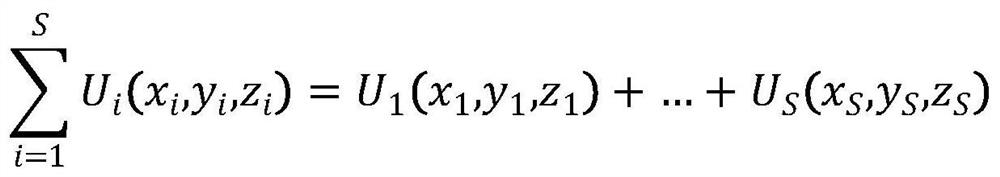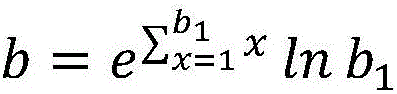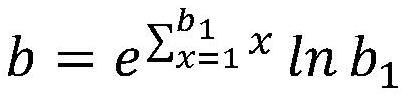Patents
Literature
34results about How to "High degree of encryption" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
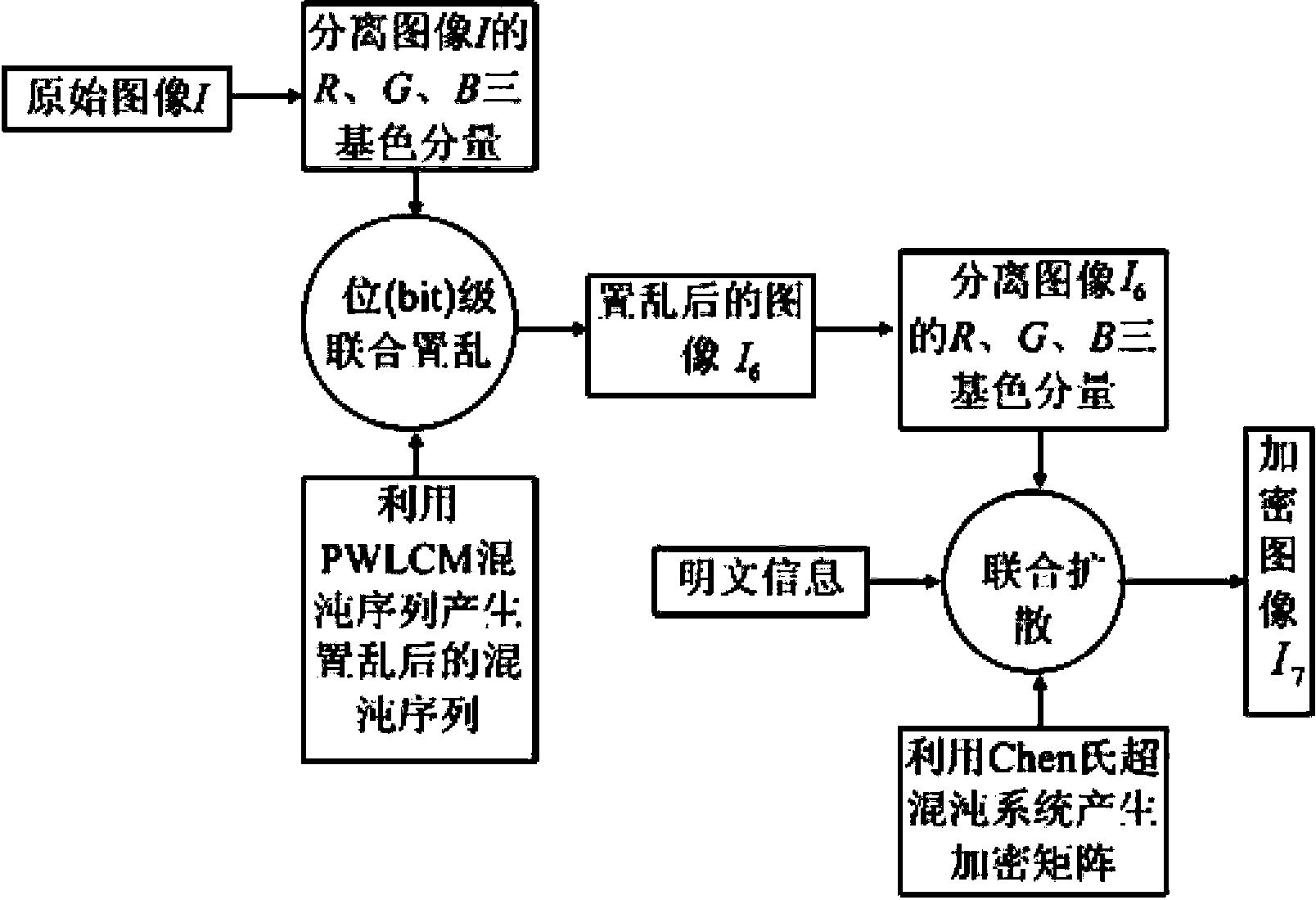
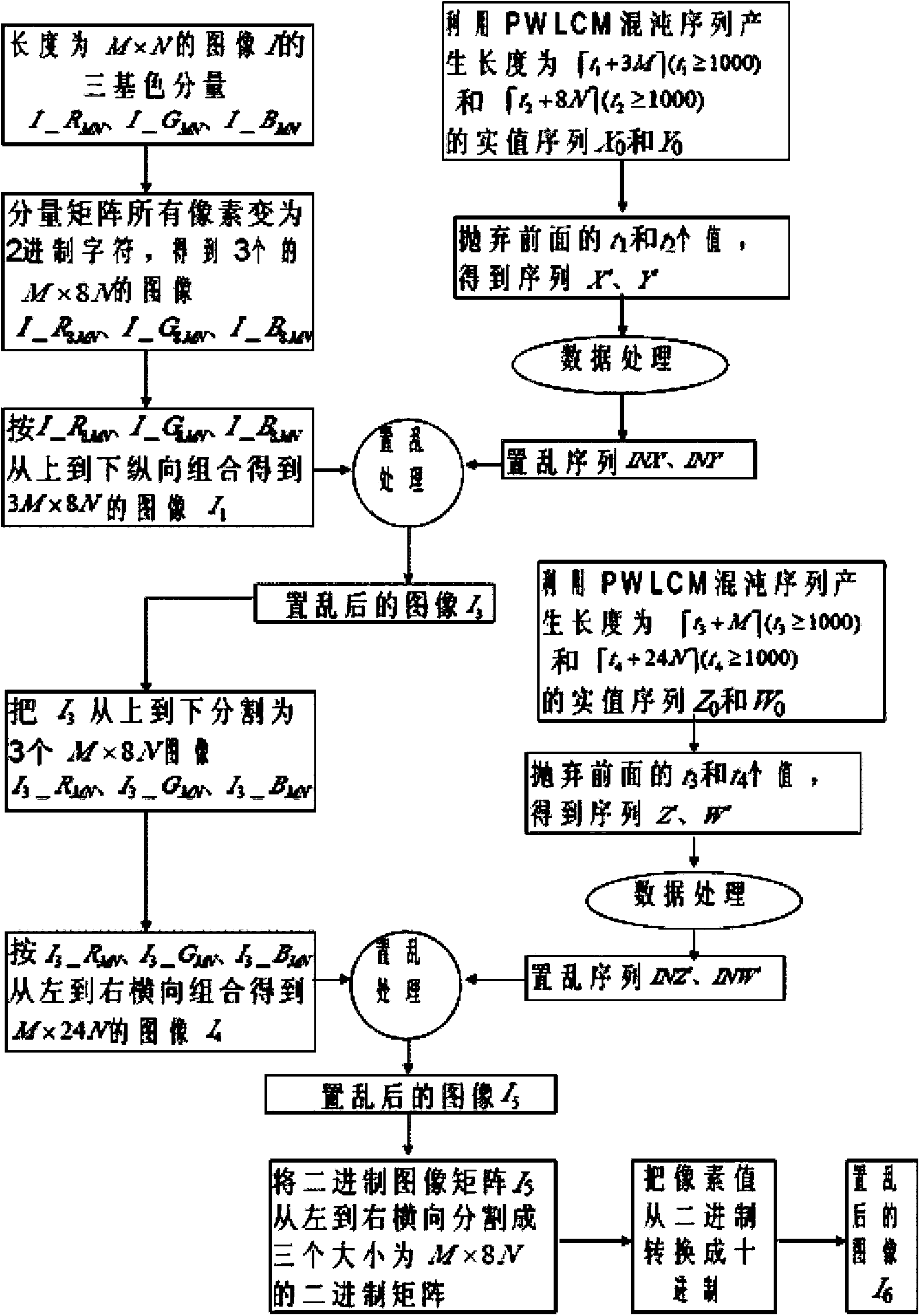
Color image encryption method based on chaos sequence and hyper-chaos system
InactiveCN103489151AImprove securityLarge key spaceImage data processing detailsChaotic systemsDiffusion
The invention relates to a color image encryption method based on a chaos sequence and a hyper-chaos system. The color image encryption method mainly comprises the following steps: an original color image is subjected to bit level united scrambling to obtain a scrambled image; the scrambled image is decomposed into three primary color components, that is R, G and B, and the hyper-chaos system is used for generating an encryption matrix which is used for encrypting the scrambled image; all pixel values of the three primary color components of the scrambled image are changed by utilizing the encryption matrix in combination with plaintext information and information of the three primary color components, united diffusion is conducted to obtain the three primary color components of the image after the united diffusion, and therefore a final encrypted image is obtained. By means of the color image encryption method, a secret key space is greatly enlarged, the safety, the encryption effect and the sensitivity of a secret key are higher, the anti-attack ability is stronger, and hardware implementation is easier.
Owner:HENAN UNIVERSITY
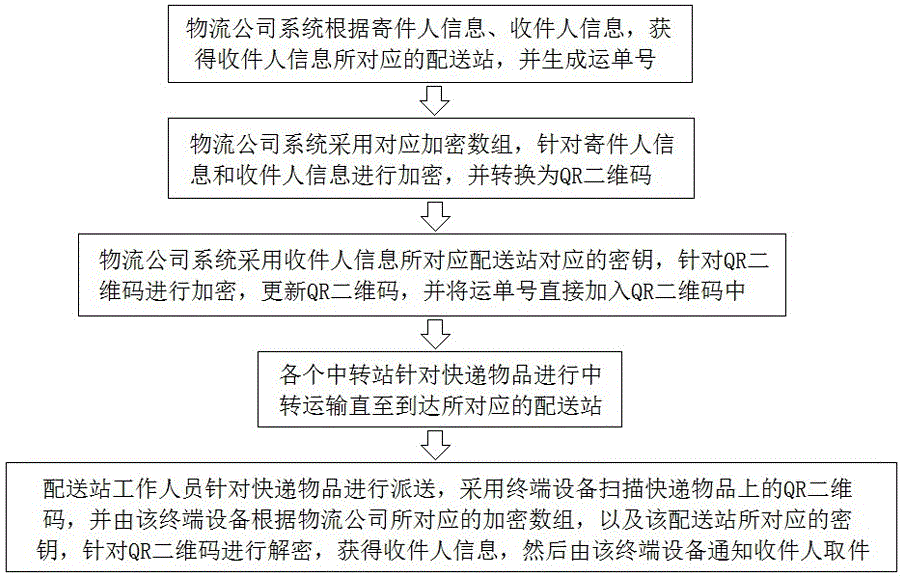
Logistics method based on QR two-dimensional code
ActiveCN107180328AImprove transfer efficiencyHigh degree of encryptionLogisticsRecord carriers used with machinesDimensional modelingEncryption
The invention relates to a logistics method based on a QR two-dimensional code. A secondary encryption mechanism is introduced, under the condition of not affecting the article taking of a user, the encryption level of information by the QR two-dimensional code is effectively strengthened, and the security is greatly improved. In the process of express goods transit, a new logistics scheduling method is introduced, the logistics transit efficiency can be effectively improved, a logistics time is shortened, and the logistics efficiency is improved.
Owner:NANJING UNIV OF POSTS & TELECOMM
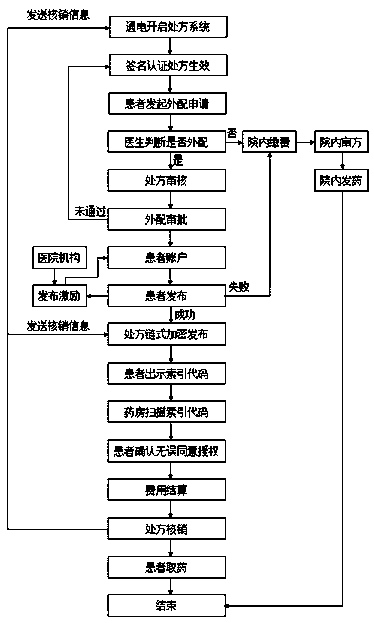
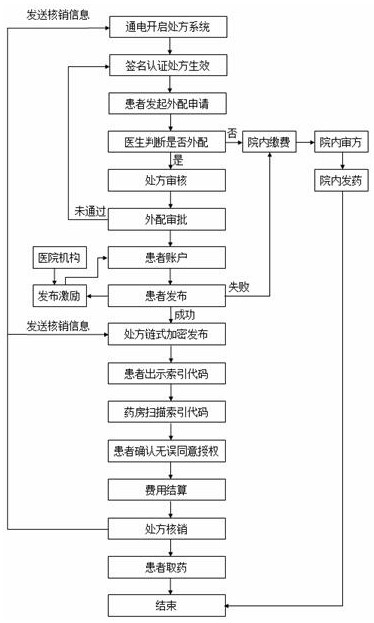
Prescription dispensing method based on blockchain technology
ActiveCN109065115AProtect personal privacyHigh degree of encryptionHealth-index calculationDrug and medicationsMedicineMedical prescription
The invention relates to a prescription dispensing method based on the blockchain technology. A personal index code and a prescription index code for the patient's personal information and a personalelectronic prescription are published and generated through blockchain encryption, the encryption degree is high, the patient's personal information and the prescription information are effectively protected, the patient's personal privacy is guaranteed, moreover, other organizations are prevented from maliciously intercepting and tampering with the patient's personal information and the prescription information.
