Friend message shielding method and device based on address list
An address book and message technology, applied in the network field, can solve the problems of inconvenient operation and use, low possibility of realization, troublesome operation, etc., and achieve the effect of enhancing personal experience, improving applicability, and high practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
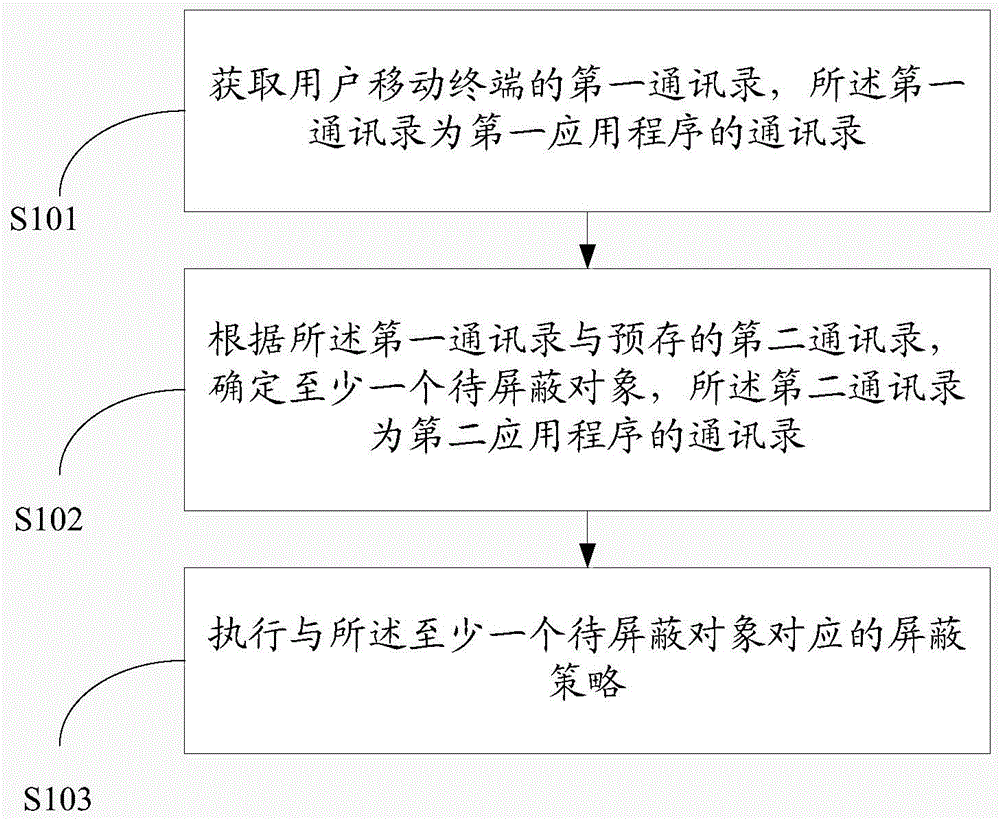
[0046] An embodiment of the present invention provides a method for blocking friend messages based on an address book, refer to figure 1 As shown, the method includes:
[0047] S101. Obtain the first address book of the user's mobile terminal, where the first address book is the address book of the first application program;
[0048] S102. Determine at least one object to be shielded according to the first address book and the pre-stored second address book, where the second address book is the address book of the second application program;
[0049] S103. Execute a screening policy corresponding to at least one object to be screened.
[0050] Wherein, obtaining the first address book of the mobile terminal includes:
[0051]Sending a request instruction for obtaining the first address book of the mobile terminal to the user; the request instruction is used to instruct the mobile terminal to upload the first address book to the server;
[0052] After receiving the request i...
Embodiment 2
[0065] An embodiment of the present invention provides a method for shielding friend messages based on an address book, referring to figure 1 As shown, the method includes:
[0066] S101. Acquire a first address book of a mobile terminal of a user, where the first address book is an address book of a first application program.
[0067] Wherein, the first address book may be an address book in the user's mobile phone or other mobile terminal, or may be an address book in an application program in the mobile phone or other mobile terminal.
[0068] Specifically, the process of obtaining the first address book on the server side may be as follows:
[0069] The server sends to the user a request instruction for acquiring the first address book of the mobile terminal; the request instruction is used to instruct the mobile device to upload the first address book to the server;
[0070] After receiving the request instruction, the mobile device displays the authorization request to...
Embodiment 3
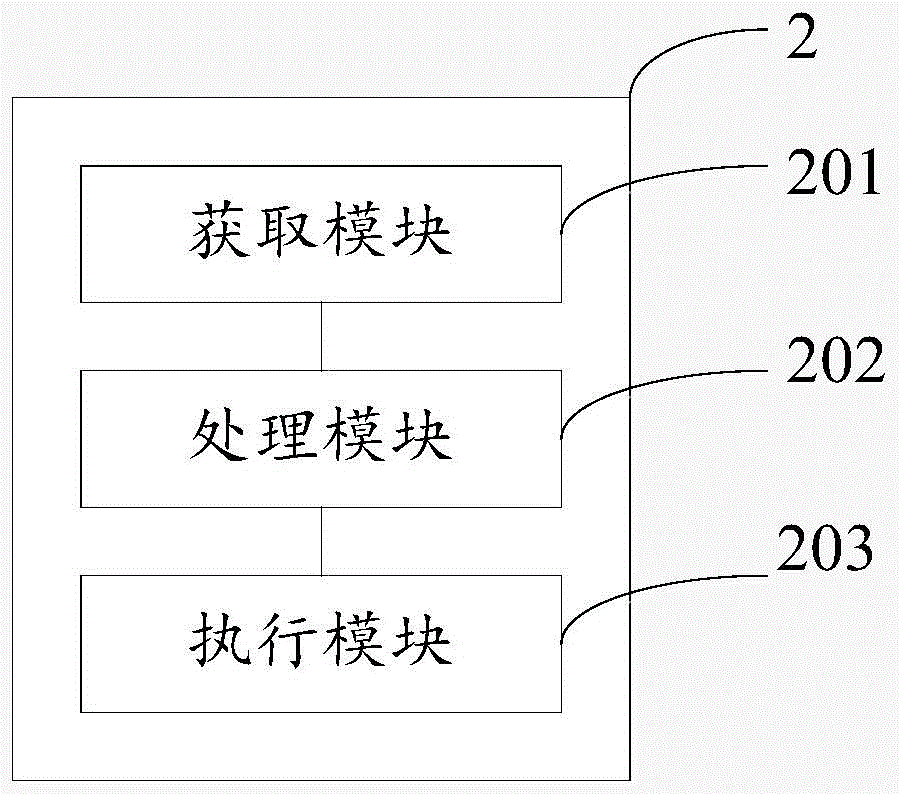
[0132] This embodiment provides a friend message shielding device based on the address book, refer to figure 2 As shown, the device 2 includes:
[0133] The acquiring module 201 is configured to acquire the first address book of the user's mobile terminal, where the first address book is the address book of the first application program;
[0134] The processing module 202 is configured to determine at least one object to be shielded according to the first address book and the pre-stored second address book, the second address book being the address book of the second application program;
[0135] An execution module 203, configured to execute a screening policy corresponding to at least one object to be screened.
[0136] The acquisition module 201 includes:
[0137] The server module sends to the user a request instruction for obtaining the first address book of the mobile terminal; the request instruction is used to instruct the mobile terminal to upload the first address...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com