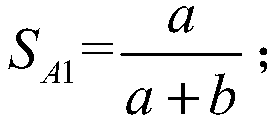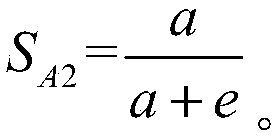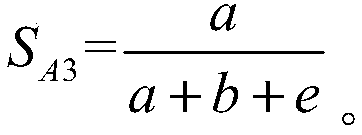Patents
Literature
63results about How to "Avoid knowing" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
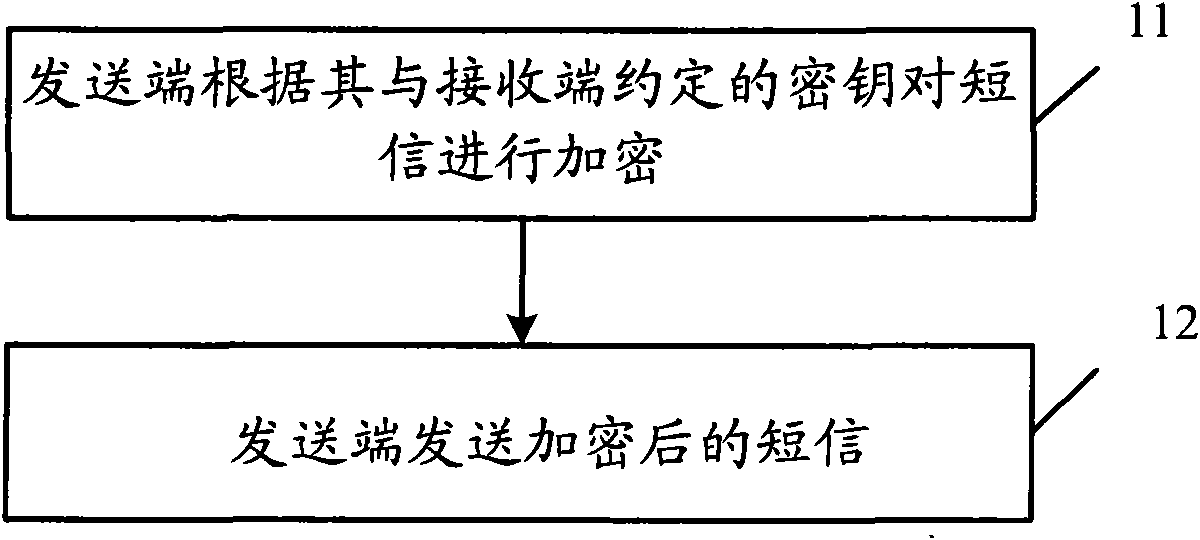
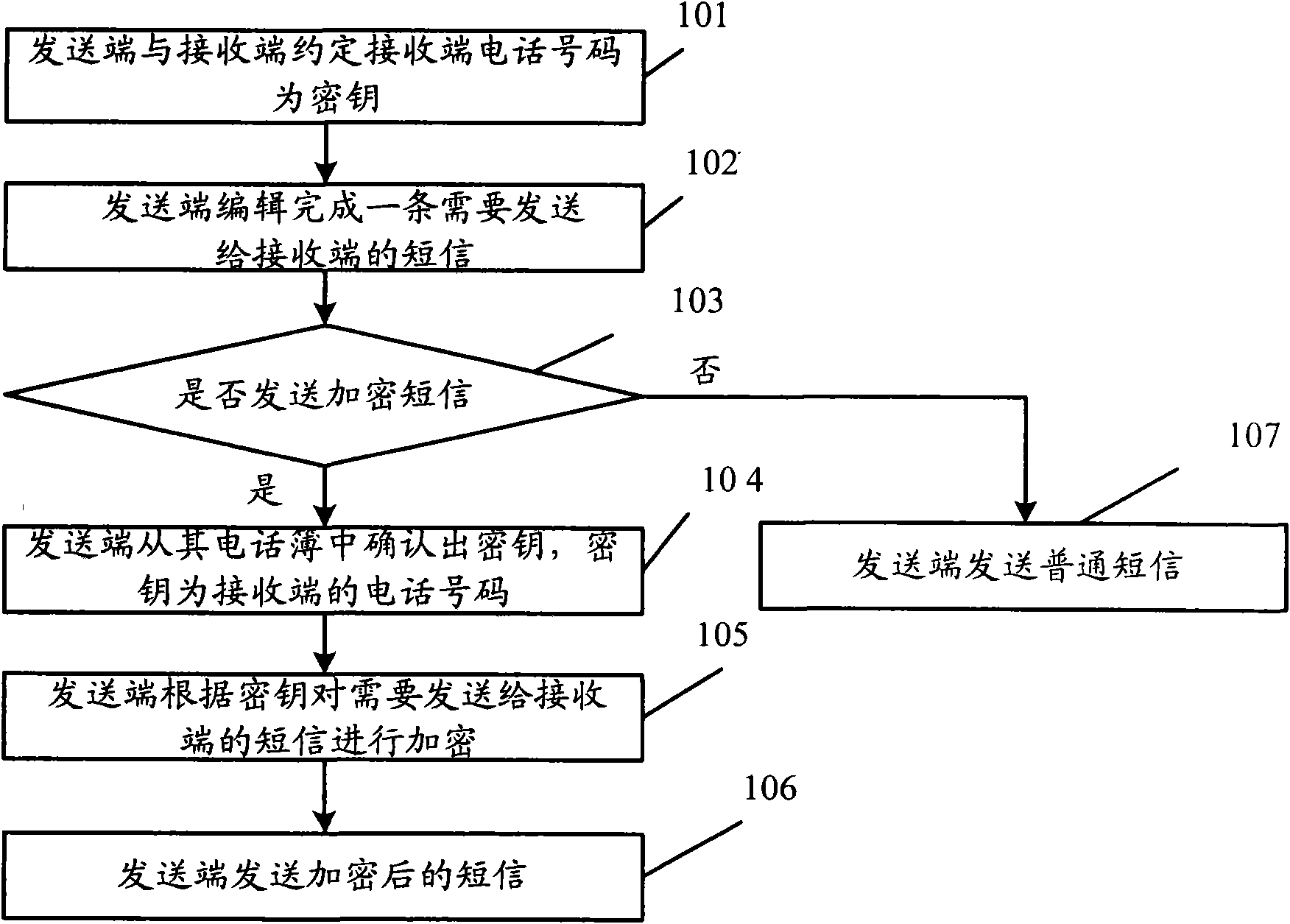
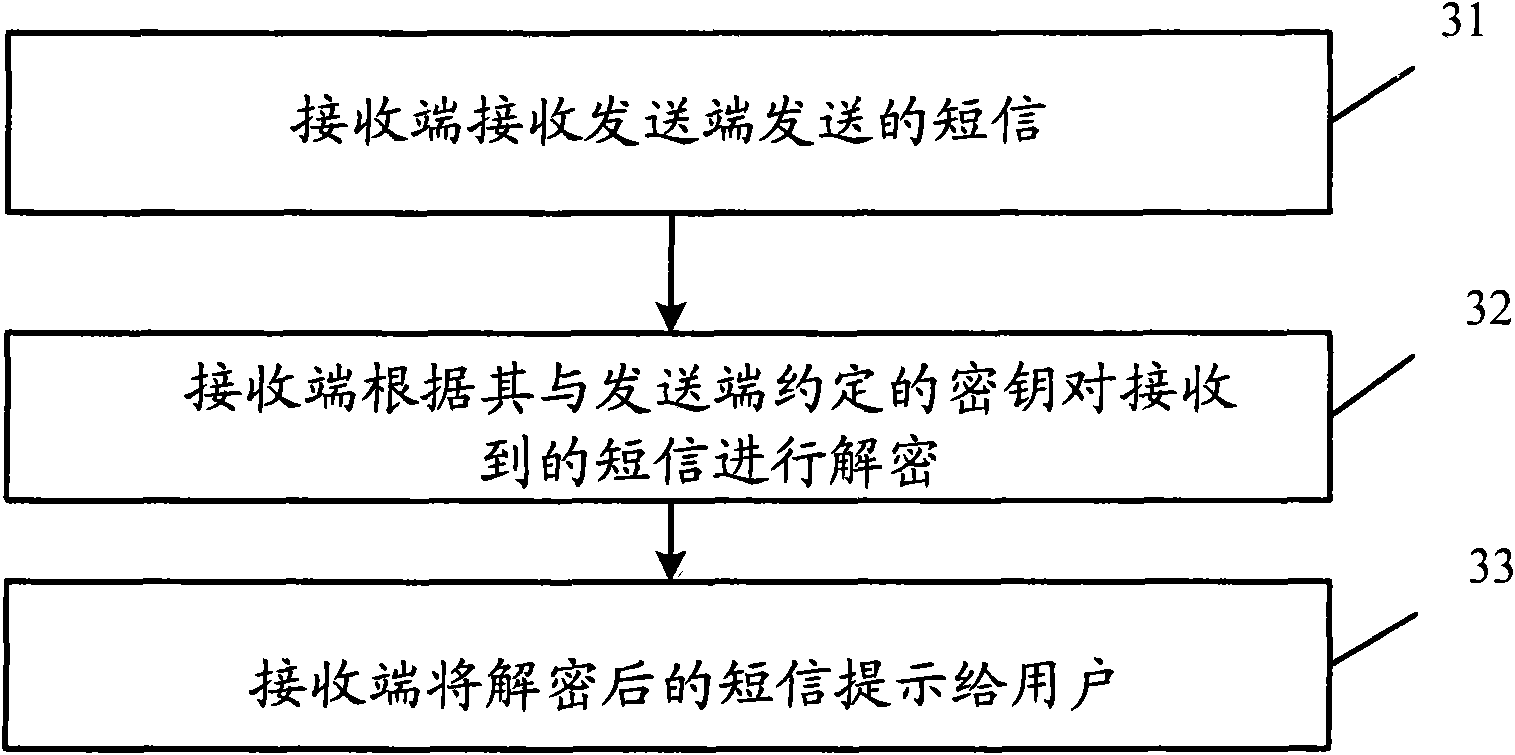
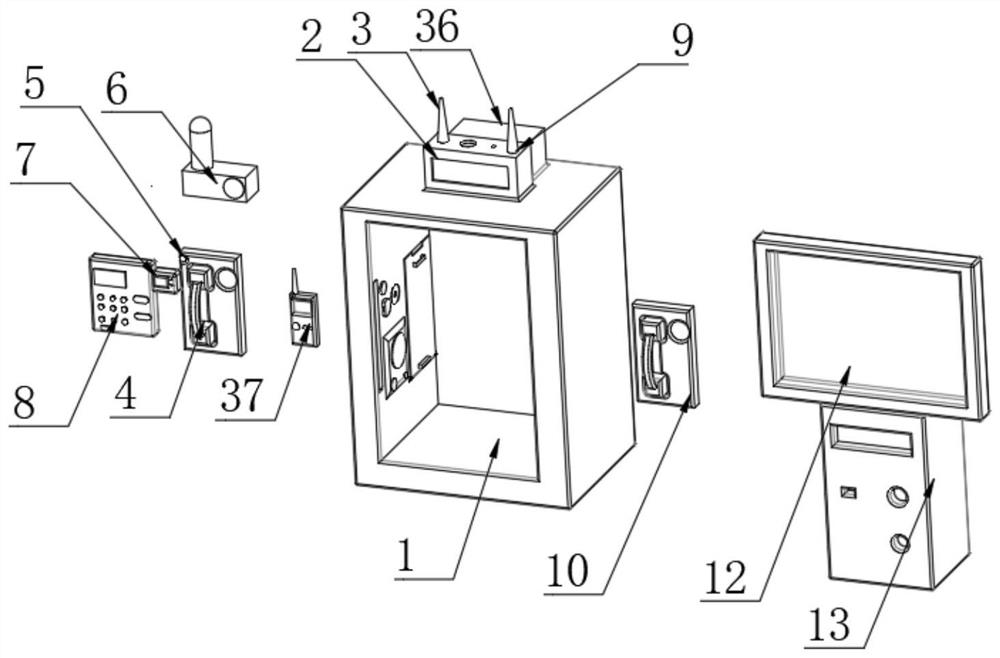
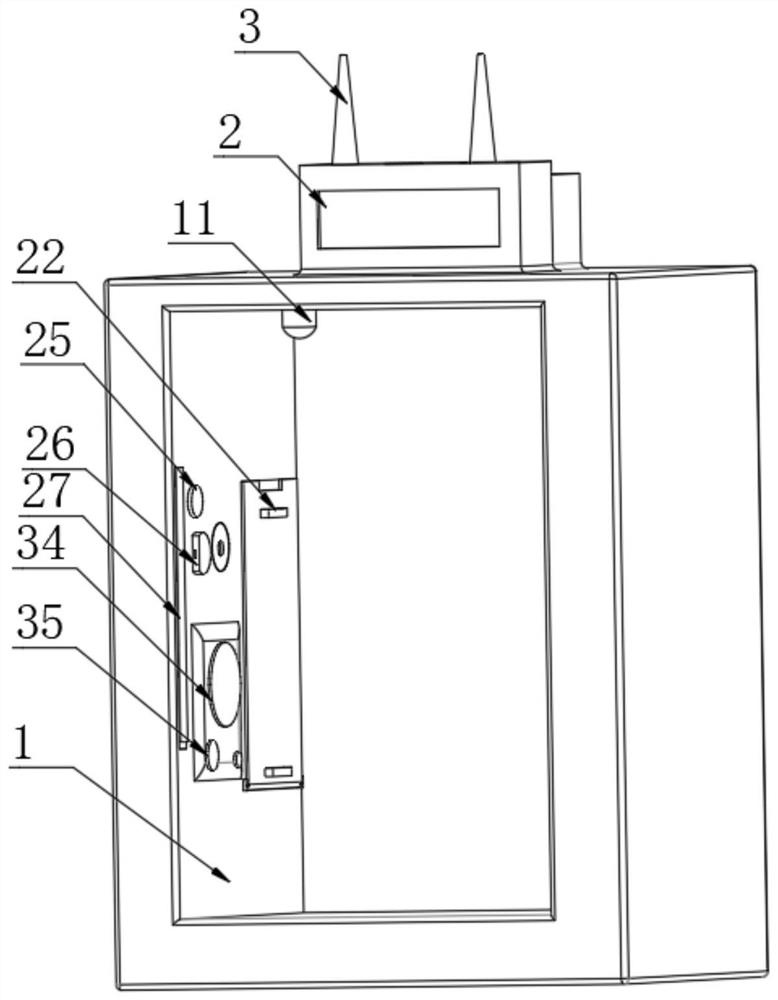
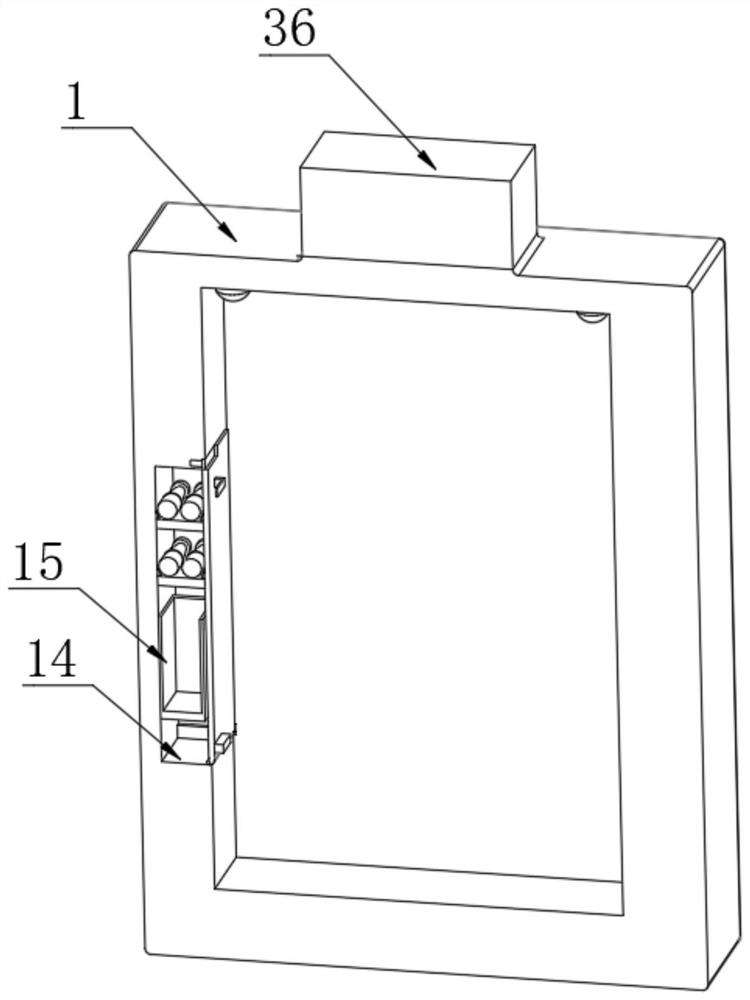
Short message sending and receiving method, short message sending and receiving device and mobile terminal
InactiveCN101626567AAvoid knowingImprove privacyMessaging/mailboxes/announcementsSecurity arrangementComputer hardwareText message
Owner:HUAWEI DEVICE (SHENZHEN) CO LTD
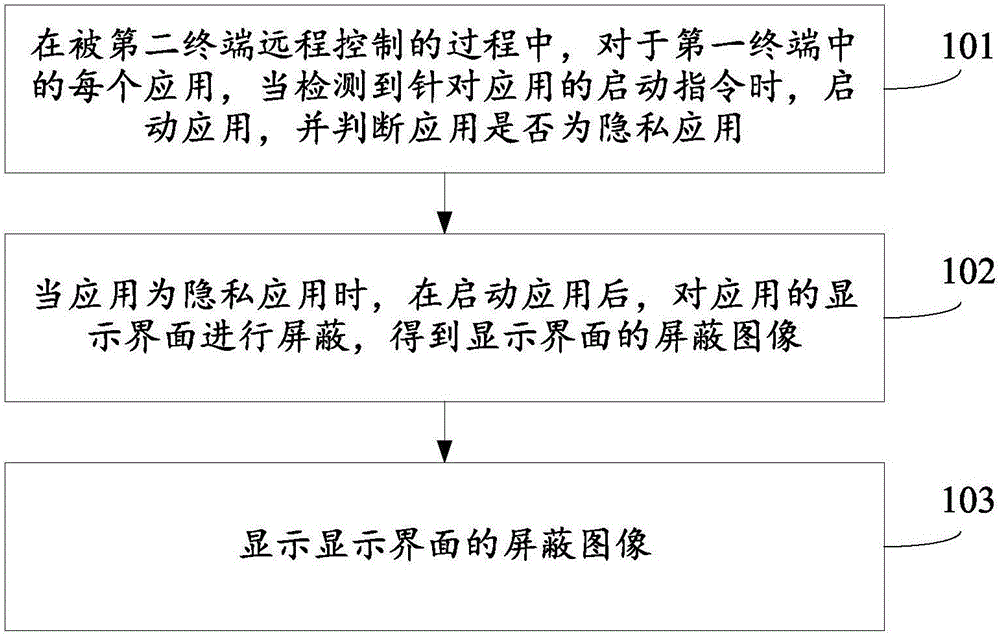
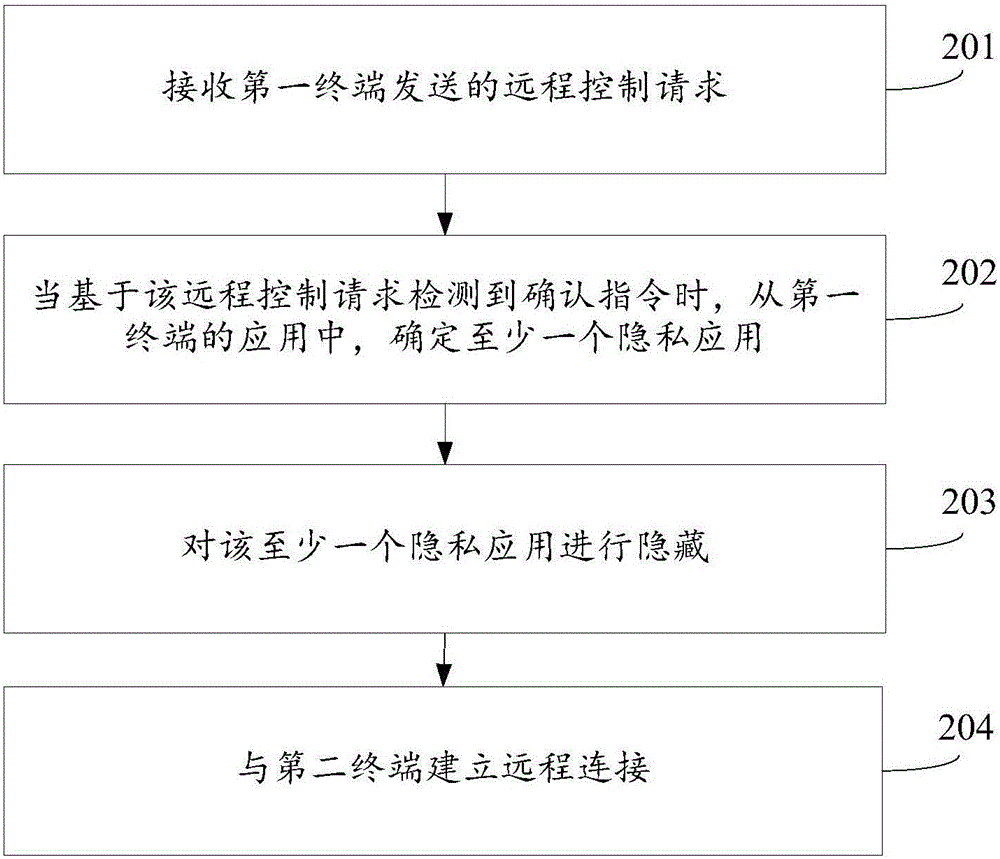
Remote control method and apparatus
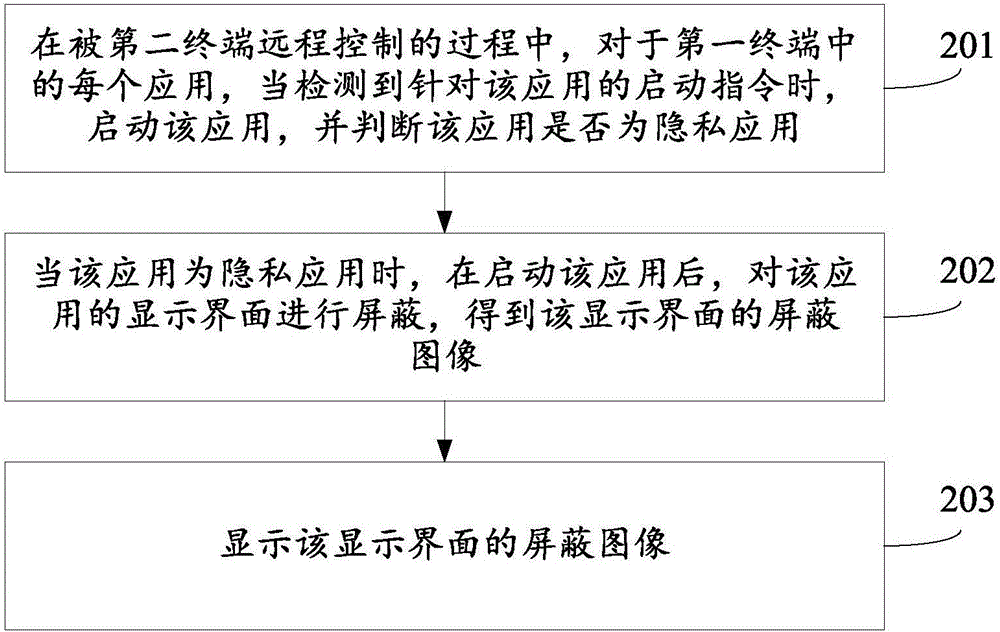
ActiveCN105956486AAvoid Privacy LeakageGuaranteed privacy and securityDigital data protectionRemote controlThe Internet
The invention relates to a remote control method and apparatus, and belongs to the technical field of internet. The method is applied to a first terminal. The method comprises the steps of starting an application when a starting instruction for the application is detected for each application in the first terminal in a process of remote control by a second terminal, and judging whether the application is a private application or not; when the application is the private application, hiding a display interface of the application after starting the application to obtain a hided image of the display interface; and displaying the hided image of the display interface. According to the method and apparatus, the privacy leakage of the first terminal can be effectively prevented to ensure privacy security of the first terminal.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
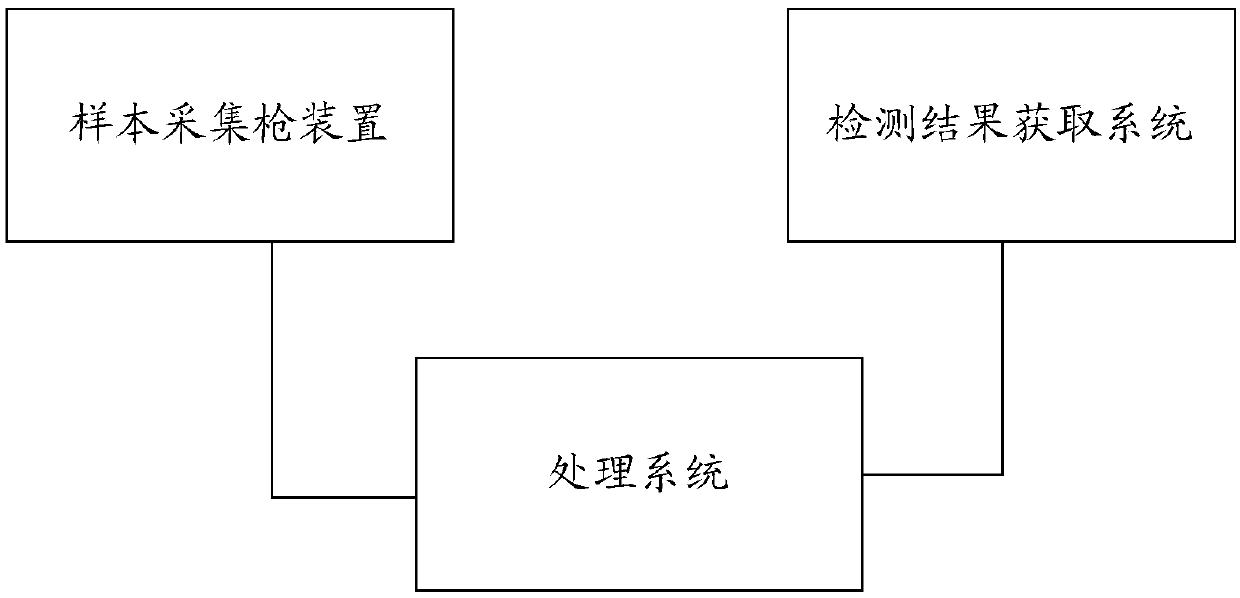
Epidemic situation preventing and monitoring general investigation system
InactiveCN109727681APrivacy protectionAvoid knowingEpidemiological alert systemsComputer hardwareTreatment system
The invention discloses an epidemic situation preventing and monitoring investigation system which comprises a sample acquisition gun device, a testing result acquiring system and a processing system.The sample acquiring gun device comprises an identity information acquiring device and a disposable sampling device with a unique identification mark. The sample acquisition gun device correlates theidentity information and the identification mark of the corresponding detecting sample and transmits to the processing system. The testing result acquiring system acquires the testing result of the testing system, correlates the testing result with the identification mark and transmits to the processing system. The processing system receives the identity information and the identification mark which are transmitted by the sample acquiring gun device and is used for receiving the testing result and the identification mark that are transmitted by the testing result acquiring system, furthermorecorrelates the corresponding identity information, the identification mark and the testing result and stores in a database. The epidemic situation preventing and monitoring investigation system has advantages of realizing real-name testing, well protecting privacy of a tested person, and settling a problem of perform disease testing when the privacy right is ensured in high-risk population.
