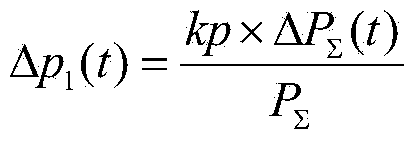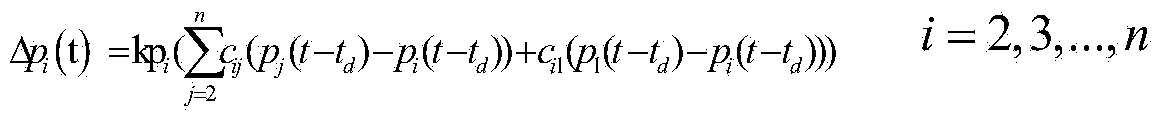Patents
Literature
393results about How to "Valid check" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
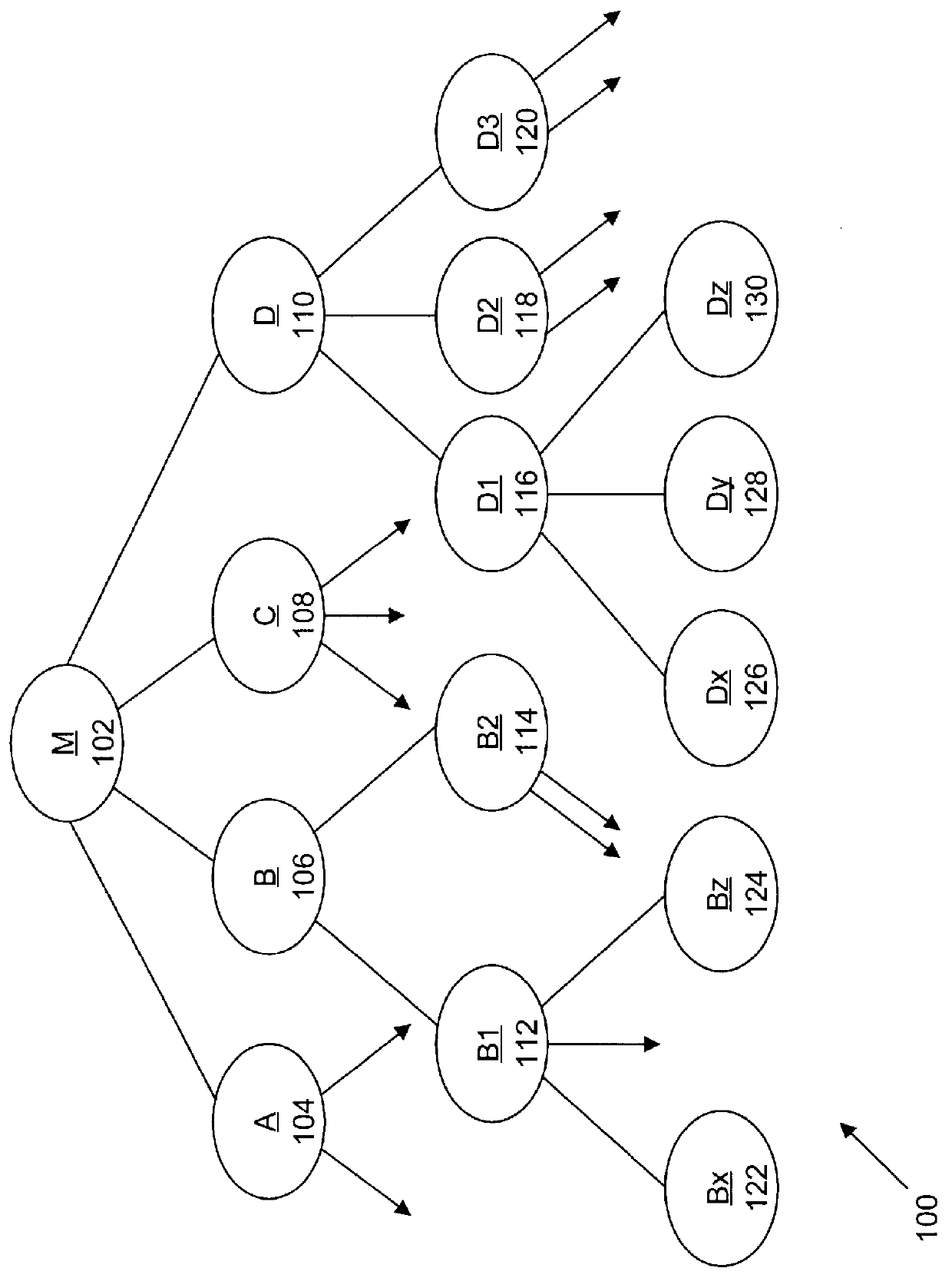
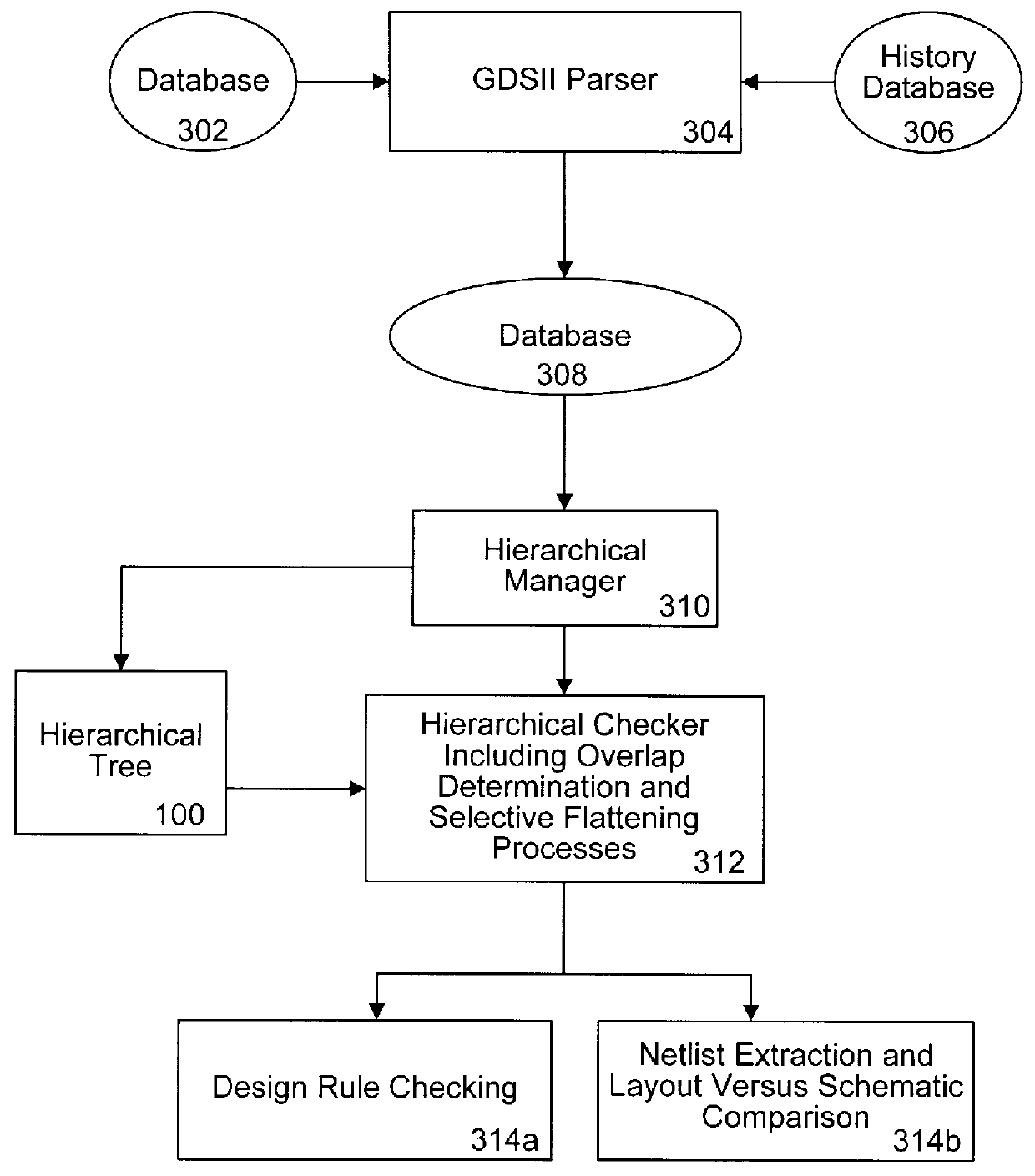
Layout overlap detection with selective flattening in computer implemented integrated circuit design
InactiveUS6011911AValid checkComputer aided designSoftware simulation/interpretation/emulationComputer architectureLayout Versus Schematic
The present invention relates to a method for efficiently performing hierarchical design rules checks (DRC) and layout versus schematic comparison (LVS) on layout areas of an integrated circuit where cells overlap or where a cell and local geometry overlap. With the present invention, a hierarchical tree describes the integrated circuit's layout data including cells having parent-child relationships and including local geometry. The present invention performs efficient layout verification by performing LVS and DRC checking on the new portions of an integrated circuit design and layout areas containing overlapping cells. When instances of cells overlap, the present invention determines the overlap area using predefined data structures that divide each cell into an array of spatial bins. Each bin of a parent is examined to determine if two or more cell instances reside therein or if a cell instance and local geometry reside therein. Once overlap is detected, the areas of the layout data corresponding to the overlap areas are selectively flattened prior to proceeding to DRC and LVS processing. During selective flattening of the overlap areas, the hierarchical tree is traversed from the top cell down through intermediate nodes to the leaf nodes. Each time geometry data is located during the traversal, it is pushes directly to the top cell without being stored in intermediate locations. This provides an effective mechanism for selective flattening.
Owner:SYNOPSYS INC
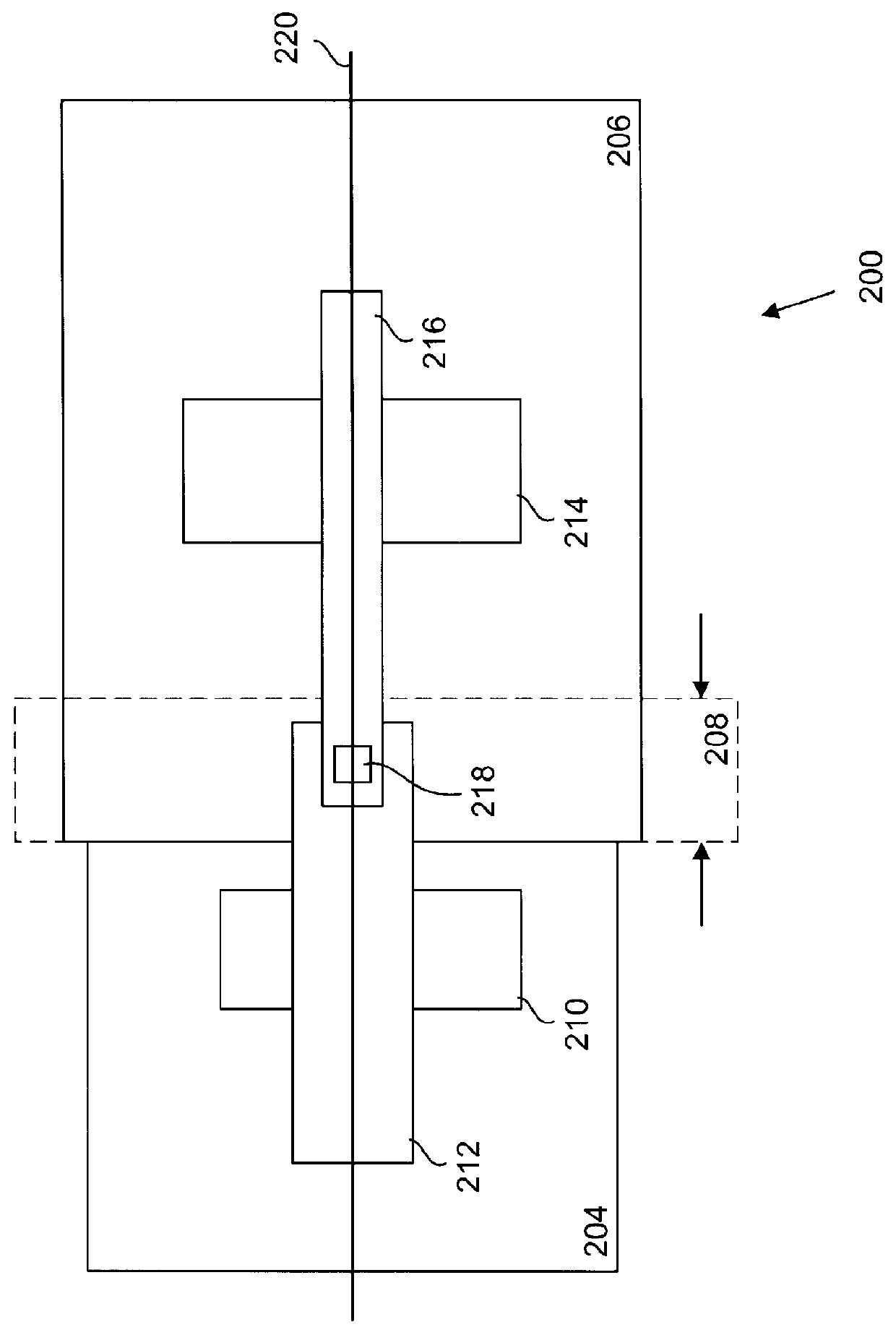
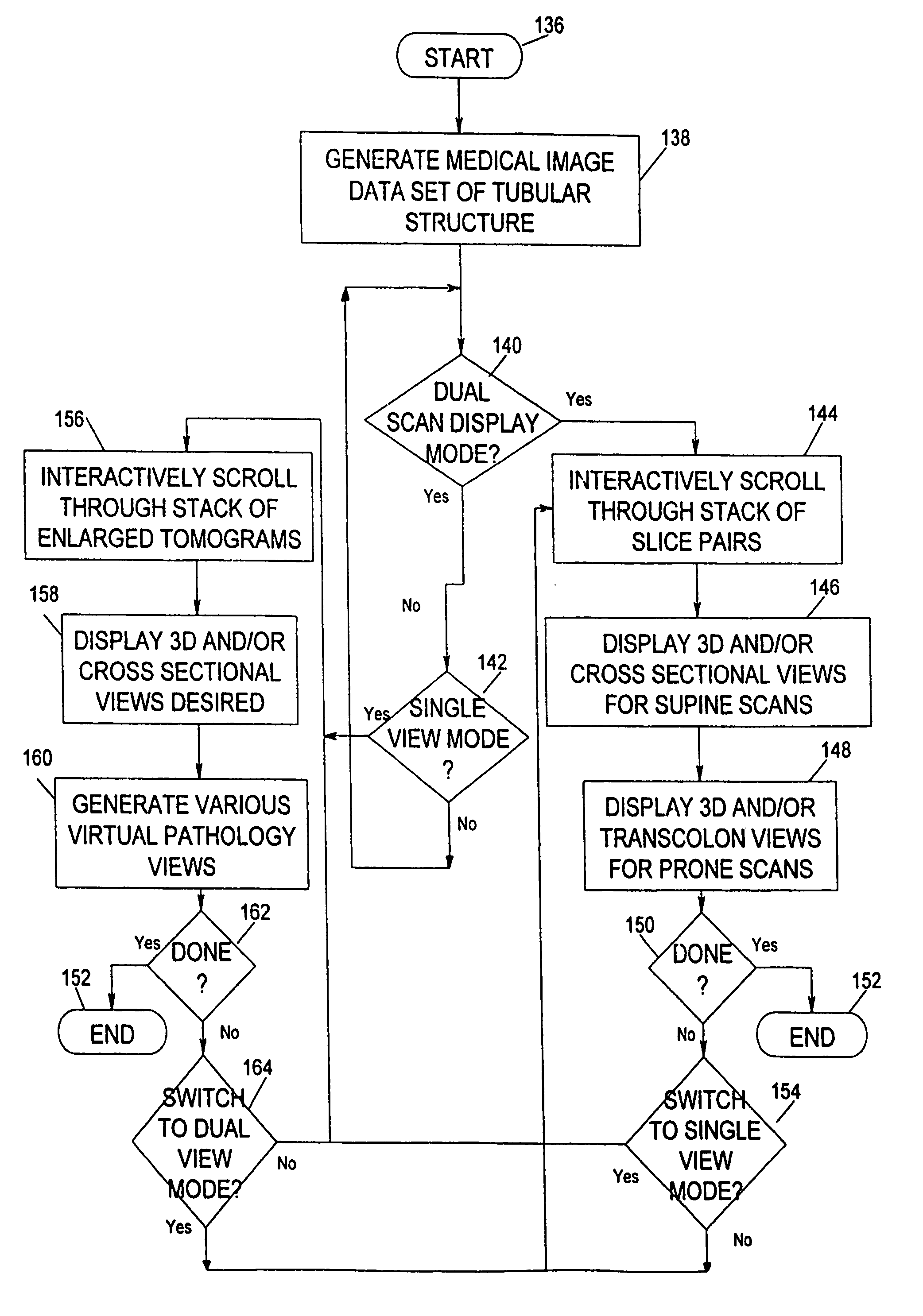
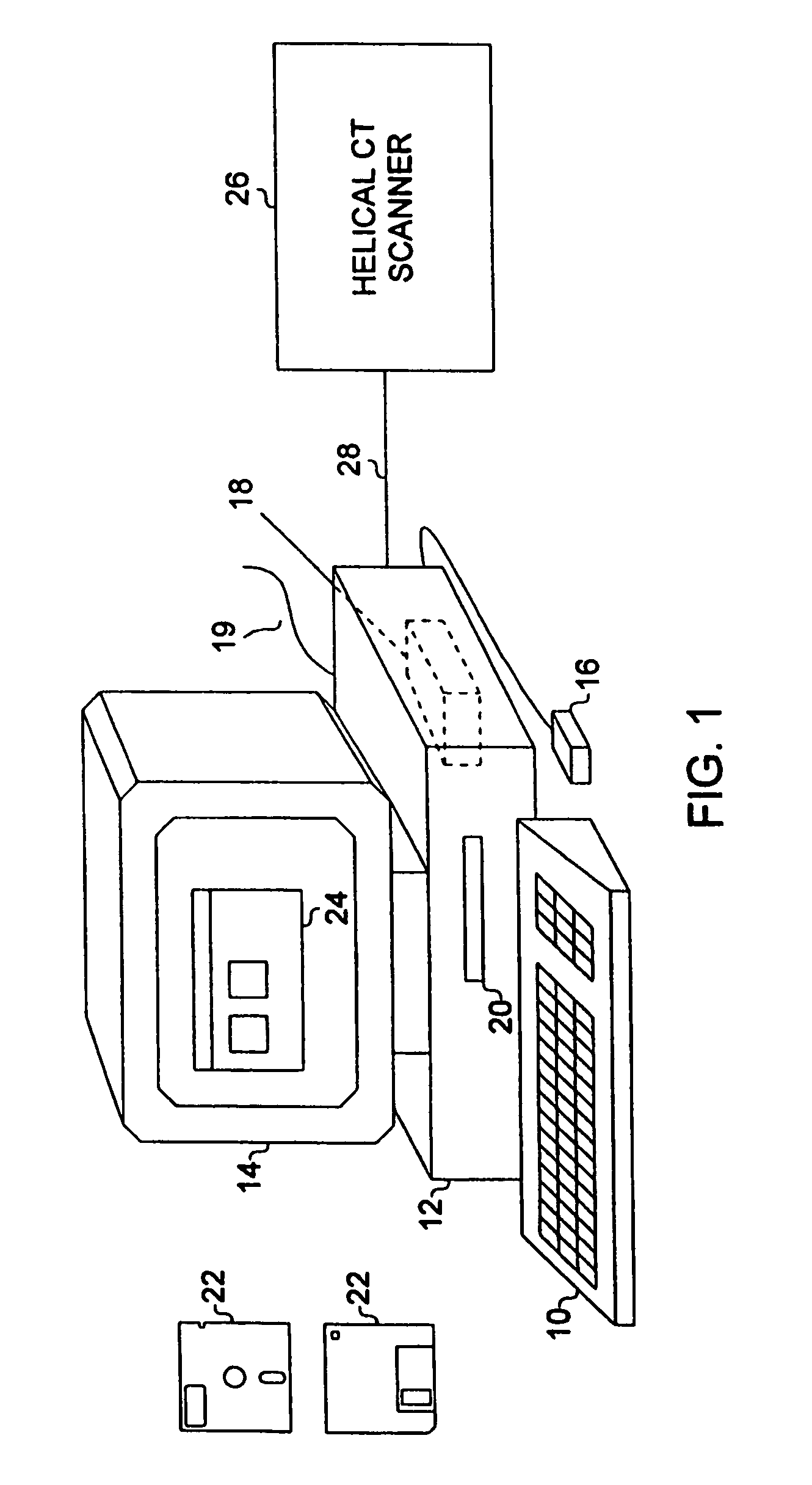
System for two-dimensional and three-dimensional imaging of tubular structures in the human body
InactiveUS6928314B1Interpretation time is not improvedStrong computing abilityImage enhancementImage analysisHuman bodyViewpoints
This invention is a system, method, and article of manufacture for imaging tubular structures of the human body, such as the digestive tract of a living person, with a medical imaging device such as a computed tomography (CT) scanner and a computer work station. The system comprises receiving a first image data set representative of a portion of the colon in a prone position and a second image data set representative of a portion of the colon in a supine position, at a series of viewpoints. At each of the viewpoints, an image is generated of the colon in the prone and supine positions. The prone and supine images of the colon are simultaneously displayed on a screen display in a dual view mode.