Owner:长沙瀚云信息科技有限公司
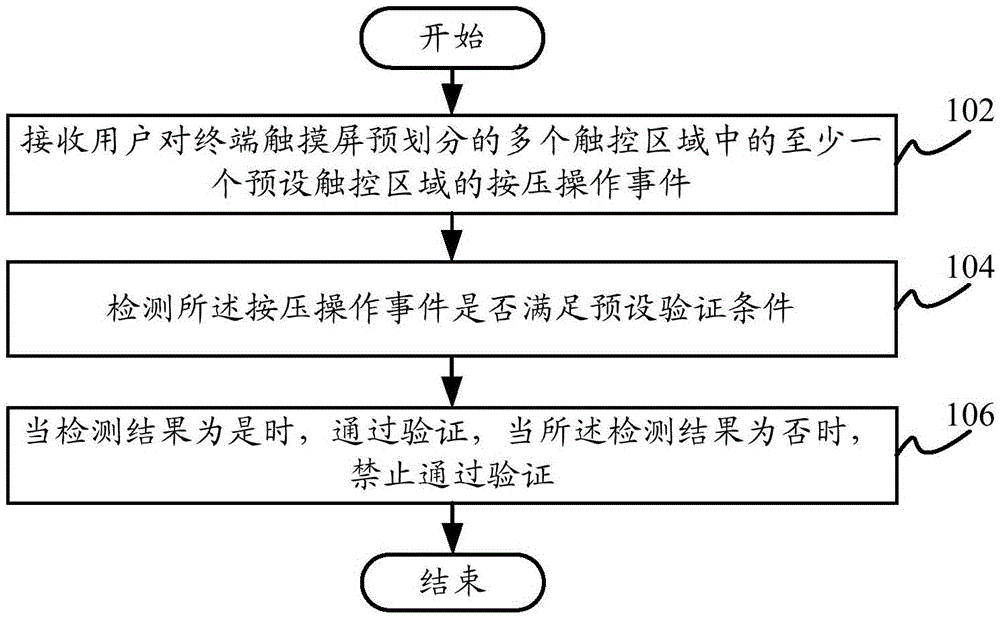
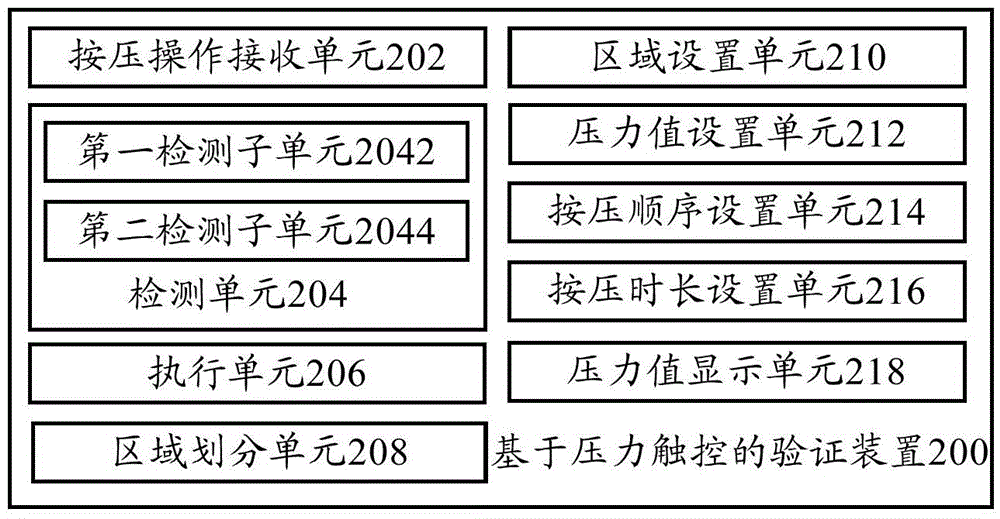
Verification method based on pressure touch control, verification device based on pressure touch control, and terminal
InactiveCN105653091AImprove securityImprove experienceInternal/peripheral component protectionInput/output processes for data processingPaymentValidation methods
The invention provides a verification method based on pressure touch control, a verification device based on pressure touch control, and a terminal, wherein the verification method based on pressure touch control comprises the following steps of receiving a pressing operation event of at least one preset touch control region in a plurality of touch control regions pre-divided by a user on a terminal touch screen; detecting whether the pressing operation event meets a preset verification condition or not; if the detection result shows that the pressing operation event meets the preset verification condition, passing the verification; and if the detection result shows that the pressing operation event does not meet the preset verification condition, forbidding to pass the verification. By using the technical scheme, the touch screen position and the touch control pressure value are combined to form dual encryption; the verification encryption degree is improved; the security of operations such as terminal unlocking and payment verification is improved; the security of personnel information and properties of the user is ensured; and the user experience is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
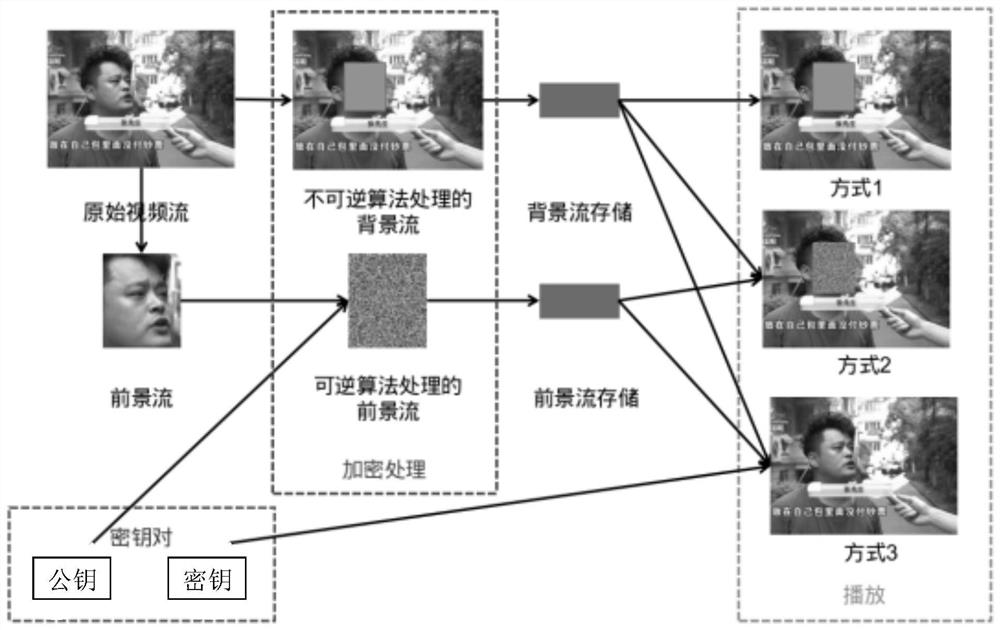
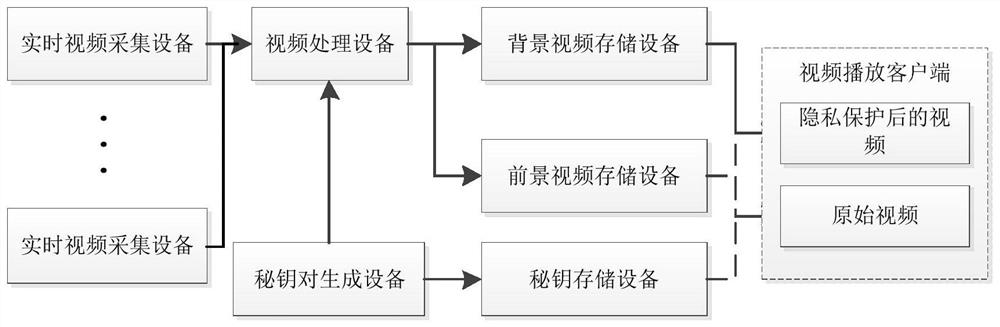
Real-time video sensitive information protection system and method
PendingCN113630587AEasy to play directlyHigh degree of encryptionGeometric image transformationDigital data protectionTemplate matchingData expansion
The invention provides a real-time video sensitive information protection system and method. The real-time video sensitive information protection method comprises the following steps: S1, collecting a real-time video stream; S2, separating the video stream, separating the video stream by an equal interval, adopting a detection algorithm to extract a preset foreground stream in each segment of video stream, and hiding privacy and sensitive information in the foreground stream through a reversible algorithm, wherein the reversible algorithm refers to a public key generated in a corresponding time interval, the detection algorithm comprises target detection and template matching algorithms, the reversible algorithm comprises a scrambling algorithm and a password book translation algorithm, and a scrambling algorithm performs data encryption through image splitting, data expansion and image combination; S3, adopting an irreversible algorithm to erase sensitive information in the video stream so as to obtain a background stream, wherein the irreversible algorithm comprises a mosaic method, a color block covering method and a frosted glass effect; and S4, restoring the original video stream. The encryption degree of the video stream can be improved, encryption is reversible, and the protection degree of personal privacy is greatly improved.
Owner:北京朗达和顺科技有限公司
Image processing method and intelligent device
PendingCN113468546AImprove securityReduce risk of leakageDigital data protectionInternal/peripheral component protectionComputer hardwareImaging processing
The invention discloses an image processing method and intelligent device and the method comprises the steps: encrypting a first area and a second area when a to-be-processed image is recognized to comprise the first region, wherein the first area comprises privacy information, and the privacy information comprises human body information and / or text information so that the encryption degree of the first sub-encrypted data is higher than that of the second sub-encrypted data, that is, the security of the first area is higher than that of the second area, so that the security coefficient of the first area can be improved, and the risk that privacy information is leaked is reduced. Moreover, the encryption degree of the first sub-encrypted data is higher than that of the second sub-encrypted data, so that when the first area and the second area are encrypted, reduction of the operation speed and data processing speed can be avoided, and purposes of high security and high processing speed can be realized at the same time.
Owner:HISENSE GRP HLDG CO LTD
Micro-service security authentication method and device based on TOKEN, and storage medium
ActiveCN112653556AReduce the risk of theftNo legacy of safety certificationUser identity/authority verificationDigital data authenticationPasswordEngineering
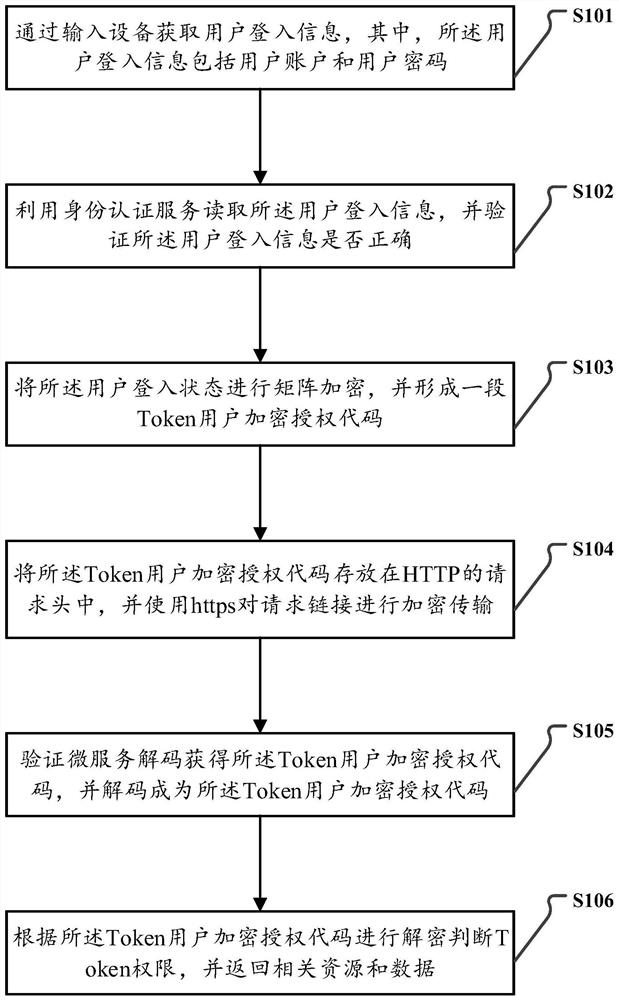
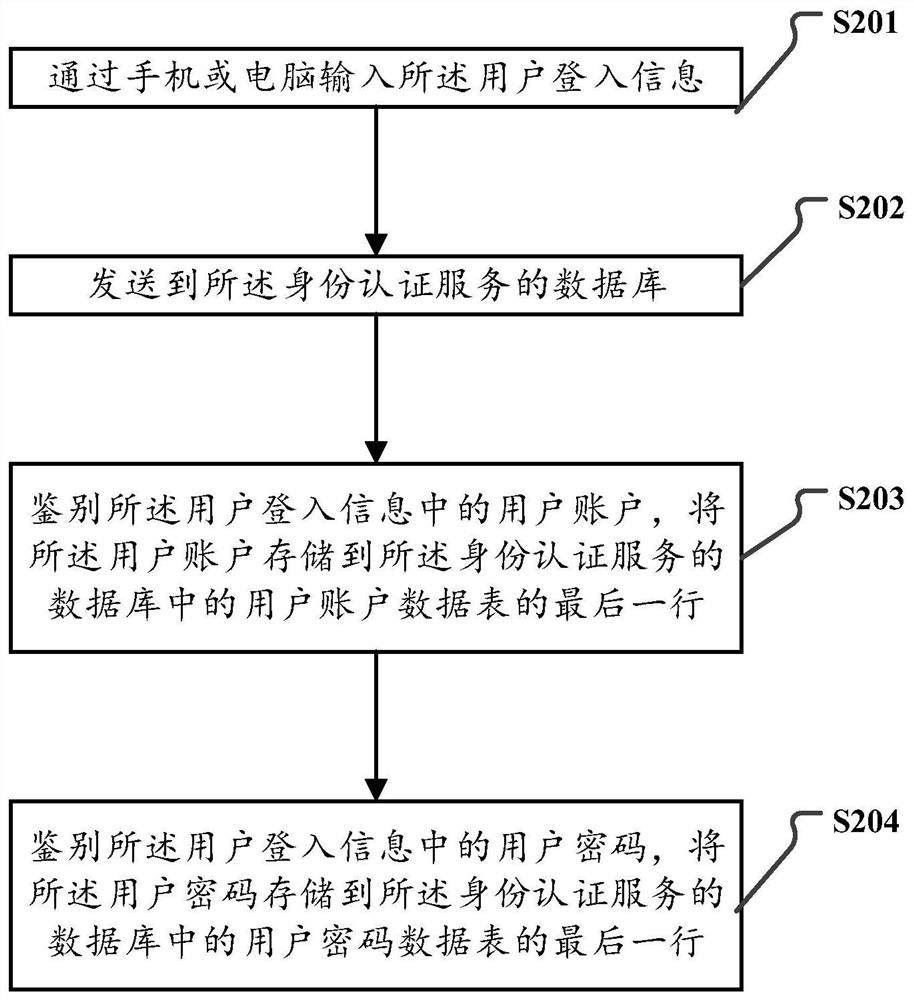
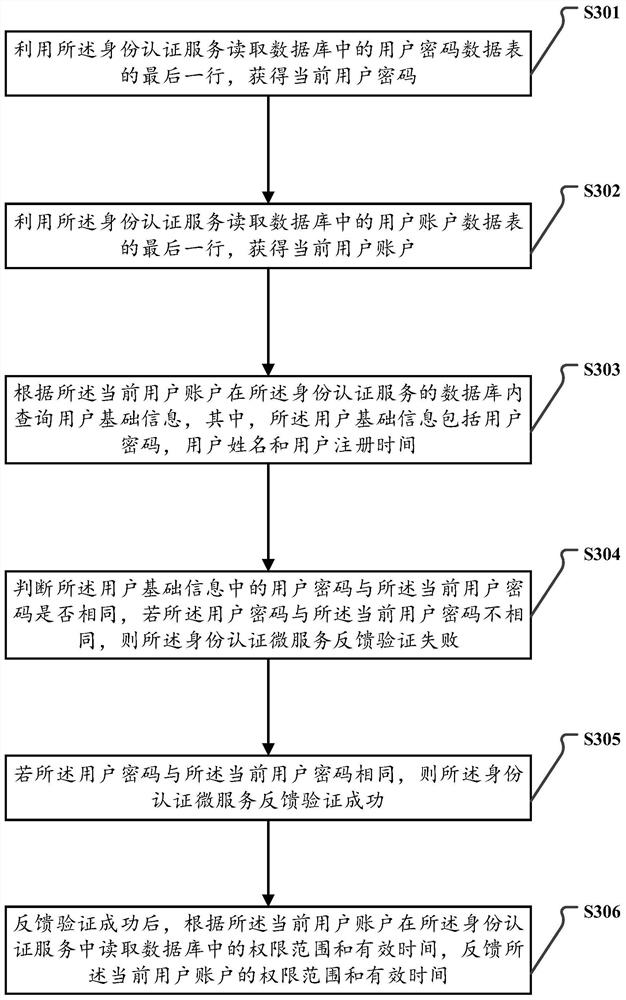
The invention provides a micro-service security authentication method and device based on TOKEN, and a storage medium. According to the scheme, the method comprises: obtaining user login information through input equipment, and the user login information comprising a user account and a user password; reading the user login information by utilizing an identity authentication service, and verifying whether the user login information is correct or not; performing matrix encryption on the user login state, and forming a section of Token user encryption authorization code; storing the Token user encryption authorization code in a request header of an HTTP, and performing encryption transmission on a request link by using https; and the verification micro-service decoding to obtain the Token user encryption authorization code, decrypting the Token user encryption authorization code to judge the Token permission, and returning related resources and data. According to the scheme, the security of the system is improved by designing a complete set of authentication system, and dual encryption measures are used in the process of transmitting and receiving Token user encryption authorization codes, so that the security of account information in the system of the micro-service architecture can be reliably protected.
