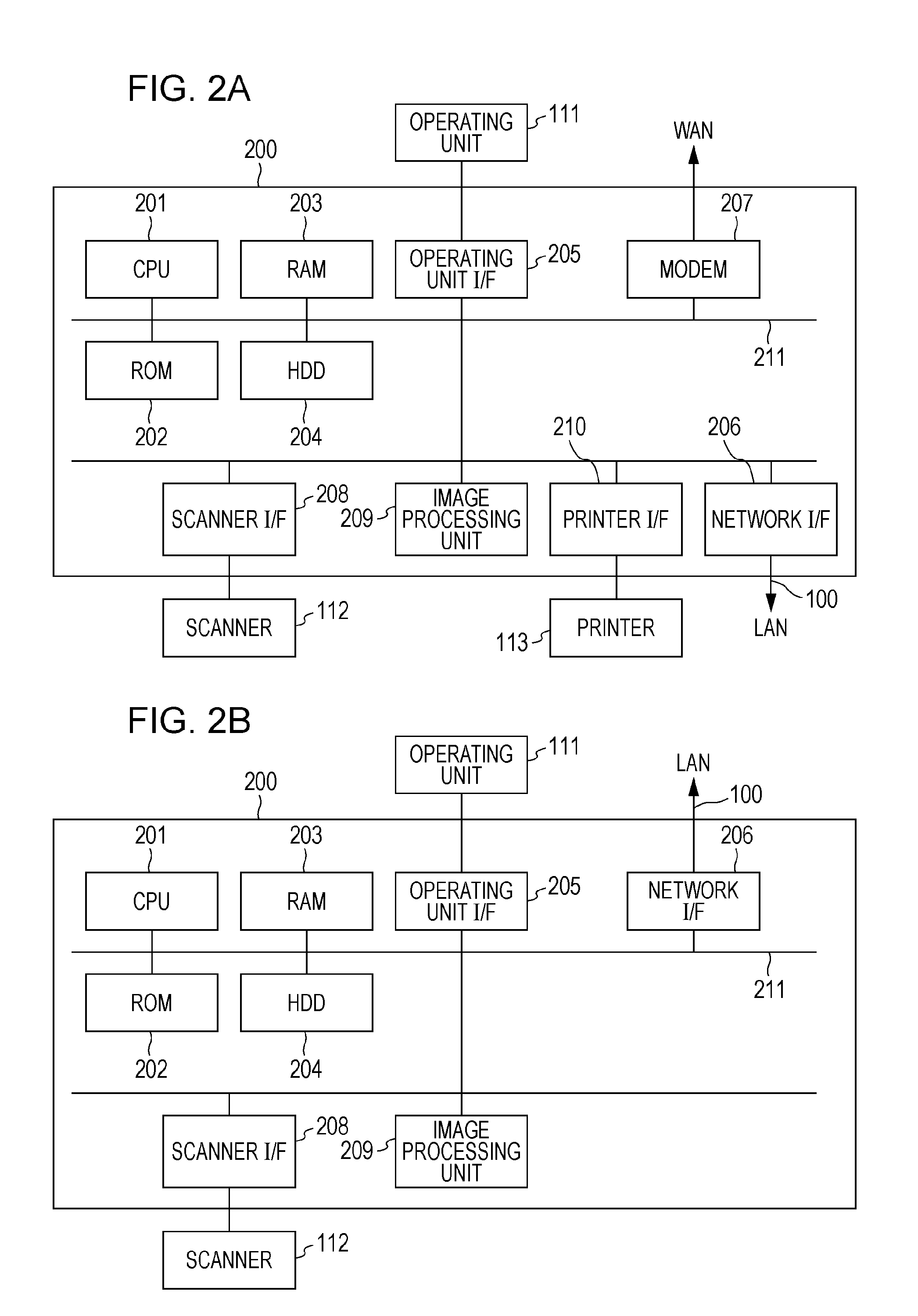
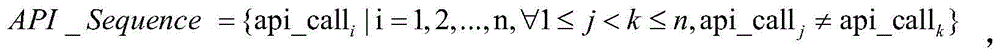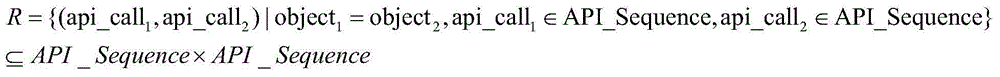Patents
Literature
684 results about "Analysis working" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
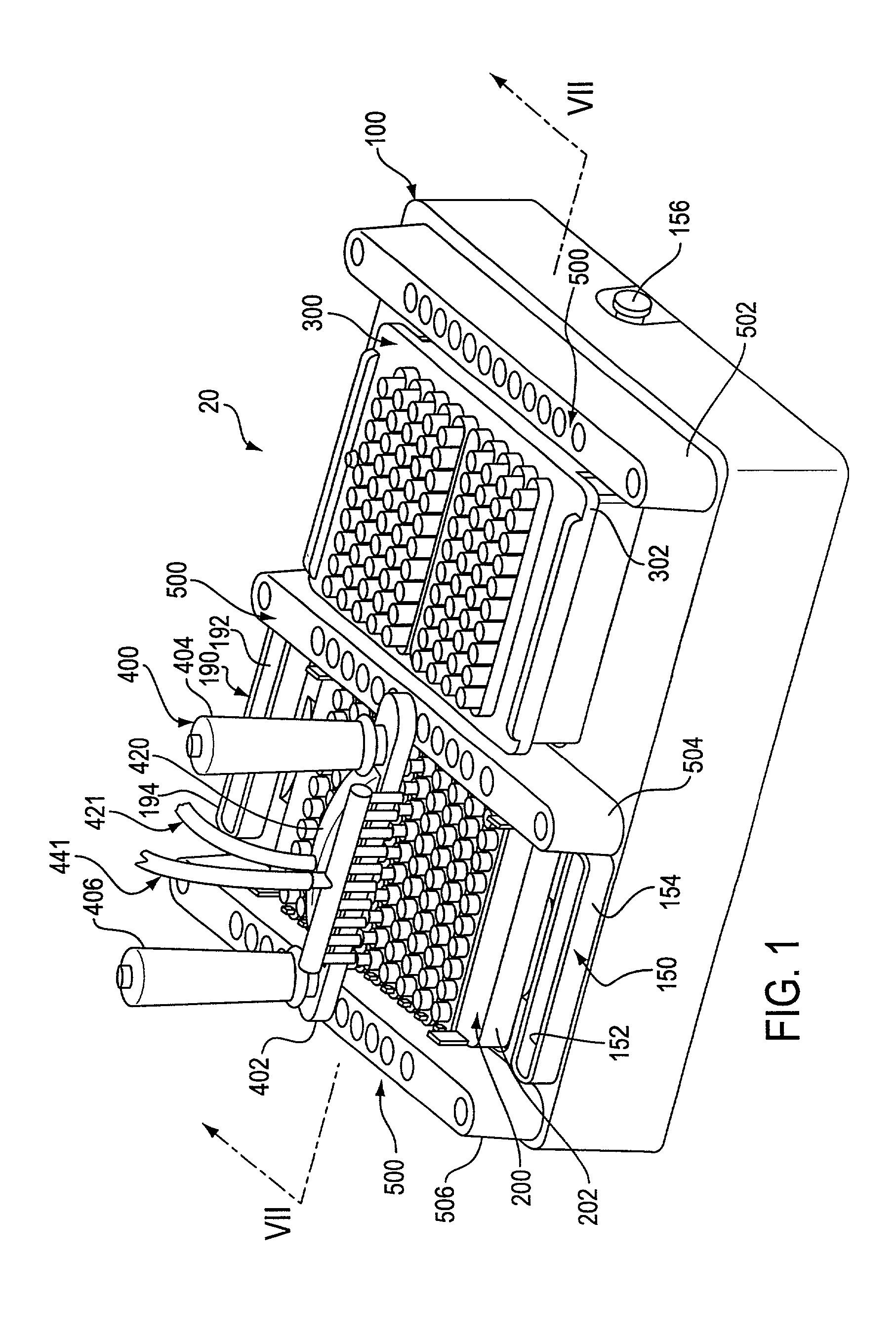
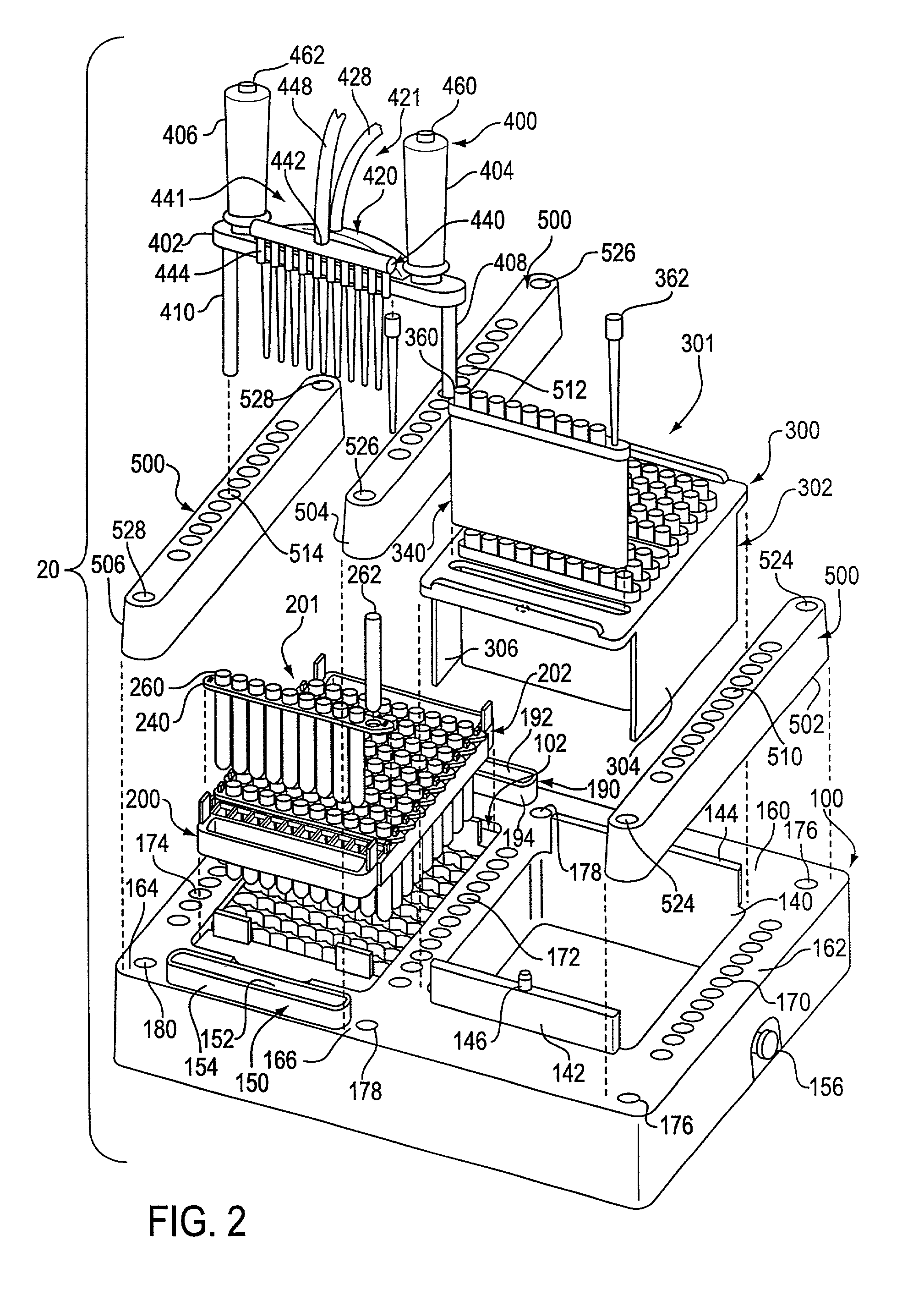
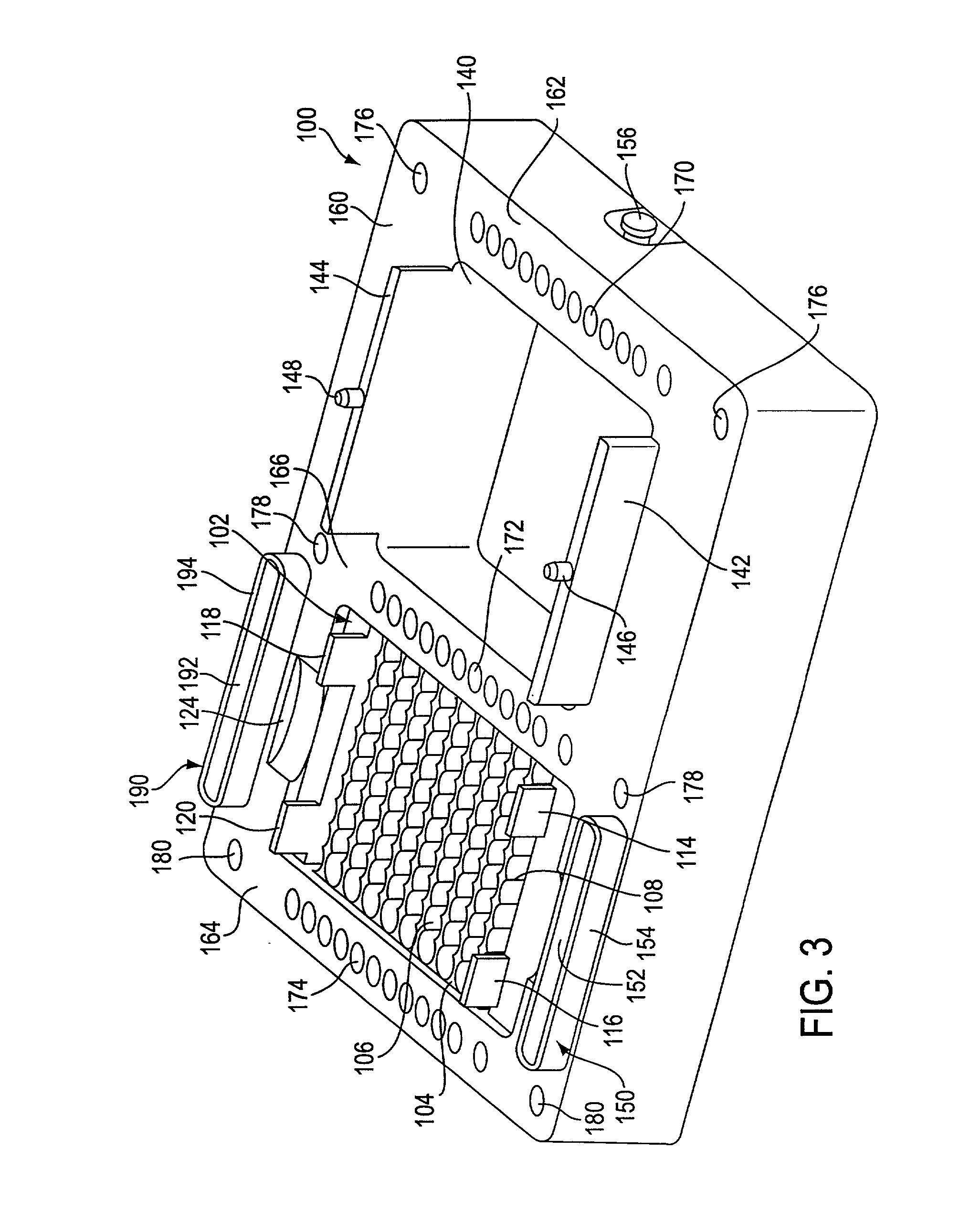
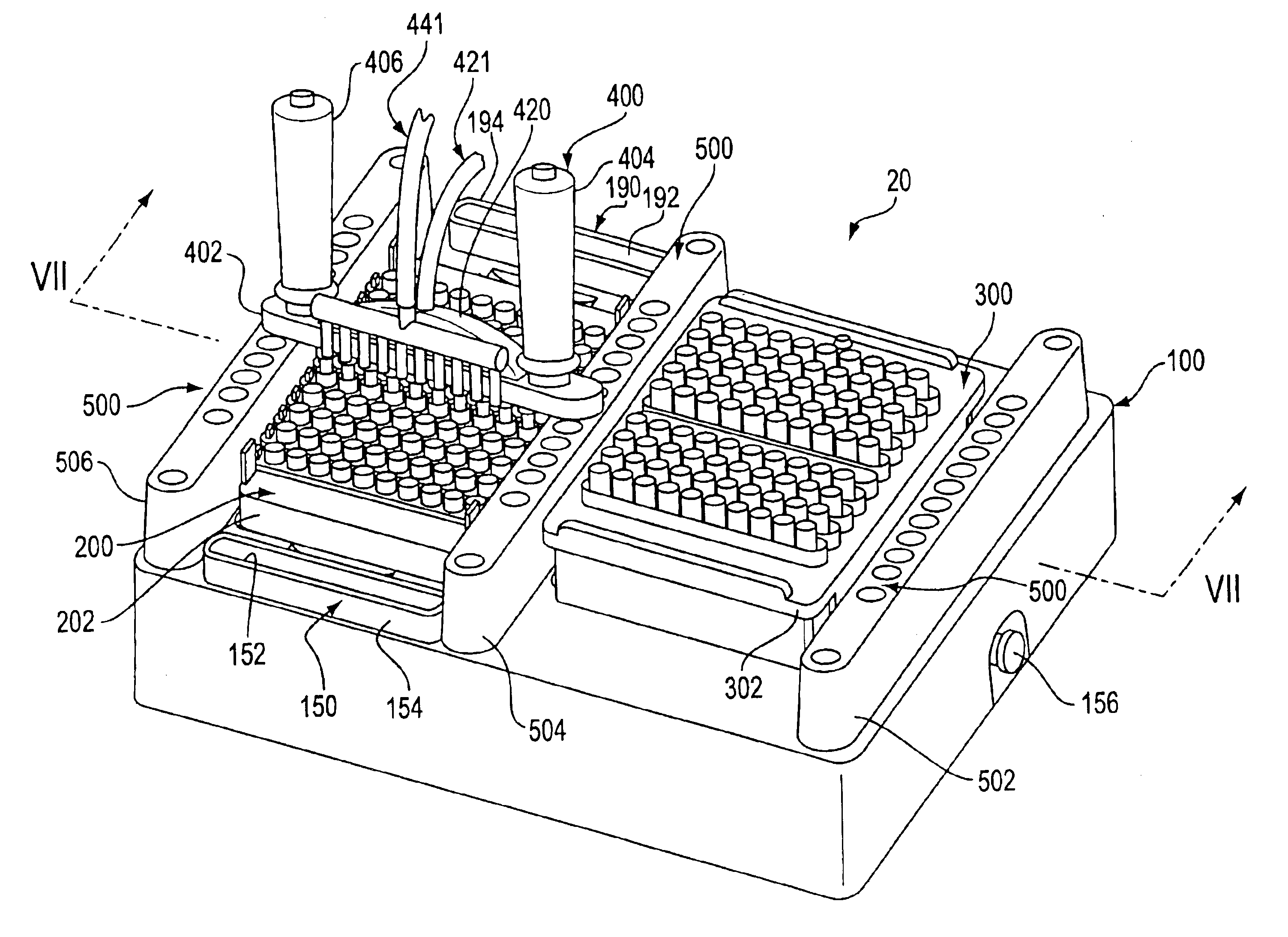
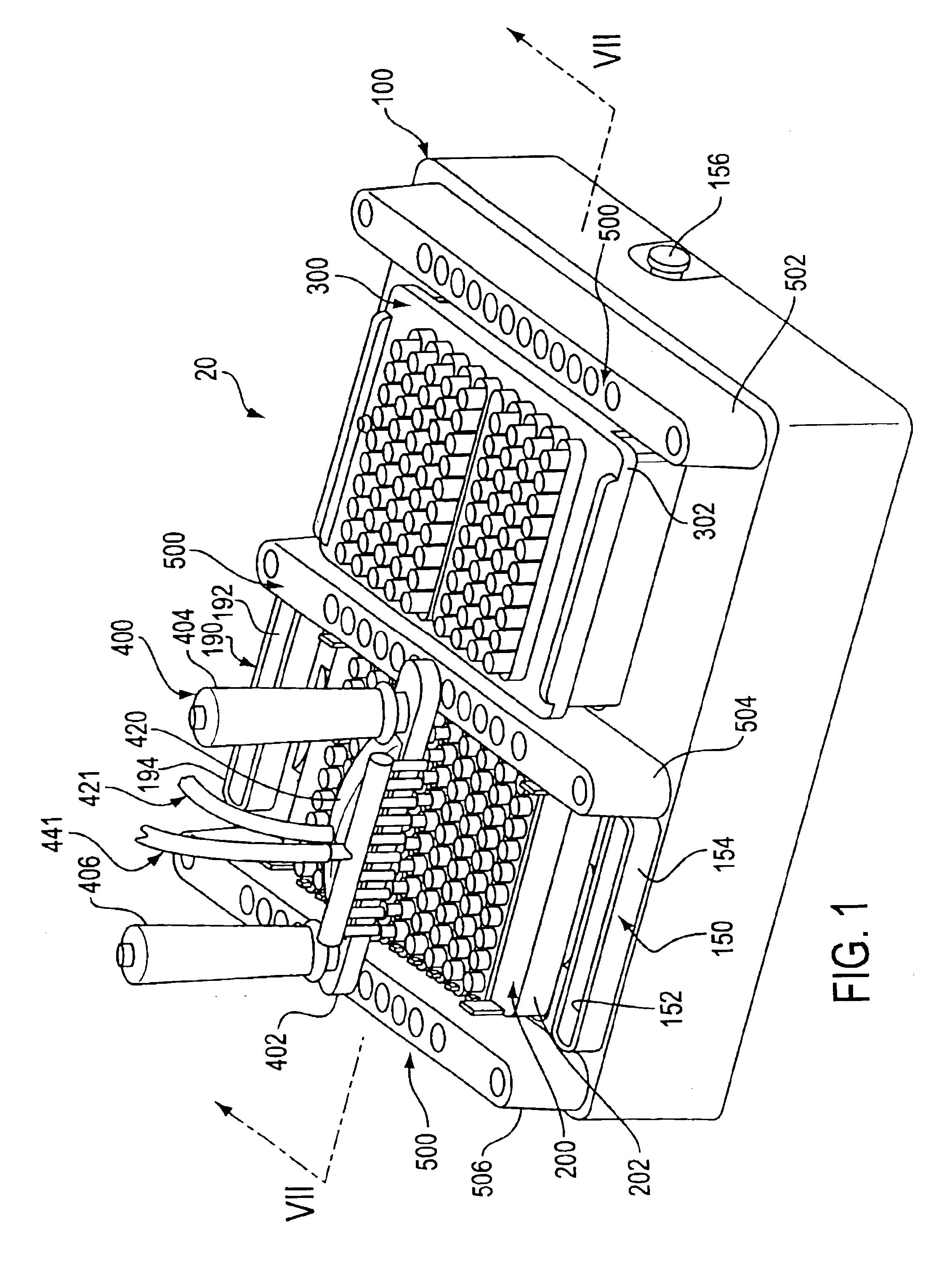
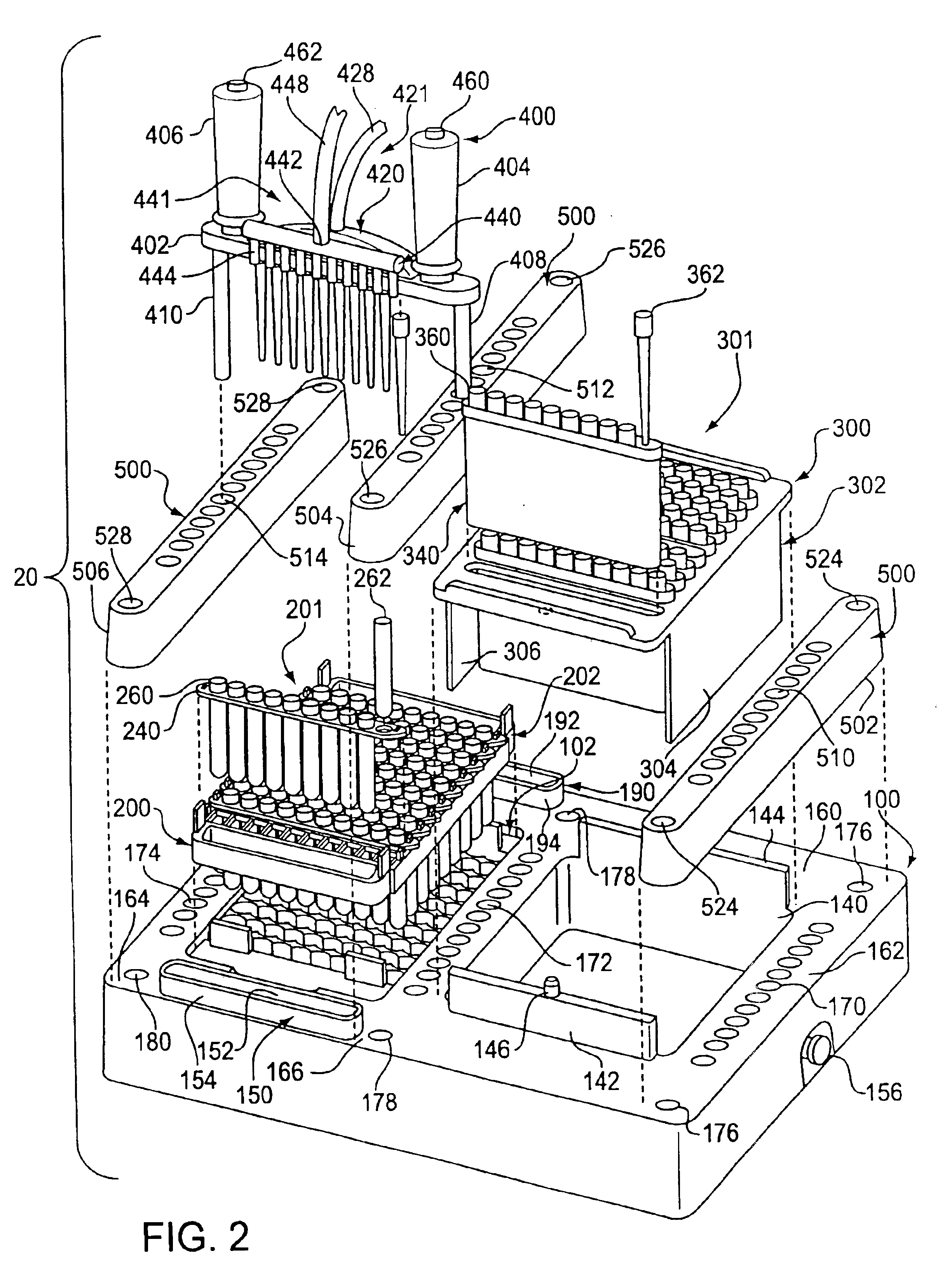
Assay work station
InactiveUS20010012492A1Withdrawing sample devicesMaterial analysis by optical meansAnalysis workingBiomedical engineering
A work station for simultaneously performing multiple assays includes a base structure, a receptacle rack assembly received within a receptacle rack well formed in the base structure, a pipette tip rack assembly received within a pipette tip rack well formed in the base structure, a multiple conduit substance transfer device, and substance transfer device positioning structure. The receptacle rack assembly holds a plurality of receptacles in which a plurality of individual assays are performed, and the pipette tip rack assembly holds a plurality of contamination limiting pipette tips. The substance transfer device is capable of simultaneously dispensing substances into two or more receptacles or simultaneously removing substances from two or more receptacles. Alternatively, the substance transfer device is capable of simultaneously dispensing substances into two or more receptacles, and, at about the same time, simultaneously removing substances from two or more receptacles. The positioning structure permits the substance transfer device to be positioned with respect to the receptacle rack assembly or the pipette tip rack assembly.