Owner:MAYO FOUND FOR MEDICAL EDUCATION & RES
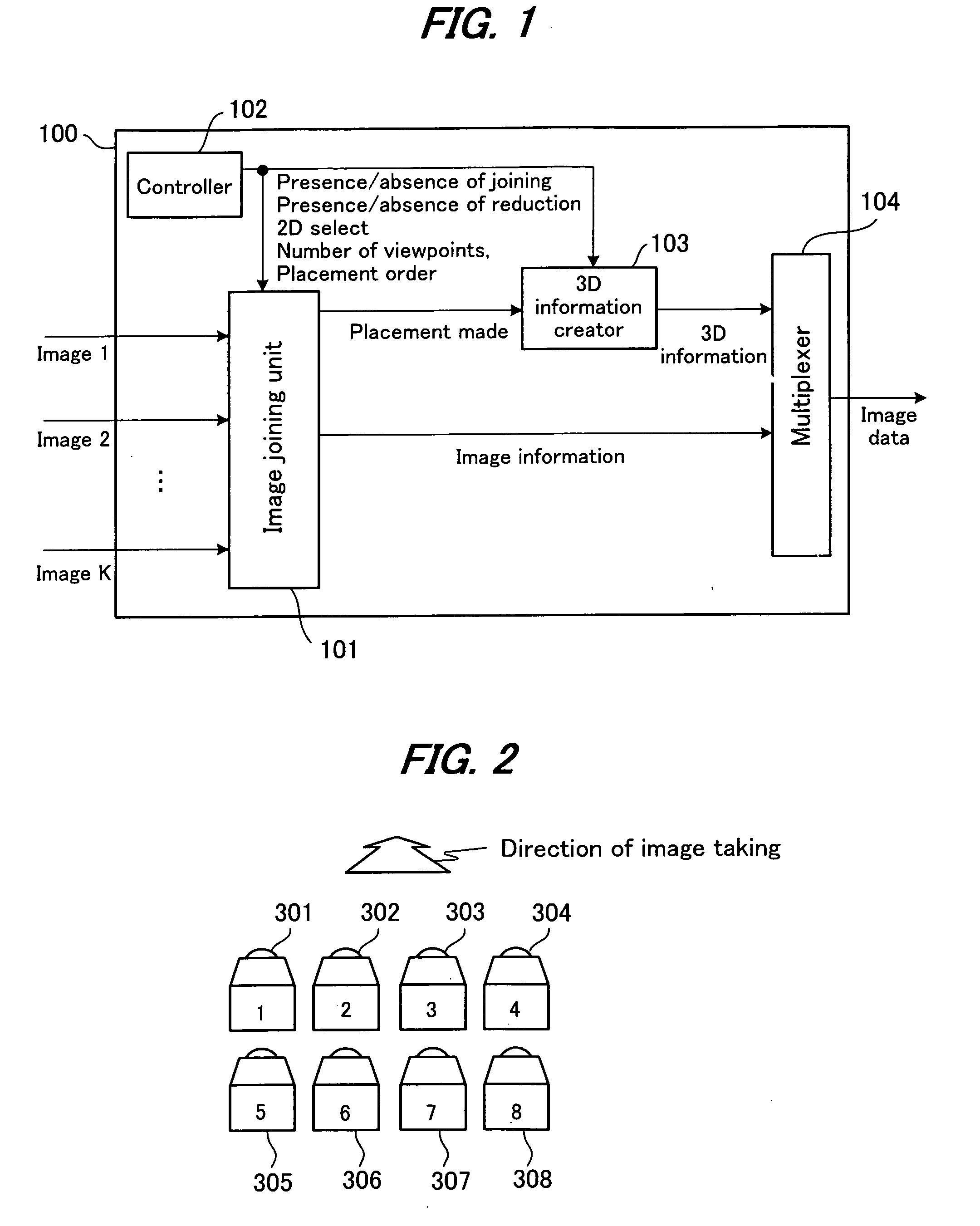
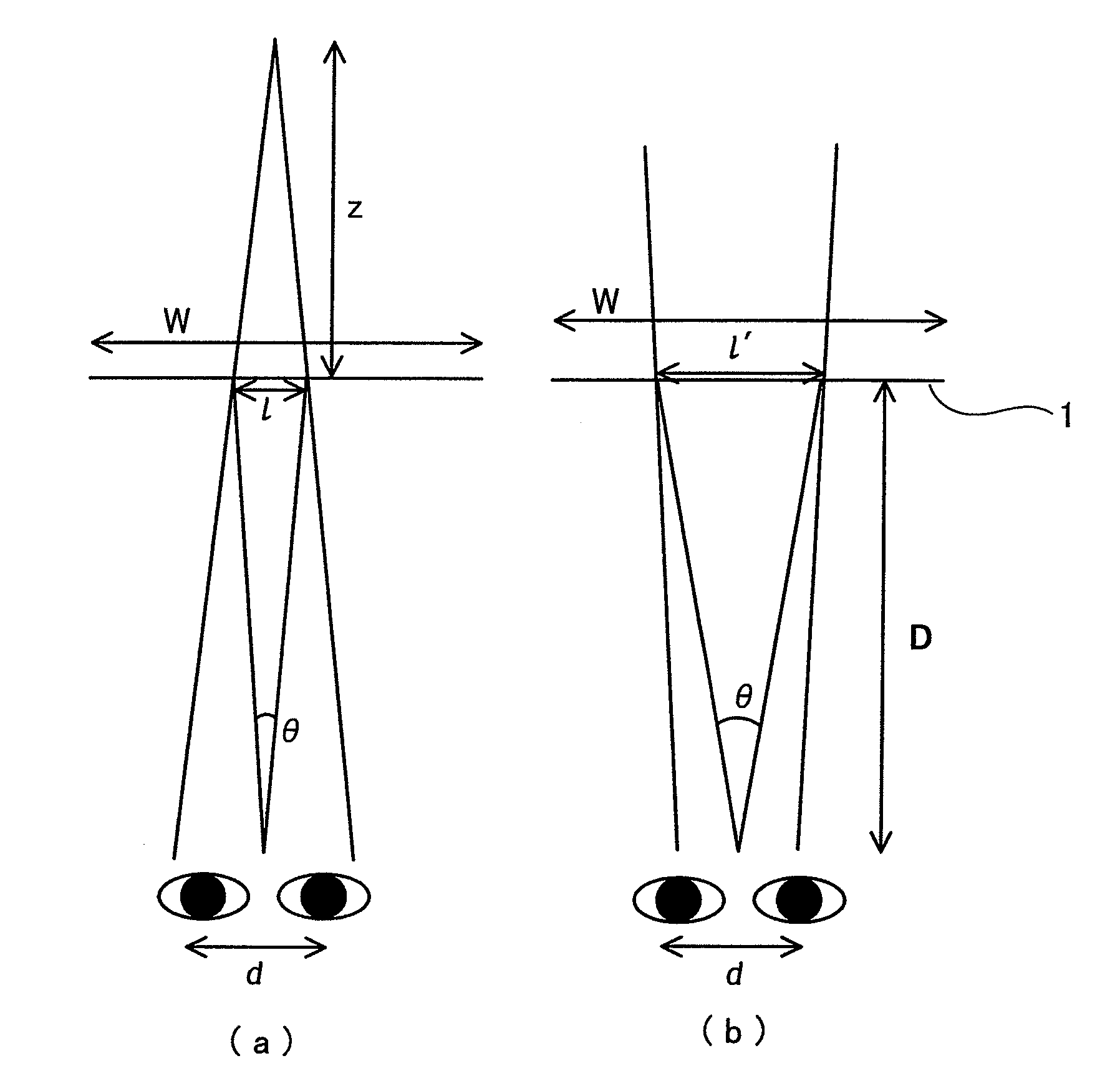
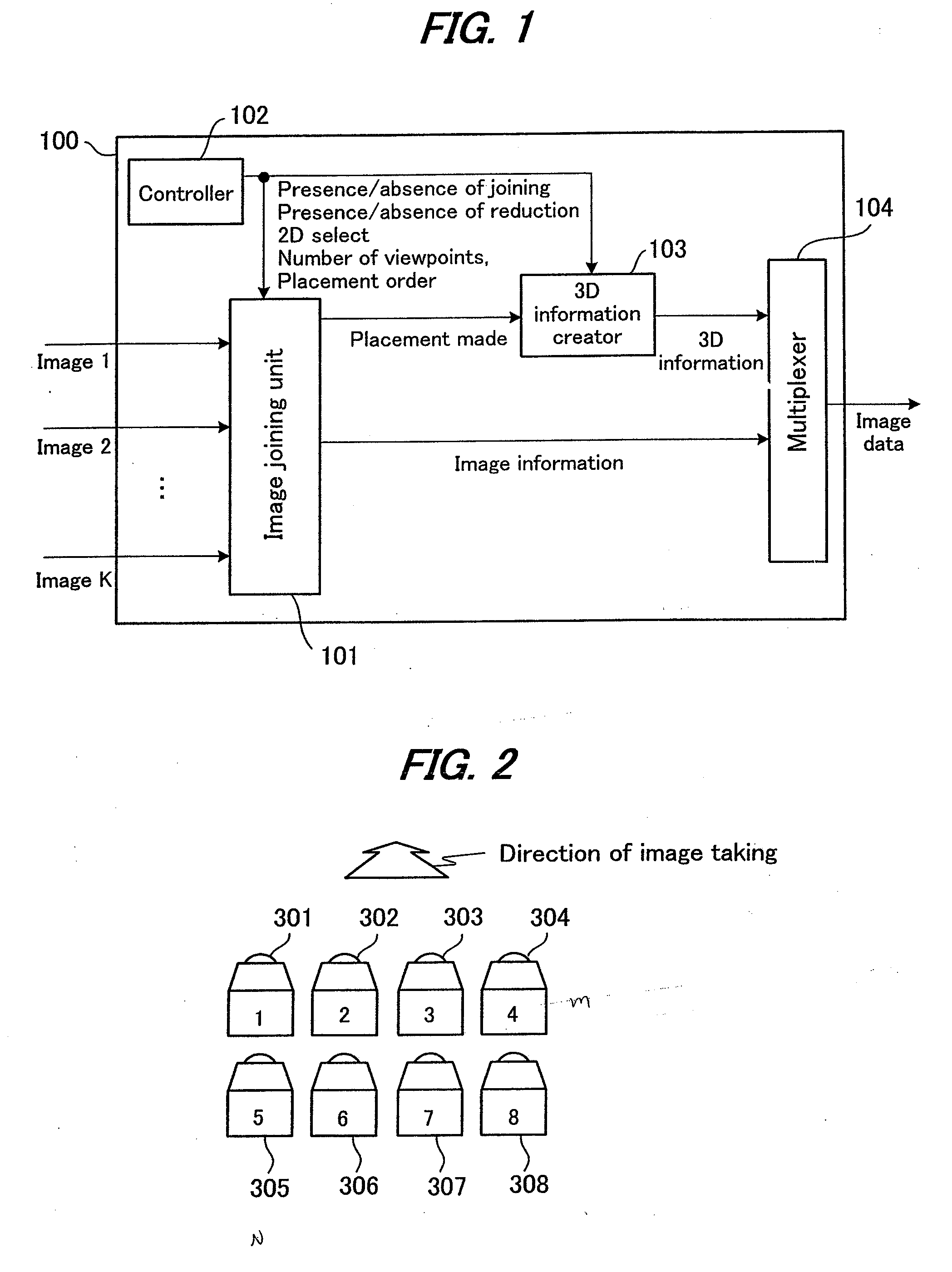
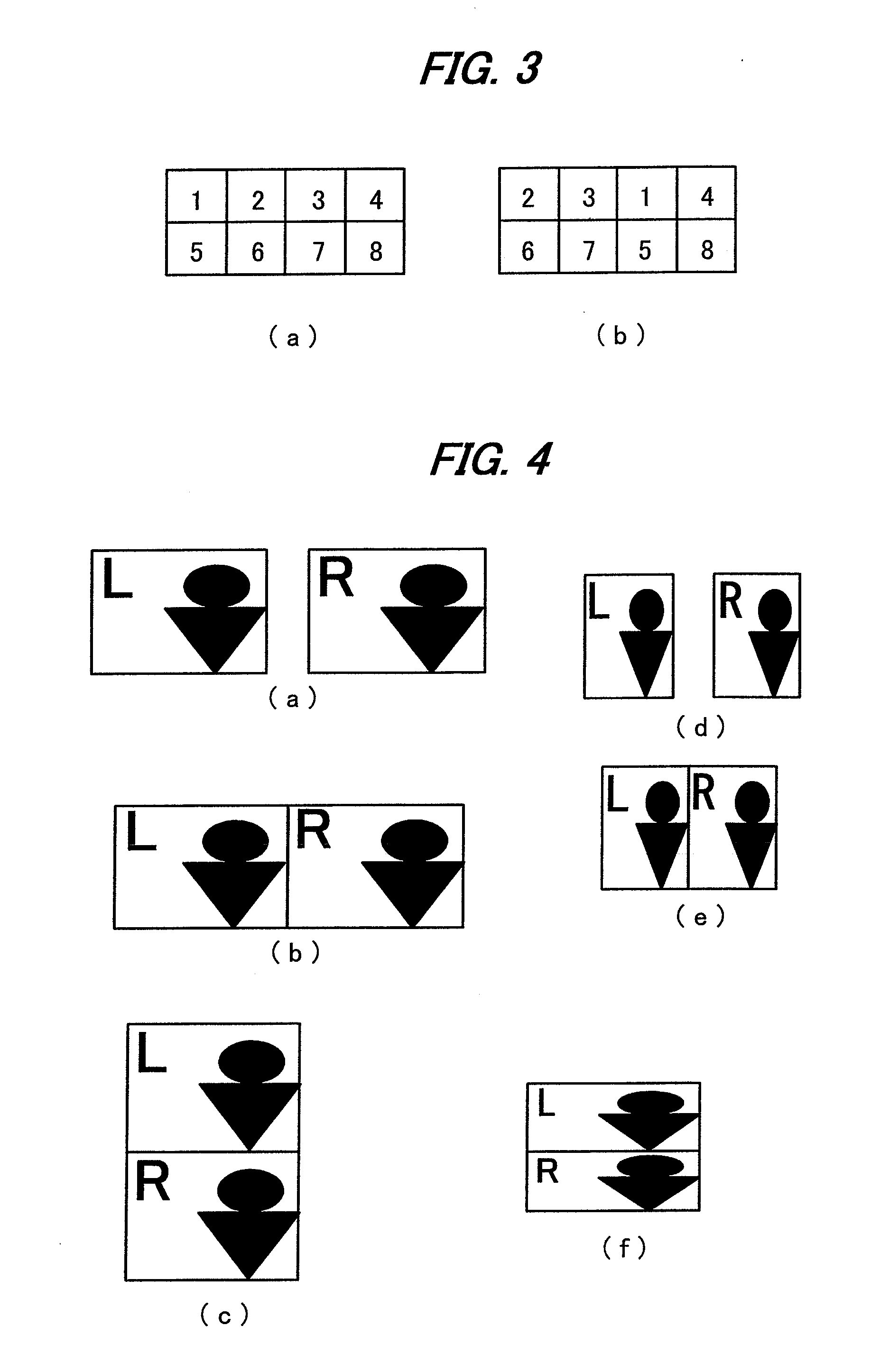
3-Dimensional image creation device, 3-dimensional image reproduction device, 3-dimensional image processing device, 3-dimensional image processing program, and recording medium containing the program
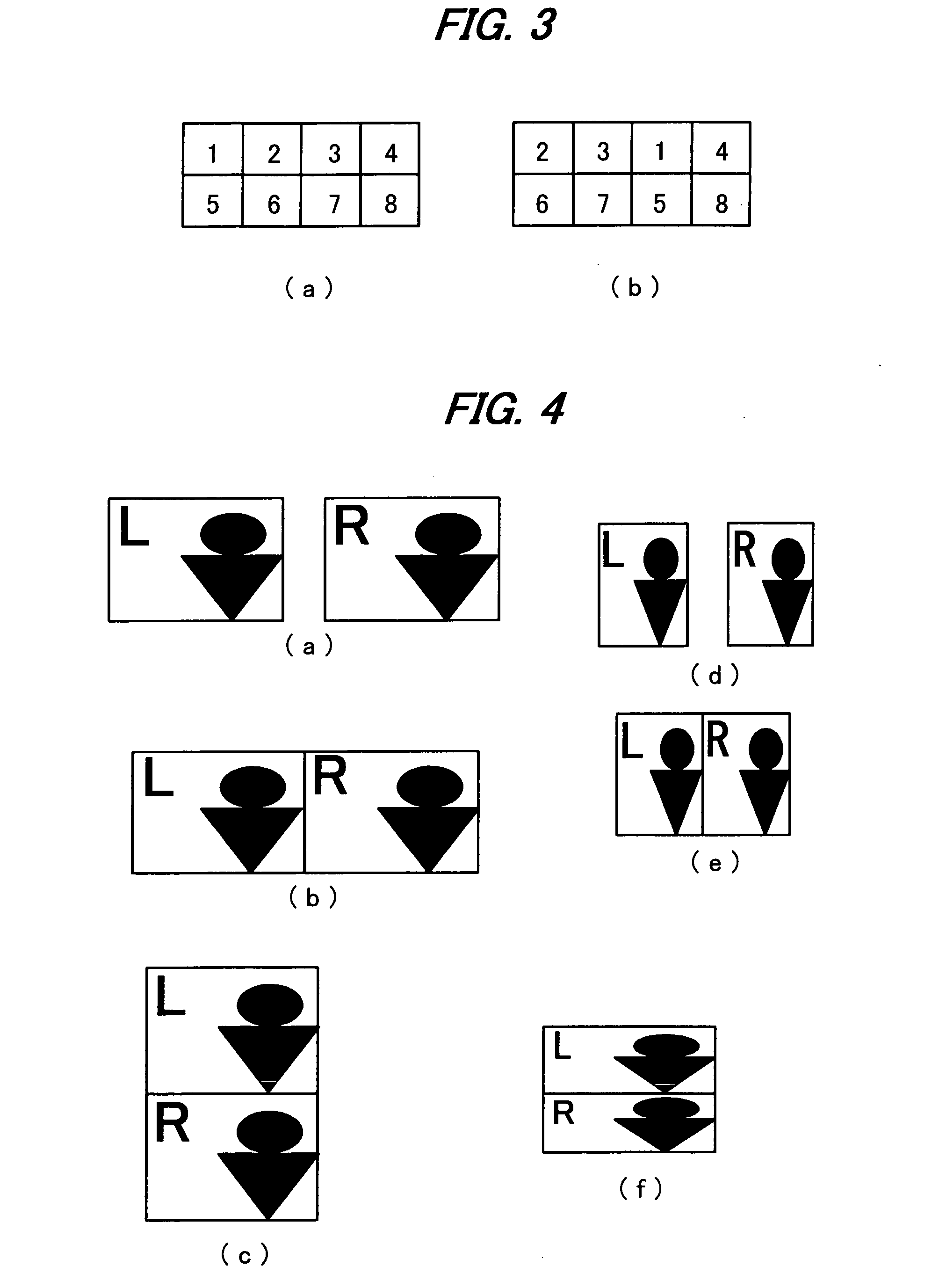
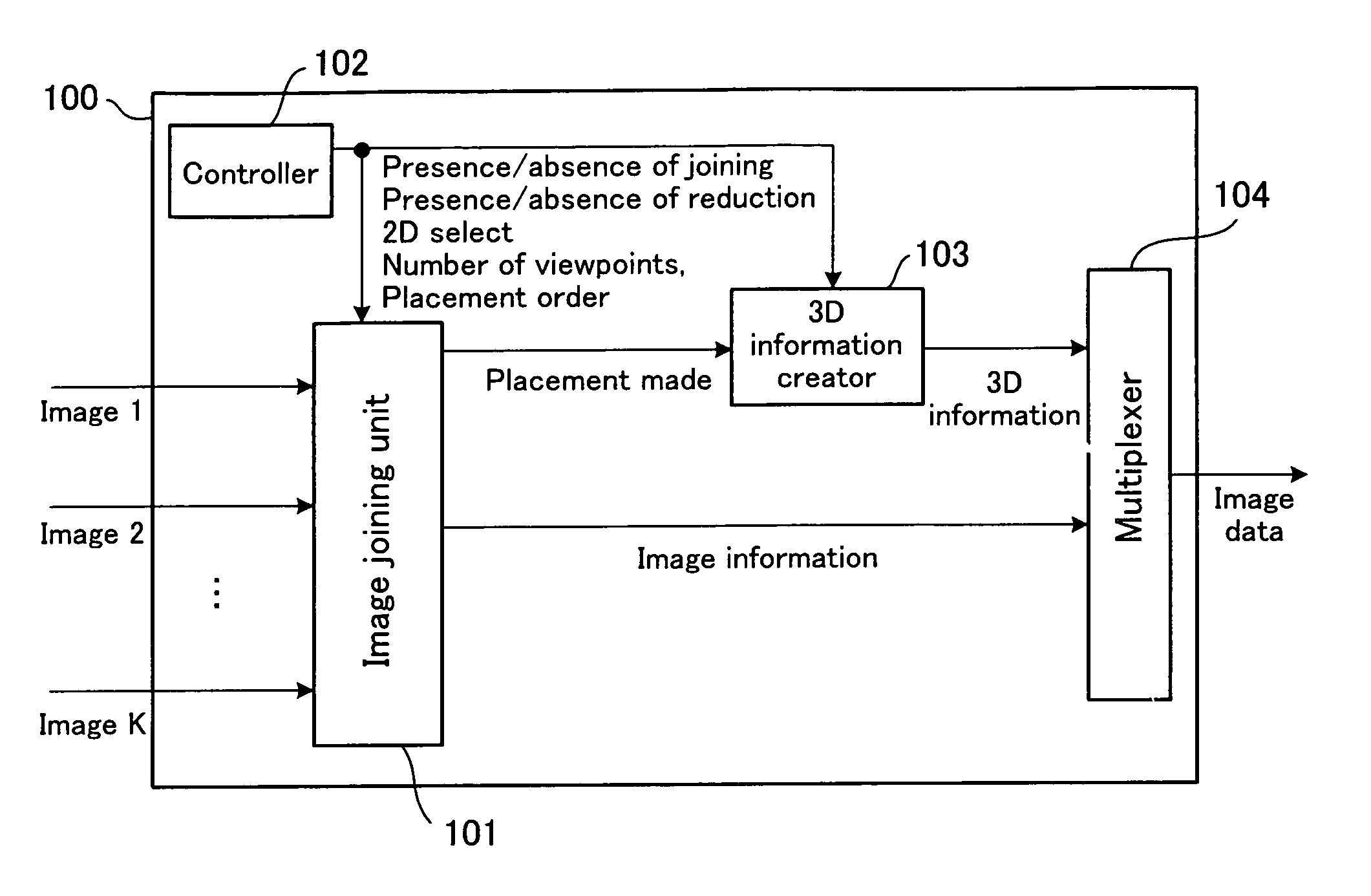
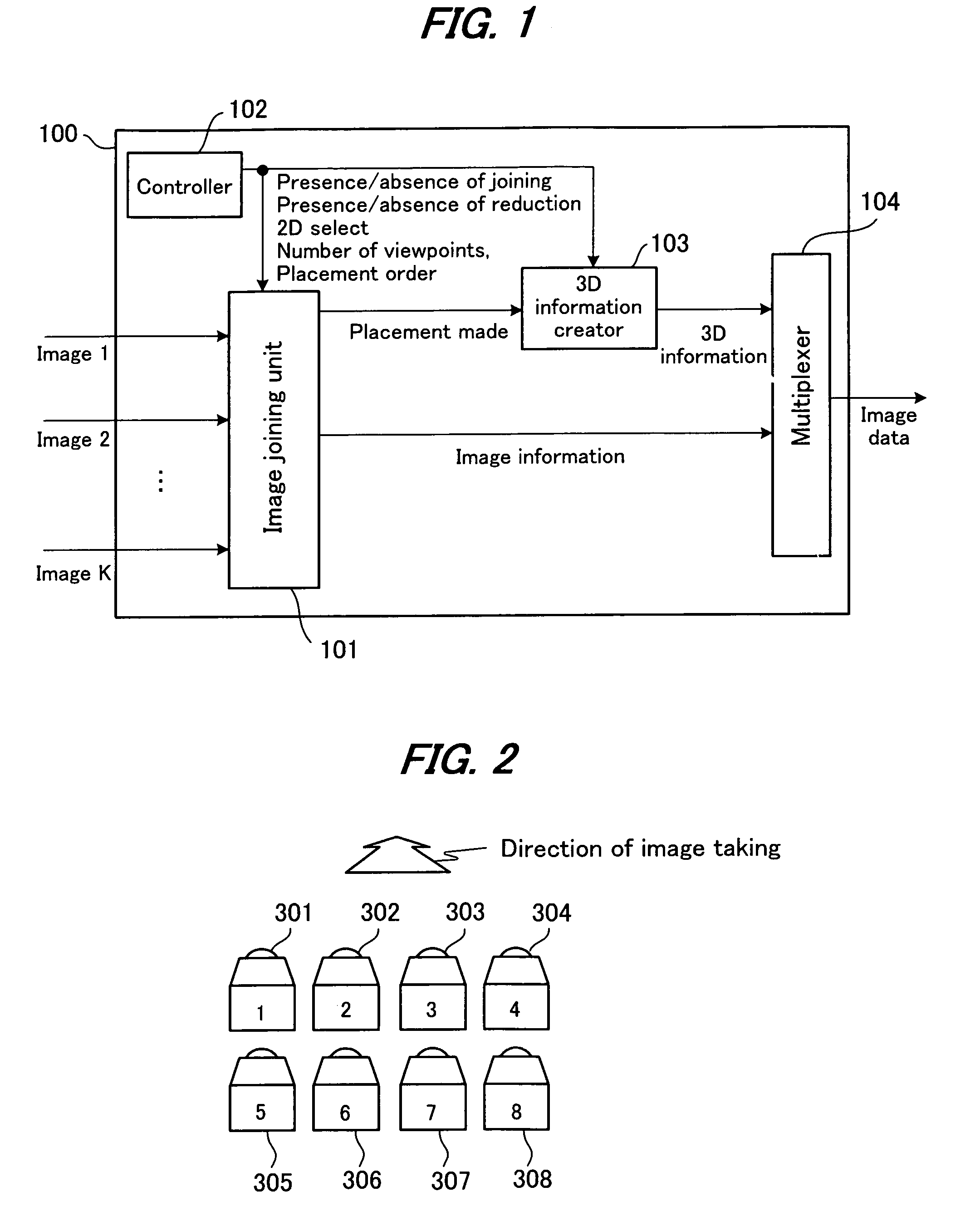
InactiveUS20060192776A1Stereoscopic view difficultValid checkCharacter and pattern recognitionSteroscopic systemsData information3d image
An image signal composed of sequential frames is input to a 3-dimensional image creating apparatus, frame by frame. A controller (102) designates the presence / absence of reduction, the presence / absence of joining and 2D select. An image converter (101) creates image data in the format designated by the presence / absence of reduction and the presence / absence of joining. A 3D information creator (103) creates 3D information necessary for displaying the image as a 3-dimensional image by formatting the presence / absence of reduction, the presence / absence of joining and 2D select. A multiplexer (104) converts image data and 3D information in a predetermined format and outputs them to the outside. In this way, it is possible to make the image data for 3-dimensional display versatile and select an arbitrary viewpoint image efficiently.
Owner:SHARP KK
Access control for a packet-oriented network, taking into account resilience requirements
InactiveUS20060187817A1Rapid responseAvoid problemsError preventionFrequency-division multiplex detailsTraffic capacityQuality of service
The invention relates to a method for providing resources for adapting the routing process in response to the failure of a network element in a packet-oriented network. Barring checks that use thresholds are provided to control the volume of traffic in the network. Data packets are barred if their routing would otherwise mean the crossing of a threshold. According to the invention, the thresholds are defined by taking into account failure topologies or possible malfunction scenarios, to ensure that a corresponding malfunction does not lead to an overload in the network. Said definition of the thresholds allows resources to be provided or reserved to all intents and purposes for intercepting malfunctions. The advantage of the invention is that quality criteria can be upheld and quality of service features guaranteed, even during the malfunctions.
Owner:NOKIA SIEMENS NETWORKS GMBH & CO KG
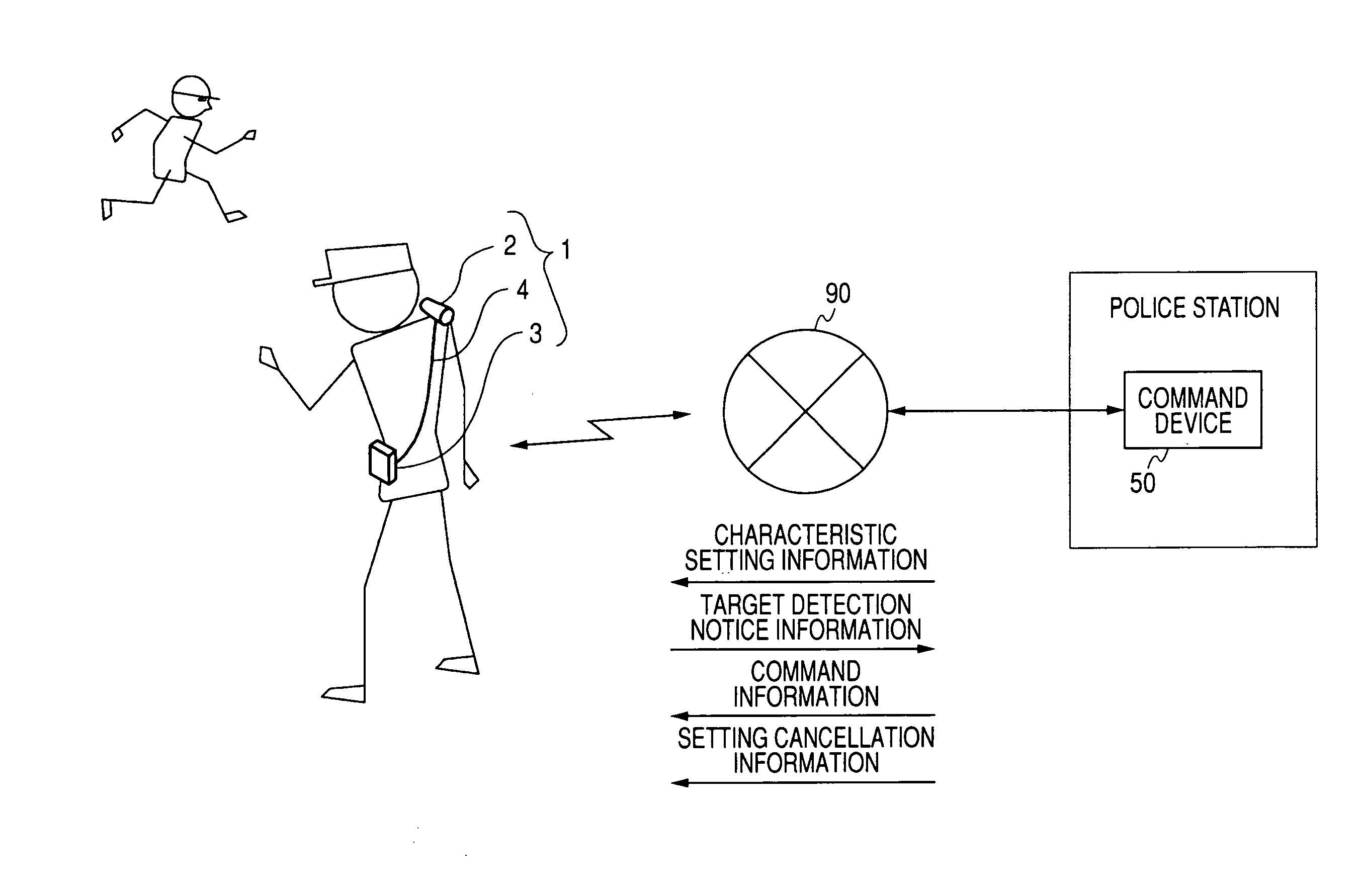
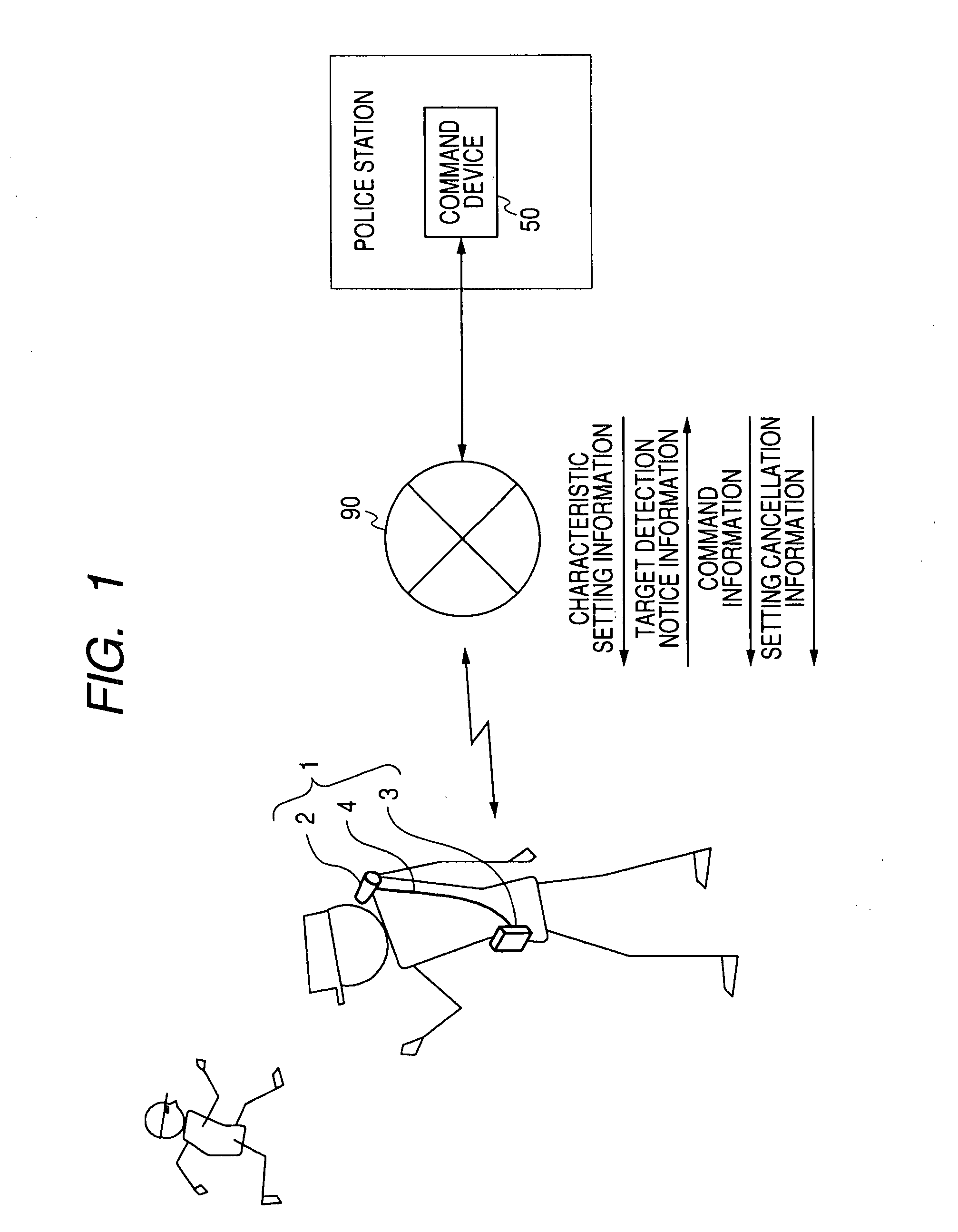
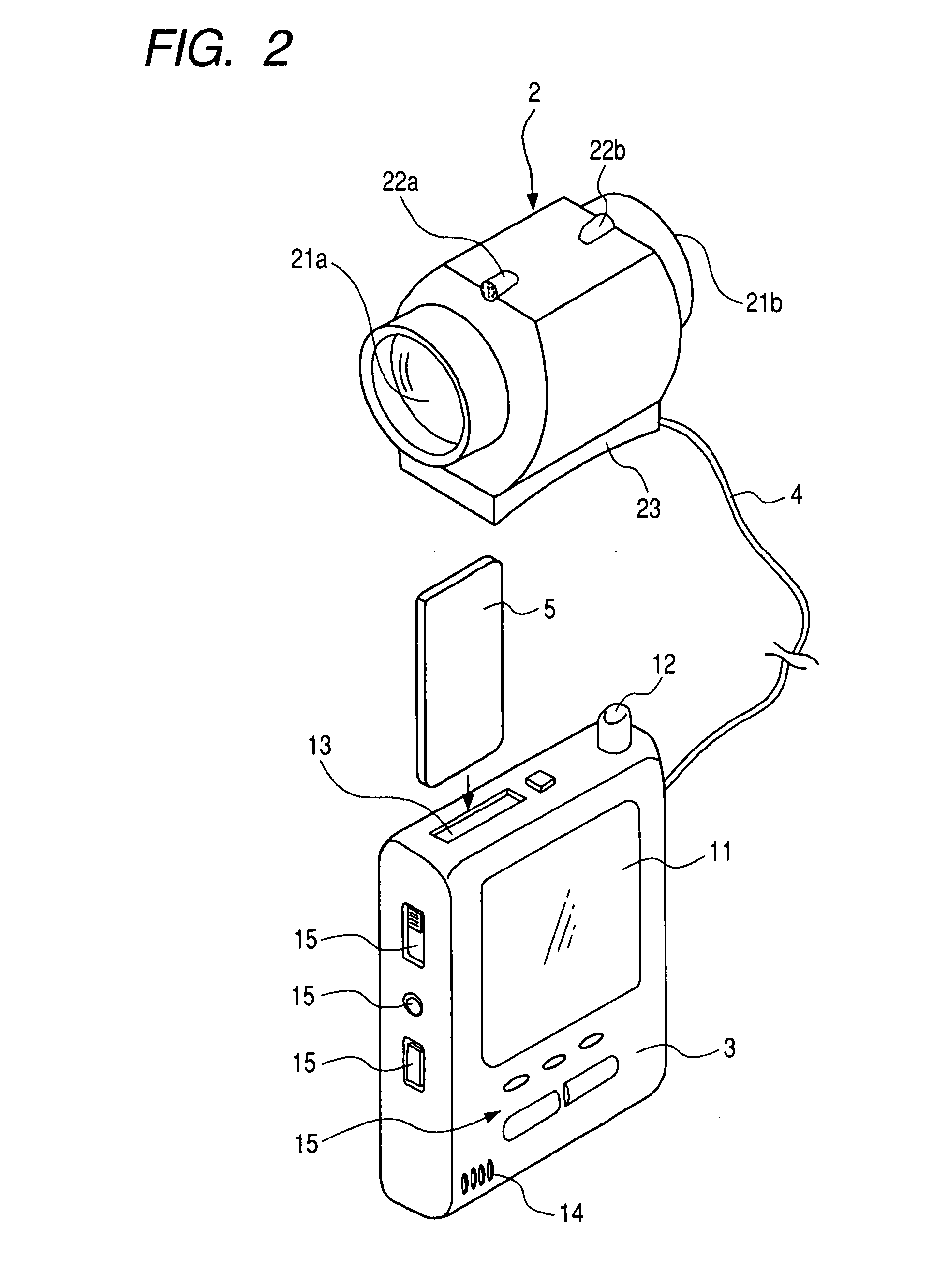
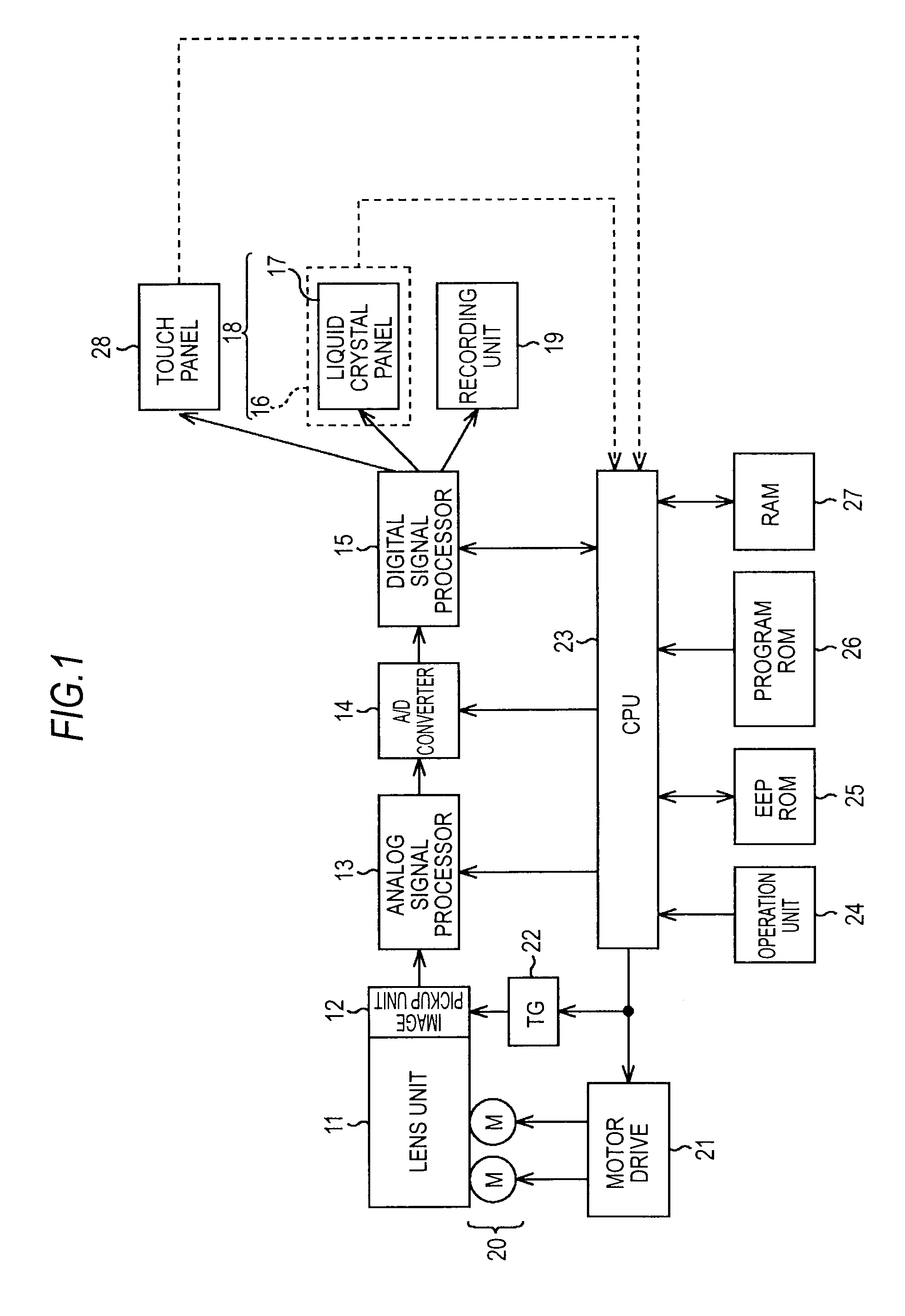
Command system, imaging device, command device, imaging method, command processing method, and program
InactiveUS20080030580A1Accurate and effectiveAccurate imagingCharacter and pattern recognitionClosed circuit television systemsCommunication unitData set
A command system includes: a portable imaging device; and a command device configured to communicate with the imaging device. The imaging device includes: an imaging unit; a communication unit; a characteristic data setting unit; a target image detecting unit; a recording unit; and an imaging process control unit, and the command device includes: a communication unit; and a characteristic setting information generating unit.