Owner:戚本昊
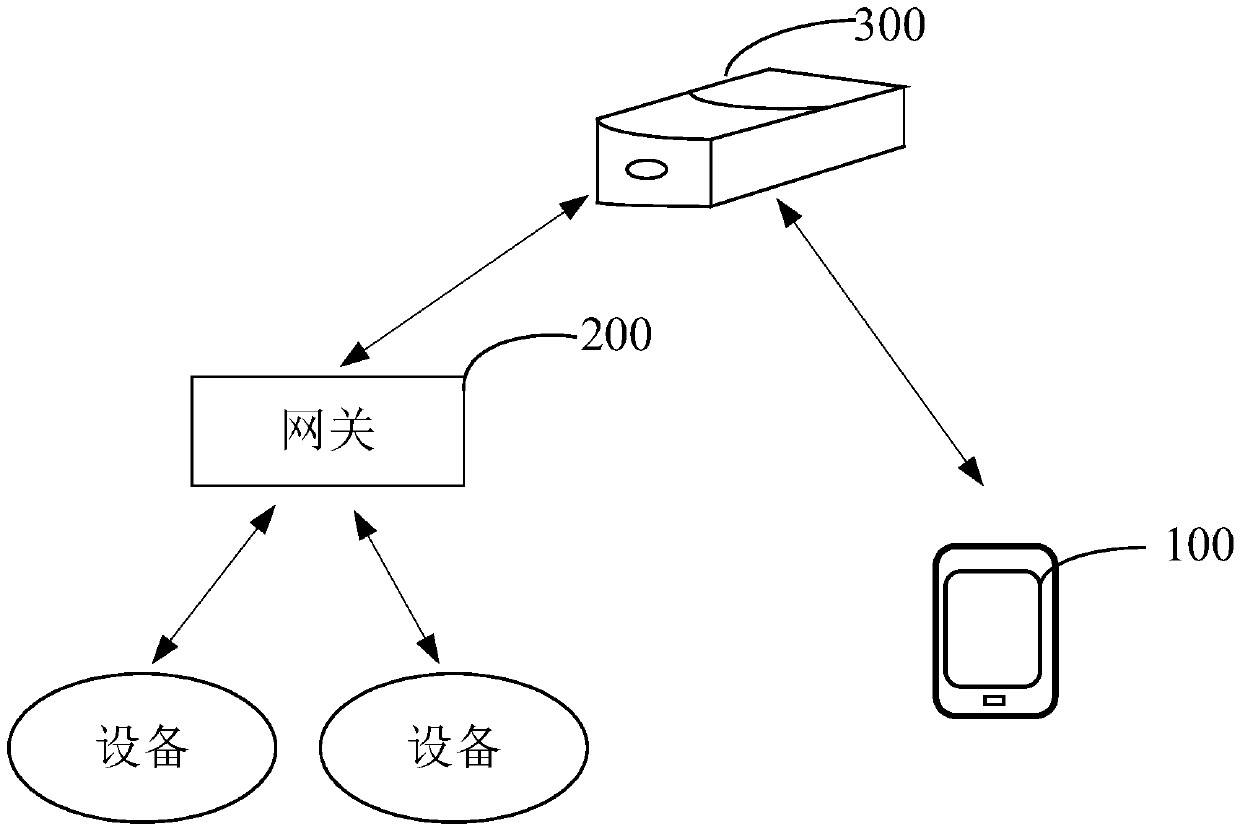
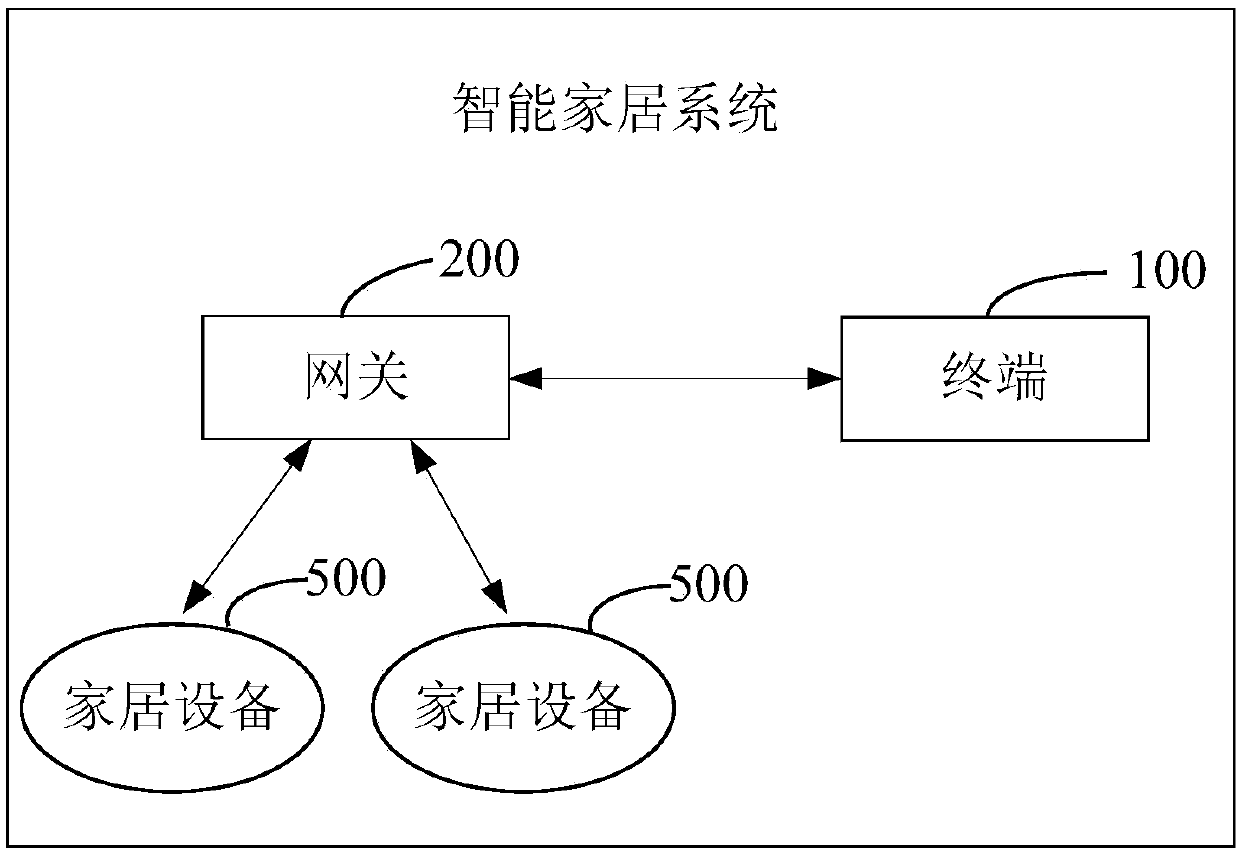
Intelligent home system, information encryption method, information encryption device and terminal
InactiveCN107948178AEnsure communication securityImprove securityKey distribution for secure communicationData switching by path configurationCommunications securityComputer terminal
The invention discloses an intelligent home system, an information encryption method, an information encryption device and a terminal, and belongs to the technical field of computer application. The intelligent home system comprises the terminal, a gateway and home equipment, wherein when generating control information according to a triggered control operation, the terminal obtains a key sequencenumber sent by the gateway, selects a key from stored key sequences according to the key sequence number to obtain an encryption key, encrypts the control information, and sends the encrypted controlinformation to the gateway; and, when receiving the encrypted information sent by the terminal, the gateway selects a decryption key according to the sent key sequence number, decrypts the encryptedinformation to obtain the control information, and sends the control information to the related home equipment, so that the home equipment works according to the control information. The invention further provides the information encryption device and the terminal. By means of the intelligent home system, the information encryption method, the information encryption device and the terminal disclosed by the invention, communication security in a local area network can be ensured; and the security of controlling the home equipment through the local area network can be improved.
Owner:SHENZHEN LUMIUNITED TECH CO LTD
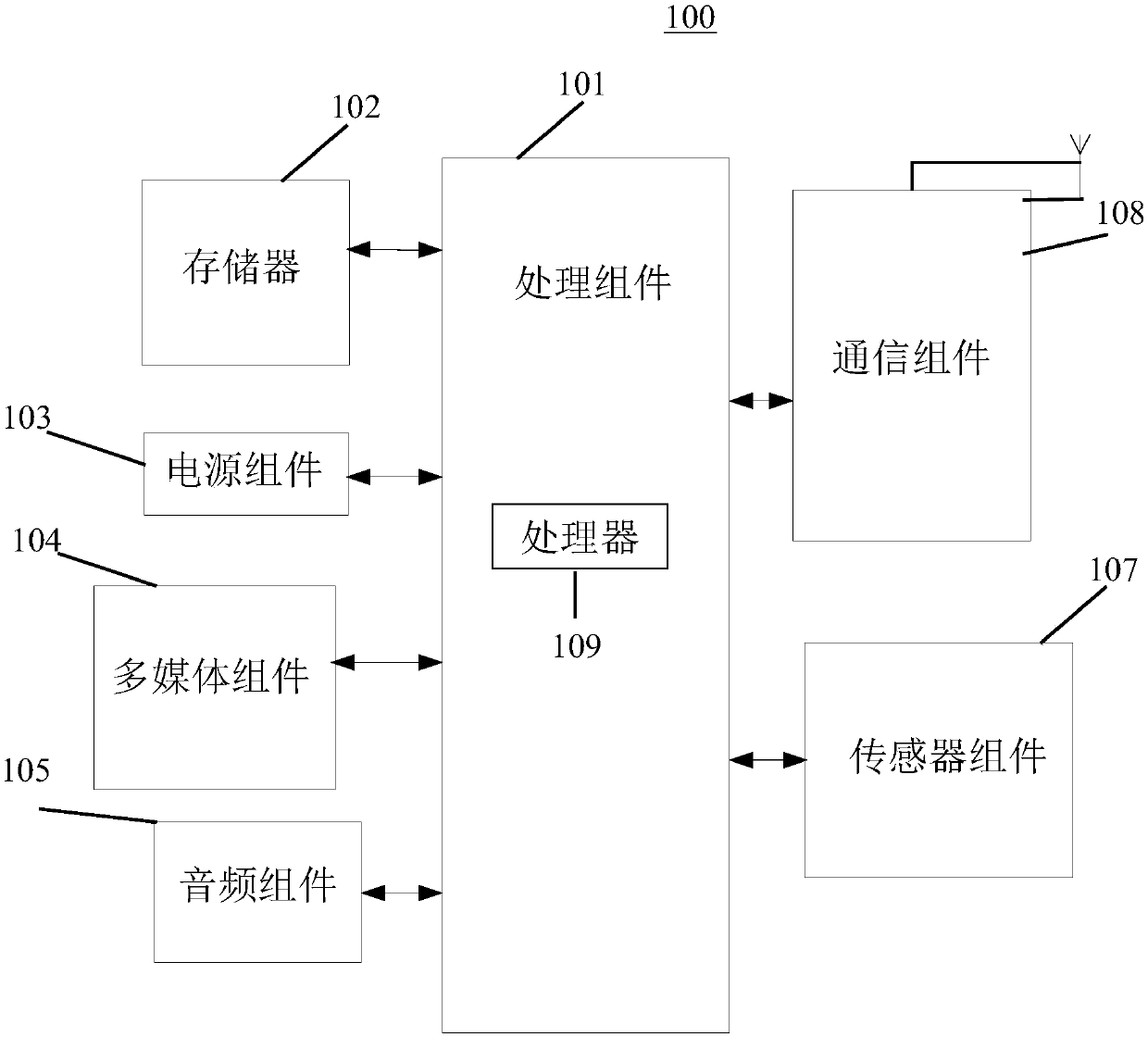
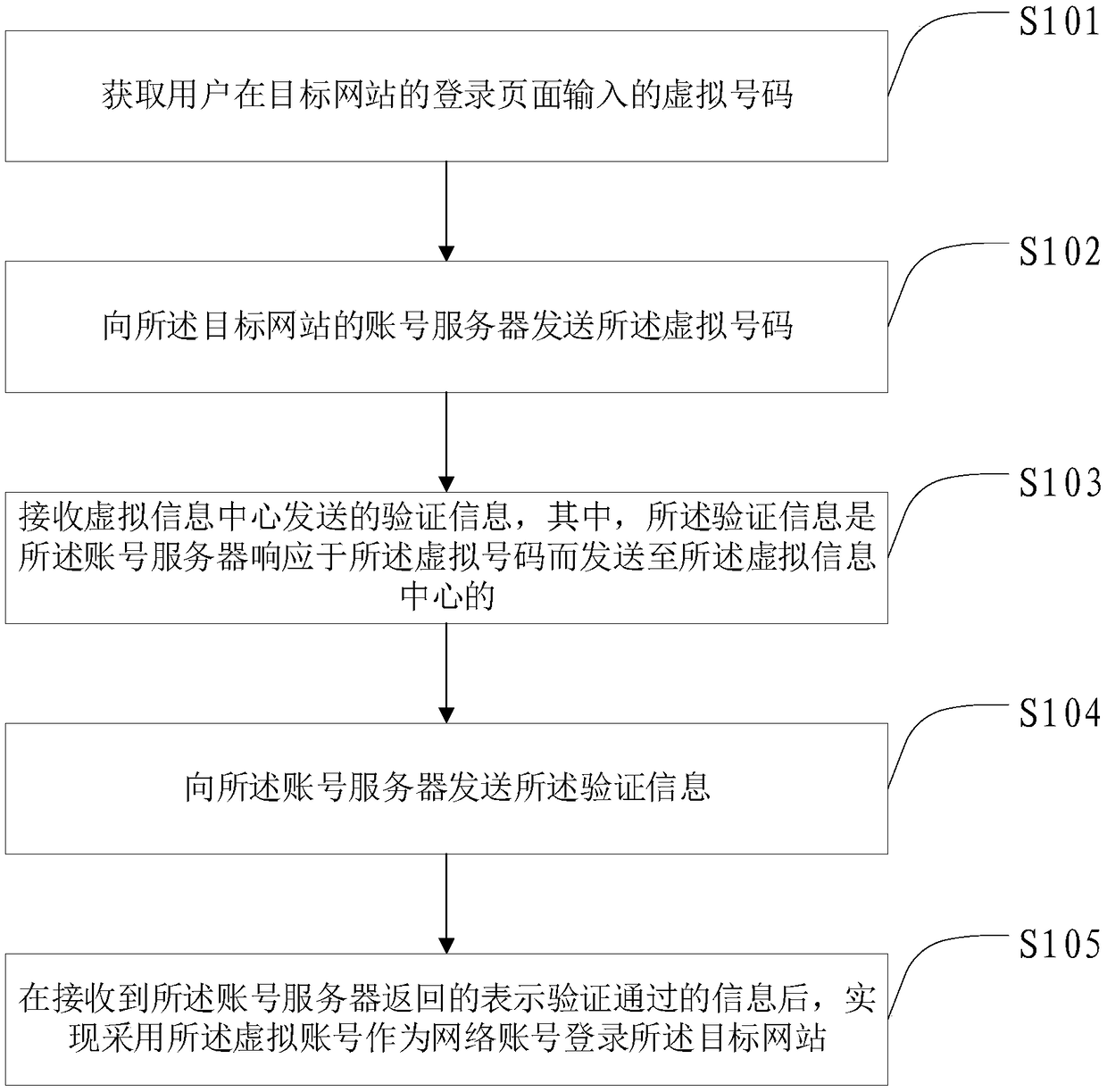
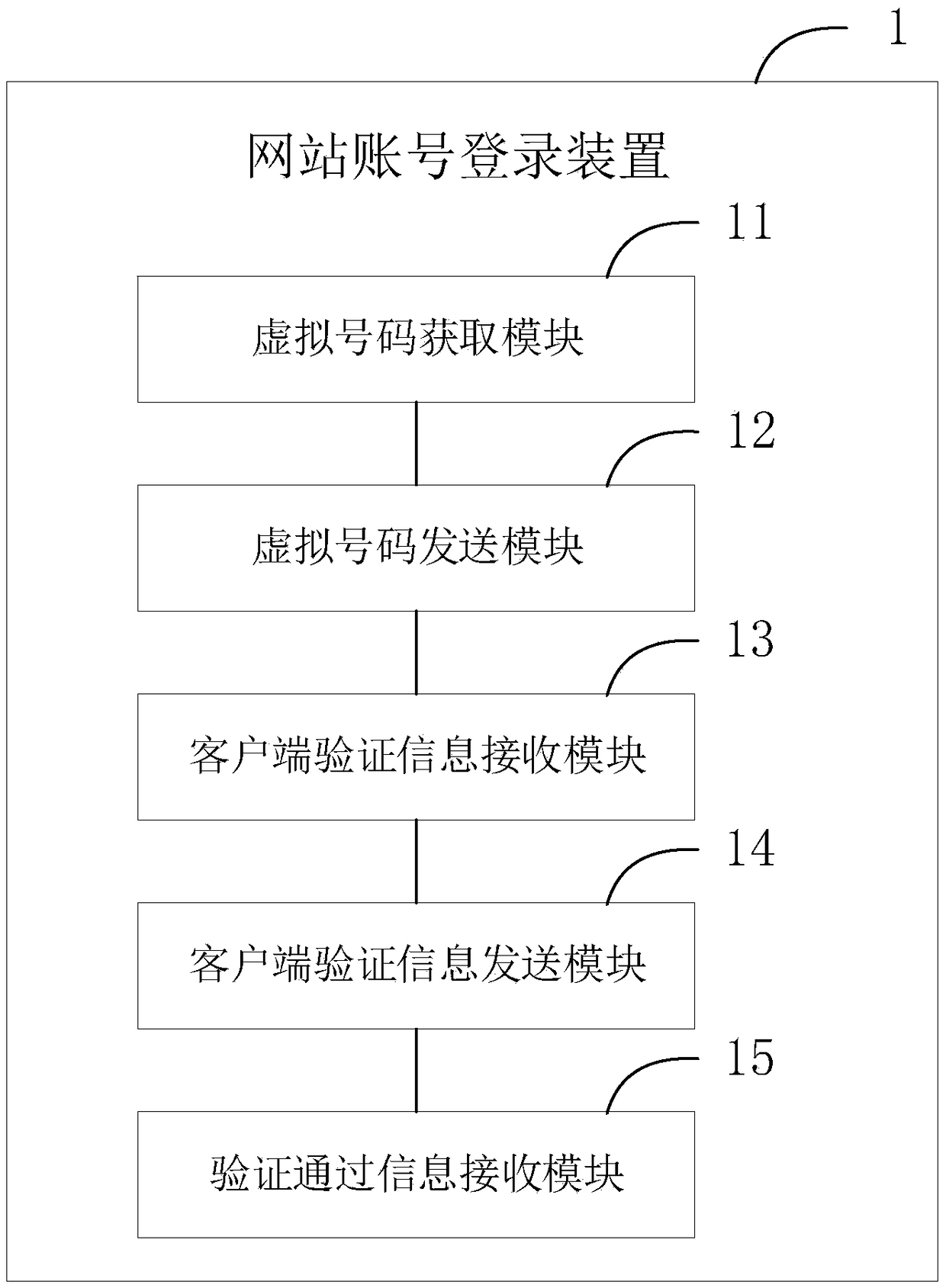
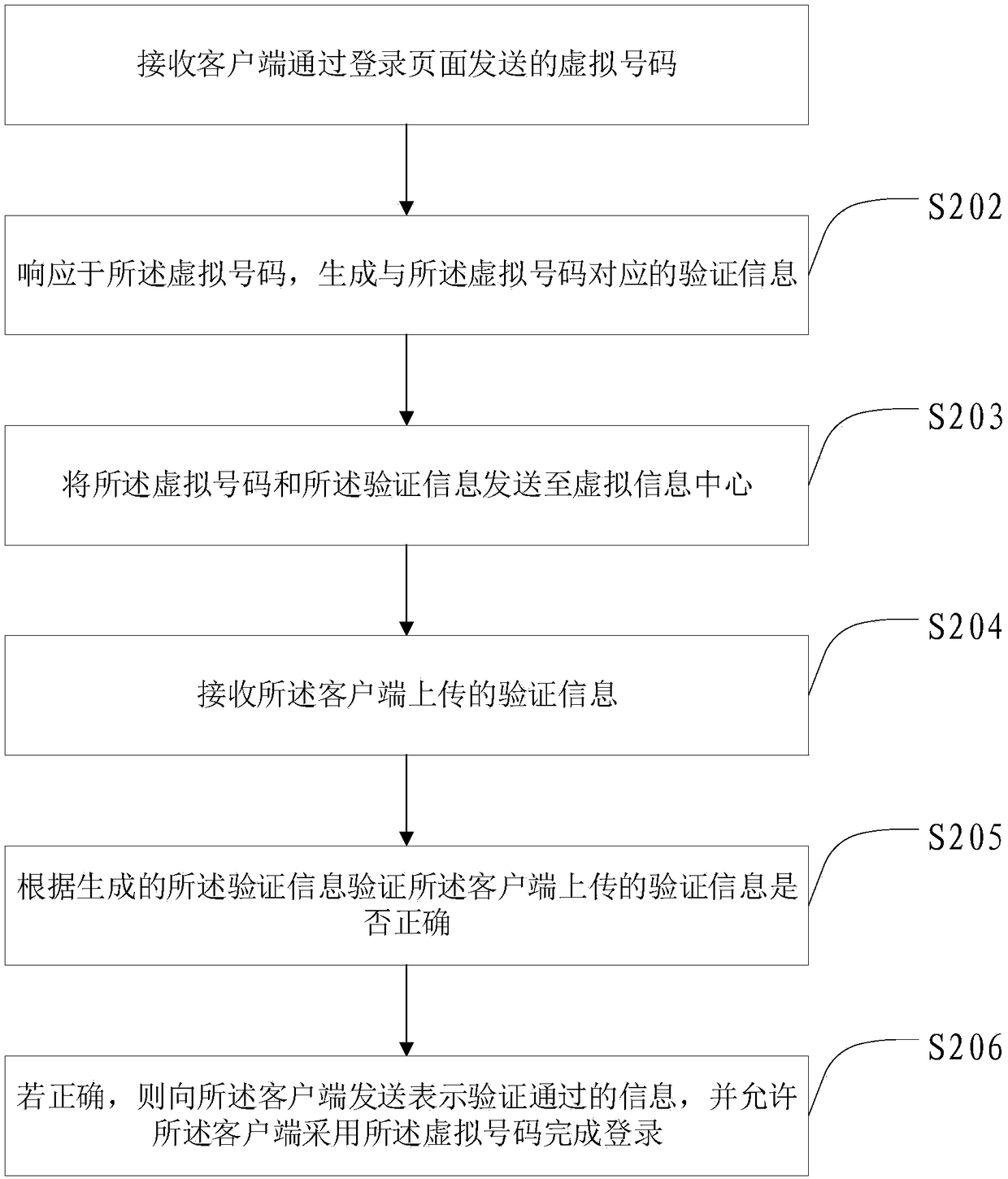
Method and device for website account login, verification and verification information processing and system
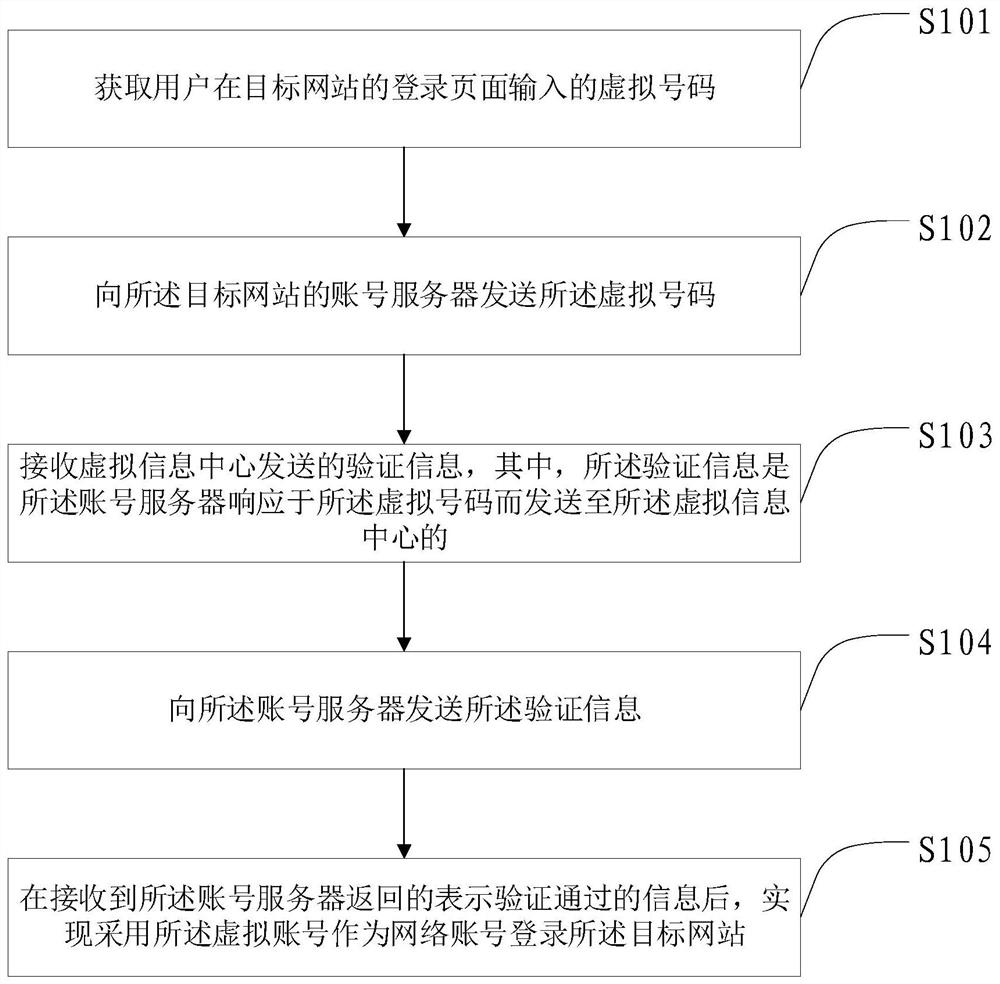
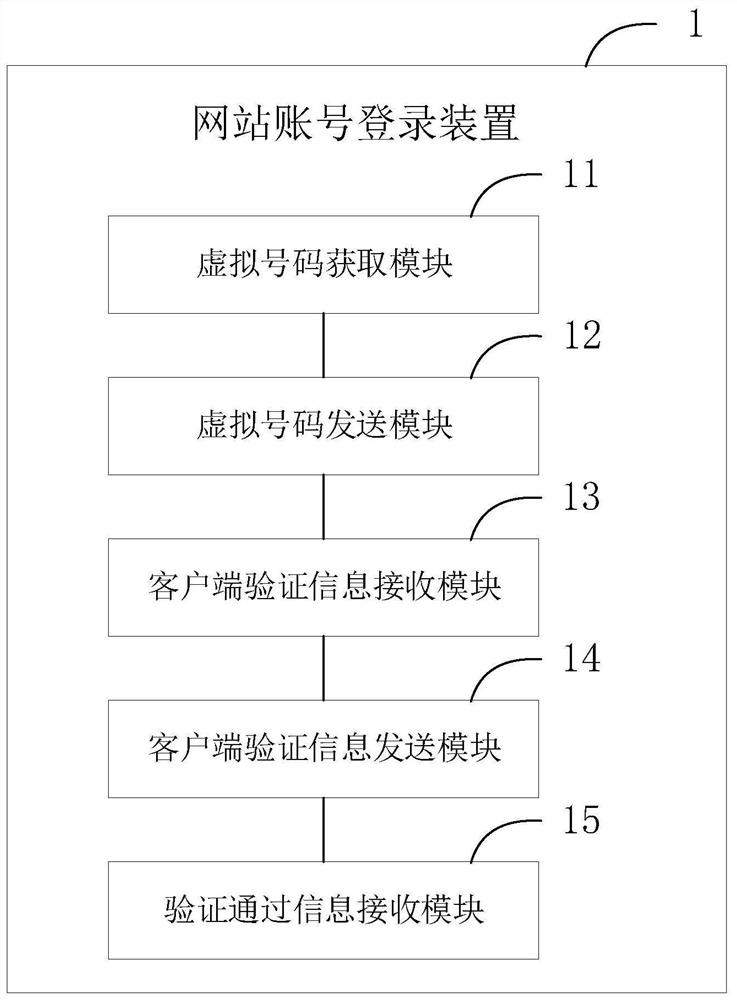
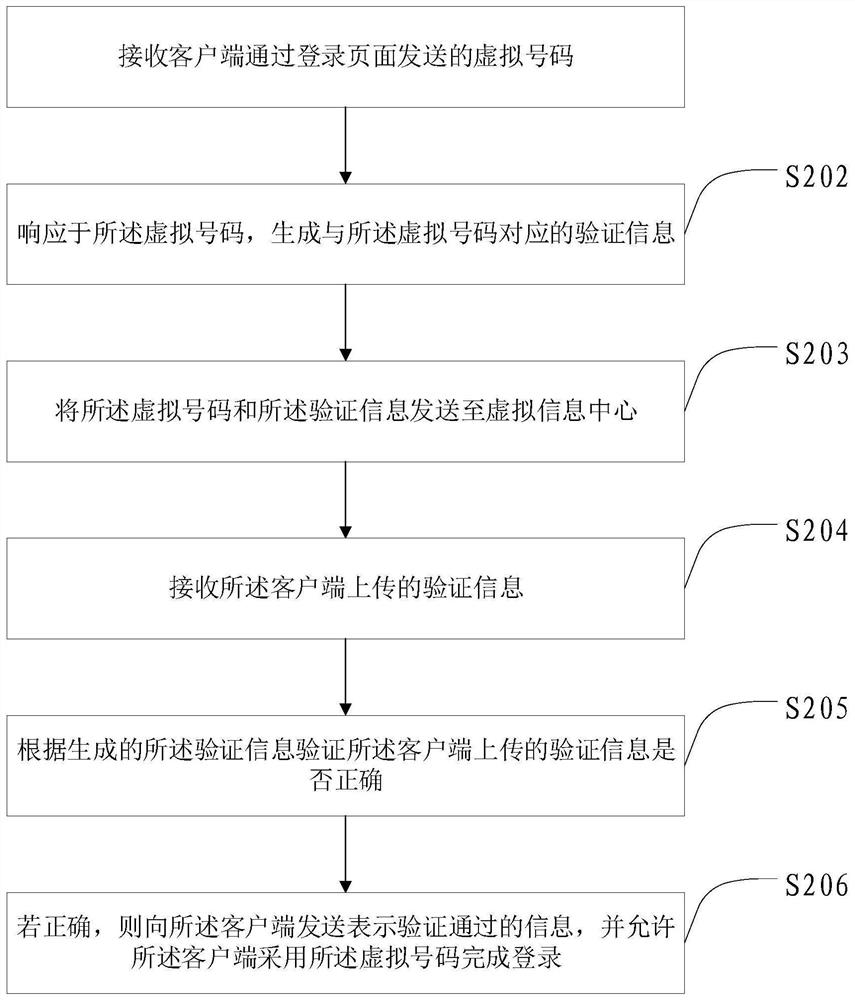
The invention provides a method and device for website account login, a method and device for login verification, a method and device for verification information processing and a website account login system. The website account login method comprises the steps that a virtual number input in a login page of a target website by a user is acquired; the virtual number is sent to an account server ofthe target website; verification information sent by a virtual information center is received; the verification information is sent to the account server; after information which represents that theverification is valid and is returned by the account server is received, it is achieved that a virtual account is adopted to serve as a network account to login the target website. Compared with the prior art, the virtual number is adopted to replace a phone number to login the website, so that it is avoided that the phone number is known by the website, thereby being capable of ensuring that thephone number of the user is not disclosed by the website.