Owner:GEN PROBE INC
Assay work station
A work station for simultaneously performing multiple assays includes a base structure, a receptacle rack assembly received within a receptacle rack well formed in the base structure, a pipette tip rack assembly received within a pipette tip rack well formed in the base structure, a multiple conduit substance transfer device, and substance transfer device positioning structure. The receptacle rack assembly holds a plurality of receptacles in which a plurality of individual assays are performed, and the pipette tip rack assembly holds a plurality of contamination limiting pipette tips. The substance transfer device is capable of simultaneously dispensing substances into two or more receptacles or simultaneously removing substances from two or more receptacles. Alternatively, the substance transfer device is capable of simultaneously dispensing substances into two or more receptacles, and, at about the same time, simultaneously removing substances from two or more receptacles. The positioning structure permits the substance transfer device to be positioned with respect to the receptacle rack assembly or the pipette tip rack assembly.
Owner:GEN PROBE INC
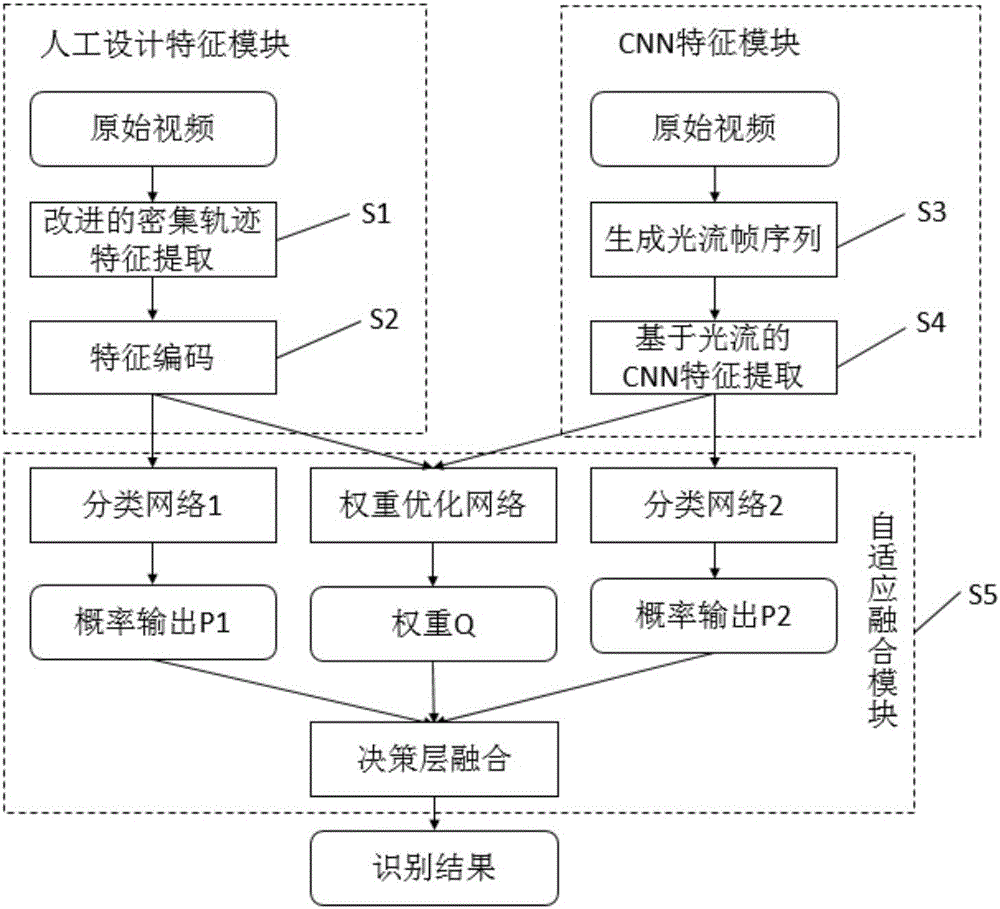
Infrared behavior identification method based on adaptive fusion of artificial design feature and depth learning feature
