an embedded CPU, a random interrupt generation module, a random instructiongeneration module and a true random number generator. The true random number generator is used for generating a true random number, the random interrupt generation module is used for generating a random interrupt signal according to the true random number, the random instruction generation module is used for generating a random instruction according to the true random number, and the embedded CPUexecutes the random instruction according to the random interrupt signal. According to the invention, the random instruction insertion mode is used, the power consumption generated when the embeddedCPU executes encryption and decryption operation is disturbed, and under the condition that an original embedded CPU is not modified, the encryption and decryption processes of DPA protection and CPUprotection are carried out on the embedded CPU, and therefore when a user uses the embedded CPU for encryption and decryption, an attacker can be prevented from cracking a secret key through DPA, andencrypted information is protected against leakage.
Owner:ELECTRIC POWER RESEARCH INSTITUTE, CHINA SOUTHERN POWER GRID CO LTD +2
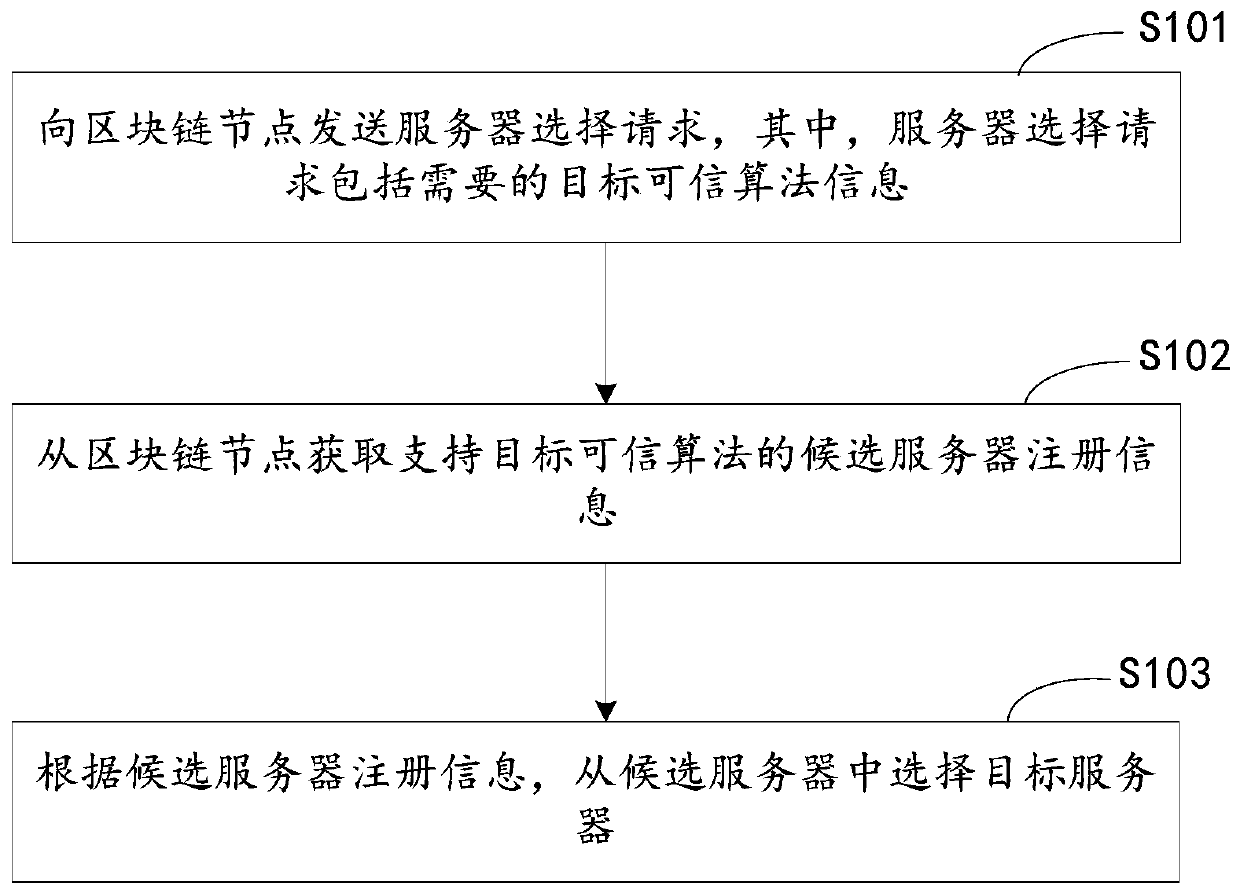
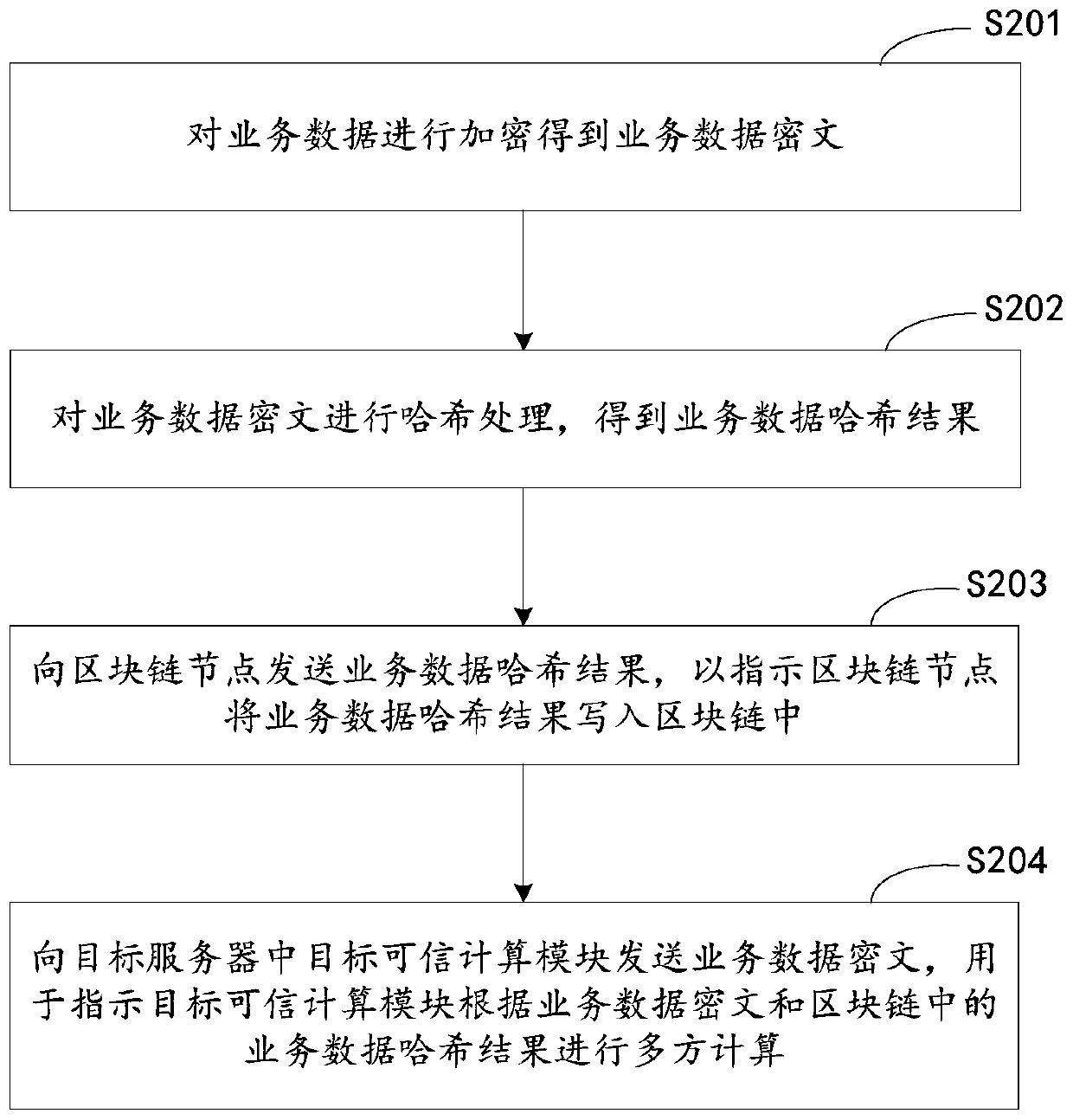
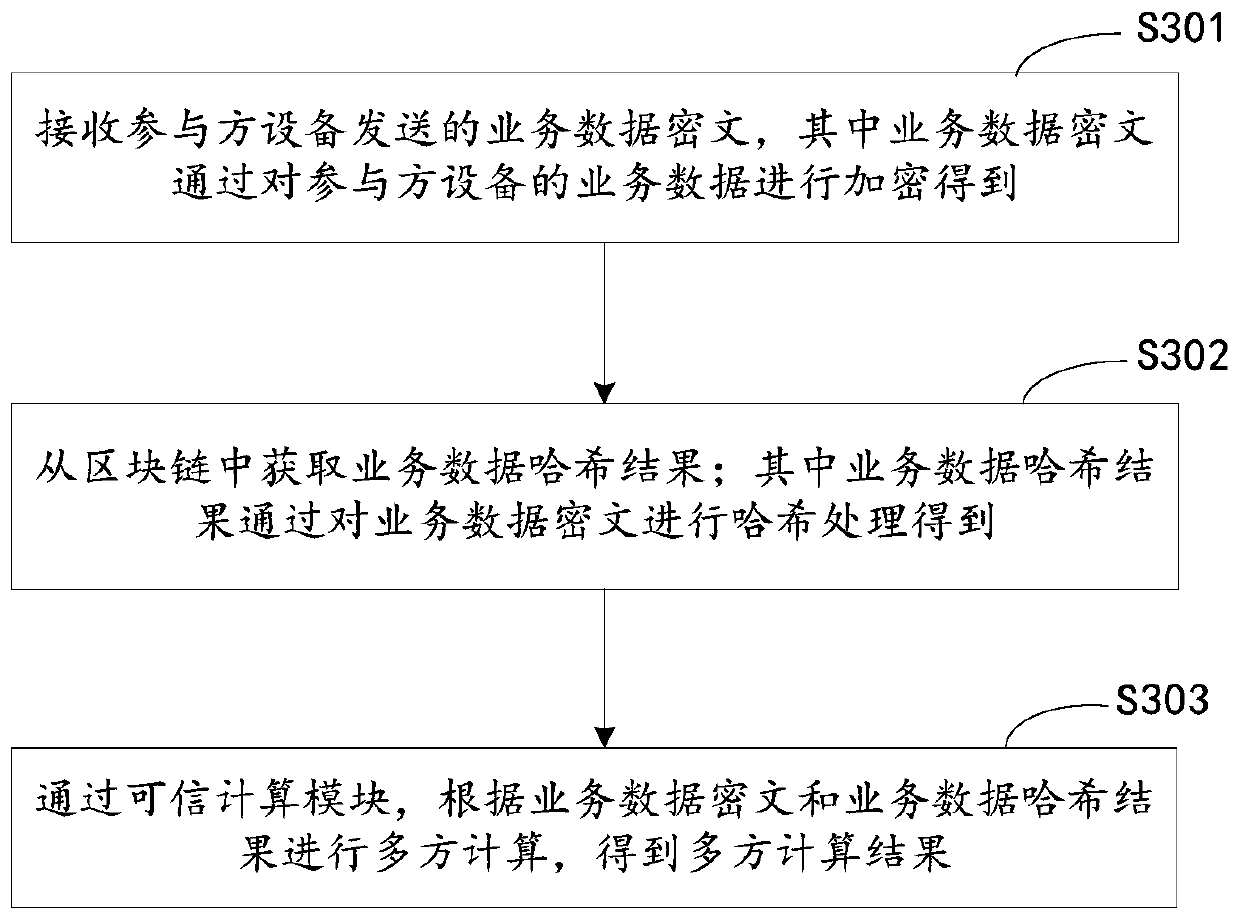
Multi-party computing method and device based on blockchain, equipment and medium
ActiveCN111222165ANot to be leakedImprove securityDigital data protectionSecuring communicationCiphertextTrusted Computing
The embodiment of the invention discloses a multi-party computing method and device based on blockchain, equipment and a medium, and relates to the blockchain technology in the technical field of computers. The method comprises the following steps: encrypting service data to obtain a service data ciphertext; performing hash processing on the service data ciphertext to obtain a service data hash result; sending a service data hash result to the blockchain node to indicate the blockchain node to write the service data hash result into the blockchain; and sending the service data ciphertext to atarget trusted computing module in the target server, wherein the service data ciphertext is used for indicating the target trusted computing module to perform multi-party computing according to the service data ciphertext and the service data hash result in the blockchain. According to the embodiment of the invention, a solution considering the security and reliability of multi-party computing data is provided, and conditions are provided for ensuring the security and reliability of the data.
