Encryption method for network security
An encryption method and network security technology, applied in the encryption field of network security, can solve problems such as uneven security, high cost, troublesome deployment, etc., and achieve key security, ensure security, and improve encryption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
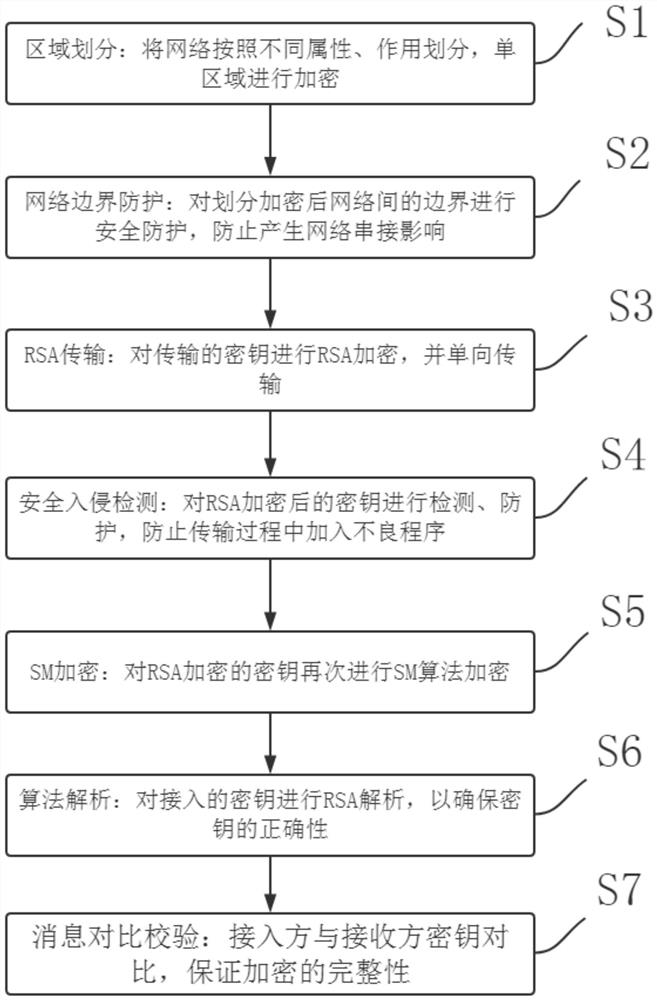
[0025] see figure 1 , the present invention provides a kind of technical scheme: a kind of encryption method of network security, comprises the following steps:
[0026] Step 1. Regional division: divide the network according to different attributes and functions, and encrypt a single area.
[0027] Step 2. Network boundary protection: Security protection is carried out on the boundary between divided and encrypted networks to prevent the impact of network connection.
[0028] Step 3, RSA transmission: perform RSA encryption on the transmitted key and transmit it in one direction.
[0029] Step 4: Security intrusion detection: detect and protect the RSA encrypted key to prevent bad programs from being added during transmission.
[0030] Step 5, SM encryption: Encrypt the RSA encrypted key with the SM algorithm again.
[0031] Step 6. Algorithm analysis: Perform RSA analysis on the accessed key to ensure the correctness of the key.
[0032] Step 7. Message comparison and ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com