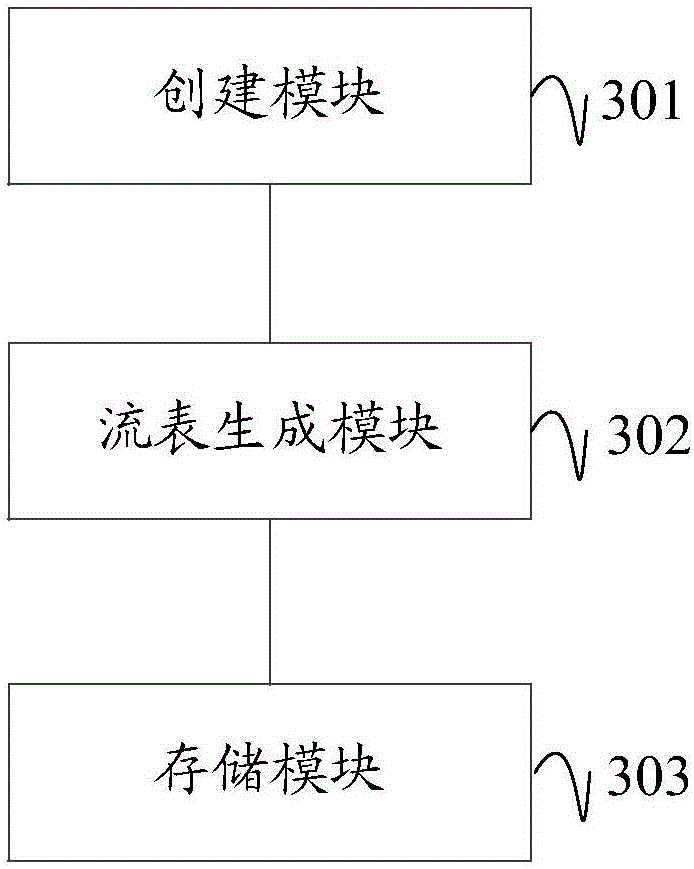
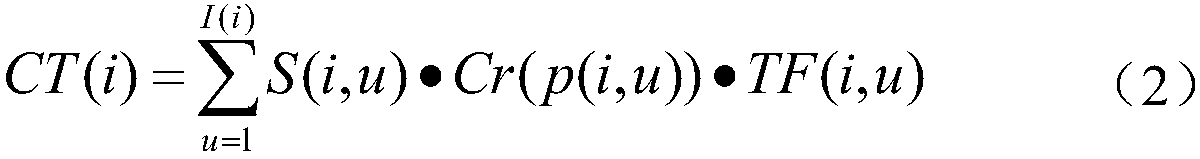Patents
Literature
68results about How to "Increase forwarding rate" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
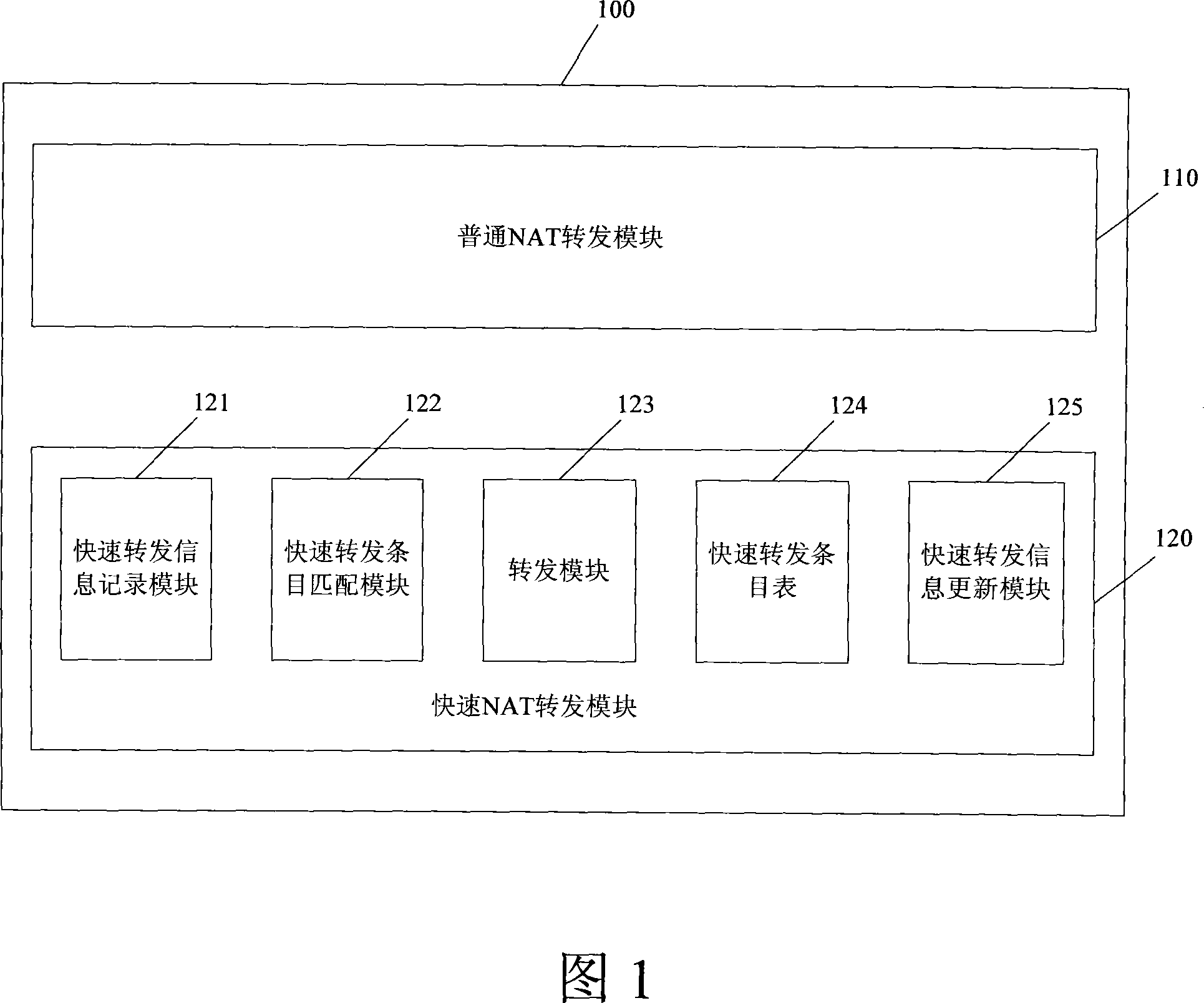
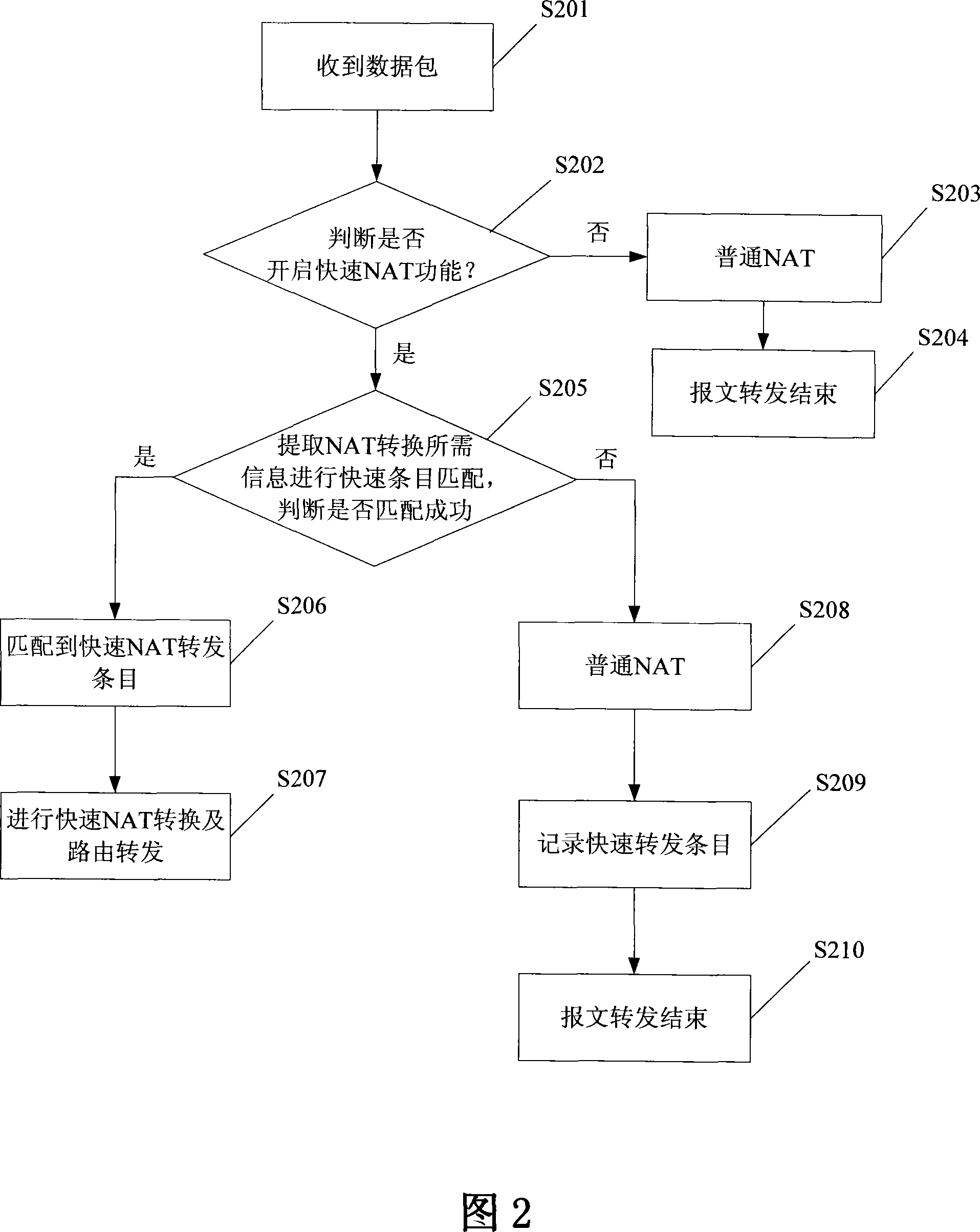
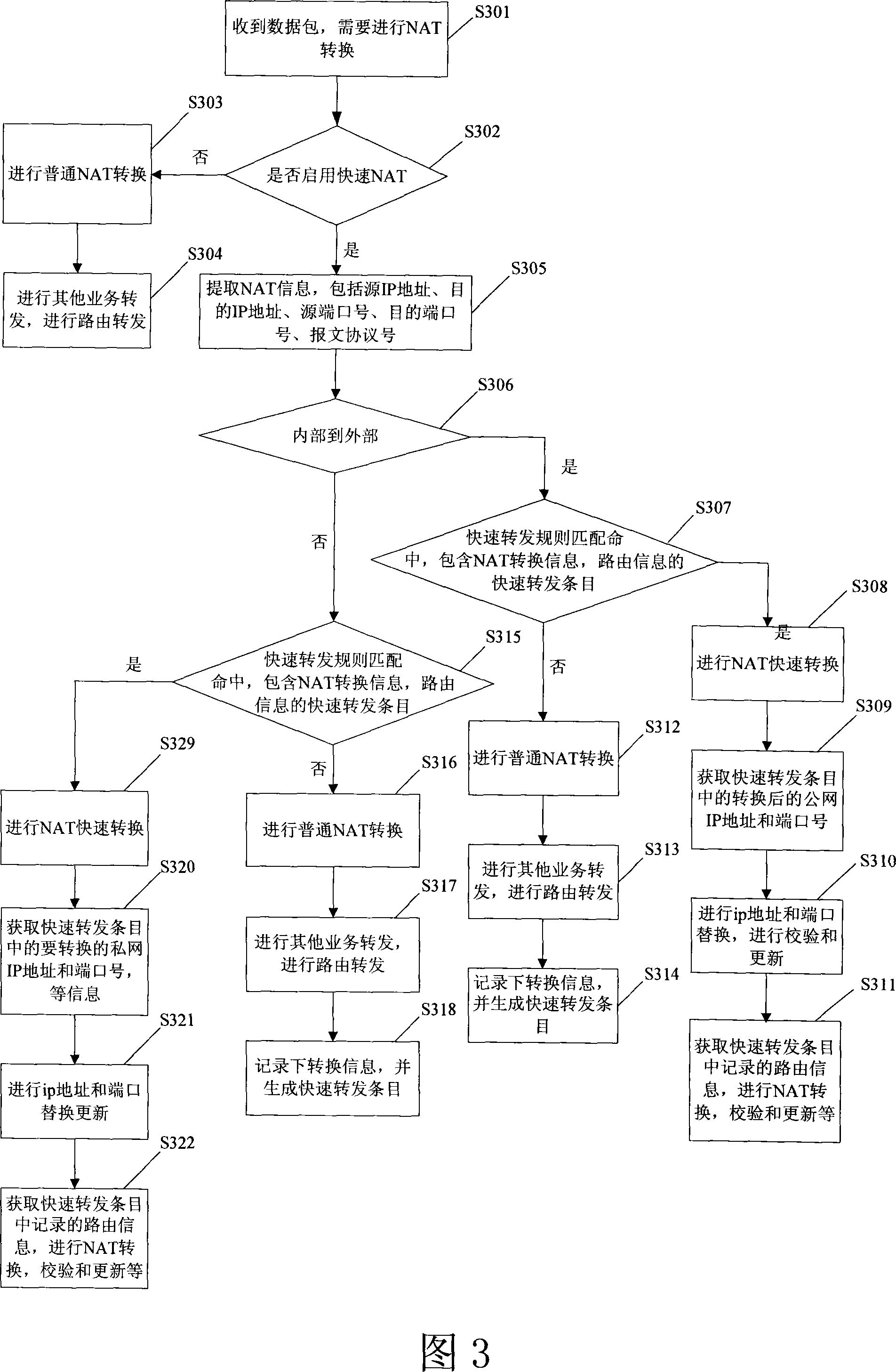
Network address switching retransmitting device and method
InactiveCN101068212AIncrease forwarding rateForwarding performance impactData switching networksRelevant informationNormal mode
A conversion-retransmission device of network address consists of a normal network address conversion-retransmission module for carrying out conversion of network address and retransmission of data packet in normal mode and a fast network address conversion-retransmission module for recording retransmission key information required by retransmission of data packet. Its converting-retransmitting method is also disclosed.
Owner:ZTE CORP
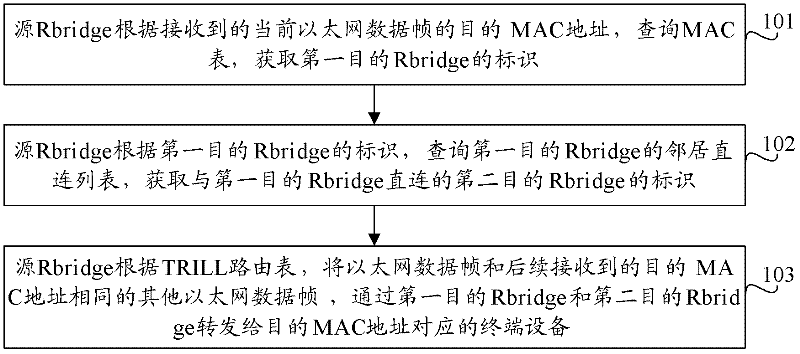
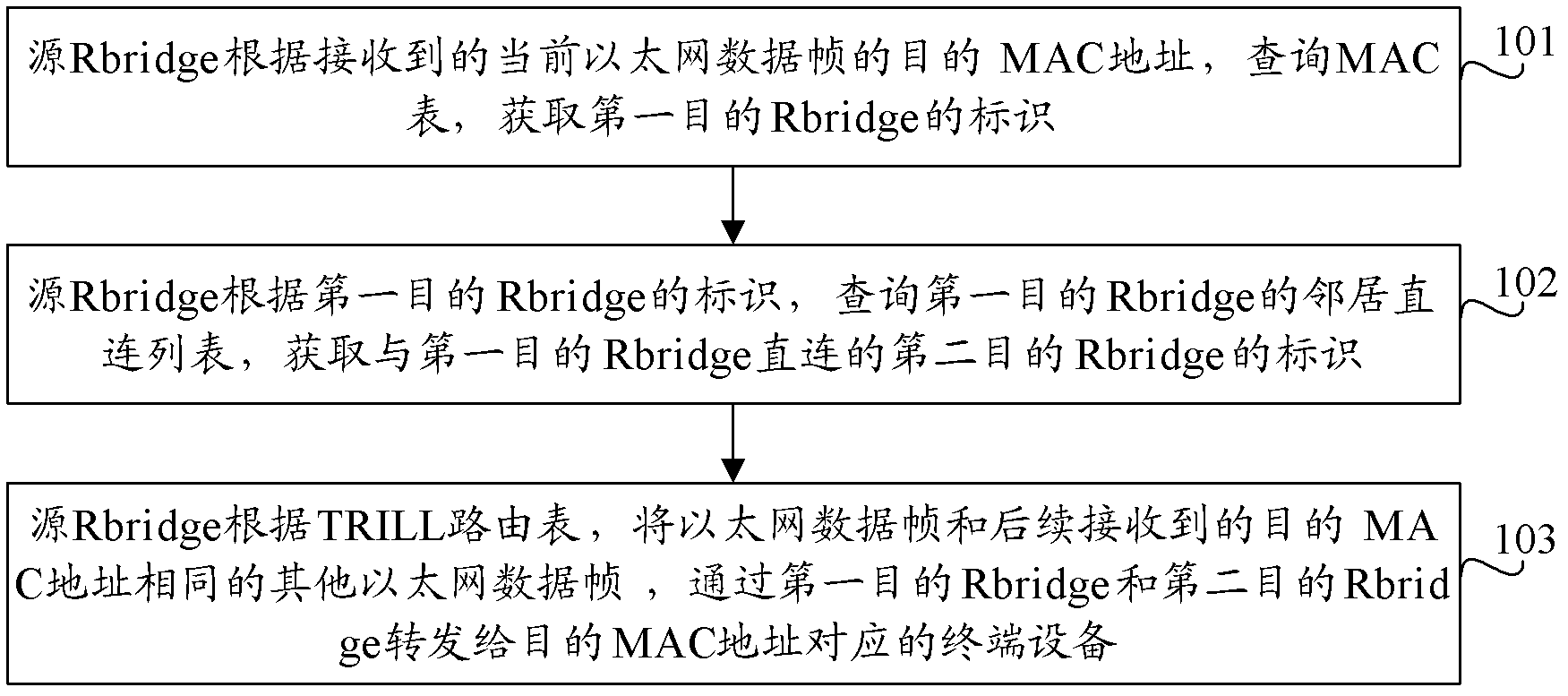
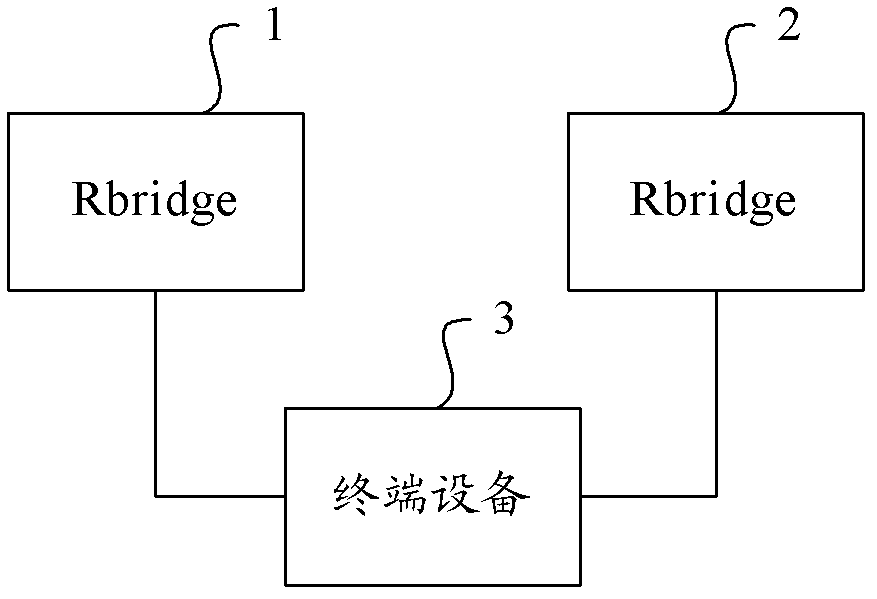
Message forwarding method, system and routing switch
InactiveCN102244614AIncrease forwarding rateIncrease profitData switching networksTerminal equipmentInterconnection
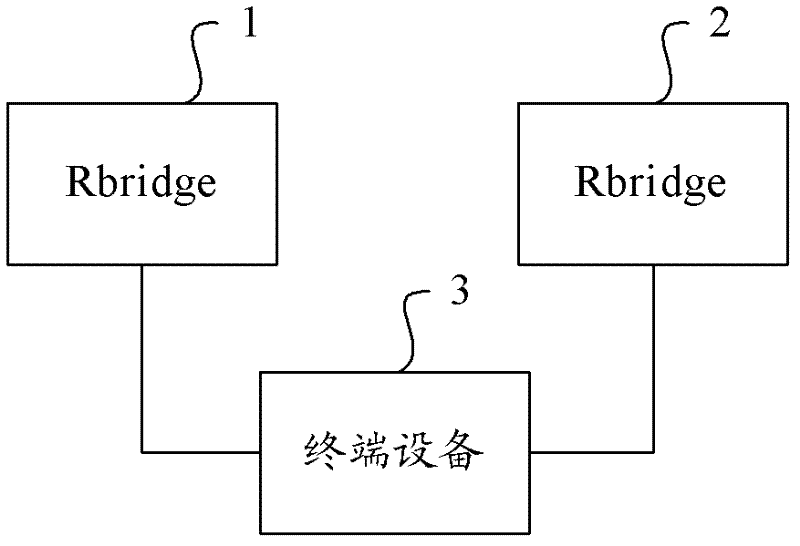
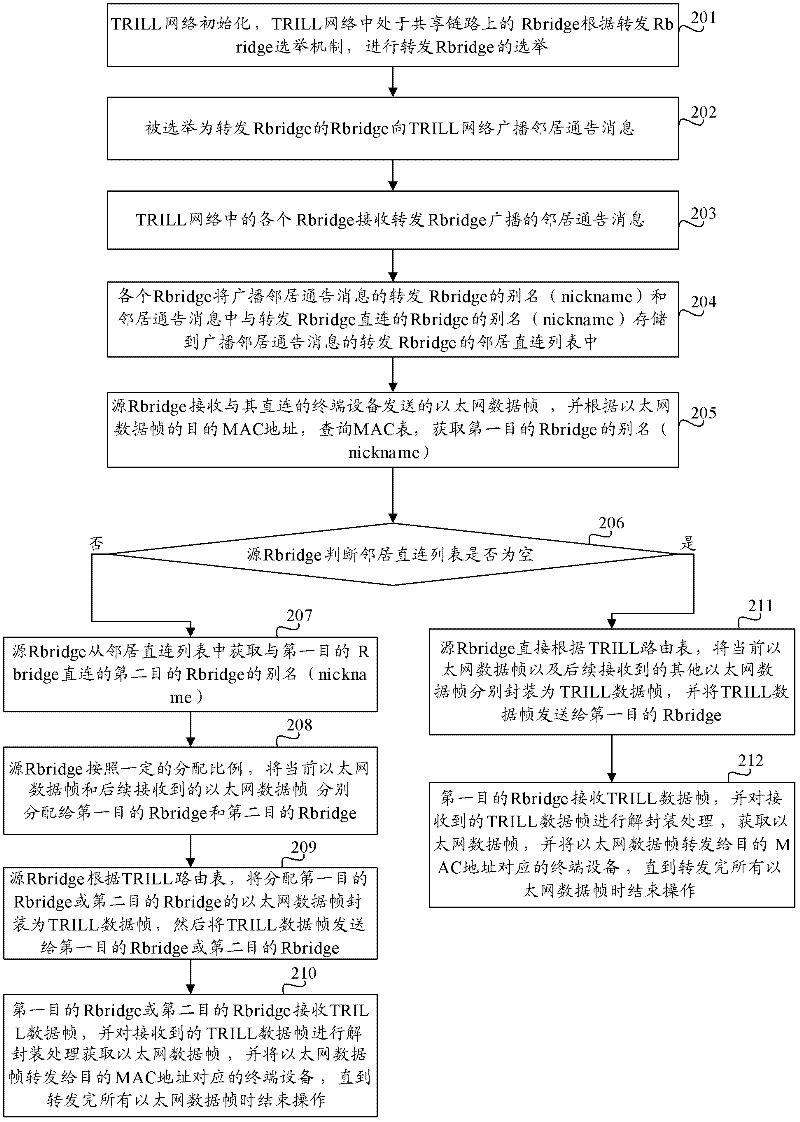
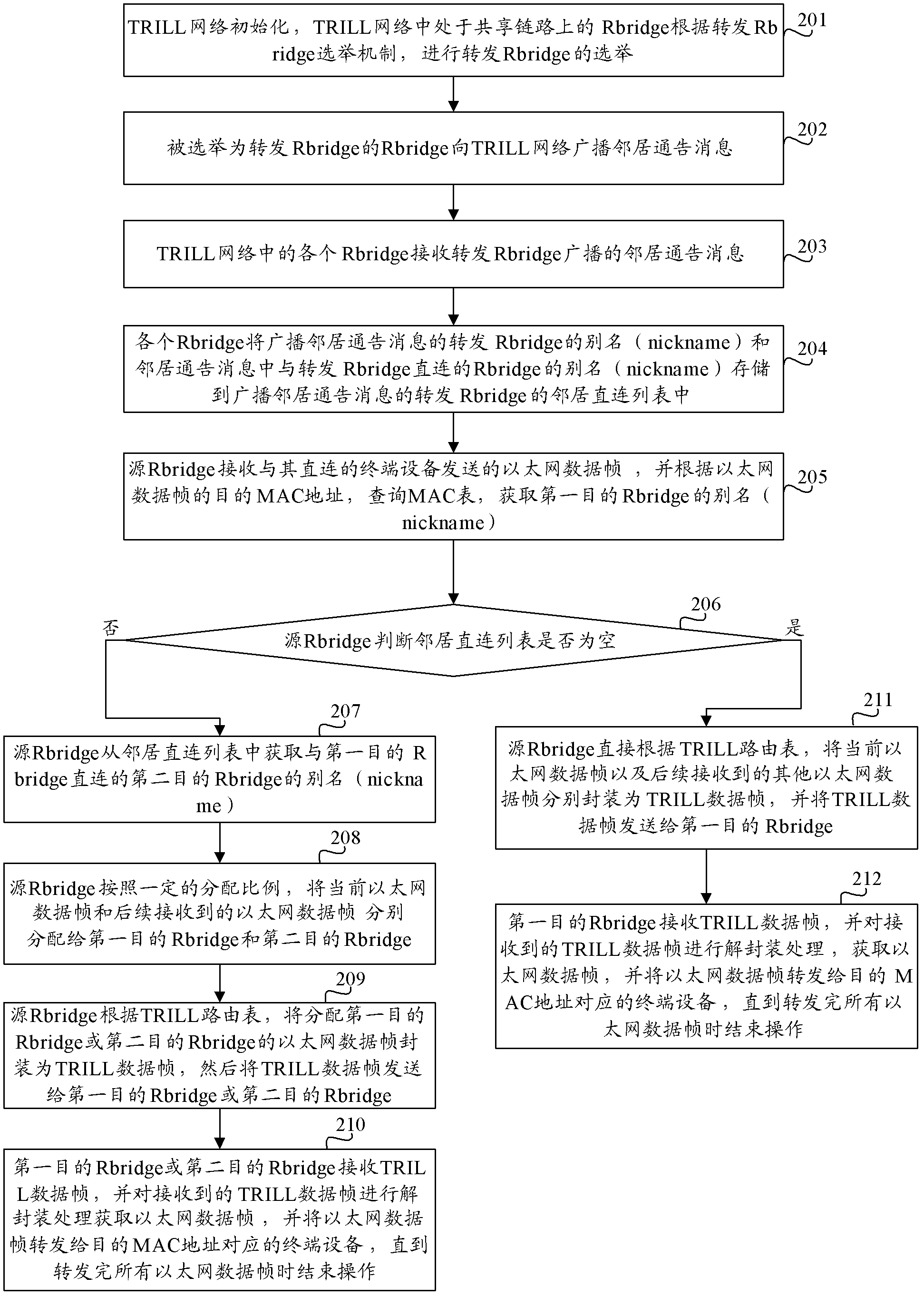
The invention provides a message forwarding method and system as well as a routing switch. The message forwarding method comprises steps of inquiring an MAC (Media Access Control) chart and obtaining an identification of a first target routing switch by a source routing switch according to a received target MAC address of the current Ethernet data frame; inquiring a neighbor connecting list of the first target routing switch and obtaining an identification of a second routing switch directly connected with the first target routing switch by the source routing switch according to the identification of the first target routing switch; and forwarding the Ethernet data frames and following received other Ethernet data frames with the same MAC address to a terminal device corresponding to the target MAC address through the first target routing switch and the second target routing switch by the source routing switch according to a TRILL (Transparent Interconnection of Lots of Link) routing table. According to the technical scheme of the invention, the waste of link bandwidth resources can be reduced, and the utilization rate of the link bandwidth resources is improved.