Owner:BEIJING BAIDU NETCOM SCI & TECH CO LTD
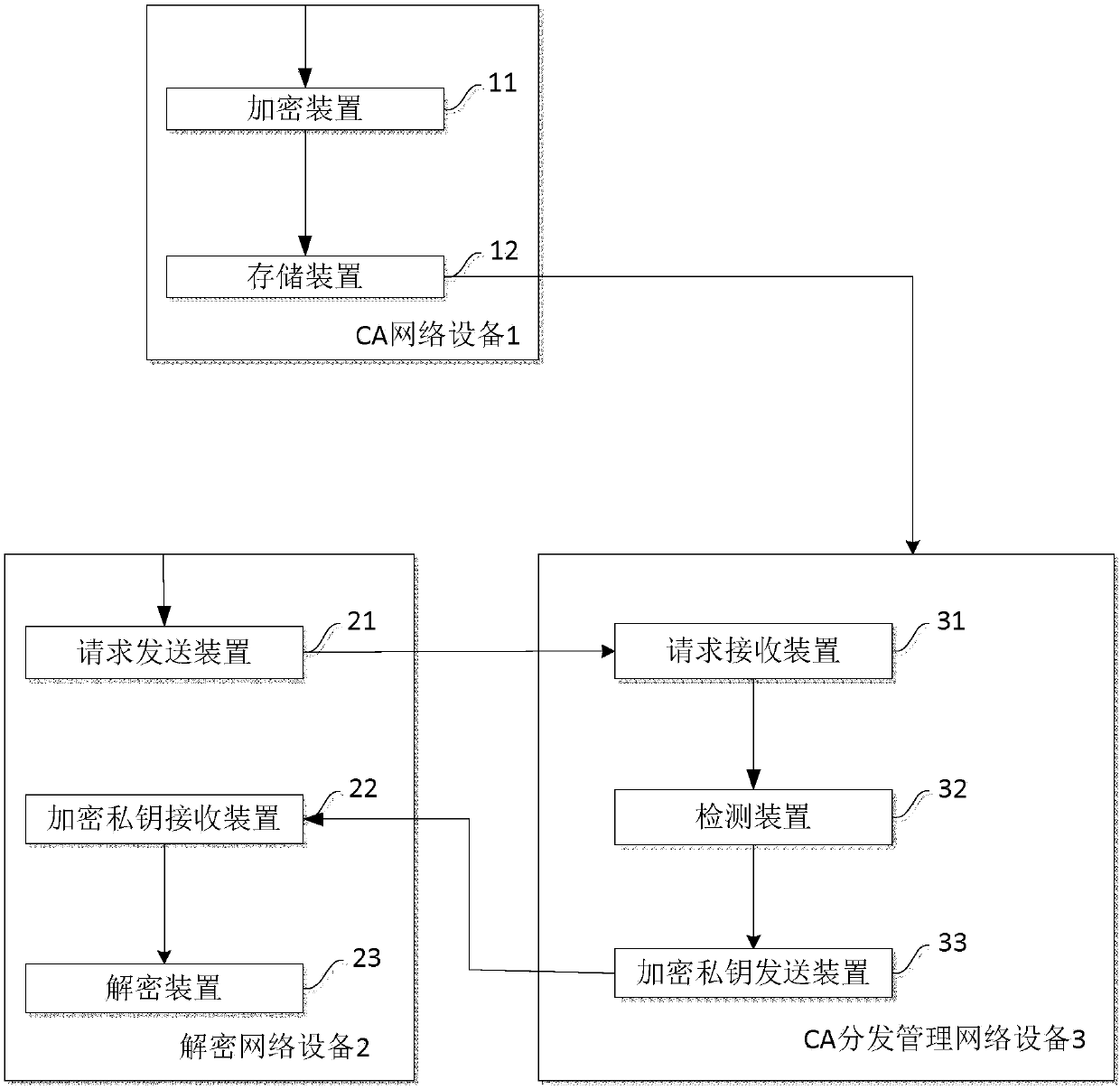
Method and device for decryption with website certificate private key of target website
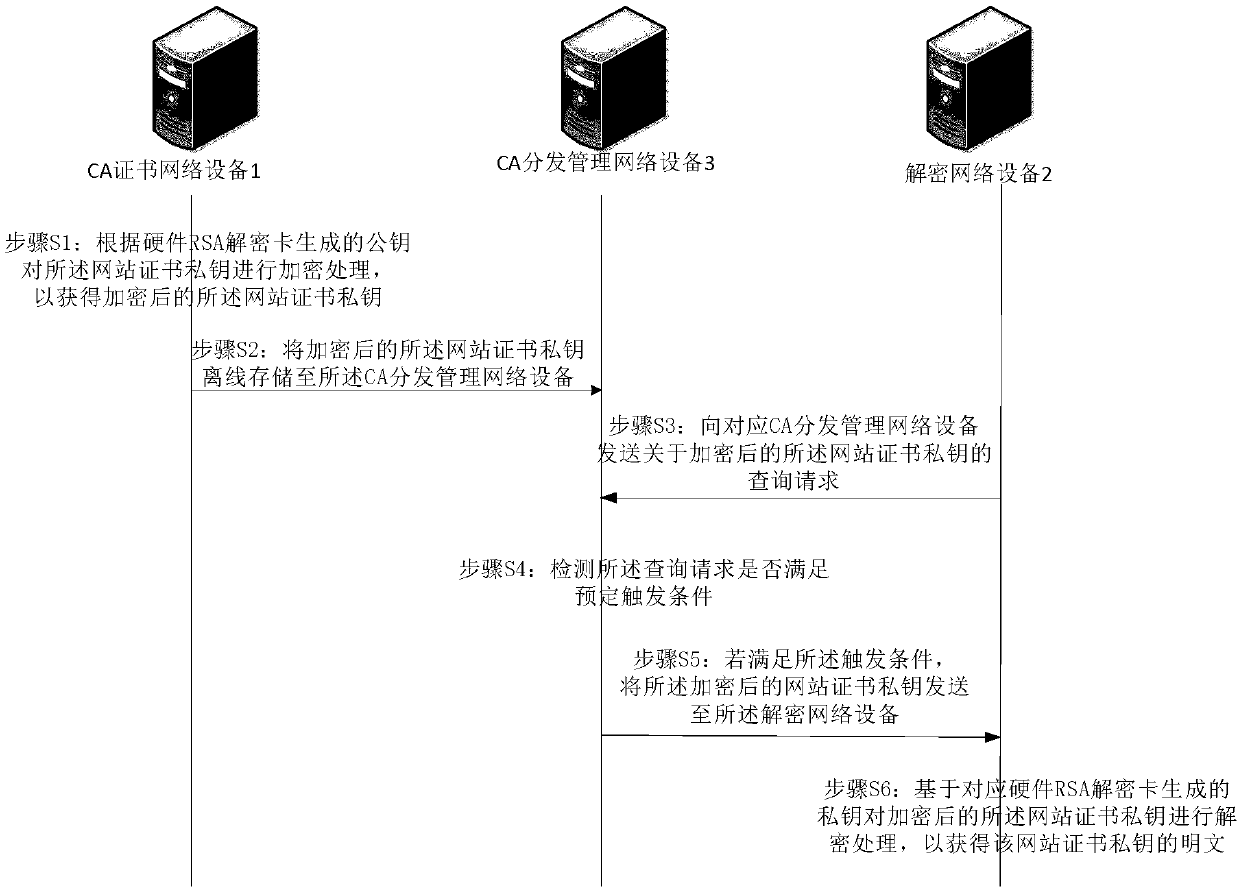
InactiveCN107809412AEnsure safetyImprove securityPublic key for secure communicationUser identity/authority verificationPlaintextCiphertext
The invention aims at providing a method and a device for decryption with a website certificate private key of a target website. Concretely, a decryption network device sends a query request about anencrypted website certificate private key to a corresponding CA distribution management network device, receives the encrypted website certificate private key sent by the CA distribution management network device in response to the query request, performs decryption processing for the encrypted website certificate private key based on a private key generated by a corresponding hardware RSA decryption card so as to obtain a plaintext of the website certificate private key. Compared with the prior art, the method and the device provided by the invention realize the following beneficial effects:during a distribution process of the website certificate private key, the website certificate private key is encrypted, and asymmetric encryption is used, thus, safety of an encrypted secret key is guarantee further; and neither the hardware RSA decryption card nor the decryption network device where the hardware RSA decryption card is located stores the plaintext or a ciphertext of the website certificate private key permanently, so that the risk of being stolen of the website certificate private key is reduced further.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Secure data access method for alliance chain
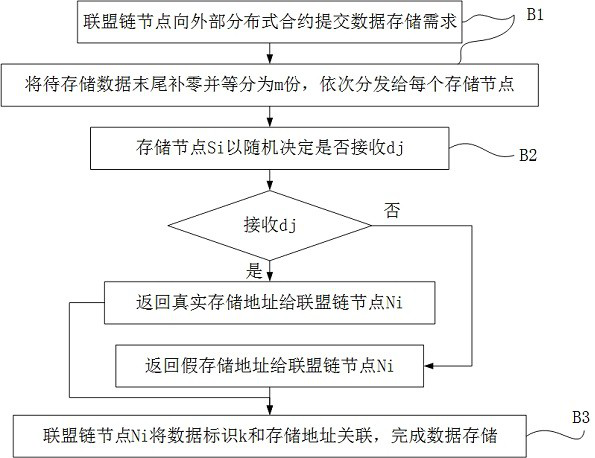
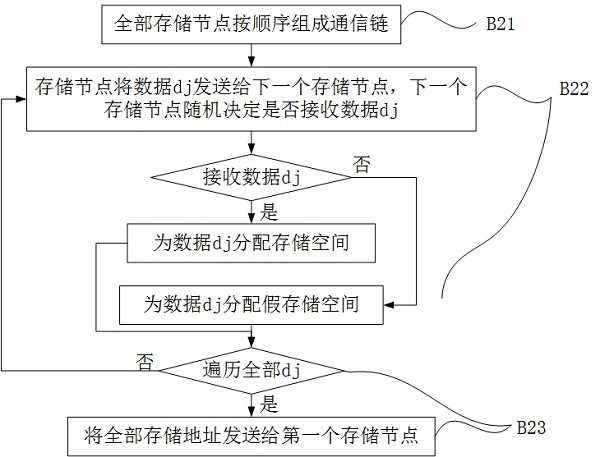
ActiveCN112597526ANot to be leakedDoes not affect operationDigital data protectionComplete dataAccess method
The invention relates to the technical field of block chains, in particular to a security data access method for an alliance chain, which comprises the following steps: A) access agent layer construction: an external consensus protocol is published, and the storage space of a storage node is uniformly addressed; B) data storage: B1) the alliance chain node submits a data storage demand; B2) the external consensus protocol sequentially distributes the data to the storage nodes, and the storage nodes decide whether to receive the data or not according to a certain probability; B3) the alliance chain node associates the data identifier with the storage addresses; and C) data extraction: C1) the alliance chain node submits a data extraction demand, C2) calculates whether an output address is areal storage address through a secure multi-party, and C3) performs external consensus protocol splicing to obtain data and complete data extraction, The method has the substantive effects that the data can be obtained only in the alliance chain, and the data on the alliance chain is ensured not to be leaked.
