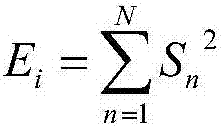Patents
Literature
110 results about "Value code" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
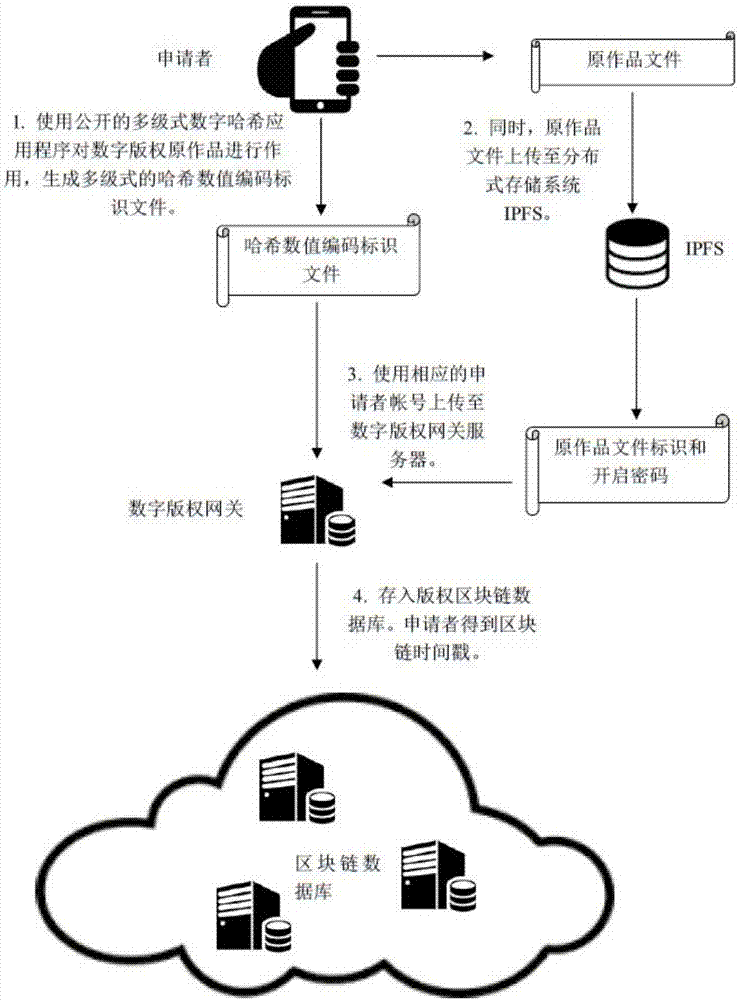
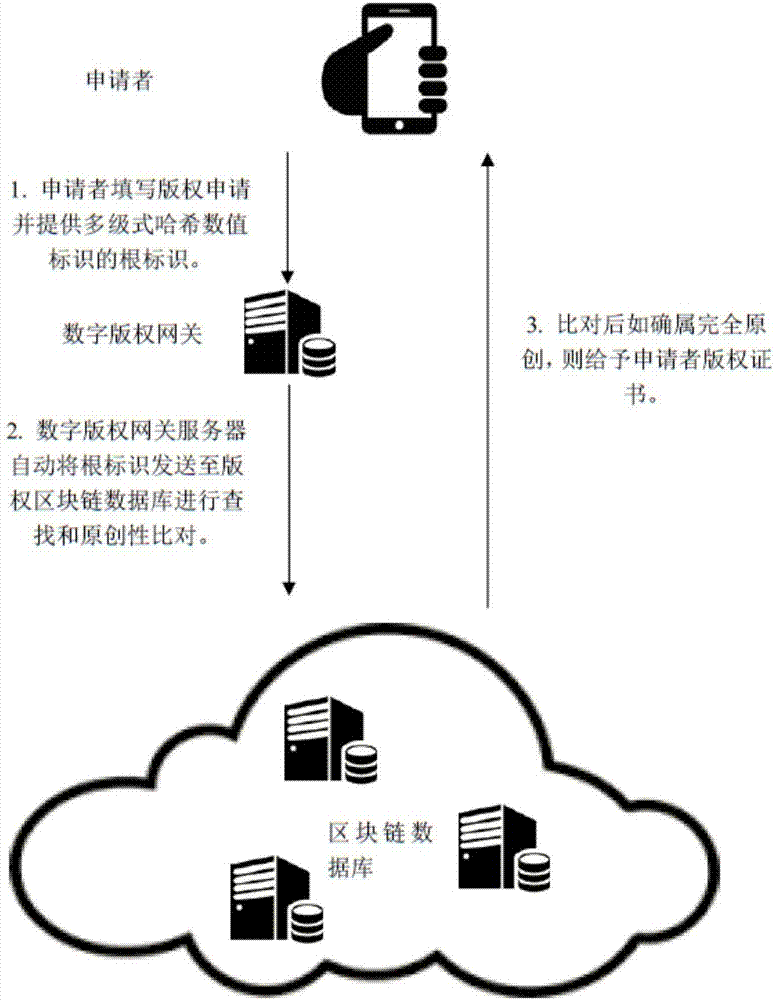
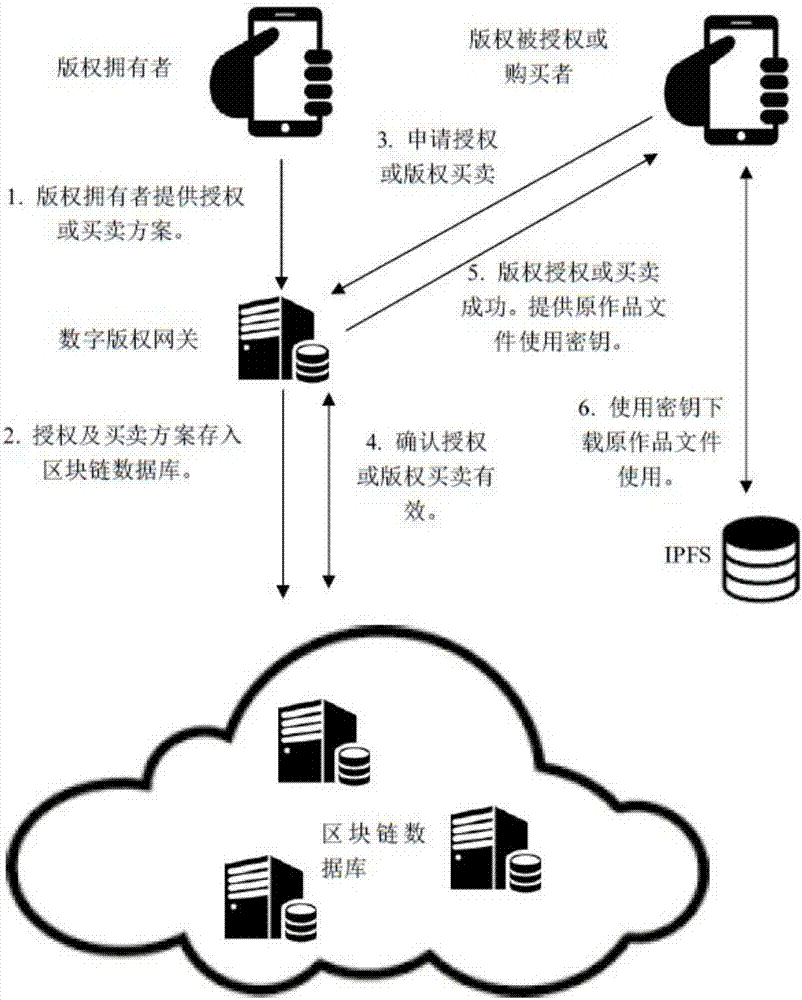
Copyright authorization method based on block chain
InactiveCN107086920AGuaranteed confidentialityShorten the overall cycleUser identity/authority verificationAuthorization certificateFinancial transaction
The invention discloses a copyright authorization method based on a block chain. The method comprises steps of: 1, uploading a work to a client so as to enable the work to become a multi-level hash value code identification document; 2, generating a self identity identifier in a copyright block chain database; 3, enabling a digital copyright gateway server to store the generated multi-level hash value code identification document uploaded by an applicant in self identity into a copyright block chain database; 4, enabling the applicant to fill in a copyright application agreement in detail through a digital copyright application website; 5, enabling the digital copyright application website system to search the duplicate records of various levels of digital identification codes in the block chain database, and to give a copyright authorization conclusion; 6, determining the ownership of copyright according to the copyright authorization conclusion, and sending to the applicant a copyright authorization certificate or an electronic copyright authorization certificate; and 7, enabling two copyright traders to apply for authorization and an authorization transaction at the digital copyright application website system. The method solves the shortcomings of conventional copyright authorization and ensures the high security and reliability of the copyright.
Owner:无锡井通网络科技有限公司
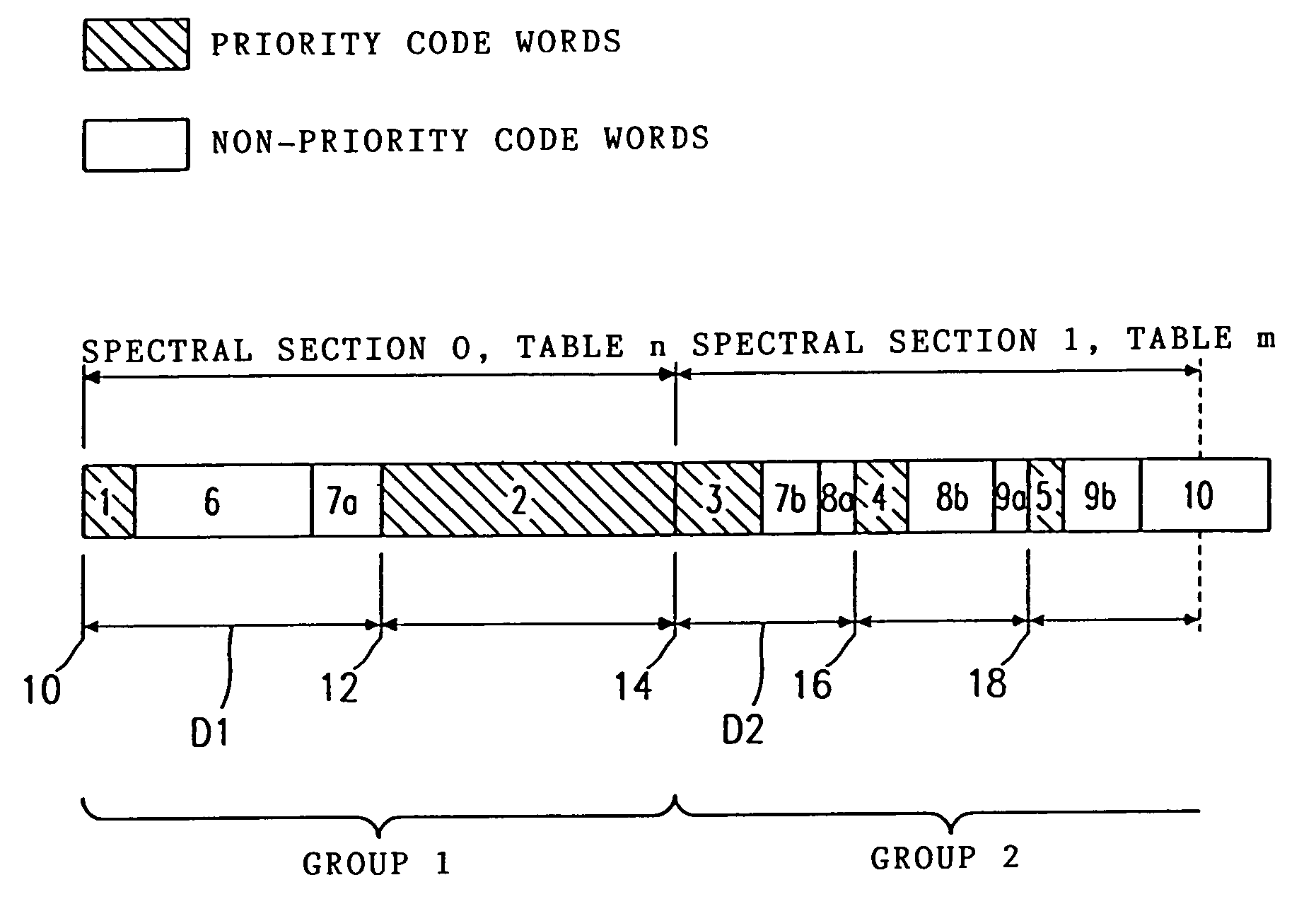
Methods and devices for coding or decoding an audio signal or bit stream
InactiveUS6975254B1Increase probabilityConvenient amountBroadcast with distributionSpeech analysisFrequency spectrumGrating
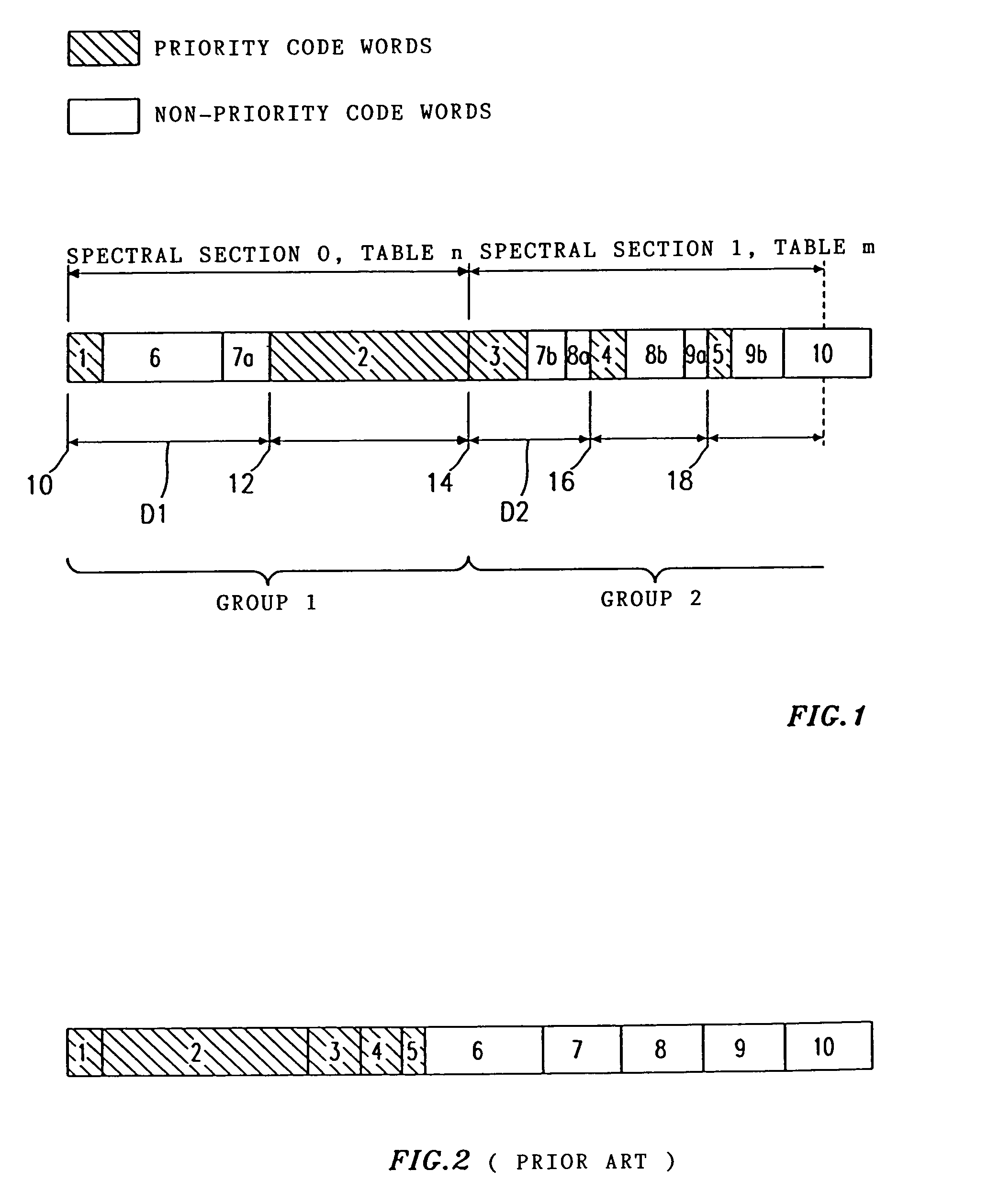
In a method for coding an audio signal to obtain a coded bit stream, discrete-time samples of the audio signal are transformed into the frequency domain to obtain spectral values. The spectral values are coded with a code table having a limited number of code words of different lengths to obtain spectral values coded by code words, the length of a code word assigned to a spectral value being that much shorter the higher the probability of occurrence of the spectral value is. A raster is then specified for the coded bit stream, the raster having equidistant raster points and the distance between the raster points depending on the code table(s) used. In order to obtain error-tolerant Huffman coding, priority code words, which represent particular spectral values which are psychoacoustically more important than other spectral values, are so arranged in the raster that the start of each priority code word coincides with a raster point.
Owner:FRAUNHOFER GESELLSCHAFT ZUR FOERDERUNG DER ANGEWANDTEN FORSCHUNG EV
Tourism electronic contract digital certificate storage system and certificate storage method based on regional chain
InactiveCN109064120AImprove performanceAchieve zero lossFinanceOffice automationElectronic contractsDigital storage
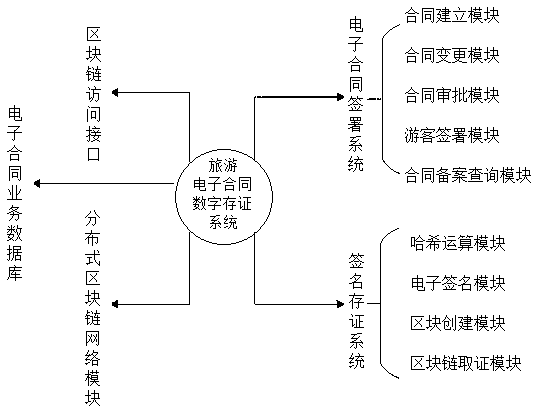
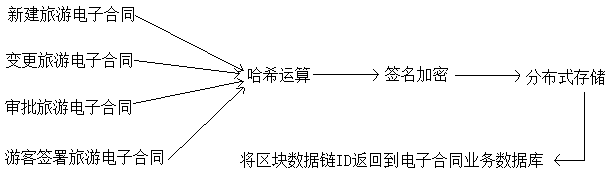
The invention discloses a tourism electronic contract digital storage system and a storage method based on a regional chain, which comprises an electronic contract signing system, an electronic contract service database, a block chain access interface, a distributed block chain network module and a signature storage system. The electronic contract signing system includes contract establishing module, contract changing module, contract approving module, tourist signing module and contract filing inquiry module. The signature storage system comprises a hash operation module, an electronic signature module, a block creation module and a block chain forensics module. Hash operation is carry out on that business data related to the electronic contract to form the hash value code certificate data; Signing and encrypting the generated hash value encoded certificate data combined with the operator private key of the related service; Distributed storage of hash value encoded certificate data iscarried out in the node of the area chain; The invention adopts the block chain technology, realizes the electronic management of the contract, realizes the zero loss of the electronic contract data,and ensures that the transmission process cannot be tampered with.
Owner:MASHANGYOU TECH CO LTD
Nerve network system for realizing genetic algorithm
InactiveCN1450493AEasy to implementHigh speedGenetic modelsPhysical realisationNerve networkRelationship - Father
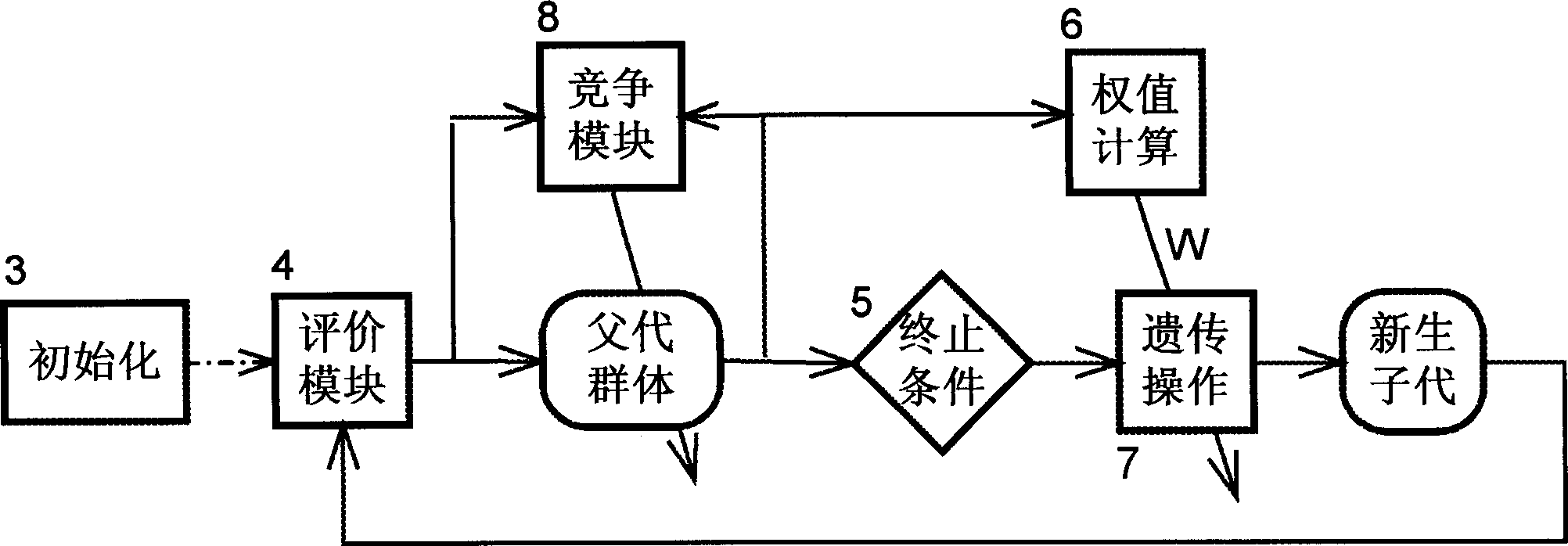
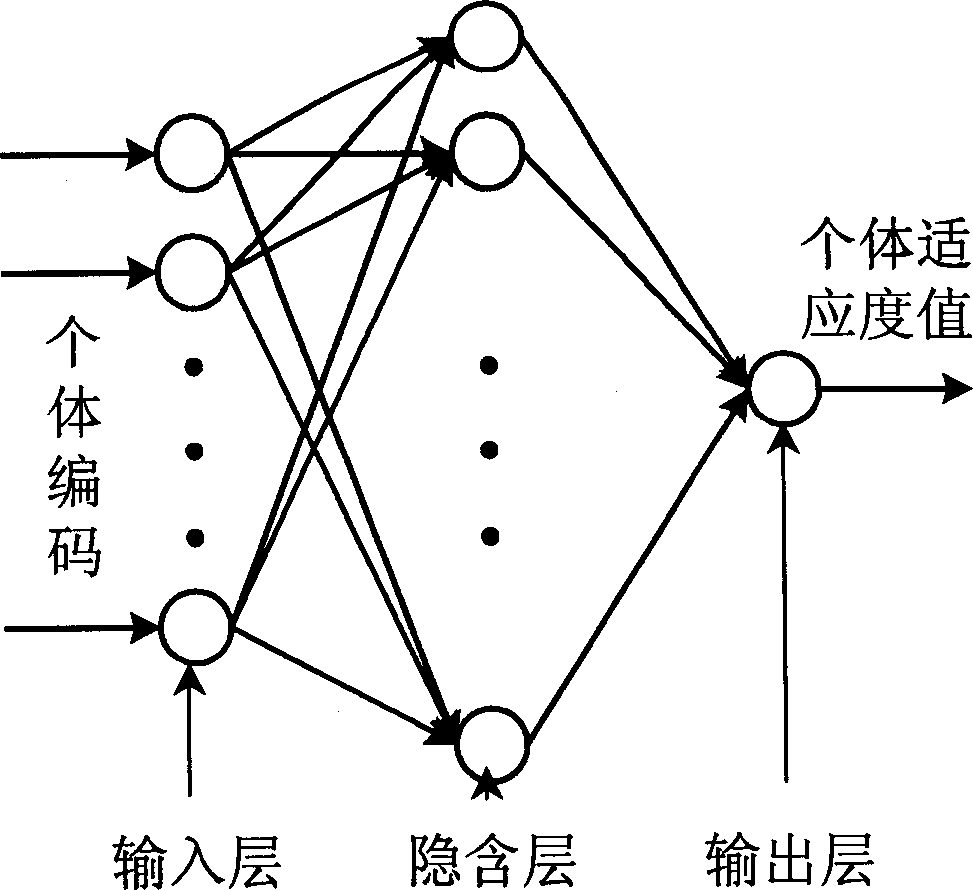
The invention is nerve net system which can realize heredity arithmetic. It is made up of computer nerve net model component and the interfaces. The character lies in: 1. after that the computer setsthe population size, coding type and length, heredity operation probability and the arithmetic ending condition of the arithmetic, the nerve net uses population size to realize the whole heredity operation including selection, crossing, mutation and personal adaptability value, and outputs the optimized calculation and result through computer; 2. designs the heredity operation nerve net model which can realize multi-father crossing operation and multi-gene mutation operation, realizes the two operation of two-value coding heredity arithmetic and real number coding heredity arithmetic.