Owner:BEIJING GZT NETWORK TECH
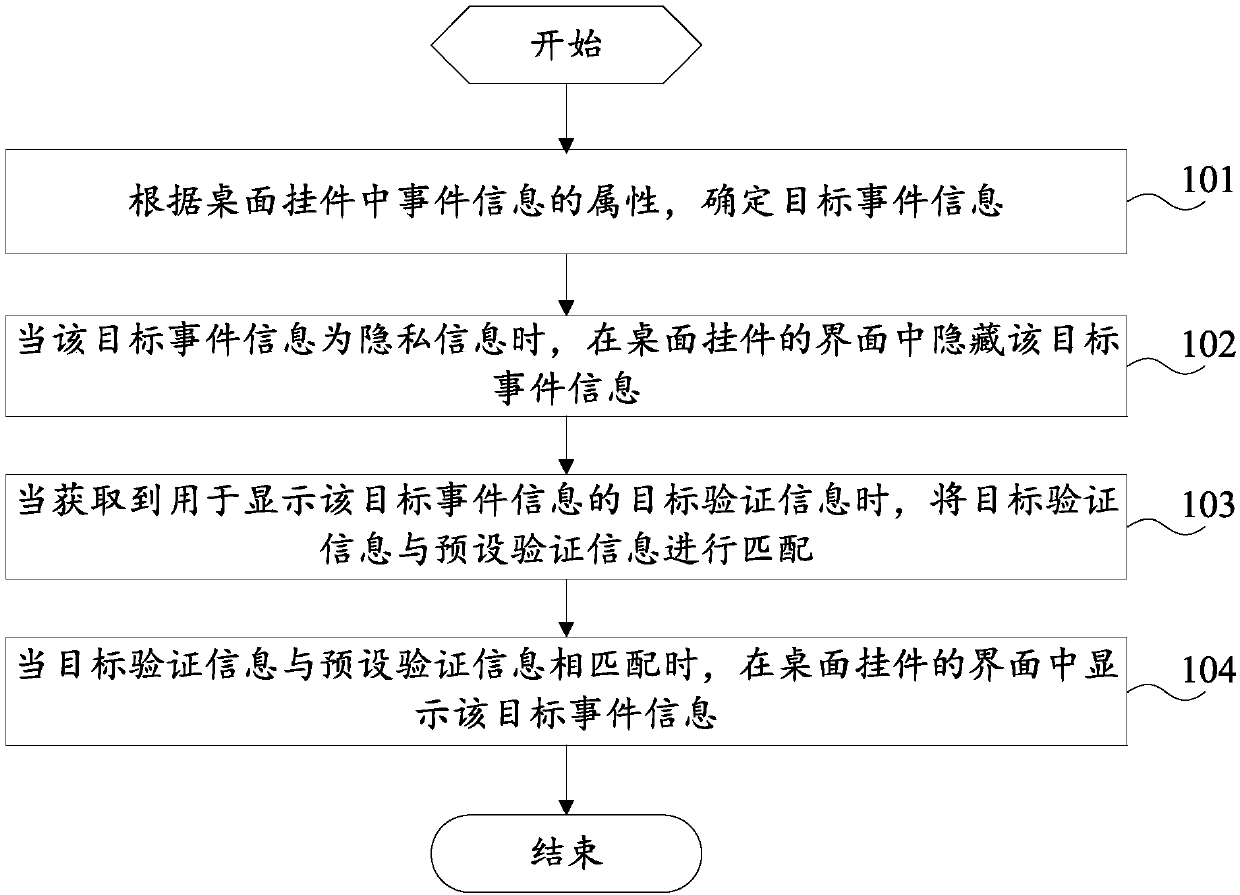
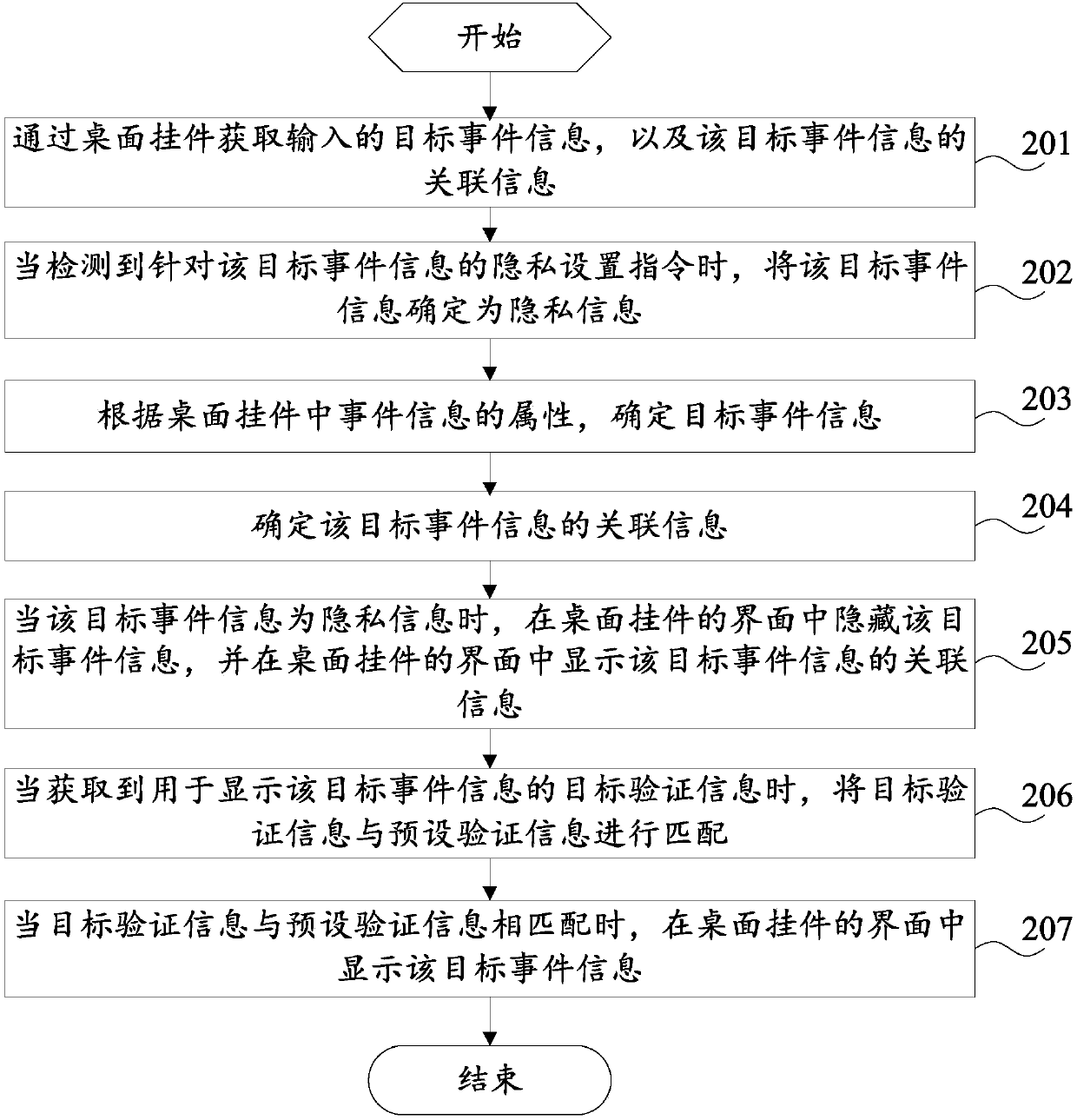
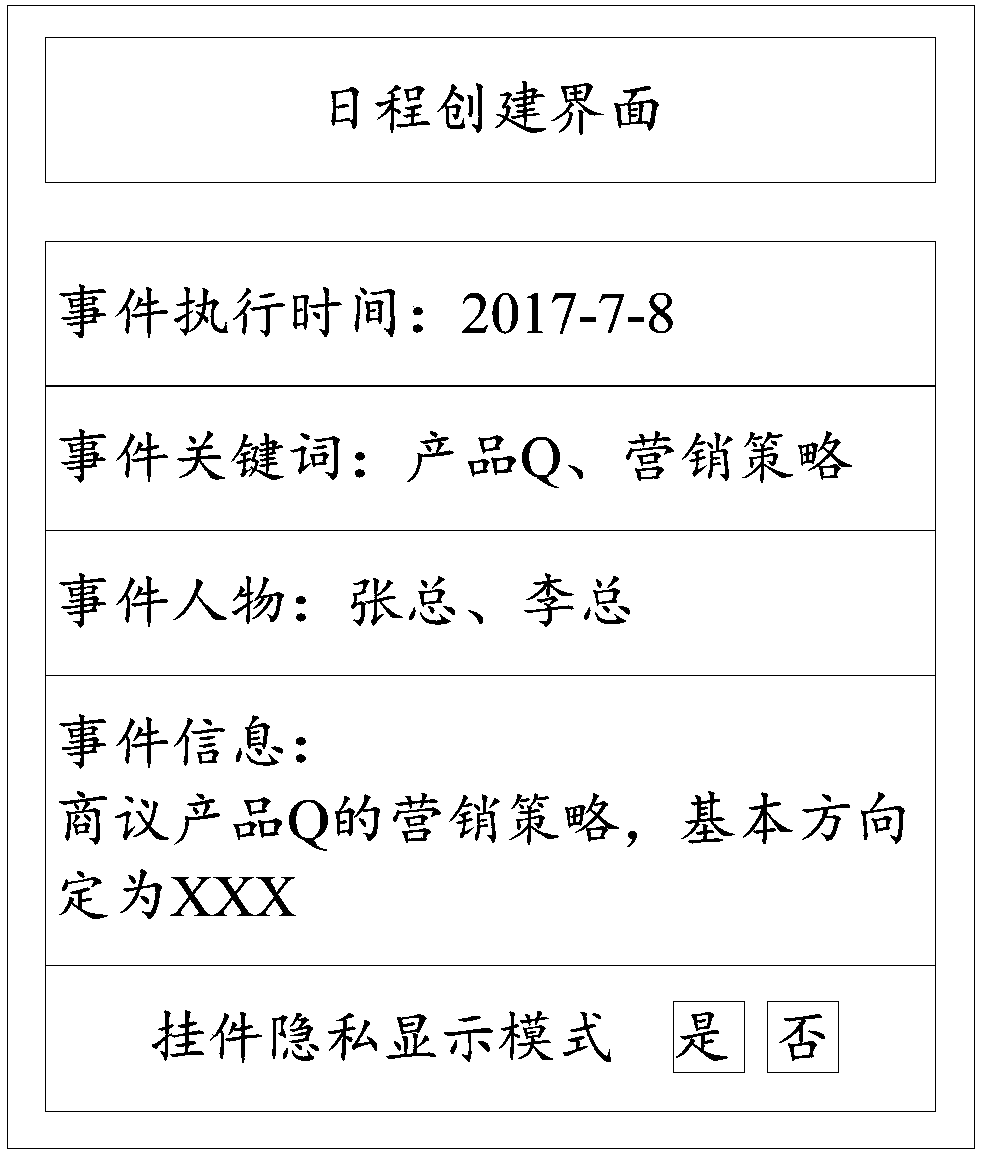
Information processing method and mobile terminal
InactiveCN107832110AAvoid knowingReduce risk of leakageDigital data protectionProgram loading/initiatingInformation processingUser privacy
The invention provides an information processing method and a mobile terminal, and relates to the technical field of information processing. The method comprises the steps that target event information is determined according to attributes of event information in a desktop pendant; the target event information is hidden in an interface of the desktop pendant; when the target event information is private information, target validation information is matched with preset validation information; when the target validation information is matched with the preset validation information, the target event information is displayed in an interface of the desktop pendant. Accordingly, when the target event information is the private information, hiding is conducted first, and then when the target validation information passes validation, the target event information is displayed in the desktop pendant, but not directly displayed in the desktop pendant; therefore, the phenomenon that private eventinformation is known by others can be avoided, and then the risk that user privacy leaks through the desktop pendant is lowered.
