Short message sending and receiving method, short message sending and receiving device and mobile terminal
A sending method and technology of a sending device, applied in the field of communication, can solve the problems of unfavorable privacy of short message content, and achieve the effect of high privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
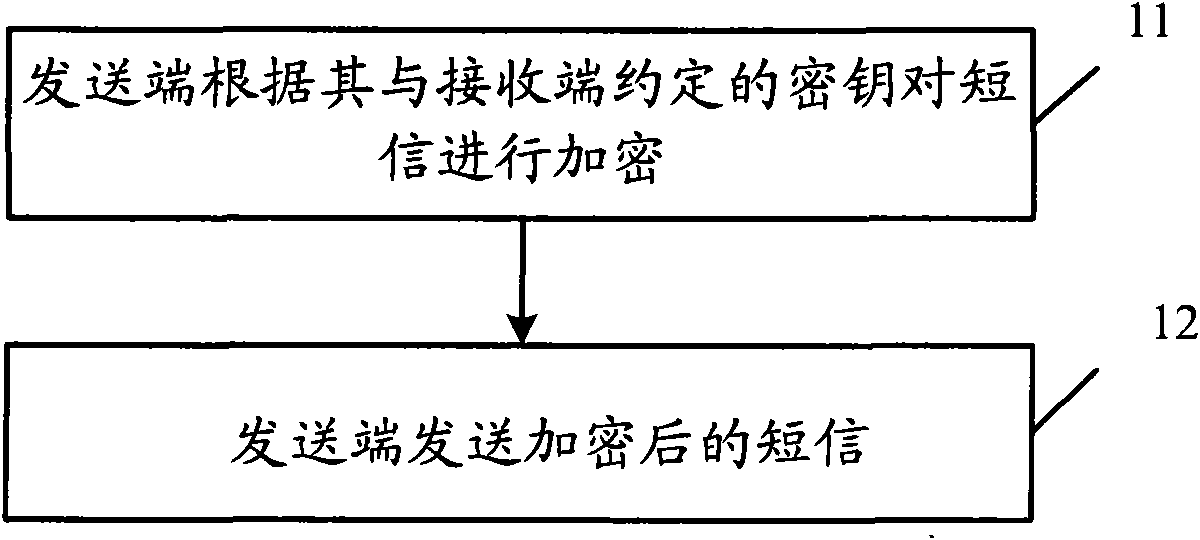
[0043] Such as figure 1 As shown, the embodiment of the present invention provides a short message sending method, including:
[0044] Step 11, the sending end encrypts the short message according to the key agreed between it and the receiving end.
[0045] Step 12, the sender sends the encrypted short message.
[0046] Keys can be symmetric or asymmetric.
[0047] The symmetric key means that the encryption key of the sending end to the SMS is the same key as the decryption key of the receiving end to the SMS, and the encryption and decryption algorithm is a symmetric encryption algorithm, that is, the encryption and decryption algorithms use the same algorithm. That is, the keys agreed by the sender and the receiver are consistent: a key uniquely corresponds to a pair of sender and receiver.
[0048] Asymmetric key refers to the key that the sending end encrypts the SMS and the receiving end decrypts the SMS. For example, the encryption key is a public key, the decryption...
