FPGA-based network security acceleration card and FPGA-based network security acceleration method
A network security, accelerator card technology, applied in the field of data transmission
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
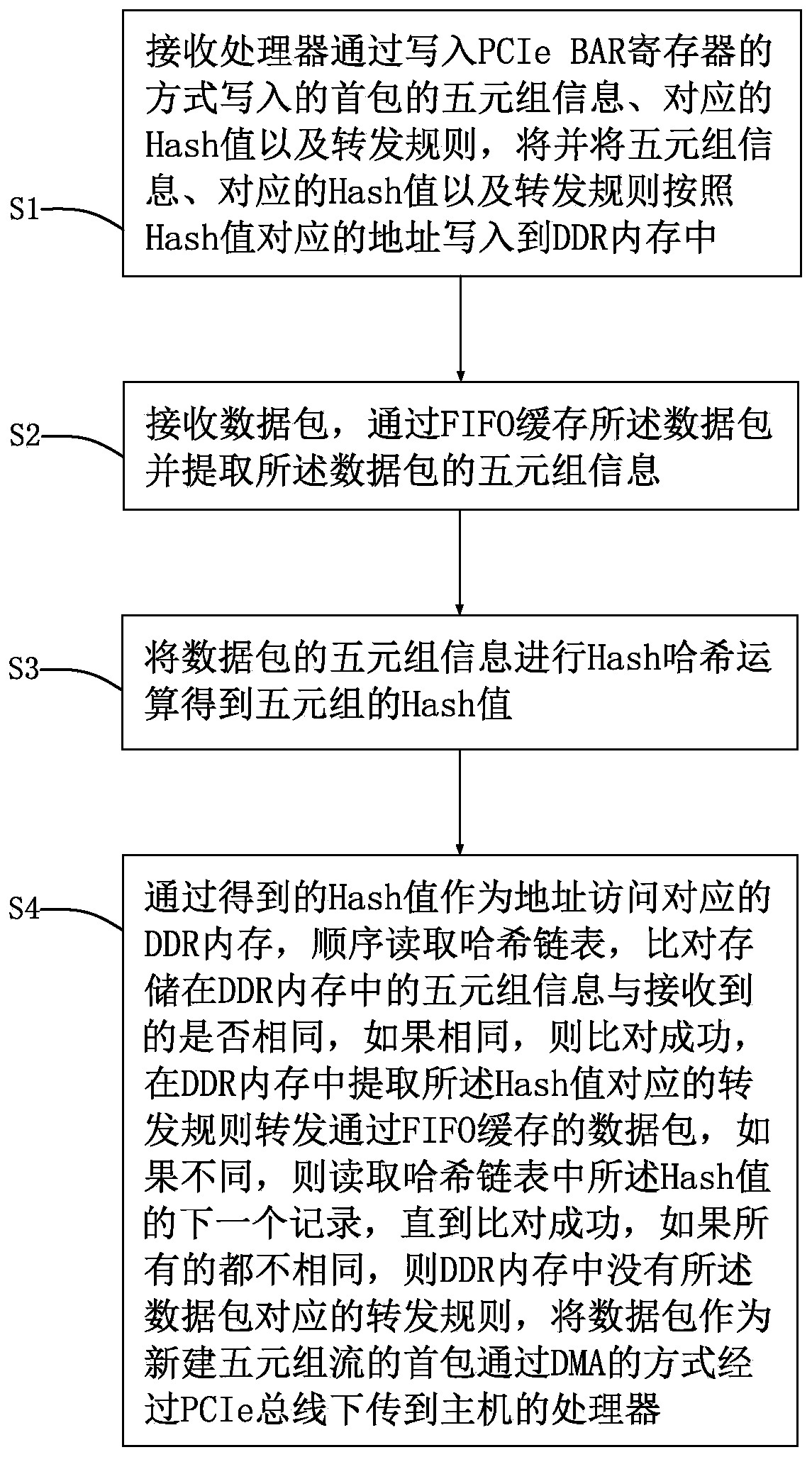
[0027] The present invention provides a method for accelerating network security based on FPGA, such as figure 1 , figure 2 shown, including the following steps:
[0028] S1: The receiving processor writes the quintuple information, corresponding Hash value, and forwarding rules of the first packet by writing into the PCIe BAR register, and converts the quintuple