ActiveCN105787458AImprove reliabilityInnovative feature fusionCharacter and pattern recognitionNeural learning methodsData setFeature coding
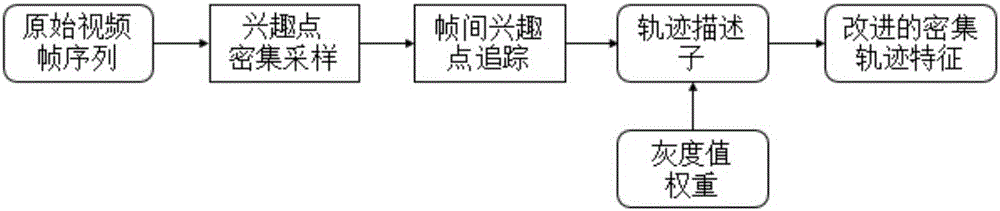
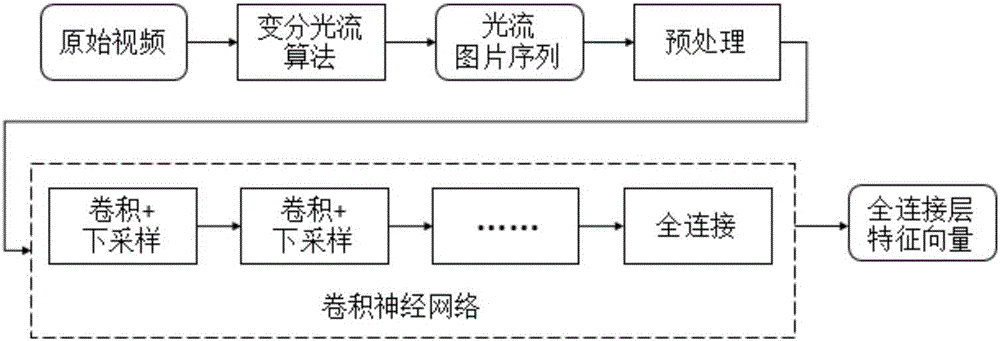
The invention relates to an infrared behavior identification method based on adaptive fusion of an artificial design feature and a depth learning feature. The method comprises: S1, improved dense track feature extraction is carried out on an original video by using an artificial design feature module; S2, feature coding is carried out on the extracted artificial design feature; S3, with a CNN feature module, optic flow information extraction is carried out on an original video image sequence by using a variation optic flow algorithm, thereby obtaining a corresponding optic flow image sequence; S4, CNN feature extraction is carried out on the optic flow sequence obtained at the S3 by using a convolutional neural network; and S5, a data set is divided into a training set and a testing set; and weight learning is carried out on the training set data by using a weight optimization network, weight fusion is carried out on probability outputs of a CNN feature classification network and an artificial design feature classification network by using the learned weight, an optimal weight is obtained based on a comparison identification result, and then the optimal weight is applied to testing set data classification. According to the method, a novel feature fusion way is provided; and reliability of behavior identification in an infrared video is improved. Therefore, the method has the great significance in a follow-up video analysis.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