Owner:浙江数秦科技有限公司
Multi-party joint training method, device, system and equipment for business model
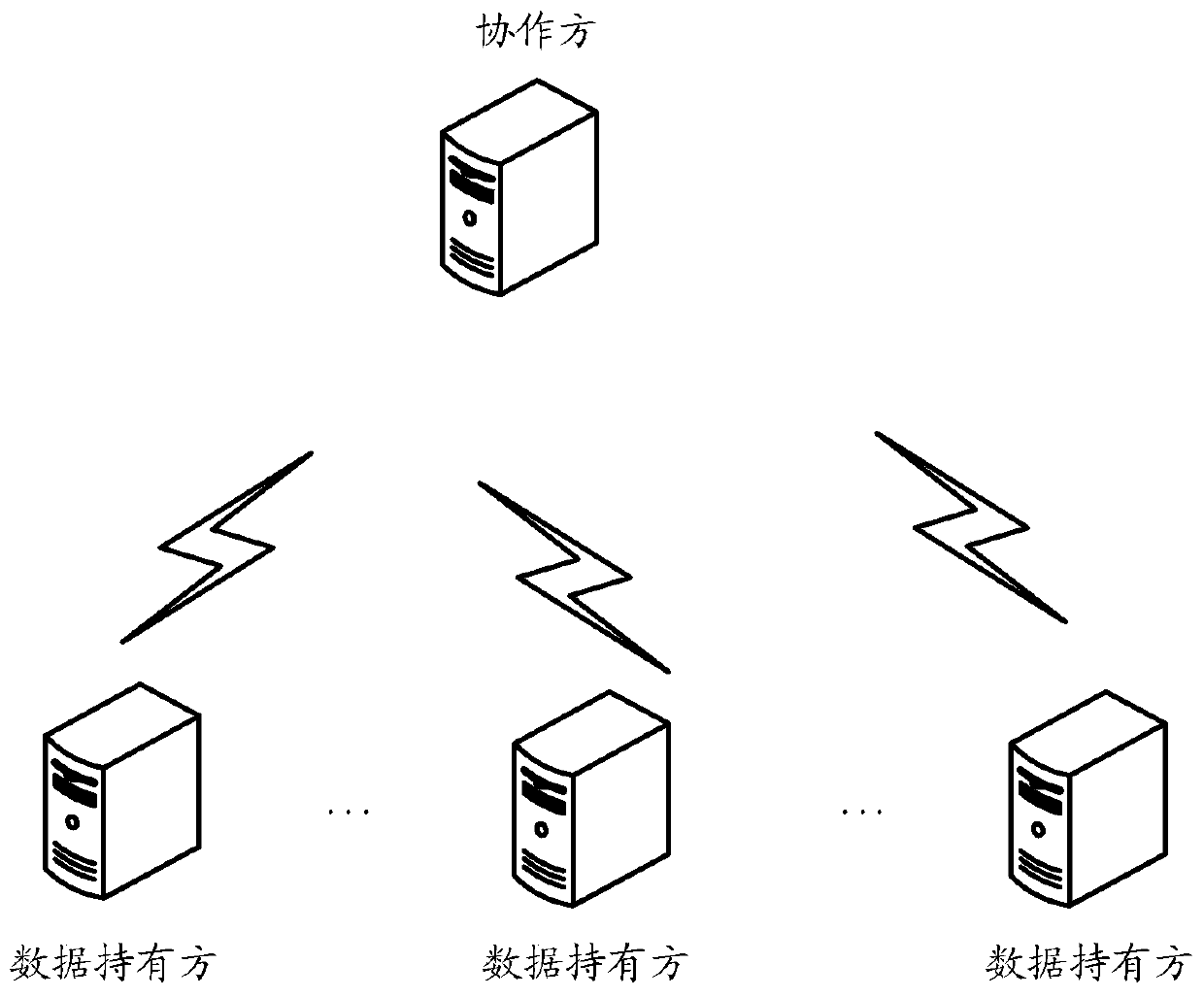
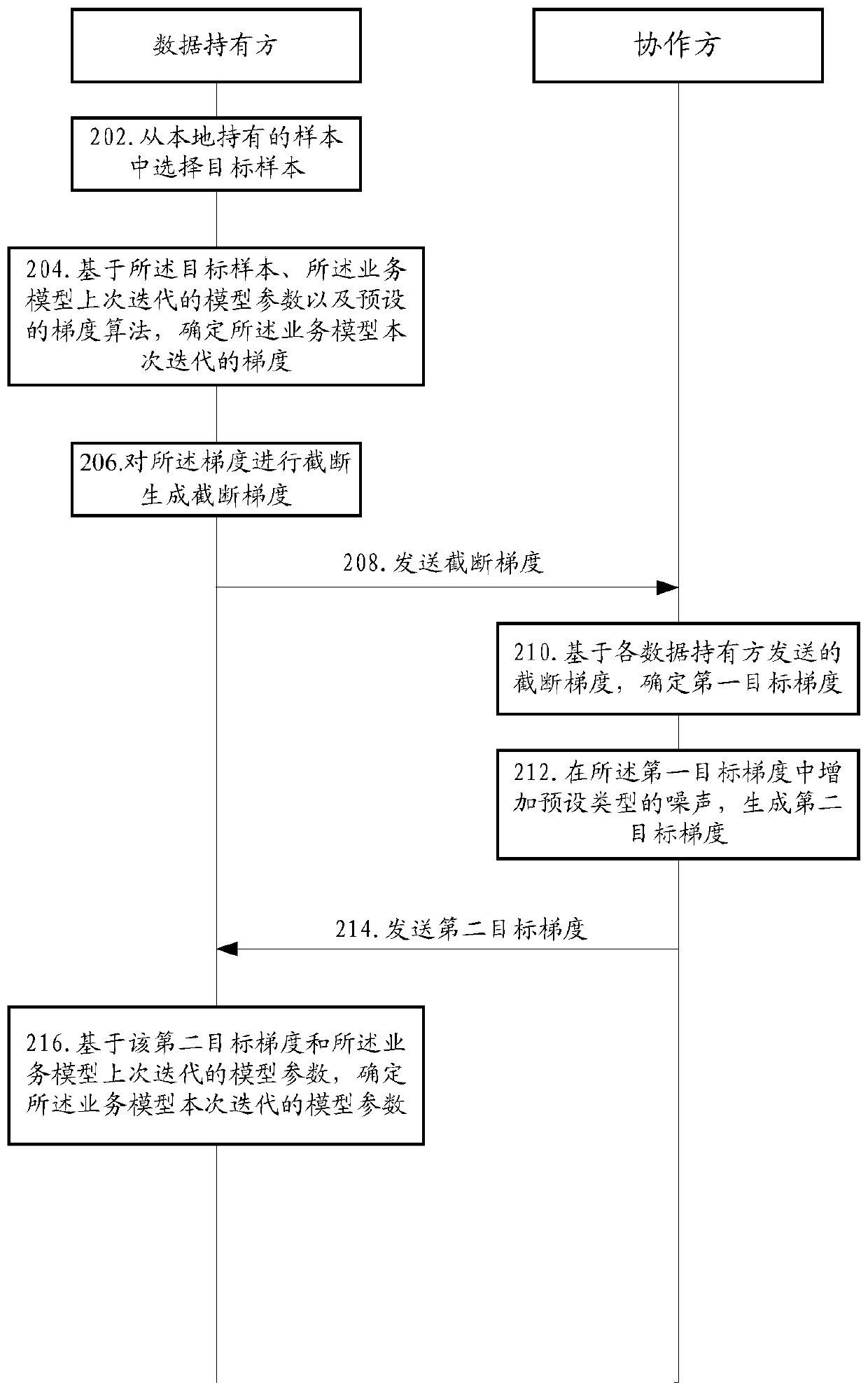
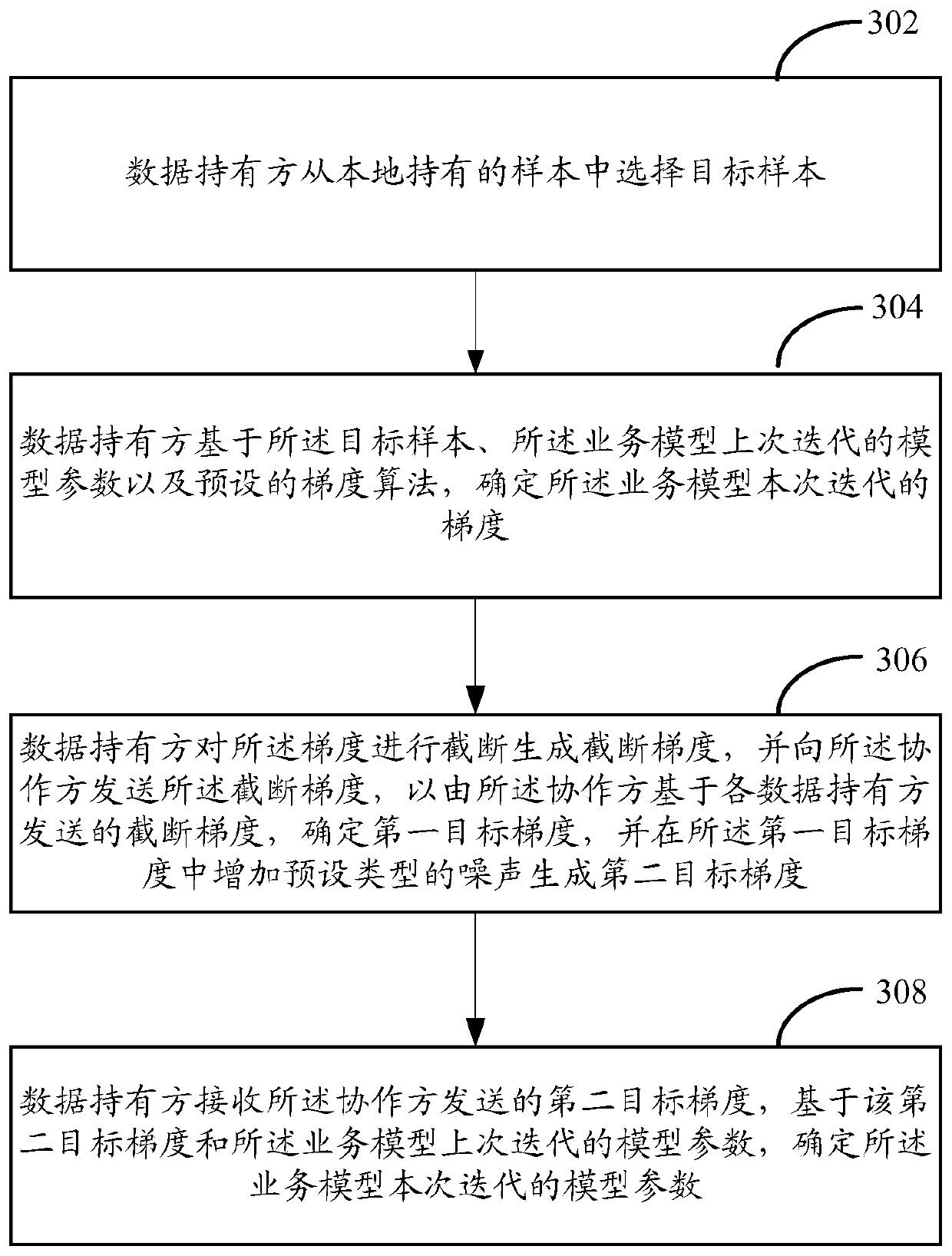
ActiveCN111461215AProtection from being leakedNot to be leakedCharacter and pattern recognitionDigital data protectionIndividual dataModel parameter
The invention provides a multi-party joint training method, device, system and equipment for a business model. The method comprises the following steps: in a multi-party joint training service model process, data holders cut off the gradient of the iteration and then send the cut-off gradient to the collaboration party; and the collaboration party calculates a first target gradient based on the truncation gradient sent by each data holder, and adds noise in the first target gradient to obtain a second target gradient, so that each data holder determines a model parameter of the current iteration based on the second target gradient and the model parameter of the last iteration. According to the method, the calculated gradient is cut off through the data holder, and noise is added to the first target gradient summarized by the collaboration party, so that personal data leakage is prevented in a differential privacy mode in the model training process.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
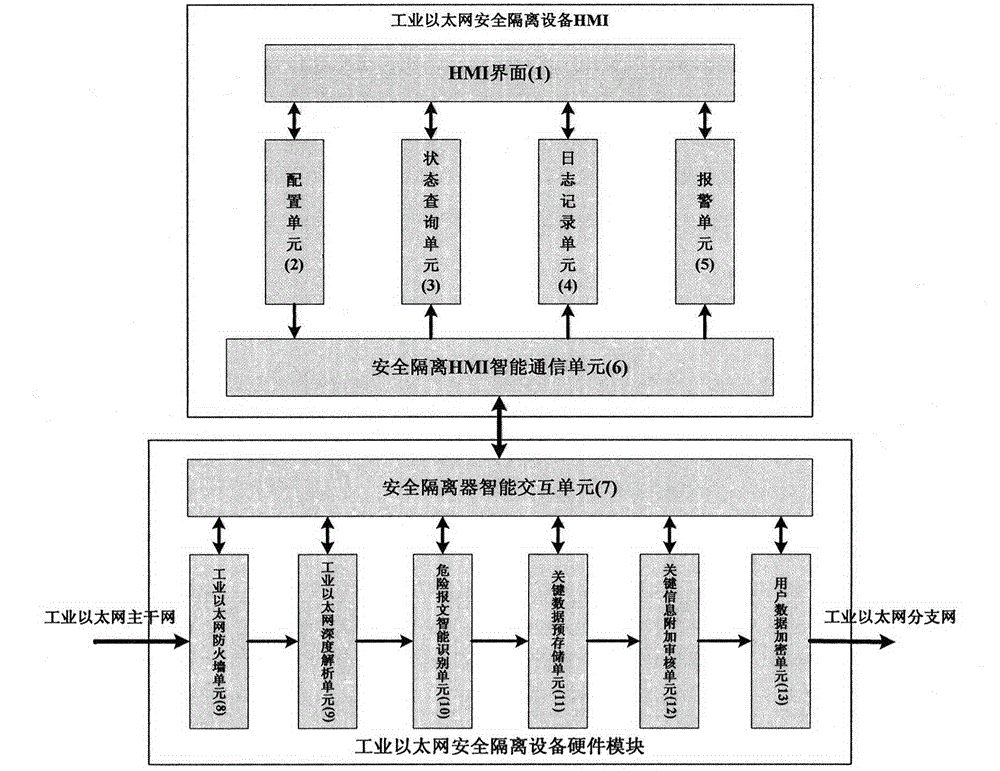
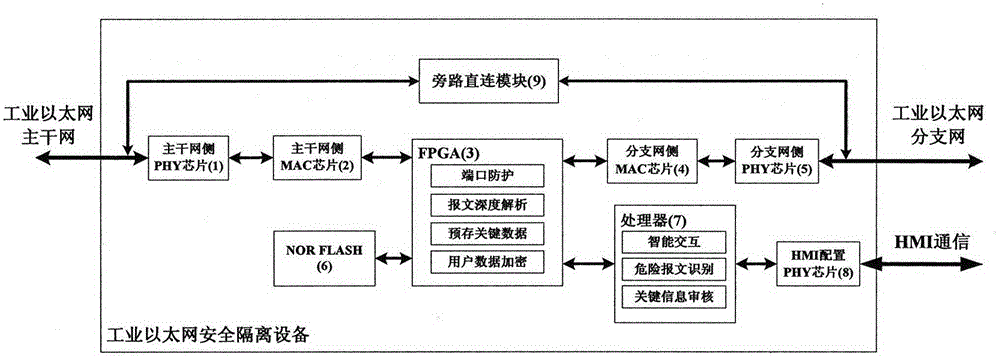
Secure isolation system applied to PROFINET industrial Ethernet
InactiveCN106161330APrevent unauthorized accessNot to be leakedTransmissionResearch ObjectNetwork communication
The invention discloses a secure isolation system applied to a PROFINET industrial Ethernet. Taking the PROFINET real-time Ethernet with wide application prospect as a research object, a PROFINET-based dedicated industrial information security device is developed by combining a PROFINET communication protocol depth detection function with a general industrial firewall function. Besides the functions of blocking network attack and defending viruses, preventing unauthorized access of a control network and field equipment and protecting general information security of data encryption, identity authentication and