information, corresponding Hash values, and forwarding rules according to the Hash value. The corresponding address is written into the DDR memory, and the forwarding rules include security policies, routing information and processing policies;
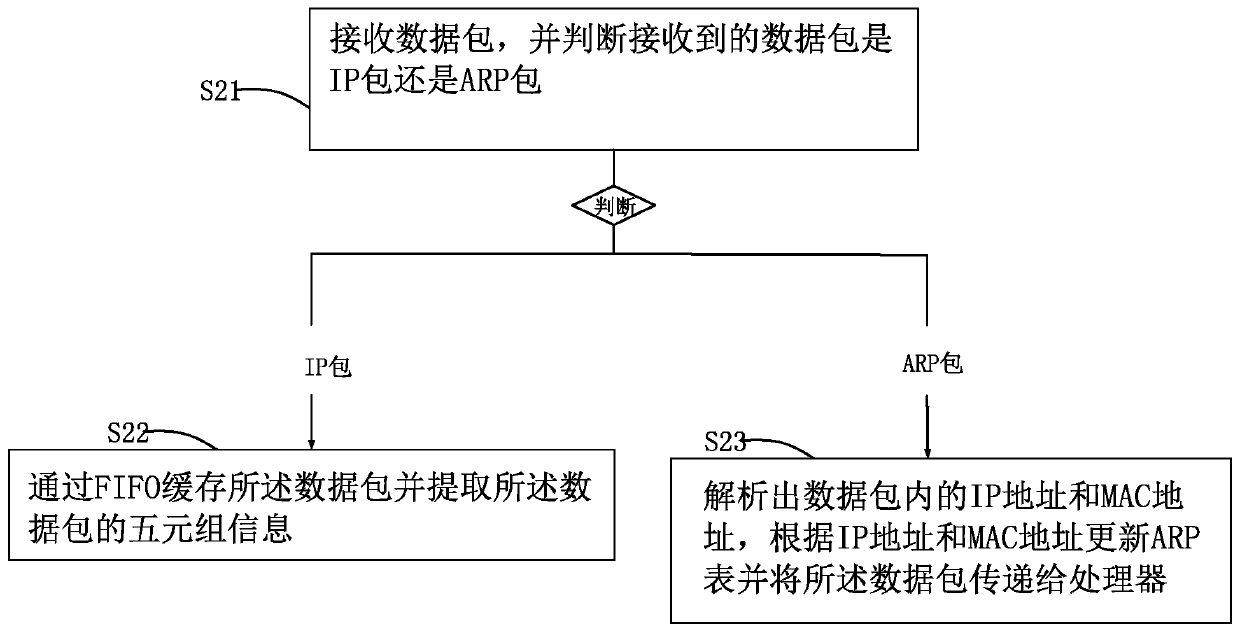
[0029] S2: receiving a data packet, buffering the data packet through FIFO and extracting the quintuple information of the data packet;
[0030] S3: Perform a hash operation on the quintuple information of the data packet to obtain the hash value of the quintuple;
[0031] S4: Access the corresponding DDR memory by using the obtained Hash value as the address, read the ha...