Owner:BEIJING UNIV OF TECH
Dynamic coded lock system for acquiring codes by virtue of table look-up
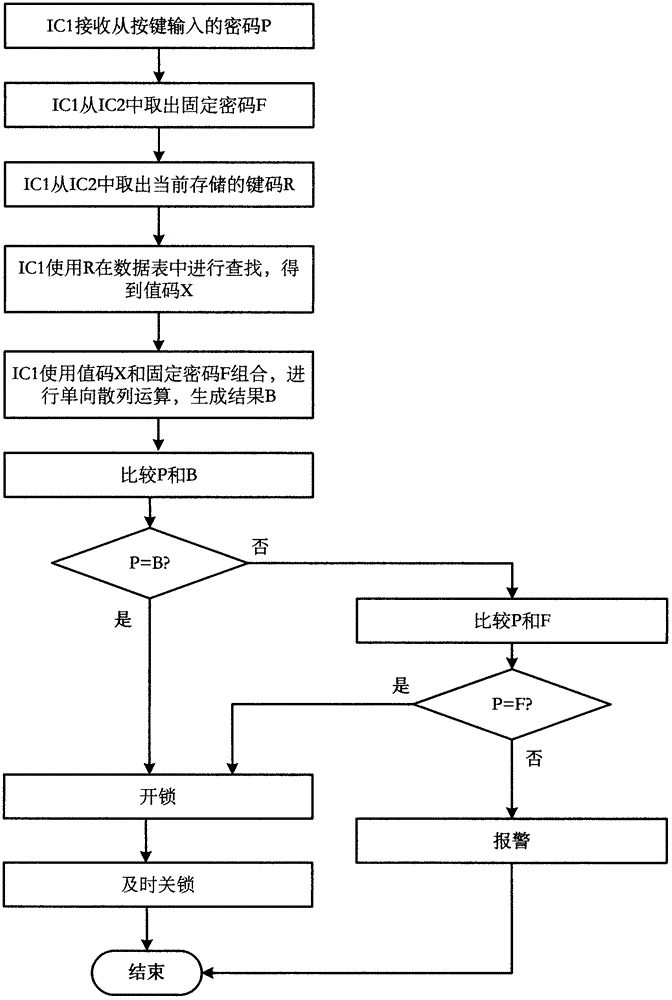
InactiveCN104537738AEasy to manageEasy to findElectric permutation locksIndividual entry/exit registersProgramming languageLock manager
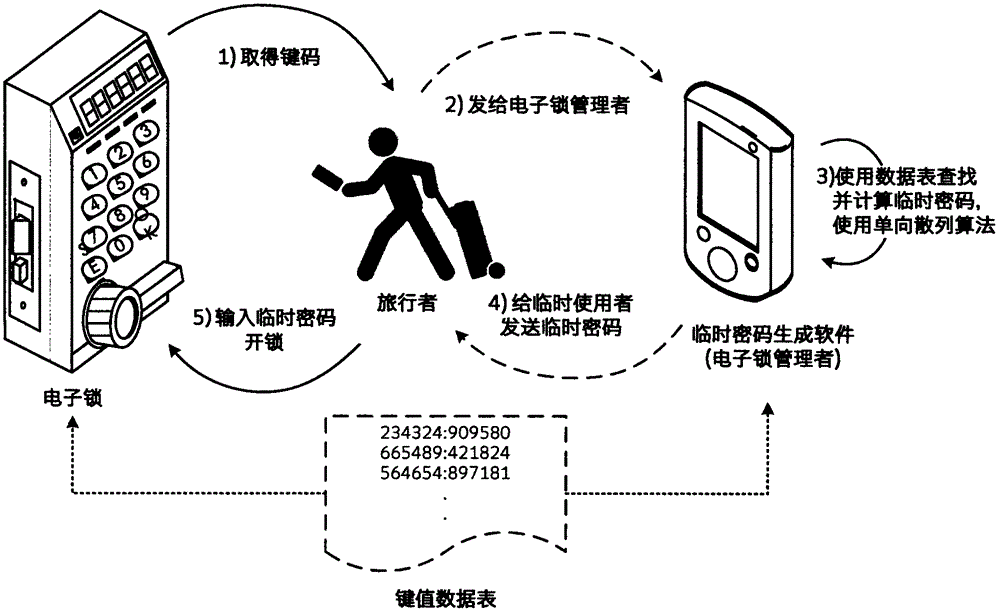
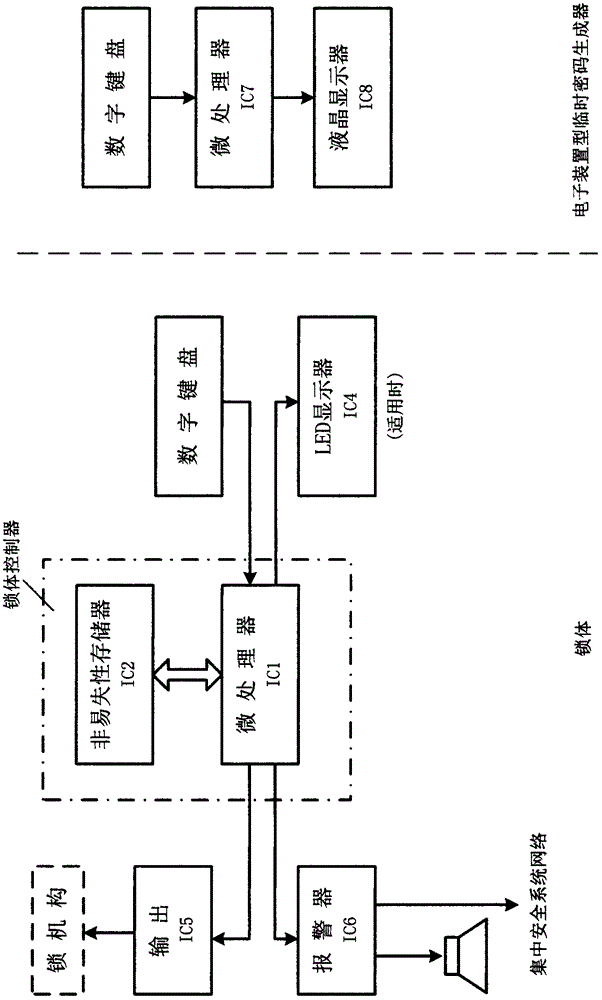
The invention provides a dynamic coded lock system for acquiring codes by virtue of table look-up. The dynamic coded lock system comprises a lock body and a temporary code generator, wherein a fixed code and a key-value data table of a coded lock are stored in a nonvolatile memory in the lock body; when an electronic lock is used by a temporary user, a key code R is displayed by the electronic lock, a temporary code for unlocking the lock is obtained by finding a corresponding value code X in the data table by virtue of the key code R, besides, the fixed code can be used as a parameter to convert the value code X into the temporary code for use, and the temporary code is calculably changed along the changing of the fixed code or the difference of key codes displayed in each time. Therefore, the temporary code can be calculated by a coded lock manager knowing the fixed code and the data table in the coded lock when the key code is received, and after the temporary code is passed to the temporary coded lock user, the lock can be locked by the temporary coded lock user by virtue of the temporary code in a valid time period.
Owner:袁磊
Apparatus and method for receiving data in a communication system
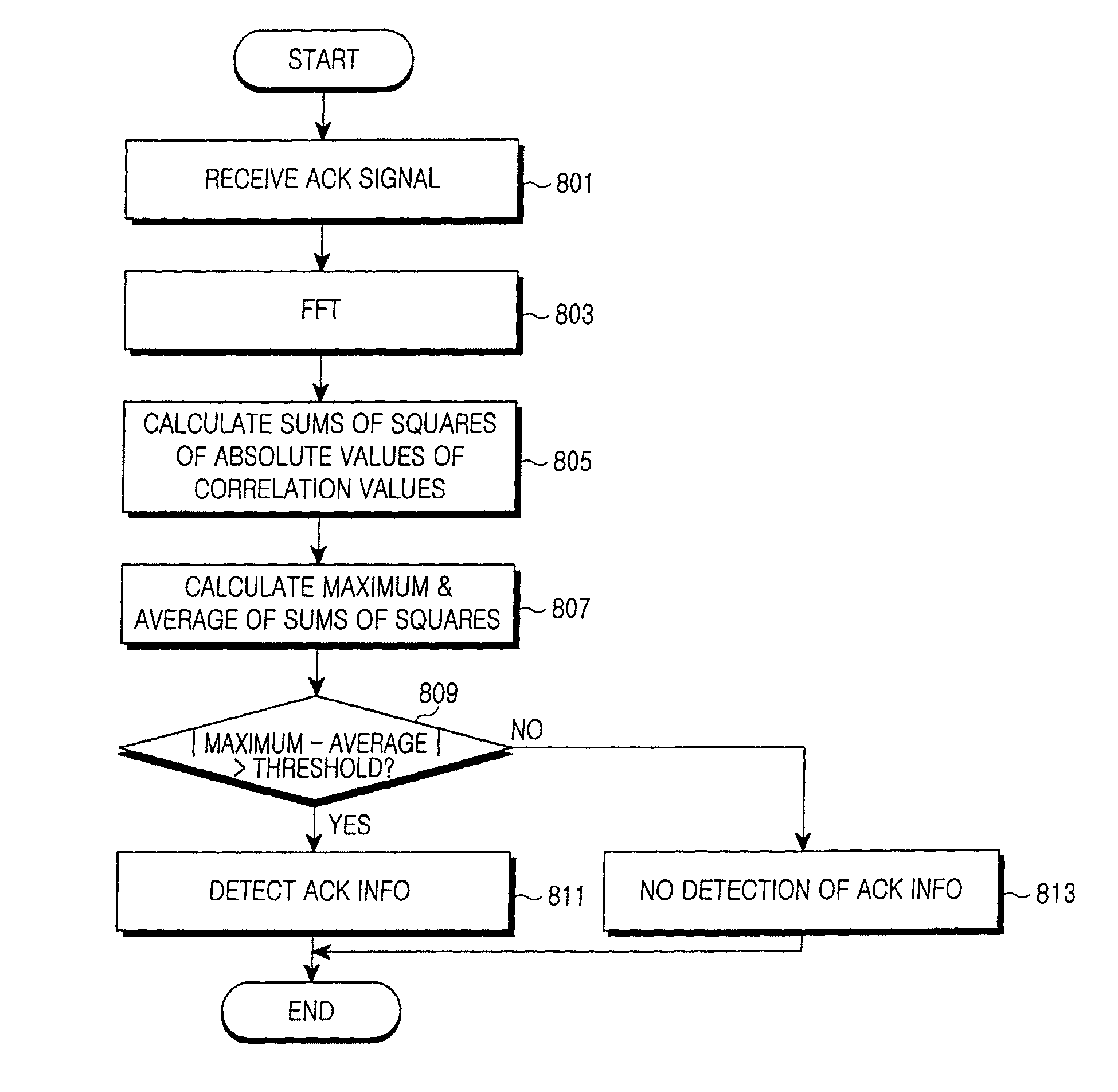
ActiveUS7995615B2Improve efficiencyIncrease ratingsError prevention/detection by using return channelCode division multiplexCommunications systemData transmission
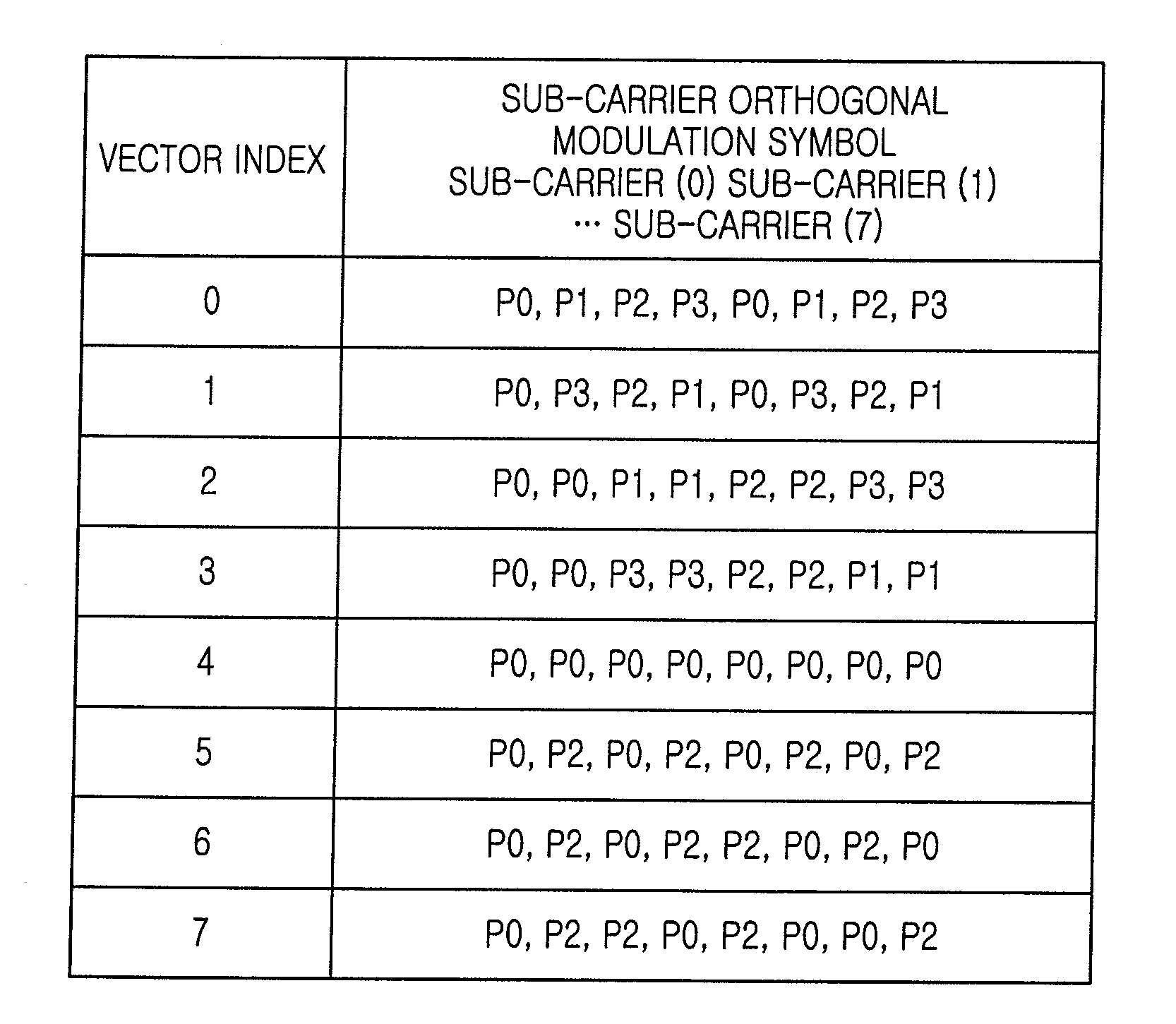
An apparatus and method for receiving data in a communication system are provided. The method includes identifying first codewords, which have been used in transmission of data by a transmitter, in the data received from the transmitter, setting third codewords by adding second codewords to the identified first codewords, calculating correlation values of orthogonal vectors corresponding to the third codewords and detecting information included in the data based on the calculated correlation values. Accordingly, feedback information may be better received and detected.
Owner:SAMSUNG ELECTRONICS CO LTD
Prepaid pay television system
ActiveUS20050177514A1Low costTelevision system detailsAnalogue secracy/subscription systemsTelevision systemData stream
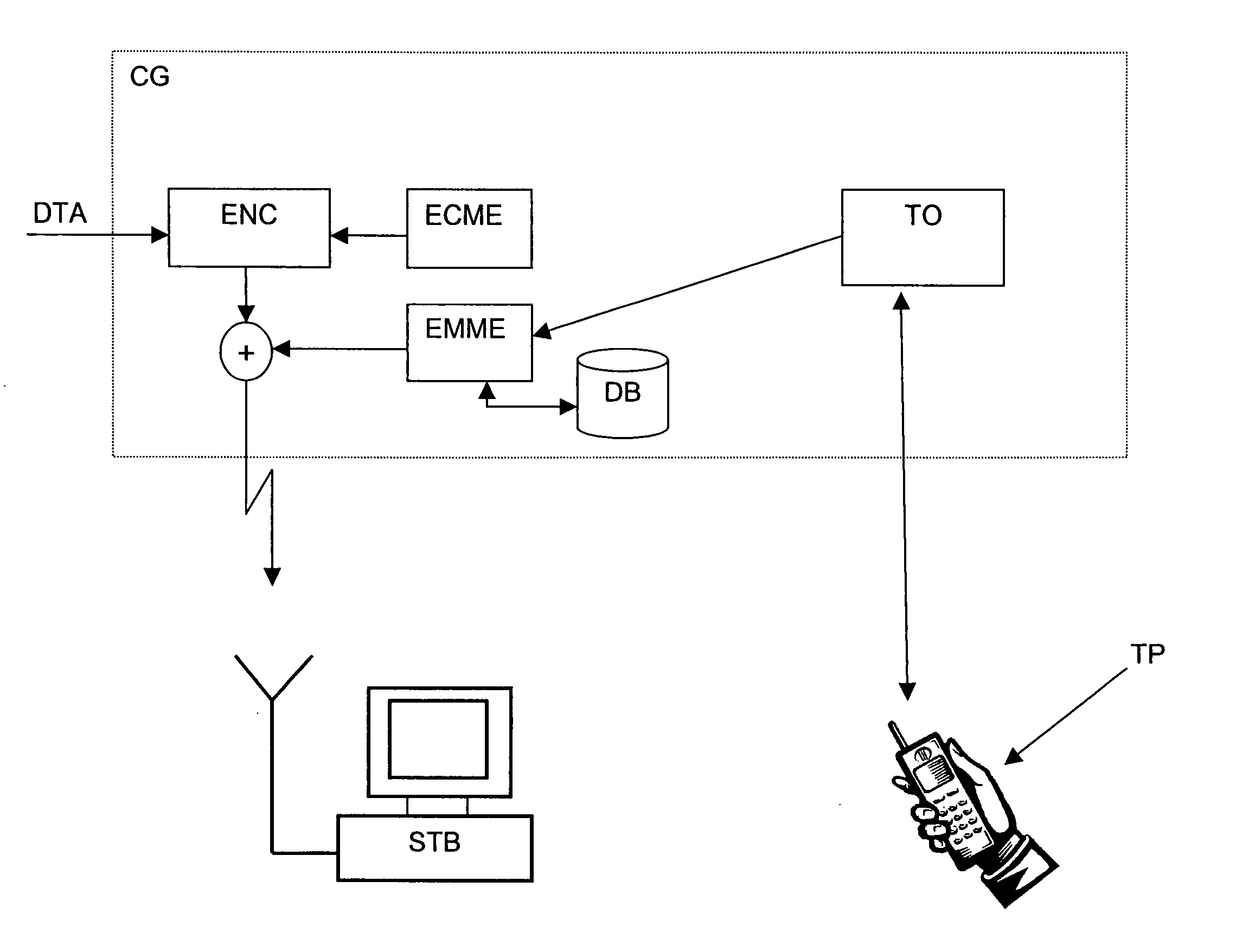
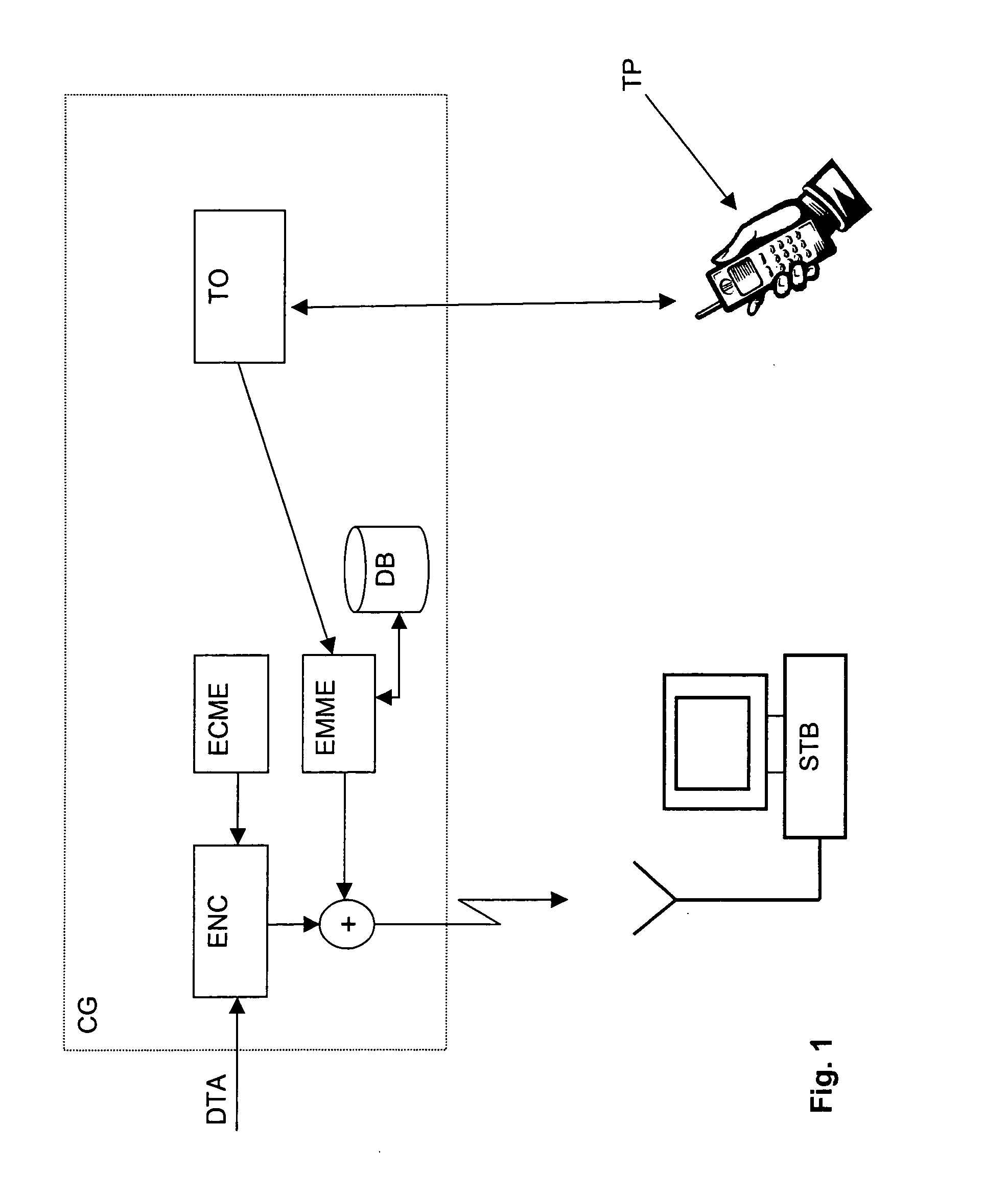
The aim of this invention is to propose an innovating way to offer access to paying TV to a large clientele all by drastically diminishing the costs connected to the management of the subscribers. This aim is reached by a system having a managing center (CAS) transmitting a data stream encrypted by control words (CW), these control words being included in control messages (ECM), this data stream intending to be received by at least one user unit (STB) linked to a security module (SC) identified by a unique address (UA), this security module (SC) containing a credit (CR) which is deducted according to the purchase of products or the consumption of data stream, characterized in that the security user comprises means to deduct the credit of an amount (M1) relating to a product or an amount (M2) relating to a duration (T), this amount (M1, M2) and / or this duration (T) being defined in the management message (ECM) or in a management message (EMM), the user having means to transmit to the managing center (CAS) a representative identifier of the unique address (UA) and a value code representing an amount (TA) of credit to reload (CR), the managing center having means to deal with and check the value code (VC) and to transmit, an encrypted message having the unique address (UA) and the amount (TA) to reload the credit (CR) to the security module (SC).
