Industrial control network data security system
A data security and industrial control network technology, applied in the field of information network security, to achieve the effect of sacrificing efficiency, realizing safe transmission, and high forwarding rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] In order to further understand the invention content, characteristics and effects of the present invention, the following examples are given, and detailed descriptions are as follows in conjunction with the accompanying drawings:
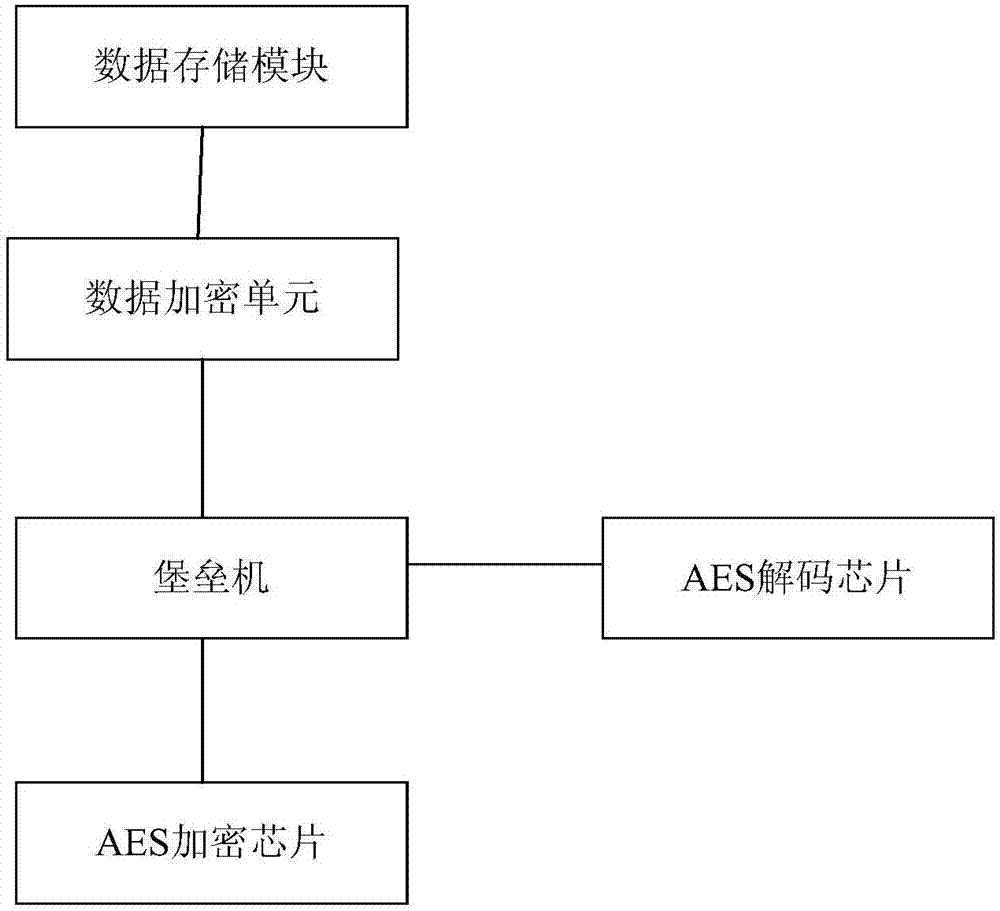
[0018] see figure 1 , an industrial control network data security system, used to improve the security of data interaction between public cloud and private cloud; including:
[0019] An encryption module for encrypting plaintext information into ciphertext; the encryption module includes an AES encryption chip, a bastion machine, a data encryption unit, and a data storage module; the AES encryption chip performs data interaction with the bastion machine through the Zigbee protocol; The bastion host performs data interaction with the data encryption unit through the https protocol; the data encryption unit performs data interaction with the data storage module through the https protocol;
[0020] A decryption module for decrypting ciphertext ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com