Owner:SONY CORP
Decrypting data
ActiveUS9584311B2Prevent tamperingGuaranteed normal executionSecret communicationCommunication with homomorphic encryptionHomomorphic encryptionComputer program
A device for decrypting data includes a number of devices secured by at least one security device. The secured devices include a receiver for receiving calculation data encrypted using a homomorphic encryption function and a decryptor for decrypting the encrypted calculation data by carrying out the inverse of the homomorphic encryption function on the encrypted calculation data using a private key assigned to the homomorphic encryption function. A method and a computer program product for decrypting data are also provided.
Owner:SIEMENS AG
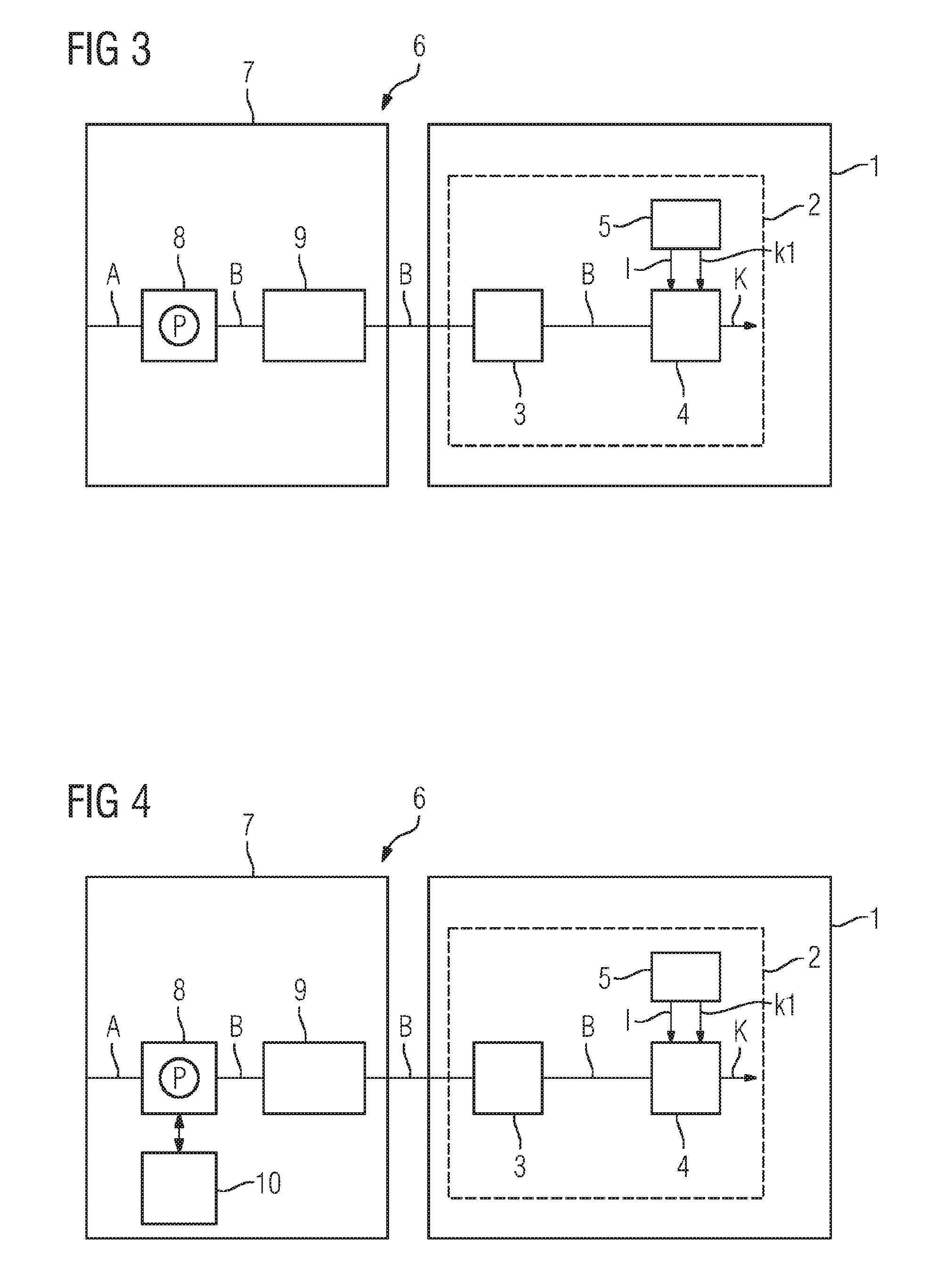
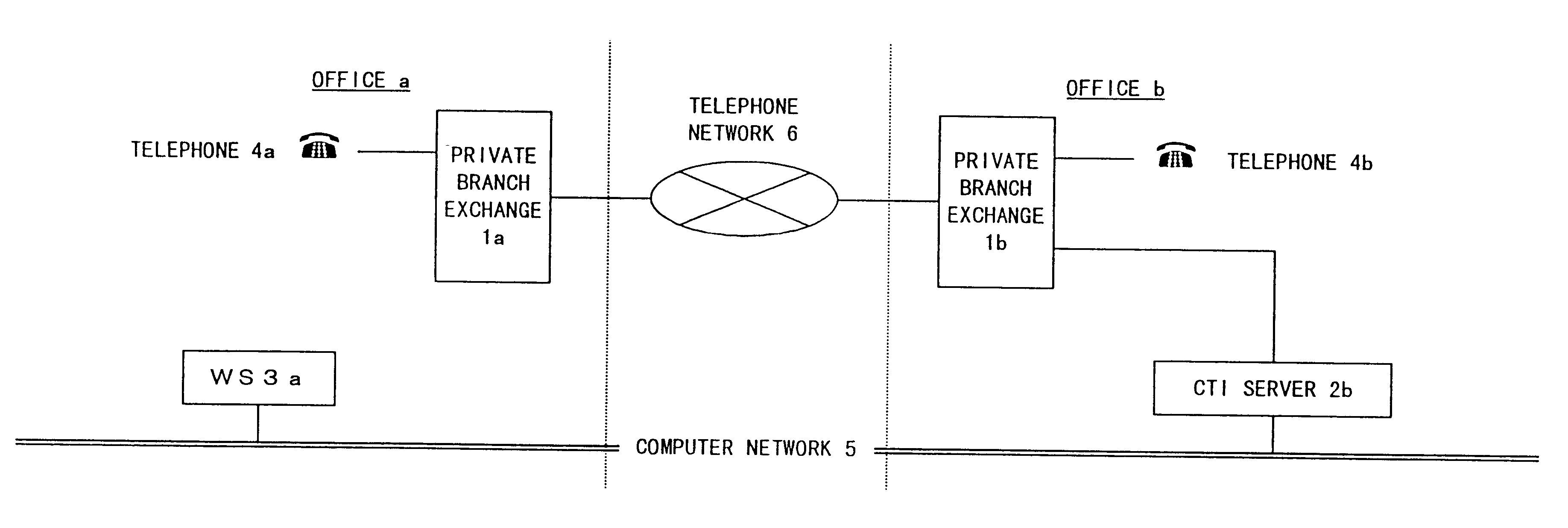
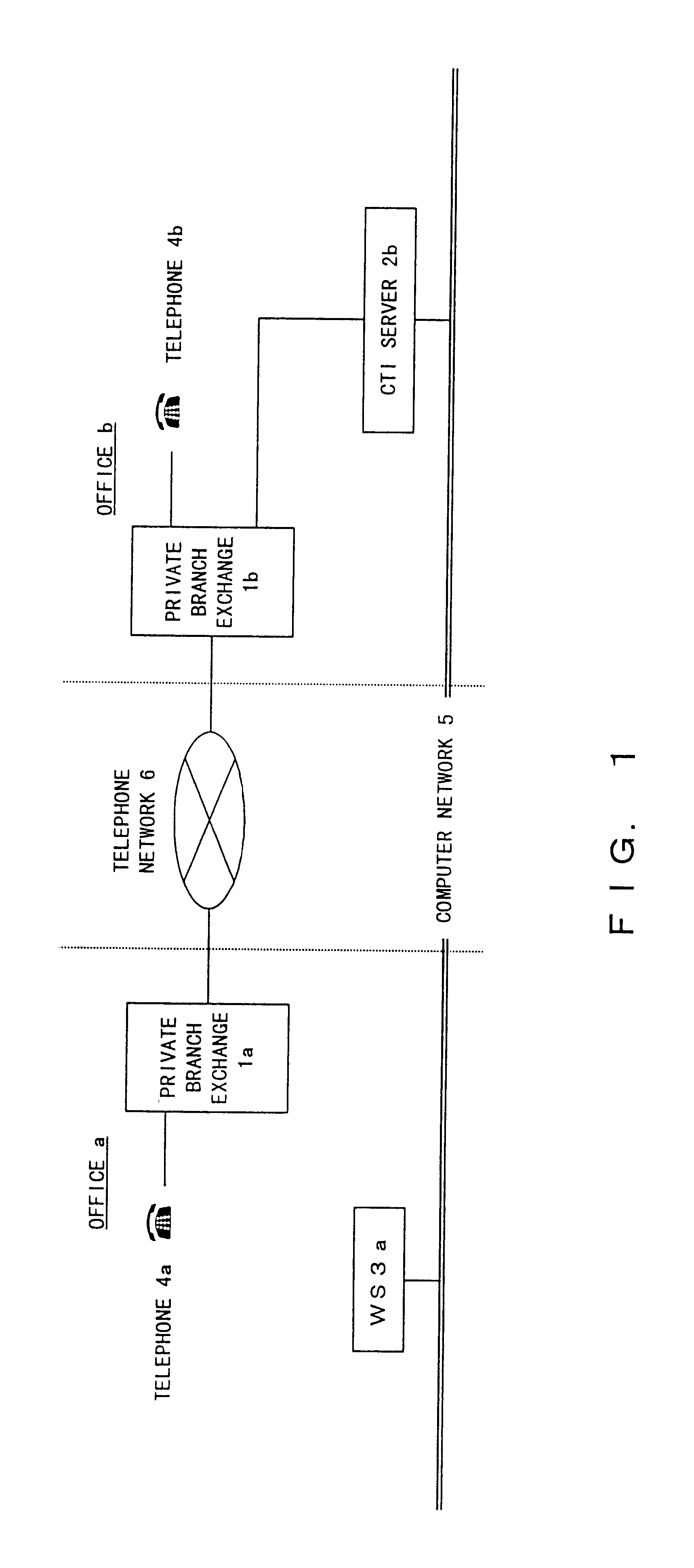
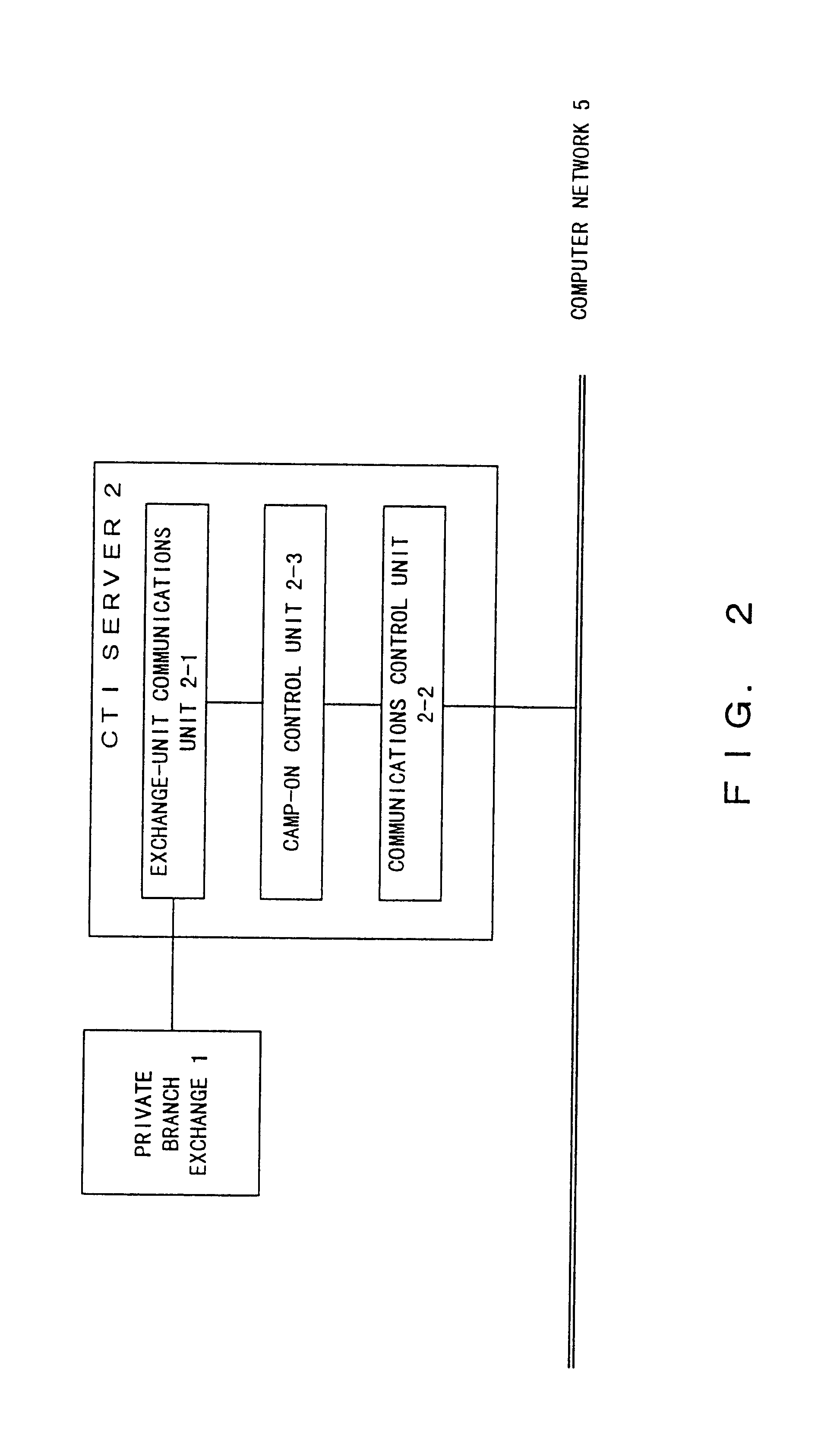
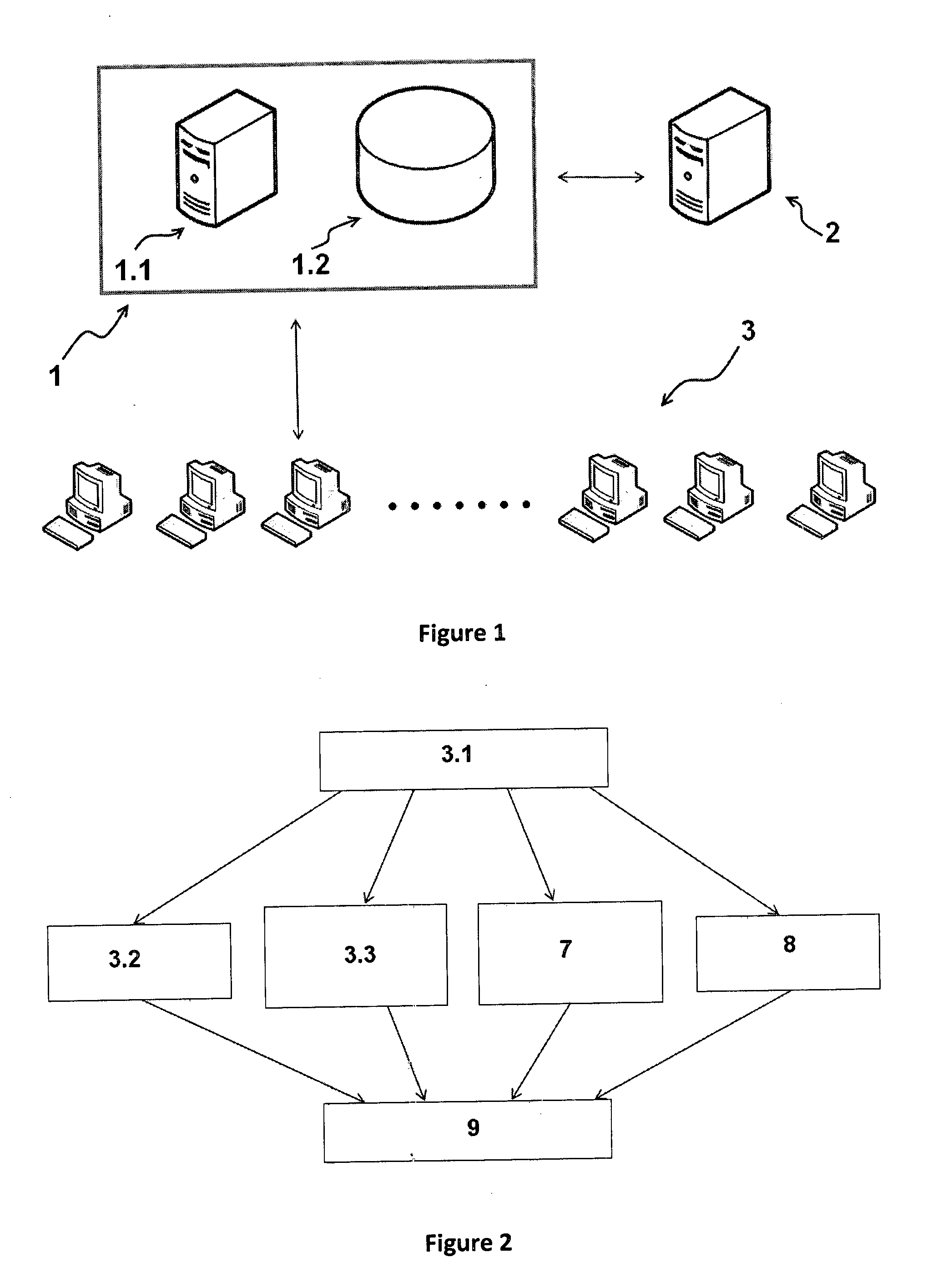
CTI Control System
InactiveUS6760322B1Valid checkGuaranteed normal transmissionMultiplex system selection arrangementsSpecial service for subscribersControl systemBranch exchange
When a telephone a belonging to an office a calls up a telephone b belonging to an office b, a subscriber of the telephone a operates a WS a connected to a computer network and edits camp-on request information when the telephone b is busy. The camp-on request information is transferred from the WS a to a CTI server b belonging to the office b connected to the computer network. The CTI server unit b performs camp-on control between the telephone b belonging to the office b and the telephone a belonging to the office a by controlling a private branch exchange b based on a schedule corresponding to the received camp-on request information.
