Access Control Policy Test Automatic Generation Method Based on Code Generation and Symbolic Execution
An access control strategy and symbolic execution technology, which is applied in the fields of information security cross-technology applications, software testing, and software engineering, can solve problems such as huge time overhead and XACML request redundancy, and achieve strong scalability, high degree of automation, and reduced overhead Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention will be further described below in conjunction with the accompanying drawings.
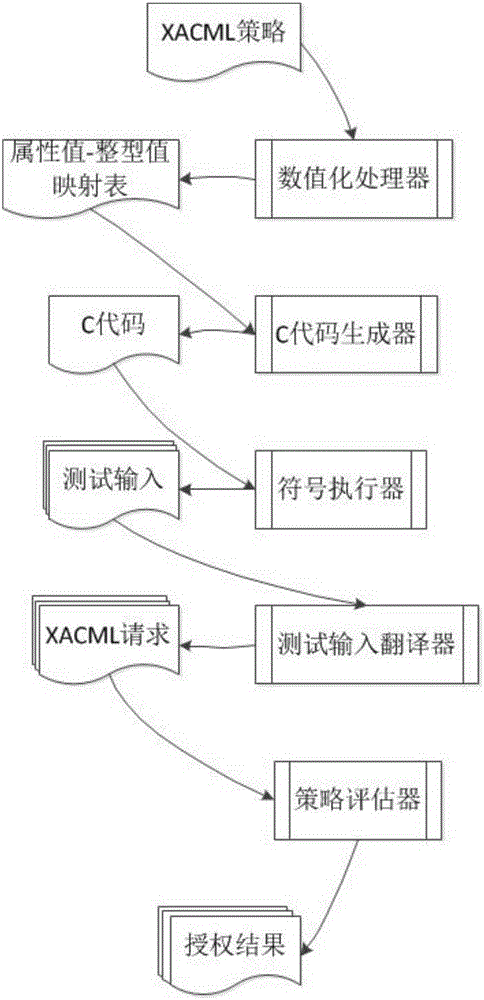
[0052] refer to figure 1 , the present invention has five functional components, namely: numerical processor, C code generator, symbol executor, test input translator and strategy evaluator. Among them, the numerical processor converts complex attribute values appearing in the XACML policy into integer values, the C code generator converts the XACML policy into semantically equivalent C code, and the symbolic executor uses the symbolic execution tool to generate the test input of the C code , the test input translator translates the obtained test input into an XACML request, and the policy evaluator evaluates the XACML request and returns a response result.
[0053] In the specific implementation, the working process and input and output of each functional component are as follows:
[0054] (1) Numerical processor
[0055] refer to figure 1 , the numerical proces...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com