Embodiment 2
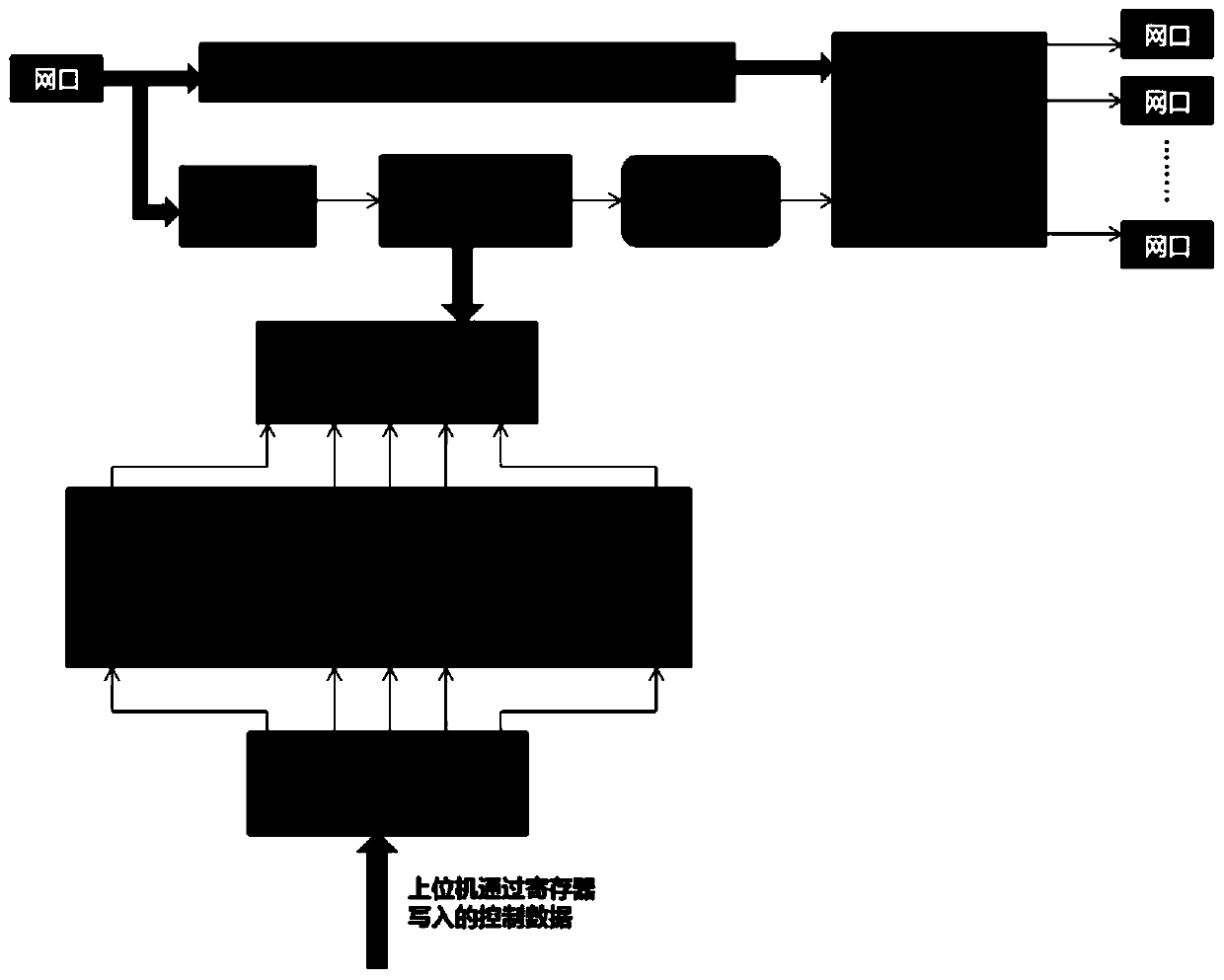
[0064] An FPGA-based network security accelerator card, such as Figure 5 As shown, including the following parts:
[0065] The information writing module 1 is configured to receive the quintuple information, the corresponding Hash value and the forwarding rules of the first packet written by the receiving processor by writing the PCIe BAR register, and convert the quintuple information, the corresponding Hash value Value and forwarding rules are written in the DDR memory according to the address corresponding to the Hash value, and the forwarding rules include security policies, routing information and processing policies;
[0066] The extraction module 2 is configured to receive the data packet, cache the data packet through the FIFO and extract the quintuple information of the data packet;
[0067] The hash operation module 3 is configured to perform Hash operation on the quintuple information of the data packet to obtain the Hash value of the quintuple;
[0068] The data...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com