Owner:FUJITSU LTD
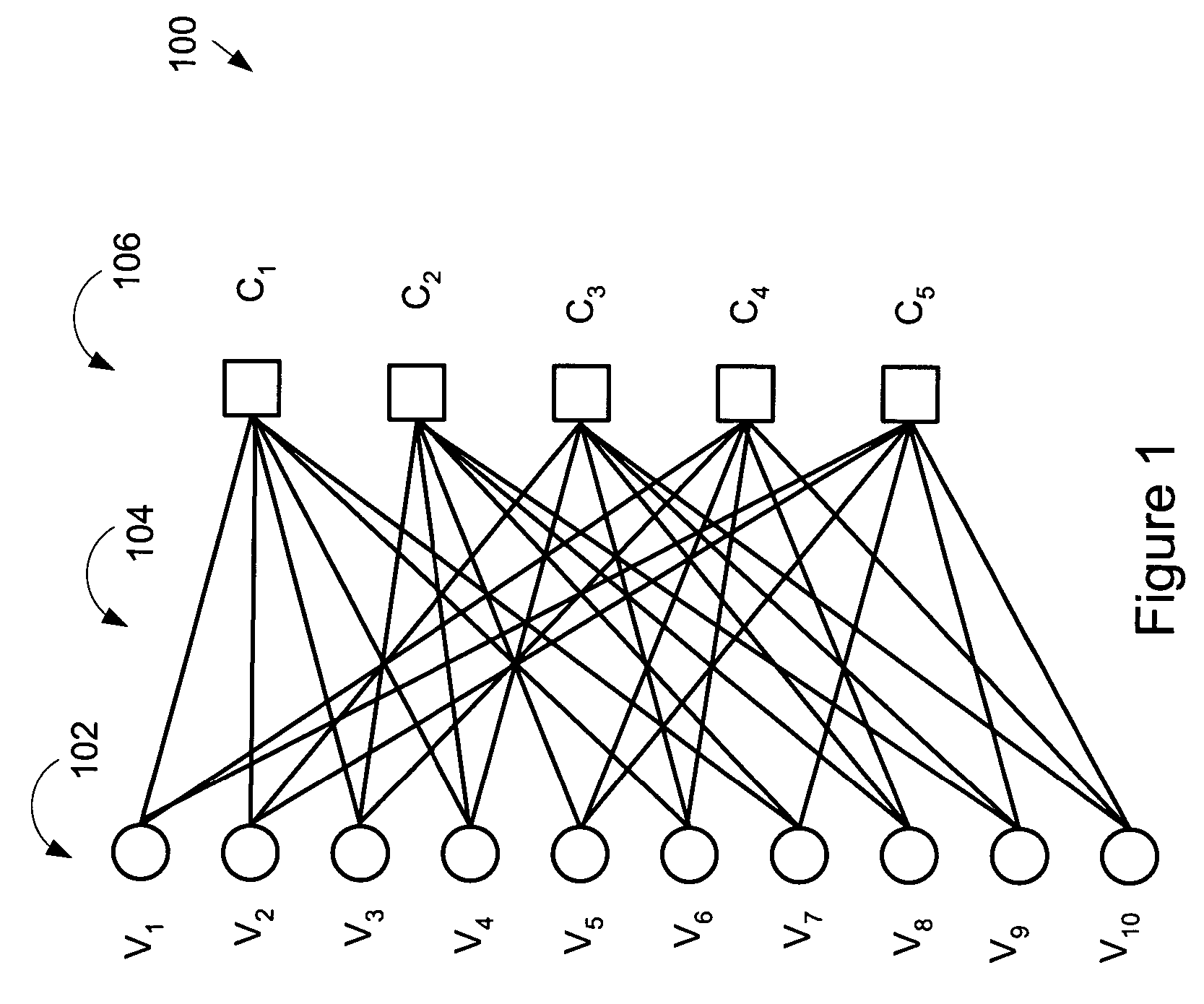
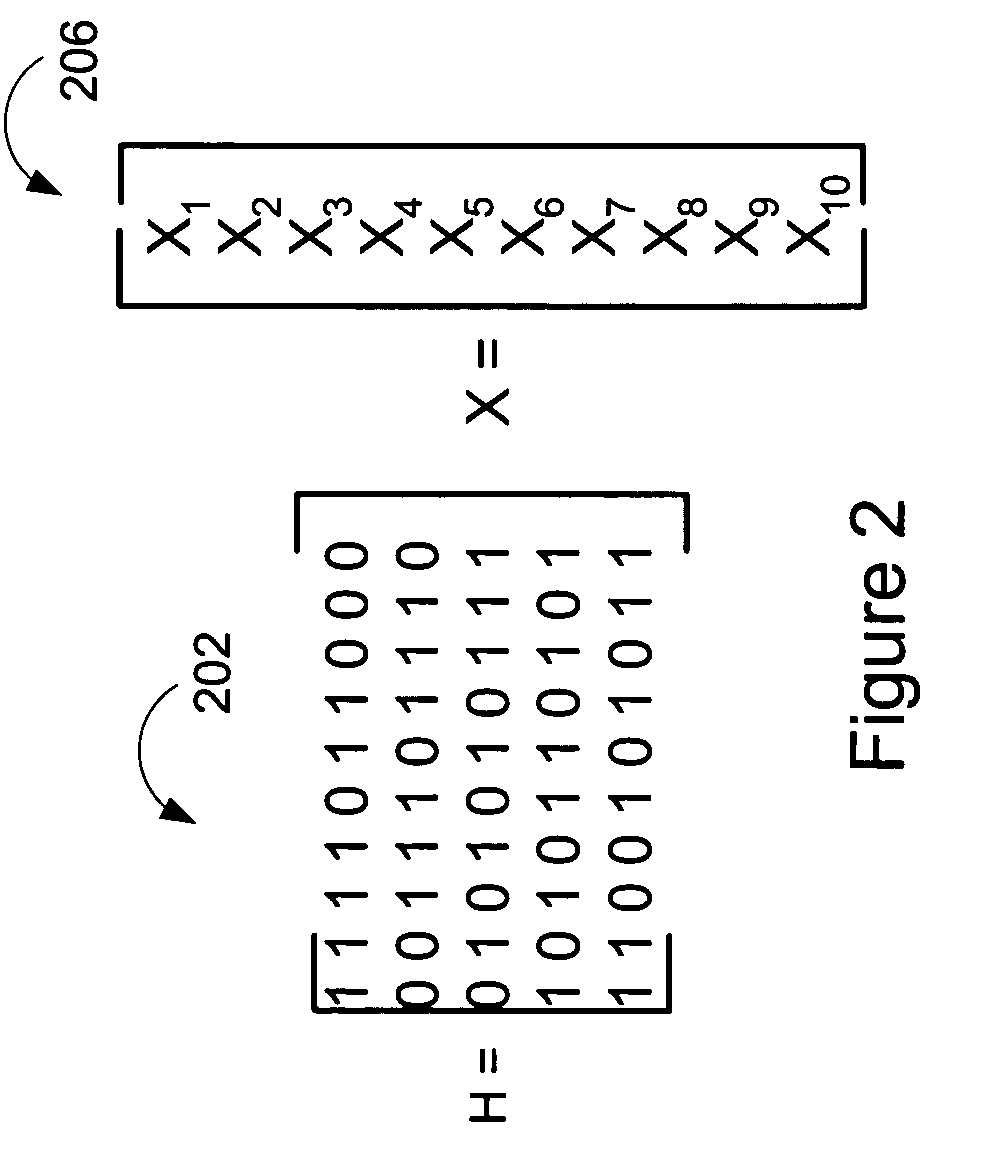
Memory efficient LDPC decoding methods and apparatus
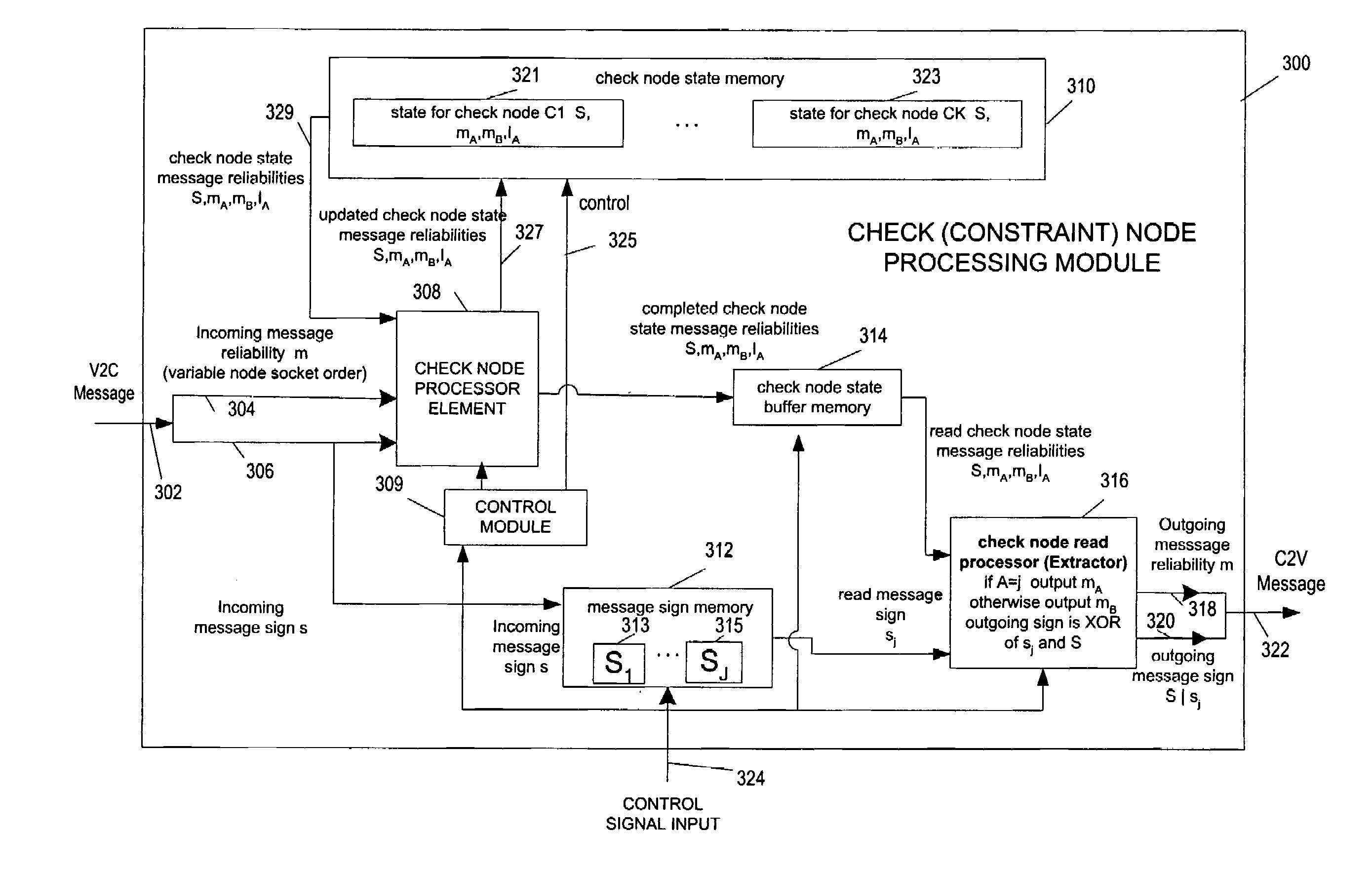
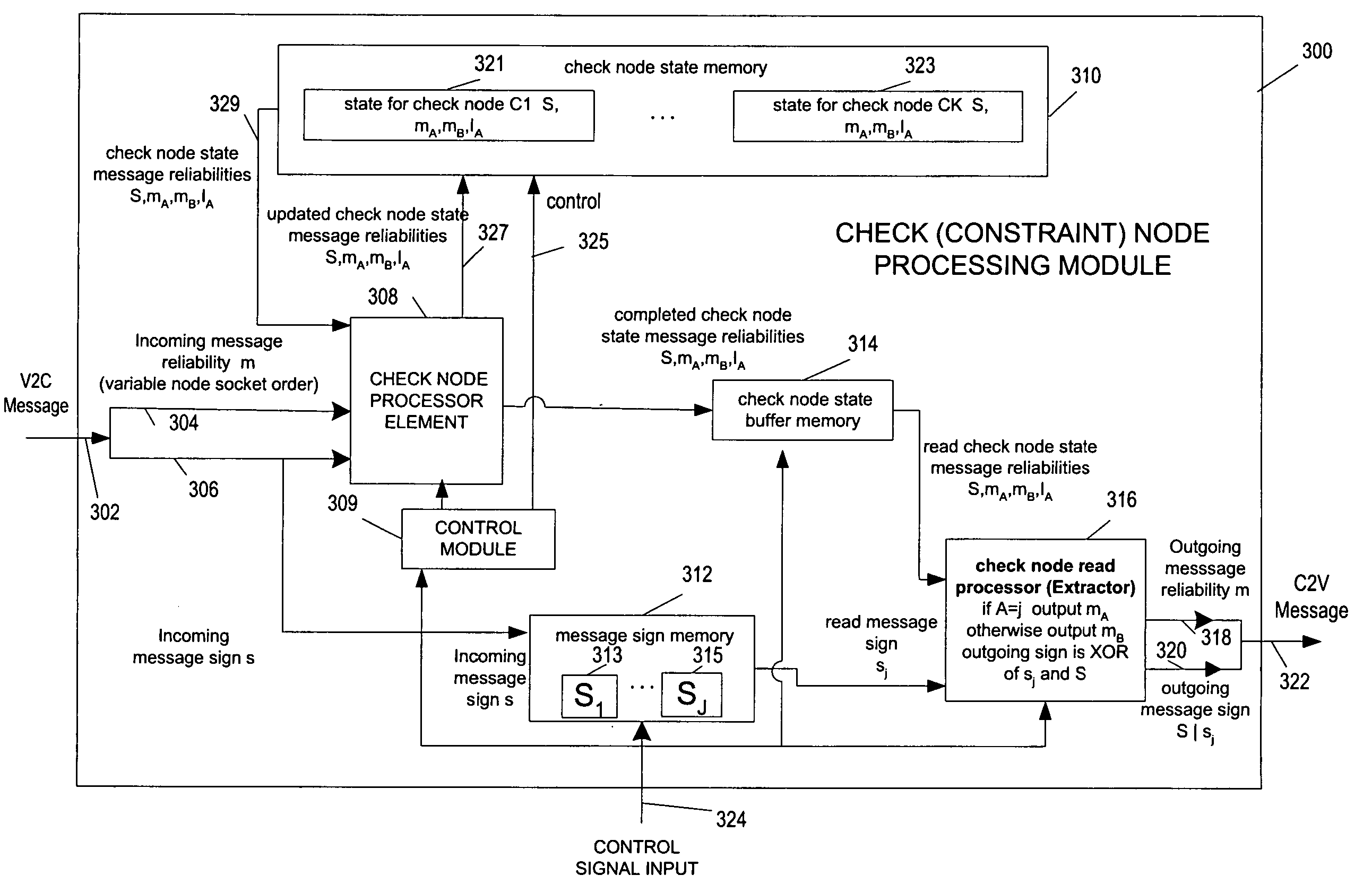
ActiveUS7127659B2Avoiding and reducing delayAvoids significant delayError detection/correctionError correction/detection using multiple parity bitsParallel computingDecodes
Methods and apparatus for implementing memory efficient LDPC decodes are described. In accordance with the invention message information is stored in a compressed state for check node processing operations. The state for a check node is fully updated and then subject to an extraction process to generate check node to variable node messages. The signs of messages received from variable nodes may be stored by the check node processor module of the invention for use in message extraction. The check node processor can process messages in variable node order thereby allowing the variable node processor and check node processor to operate on messages in the same order reducing or eliminating the need to buffer and / or reorder messages passed between check nodes and variable nodes. Graph structures which allow check node processing on one graph iteration to proceed before the previous graph iteration has been completed are also described.
Owner:QUALCOMM INC
Memory efficient LDPC decoding methods and apparatus
ActiveUS20060026486A1Significant delayAvoiding and reducing delayError detection/correctionError correction/detection using multiple parity bitsLdpc decodingDecodes
Methods and apparatus for implementing memory efficient LDPC decodes are described. In accordance with the invention message information is stored in a compressed state for check node processing operations. The state for a check node is fully updated and then subject to an extraction process to generate check node to variable node messages. The signs of messages received from variable nodes may be stored by the check node processor module of the invention for use in message extraction. The check node processor can process messages in variable node order thereby allowing the variable node processor and check node processor to operate on messages in the same order reducing or eliminating the need to buffer and / or reorder messages passed between check nodes and variable nodes. Graph structures which allow check node processing on one graph iteration to proceed before the previous graph iteration has been completed are also described.
Owner:QUALCOMM INC
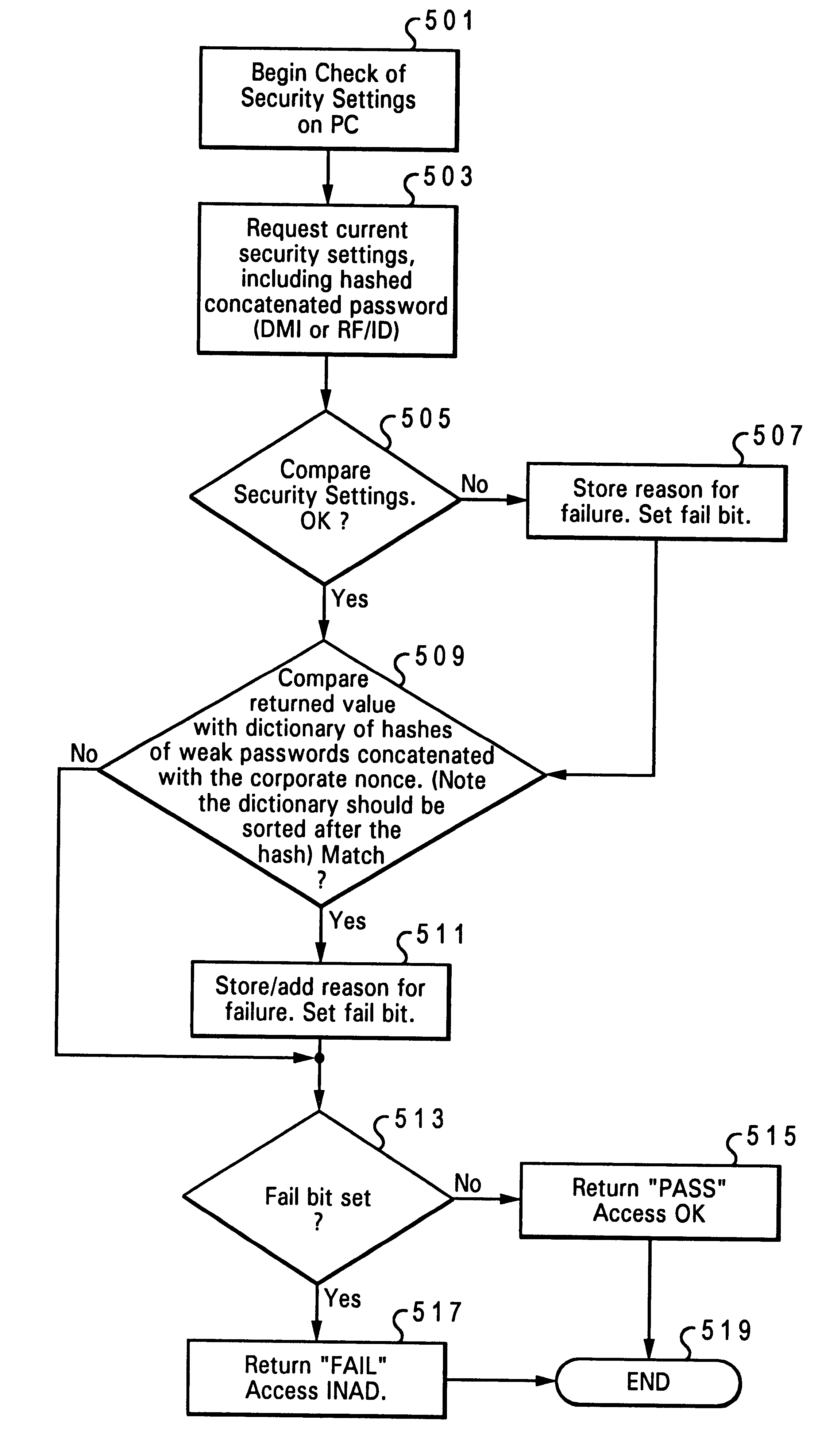
Discrete, background determination of the adequacy of security features of a computer system
InactiveUS6748544B1Valid checkReduce the possibilityDigital data processing detailsDigital computer detailsData processing systemComputerized system
A system for checking the level of system security on a PC platform is disclosed. The system comprises of a Radio Frequency Identification (RFID) unit. The RFID unit scans a PC platform and extracts relevant security information from its Basic Input / Output System (BIOS). The extracted information is analyzed by a data processing system connected to the RFID unit to determine if the security access available on the PC platform is adequate. A threshold adequacy level is established by a system manager. When the security on the PC is inadequate, a signal is generated to alert the network manager and / or the user of the PC to upgrade the PC's security.
Owner:GOOGLE LLC
3-Dimensional image creation device, 3-dimensional image reproduction device, 3-dimensional image processing device, 3-dimensional image processing program, and recording medium containing the program
InactiveUS7636088B2Valid checkCharacter and pattern recognitionSteroscopic systemsConsecutive frameImaging data
An image signal composed of sequential frames is input to a 3-dimensional image creating apparatus, frame by frame. A controller (102) designates the presence / absence of reduction, the presence / absence of joining and 2D select. An image converter (101) creates image data in the format designated by the presence / absence of reduction and the presence / absence of joining. A 3D information creator (103) creates 3D information necessary for displaying the image as a 3-dimensional image by formatting the presence / absence of reduction, the presence / absence of joining and 2D select. A multiplexer (104) converts image data and 3D information in a predetermined format and outputs them to the outside. In this way, it is possible to make the image data for 3-dimensional display versatile and select an arbitrary viewpoint image efficiently.
Owner:SHARP KK
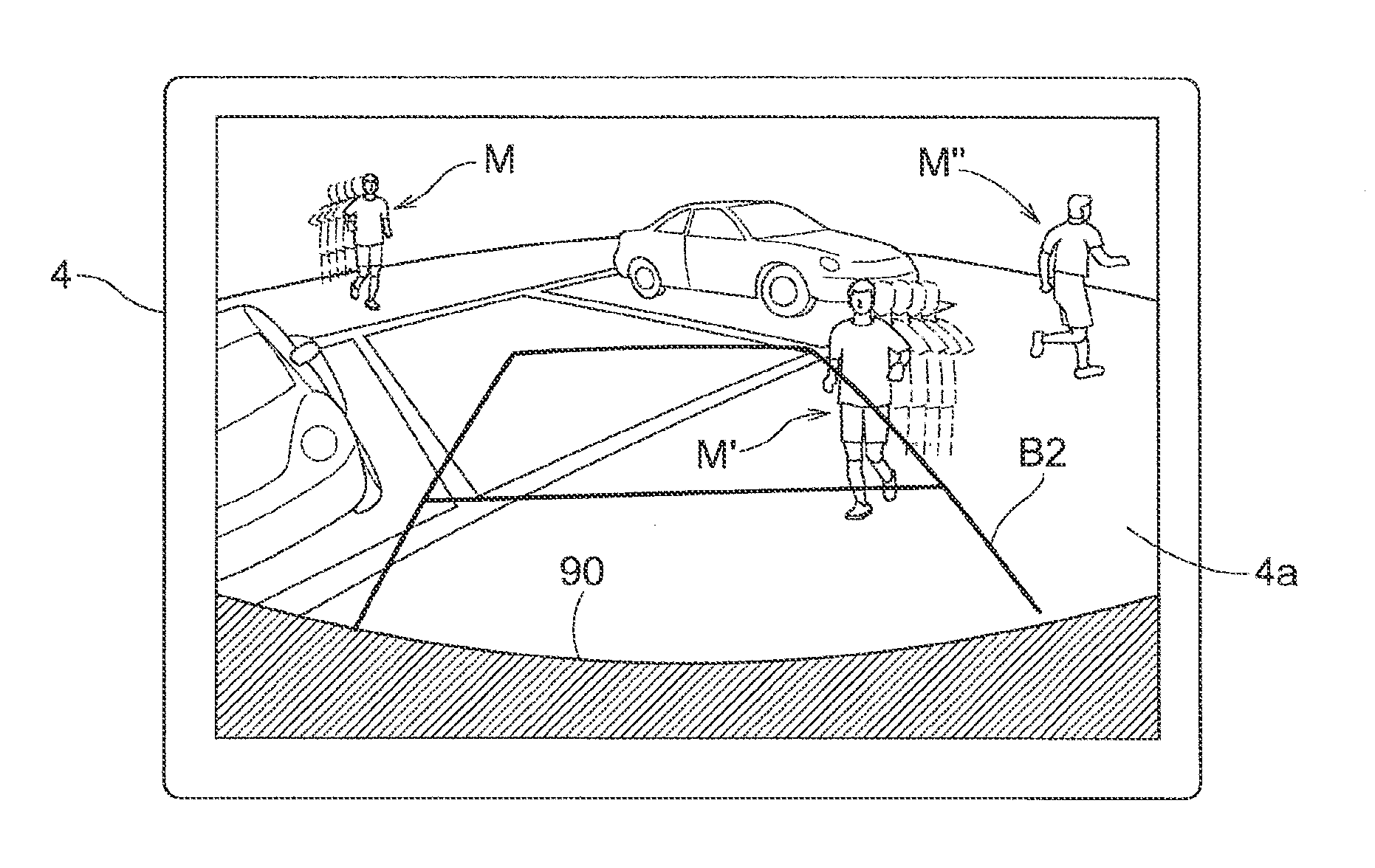
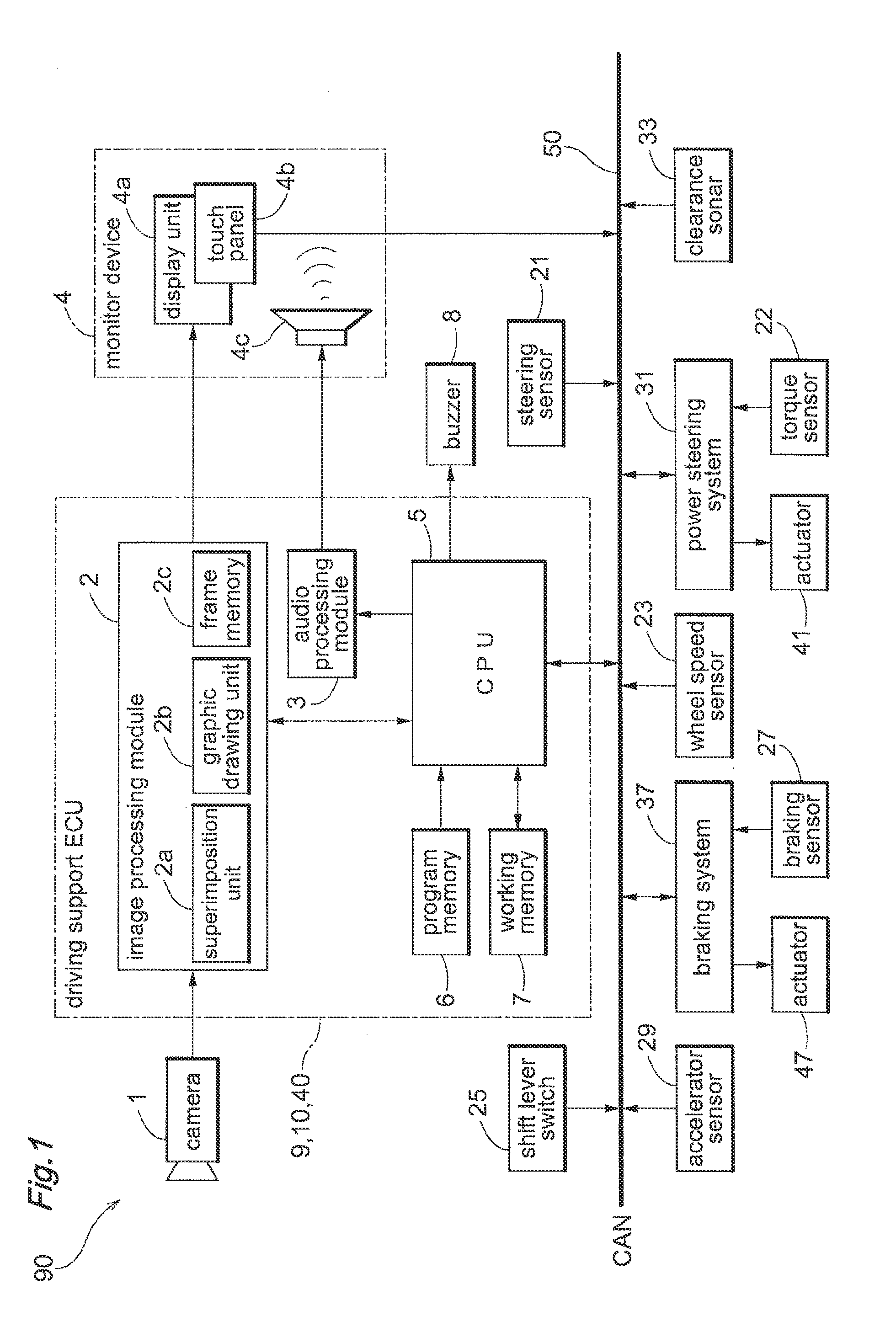
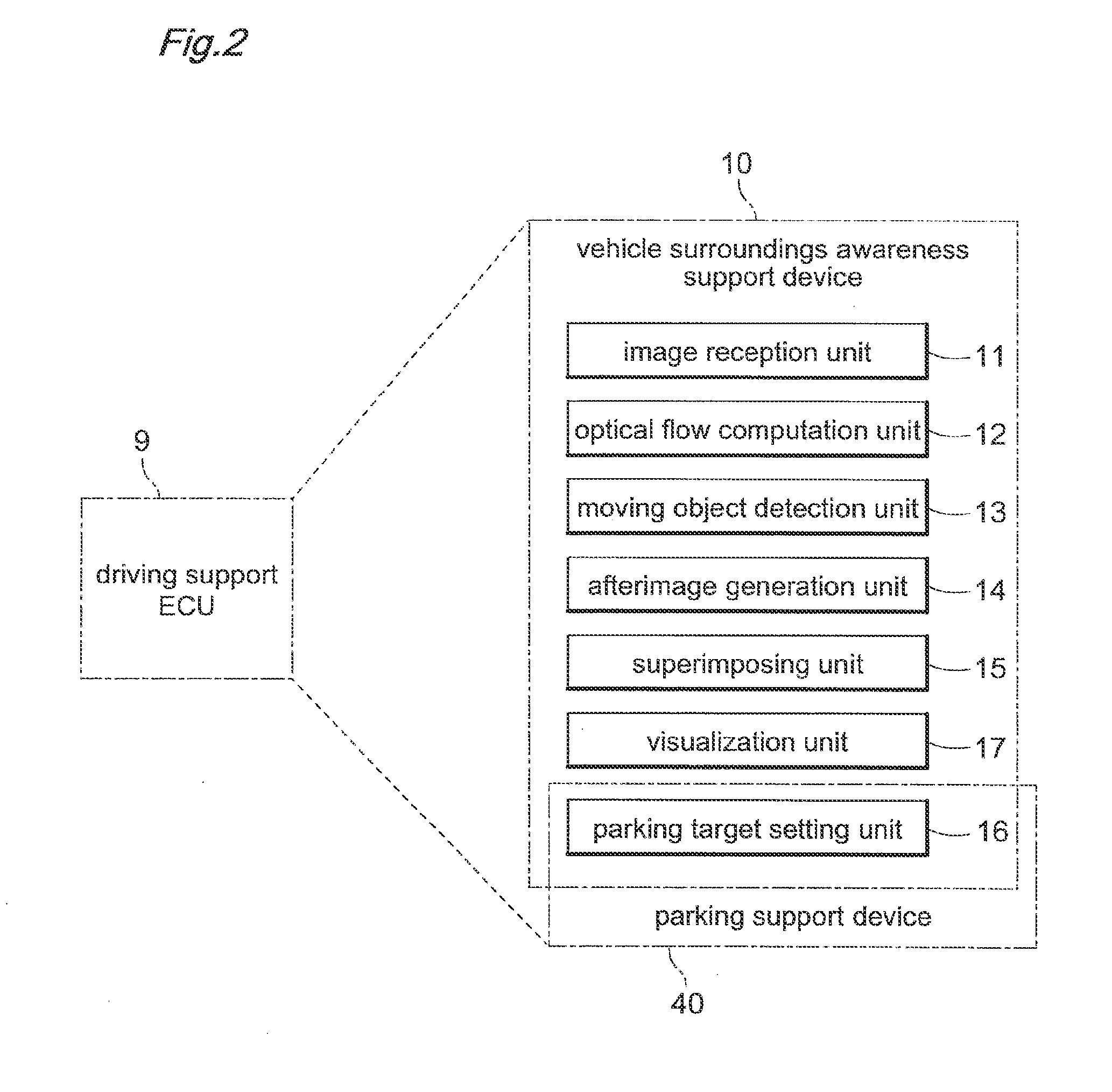
Vehicle surroundings awareness support device
InactiveUS20120133769A1Preventing excessive detectionExcessive superimposingImage enhancementImage analysisDriver/operatorDisplay device
Provided is a vehicle surroundings awareness support device capable of providing a prompt for a driver to intuitively direct their attention, without the driver feeling hassled. Captured images comprising a plurality of frames taken sequentially by an onboard camera for imaging the surroundings of the vehicle are received; an optical flow is computed on the basis of feature points contained in the plurality of frames imaged at different times; moving objects in the surroundings of the vehicle are detected on the basis of the optical flow; and a display for showing movement trajectories for the moving objects is superimposed on the captured images on the basis of the optical flow.