Owner:光大兴陇信托有限责任公司
Access control system and method based on image recognition technology
InactiveCN109979056AImprove securityHigh degree of encryptionSensing radiation from moving bodiesIndividual entry/exit registersControl systemMedia access control
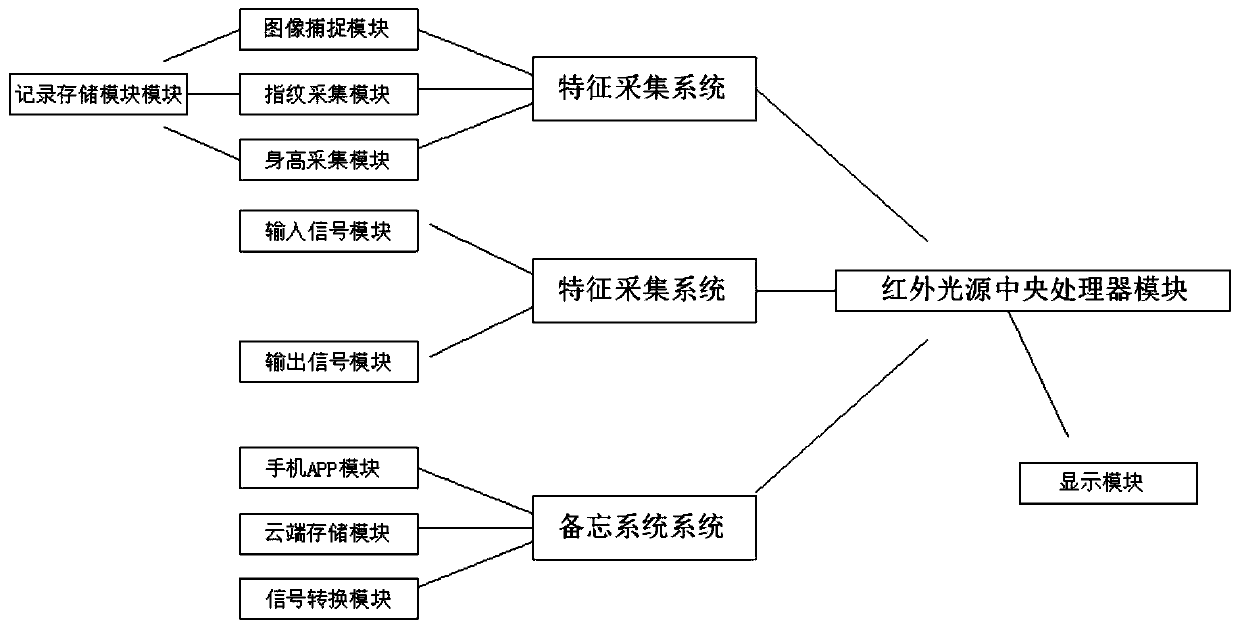
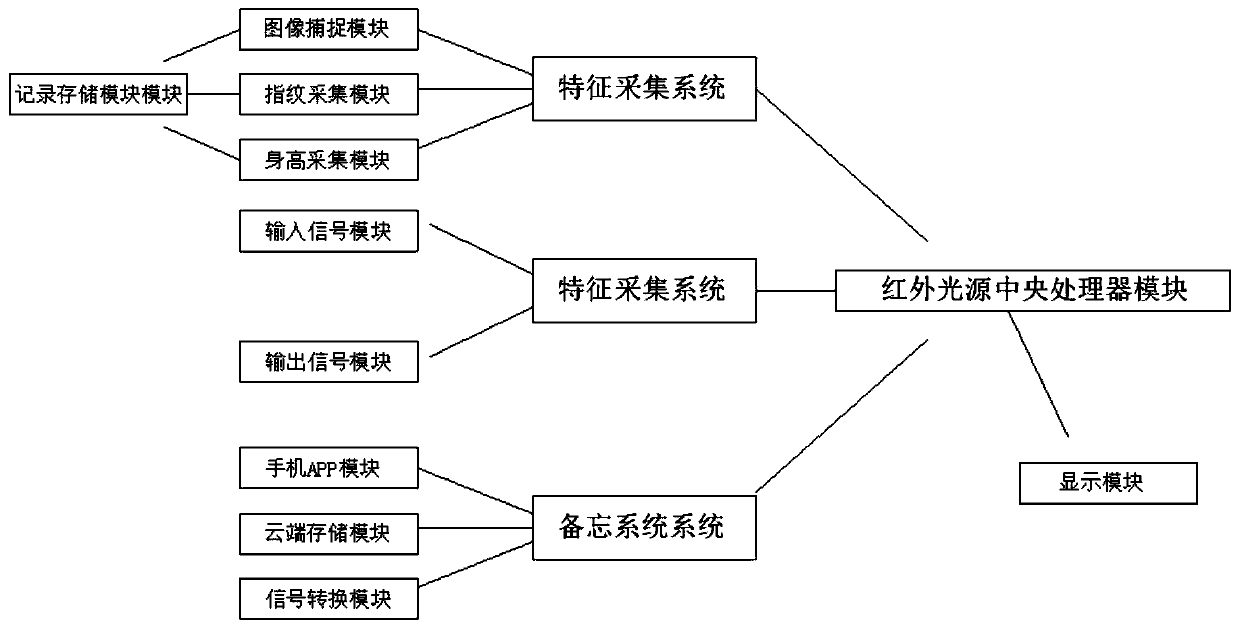
The invention discloses an access control system based on an image recognition technology. The access control system comprises a feature acquisition system, a feature verification system and a memorandum system, wherein the feature acquisition system comprises an image capturing module, a fingerprint acquisition module, a height acquisition module, an infrared light source central processing calculation module and a recording and storage module, the feature verification module comprises an input signal module and an output signal module, and the memorandum system comprises a mobile phone APP module, a cloud storage module, a signal conversion module and a display module. By means of an infrared sensing module arranged in the access control system, the access control system can only be opened when sensing the temperature of an object during the opening and closing of the access control system, thus a duplicated fingerprint or a photographed face picture cannot pass the detection of theaccess control system, the safety factor of the access control system is effectively increased, and memorandum events stored in advance on the display screen are observed, so as to remind the staff tohandle the pending events in time and avoid forgetting them.
Owner:彭喆
Water-based fluorescent ink as well as preparation method and application thereof in full-color printing and encryption anti-counterfeiting
PendingCN113755057AIncrease storage spaceHigh degree of encryptionPattern printingInksColor printingComputer printing
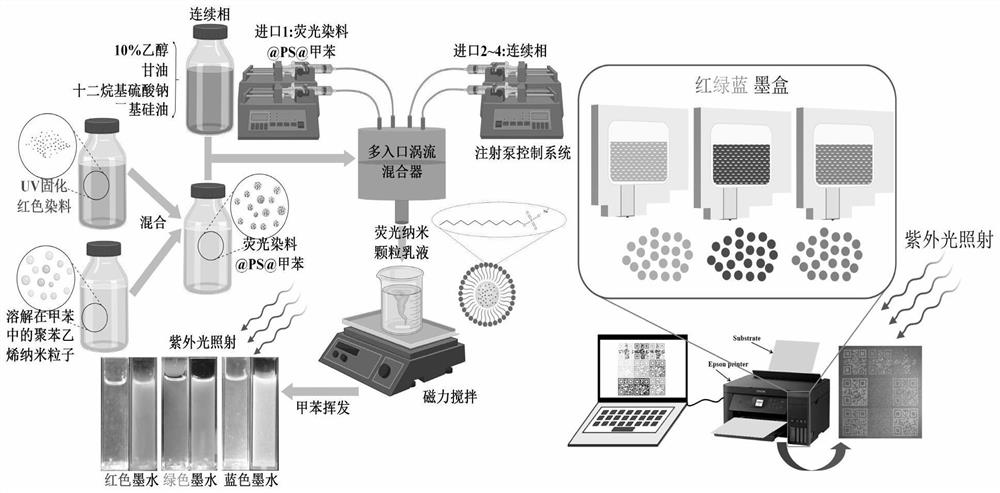
The invention relates to the technical field of water-based fluorescent ink, and provides water-based fluorescent ink as well as a preparation method and application thereof in full-color printing and encryption anti-counterfeiting. The water-based fluorescent ink provided by the invention comprises the components: polystyrene nanoparticles, a surfactant, water, ethanol, glycerol and a UV-cured fluorescent dye, wherein the fluorescent dye is a red, green or blue fluorescent dye. The fluorescent ink with three colors of red, green and blue is prepared by adopting an instantaneous nano precipitation method, the high-viscosity fluorescent dye is dispersed and transferred from an oil phase to a water phase, and the obtained water-based fluorescent ink takes water as a main continuous phase, is good in safety and relatively low in viscosity, can be used for a high-flux civil ink-jet printer and can realize diversification and high efficiency of printed patterns. Patterns printed by the ink are completely invisible under natural light, different colors are displayed under ultraviolet light with different wavelengths, the ink can be used for full-color printing, the pattern quality is good, and the ink has wide application prospects in fluorescent color-changing encryption and anti-counterfeiting.
Owner:HARBIN INST OF TECH SHENZHEN GRADUATE SCHOOL
Memory chip for imaging equipment
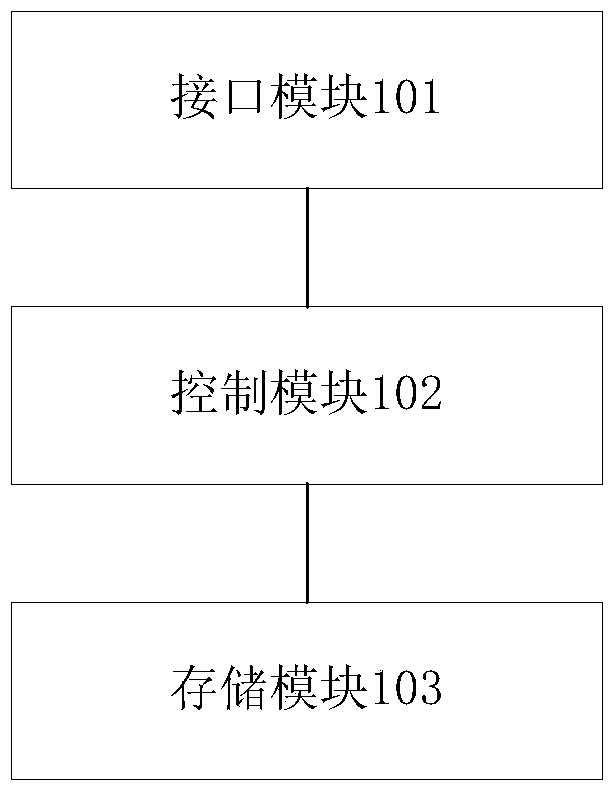
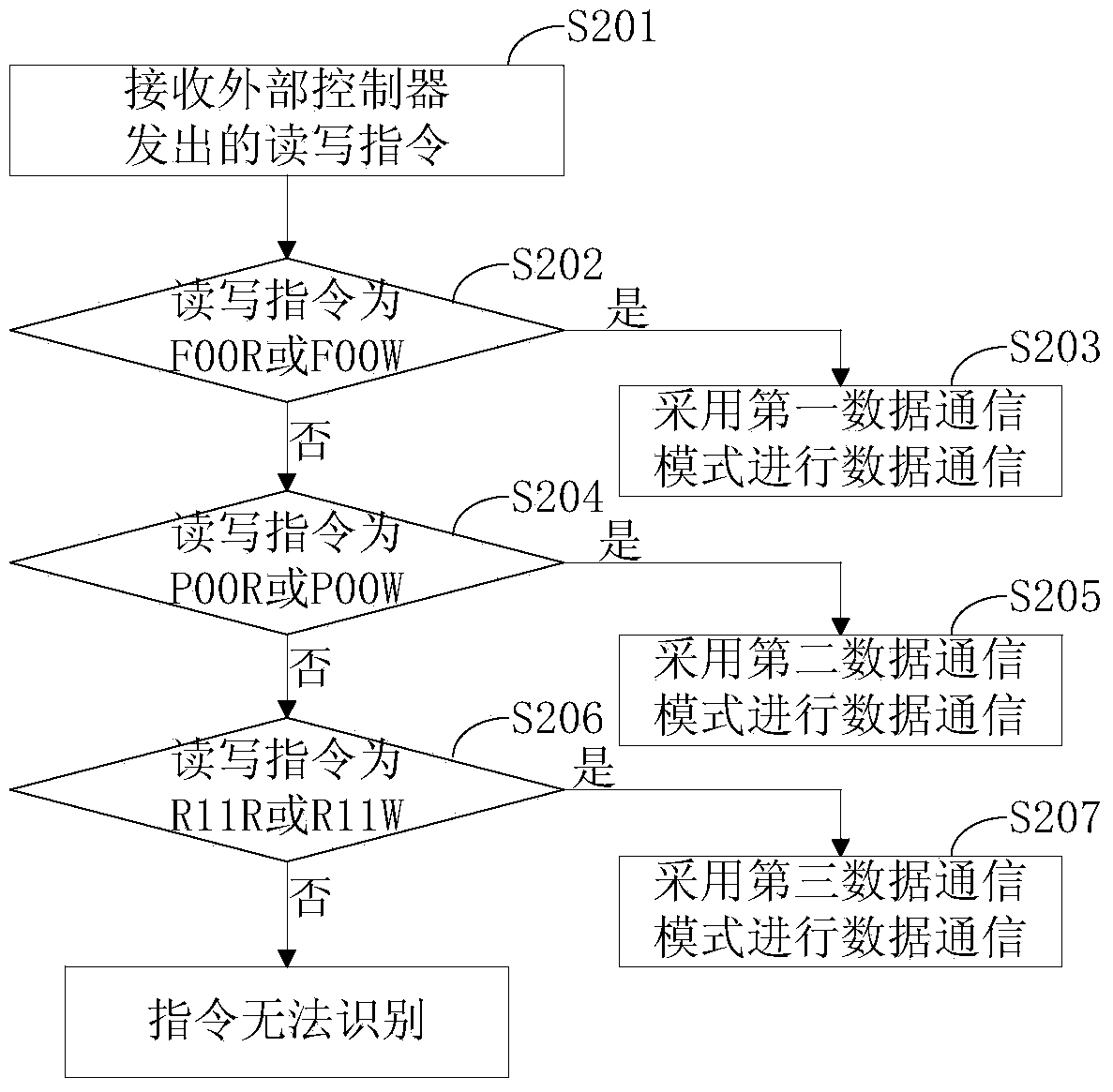
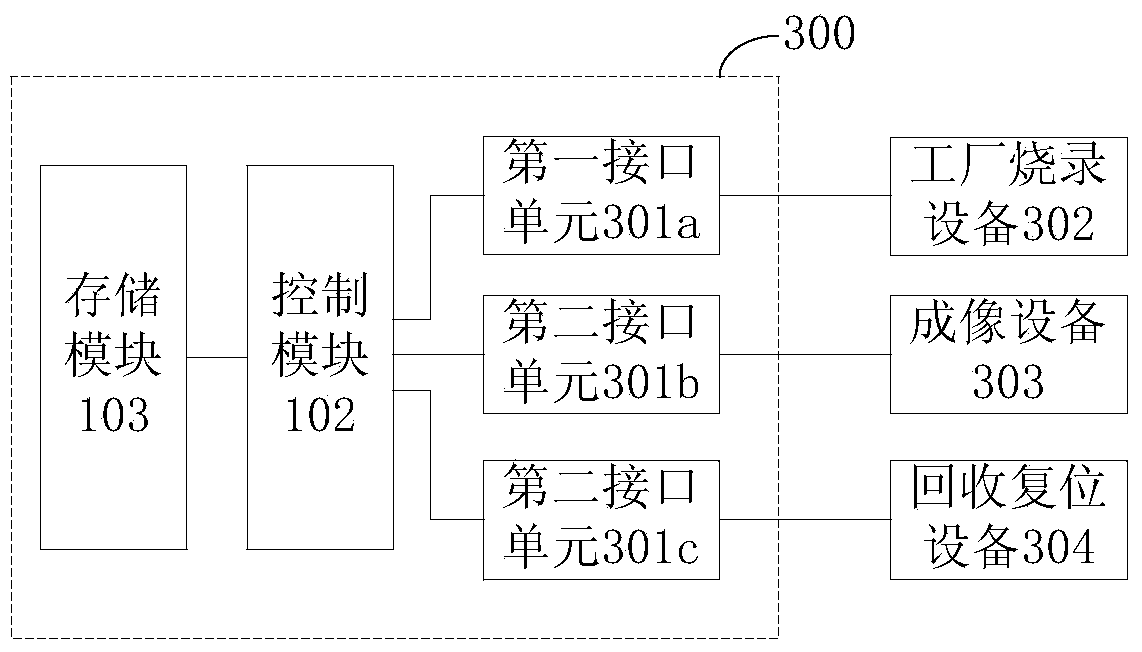
ActiveCN104029491AImprove reliabilityImprove practicalityElectrographic process apparatusPrintingMemory chipComputer module
The invention discloses a memory chip for imaging equipment. The memory chip comprises an interface module connected with an external controller and used for receiving a signal emitted by the external controller, a memory module for storing information related to an imaging box, and a control module connected between the interface module and the memory module and used for configuring the memory chip to a corresponding data communication mode according to the signal emitted by the external controller so as to realize data communication between the memory module and the external controller, wherein the control module can configure the data communication mode of the memory chip to a recovery resetting mode or a factory burning mode; and in the factory burning mode, the encryption degree of communication data is lower than the encryption degree of communication data in the recovery resetting, and the transmission speed and the transmission reliability of the data are higher than the transmission speed and the transmission reliability of the data in the recovery resetting. When recovery resetting is performed for the memory chip, the security of the communication data between the chip and the external controller is guaranteed.