Embodiment 2
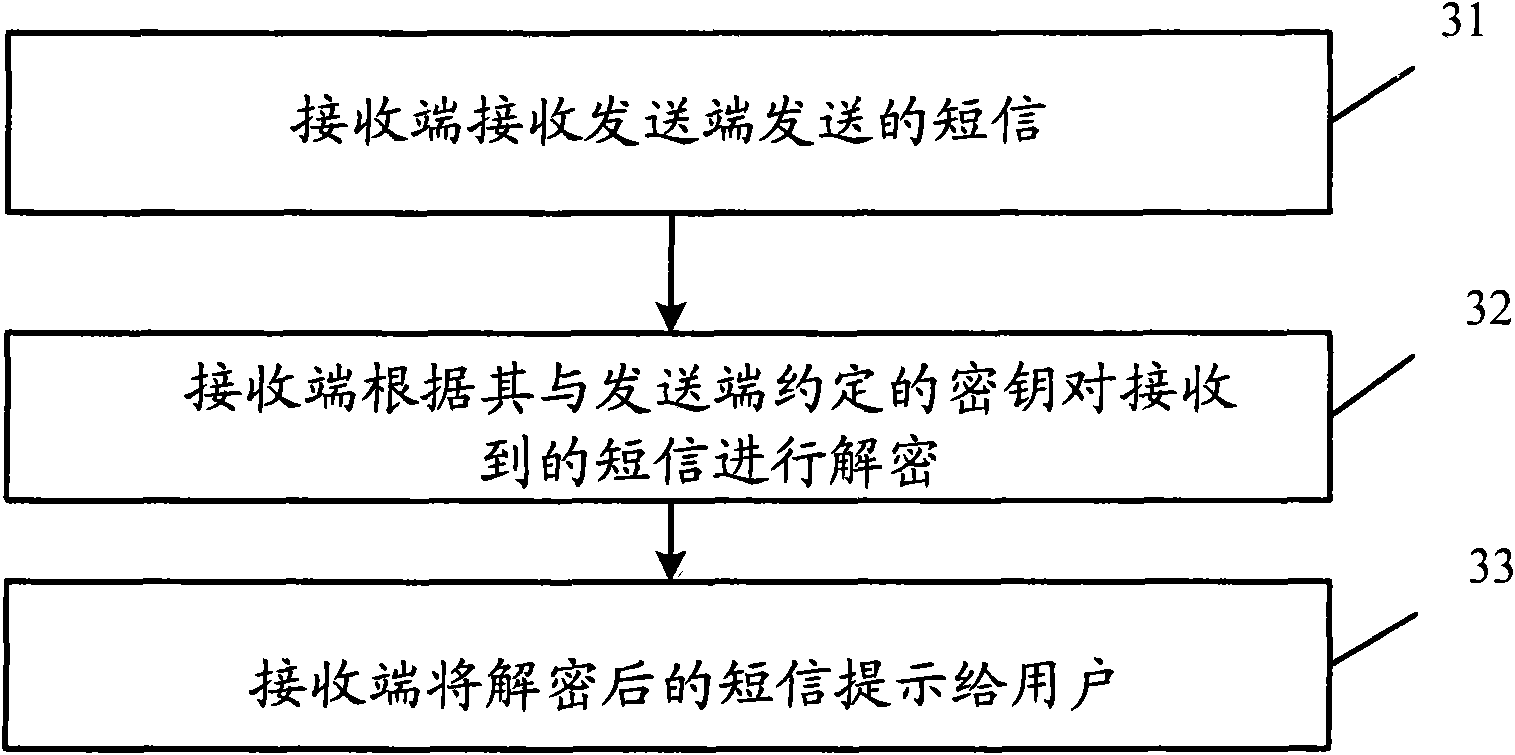
[0075] As shown in Figure 3, corresponding to a short message sending method described in the embodiment, the embodiment of the present invention provides a short message receiving method, including:
[0076] Step 31, the receiving end receives the short message sent by the sending end.
[0077] Step 32, the receiving end decrypts the received short message according to the key agreed between the receiving end and the sending end.
[0078] Step 33, the receiving end prompts the decrypted short message to the user.
[0079] Similarly, the key may be a symmetric key or an asymmetric key, and the symmetric key and the asymmetric key have been described in Embodiment 1, and details will not be repeated here.
[0080] Optionally, the short message receiving method of the embodiment of the present invention also includes, before step 32 that the receiving end decrypts the received short message according to the key agreed with the sending end,
[0081] The receiving end judges whe...
