Ciphertext access control method based on CP-ABE (Ciphertext-Policy Attribute-Based Encryption)
A CP-ABE, access control technology, applied in ciphertext access control (that is, encrypting and controlling the user's decryption ability, the ciphertext access control field based on CP-ABE, can solve problems such as the inability to meet the security requirements of information sharing, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0068] In order to make the purpose of the present invention, technical solutions and advantages clearer, the following combination Figure 1-Figure 6 and specific examples to clearly and completely describe the invention.
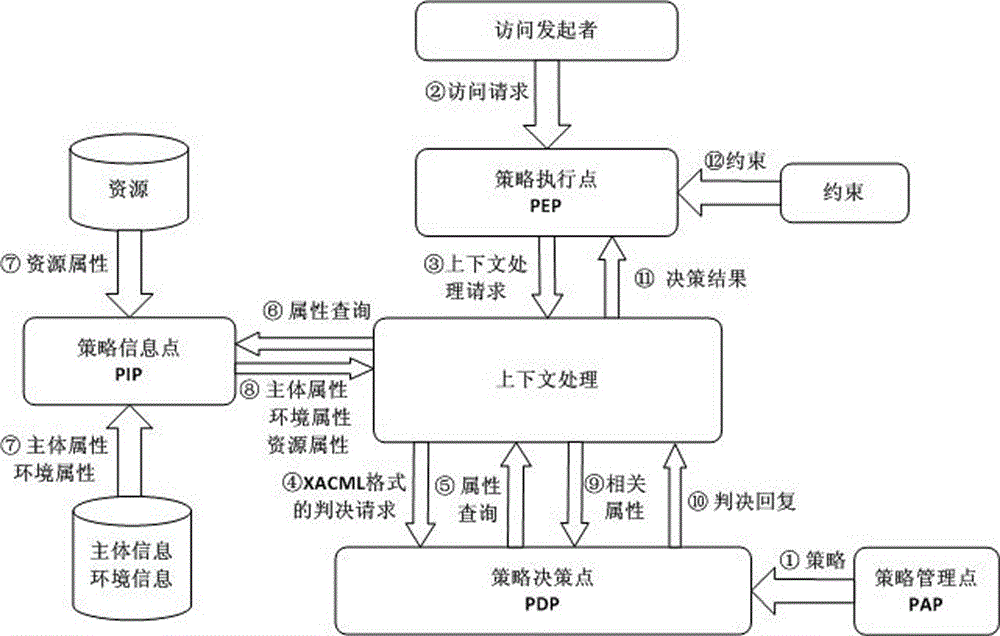
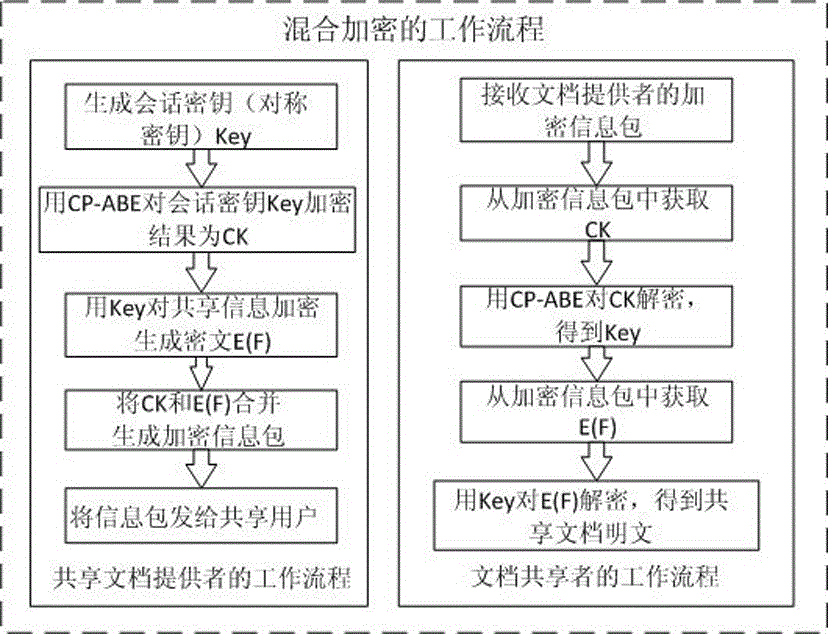
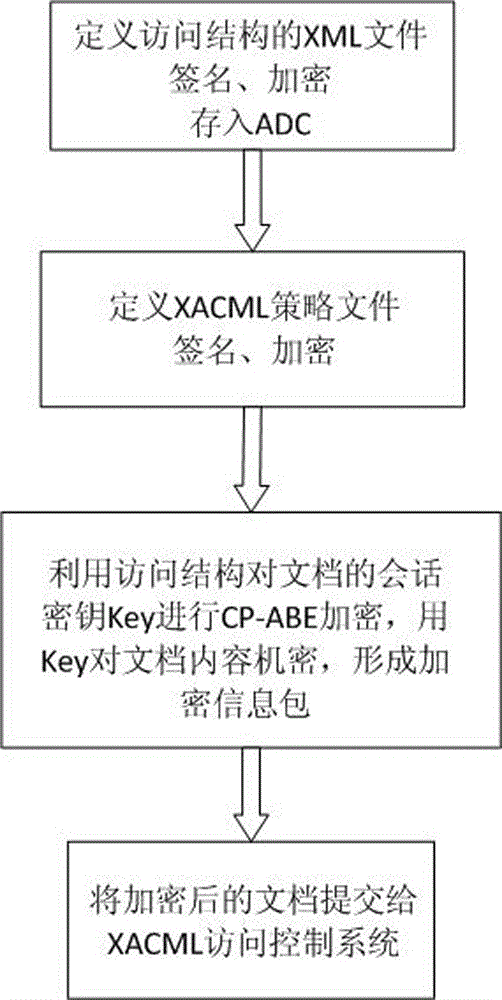
[0069] This embodiment classifies shared resources, those resources that cannot be shared with independent electronic documents, such as hardware devices, real-time information queries that do not form query result files, etc., the user's access rights are all recorded in their attribute certificates AC, access control adopts Technologies such as PMI mechanism, role-based access control model and XACML access control; and those resources that can be shared in the form of independent electronic documents use CP-ABE mechanism to achieve a sharing effect similar to broadcasting. Therefore, in our XACML access control model, its data flow model is as figure 1 As shown, add CP-ABE policies. These policies only include the operating environment conditions and p...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com