Owner:NAGRAVISION SA
Method for point of sale consumer packaged goods and lottery promotions
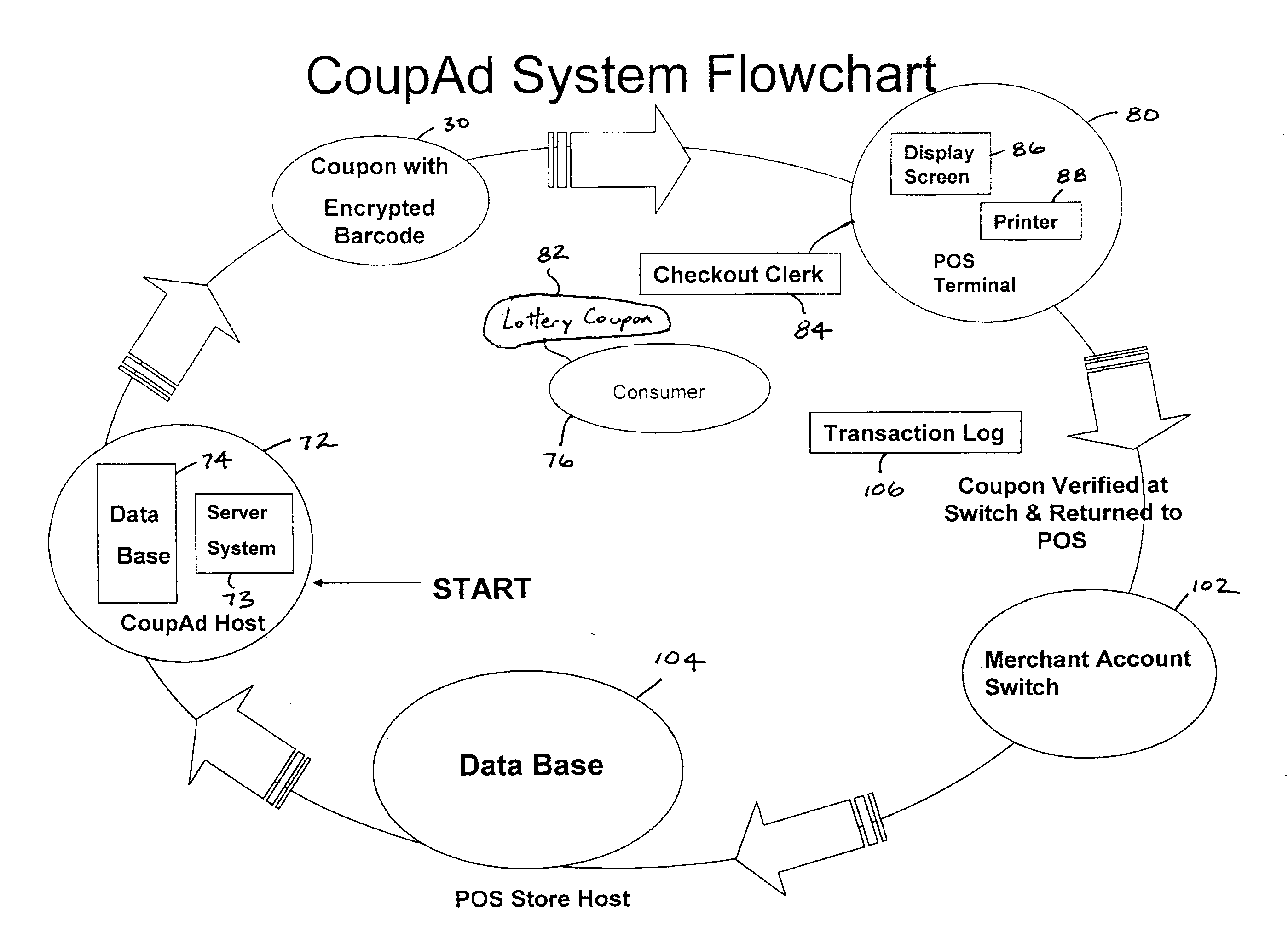
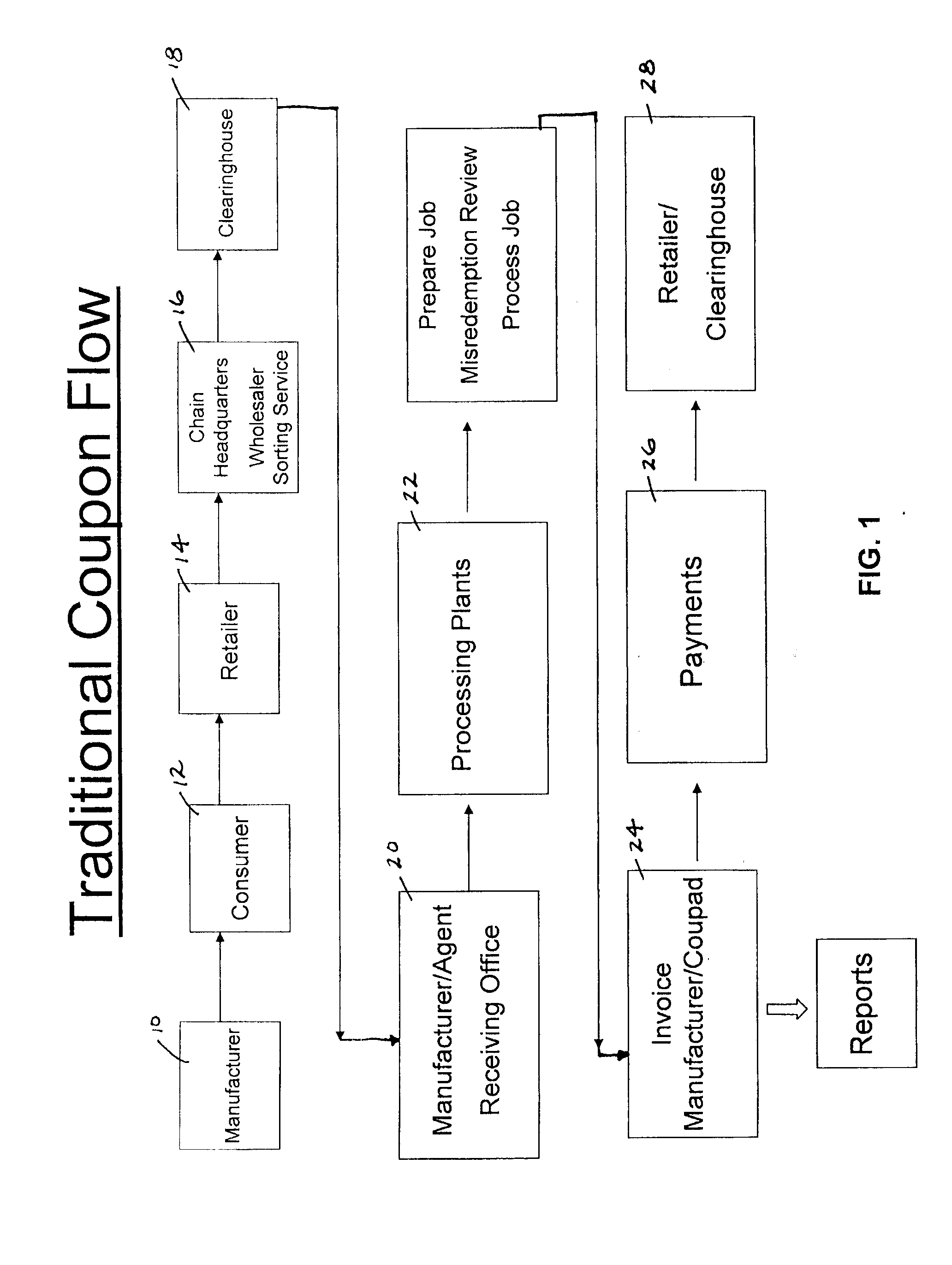
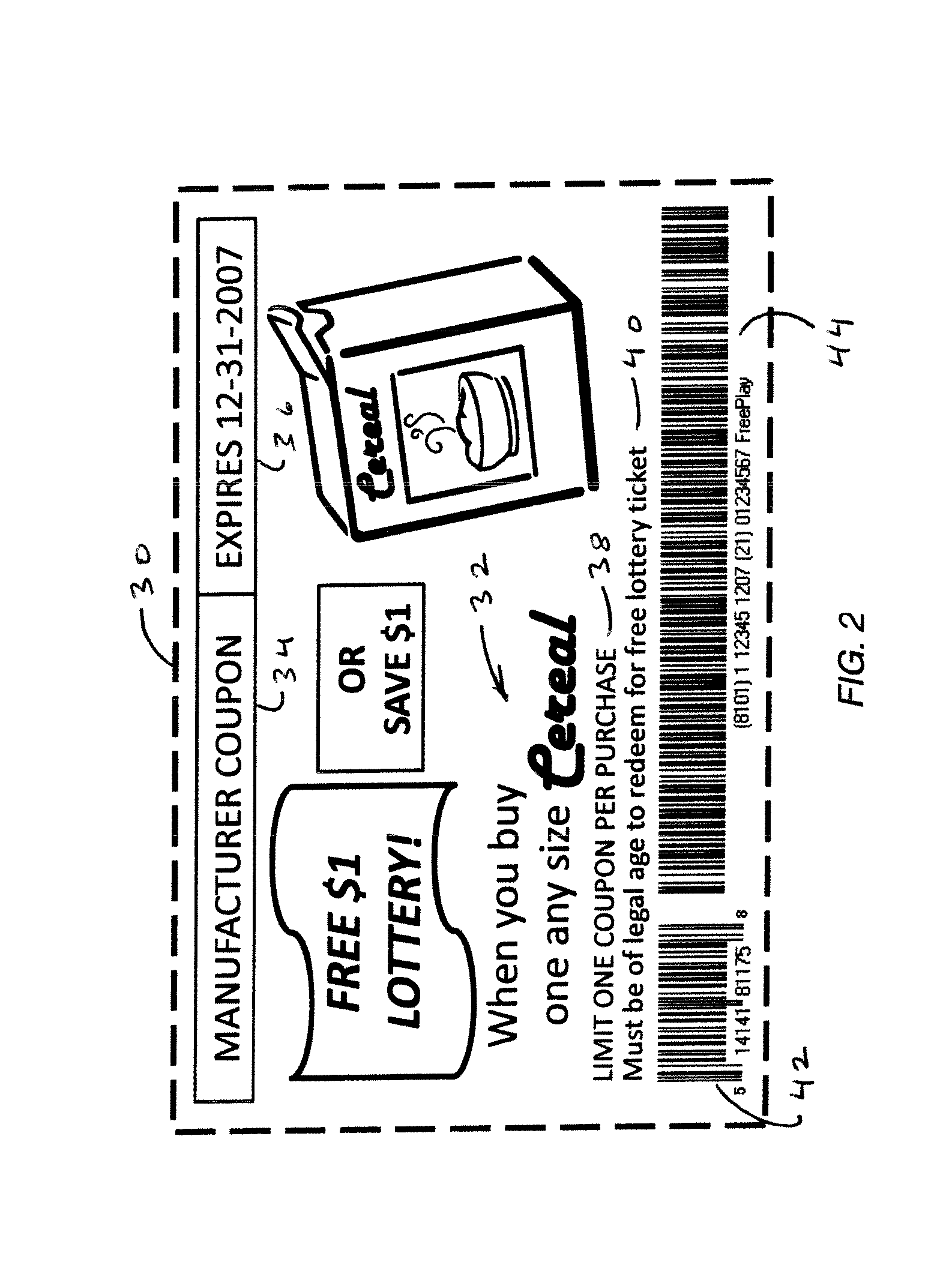
A method and system for point of sale consumer packaged goods and lottery promotions. A discount coupon is generated having two barcodes. The first barcode encodes standard UPC barcode data including, e.g., manufacturer ID, retail product or a retail product family, and discount value code. The second barcode encodes a FreePlay identifier code. A POS system scans the barcodes and the FreePlay identifier code is recognized. Based on this, the consumer is offered a choice of a Lottery FreePlay coupon in lieu of the discount on the retail product. When the consumer accepts the choice of a Lottery FreePlay coupon, a Lottery FreePlay coupon is printed for the consumer in lieu of giving the consumer a discount on the retail product. The Lottery FreePlay coupon is redeemable at an authorized lottery booth for a lottery ticket having a purchase price based on the discount value code.
Owner:DAVIS DAVID L
Apparatus and method for receiving data in a communication system
ActiveUS20080151938A1High data efficiencyIncrease data rateError prevention/detection by using return channelCode division multiplexCommunications systemData transmission
An apparatus and method for receiving data in a communication system are provided. The method includes identifying first codewords, which have been used in transmission of data by a transmitter, in the data received from the transmitter, setting third codewords by adding second codewords to the identified first codewords, calculating correlation values of orthogonal vectors corresponding to the third codewords and detecting information included in the data based on the calculated correlation values. Accordingly, feedback information may be better received and detected.
Owner:SAMSUNG ELECTRONICS CO LTD
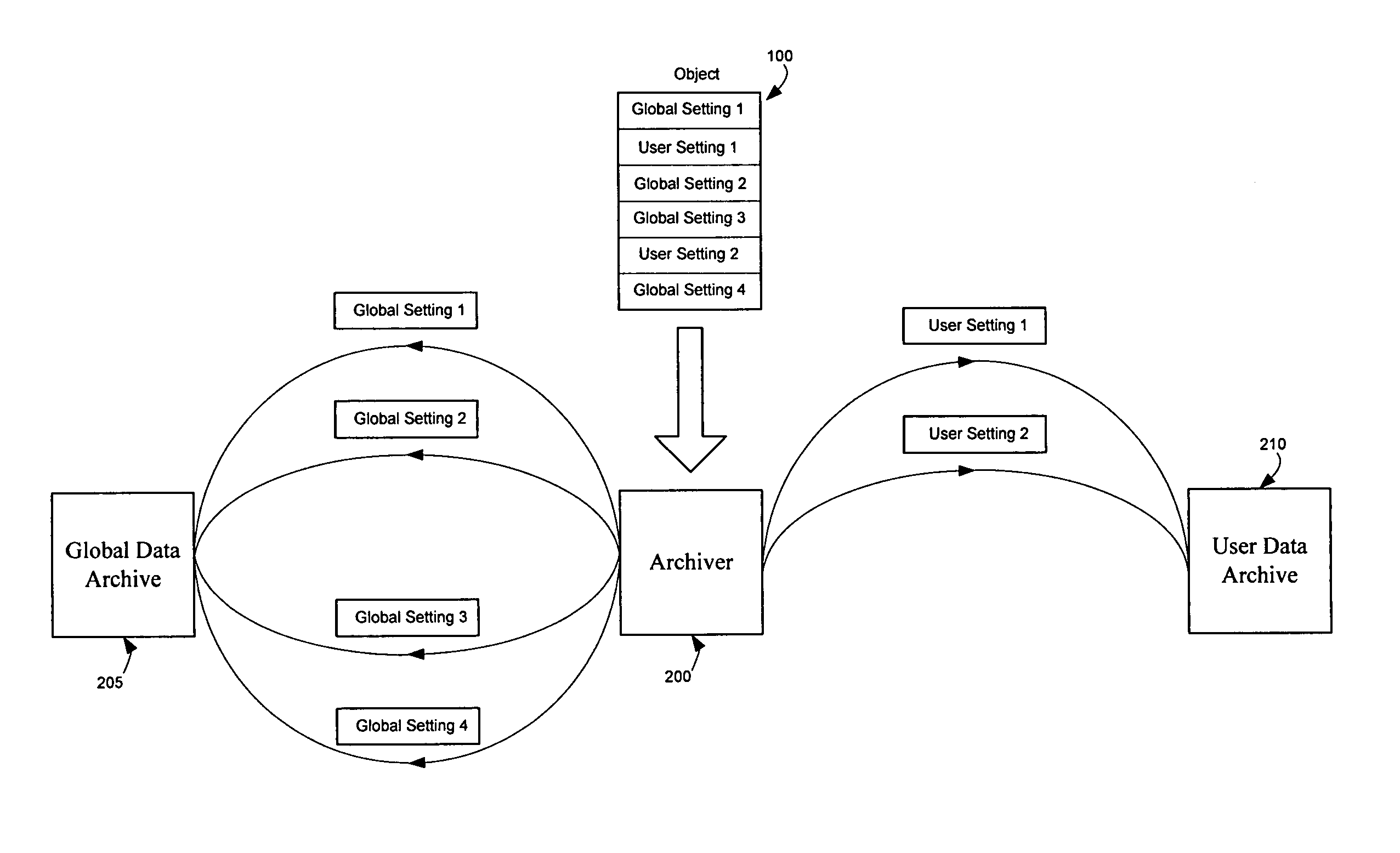
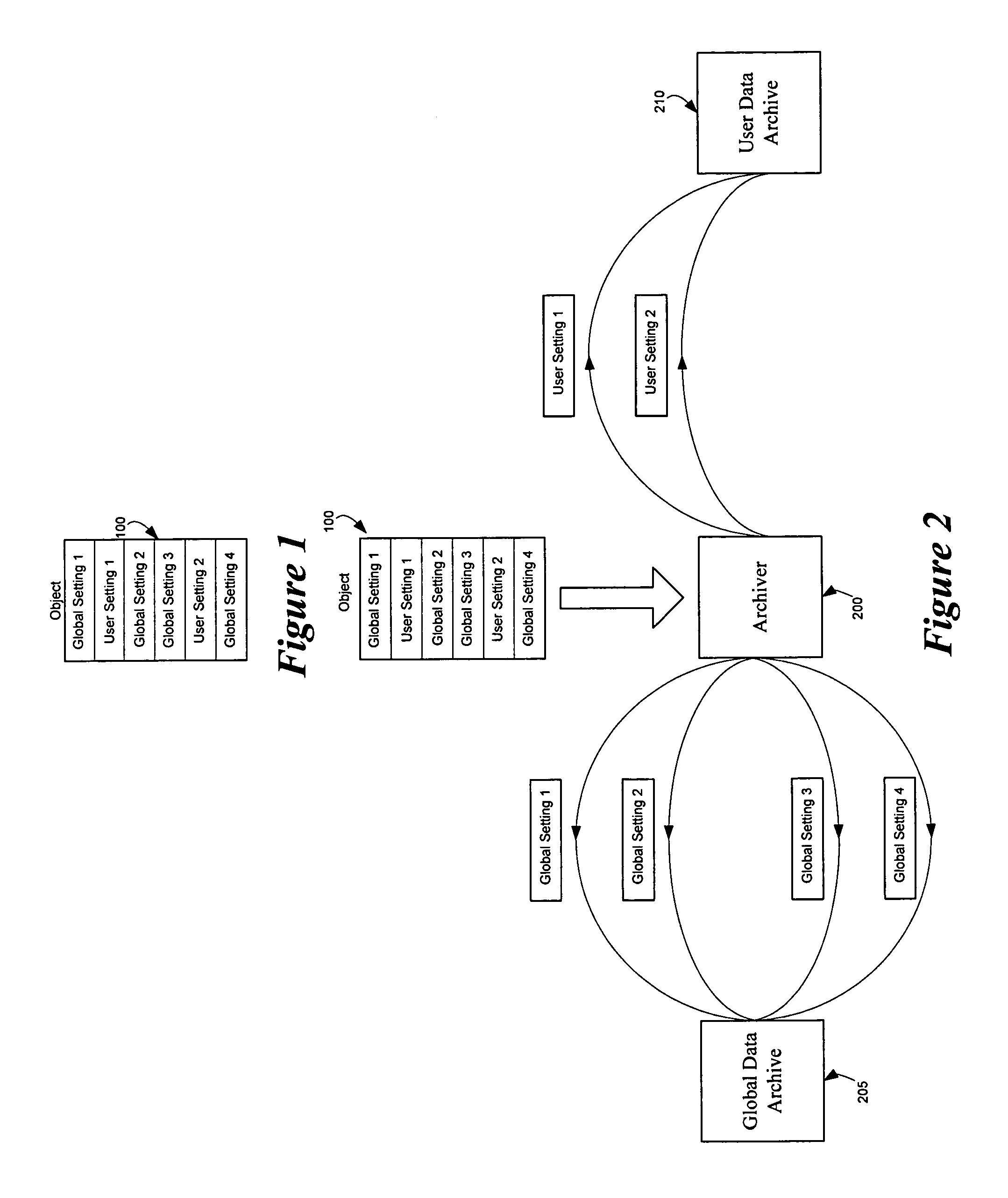
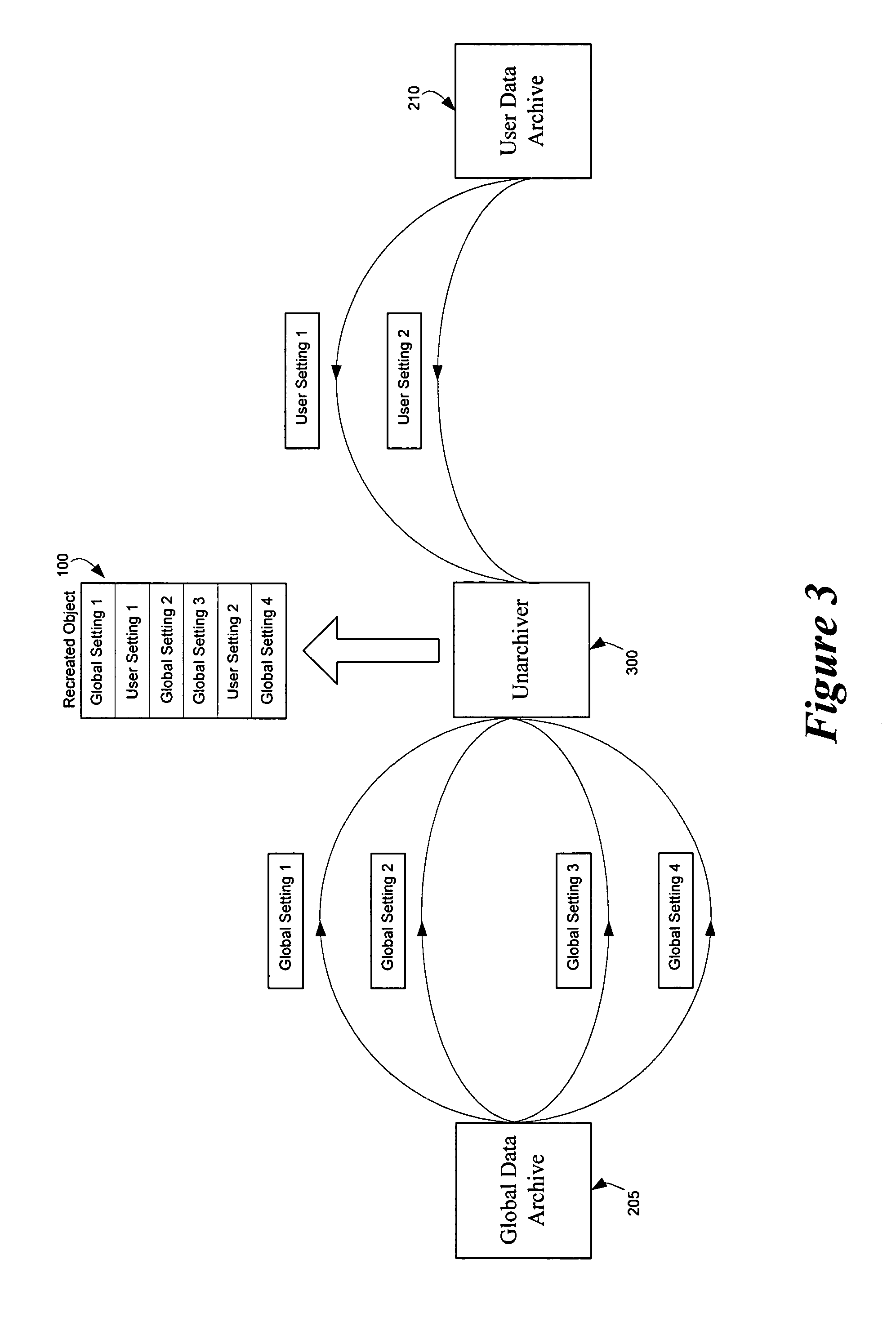
Method and apparatus for archiving and unarchiving objects
InactiveUS7117293B1Data processing applicationsObject oriented databasesMulti user environmentDatabase
Owner:APPLE INC
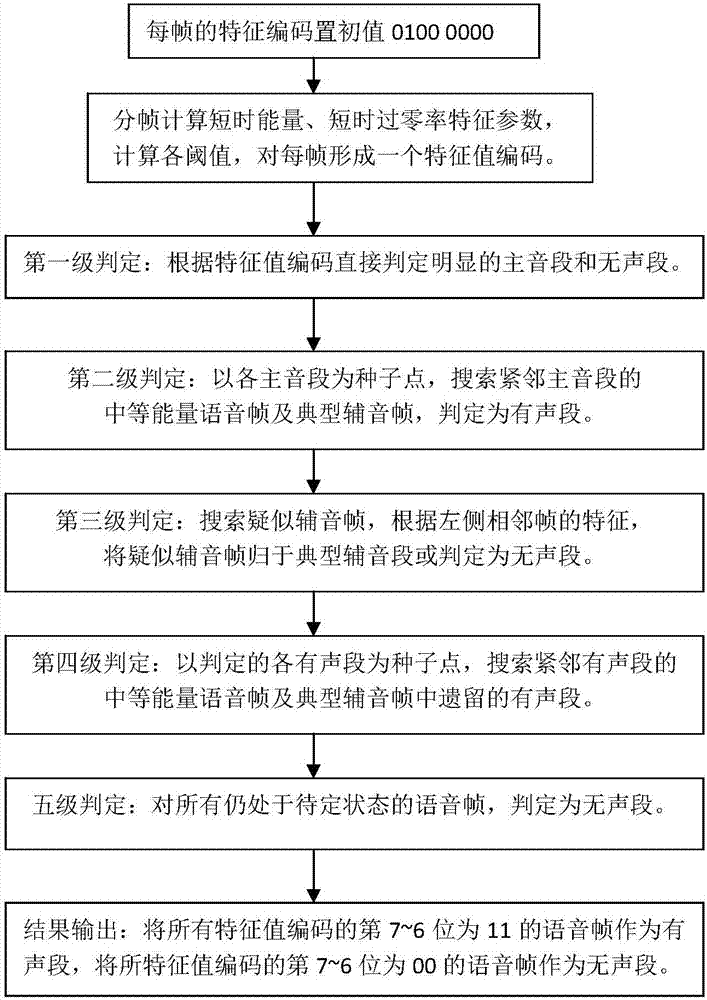
Voice signal endpoint detection method based on characteristic value code
The invention discloses a voice signal endpoint detection method based on a characteristic value code. Characteristic parameters including a short-time energy and a short-time zero-crossing rate are extracted in frames, an average value of the short-time energy, an average value of the short-time zero-crossing rate and a maximal value of the short-time zero-crossing rate are calculated, four thresholds are set for the short-time energy via a statistical result and empirical parameters, one threshold is set for the short-time zero-crossing rate, a voice characteristic is coded according to the thresholds, and endpoint detection is carried out on a voice signal according to five-grade determination rules on the basis of the characteristic value code of each frame. The lowest threshold is set for the short-time energy of an audio segment, suspected voices are accepted / rejected according to the rules by combining characteristics of the adjacent frames, the five-grade determination rules can handle with different complex conditions effectively, false detection and neglected detection are avoided, and the correct rate of endpoint detection of the voice signal can be improved substantially.
Owner:NANJING UNIV OF SCI & TECH
Fast Image Retrieval Method Based on Asymmetric Depth Discrete Hash, Retrieval Model and Model Construction Method
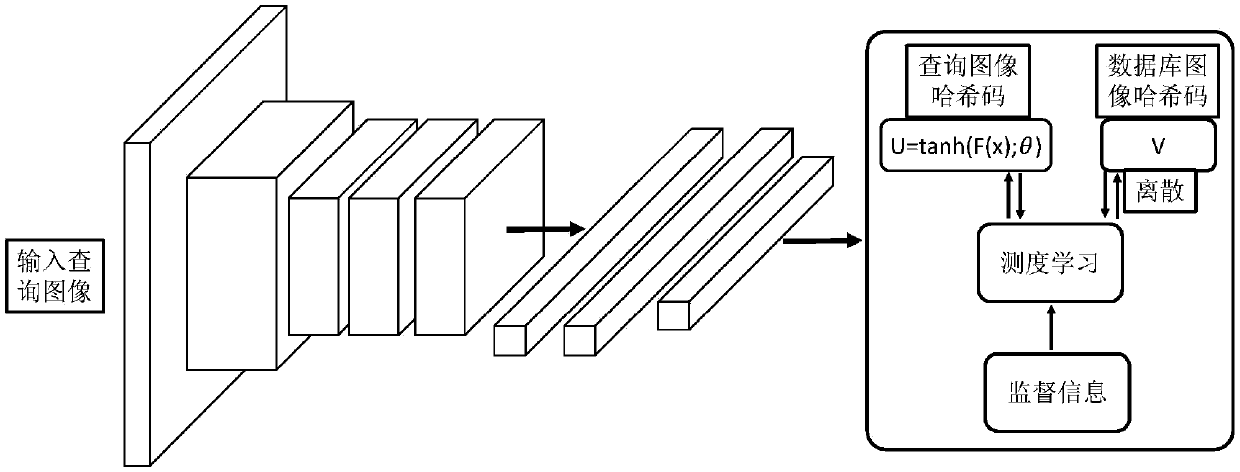
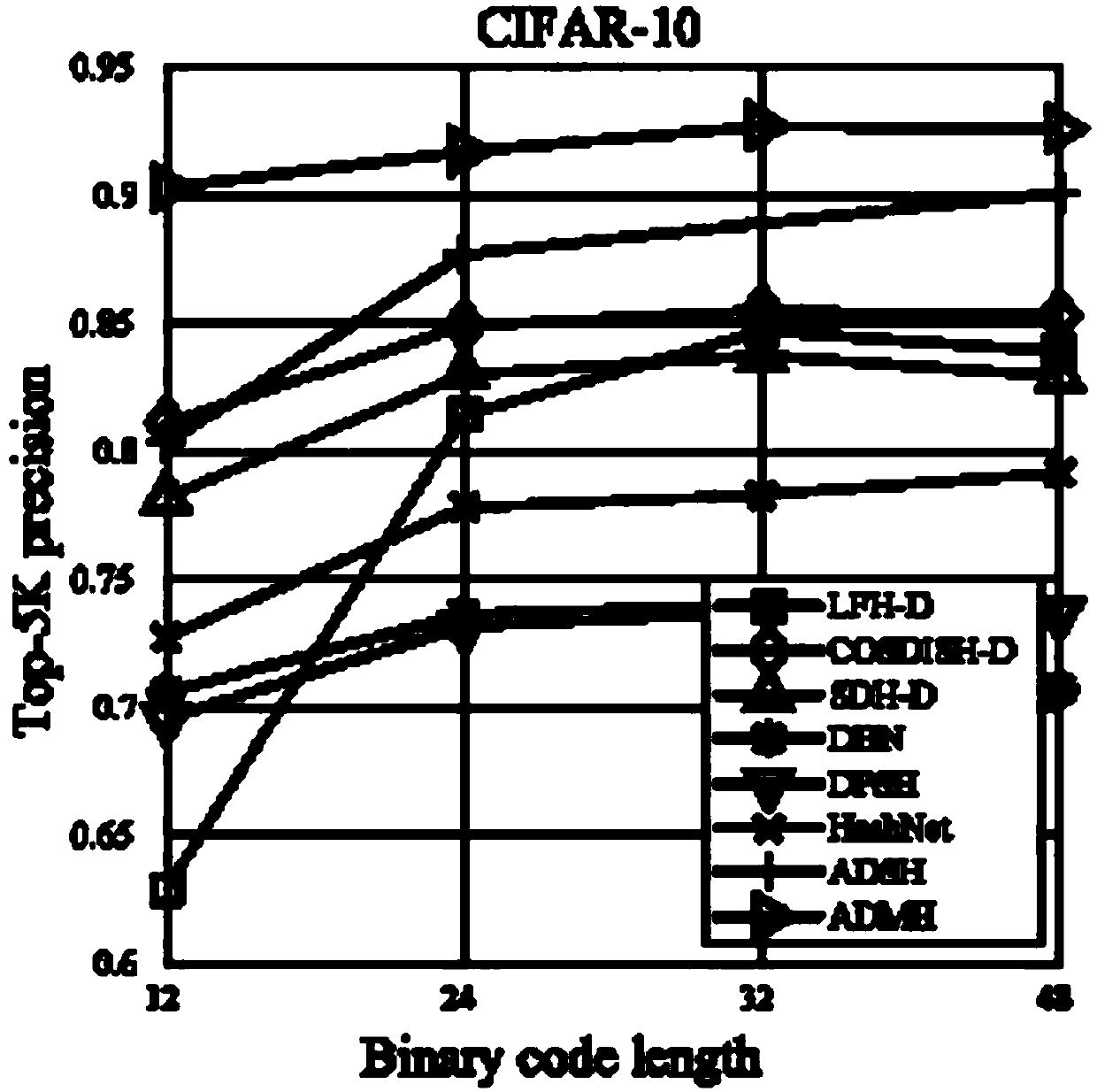
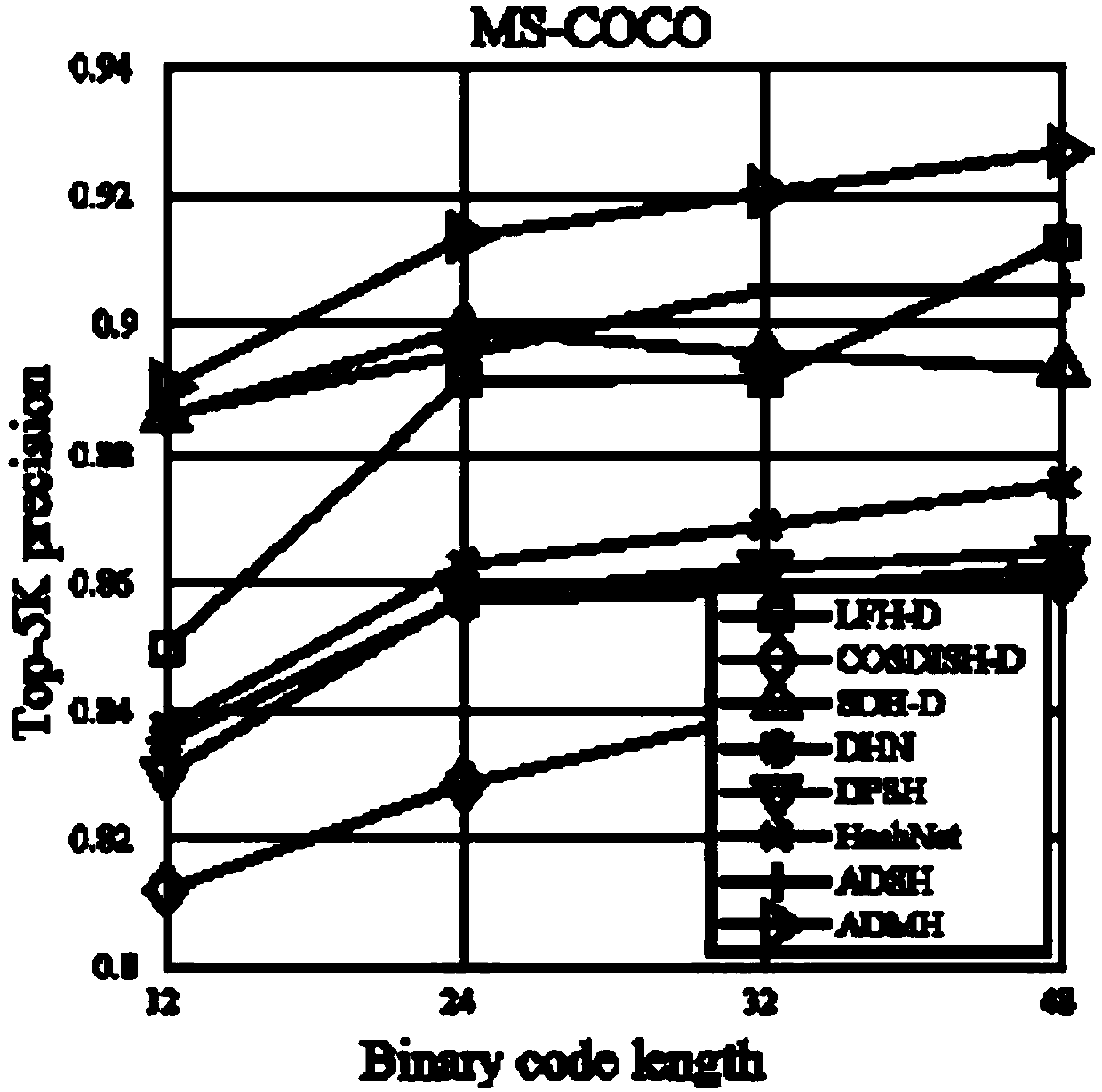
The invention provides a fast image retrieval method based on asymmetric depth discrete hash, a method for constructing a retrieval model and a retrieval model, wherein that scheme of the invention considers the compactness within a class and the separability between the hash codes of a query image and a database image, constructs a measure learning model, and simultaneously learn an approximate binary code of the query image and a discrete hash code of the database image through depth learning and discrete optimization; By constructing an asymmetric hash code learning framework, combining measure learning, depth learning and discrete optimization, a depth convolutional neural network is trained to learn discrete discriminant hash codes for database images and query images. So that the minimum Hamming distance between classes of hash codes is greater than the maximum Hamming distance within the class.