Owner:RUIJIE NETWORKS CO LTD
CAN (Controller Area Network) to Ethernet gateway with filtering function and data transmission method based on gateway
ActiveCN103812765AIncrease forwarding rateReduce consumptionNetwork connectionsTraffic capacitySearch data structure
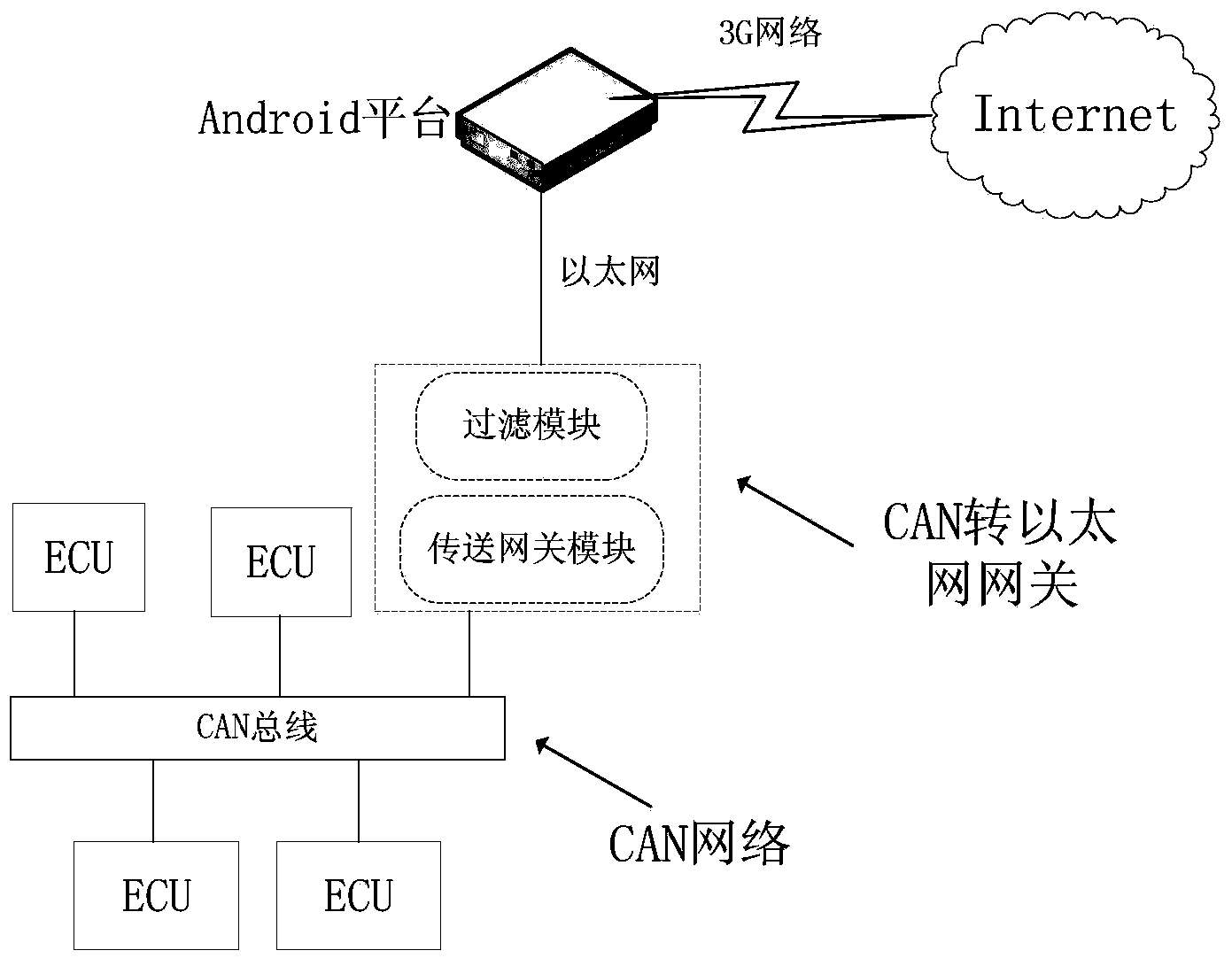
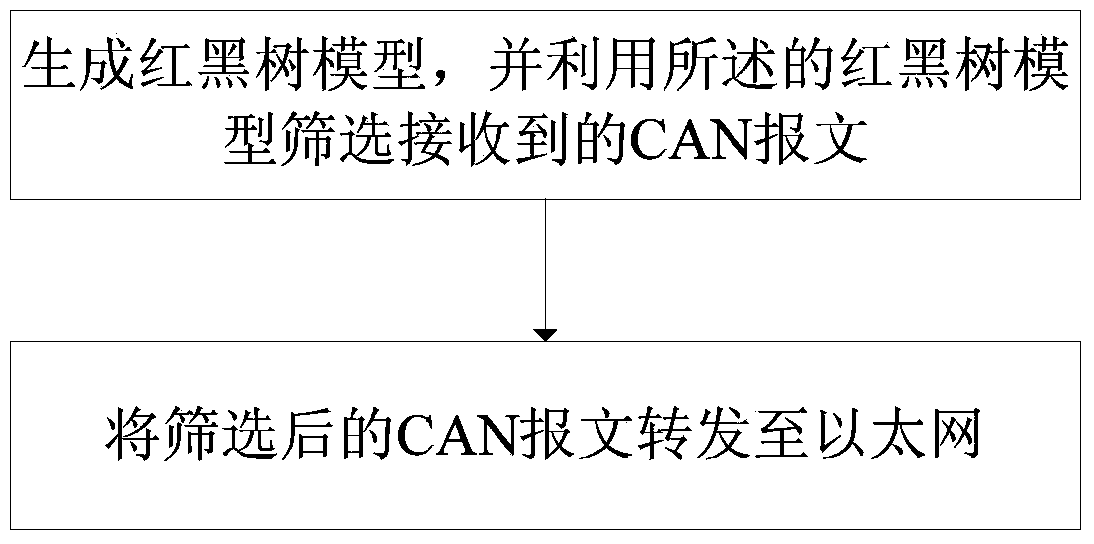
The invention discloses a CAN (Controller Area Network) to Ethernet gateway with a filtering function and a data transmission method based on the gateway. The CAN to Ethernet gateway with the filtering function comprises a filtering module for generating a red-black tree model according to the configuration of a host, and screening received CAN messages by using a red-black tree, and a transmission gateway module for forwarding the screened CAN messages to the Ethernet. The gateway is provided with the filtering module, the filtering module is used for screening the received CAN messages, and the transmission gateway module is used for only forwarding the screened CAN messages, thereby lowering the flow consumption. Moreover, by organizing a searched data structure through the red-black tree model, a judgment on whether received CAN messages have matched configuration or not can be made rapidly by searching the red-black tree to finish screening.
Owner:ZHEJIANG UNIV
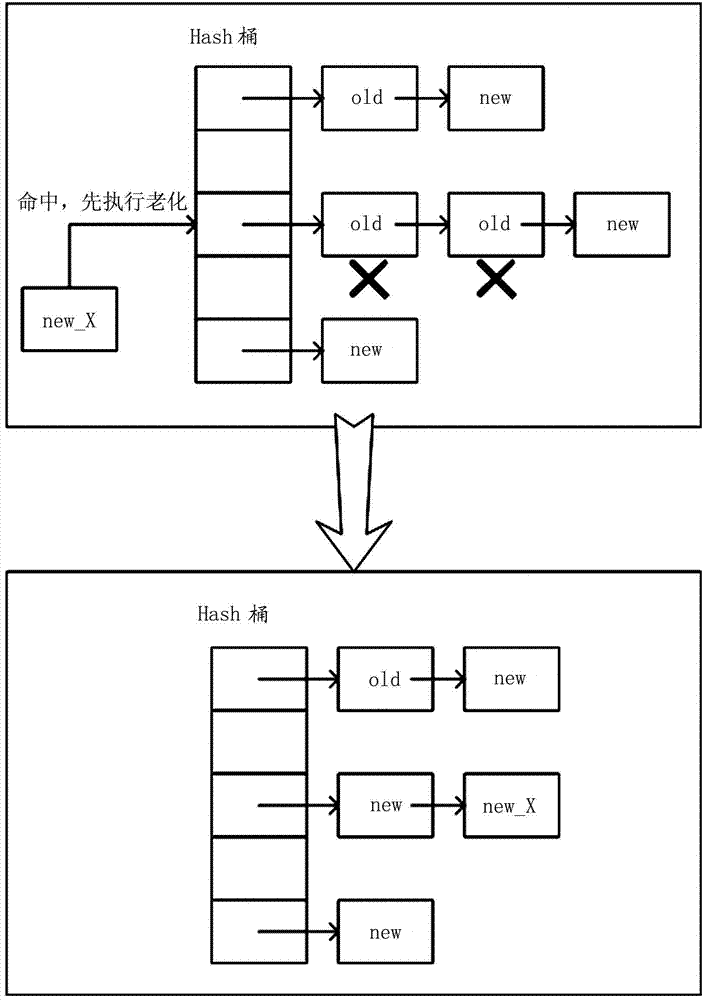
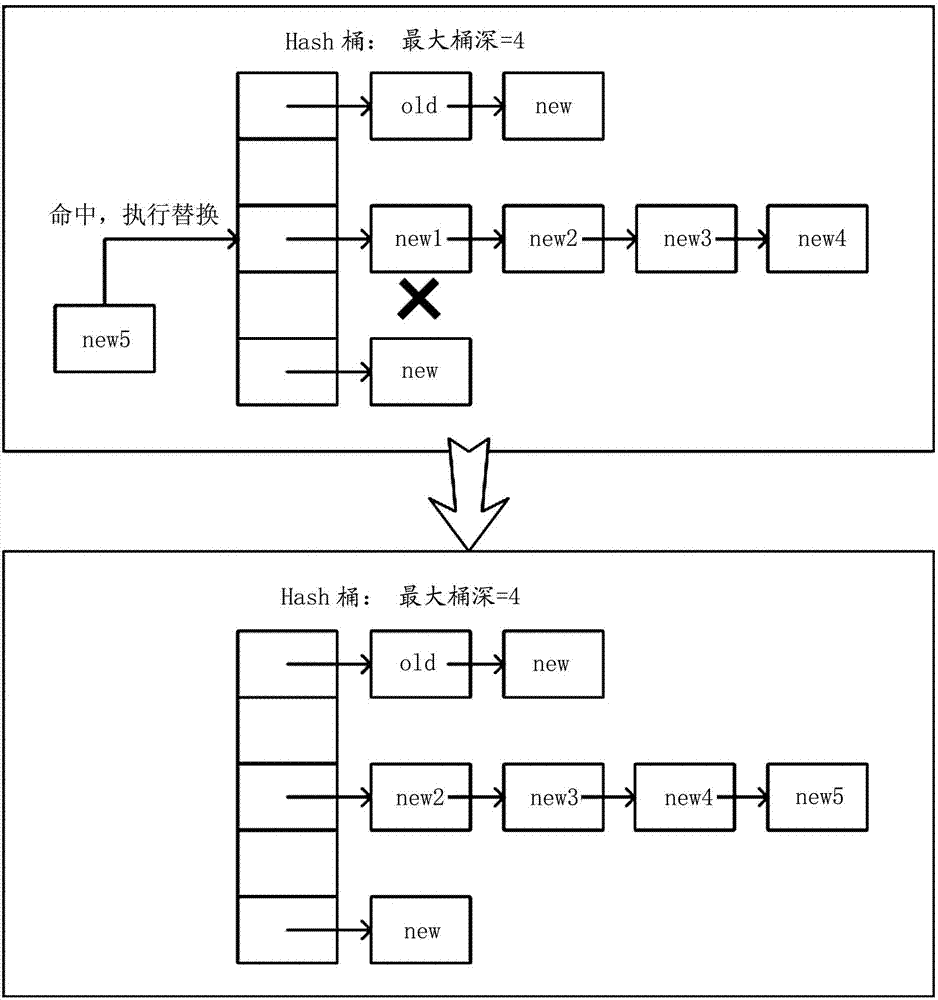
Flow table aging method and device of quick forwarding engine, and switch
ActiveCN102780641AImprove effectivenessIncrease forwarding rateData switching networksAge methodSoftware engineering
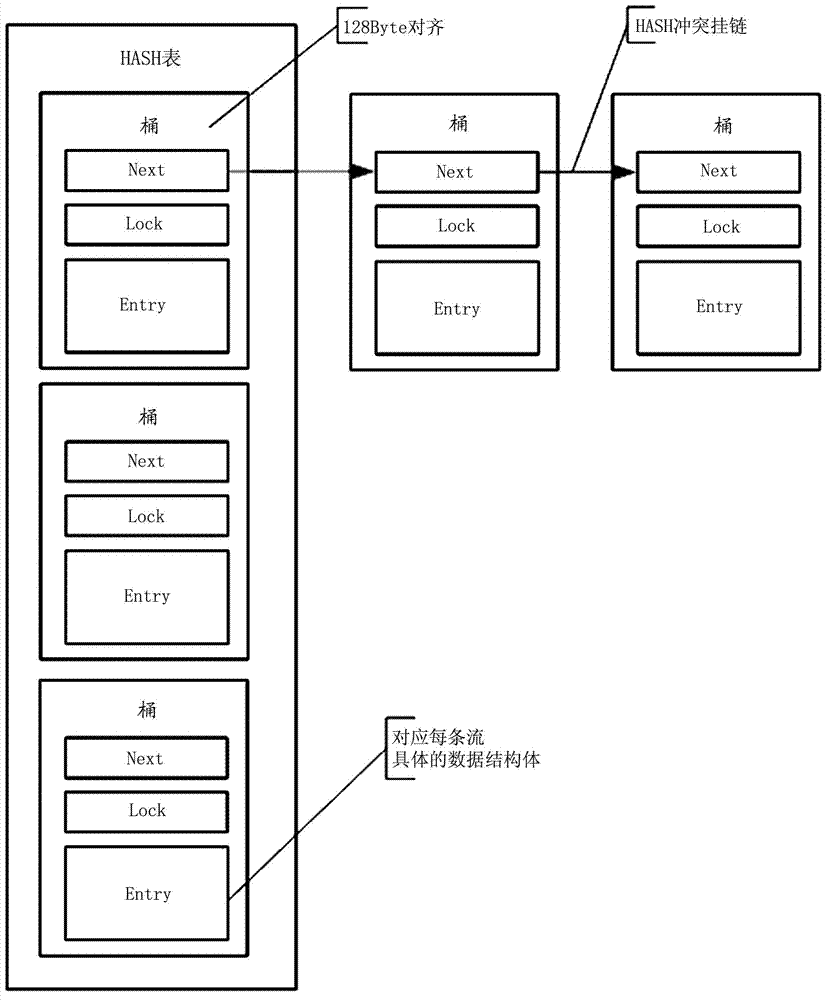
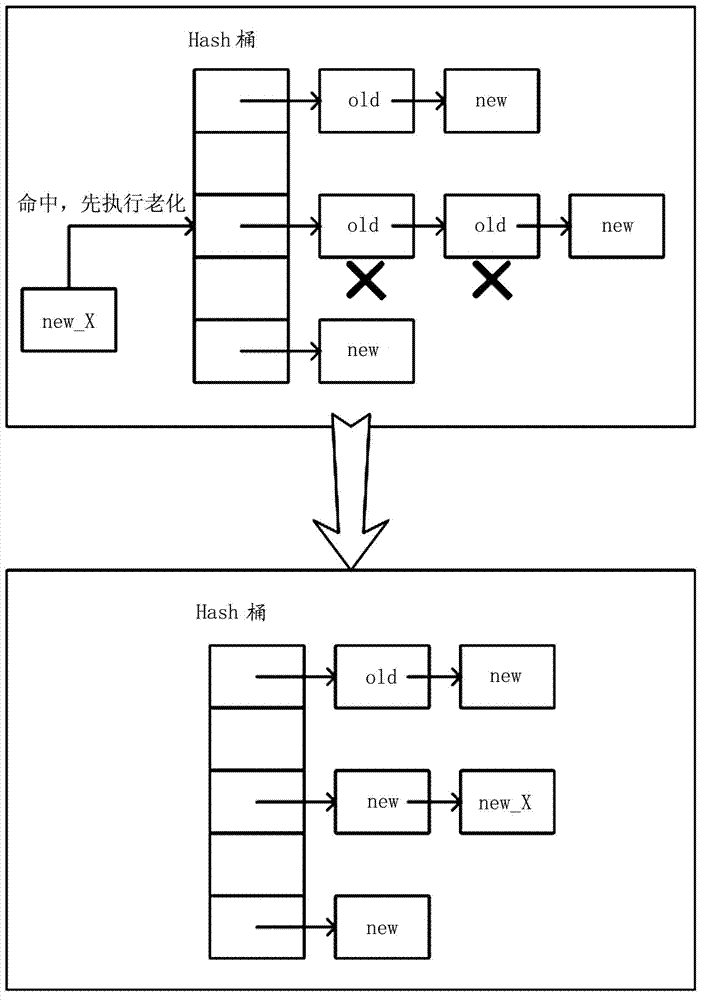
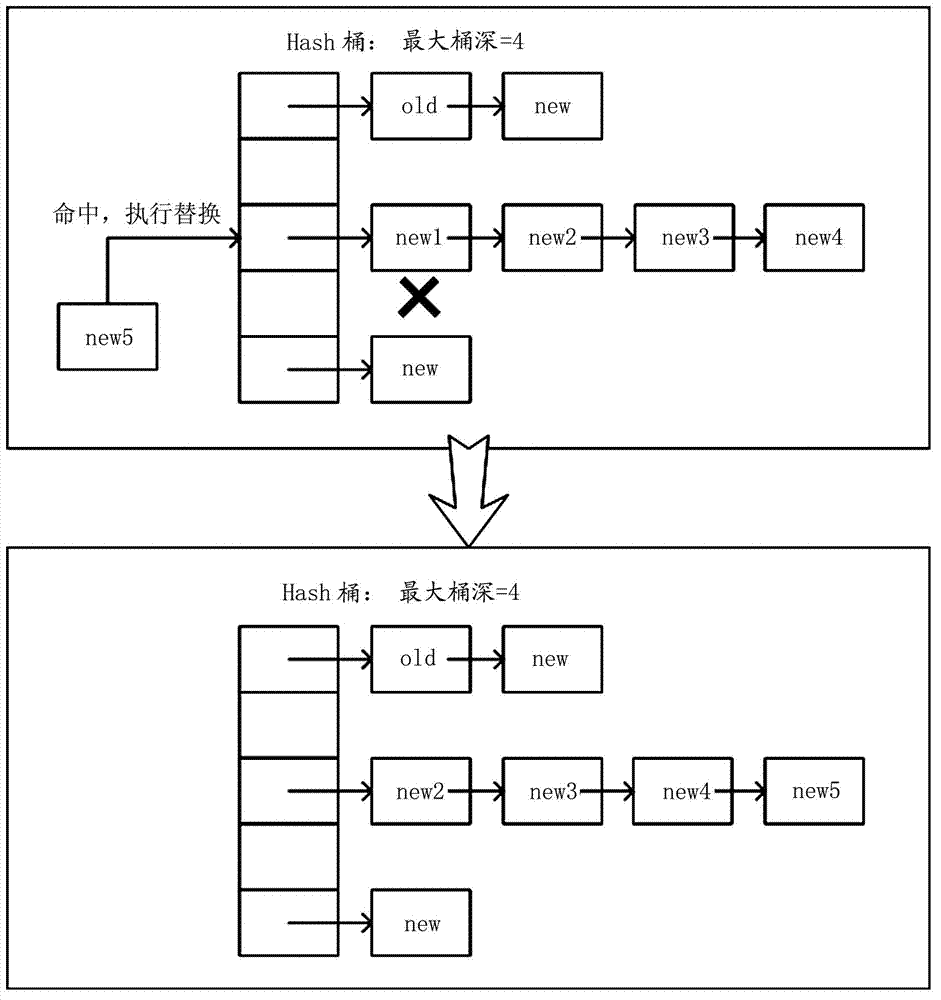
The invention provides a flow table aging method and device of a quick forwarding engine, and a switch. The flow table aging method of the quick forwarding engine comprises the following step: when Hash is matched with a Hash bucket comprising at least one flow table item through five-element information in a flow table in the form of a Hash table, deleting the flow table items of which the creating time is longer than a preset time period according to a creating time stamp of each flow table item in the matched Hash bucket.
Owner:BEIJING HAN NETWORKS TECH CO LTD
Hash Bloom filter (HBF) for name lookup in NDN and data forwarding method
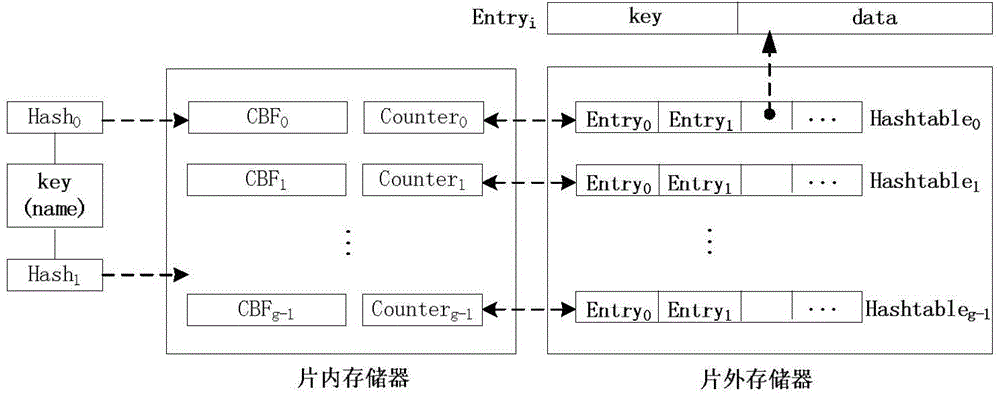
ActiveCN104579974ALower overall cost of accessReduce access overheadData switching networksComputer hardwareBloom filter
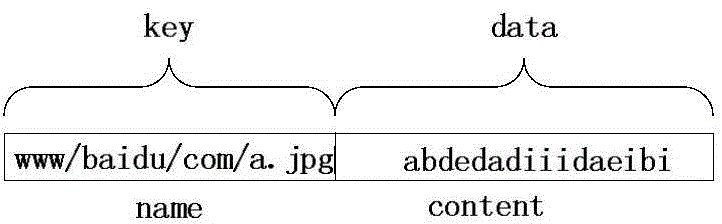
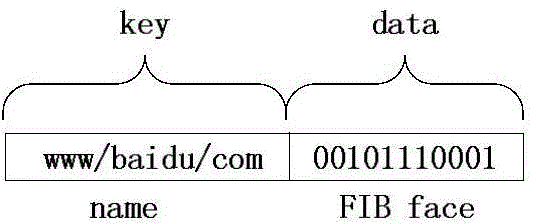
The invention discloses a Hash Bloom filter (HBF) for name lookup in an NDN and a data forwarding method. The Hash Bloom filter comprises g counter Bloom filters positioned in an on-chip memory, g counters and g Hash tables positioned in an off-chip memory, wherein each Hash table is associated with one counter Bloom filter and one counter; the Hash Bloom filter uniformly disperses and stores FIB / CS / PIT table entry complete information in an NDN router in the g counter Bloom filters and g Hash tables. The HBF utilizes the positioning and filtering functions of CBF in the on-chip memory to greatly reduce the access expenses of the off-chip memory, so that the overall access cost of the HBF is reduced, the data package forwarding rate is increased, and flooding attack is effectively avoided.