the like, the system also deeply analyzes the communication characteristic of the PROFINET network, and effectively recognizes abnormal communication situations on the network by predicting network communication behaviors according to configuration information and monitoring a communication relation, a real-time throughput and a non-real-time bandwidth at the initial networking stage, as well as deeply detecting data packets of a PROFINET application layer and the like. When a security threat appears, the contact between the PROFINET network and the external network is timely ''isolated'', and a hazard identification processing and alarm log is sent, so that security download can be performed on an out-of-control or fault main station.
Owner:INSTR TECH & ECONOMY INST P R CHINA
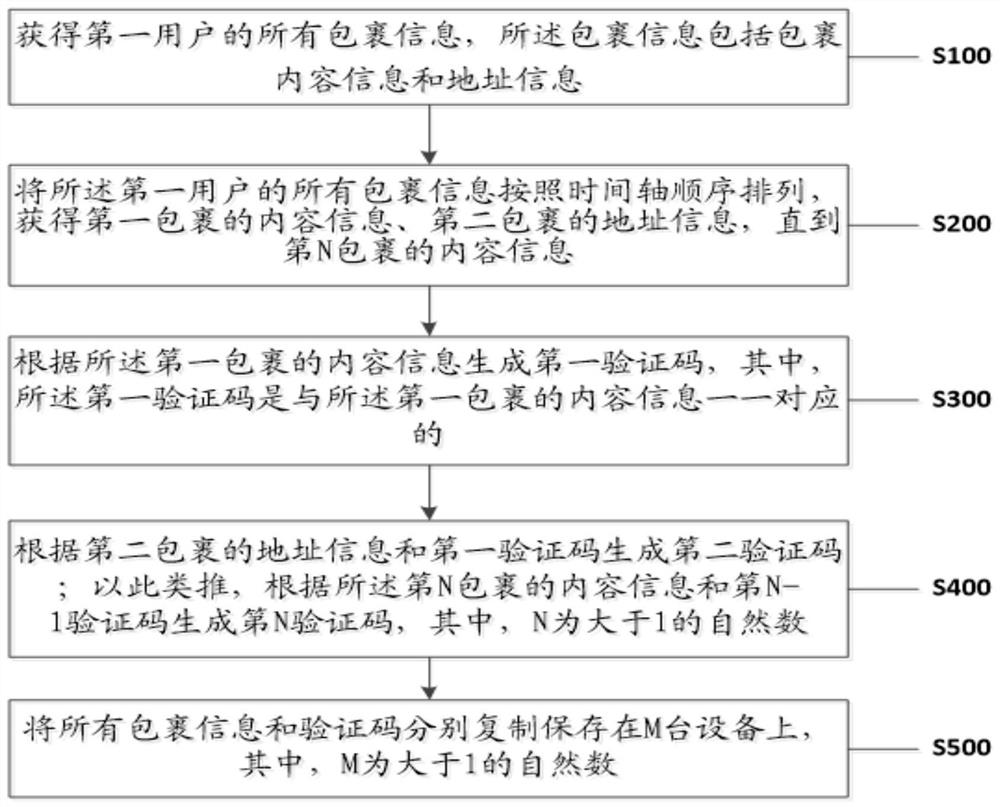
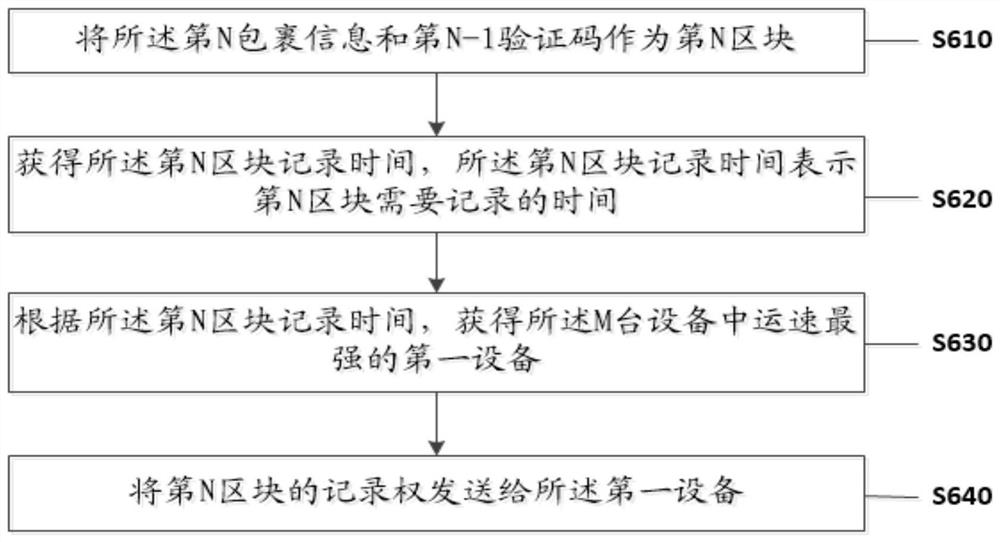
Information processing method and system for improving automatic logistics confidentiality of community
ActiveCN112035879AImprove confidentialityImprove securityDigital data protectionMachine learningInformation processingLogistics management
The invention discloses an information processing method for improving automatic logistics confidentiality of a community. The method comprises the steps of obtaining all parcel information of a firstuser; arranging all parcel information of the first user according to a time axis sequence to obtain content information of a first parcel and address information of a second parcel until content information of an Nth parcel is obtained; generating a first verification code according to the content information of the first package; generating a second verification code according to the address information of the second package and the first verification code; in the same way, generating an Nth verification code according to the content information of the Nth package and the N-1th verificationcode, wherein N is a natural number larger than 1; copying and storing all the parcel information and the verification codes on M devices respectively, wherein M is a natural number larger than 1. The problem that parcel information and personal information of a user are not leaked is solved, and logistics confidentiality and safety are improved.
