Encryption and decryption system and encryption and decryption method for mobile phone privacy data
A privacy data, mobile phone encryption technology, applied in the field of mobile communication and information security, can solve the problems of low software performance, performance problems, slow decryption reading speed, etc., to achieve simple encryption keys, high encryption degree, and improved performance. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0025] A method for encrypting and decrypting mobile phone privacy data, comprising the following steps:
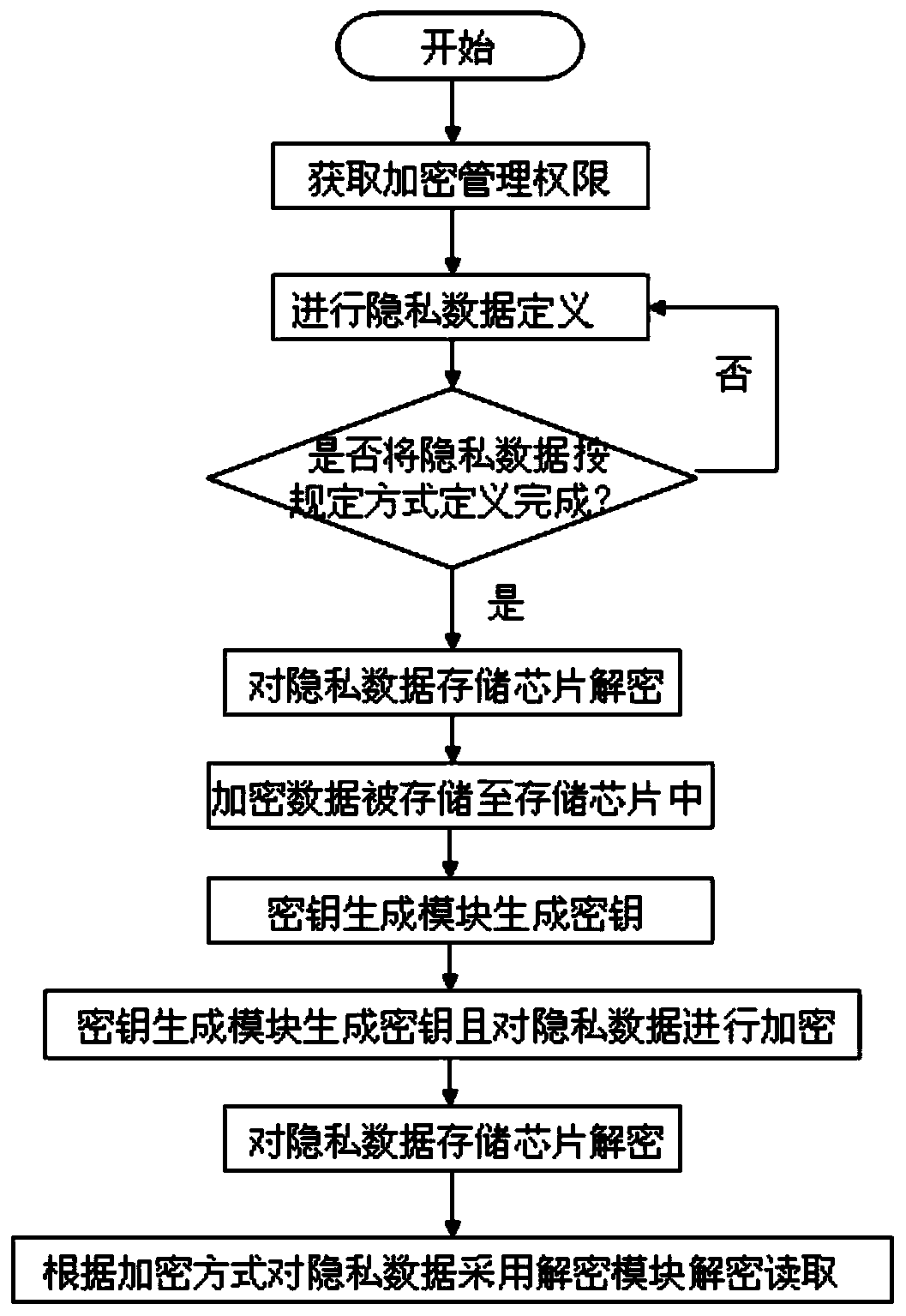
[0026] First, obtain the encryption management authority to encrypt the mobile phone privacy data through the authority management module, and only after obtaining the authority can you operate and manage the encrypted and encrypted private data on the mobile phone;
[0027] Secondly, through the privacy data definition module, the encryption level definition of the privacy data of the mobile phone that needs to be encrypted is defined as low-level encryption, medium-level encryption or high-level encryption. After encryption definition, the privacy data is stored in the encrypted data storage module. automatically stored in the memory chip of the encrypted data storage module of the mobile phone under the program call of the control processor;
[0028] Once again, the control processor of the encrypted data storage module obtains the unique identification ID of the smart...