Embodiment 3
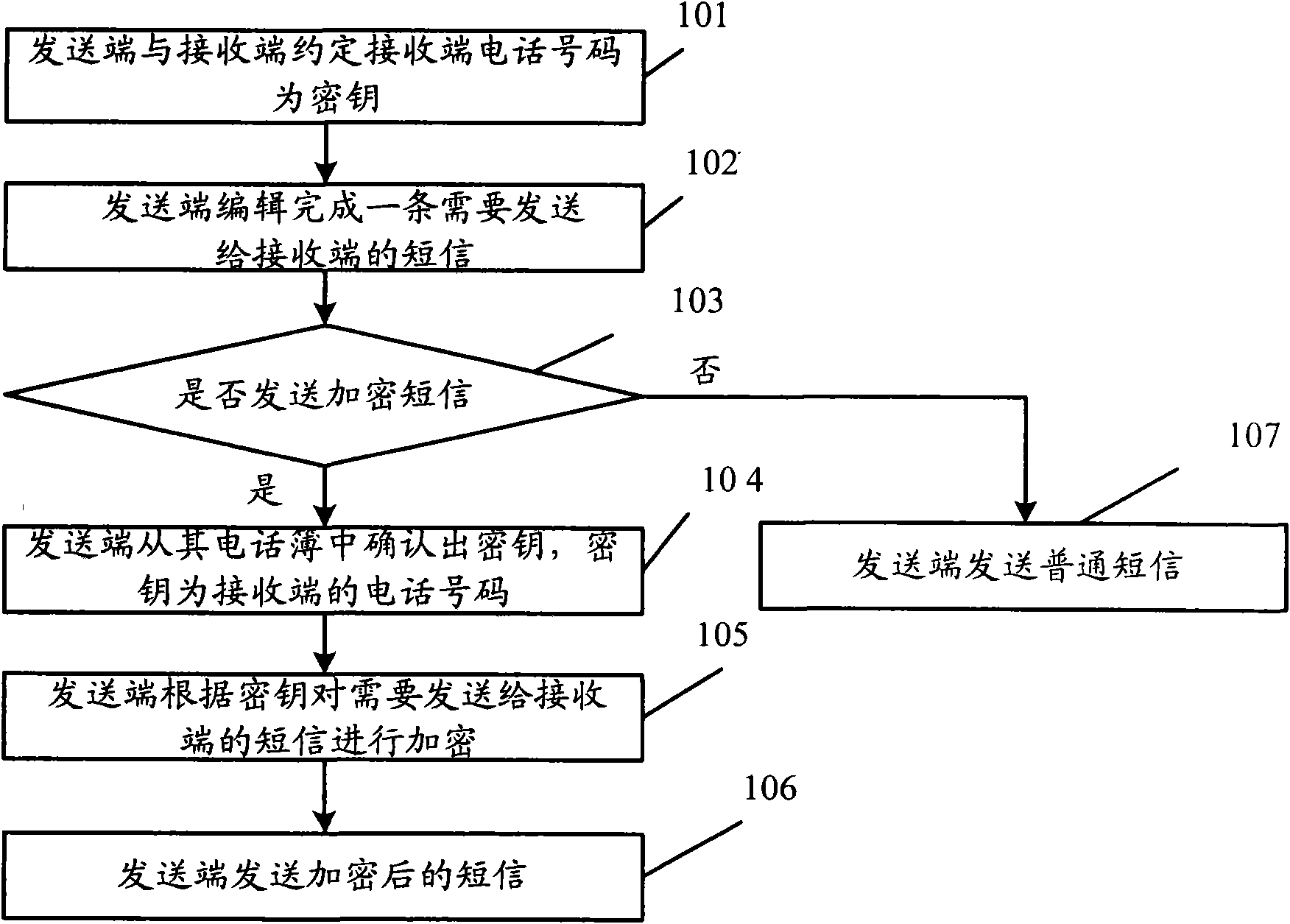
[0101] Such as Figure 5 As shown, corresponding to the short message sending method described in Embodiment 1, the embodiment of the present invention provides a short message sending device, including:
[0102] Short message editing unit 51, used for editing short messages.
[0103] The encryption unit 52 is configured to encrypt the short message according to the key agreed between the sending end and the receiving end.
[0104] A sending unit 53, configured to send the encrypted short message.
[0105] Such as Figure 6 As shown, optionally, the short message sending device of the embodiment of the present invention may also include:
[0106] The short message encryption prompt unit 54 is used to prompt the user whether to encrypt the short message.
[0107] The judging unit 55 is configured to accept the user's input and judge whether the user agrees to encrypt the short message.
[0108] Moreover, the encryption unit 52 is also configured to encrypt the short messag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com