Cloud computing unified identity authentication method based on SAML and XACML
An identity authentication and cloud computing technology, which is applied in the field of unified identity authentication of cloud computing based on SAML and XACML, can solve the problems of repeated issuance of digital certificates, cumbersome use, repeated authentication, etc., and achieve unified identity authentication and management of access control rights Control problems, the certification process is safe and stable, and the effect of avoiding repeated issuance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
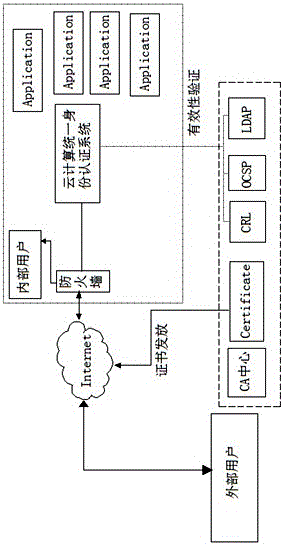
[0017] Such as figure 1 As shown, a method of cloud computing unified identity authentication based on SAML and XACML, the method defines identity provider (IP: Identity Provider) and service provider (SP: ServiceProvider) by using SAML standard to form different security domains , realize the exchange of authentication and authorization data between different security domains; and use XACML to realize the general access control policy of request / response and the framework of enforcing the authorization policy, and realize the execution of the access control policy in the cloud computing environment , so as to realize the unified identity authentication and permission access control of cloud computing.
[0018] The XACML is a general access control policy language for determining request / response and a framework for executing authorization policies, which can be widely used in the distributed environment of cloud computing, mainly for the description of security policies such ...
Embodiment 2
[0020] On the basis of Embodiment 1, the method described in this embodiment forms a standard SAML request by integrating functions such as SAML construction, parsing, signature, and encryption, and then the client sends the SAML request to the server, and then A SAML response is returned by the server.
[0021] The transmission of data is expressed in XML format conforming to the SAML specification. SAML relies on comprehensive security standards such as SSL and X.509 to protect the security of communication between the SAML source site and the target site. All communications between the source and destination sites are encrypted. And digital certificates are used to ensure that both sites participating in the SAML interaction can verify each other's identities.
Embodiment 3
[0023] On the basis of Embodiment 1 or 2, the SAML request described in this embodiment is an X.509 certificate implemented by domestic encryption technology, replacing the original international public algorithms such as RSA, by defining an XML in SAML Signature (XMLSignature) element to identify the certification center, this element contains an X.509 certificate based on a domestic cryptographic algorithm with a public key, expiration date and usage policy; the XML signature also contains the signature value itself, and the signature value is determined by Certificate authority generated for element content. The signature can be verified using the public key information of the authority in the X509 certificate. This ensures the security, validity and integrity of the information.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com