Owner:AISIN SEIKI KK
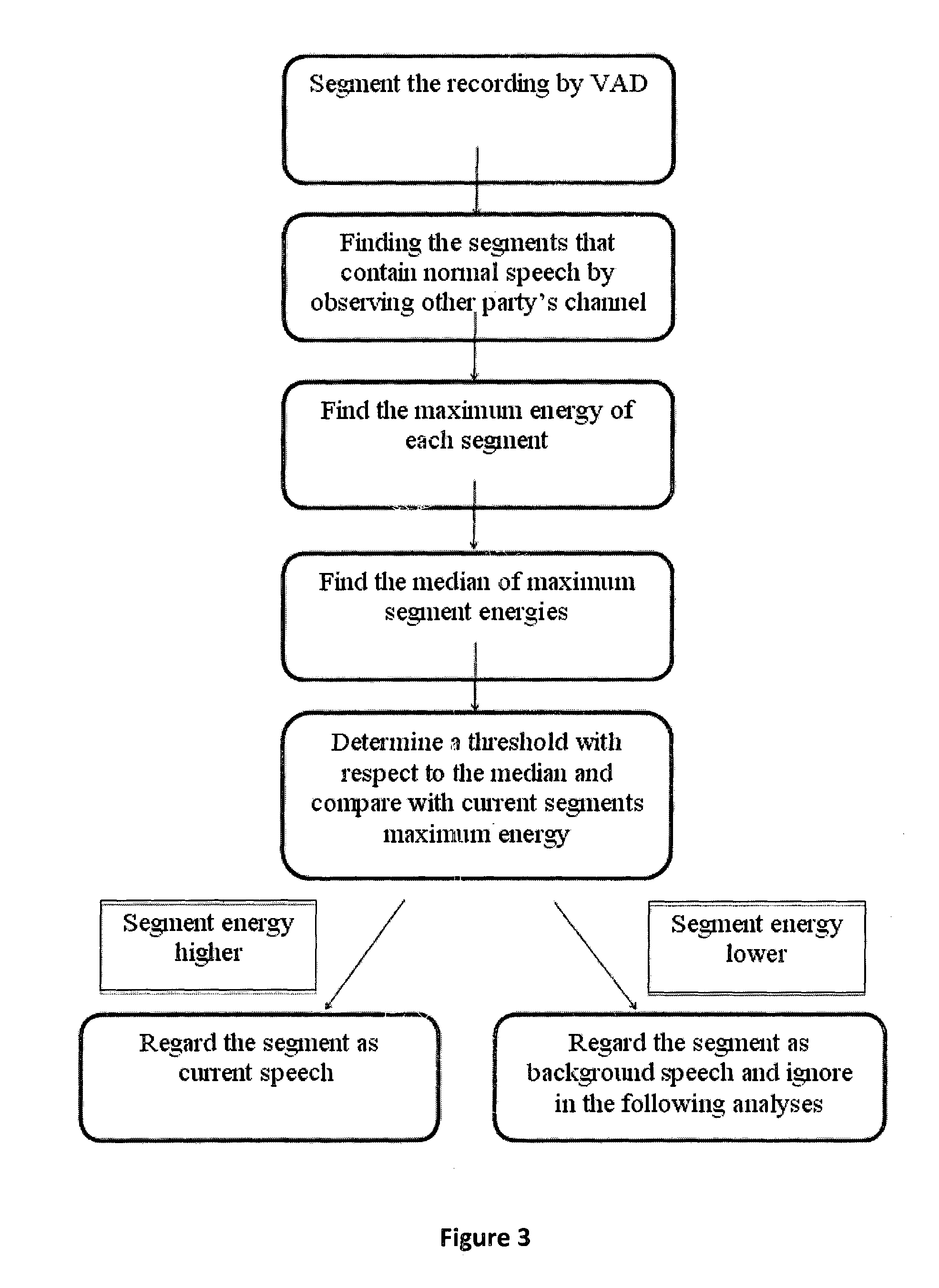
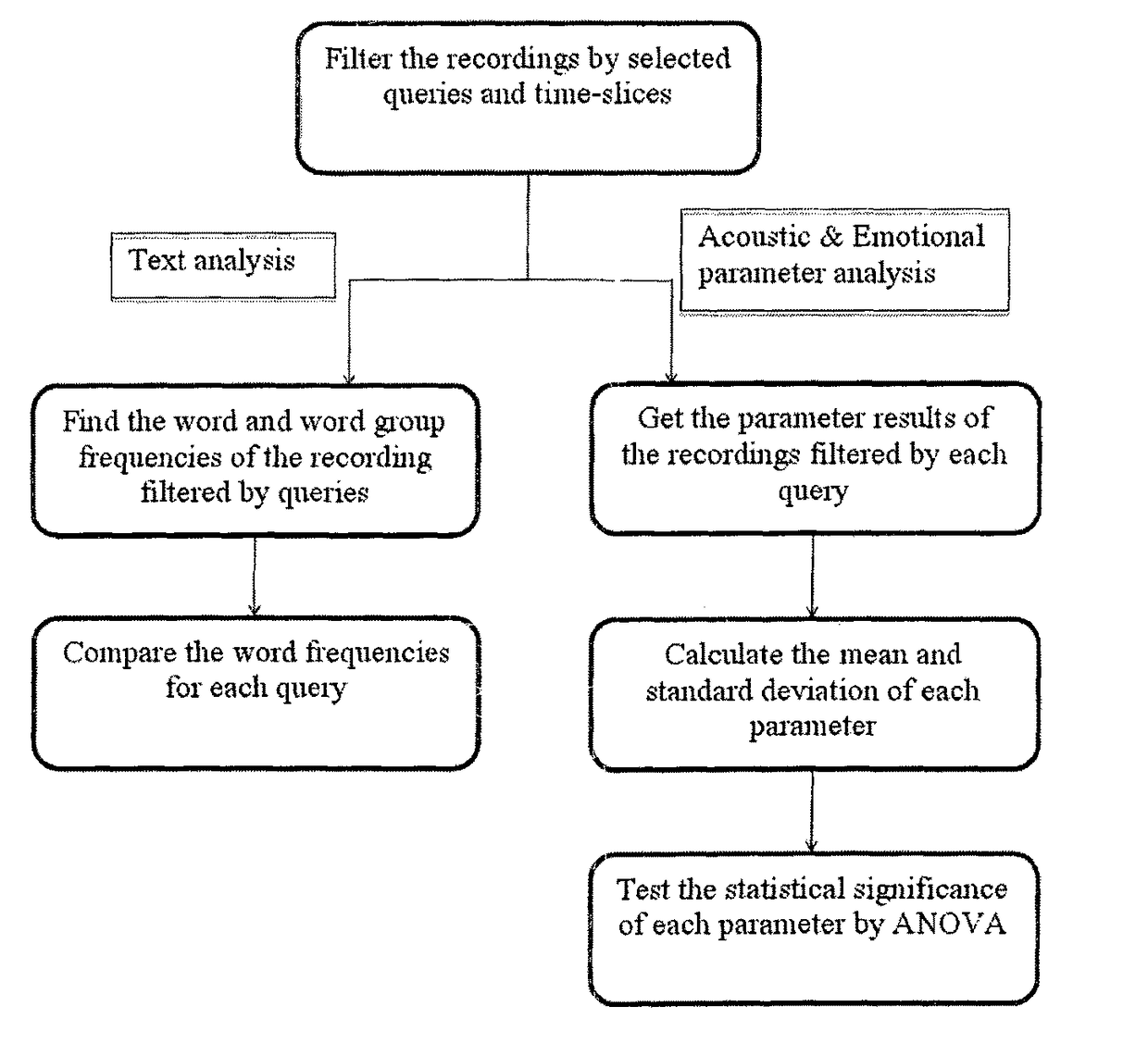
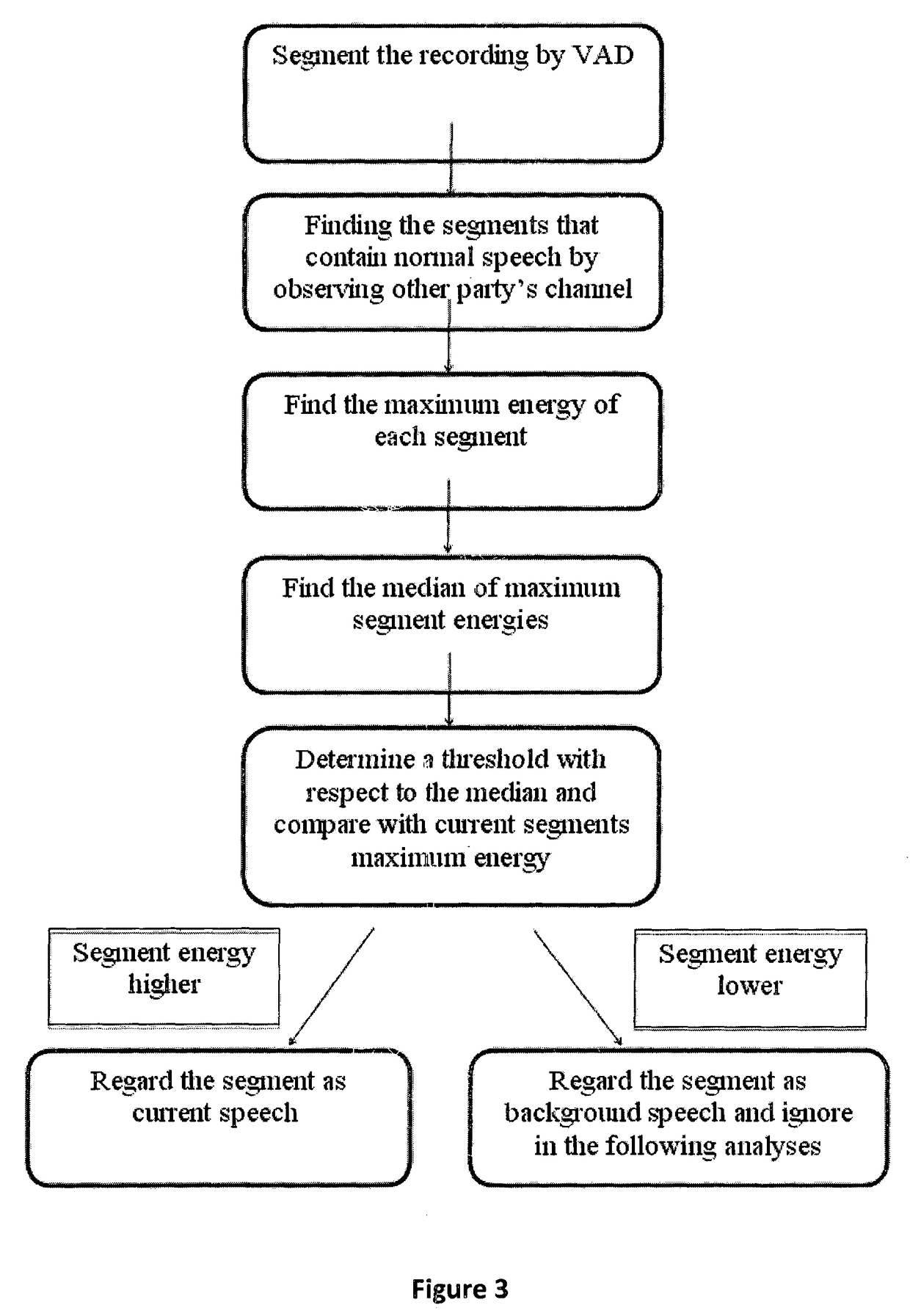
Speech analytics system and methodology with accurate statistics
ActiveUS20150350438A1Eliminate disadvantageLow costAutomatic call-answering/message-recording/conversation-recordingSpecial service for subscribersSpeech analyticsSpeech sound
The present invention relates to implementing new ways of automatically and robustly evaluating agent performance, customer satisfaction, campaign and competitor analysis in a call-center and it is comprising; analysis consumer server, call pre-processing module, speech-to-text module, emotion recognition module, gender identification module and fraud detection module.
Owner:SESTEK SES & ILETISIM BILGISAYAR TEKNOLOJILERI SANAYII & TICARET ANONIM SIRKETI
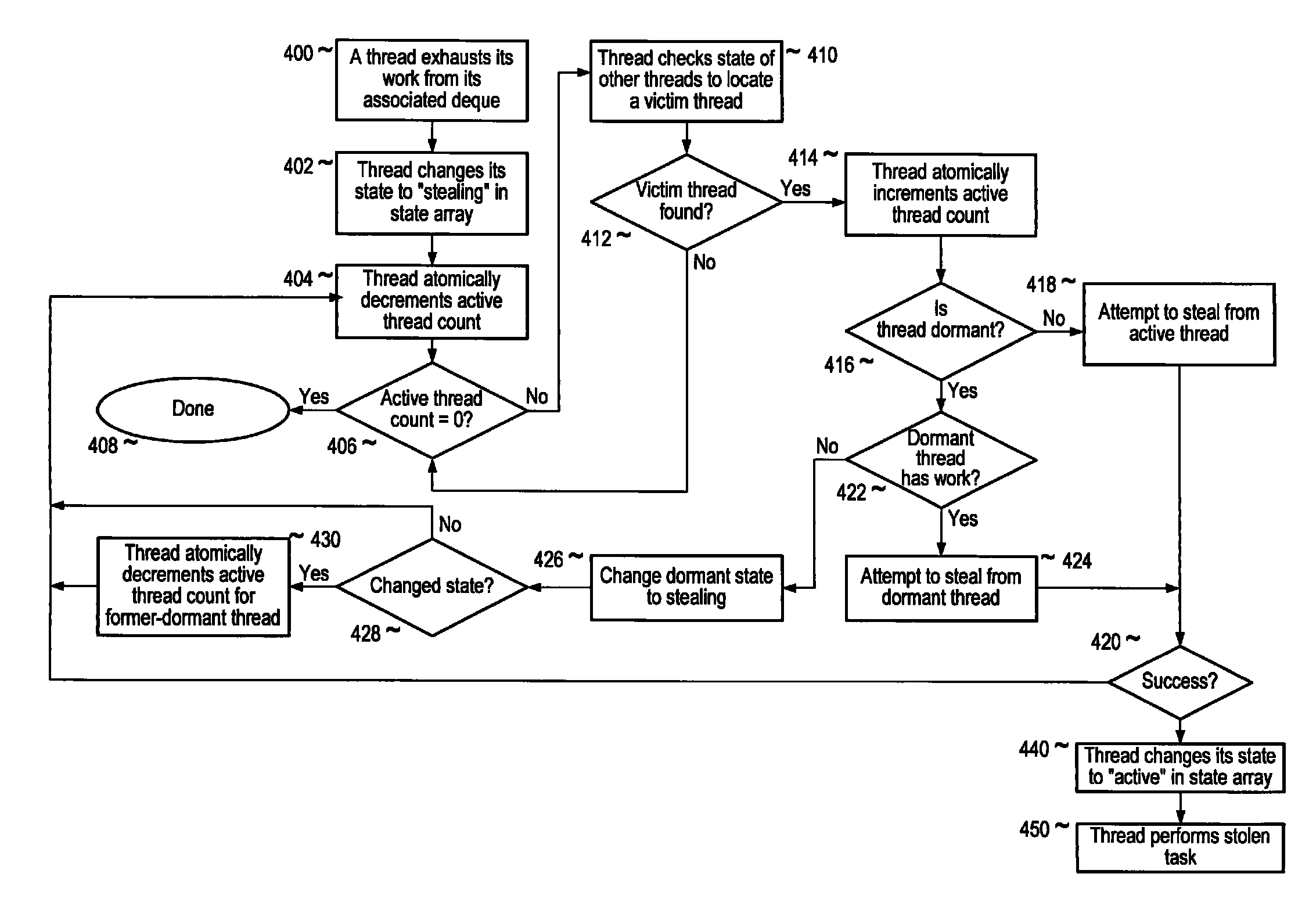
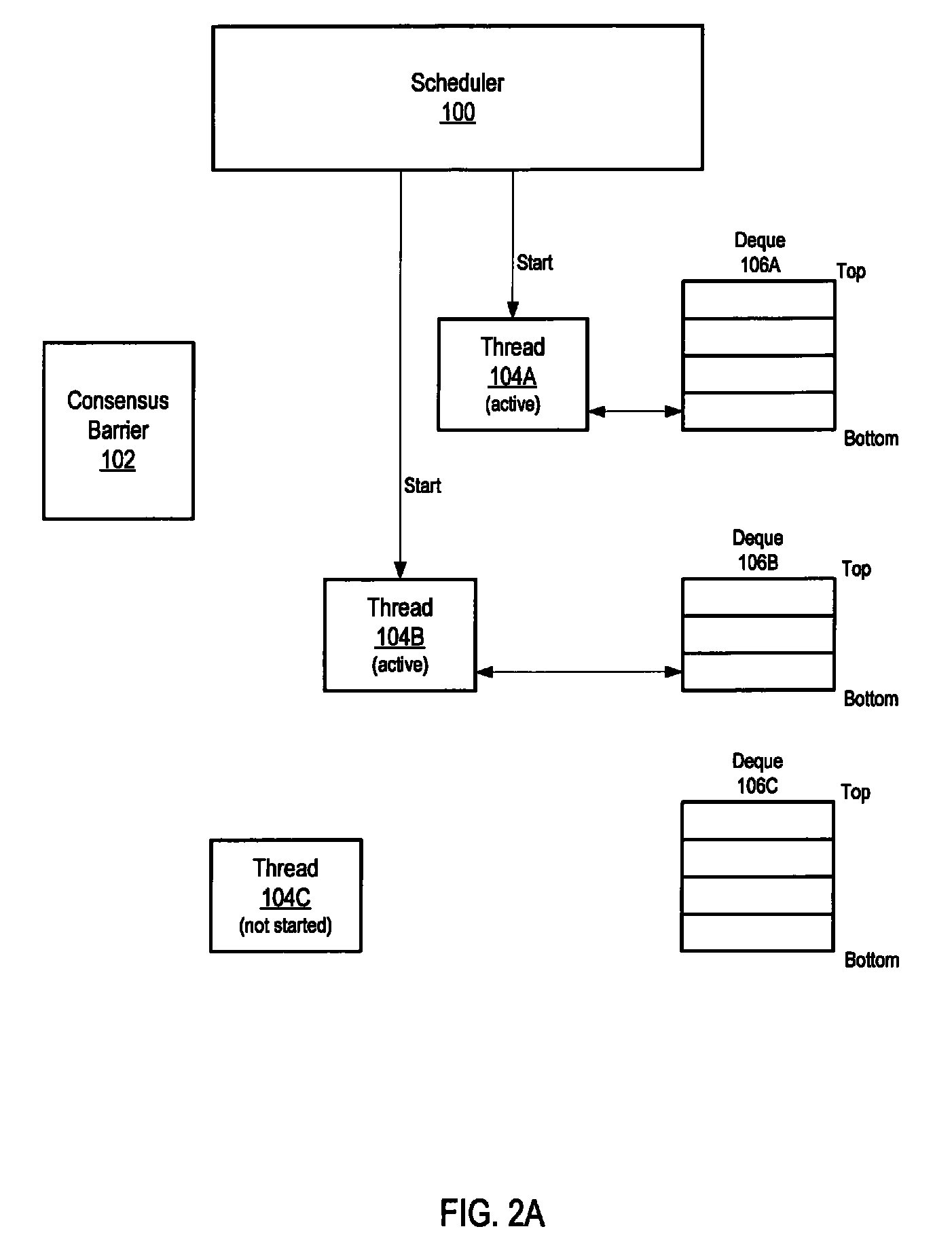
Barrier synchronization method and apparatus for work-stealing threads
ActiveUS7945911B1Valid checkProgram synchronisationSpecial data processing applicationsWaste collectionParallel computing
Method and apparatus for barrier synchronization of threads, for example work-stealing threads. Embodiments may provide a consensus barrier synchronization mechanism that allows a “stop world” operation being performed by two or more worker threads configured to “steal” work from other threads to complete, even if one or more of the threads are not scheduled / started by the thread scheduler and thus do not rendezvous or “check in” at a consensus barrier in a timely manner. In embodiments, portions (subtasks) of the overall task which were assigned to the tardy thread may have been completed by other work-stealing threads, and one of the other threads may check in the tardy thread at the consensus barrier upon determining that the thread is dormant and does not have any more apportioned work to be performed. In one embodiment, the task being performed may be garbage collection for a process.
Owner:ORACLE INT CORP
3-dimensional image creating apparatus, 3-dimensional image reproducing apparatus, 3-dimensional image processing apparatus, 3-dimensional image processing program and recording medium recorded with the program
InactiveUS20100039499A1Valid checkCharacter and pattern recognitionCathode-ray tube indicatorsViewpointsConsecutive frame
An image signal composed of sequential frames is input to a 3-dimensional image creating apparatus, frame by frame. A controller (102) designates the presence / absence of reduction, the presence / absence of joining and 2D select. An image converter (101) creates image data in the format designated by the presence / absence of reduction and the presence / absence of joining. A 3D information creator (103) creates 3D information necessary for displaying the image as a 3-dimensional image by formatting the presence / absence of reduction, the presence / absence of joining and 2D select. A multiplexer (104) converts image data and 3D information in a predetermined format and outputs them to the outside. In this way, it is possible to make the image data for 3-dimensional display versatile and select an arbitrary viewpoint image efficiently.
Owner:SHARP KK
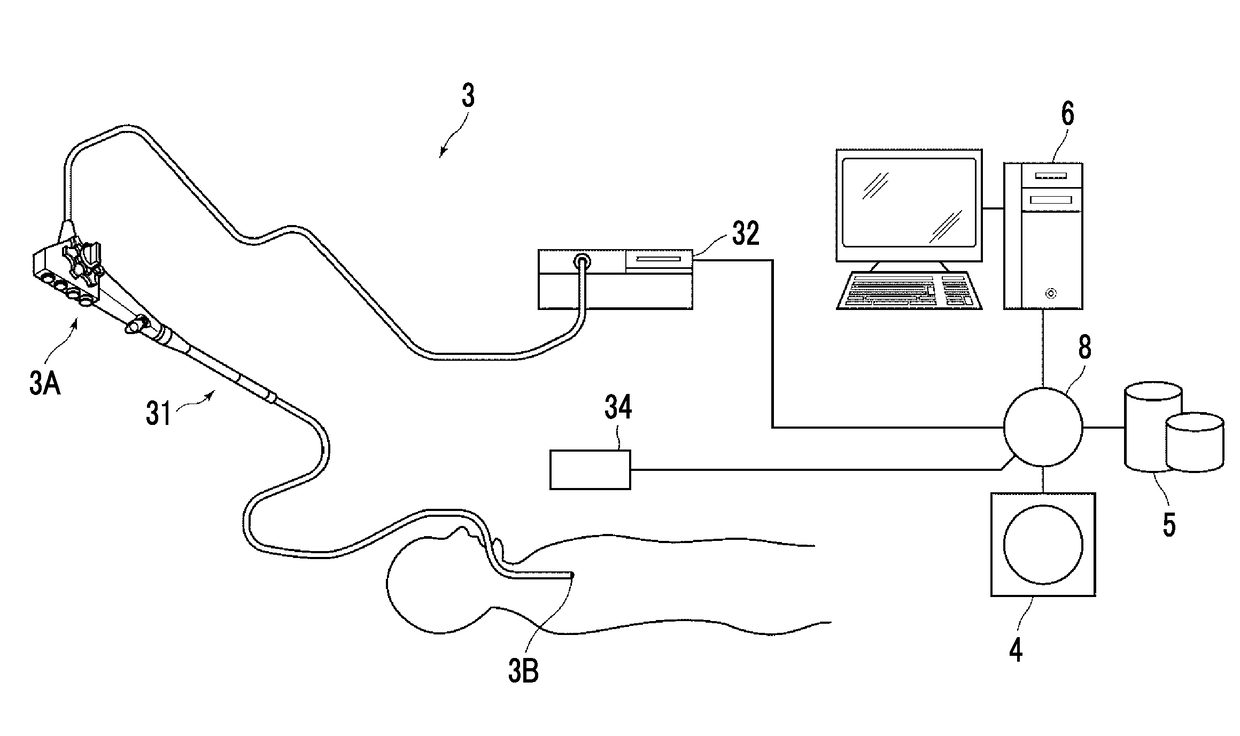
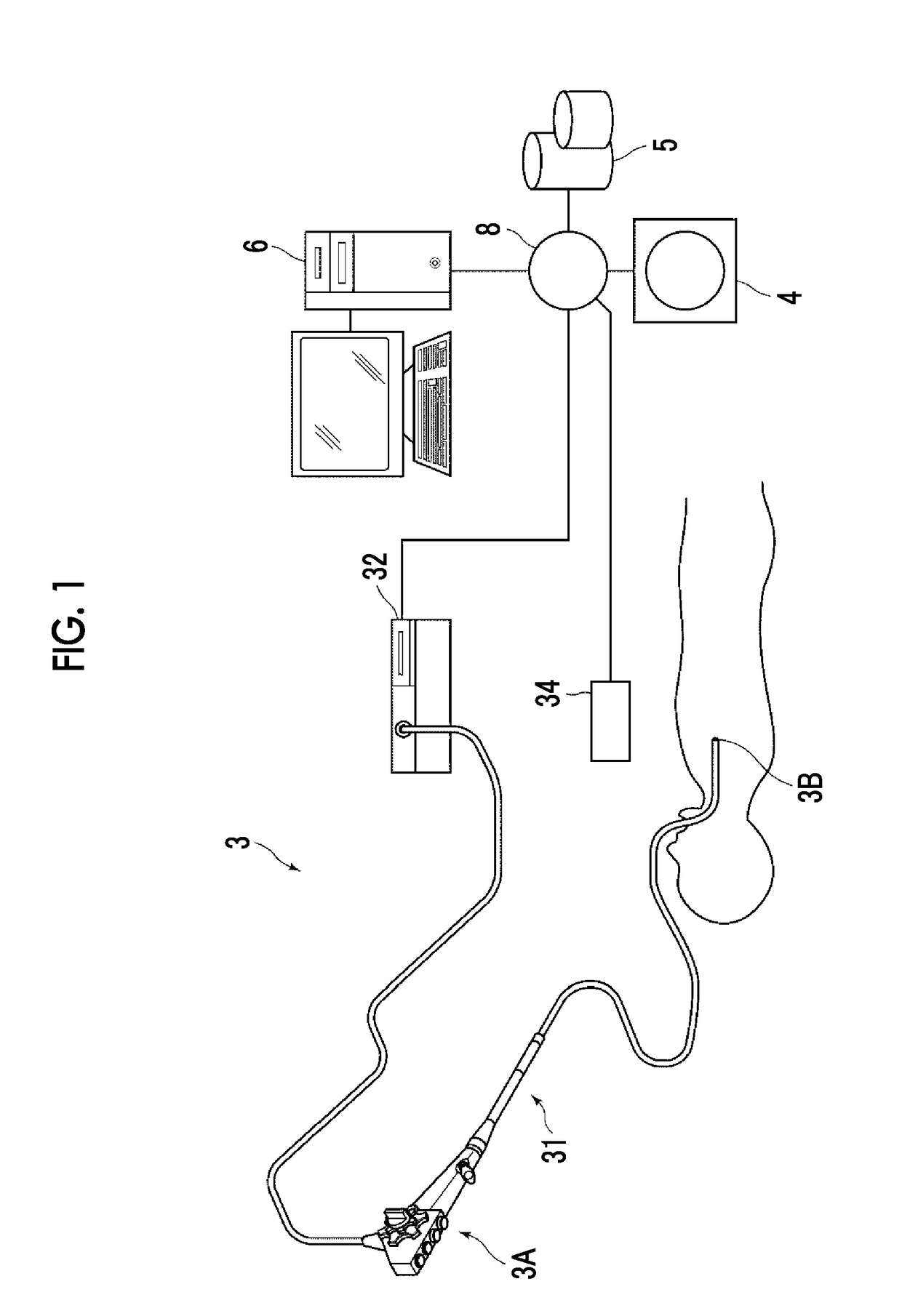
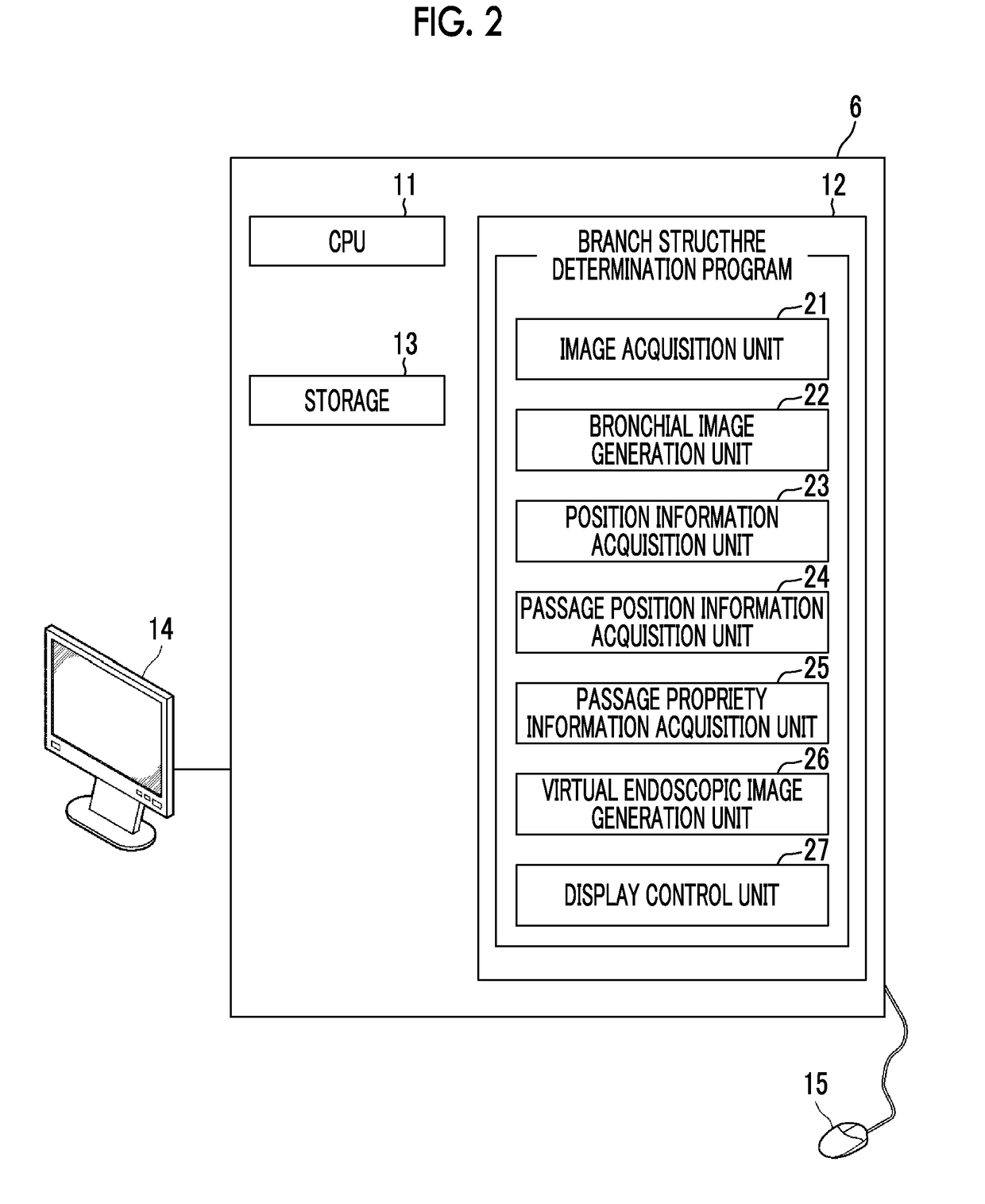
Endoscopic examination support device, endoscopic examination support method, and endoscopic examination support program
InactiveUS20170340241A1Easy to identifyValid checkUltrasonic/sonic/infrasonic diagnosticsBronchoscopesInformation transmissionEndoscope
A bronchial image generation unit generates a bronchial image and a position information acquisition unit acquires position information of an endoscope in a bronchus. A passage position information acquisition unit acquires passage position information representing a passage position of the endoscope and a passage propriety information acquisition unit acquires passage propriety information representing portions through which the endoscope can be passed and a portion through which the endoscope cannot be passed. A display control unit displays a bronchial image by changing a display state of a portion of the bronchial image through which the endoscope has been passed and a portion of the bronchial image through which the endoscope has not been passed using the passage position information, and changing a display state of portions of the bronchial image through which the endoscope can be passed and cannot be passed using the passage propriety information.