Owner:KUNMING UNIV OF SCI & TECH
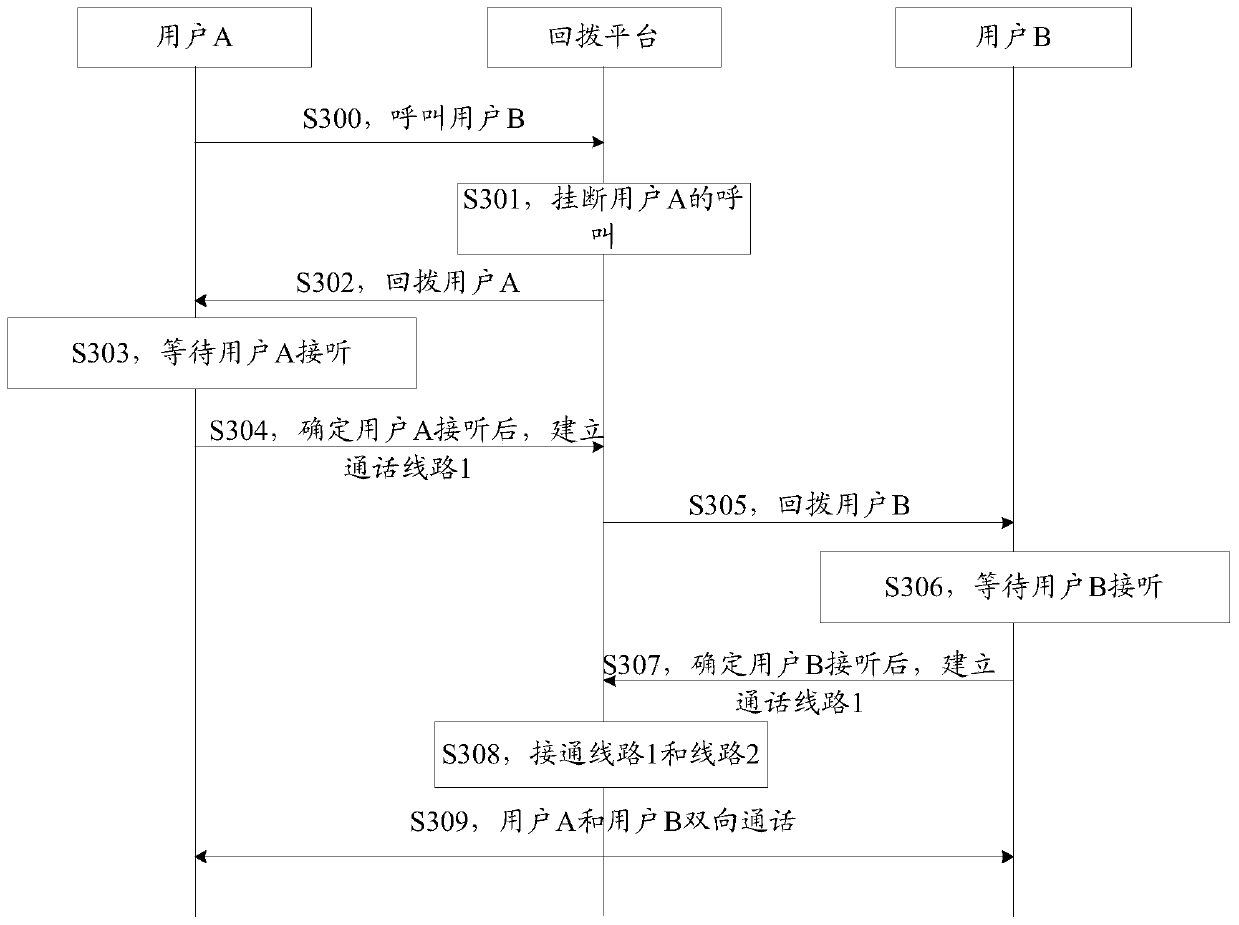
Communication method and device based on team instant messaging application and storage medium
ActiveCN111182159ANot to be leakedMeeting Communication NeedsSpecial service for subscribersSupervisory/monitoring/testing arrangementsComputer securityEngineering
The invention provides a communication method and device based on a team instant messaging application and a storage medium, which are used for reducing communication obstacles among users and improving the working efficiency on the premise of protecting private information of the users. The method comprises the steps of in response to a call request for carrying out a call by using a public fee telephone, determining a calling subscriber identity label and a called subscriber identity label carried in the call request, wherein the call request is obtained by triggering a dialing entrance corresponding to a telephone number hiding mode in a personal information display page of the team instant messaging application client; and sending a communication request carrying the calling user identity identifier and the called user identity identifier to a server, so that the server sends a callback request to the calling user terminal and the called user terminal to establish a call. Accordingto the team instant messaging application, on the premise of ensuring that the telephone number is not leaked, the requirement of communication between users through the telephone number is met, communication obstacles between the users are reduced, and the working efficiency is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Application authority control method and device, and mobile terminal
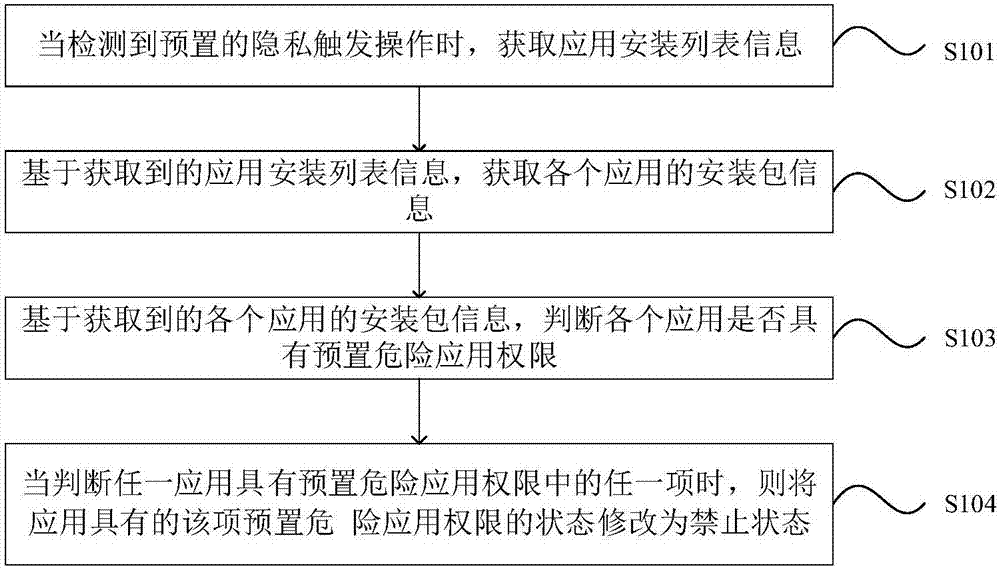
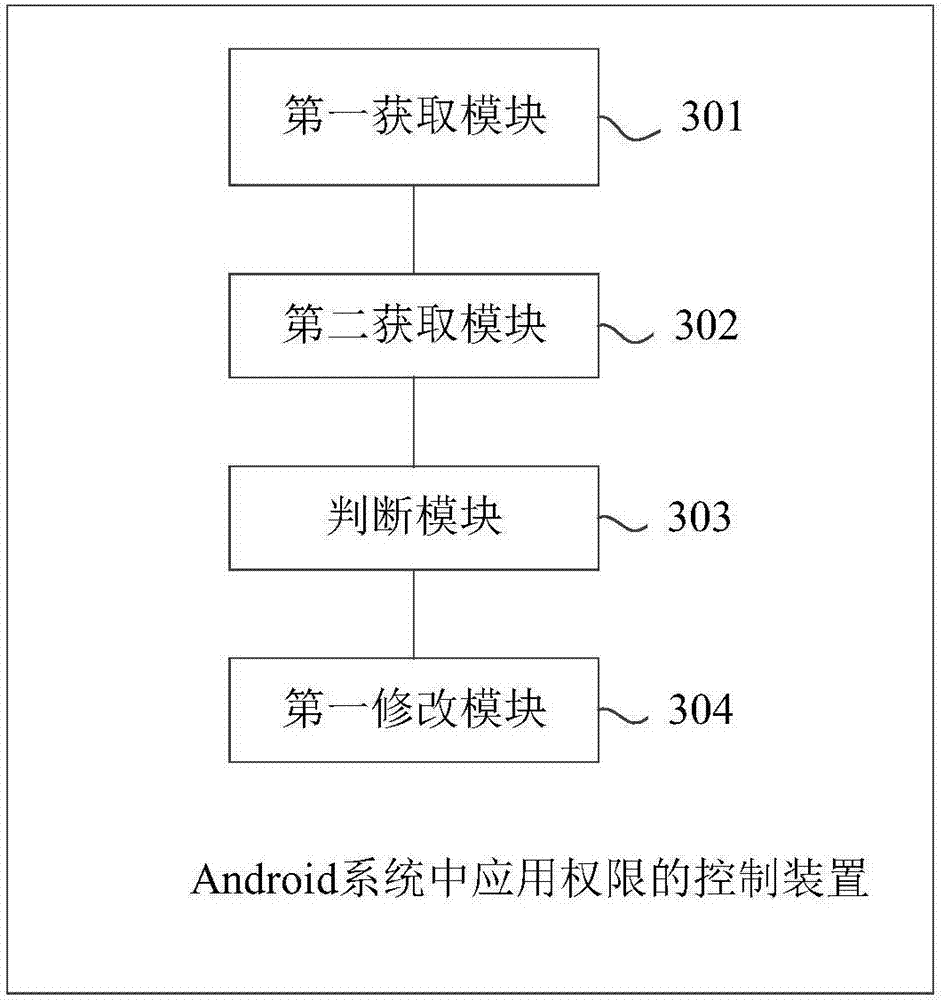
InactiveCN107343103AGuaranteed privacy and securityGuarantee property securityComputer security arrangementsSubstation equipmentComputer terminalApplication software
The invention provides an application authority control method and device in an Android system, and a mobile terminal. The method comprises steps that when predetermined privacy trigger operation is detected, the application installation list information is acquired; based on the acquired application installation list information, the installation packet information of each application is acquired; based on the acquired installation packet information of each application, whether each application has predetermined danger application authorities is determined; when any application is determined to have any item of the predetermined danger application authorities, a state of the predetermined danger application authority of the application is modified to be a prohibition state. The method is advantaged in that all the applications installed on the mobile terminal are automatically prohibited from acquiring the danger application authorities, the privacy information and the property information of the user are guaranteed to not be acquired by malicious applications or not be leaked by other applications; privacy safety and property safety of the user are guaranteed, and Android system safety is further improved.