Owner:HUNAN UNIV
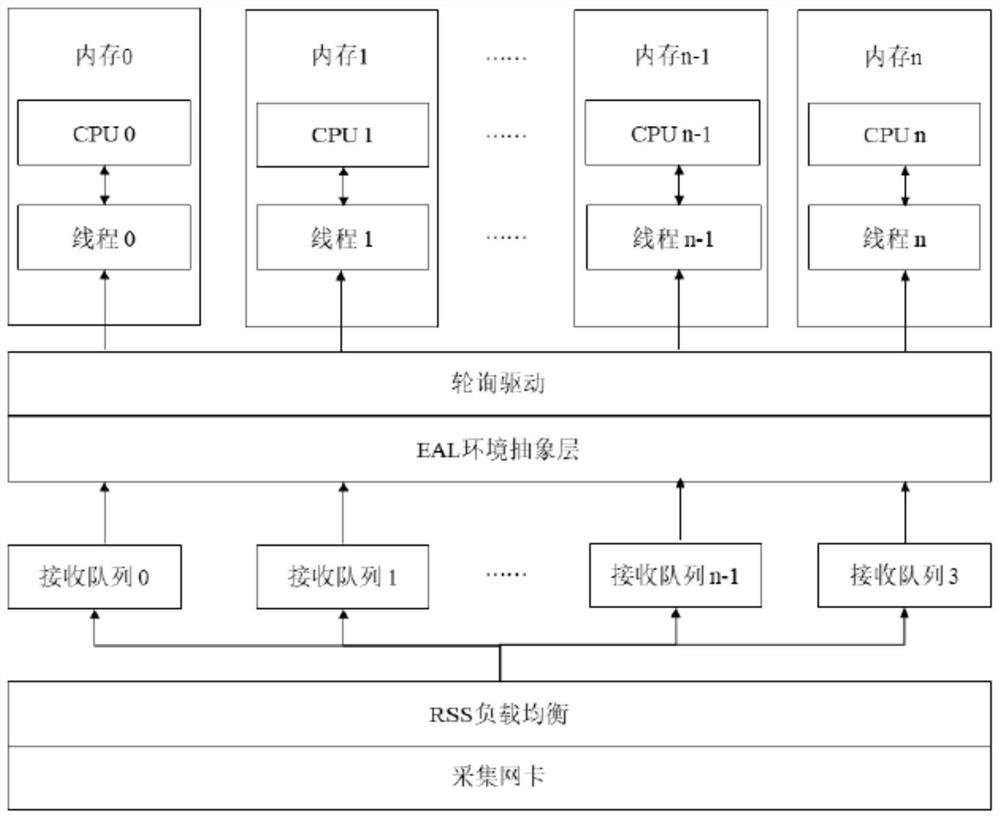
Firewall based on DPDK virtualization management system and implementation method thereof
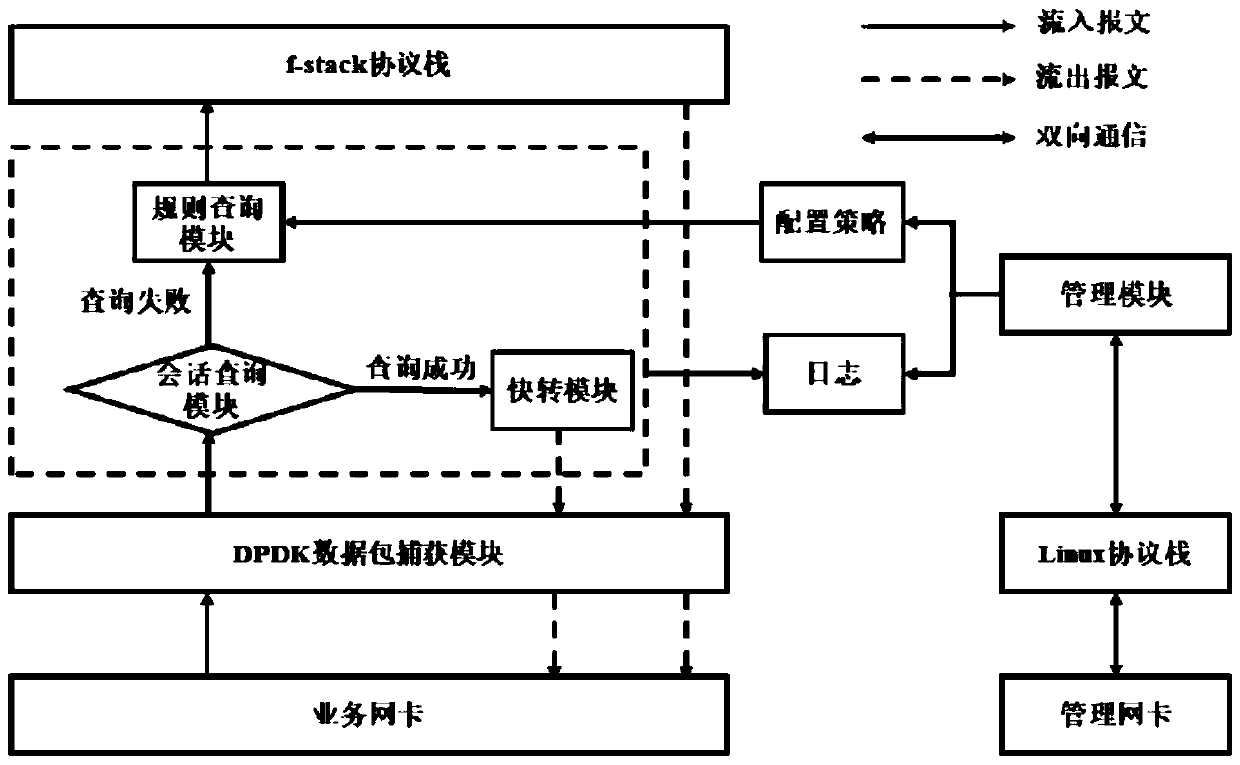
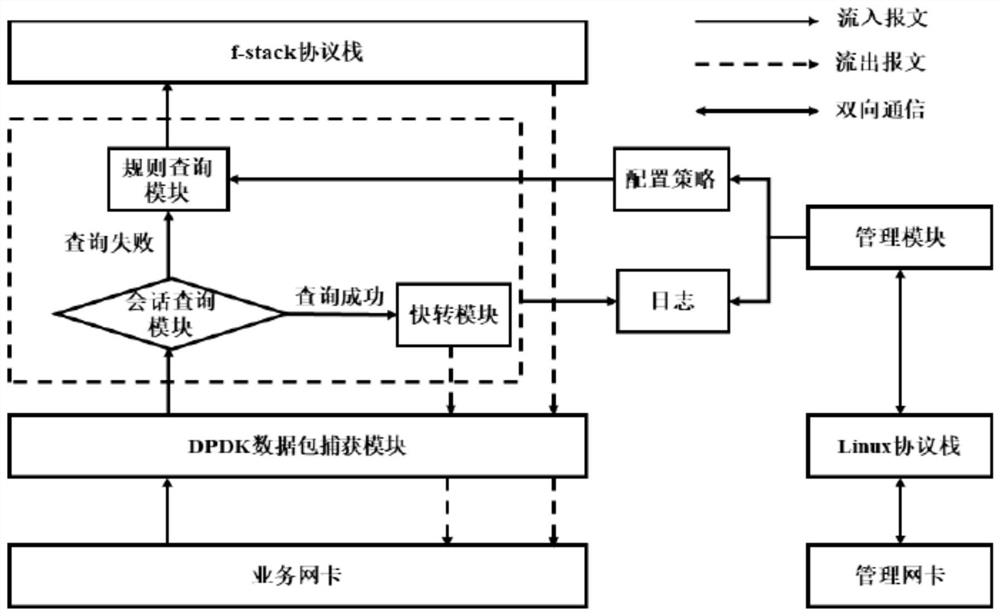
The invention provides a firewall based on a DPDK virtualization management system and an implementation method thereof. According to the invention, interruption is intercepted by using a DPDK pollingtechnology; according to the working principle that the UIO technology bypasses the kernel protocol stack and the message received by the network card is mapped to the user mode protocol stack f-stack through the UIO technology, the performance consumption during data packet capture is greatly reduced, and the data packet processing performance of the firewall is improved. A quick forwarding pathis added before a data packet enters an f-stack protocol stack; according to the method, session check is carried out on the data packet captured by the DPDK, and the flow of which the session is established is directly forwarded from the recorded port, so that the performance loss of the data packet in the process of passing through the protocol stack is reduced, the packet forwarding rate is improved, and the data processing performance of the firewall of the virtualization management system is further improved.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Address learning in a layer two bridging network
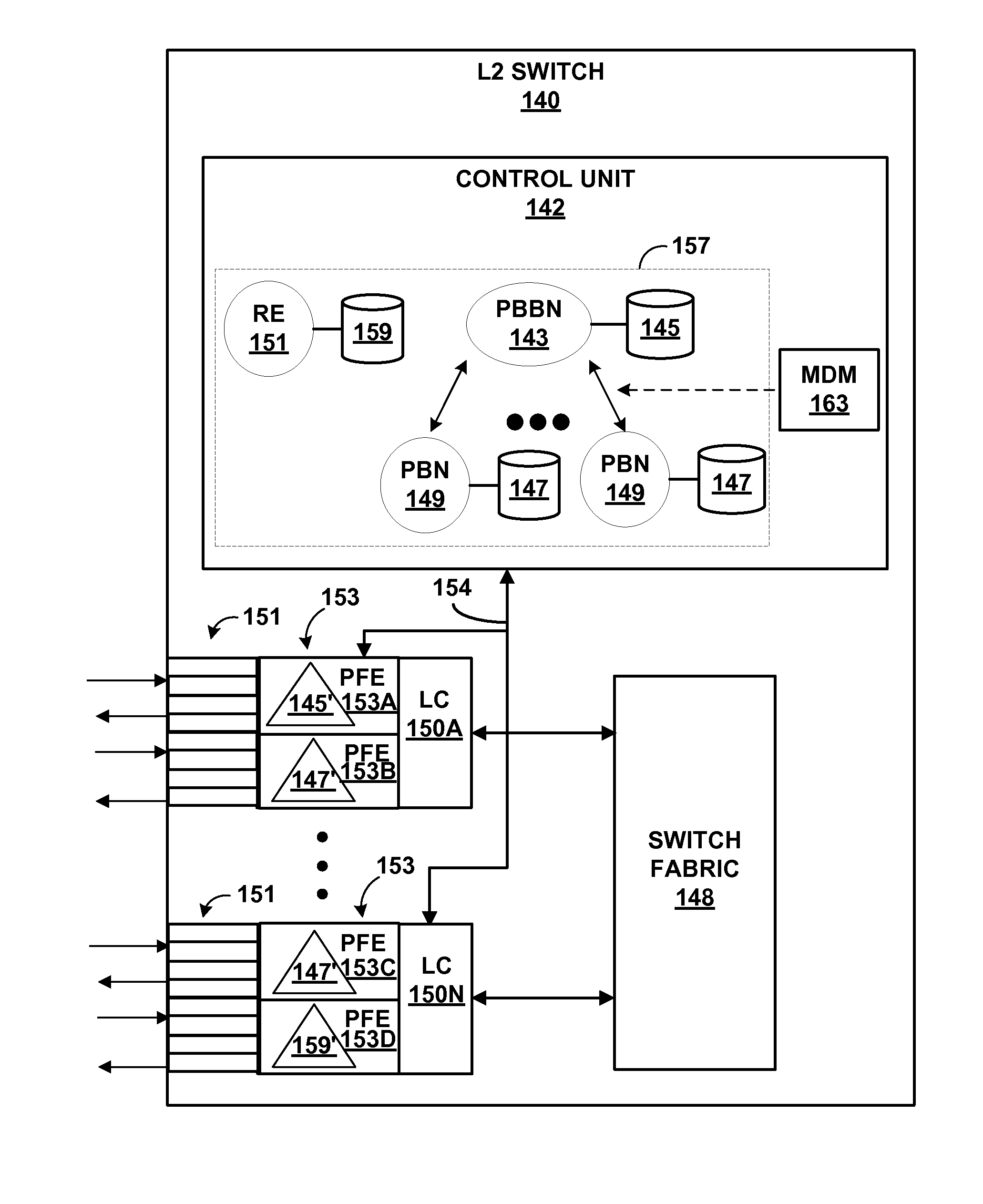
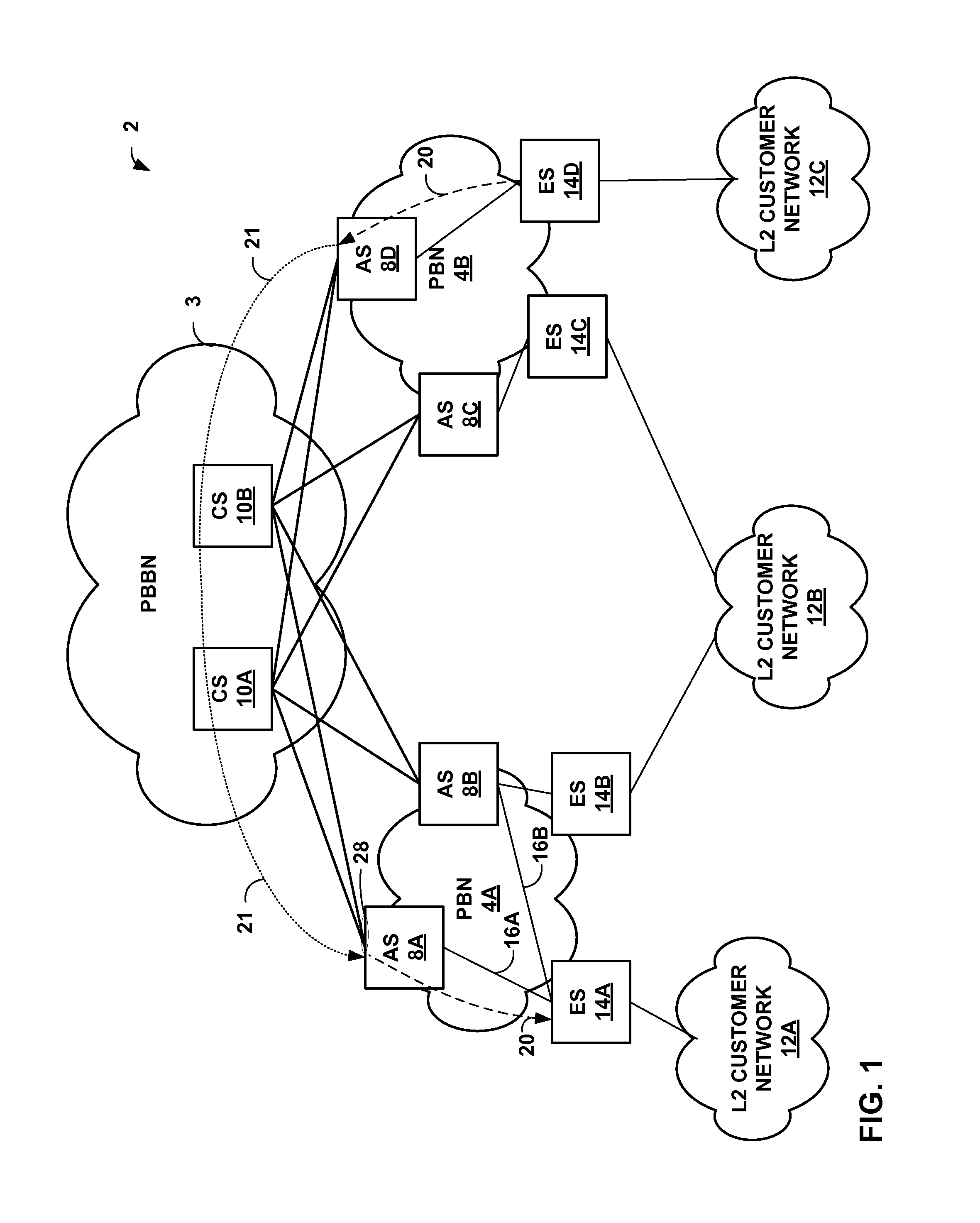
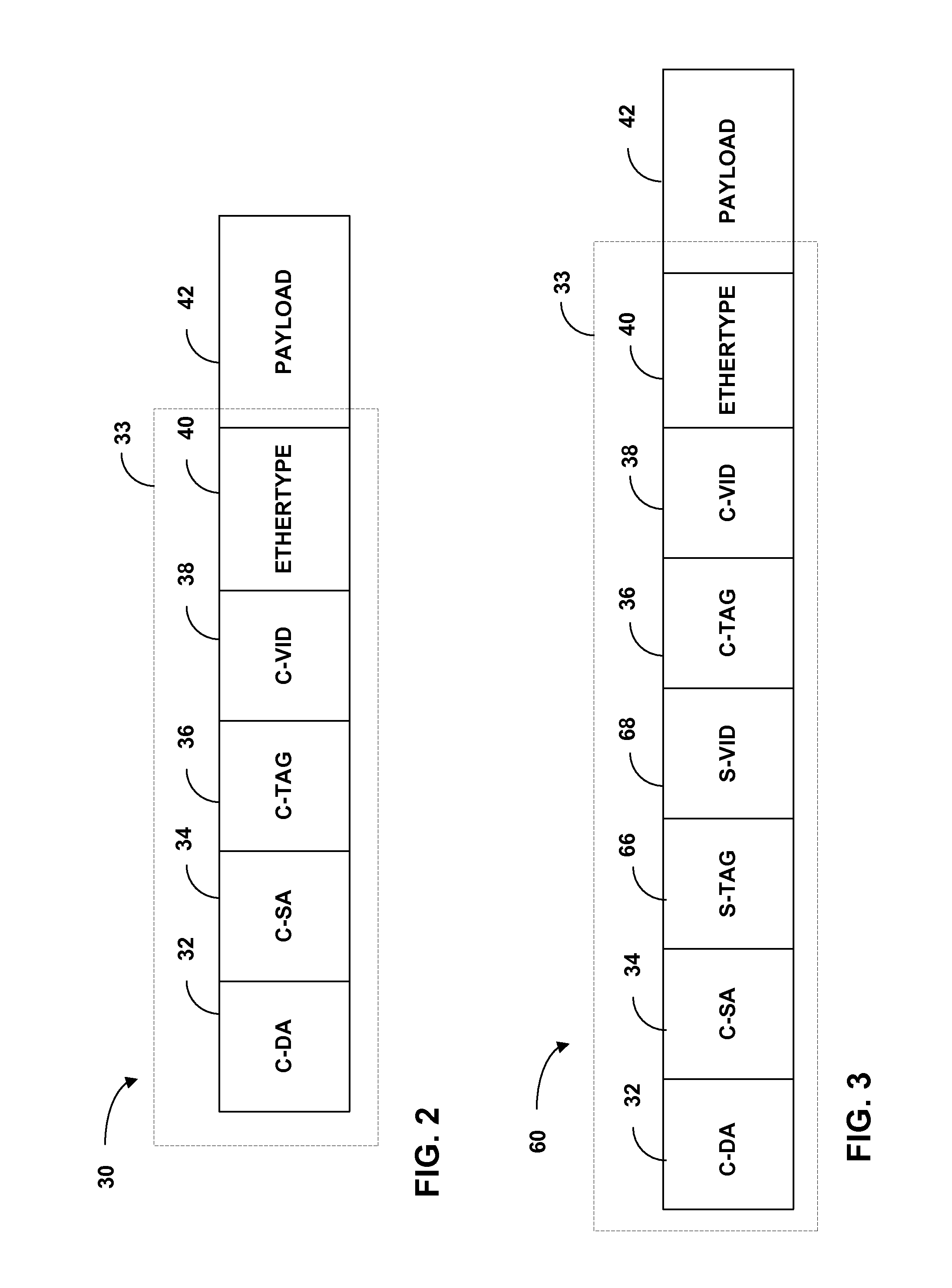
InactiveUS8520680B1Increase forwarding ratePrevent leakageData switching by path configurationNetwork addressingNetwork address
A network system includes a provider backbone bridged network (PBBN) and a multi-homed provider bridge network (PBN) having an L2 switch that operate as backboned edge bridge (BEBs) to bridge L2 packets between the PBN and the PBBN. The L2 switch executes a PBBN routing instance and a separate PBN routing instance. A plurality of packet-forwarding engine (PFE) of the L2 switch are configured to forward L2 packets between interfaces of the PBN routing instance and the PBBN routing instance. The PFEs store L2 network address tables that specify L2 network addresses reachable by the interfaces. The PFEs of the L2 switch are configured to selectively share L2 network addresses between the L2 network address tables of the PBN routing instance and the L2 network address tables of the PBBN routing instance.
Owner:JUMIPER NETWORKS INC
Collection method of subscriber network use data
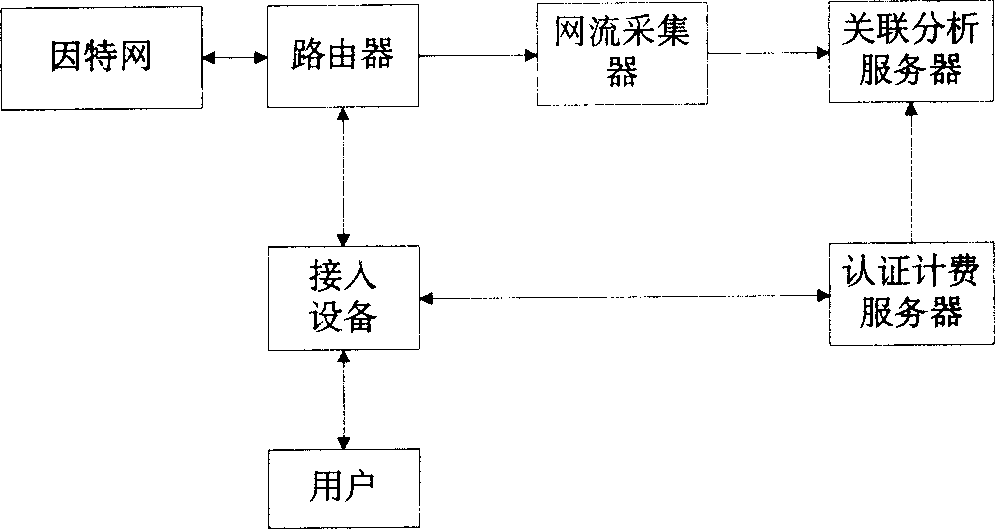
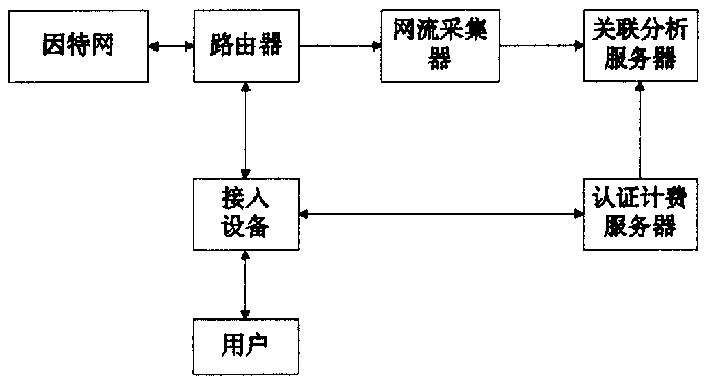
InactiveCN1494268ADoes not reduce forwarding rateIncrease forwarding rateMetering/charging/biilling arrangementsUser identity/authority verificationReal-time chargingAuthentication
Owner:HUAWEI TECH CO LTD
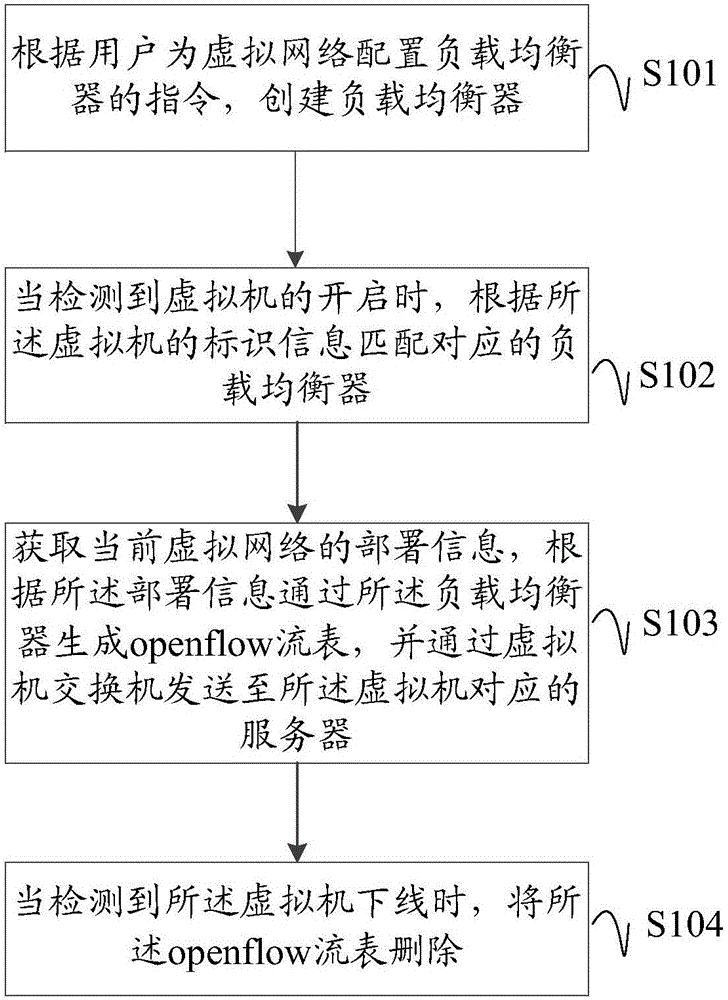
Method and device for realizing load balancing of virtual network
ActiveCN106850459AIncrease flexibilityImprove acceleration performanceResource allocationData switching networksVirtualizationTraffic capacity
The embodiment of the invention discloses a method for realizing load balancing of a virtual network. The method comprises the following steps: creating a load balancer of the virtual network, generating a load balancing flow table by the load balancer, and when detecting that a virtual machine is started, issuing a generated openflow flow table to a server that the virtual machine belongs to; and when detecting that the virtual machine is offline, deleting the previously generated flow table. With the migration of the virtual machine, the corresponding openflow flow table is added or deleted, which accurately reflects the flow characteristics of the virtual machine and realizes the load balancing of the virtual network. The method of the invention not only reduces the complexity of routing configuration, effectively guides packet forwarding, and enhances the data forwarding rate, but also increases the flexibility and scalability of the virtual network, and is beneficial to improving the overall working rate and data security of the virtual network. In addition, the embodiment of the invention further provides a corresponding implementation device, which further makes the method more practical and the device has the corresponding advantages.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
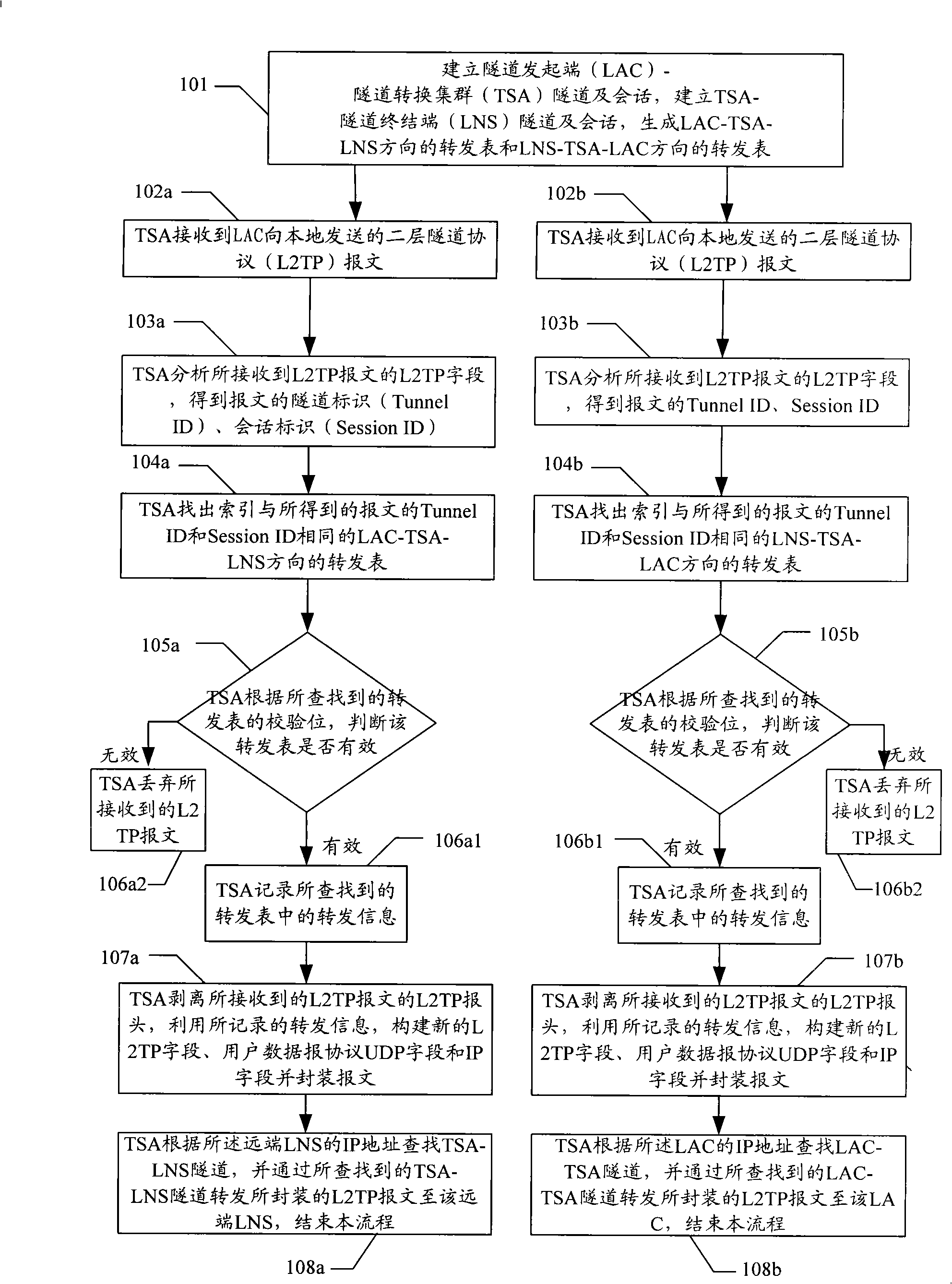
Method for implementing tunnel conversion of bi-layer tunnel protocol
ActiveCN101304387AIncrease forwarding rateSave resourcesNetworks interconnectionForward speedComputer science
The invention discloses a method for realizing tunneling conversion of two-layer tunneling protocol. The method establishes a TSA-tunnel terminal end LNS tunnel and a dialogue to distribute a forwarding table including the forwarding message with an LAC-TSA-LNS direction and the forwarding table with an LNS-TSA-LAC direction by establishing tunnel starting terminal LAC-tunnel conversion cluster TSA tunnel and a dialogue, which leads to get the conversion messages by searching the forwarding table one time in the process of forwarding LAC or the L2TP messages of the far end LNS forwarding TSA. The method of the invention can help reduce the occupied TSA resource by the static tunnel conversion, thereby further increasing the message forwarding speed.