Owner:FUJIFILM CORP
Information processing apparatus, information processing method, and program
InactiveUS20100053355A1Valid checkSimply and intuitively performTelevision system detailsCathode-ray tube indicatorsInformation processingComputer hardware
An information processing apparatus includes: display means; operation input receiving means; and display control means for making a display control of allowing an image to correspond to an image card as an object imitating a real card, displaying a check image, which indicates a shape in which a plurality of the image cards overlap, on the display means, displaying one of an image corresponding to a specific image card and information indicating the image in a partial or overall area of the specific image card when a check operation indicating an instruction to check the specific image card is received, and changing a display state of the display means from a first state where the checking image is displayed to a second state where the image corresponding to the specific image card is displayed when a selection operation indicating that the specific image card is selected is received.
Owner:SONY CORP
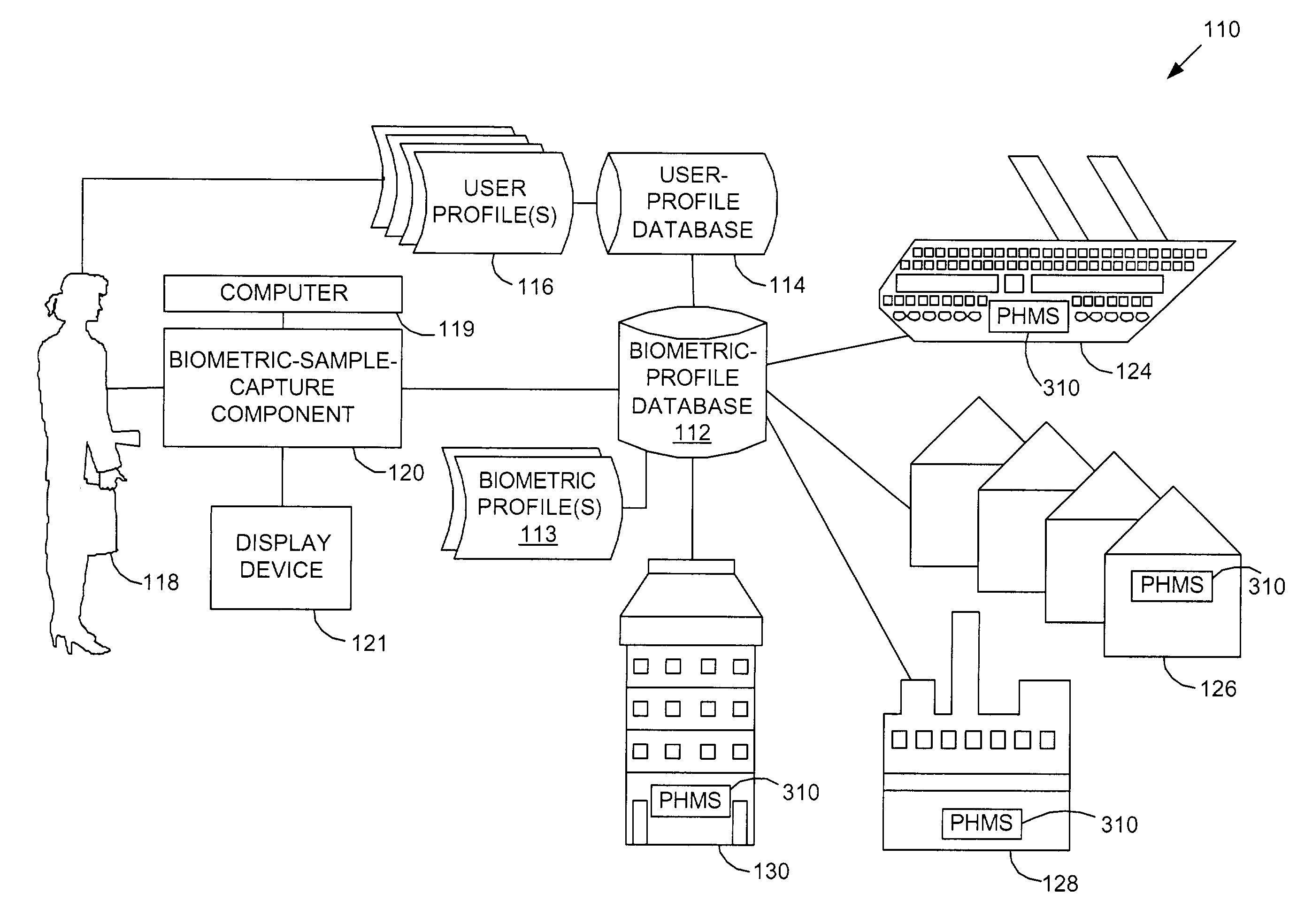
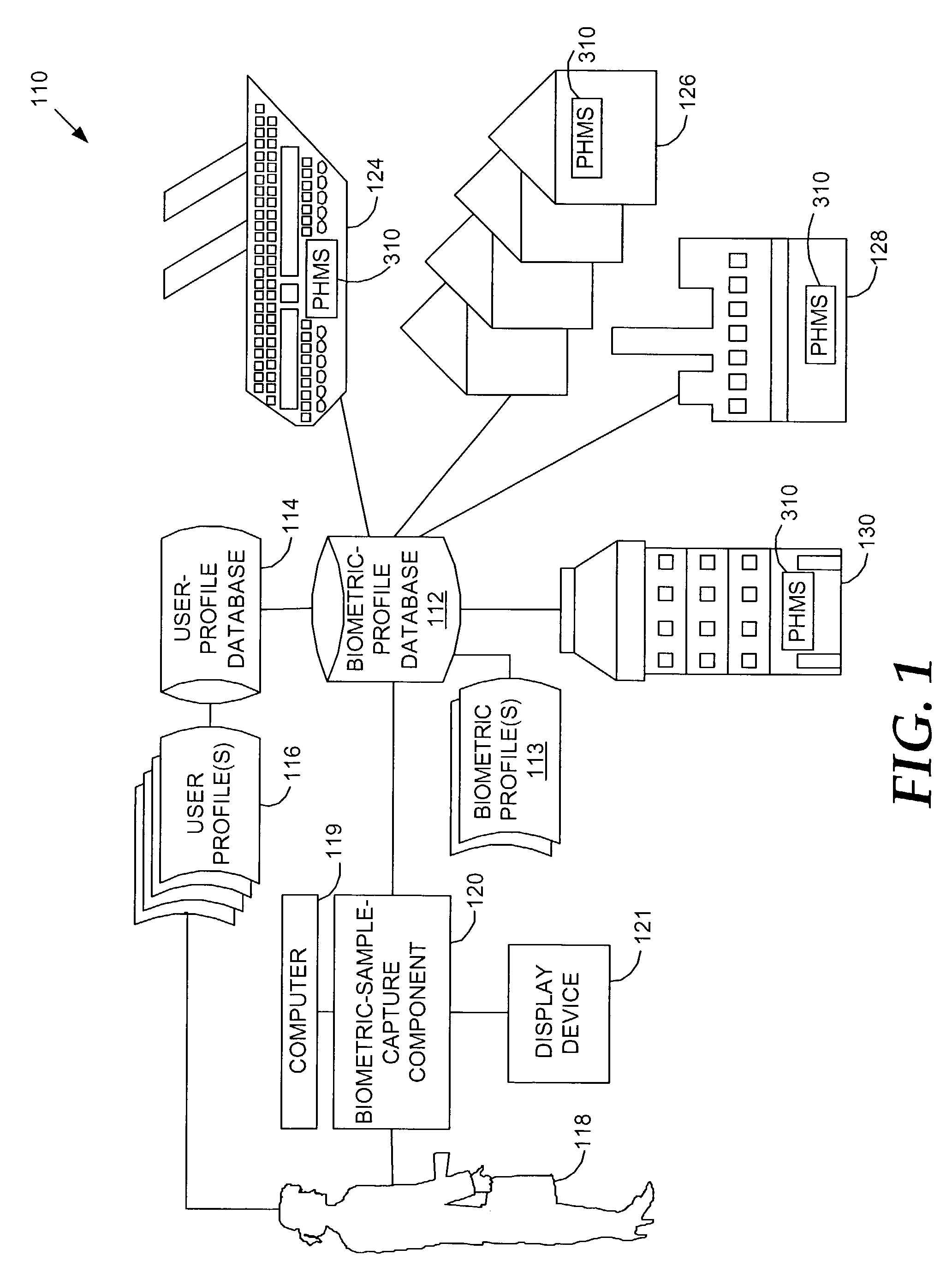
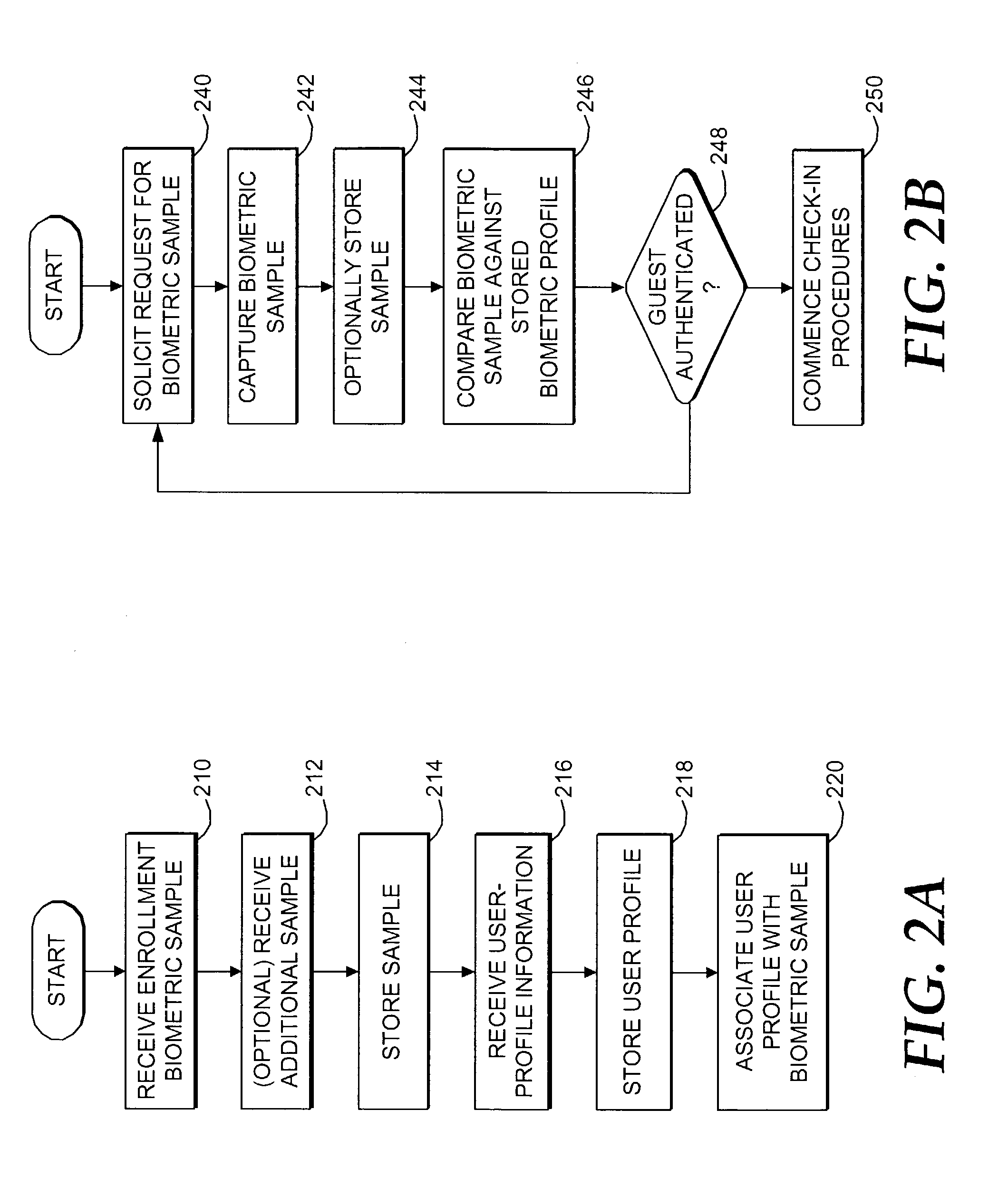
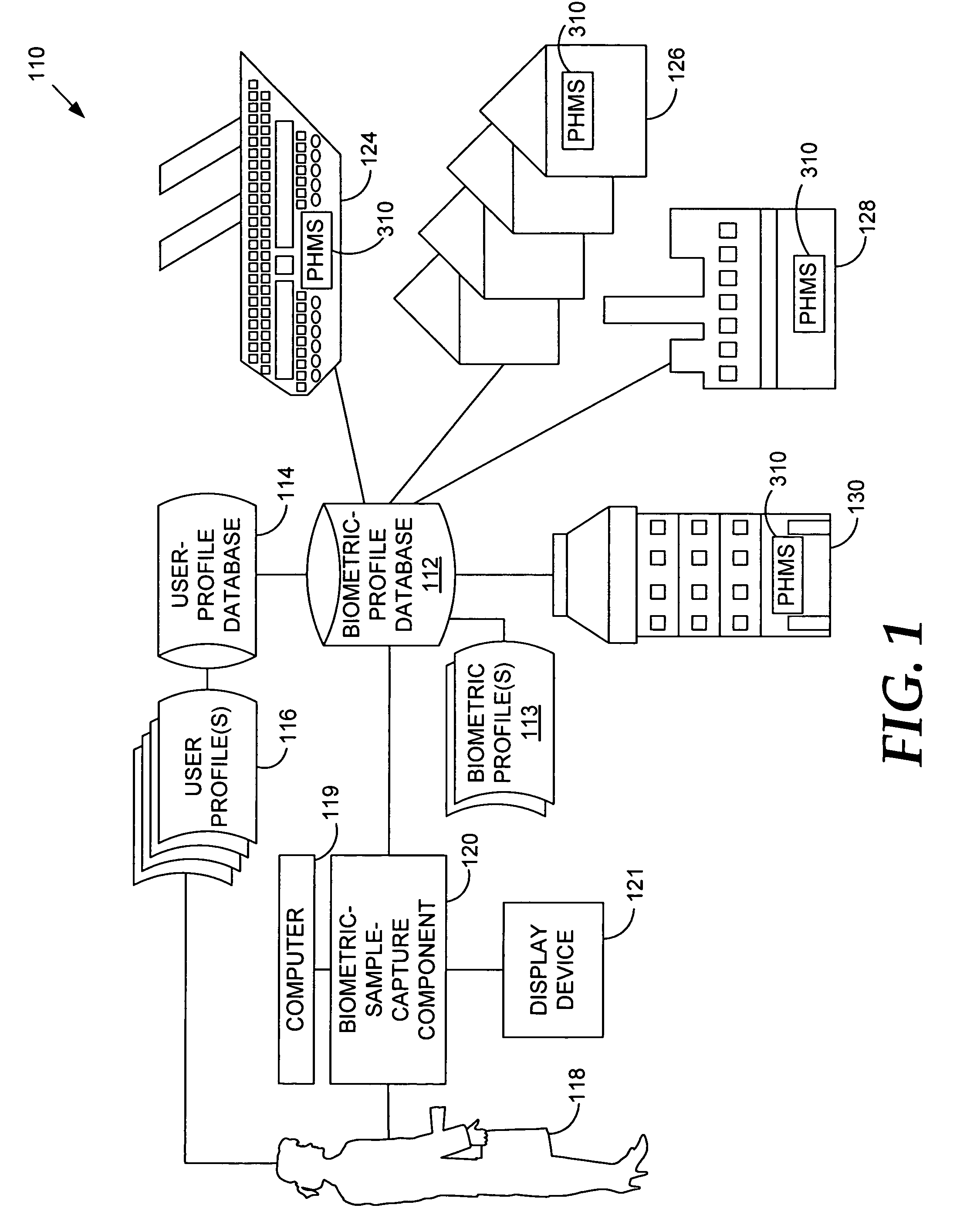
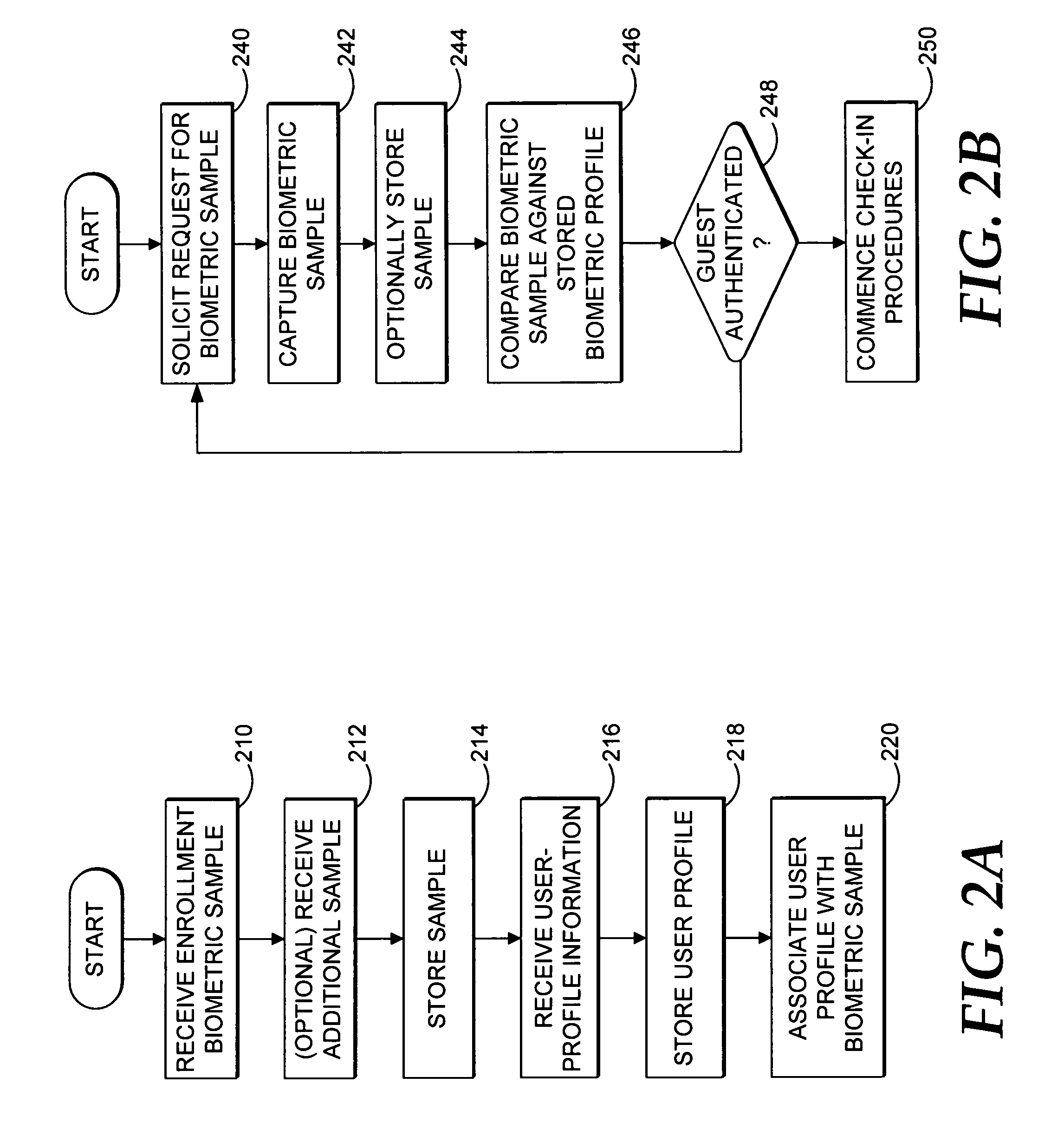
Biometric authentication of hospitality-site customers
ActiveUS6985070B1Valid checkReduce the possibilityElectric signal transmission systemsImage analysisInternet privacyUser profile
A method and system for checking a guest into a hospitality site is provided. A biometric sample is captured from a guest using a biometric-sample-capture device to create a portable biometric profile. The biometric sample is compared to a biometric sample previously stored in a memory location. If the guest is authenticated, he / she is approved for check-in. A user profile can be retrieved that has a set of user preferences. These user preferences can then be used to customize the guests stay at the hospitality site. Many hospitality sites can remotely access the biometric profile to effect authentication.
Owner:T MOBILE INNOVATIONS LLC
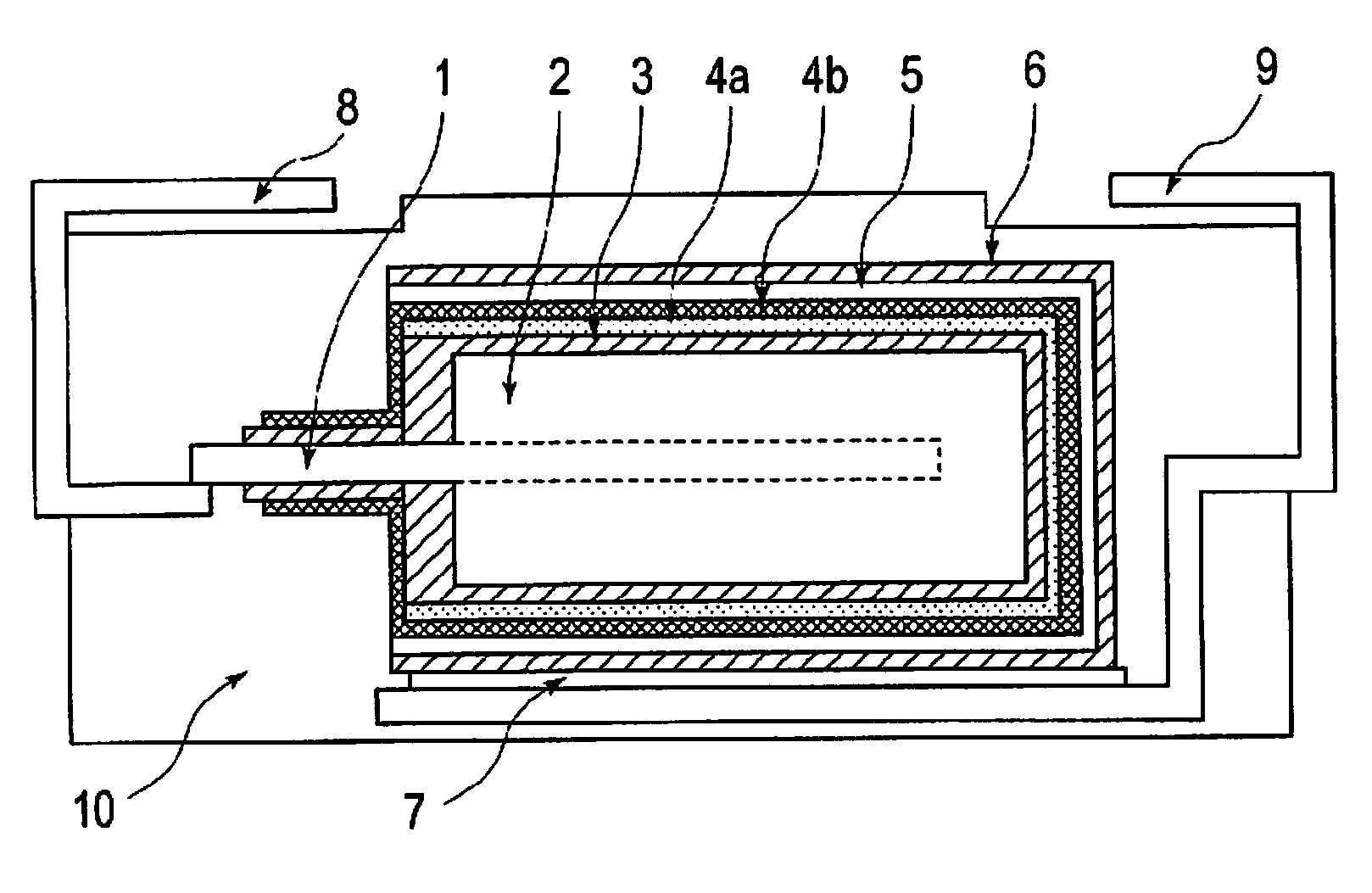
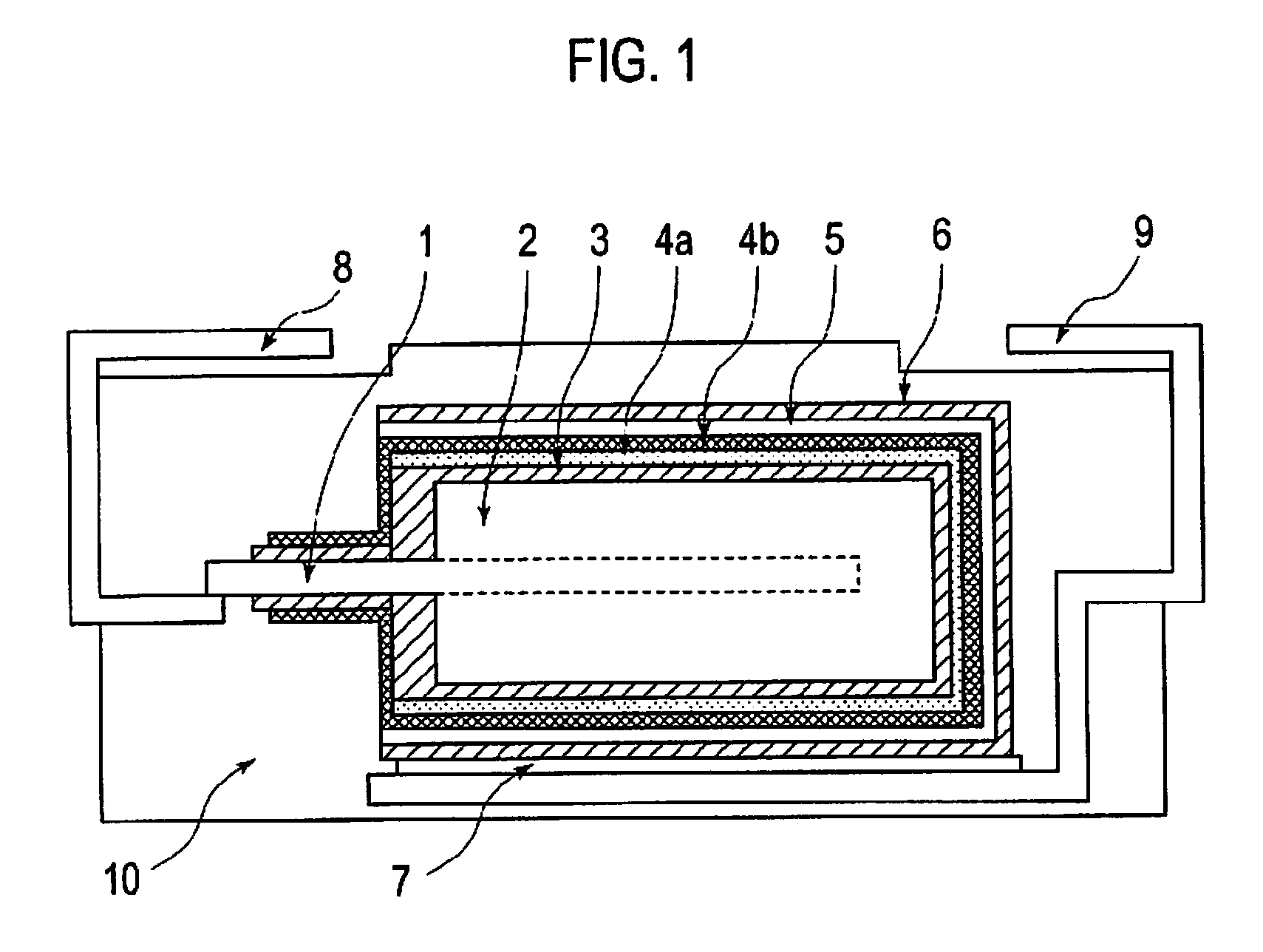
Solid electrolytic capacitor
ActiveUS20090128997A1Reduce capacitanceAdhesivenessAnodisationSolid electrolytic capacitorsElectrolysisConductive polymer
An aspect of the invention provides a solid electrolytic capacitor that comprises: an anode formed of a valve metal or an alloy mainly made of a valve metal; a dielectric layer formed on a surface of the anode; a first conducting polymer layer formed on the dielectric layer, the first conducting polymer layer containing a non-ionic surfactant; a second conducting polymer layer formed on the first conducting polymer layer; and a cathode layer formed on the second conducting polymer layer.