Owner:成都快眼科技有限公司
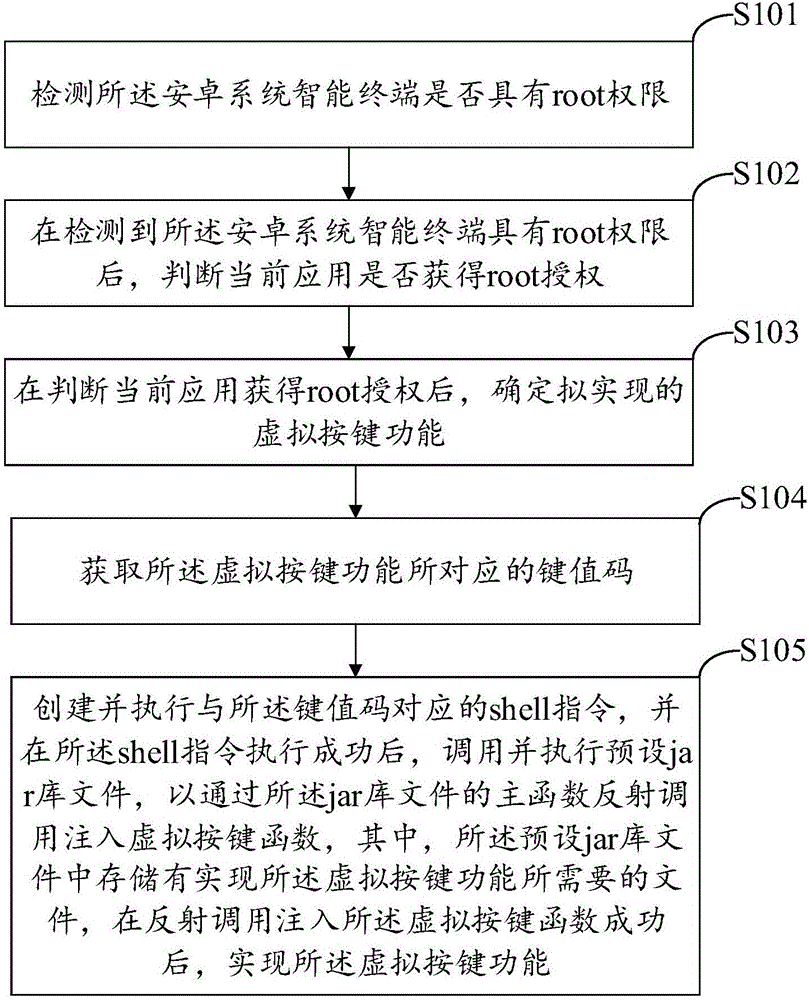
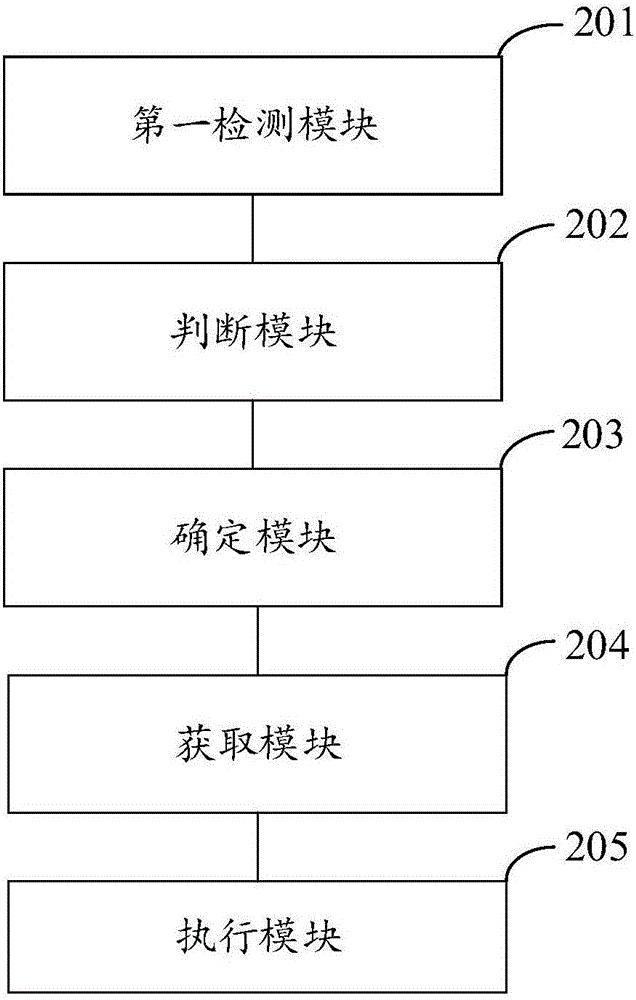
Virtual press key realization method and device of Android system intelligent terminal
ActiveCN106371752AProtect physical buttonsEasy to implementProgram controlInput/output processes for data processingComputer hardwareValue code
The invention discloses a virtual press key realization method and device of an Android system intelligent terminal. The method comprises the following steps of detecting whether the Android system intelligent terminal has the root authority or not; when the condition that the Android system intelligent terminal has the root authority is detected, judging whether the current application obtains the root authority or not; after the condition that the current application obtains the root authority is judged, determining the virtual press key function to be realized; obtaining key value code corresponding to the virtual press key function; creating and executing a shell instruction corresponding to the key value code; after the shell instruction is successfully executed, calling and executing the preset jar base file so as to perform reflection calling of an injection virtual press key function through the main function of the jar base file, wherein the jar base file stores files required for realizing the virtual press key functions; after the reflection calling of the injection virtual press key function is successful, realizing the virtual press key function. The method has the advantages that the virtual press key functions can be conveniently realized; low cost, flexibility and reliability are realized.
Owner:竞技世界(北京)网络技术有限公司
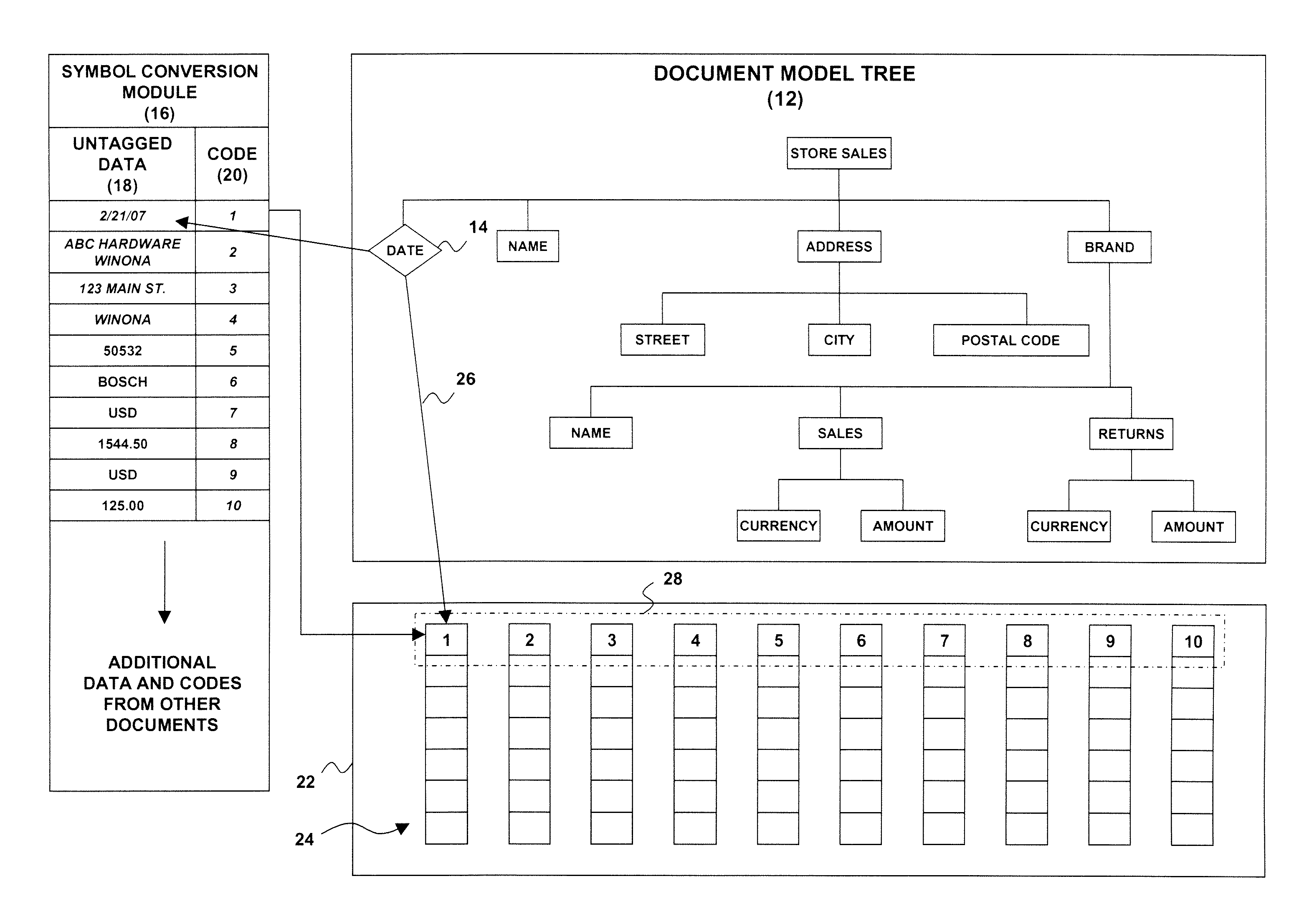
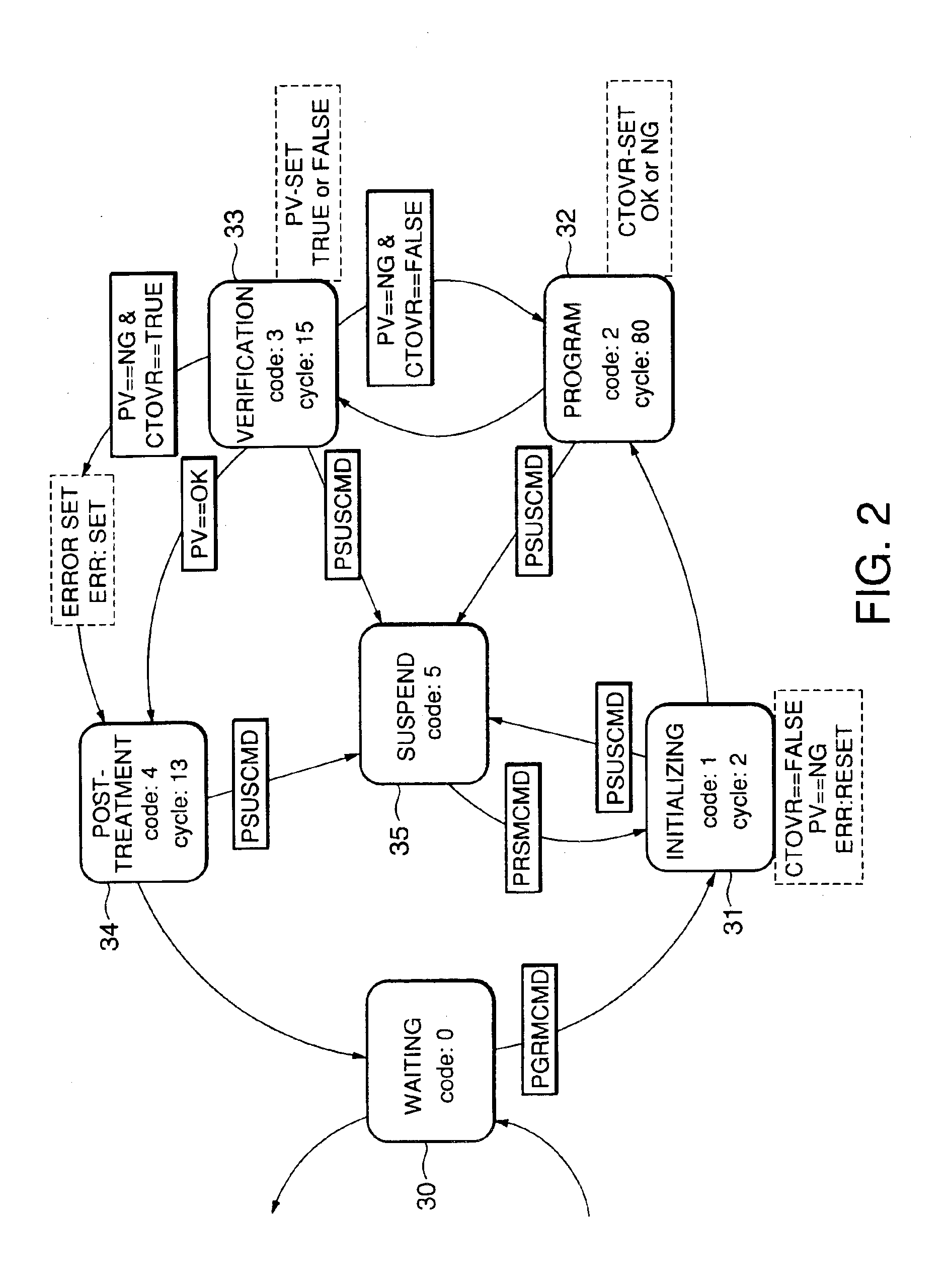
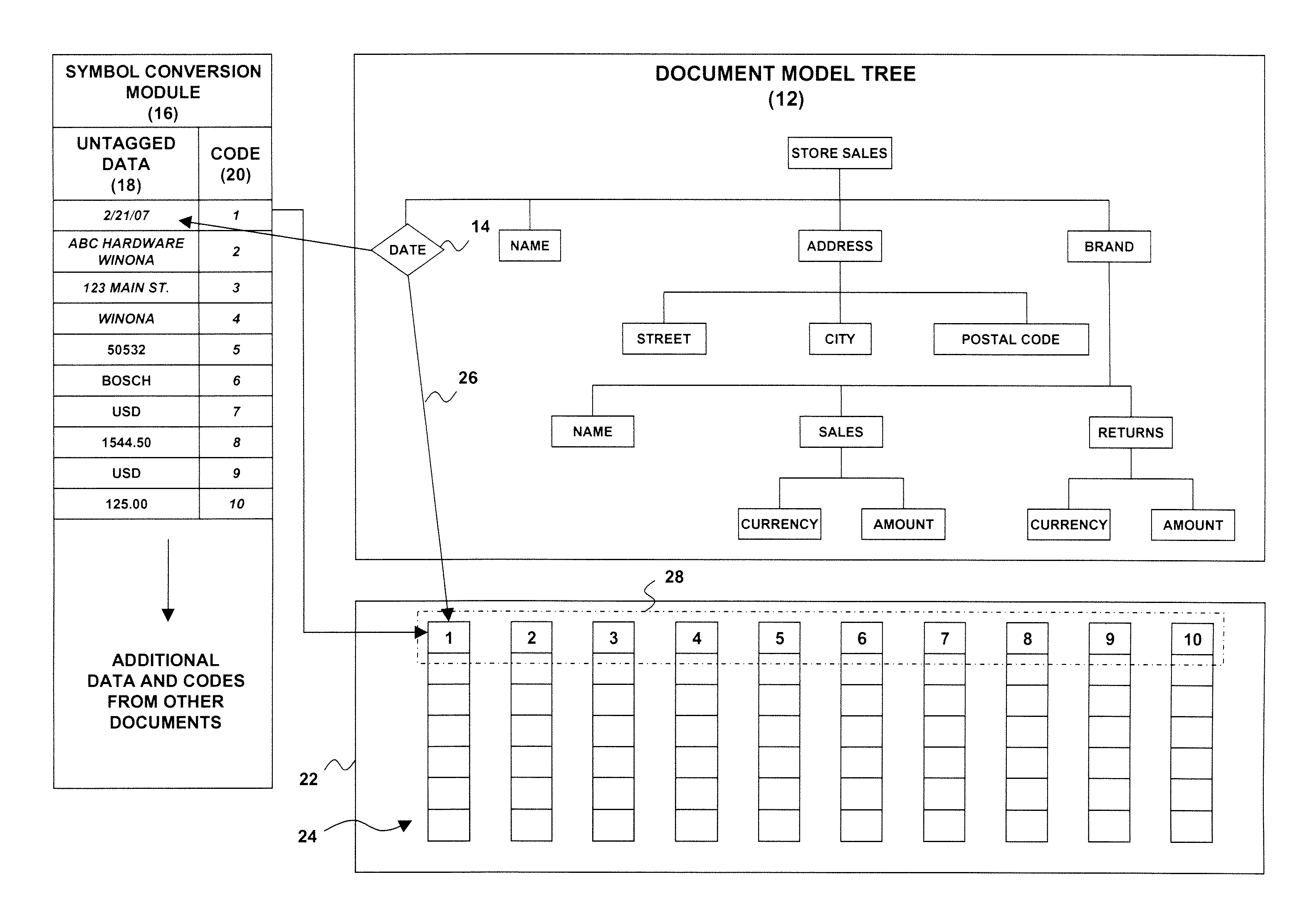
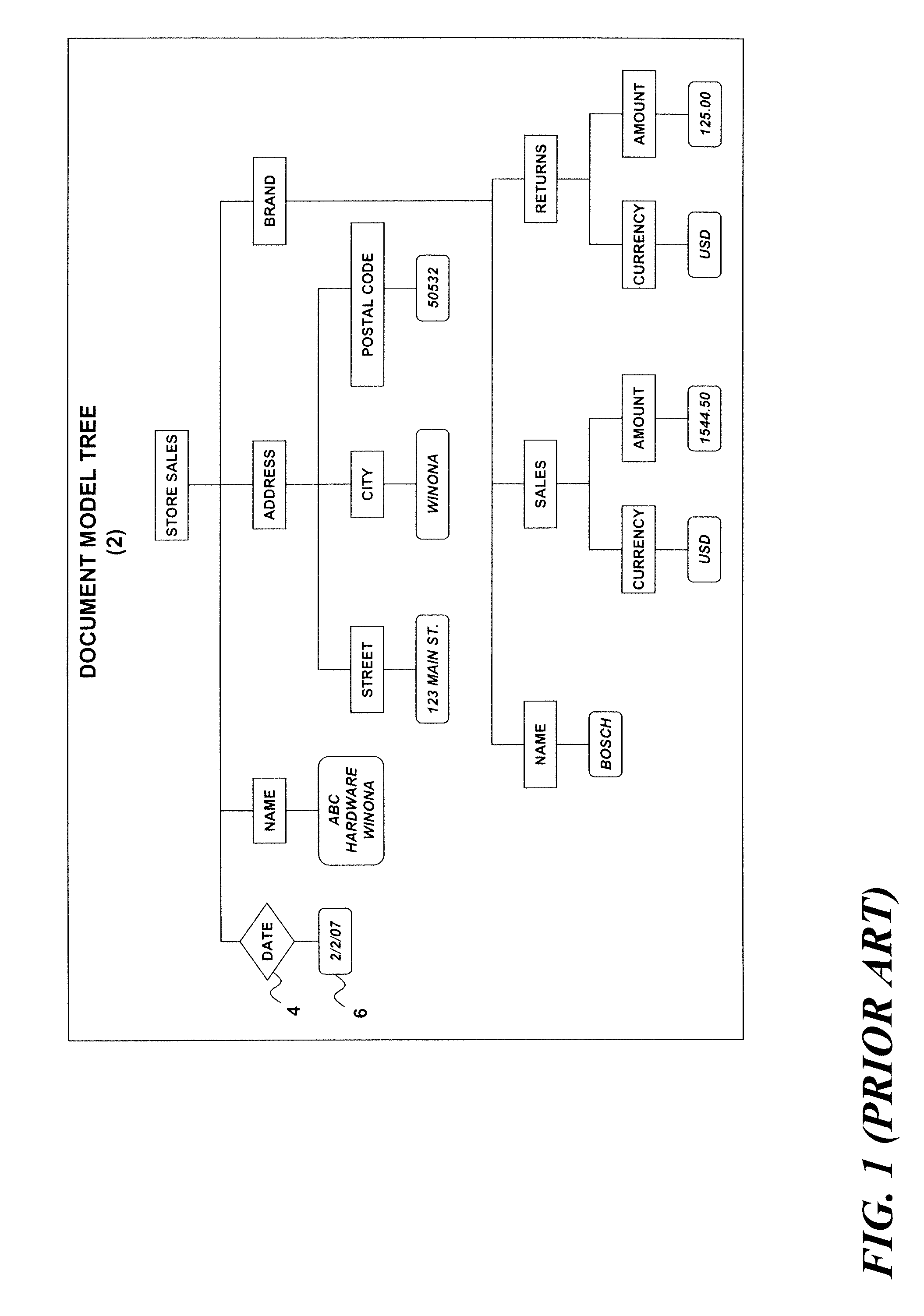
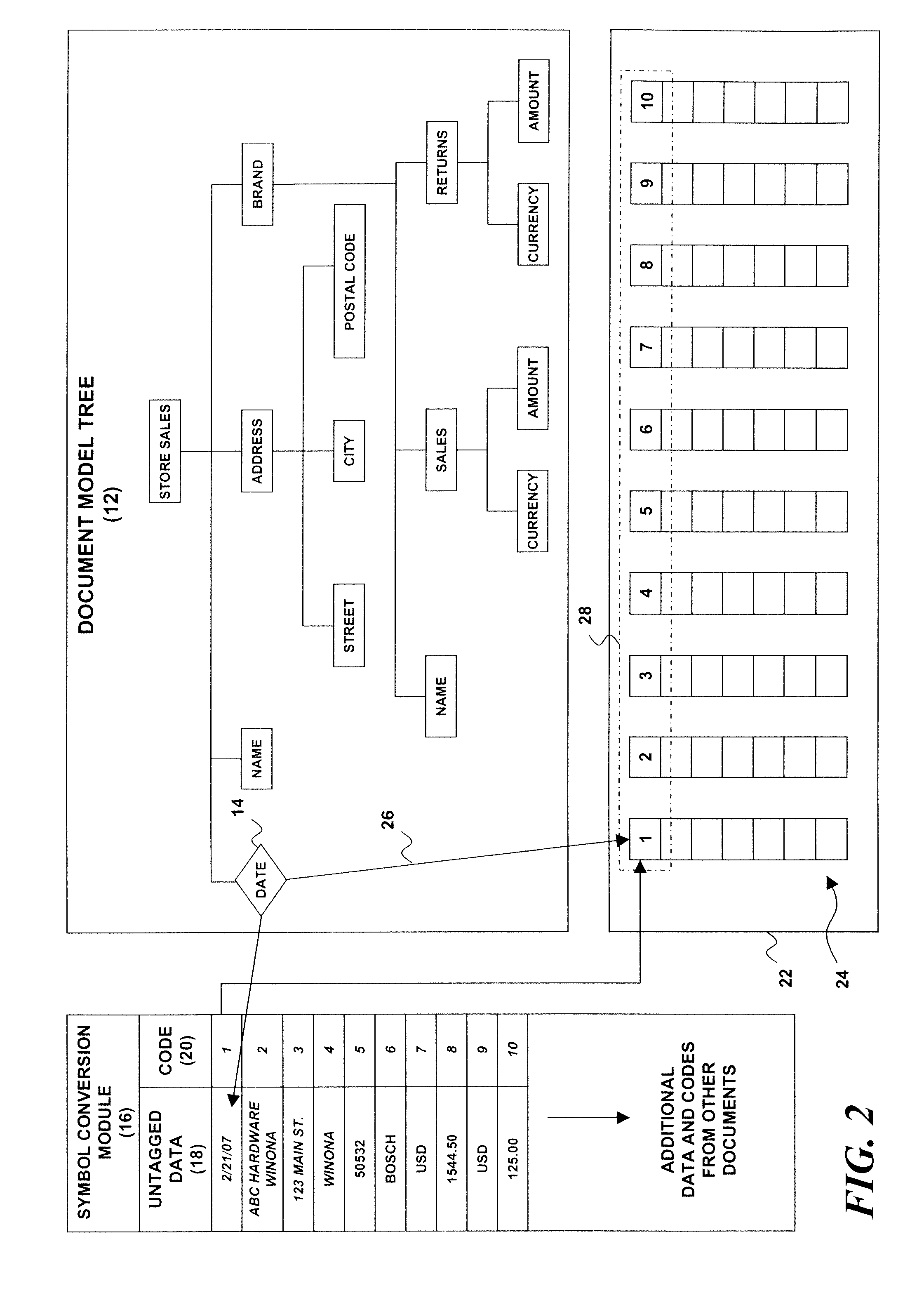
System and method for storage, management and automatic indexing of structured documents