Owner:VIVO MOBILE COMM CO LTD
Image processing method and device, computer readable medium and electronic equipment
ActiveCN111182169AImprove flexibility and scalabilityGuaranteed security and privacyDigital video signal modificationImage basedEngineering
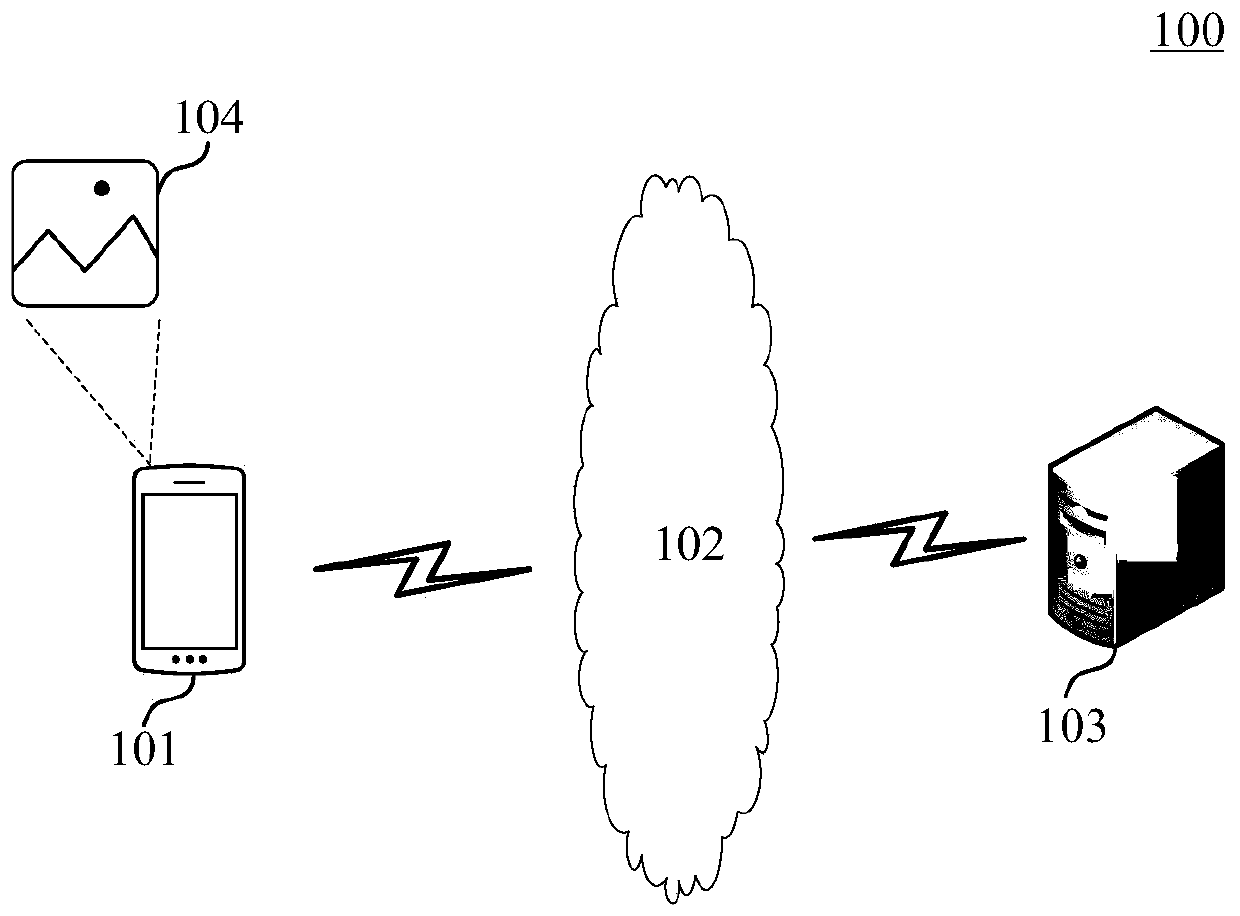
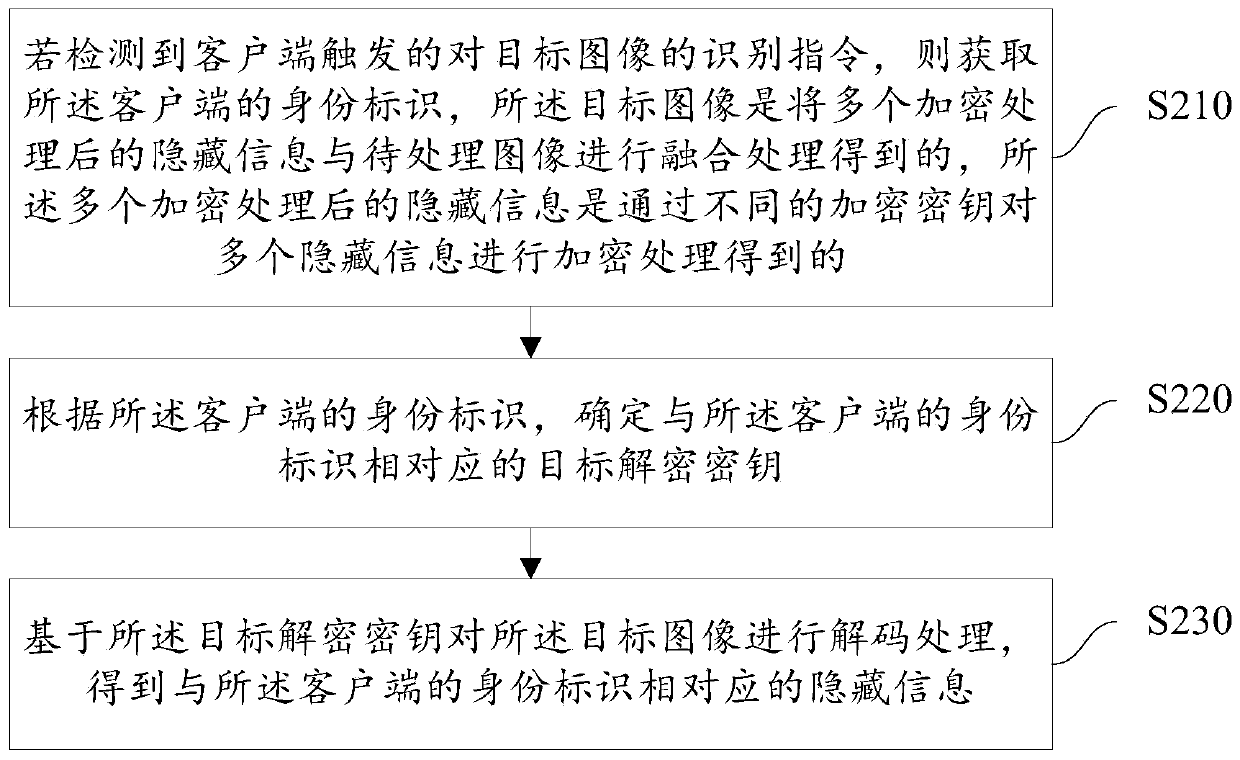
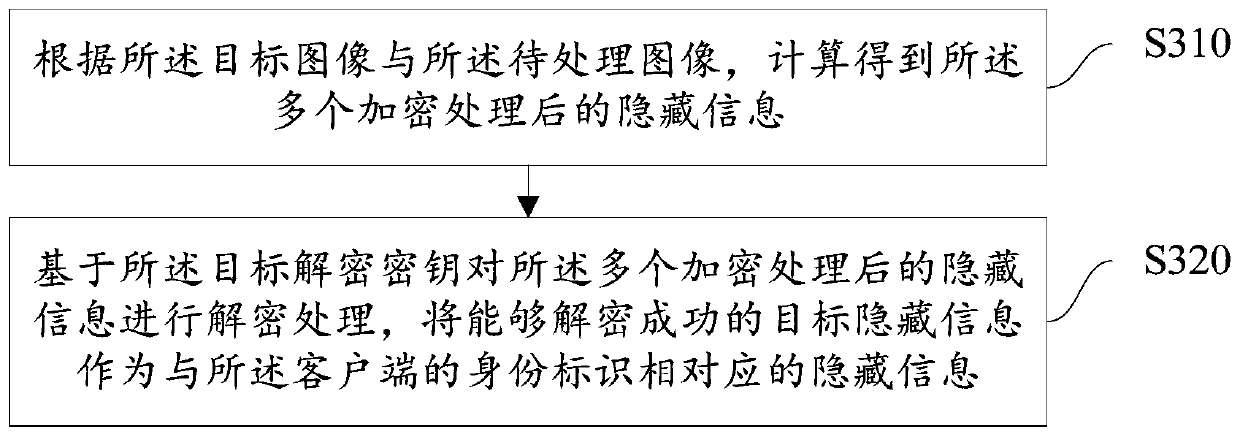
The embodiment of the invention provides an image processing method and device, a computer readable medium and electronic equipment. The image processing method comprises the steps of if an identification instruction for a target image triggered by a client is detected, obtaining an identity identifier of the client, wherein the target image is obtained by fusing the plurality of encrypted hiddeninformation with a to-be-processed image, and the plurality of encrypted hidden information is obtained by encrypting the plurality of hidden information through different encryption keys; determininga target decryption key corresponding to the identity identifier of the client according to the identity identifier of the client; and decoding the target image based on the target decryption key toobtain hidden information corresponding to the identity identifier of the client. According to the technical scheme of the embodiment of the invention, different information can be identified from thesame image according to the identity identifiers of different clients; the image identification requirements in different scenes are met; and the expandability and flexibility of the image identification information are improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Data searching method and client side
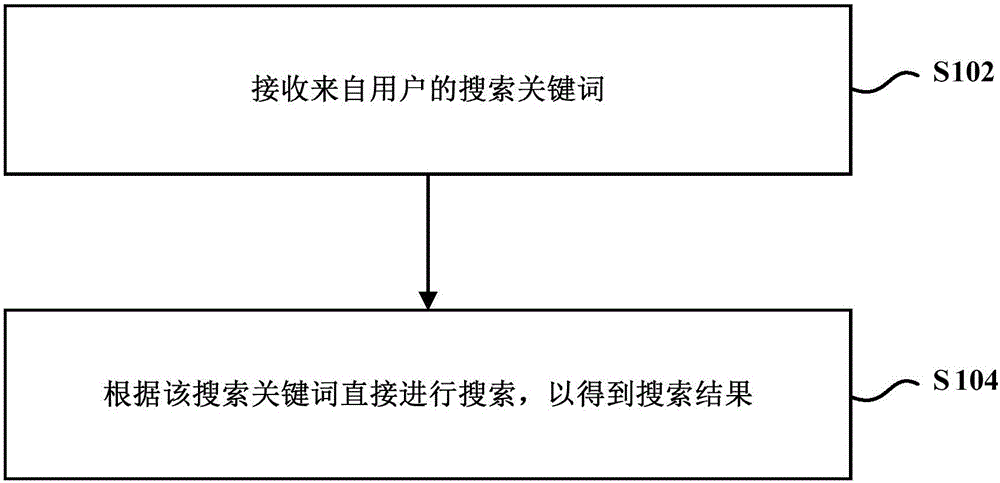
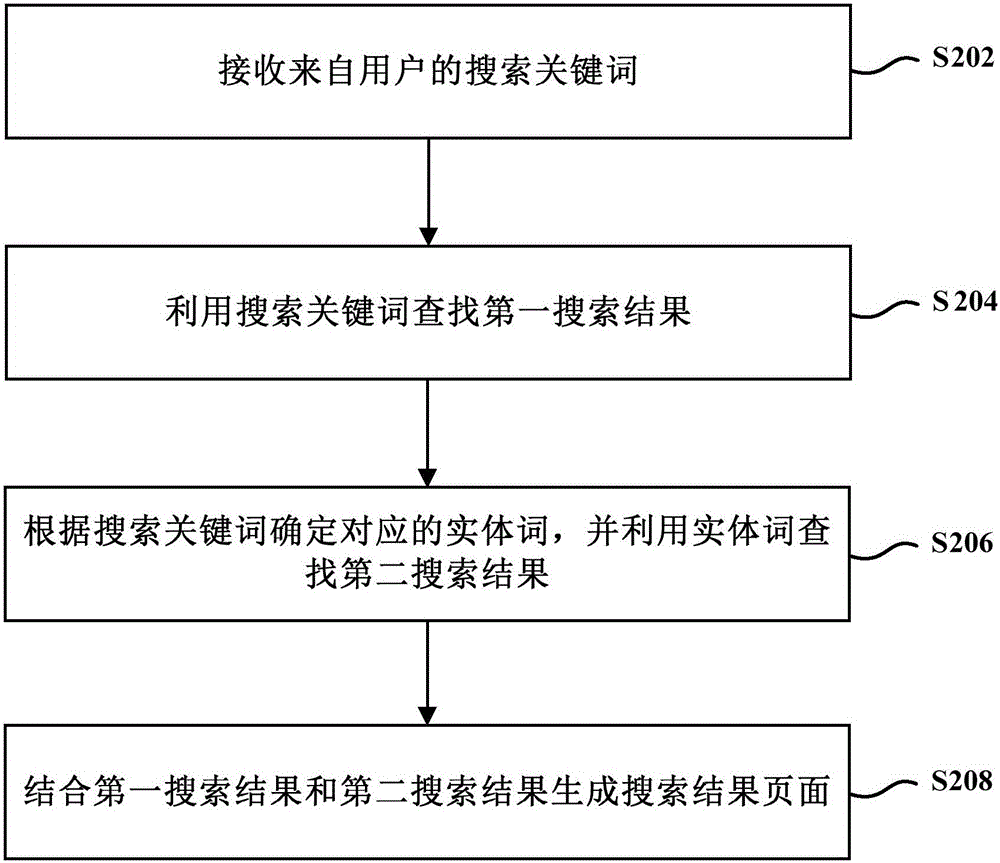
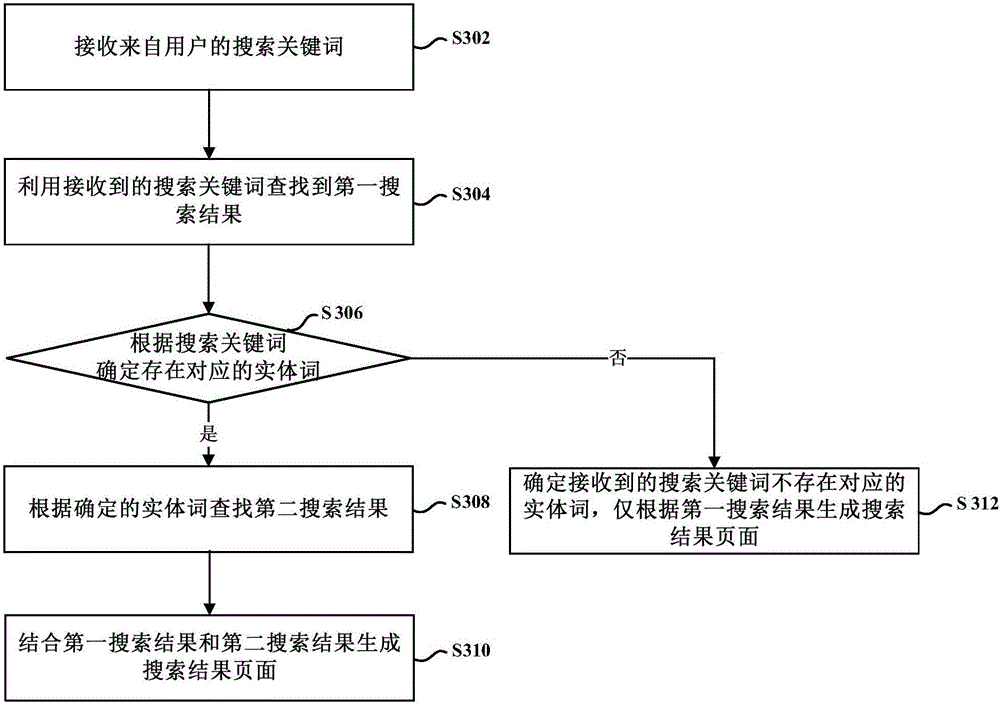
ActiveCN106096003AImprove the efficiency of search operationsImprove experienceSpecial data processing applicationsClient-sideData search
The invention provides a data searching method and a client side. The method comprises the steps of receiving search keywords from a user, searching for a first search result by means of the search keywords, determining corresponding entity words according to the search keywords and searching for a second search result by means of the entity words, and generating a search result page according to the first search result and the second search result. By the adoption of the data searching method, supplement of a first search result which is the only result that can be obtained in the prior art can be achieved, so that the search results obtained according to the search keywords of the user can cover more information of various types related to the search keywords.
Owner:BEIJING QIHOO TECH CO LTD
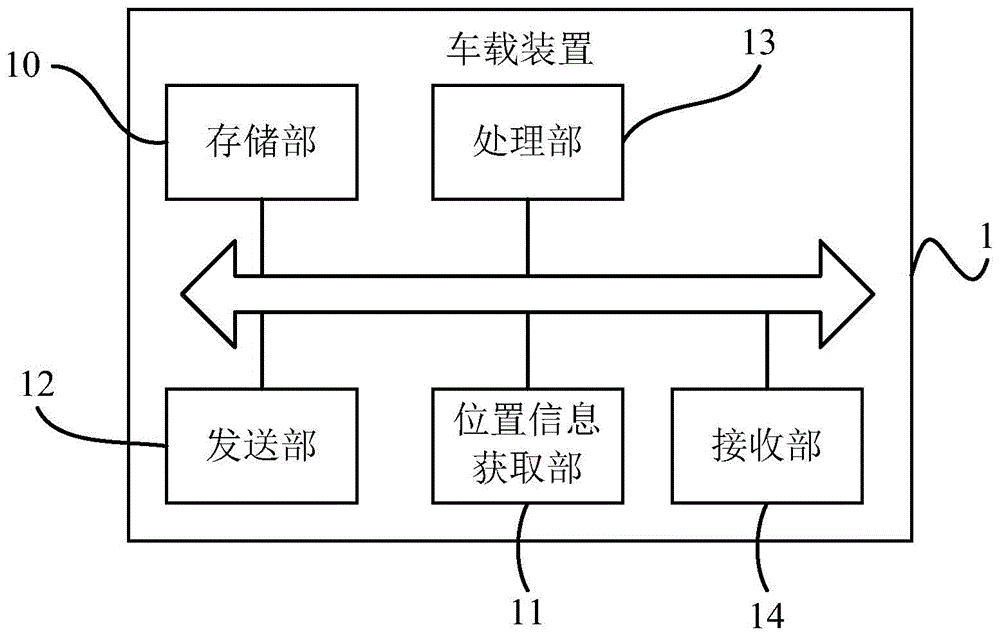
Method and vehicle-mounted apparatus for sharing vehicle position information
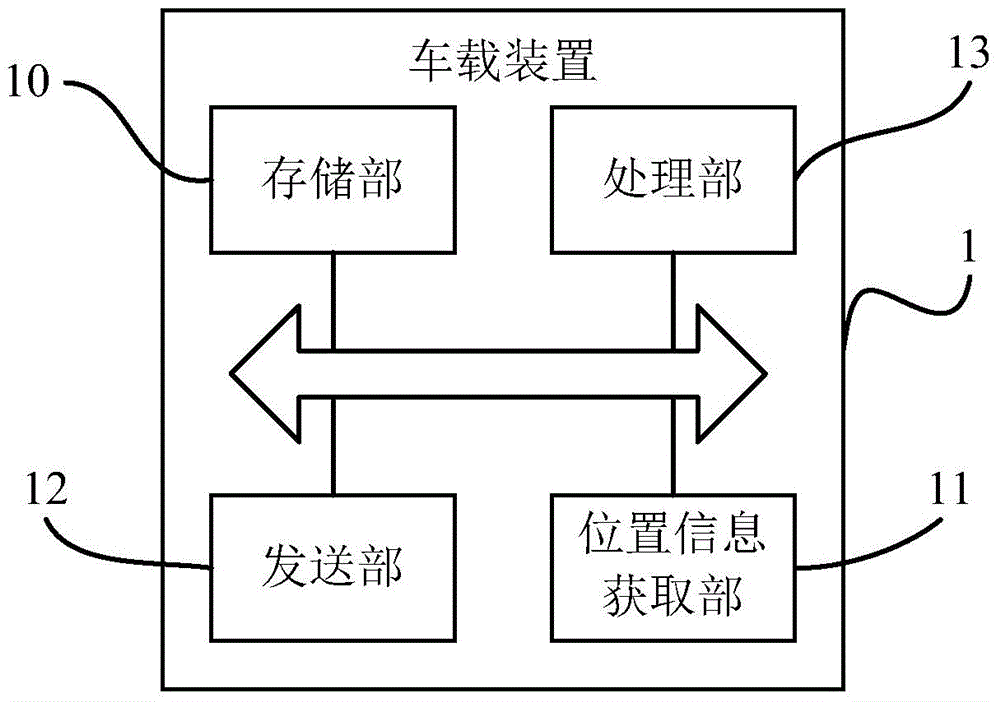
InactiveCN104809903AAcquisition speed is fastImprove synchronicityRoad vehicles traffic controlReal-time computing
The invention discloses a method and vehicle-mounted apparatus for sharing vehicle position information, and belongs to the technical field of communications, for solving the problem that vehicle position information notified by a server is different from position information of an actually driving vehicle in the prior art. The vehicle-mounted apparatus for sharing the vehicle position information comprises: a storage portion for storing identification numbers of vehicles included in a group which shares the vehicle position information; a position information obtaining portion for obtaining the position information of the vehicles included in the group; a sending portion for sending the position information and the driving route of a specific vehicle; and a processing portion for controlling the position information and the driving route of the specific vehicle and controlling the sending portion to send a driving route set on the specific vehicle to other vehicles among the vehicles included in the group.
Owner:FAURECIA CLARION ELECTRONICS (XIAMEN) CO LTD
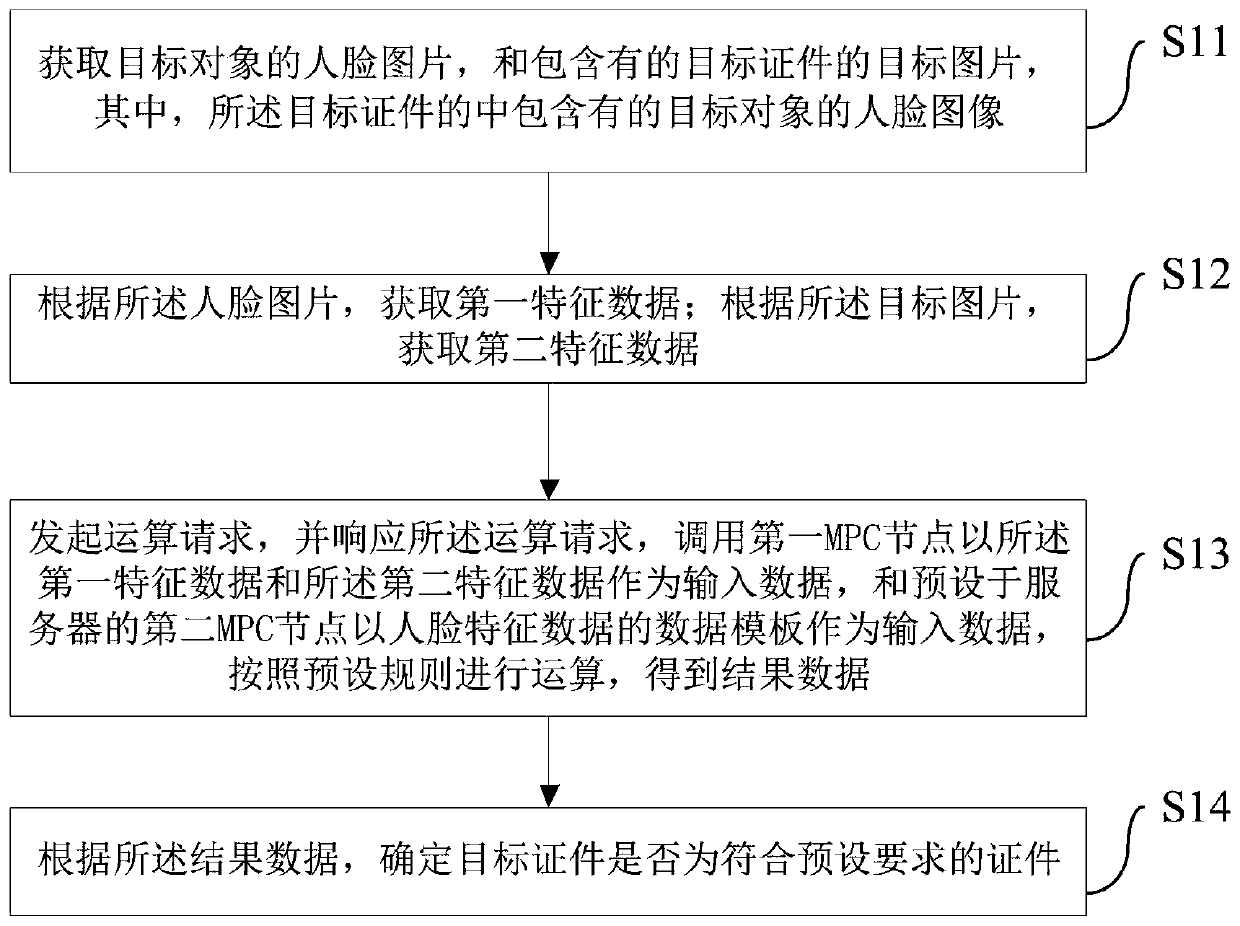
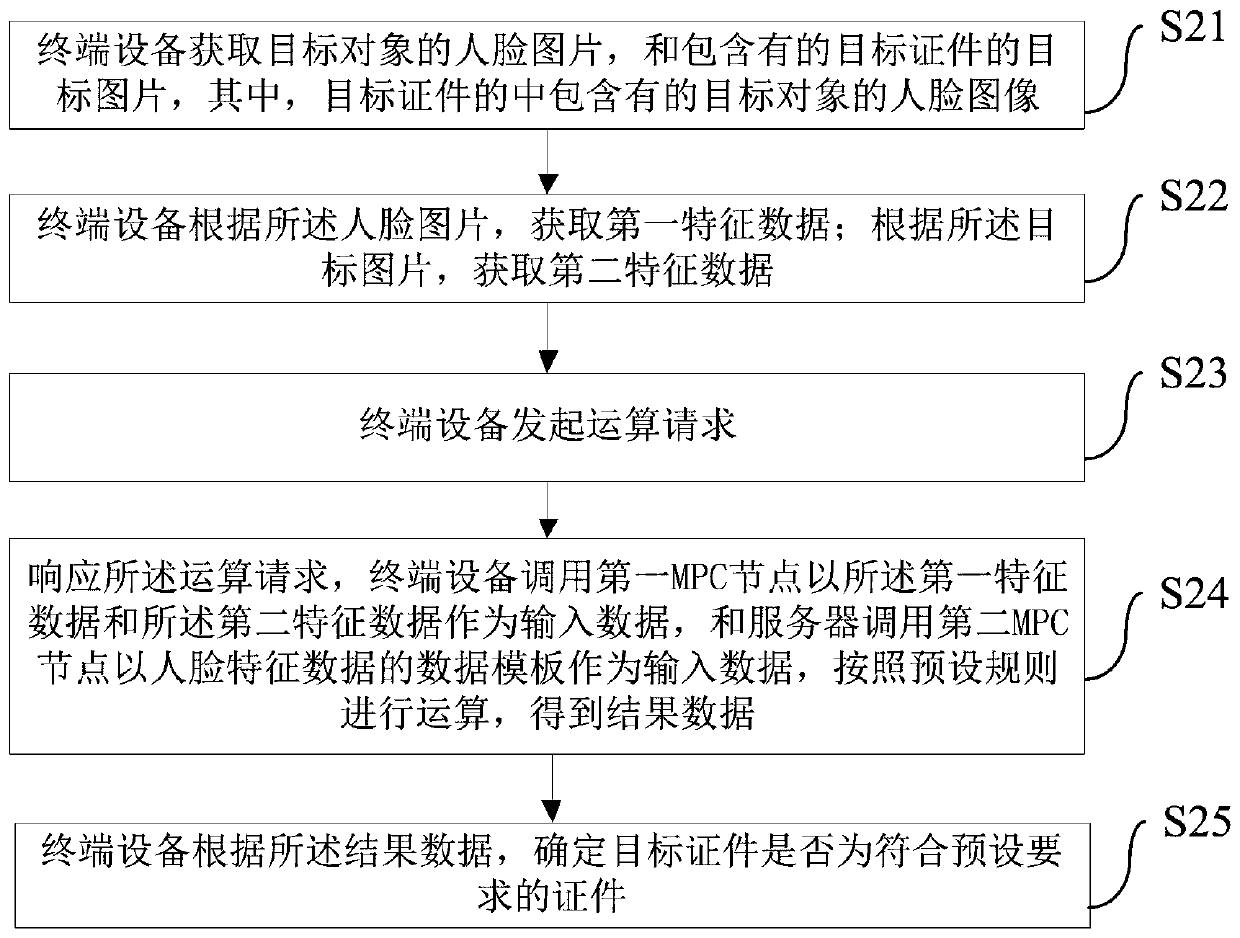
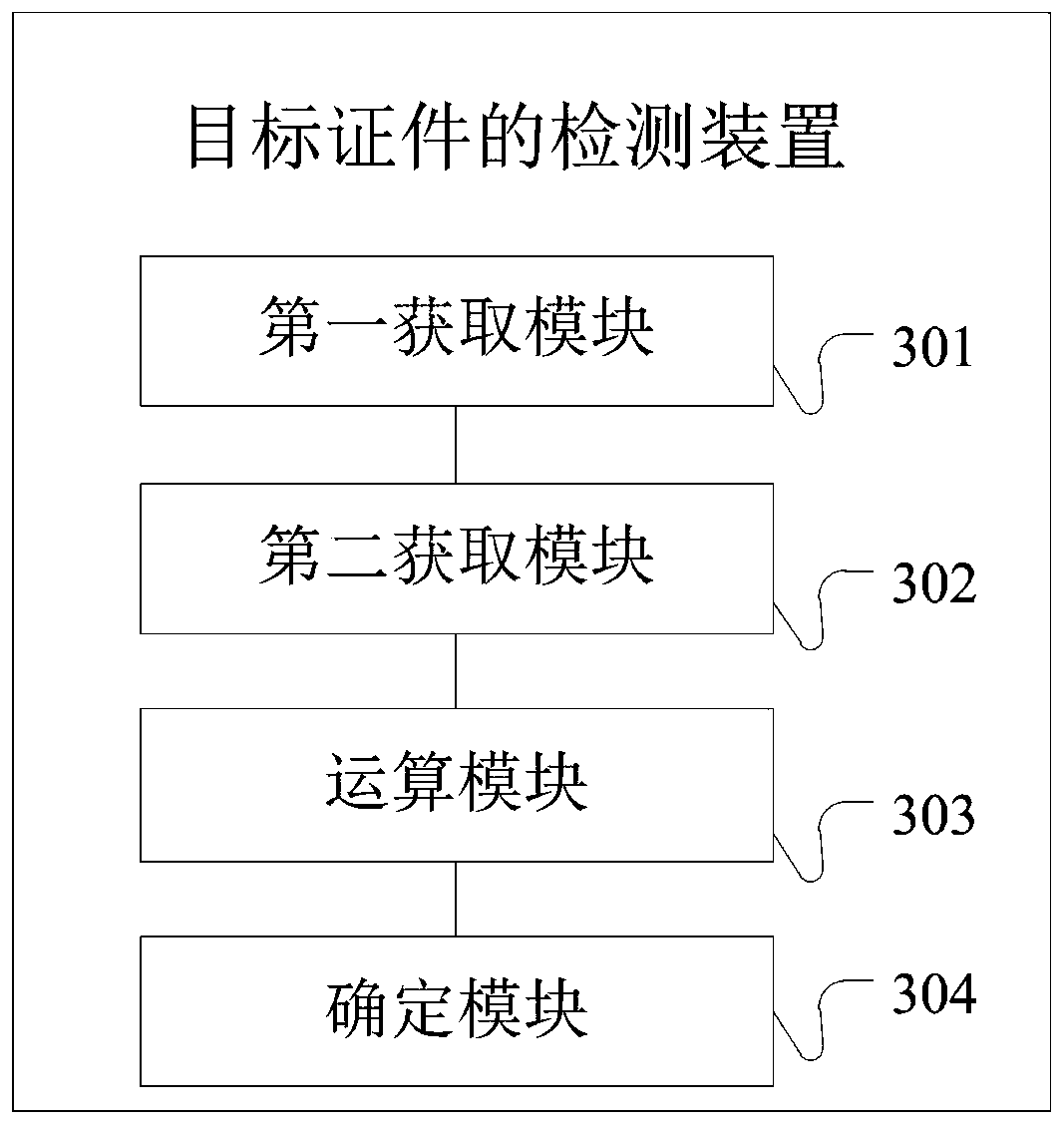
Target certificate detection method and device and terminal equipment
ActiveCN109902611AAvoid knowingEfficient detectionCharacter and pattern recognitionDigital data protectionTerminal equipmentFeature data
Embodiments of the invention provide a target certificate detection method and apparatus, and a terminal device. The method comprises the steps of obtaining a face image of a target object and a target image containing a target certificate; Respectively acquiring first feature data and second feature data according to the picture data; Calling the first MPC node to take the first feature data andthe second feature number as input data; a second MPC node preset in the server takes a data template of the face feature data as input data; carrying out operation according to preset rules, and detecting whether the target certificate meets a preset requirement or not; According to the scheme, the first MPC node of the terminal equipment and the second MPC node of the server are called to take respective owned data as input; The operation is performed according to the preset rule to determine the authenticity of the target certificate, so that the terminal equipment or the server is prevented from knowing the data owned by the opposite side, and the technical problem that the data privacy of the user cannot be protected in the detection process is solved.