Owner:SANYO ELECTRIC CO LTD
Biometric authentication of hospitality-site customers
InactiveUS7116211B1Valid checkReduce the possibilityElectric signal transmission systemsImage analysisInternet privacyUser profile
A method and system for checking a guest into a hospitality site is provided. A biometric sample is captured from a guest using a biometric-sample-capture device to create a portable biometric profile. The biometric sample is compared to a biometric sample previously stored in a memory location. If the guest is authenticated, he / she is approved for check-in. A user profile can be retrieved that has a set of user preferences. These user preferences can then be used to customize the guests stay at the hospitality site. Many hospitality sites can remotely access the biometric profile to effect authentication.
Owner:SPRINT CORPORATION
Data storage method and apparatus utilizing evolution and hashing
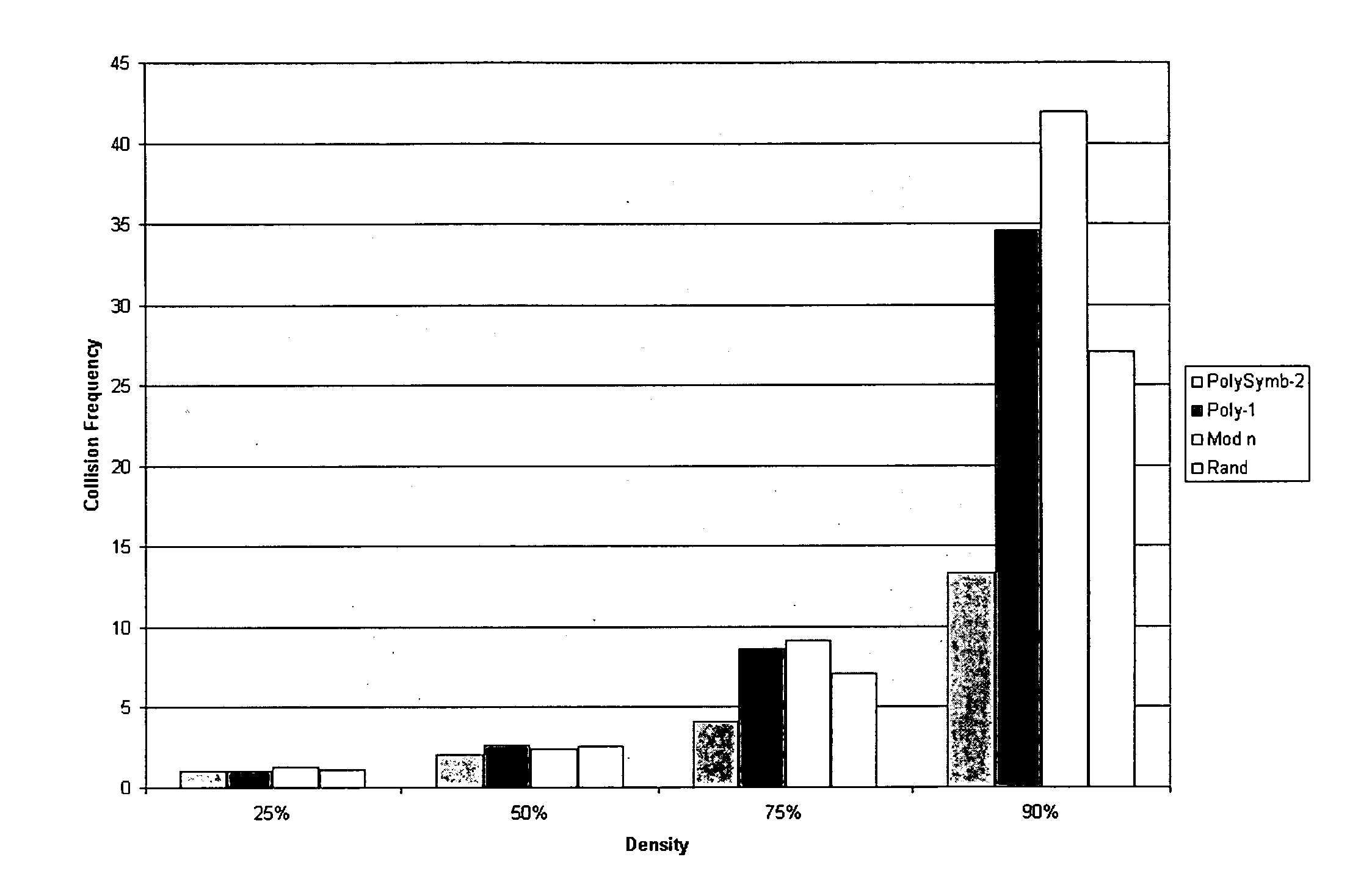
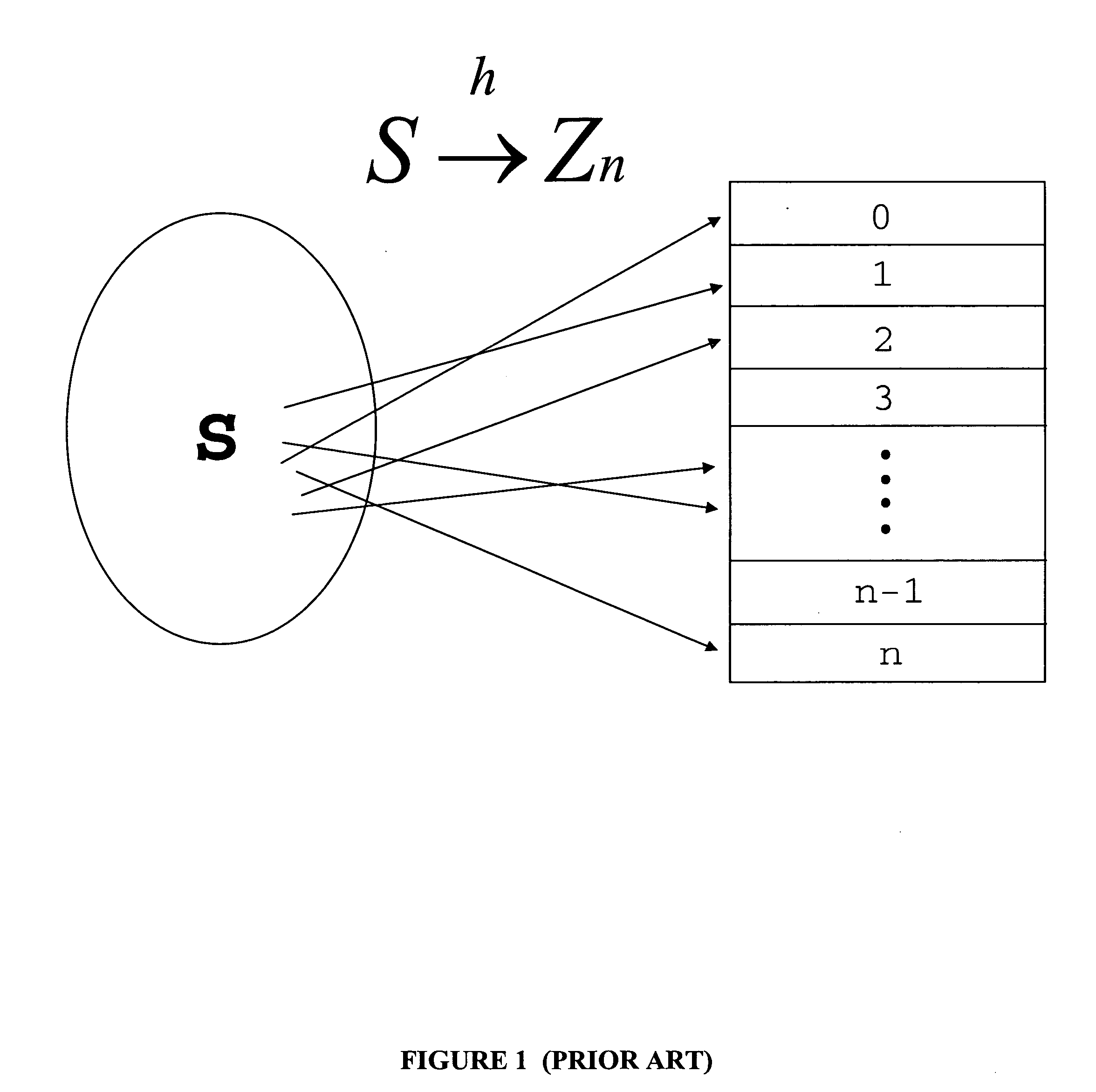
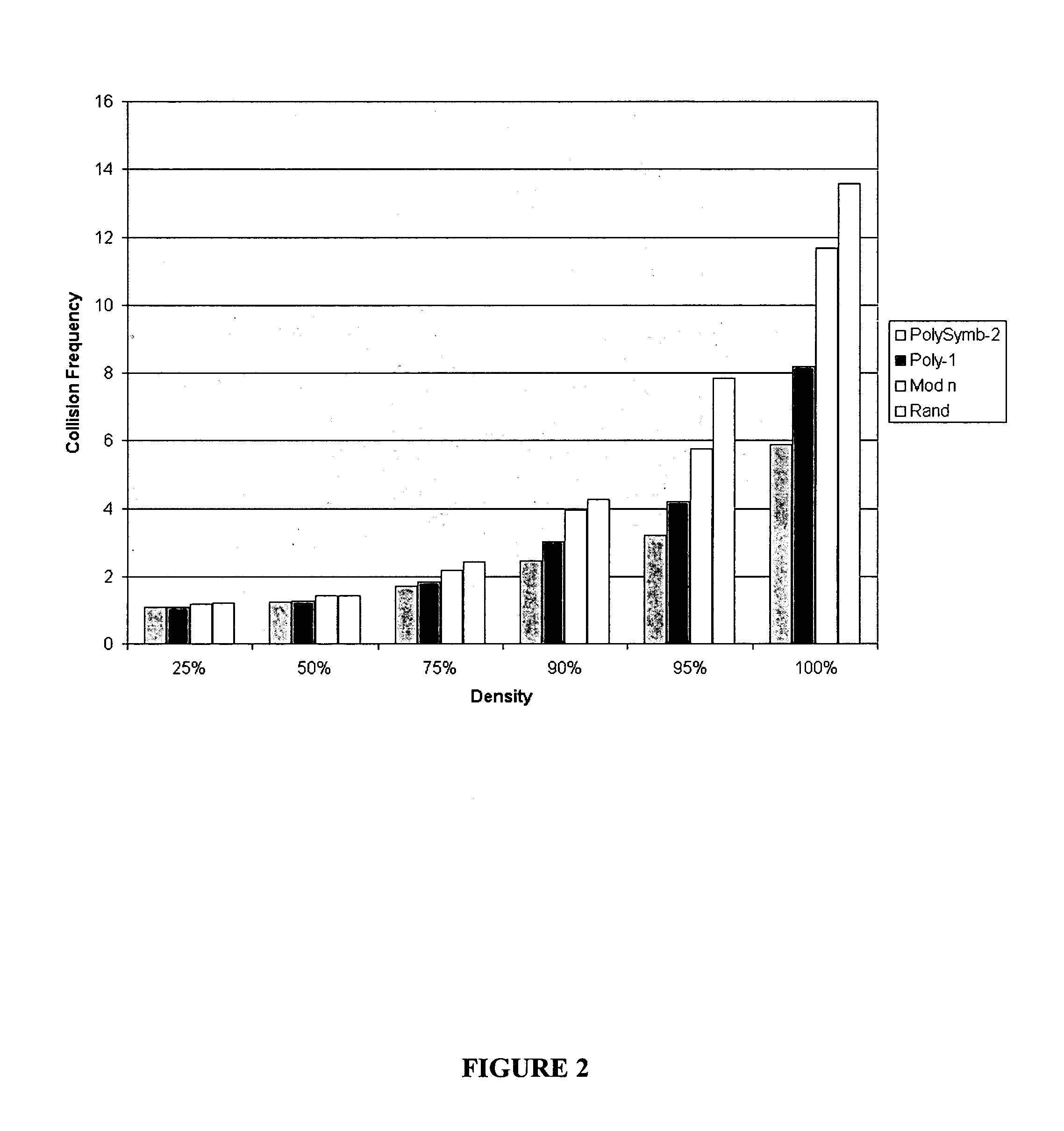
InactiveUS20070083531A1Improve efficiencyImprove speedDigital data processing detailsSecuring communicationPopulationEvolution strategy
Hashing functions have many practical applications in data storage and retrieval. Perfect hashing functions are extremely difficult to find, especially if the data set is large and without large-scale structure. There are great rewards for finding good hashing functions, considering the savings in computational time such functions provide, and much effort has been expended in this search. This in mind, we present a strong competitive evolutionary method to locate efficient hashing functions for specific data sets by sampling and evolving from the set of polynomials over the ring of integers mod n. We find favorable results that seem to indicate the power and usefulness of evolutionary methods in this search. Polynomials thus generated are found to have consistently better collision frequencies than other hashing methods. This results in a reduction in average number of array probes per data element hashed by a factor of two. Presented herein is an evolutionary algorithm to locate efficient hashing functions for specific data sets. Polynomials are used to investigate and evaluate various evolutionary strategies. Populations of random polynomials are generated, and then selection and mutation serve to eliminate unfit polynomials. The results are favorable and indicate the power and usefulness of evolutionary methods in hashing. The average number of collisions using the algorithm presented herein is about one-half of the number of collisions using other hashing methods. Efficient methods of data storage and retrieval are essential to today's information economy. Despite the cur-rent obstacles to creating efficient hashing functions, hashing is widely used due to its efficient data access. This study investigates the feasibility of overcoming such obstacles through the application of Darwin's ideas by modeling the basic principles of biological evolution in a computer. Polynomials over Zn are the evolutionary units and it is believed that competition and selection based on performance would locate polynomials that make efficient hashing functions.
Owner:HUSSAIN DANIAR
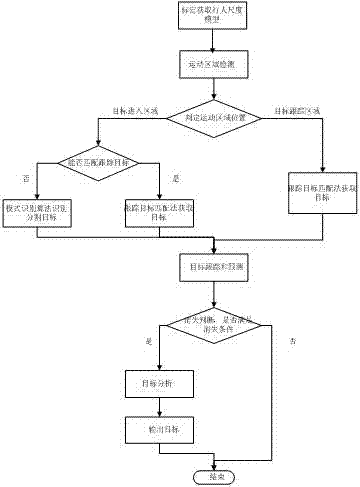
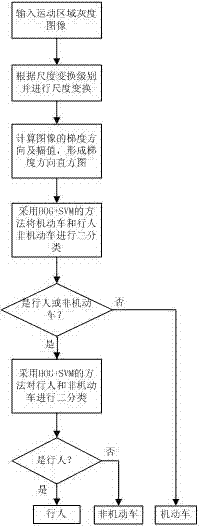
Road pedestrian and non-motor vehicle detection method based on video analysis
ActiveCN103400157AReduce computational complexitySmall amount of calculationImage analysisCharacter and pattern recognitionRegion detectionRecognition algorithm
The invention discloses a road pedestrian and non-motor vehicle detection method based on video analysis. The method comprises the steps of detection region setting and scale model calibration, including 1) performing moving region detection to a current frame image to obtain all moving regions; 2) performing target detection and tracking to the moving regions: if the moving regions are in a target entering region, firstly a tracking target matching method is adopted to perform calculation of matching the existing tracking targets with the moving regions, the moving regions which are failed to be matched are detected by adopting a mode recognition algorithm to detect moving target types and moving target position information; and if the moving regions are in a target tracking region, performing calculation of matching the existing tracking targets with the moving regions to obtain the matched positions of the tracking targets in the current frame; and 3) performing target prediction. The detection method disclosed by the invention has the advantages that the calculation complexity is effectively reduced, the calculation amount is small, the calculation speed is fast and the detection accuracy is high.
Owner:QINGDAO HISENSE TRANS TECH
Rollout drop down shelves
InactiveUS8424693B1Efficient accessFacilitates efficient storageShow cabinetsKitchen cabinetsForward slidingEngineering
Owner:HOOVER JAMES A
Remote-control detection device for overhead line
ActiveCN102412523AGuarantee the safety of lifeImprove efficiencyTelevision system detailsTransmission systemsForeign matterRemote control
The invention discloses a remote-control detection device for an overhead line. The remote-control detection device comprises a travelling mechanism, a camera shooting mechanism, a power supply, a control system, and a frame with a cradle head arranged at the bottom end and a hanging hook arranged at the upper part, wherein the travelling mechanism, the camera shooting mechanism and the power supply are all arranged on the frame; the power supply is connected with the travelling mechanism, the camera shooting mechanism and the control system respectively; and the control system is used for controlling the operation of the power supply, the travelling mechanism and the camera shooting mechanism. With the remote-control detection device being remotely controlled on the ground by a person, whether foreign matters exist on the overhead line can be detected clearly and definitely, and therefore the efficiency and accuracy of detection is improved, and the life safety of the person can be ensured.
Owner:南京炬名电力科技有限公司
Imaging apparatus and method for controlling the same
ActiveUS20140184848A1Valid checkTelevision system detailsColor signal processing circuitsDisplay deviceImaging equipment
An imaging apparatus capable of performing image display that allows a user to more effectively check images of a group composed of a plurality of images generated in response to a single shooting instruction, includes a control unit configured to perform control to cause an imaging unit to generate a plurality of images in response to a single shooting instruction, and a display control unit configured to, as automatically performed review display after shooting in response to the shooting instruction, perform control to sequentially display the plurality of generated images one by one on a display unit, and then display the plurality of images in a multi-display form on the same screen.
Owner:CANON KK
Active power distribution network control strategy and method
ActiveCN104377826AAchieve optimizationAchieve coordinationSingle network parallel feeding arrangementsSystems intergating technologiesPower gridMaterial resources
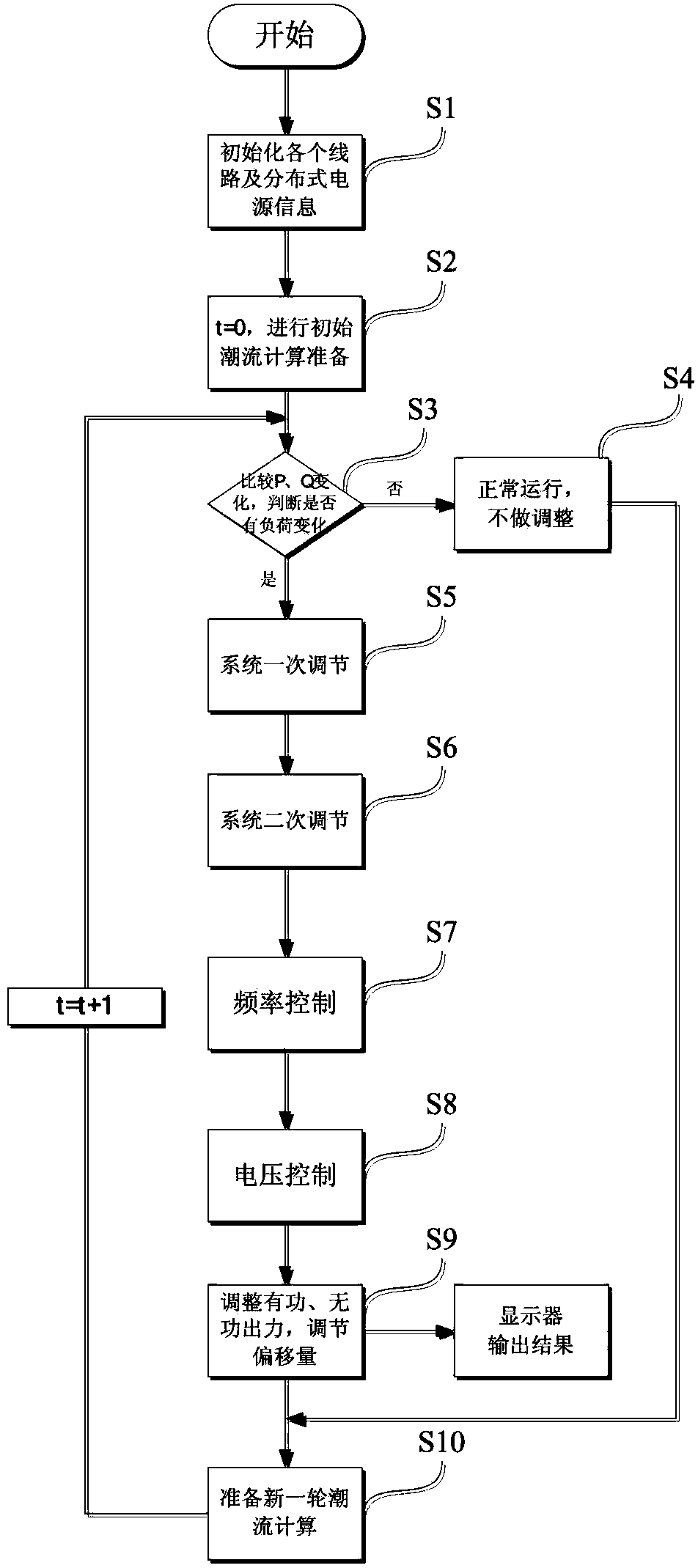
The invention discloses an active power distribution network control strategy and method. The method includes the following steps that firstly, all circuits and distributed power source information are initialized; secondly, t is equal to zero, and initial load flow calculation preparation is conducted; thirdly, the changes of P and Q are compared, whether load changes exist or not is judged; fourthly, normal operation is conducted, and adjustment is not made; fifthly, primary adjustment of a system is conducted; sixthly, secondary adjustment of the system is conducted; seventhly, frequency control is conducted; eighthly, voltage control is conducted; ninthly, active output and reactive output are adjusted, and the offset is adjusted; tenthly, a new round of load flow calculation is prepared. According to the active power distribution network control strategy and method, global optimization can be achieved only with the communication of local information, the control efficiency is improved, and the control cost is reduced; due to the layered control over an active power distribution network, the logic and the function of protection can be verified more comprehensively, more efficiently and faster, the functions of control and protection are fully developed, the safe and reliable operation of a power grid is ensured, the debugging manpower and the debugging material resources are greatly saved, the production cost is lowered, and industrialization, application and popularization in the future are facilitated.