Owner:ZTE CORP
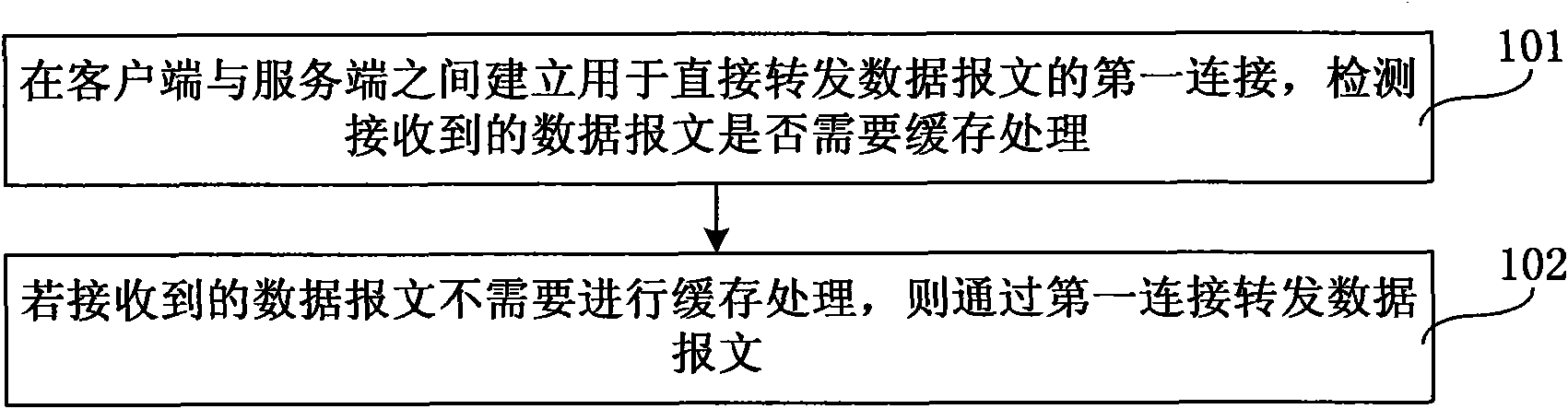
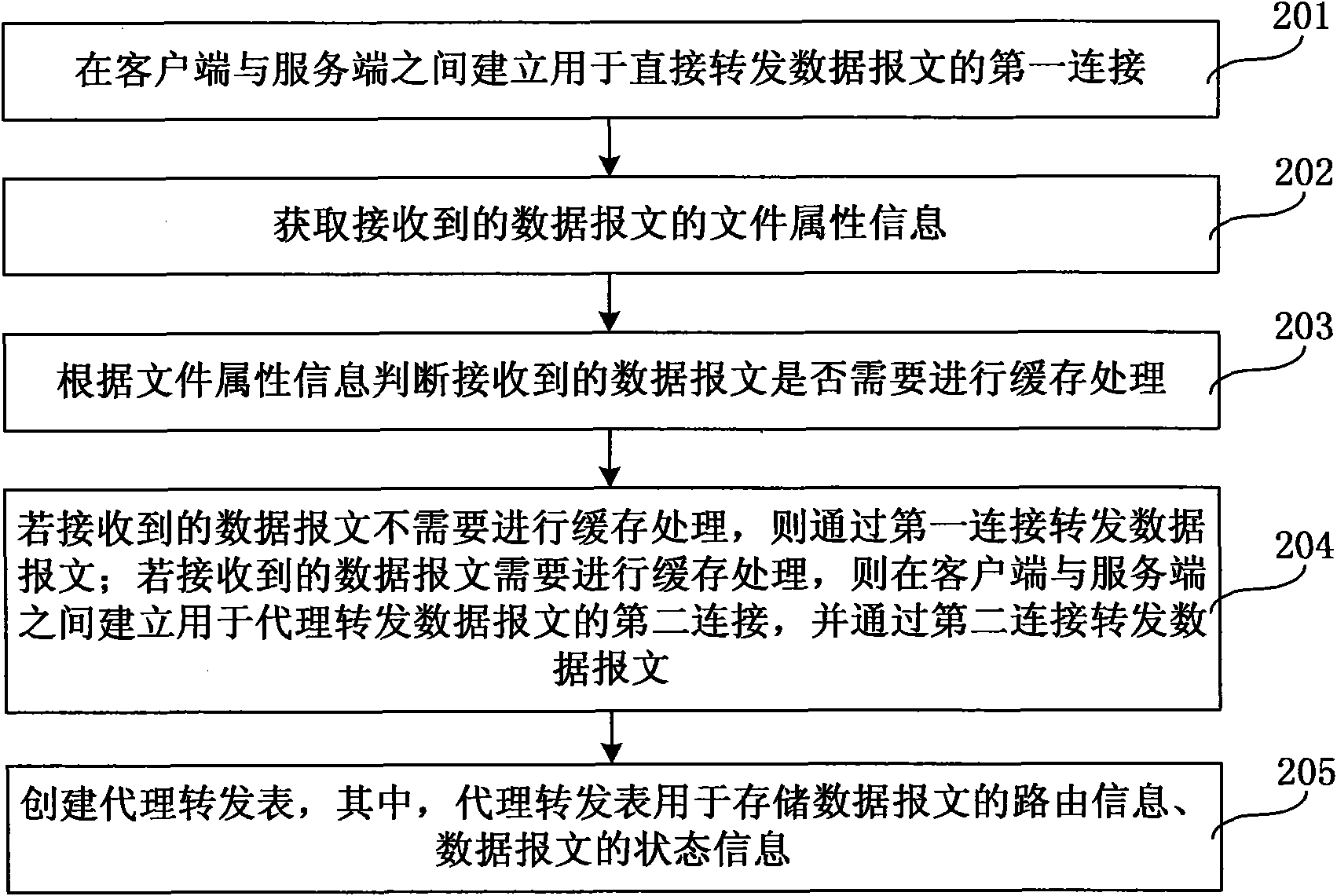
Network agent realizing method and device
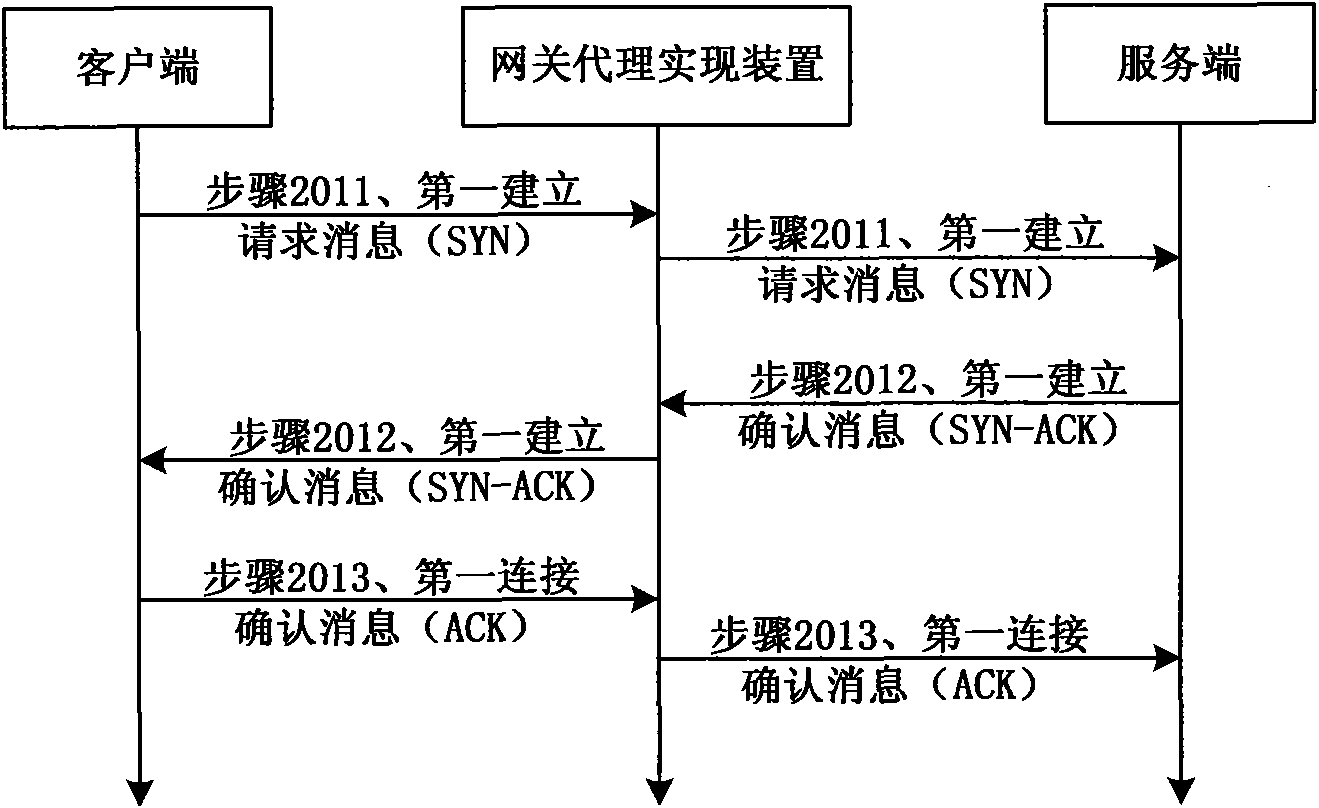
InactiveCN101645894AIncrease forwarding rateImprove processing efficiencyError prevention/detection by using return channelData switching networksNetwork agentClient-side
The embodiment of the invention relates to a network agent realizing method and a device, wherein the method comprises the following steps: establishing a first connection used for directly transmitting a data message between a client side and a service side, and detecting whether the received data message needs cache processing or not; if the received data message does not need cache processing,transmitting the data message through the first connection. Due to the fact that the network agent realizing method and the device detect whether the received data message needs cache processing or not, if when the received data message does not need cache processing, the data message is directly transmitted by the first connection, and data messages which do not require cache processing does notneed to be cached and transmitted, the transmitting speed and the processing efficiency of the data message are increased.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
Method for extending MPLS VPN access through public network and PE equipment
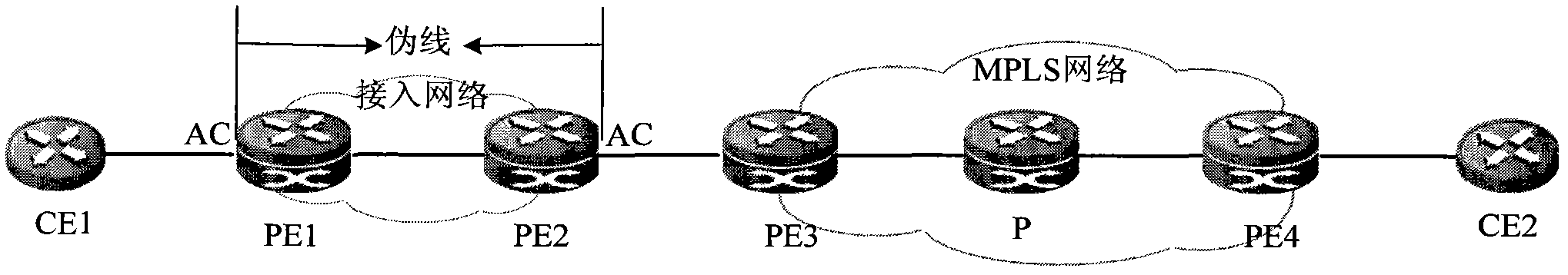
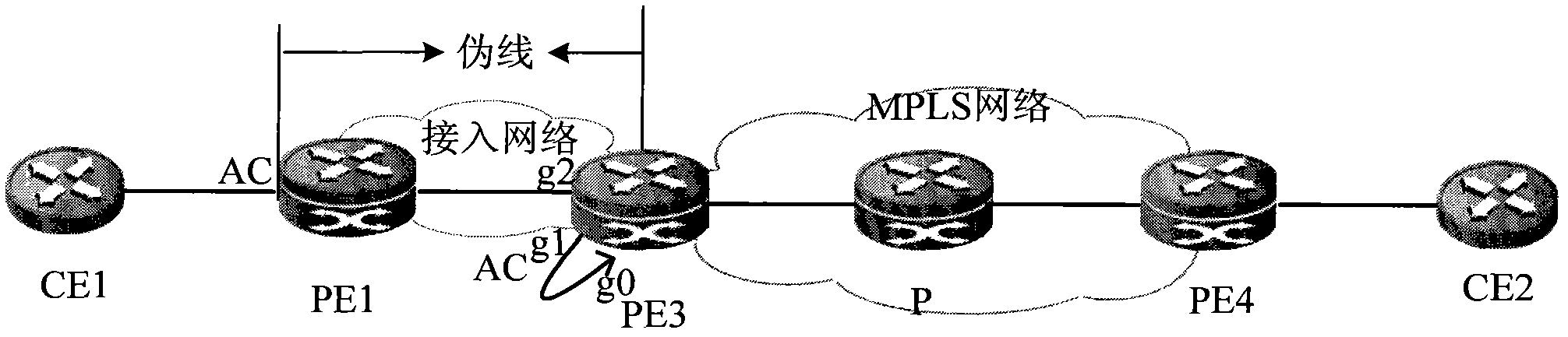
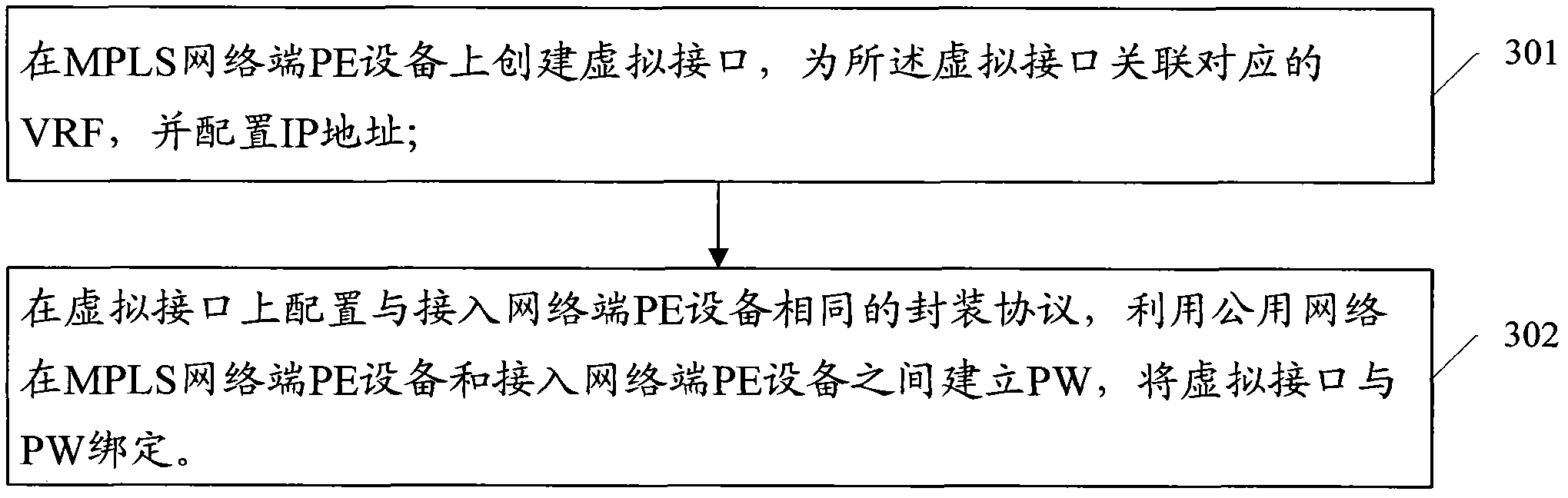
InactiveCN102082738AIncrease forwarding rateReduce transmission delayNetworks interconnectionPrivate networkIp address
The invention provides a method for extending multi-protocol label switching (MPLS) virtual private network (VPN) access through a public network and provider edge (PE) equipment. The method is applied to the public network comprising MPLS network PE equipment and access network PE equipment. The method comprises the following steps of: creating a virtual interface on the MPLS network PE equipment, associating corresponding virtual routing forward (VRF) for the virtual interface, and configuring an internet protocol (IP) address; and configuring the same encapsulation protocol as the access network PE equipment on the virtual interface, establishing a pseudo wire (PW) between the MPLS network PE equipment and the access network PE equipment by using the public network, and binding the virtual interface and the PW. The method can improve the forwarding velocity of the message and reduce the transmission time delay of the message.
Owner:MAIPU COMM TECH CO LTD
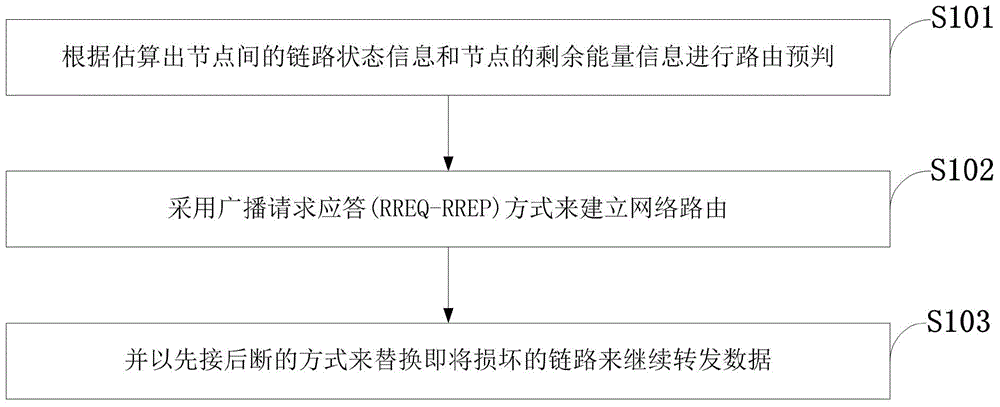
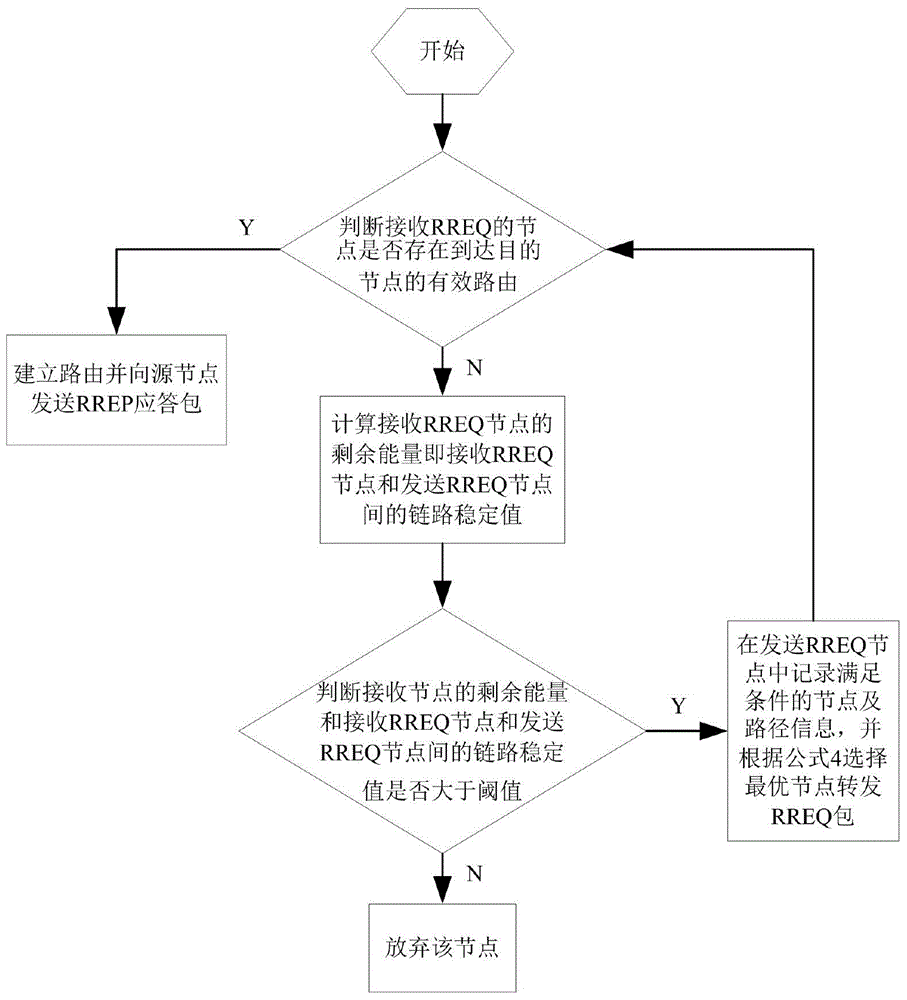
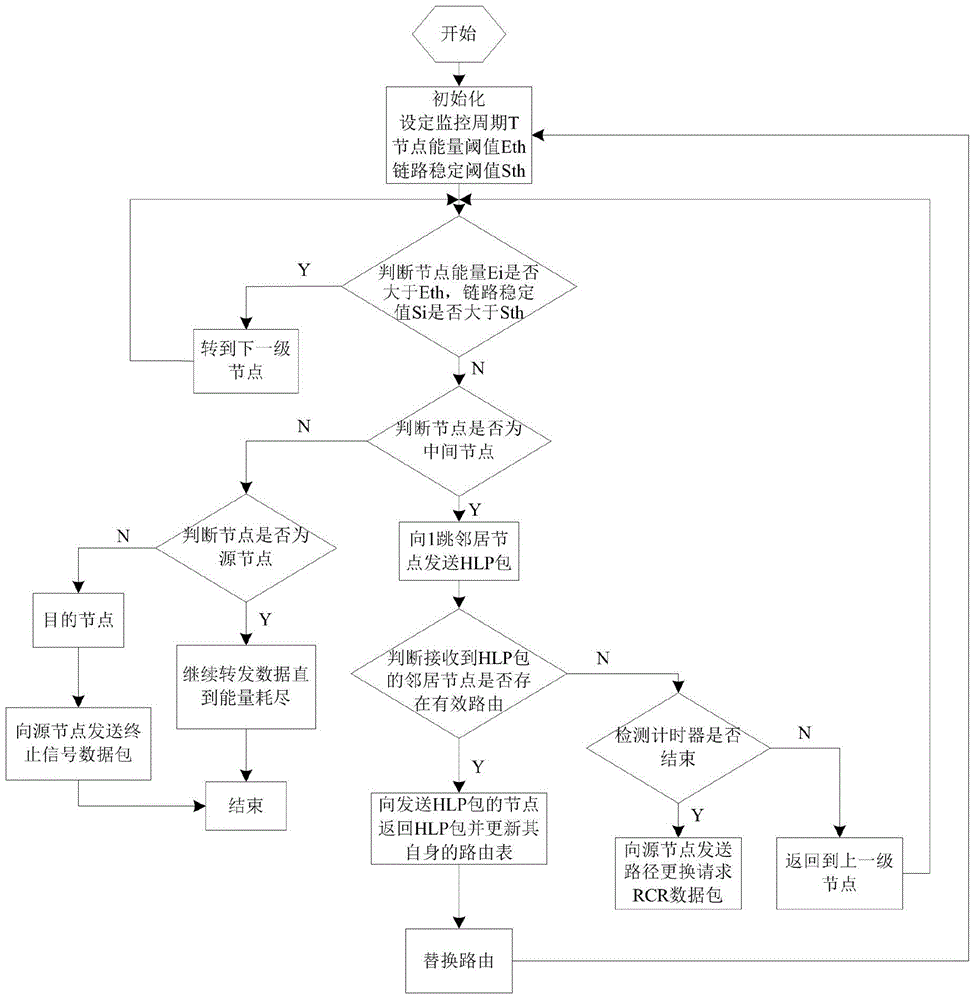
Internet-of-Things route repairing method based on link stability and energy sensing
ActiveCN103986648AImproved routing stabilityReduce energy consumptionData switching by path configurationRest energyEnergy sensing
The invention discloses an Internet-of-Things route repairing method based on link stability and energy sensing. The method comprises the steps that routing pre-judging is conducted according to the estimated link state information between nodes and the rest energy information of the nodes, a broadcast request-response mode is used for establishing a network route, a make-before-break mode is used for replacing links which are about to be damaged to continuously forward data, so that the stability of the route is improved, energy consumption of the nodes is saved, and the service life of the network is prolonged. According to the Internet-of-Things route repairing method based on link stability and energy sensing, a make-before-break route repairing mechanism is established, the performance index of link stability and the performance index of node energy are combined, the rest energy of the nodes and the link state information of the nodes are detected periodically, a replacing route for forwarding the data is actively established, the network overhead is effectively controlled, the data forwarding efficiency is improved, the network service life is prolonged, network delay is lowered, the stability degree of the network is improved, and the route keeping time of the network is prolonged.