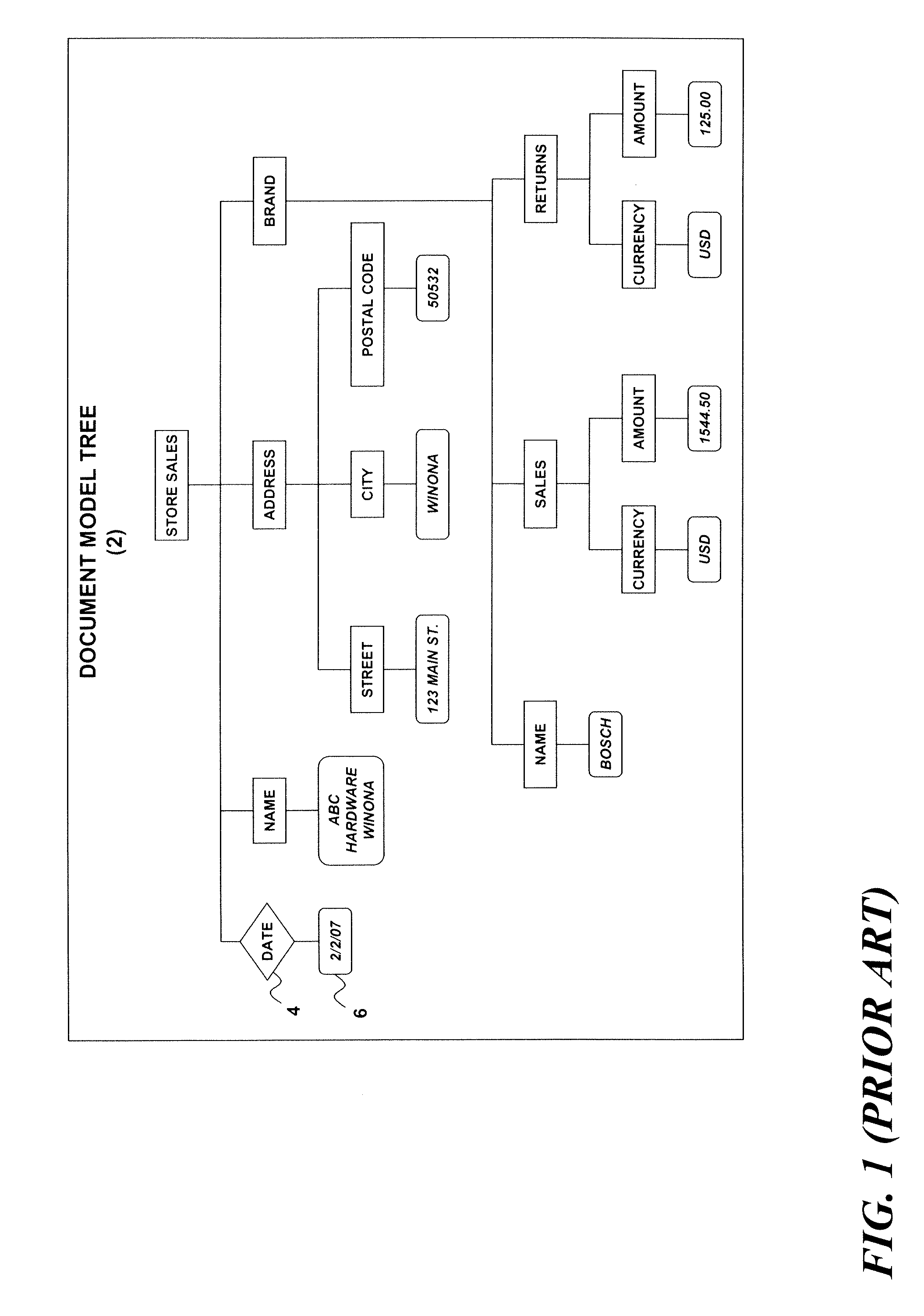
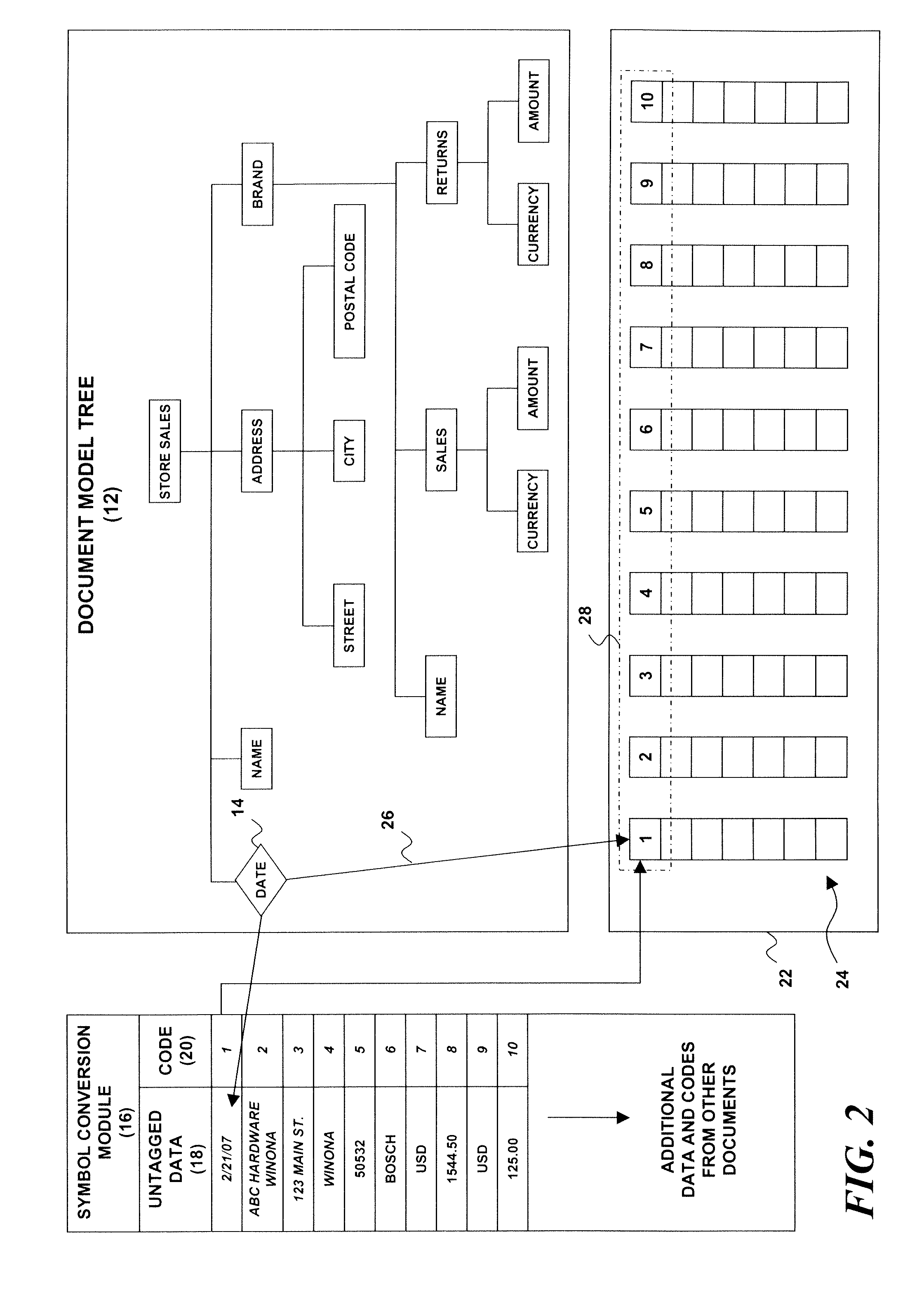
InactiveUS20090077009A1Digital data information retrievalDigital data processing detailsAutomatic indexingDocument model
A structured document storage and management technique utilizes a generic document model tree that contains structured document nodes. A symbol conversion module contains untagged data associated with one or more of the structured document nodes and with a corresponding number of value codes. An encoded vector set includes a set of encoded vectors corresponding to the one or more structured document nodes having associated untagged data. Each of the encoded vectors contains one of the value codes at an index position that corresponds to a particular structured document.
Owner:LINKEDIN
Image coding apparatus, method for coding image, program therefor, image decoding apparatus, method for decoding image, and program therefor
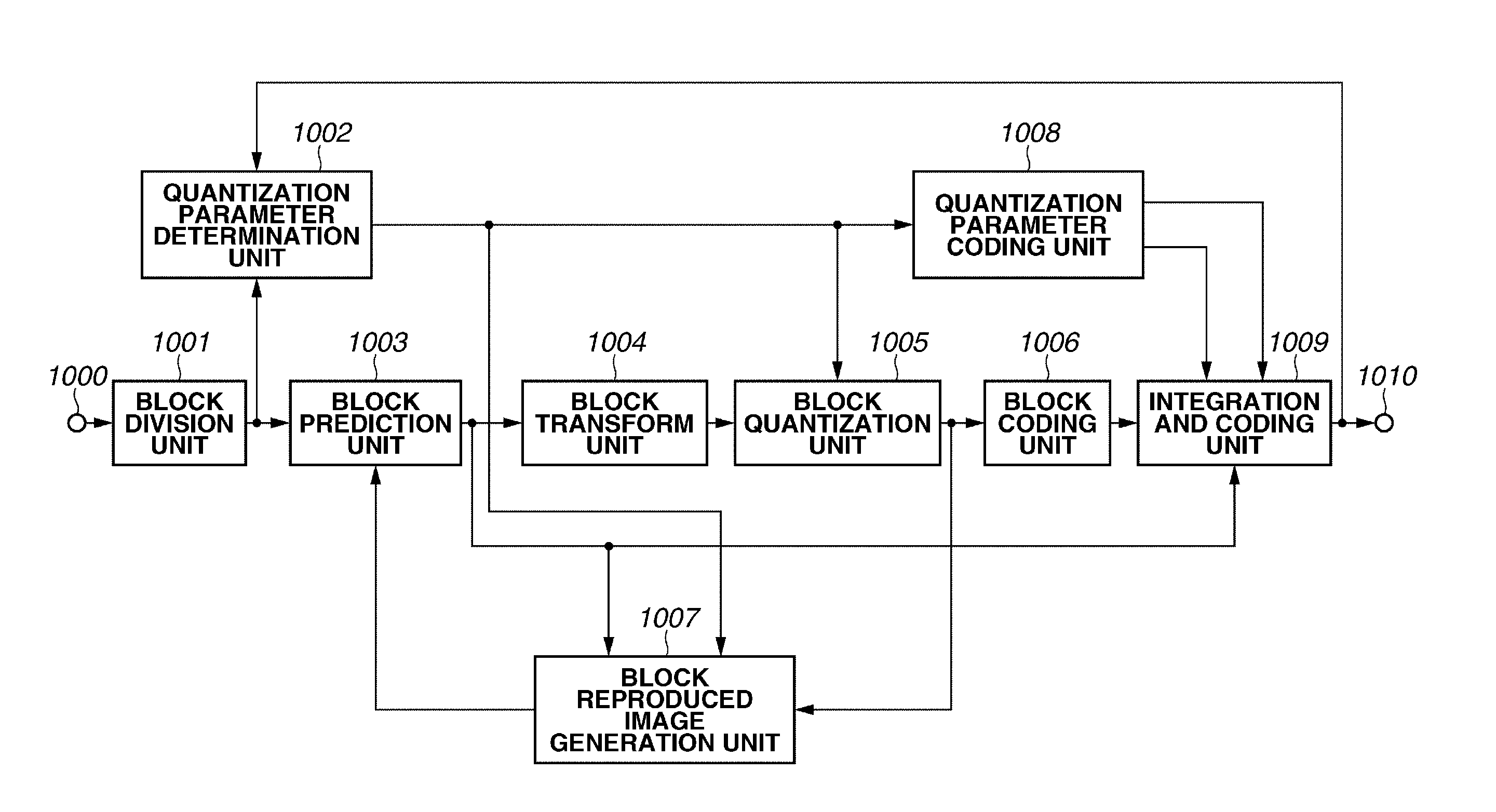
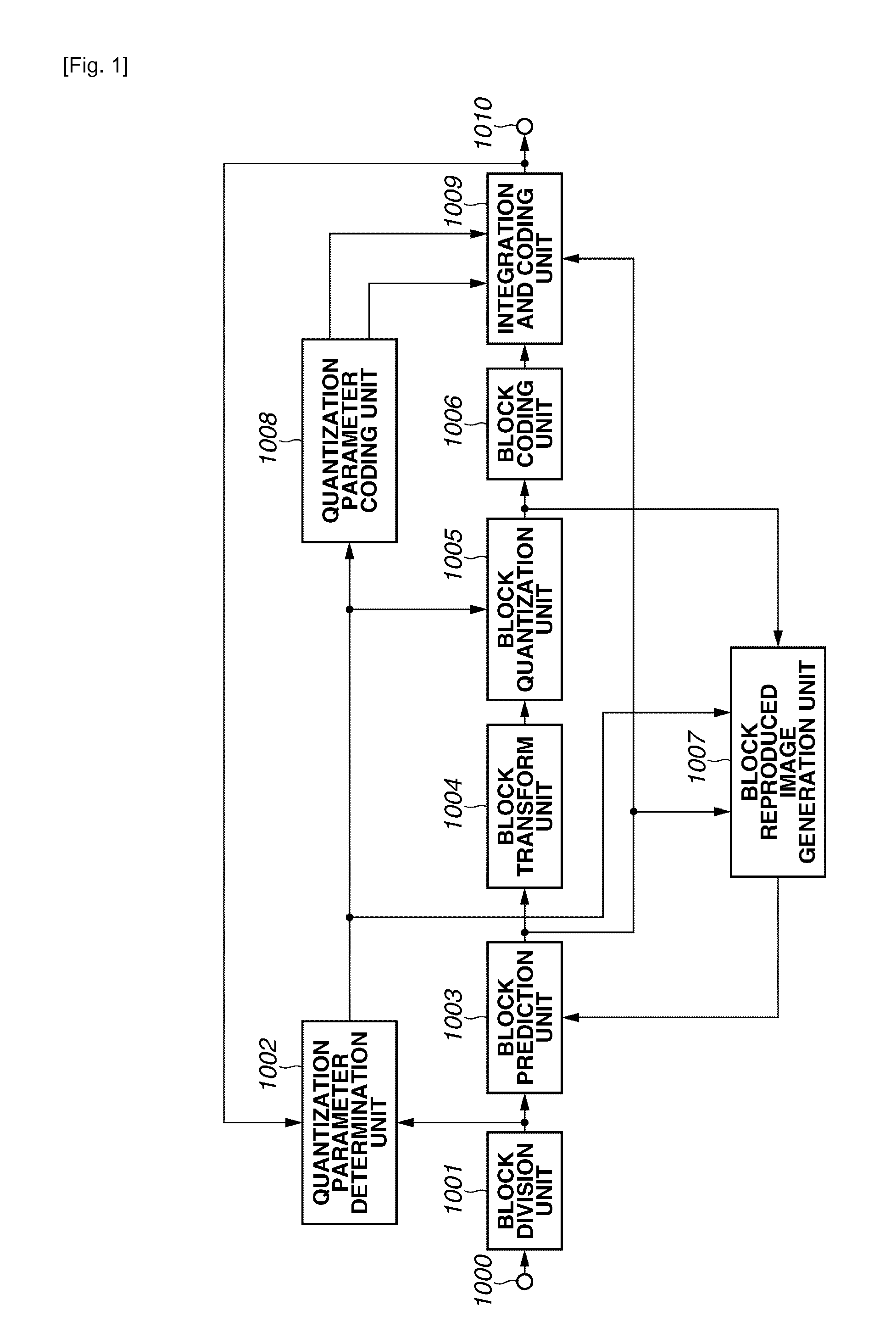
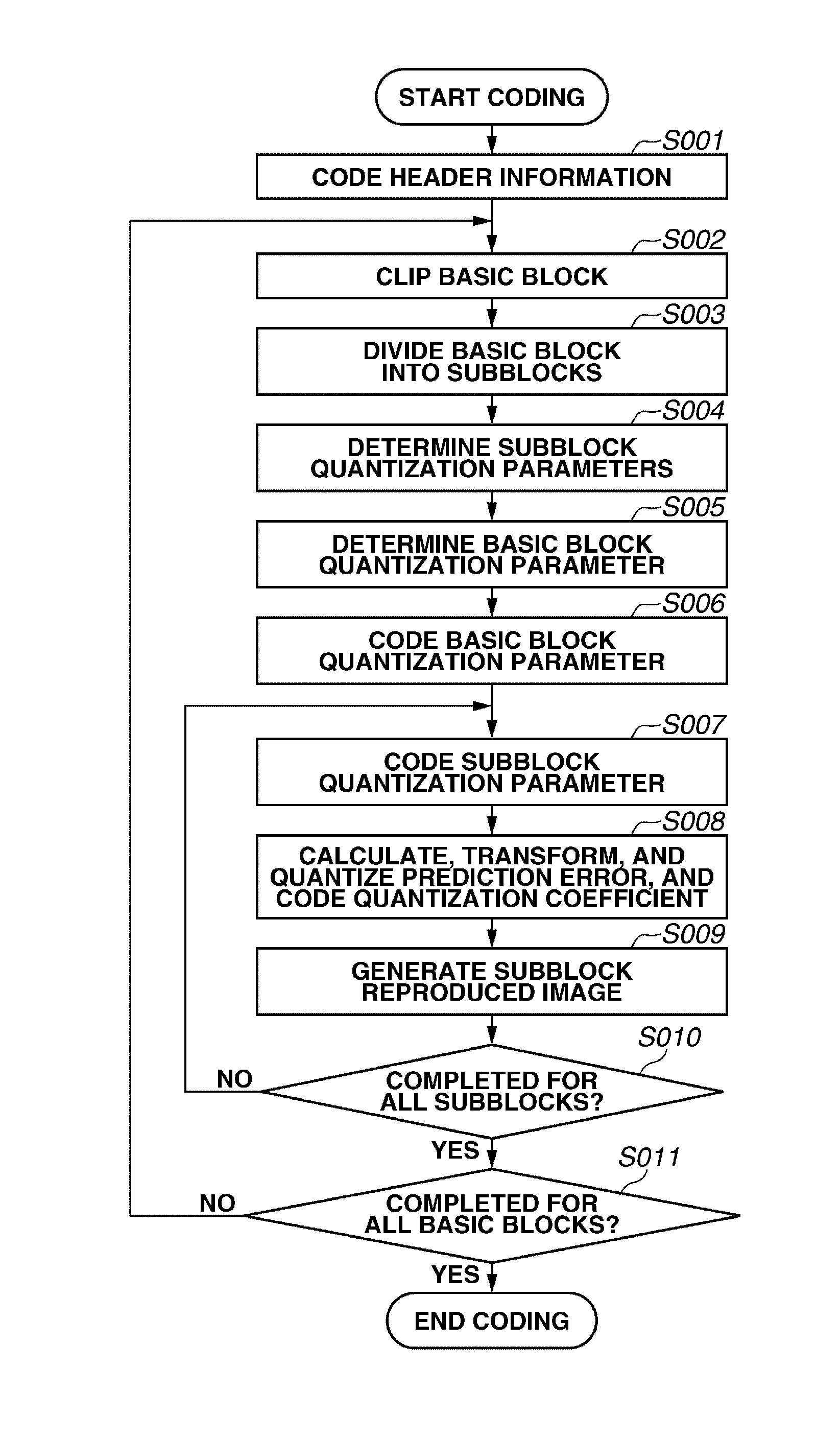
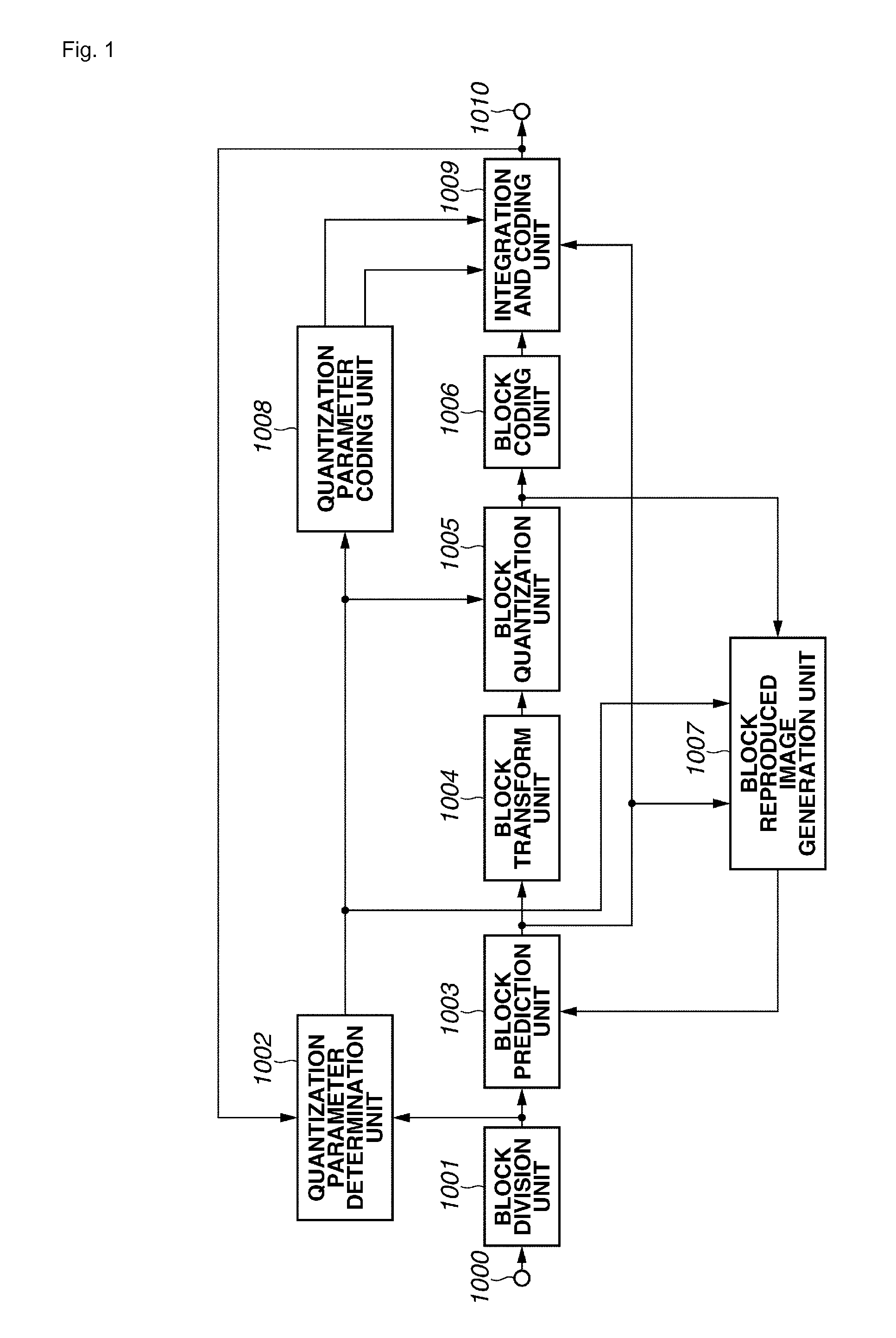
ActiveUS20130343665A1High speed machiningEase of parallel processingCharacter and pattern recognitionTelevision systemsImaging processingBasic block
An image processing apparatus includes a division unit configured to divide an input image into a plurality of subblocks subjected to quantization control a subblock quantization parameter calculation unit configured to calculate a quantization parameter of each of the subblocks, a basic block quantization parameter calculation unit configured to set a basic block including at least two subblocks and to calculate a quantization parameter of the basic block, a difference value calculation unit configured to calculate a difference value between the quantization parameter of the basic block and the quantization parameter of each subblock included in the basic block, and a difference value coding unit configured to code the difference value.