Owner:APEX MICROELECTRONICS CO LTD
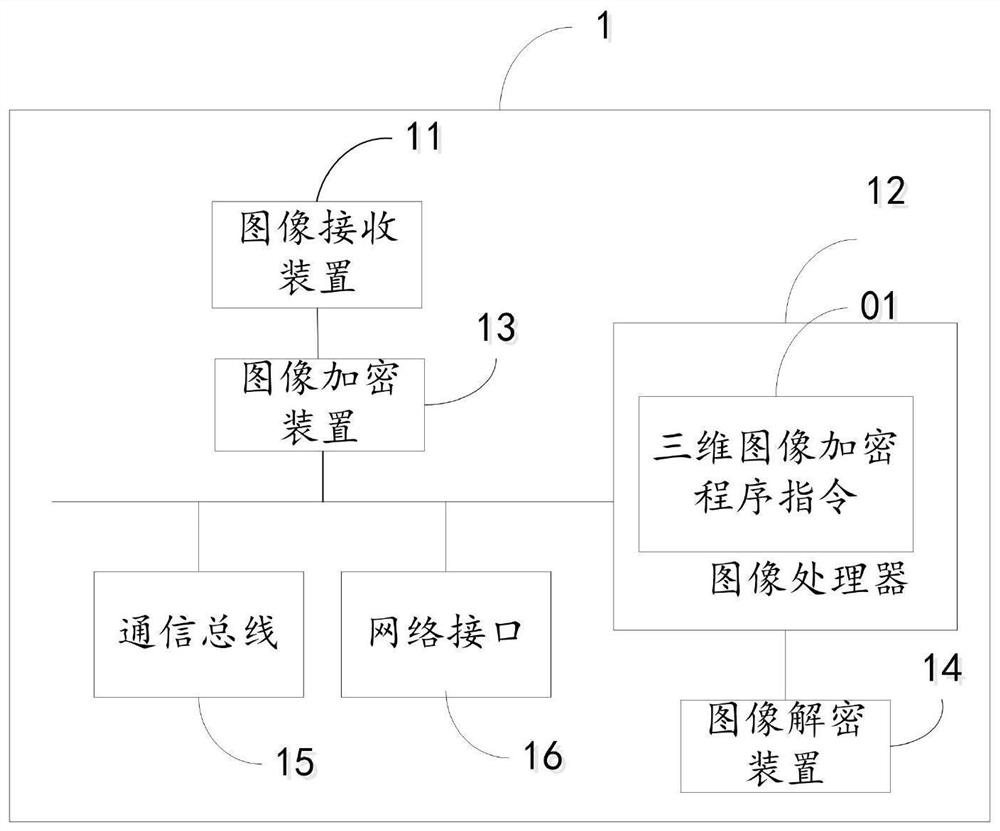
Three-dimensional image encryption method and system based on computer-generated hologram
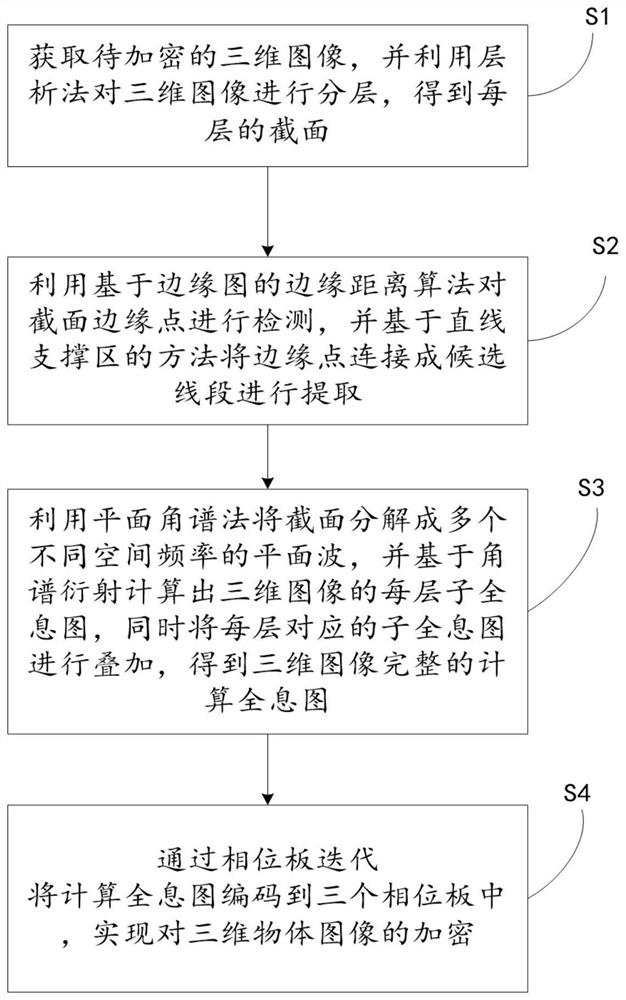
InactiveCN111767562AReduced edge retention characteristicsReduce smoothnessImage enhancementImage analysisAlgorithmEdge maps
The invention relates to the technical field of three-dimensional image encryption, and discloses a three-dimensional image encryption method based on a computer-generated hologram, which comprises the following steps of acquiring a three-dimensional image to be encrypted, and layering the three-dimensional image by using a tomography method to obtain a cross section of each layer, detecting section edge points by using an edge distance algorithm based on an edge graph, connecting the edge points into candidate line segments based on a linear support area method, decomposing the cross sectioninto a plurality of plane waves with different spatial frequencies by using a plane angular spectrum method, calculating each layer of sub-hologram of the three-dimensional image based on angular spectrum diffraction, and superposing the sub-holograms corresponding to the layers to obtain a complete computer-generated hologram of the three-dimensional image, and encoding the computer-generated hologram into the three phase plates through phase plate iteration, so that the encryption of the three-dimensional object image is realized. The invention further provides a three-dimensional image encryption system based on the computer-generated hologram. Thus, encryption of the three-dimensional image is realized.
Owner:汪金玲
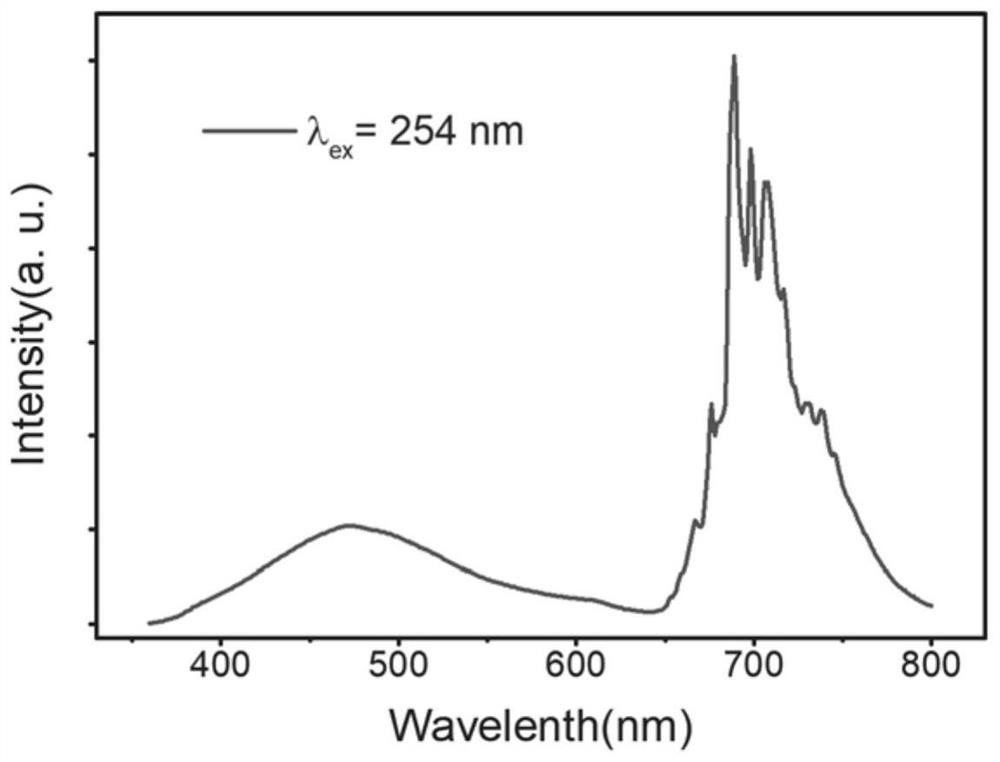
Long-afterglow nanoparticle with fluorescence encryption anti-counterfeiting characteristics, and preparation method thereof
ActiveCN111607395AAchieve irradiationAchieve launchMaterial nanotechnologyStampsOptical propertyFluorescence
The invention provides a long-afterglow nanoparticle with fluorescence encryption anti-counterfeiting characteristics, and a preparation method thereof. The long-afterglow nanoparticle is composed oftwo nanoparticles, namely a ZnAlxGeyO(2+3x+4y) / 2 nanoparticle serving as interference information and a ZnAlx-zCrzGeyO(2+3x+4y) / 2 nanoparticle serving as anti-counterfeiting information, wherein x isgreater than 0 and less than or equal to 2, y is greater than 0 and less than or equal to 1, z is greater than 0 and less than or equal to 0.3, and z is less than x; the ZnAlx-zCrzGeyO(2+3x+4y) / 2 nanoparticle emits visible light under the excitation of ultraviolet light, and emits near-infrared light under the stop of the excitation of the ultraviolet light; and the ZnAlxGeyO(2+3x+4y) / 2 nanoparticle emits visible light under the excitation of ultraviolet light, and does not emit light when the excitation of the ultraviolet light is stopped. A fluorescent anti-counterfeiting ink can be preparedby utilizing different optical characteristics of the two nanoparticles, digital anti-counterfeiting and two-dimensional code anti-counterfeiting application of fluorescent encryption is realized, the encryption and anti-counterfeiting processes are easy to operate, the encryption degree is high, the encryption stability is high, the anti-counterfeiting concealment is strong, and the identification degree is high.
Owner:HANSHAN NORMAL UNIV
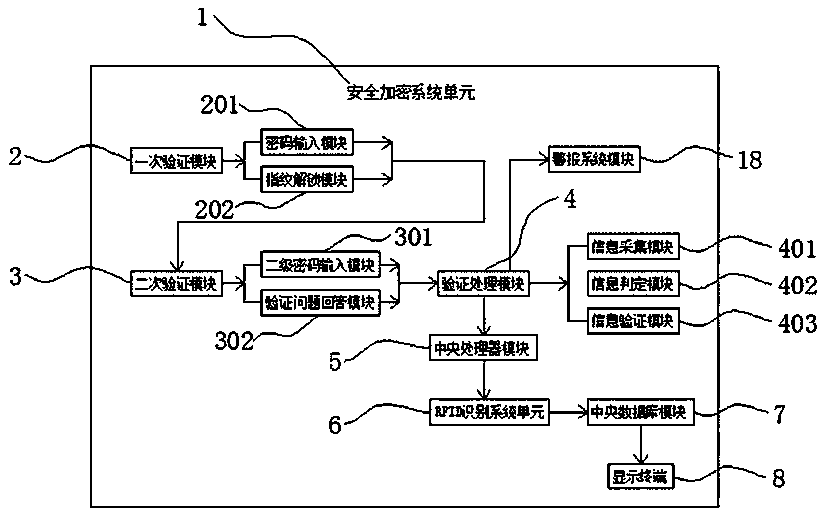
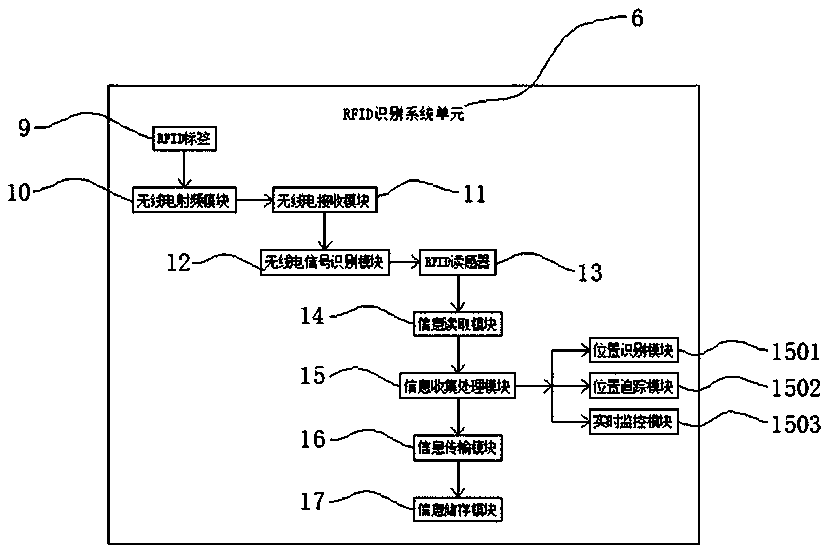
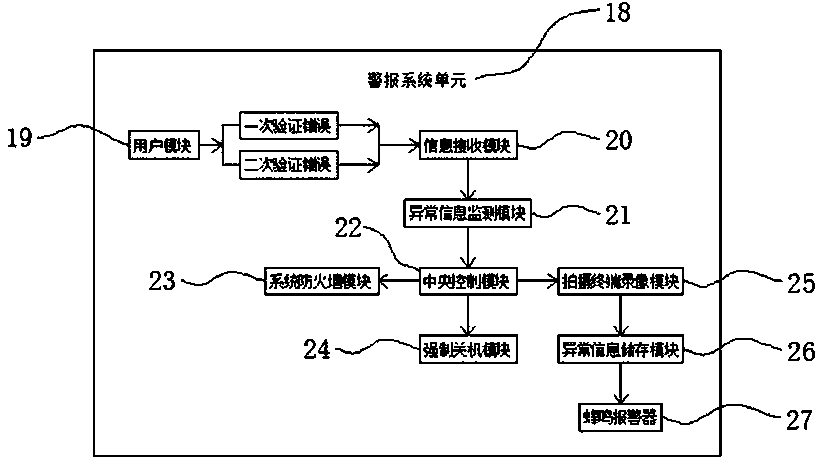
A computer encryption system adopting an RFID identification system
InactiveCN109726576AEffective Double EncryptionImprove securityDigital data protectionDigital data authenticationRadio receptionPassword
The invention discloses a computer encryption system adopting an RFID identification system, and relates to the technical field of computers. The system comprises a security encryption system unit, anRFID identification system unit and an alarm system unit; the inner side of the security encryption system unit comprises a primary verification module and a secondary password input module; the output end of the secondary password input module is electrically connected with a verification processing module; the output end of the verification processing module is electrically connected with a central processing unit module; the RFID identification system unit is electrically connected to the output end of the central processing unit module; the output end of the RFID identification system unit is electrically connected with a central database module, the output end of the central database module is electrically connected with a display terminal, and the inner side of the RFID identification system unit comprises a radio receiving module. The computer encryption system has the beneficial effects that the data encryption device can effectively perform double encryption on the data through verification setting of the primary verification module and the secondary verification module.
Owner:LAIWU VOCATIONAL & TECHNICAL COLLEGE
Face acquisition system based on edge intelligent perceptron and privacy protection method
PendingCN114373200AImprove securityPrevent theftCharacter and pattern recognitionDigital data protectionPattern recognitionFeature extraction
The invention relates to a face acquisition system and privacy protection method based on an edge intelligent perception body, and the method comprises a face encryption process and a face decryption process, and the face information encryption process comprises the steps: obtaining a face image through the edge perception body, and obtaining a plurality of face regions in the face image; performing noise processing by using the feature extraction result of the face reference image, and performing superposition to protect the semantic features of the face; carrying out fuzzy processing on the face region and then storing the face region; in the face information decryption process, the visual terminal recognizes the face semantic features of a terminal user to form a decryption key, the face feature cloud database is traversed through a spatial-temporal index to carry out key matching, face feature self-decryption face pairing is achieved, then the encrypted video is presented through the generative adversarial network associated with the semantic features, and the face information is decrypted through the generated adversarial network associated with the semantic features. And multi-face targeted decryption in the image is realized. Compared with the prior art, the method has the advantages of image localization distributed storage, face feature cloud edge collaborative encryption, low-delay semantic transmission and the like.
Owner:TONGJI UNIV
Bar code generation and identification method
PendingCN109919281AAvoid repeated mistakesAvoid multiple usesRecord carriers used with machinesBarcodeIntelligent equipment
The invention discloses a bar code generation and identification method. The method comprises the following steps: (1) a user determines a bar code instruction according to requirements and sends thebar code instruction to a server; (2) the server receives the instruction and then processes the instruction to generate a random bar code; and (3) barcode recognition and application are carried outby using the intelligent equipment terminal. The method can effectively avoid the conditions of repeated errors of barcodes and multiple purposes of one code, is high in encryption degree, low in costand high in efficiency, and is convenient for large-scale popularization and application.