System for organising social media content to support analysis, workflow and automation
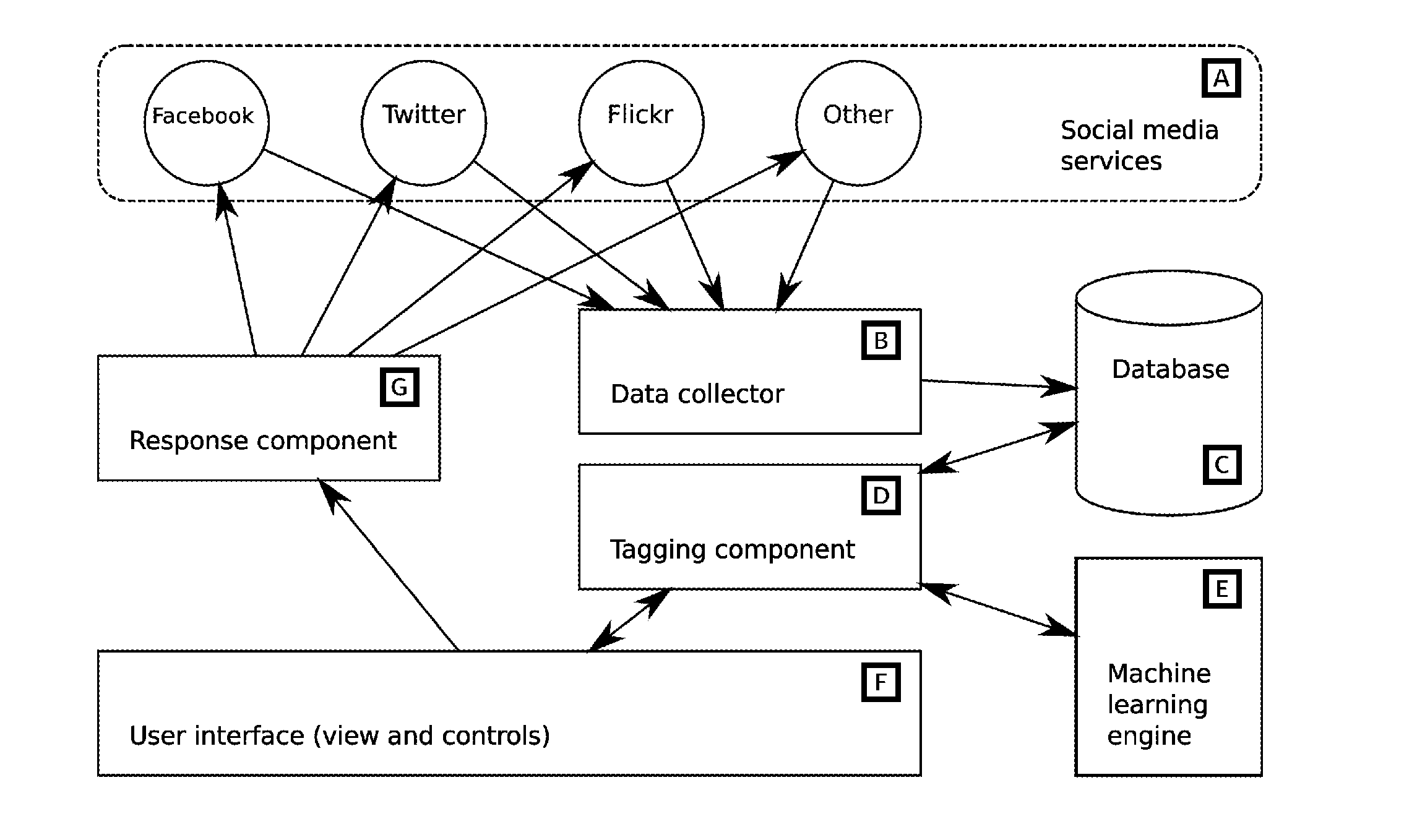
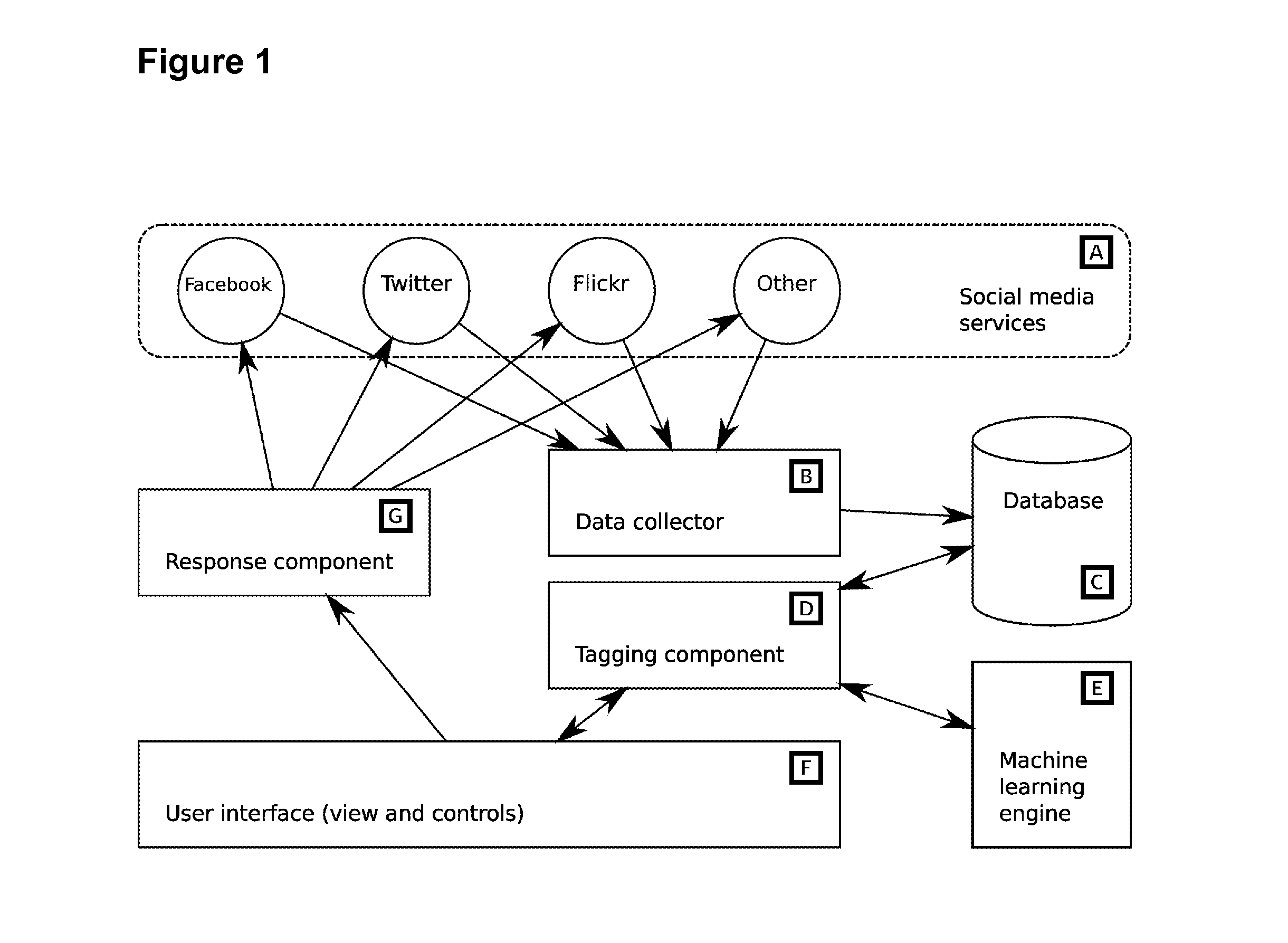
InactiveUS20110078584A1Optimize volumeEasy to handleInput/output for user-computer interactionDigital computer detailsSocial mediaApplication software
A social media workflow application includes a social media search component executable by a computing system, a tagging system for annotating search results with textual tags, and a user interface enabling the display of filtered results based on tag, and potentially other, criteria. The new invention is a system to automate tagging and other actions, and the use of such automation to provide a flexible semi-automated workflow tool for the improved use of social media, with particular relevance for marketing and public communications business functions.
Owner:WINTERWELL ASSOCS
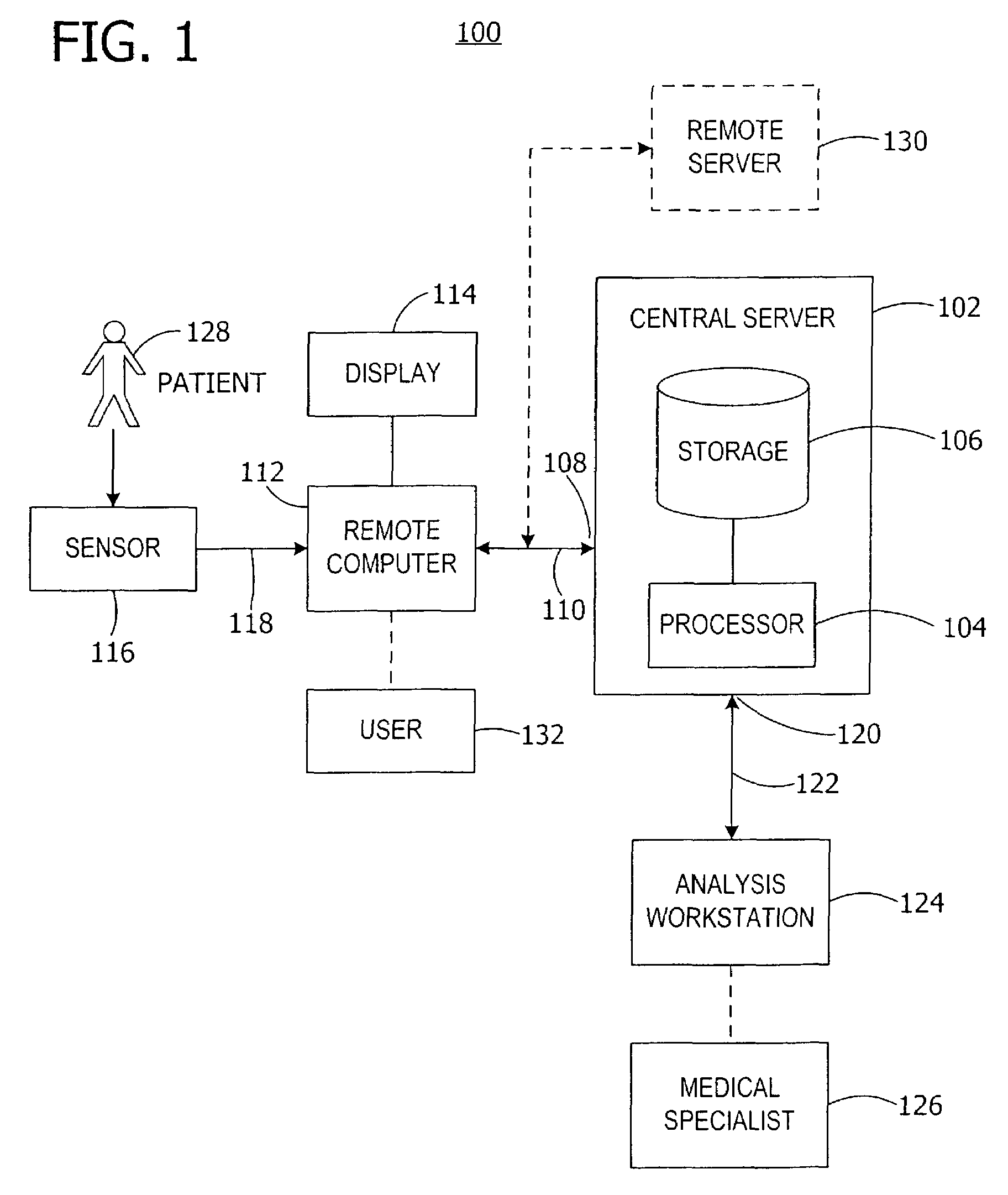
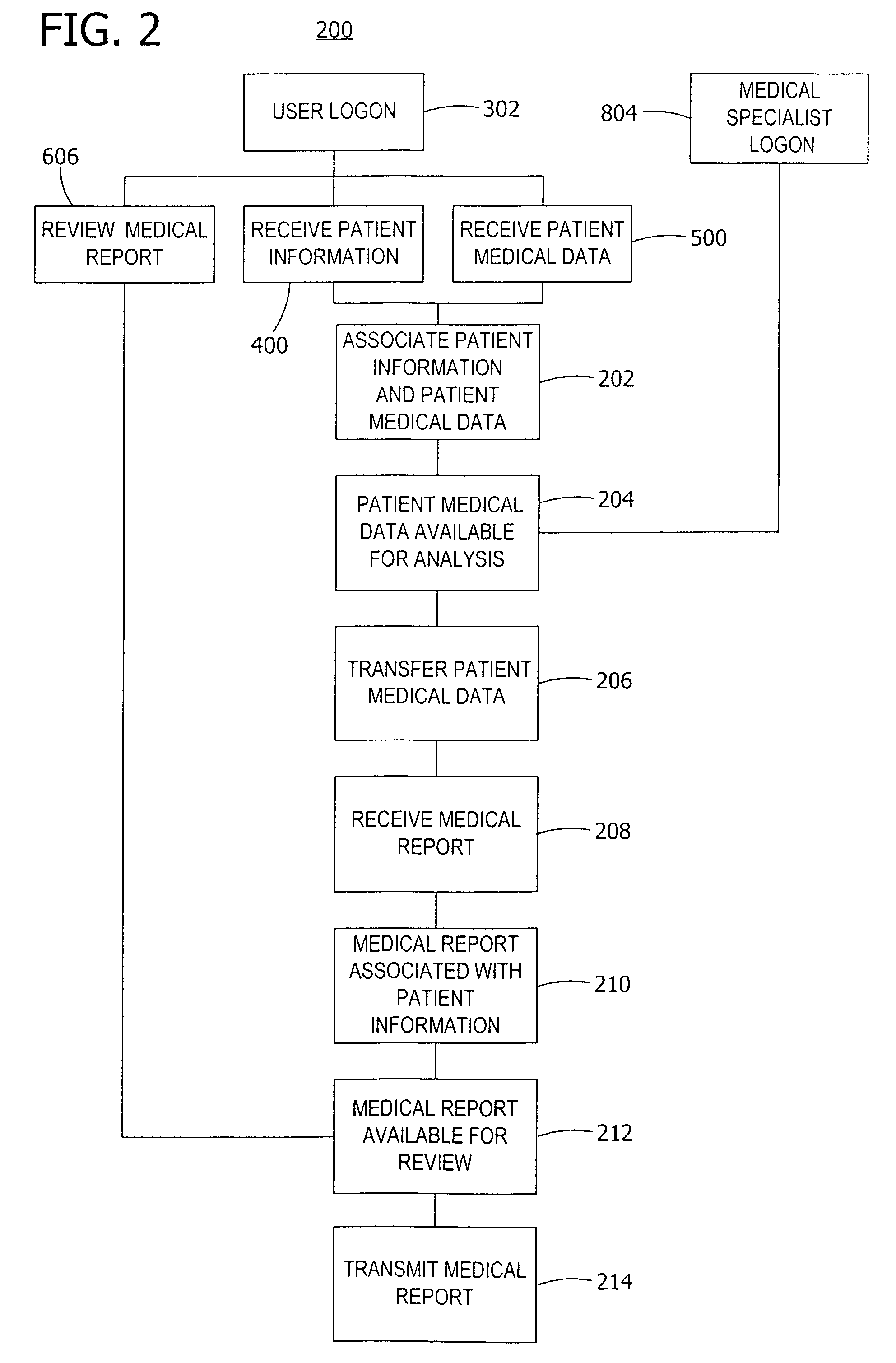
System and method for handling the acquisition and analysis of medical data over a network
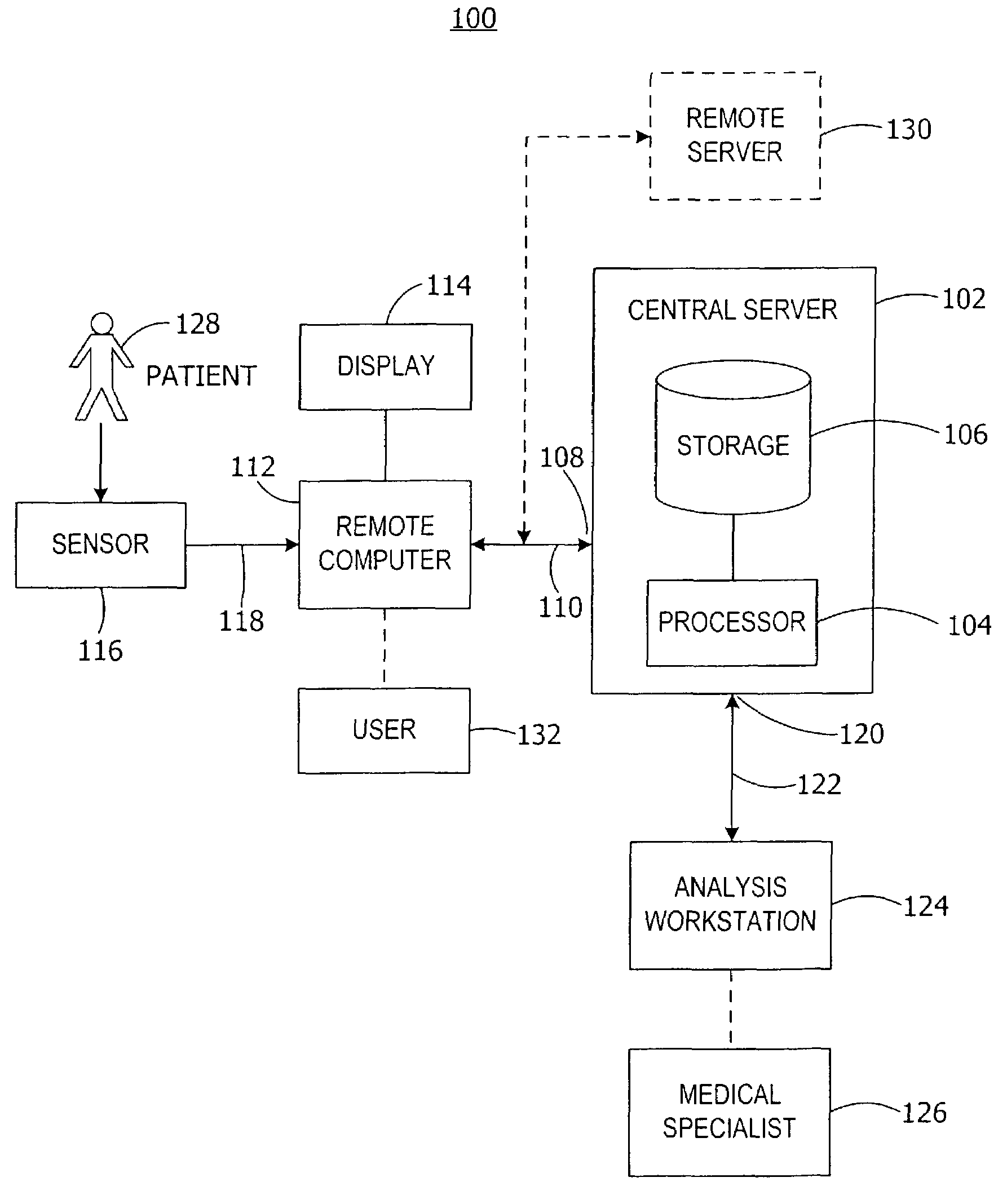
InactiveUS7353179B2Secure, timely and efficientLocal control/monitoringTelemedicineAnalysis workingRemote computer