Owner:CANON KK
Method and system for extracting facial features
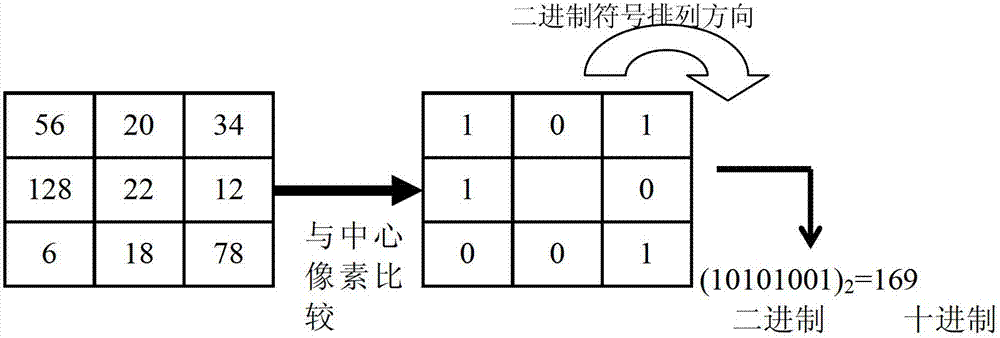
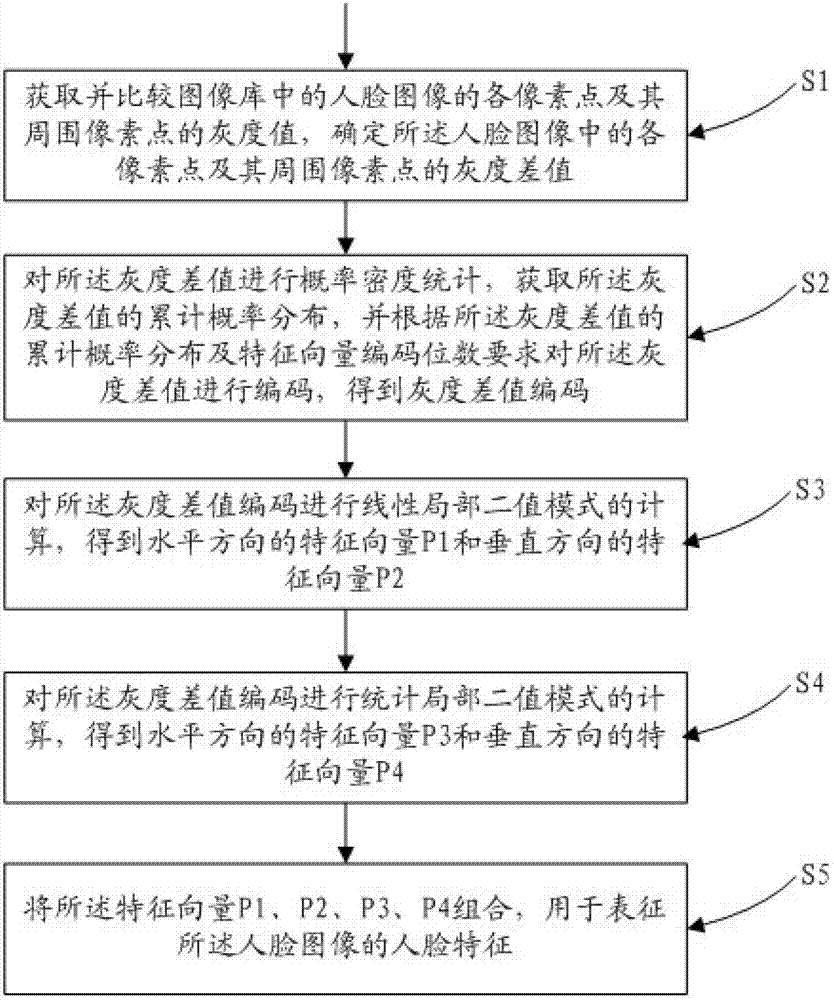
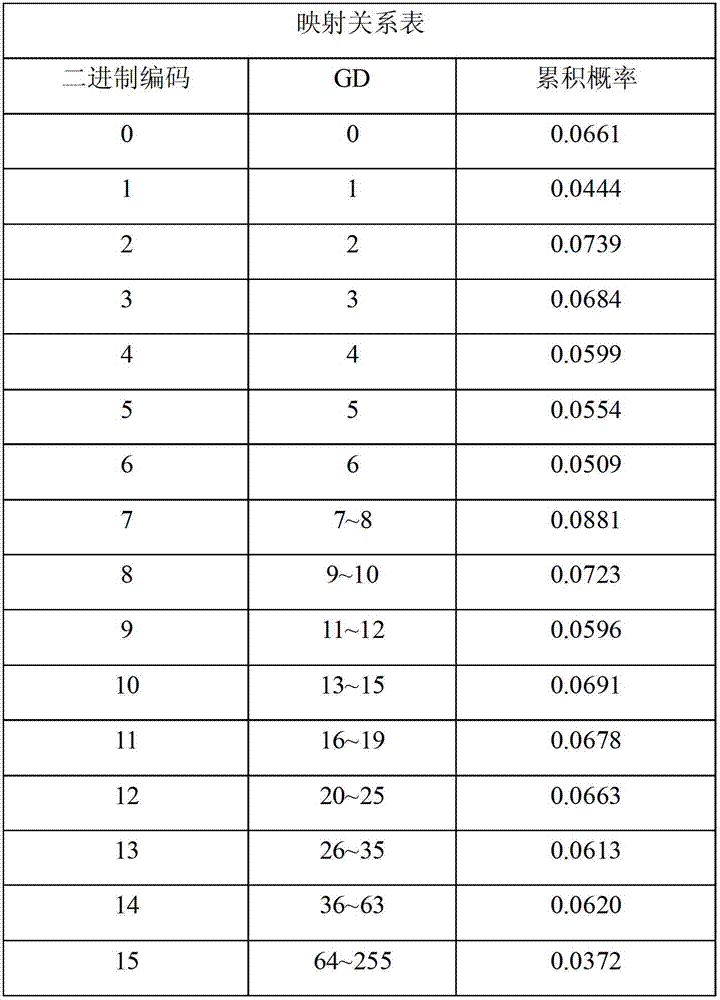
InactiveCN102880870AMeet the calculation speedMeet computing requirementsCharacter and pattern recognitionFeature vectorPerpendicular direction
The invention provides a method and a system for extracting facial features. The method comprises the following steps of: 1, acquiring and comparing grayscale values of each pixel of a facial image and surrounding pixels in an image library, and determining grayscale difference values between the pixels and the surrounding pixels in the facial image; 2, performing probability density statistics on the grayscale difference values to obtain the accumulated probability distribution of the grayscale difference values, and encoding the grayscale difference values according to the accumulated probability distribution of the grayscale difference values and a requirement for the number of feature vector encoding bits to obtain grayscale difference value codes; 3, performing computation on the grayscale difference value codes in a linear local binary mode to obtain a feature vector P1 in a horizontal direction and a feature vector P2 in a perpendicular direction; 4, performing computation on the grayscale difference value codes on a statistical local binary mode to obtain a feature vector P3 in the horizontal direction and a feature vector P4 in the perpendicular direction; and 5, combining the feature vectors P1, P2, P3 and P4 to represent the facial features of the facial image.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
Device for simulating thermistor type temperature sensor
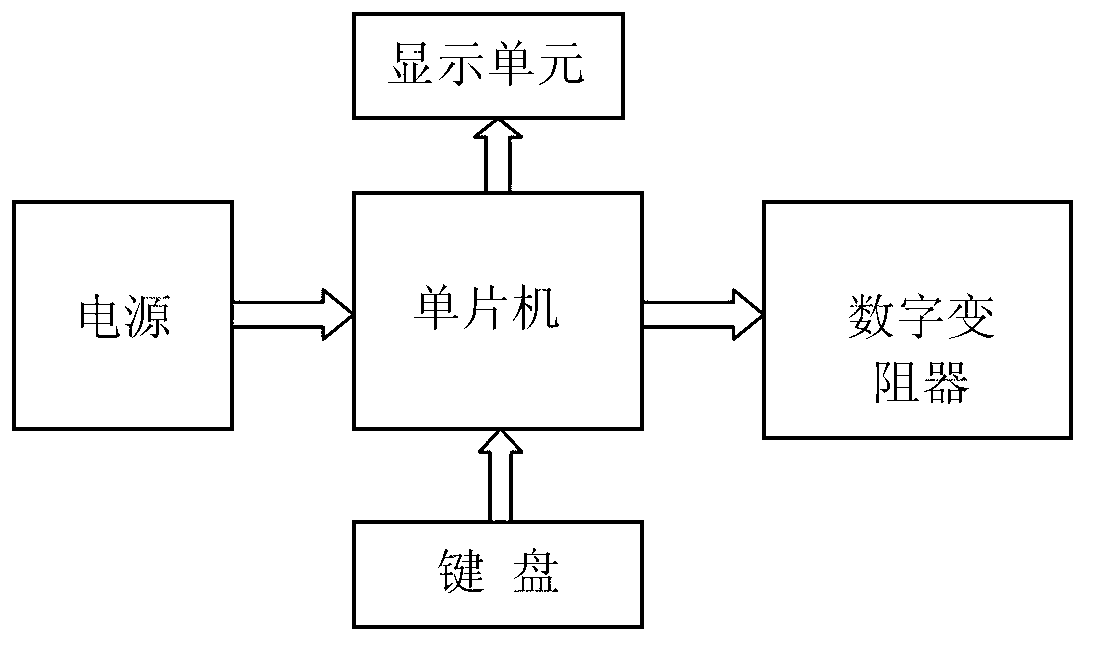
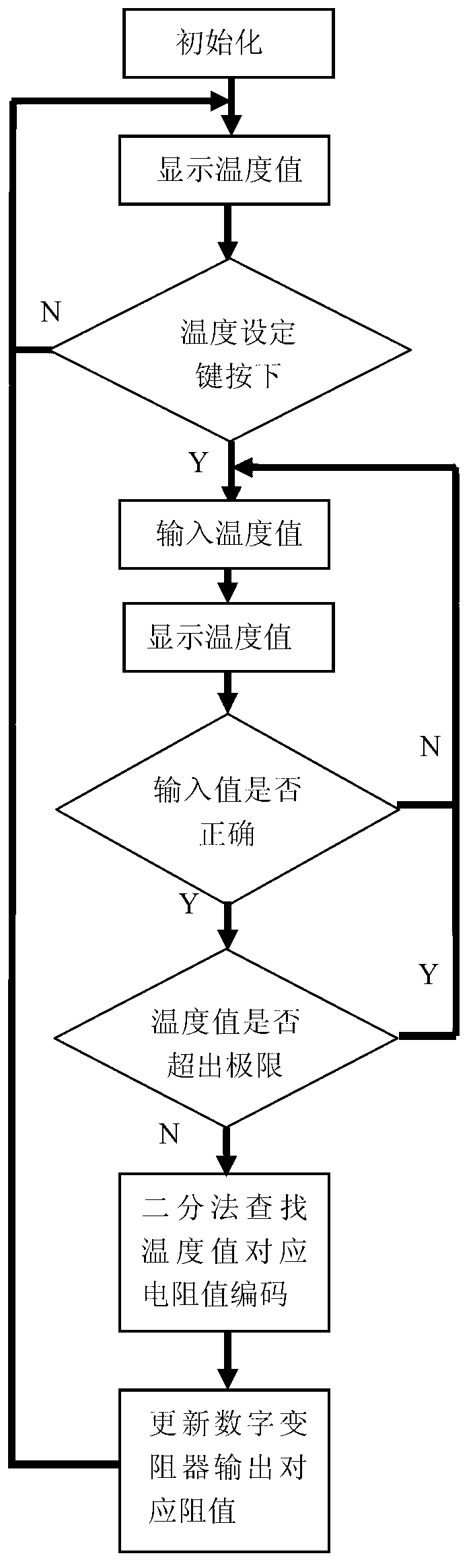
InactiveCN103177641AHigh precisionSolution to short lifeEducational modelsElectrical resistance and conductanceThermistor
The invention relates to a simulating device, particularly to a device for simulating a thermistor type temperature sensor. The device for simulating the thermistor type temperature sensor comprises a power supply, a processing module, an input module, a display module and a digital rheostat, wherein the power supply is respectively connected with the processing module, the input module and the display module; the processing module is respectively connected with the input module, the display module and the digital rheostat; the input module is used for inputting a temperature value; and the processing module controls the display module according to the received temperature value to display the temperature value and processes the temperature value to obtain a resistance value code corresponding to the temperature value, and the digital rheostat is controlled through the code to output the resistance value. The device has the characteristics of high precision, long service life, convenience and simplicity in operation and also has the advantages of small size, light weight, convenience in carrying, and good expandability. The device is especially suitable for simulating the thermistor type temperature sensor.
Owner:SICHUAN CHANGHONG ELECTRIC CO LTD
Integrated intelligent variable capacitor
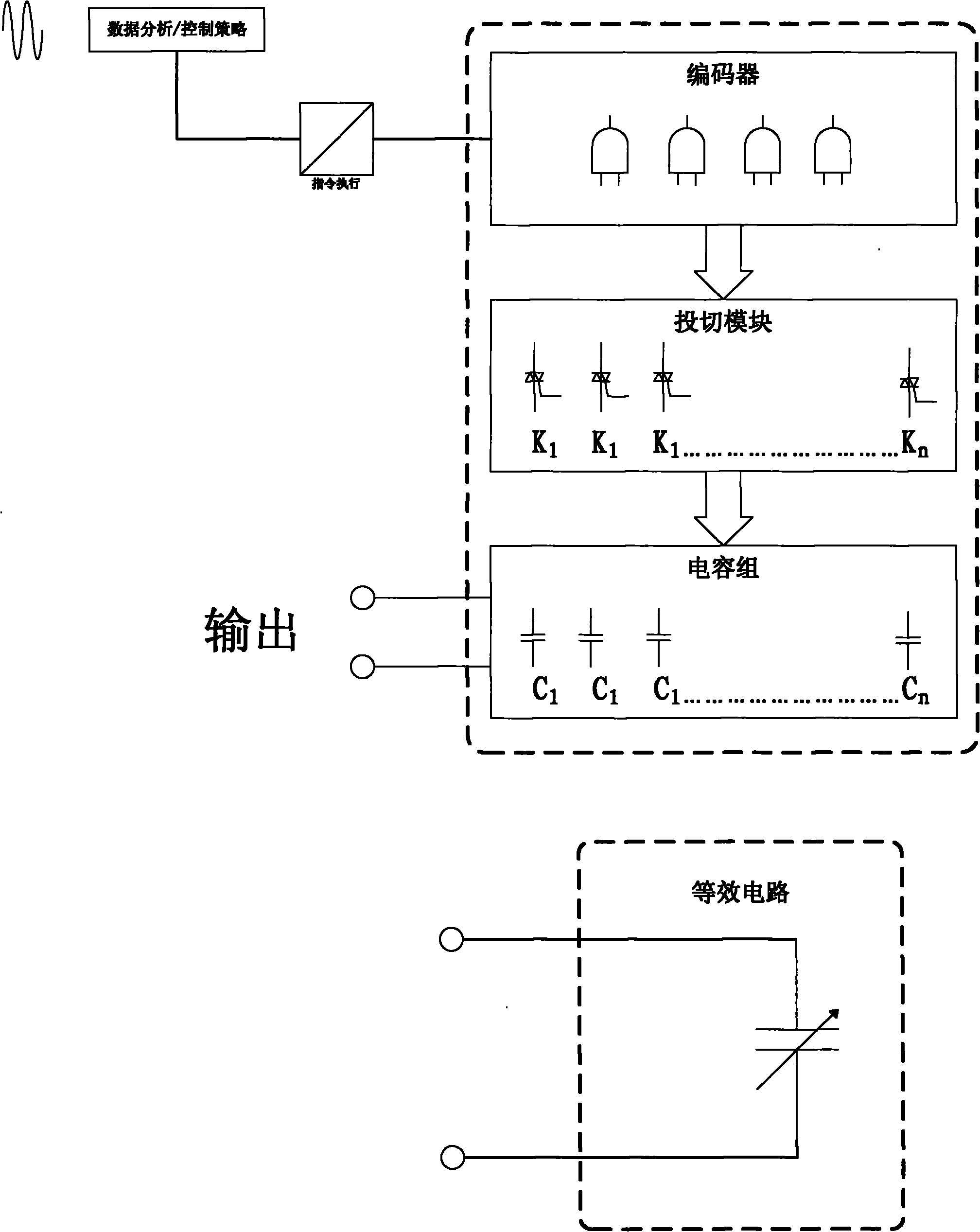
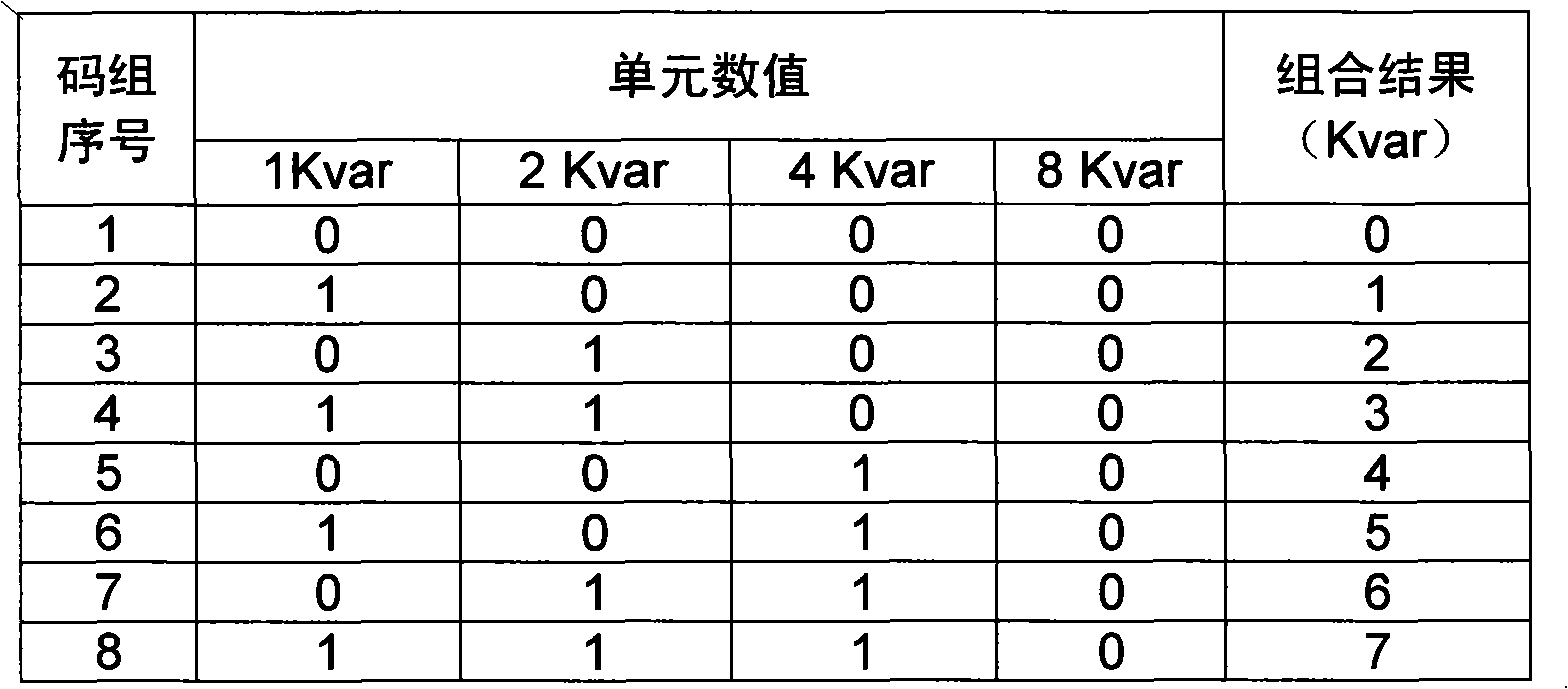
InactiveCN102013686AAchieve replaceable workAvoid heat damageReactive power adjustment/elimination/compensationReactive power compensationCapacitanceControl system
The invention discloses an integrated intelligent variable capacitor, which comprises a shell and a capacitor bank arranged in the shell. The integrated intelligent variable capacitor is characterized in that: the capacitor bank comprises a plurality of basic capacitor units, wherein the minimum capacitance value in the basic capacitor units is used as a base number, and the multiplying power of the capacitance value of each basic capacitor unit relative to the base number corresponds to a digital value with bit right in a numerical value coding system; and the capacitor bank is provided with a control system and a switching mechanism, wherein the control system comprises a control signal receiving device and a coding scheme generating device, and the coding scheme generating device generates a code according to the control signal received by the control signal receiving device to control the operation of the switching mechanism and realize output of capacitance values. Adjustment of random precision and random range of the capacitor can be realized, and the capacitor can be conveniently manufactured into nominal series products and products of special specifications customized according to special requirements.
Owner:SUZHOU DINGAN ELECTRONICS TECH
Self-discharge screening method for improving matching consistency of lithium ion batteries
InactiveCN109482521AFully self-dischargedAccurate measurementSortingElectrical batteryScreening method
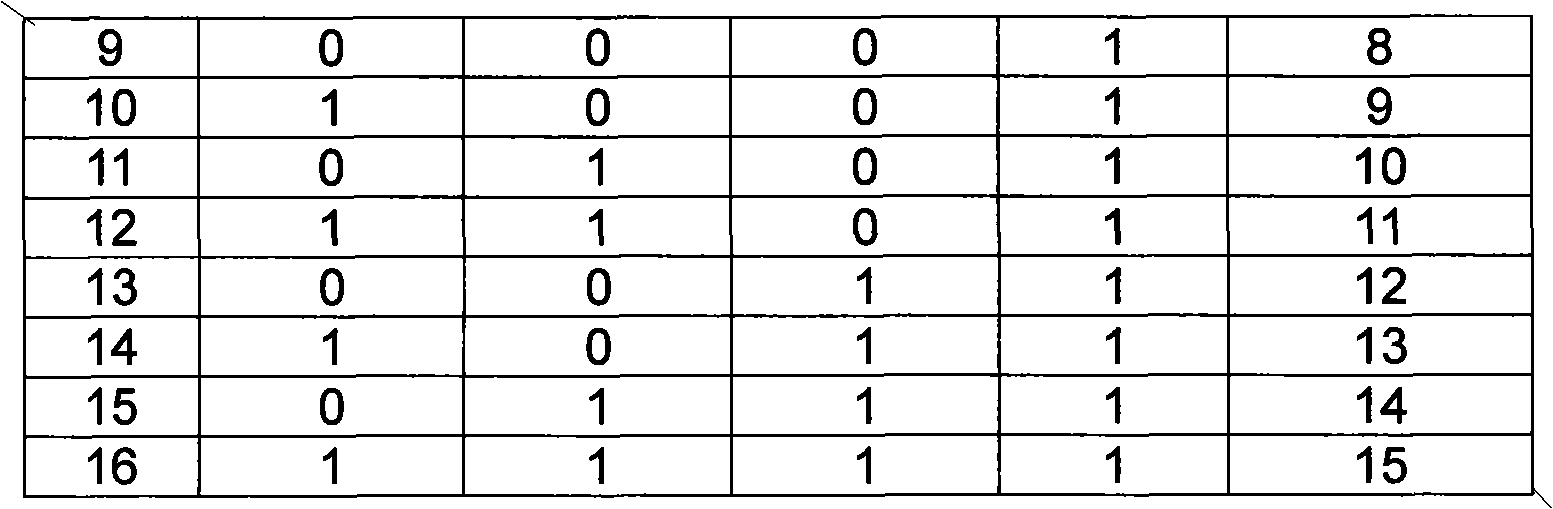
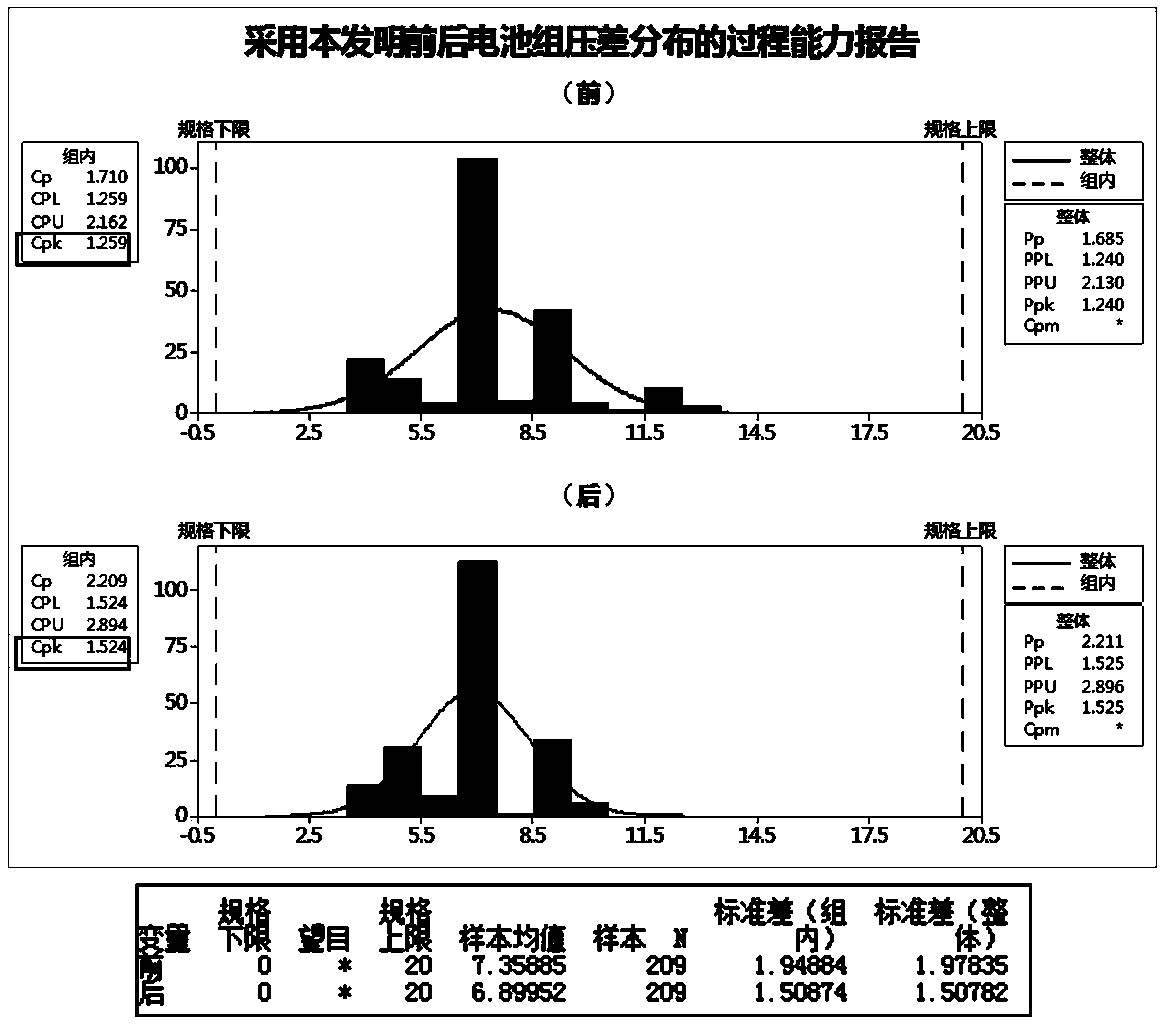
The invention discloses a self-discharge screening method for improving the matching consistency of lithium ion batteries. The self-discharge screening method for improving the matching consistency ofthe lithium ion batteries comprises the following steps that after the same batch of batteries are subjected to conventional capacity grading, 5-20% SOC state-of-charge electric quantity is charged in a 4-6A current constant current charging mode. After the batteries are put on hold at normal temperature for 24-48h, the battery voltage is measured as OCV1, then the temperature is turned to 45 DEGC, and the batteries are put on hold for 120-168h, then the battery voltage is measured as OCV 2, then the batteries are put on hold at normal temperature, the battery voltage is measured as OCV3 again, values of OCV1, OCV2 and OCV3 are measured, and the voltage difference is calculated, that is , delta V1= OCV1-OCV2 and delta V2= OCV2-OCV3; and an out-of-tolerance value code of the delta V1 is VO1, an out-of-tolerance value code of the delta V2 is VO2, a batch of out-of-tolerance batteries can be roughly eliminated with a VO1 set value, and then a batch of the batteries can be finely eliminated with a VO2 set value. The self-discharge screening method for improving the matching consistency of the lithium ion batteries has simple and convenient implementation, high matching precision, good consistency and high matching efficiency, and is especially suitable for batch production application.
