Patents
Literature
265 results about "Rule checking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
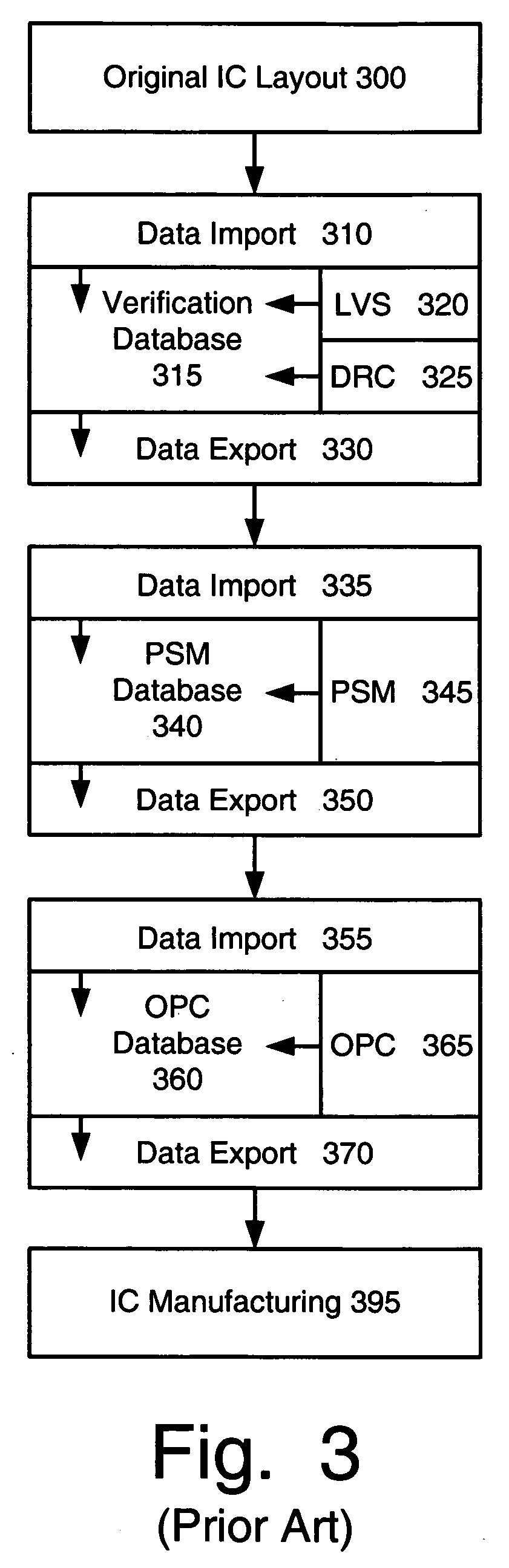
Method for comprehensively verifying design rule checking runsets
InactiveUS6732338B2Extraction of informationComputer aided designSoftware simulation/interpretation/emulationComputer architectureDesign rule checking
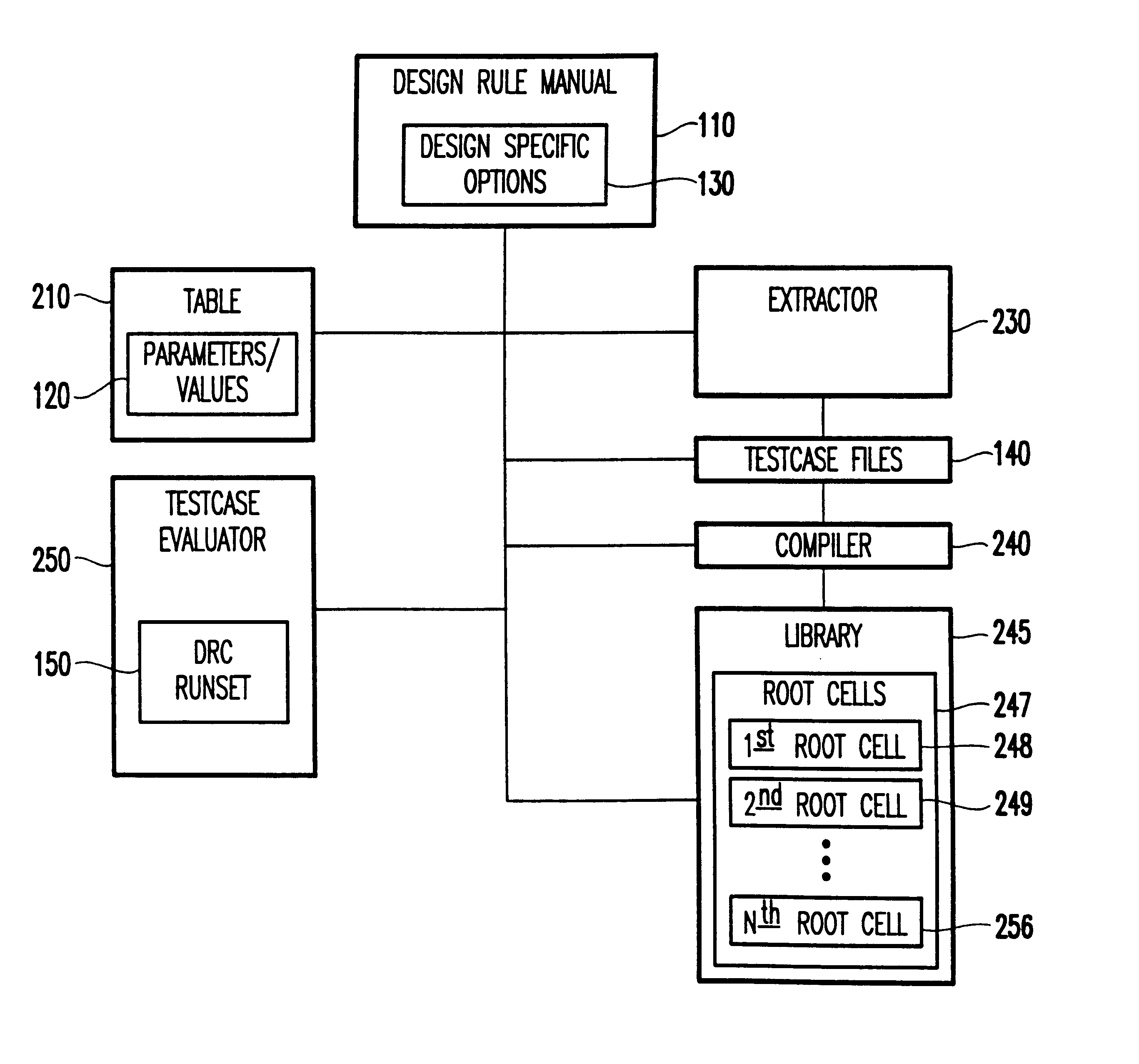
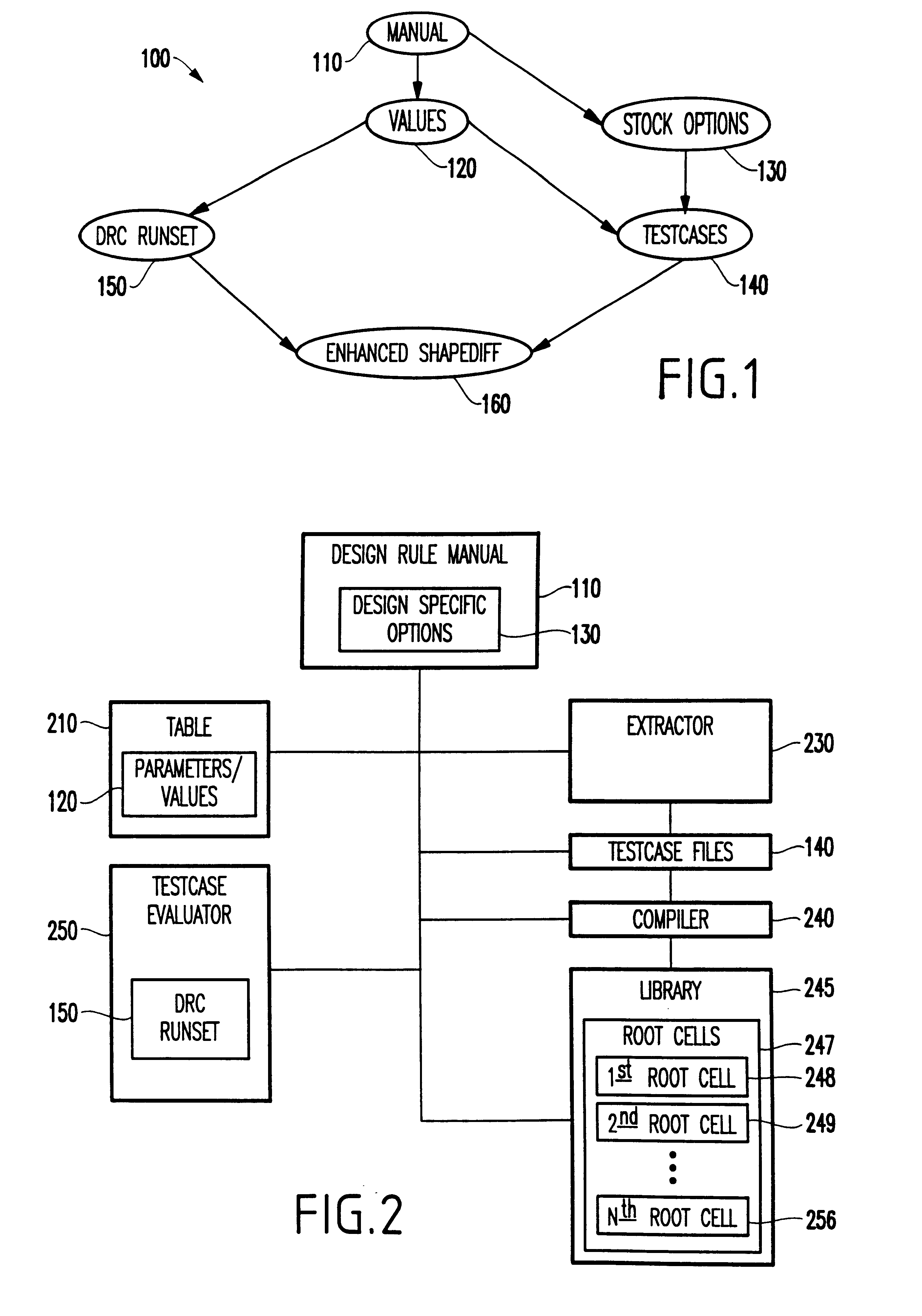
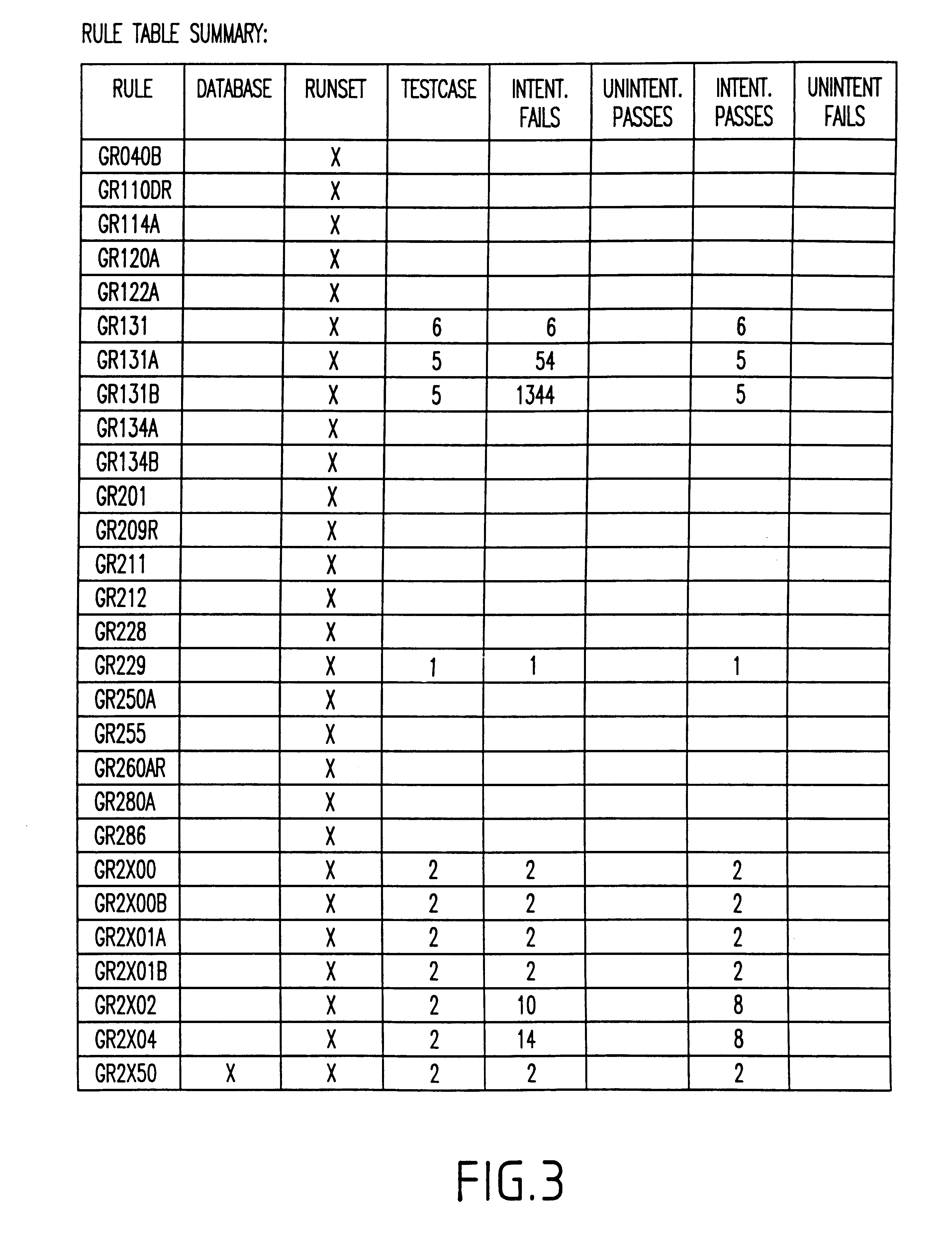
A system and method for automatically creating testcases for design rule checking comprises first creating a table with a design rule number, a description, and the values from a design rule manual. Next, any design specific options are derived that affect the flow of the design rule checking, including back end of the line stack options. Then, the design rule values and any design specific options (including back end of the line stack options) are extracted into testcases. Next, the testcases are organized such that there is one library with a plurality of root cells, further comprising one root cell for checking all rules pertaining to the front end of the line, and another root cell for checking design specific options including back end of the line stack options. Finally, the DRC runset is run against the testcases to determine if the DRC runset provides for design rule checking.
Owner:IBM CORP
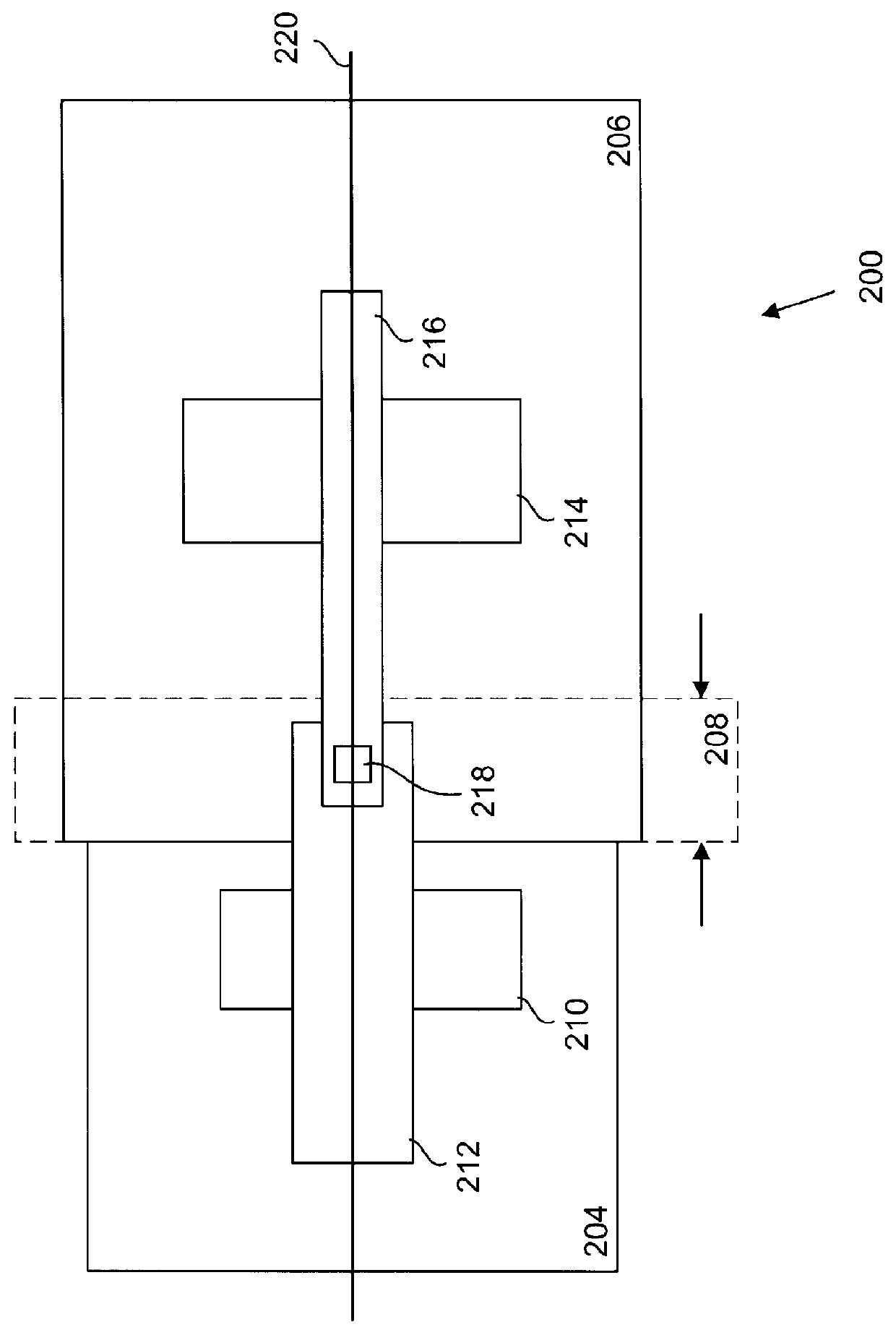
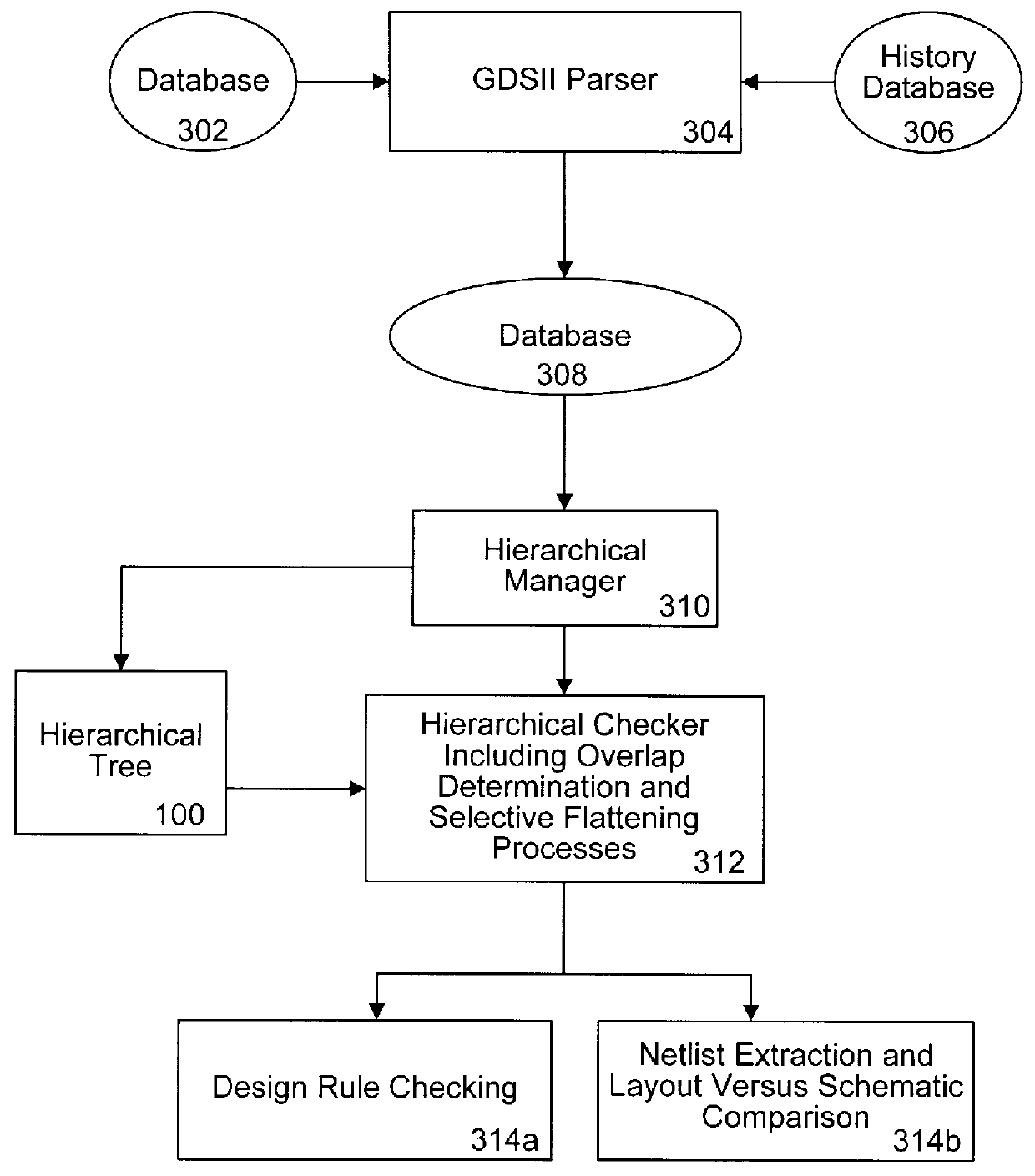
Layout overlap detection with selective flattening in computer implemented integrated circuit design
InactiveUS6011911AValid checkComputer aided designSoftware simulation/interpretation/emulationComputer architectureLayout Versus Schematic
The present invention relates to a method for efficiently performing hierarchical design rules checks (DRC) and layout versus schematic comparison (LVS) on layout areas of an integrated circuit where cells overlap or where a cell and local geometry overlap. With the present invention, a hierarchical tree describes the integrated circuit's layout data including cells having parent-child relationships and including local geometry. The present invention performs efficient layout verification by performing LVS and DRC checking on the new portions of an integrated circuit design and layout areas containing overlapping cells. When instances of cells overlap, the present invention determines the overlap area using predefined data structures that divide each cell into an array of spatial bins. Each bin of a parent is examined to determine if two or more cell instances reside therein or if a cell instance and local geometry reside therein. Once overlap is detected, the areas of the layout data corresponding to the overlap areas are selectively flattened prior to proceeding to DRC and LVS processing. During selective flattening of the overlap areas, the hierarchical tree is traversed from the top cell down through intermediate nodes to the leaf nodes. Each time geometry data is located during the traversal, it is pushes directly to the top cell without being stored in intermediate locations. This provides an effective mechanism for selective flattening.