Owner:云南纳博生物科技有限公司
Key agreement method, device and system
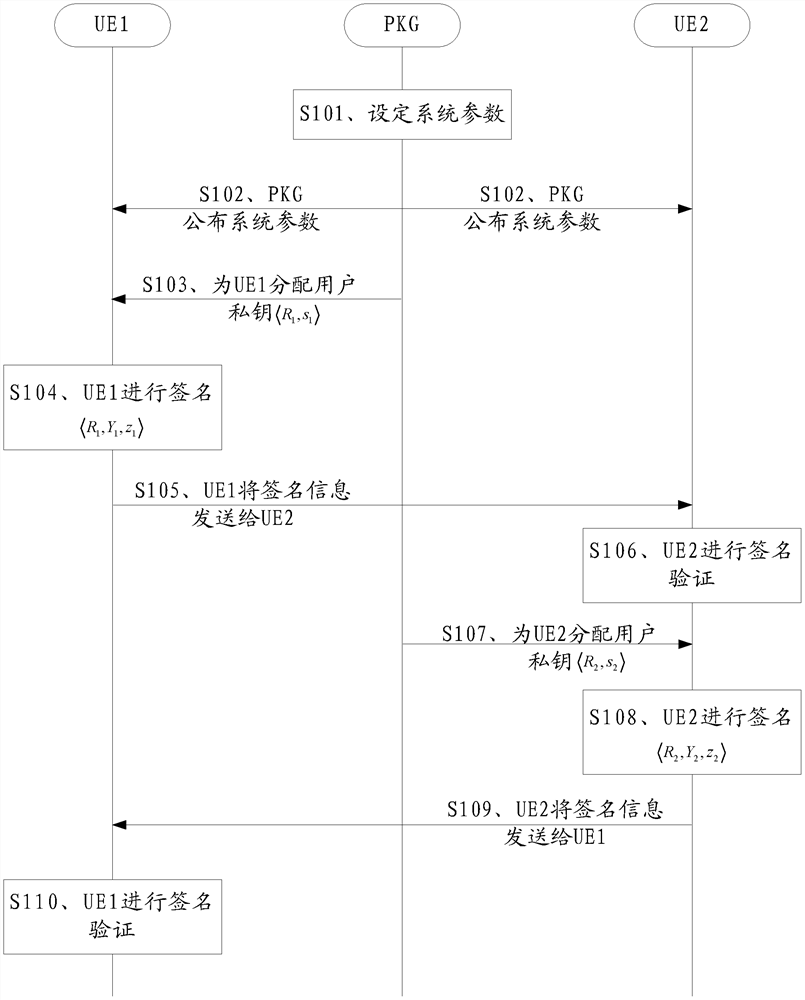
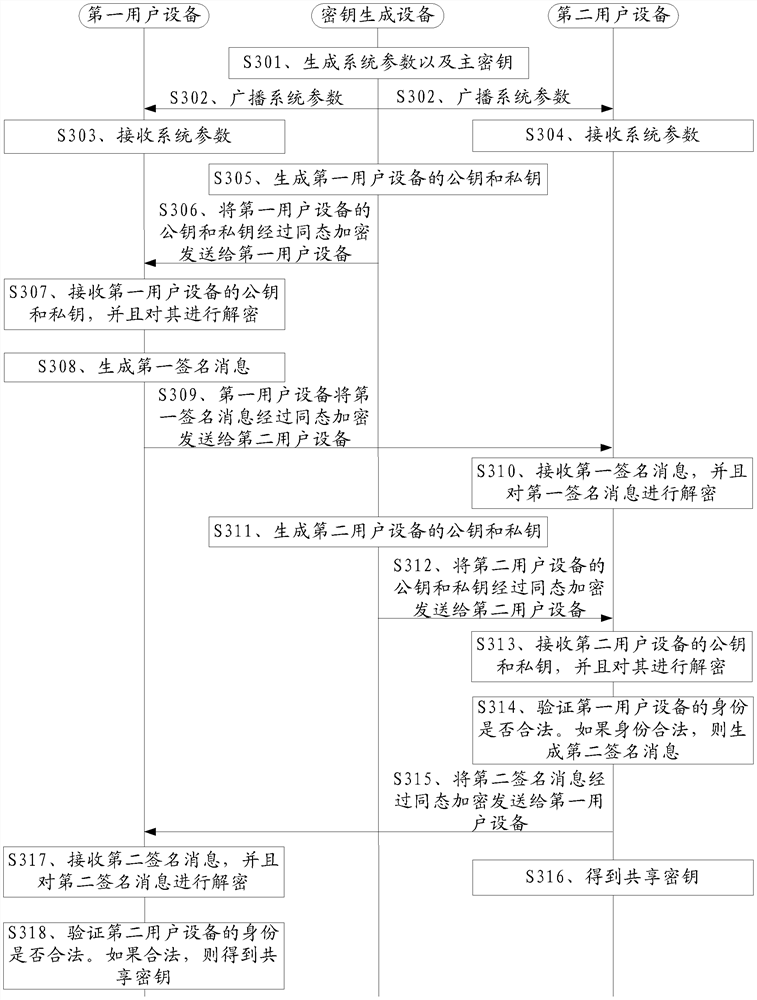
InactiveCN107925578BHigh degree of encryptionSmall communication and computational overheadUser identity/authority verificationTelecommunicationsKey generation
Disclosed are a key negotiation method, device and system, relating to the field of wireless communications and used for solving the problem of a low degree of encryption when a BNN-IBS is applied to a D2D wireless communication network for key negotiation. The key negotiation method comprises: when a key generation device sends a public key and a private key of a first user equipment to the first user equipment, when the key generation device sends a public key and a private key of a second user equipment to the second user equipment, when the first user equipment sends a first signature message to the second user equipment, and when the second user equipment sends a second signature message to the first user equipment, performing homomorphic encryption. The embodiments of the present invention are applied to a D2D wireless communication network.
Owner:HUAWEI TECH CO LTD
Prescription outsourcing method based on block chain technology
ActiveCN109065115BProtect personal privacyHigh degree of encryptionHealth-index calculationDrug and medicationsElectronic PrescriptionsMedical emergency
Owner:长沙瀚云信息科技有限公司
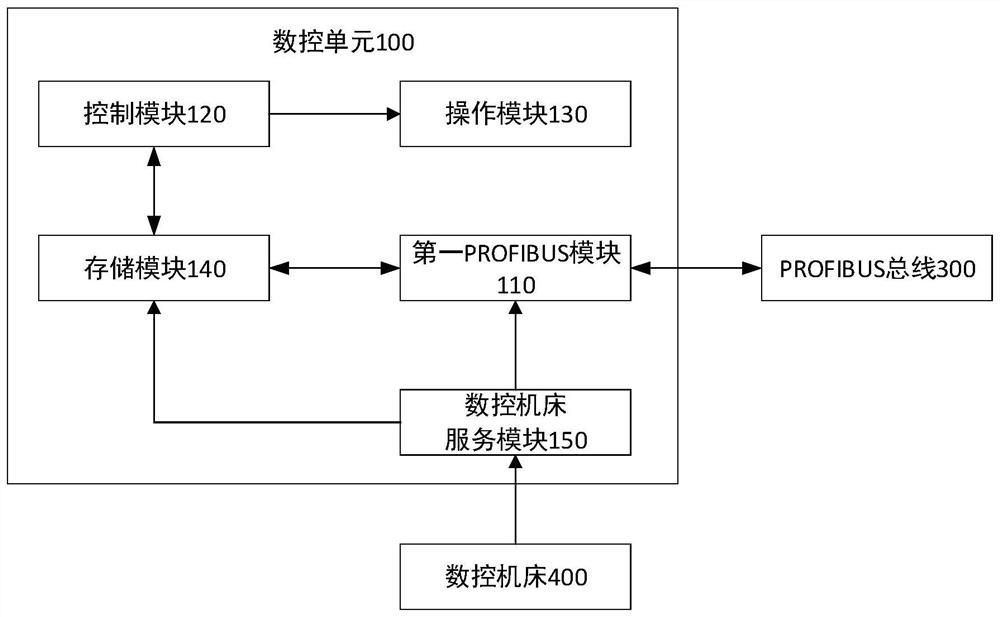
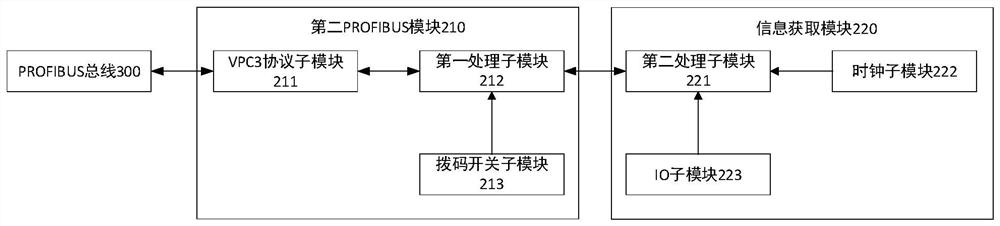
A Hardware Encryption Device Based on Profibus
ActiveCN108667793BHigh degree of encryptionNot easy to brute forceTransmissionComputer hardwareNumerical control
The present invention relates to the field of encryption control, in particular to a hardware encryption device based on a PROFIBUS bus. The hardware encryption device includes a numerical control unit, an encryption unit and a PROFIBUS bus, and the PROFIBUS bus is respectively connected to the numerical control unit and the encryption unit; wherein, the The numerical control unit sends an operation request to the encryption unit through the PROFIBUS bus, and the encryption unit feeds back encryption state information to the numerical control unit through the PROFIBUS bus according to the operation request. The hardware encryption device implements hardware encryption based on the PROFIBUS bus, which has a high degree of encryption and is difficult to be cracked by violence.
Owner:HANS LASER TECH IND GRP CO LTD +1
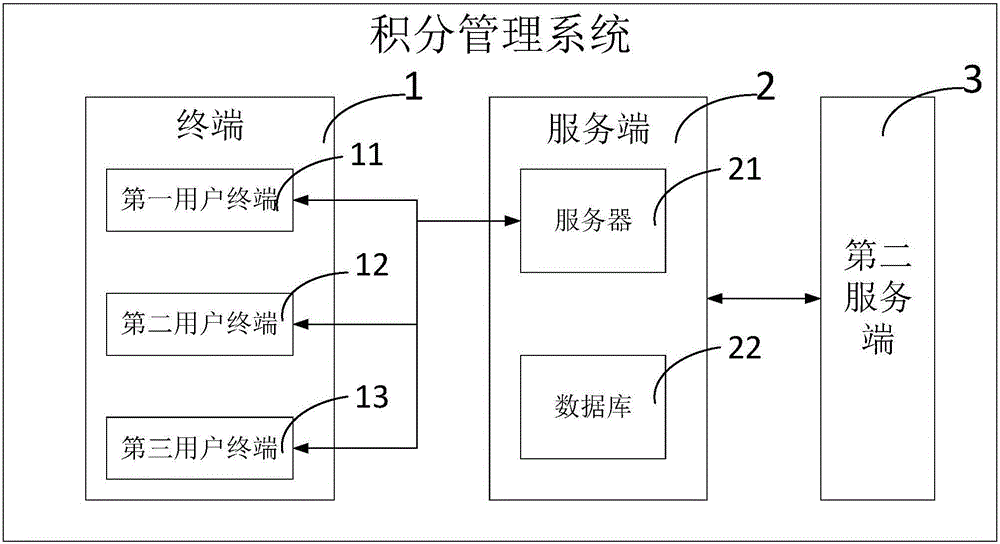
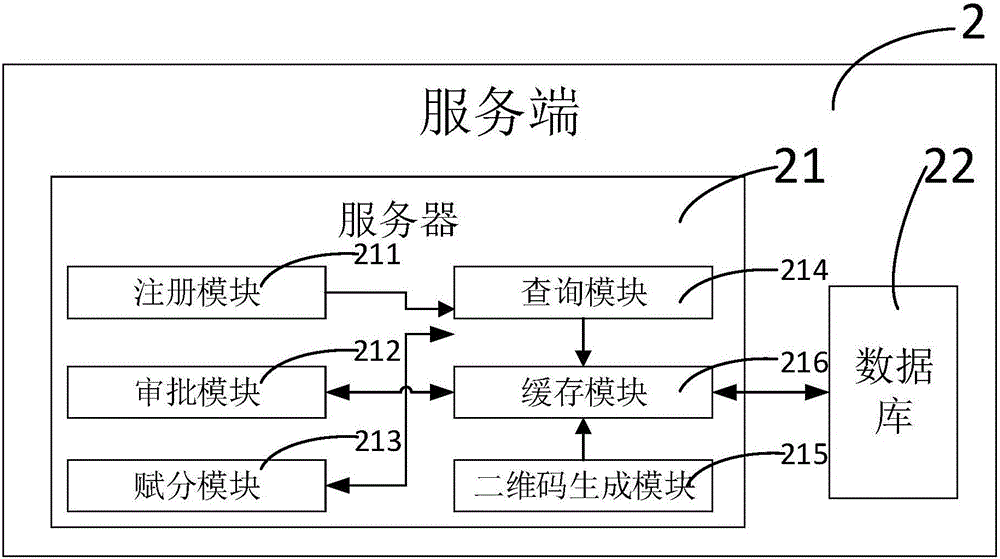
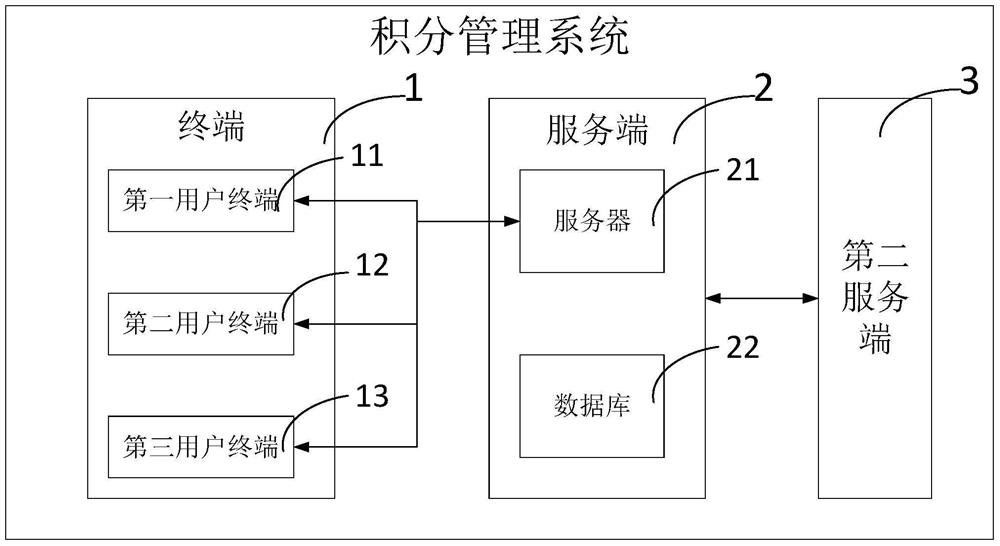
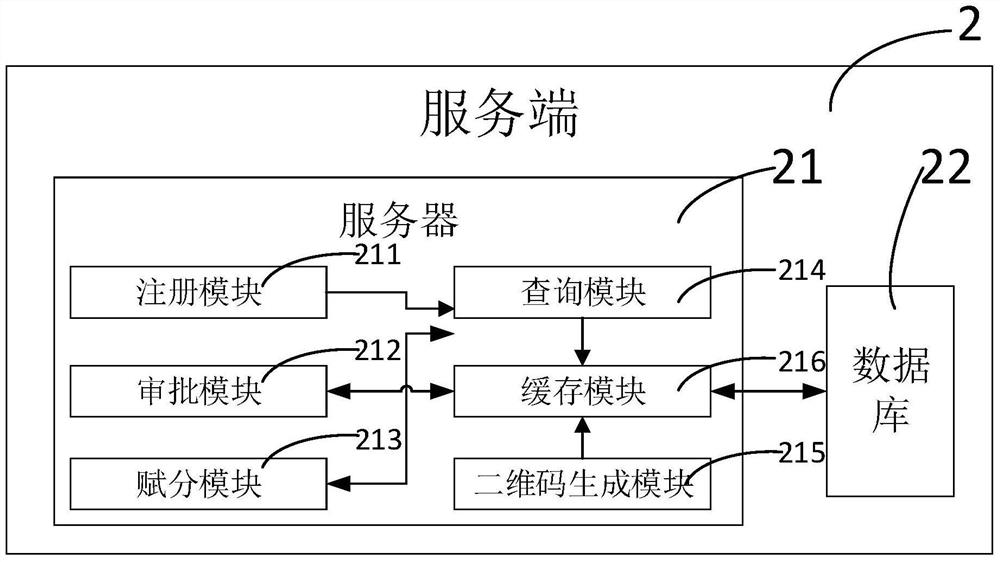
Point management system
ActiveCN106023040AIncreased complexityReduce the value sizeData processing applicationsComputer terminalManagement system
The invention discloses a point management system comprising a terminal via which a user sends an operation request and checks returning data, a server end connected with the terminal, and a second server end connected with the server end, wherein the server end receives the operation request and conducts operation on internal data according to the operation request or transmits the returning data to the terminal, data interaction is performed between the server end and the second server end in a timed manner, and therefore points management can be achieved via the point management system, and data can be rapidly and safely transmitted between the server end and the second server end.
Owner:浙江奥奈斯特信息科技有限公司
A points management system
ActiveCN106023040BIncreased complexityReduce the value sizeData processing applicationsEnd userManagement system
The invention discloses a point management system, which includes: a terminal, through which the user sends an operation request and checks the returned data; a server, which is connected to the terminal, receives the operation request, and sends internal The data is operated or the returned data is sent to the terminal; the second server, which is connected to the server, regularly performs data interaction. In this way, the points management system can manage points, and can quickly and safely transfer data between the server and the second server.