Owner:JIANGSU FRONT NEW ENERGY +1
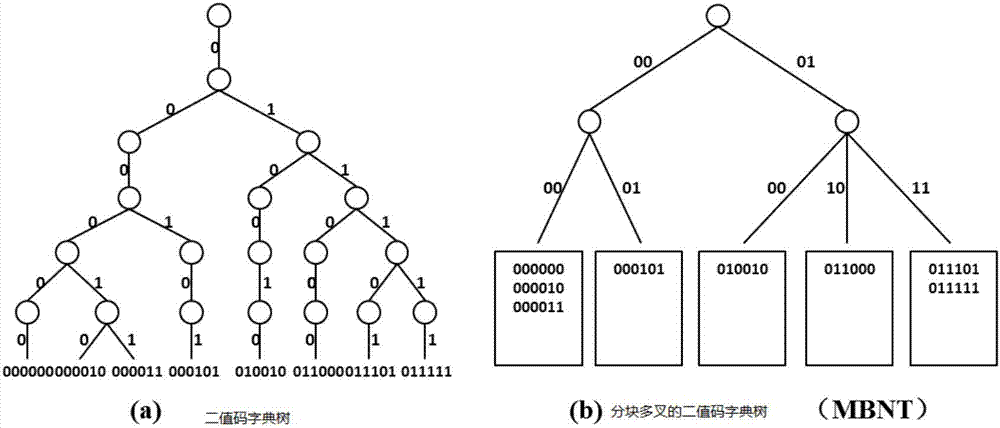
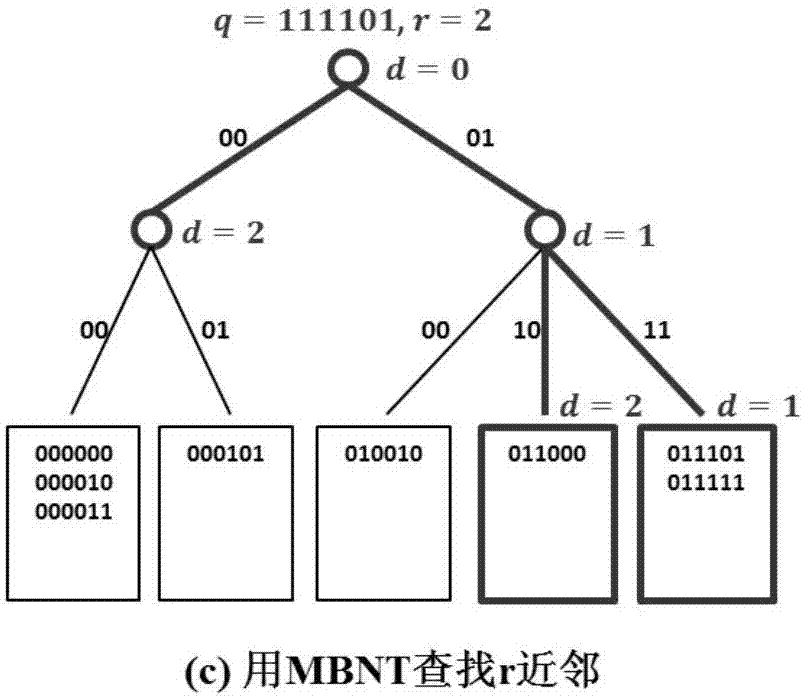
Binary code dictionary tree-based search method
ActiveCN106980656AAvoid finding missing problemsReduce the number of lookupsStill image data indexingSpecial data processing applicationsTheoretical computer scienceHamming space
The invention discloses a binary code dictionary tree-based search method. The method comprises the steps of obtaining a binary code of each image in a database, and dividing each binary code into m sections of substrings; for the jth sections of the substrings of all images in the database, establishing a binary code dictionary tree of the jth sections of the substrings, wherein the number of binary code dictionary trees is m, and each binary code dictionary tree comprises internal nodes and external nodes; obtaining the binary code of the to-be-queried image and the m sections of the substrings of the binary code; for the jth section of the substring of the binary code of the to-be-queried image, searching for the binary code with a Hamming distance not exceeding a value defined in the specification in the binary code dictionary tree corresponding to the jth sections of the substrings of all the images in the database; and traversing all the substrings of the binary code of the to-be-queried image to obtain a query result of each substring, wherein j is smaller than or equal to m. According to the method, the search quantity can be reduced during accurate nearest neighbor search of Hamming space, so that the search speed is increased.
Owner:PEKING UNIV
Image searching method and device, and image searching system
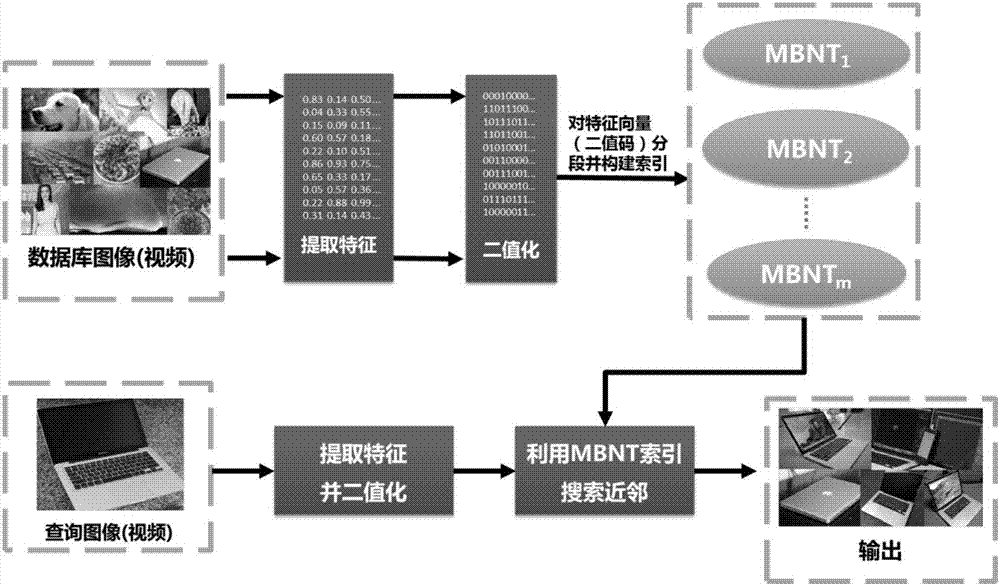
ActiveCN105989001AShorten the timeHigh precisionSpecial data processing applicationsComputer visionVisual perception
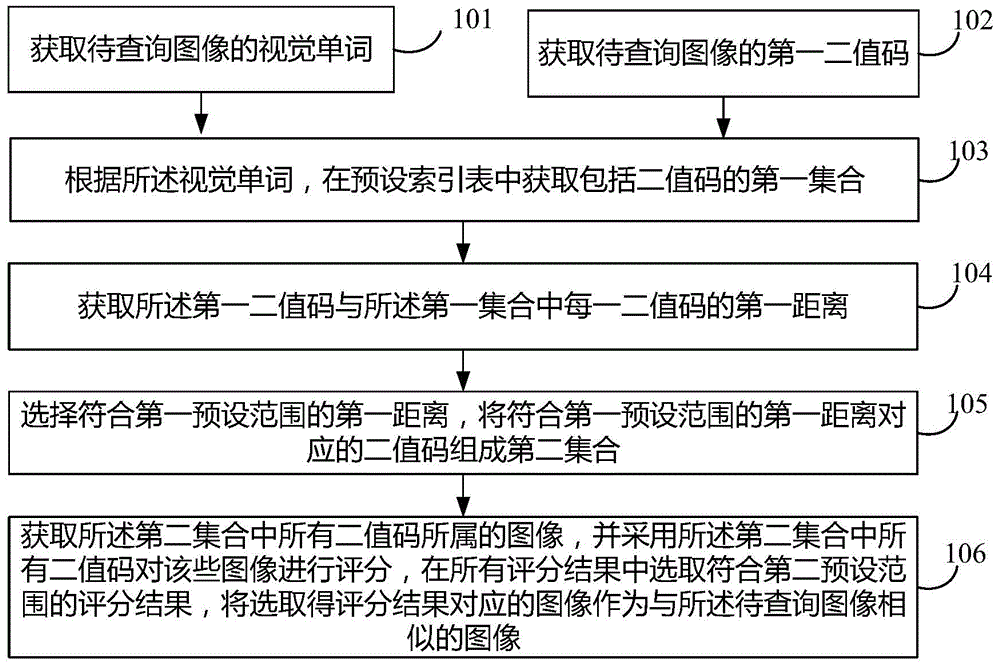
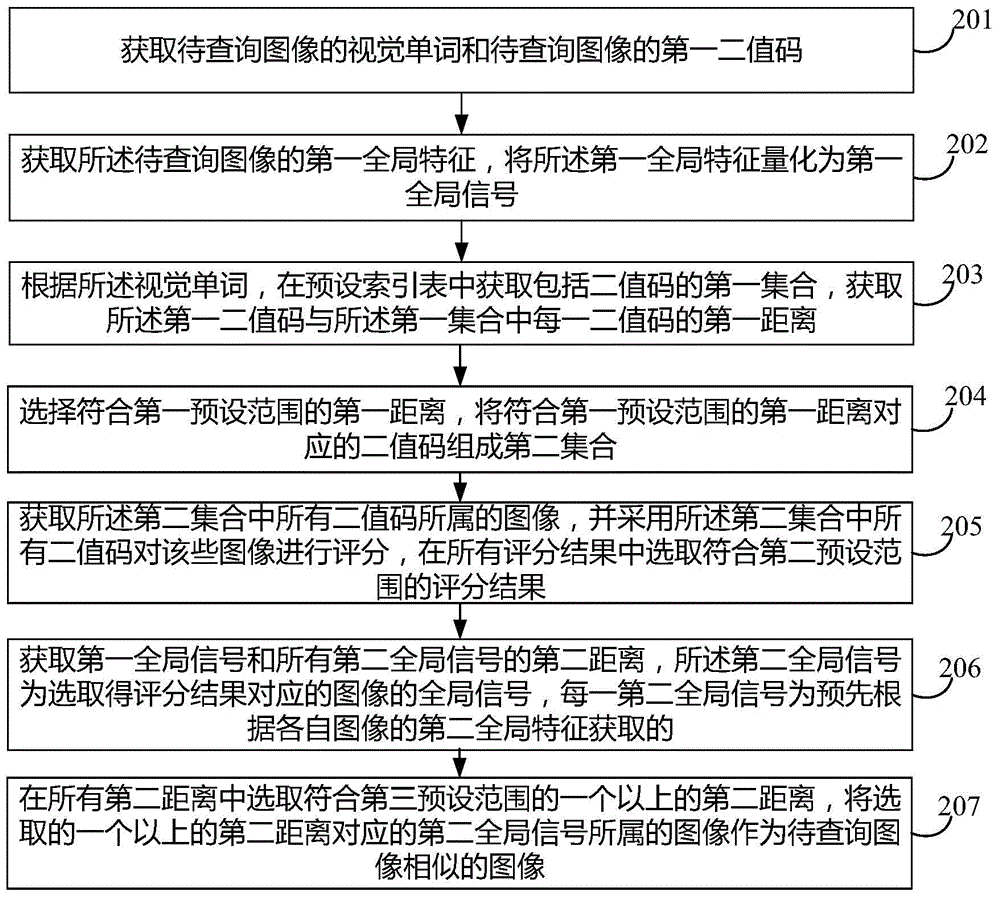
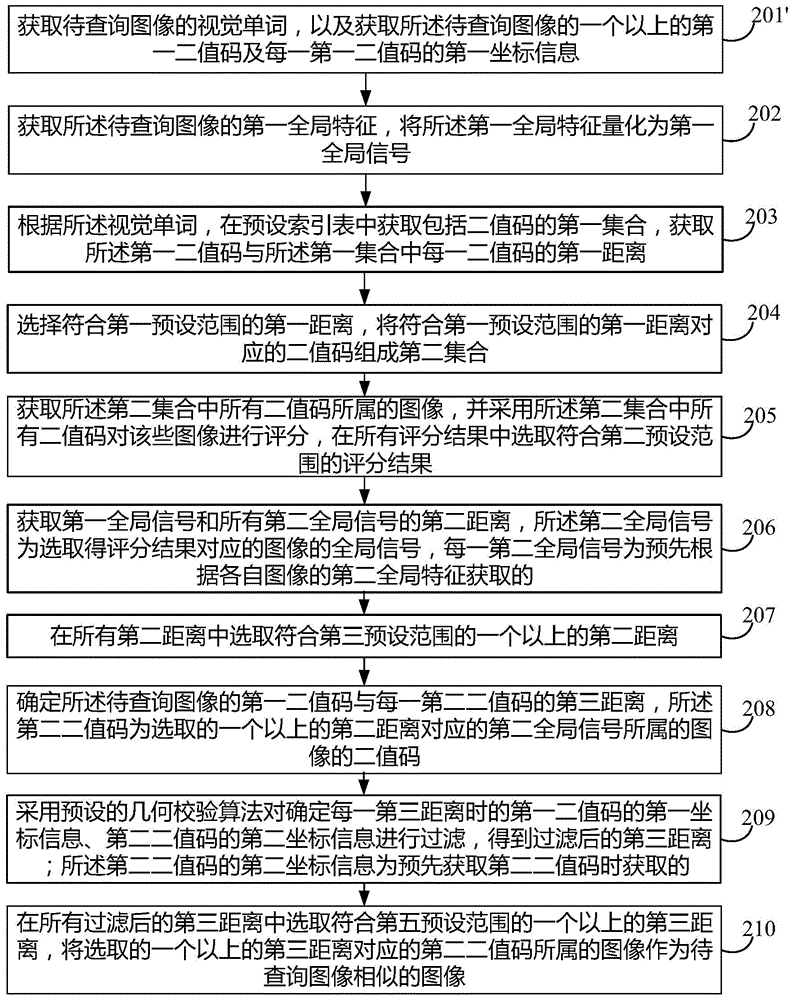
The invention discloses an image searching method and device, and an image searching system. The image searching method includes: acquiring a vision word of an image to be searched; acquiring a first set including binary codes from a preset index table according to the vision word; acquiring a first binary code of the image to be searched; acquiring a first distance between the first binary code and each binary code of the first set; selecting the first distance meeting a first preset range, allowing binary codes corresponding to the first distance meeting the first preset range to form a second set; acquiring images to which all the binary codes of the second set belong, and scoring the images by means of all the binary codes of the second set, selecting a scoring result meeting a second preset range from all the scoring results, using an image corresponding to the selected scoring result as an image similar to the image to be searched. The image searching method can improve the searching speed of images, improve the searching efficiency, and improve the searching accuracy of the images.
Owner:PEKING UNIV
Lossless information hiding method based on data difference value
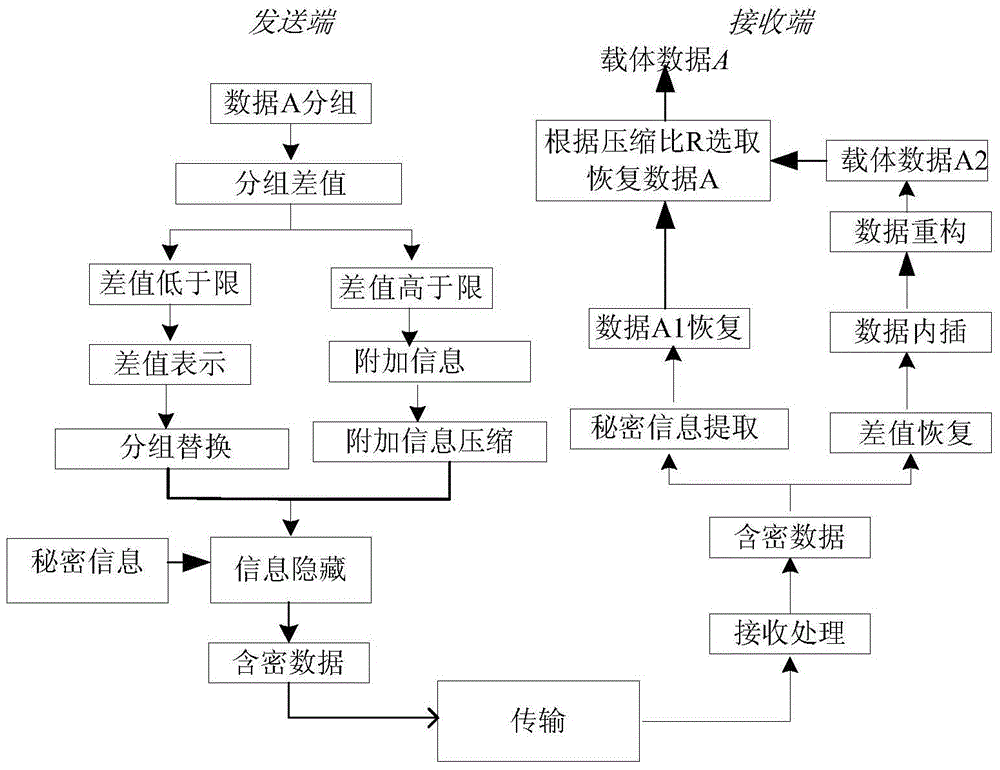
ActiveCN105227962AWith anti-compression and anti-noise abilityReduce capacityDigital video signal modificationData compressionOriginal data
The invention provides a lossless information hiding method based on a data difference value, which can achieve high-capacity lossless information hiding in various data (such as image data). The lossless information hiding method based on the data difference value is characterized in that secrete information and a difference value are jointly encoded and then are hidden in data to be transmitted, and a receiving end can completely recover the secrete information and original data. According to the lossless information hiding method based on the data difference value, information hiding is performed on only a half of original image data, and information joint hiding is performed on the other half of original image data; after the receiving end corrects the difference value, the original data can be recovered; therefore, the limitation of the traditional least significant bit data compression method is broken through, difference value coding as the cost facilitates the improvement of lossless information hiding capacity, the lossless hiding capacity of the general data is within 1 / 16 to 7 / 16, and the certain anti-compression and anti-noise properties are provided.
Owner:XIAN INSTITUE OF SPACE RADIO TECH
Implementation method of multi-channel temperature chip interface based on fpga
InactiveCN106508008BSave logic resourcesDoes not take up CPU timeInput/output processes for data processingShift registerProcessor register
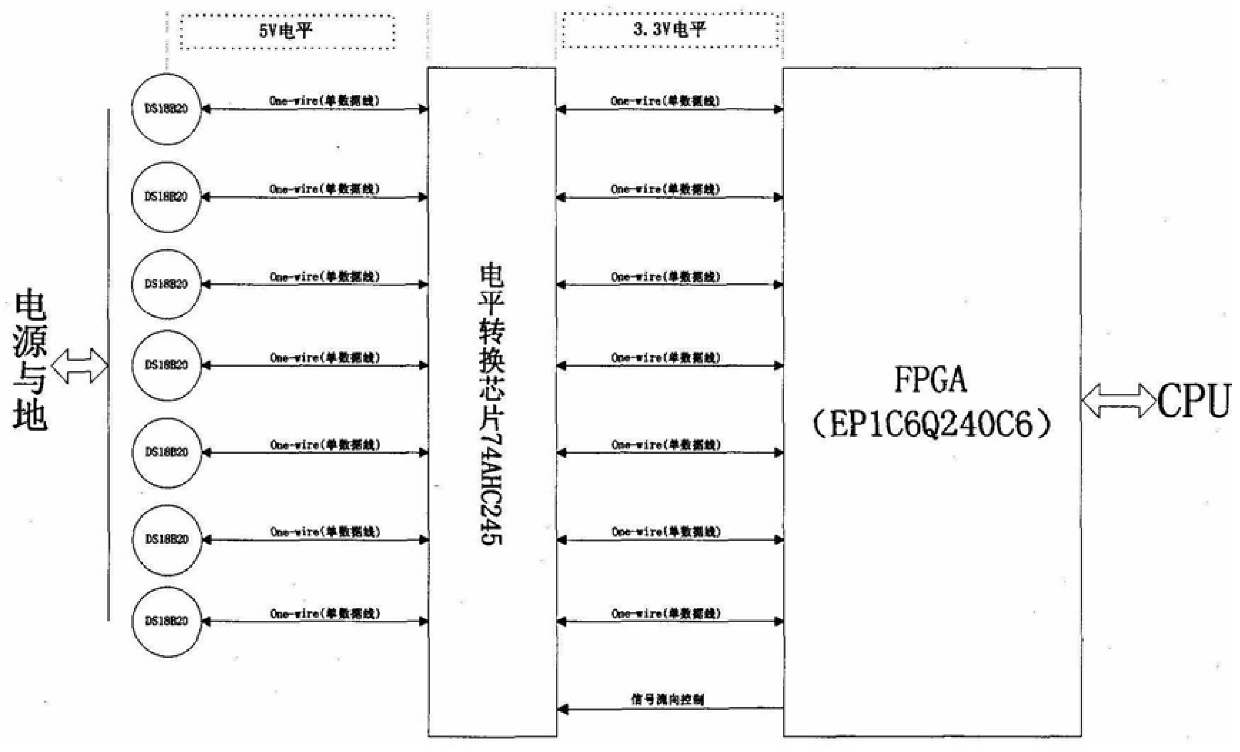
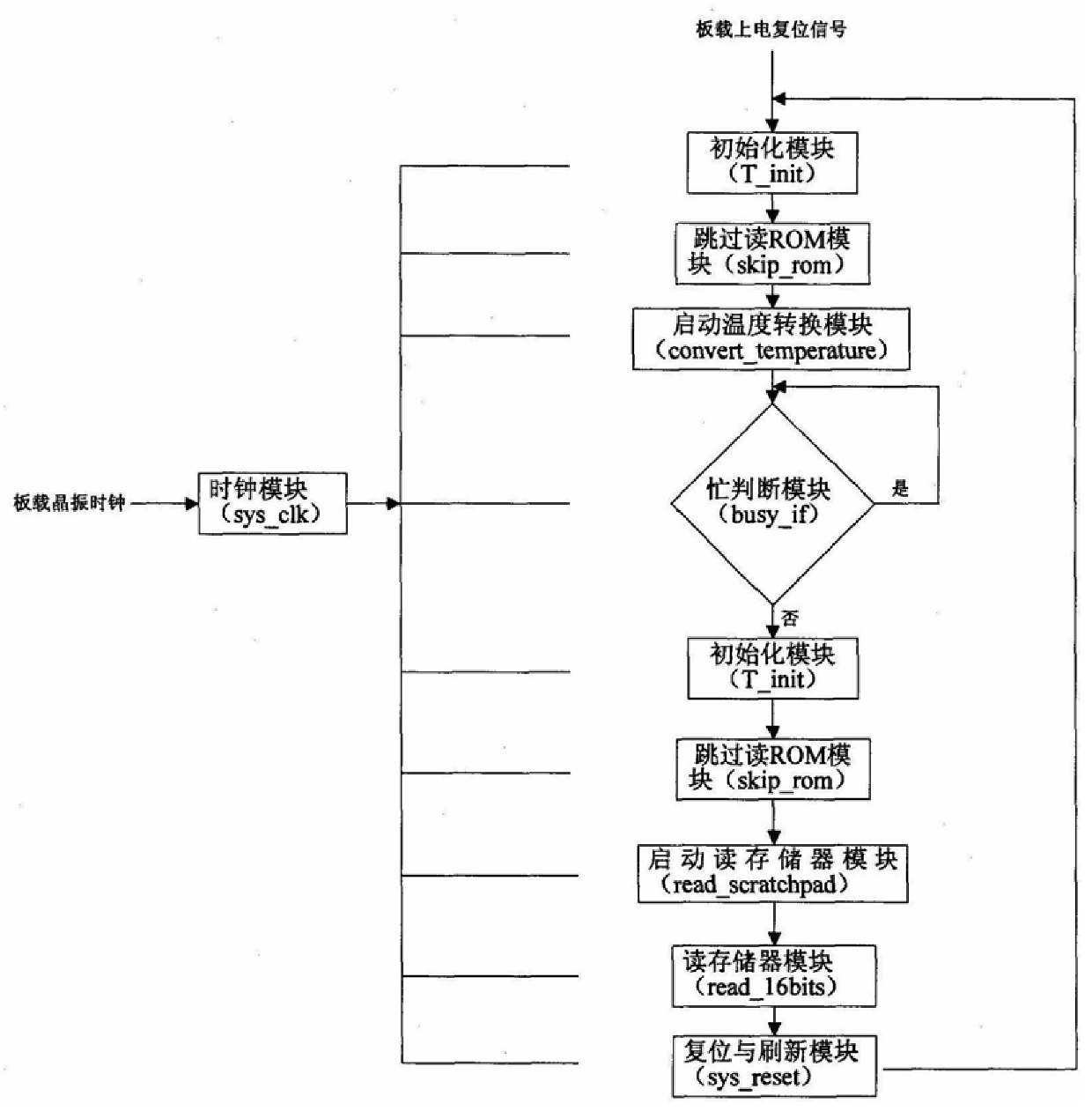
FPGA-based multi-channel temperature chip interface implementation method, the steps include: (1) frequency division to obtain the system clock (2) system reset (3) system initialization (4) simultaneously write to the n-way temperature chip and skip reading the ROM code, by writing 0 and write 1 operations are completed in order from low to high; then write the start temperature conversion code to n channels at the same time (5) judge whether n channels are busy, if all channels are busy, continue to query until n channels are not busy, the system performs the second Initialize (6) skip reading ROM codes for n channels at the same time, and then write and start reading temperature value codes for n channels at the same time (7) read the temperature values of each channel and store them in corresponding registers, and address each shift register for The CPU reads (8) the system is reset, and a new round of temperature collection is started. The present invention realizes the method of generating timing in FPGA and communicating with multi-channel temperature chips through the idea of parallel processing, and solves the existing problems of low temperature acquisition accuracy, too much FPGA resources occupied, and too much CPU time occupied by timing operations.