Owner:SYNOPSYS INC
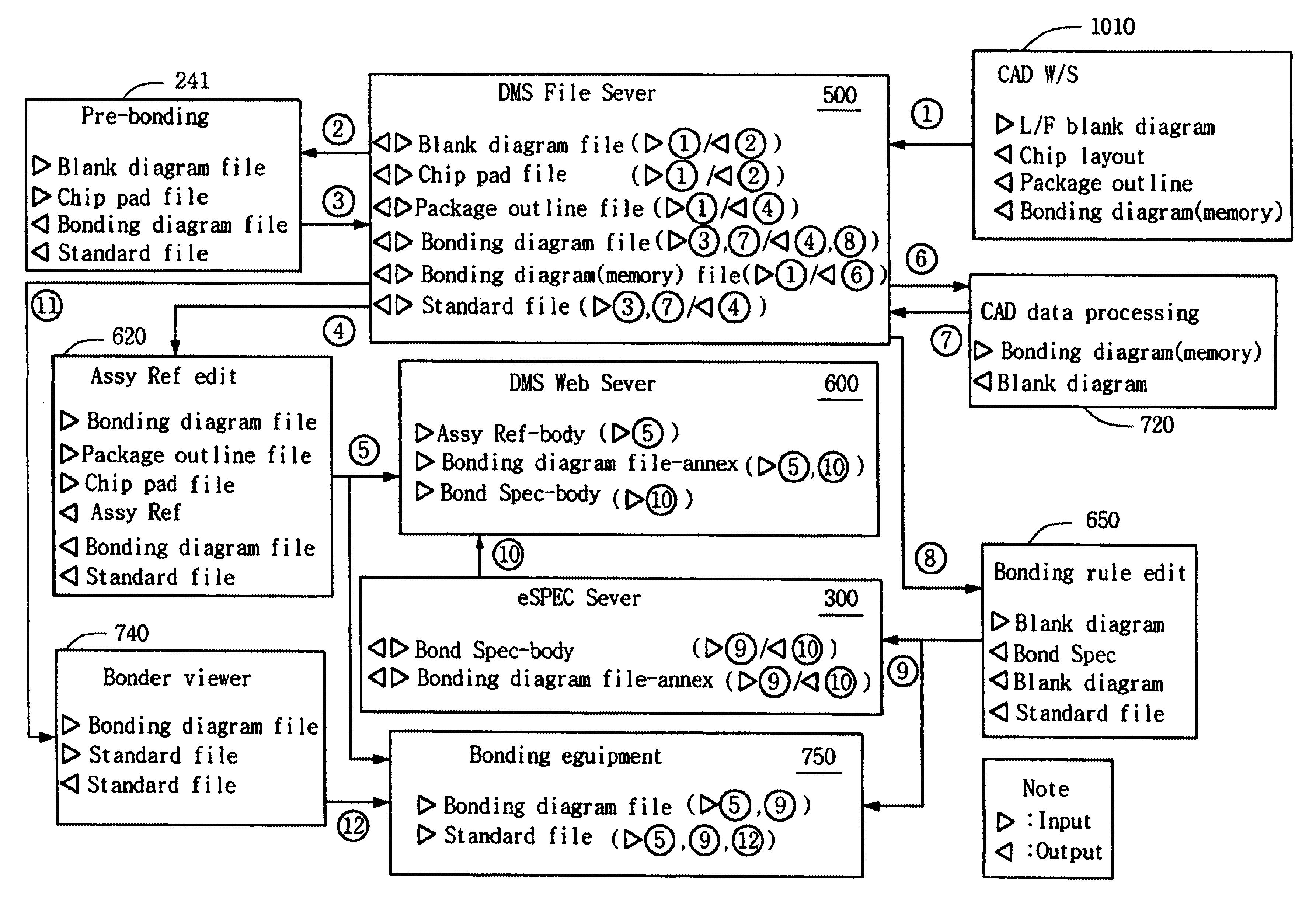
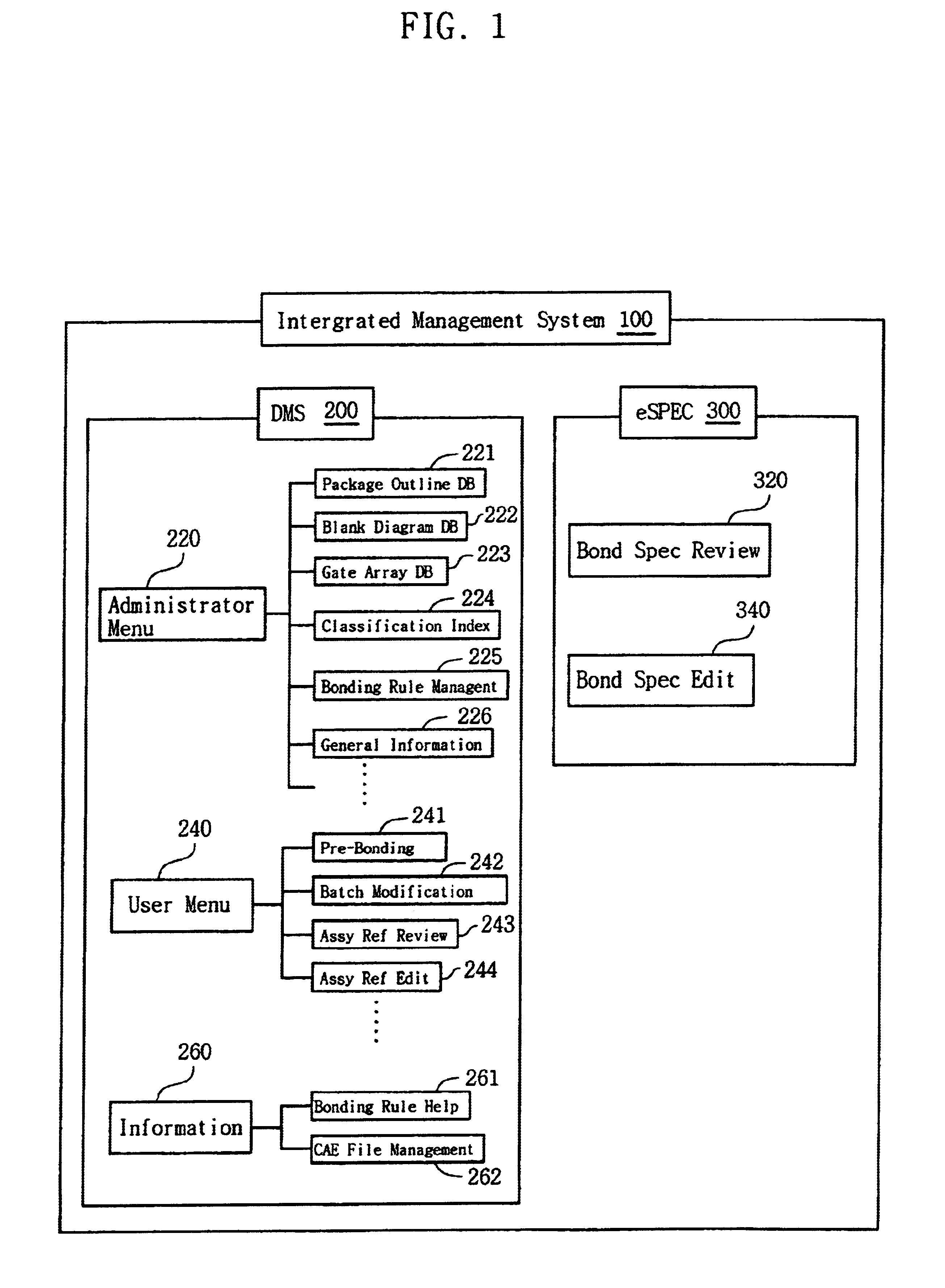
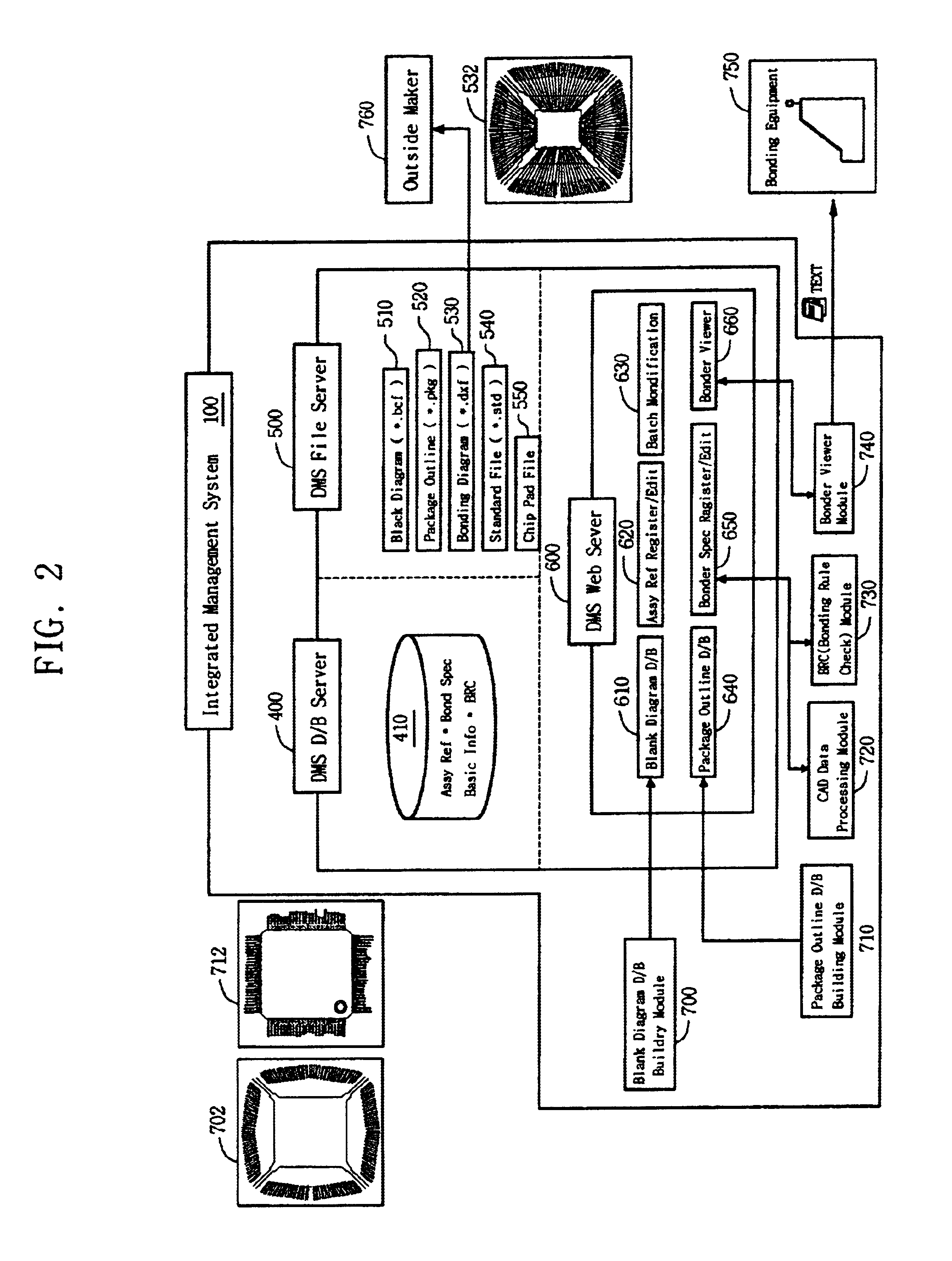
Management system for automated wire bonding process
InactiveUS6851100B1Solid-state devicesSemiconductor/solid-state device manufacturingWeb serviceDatabase server
An integrated management system is provided for automatically executing a procedure of reviewing and editing an assembly reference and a bonding specification used for manufacturing IC packages. The system includes a drawing management system (DMS) that creates the assembly reference, and a bonding specification drawing system that creates, based on the assembly reference, the bonding specification. The integrated management system further includes a DMS database server that stores and manages the assembly reference and the bonding specification, a DMS file server that manages a blank diagram, a package outline, a bonding diagram, and a standard file, and a DMS web server that provides a web interface to a user for permitting a remote access. In particular, the drawing management system has a bonding rule check module that verifies whether the bonding specification meets a bonding rule suitable for an automated wire bonding process. The drawing management system produces the standard file to be transmitted to bonding equipments.
Owner:SAMSUNG ELECTRONICS CO LTD
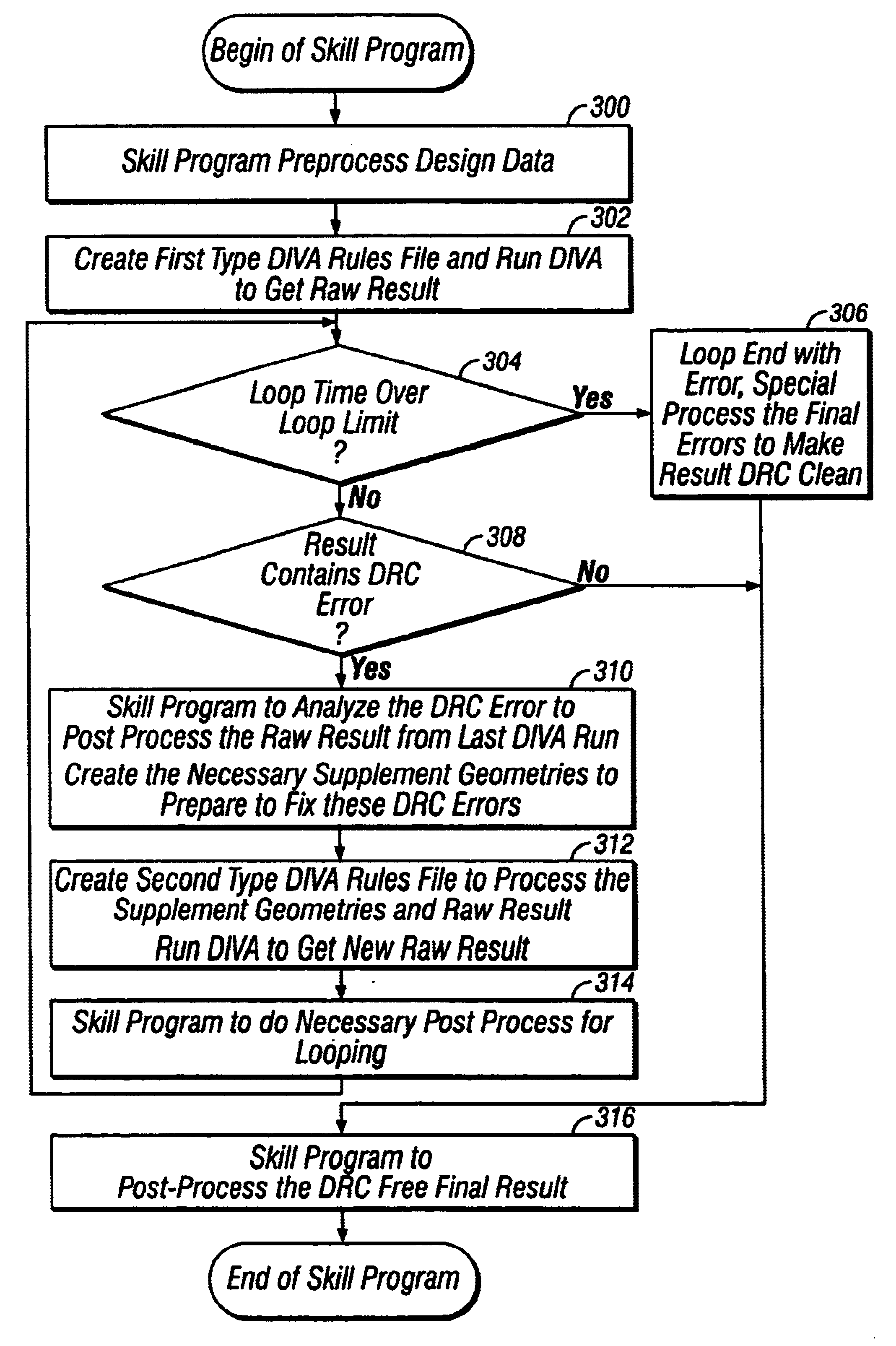
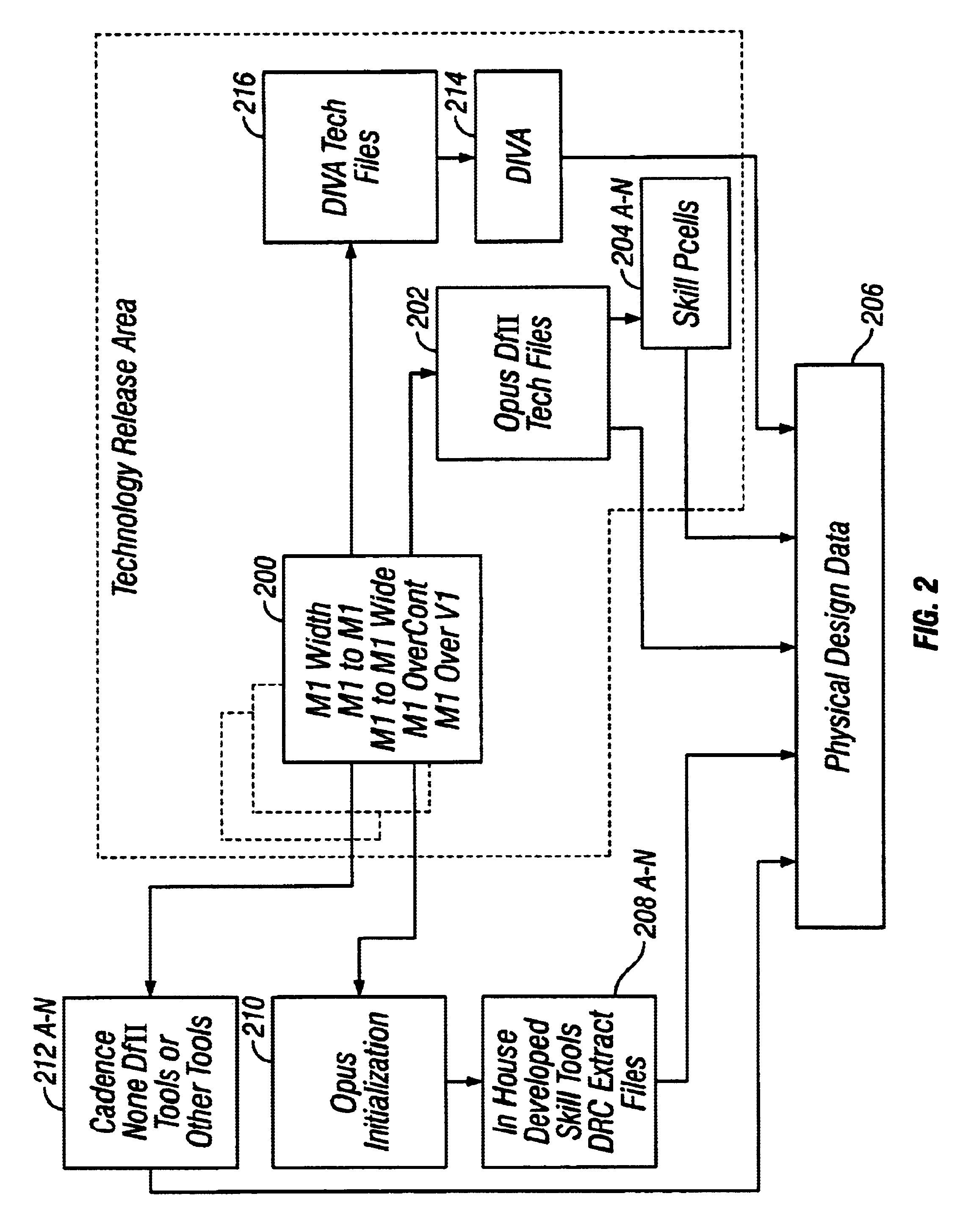
Method and system for automating design rule check error correction in a CAD environment
InactiveUS6637013B1Computer programmed simultaneously with data introductionComputer aided designComputer Aided DesignSoftware engineering
In a computer-aided design environment, a technique for automating design rule check error corrections in a CAD environment contemplates the use of an automation program, such as a SKILL program, to automatically and continuously run a design rule check utility program to generate intermediate results which are processed by the automation program and then supplied back to the design rule check utility program again for execution. The whole process is repeated, in an iterative manner, as many times as needed until a final result is achieved.
Owner:ORACLE INT CORP
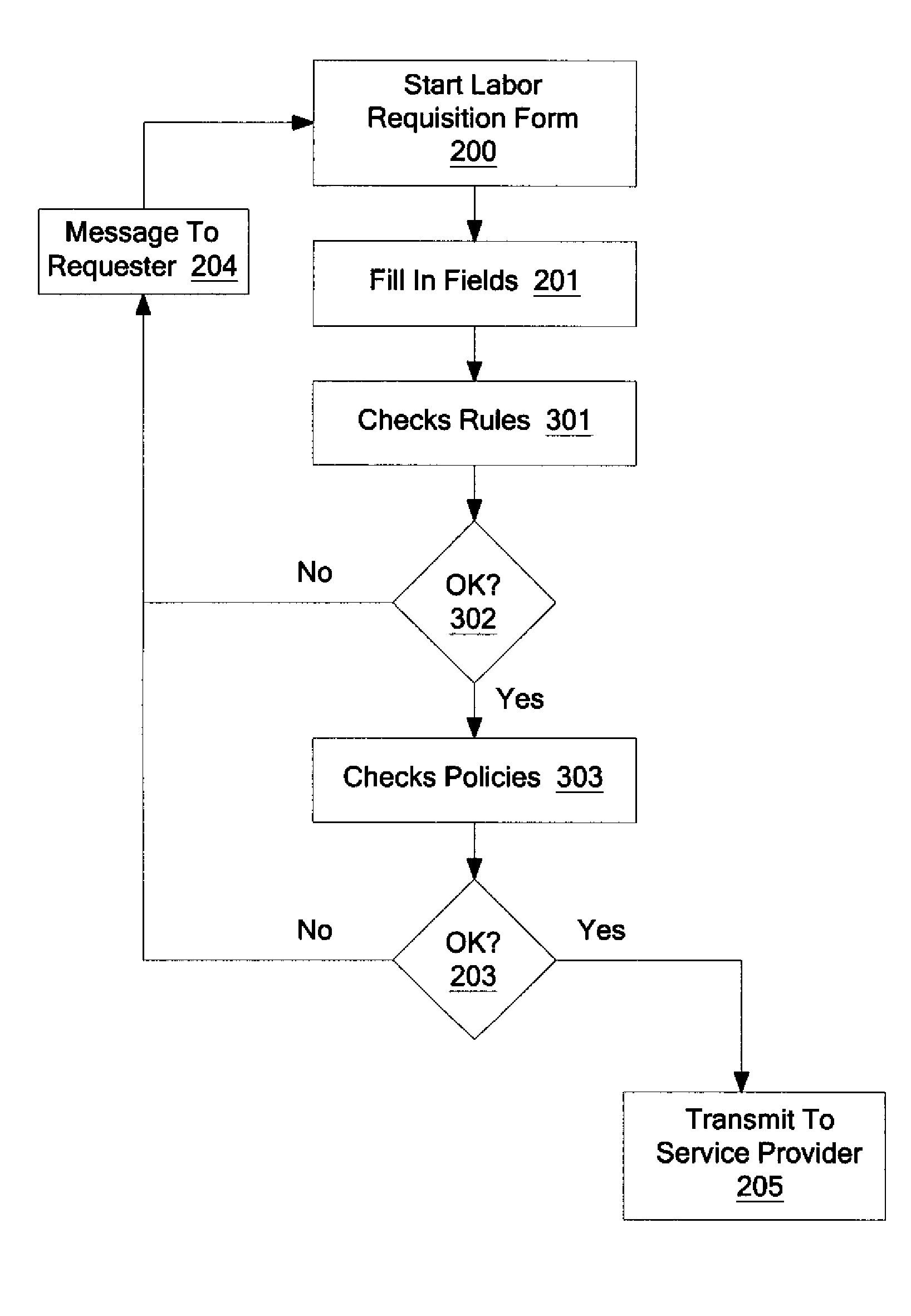
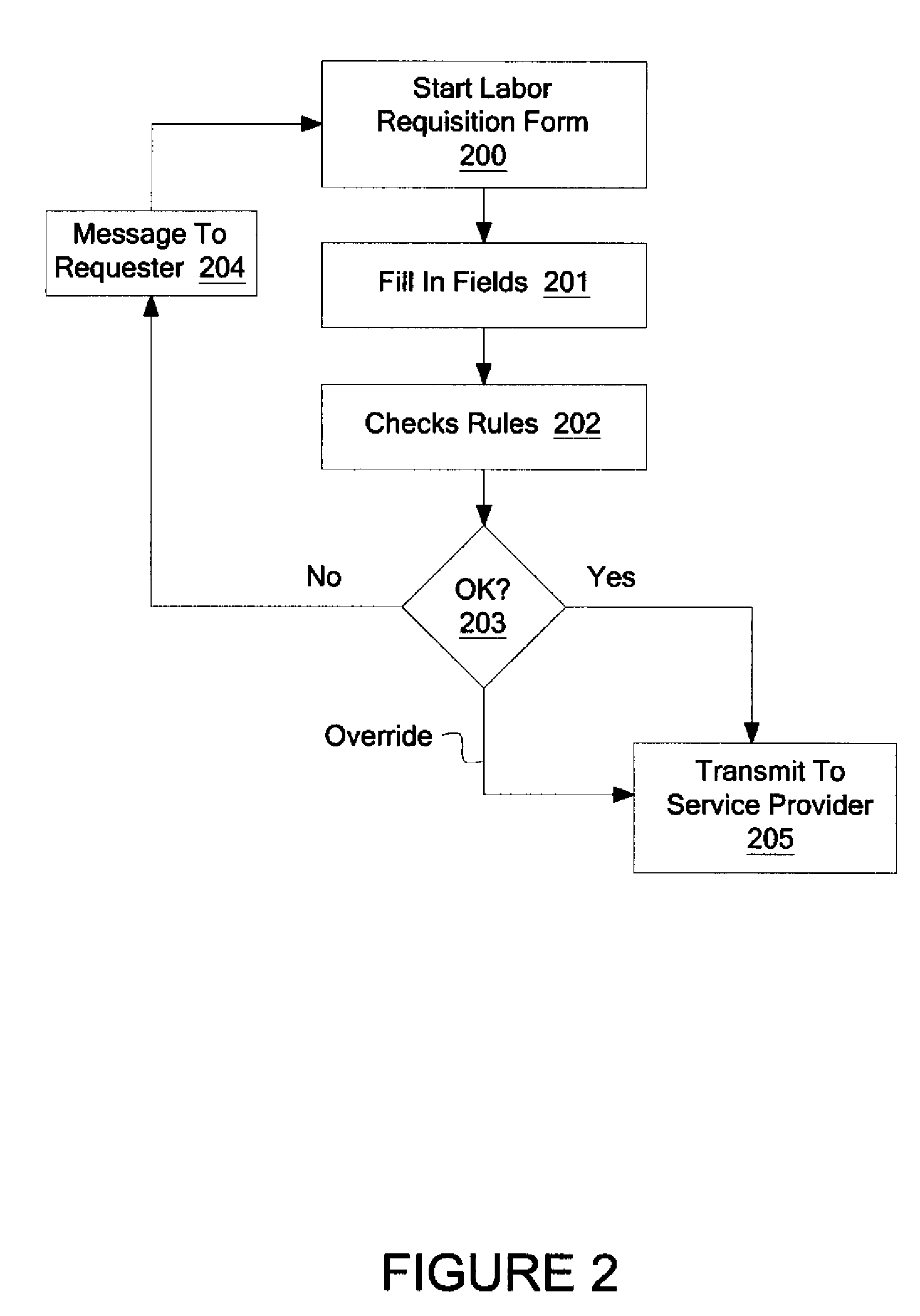
System and method for flexible handling of rules and regulations in labor hiring
A method and system are described for flexible handling of rules and regulations in labor hiring, comprising of receiving a requisition form from a computing device, at least partially completed by a requestor; automatically performing a rules check on the requisition form; in response to a field entry on the form violating a predefined rule, returning the requisition form to the requester to correct or providing the requisition form to a supervisor to override a field entry violating a predefined rule; and in response to no field entry on the form violating a predefined rule, transmitting the form to a service provider.
Owner:DEEM
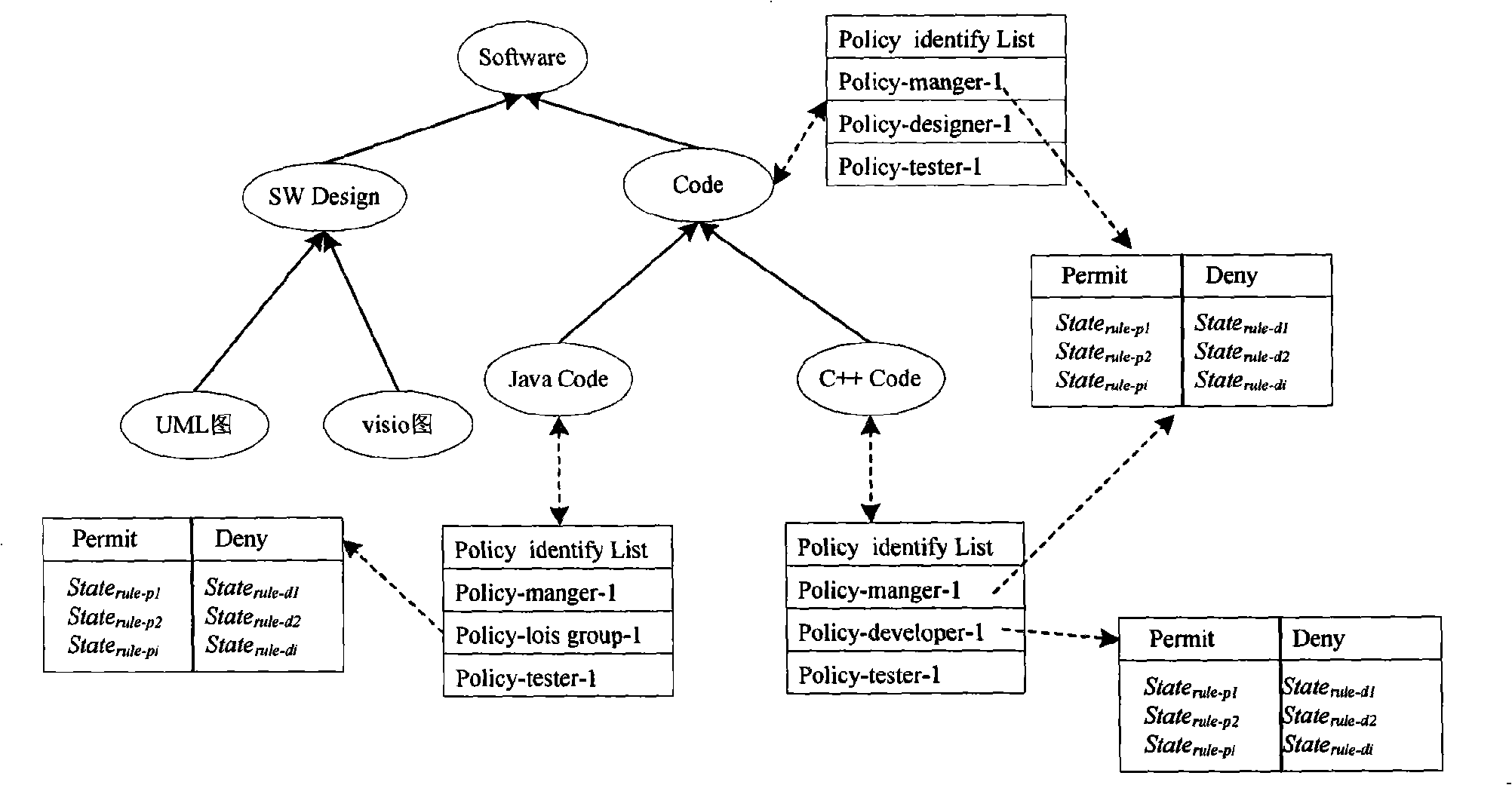
XACML policy rule checking method
InactiveCN101339591AOptimize strategy structureImprove the efficiency of strategy judgmentDigital data authenticationSemantic treeState dependent
The invention provides an XACML strategy rule detecting method, belonging to the field of authorized strategy analysis in information safety. According to the XACML strategy rule, the method has a rule status definition, a rule status correlation definition and a conflict type analysis; on the basis, a strategy index based on a semantic tree is established, a concrete XACML strategy rule detection is carried out and the rule conflict and the rule redundancy are analyzed; the detection method comprises two types: a conflict detection method based on a property level operation correlation and a detection method for other typed conflicts based on the status correlation. In the redundancy analysis, the analysis determining method of the rule redundancy is given respectively in the algorithms of allowing priority, refusing priority and the first-time application dispelling. By adopting the detection method, the strategy manager can precisely locate the rules causing the conflict and the reasons for the conflict; in the redundancy analysis, according to the analysis result, the strategy structure can be optimized and the redundancy rules which has no influence on accessing the determining result can be deleted, therefore, the strategy determining efficiency is improved.