Owner:BEIJING YUANXIN SCI & TECH
Information processing method and encryption device
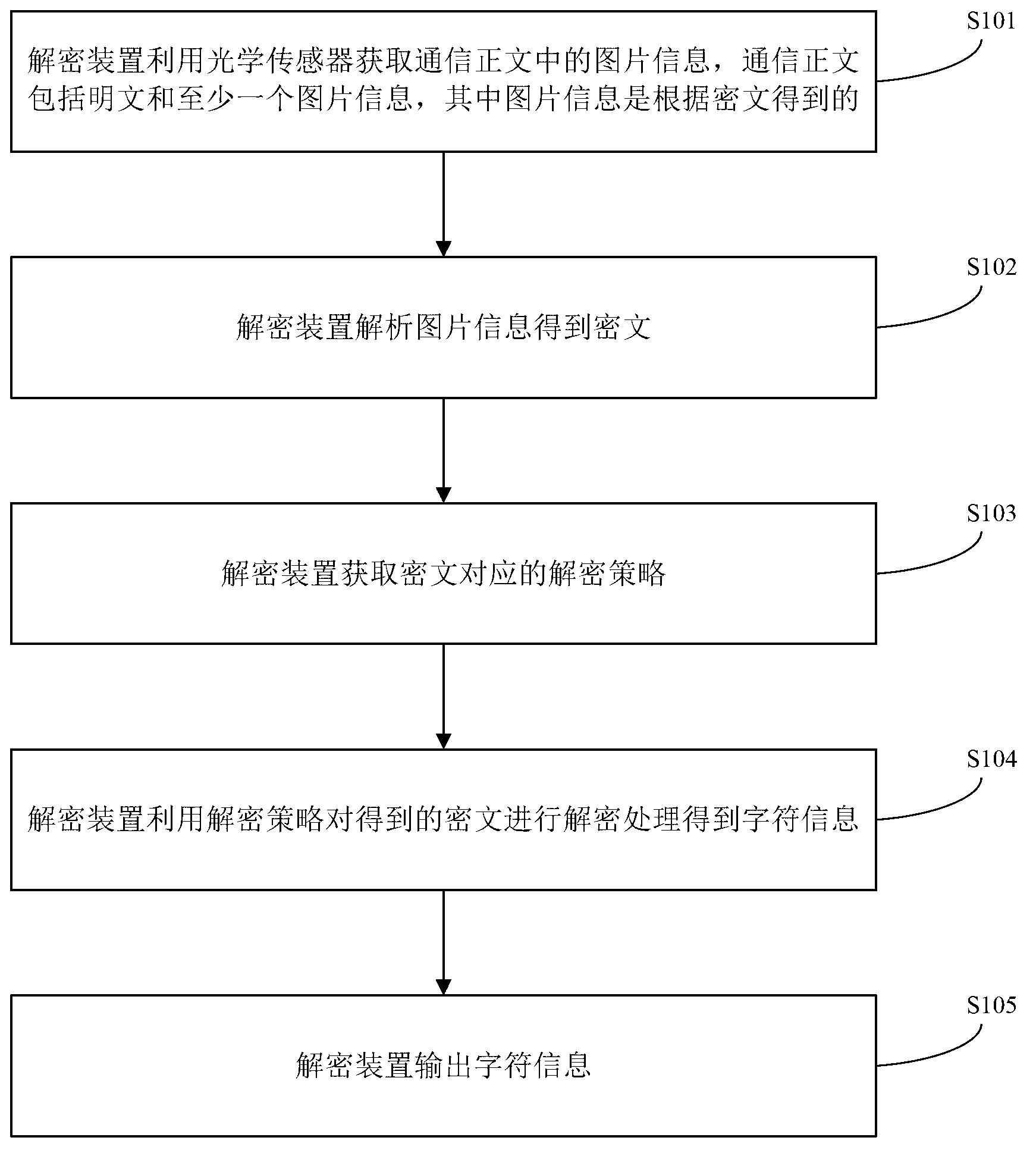
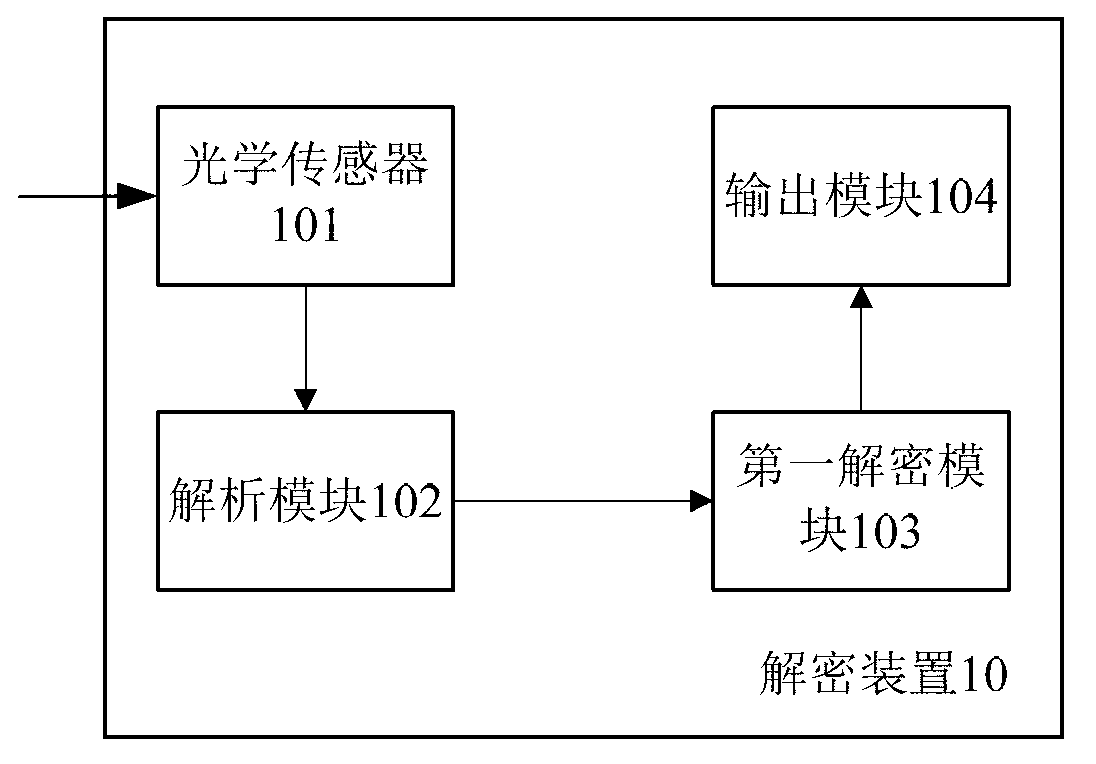
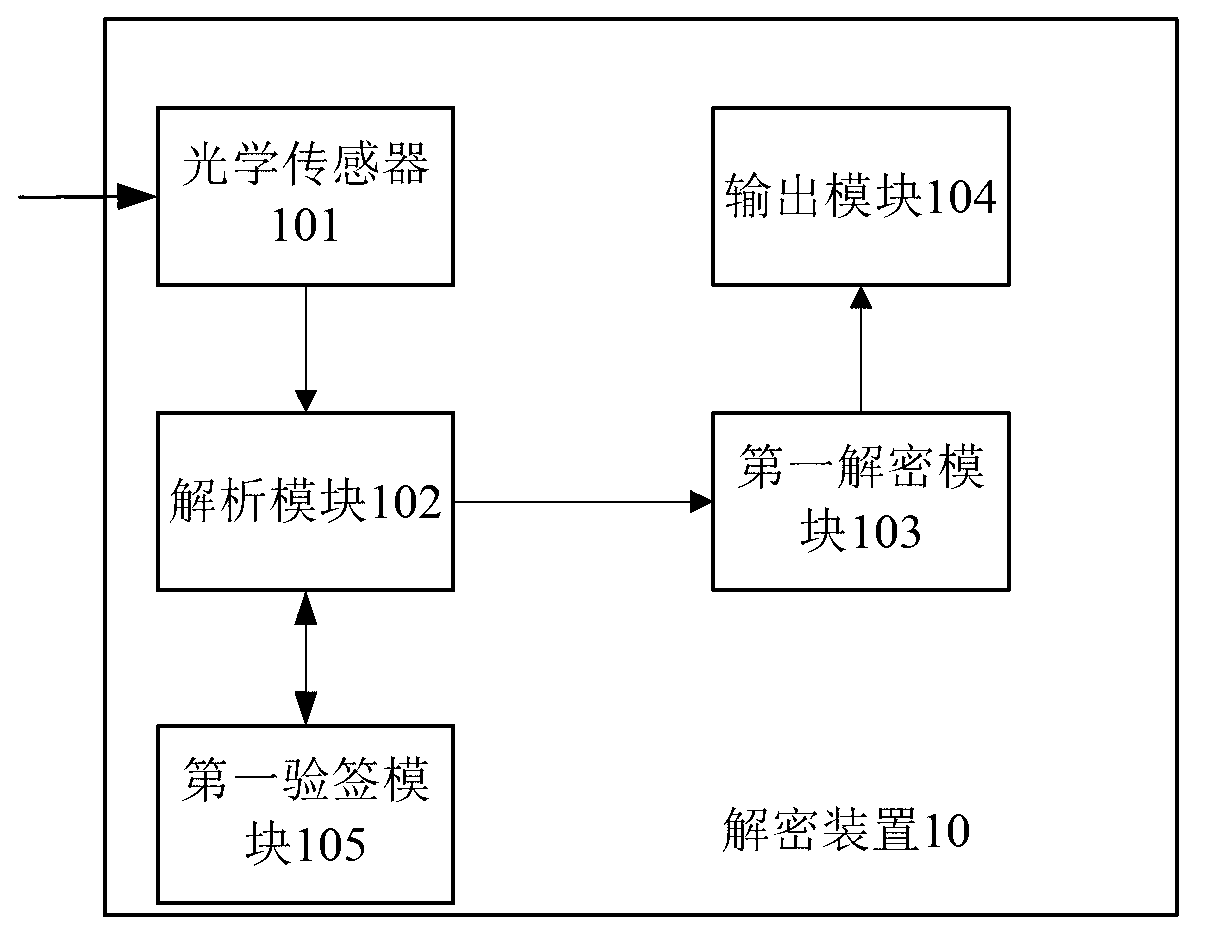
ActiveCN103236929AEnsure safetyImprove processing efficiencyUser identity/authority verificationCoding/ciphering apparatusPlaintextCommunications security
The invention provides an information processing method, which comprises the following steps that an encryption device obtains picture information in communication texts through an optical sensor, wherein the communication texts comprise plaintexts and at least one piece of picture information, and the picture information is obtained according to ciphertexts; the encryption device analyzes the ciphertexts obtained by the picture information; the encryption device obtains encryption strategies corresponding to the ciphertexts; the encryption device carries out encryption processing on the ciphertexts according to the encryption strategies, and character information is obtained; and the encryption device outputs the character information. When the technical scheme provided by the invention is adopted, the key information in the communication process can be enabled not to be leaked, meanwhile, because the picture information only contains one part of key information, the analysis and encryption data quantity of the encryption device is little through being compared with that of the whole full text encryption, the communication safety is enabled, and meanwhile, the information processing efficiency is also improved.