A central server controls the receipt and analysis of patient medical data and patient information. The central server receives patient medical data and patient information from a remote computer. A storage system stores the received patient medical data, patient information, and the associated medical report prepared at analysis workstations at any location after analysis of the patient medical data. A processor controls access to and analysis of the patient medical data by analysis workstations and controls access to the medical report. The central server transmits the patient medical data to and receives the associated medical report from analysis workstations. The central server transmits the medical report associated with the patient medical data to the remote computer. Also, a method controls the acquisition and analysis of patient medical data over a network by a central server from a remote computer operably interconnected by the network with the central server.
Owner:ERESTECH
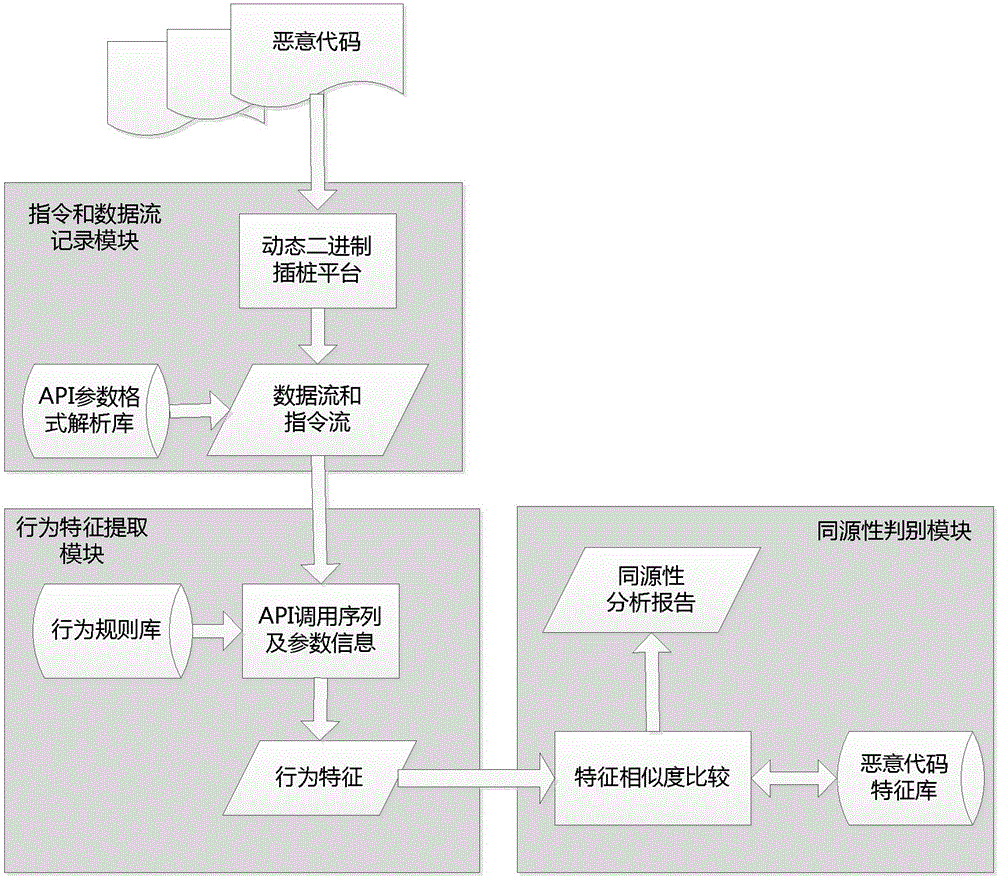
Behavior characteristic similarity-based malicious code homology analysis method
ActiveCN104866765AEasy to analyzeExact homologyPlatform integrity maintainanceProgramming languageAnalysis working
The invention provides a behavior characteristic similarity-based malicious code homology analysis method, which comprises the steps of: firstly extracting and quantifying behavior characteristics representing malicious codes based on a dynamic binary pile platform, on this base, measuring the similarity of the behavior characteristics among different malicious codes, and reflecting a homology judgment result of the malicious codes with the similarity of the behavior characteristics. By using the invention, the malicious codes collected