Owner:ANHUI UNIV OF SCI & TECH
Downlink message forwarding method and AP device
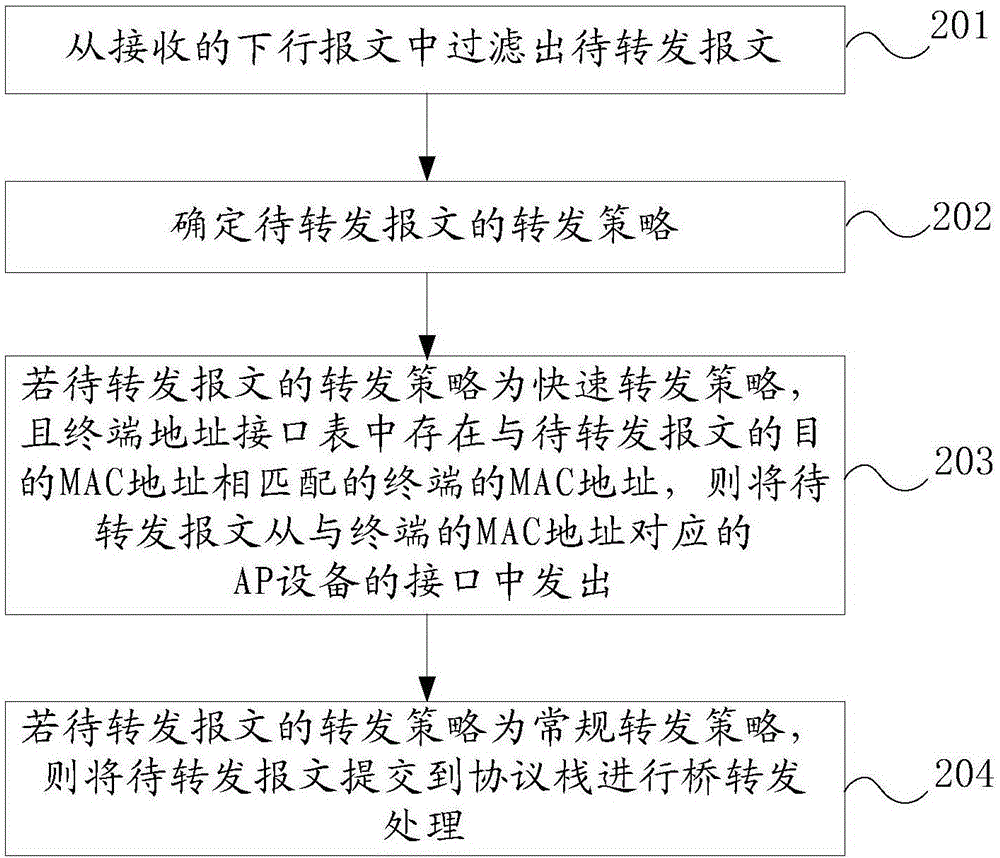
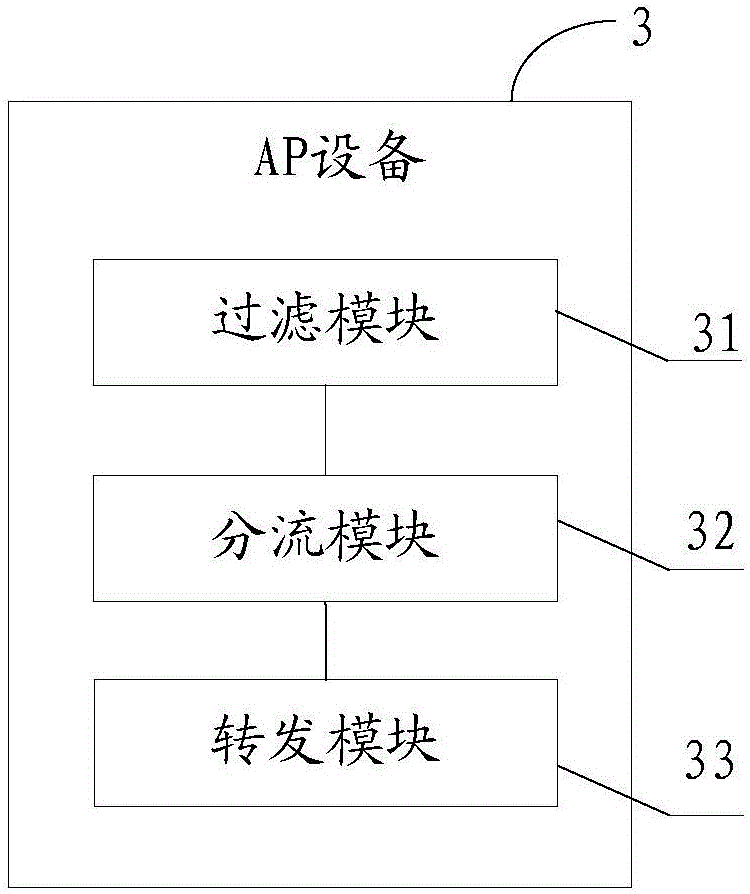
ActiveCN106685827AIncrease forwarding rateAvoid wastingData switching networksData connectionTerminal equipment
The embodiments of the invention provide a downlink message forwarding method and an AP device, relate to the technical field of communication, and aim to improve the speed of message forwarding. The method comprises the following steps: a wireless access point AP device filters out a message to be forwarded from received downlink messages, wherein the destination MAC address of the message to be forwarded points to the AP device or a terminal device in data connection with the AP device or the destination MAC address of the message to be forwarded is not a unicast address; determining the forwarding strategy of the message to be forwarded; if the forwarding strategy of the message to be forwarded is a fast forwarding strategy and there is a terminal MAC address matching the destination MAC address of the message to be forwarded in a terminal address interface table, sending the message to be forwarded from the interface of an AP device corresponding to the terminal MAC address; and if the forwarding strategy of the message to be forwarded is a conventional forwarding strategy, submitting the message to be forwarded to a protocol stack for bridge forwarding. The method and the device are applied to downlink message forwarding.
Owner:MAIPU COMM TECH CO LTD
Named data network forwarding method based on flow control
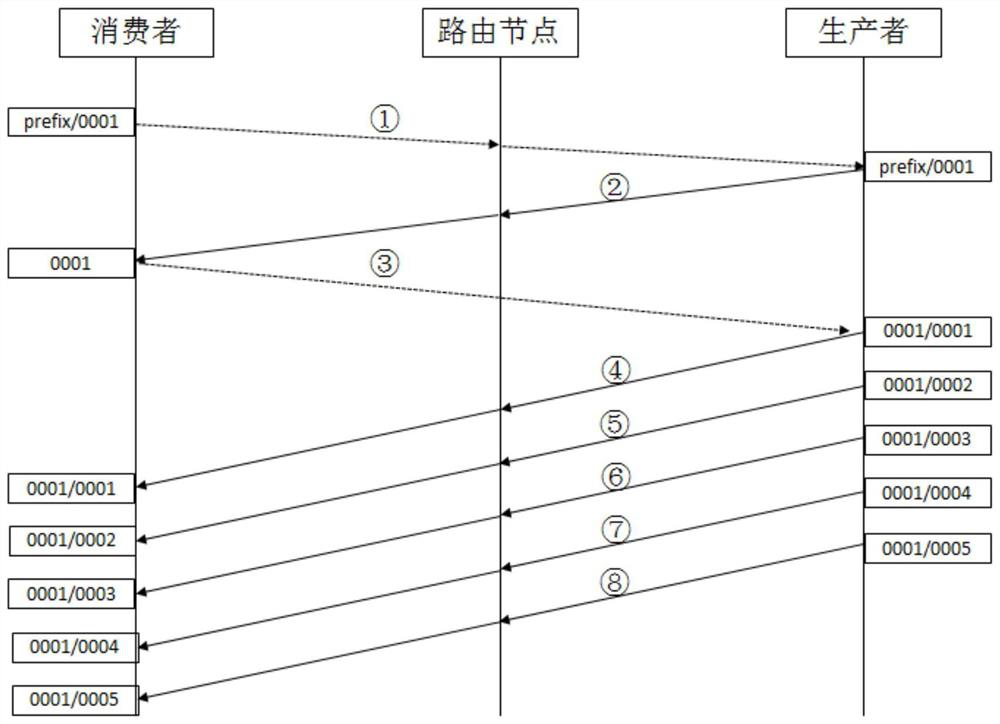
ActiveCN112039781AFast forwardingIncrease forwarding rateData switching networksHigh level techniquesStreaming dataData pack
The invention provides a named data network forwarding method based on flow control, and relates to the technical field of computer network data communication. The named data network forwarding methodbased on flow control comprises the following specific steps that S1, when a consumer applies for streaming media data or a large file, a streaming interest packet format is adopted, a streaming transmission sequence number (TSN) is allocated to an interest packet, and then the interest packet is sent out; S2, after arriving at an on-way routing node, if an intermediate routing node has the cachecontent matched with the transmission sequence number, the requested content is directly returned by the intermediate routing node; and if the intermediate node has no corresponding content, the interest packet is forwarded. By adopting a data flow control mode, a transmission serial number and a serial number are allocated to a flow data packet, and a consumer only needs to send two interest packets: a request flow transmission connection establishment interest packet and a flow transmission start interest packet, so that a producer can send all flow data to the consumer packet by packet insequence, and all the data can be pulled back at a time.
Owner:北京同创神州航天科技有限公司
FPGA-based network security acceleration card and FPGA-based network security acceleration method
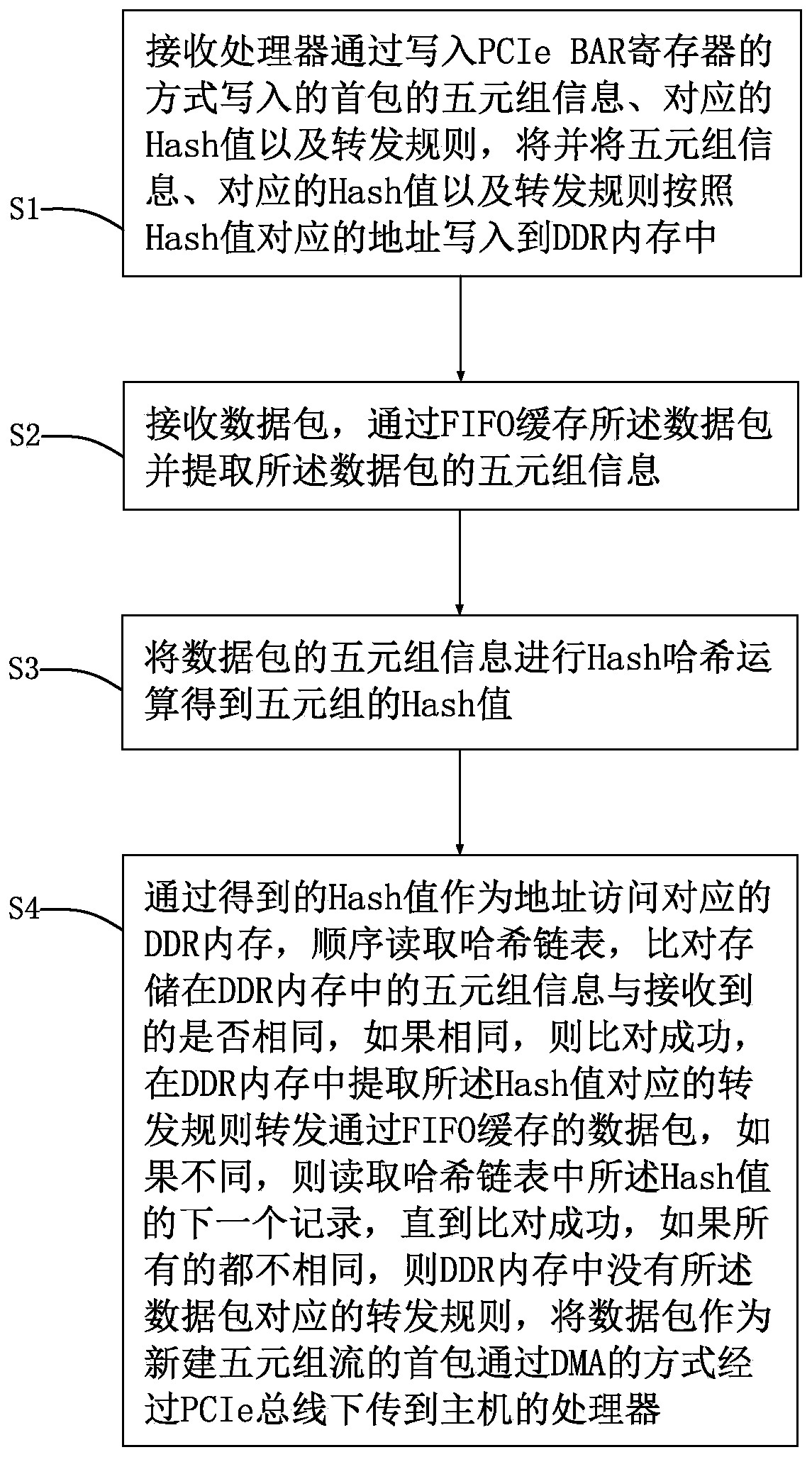
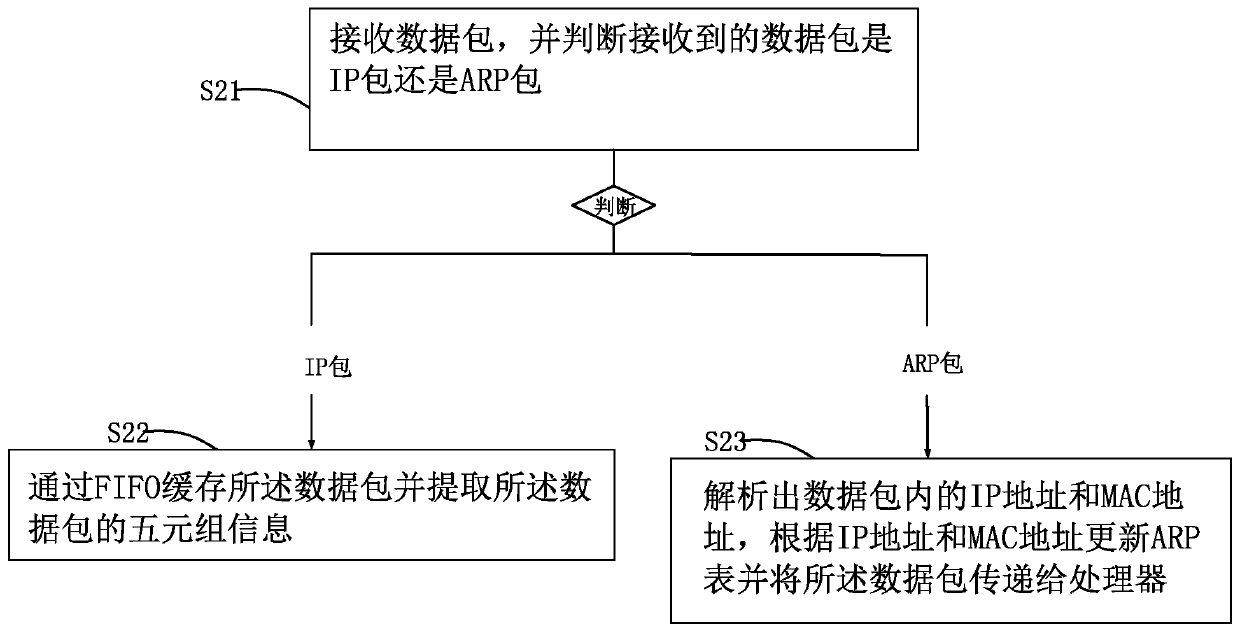
PendingCN111597142AIncrease forwarding rateArchitecture with single central processing unitElectric digital data processingComputer hardwareEngineering
The invention belongs to the technical field of data transmission, and particularly relates to an FPGA-based network security acceleration card and an FPGA-based network security acceleration method.The invention provides a novel FPGA-based network security acceleration card and a novel FPGA-based network security acceleration method. According to the FPGA-based network security acceleration cardand the FPGA-based network security acceleration method, a classic quintuple accurate matching flow forwarding mode is adopted to process network messages; and network processing shunting can be carried out on the processor, so that the processor can be liberated from heavy work, and some things which must be done by the processor can be handled, and the data forwarding rate can be further improved.
Owner:北京光润通科技发展有限公司
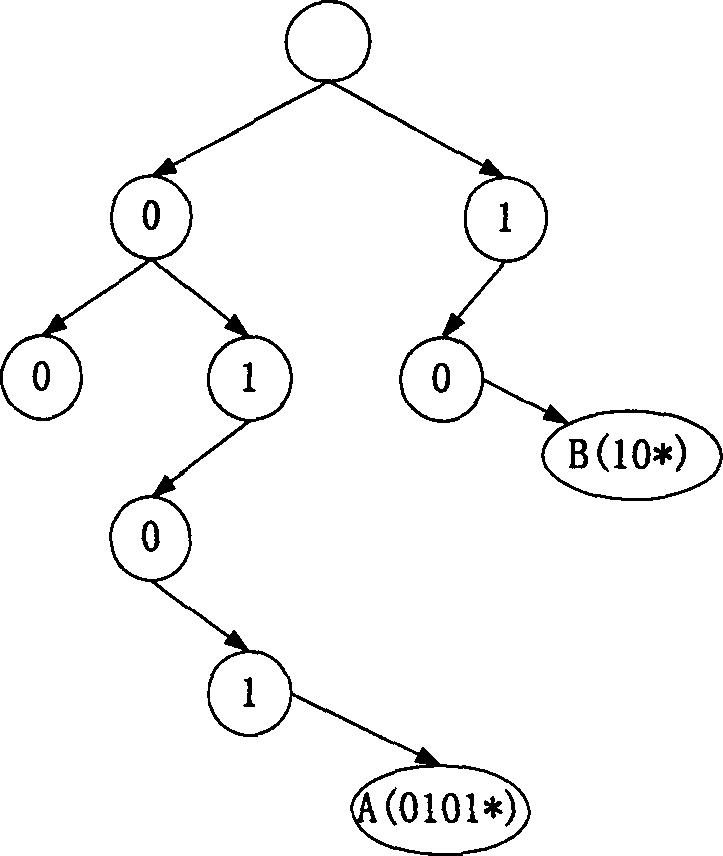
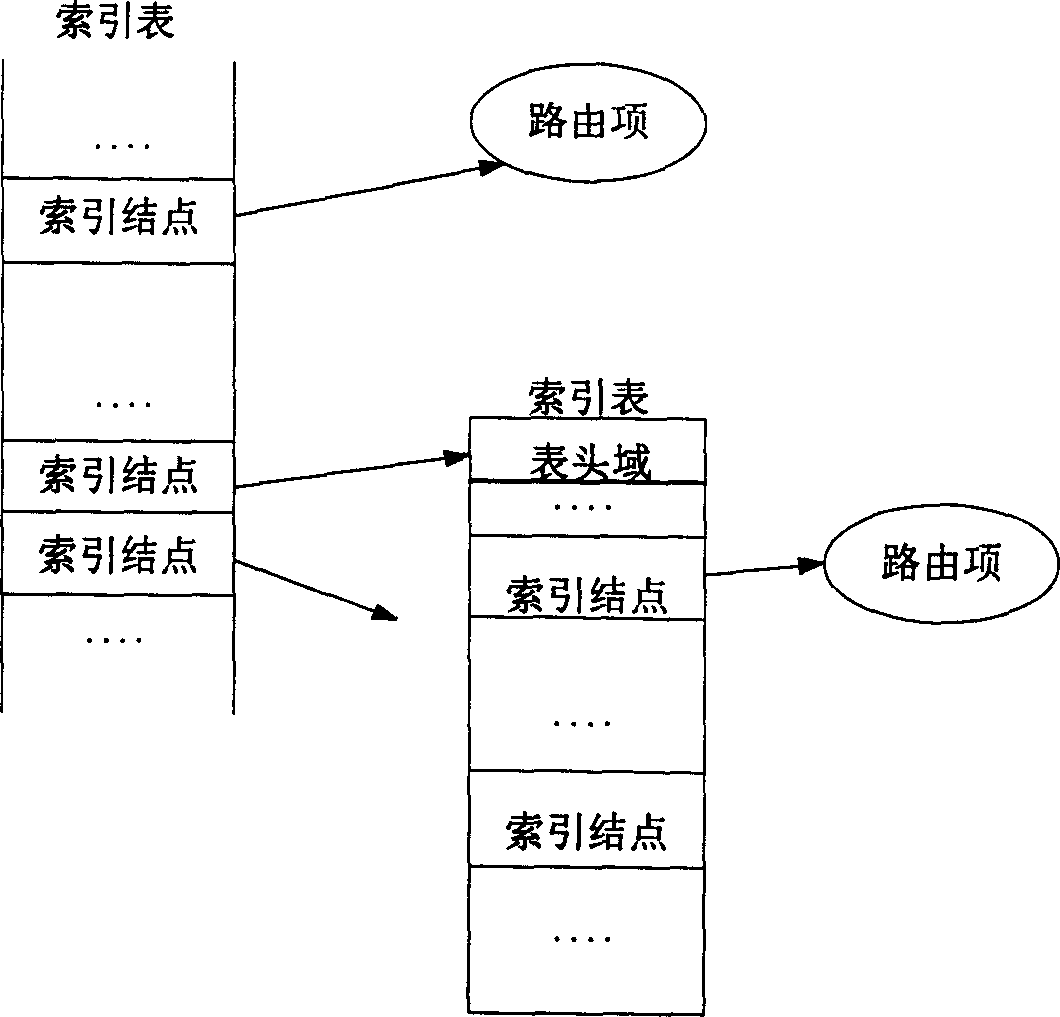
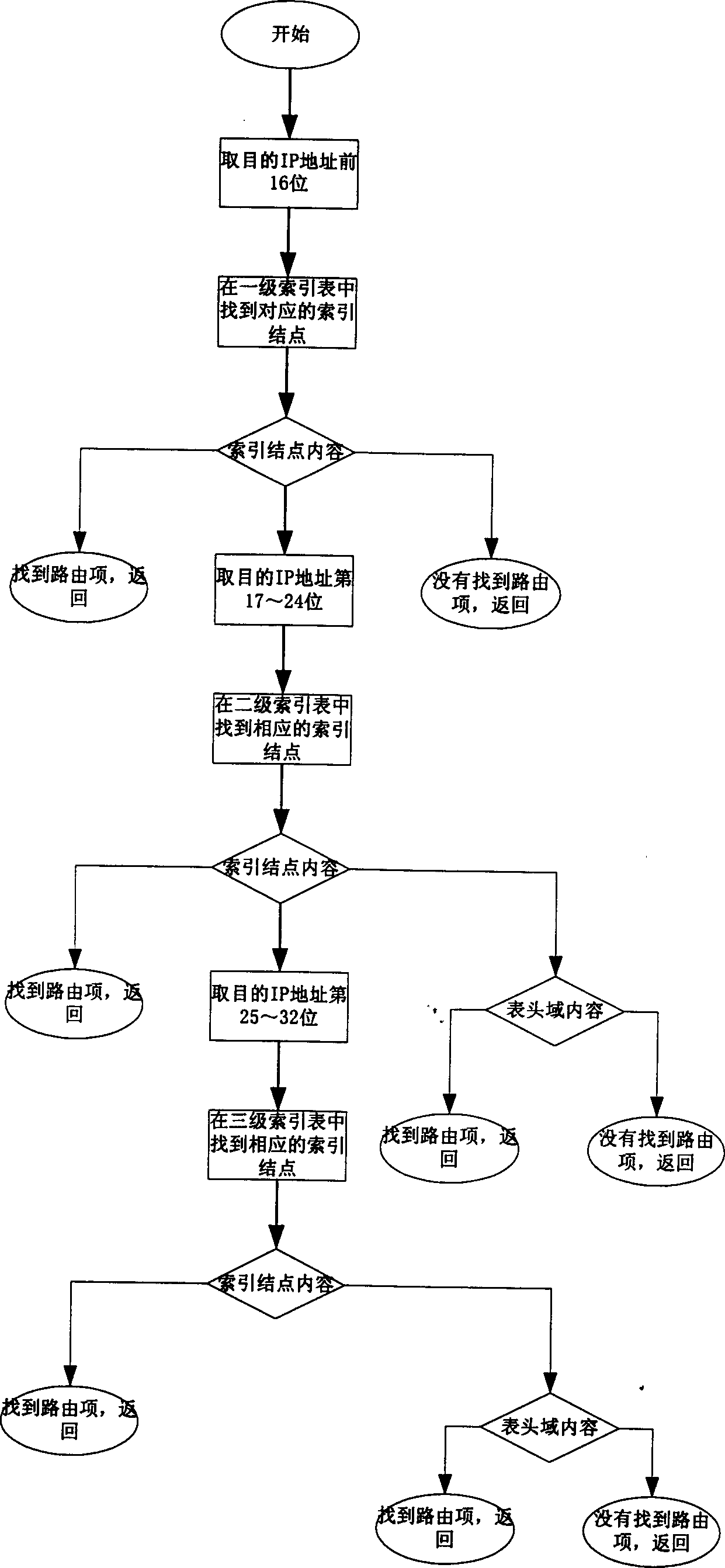
Method for building-up route table and searching route items thereby
InactiveCN1553655AImprove search efficiencySolve problemsData switching by path configurationSelection arrangementsRouting tableComputer science
This invention is relative to a method for constructing routing list and looking up route entry by using the routing list. It includes generating one level or multi level index table; stores the route entry in the above index table according to length of each level index table. The invention has following advantages: easy to maintain, fast looking up the route entry, and automatically expanding.
