XACML policy rule checking method
A detection method and rule-based technology, applied in the direction of instruments, digital data authentication, electronic digital data processing, etc., can solve problems such as constraints
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
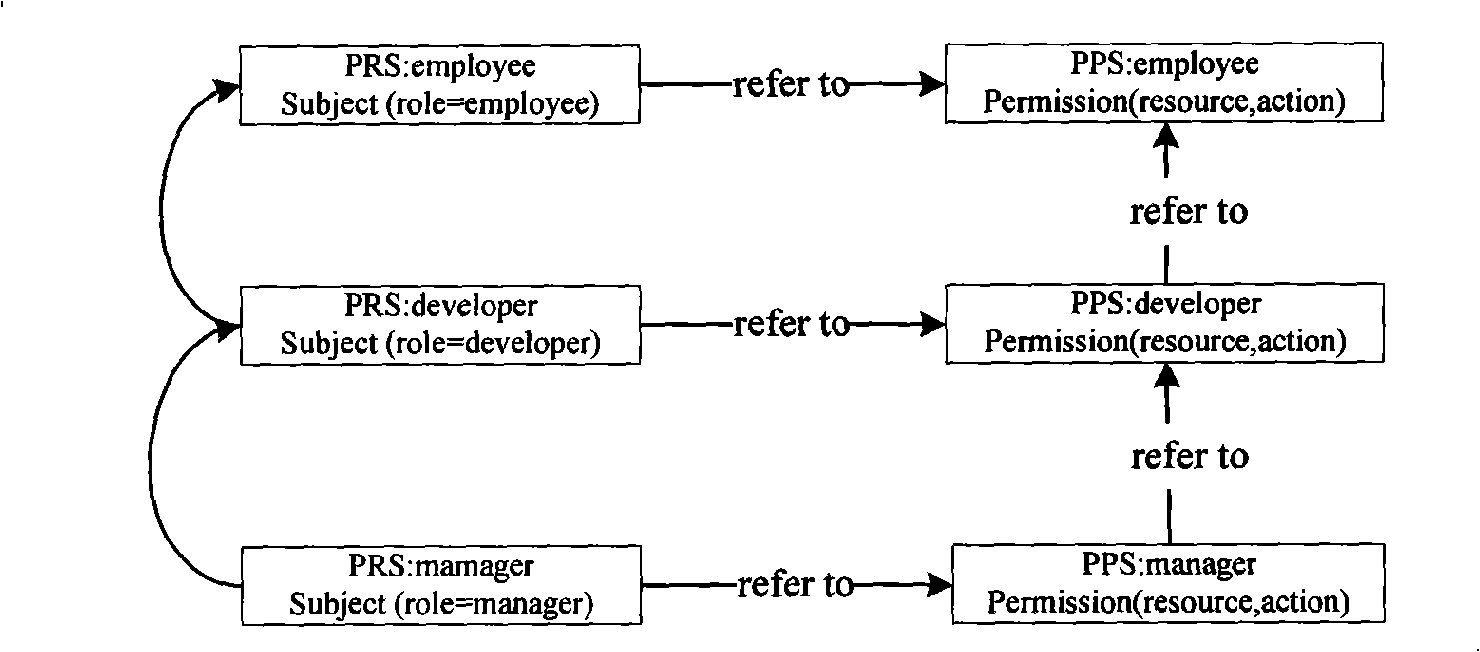
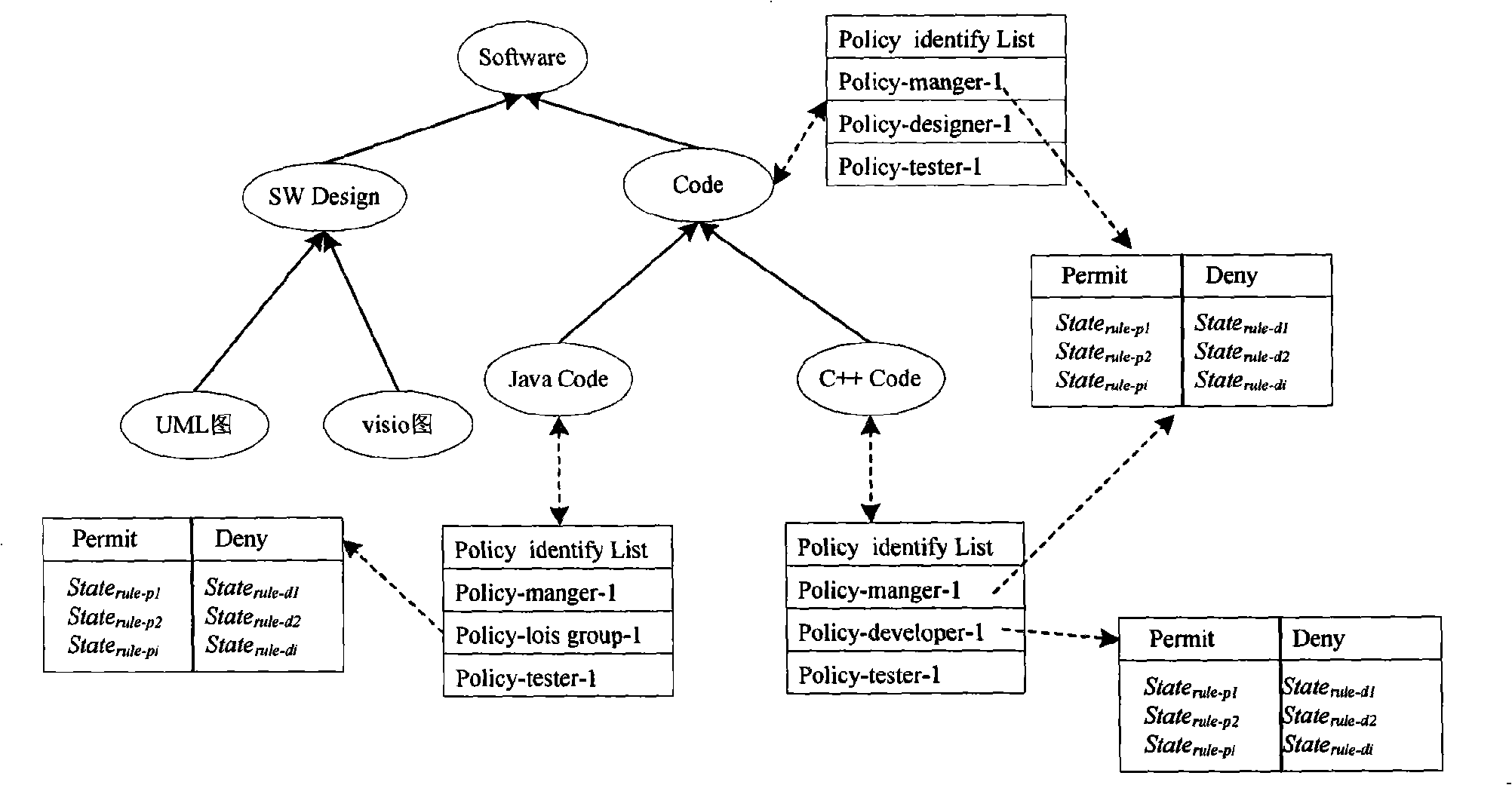
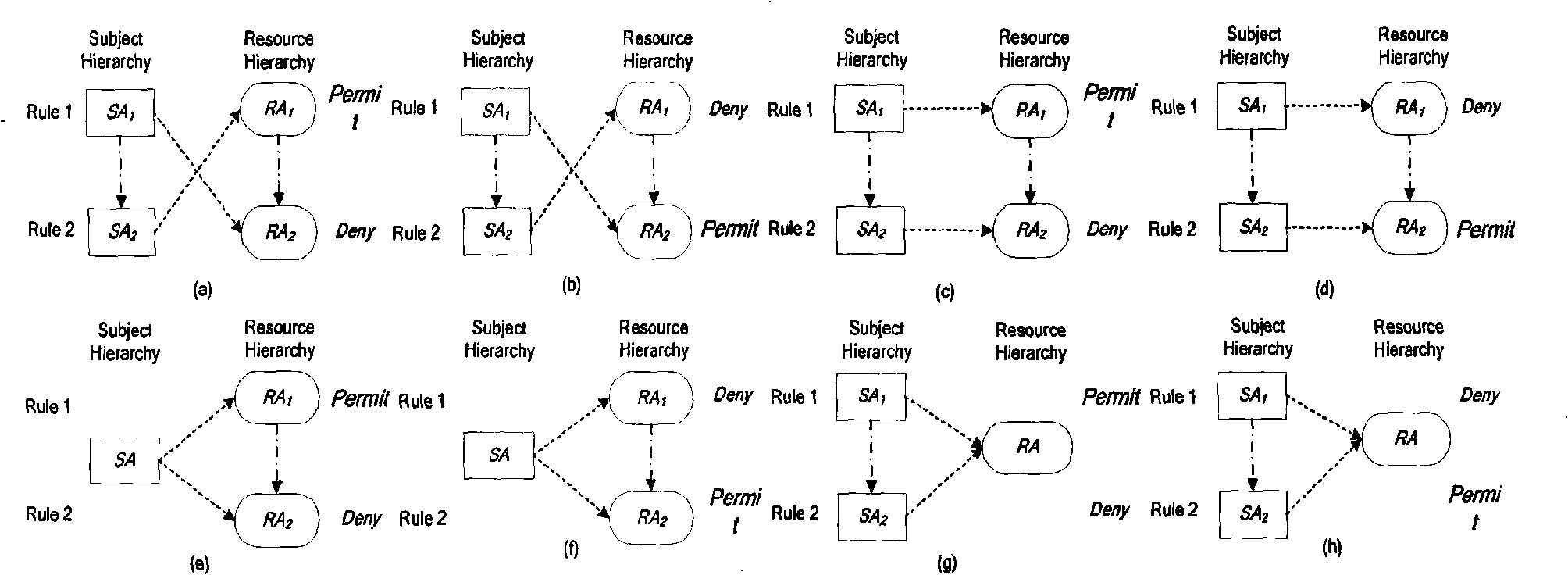
[0075] Figure 4 A conflict detection algorithm based on attribute-level operational association is described. The input of the algorithm includes the subject attribute policy pol to be detected and the permission policy list of the upper-level subject attribute that is referenced and inherited by it, and the output is a pair(rule p , rule d ) set conSet composed of. The specific process of the algorithm is as follows. For the permit type rule rule in pol p , determine the rule p Medium resource attribute resAttr p Node on the semantic tree res , to Node res Each policy pol in its own policy identification list Δ to test. Analyze pol one by one Δ The deny type rule in the rule d , if the rule p and rule d The state dependency is State rule p ↔ ( res , ac ) State ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com