Owner:JUZIX TECH SHENZHEN CO LTD +1
Mobile downloading data transmission method with privacy protecting function
ActiveCN104486294ASecure transmissionThe effect of reducing the efficiency of the transmissionError prevention/detection by using return channelEncryption apparatus with shift registers/memoriesContent distributionReliable transmission
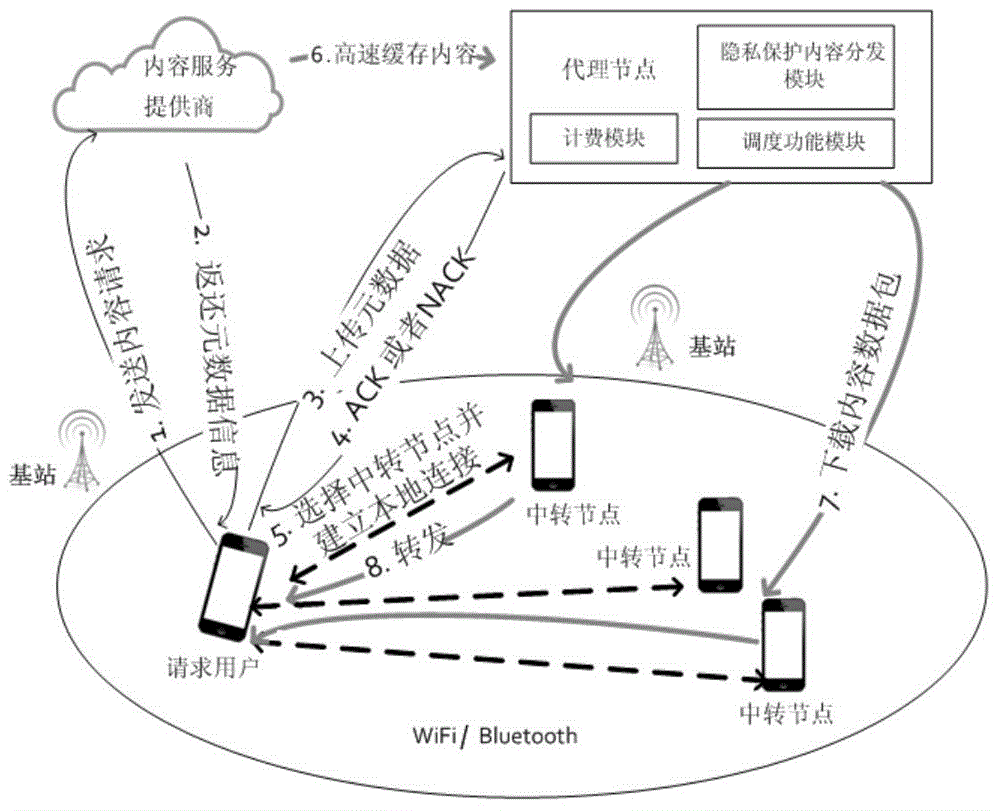
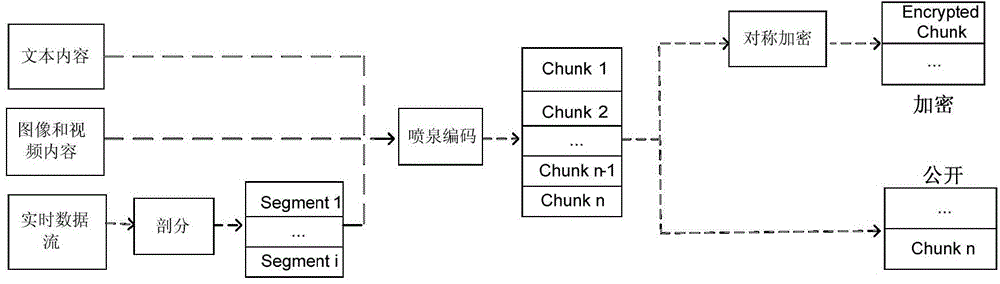
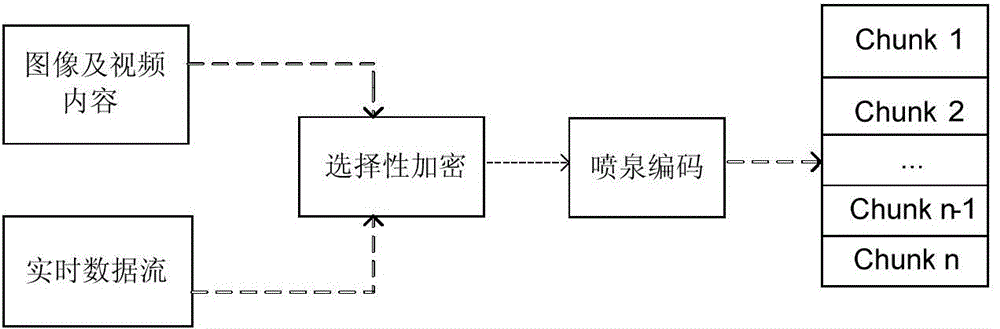
The invention discloses a mobile downloading data transmission method with a privacy protecting function. A credible agent node is introduced by the method, and after being encrypted by the agent node, data is distributed to a transfer node, so that the transfer node is prevented from learning the address of user request content, meanwhile; a data packet can be enabled to be distributed to the transfer node in a low-overhead way by using a privacy protection content distribution algorithm, so that privacy is not leaked to a third part in a wireless transmission process, and the reliability of data transmission on a wireless channel is not damaged. According to the method provided by the invention, private information, such as personal browsing record and request content, is enabled not to be leaked to the third part while the internet network data transmission rate can be effectively improved for a mobile user; meanwhile, in consideration of limitation of a mobile terminal resource and the dynamic nature of a wireless network, while a privacy protection mechanism is introduced, the influence on the data transmission efficiency is reduced as soon as possible, and safe and reliable transmission of the data is guaranteed in a low-overhead way.
Owner:WUXI TSINGHUA NAT LAB FOR INFORMATIONSCI & TECH INTERNET OF THINGS TECH CENT
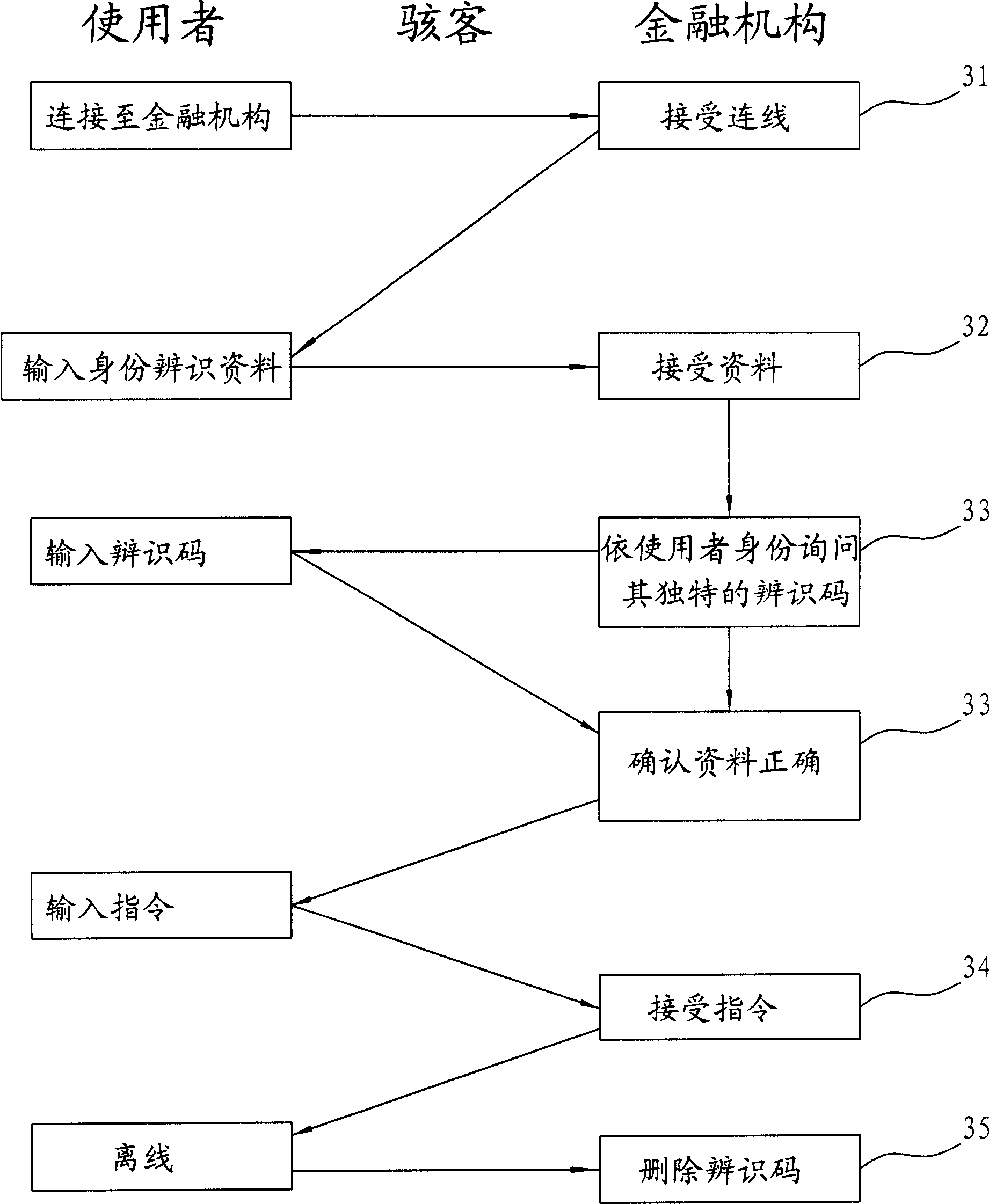
Attestation method and safe identification method for network identity
InactiveCN1738240AAvoid knowingEffectively confirm the authenticityUser identity/authority verificationSpecial data processing applicationsIdentity recognitionClient data
The invention relates to an identification method of network identification and a safe recognizing method. The network server replaces the identification information of user with a code, to store the identification information of user only in the identification data base which connects the server; the identification center for security identification only supports the reorganization that if said code can supply relative identification code. So the network manager can authorize the proxy to process the identification correctly without worrying the leakage of user's information. In addition, the invention stores a checked on-line website list in the identification code device to find counterfeit websites for reducing the probability of successfully cheating the identification information of user.
Owner:彭国展
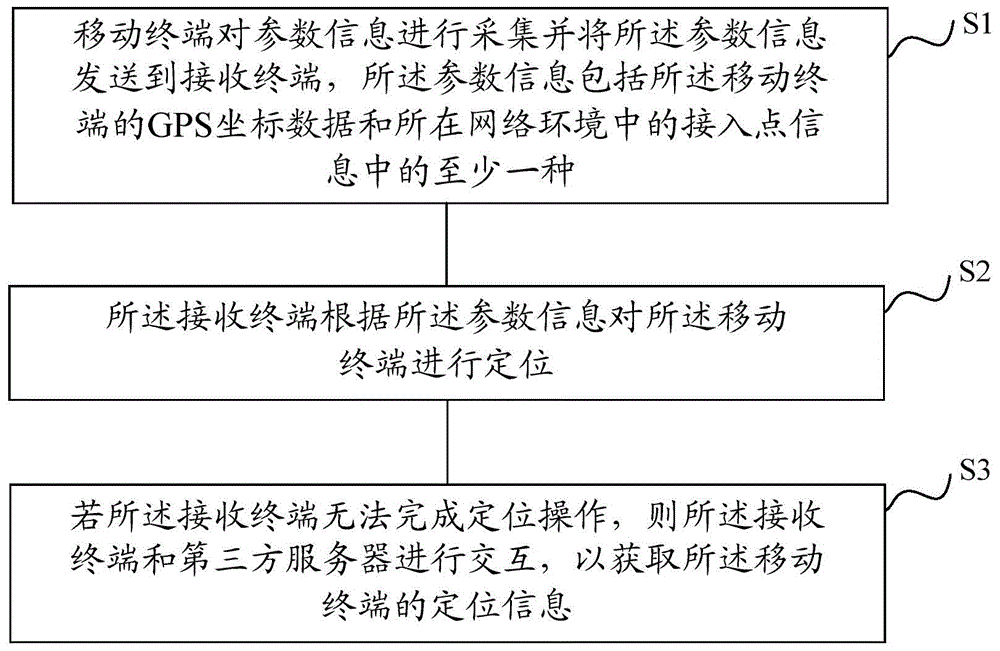
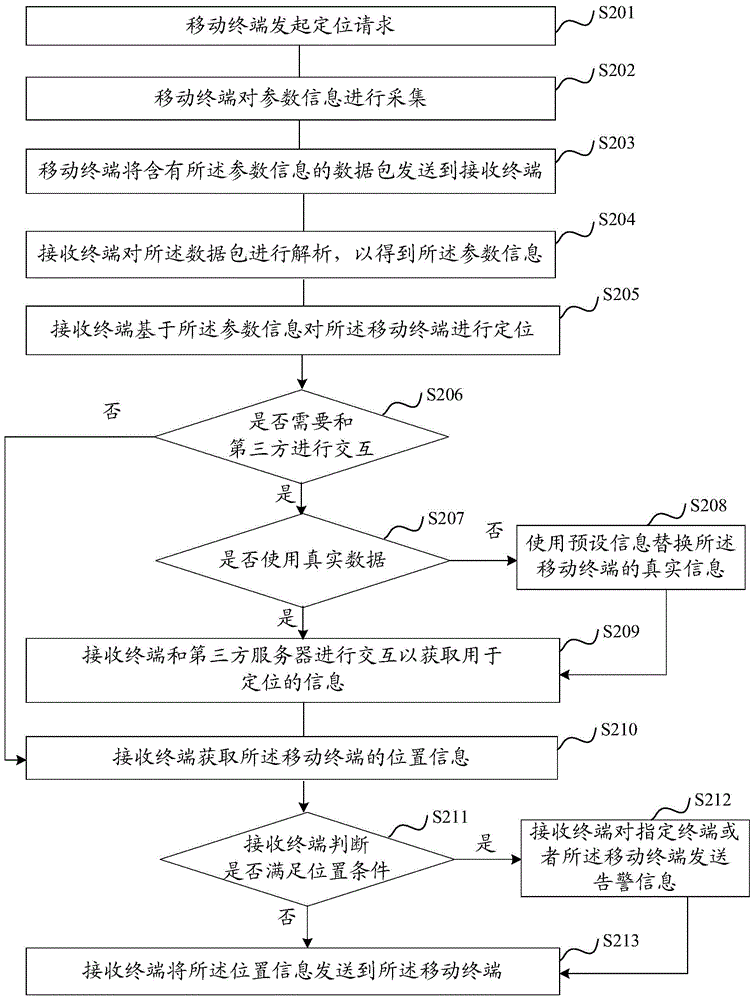
Positioning method of mobile terminal and positioning system
ActiveCN105142102AReduce configuration requirementsLow data processing capability requirementsLocation information based serviceHigh level techniquesPositioning systemComputer engineering
The invention provides a positioning method of a mobile terminal and a positioning system. The positioning method comprises the following steps that: (1) the mobile terminal collects parameter information and sends the parameter information to a receiving terminal, and the parameter information comprises the access point information of the mobile terminal in a network environment, (2) the receiving terminal positions the mobile terminal according to the parameter information, and (3) if the receiving terminal can not complete a positioning operation, the receiving terminal a third partly server carry out interaction to obtain the positioning information of the mobile terminal. According to the method, the hardware configuration requirement of the mobile terminal is low, the hardware needed by GPS and other positioning methods are not needed, the complex positioning data processing by the mobile terminal is not needed, the data processing ability requirement of the mobile terminal is low, in the process of positioning the mobile terminal, the hardware cost is effectively reduced, and the system power consumption is reduced.
Owner:SPREADTRUM COMM (SHANGHAI) CO LTD
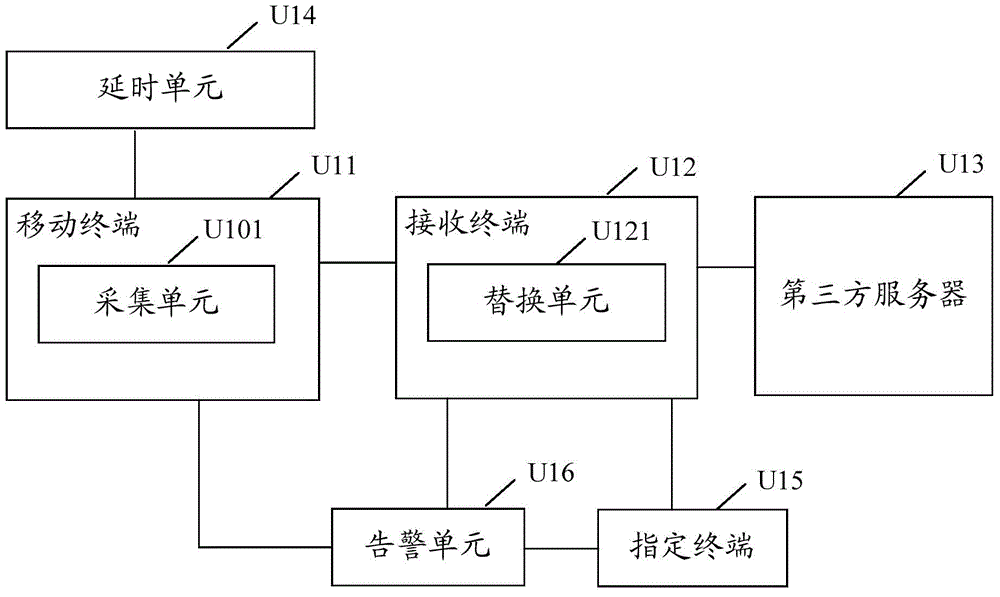
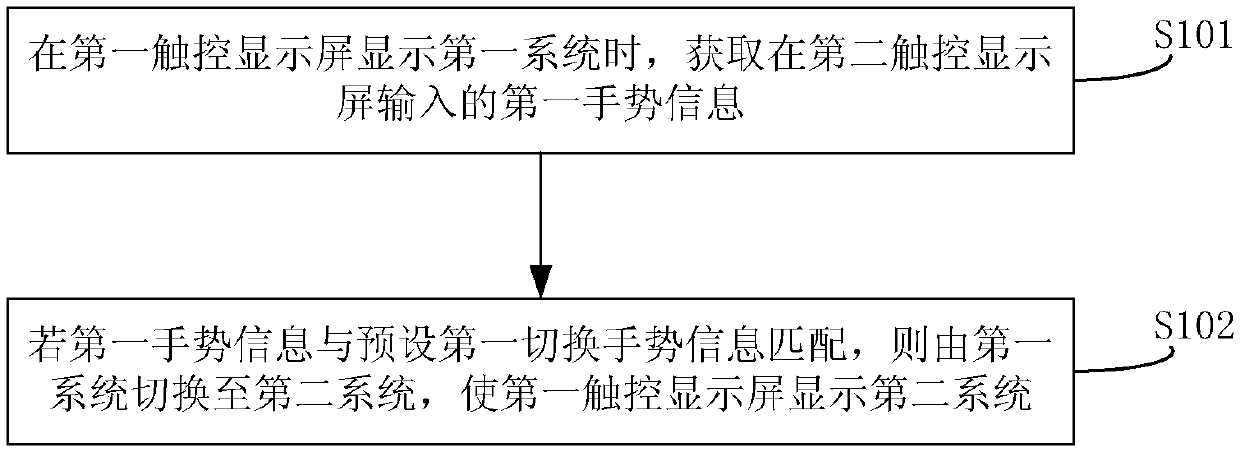
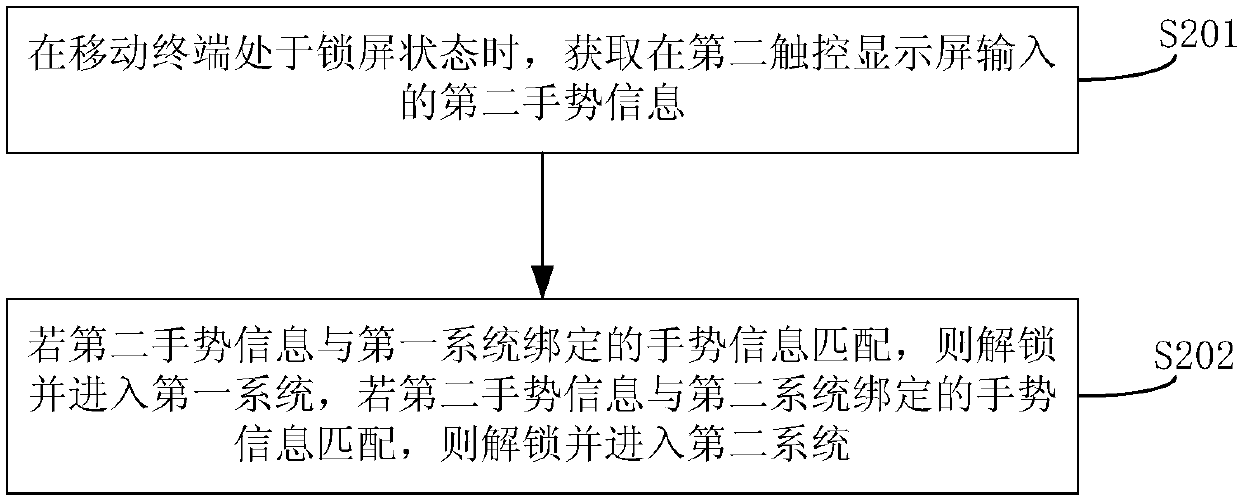
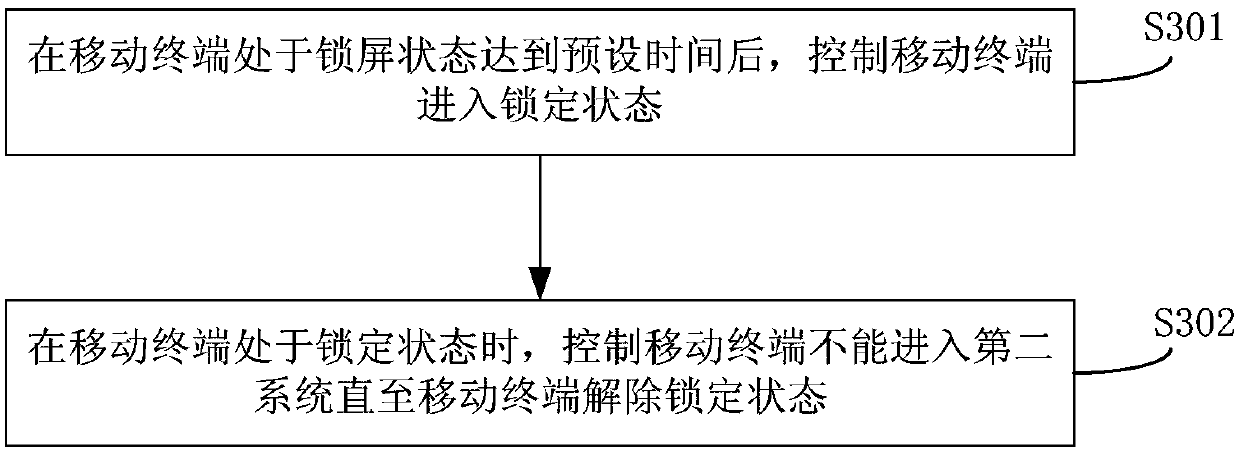
System switching method, mobile terminal and device based on dual screens
ActiveCN108037884AAvoid knowingImprove experienceDigital output to display deviceComputer engineering
The application discloses a system switching method, a mobile terminal and a device based on dual screens. The method comprises the steps that when a first touch control display screen displays a first system, first gesture information input on a second touch control display screen is obtained; if the first gesture information matches preset first switching gesture information, then the first system is switched to a second system, so that the first touch control display screen displays the second system. Through the above method, the system switching method, the mobile terminal and the devicebased on the dual screen can avoid the gesture information being known to others as much as possible.