Owner:浙江奥奈斯特信息科技有限公司
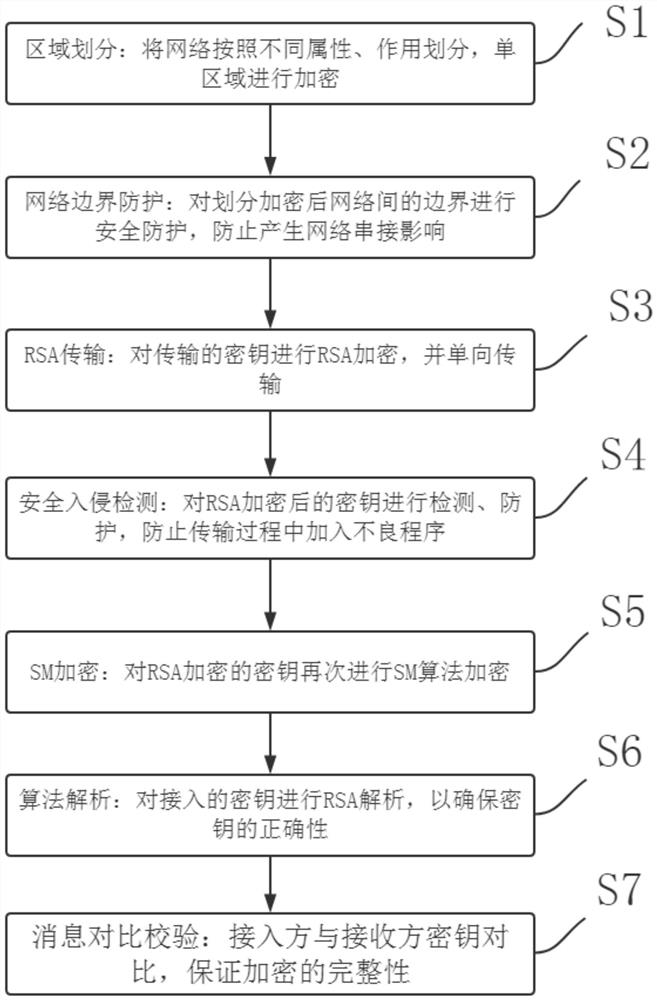
Encryption method for network security
The invention provides a network security encryption method, and relates to the technical field of network security. The method comprises the following steps: S1, region division: dividing a network according to different attributes and effects, and encrypting a single region, and S2, network boundary protection: performing security protection on boundaries among the divided and encrypted networks to prevent the influence of network concatenation. According to the method, large environment of the whole network is regionally divided into different small environments, the boundary of each small environment is protected, on one hand, the encryption degree can be improved, on the other hand, encryption access can be finely divided, encryption is carried out according to different levels, and the encryption is more meticulous; and through RSA and SM encryption, it can be ensured that the internal key is safer and is not prone to being cracked and infected by common programs. Therefore, it can be guaranteed that the secret key is in a relatively safe environment state in the transmission process, and after the secret key is received, the secret key is cracked and compared through corresponding hardware and software so that the safety of the file can be guaranteed.
Owner:严聚卫
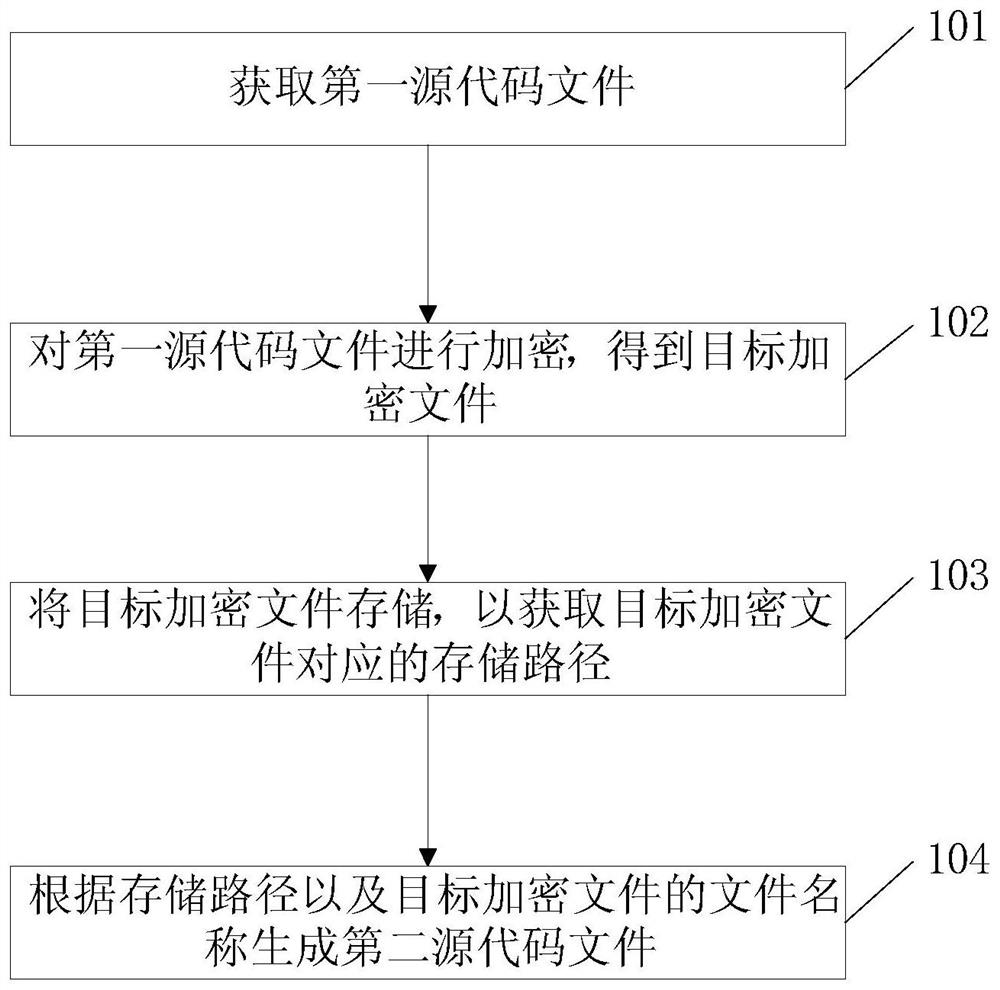
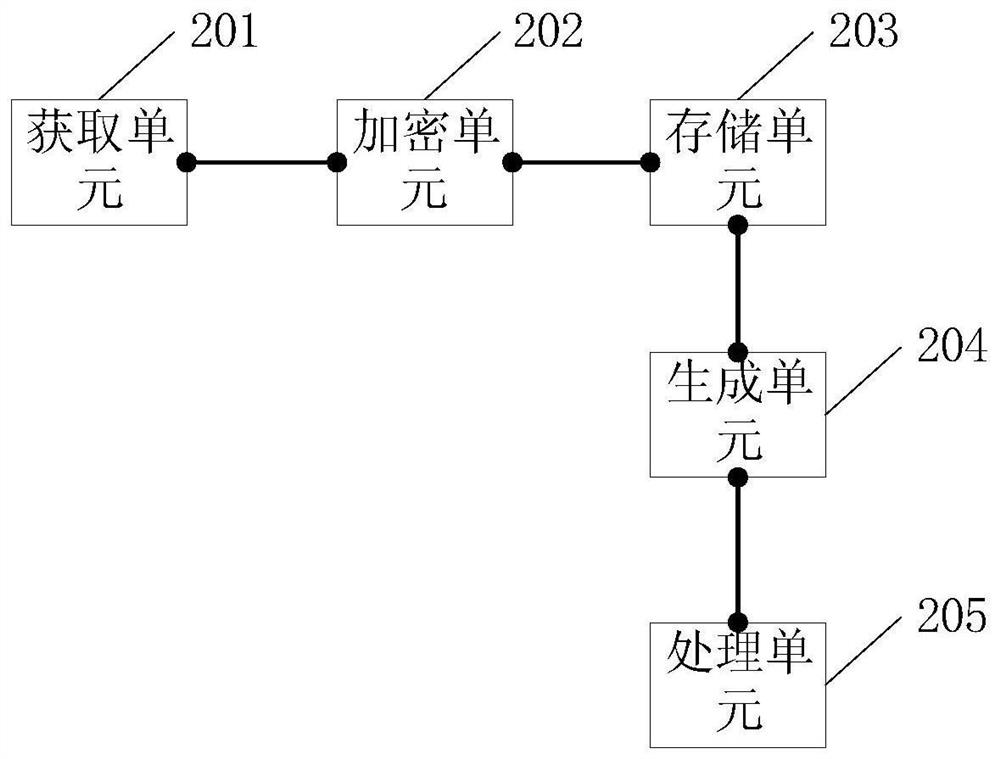
Source code file generation method and related equipment
PendingCN111625278ANot crackedWill not affect the performanceProgram documentationDigital data protectionSource code fileEngineering
The invention provides a source code file generation method and related equipment, and aims to improve the encryption degree of a source code file and protect the source code file from being decrypted. The method comprises the steps of obtaining a first source code file; encrypting the first source code file to obtain a target encrypted file; storing the target encrypted file to obtain a storage path corresponding to the target encrypted file; and generating a second source code file according to the storage path and the file name of the target encrypted file.
Owner:SHENZHEN YUNZHIJIA NETWORK CO LTD
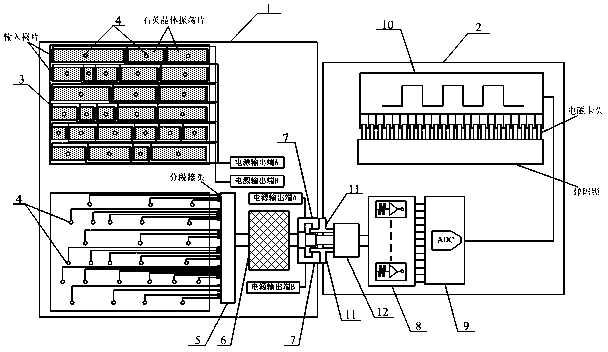
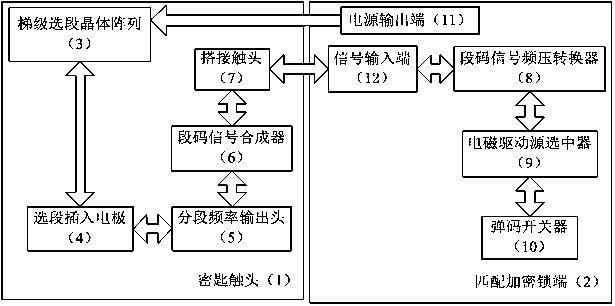
Frequency electromagnetic lockset
InactiveCN110580753AAvoid repetitionHigh degree of encryptionIndividual entry/exit registersElectronic accessVoltage converter
The invention discloses a frequency electromagnetic lockset comprising a key contact and a matched encryption lock end. The key contact includes a stepped segment selection crystal array, selected insertion electrodes, a segmented frequency output head, a segment code signal synthesizer and a lap joint contact. The matched encryption lock end includes a segment code signal frequency-to-voltage converter, an electromagnetic driving source selector and an elastic code switch. The selected insertion electrodes are inserted into different position segments of the stepped segment selection crystalarray; the segment frequency output head is connected to the selected insertion electrodes by a segmented joint; and a signal output terminal of the segmented frequency output head is connected to thesegment code signal synthesizer. The key contact is connected to a power output terminal and a signal input terminal of the matched encryption lock end through a lap joint; a signal input terminal isconnected to the segment code signal frequency-to-voltage converter; the segment code signal frequency-to-voltage converter is connected to the electromagnetic driving source selector; the electromagnetic driving source selector is connected to the elastic code switch by an electromagnetic head. The frequency electromagnetic lockset has advantages of high safety and low energy consumption; and repeatability of a mechanical lock and insecurity of the electronic access control lock are overcome.
Owner:HANGZHOU ZHIHUI TECH CO LTD
Multi-anti-counterfeiting method and multi-anti-counterfeiting element based on structural color
PendingCN114834172AHigh resolutionStrong color fastnessDuplicating/marking methodsPattern printingEngineeringStructural coloration
The invention discloses a multi-anti-counterfeiting method and a multi-anti-counterfeiting element based on structural colors. The anti-counterfeiting method comprises the steps that a photonic crystal layer is formed on the surface of an object to be subjected to anti-counterfeiting, the photonic crystal layer at least comprises a first preset pattern and a second preset pattern which are invisible under visible light irradiation, and the first preset pattern serves as a first anti-counterfeiting mark and is composed of a first photonic crystal displaying a first reflection wavelength; the second preset pattern is composed of a second photonic crystal displaying a second reflection wavelength, the second preset pattern and the first preset pattern are complementary to each other and jointly serve as a second anti-counterfeiting mark, and the first reflection wavelength and the second reflection wavelength are different from each other; external stimulation is applied to the photonic crystal layer so that the first preset pattern and the second preset pattern can be sequentially converted into a visible state from an invisible state, the first anti-counterfeiting mark and the second anti-counterfeiting mark can be sequentially displayed, and complete encrypted information can be read after integration. According to the invention, multiple anti-counterfeiting is realized, the imitation difficulty is increased, and the encryption degree is improved.