in a network can be subject to homology analysis, and a powerful support is provided for tracing of a subsequent attack source. The method can correctly reflects the homology among samples of the malicious codes, correctly differentiates the samples of the malicious codes without homology, and has important guidance and reference significances in analysis work of the homology of the malicious codes.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
Automated system adaptation technique particularly for data storage systems
InactiveUS6978259B1Simple designInput/output to record carriersError detection/correctionComputerized systemAnalysis working
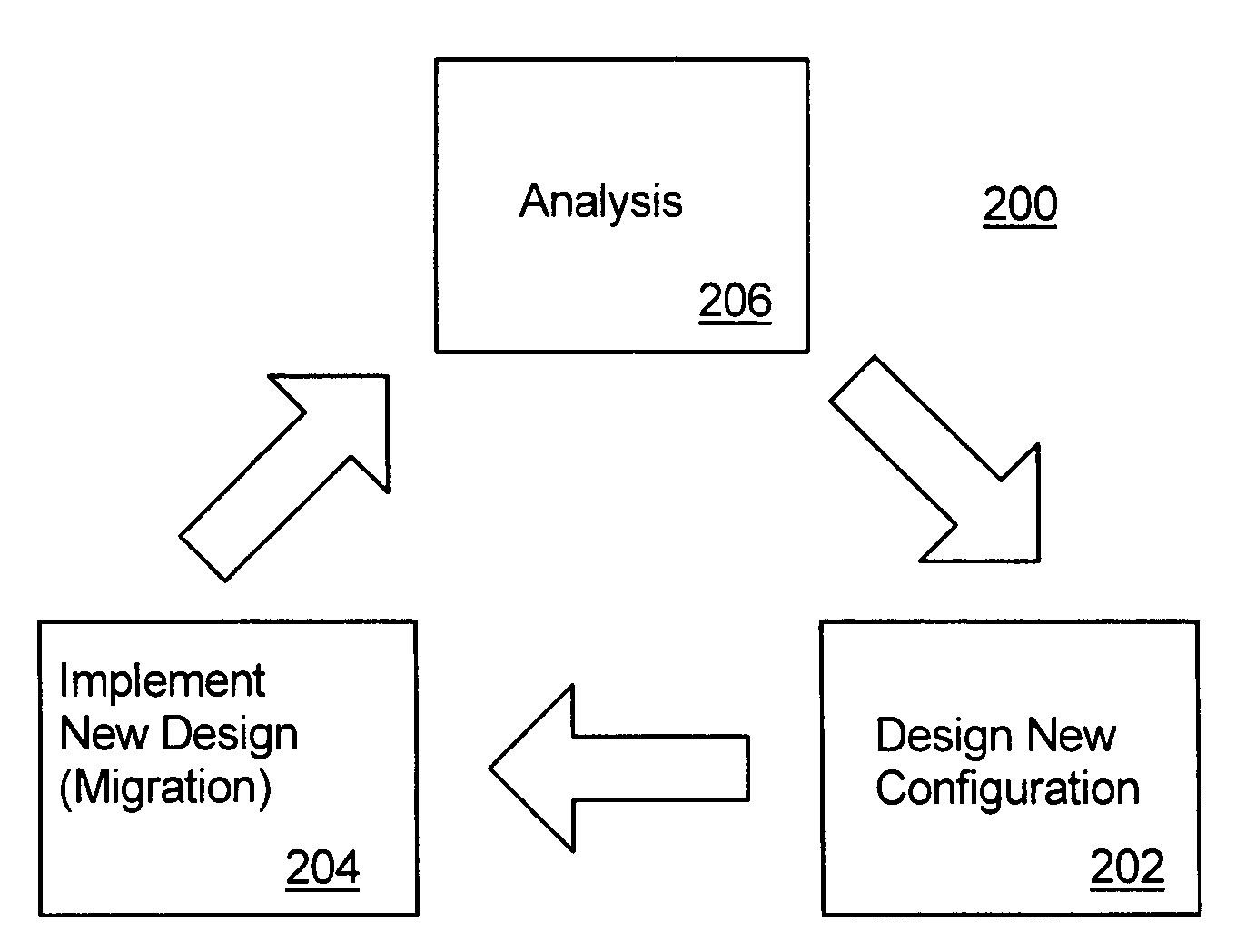
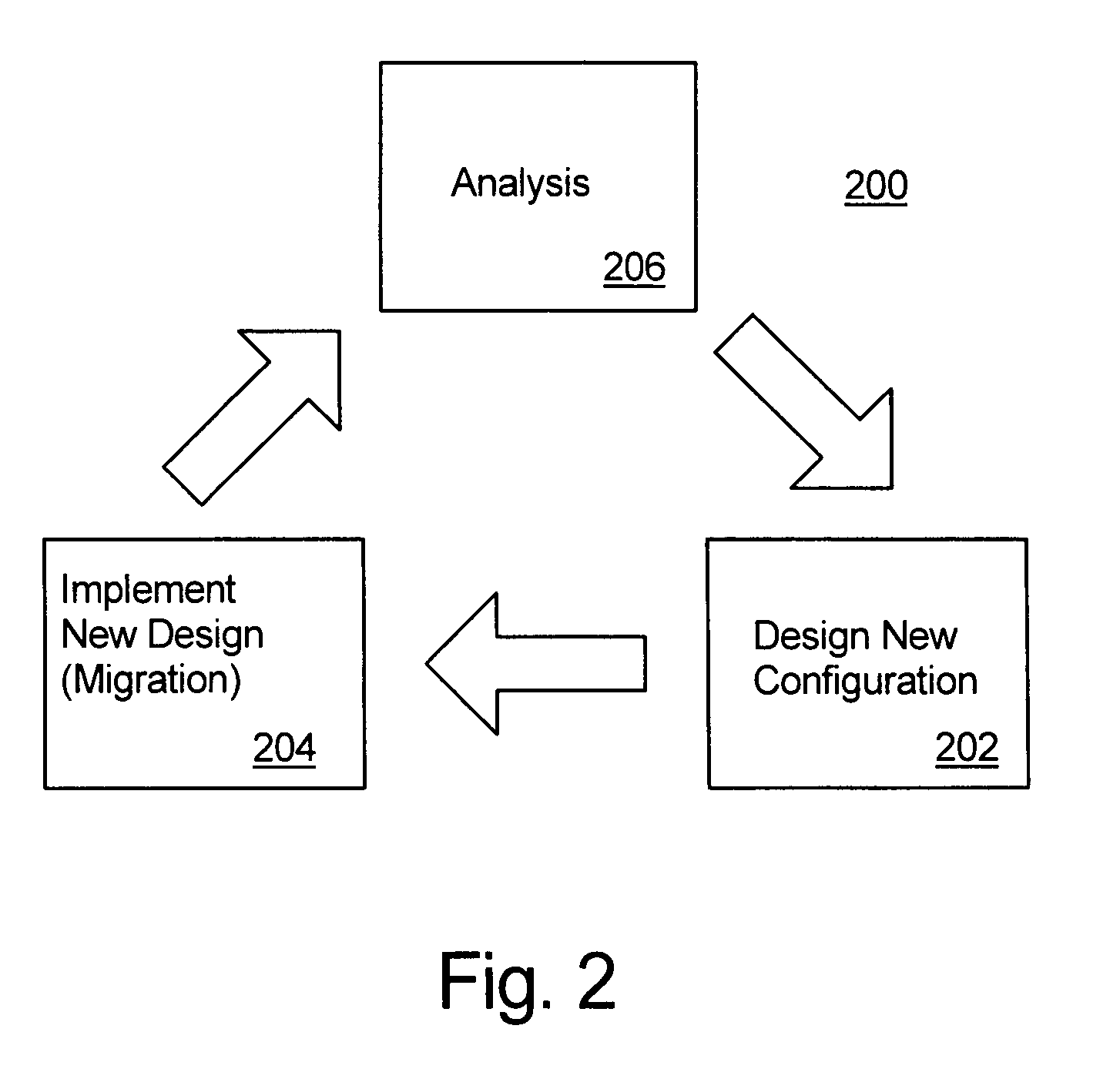
An automated system adaptation technique for computer systems, networks and subsystems generally and, more particularly, for data storage systems. The invention programmatically designs, configures and manages a system, such as a data storage system. This is accomplished by performing a sequence of steps in an iterative loop, including analyzing the operation of the system under a workload, generating a new design based on the analysis and migrating the existing system to the new design. By systematically exploring a large design space and developing designs based on analyses of the workload, the invention generates designs that are improved in comparison to conventional design techniques. By programmatically repeating these tasks, the invention causes the system to converge to one that supports the workload without being over-provisioned.