Owner:BEIJING ZHUMU LANGMA MOBILE COMM CO LTD
Data query method, device and equipment and computer readable storage medium
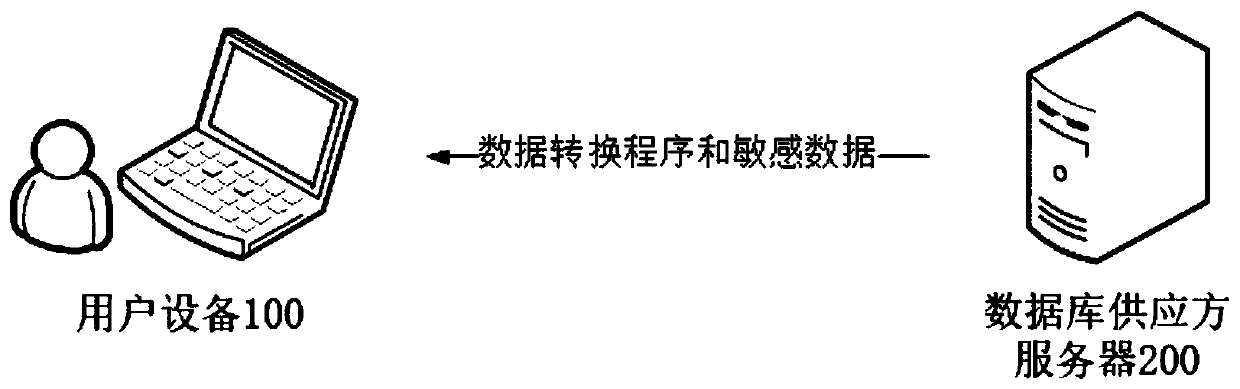
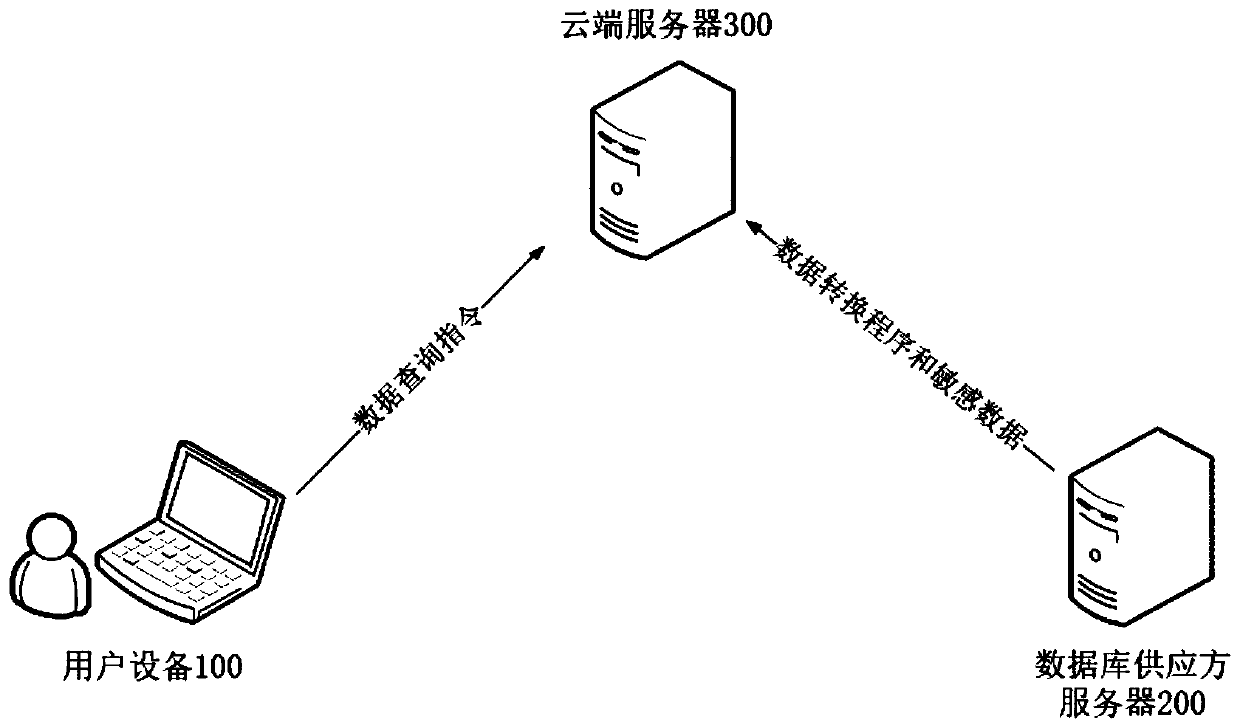
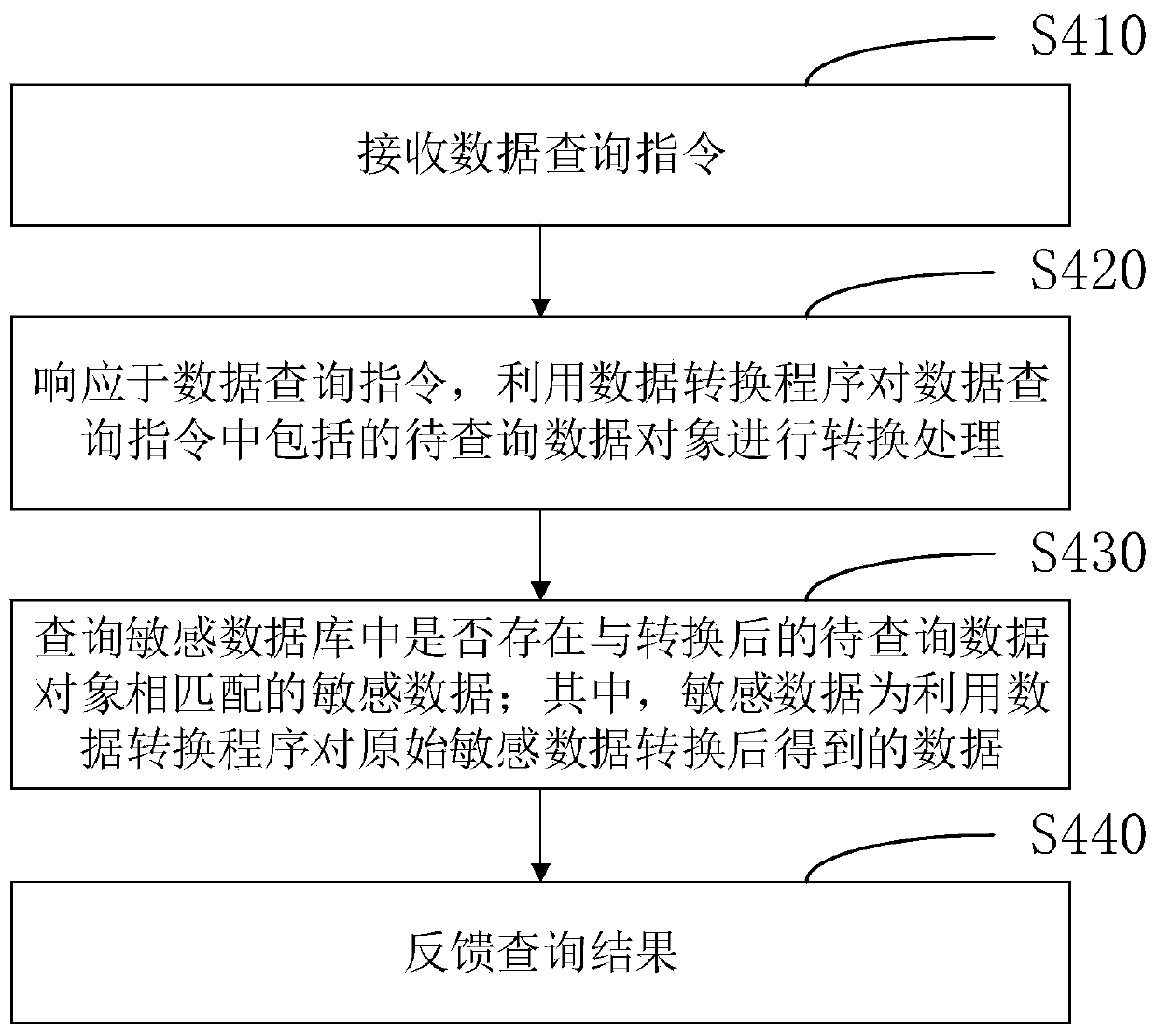
PendingCN110210251AImprove privacy and securityAvoid knowingDigital data information retrievalDigital data protectionData queryData mining
One or more embodiments of the present specification provide a data query method, apparatus and device, and a computer readable storage medium. In one embodiment, the data query method comprises the following steps: receiving a data query instruction; in response to the data query instruction, performing conversion processing on a to-be-queried data object included in the data query instruction byusing a data conversion program; inquiring whether sensitive data matched with the converted to-be-inquired data object exists in a sensitive database or not; wherein the sensitive data is data obtained by converting the original sensitive data by using a data conversion program; feeding back query results.
Owner:ADVANCED NEW TECH CO LTD
Guard personnel monitoring system and method based on Internet of Things
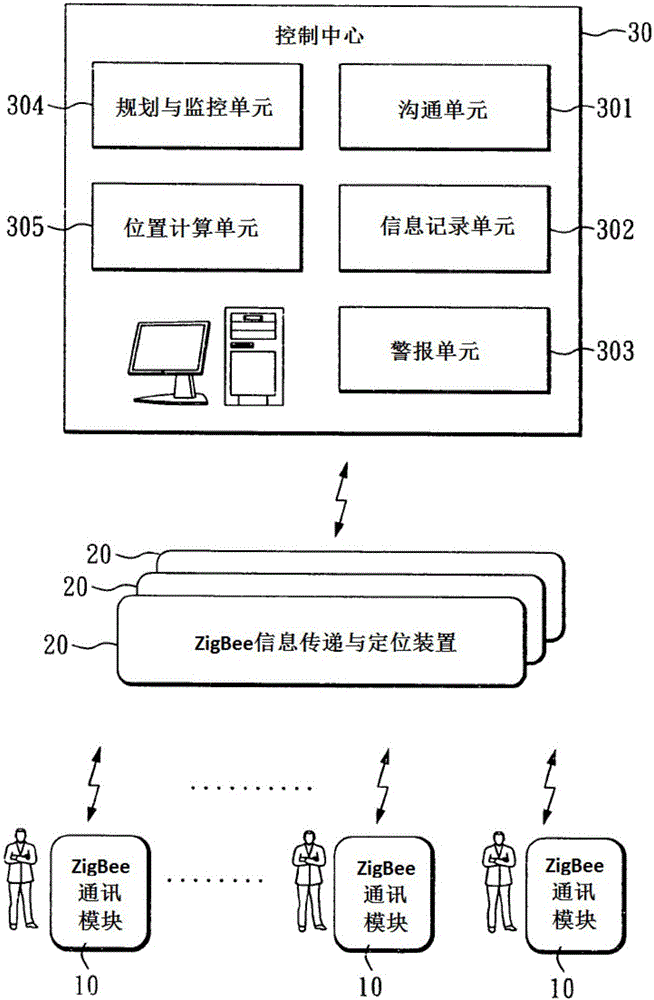
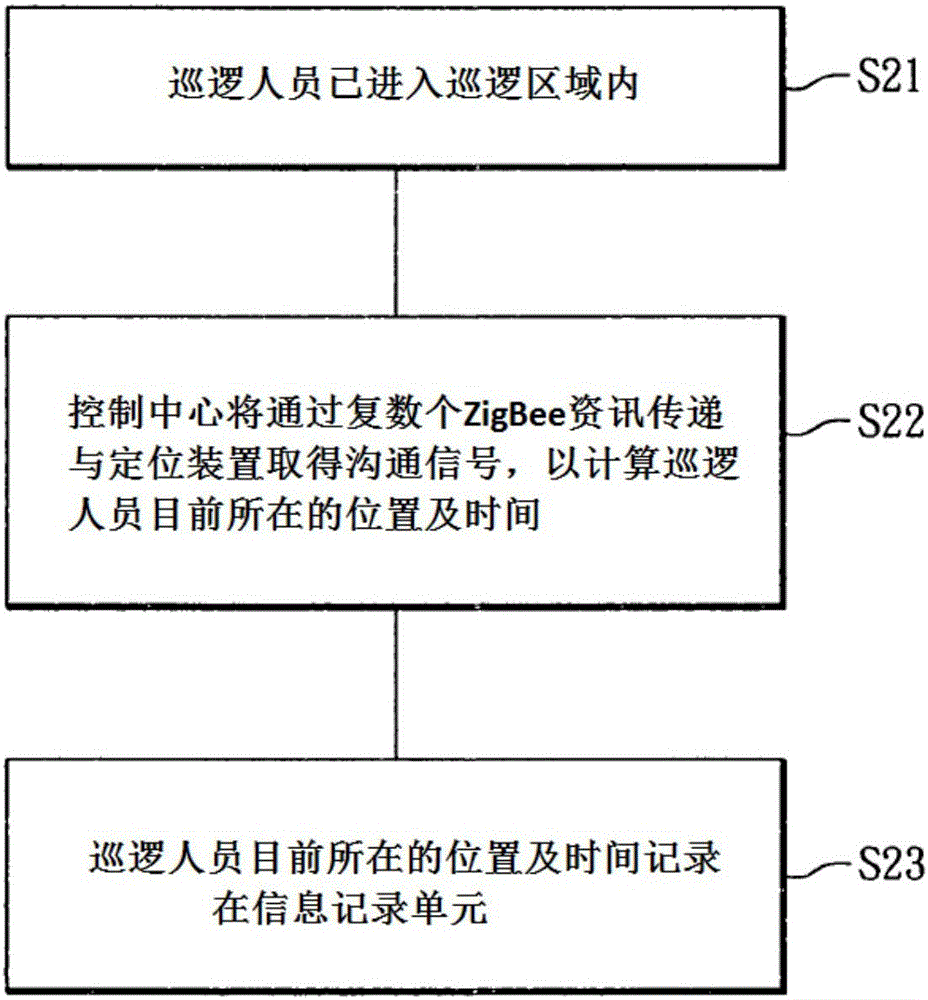
InactiveCN105788020AAvoid knowingEliminate troubleChecking time patrolsThe InternetMonitoring system
The invention relates to a guard personnel monitoring system and method based on the Internet of Things.The system comprises a ZigBee communication module, multiple ZigBee information transmitting and positioning devices arranged at different positions within the patrol range respectively, and a control center used for monitoring the moving condition of the ZigBee communication module.Position information of the ZigBee communication module can be calculated.According to the guard personnel monitoring system and method, the positions of patrol personnel in the patrol area can be mastered, and a response to an emergency situation can be made.Besides, the patrol personnel do not need to swipe cards or sign in on specific sites, and various troubles caused by actual wiring can be saved.
Owner:吴干
A method and system for evaluating user data value
InactiveCN109447474AAvoid knowingThe assessment results are accurateProduct appraisalResourcesData setAssessment data
The application provides a method and system for evaluating user data value. The system includes a cost determination module for determining the acquisition cost of the data set to be evaluated; an adjustment weight determination module which is configured to determine the attribute tag corresponding to each piece of user data in the data set to be evaluated, and calculate the adjustment weight ofeach attribute tag based on the usage weight of each piece of user data corresponding to the attribute tag when each piece of user data covered by each attribute tag is used; an adjustment factor determination module which is configured to calculate an adjustment factor of each attribute tag according to the total number of times the user data covered by each attribute tag is used and the adjustment weights corresponding to each attribute tag; and an evaluation module which is used for determining the value of the data set to be evaluated according to the adjustment factors of each attributelabel and the acquisition cost of the data set to be evaluated. Embodiments of the present application can prevent the privacy of a user from being known by others, and can obtain more accurate evaluation results.
Owner:GUOXIN YOUE DATA CO LTD
Method for storing confidential information in cloud computing environment
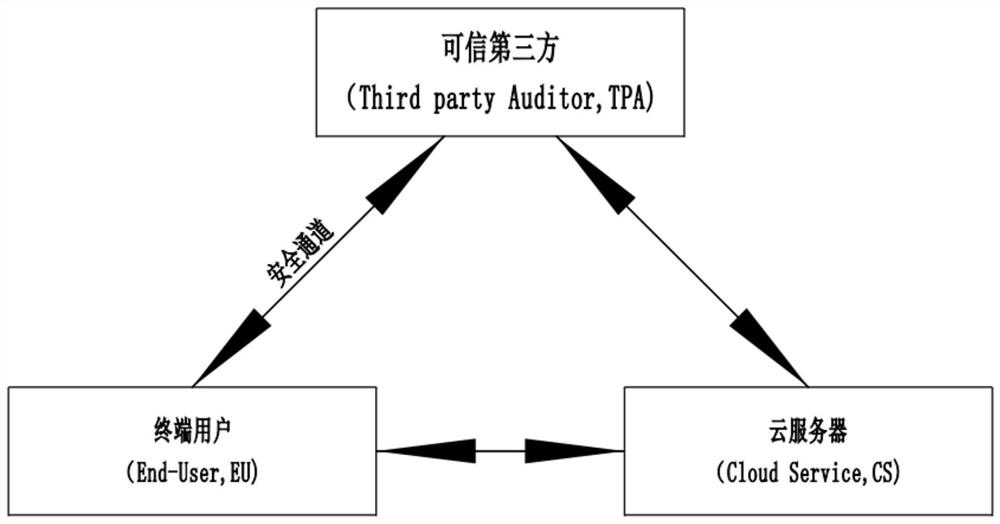
PendingCN112800462AGuaranteed correctnessIntegrity guaranteedDigital data protectionCommon keyData store
The invention relates to the technical field of computer storage methods, in particular to a method for storing confidential information in a cloud computing environment, which comprises the following processes: (1) determinin participants; (2) adopting an encryption algorithm; (3) building an architecture model of the SCBRHD; (4) carrying out SCBRHD scheme operation; and (5) carrying out an SCBRHD algorithm process. The method has the advantages that the RSA algorithm and the DES algorithm are used for executing encryption, decryption and data authentication, the safety of the data is ensured by calculating the Hash abstract and comparing, in the SCBRHD, only the EU can decrypt the data received from the trusted third party TPA, because the data is encrypted by the public key d2 of the EU, only the corresponding private key pk2 can performdecryption. The private key is only known by the EU, so that the correctness of the data is ensured, and when the EU wants to read the data stored on the CS, the TPA requires to execute data integrity verification on the data from the CS, so that the integrity of the data is ensured.
Owner:广东浩云长盛网络股份有限公司
Video-audio access control intercom system and method
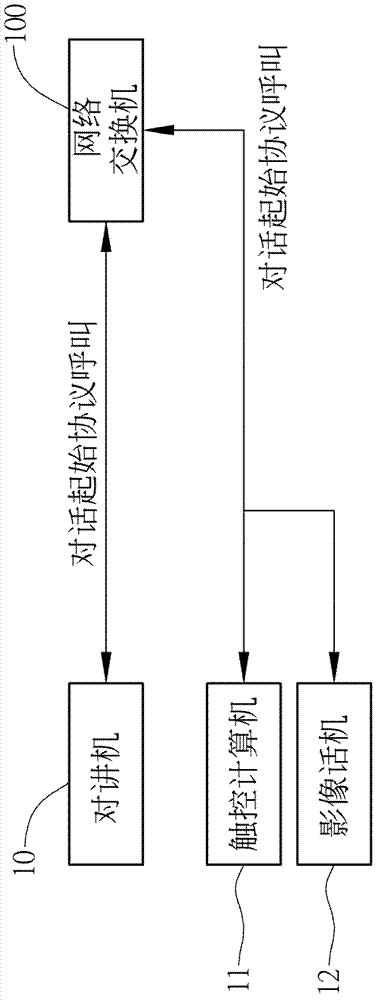
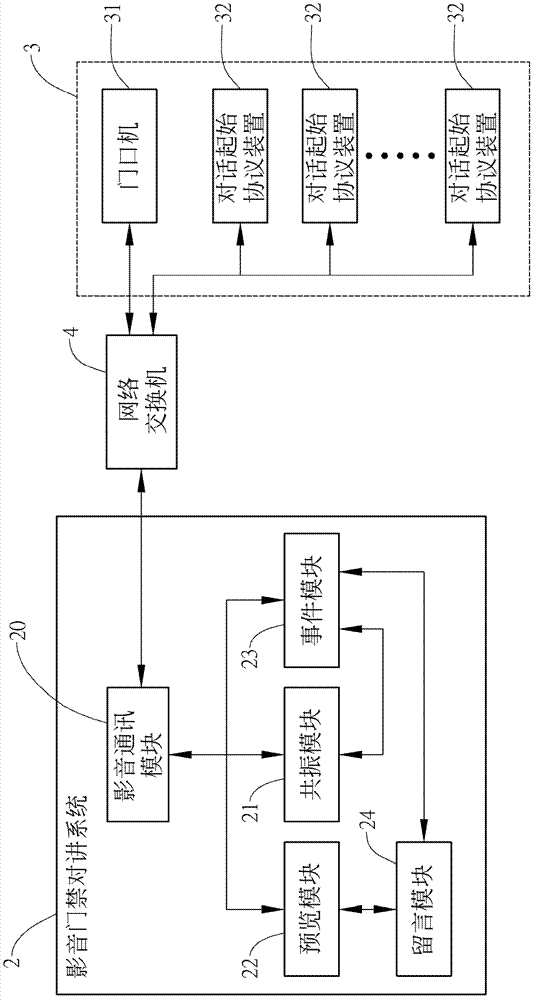
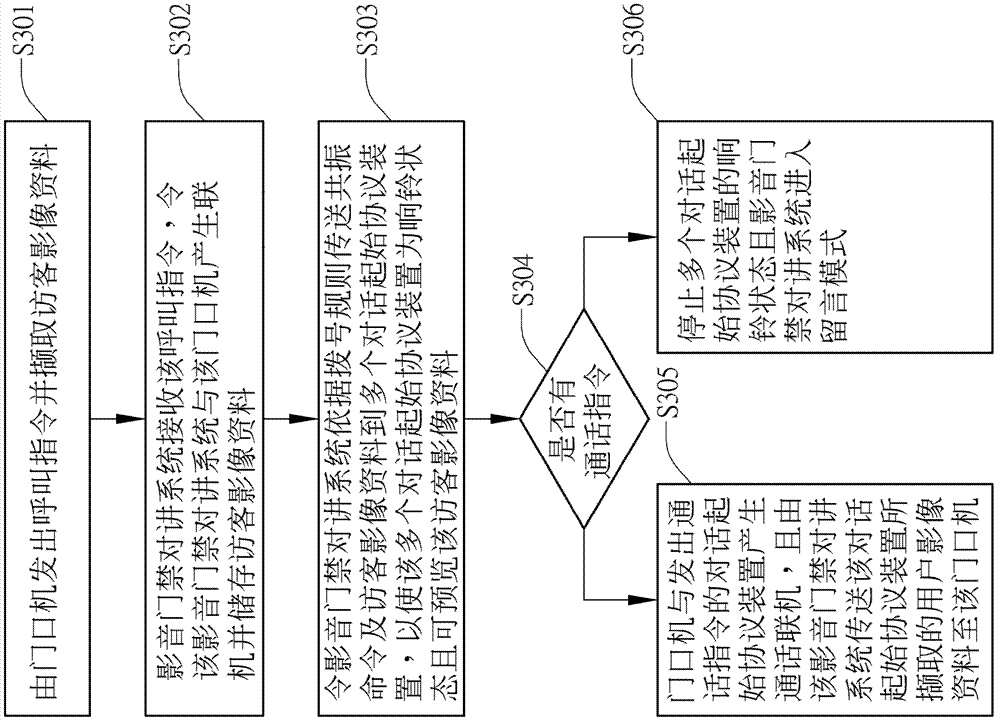
InactiveCN103166946AAvoid knowingImprove privacyClosed circuit television systemsTransmissionResonanceMassage
The invention provides a video-audio access control intercom system and method, wherein a video-audio communication module receives an online request sent by a outdoor set to establish a linkage at two terminals, and transmits images acquired by the outdoor set to a preview module to store, and a video-audio communication module notifies a resonance module to send a resonance command to a dialogue starting agreement device to bell, and transmits the images to all dialogue starting agreement devices for preview when a user receives a call. after an module receives communication instructions sent by the dialogue starting agreement devices used by the user, the resonance module is notified no longer to bell responding to other devices, and generates an image communication between the dialogue starting agreement devices used by the user and the outdoor set; otherwise, a message leaving module is notified to enter a massage leaving mode. The access control intercom system can integrate image preview, communication device resonance and guest message leaving feedback, in order to ensure user privacy and have convenience.