Owner:TENDYRON CORP
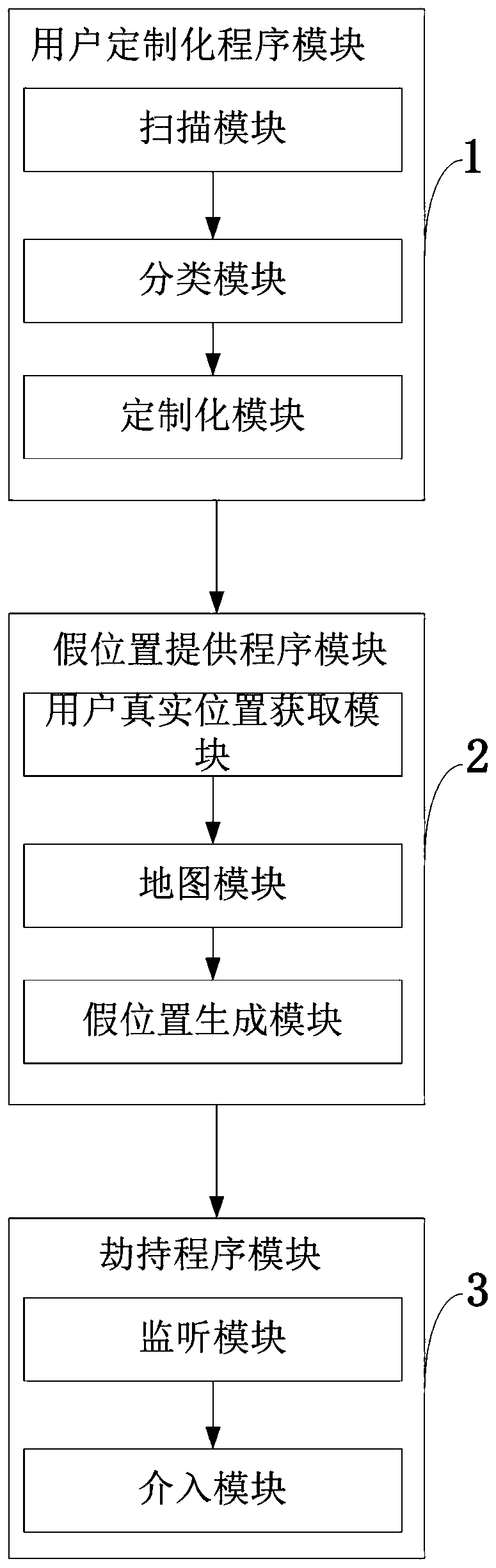
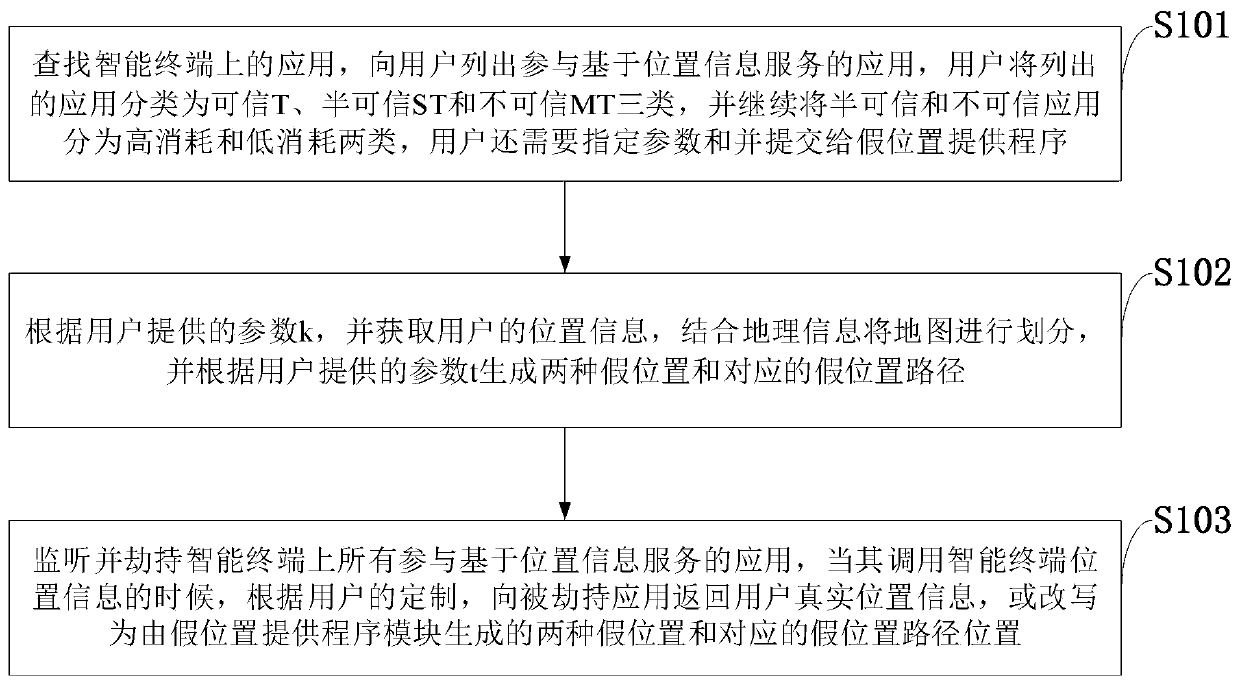
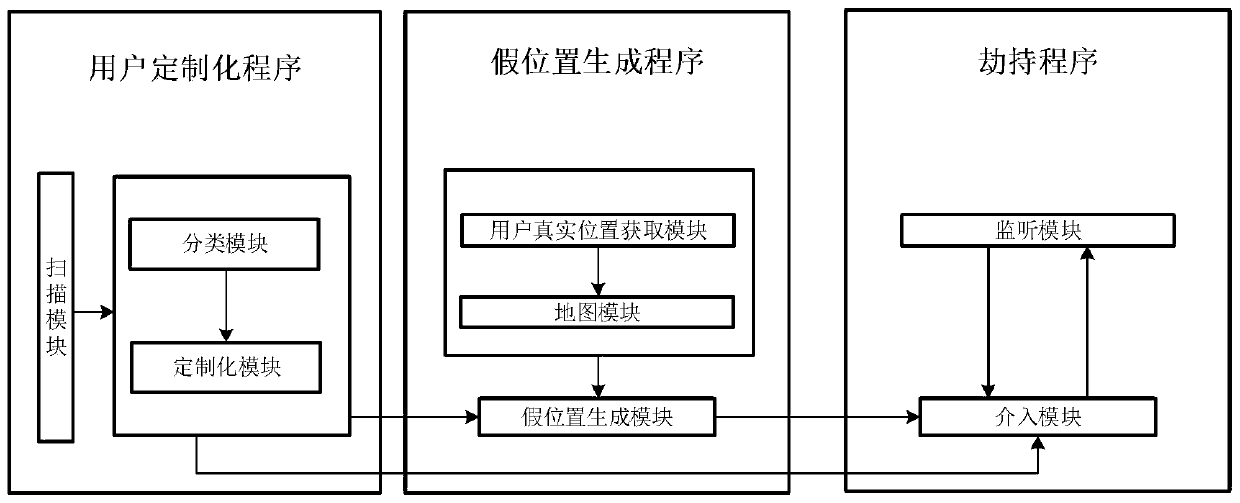
Customized position data privacy protection system and method for mobile terminal application
ActiveCN111148039AAchieve protectionImprove protectionLocation information based serviceSecurity arrangementPathPingData privacy protection
The invention belongs to the technical field of information security, and discloses a customized position data privacy protection system and method for a mobile terminal application, and the method comprises the steps: searching an application on an intelligent terminal, and listing applications participating in a position information-based service for the user; obtaining position information of the user according to the parameter k provided by the user, dividing a map and generating two false positions and corresponding false position paths according to the parameter t provided by the user; and monitoring and hijacking all applications participating in the location information-based service on the intelligent terminal, and providing location information or two false locations and corresponding false location path locations of the intelligent terminal. The position privacy data of the mobile terminal user is protected, and the position data of the user is prevented from being leaked; the flexible deployment of the intelligent terminal user position privacy data protection system is realized; the location data privacy of the intelligent terminal user can be protected on the premiseof normally providing location information-based service.
Owner:XIDIAN UNIV
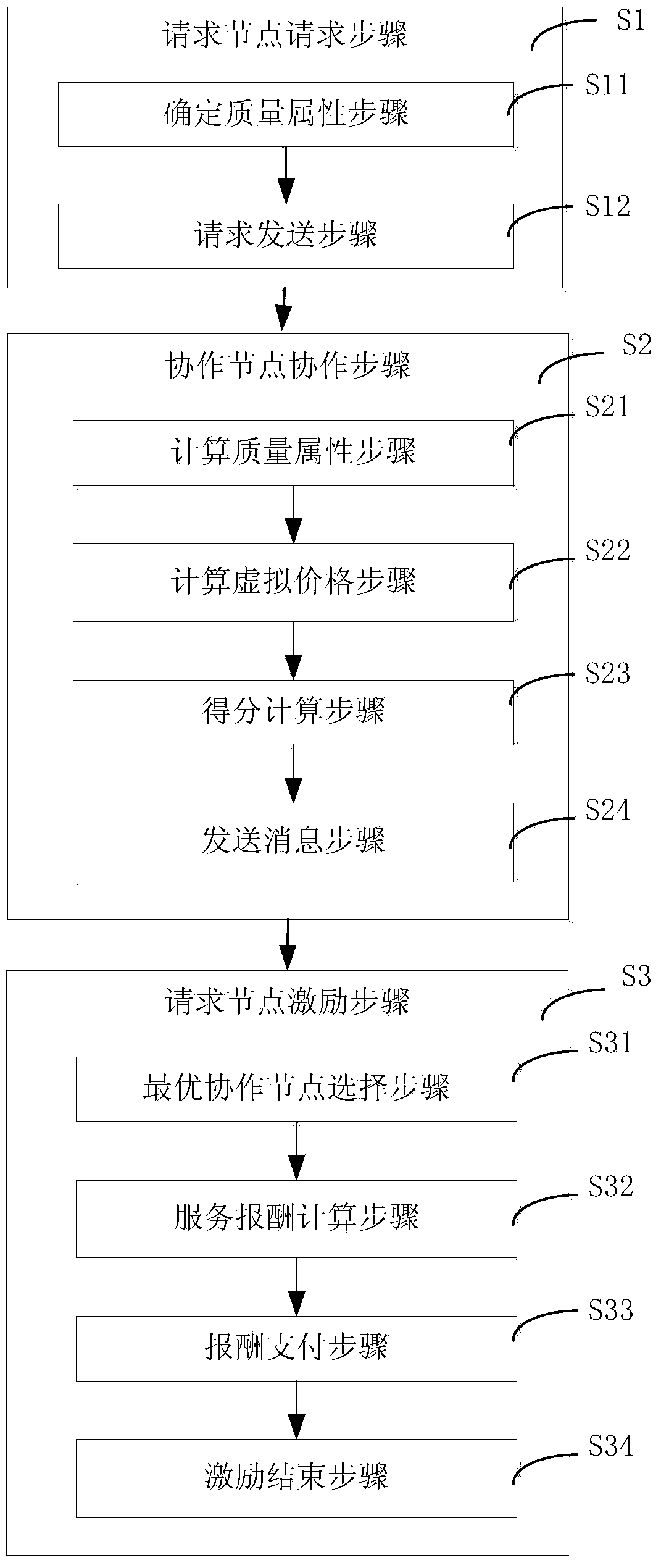
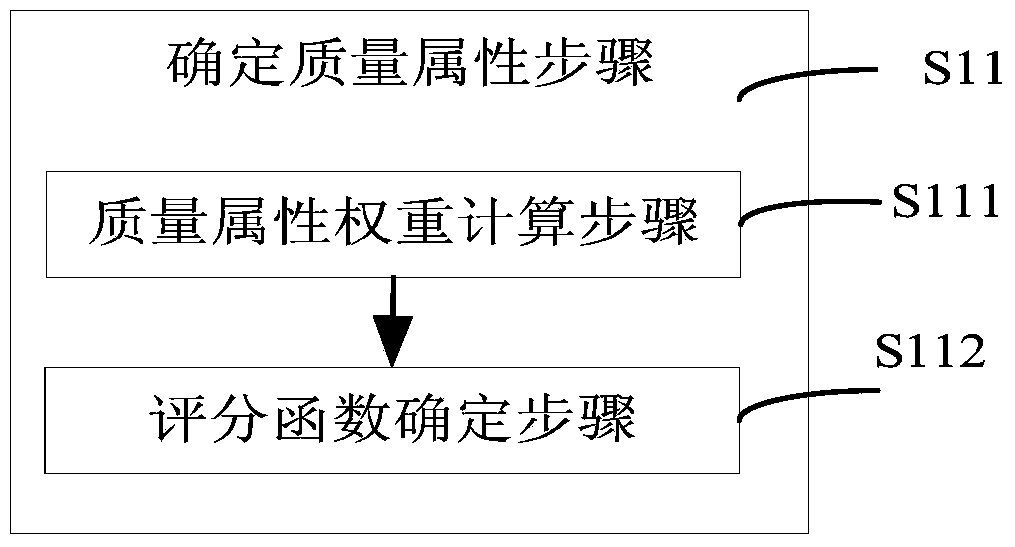
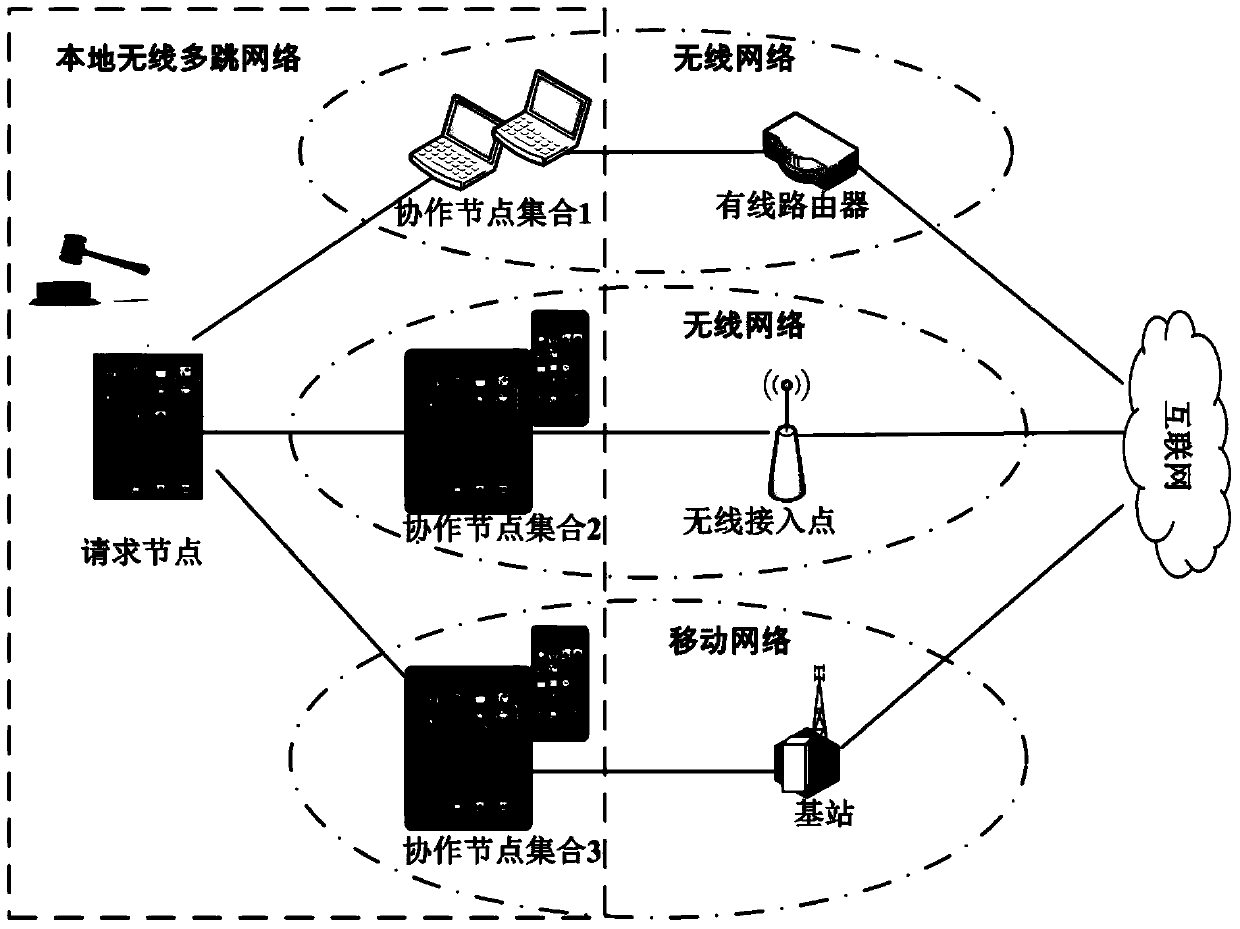
Content downloading application exciting method oriented to intelligent terminal and system thereof
ActiveCN103747536AGuarantee authenticityNot to be leakedConnection managementTransmissionMix networkThe Internet
The invention discloses a content downloading application exciting method oriented to an intelligent terminal and a system thereof. The method is applied to a hybrid network with diversified network interfaces; a requesting node can access a cooperation node of an Internet through excitation to indirectly acquire required network content. The method comprises a requesting node requesting step that the