Owner:SICHUAN AEROSPACE LIAOYUAN SCI & TECH CO LTD
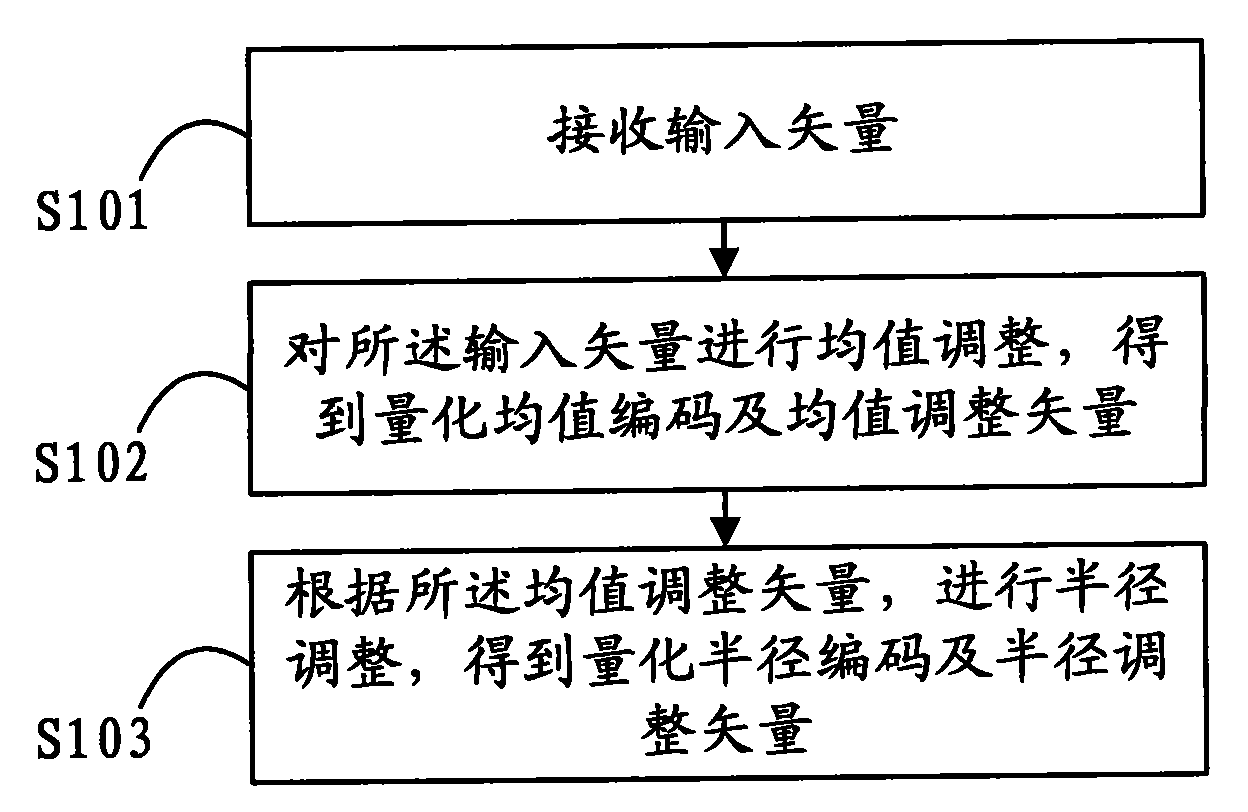
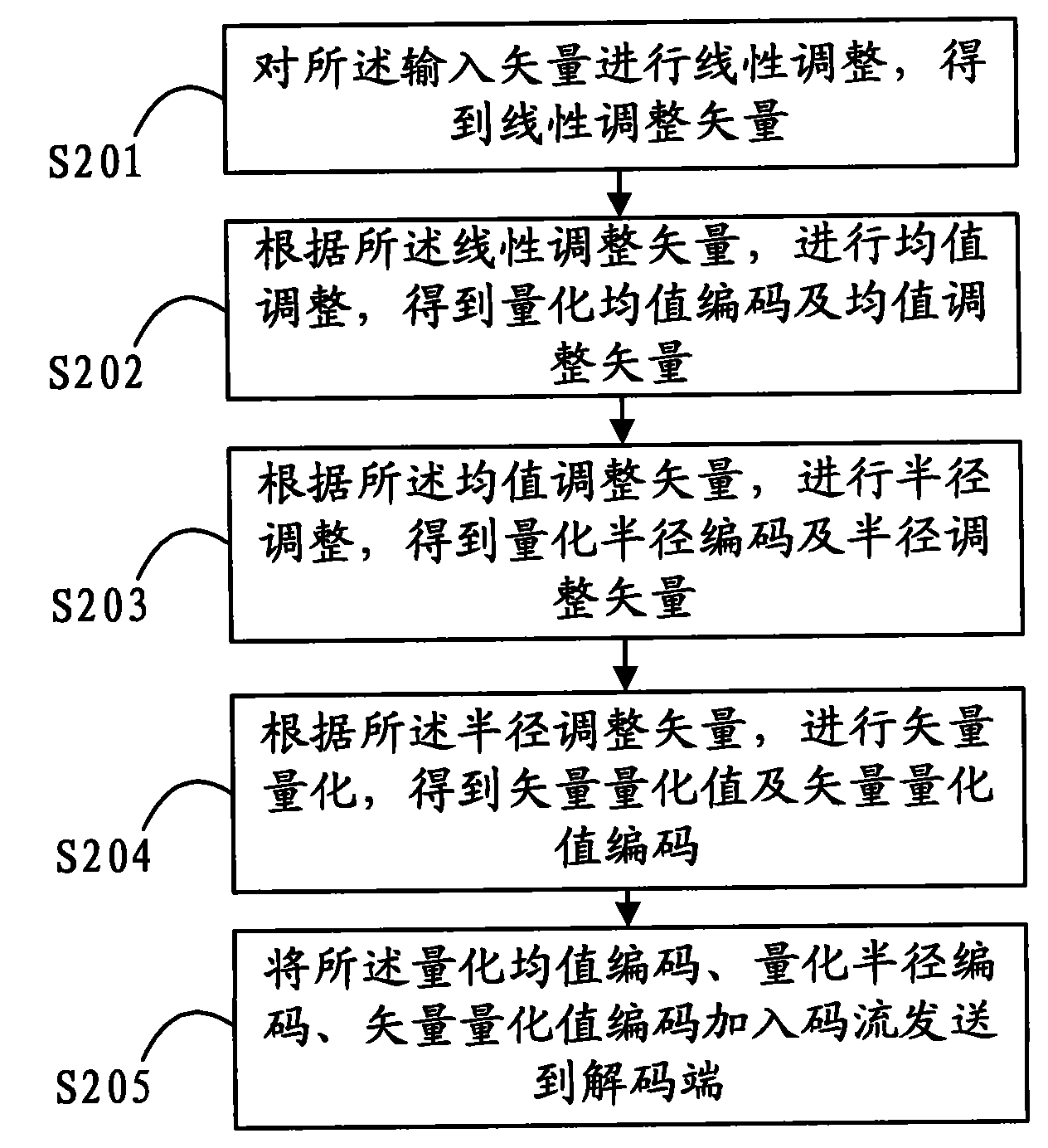
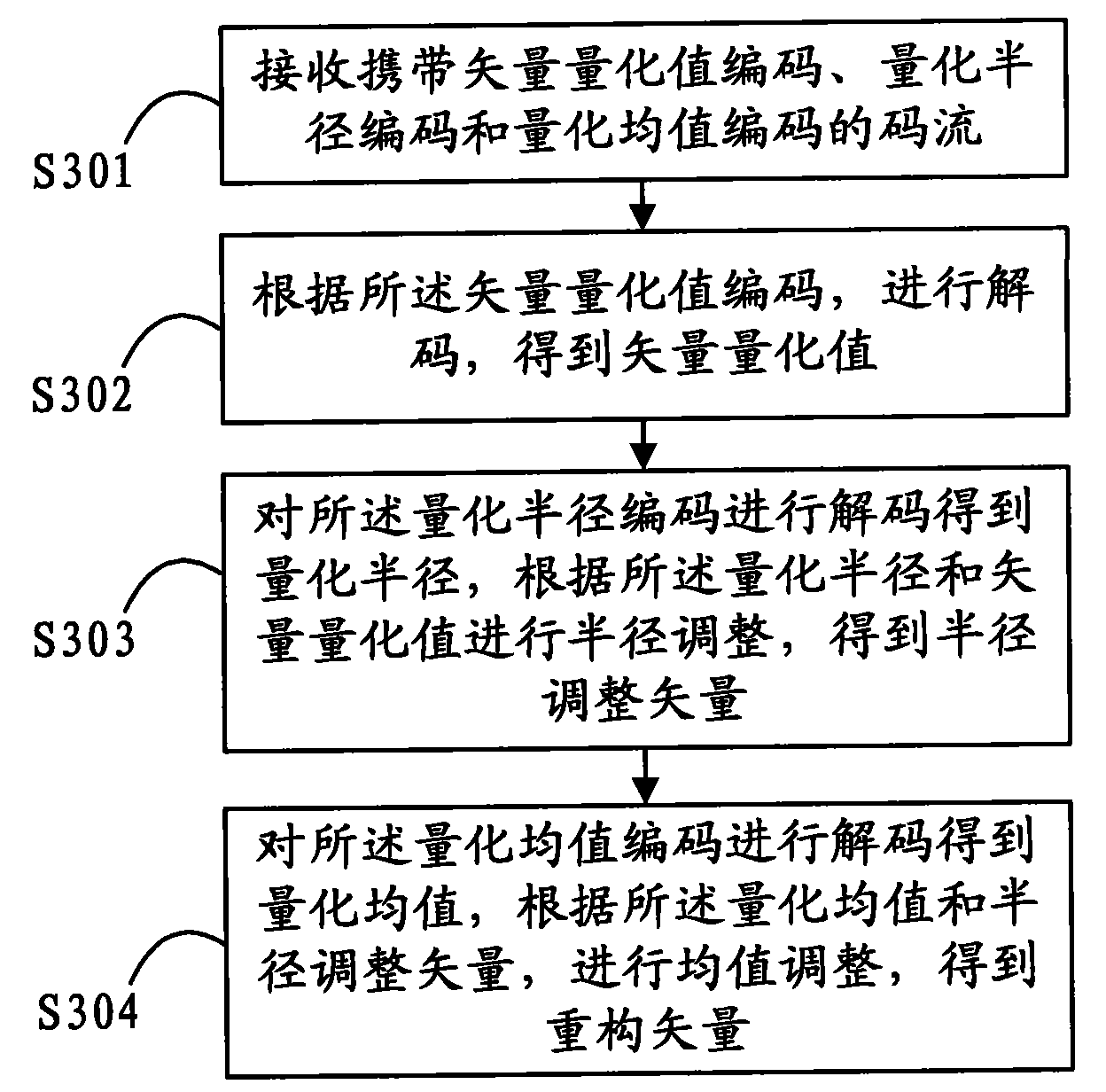
Method and device for regulating vector as well as method and device for decoding regulated vector
InactiveCN101588182ASpherical radius reductionReduce quantization errorCode conversionData compressionComputer science
The embodiment of the invention discloses a method and a device for regulating a vector as well as a method and a device for decoding a regulated vector, which belong to the technical field of data compression and are designed in order to solve the problem that the quantization error of a whole quantizer is large due to large radius of spherical quantization in the spherical quantization process in the prior art. The method for regulating a vector provided in the embodiment of the invention comprises the following steps: receiving an input vector; regulating the average value of the input vector to obtain a quantization average value code and an average value regulation vector; and regulating the radius according to the average value regulation vector to obtain a quantization radius code and a radius regulation vector. The invention shortens the spherical quantization radius through regulation, thereby reducing the quantization error.
Owner:HUAWEI TECH CO LTD
Keyboard input method of control system display control terminal
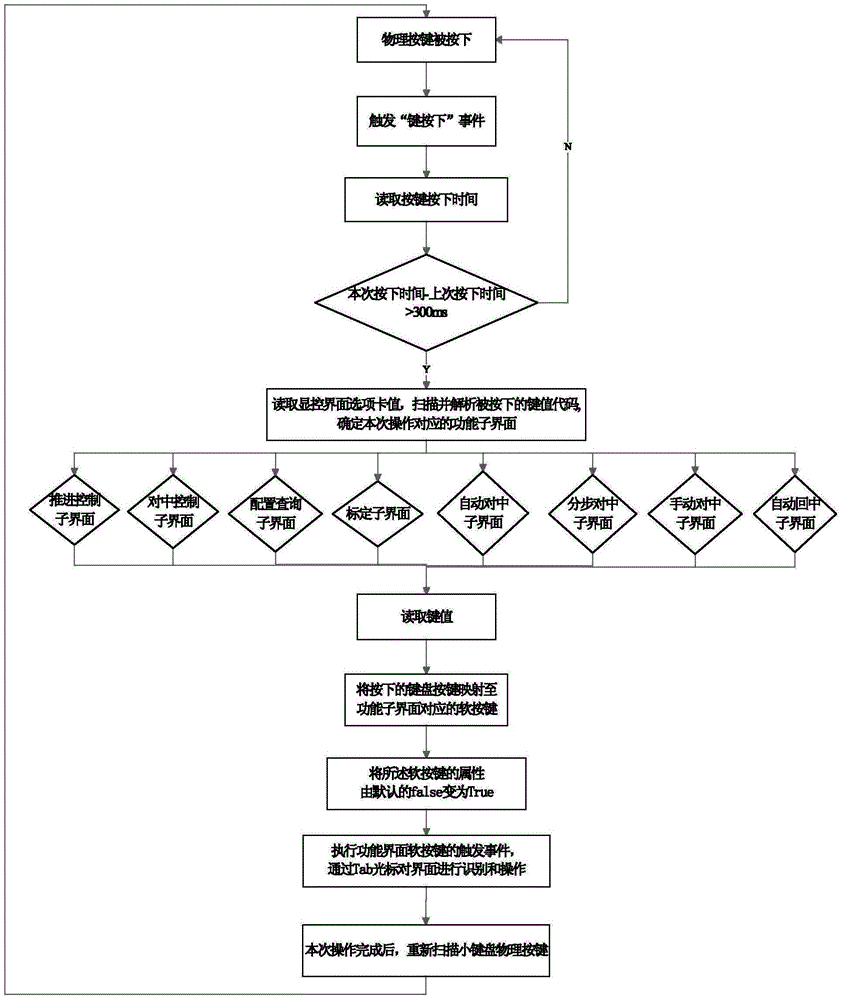
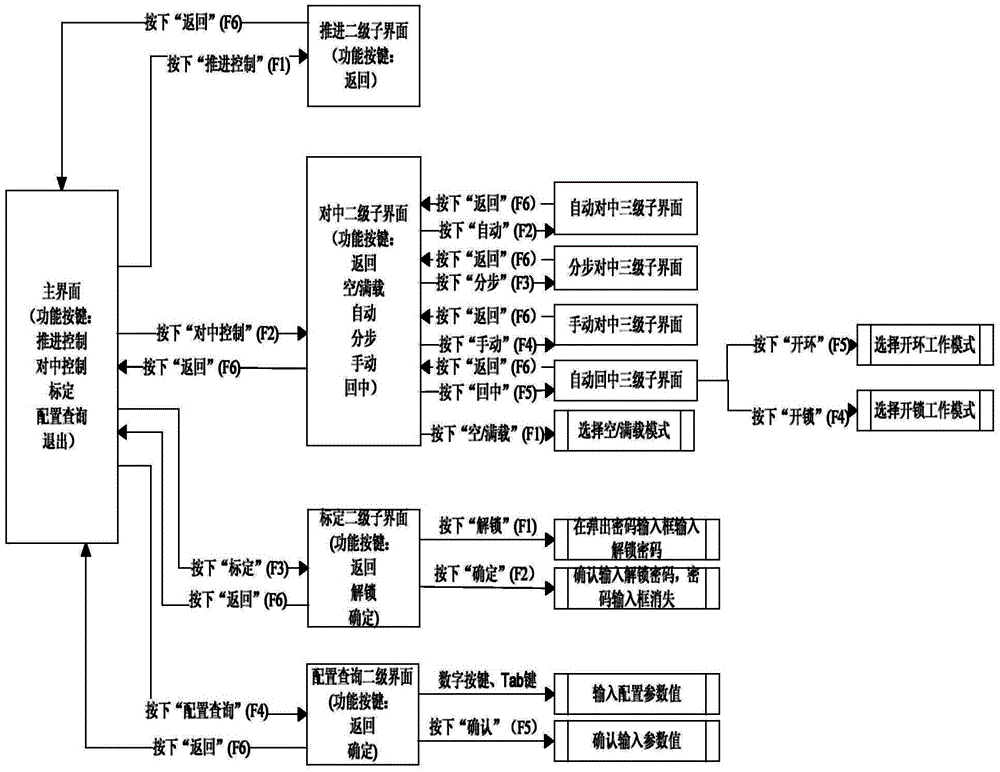
InactiveCN104007837AOvercome multi-functional operation needsRealize the mappingInput/output processes for data processingSoft keyKey pressing
The invention provides a keyboard input method of a control system display control terminal. According to the method, small keyboard physical keys, user function interface soft keys of the display control terminal and a mapping module are included, and the method comprises the steps that when the small keyboard physical keys are pressed, a key-pressing event is triggered, when the key trigger time at two times is longer than 300ms, the mapping module reads tab information of a main interface, the pressed key value code is scanned, the soft keys corresponding to the pressed key value are analyzed through the mapping module, the key attribute is changed to be true from acquiescent false, a static value change event is triggered, and the corresponding function trigger is achieved. The keyboard input method has the advantages that the defect that due to the facts that the space size is restrained, and the number of the small keyboard physical keys is limited, the multifunctional operation requirement of a user for the control system display control terminal cannot be met is overcome, reuse and expanding of the small keyboard physical keys is achieved, and the real-time man-machine interaction of a complex control system is completed.
Owner:BEIJING INST OF SPACE LAUNCH TECH +1
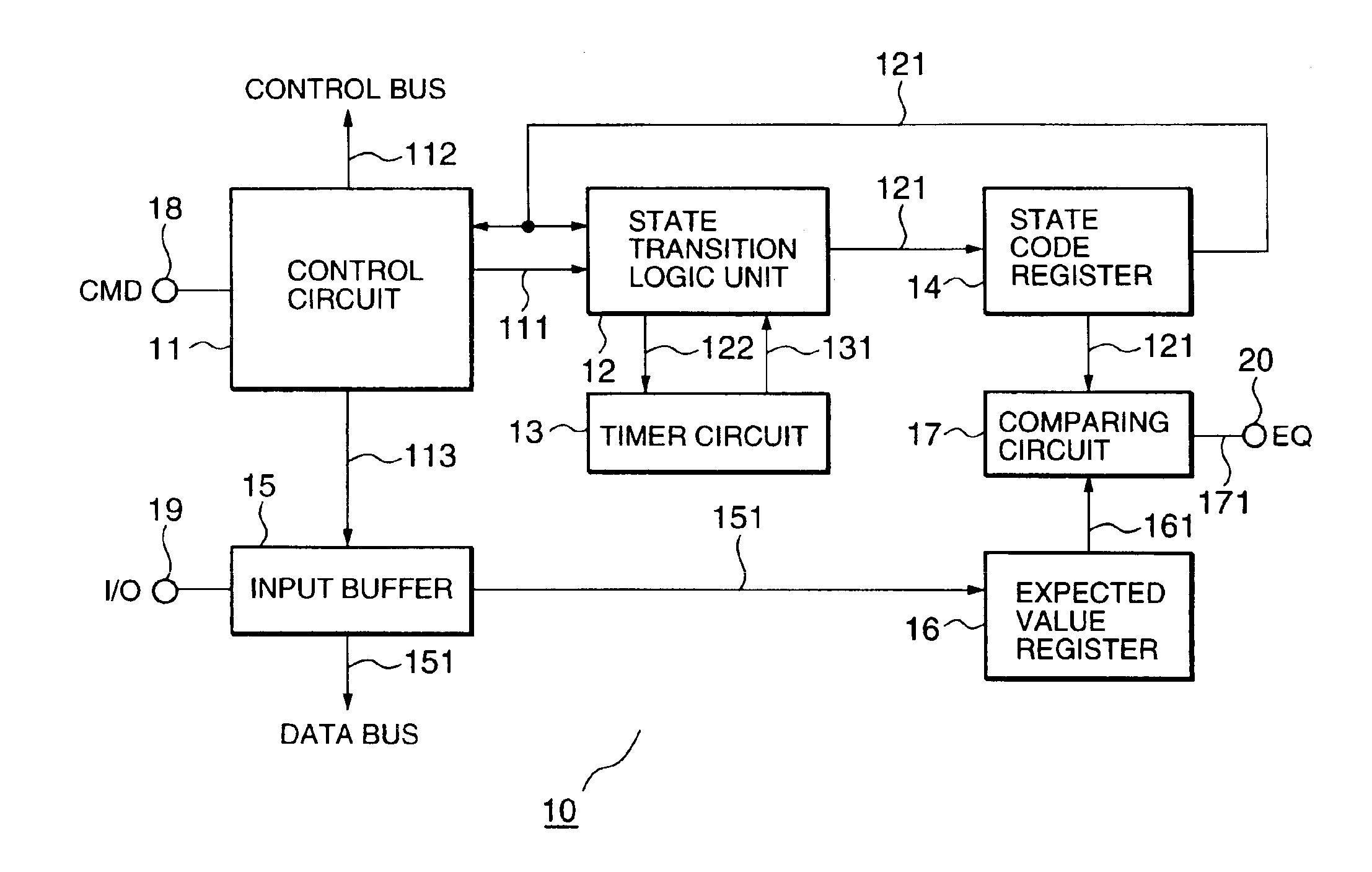
Semiconductor device and a method for checking state transition thereof
ActiveUS6917220B2Ease of evaluationEasy to analyzeDigital circuit testingDetecting faulty computer hardwareComputer hardwareProcessor register
A semiconductor device includes a state code register that stores a state code representing a present internal state. A state transition logic unit is configured to determine a state code for a next internal state to be transited in accordance with a predetermined logic, based on a state code provided from the state code register and an input command instructing transition to a required state, and to set the determined state code into the state code register with synchronizing an internal clock. An expected value register is configured to hold an internal state to be detected, as an expected value code and a comparing unit compares the state code set in the state code register by the state transition logic unit to the expected value code in the expected value register and supplying an equal state signal when they coincide.
Owner:KIOXIA CORP
System and method for storage, management and automatic indexing of structured documents
InactiveUS7844633B2Digital data information retrievalDigital data processing detailsAutomatic indexingDocument model
Owner:LINKEDIN
Single-recognizer multi-gate access control device and method based on iris recognition
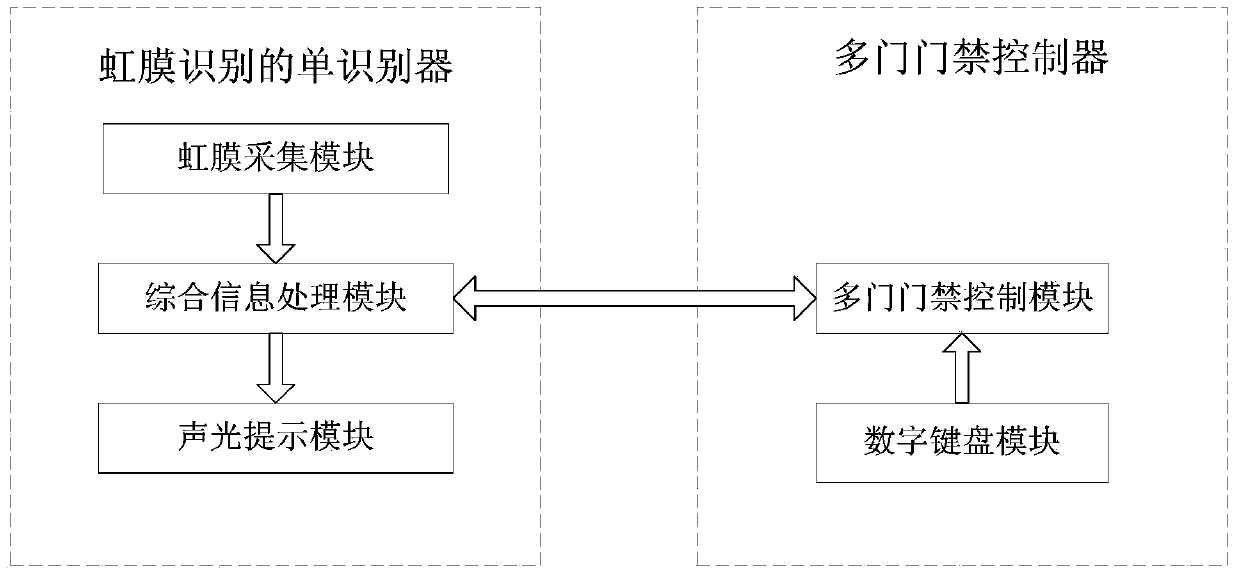
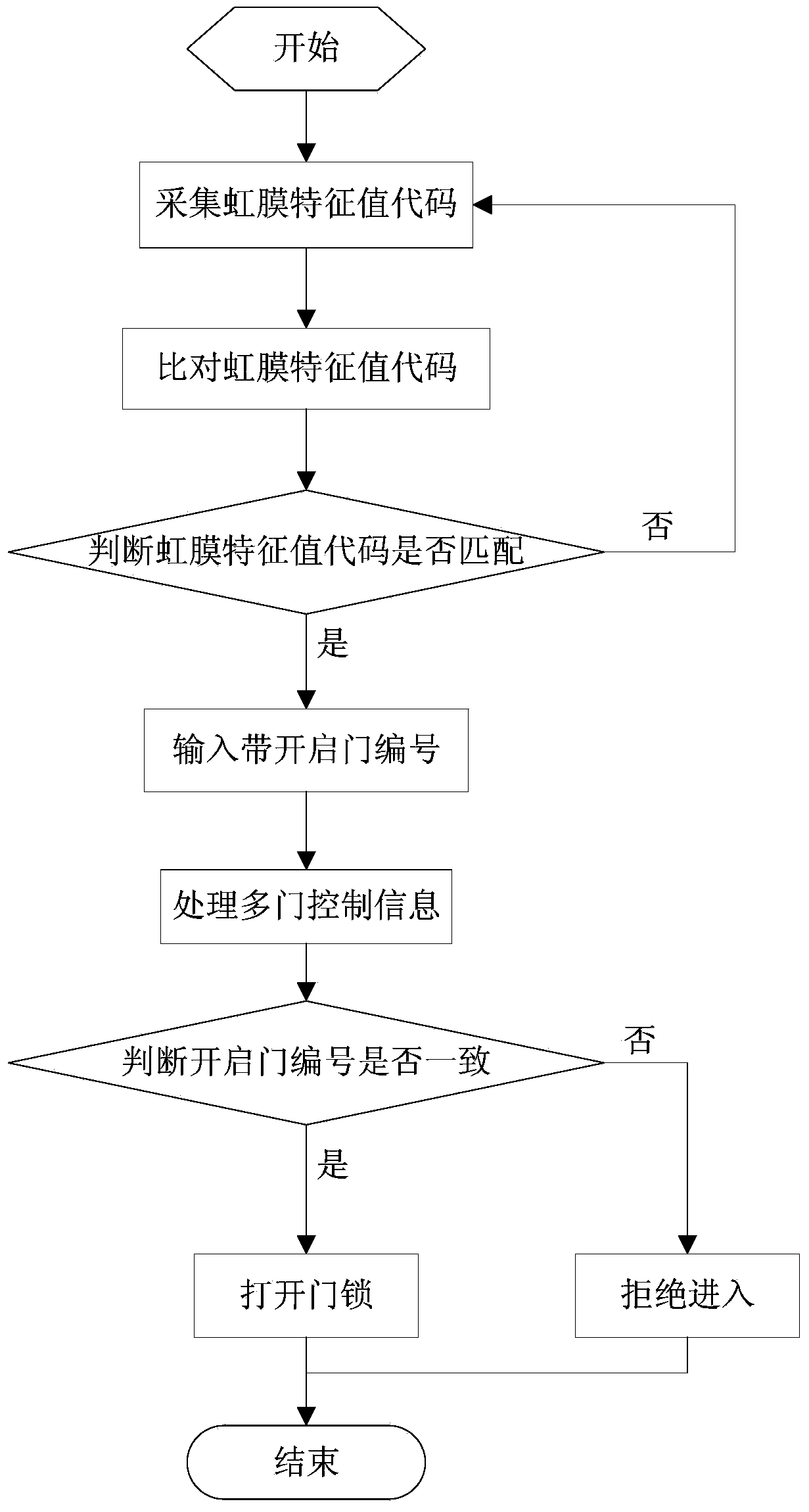
ActiveCN104217484ALow costEasy to installCharacter and pattern recognitionIndividual entry/exit registersInformation processingIris recognition
The invention discloses a single-recognizer multi-gate access control device and method based on iris recognition. The device comprises a single iris recognizer and a multi-gate access controller, wherein the single iris recognizer comprises an iris acquiring module, a comprehensive information processing module and an acousto-optical prompting module; the multi-gate access controller comprises a multi-gate access control module and a digital keyboard module. The method comprises the following steps: acquiring an iris characteristic value code, comparing the iris characteristic value code with a pre-registered iris characteristic value code; judging whether the iris characteristic value code is in matching; inputting a to-be-opened gate number; processing multi-gate control information; judging whether the to-be-opened gate number is consistent with a pre-registered authorized opened gate number; opening a lock; and denying access. The multi-gate control is carried out through the single iris recognizer, the security and the reliability of the access control system are improved, and the cost is reduced.
Owner:西安凯虹电子科技有限公司
Image coding apparatus, method for coding image, program therefor, image decoding apparatus, method for decoding image, and program therefor
ActiveUS9277221B2High speed machiningEase of parallel processingCharacter and pattern recognitionDigital video signal modificationImaging processingBasic block
An image processing apparatus includes a division unit configured to divide an input image into a plurality of subblocks subjected to quantization control a subblock quantization parameter calculation unit configured to calculate a quantization parameter of each of the subblocks, a basic block quantization parameter calculation unit configured to set a basic block including at least two subblocks and to calculate a quantization parameter of the basic block, a difference value calculation unit configured to calculate a difference value between the quantization parameter of the basic block and the quantization parameter of each subblock included in the basic block, and a difference value coding unit configured to code the difference value.
Owner:CANON KK
Producing method capable of global indexing coding sequence and uses thereof
InactiveCN101042295AImprove efficiencyImprove rebuild efficiencyImage codingUsing optical meansTheoretical computer scienceValue code
This invention relates to one generation method for whole index codes sequence, which comprises the following steps: giving codes set as P={c1, c2, c3, ...cp}, p>=3 with cp for special physical values codes with k for code length; generating k element set w ranking as sizes to form set V and to select p-1 code as initial codes and to delete p-1 code; using the last k-1 unit code as initial one in set V and selecting maximum codes into S for connection and adding the last unit code into S and to delete this code; repeating above steps till all codes in set V into S sequence to form one longest whole index codes sequence.
Owner:ZHEJIANG UNIV OF TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com