Owner:CHUNGHWA TELECOM CO LTD
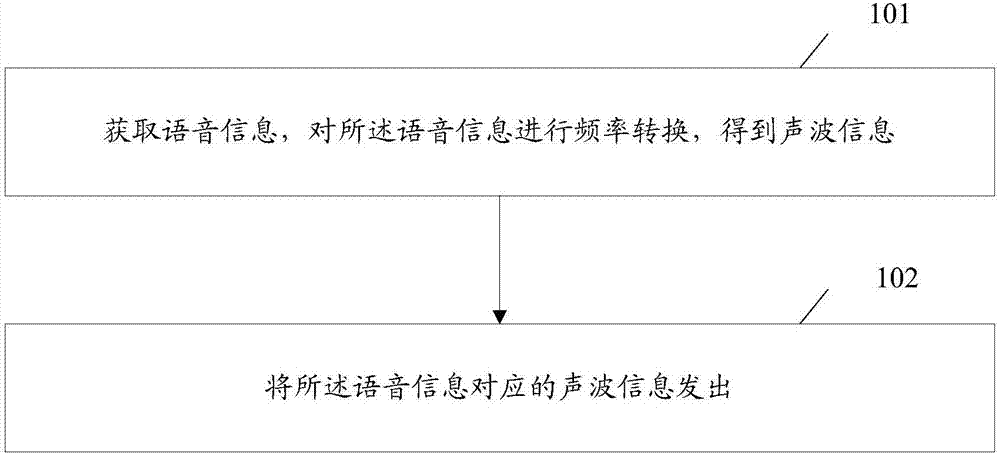
Information processing method and electronic equipment
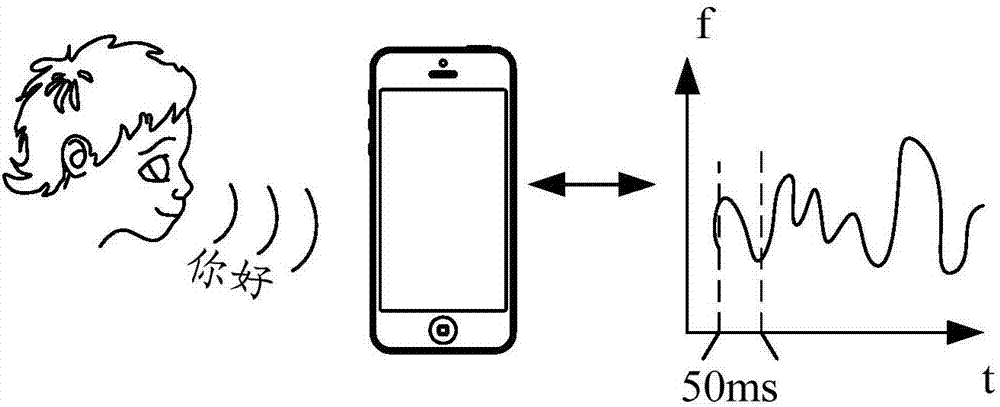
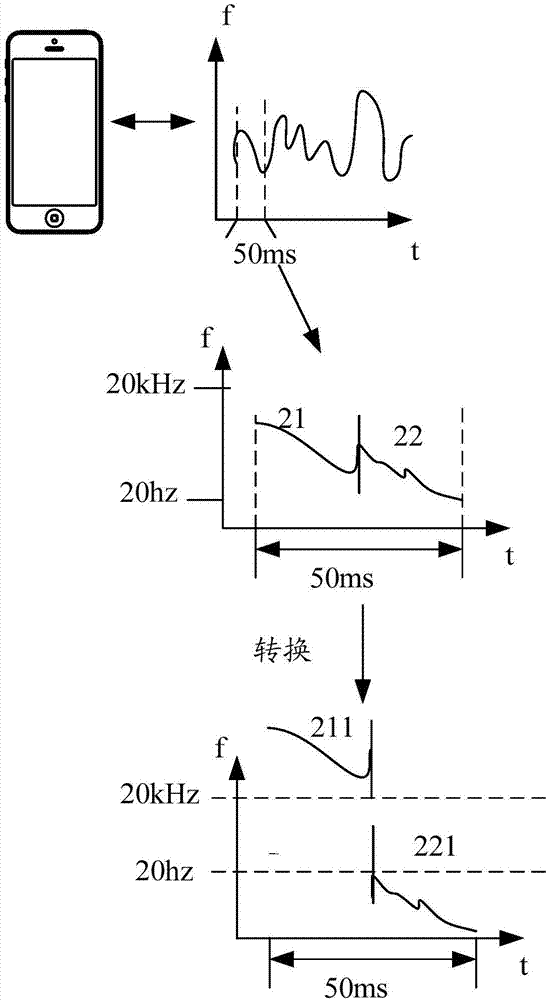
ActiveCN107153796AGuaranteed privacyImprove interaction privacyInternal/peripheral component protectionSound input/outputInformation processingFrequency conversion
The invention discloses an information processing method and electronic equipment. The method includes the steps that voice information is acquired, and frequency conversion is conducted on the voice information to obtain acoustic wave information; the frequency range where the acoustic wave information is located cannot be directly perceived by a human ear; the acoustic wave information corresponding to the voice information is transmitted, so that a targeted object can produce audio frequency resonance based on the acoustic wave information, and the voice information in the frequency range which can be directly perceived by the human ear is acquired.
Owner:LENOVO (BEIJING) LTD
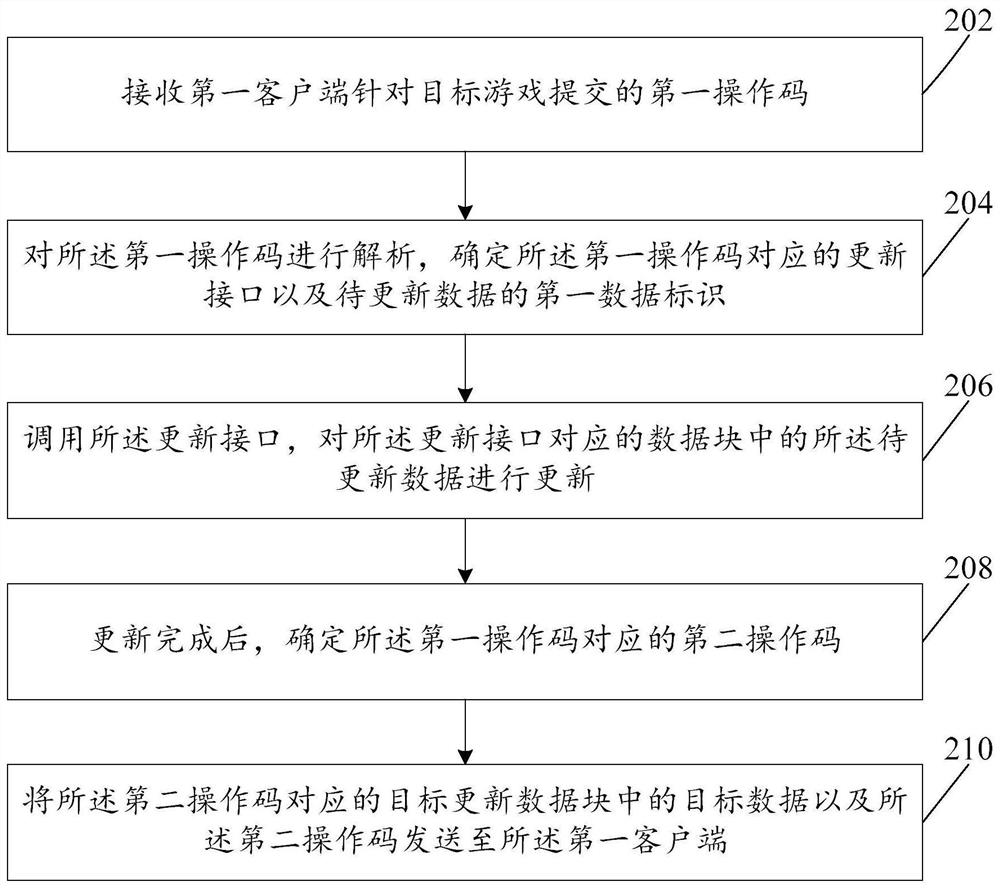
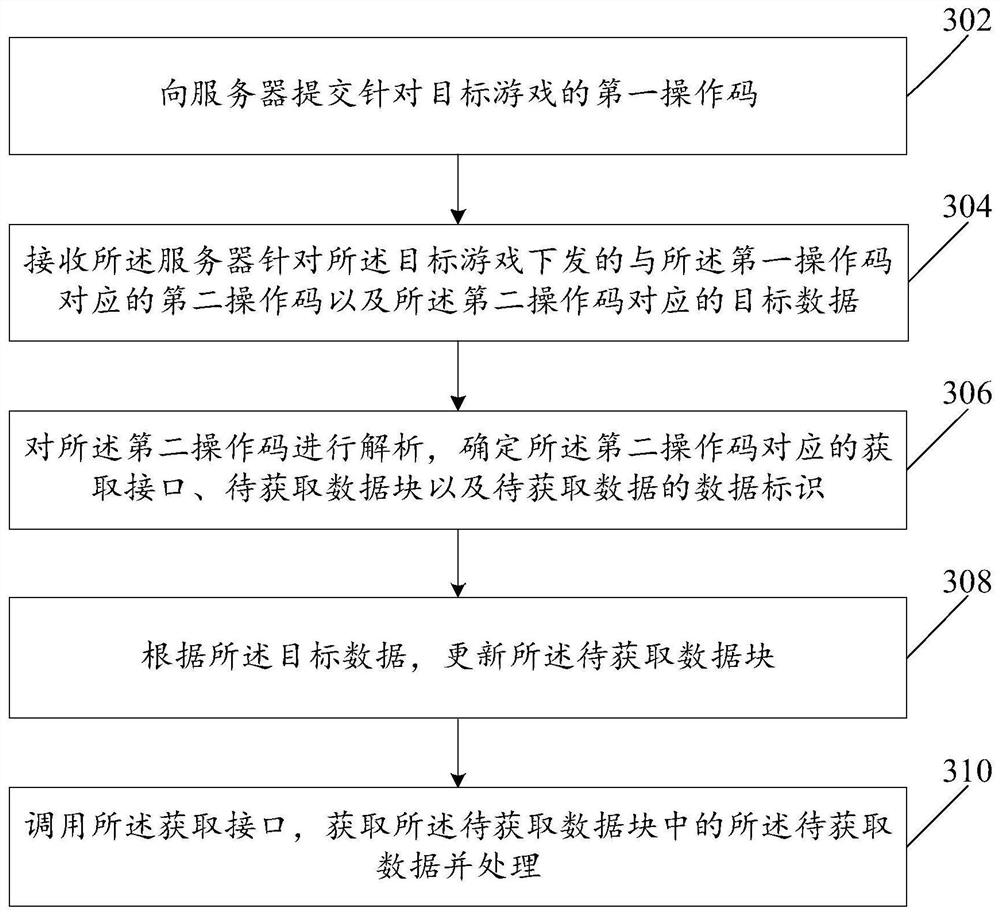
Data processing method and device
The invention provides a data processing method and device. The data processing method comprises the steps: receiving a first operation code submitted by a first client for a target game; analyzing the first operation code, and determining an updating interface corresponding to the first operation code and a first data identifier of to-be-updated data; calling the updating interface, and updatingthe to-be-updated data in the data block corresponding to the updating interface, the input of the updating interface being the first data identifier, and the interface type of the updating interfacebeing in one-to-one correspondence with the data type of the data block; after updating is completed, determining a second operation code corresponding to the first operation code, the second operation code being an operation code for the first client in the target game; and sending target data in a target update data block corresponding to the second operation code and the second operation code to the first client, the target data including updated data corresponding to the to-be-updated data.
Owner:ZHUHAI KINGSOFT ONLINE GAME TECH CO LTD
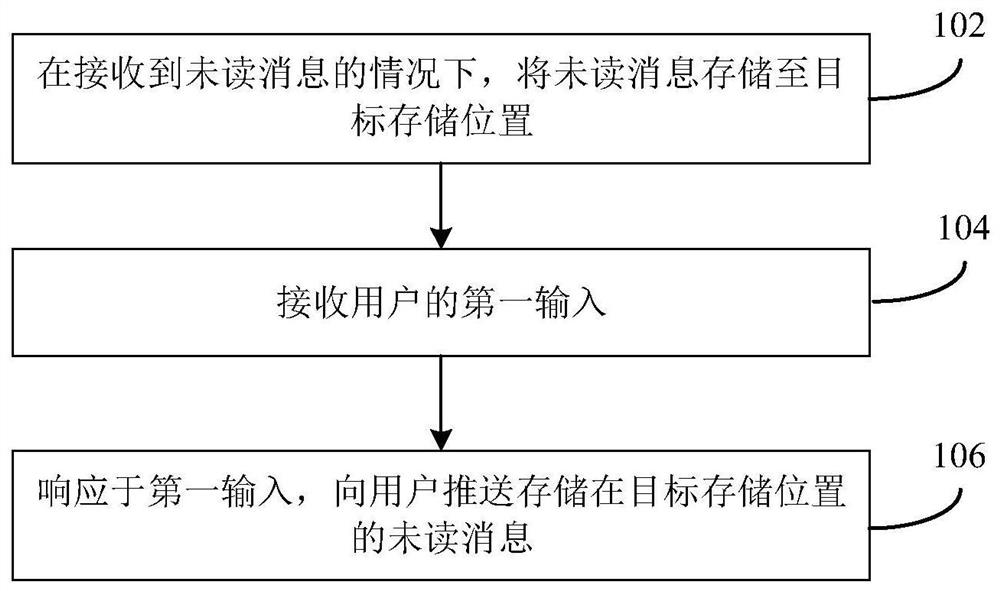
Message pushing method and device, electronic equipment and storage medium
ActiveCN111669460AAvoid knowingImprove user experienceSubstation equipmentInput/output processes for data processingComputer networkEngineering
The invention discloses a message pushing method and device, electronic equipment and a storage medium, and belongs to the field of electronic equipment. The method comprises the steps of: storing anunread message to a target storage position under the condition that the unread message is received; receiving a first input of a user; and in response to the first input, pushing the unread message stored in the target storage position to the user. By utilizing the embodiment of the invention, the unread message cannot be pushed once received, and the situation in which a non-user himself / herselfknows that the message is received when the message is pushed can be avoided, so that the privacy of the user is prevented from being leaked, and the use experience of the user is improved.
Owner:VIVO MOBILE COMM CO LTD
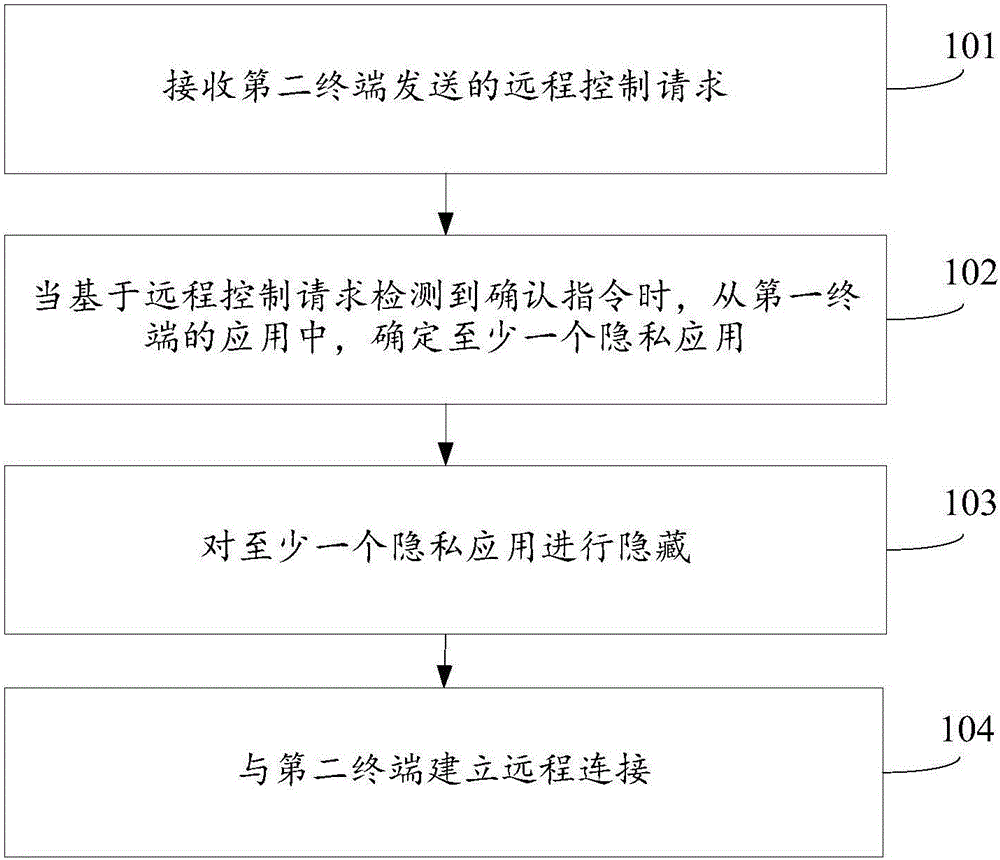
Remote control method and device
ActiveCN105956489AAvoid Privacy LeakageAvoid knowingDigital data protectionThe InternetComputer terminal
The invention discloses a remote control method and device, and belongs to the technical field of the Internet. The method is applied to a first terminal. The method comprises the steps of receiving a remote control request sent by a second terminal; determining at least one private application from the applications in the first terminal when an acknowledgement instruction is detected based on the remote control request; hiding the at least one private application; and establishing remote connection with the second terminal. According to the method and the device, the second user is avoided from knowing the application information of the private application in the first terminal, the private application in the first terminal is avoided from being started by the second user due to misoperation, and the privacy of the first terminal can be prevented from being leaked.
Owner:BEIJING XIAOMI MOBILE SOFTWARE CO LTD
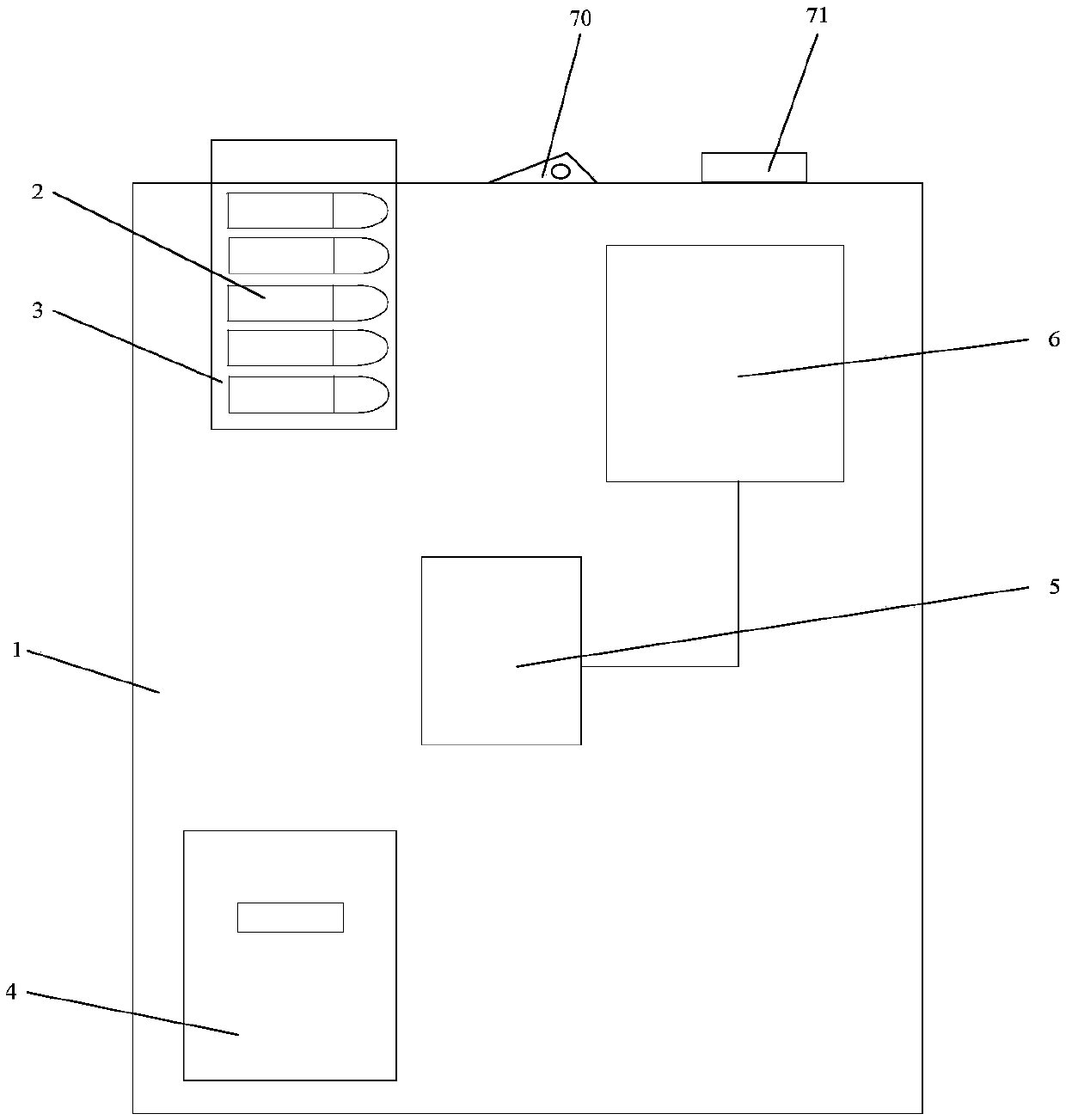
Hydraulic ring geological crack measuring device
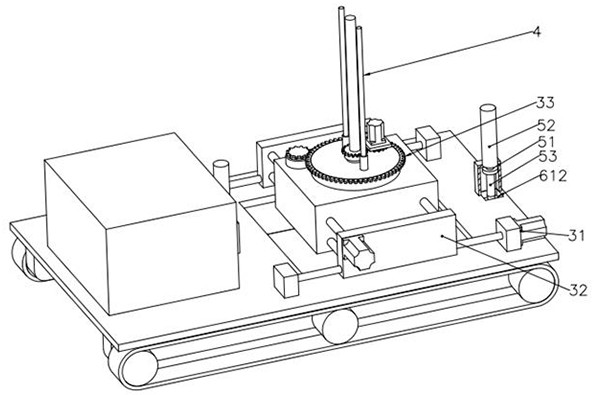
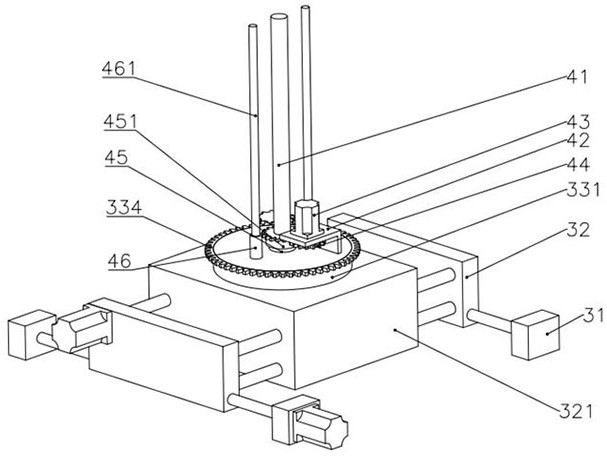
ActiveCN114812344AHigh measurement accuracyEasy to operateTelevision system detailsMechanical clearance measurementsMobile vehicleIn vehicle
The invention belongs to the technical field of hydraulic ring geological detection, and relates to a hydraulic ring geological crack measuring device, which comprises a control box and a remote controller, and further comprises a mobile vehicle body, a width measuring mechanism, a position adjusting mechanism and a lifting mechanism, the width measuring mechanism comprises a fixed support, a bidirectional screw rod, a balance slide rod, a first motor and two synchronous pressing blocks, the fixed support is provided with scales, the front part of each synchronous pressing block is provided with a distance compensation assembly, the compensation assembly is provided with a measuring plate, the side wall of each synchronous pressing block is provided with a steering assembly, and the steering assembly is provided with a camera. The synchronous abutting block is provided with a first threaded hole and a sliding hole. According to the invention, the measurement accuracy of the crack width is improved, the operation is very convenient, and the safety is high.
Owner:烟台鲁东勘察测绘有限公司
Privacy protection method and system for blockchain real-name communication
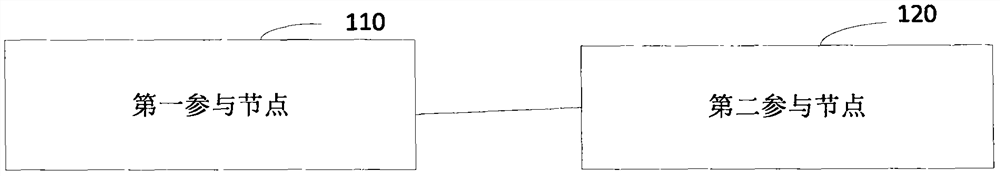
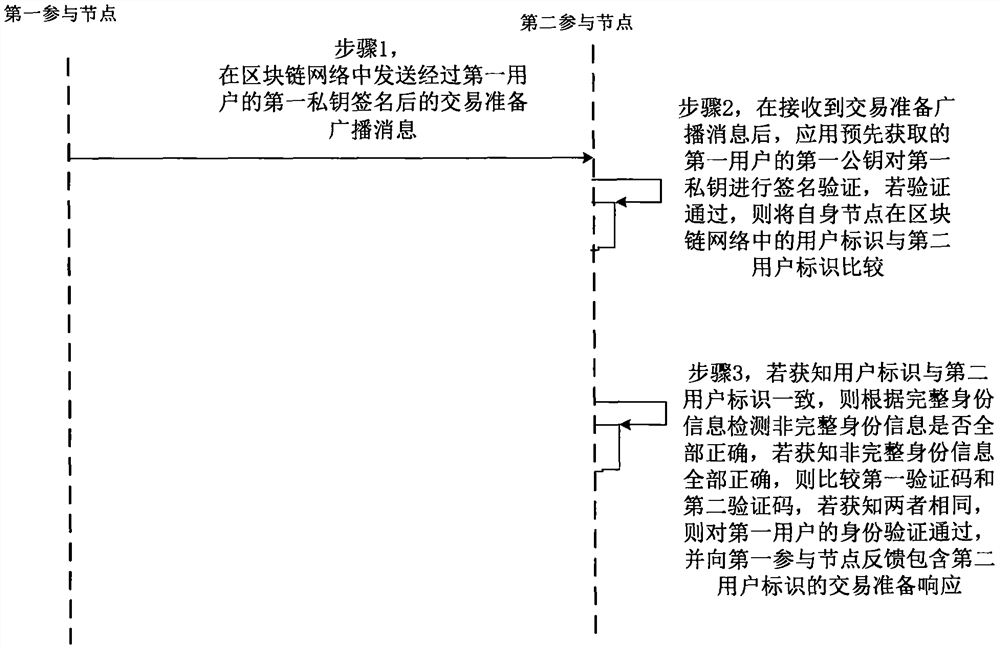
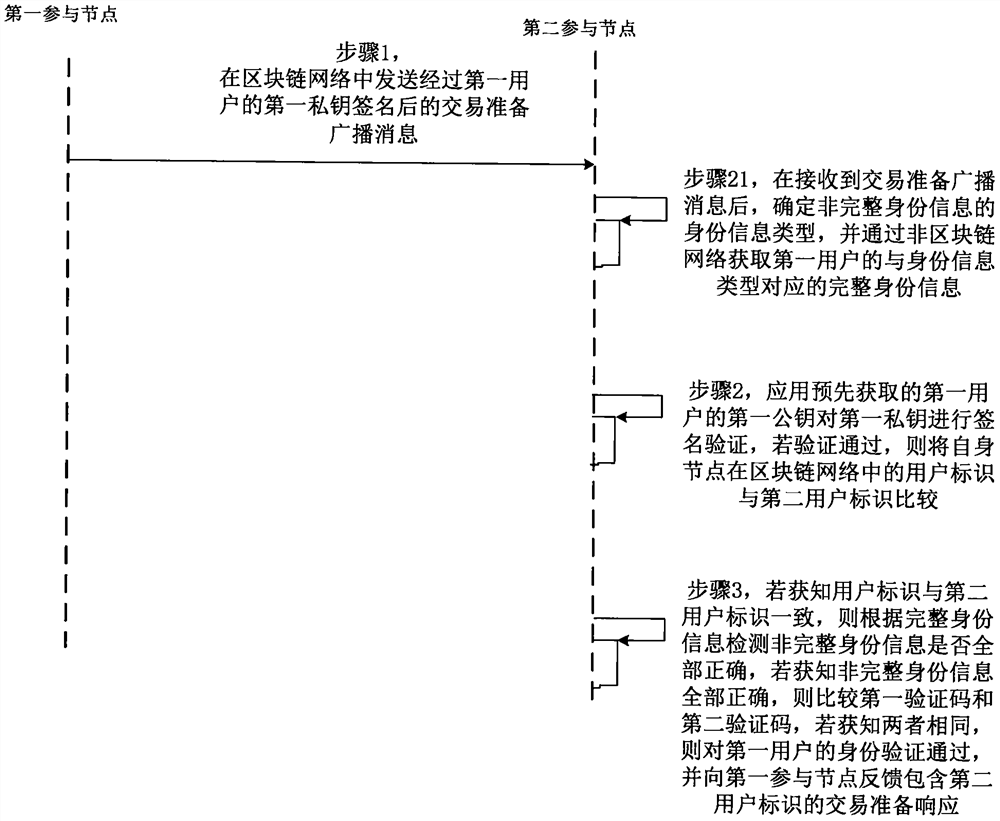
ActiveCN108960832BProtect private informationAvoid knowingPayment protocolsComputer networkPrivacy protection
The present invention discloses a privacy protection method and system for blockchain real-name communication, wherein the method includes: a first participating node sends a transaction preparation broadcast message signed by the first private key of the first user in the blockchain network ; After the second participating node receives the transaction preparation broadcast message, it uses the first public key of the first user to verify the signature of the first private key. Comparing the two user IDs, if it is known that the two are the same, then calculate the complete identity information of the first user obtained through the non-blockchain network to obtain the second verification code of the first user, and if it is known that the two are the same, then determine that it is not The complete identity information is all correct, and a transaction preparation response containing the second user ID is fed back to the first participating node. Thus, the privacy information of blockchain nodes is protected during real-name communication.