Owner:HUAWEI TECH CO LTD
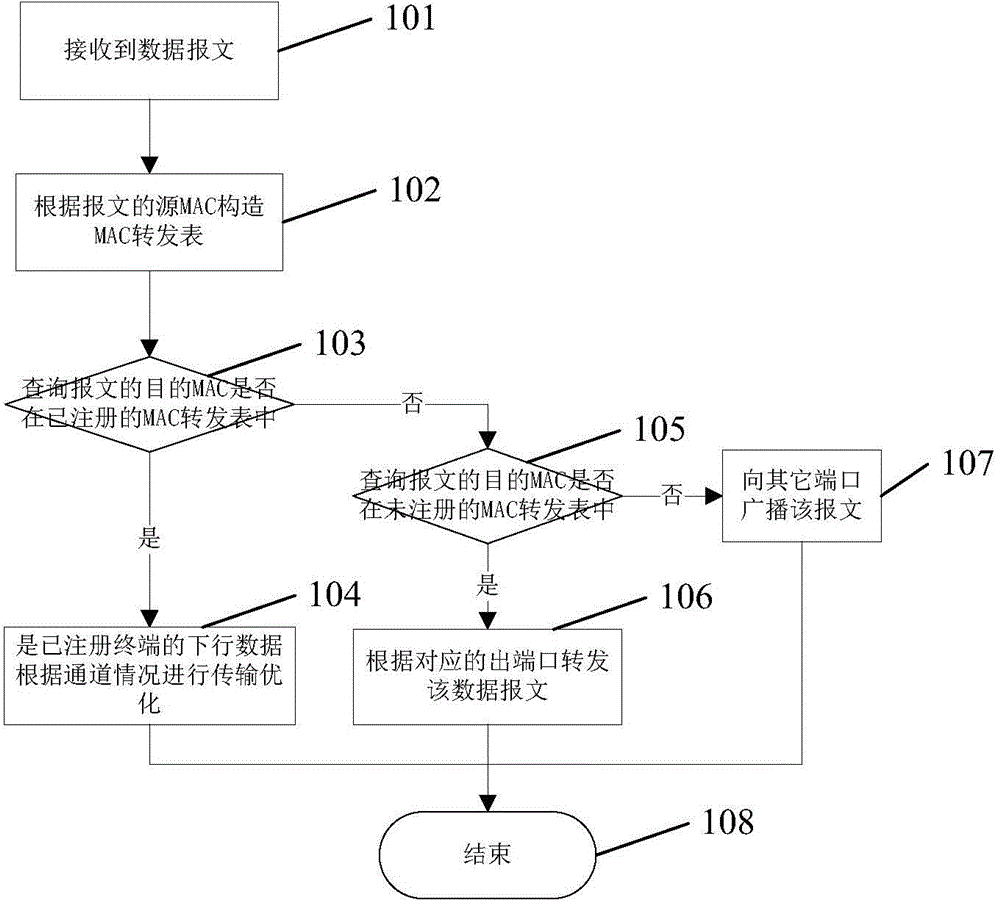
Forward processing method of data message in access gateway
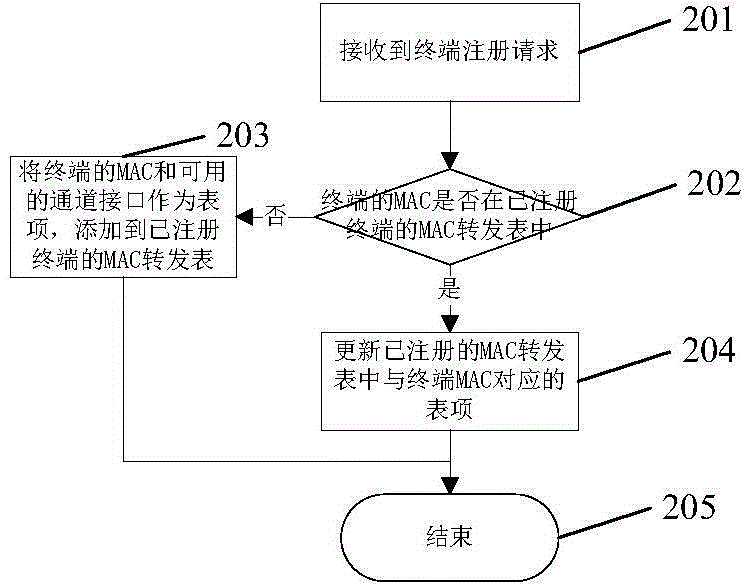
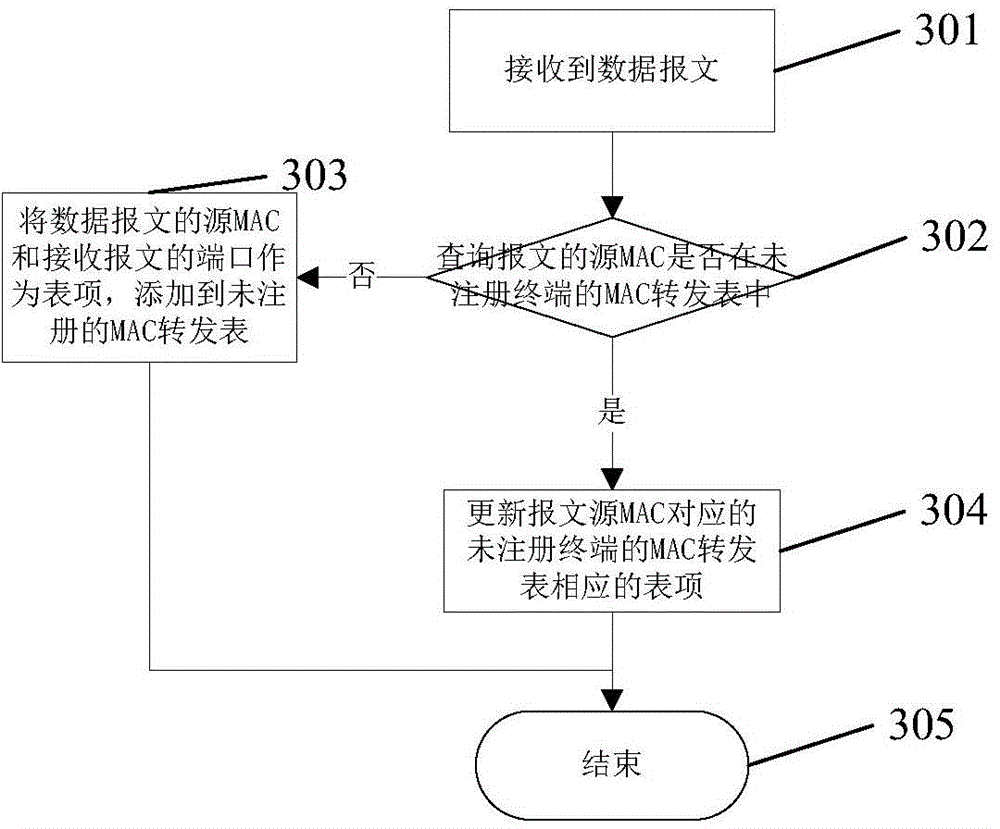
ActiveCN104660509AIncrease forwarding rateReduce update frequencyData switching networksLearning basedPort forwarding
The present invention relates to a data packet forwarding processing method in an access gateway, comprising: an access gateway receiving a data packet; the access gateway performing learning based on a source MAC address of the packet and constructing a MAC forwarding table; the access gateway querying whether a destination MAC address of the data packet is in a MAC forwarding table of a terminal that is registered, and if yes, performing transmission optimization based on a channel situation of the terminal: for an IP channel, performing transparent transmission, for a QAM channel, performing MPE / TS encapsulation, and for other channels, performing corresponding processing based the channel situation of the terminal; otherwise, the access gateway continuing to query whether the destination MAC of the data packet is in a MAC forwarding table of a terminal that is not registered, and if yes, the access gateway forwarding the data packet to a corresponding port based on a corresponding MAC forwarding table entry in the MAC forwarding table of the terminal that is not registered; otherwise, the access gateway broadcasting the data packet to all other ports except a port that receives the data packet.
Owner:ZHENGZHOU SEANET TECH CO LTD
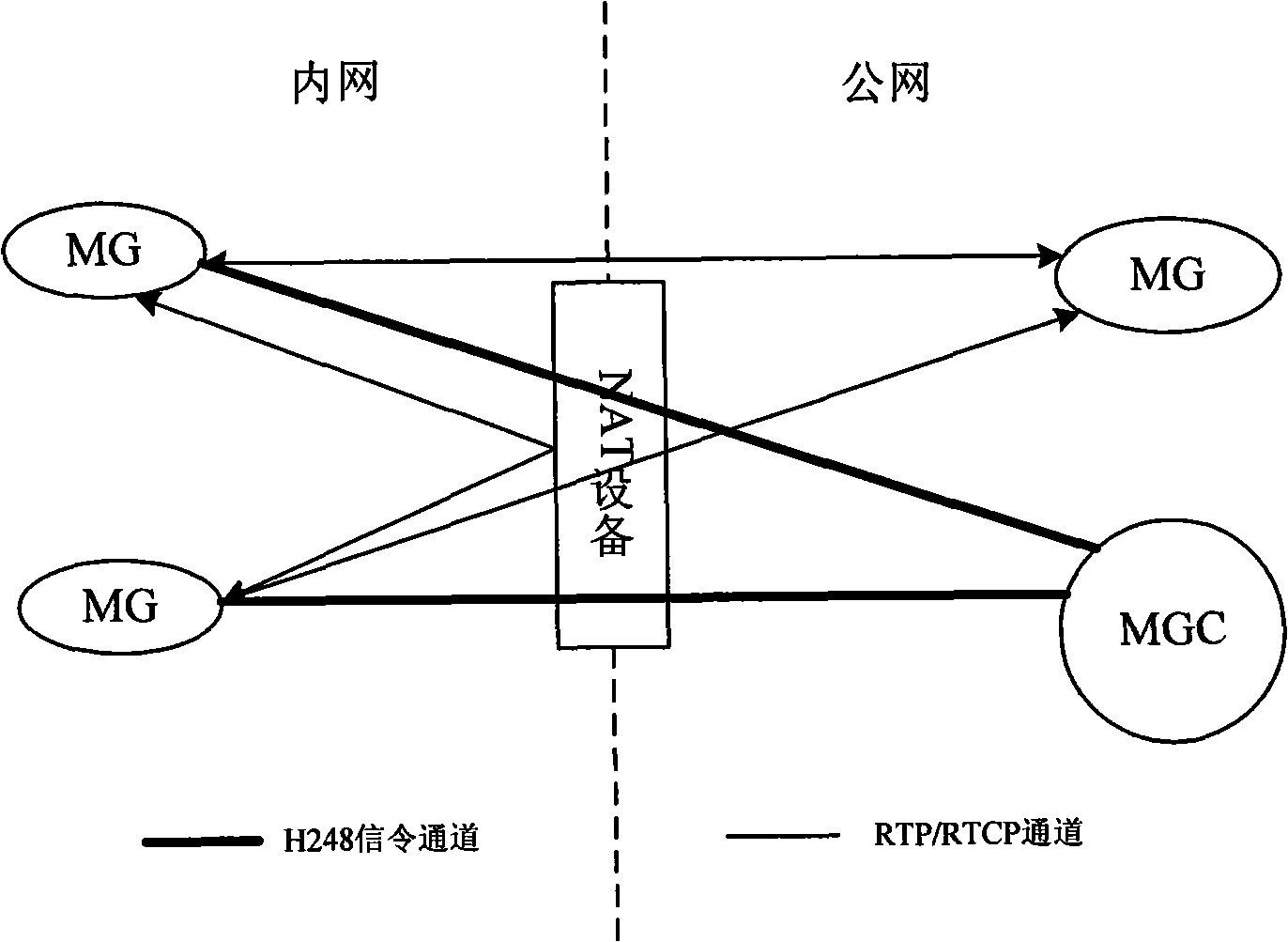
Implementing method for H248 protocol to get through NAT device
InactiveCN101335739AIncrease forwarding rateSave resourcesData switching networksNetwork addressingNetwork address
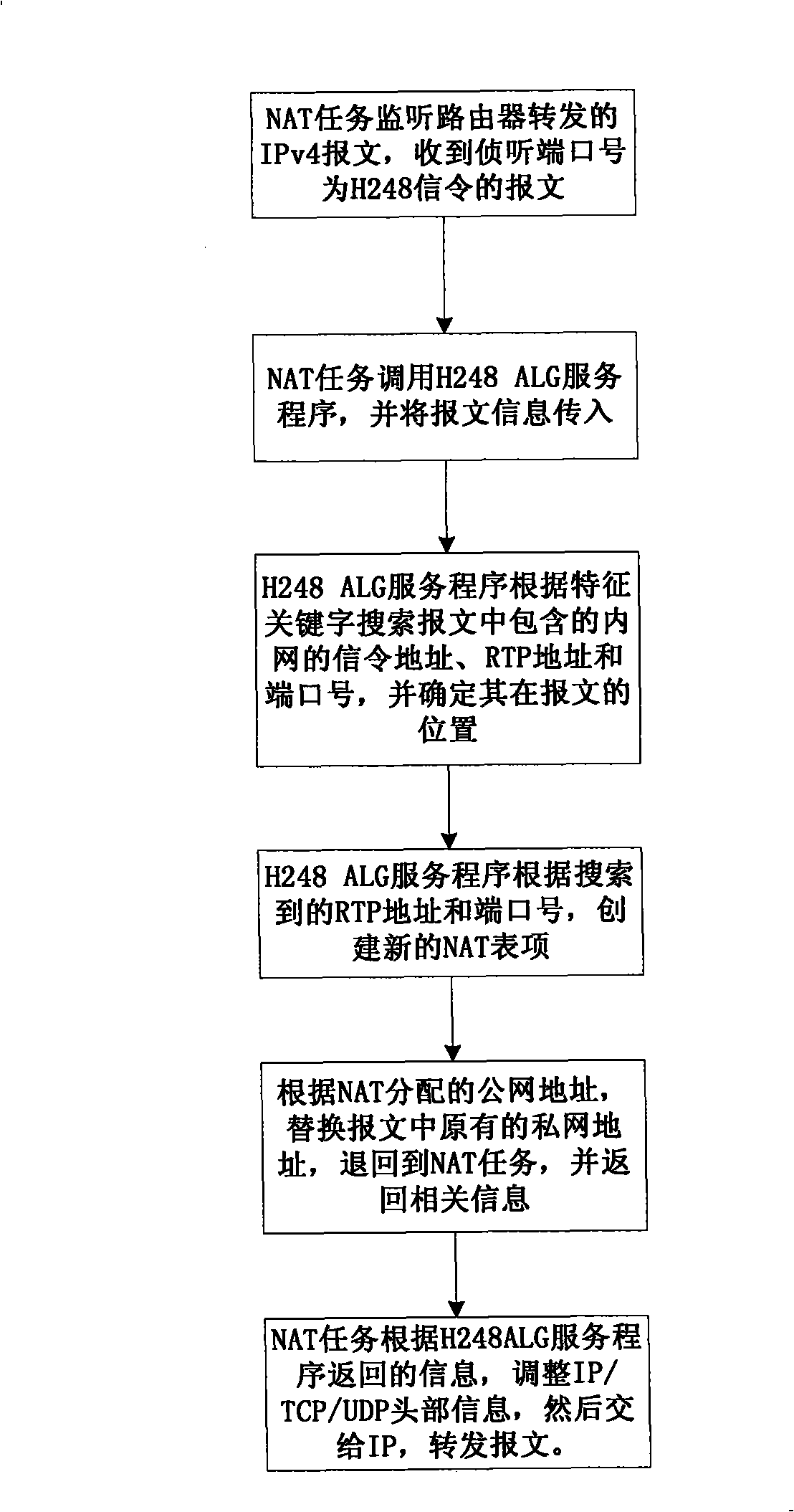
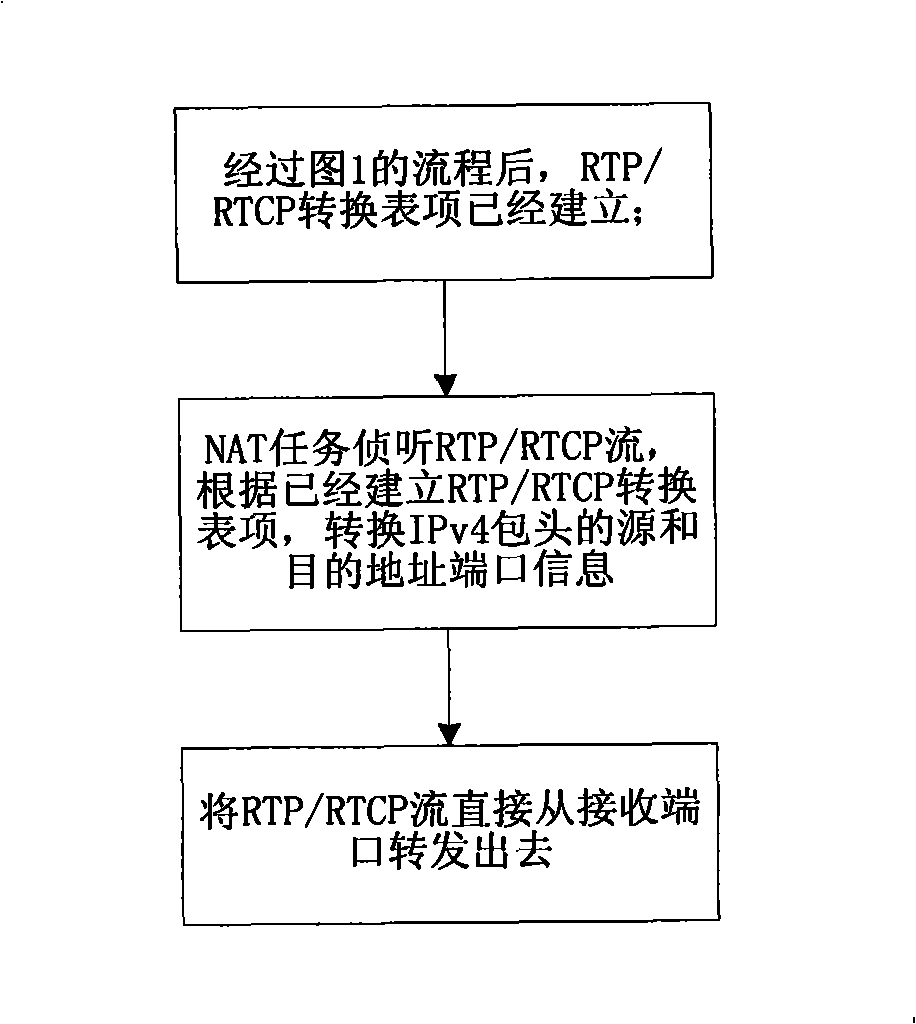
The invention discloses a realization method for the H248 protocol through an NAT device, which adopts keyword search and matching mode to replace the internal network address information in the signaling message load and then automatically creates a conversation connection on an NAT device to connect the RTP / RTCP channel between the MG / IAD on the inside user network of the NAT device and the media gateway control server (MGC); finally, an NAT task makes a choice on message forwarding path towards the RTP / RTCP message of the internal network according to the configuration; a first choice, the message is directly forwarded to the internal network, thereby realizing the exchange between the internal network media gateways while the internal network media gateway still uses a public network address which is registered onto the MGC of the public network; a second choice, the message is forwarded to the public network, thereby realizing the exchange with the public network media gateway. The method improves the forwarding rate of the message in the use process, occupies less system resources and simplifies the configuration tasks.
Owner:SHANGHAI BAUD DATA COMM
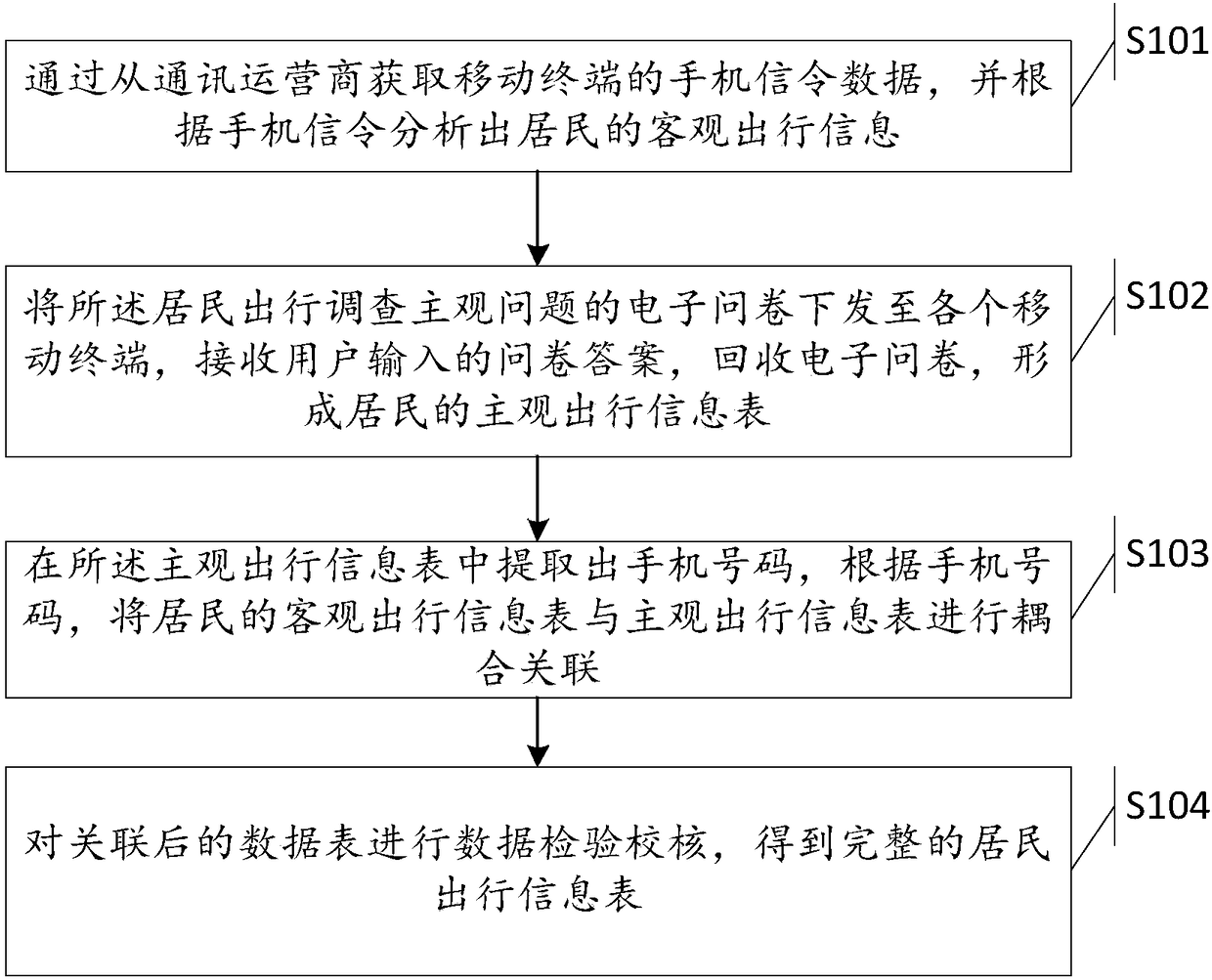
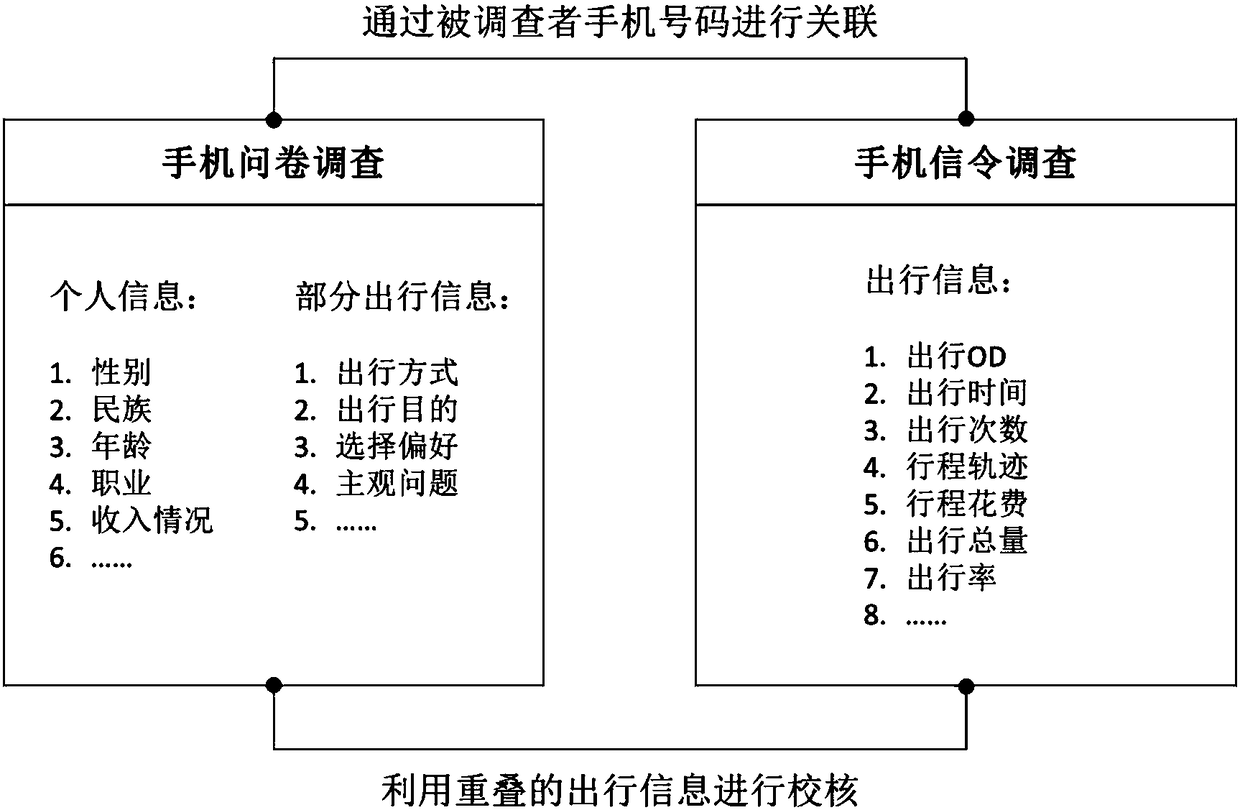
Resident travel survey method and system
InactiveCN108269019AIncrease forwarding rateHigh recovery rateResourcesTransmissionMobile phone signalData mining
The invention discloses a resident travel survey method and system. The method comprises the steps of obtaining an objective travel information table of a resident after performing a big data processing analysis by acquiring mobile phone signaling data of a communication operator; pushing a subjective problem electronic questionnaire to a mobile terminal, recycling the questionnaire after a user finishes answering, and obtaining a subjective travel information table; then, extracting a mobile phone number from the recycled electronic questionnaire, and associatively coupling the objective travel information table with the subjective travel information table according to the mobile phone number, and verifying and checking the subjective and objective travel tables to finally obtain a complete resident travel survey result. According to the invention, the electronic questionnaire is pushed through the network, the problems that the door-to-door mode of the traditional questionnaire is difficult to implement, the sampling rate is low and the like are solved, and the coupling association between the signaling and the questionnaire greatly simplifies the complexity of the electronic questionnaire, and the recycled electronic questionnaire data and the mobile phone signaling data are checked against each other to ensure the accuracy and reliability of the survey data.