Owner:HEWLETT-PACKARD ENTERPRISE DEV LP
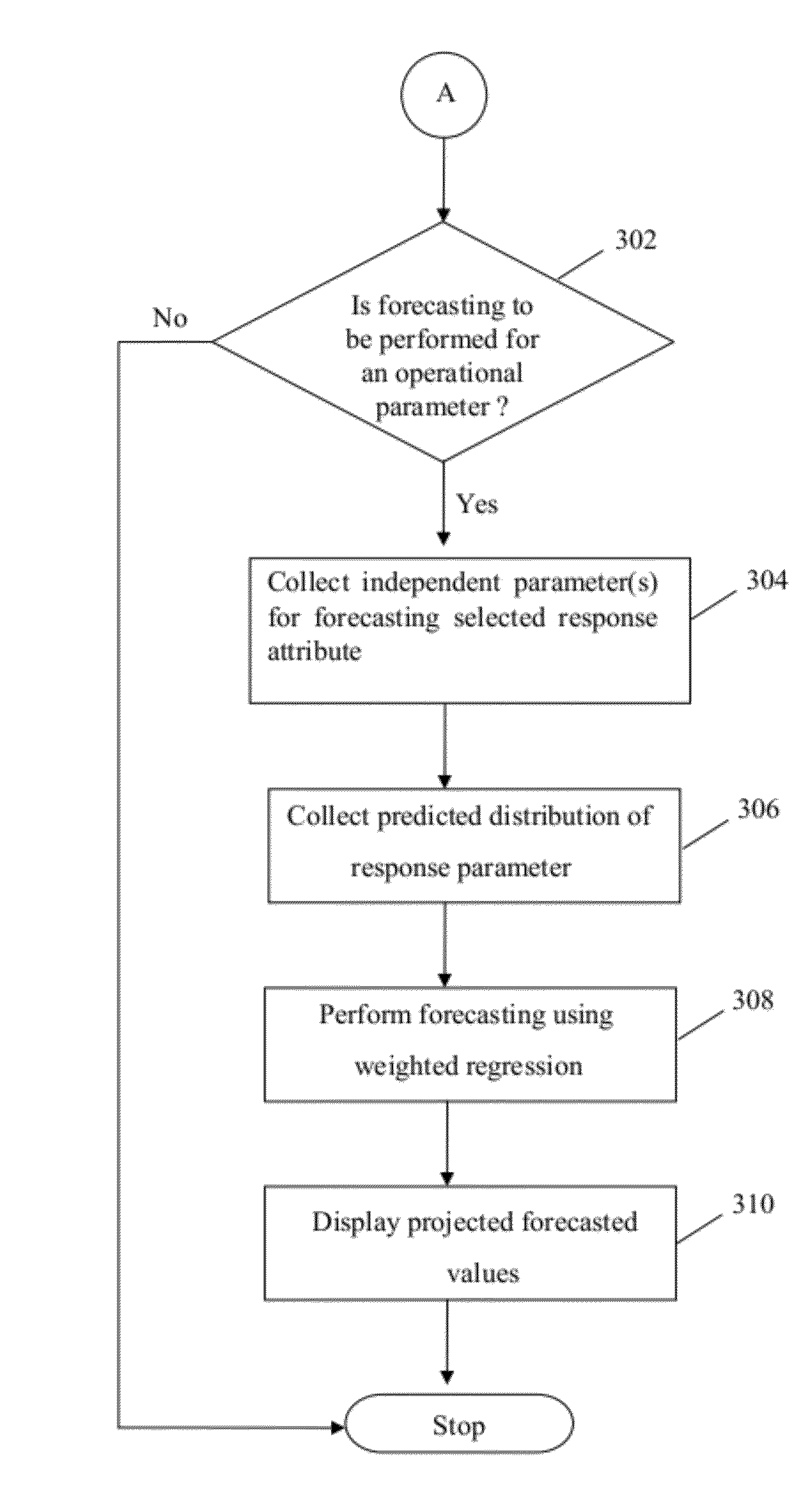
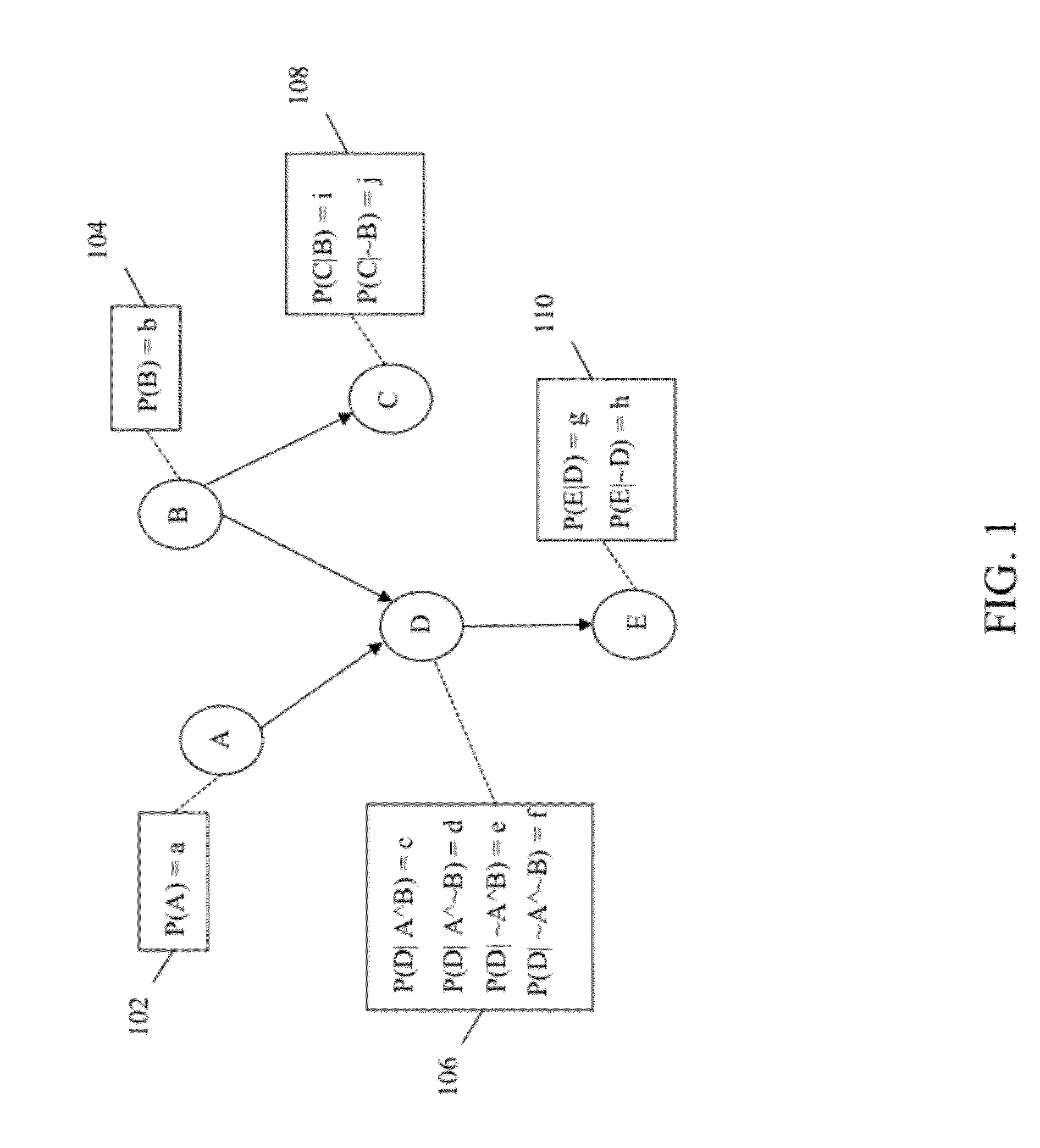
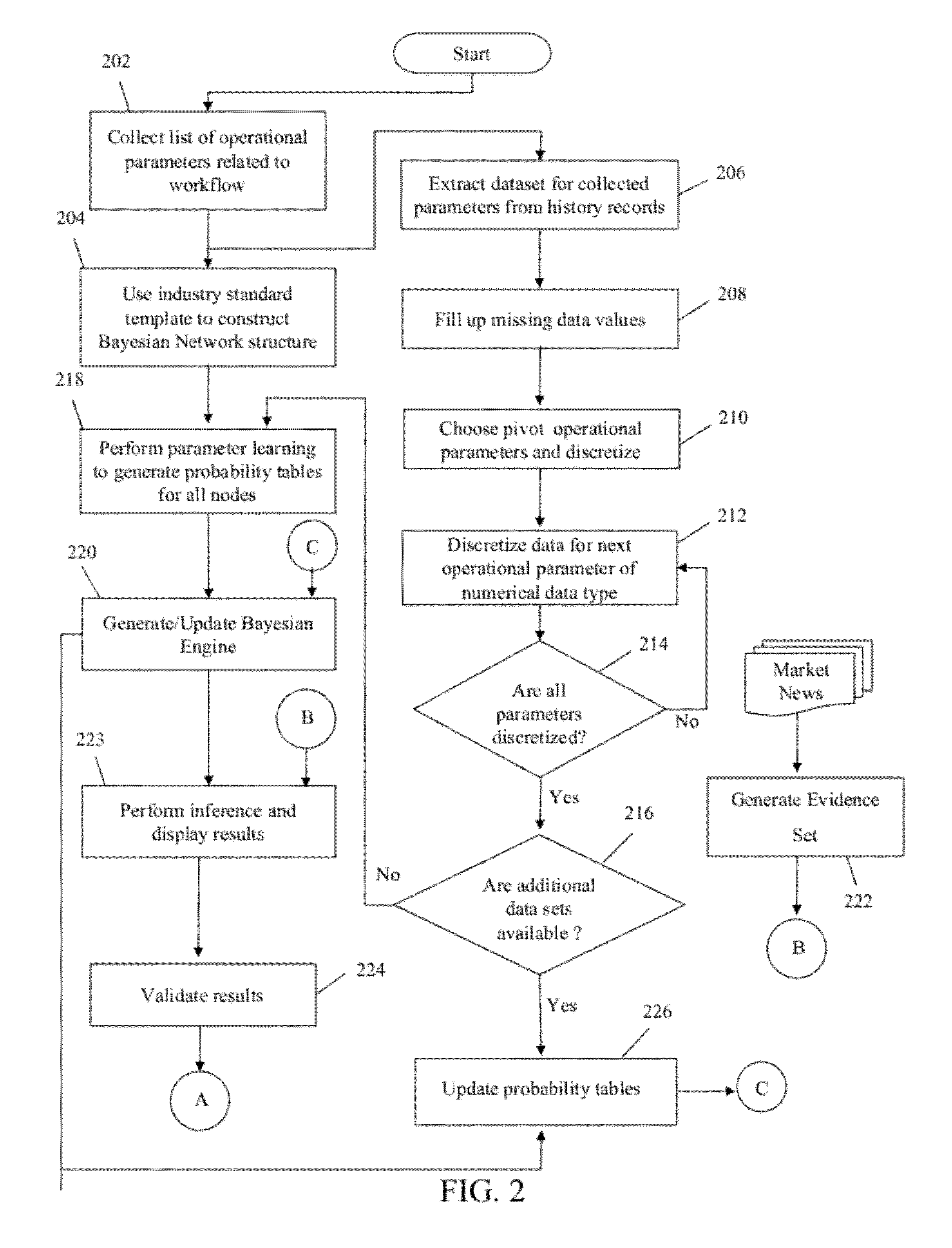
Method and system for estimation and analysis of operational parameters in workflow processes
A system and method for estimation and analysis of operational parameters in workflow processes in order to establish effect of parameters on one or more critical parameters is provided. The method includes creating a Bayesian network including one or more operational nodes representing one or more operational parameters and one or more critical nodes representing one or more critical parameters. The method further includes generating an evidence set based on market events and deducing inferences based on the generated evidence set and Bayesian engine. Inferences are deduced by determining possible discrete states of operational parameters associated with one or more target nodes and their probability distribution values. Deduced inferences are then validated to confirm strength of probability distribution values. Forecasting for a selected operational parameter is performed by obtaining probability distribution of independent parameters and then performing forecasting for the selected parameter using Bayesian locally weighted regression model.
Owner:INFOSYS LTD
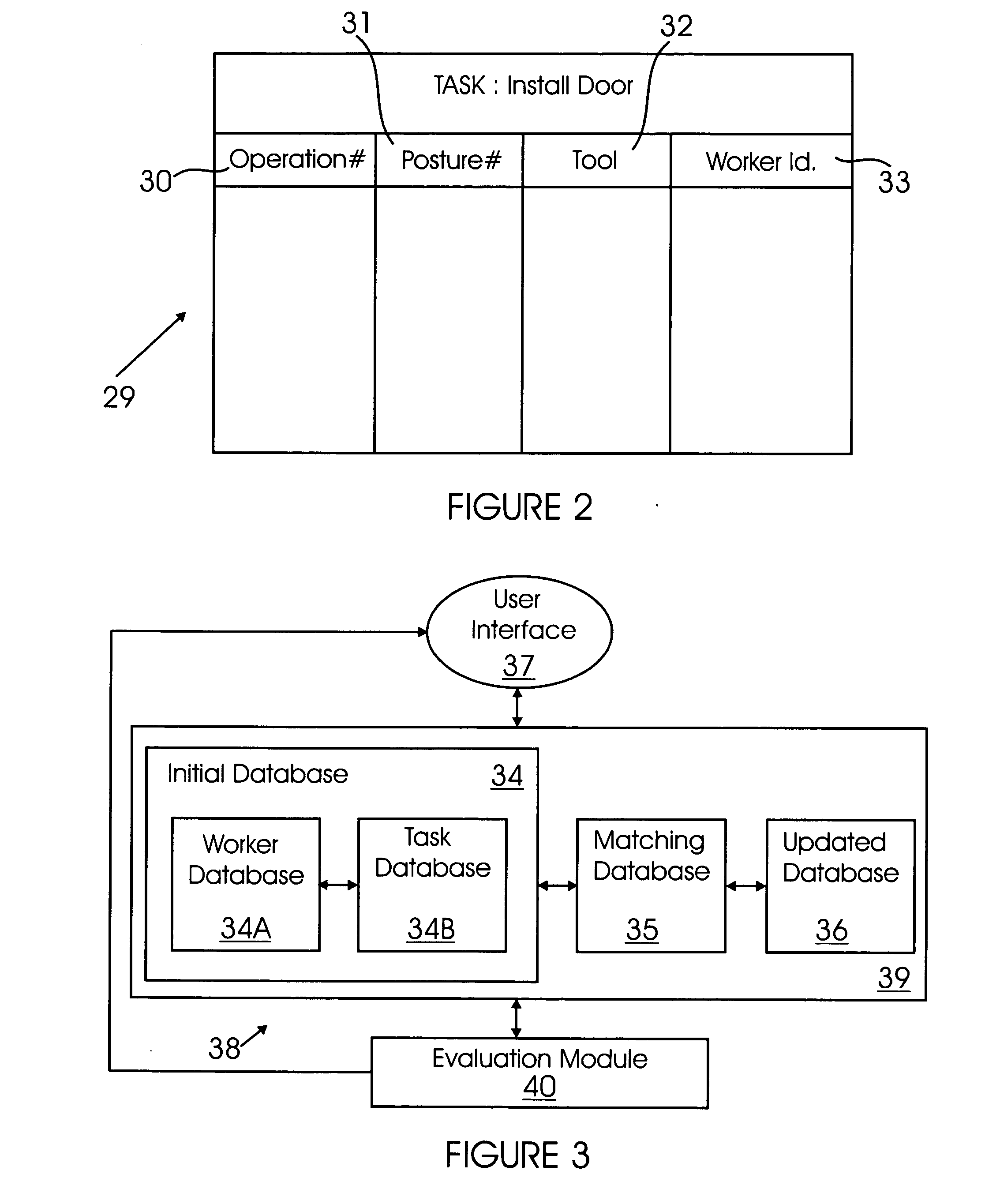
Automated factory work analyzer
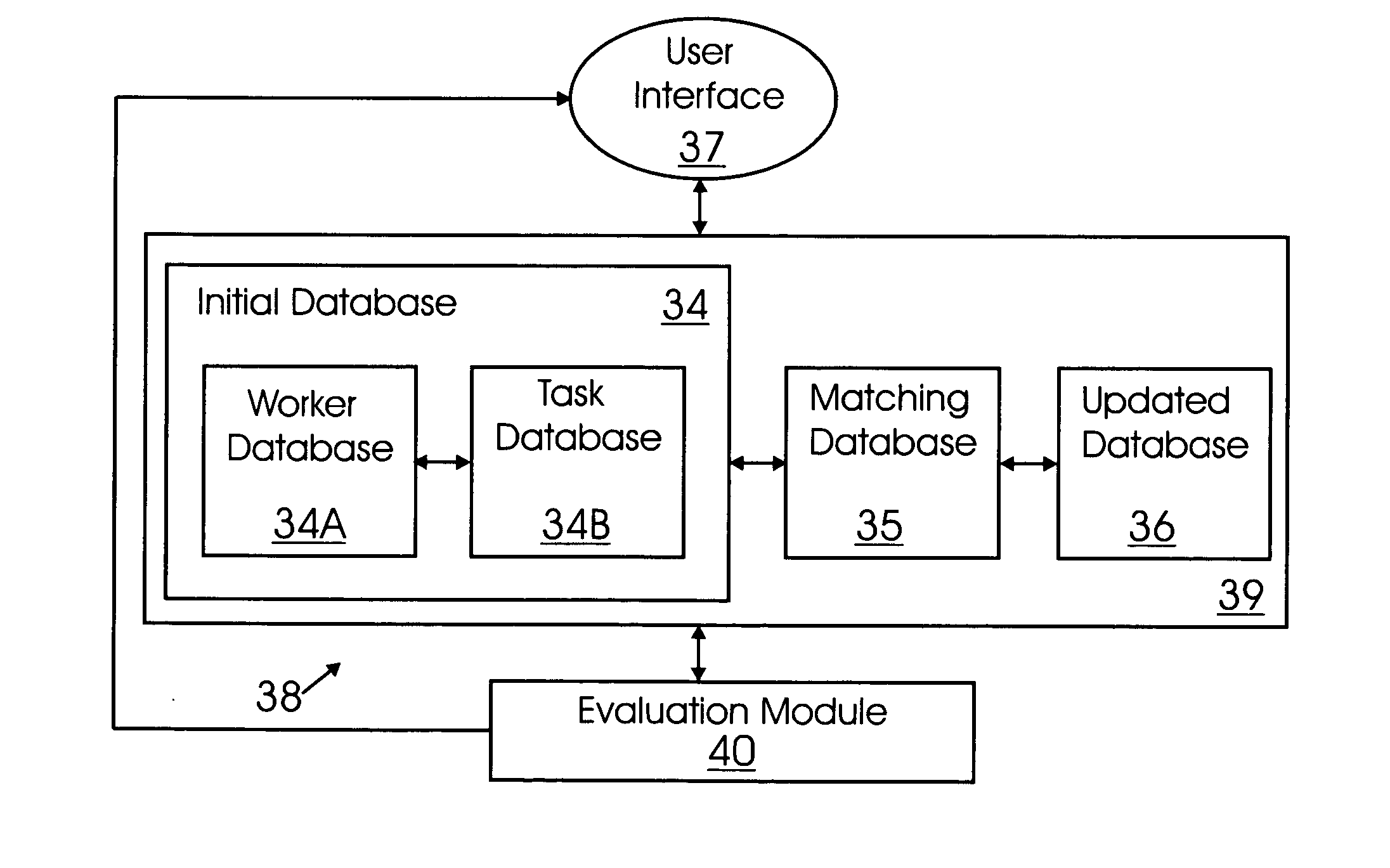
InactiveUS20060259472A1ResourcesSpecial data processing applicationsAnalysis workingArtificial intelligence