Owner:YUNNAN POWER GRID CO LTD ELECTRIC POWER RES INST
Error verification method of CA oscillating structure five-axis machine tool
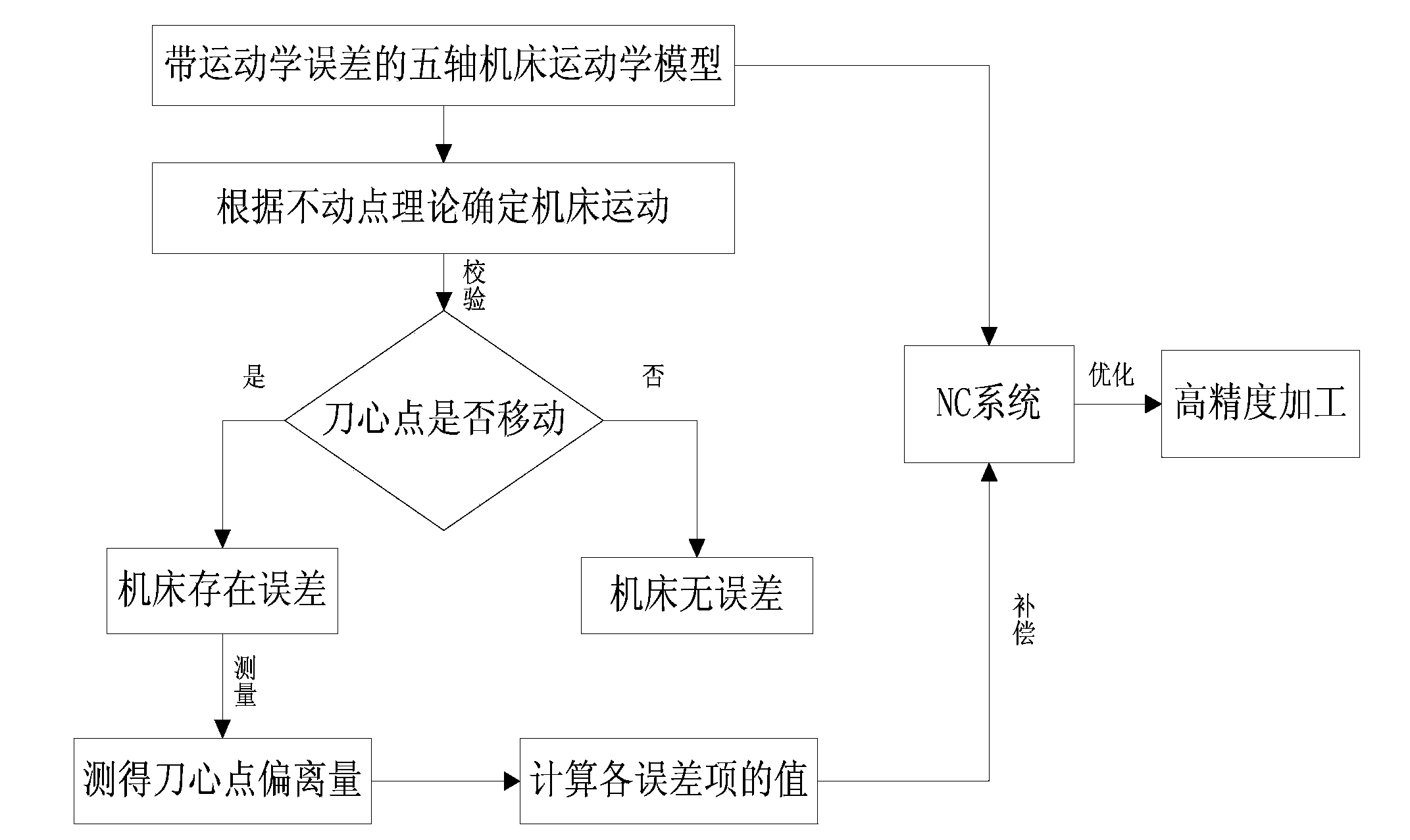
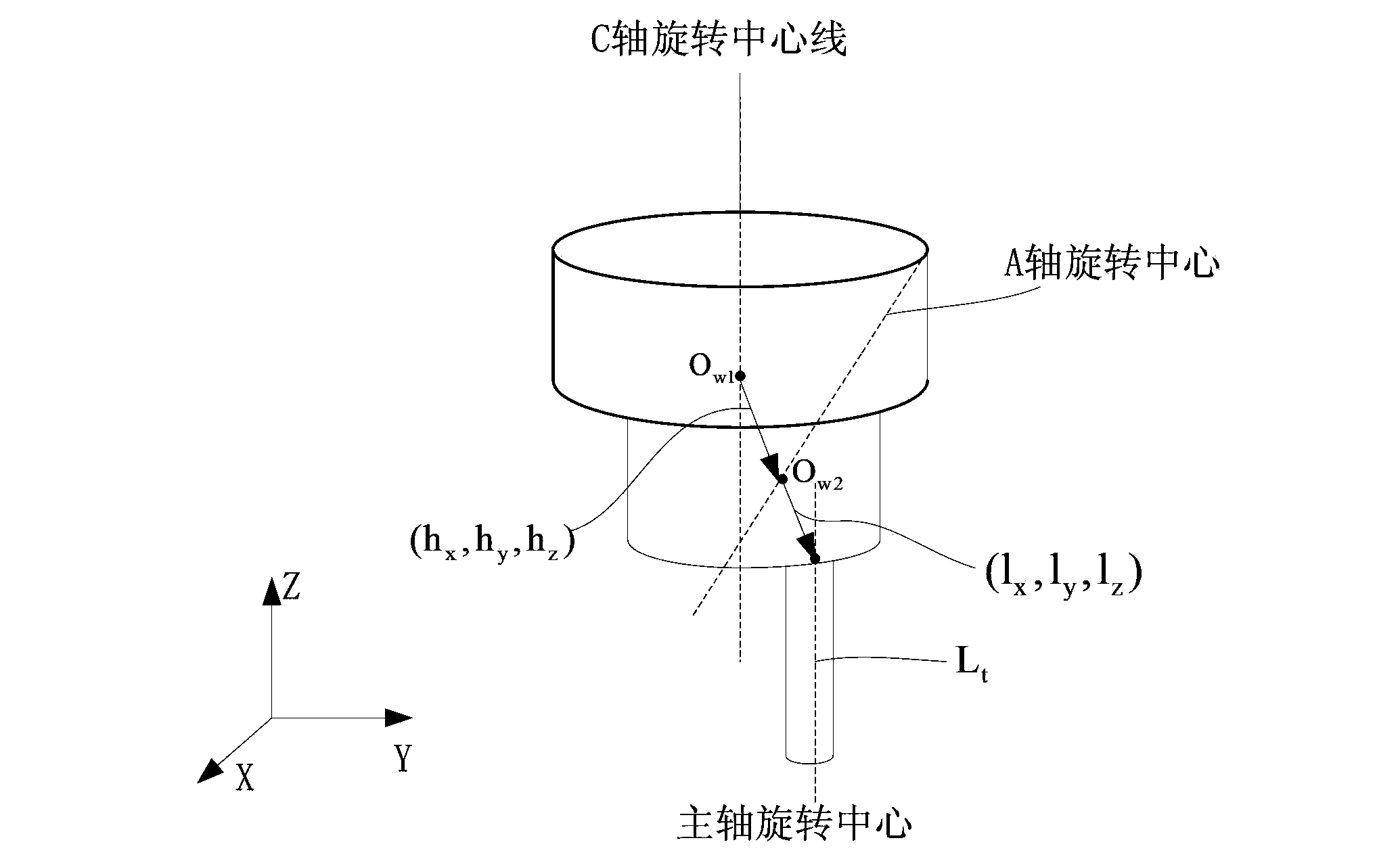
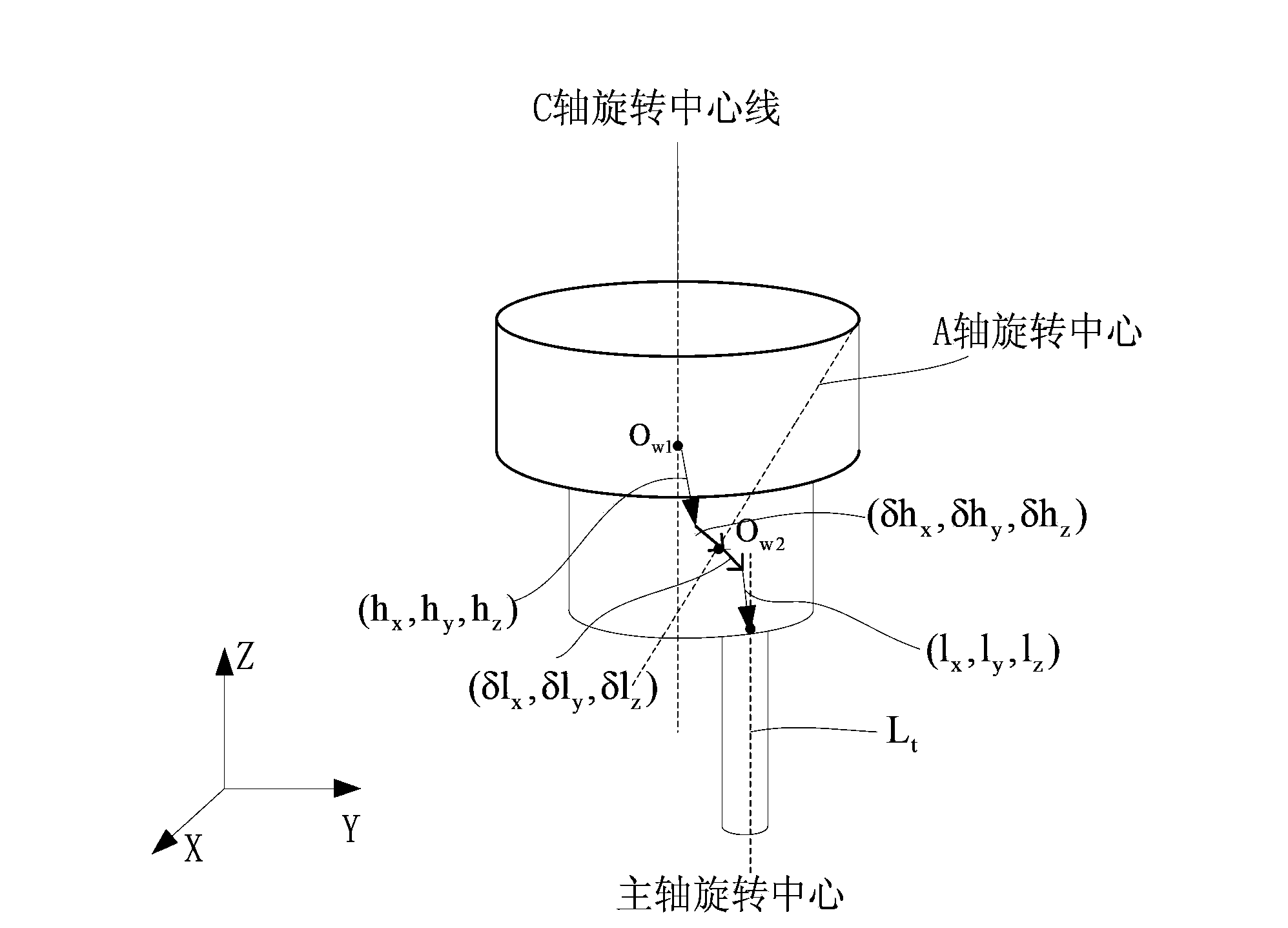
ActiveCN103809513AAnalytical scienceEfficient analysisProgramme controlComputer controlNumerical controlRotational axis
The invention relates to the technical field of numerical control, and specifically relates to an error verification method of a CA oscillating structure five-axis machine tool. The error verification of a CA oscillating five-axis machine tool is finished in a high-efficient manner by use of a simple measuring device, the deviation direction of the measuring device, and a meter checking mode. The structure of a five-axis machine tool is analyzed through an error-free kinematic model and an error-containing kinematic model, by combining with the motion interval and the motion direction of a turning shaft, the mobile direction of a measuring point is analyzed, and the mobile direction of each compensation amount needed by actual machine tool error correction is solved so as to finish correction of machine tool structure error parameters. According to the invention, simple measuring devices such as a verification rod and the like are utilized, and the method provided by the invention can be applied to obtaining the deviation of each error item through effective and accurate measuring.
Owner:SHENYANG GOLDING NC & INTELLIGENCE TECH CO LTD
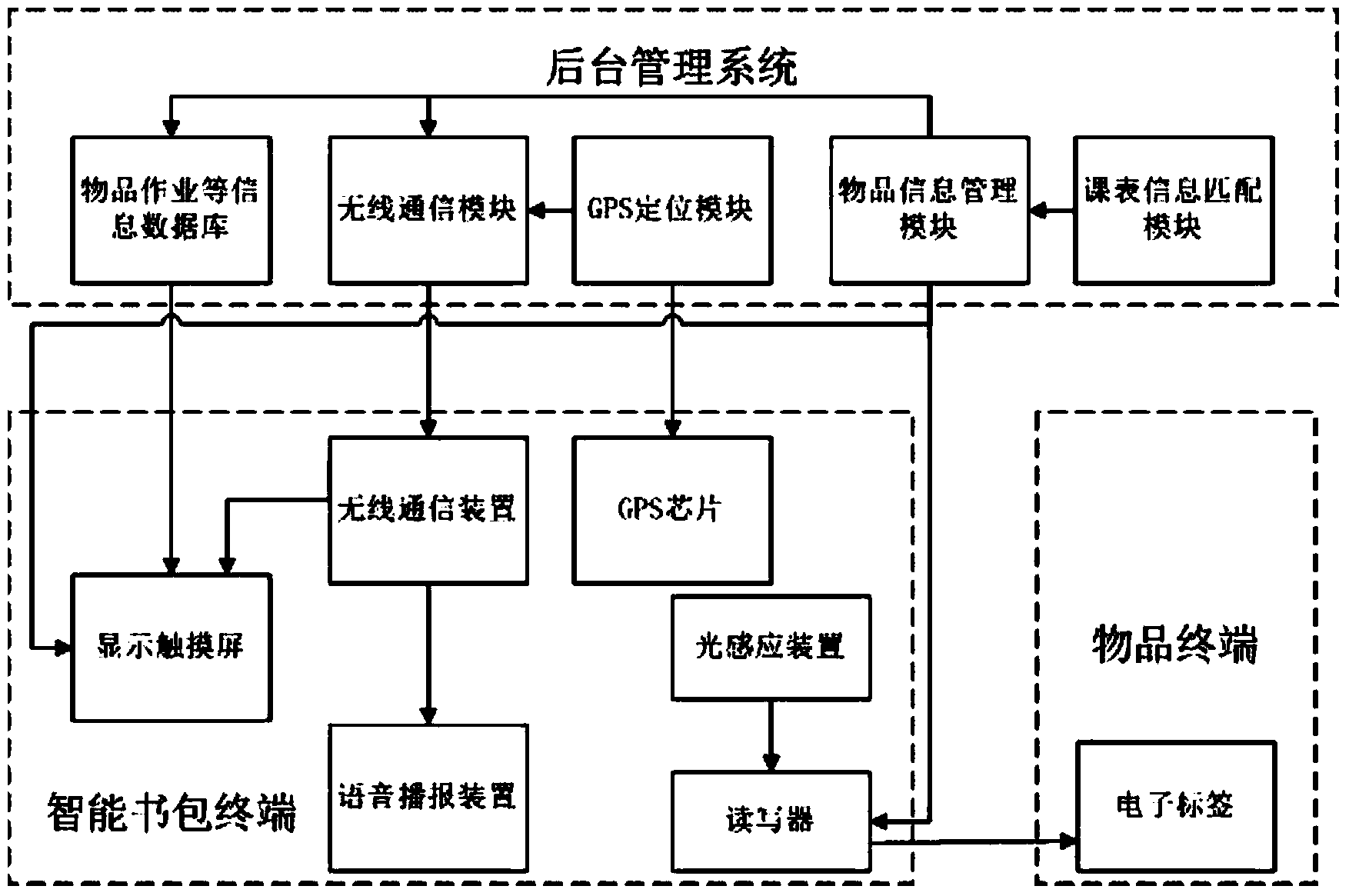
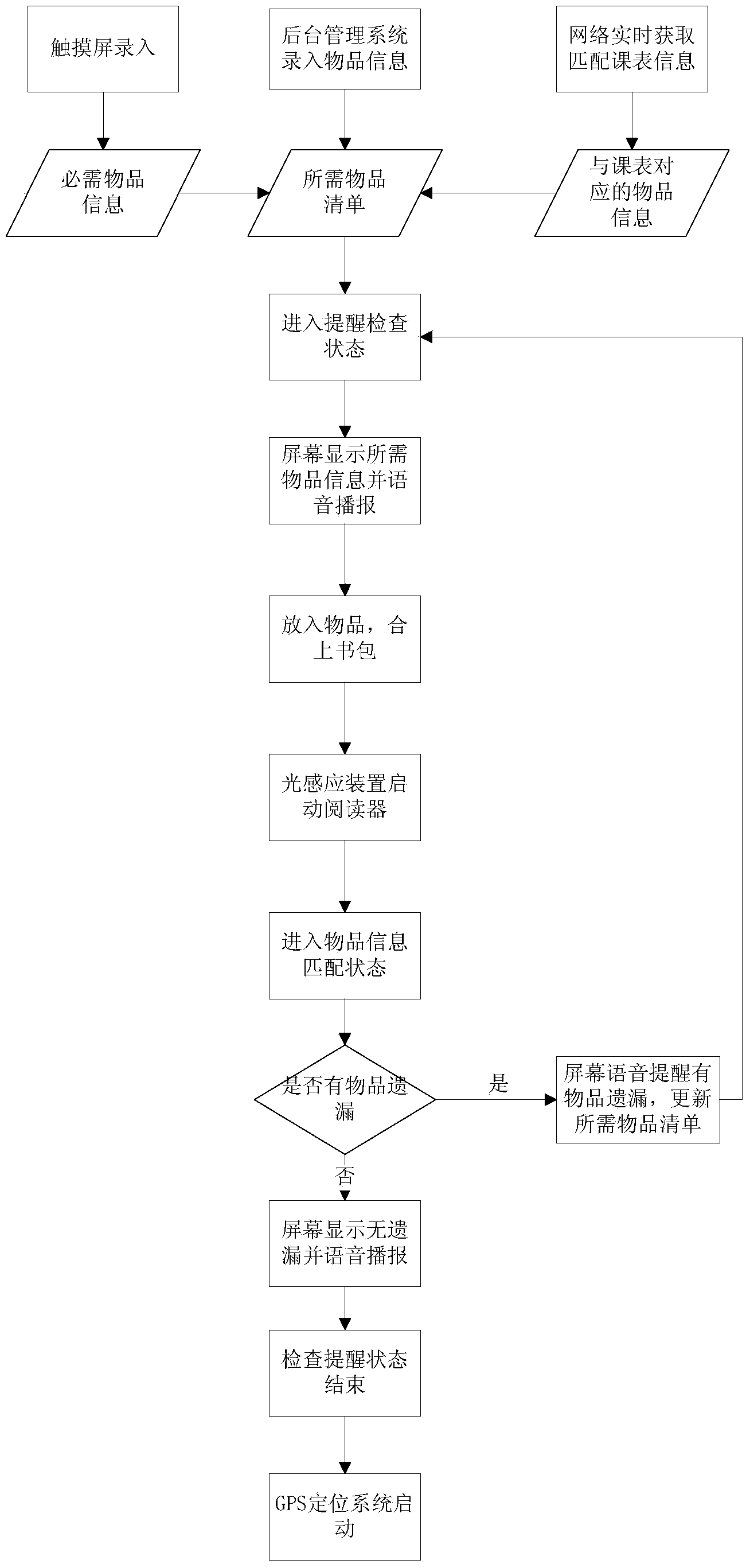
Intelligent bag item, homework and data checking and reminding system and method
The invention discloses an intelligent bag item, homework and data checking and reminding system and method. The intelligent bag item, homework and data checking and reminding system comprises a background management system module, an intelligent bag terminal module and an item terminal module which can work cooperatively. According to the intelligent bag item, homework and data checking and reminding system and method, non-contact information collection is performed on electronic tags which are pasted on items through a wireless radio frequency technology, the required items are matched through the information such as network class schedules and intelligent input, users are reminded of the missing state of the items through a screen and a voice and reminded of the information such as updated homework and teaching materials timely through a network push technology, the positions of bags and students are positioned through a GPS (Global Position System) technology, and accordingly the intelligent checking and reminding of the items, the homework and the like and the safe positioning and monitoring of the students can be achieved finally.
Owner:HOHAI UNIV CHANGZHOU
Speech analytics system and methodology with accurate statistics
ActiveUS9672825B2Low costEliminate needSpecial service provision for substationAutomatic call-answering/message-recording/conversation-recordingPattern recognitionSpeech sound
The present invention relates to implementing new ways of automatically and robustly evaluating agent performance, customer satisfaction, campaign and competitor analysis in a call-center and it is comprising; analysis consumer server, call pre-processing module, speech-to-text module, emotion recognition module, gender identification module and fraud detection module.
Owner:SESTEK SES & ILETISIM BILGISAYAR TEKNOLOJILERI SANAYII & TICARET ANONIM SIRKETI
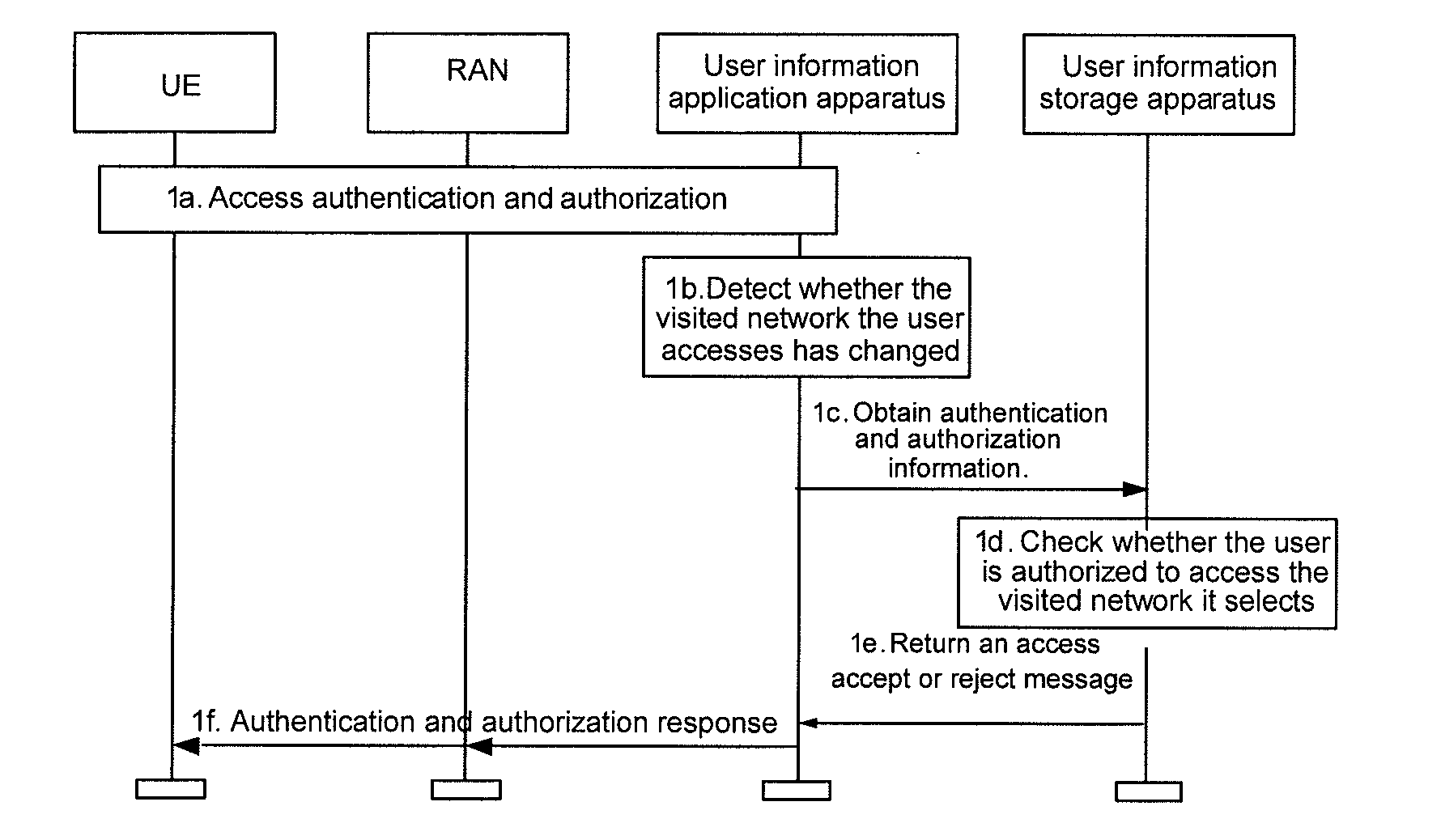
Method, system and apparatus for accessing a visited network
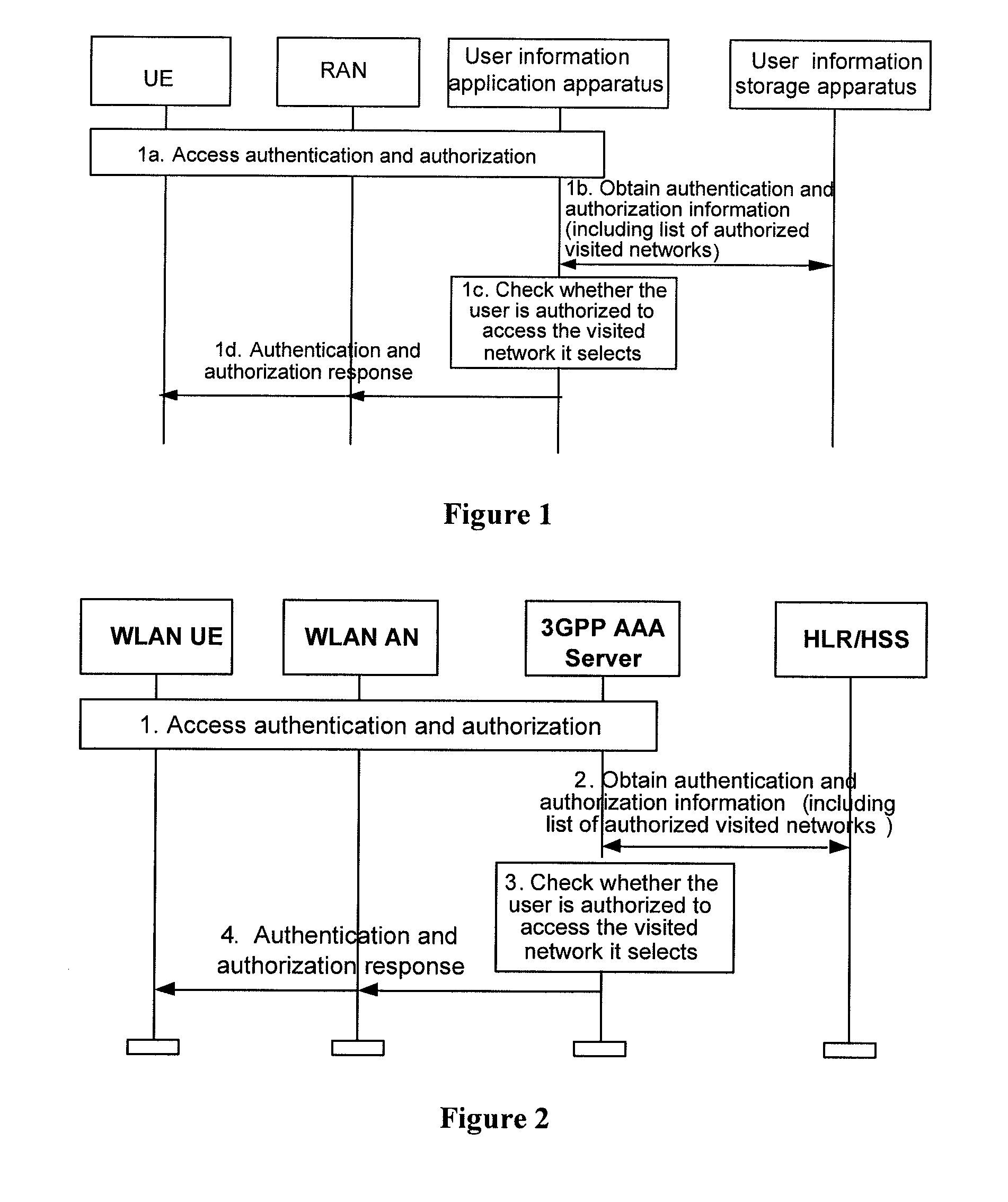
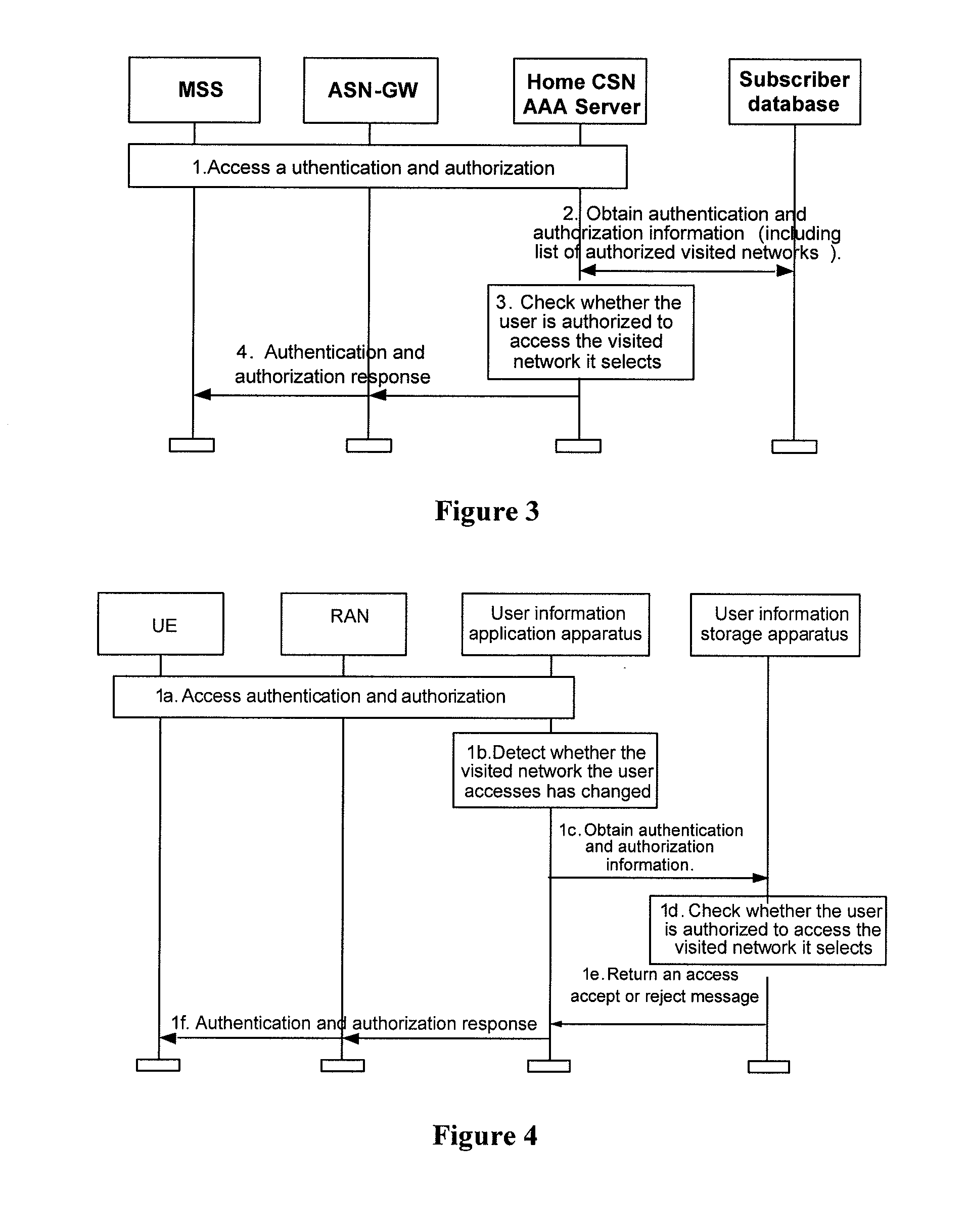
ActiveUS20090049526A1Accurate checkValid checkDigital data processing detailsComputer security arrangementsUser information
The embodiments of the present invention disclose a method for accessing a visited network. The method includes: a user selects a visited network and initiates an access request to a user information application apparatus; when the user information application apparatus detects that the visited network has changed, it obtains a list of authorized visited networks from a user information storage apparatus and checks whether the user is authorized to access the visited network; or the user information storage apparatus checks whether the user is authorized to access the visited network; if the user is authorized to access the visited network, the user information application apparatus returns an access accept response to the user, allowing the user to access the visited network. The embodiments of the present invention also disclose systems and apparatuses for accessing a visited network. The embodiments of the present invention make it possible to accurately check whether the user is authorized to access a visited network.
Owner:HUAWEI TECH CO LTD
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com