Owner:INST OF SOFTWARE - CHINESE ACAD OF SCI
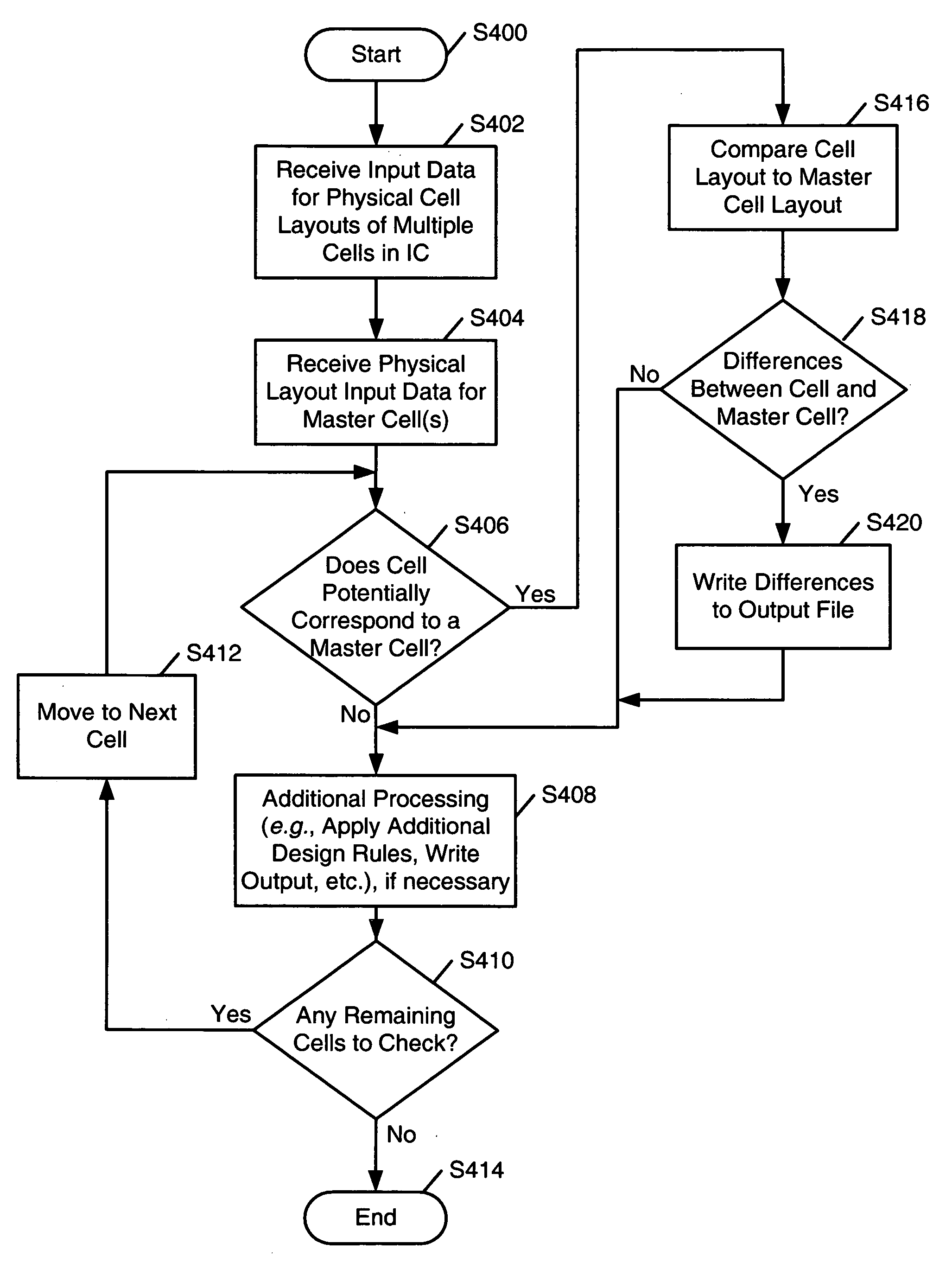
In-line XOR checking of master cells during integrated circuit design rule checking
ActiveUS20060090146A1Computer aided designSpecial data processing applicationsComputer hardwareComputer architecture
Systems and methods for verifying integrated circuit designs: (a) receive input corresponding to physical layouts of cells of the design and available master cells. The systems and methods then determine if the design cells are intended to correspond to one of the master cells, and if so, the systems and methods then determine if the layouts of the cells and the corresponding master cells match one another, e.g., by a layout vs. layout comparison of the design cell with the master cell to determine if the coordinates of the polygon(s) in the design cell match corresponding coordinates of the polygon(s) in the master cell. An “XOR” comparison may be used to determine if the design cell features match the corresponding master cell features. Computer-readable media may be adapted to include computer-executable instructions for performing such methods and operating such systems.
Owner:SIEMENS PROD LIFECYCLE MANAGEMENT SOFTWARE INC
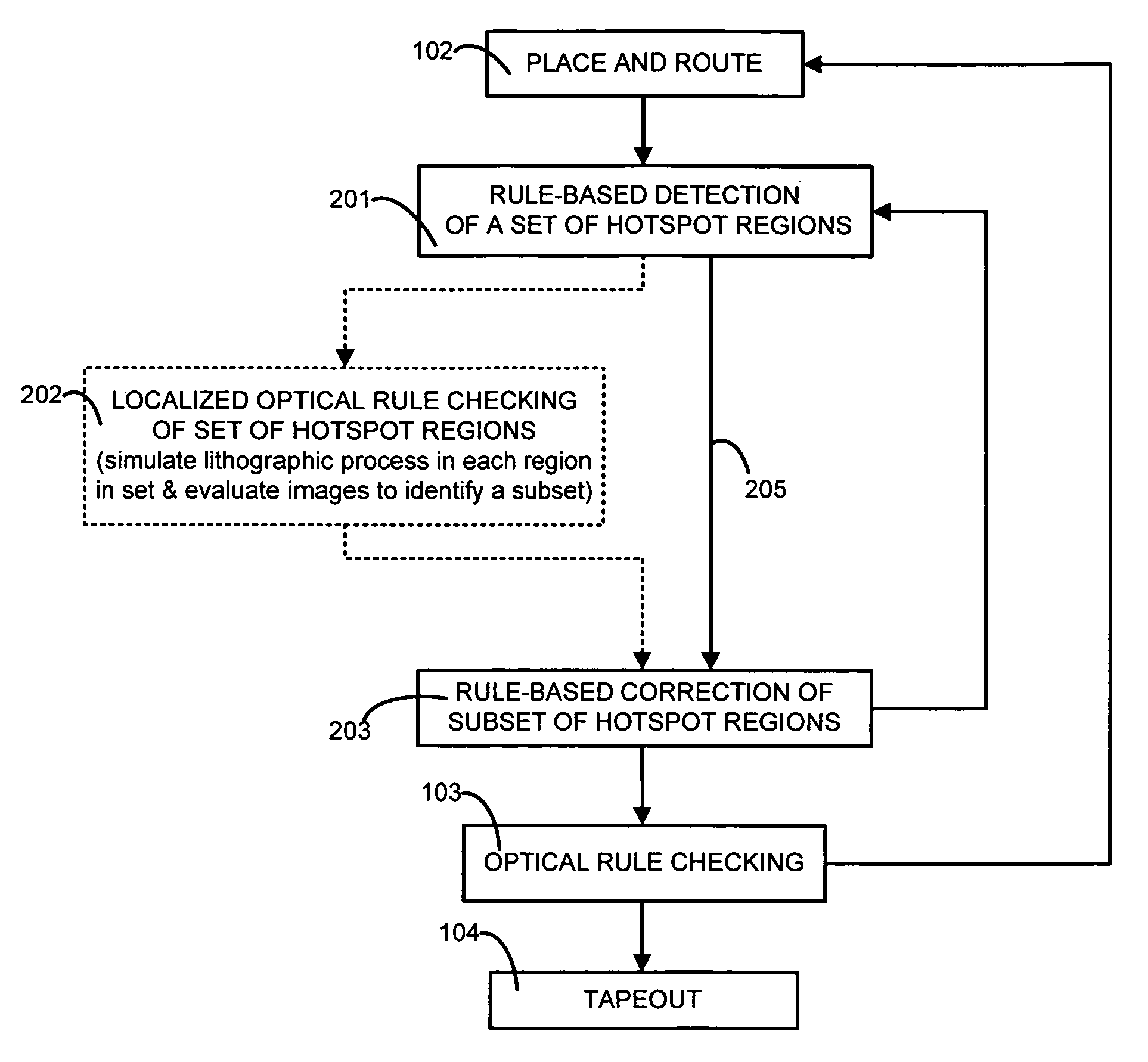
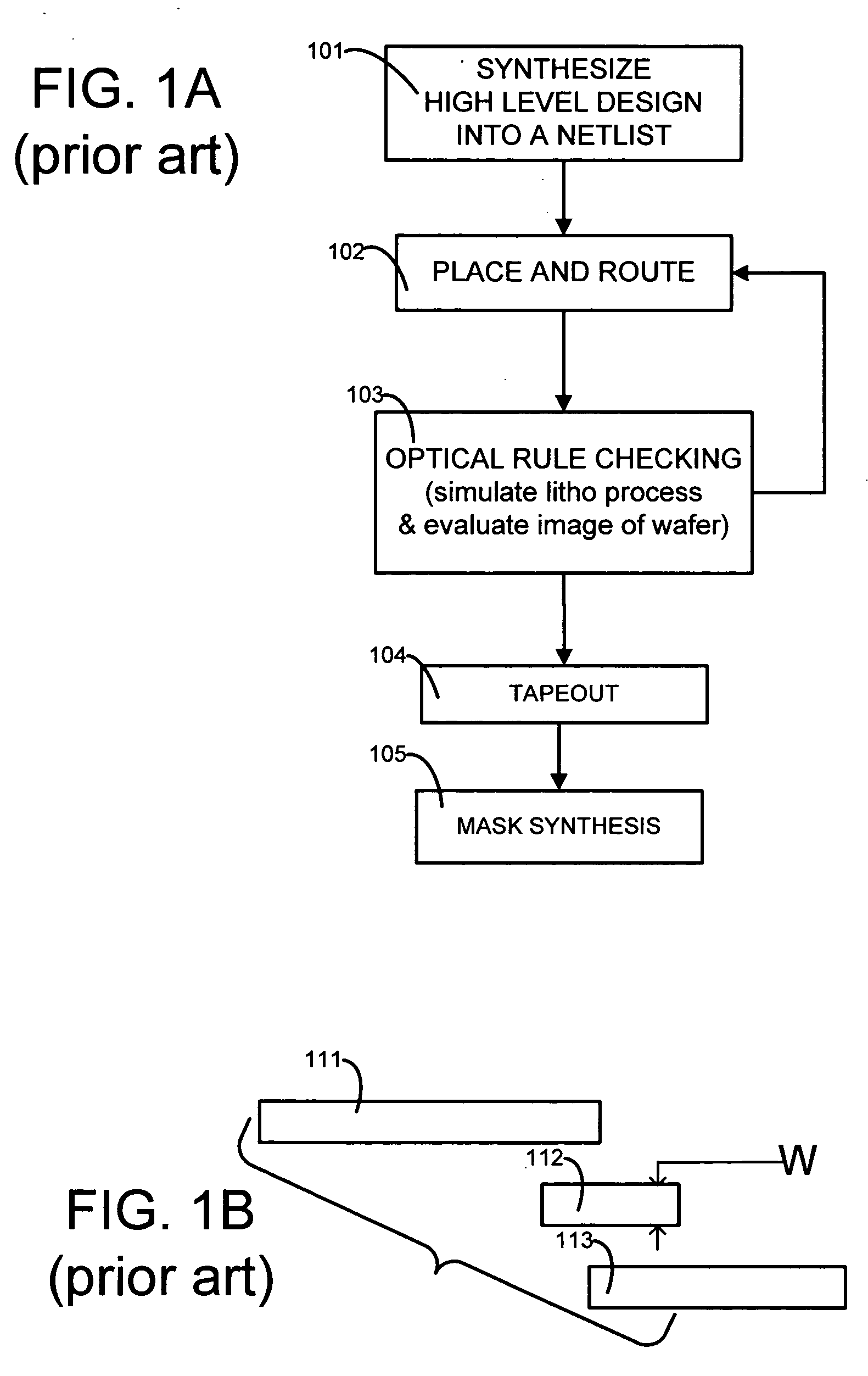
Fast lithography compliance check for place and route optimization
A computer is programmed to use at least one rule to identify from within a layout of an IC design, a set of regions likely to fail if fabricated unchanged. An example of such a rule of detection is to check for presence of two neighbors neither of which fully overlaps a short wire or an end of a long wire. The computer uses at least another rule to change at least one region in the set of regions, to obtain a second layout which is less likely to fail in the identified regions. An example of such a rule of correction is to elongate at least one of the two neighbors. The computer may perform optical rule checking (ORC) in any order relative to application of the rules, e.g. ORC can be performed between detection rules and correction rules i.e. performed individually on each identified region prior to correction.
Owner:SYNOPSYS INC
Automatic code rule checking platform
ActiveCN103309804AReduce late riskQuality improvementSoftware testing/debuggingAnalysis workingPersonal computer
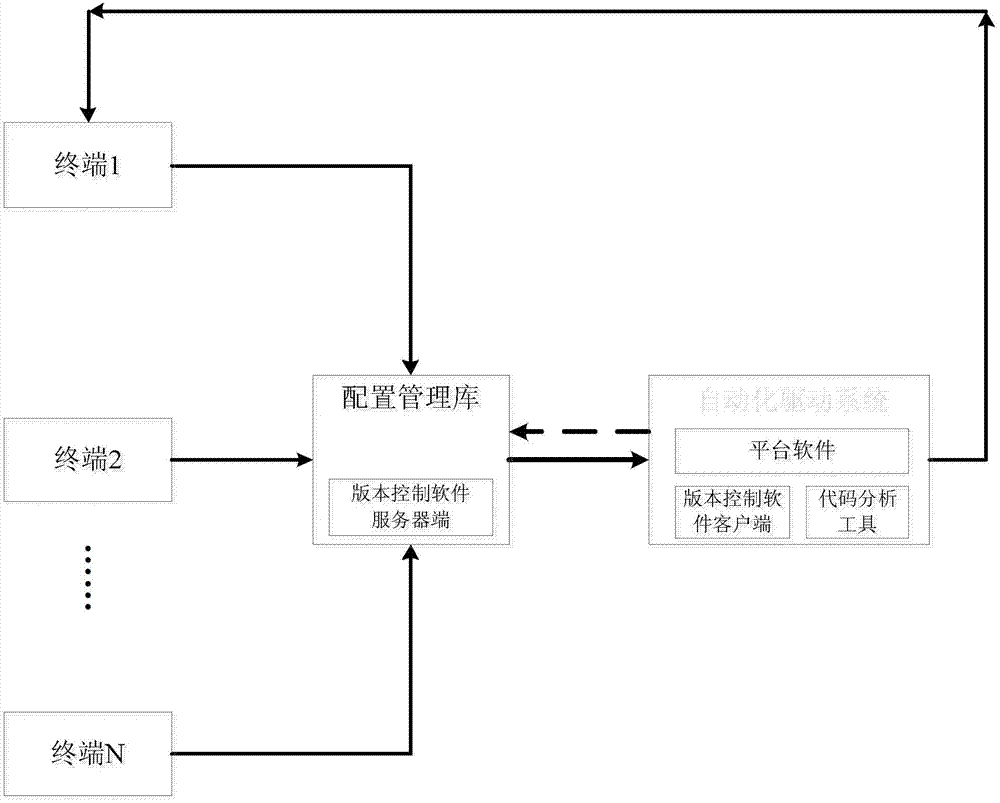
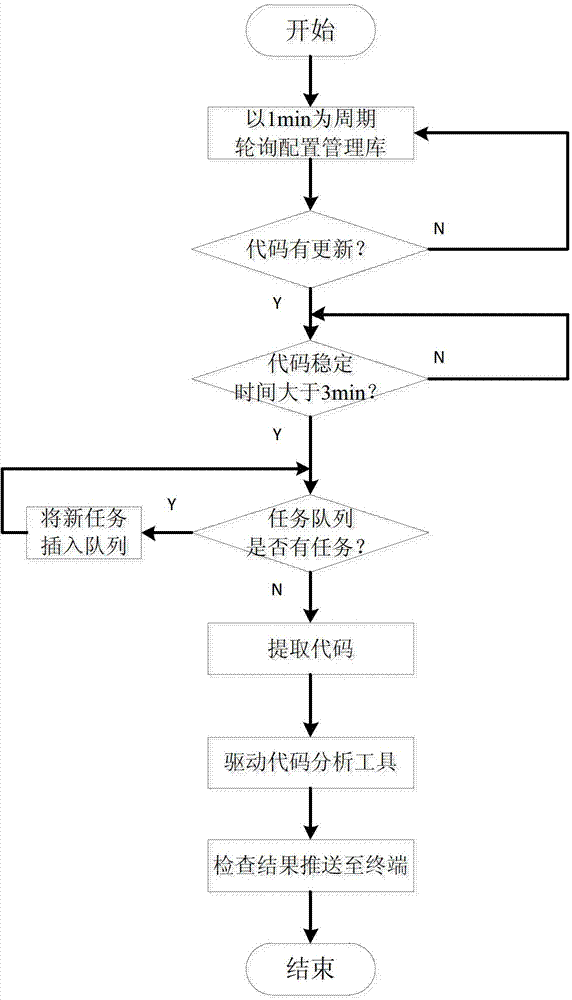
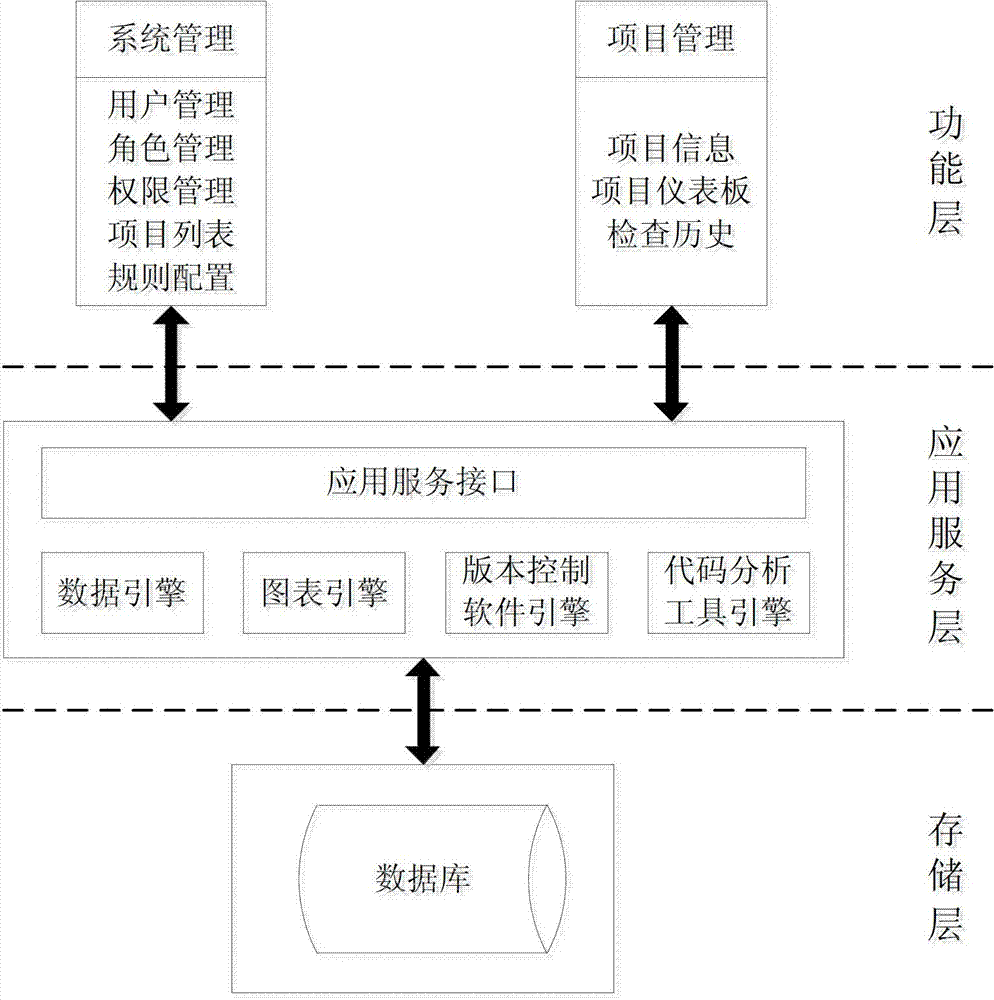
The invention discloses an automatic code rule checking platform, which aims at providing the automatic code rule checking platform which helps developers find and overcome code defects in time. The automatic code rule checking platform is realized through the following technical scheme: codes which are edited or modified by a personal computer terminal are submitted to a configuration management library through a version control software client; an automatic driving system monitors the configuration management library in a polling mode; when the codes in the configuration management library are changed, platform software starts the version control software client to extract updated codes in the configuration management library, and a code analysis tool is called to check a code rule; the version control software client searches for the codes from the configuration management library and submits the codes to the code analysis tool to check the code rule; the code analysis tool executes code analysis work according to the item information, the check condition and the code check rule set configured or set by a terminal user, and the platform software shows check results to the developers.
Owner:10TH RES INST OF CETC
Method and system for ontology-enabled traceability in design and management applications
InactiveUS20120143570A1Enhanced Semantic RepresentationSpecial data processing applicationsNetwork management applicationDesign rule checking
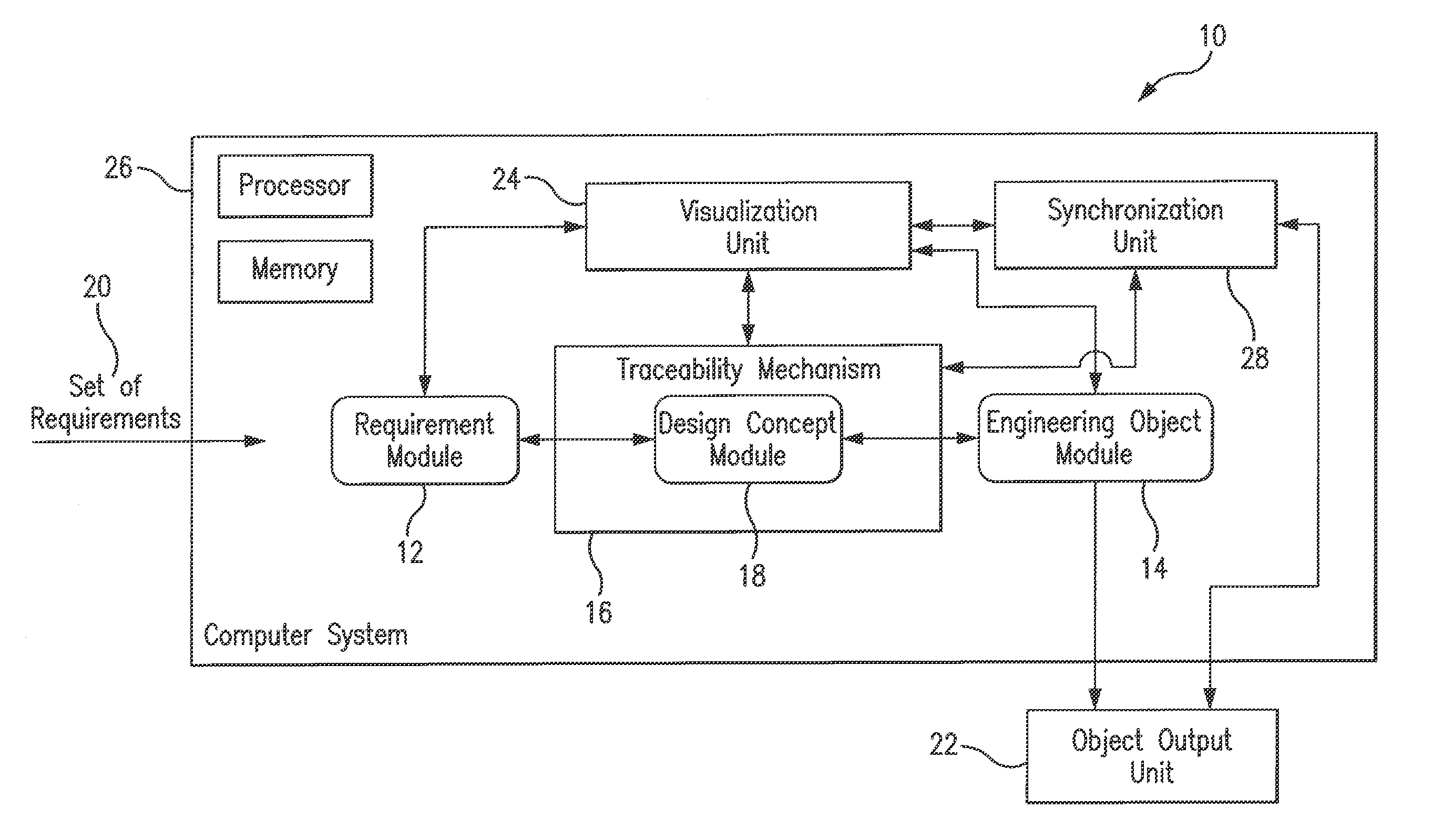
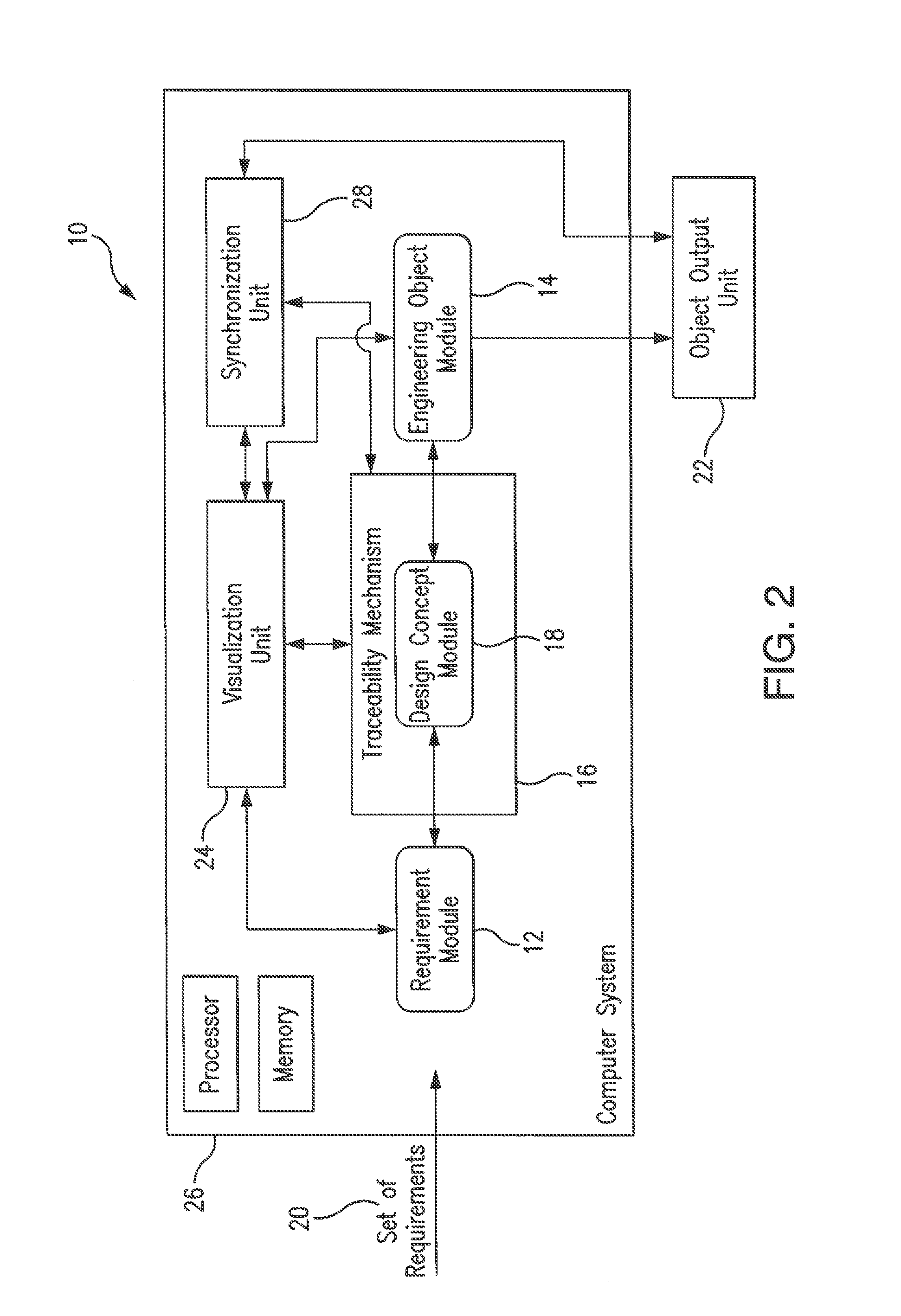
A system and method for ontology-enhanced traceability in design and management applications employ ontology nodes embedded in a processor executable traceability link (network) coupling processor executable requirement modules to processor executable engineering object modules to facilitate in all stages of engineering object development. The engineering object development occurs through multiple models of computation, control, and visualization platform networked together via ontology-enhanced traceability mechanism. Processor executable design rule checking module embedded in the design concept nodes creates a pathway for the development process validation and verification at early stages of the object lifecycle. Linking of ontologies / meta-models is performed for the purposes of supporting ontology-enabled traceability across multiple domains.