Owner:珠海市规划设计研究院
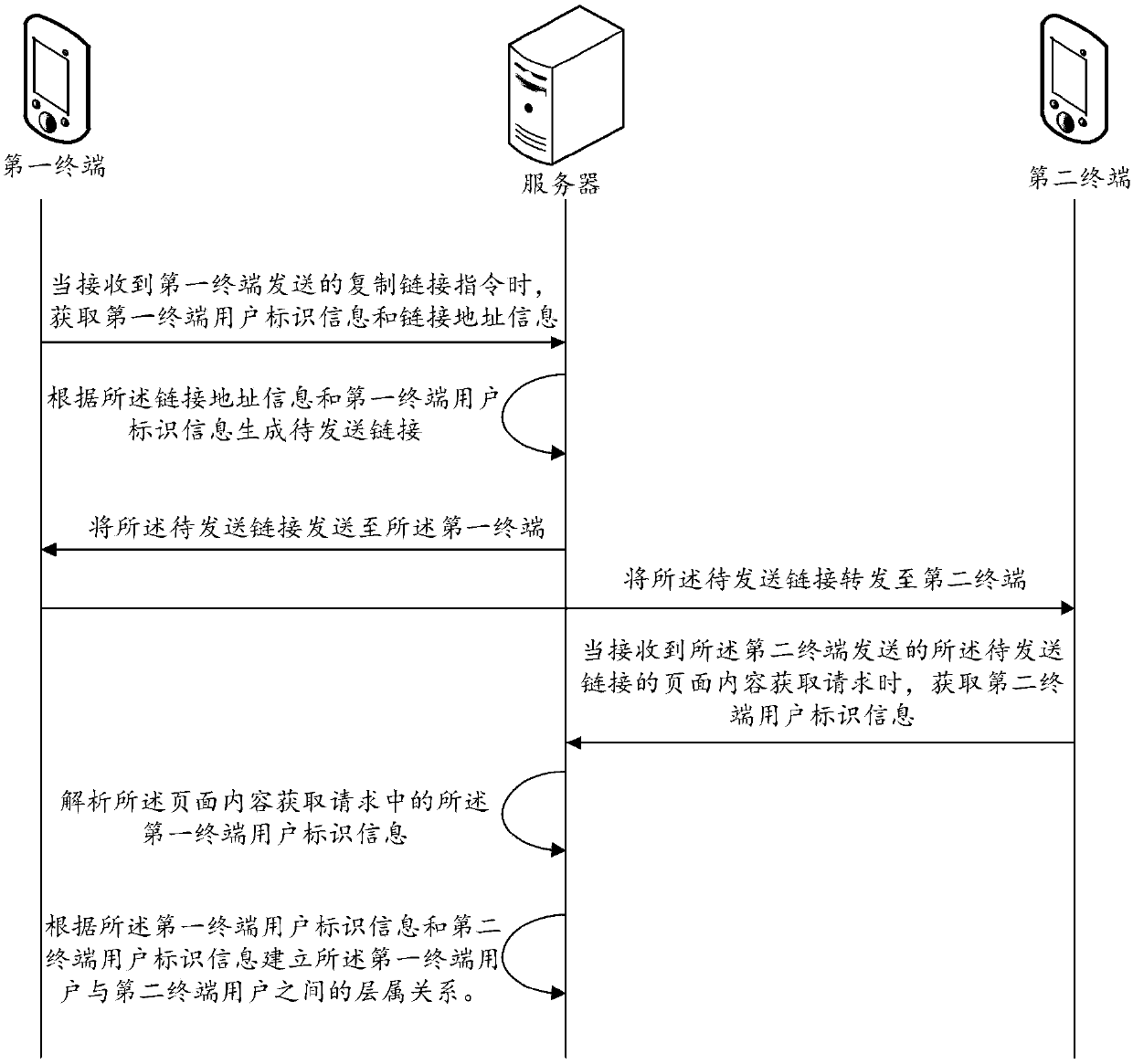
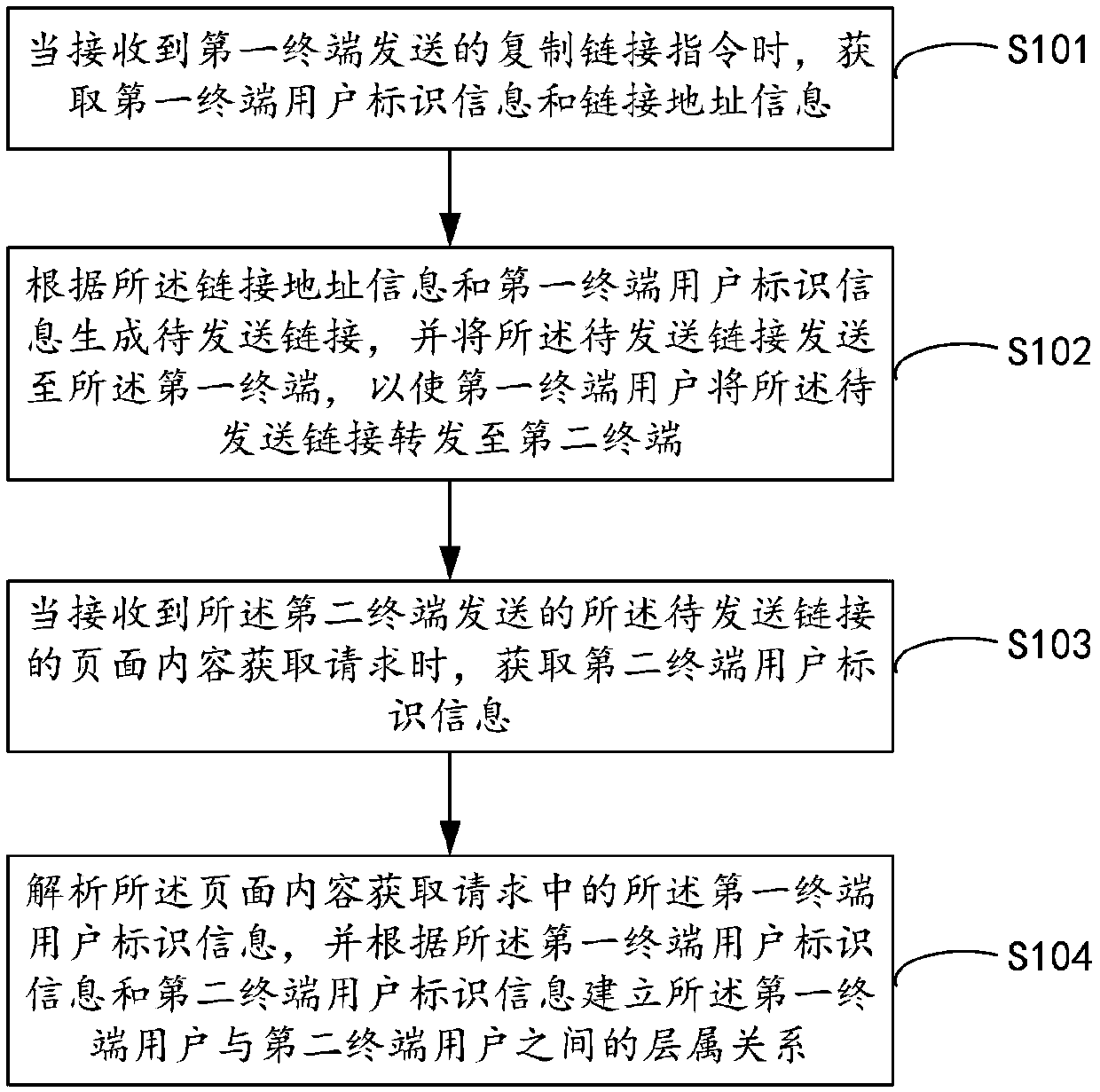
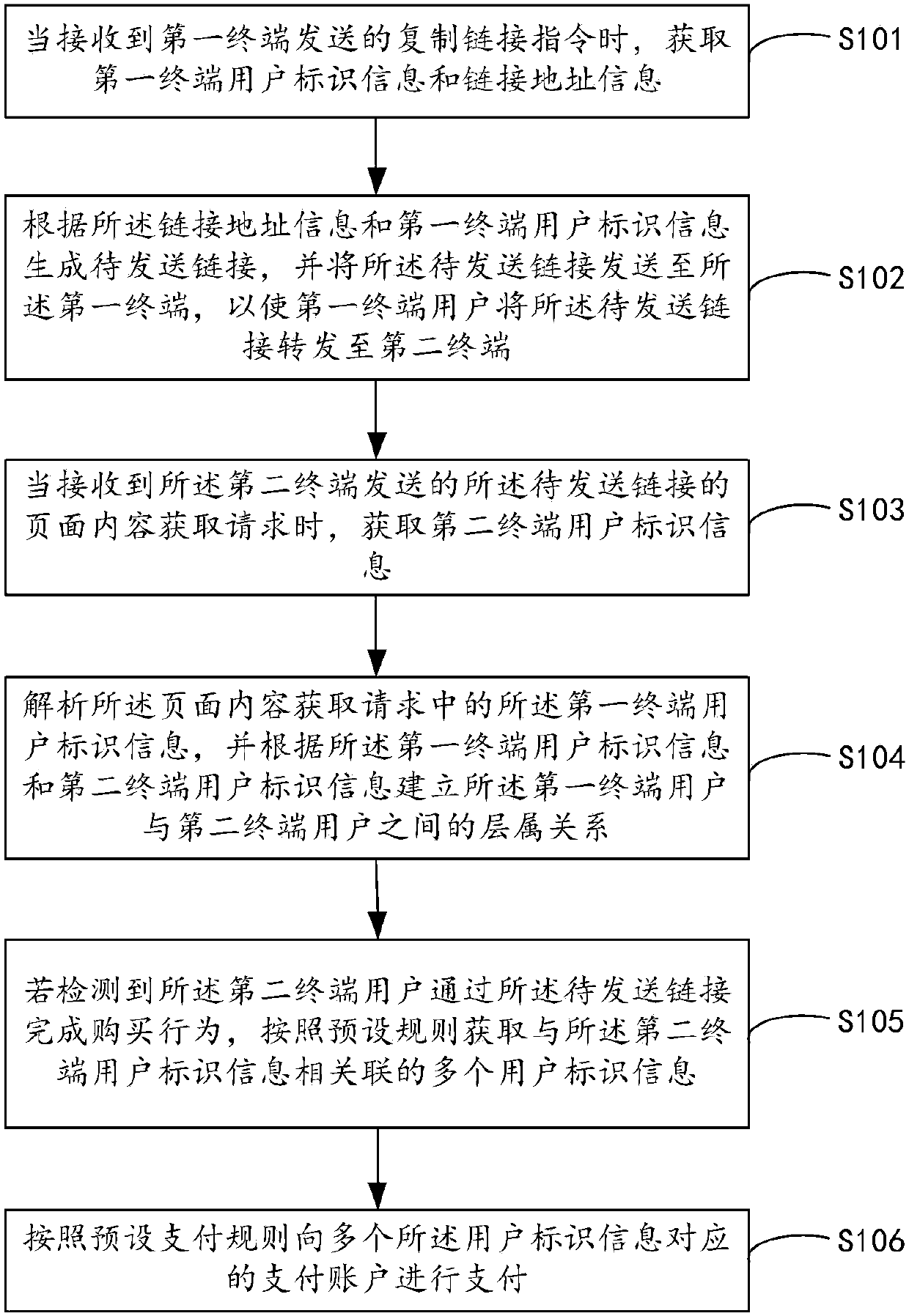
Method and device for establishing user hierarchical relationships, server and storage medium
InactiveCN107909243AImprove relevanceIncrease motivationResourcesTransmissionComputer terminalUser participation
The embodiment of the present application discloses a method and a device for establishing user hierarchical relationships, a server and a storage medium. The method includes steps of: when a copy link instruction sent by a first terminal is received, acquiring user identification information of the first terminal and link address information; generating a to-be-sent link according to the link address information and the user identification information of the first terminal, and sending the to-be-sent link to the first terminal, to enable the user of the first terminal to forward the to-be-sent link to a second terminal; and when a page content acquisition request of the to-be-sent link sent by the second terminal is received, acquiring user identification information of the second terminal; parsing the user identification information of the first terminal in the page content acquisition request, and establishing a hierarchical relationship between the user of the first terminal and the user of the second terminal according to the user identification information of the first terminal and the user identification information of the second terminal. This method can enhance the degreeof association between users, mobilize the enthusiasm of users to participate in link forwarding, and improve the link forwarding rate.
Owner:CHINA PING AN LIFE INSURANCE CO LTD
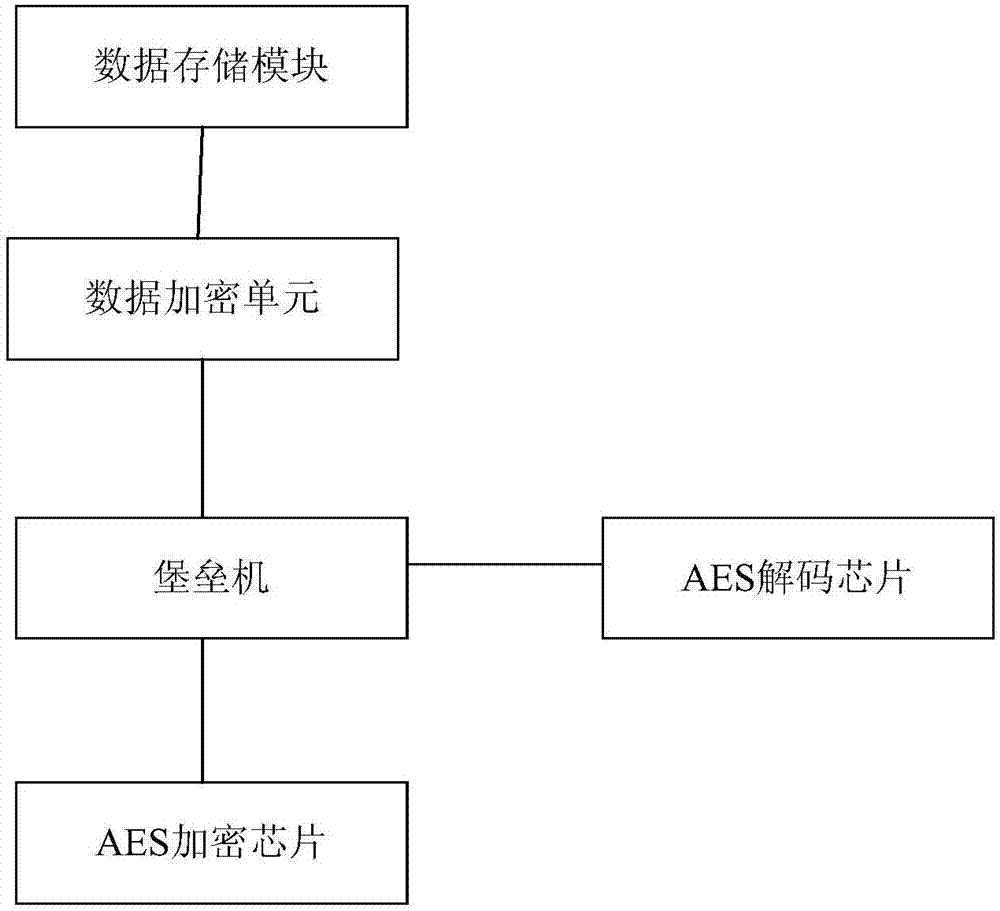
Industrial control network data security system
InactiveCN107493287AEliminate the danger of intrusion into private servicesReliable confidentialityEncryption apparatus with shift registers/memoriesPlaintextCiphertext
The invention discloses an industrial control network data security system, and relates to the technical field of information network security. The industrial control network data security system is used for improving the security of data interaction between public cloud and private cloud. The industrial control network data security system is characterized by at least comprising an encryption module used for encrypting plaintext information into a ciphertext, wherein the encryption module comprises an AES encryption chip, a fortress machine, a data encryption unit and a data storage module, the AES encryption chip performs data interaction with the fortress machine through a Zigbee protocol, the fortress machine performs data interaction with the data encryption unit through an https protocol, and the data encryption unit performs data interaction with the data storage module through the https protocol; and a decryption module used for decrypting the ciphertext into a plaintext, wherein the decryption module comprises an AES decoding chip. By adoption of the above technical scheme, the industrial control network data security system disclosed by the invention can improve the security of the data interaction between the public cloud and the private cloud.
Owner:天津中新智冠信息技术有限公司
Label searching method and device
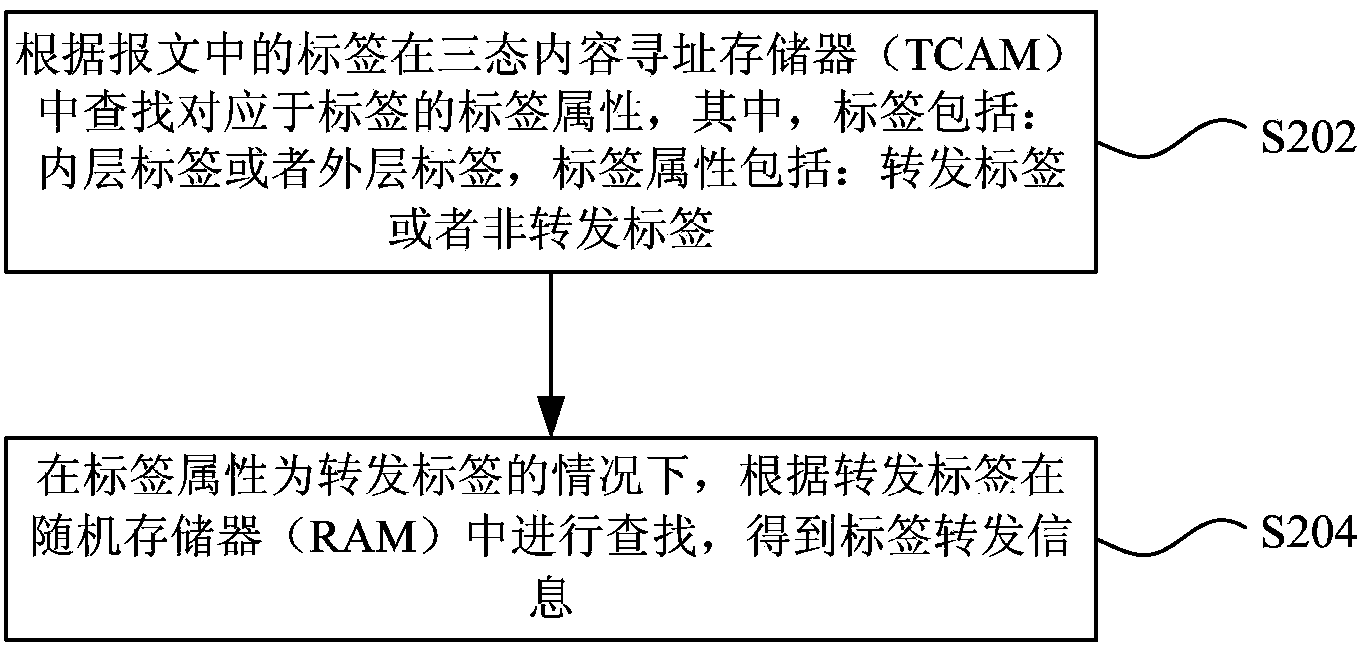
InactiveCN104348721AIncrease forwarding rateSolve UtilizationData switching networksRandom access memoryTernary content addressable memory
Disclosed are a method and device for label lookup. The method for label lookup comprises: looking up, on the basis of a label in a packet, in a ternary content-addressable memory (TCAM) for a label attribute corresponding to the label, where the label comprises: an inner-layer label or an outer-layer label, and, the label attribute comprises: a forwarding label or a non-forwarding label; and, insofar that the label attribute is the forwarding label, looking up in a random access memory (RAM) on the basis of the forwarding label, and acquiring label forwarding information. The present invention achieves the effect of conserved network resources and increased packet forwarding rate.
Owner:ZTE CORP
Automatic water supply device for building projects
InactiveCN107426791AReduce energy consumptionExtend the life cycleData switching networksHigh level techniquesEngineeringWater level
The invention belongs to the technical field of water supply, and discloses an automatic water supply device for building projects. The device comprises a water cabin, wherein a silicon battery panel is laid on the top of the water cabin; a water supply pipe is arranged at the right end of the water cabin; a water level alarm apparatus is embedded into the bottom of the right end of the water cabin; an underground pipe is arranged at the bottom of the water cabin; a machine case is fixed in the water cabin via a bolt; an energy accumulator is fixed on the left side of the machine case via a bolt; a water level monitor is embedded into the top of the machine case; a controller is arranged on the right side of the machine case; a water pump is fixed to the lower part of the machine case via a bolt; a water drain pipe is joined with the right end of the water pump; the underground pipe is joined with the bottom of the water pump; the silicon battery panel is connected with the energy accumulator via an electric circuit; and the energy accumulator, the water level monitor, the controller and the water pump are connected via the electric circuit. According to the device provided by the invention, the silicon battery panel is arranged, so that efficient clean energy can be provided, and the device is energy-saving, economical and environmentally friendly; the water level alarm apparatus is arranged, so that too low water level can be alarmed in advance, and a construction period is prevented from being influenced by untimely water supply; the device is simple to construct, convenient and practical.