requesting node determines the preference of cooperation service and sends a cooperation service request to the cooperation node, a cooperation node cooperating step that the cooperation node judges whether to execute cooperation according to content of the request after receiving the request of the requesting node, then calculates a cooperation service score after determining to execute cooperation and supplies a cooperation service scheme, and a request node exciting step that the optimal cooperation node is selected to execute excitation according to the cooperation service score and the cooperation service scheme which are supplied by the cooperation node, and service remuneration is paid to the optimal cooperation node.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
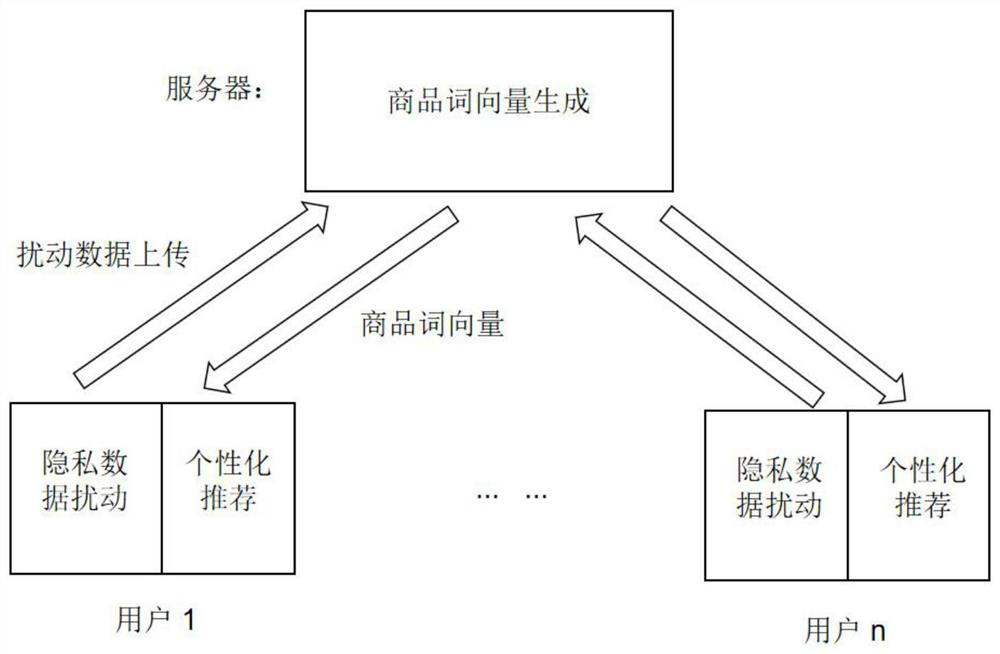
Recommendation system based on localized differential privacy
ActiveCN111768268AIndistinguishableNot to be leakedDigital data protectionBuying/selling/leasing transactionsPrivacy protectionThird party
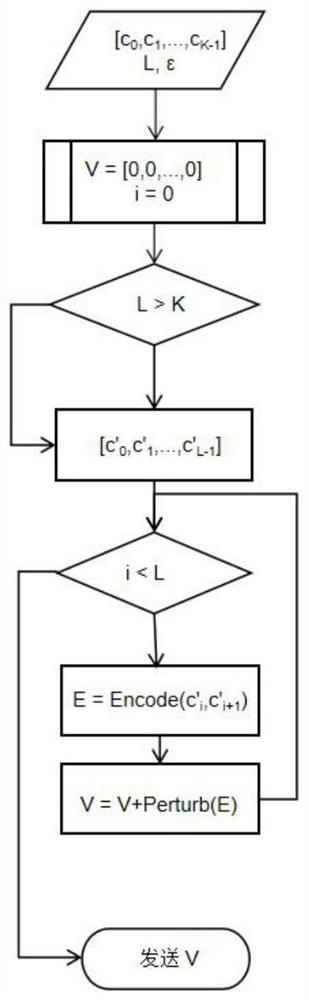
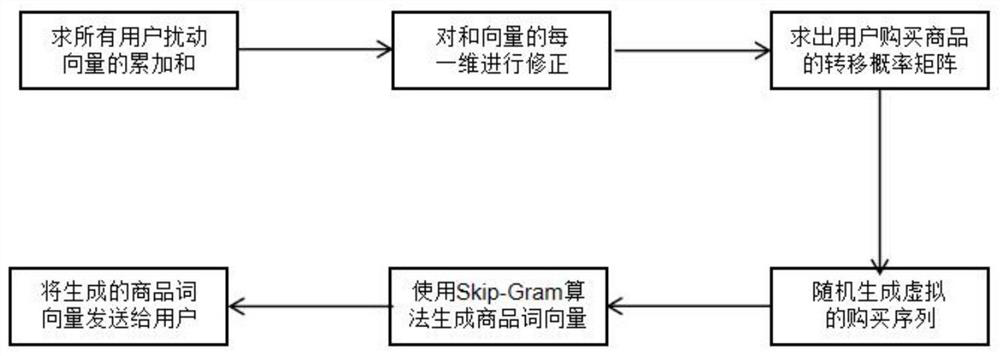
The invention discloses a recommendation system based on localized differential privacy, and the main process comprises the following steps that: (1) each user side encodes related historical commodity purchasing behavior data, then disturbs the data by using a random disturbance algorithm meeting the localized differential privacy, and finally sends the disturbed data to a server side; (2) the server side collects all disturbed data, then reconstructs relevant information of historical purchase behaviors of the user, and finally maps the relevant information into a low-dimensional vector by using a graph embedding algorithm and returns the low-dimensional vector to the user side; (3) each user side calculates a respective recommended candidate set through the finally generated vector, thereby finishing commodity recommendation under the condition of privacy protection. According to the invention, a localized differential privacy protection technology is used, and the system does not need a trusted third party as a medium, thereby guaranteeing that the privacy information of each user is not stolen by the third party, and also guaranteeing the usefulness of a final recommendation result of the system.
Owner:BEIHANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com