Owner:UNIV OF MARYLAND
System and method of detecting design rule noncompliant subgraphs in circuit netlists
ActiveUS20130125072A1Increase flexibilityEasy to useCAD circuit designSoftware simulation/interpretation/emulationGraphicsTheoretical computer science
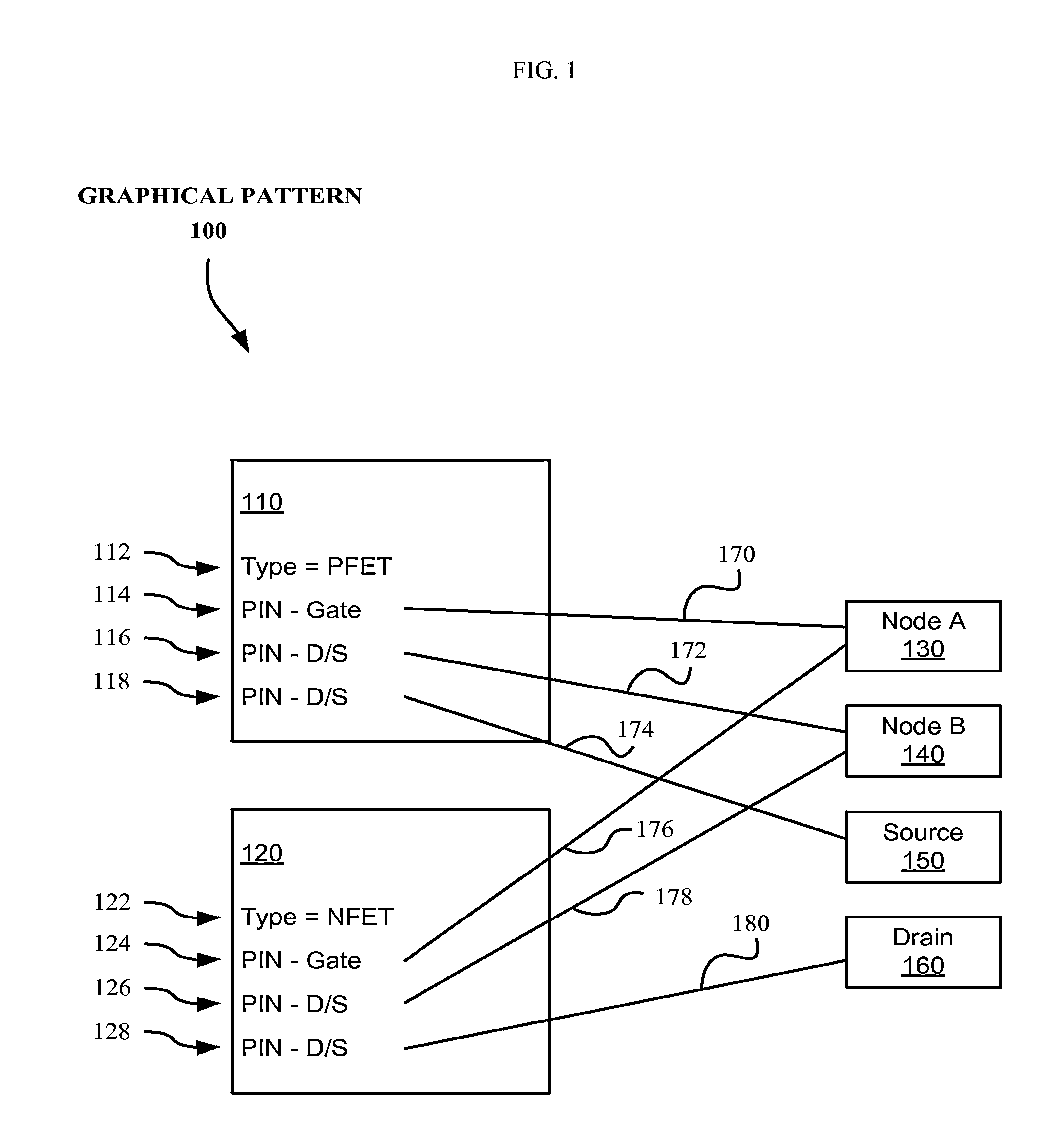
An automated system and method of performing electronic design rule checking on the netlist of an integrated circuit composed of a plurality of subgraphs. The electronic design rule is embodied as a two part template with a target subgraph specification and a design rule compliance check specification. The target subgraph specification often is at least partially defined by an interactive visual programming section that allows the user to construct a graphic specification of the target netlist. The method first searches the netlist for target subgraphs that match the target subgraph specification, and the user can verify proper target selection. The method then performs rule checks on these search targets, and non compliant subnets identified. Flexibility is enhanced by use of search wildcards, attribute ranges, and various short user scripts which may contain various Boolean logical operations.
Owner:INSIGHT EDA
Rule checking system and rule checking method for recognizing medical insurance reimbursement violations
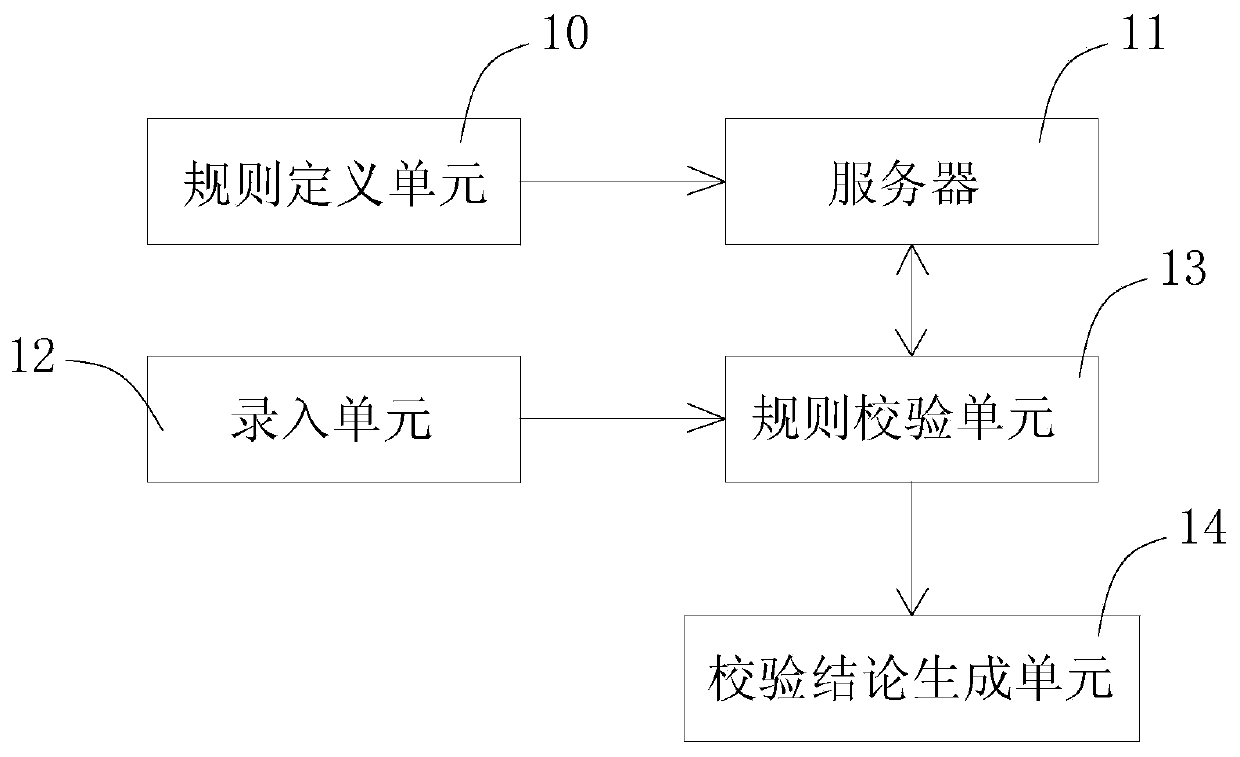
ActiveCN104182824AReduce the number of repeated fetchesAvoid red tapeResourcesProgramming languageSystem maintenance
The invention discloses a rule checking system for recognizing medical insurance reimbursement violations. The rule checking system comprises a rule defining unit, a server, a type-in unit, a rule checking unit and a checking conclusion generating unit, wherein system maintenance personnel type in rules capable of recognizing the medical insurance reimbursement violations according to experience and store rule data lists and threshold values of each rule datum into a database to be used as the rule checking basis; in the rule checking process, the rule checking unit sequentially calculates a deviation value between each datum in a medical insurance settlement list and the corresponding threshold; the checking conclusion generating unit judges whether the insurance reimbursement behavior belongs to a dishonoring behavior or a suspicious behavior or a normal behavior according to the deviation value of each datum, so that the validity or the violation of the medical insurance reimbursement behavior is automatically judged.
Owner:PING AN MEDICAL & HEALTHCARE MANAGEMENT CO LTD +1
Variable-clause electronic contract automatic generation method in business to customer (B2C) transaction
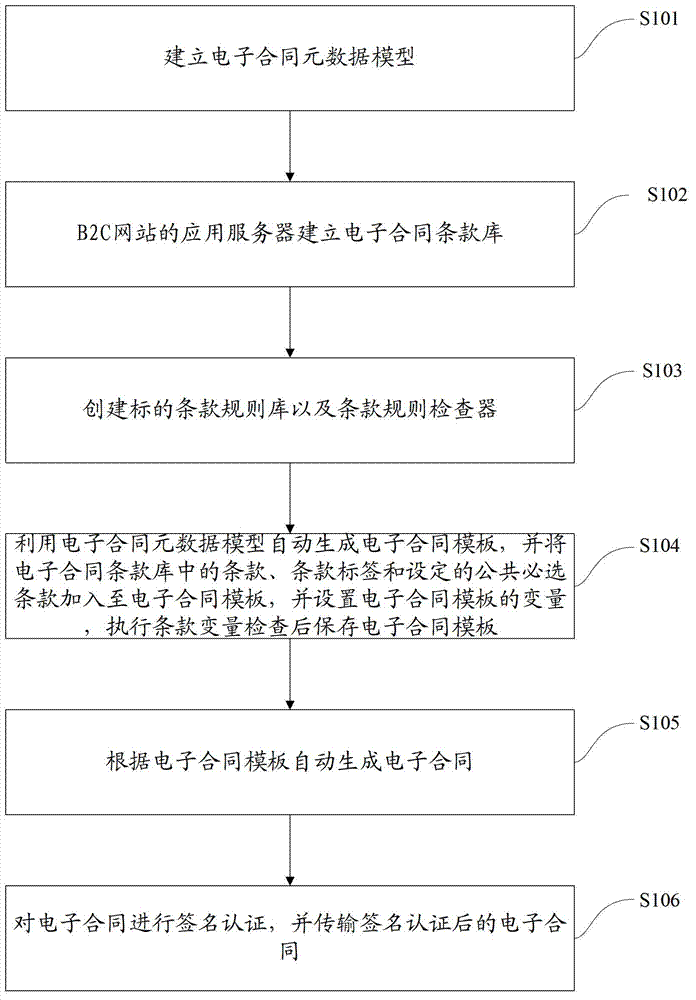
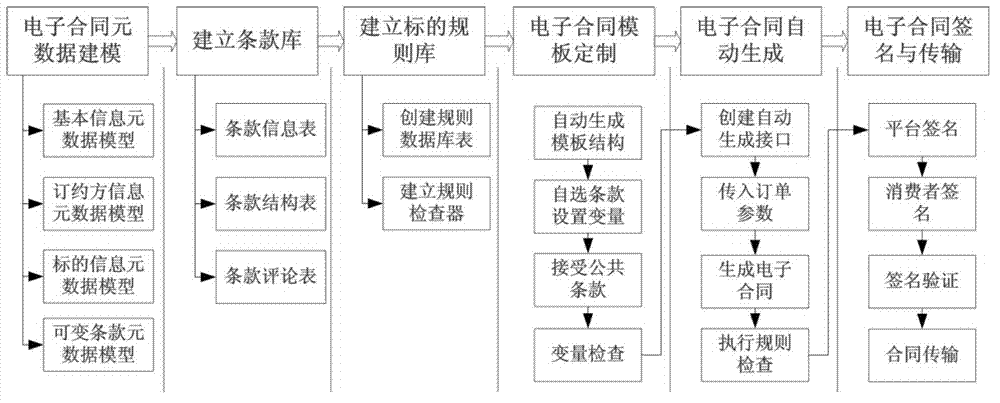
InactiveCN102855304AComputer security arrangementsBuying/selling/leasing transactionsElectronic contractsApplication server
The invention discloses a variable-clause electronic contract automatic generation method in a business to customer (B2C) transaction. The method comprises the following steps of: establishing an electronic contract metadata model; establishing an electronic contract clause base by an application server of a B2C website; establishing an object clause ruler base and a clause rule checker; automatically generating an electronic contract template through the electronic contract metadata model, adding clauses, clause labels and set public required clauses in the electronic contract clause base into the electronic contact template, setting a variable of the electronic contract template, and storing the electronic contract template after checking clause variables; automatically generating an electronic contract according to the electronic contract template; and performing signature authentication on the electronic contract, and transmitting the electronic contract subjected to the signature authentication. By the method, the contract template can be supplied, and variable clauses in the electronic contract are compatible.
Owner:TSINGHUA UNIV
Programmable Electrical Rule Checking
InactiveUS20100306720A1Computer aided designSoftware simulation/interpretation/emulationComputer architectureCircuit design
Electrical rule checking techniques for analyzing integrated circuit design data to identify specified circuit element configurations. Both tools and methods implementing these techniques may be employed to identify circuit element configurations using both logical and physical layout information for the design data. A set of commands are provided that will allow a user to program a programmable electrical rule check tool to identify a wide variety of circuit element configurations, using both logical and physical layout data, as desired by the user.
Owner:PIKUS F G +2
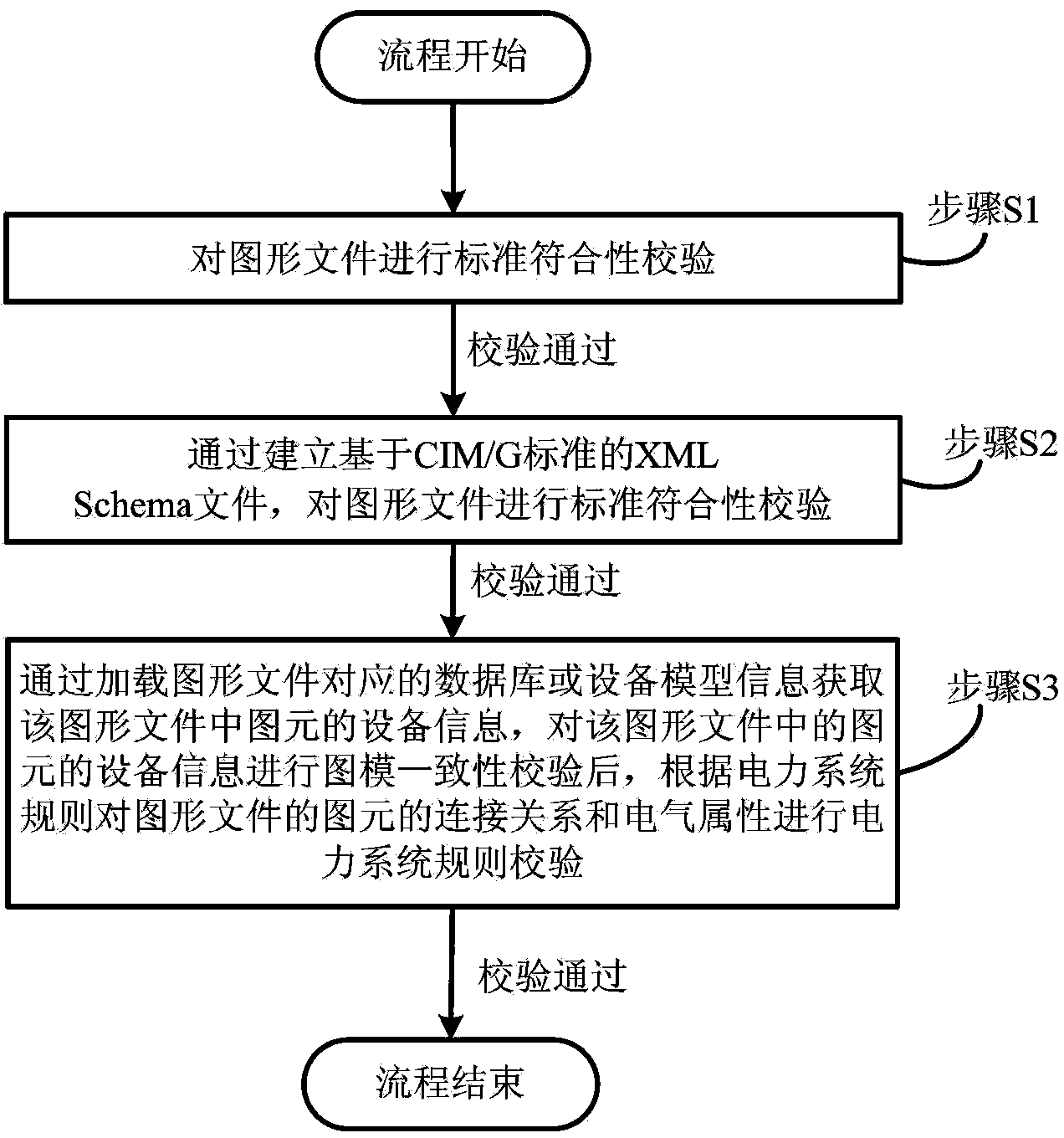
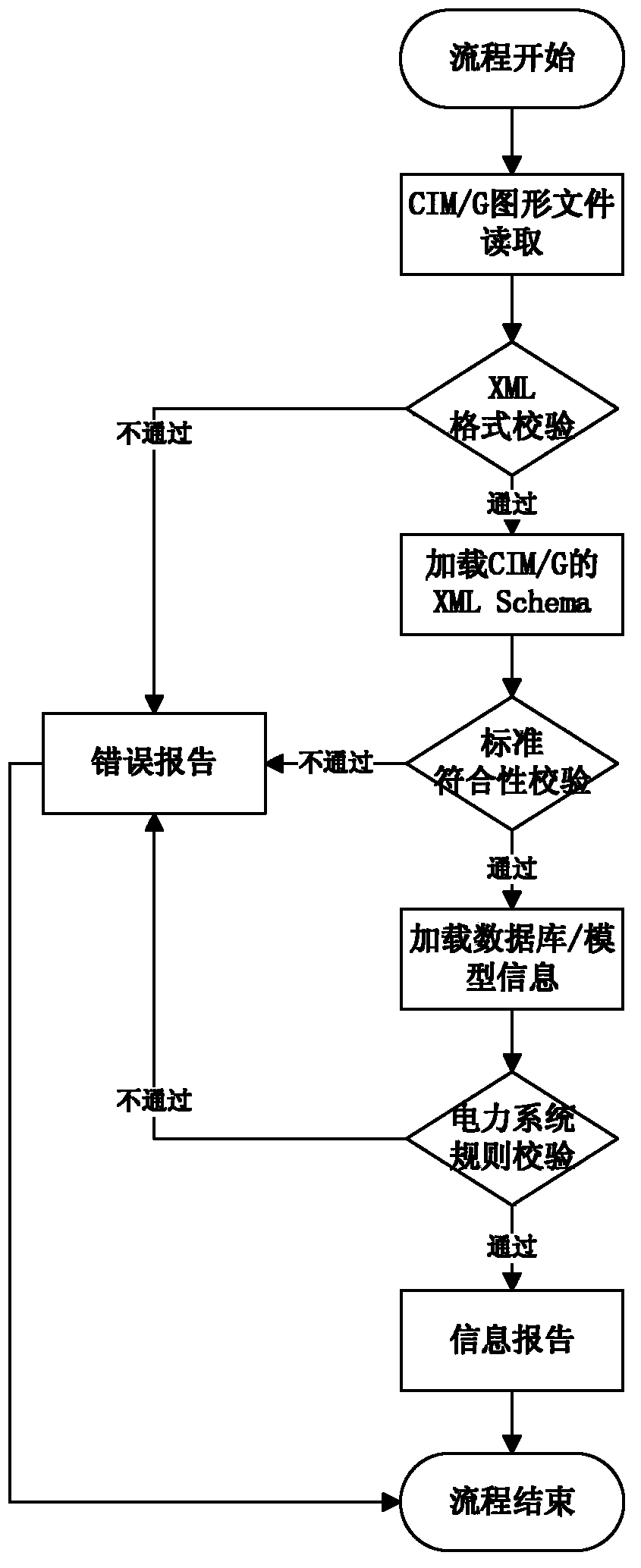
Interoperation picture file checking method based on CIM/G standard
InactiveCN103353871AGuaranteed correctnessReduce unresolvable problemsSpecial data processing applicationsXML schemaGraphics
The invention provides an interoperation picture file checking method based on a CIM / G standard, which comprises the following steps: step 1, checking the correctness of the format of a picture file through the XML format examination, step 2, carrying out the standard conformity checking on the picture file through establishing an XML Schema file based on the CIM / G standard, and step 3, acquiring the device information of the pels in the picture file through loading corresponding database or device model information of the picture file, and carrying out the power system rule checking on the connection relation and the electrical properties of the pels in the picture file according to a power system rule after carrying out the picture-model consistency checking on the device information of the pels in the picture file. The interoperation picture file checking method, provided by the invention, can judge whether the interoperation picture file has a problem from the multiple aspects or not, and reduces the problem that information cannot be analyzed, which is caused by that data interaction correctness is influenced or the operation standard is not met, which are resulted from file format mistake.
Owner:STATE GRID CORP OF CHINA +2
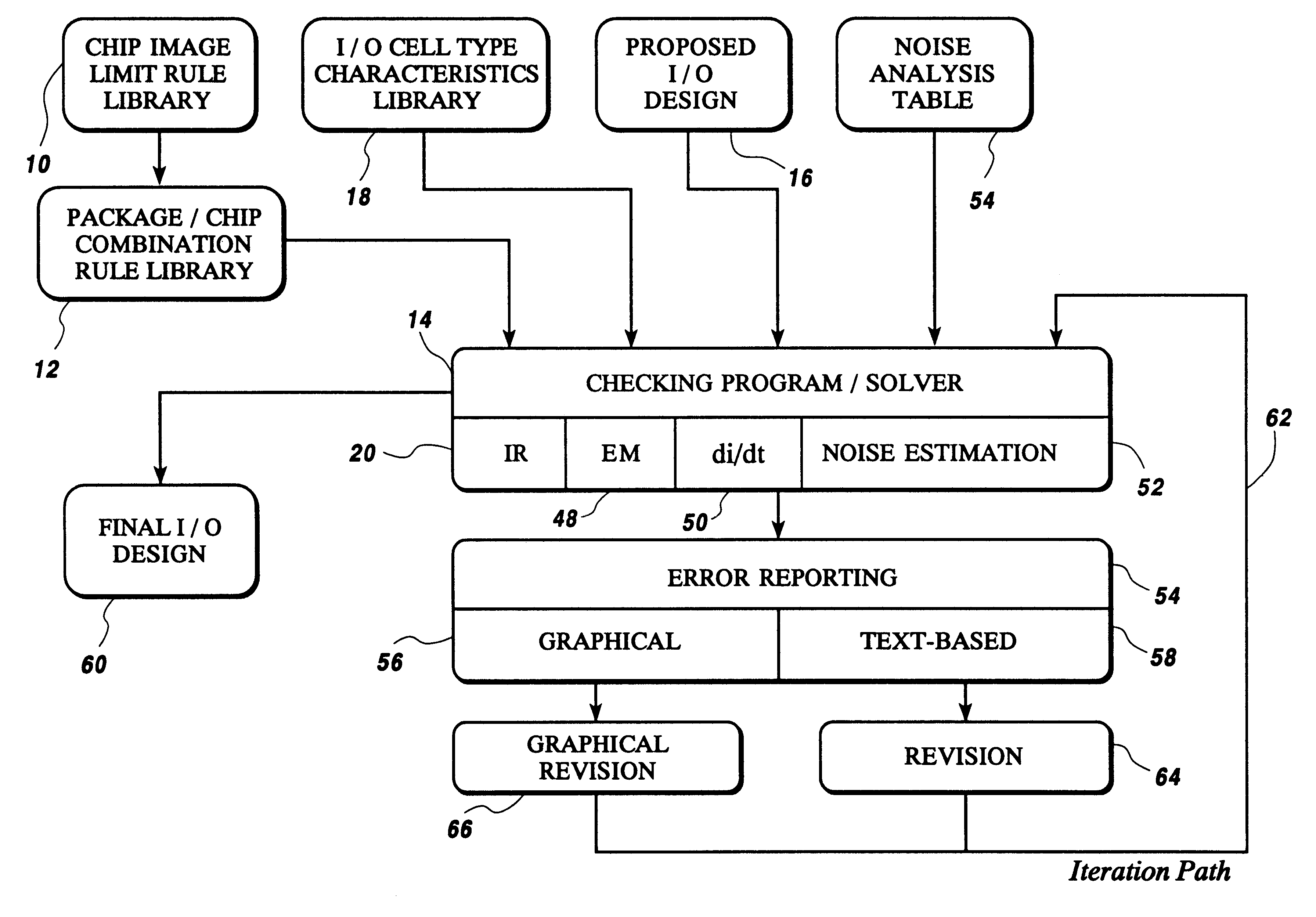
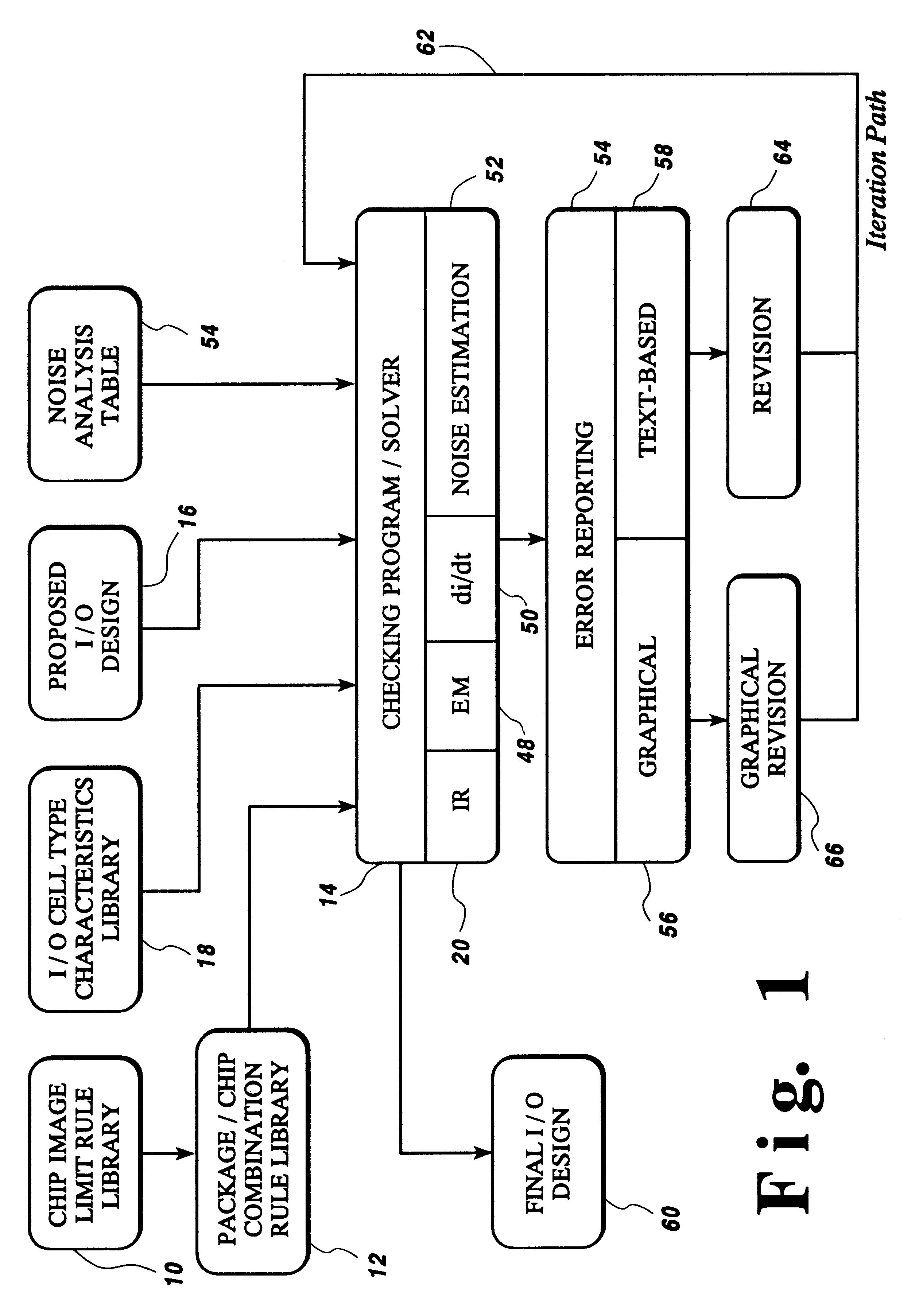
Fast method of I/O circuit placement and electrical rule checking
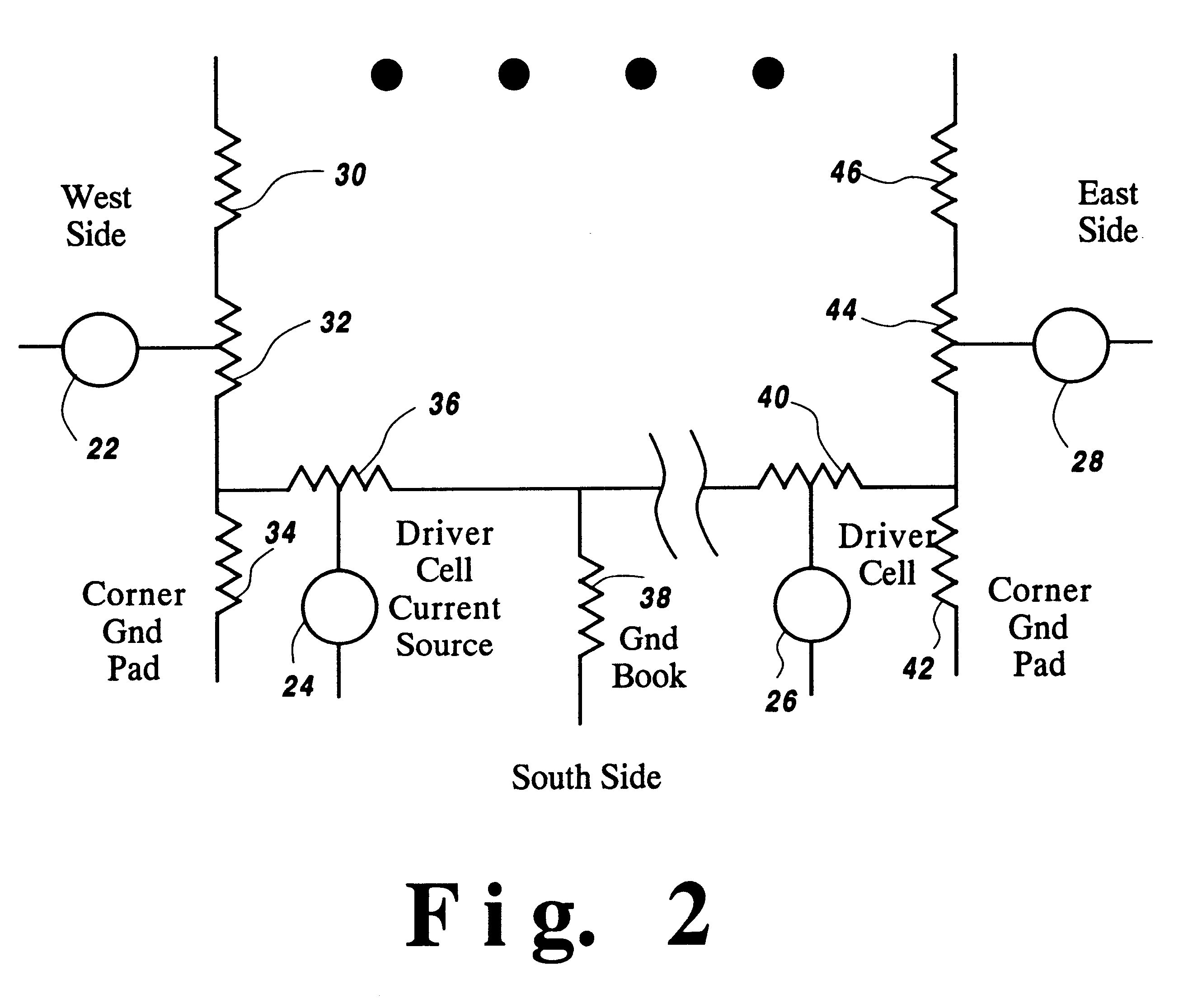
InactiveUS6584606B1Computer programmed simultaneously with data introductionComputer aided designVoltage dropIntegrated circuit layout
A method of analyzing I / O cell layouts for integrated circuits, such as ASICs, includes defining a proposed I / O cell layout on a selected chip image, providing a set of limit rules for electromigration, IR voltage drop and di / dt noise for the selected chip image, providing characteristics for each I / O cell type used in the proposed I / O cell layout, checking the proposed I / O cell layout by applying the limit rules to the proposed I / O cell layout and reporting all I / O cells used in the proposed I / O cell layout that do not meet the limit rules for the selected chip image.
