Secure data access method for alliance chain
An access method and security data technology, applied in digital data protection, electronic digital data processing, computer security devices, etc., can solve problems such as alliance chain data leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0033] A secure data access method for alliance chains, comprising the following steps:
[0034] Step A) Build the access proxy layer 200:
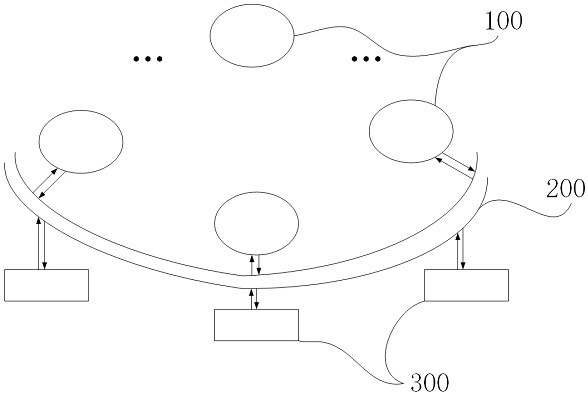
[0035] Such as figure 1 As shown, the external consensus protocol is released on the alliance chain, and the alliance chain nodes Open up the chain data storage area 300 on its own storage device, and the external consensus protocol takes over the data access authority of the chain data storage area 300, and records the chain data storage area 300 as a storage node , The number of nodes in the alliance chain is 100, and the external consensus protocol will store the nodes Unified addressing of the storage space, and set the data buffer , alliance chain node It only knows its own unified address.
[0036] Step B) Data storage:
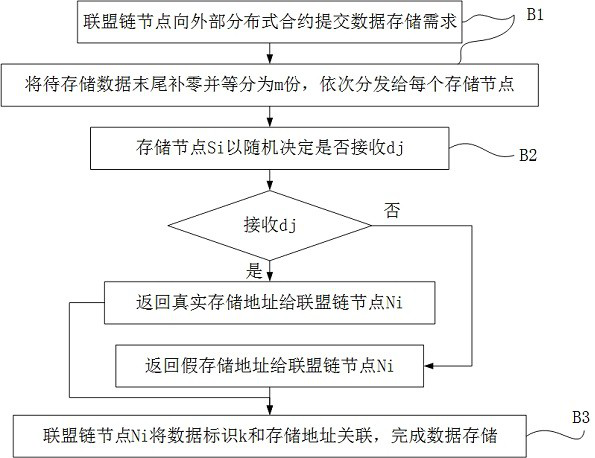
[0037] Such as figure 2 As shown, the data Stored procedures include:
[0038] Step B1) Consortium chain node Submit data storage requirements to the external consensus protocol, and the data to...
Embodiment 2
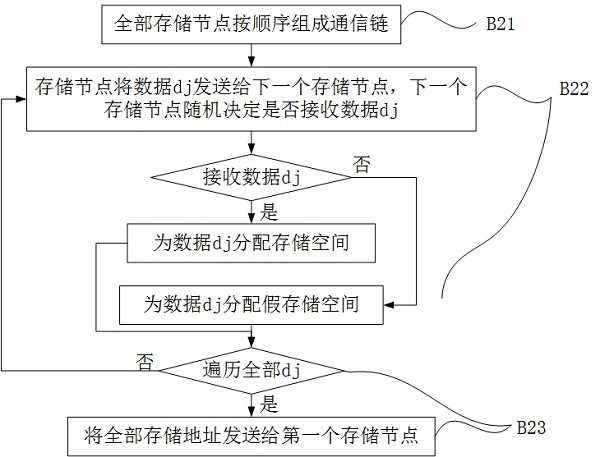
[0053] A secure data access method for consortium chains, this embodiment is based on the first embodiment, the storage node The unified addressing of the storage space has been improved, such as Figure 5 As shown, in step A), the external consensus protocol will store the node The method for unified addressing of the storage space includes: Step A1) The external consensus protocol according to the storage node The size of the storage space allocates multiple addressing intervals, and each addressing interval can index storage nodes of all storage space and there is surplus; step A2) storage nodes Randomly extract some addresses from each addressing interval as false addresses, addressing as false addresses points to the same storage area, and the rest of the addressing points to the real storage area; step A3) storage node Set the order of multiple addressing intervals, and set the addressing switching cycle. After each switching cycle, the storage node Loop switc...
Embodiment 3
[0055] A secure data access method for consortium chains. This embodiment is based on the first embodiment, and the participating data The access consortium chain node 100 has been further improved. In this embodiment, the alliance chain node Submit data storage requirements to the external consensus protocol, and the data to be stored is , the external consensus protocol randomly selects storage nodes middle Participate in storing data as , will participate in storage nodes and their order are recorded in tabular form and identified with the data The association is stored in the alliance chain node Corresponding storage node On the alliance chain node need to restore data , recorded according to the table storage nodes and their order, construct secure multi-party computations, obtain recovered data , to complete the data access. This embodiment records that the technical solution is suitable for data access of consortium chains with many nodes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com