Owner:李秋红
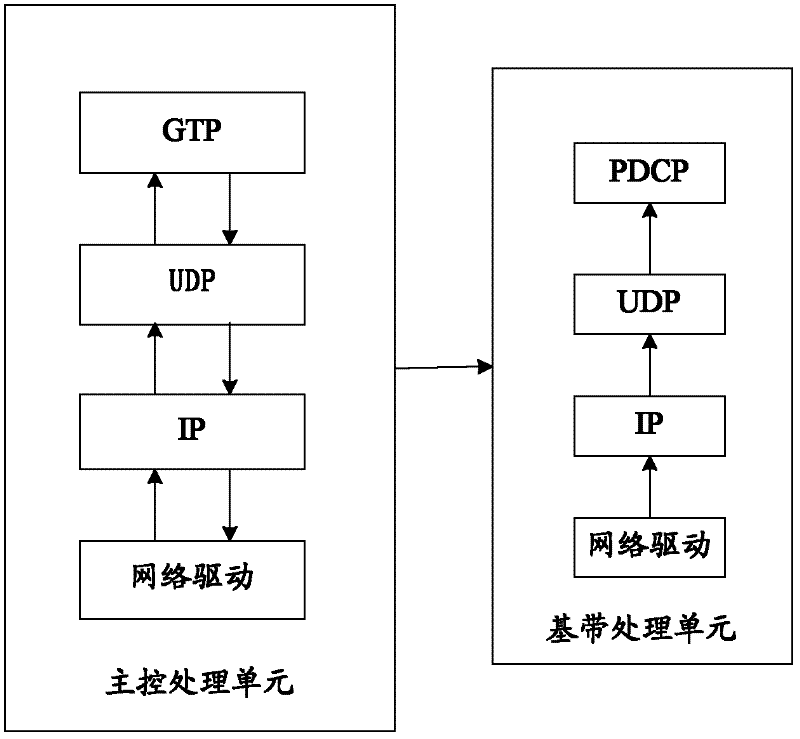
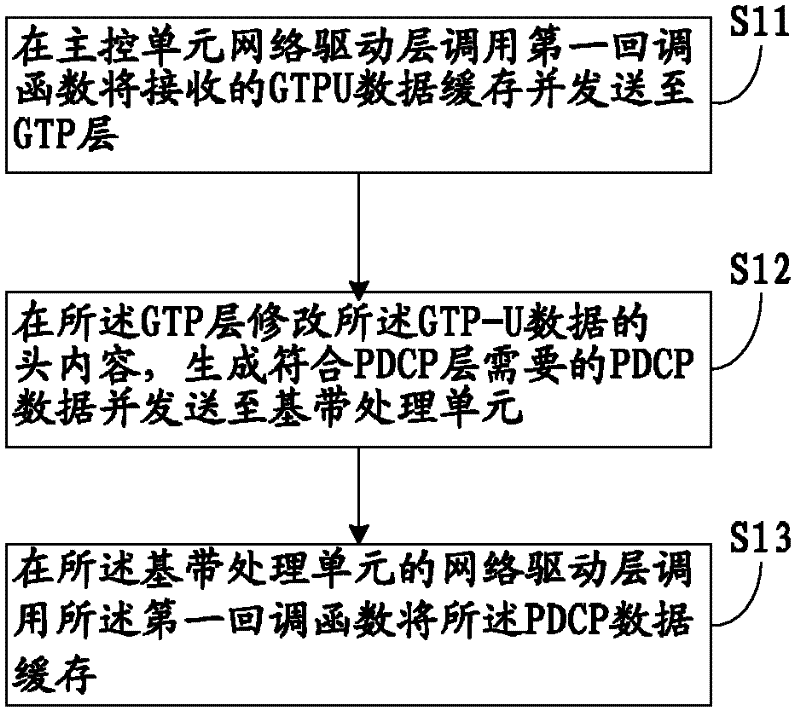
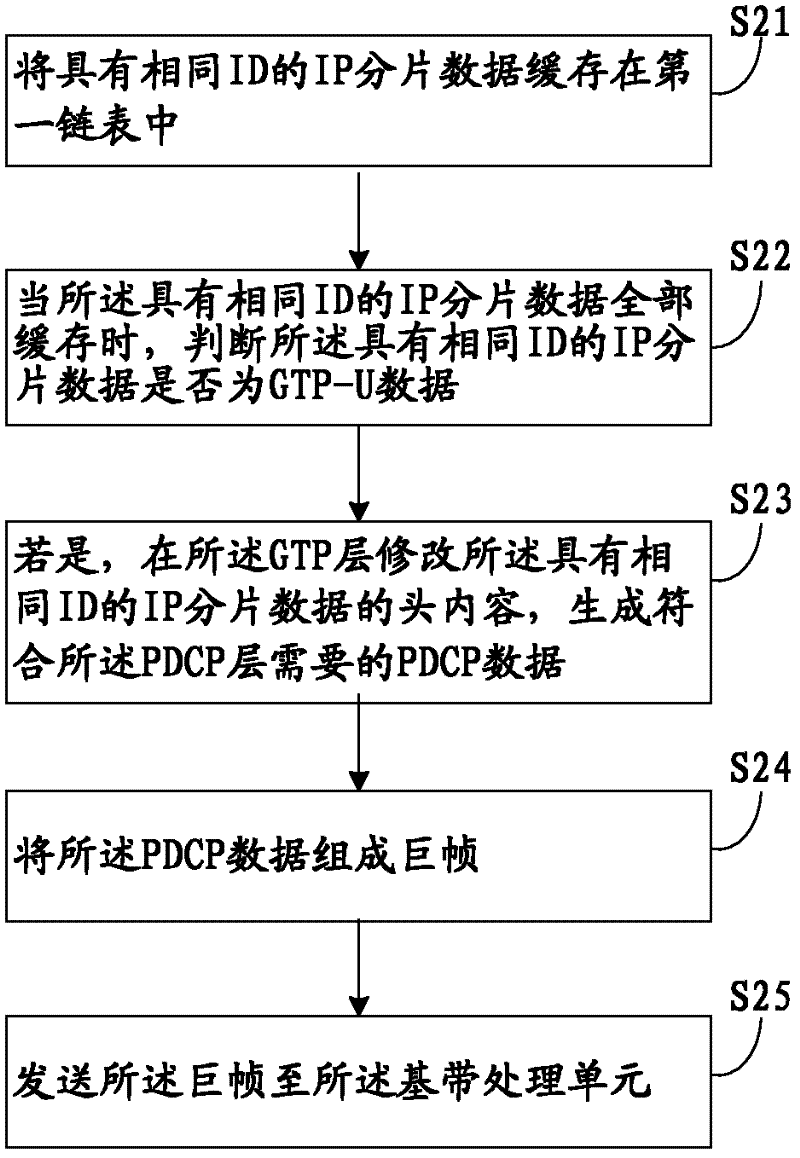
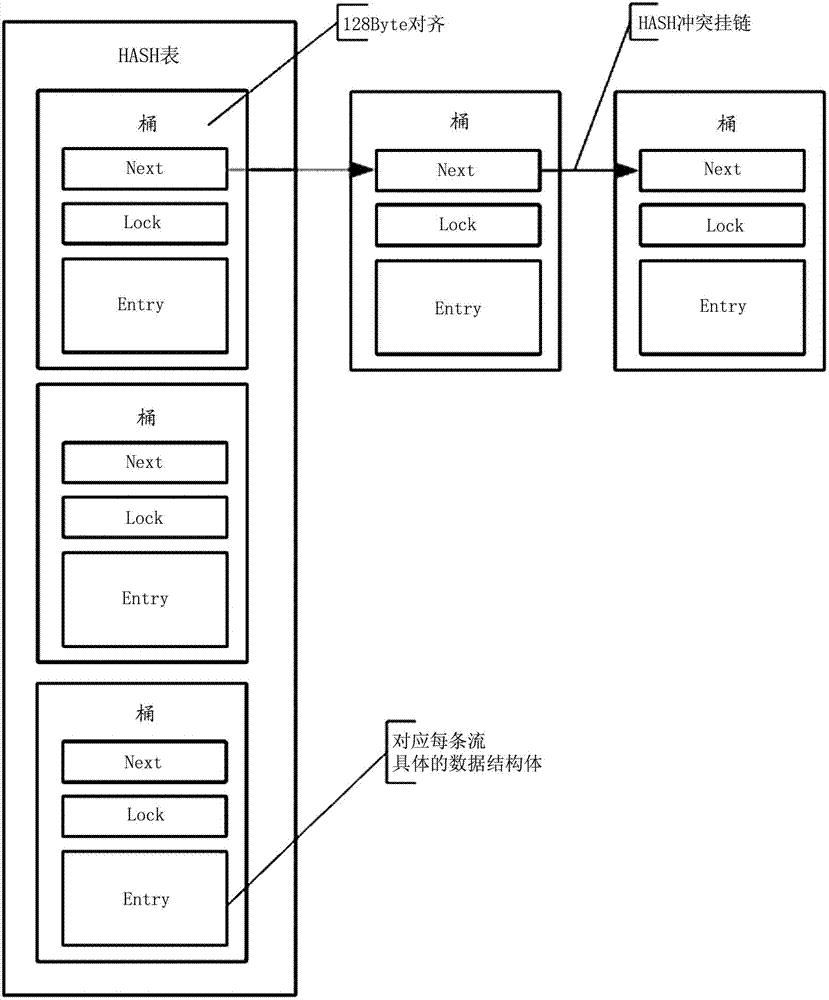
GTP-U (General Tunneling Protocol-User) data forwarding method
The invention discloses a GTP-U (General Tunneling Protocol-User) data forwarding method. The method comprises the following steps of: calling a first call back function to cache the received CTP-U data by a network driving layer of a main control unit and sending the data to a GTP (General Tunneling Protocol) layer; revising a head content of the GTP-U data on the GTP layer to generate PDCP (Packet Data Convergence Protocol) data which accords with the requirements of a PDCP layer and then sending the PDCP data to a baseband processing unit; and calling the first call back function to cache the PDCP data by the network driving layer of the baseband processing unit. The invention further provides a forwarding method of the GTP-U data and the method comprises the following steps of: sending the data received by the baseband processing unit to the main control unit; calling a second call back function to cache the data by the network driving layer of the main control unit and sending the data to the GTP layer; revising the head content of the received data on the GTP layer to generate the GTP-U data needed by the GTP layer and sending the data. With the adoption of the method provided by the invention, the data can be transmitted without entering a protocol stack of a TCP / IP (Transmission Control Protocol / Internet Protocol) and the forwarding speed of the data is improved.
Owner:WUHAN HONGXIN TELECOMM TECH CO LTD
Flow table aging method and device of quick forwarding engine, and switch
ActiveCN102780641BImprove effectivenessIncrease forwarding rateData switching networksAge methodTime segment
The invention provides a flow table aging method and device of a quick forwarding engine, and a switch. The flow table aging method of the quick forwarding engine comprises the following step: when Hash is matched with a Hash bucket comprising at least one flow table item through five-element information in a flow table in the form of a Hash table, deleting the flow table items of which the creating time is longer than a preset time period according to a creating time stamp of each flow table item in the matched Hash bucket.
Owner:BEIJING HAN NETWORKS TECH CO LTD
Message forwarding method, system and routing switch
InactiveCN102244614BIncrease forwarding rateIncrease profitData switching networksTerminal equipmentNetwork data
The invention provides a message forwarding method, system and routing switch. The method includes: the source routing switch queries the MAC table according to the received destination MAC address of the current Ethernet data frame, and obtains the identifier of the first destination routing switch; the source routing switch queries the first destination routing switch according to the identifier of the first destination routing switch The neighbor direct connection list of the switch obtains the identification of the second destination routing switch directly connected to the first destination routing switch; the source routing switch uses the TRILL routing table to transfer the Ethernet data frame to the subsequent received Ethernet data frame with the same destination MAC address. The network data frame is forwarded to the terminal device corresponding to the destination MAC address through the first destination routing switch and the second destination routing switch. The technical scheme of the invention can reduce the waste of link bandwidth resources and improve the utilization rate of link bandwidth resources.
Owner:RUIJIE NETWORKS CO LTD
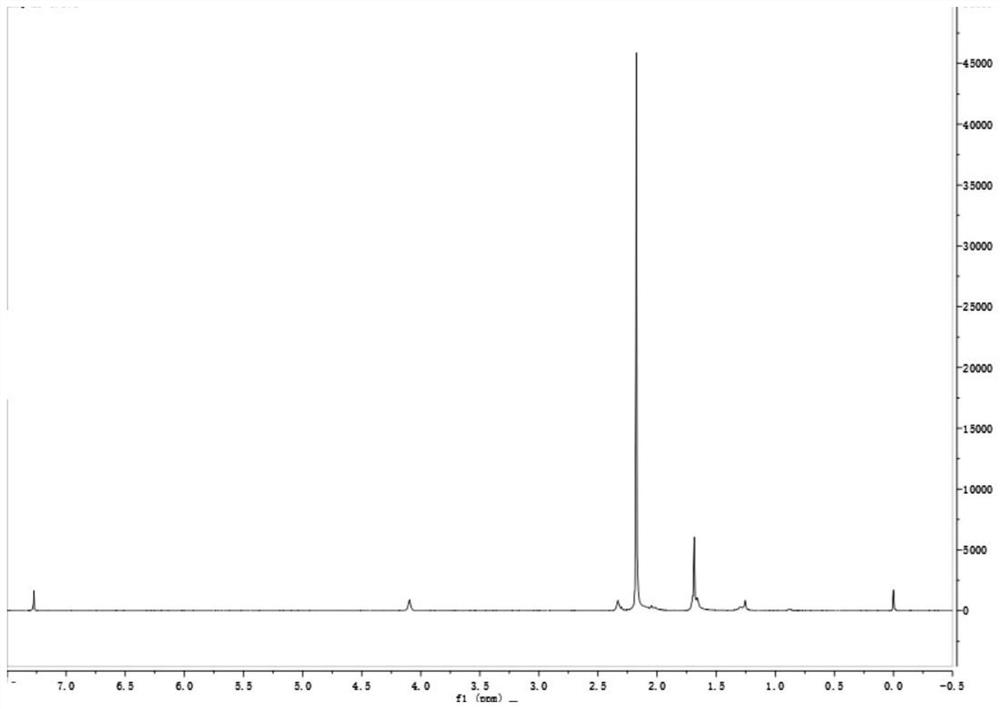
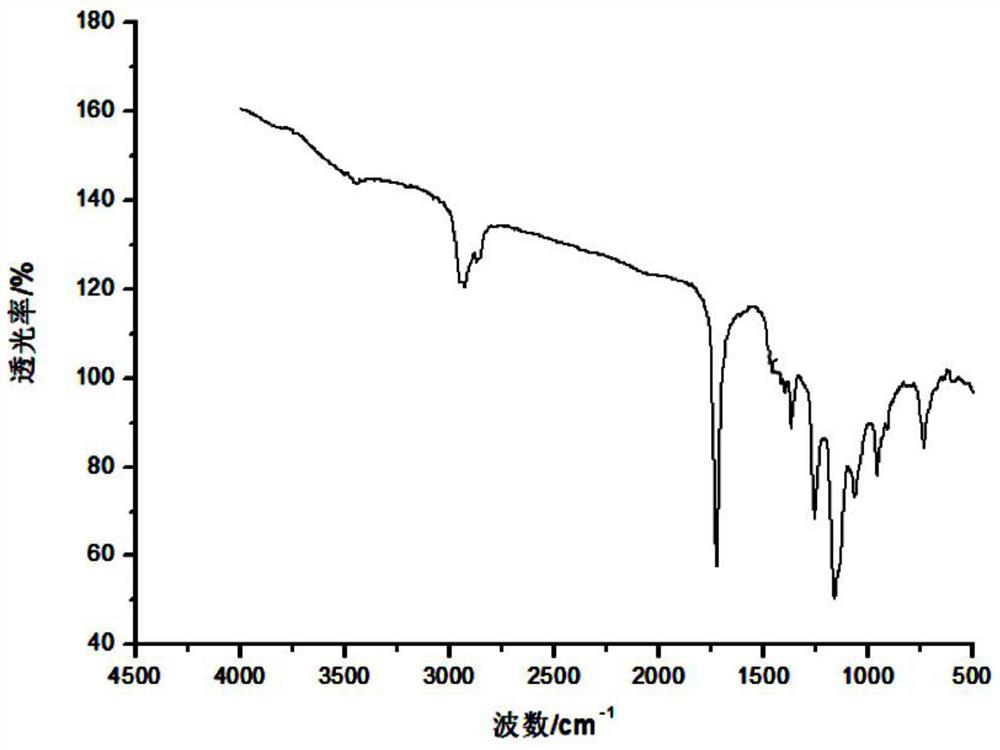
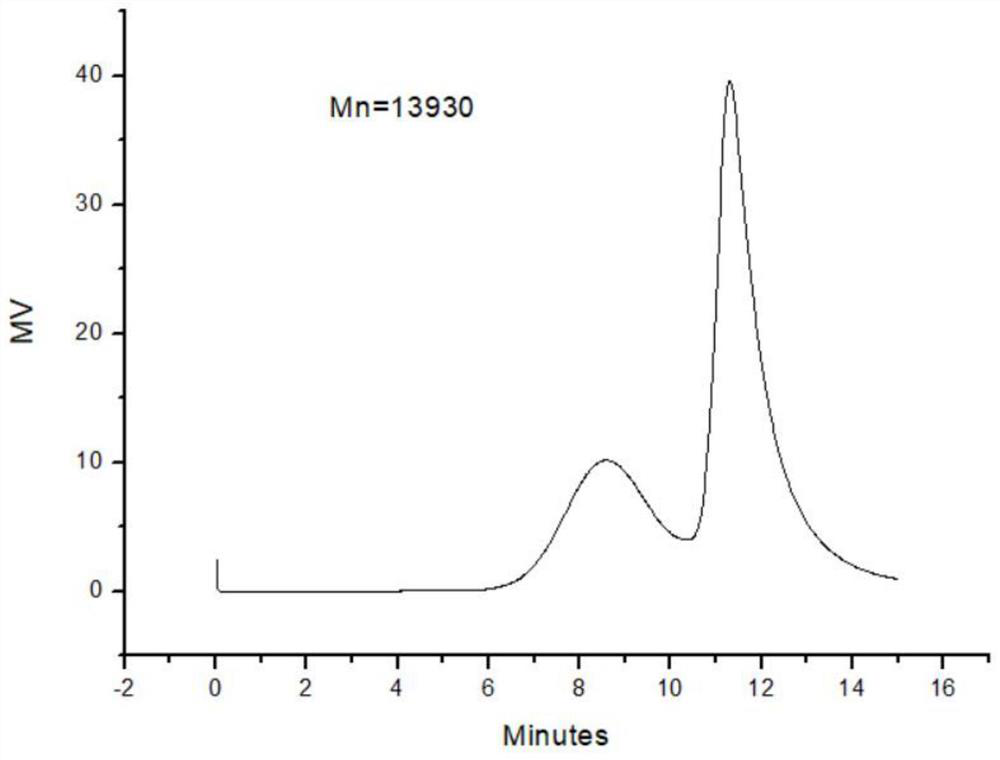
A kind of polymer and its preparation method and application
The invention discloses a high-molecular polymer and its preparation method and application. It is prepared by reacting castor oil, polybutylene adipate and diethylene glycol divinyl ether as reactants. Castor oil, polyhexamethylene Butylene diacid and toluene are mixed to obtain mixed solution A; then mixed solution A, p-toluenesulfonic acid and tetrahydrofuran are mixed to form mixed solution B; then diethylene glycol divinyl ether is added dropwise to mixed solution B to react , the final conversion rate of the present invention can reach more than 90%; the prepared high molecular polymer can be used to prepare engineering plastics; Stir and mix with tetrahydrofuran, put into an oven and react to obtain engineering plastics. Because the engineering plastics of the present invention can undergo acid degradation, they are very friendly to the environment; at the same time, the engineering plastics have high tensile strength and bending strength under normal conditions, which can meet the needs of actual production and life.
Owner:WENZHOU UNIV
Traffic information identification and forwarding method based on dual trust mechanism in the Internet of Vehicles environment
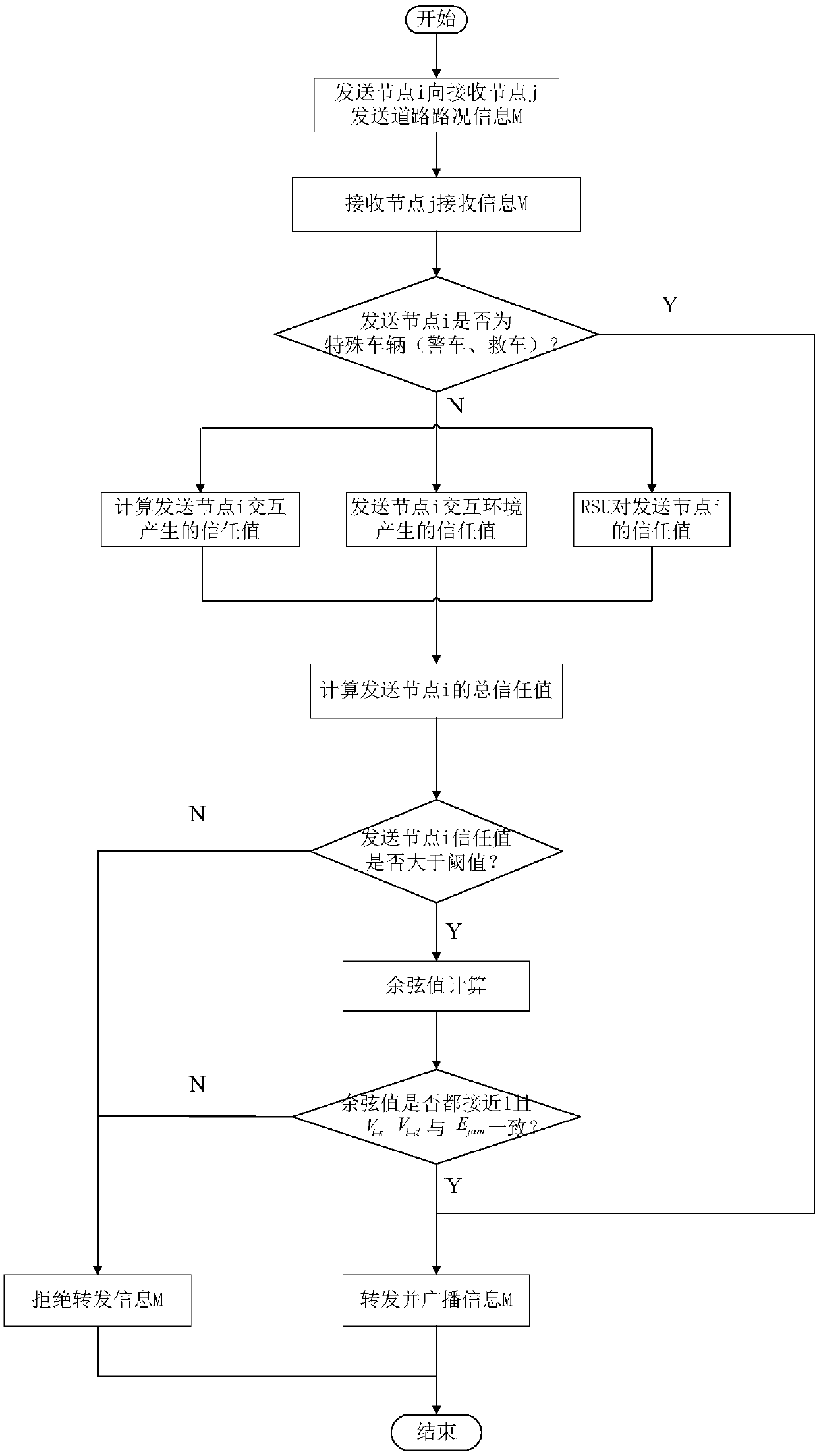
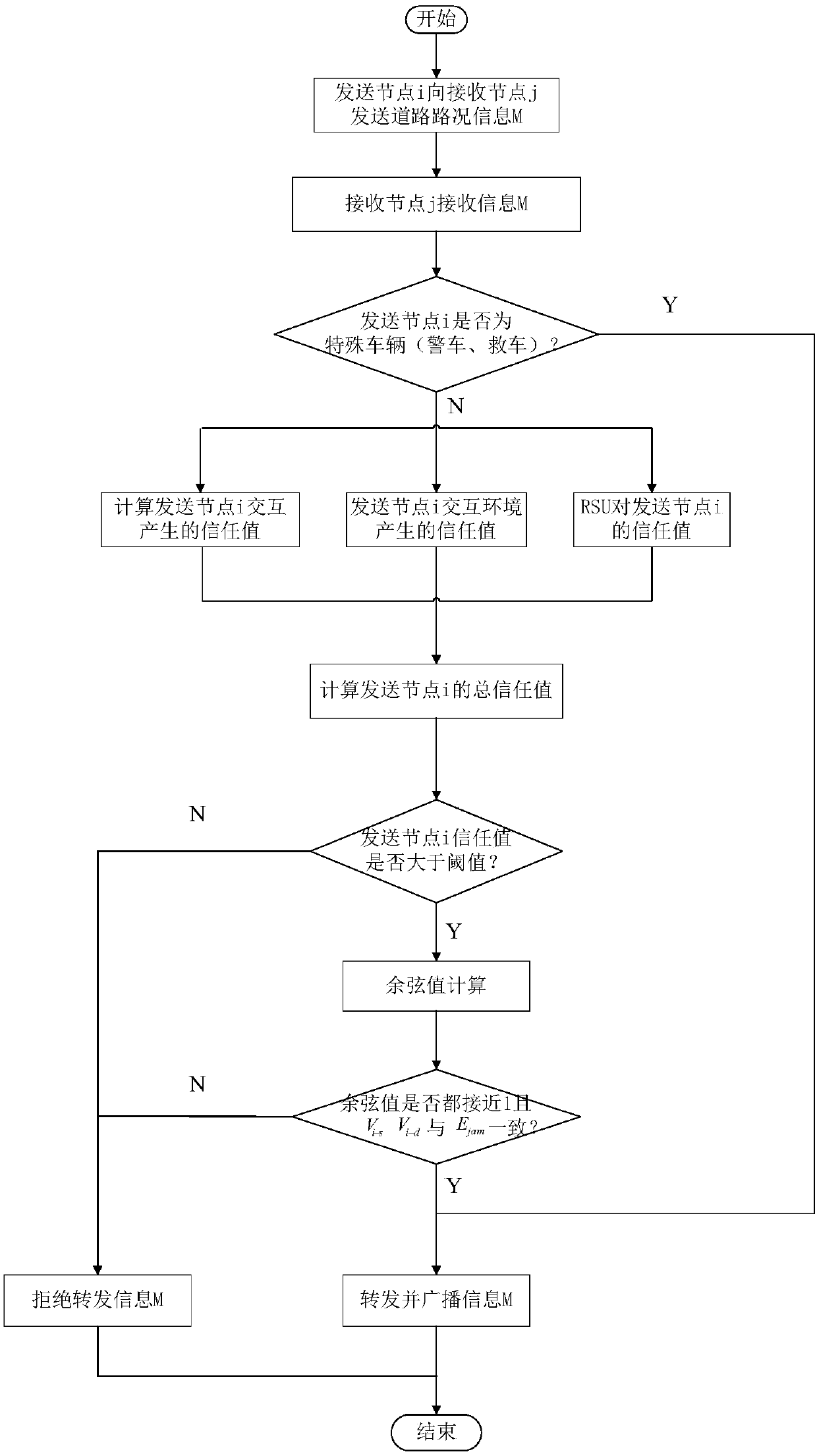
InactiveCN108053665BIncrease forwarding rateArrangements for variable traffic instructionsData switching networksCosine similarityIn vehicle
The present invention provides a traffic information identification and forwarding method with a dual trust mechanism in the Internet of Vehicles environment. 1. Sending node i sends road condition information M to receiving node j, and receiving node j receives information M; 2. Judging whether sending node i is a special vehicle, 3. The receiving node j calculates the trust value of the sending node i; 4. The receiving node j judges whether the sending node i is credible; 5. Calculates the cosine value and consistency of the angle between the road condition information M and the vehicle information MR attribute vector to evaluate them 6. Judging whether the content of the road condition information M sent by the sending node i is credible; the present invention judges whether it is credible by calculating the trust value of the mobile node, and compares the similarity of the information content based on the cosine similarity, so that the node The content of the sent information is calculated and compared by text similarity, and it is judged whether the content of the road condition information sent by the node is credible. The credibility of traffic information in the Internet of Vehicles is evaluated by using the dual trust mechanism, which effectively improves the forwarding rate of the entire Internet of Vehicles.
Owner:CHANGAN UNIV
A firewall based on dpdk virtualization management system and its implementation method
ActiveCN111371779BReduce performance consumptionImprove performanceSecuring communicationData packPathPing
The present invention provides a firewall based on the DPDK virtualization management system and its implementation method. The present invention utilizes the polling technology of DPDK to intercept interrupts, solves the loss problem caused by interrupt processing, and utilizes UIO technology to bypass the kernel protocol stack, through UIO technology maps the packets received by the network card to the working principle of f-stack, the user mode protocol stack, which greatly reduces the performance consumption when capturing data packets, and improves the performance of the firewall in processing data packets. A fast forwarding path is added before the data packet enters the f-stack protocol stack, and the session check is performed on the data packet captured by DPDK. The performance loss caused by the process of the protocol stack increases the packet forwarding rate, thereby improving the data processing performance of the firewall of the virtualization management system.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com