Owner:IBM CORP
Static analysis-based checking method of safety rules of C language
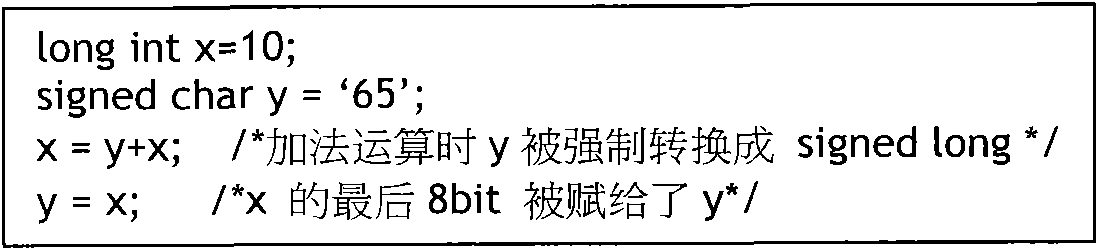
InactiveCN102012991AMake up for the lack of securityPlatform integrity maintainanceStatic timing analysisType conversion
The invention relates to a static analysis-based checking method of safety rules of C language, which comprises the following steps: 1) checking the type of the C language to avoid the occurrence of compulsory type conversion and prohibiting the declaration of the type of a generic pointer; 2) stipulating that a global variable and a local variable can not be in homonymy, and the global variable and a formal parameter of a function can not be in tautonomy; 3) limiting a cyclic variable of a control flow statement; 4) strengthening the declaration and the definition of the C language; and 5) carrying out analysis of accidence, grammar and semanteme on source codes, and finding out places which do not meet the stipulation from the source codes. The method has the advantages of being capable of finding out possible loopholes on programming of the C language under the premise that the codes do not need to be executed and effectively making up for the deficiency of insufficient safety of the C language in soft engineering.
Owner:北京神舟航天软件技术股份有限公司
Multiple code sets for multiple execution contexts
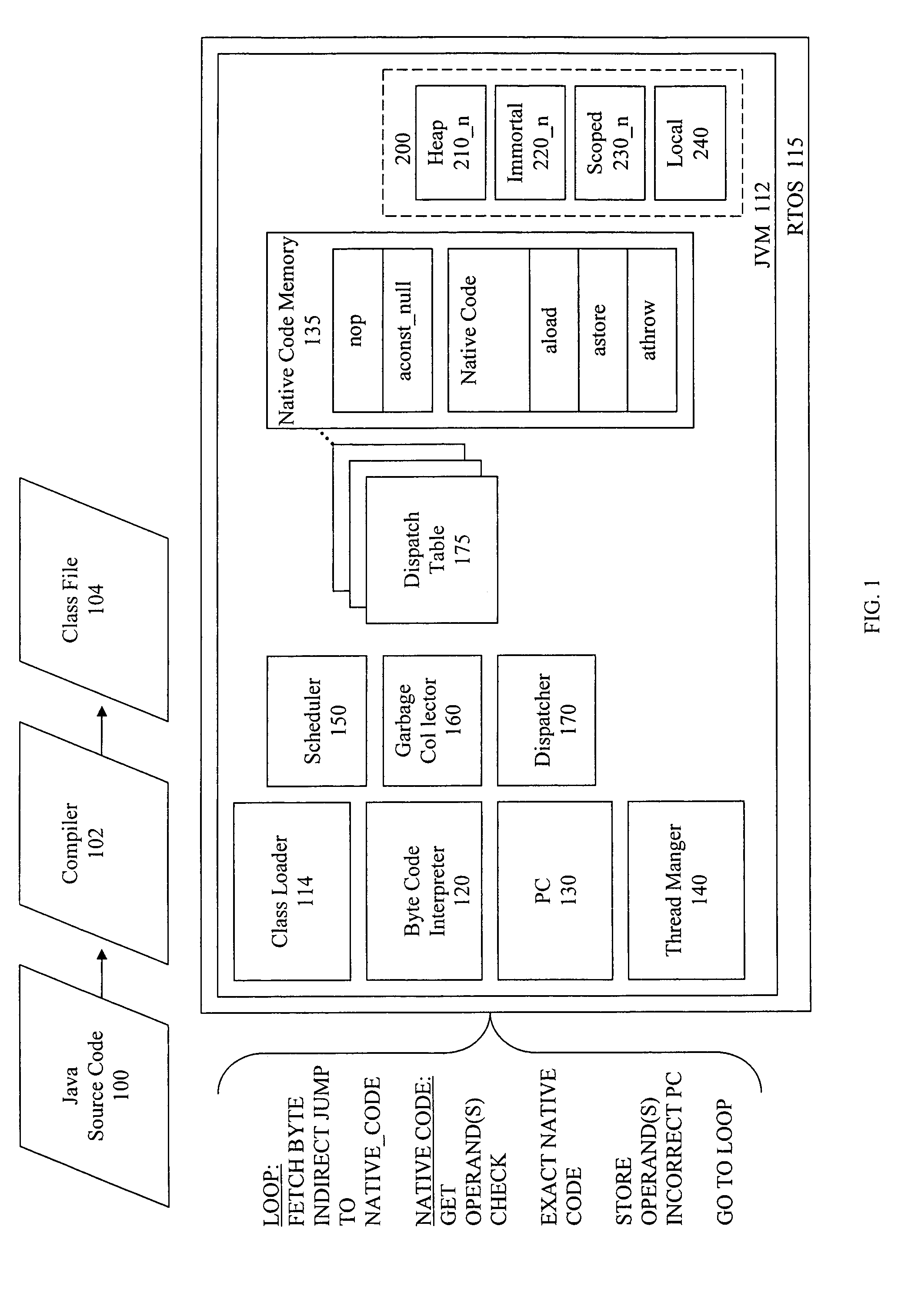
InactiveUS7496897B1Specific program execution arrangementsMemory systemsData processing systemState switching
The invention relates to optimizing software code execution during state transitions. The system handles changes in execution context using differential rule checking techniques. For instance, when a thread executing in a data processing system changes state, its new state may be subject to different rules than its previous state. To enforce these rules, the thread may be associated with software code that causes certain restrictions, such as memory restrictions, to be applied to the thread. In an interpretive environment, this can be implemented by detecting a state transition in an active thread, and responding to the state transition by associating the thread with a dispatch table that reflects its state change. The dispatch table may cause the thread to be associated with code that enforces those restrictions. In one example, different dispatch tables can be provided, each table reflecting a different state of a thread, and each causing a thread to be subject to different restrictions. In another example, the same dispatch table can be rewritten to accommodate the changed state of the thread.
Owner:TIMESYS
Verifying an IC layout in individual regions and combining results
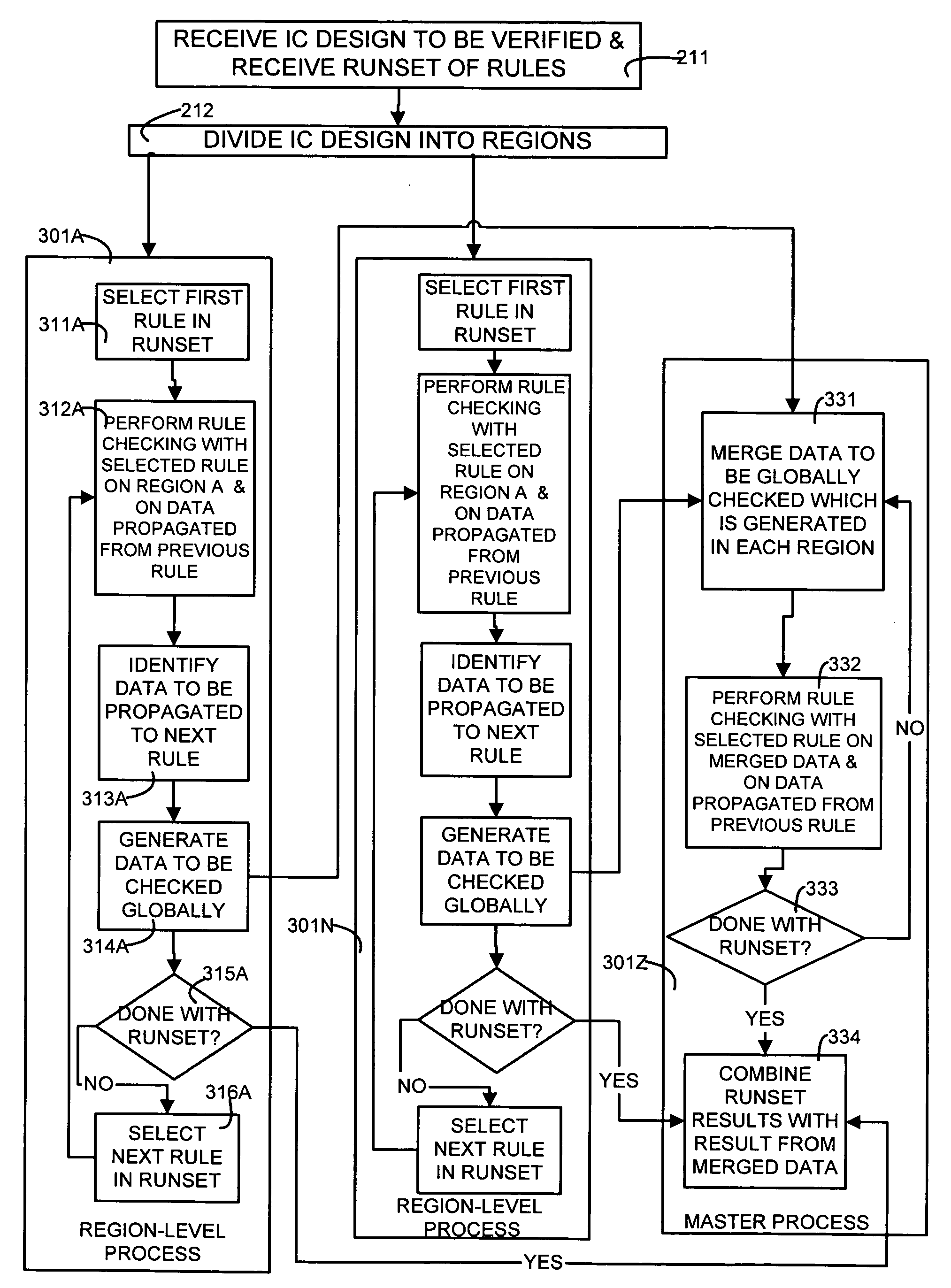
ActiveUS20060265675A1Computer aided designSoftware simulation/interpretation/emulationTheoretical computer scienceIntegrated circuit
When performing rule checking locally within any given region of a layout of an integrated circuit, certain data is generated to be checked globally, regardless of boundaries (hereinafter “to-be-globally-checked” data). The to-be-globally-checked data, resulting from execution of a given rule in each region of the IC layout, is merged across all regions, and the same rule (i.e. the given rule) is executed globally on the merged data. When an entire runset has been executed in all regions individually, and also executed globally on the merged data, the results thereof are all merged together to yield a final result of a complete execution of the entire runset over the entire IC layout. In some embodiments, certain additional data that could not be rule checked due to the presence of boundaries of adjacent regions is propagated between successive rules in each region.
Owner:SYNOPSYS INC
Testing method and system of standard cell library full model
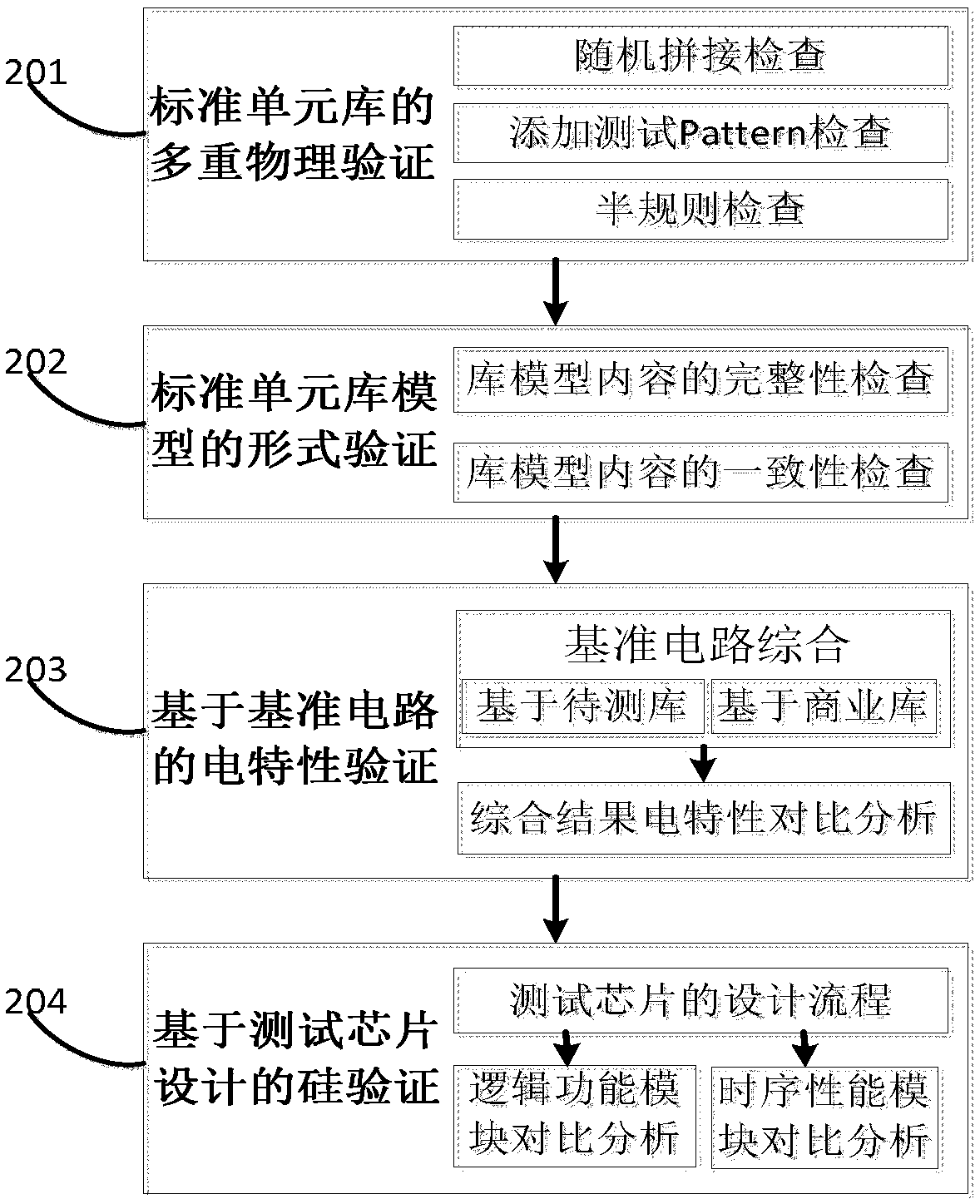
ActiveCN108830008AGuaranteed designGuaranteed successSpecial data processing applicationsComputer architectureFull model
The invention provides a testing method of a standard cell library full model. The testing method comprises the following steps that 201, multiple physical rule checking is conducted on standard celllayout; 202, form verification of a standard cell library model is performed; 203, Benchmark electrical properties of a standard cell library are verified; 204, chip design silicon verification of thestandard cell library is performed. The invention provides a testing system of the standard cell library full model. Testing verification of the standard cell library full model can be quickly completed at high coverage rate.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI
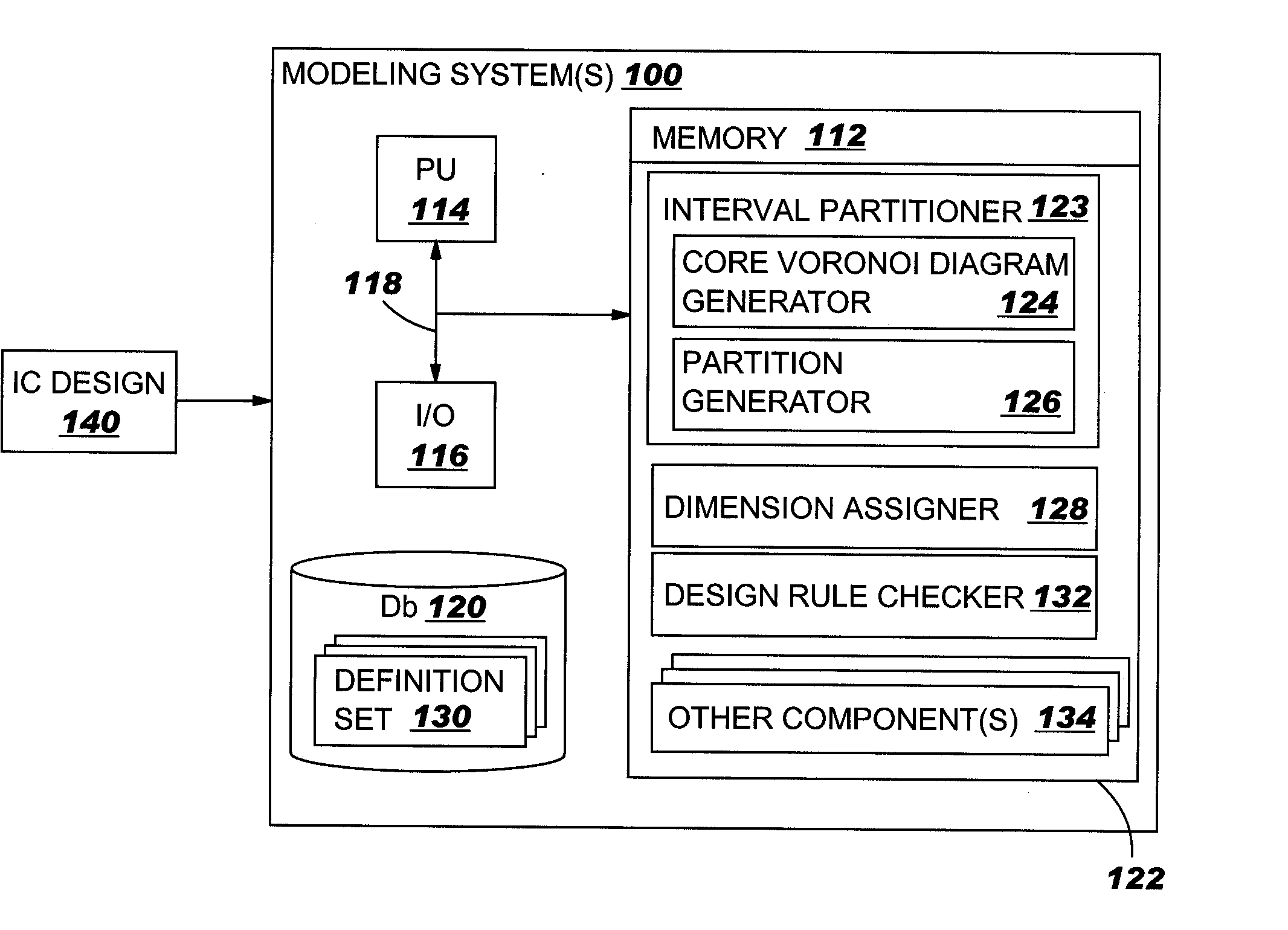
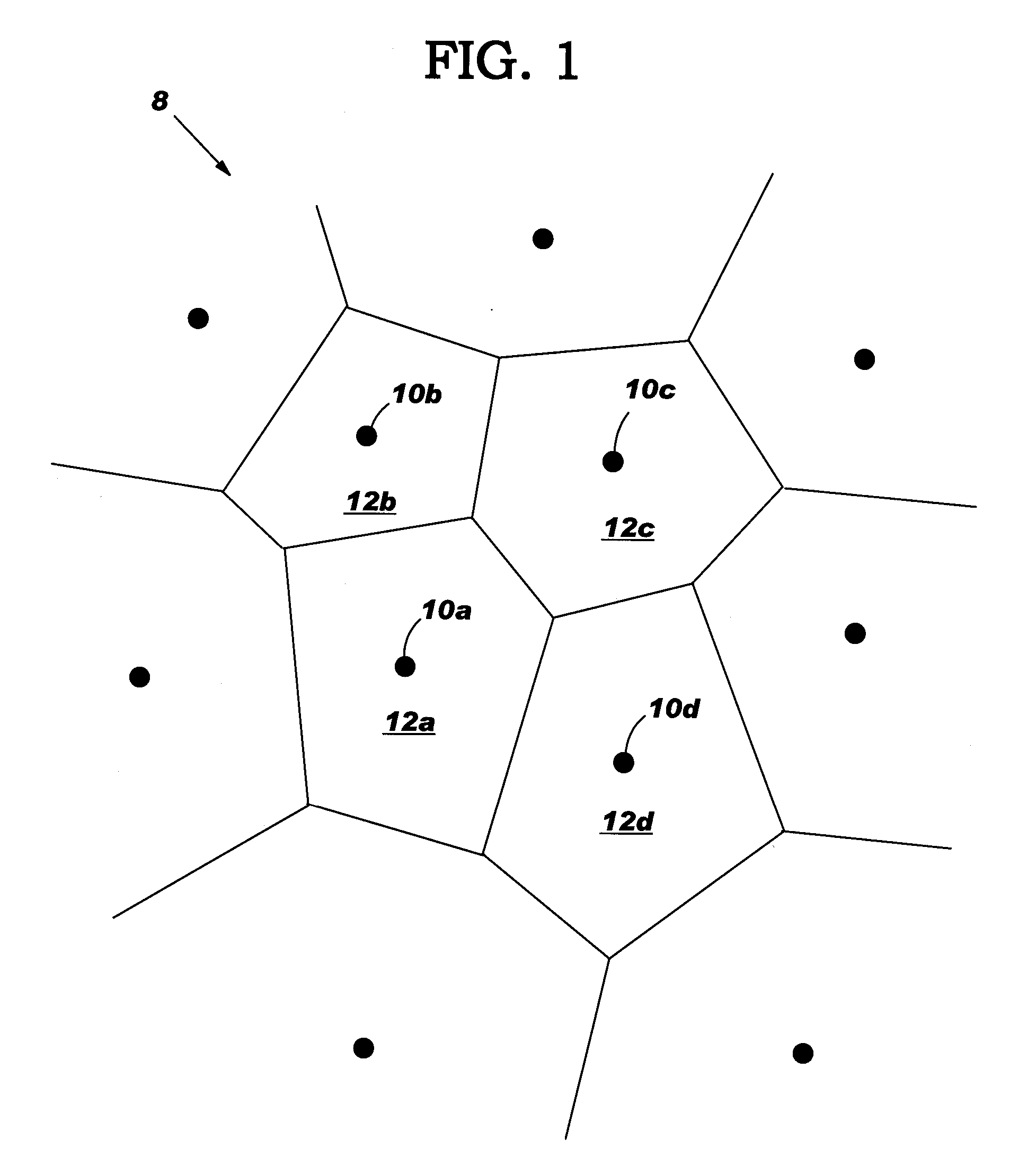
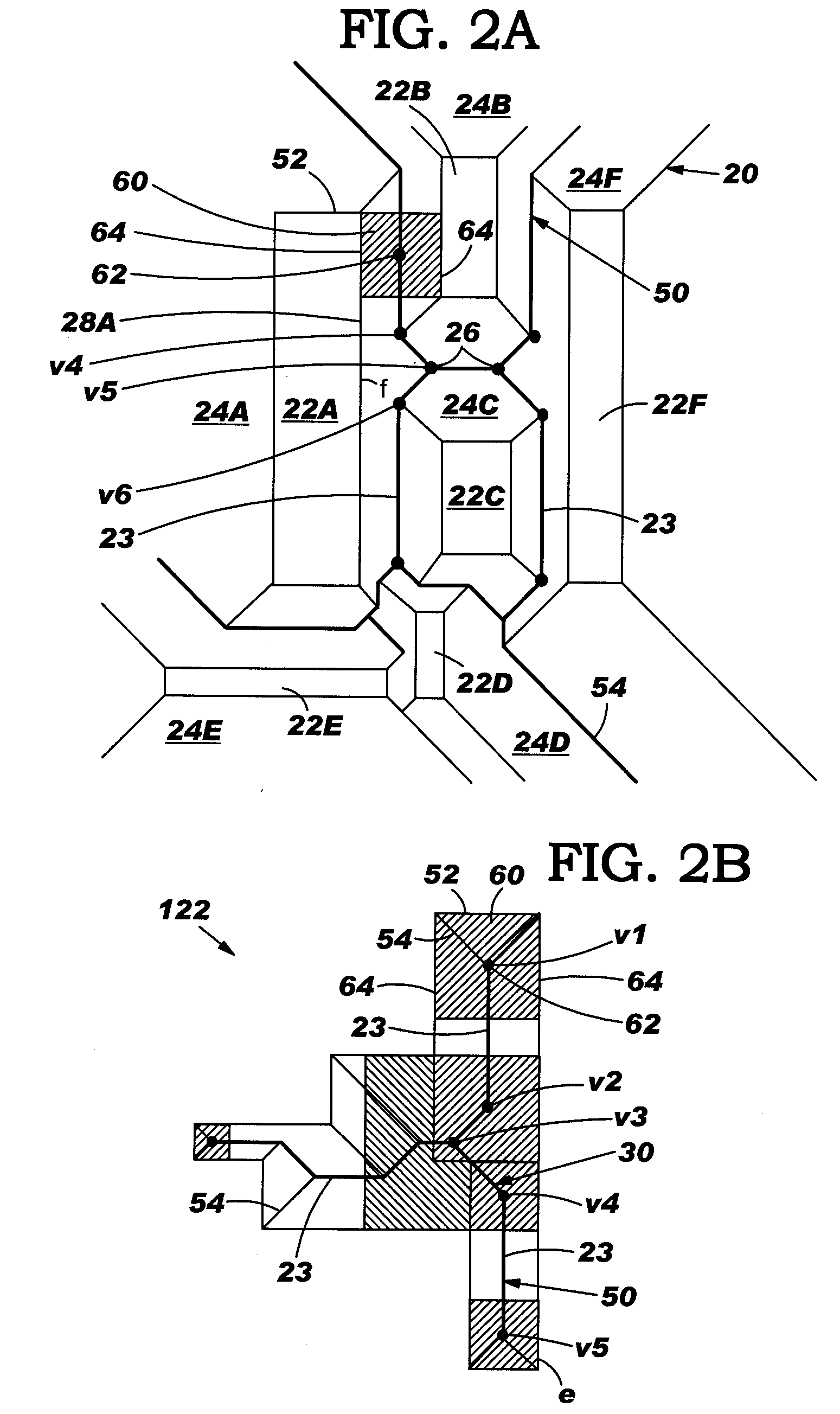
IC design modeling allowing dimension-dependent rule checking
ActiveUS20050172247A1Computer aided designSoftware simulation/interpretation/emulationComputer architectureDesign rule checking
A method, system and program product to model an IC design to include dimensions such as a local width and spacing of IC shapes in a consistent fashion. In particular, the invention uses a core portion of Voronoi diagrams to partition edges of a shape into intervals and assigns at least one dimension to each interval such as a local width and spacing. Dimension assignment can be made as any desirable definition set for width and spacing, e.g., numerical values or continuous dimension-dependent design rules. Design rule checking for dimension-dependent spacing rules given in any arbitrary functional form of width and spacing is possible. Application of the invention can be made anywhere the width and spacing of VLSI shapes play a role, e.g., relative to a single edge, neighboring edges, neighboring shapes, and / or for edges in more than one layer of the IC design.