Owner:ZHEJIANG SCI-TECH UNIV
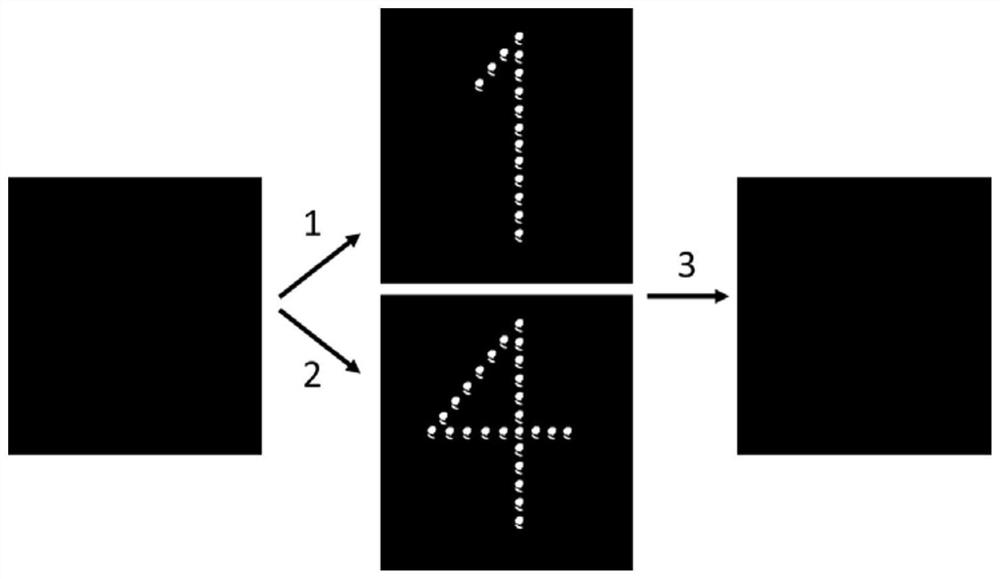
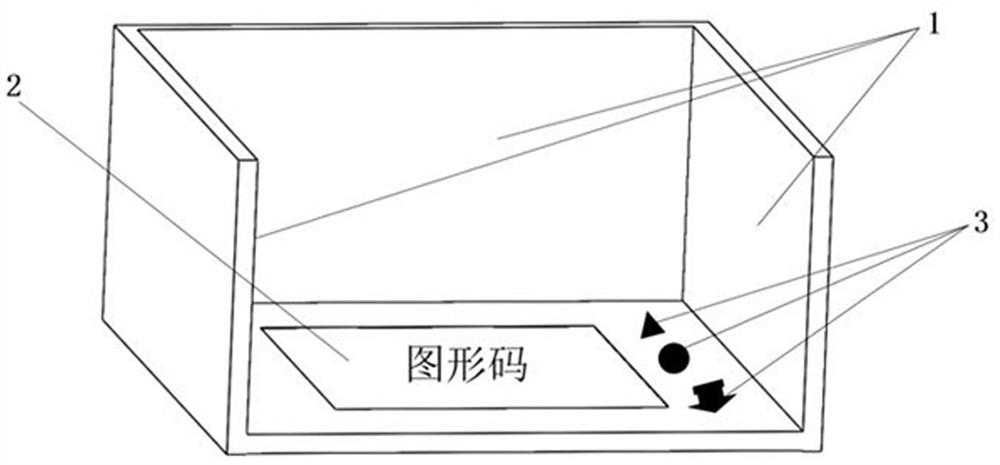
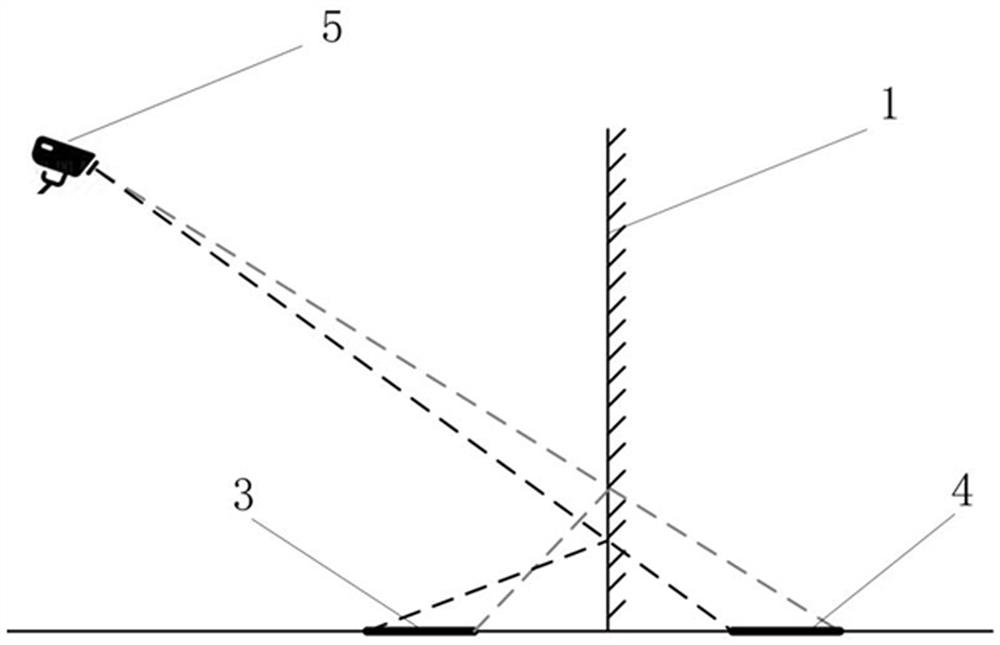
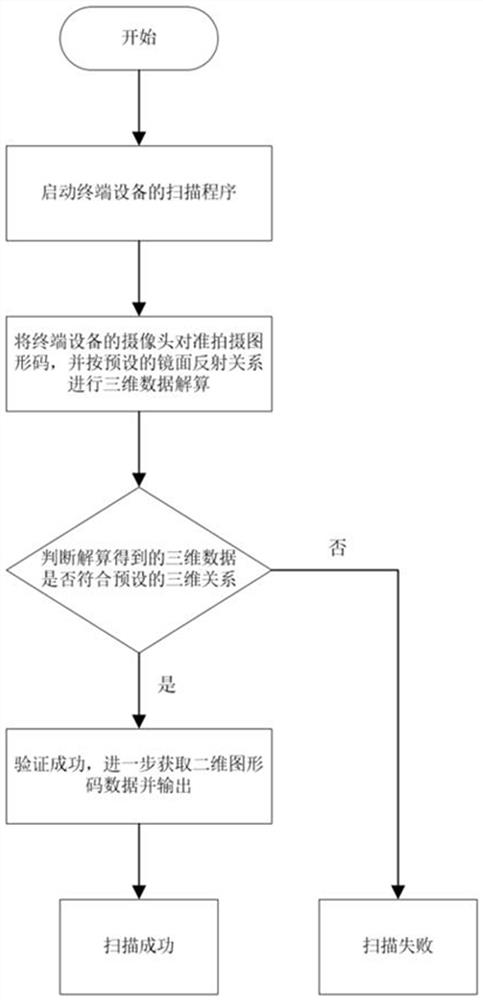
Graphic code structure with mirror surface and scanning method thereof
PendingCN112395898AEnsure safetyUniqueness guaranteedSensing by electromagnetic radiationAlgorithmMirror reflection
The invention discloses a graphic code structure with a mirror surface. The structure comprises a two-dimensional graphic code pattern, an auxiliary verification pattern and at least one mirror surface, the two-dimensional graphic code pattern and the auxiliary verification pattern are formed on the same plane, and the two-dimensional graphic code pattern provides data information which can be shot and analyzed by terminal equipment; the auxiliary verification pattern is used for providing decryption features for the two-dimensional graphic code pattern; and the mirror surface is connected with the plane forming the two-dimensional graphic code pattern and forms an angle with the plane, so that clear mirror surface mapping can be realized. The invention also provides a method for scanningthe graphic code structure, which comprises the following steps of: shooting the graphic code structure by using terminal equipment so as to obtain spatial relationship data of the auxiliary verification pattern and the pattern printed on the plane in mirror reflection, judging whether the spatial relationship is consistent with a preset value or not, and if so, indicating that the verification succeeds, and further extracting data information of the two-dimensional graphic code to finish scanning. Three-dimensional space information is added to the two-dimensional graphic code, the anti-counterfeiting effects of difficult copying, effective identification and on-site code scanning are achieved, and compared with an existing three-dimensional graphic code structure, the method has the advantages of being easy and convenient to operate and easy to popularize.
Owner:江苏楠睿科技有限公司
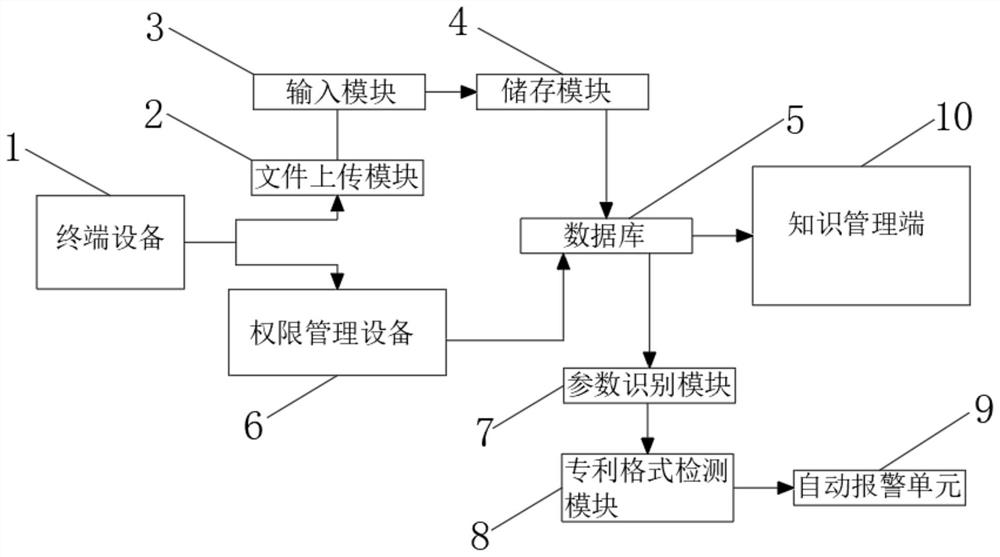
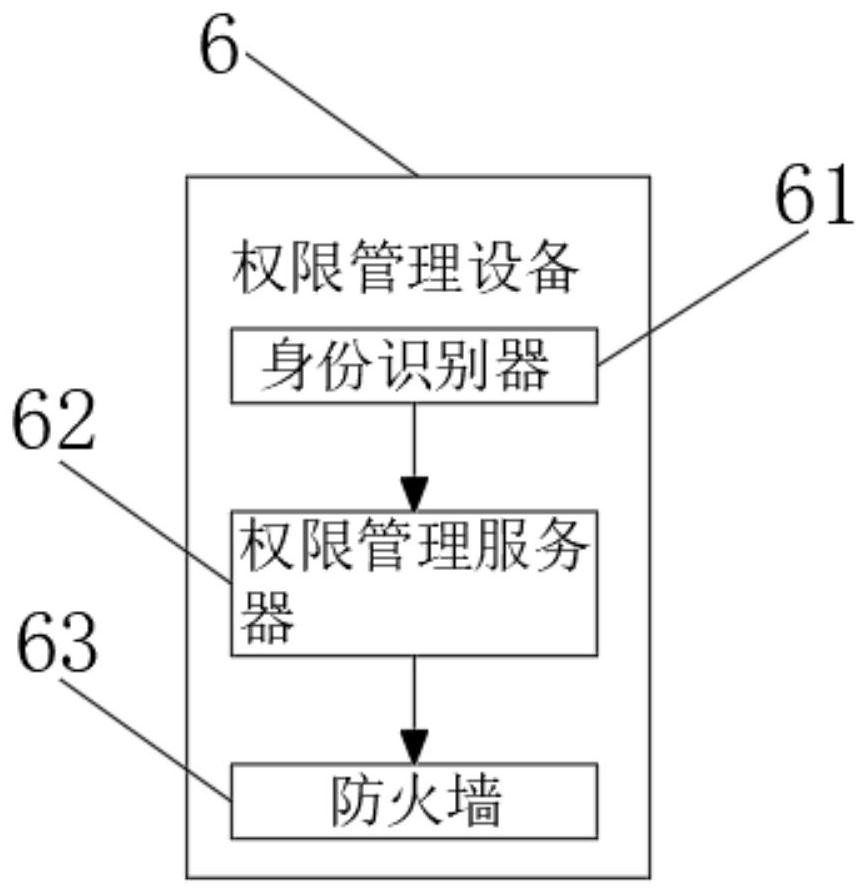
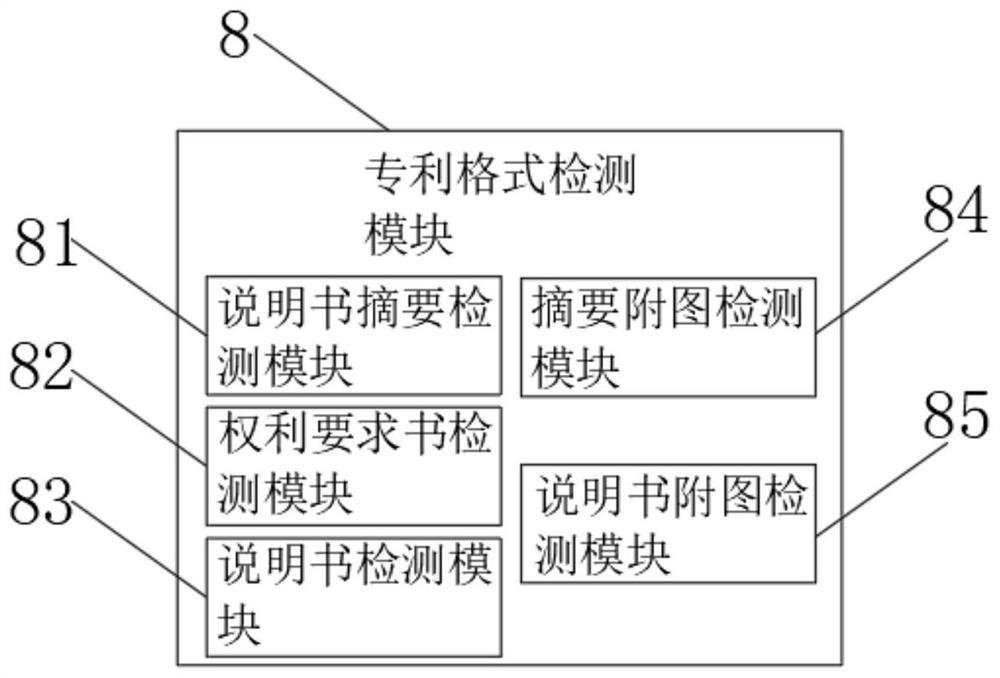
Enterprise intellectual property patent submission and incoming text intelligent management system
InactiveCN112150325AHigh degree of encryptionNot easy to attackData processing applicationsDatabase management systemsData fileEngineering
The invention relates to the technical field of intelligent management, and discloses an enterprise intellectual property patent submission and incoming text intelligent management system, and the comprises terminal equipment and a database; the output end of the terminal equipment is connected with a file uploading module and authority management equipment, and the file uploading module is used for uploading and processing intellectual property data; the authority management device is used for managing various authorities of the intelligent management system, the other end of the file uploading module is arranged at the input end of the database, and the database is used for storing uploaded intellectual property data files. According to the enterprise intellectual property patent submission and incoming text intelligent management system, it is guaranteed that when intellectual properties are accessed, authority management setting is high in encryption degree and not prone to being attacked, the situation that confidential intellectual property files are stolen is eradicated, the information safety performance is improved, an intellectual property detection module is arranged instorage equipment, and the expired intellectual properties or intellectual properties with unqualified formats can be removed conveniently.
Owner:江苏云标科技有限公司
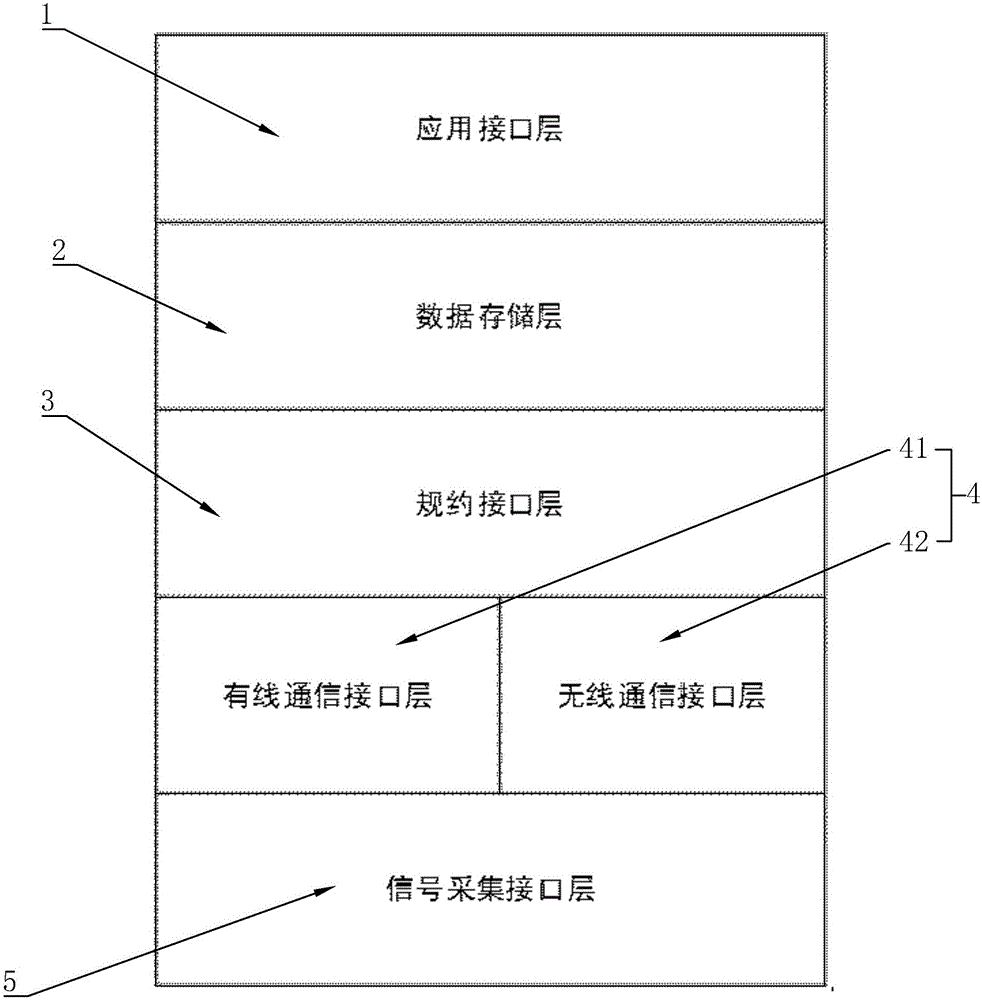
Communication method based on Ad-Hoc network wireless communication
InactiveCN106532943AHigh degree of encryptionCircuit arrangementsInformation technology support systemWired communicationComputer module
The invention discloses a communication method based on Ad-Hoc network wireless communication. The method comprises the steps that 1 an application interface layer is set in a distribution master station system; 2 a signal acquisition interface layer is connected with a signal acquisition module; 3 the signal acquisition module in step 2 is used to acquire a secondary device signal of a power grid, and then the acquired secondary device signal is transmitted to a wired communication interface layer in a wired manner; and 4 a master station private key is preloaded in a data storage layer. According to the communication method based on Ad-Hoc network wireless communication, the application interface layer is effectively set in the step 1 to receive the signal; the signal can be effectively acquired in the step 2; the signal is effectively encrypted and transmitted in the step 3; and the received encrypted signal is effectively decrypted and transmitted to the application interface layer in the step 4.