Embodiment 2
[0034] This embodiment is similar to the encryption method of embodiment 1, the difference is that in this embodiment, before the privacy data is stored in the memory chip process of the mobile phone encrypted data storage module, it is also necessary to encrypt the encrypted data memory of the mobile phone The step of decrypting the storage chip. Specifically, after the privacy data of the mobile phone is defined by the user, the privacy definition module feeds back the information to the control processor of the encrypted data storage module. Read and write password input window, after the user correctly enters the password of the storage chip, the private data will be automatically stored in the storage chip of the mobile phone encrypted data storage module under the program call of the control processor of the encryption module. The password of the window-type storage chip is a combination of numbers and / or letters set by the user; in addition, before the private data is de...
Embodiment 3
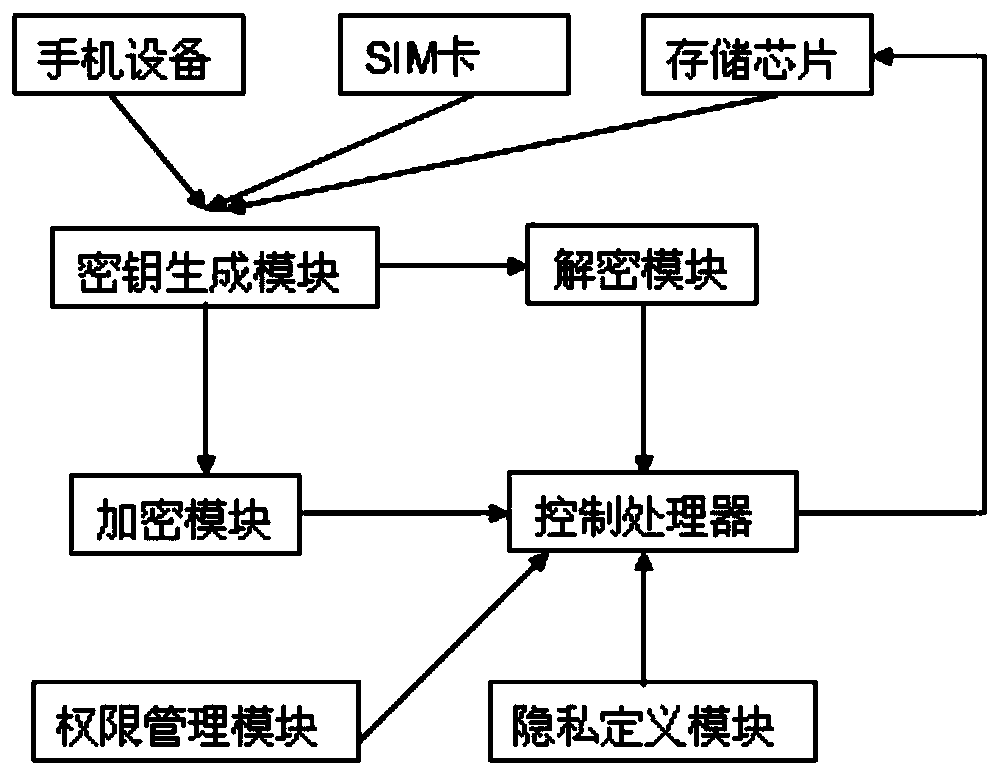
[0037] This embodiment relates to a system for the mobile phone privacy data encryption and decryption method of Embodiment 2, the system includes a smart phone device, an encrypted data storage module, a key generation module, an encryption module and a decryption module, and also includes a rights management module and Privacy data definition module, the authority management module is used to allocate authority for the encryption, decryption and read and write operations of mobile phone privacy data, and the privacy data definition module is used to pass the user with authority according to the type of privacy data and the required encryption level Define the encryption level, the encrypted data storage module includes a storage chip and a control processor, the storage chip is used to store the privacy data of the mobile phone, and the control processor is used to store the privacy data defined by the privacy definition module, Encryption and decryption, the control processo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com