Owner:GLOBALFOUNDRIES US INC
Method suitable for power data quality assessment and rule check
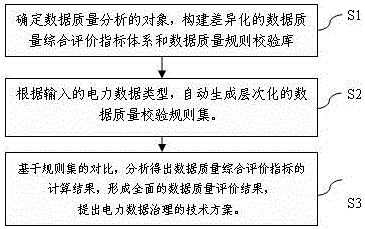
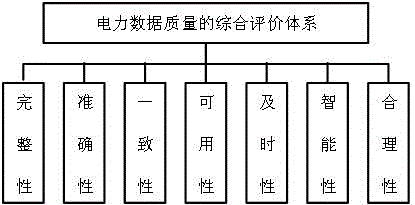
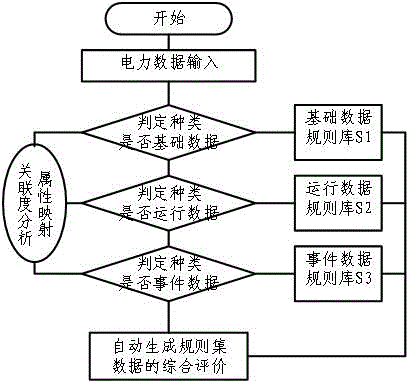
InactiveCN106649840AData processing applicationsSpecial data processing applicationsElectric power systemPower equipment
The invention discloses a method suitable for power data quality assessment and rule check. The method comprises the steps of establishing a differential data quality comprehensive evaluation index system and a data quality rule check library for a device object of a specific region in a power system and for data describing a basic feature, a running feature and an event process of a power device; and automatically generating a multilevel data check rule set based on the rule check library according to to-be-checked power data, thereby realizing automated data monitoring and check. According to the method, the power data quality comprehensive evaluation index system and the data quality rule check library are established and the multilevel power data rule set is automatically generated, so that the features of differential power data are comprehensively assessed and comprehensively evaluated; and the method is of important significance for realizing data quality management control and forming a technical scheme and a long-term mechanism of data management.
Owner:国网江西省电力有限公司经济技术研究院 +1
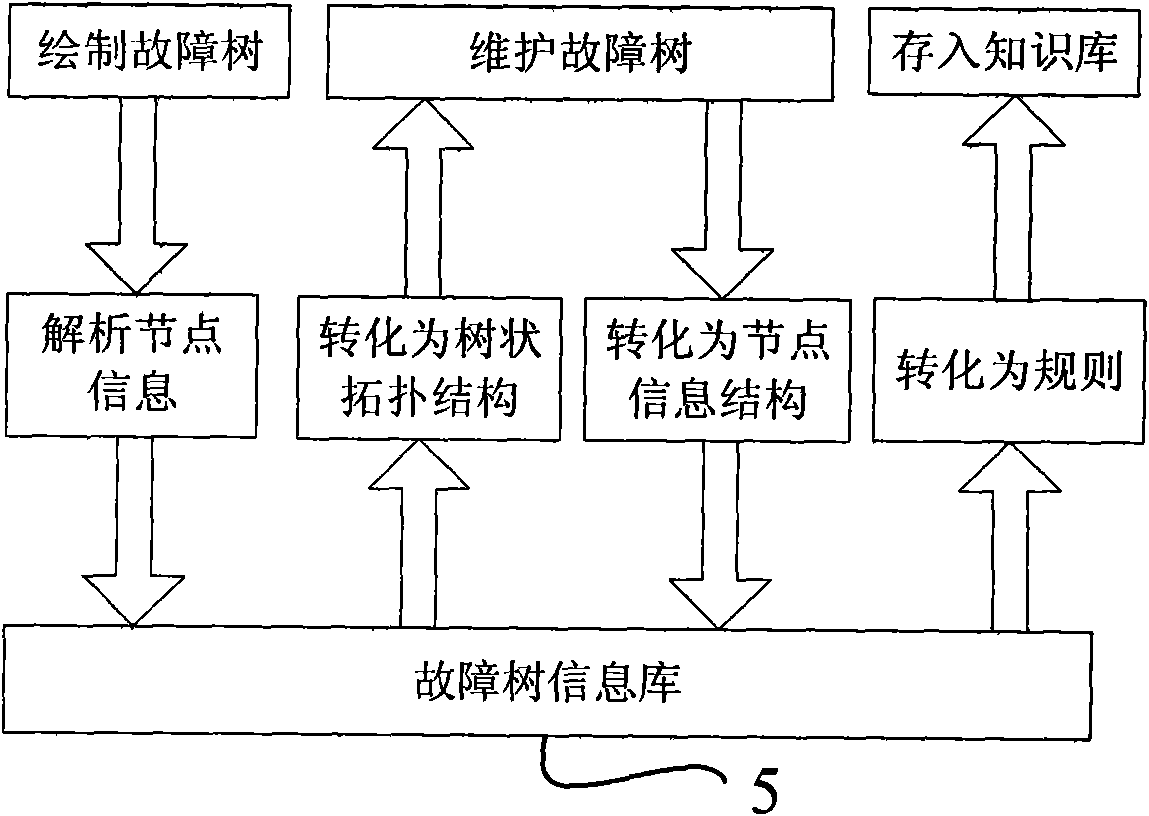
Fault diagnosis knowledge acquiring system
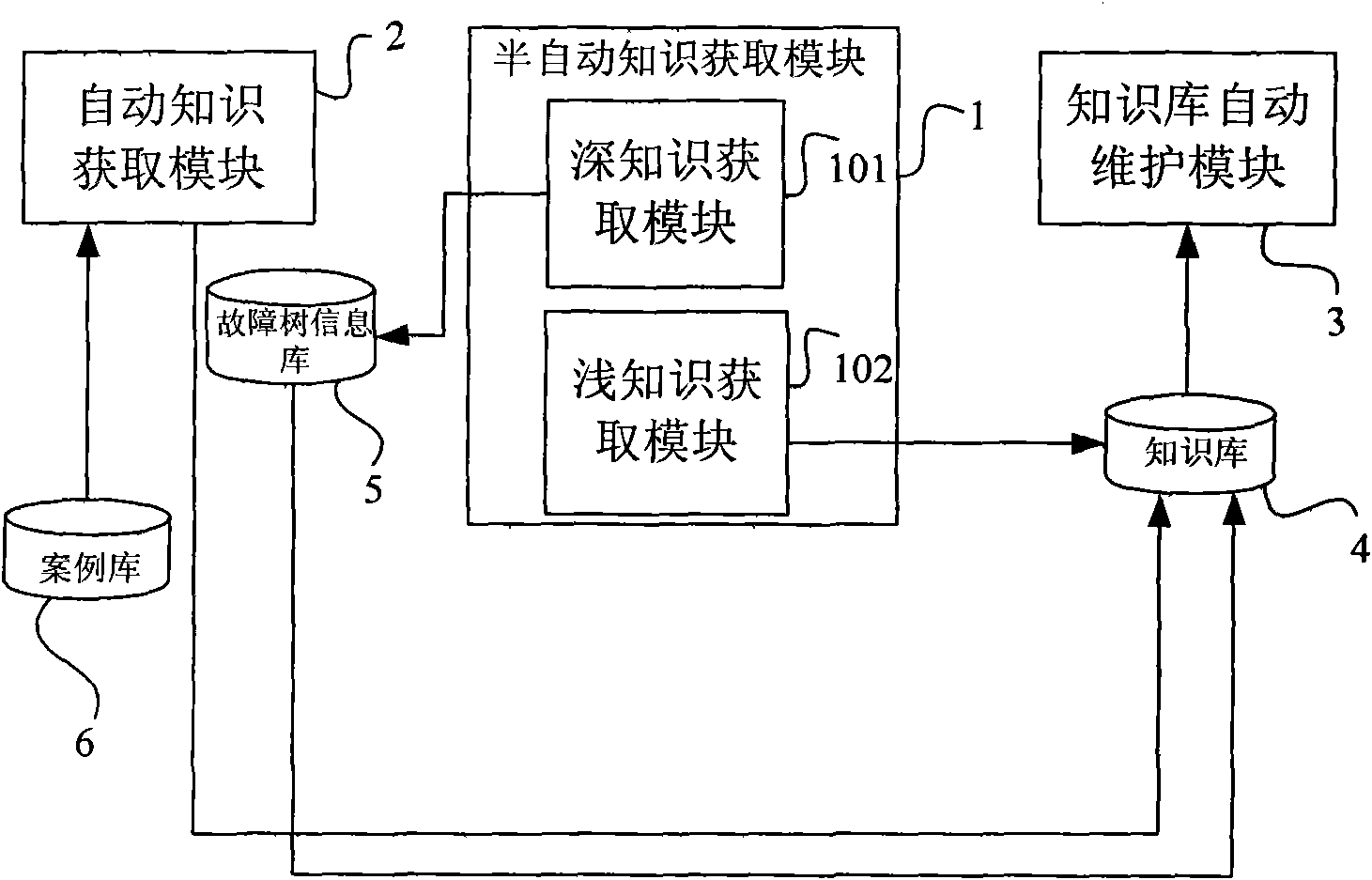
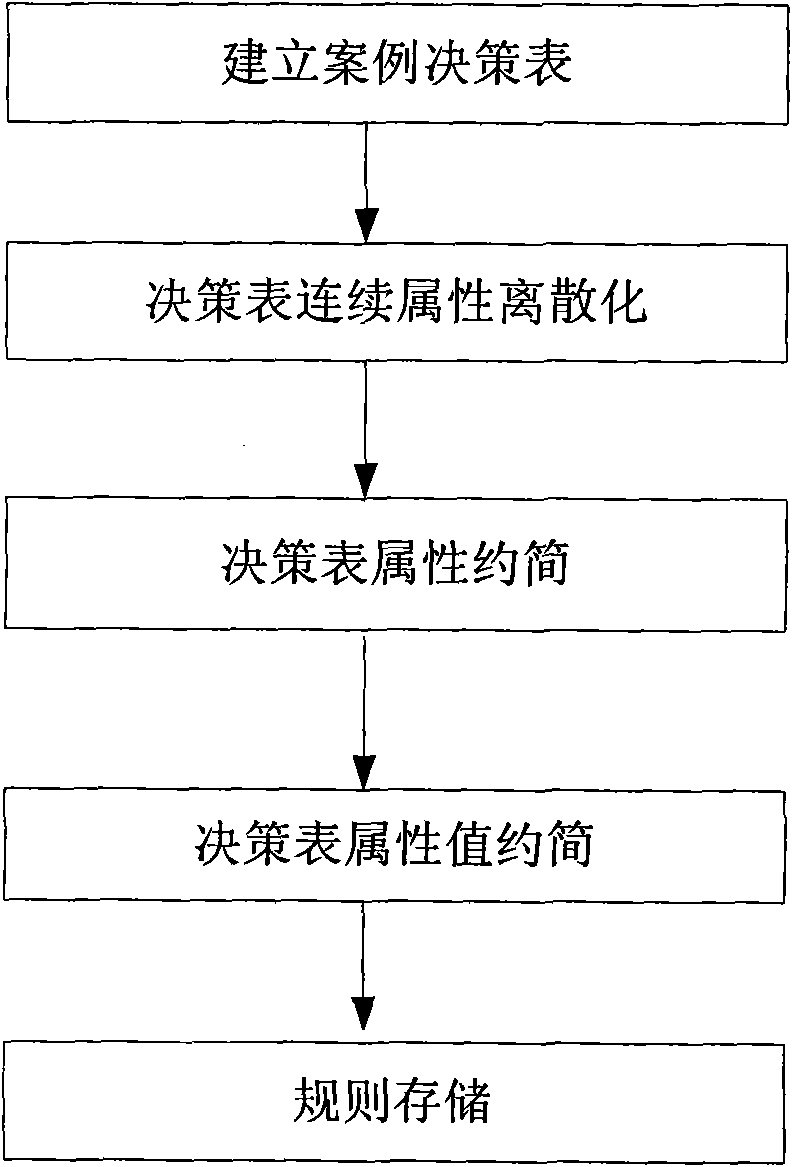
InactiveCN101877075AGuaranteed completenessAchieve optimizationKnowledge based modelsSemi automaticRough set
The invention discloses a fault diagnosis knowledge acquiring system, which comprises a semi-automatic knowledge acquiring module, an automatic knowledge acquiring module, an automatic knowledge base maintaining module, a knowledge base, a fault tree information base and a case base. The automatic knowledge acquiring module summarizes and concludes a new rule from a large number of cases stored in the case base according to the rough set theory and stores the acquired rule in the knowledge base, thus realizing automatic expansion of the knowledge base. The automatic knowledge base maintainingmodule realizes a function of automatically maintaining the knowledge base by using the character set closure and rule implication method, and the functional module can perform redundancy and circulation rule check on a rule base and provide the check result to the domain experts for judgment and processing. The invention acquires the known knowledge by using a fault tree, thereby not only indicating the logic relation in knowledge but also providing convenience for the user to maintain.
Owner:BEIHANG UNIV
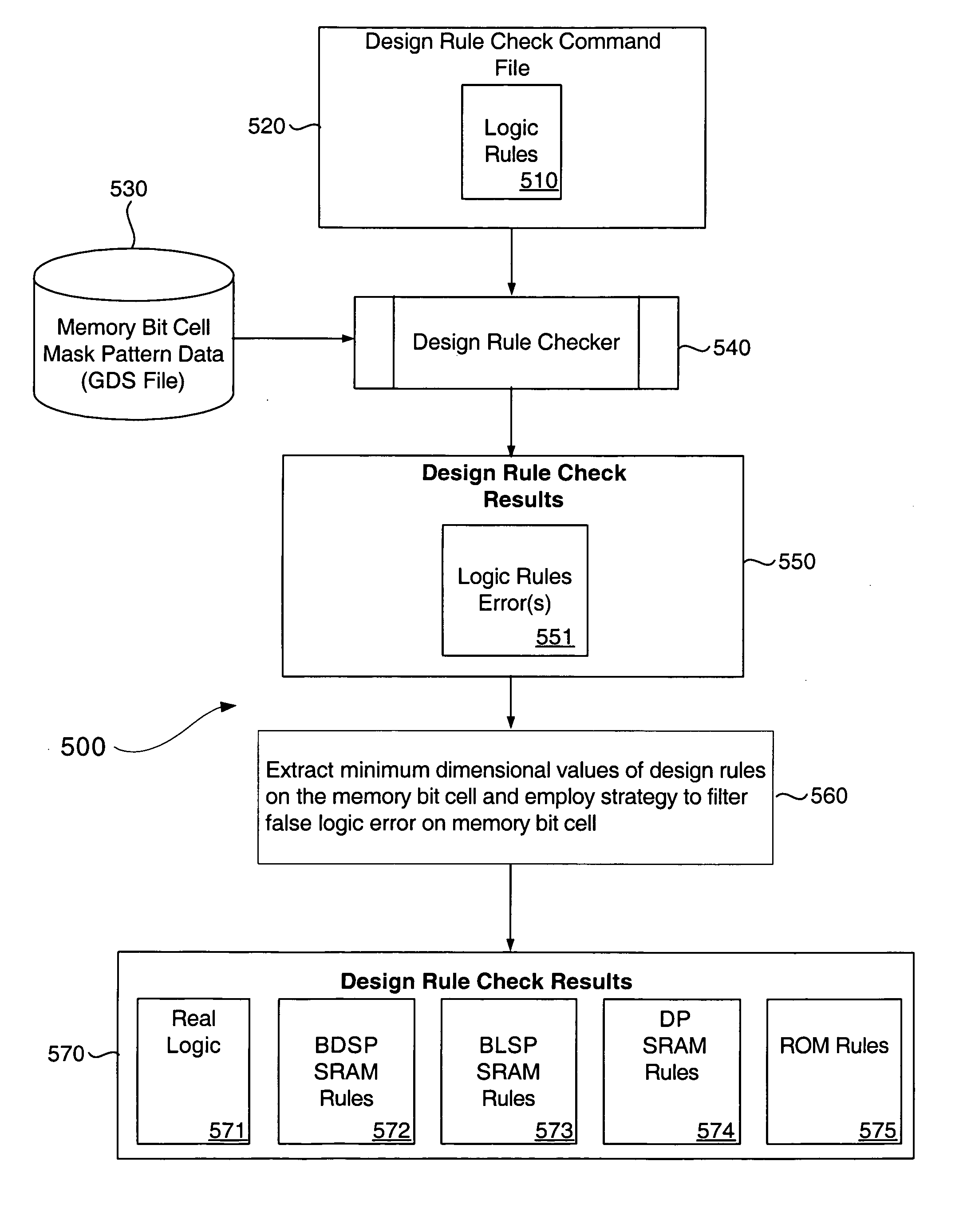
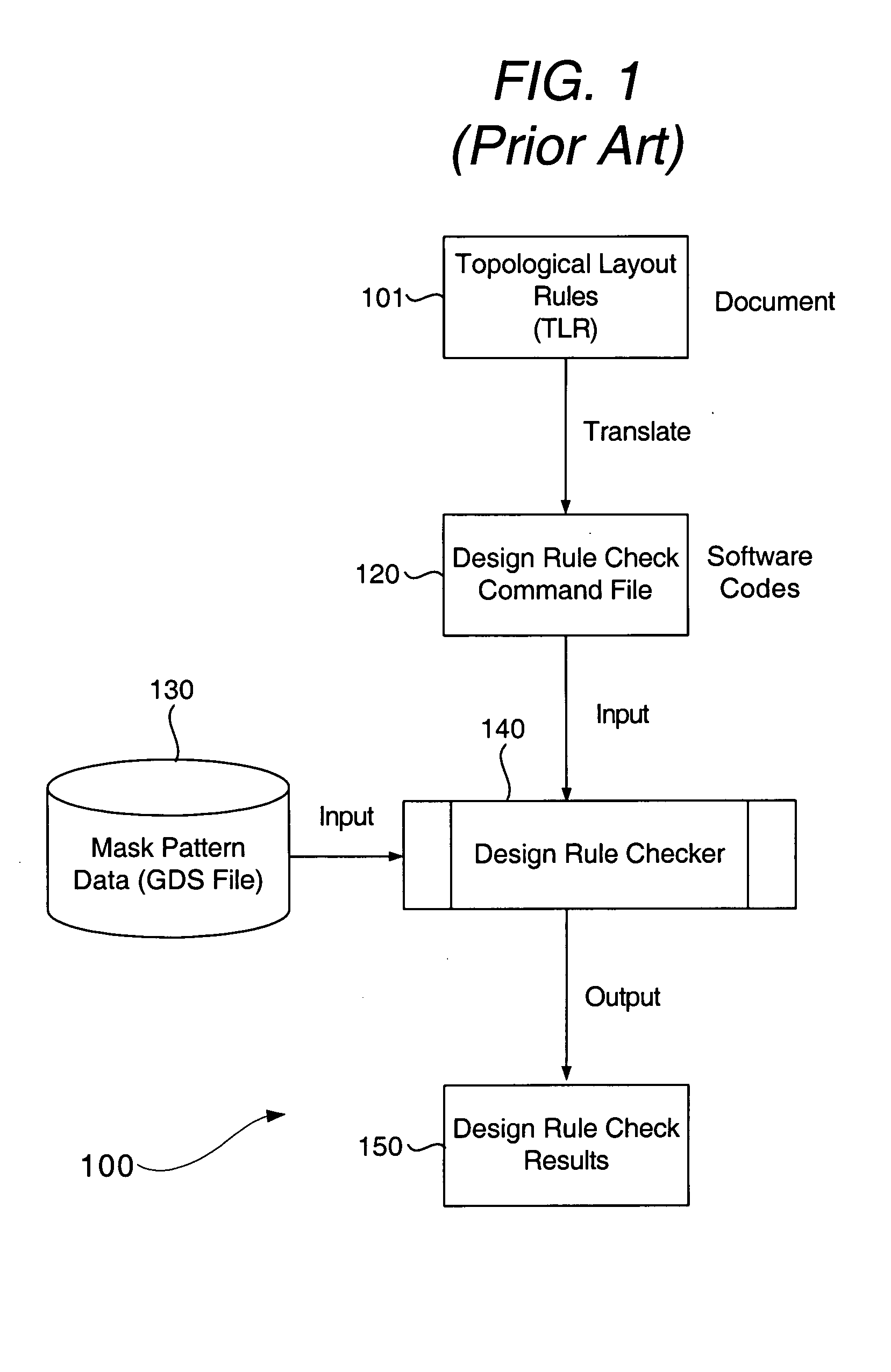
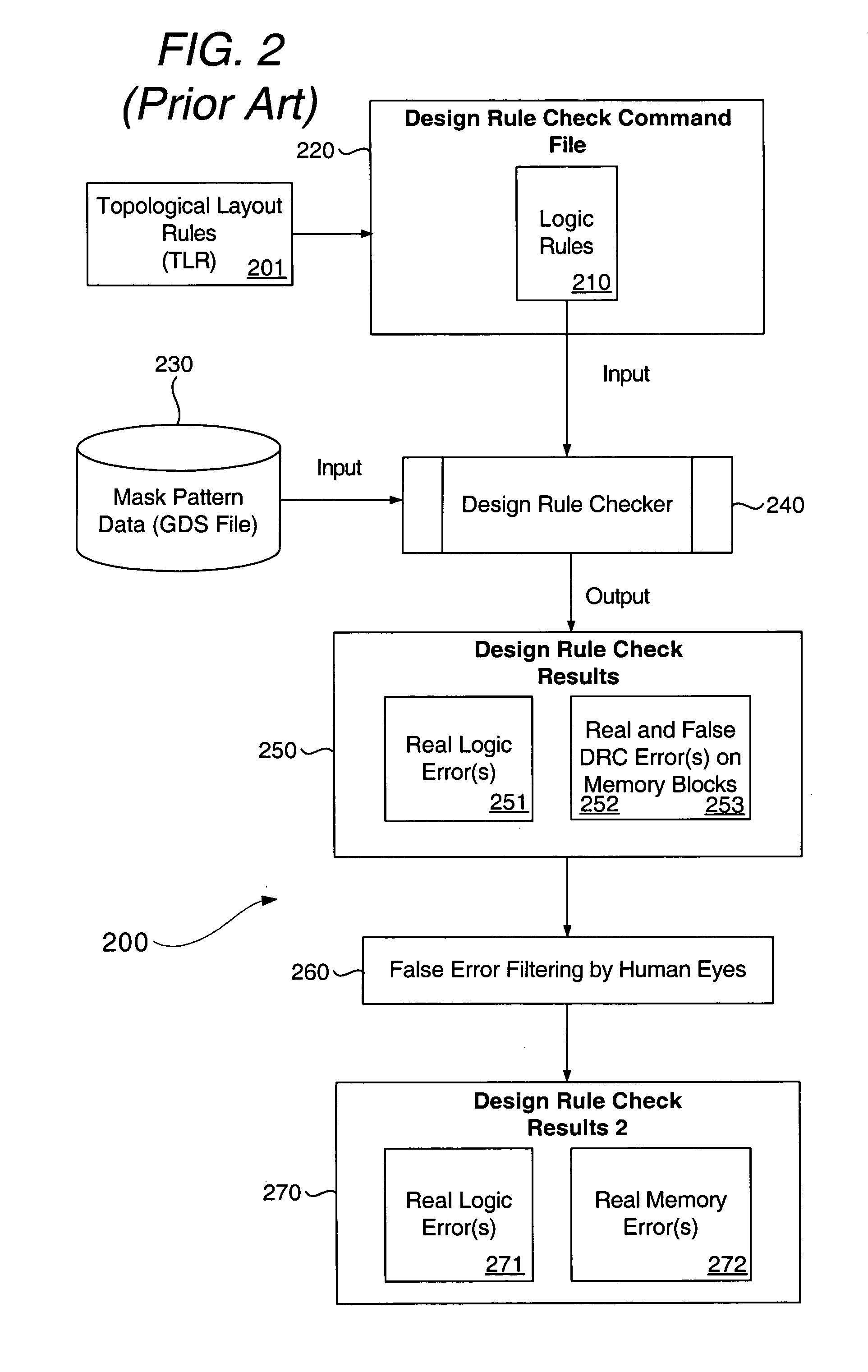
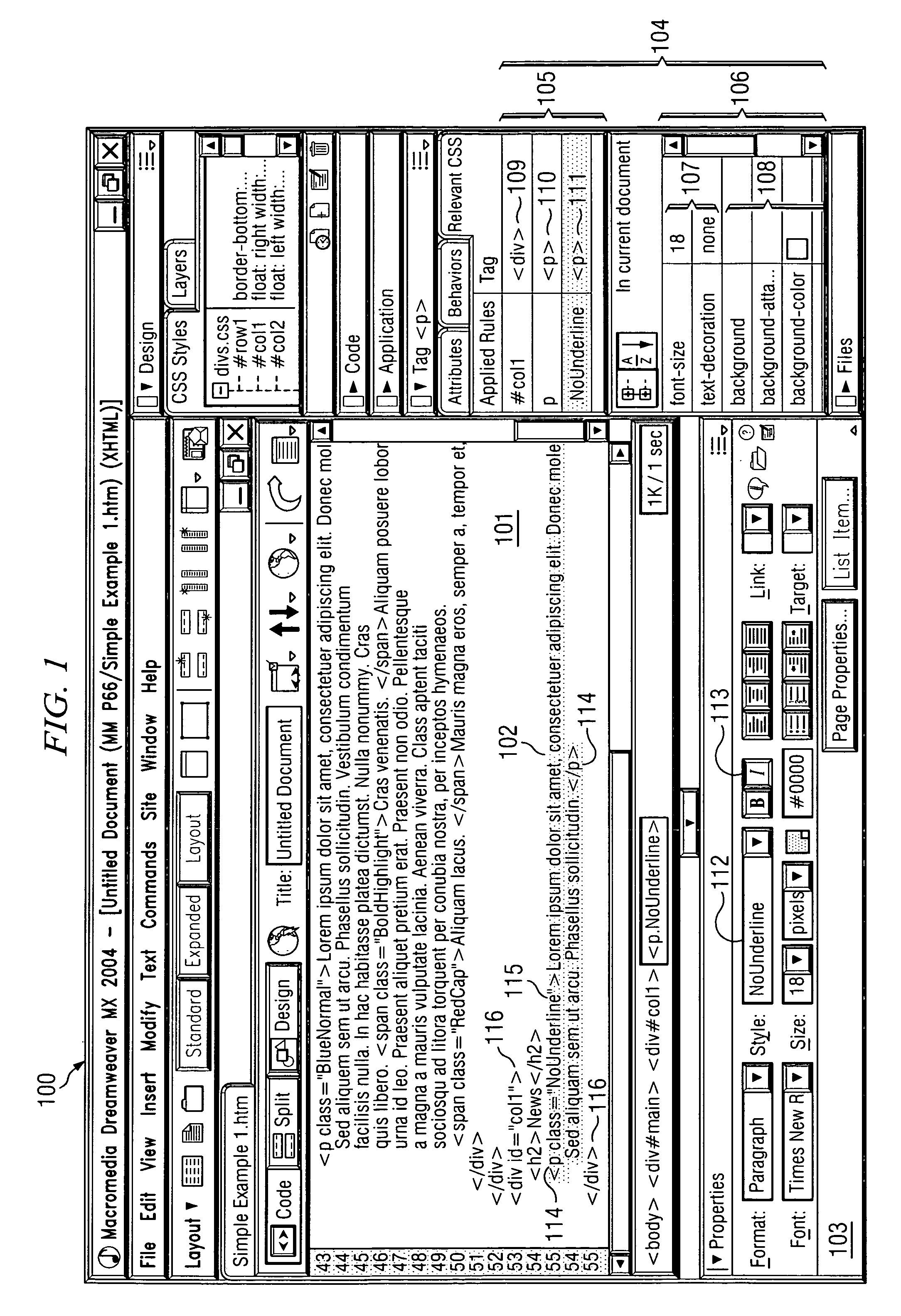
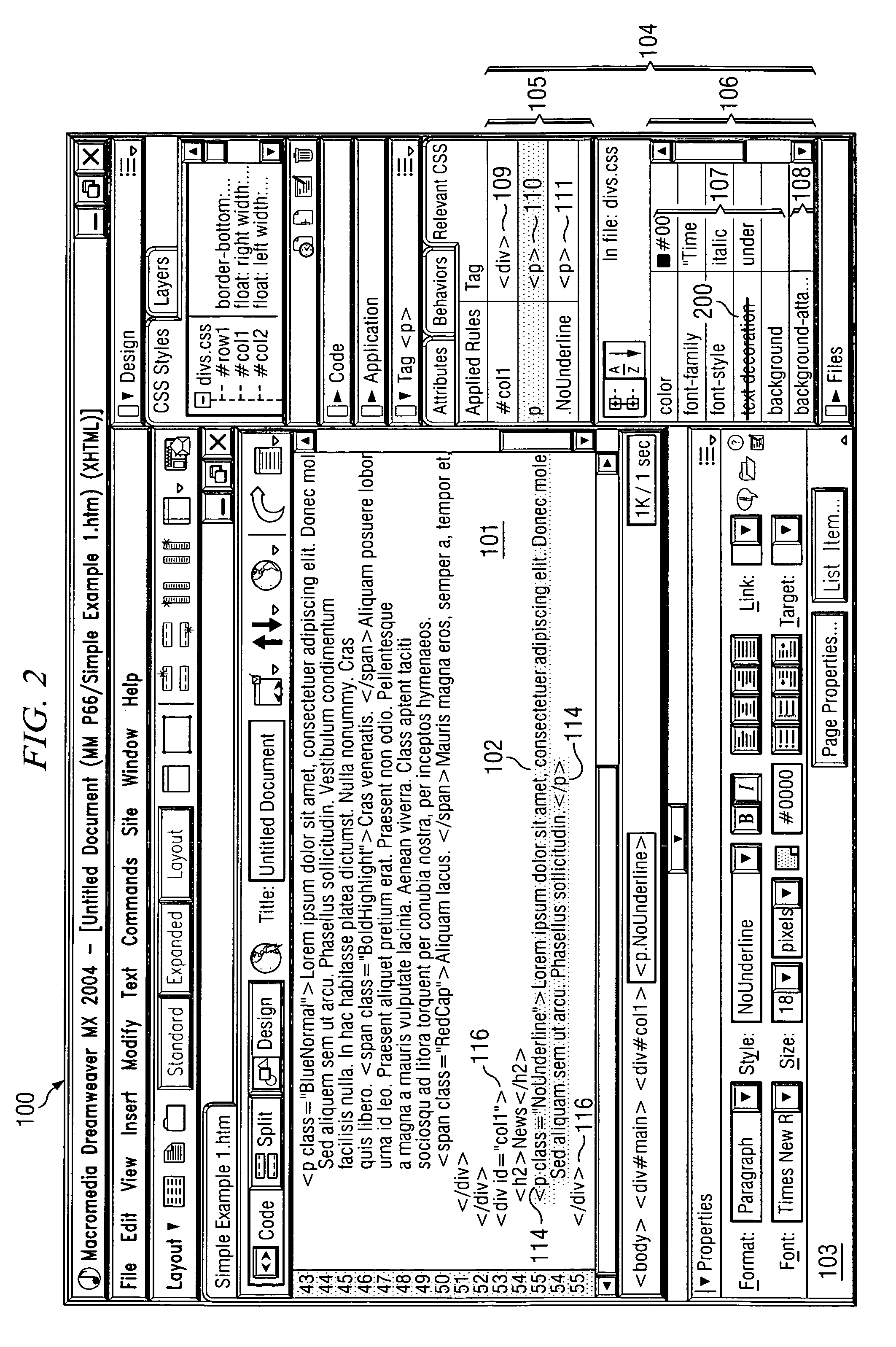
System & method for performing design rule check
InactiveUS20050086619A1Eliminate false errorError in design ruleComputer aided designSoftware simulation/interpretation/emulationComputer architectureIntegrated circuit layout
An improved system and method is disclosed for performing a design rule check on a proposed integrated circuit (IC) layout, and for creating customized design rule check command files. The individual layers of the IC (a system on chip—SOC) are separated into different regions having different kinds of features (i.e., memory or logic). Each different type of region is then analyzed in accordance with the customized design rule command file so that so-called “false errors” are eliminated. The invention thus improves, among other things, a development time for getting a design implemented in silicon.