Owner:WENZHOU ELECTRIC POWER BUREAU +2
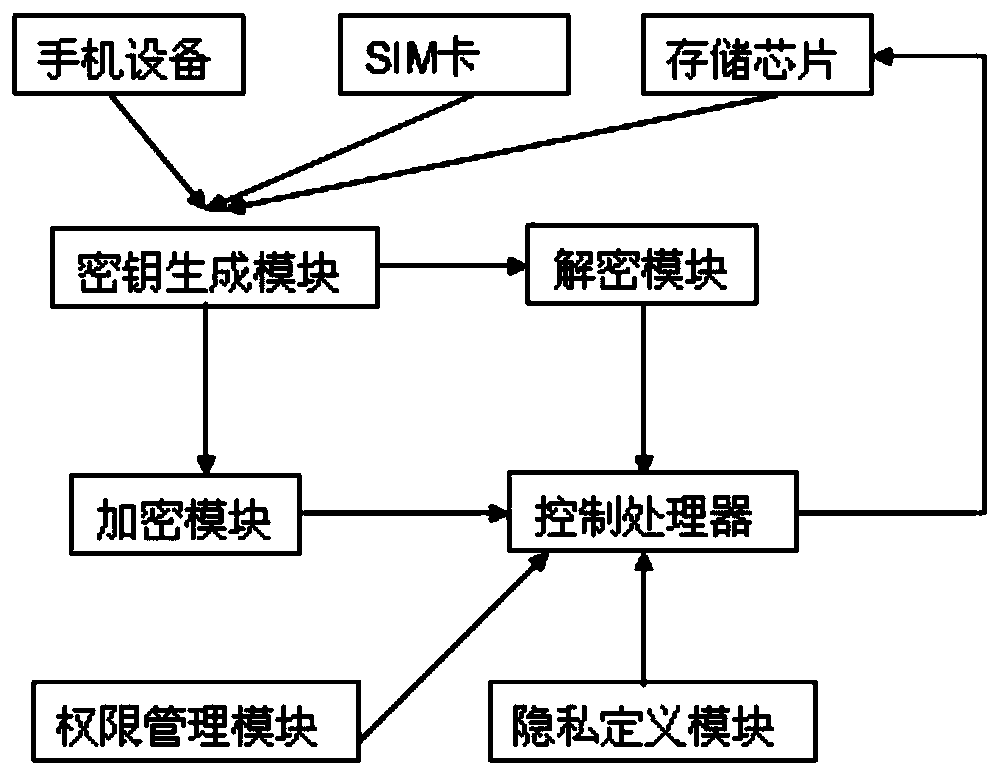
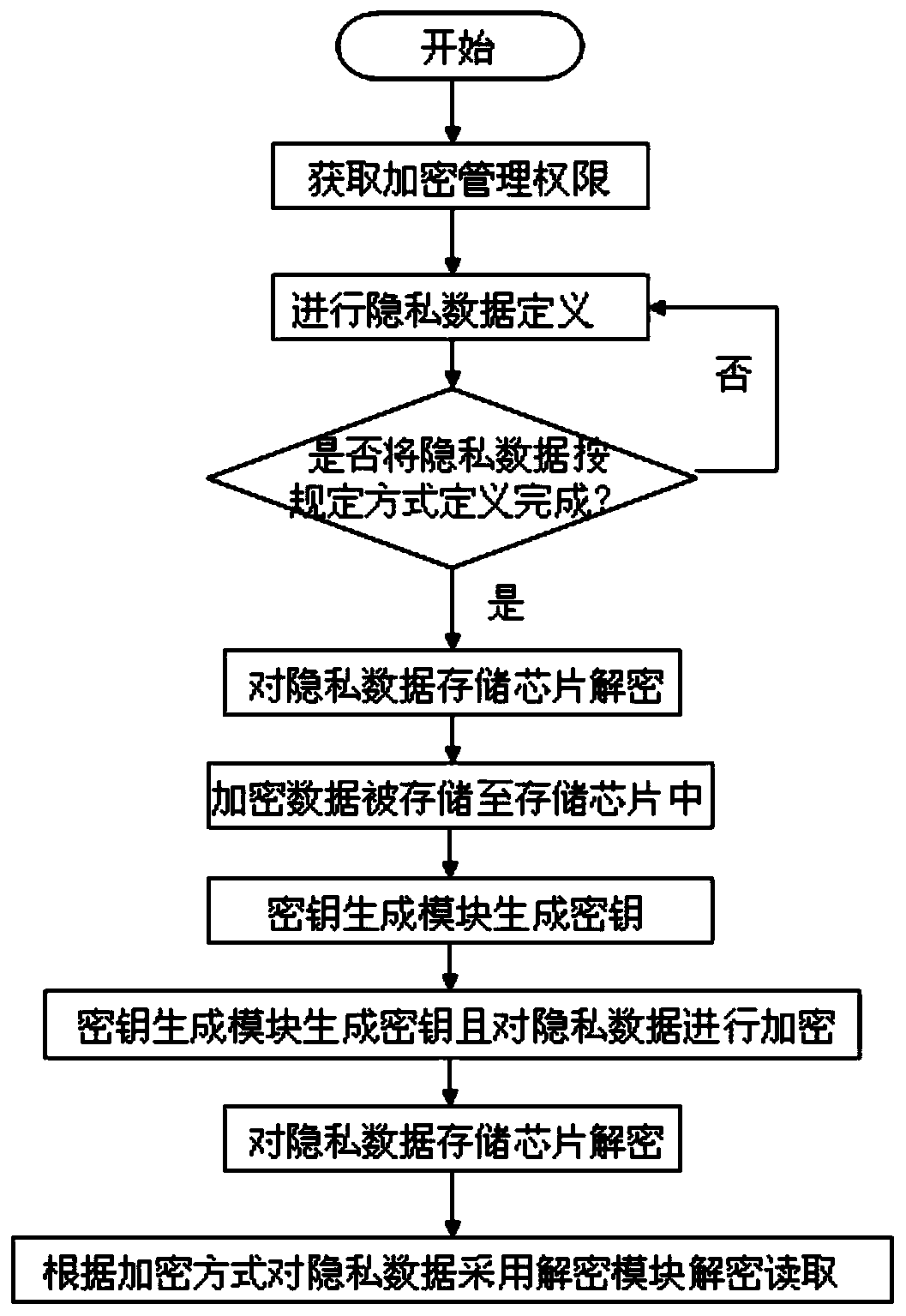
Encryption and decryption system and encryption and decryption method for mobile phone privacy data
InactiveCN106375990BDoes not take up resourcesImplement double encryptionSubstation equipmentSecurity arrangementInternet privacyUnique identifier
The invention relates to an encryption and decryption system and encryption and decryption method for private data of a mobile phone. Operation authority of private data of a mobile phone is set. A private data definition module is arranged and is used for carry out encryption level definition on the private data of the mobile phone according to the type of the private data as well as an encryption level needed by a user; the private data are stored into a specific private data storage chip; a secret key generation module is used for obtaining a unique identifier ID of the mobile phone, an IEMI number of an SIM card, an SN number of the storage chip of an encrypted data storage module and a first character or last character of a file title of the encrypted data and generating a matrix secret key to carry out encryption and decryption on the private data of the mobile phone. Therefore, the private data of the mobile phone can be encrypted or decrypted rapidly, safely, and stably.
Owner:上海统宁科技发展有限公司
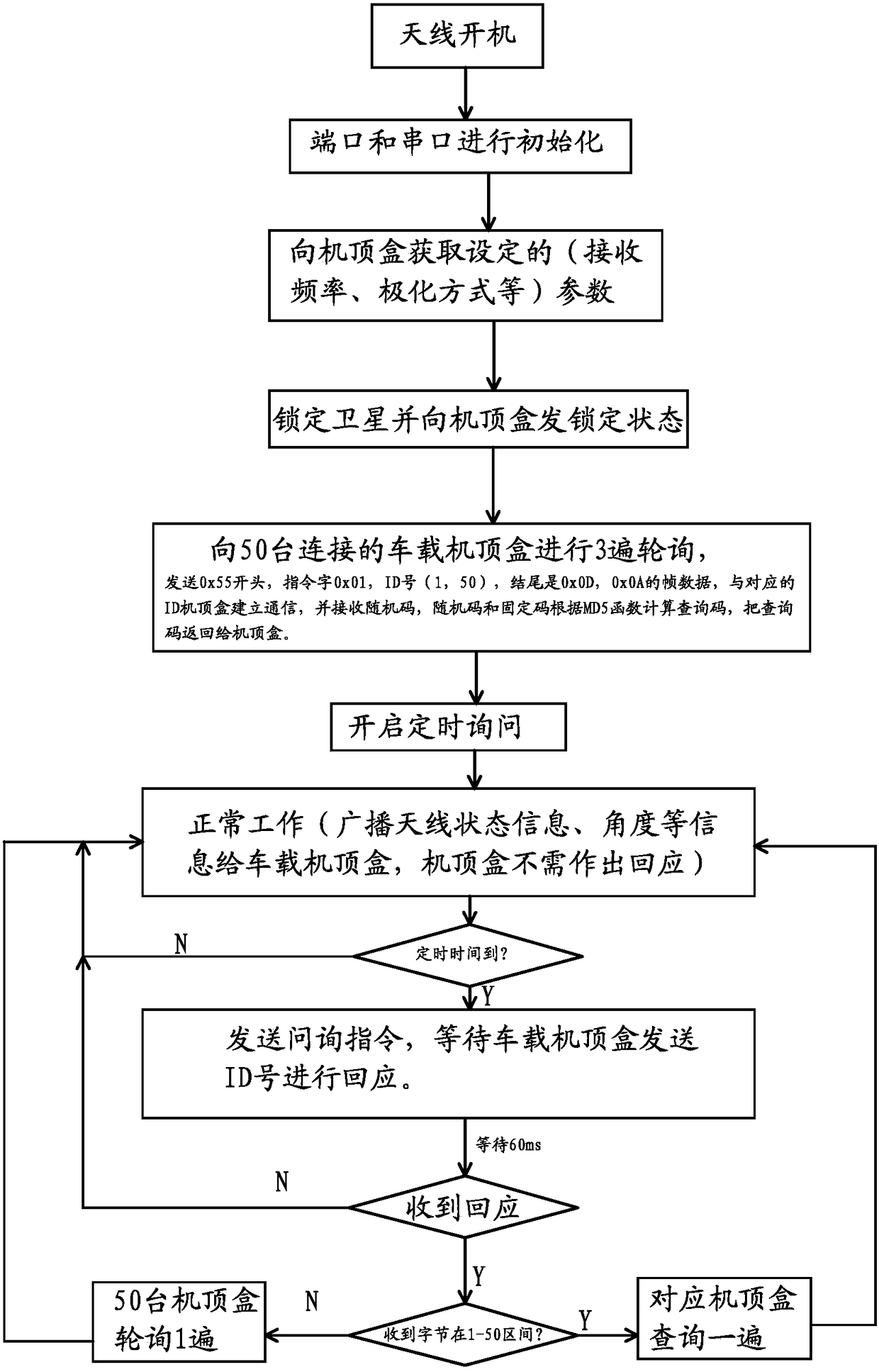
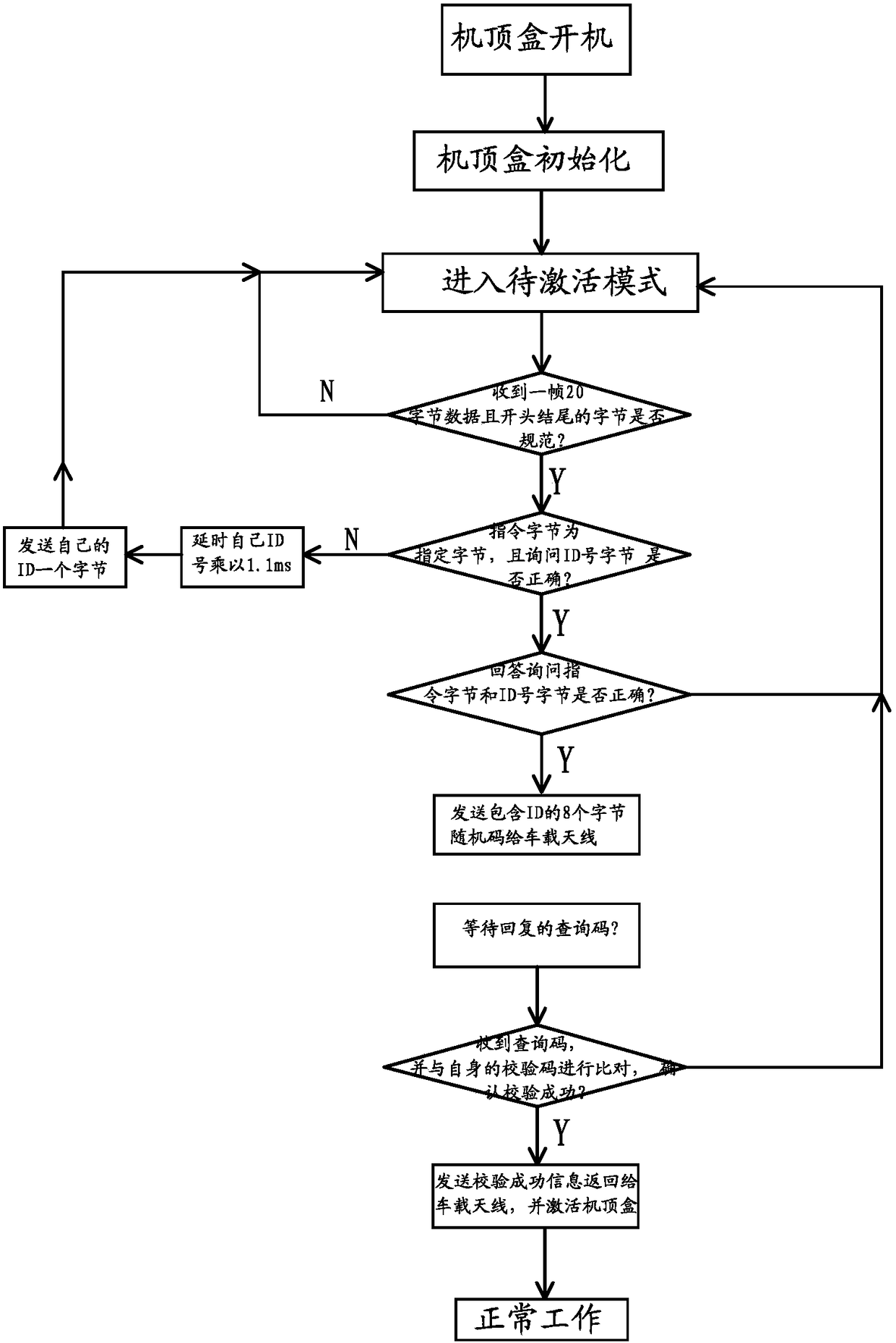
A communication encryption method between vehicle antenna and set-top box
ActiveCN105827396BIncreased encryption cracking difficultyRandomEncryption apparatus with shift registers/memoriesHigh intensitySet top box
The invention provides a vehicle-mounted antenna and a set top box communication encryption method, belongs to the communication encryption technology field and solves a problem that communication between a vehicle-mounted set top box and the vehicle-mounted antenna can be easily copied and monitored. The method comprises steps that A, a same set of plain text segments is commonly taken by the antenna and the set top box as a fixed code on the basis of mutual agreement; B, a random code containing a self ID number is sent and read by the set top box to the vehicle-mounted antenna, the random code and the fixed code are received by the vehicle-mounted antenna and are combined to form a corresponding plain text, a query code is calculated, and the query code acquired through calculation is returned to the set top box; C, according to the random code and the fixed code, the set top box carries out calculation and combination in the same mode to form a corresponding plain text, and a check code is calculated; and D, the query code is compared with the check code, if the two are completely identical, the set top box is activated and starts normal operation, if not, waiting continues. Through high-intensity encryption behaviors of the set top box and the antenna, communication can not be copied or monitored, and the set top box can be effectively prevented from being illegally used for other purposes.
Owner:ZHEJIANG CHINASTAR ELECTRONICS SCI & TECH
Multi-stage magnetic control mechanism of mechanical lock
PendingCN111779365APrevent unlockingAvoid Illegal Opening SituationsArtificial islandsNon-mechanical controlsControl switchControl theory
The invention discloses a multi-stage magnetic control mechanism of a mechanical lock. The multi-stage magnetic control mechanism of the mechanical lock is characterized by comprising a lock cylinderbody, wherein the lock cylinder body comprises a lock hole arranged in a cylindrical structure and a rotating groove for embedding a key and communicating with the lock hole, a plurality of magnetic control switches are arranged in the lock cylinder body in the depth direction of the lock hole and are arranged in different radial directions of the lock hole, an encryption included angle is arranged between the connected magnetic control switches, when the magnetic control switches and magnets in a key are in same-pole correspondence, the magnetic control switches are in an unlocking state, a reset part for resetting the magnetic control switches is arranged in the lock cylinder body, the reset part resets the magnetic control switches one by one when the key leaves the lock cylinder body,the lower end face of the lock cylinder body is connected with a lock bolt, the lock bolt is arranged at a position far away from the lock hole, and the lock bolt is opened in the rotating process ofthe lock cylinder body. The multi-stage magnetic control mechanism of the mechanical lock has the advantages of multi-stage encryption and high encryption degree and is not easily pried.
Owner:ZHEJIANG MAKEPOWER ELECTRONICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com