Double-controller-based read-write locking method and device
A dual-controller, controller technology, applied in the direction of memory address/allocation/relocation, input/output to record carrier, etc., can solve problems such as inability to adjust flexibly, and achieve the effect of accurately handling lock conflicts and reducing communication
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
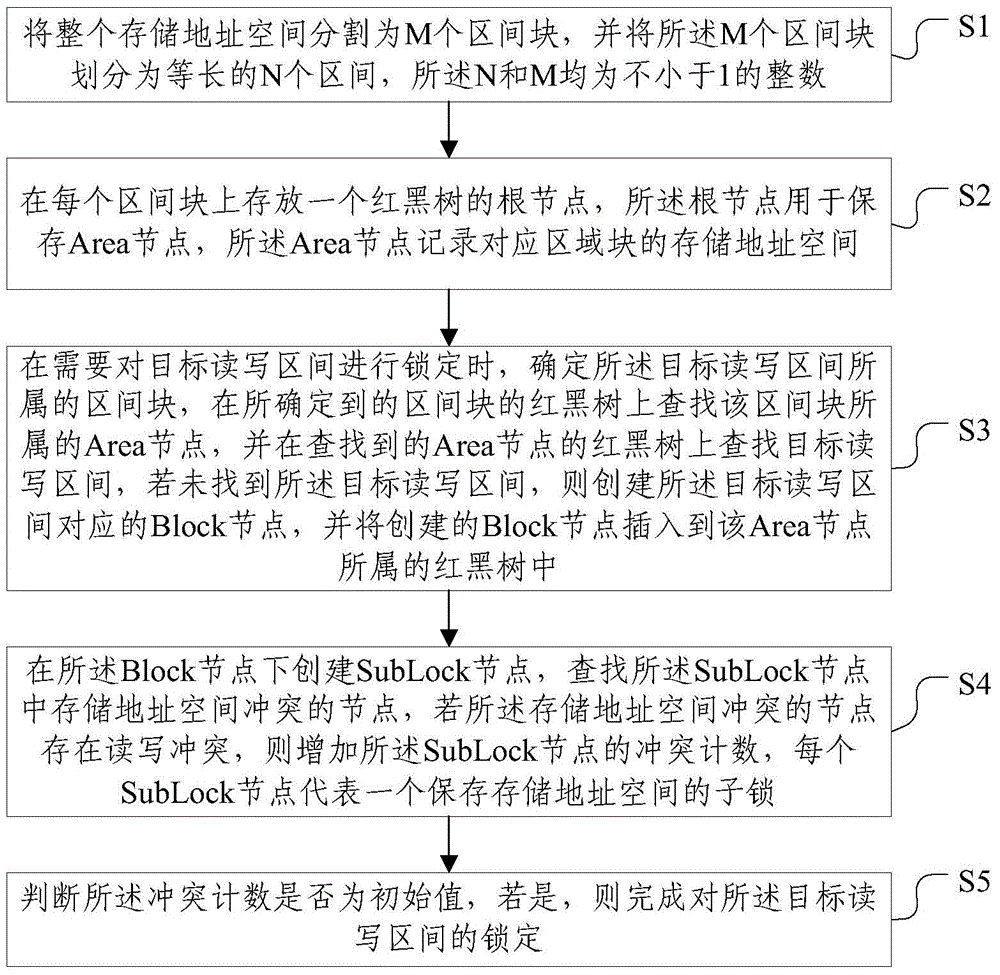
[0069] The present invention is described below with a specific embodiment, but does not limit the protection scope of the present invention. The method of this embodiment includes:
[0070] (1) Divide the entire storage address space into M intervals. The interval size can be specified when the lock is created. For example, it can be specified as the size of a strip (this is an optimization parameter). The interval is the smallest unit of ownership division. (2) Divide the entire storage address space into several equal-length interval blocks, for example, divide the 128TB storage address space into 1024 interval blocks according to 128GB, the purpose is to narrow the range of the interval block and speed up the search on the interval block Speed, this step can be seen as a simple Hash. The size of an interval block is an integer multiple of the interval size (except for the last interval block).
[0071] (3). The root node of a red-black tree is stored on each interval bl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com