Owner:UNITED MICROELECTRONICS CORP
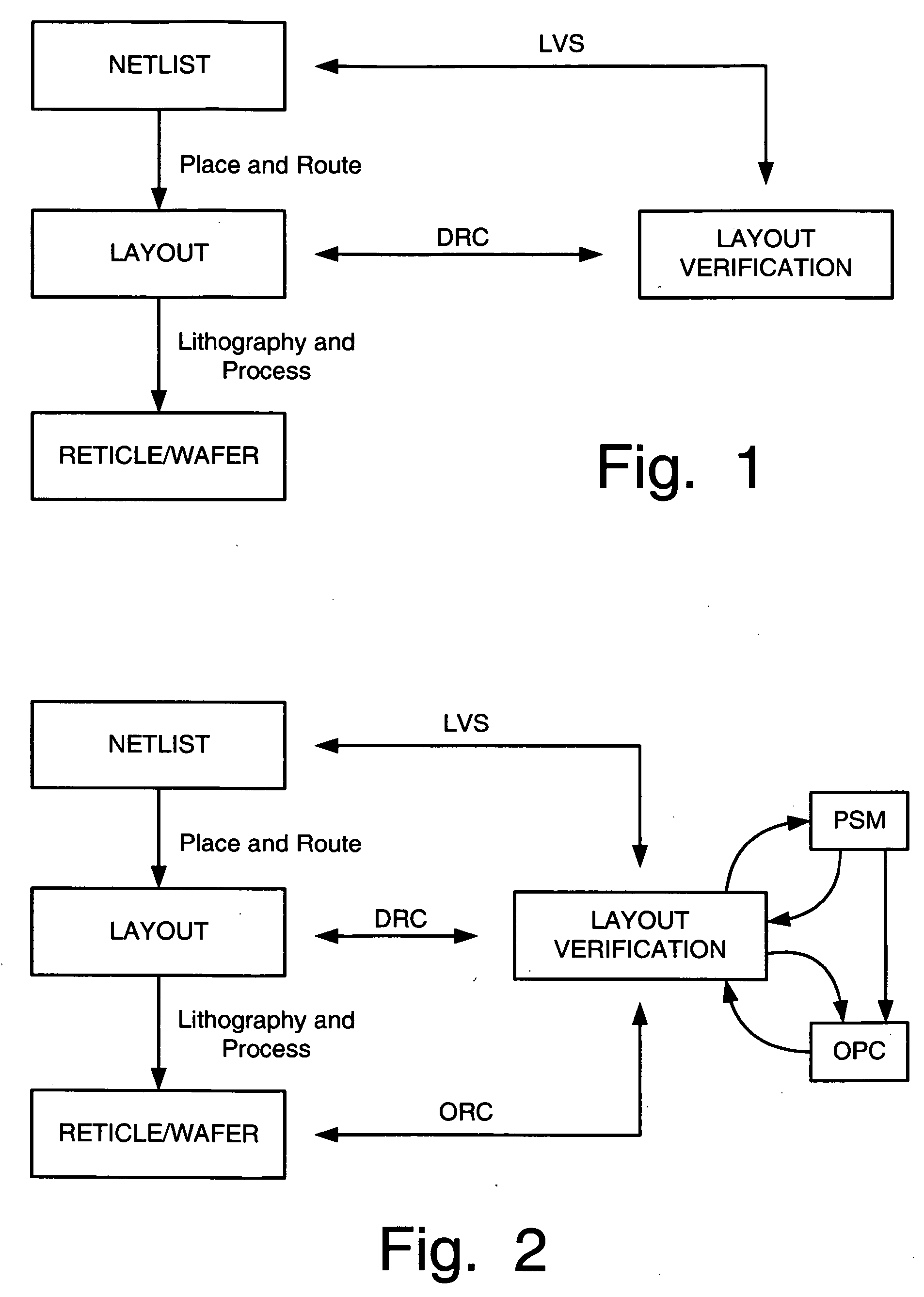
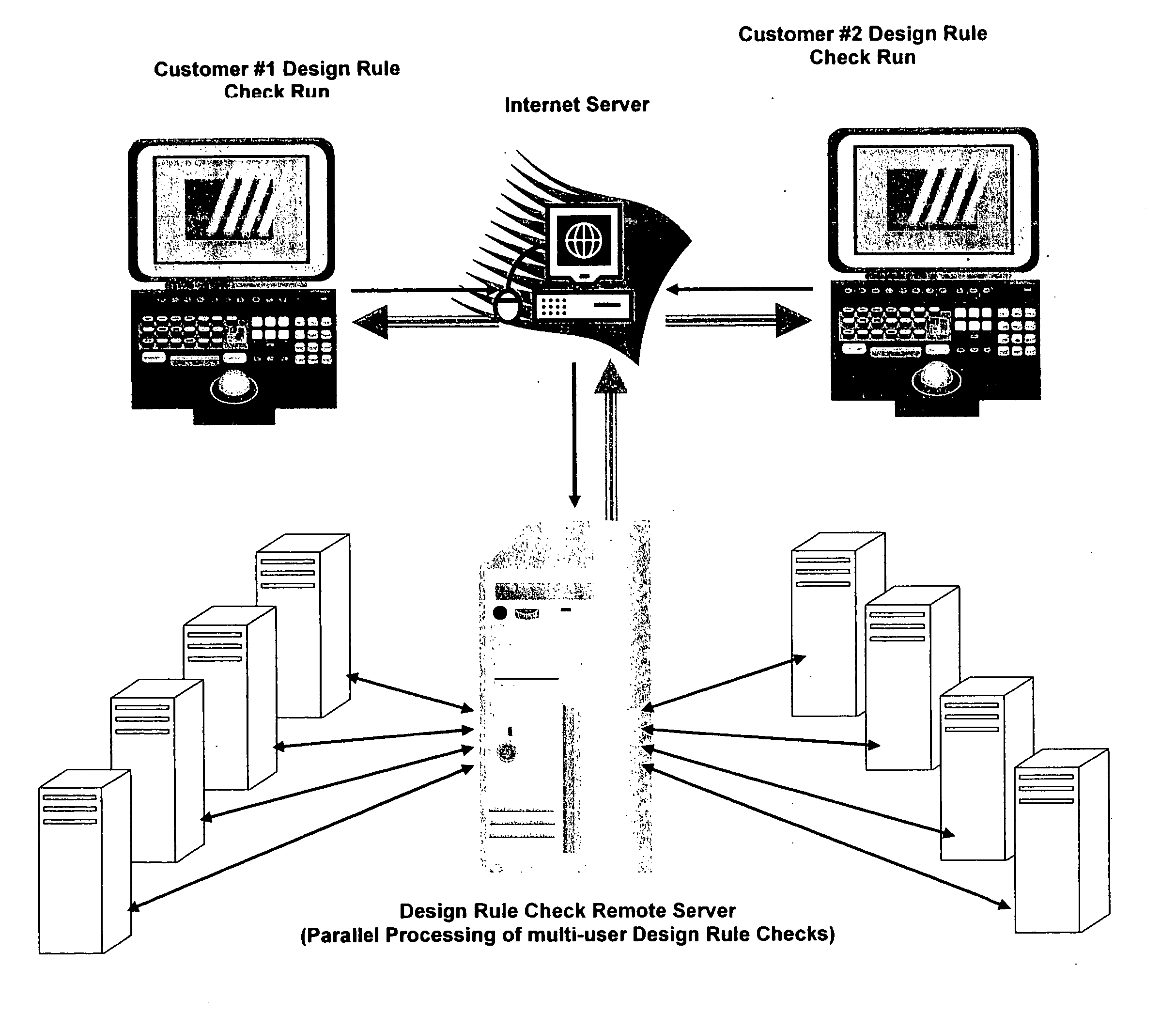
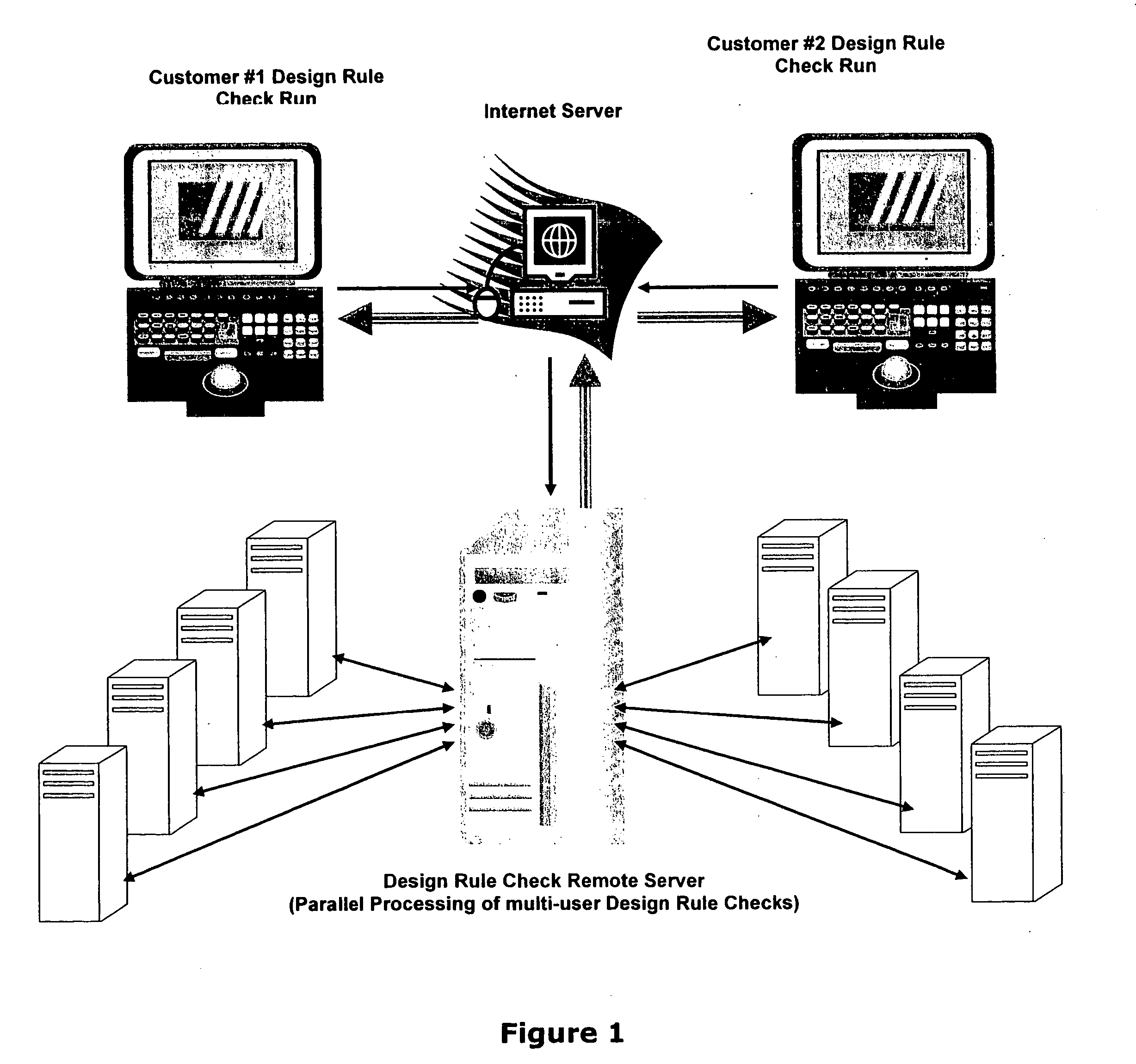
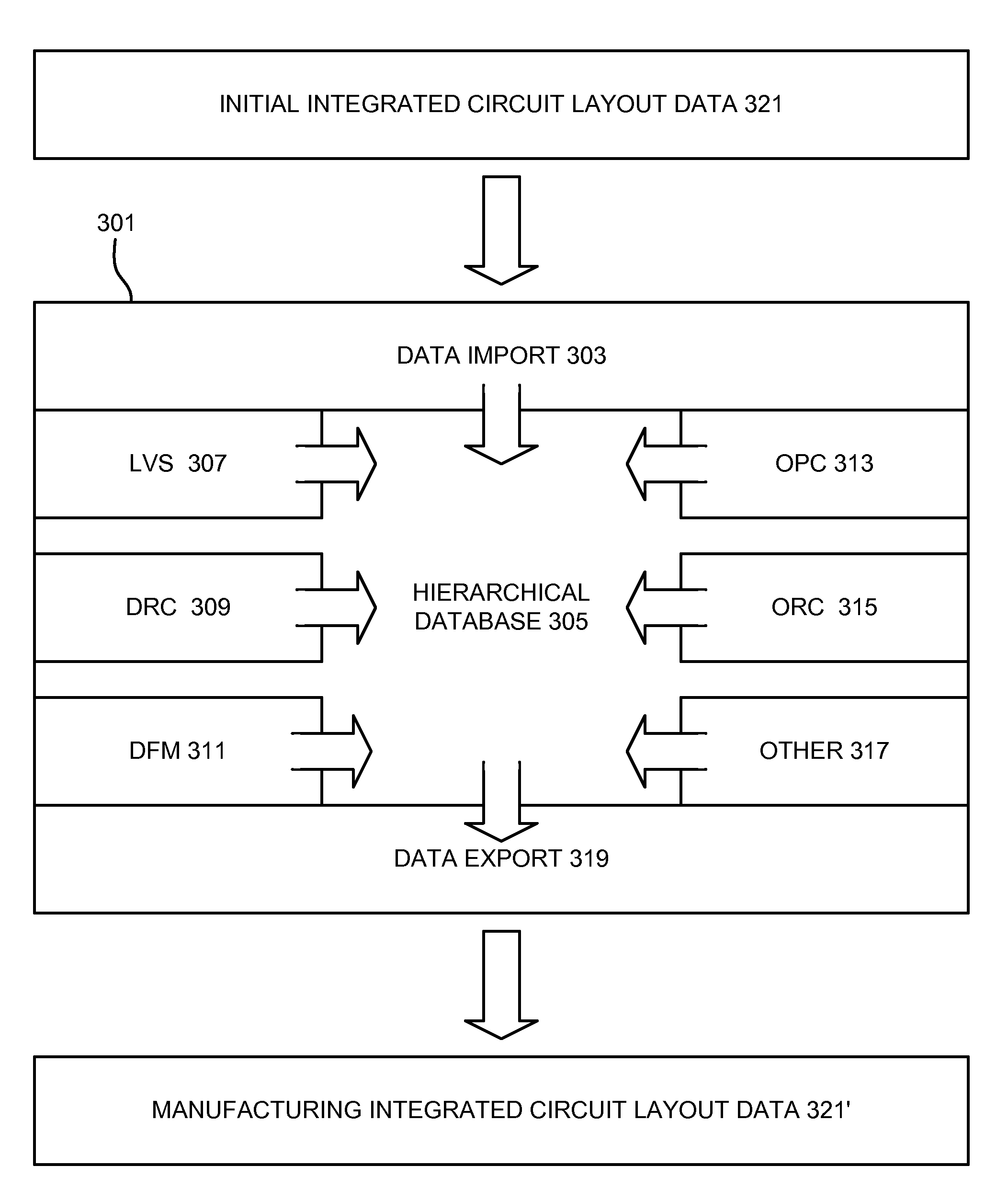
Design rule violations check (DRC) of IC's (integrated circuits) mask layout database, via the internet method and computer software
InactiveUS20060253813A1Fast resultsLow costComputer aided designSpecial data processing applicationsGuidelineSoftware design
This paper describes method and EDA (Electronic Data Automation) computer software invention for design rule violations check of mask layout database (integrated circuits layout) via the internet. The technique takes advantage of a unique algorithm to analyze the mask layout database to find mask layout polygons that are less than the minimum design rules (distances) that are determined by the fabrication process. The computer program then creates an output file that marks all design rule violations location and type. The input of the tool is a mask layout database (i.e.: layout block / s) that is made manually by a mask design specialist or automatically by automatic IC layout tools. The output of the software tool is a guideline mechanism and file to mark all design rule violations for correction. This markers file can be loaded into any industry's standard IC mask layout database editor for viewing and correction. The software performs on individual mask layout blocks and / or on hierarchical structure of mask layout blocks. The system also checks mask layout database incrementally, means only blocks that have been changed are checked. The system is activated via the internet using secured protocol. In order to reduce the cost of DRC (design rule check) computer program, corporations may log in to a main server to submit complete DRC (Design Rule Check) run. User point reference files at a local location (User's local computer) and setup all parameters on a web based interface. The system collects all local information and run a complete design rule check locally or on remote server. The system offer a web based control panel to execute all necessary setups for submitting design rule check over the internet using any secured internet browser like MS Explorer and Netscape. The system offers the option to run on a local machine (user's computer) or on the main server over the internet. The system also offers a PDA (Personal Digital Assistant) interface to launch DRC runs via industry's standard PDA's. The procedure is fully secured by 128 bit security protocol. The system supports existing industry standard rule decks like: Mentor's Calibre, Cadence's Assura and Synopsys's Hercules. All design rules can be easily imported from these rule decks to be used by DRC program on the main server. All necessary files including mask layout GDSII (or GSIII) file and technology file are securely encrypted using 128 bit protocol and send to the remote server. These files are decrypted on the remote computer and submitted for design rule check. The main remote server is distributing the task among other computer system for advanced parallel processing to achieve fast results. All results log files are encrypted using 128 bit security protocol and available for download by the user. In case of local design rule check the results files are available on the user's local machine. This approach eliminates the purchase of a full local license and enables affordable price for small and medium size chip design firms. This fact significantly reduces integrated circuits design cost and time to market factor for chip design corporations, enabling faster deliveries to their end customers.
Owner:MICROLOGIC DESIGN AUTOMATION
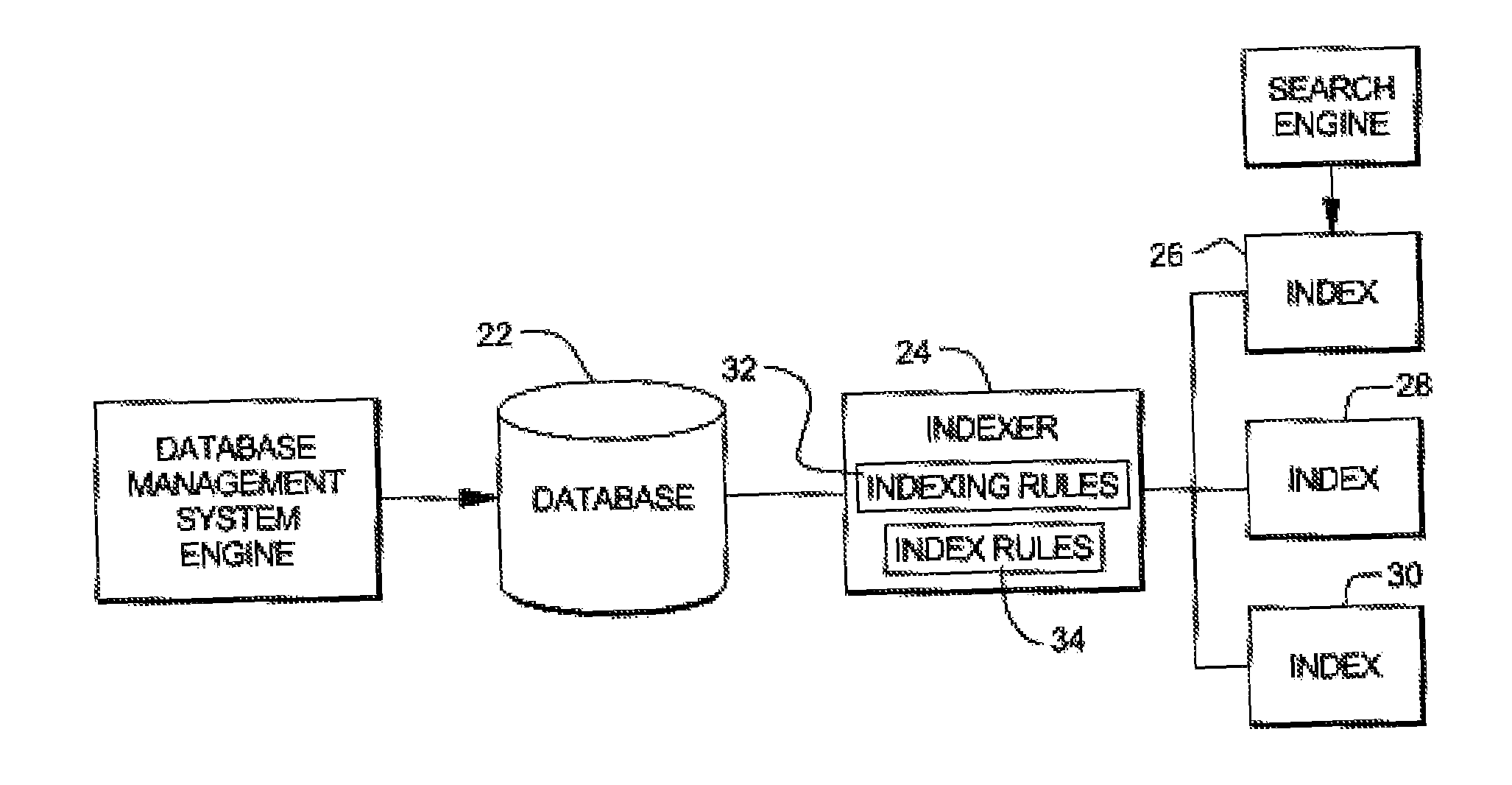
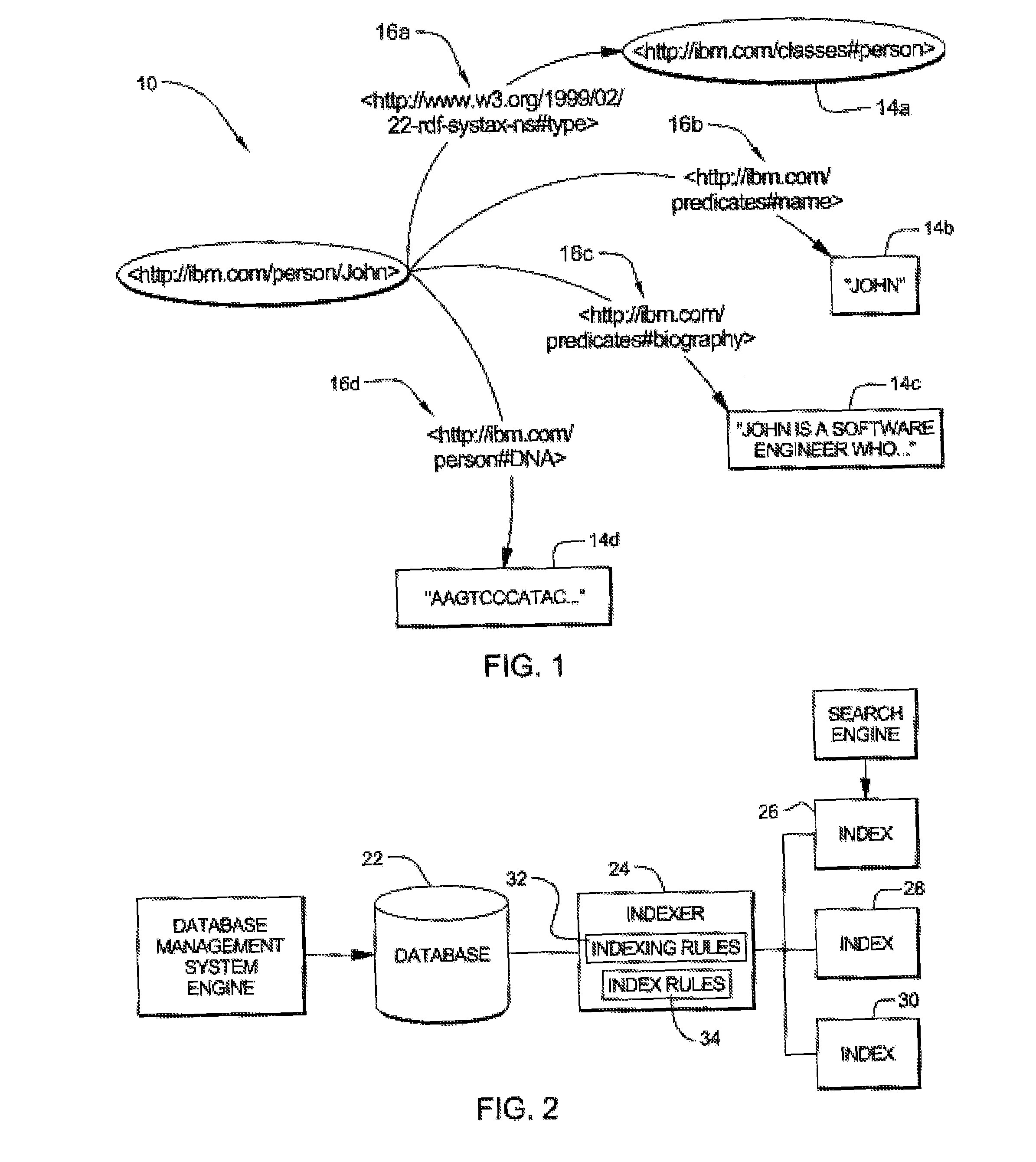
Ontology Based Text Indexing
InactiveUS20080288442A1Save spaceShorten the timeDigital data information retrievalSpecial data processing applicationsRule setsTheoretical computer science
A method and system are disclosed for indexing a set of statements, such as RDF statements, that are described in accordance with a specified ontology. The method comprises the steps of defining a set of indexing rules, and using these indexing rules to examine the statements to identify selected ones of the statements and to generate one or more indices from said selected ones of the statements. In a preferred embodiment, the rules match certain predicates of RDF statements to certain indices. Also, preferably, an RDF storage system may be configured with said set of indexing rules. When RDF statements are added to the RDF storage system, each statement is examined by the indexing subsystem. If the predicate of a statement matches one of the predicates of said set of indexing rules, that rule is applied to the statement.
