Method for implementing tunnel conversion of bi-layer tunnel protocol
A layer-2 tunneling protocol and tunneling technology, applied in the field of layer-2 tunneling protocol tunnel conversion, can solve problems such as slowing down the rate of message forwarding, affecting the rate of message forwarding, and multiple TSA resources, so as to achieve faster rate and improved Packet forwarding rate, effect of saving system resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
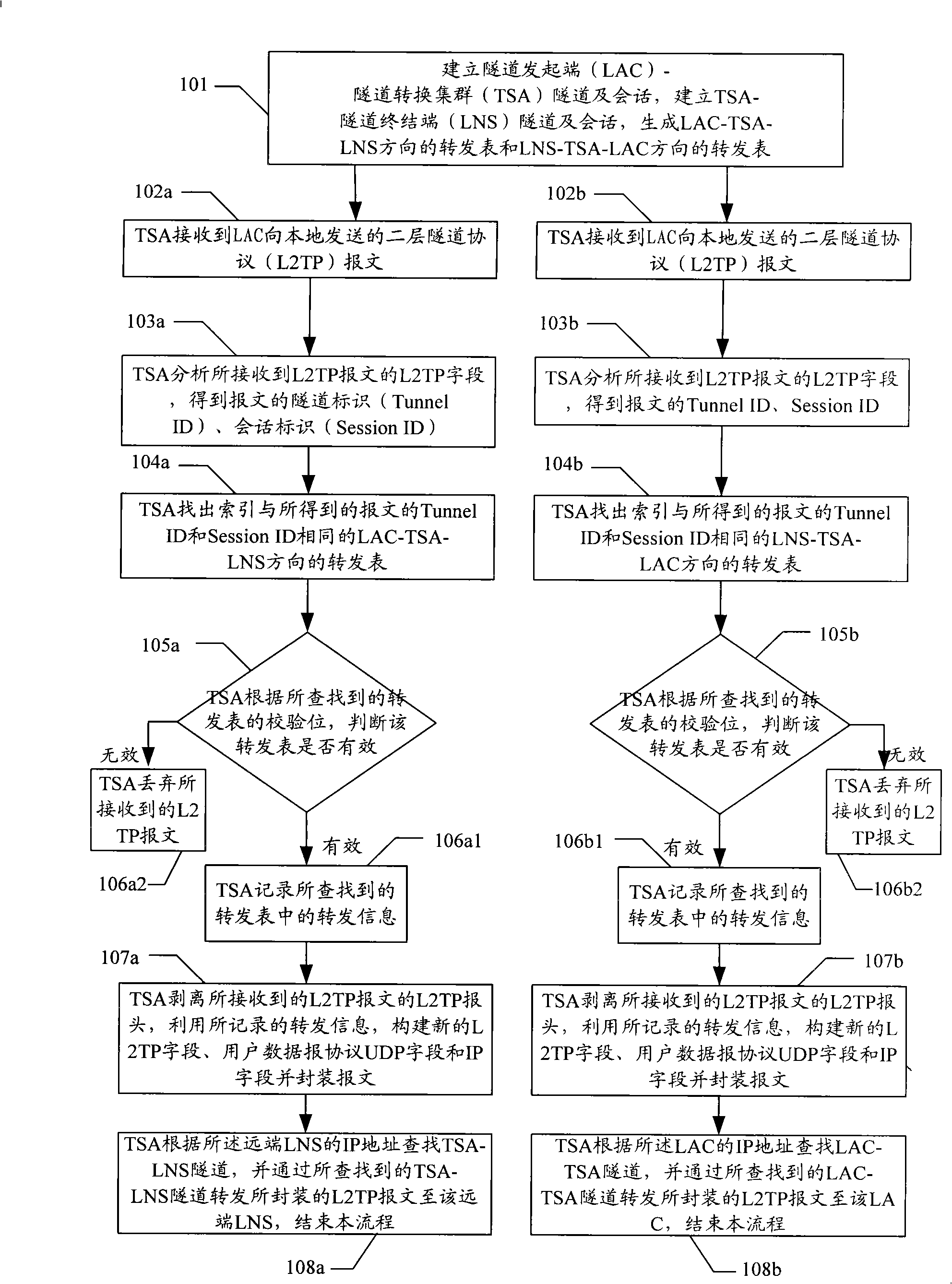
[0028] The implementation process of the method for realizing the tunnel conversion of the two-layer tunnel protocol in the present invention is as follows: figure 1 shown, including the following steps:
[0029] Step 101: Establish LAC-TSA tunnel and session, establish TSA-LNS tunnel and session, issue a forwarding table in the direction of LAC-TSA-LNS and a forwarding table in the direction of LNS-TSA-LAC; the forwarding table is in LAC-TSA tunnels and sessions, TSA-LNS tunnels and sessions are established and issued, including forwarding information;
[0030] Specifically include the following steps:
[0031] The LAC initiates a tunnel establishment request to the TSA; the TSA accepts the request and establishes a LAC-TSA tunnel and session with the LAC, and the TSA accepts the request through the TSA-LNS module and establishes a LAC-TSA tunnel and session with the LAC,
[0032] The TSA initiates a tunnel establishment request to the remote LNS; the remote LNS accepts the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com