Owner:全链通有限公司
Website account login, verification, verification information processing method, device and system
Owner:BEIJING GZT NETWORK TECH
Elevator wireless rescue system based on Internet of Things technology and using method thereof
The invention discloses an elevator wireless rescue system based on the Internet of Things technology and a using method thereof, and particularly relates to the technical field of elevator wireless rescue, the elevator wireless rescue system comprises an LORA technology wireless talkback host, a first GSM antenna is installed at the top end of the GSM wireless talkback host, and the output end of the first GSM antenna is connected with a multidirectional calling mechanism; the multidirectional calling mechanism comprises a first telephone set arranged at the output end of the first GSM antenna. The GSM wireless talkback host is started by the multidirectional calling mechanism, so that the first GSM antenna transmits a signal to the position of the first telephone set, the second GSM antenna transmits a signal to the second telephone set for calling, the mobile phone number of a maintenance worker is automatically dialed and called through the automatic dialer, trapped persons are pacified by monitoring a duty room, and the service life of the maintenance worker is prolonged. And the rescue duty room receives the rescue information at the first time and performs rescue operation, so that the rescue efficiency is effectively improved, the emotion excitation of the trapped person caused by unattended duty is avoided, the calling effect is better, and the rescue operation is efficiently realized.
Owner:无锡小爱电气有限公司
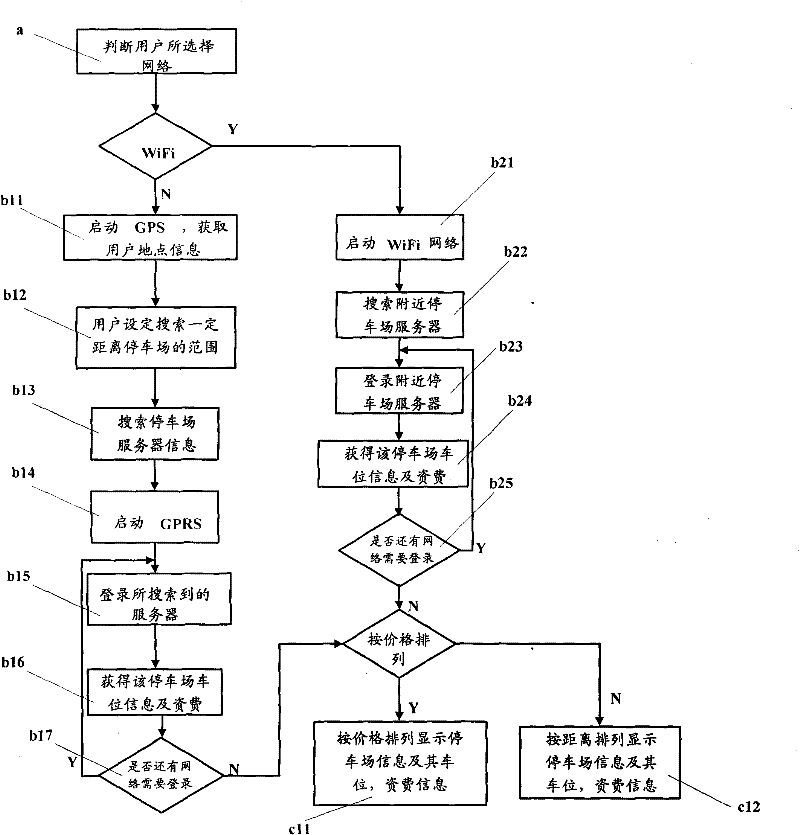
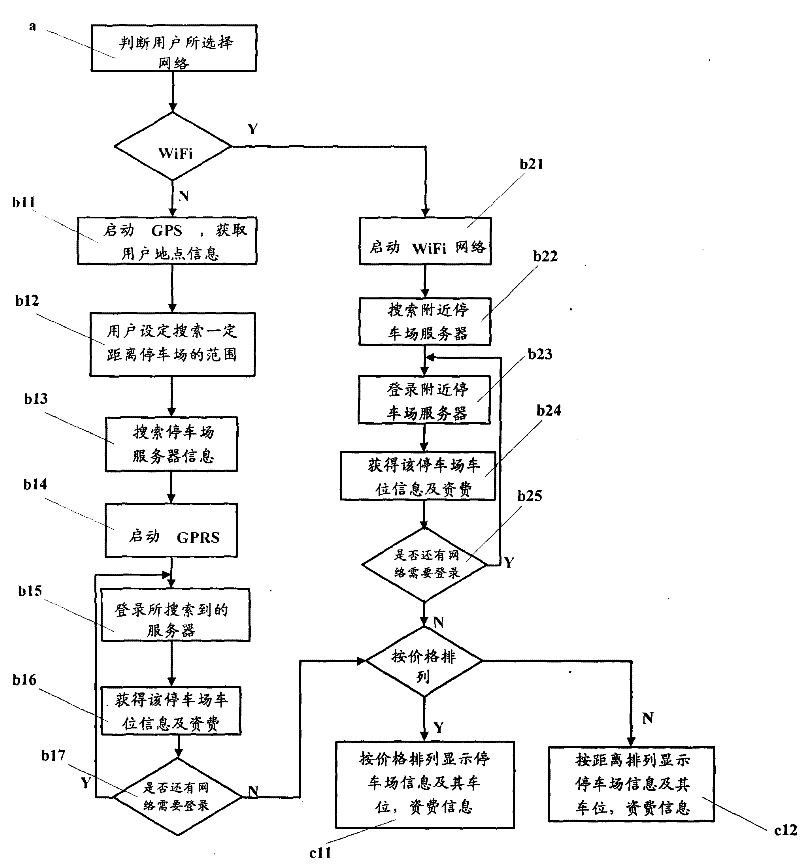
Method for obtaining parking position information of park with movable terminal
InactiveCN101783080BAvoid knowingShorten the timeAssess restrictionIndication of parksing free spacesWifi networkComputer terminal
The invention provids a method for obtaining parking position information of a park with a movable terminal, which comprises the following steps of: judging a network selected by users, starting WiFi network if the users select the WiFi network, and adopting GPRS network if users do not select the WiFi network; searching nearby park servers; logging in the searched servers with the WiFi network or the GPRS network, and obtaining the parking position information and the tariff of the parks; and displaying the obtained information on the display screen of the movable terminal according to the arrangement of the cost or the distance. By designing movable terminal software, the method is convenient for the users to fast obtain the information of the parks, avoids the phenomenon that the userscan not know the information of the park until driving to the park, leads the users to select the park with the nearest distance or the lowest price according to the obtained information, and is convenient for the users to select a better parking position with less time.
Owner:SHENZHEN COSHIP ELECTRONICS CO LTD
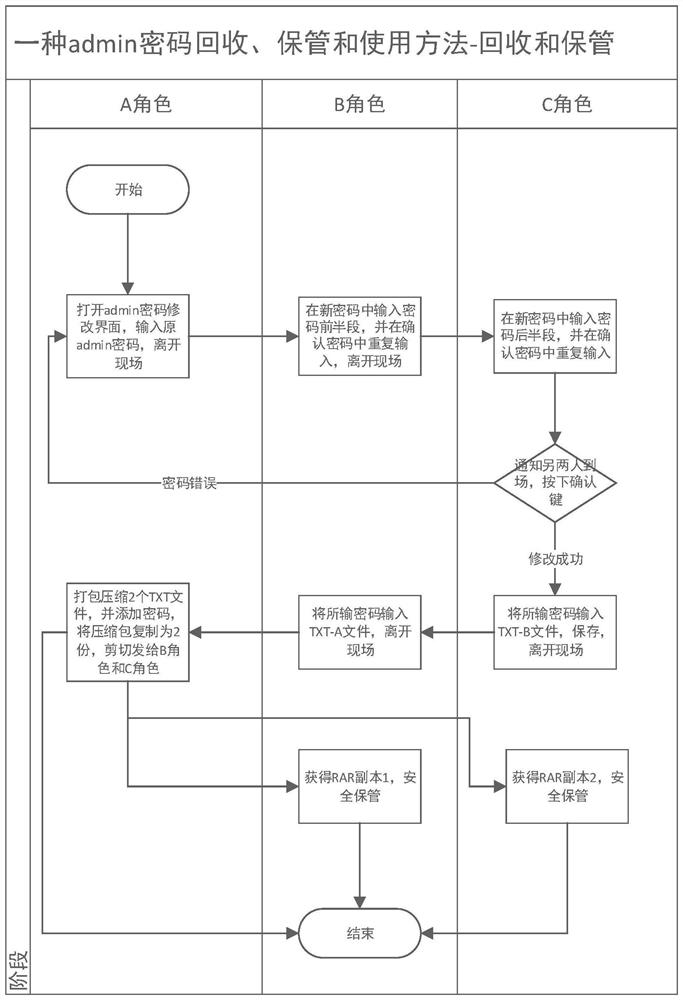
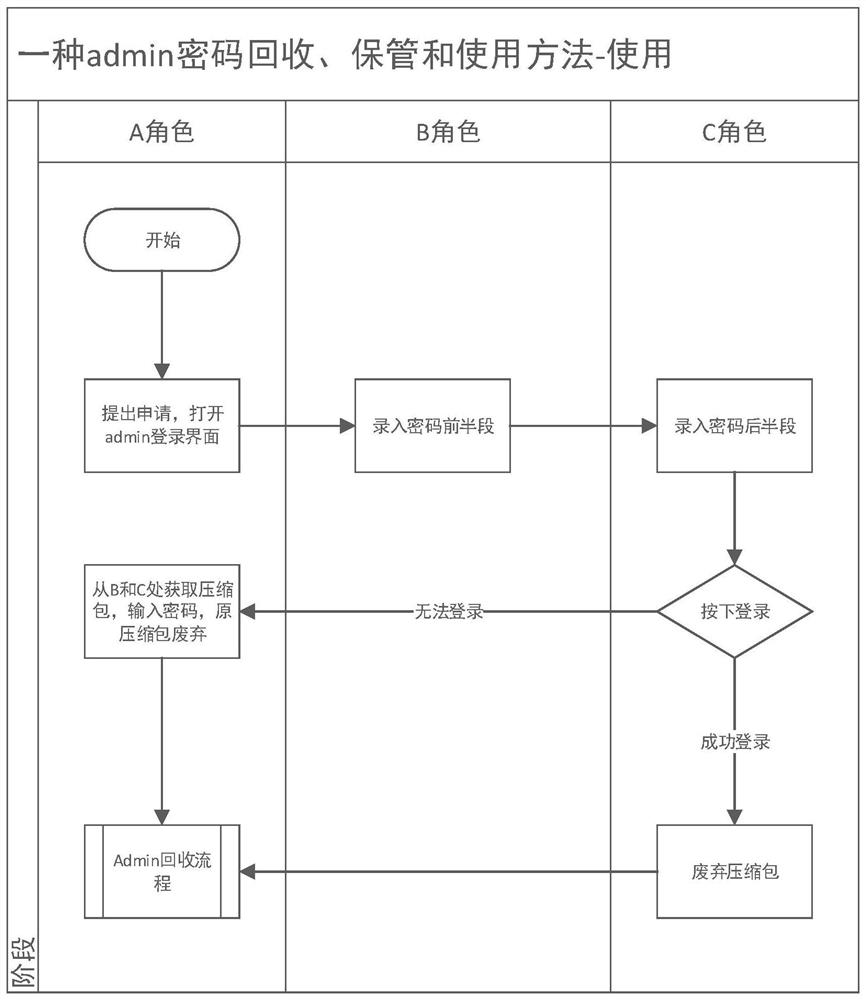
Recycling, storage, usage and device of admin password
Owner:兴业数字金融服务(上海)股份有限公司
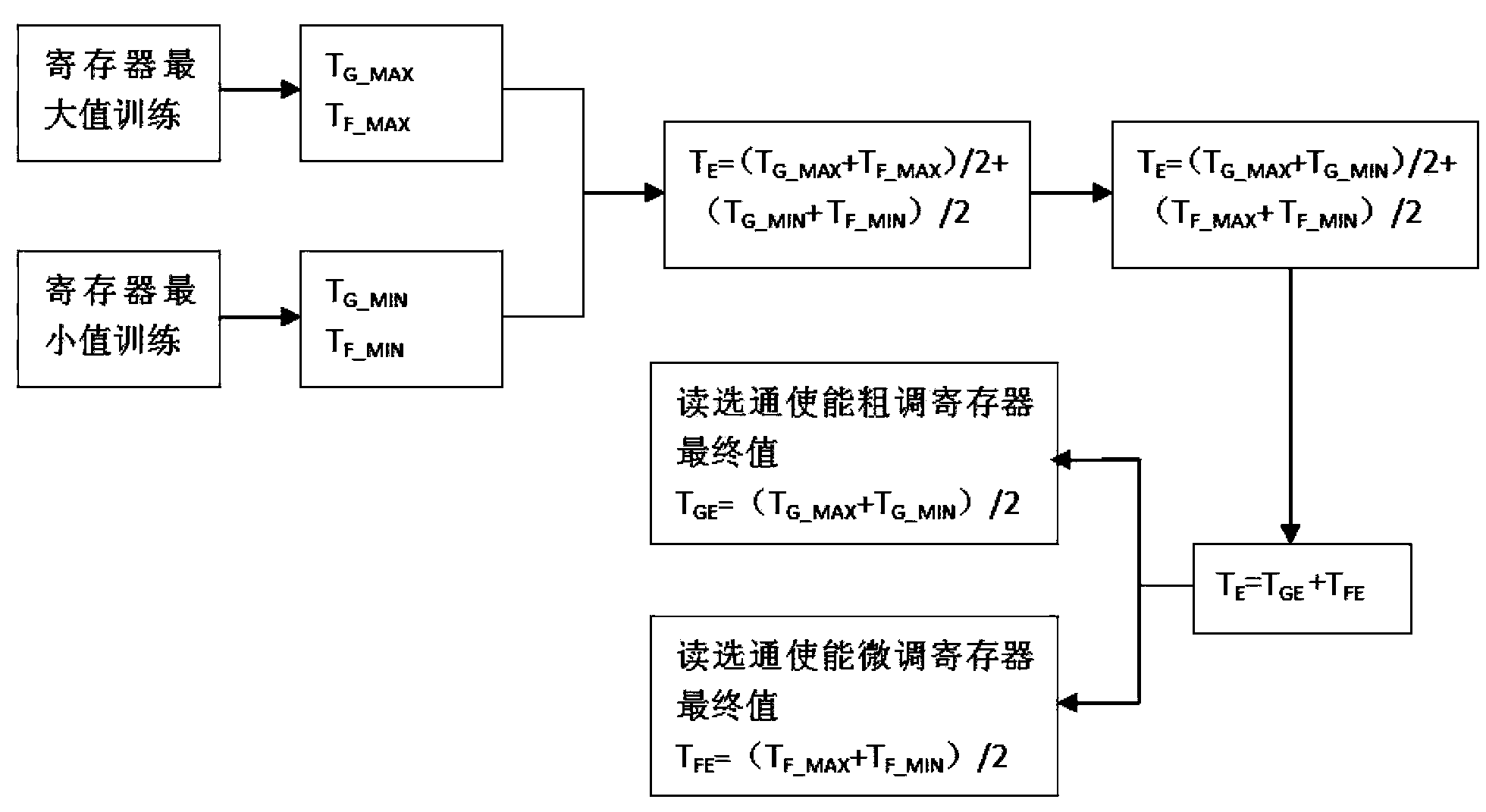
Configuration method for strobe enabling opportunity of read operation data of memory
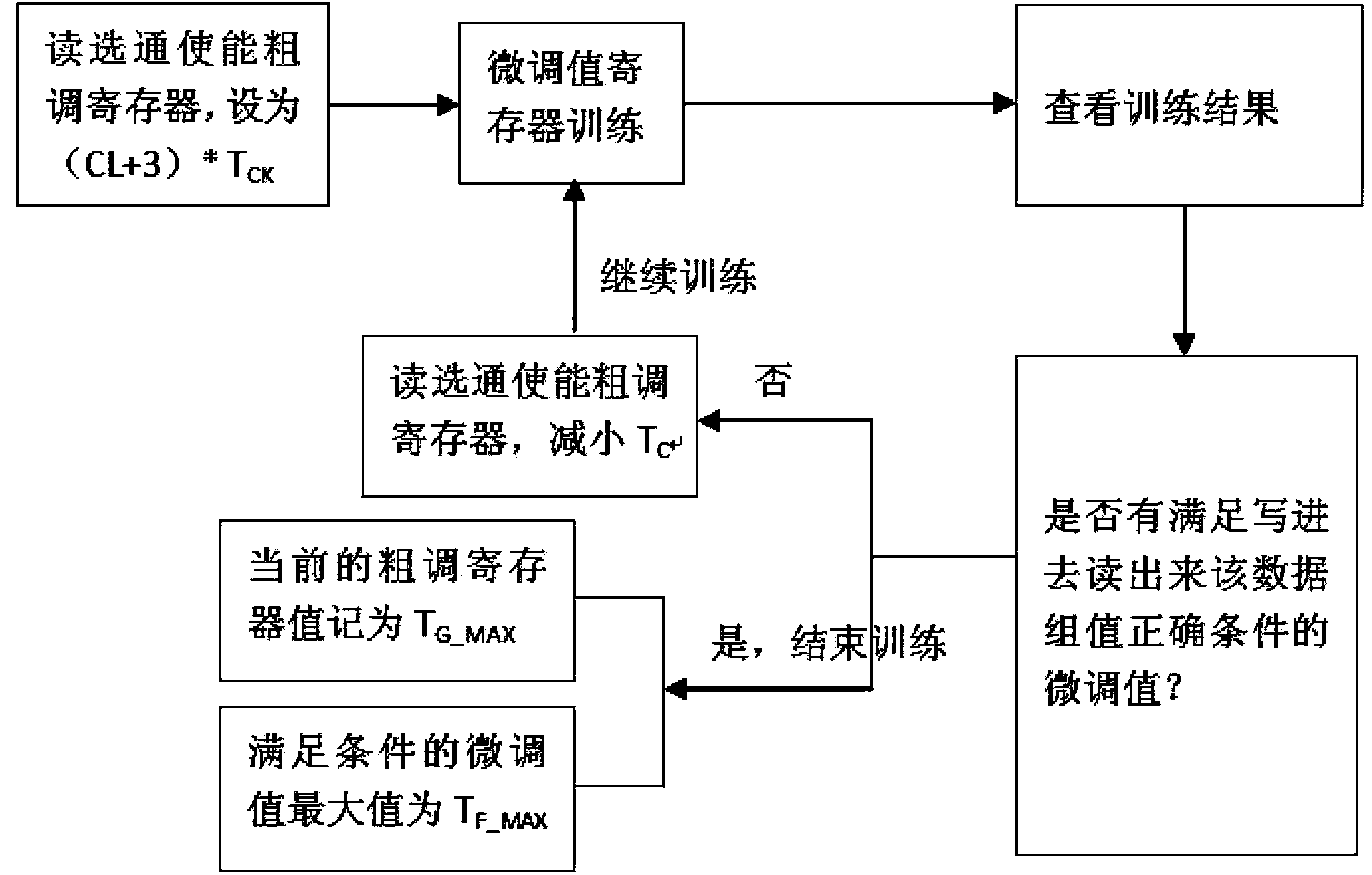
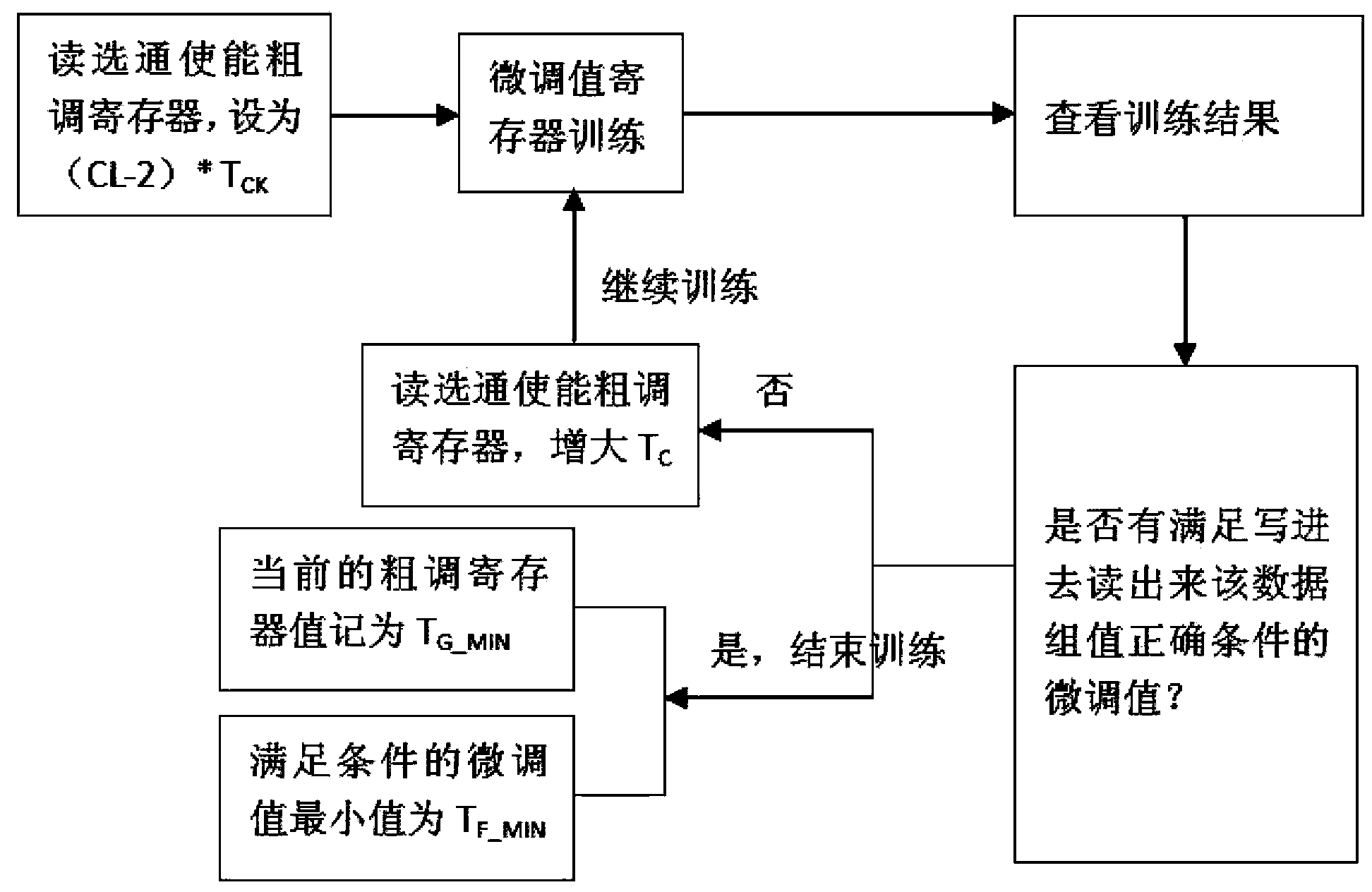
The invention discloses a configuration method for strobe enabling opportunity of read operation data of a memory. The configuration method mainly comprises the following steps of: selecting a certain data set, performing maximum value training and minimum value training of a read strobe enabling register, and acquiring the maximum value and the minimum value which can be configured by the read strobe enabling register; solving an arithmetic mean value of the two acquired values, and taking the arithmetic mean value as a read strobe enabling register final value required to be configured; and performing formula conversion, and acquiring the final value of a read strobe enabling coarse adjustment register, wherein the final value is equal to the arithmetic mean value of the coarse adjustment value corresponding to the maximum value of the read strobe enabling register and the coarse adjustment value corresponding to the minimum value; and the final value of the read strobe enabling coarse adjustment register is equal to the arithmetic mean value of the coarse adjustment value corresponding to the maximum value of the read strobe enabling register and the coarse adjustment value corresponding to the minimum value. According to the configuration method, the phenomenon that the minimum unit value of the read strobe enabling coarse adjustment register is known is prevented, and the strobe enabling opportunity of the read operation data is configured under the condition that the minimum unit of the read strobe enabling coarse adjustment register is unknown.
Owner:江苏航天龙梦信息技术有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com