Owner:IBM CORP
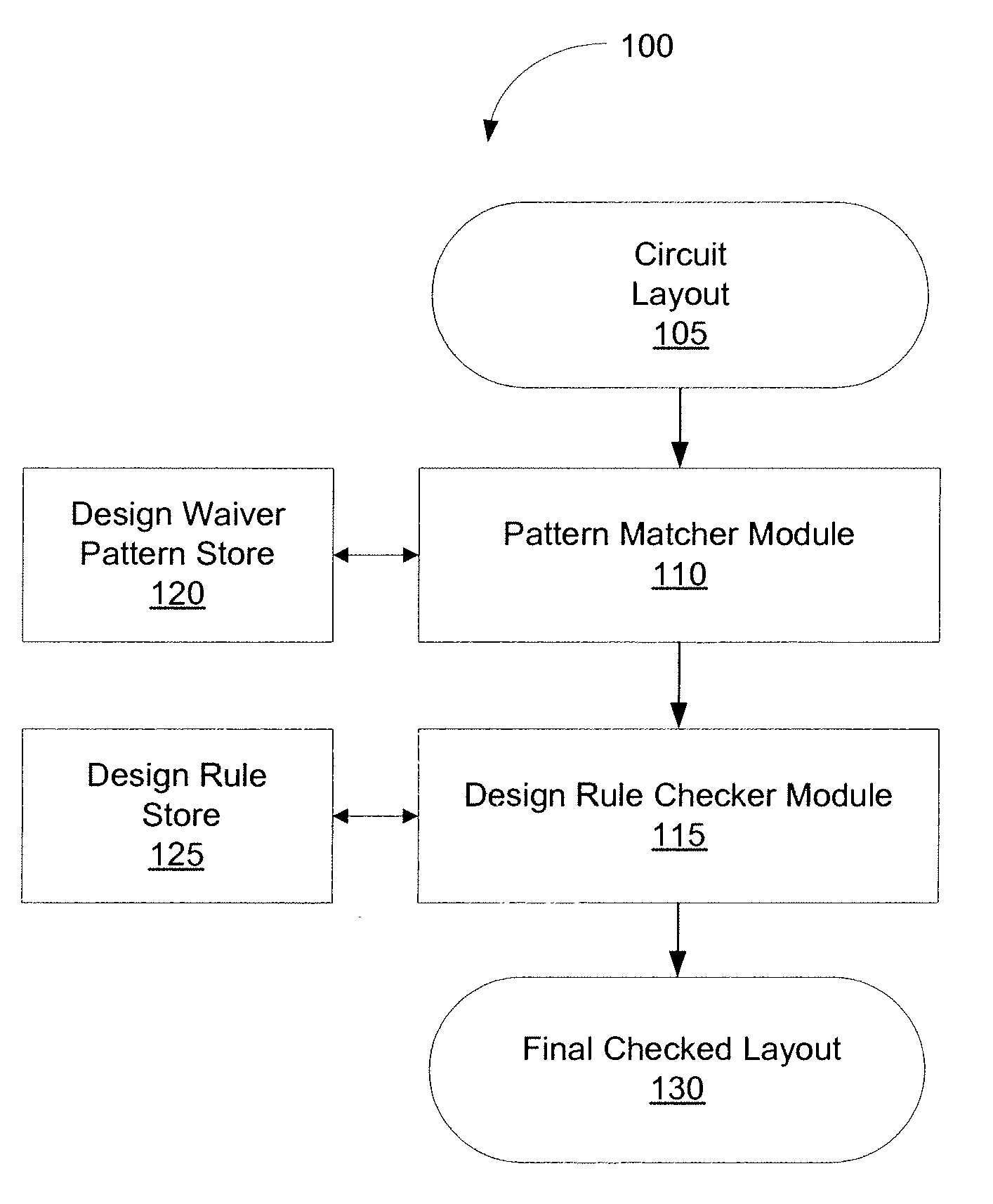
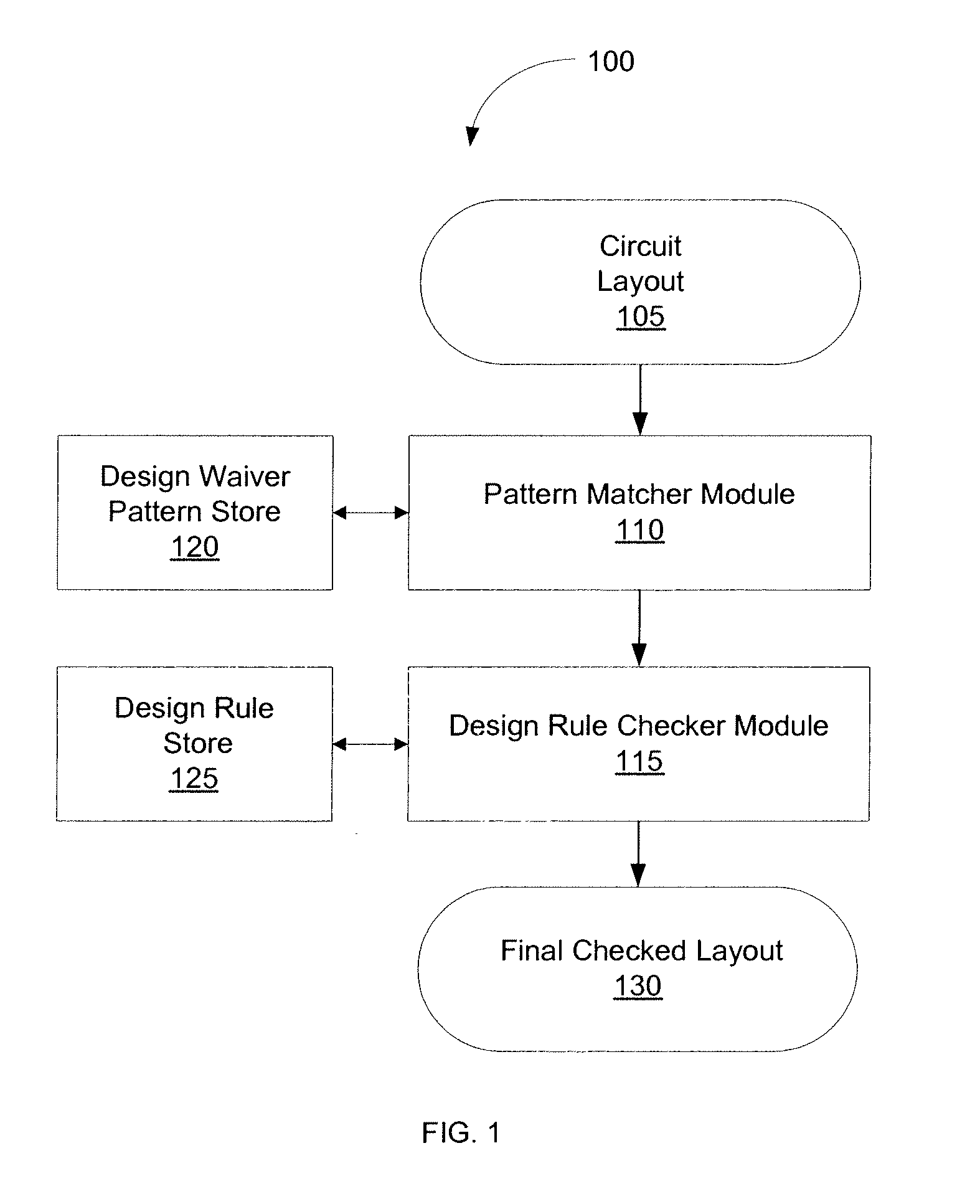
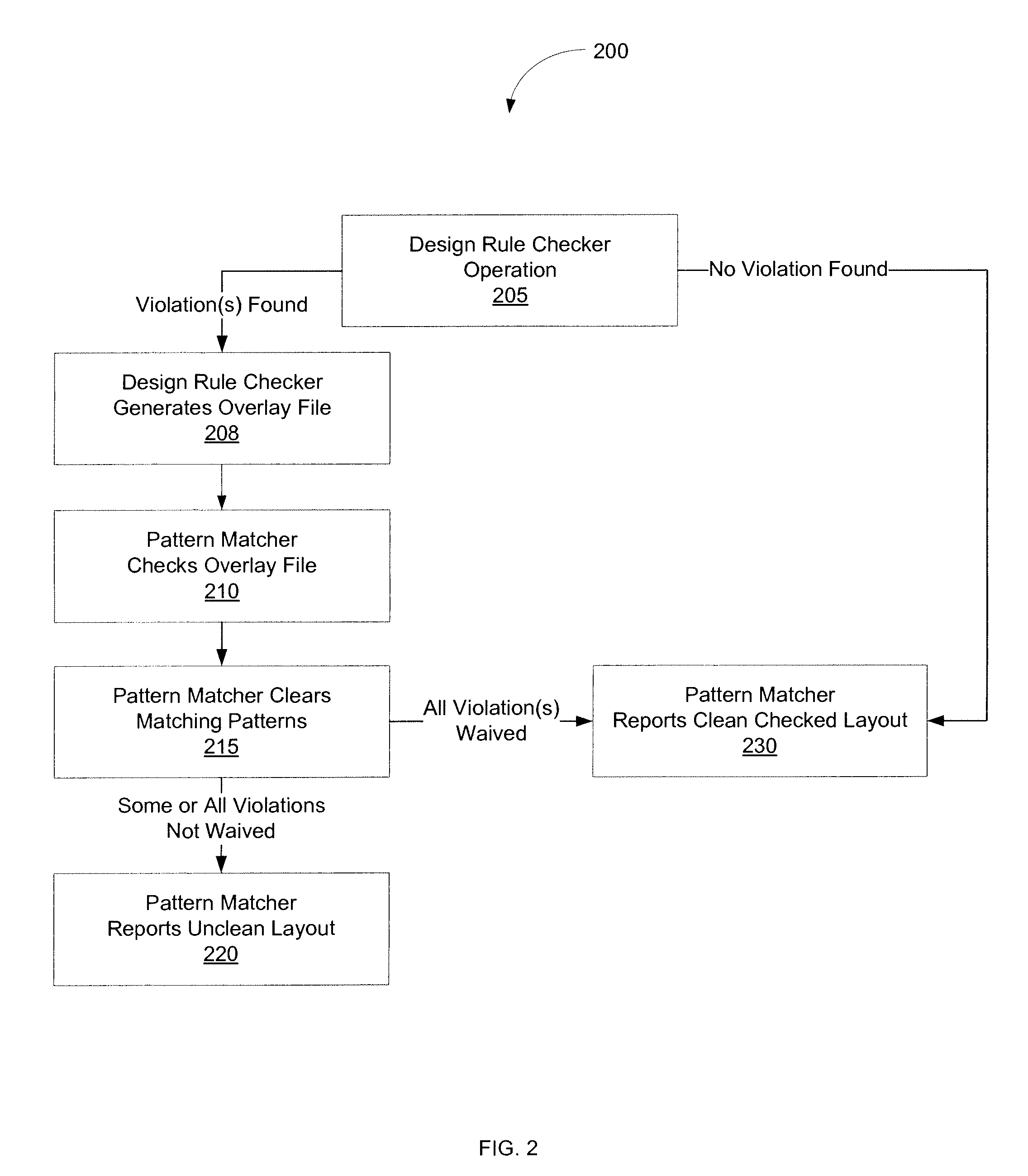
Method and system for design rule checking enhanced with pattern matching
ActiveUS20100064269A1Computer aided designSoftware simulation/interpretation/emulationIntegrated circuitDesign rule checker
According to various embodiments of the invention, systems and methods for design rule checking enhanced with pattern matching is provided, wherein the design rule checker ignores certain patterns of the layout that violate design rules during validation. One embodiment of the invention includes receiving a first layout pattern that containing the original layout of an integrated circuit pattern. The pattern matcher processes the layout pattern and designates certain patterns of the integrated circuit pattern that meet a design waiver. The pattern matcher generates a second layout pattern with the waived patterns marked. The design rule checker subsequently processes the marked layout pattern and validates all but the marked patterns of the second layout pattern against a set of specified design rules. The design rule checker generates a third layout pattern with only the unmarked patterns of the layout being validated against the set of specified design rules.
Owner:CADENCE DESIGN SYST INC
Relevant rule inspector for hierarchical documents
ActiveUS7769773B1Digital data processing detailsSemi-structured data mapping/conversionSystem identificationDocumentation
A development environment is described that includes identifying relevant code or rules applicable to various elements of a hierarchical document and displaying the relevant code or rules to a user within a display interface of the development environment. The system recognizes document elements highlighted by a user and searches through a data structure of the code or rules applied to the hierarchical document for code or rules that expressly reference the element selected by the user. The system then searches the data structure of the code or rules applied to the parent elements of the selected element. The discovered code or rules are then displayed to the user in the development environment along with any properties that are associated with the code or rules. The development system determines which of the properties do not apply to the selected element and render a marker indicating the non-applicability of that property.
Owner:ADOBE INC
Programmable Design Rule Checking
InactiveUS20090106715A1Computer aided designSoftware simulation/interpretation/emulationEngineeringDesign rule checking
An analog design-rule-check tool analyzes a microdevice design, such as an integrated circuit design, to identify occurrences of geometric elements that share a specified relationship. When the tool identifies such an occurrence of these geometric elements, it will associate or “cluster” these geometric elements together into an identifiable unit. For specified “clusters” of geometric elements, the analog design-rule-check tool will then determine the value of a measurement or measurements required by a user. Once the analog design-rule-check tool has determined the necessary measurement values, it will use those values to evaluate the function describing a model.
Owner:MENTOR GRAPHICS CORP
Method for correcting layout pattern
ActiveUS20110029939A1Reducing blind spot issueComputer aided designSoftware simulation/interpretation/emulationValidation ruleElectrical and Electronics engineering
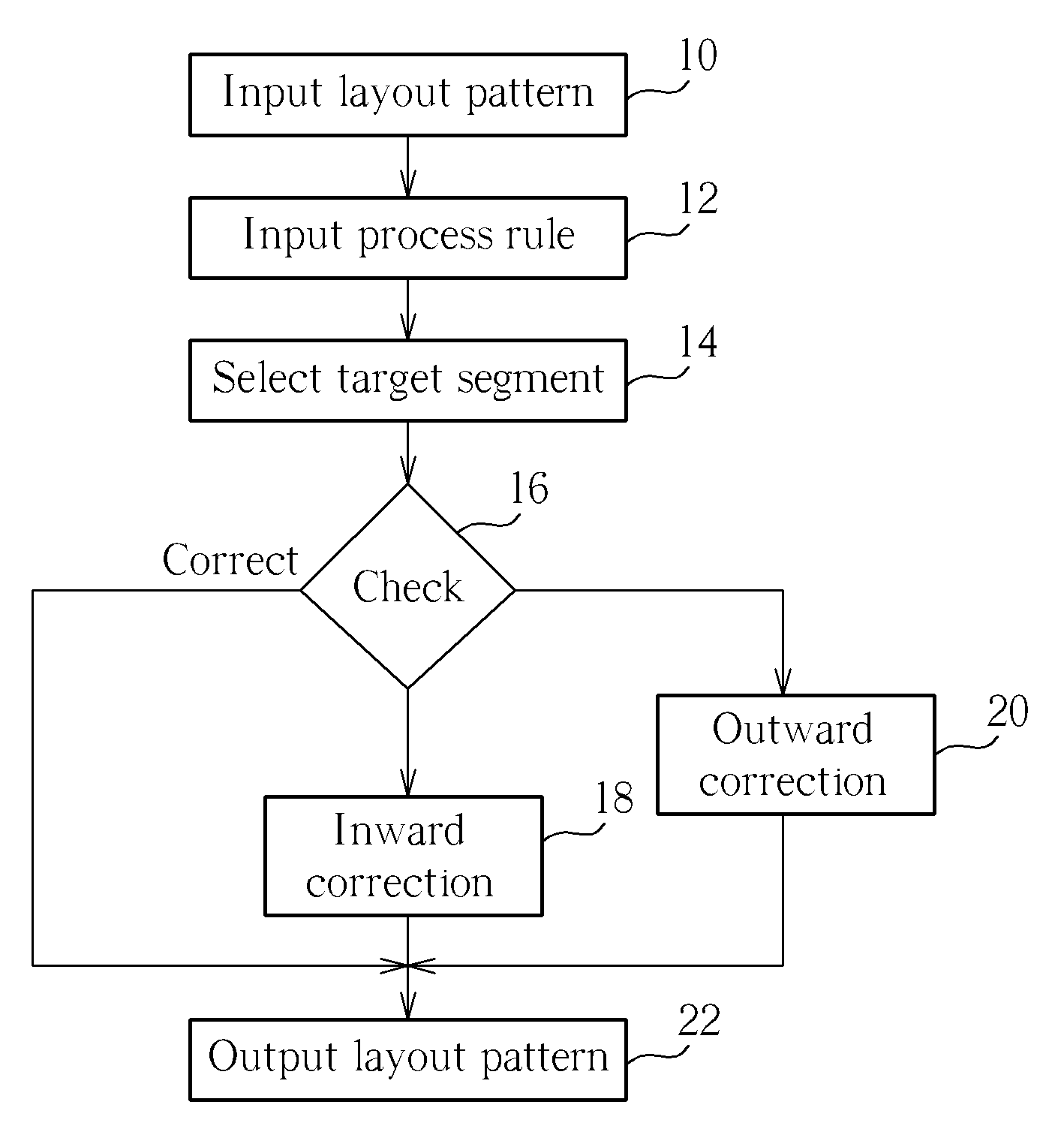
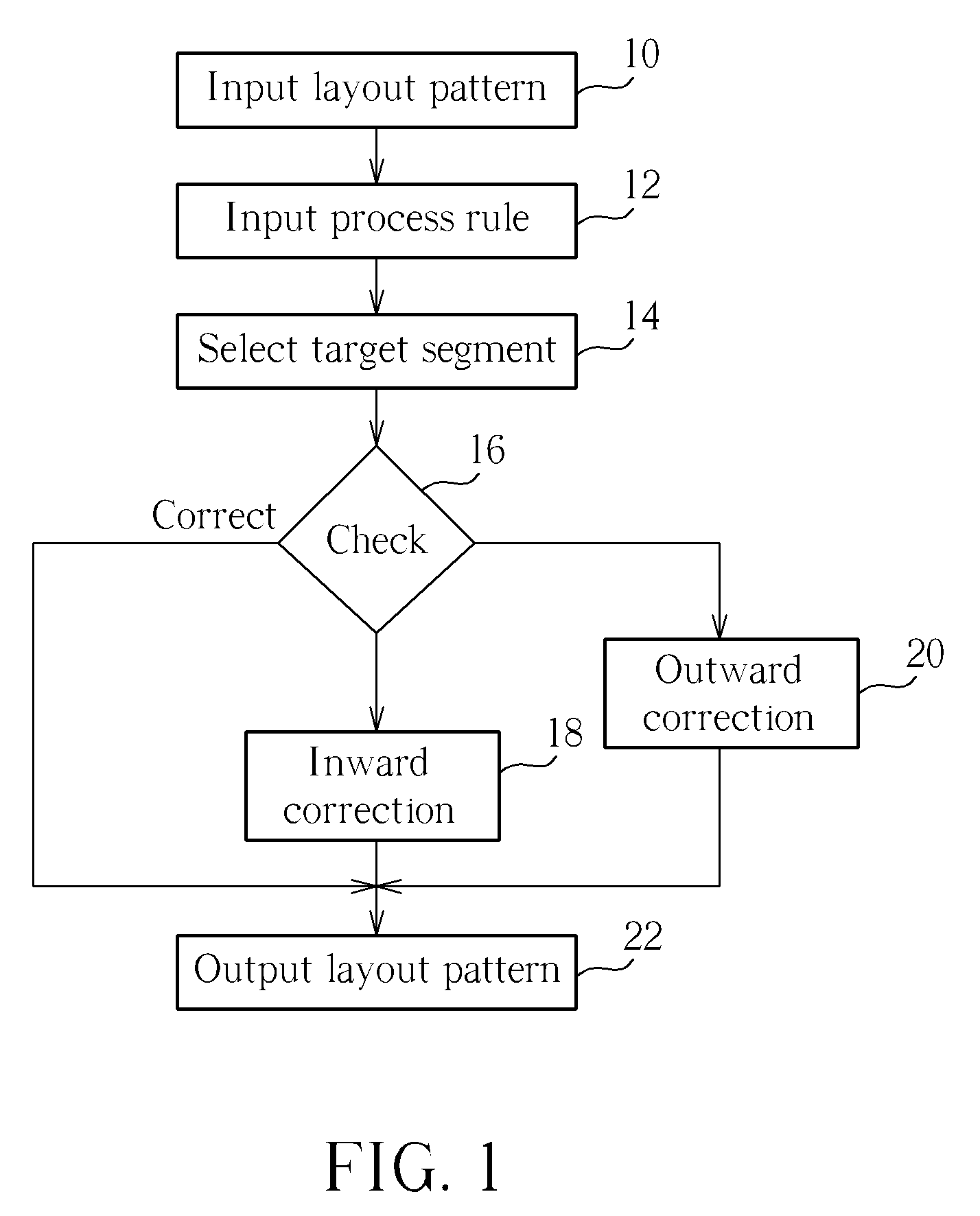
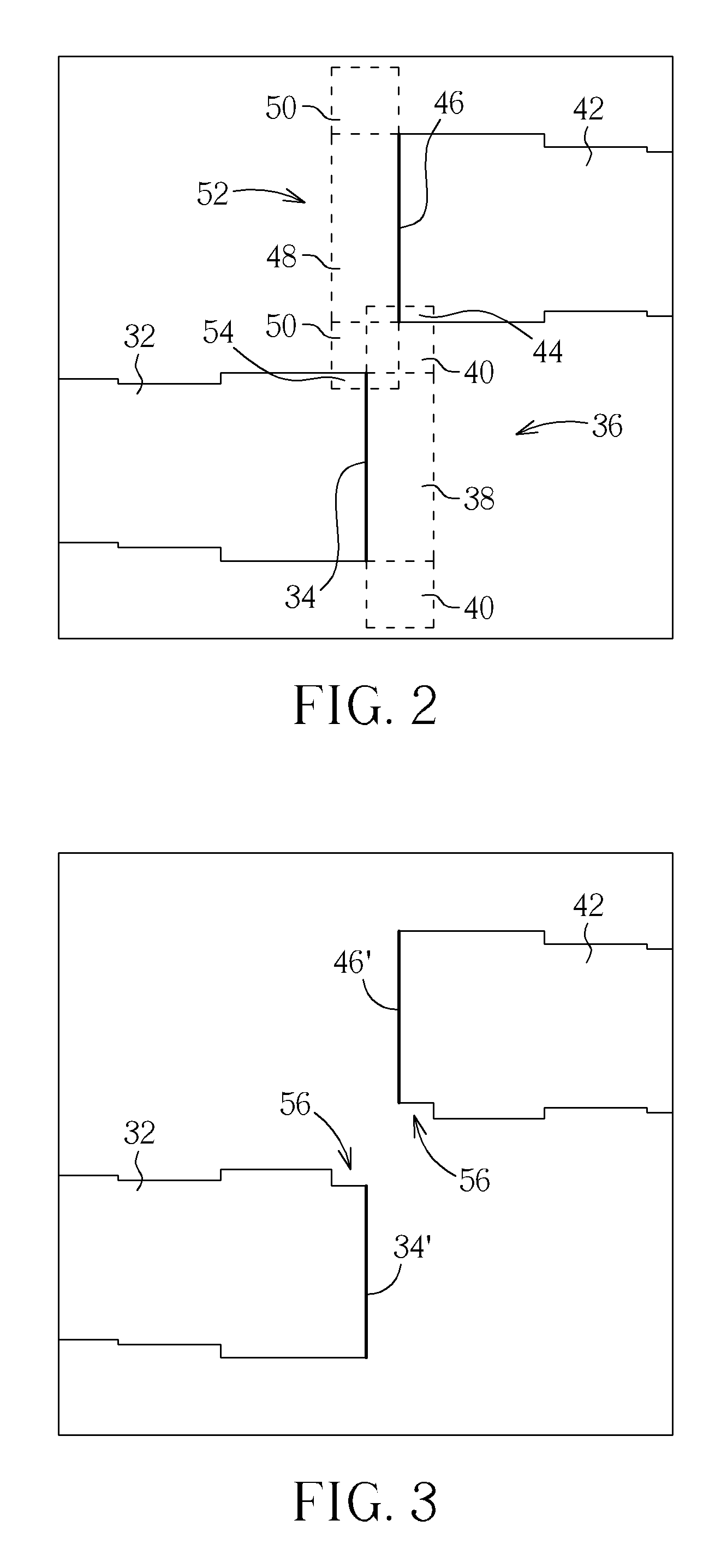
A method for correcting layout pattern is disclosed. The method includes the steps of: providing a layout pattern having at least one segment; forming a rule-checking rectangle from the segment, wherein the rule-checking rectangle comprises at least one square; verifying whether the square of the rule-checking rectangle overlaps other layout pattern; removing the portion of other layout pattern overlapped by the square to obtain a corrected layout pattern; and outputting the corrected layout pattern to a mask.
Owner:UNITED MICROELECTRONICS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com