A method and system for analyzing work in a workplace is provided. The method includes providing a worker database; providing a task database for a plurality of tasks, which includes providing one or more task configurations for each of task and including configuration attributes for the task configurations; matching worker attributes with the task configuration attributes; evaluating the match of the worker attributes with the task configuration attributes; and updating the worker database and the task database upon satisfactory matching of worker attributes with the task configuration attributes. The system includes a worker database, wherein the worker database includes one or more worker attributes; a task database for a plurality of tasks; a user interface for accessing the worker database and the task database for entering worker and task information; and an evaluation module that evaluates a match of worker attributes with the task configuration.
Owner:THE BOEING CO
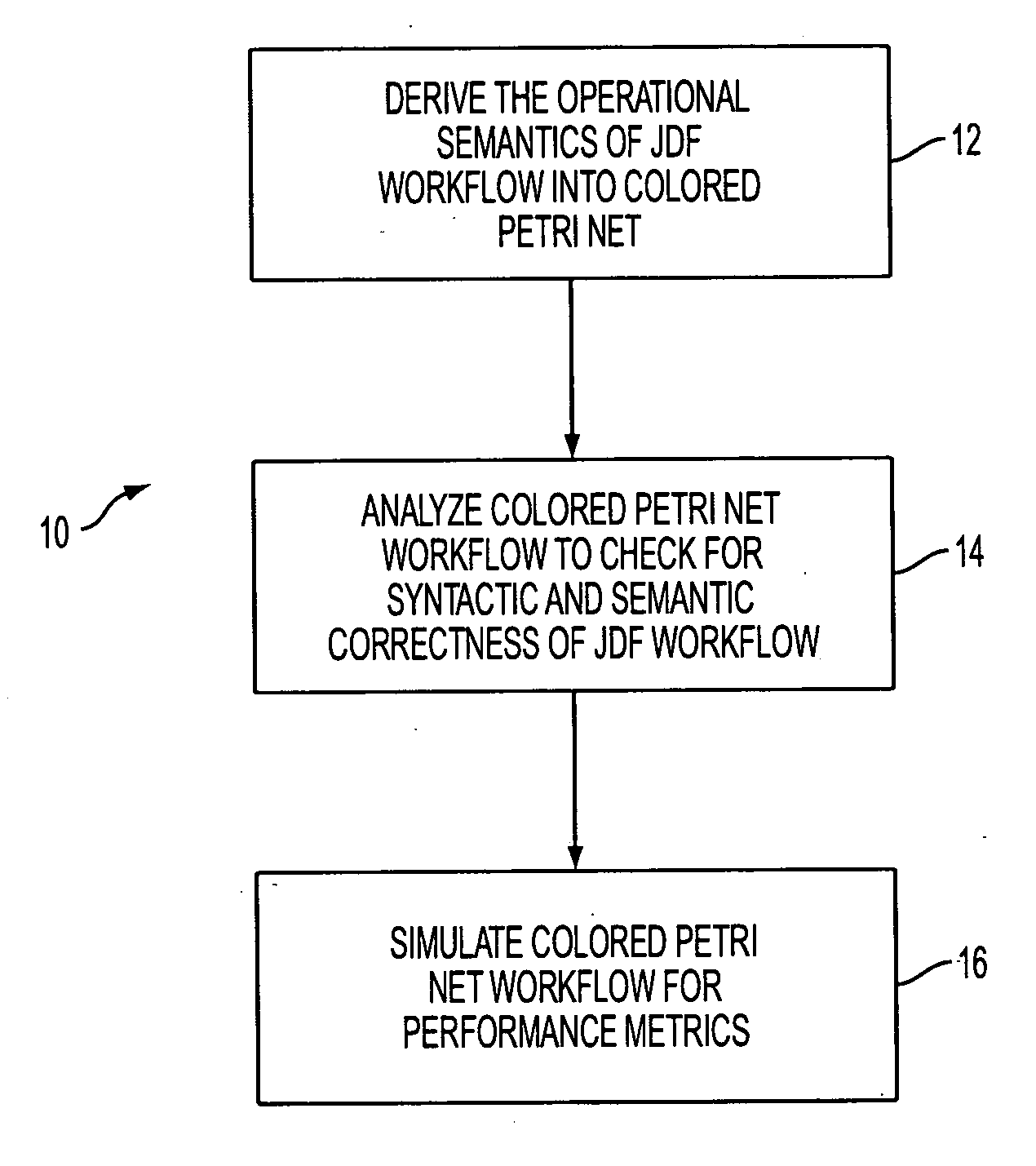
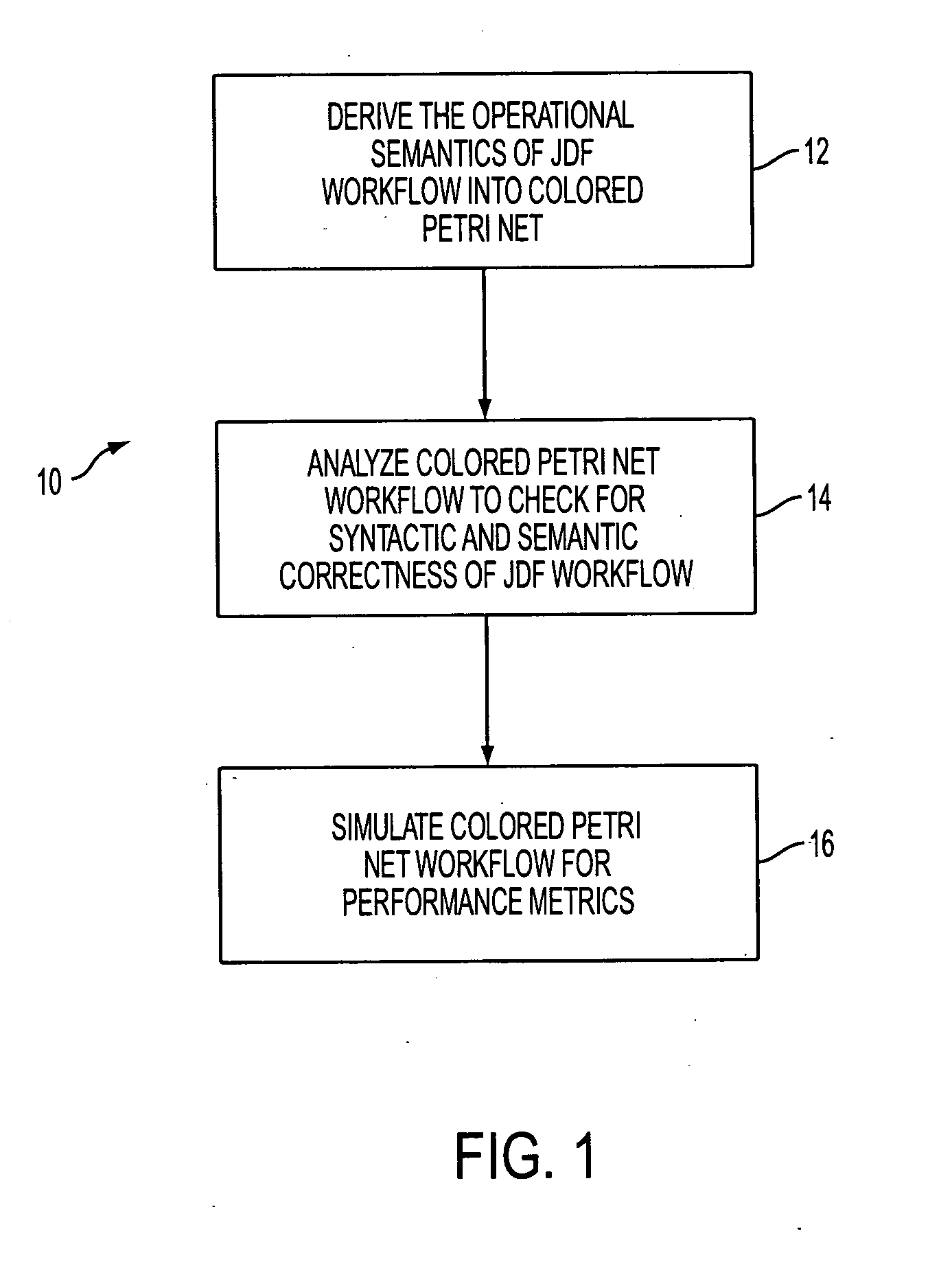
Validation and analysis of JDF workflows using colored Petri nets
A method and system for translating a JDF workflow into a colored Petri net representation. Once the workflow has been converted, the colored Petri net is validated and analyzed. This provides the ability to identify potential deadlock conditions within a JDF workflow. In addition, the model network can be used to simulate throughput and turnaround time of a workflow and the effects of resources arriving at various times.
Owner:XEROX CORP
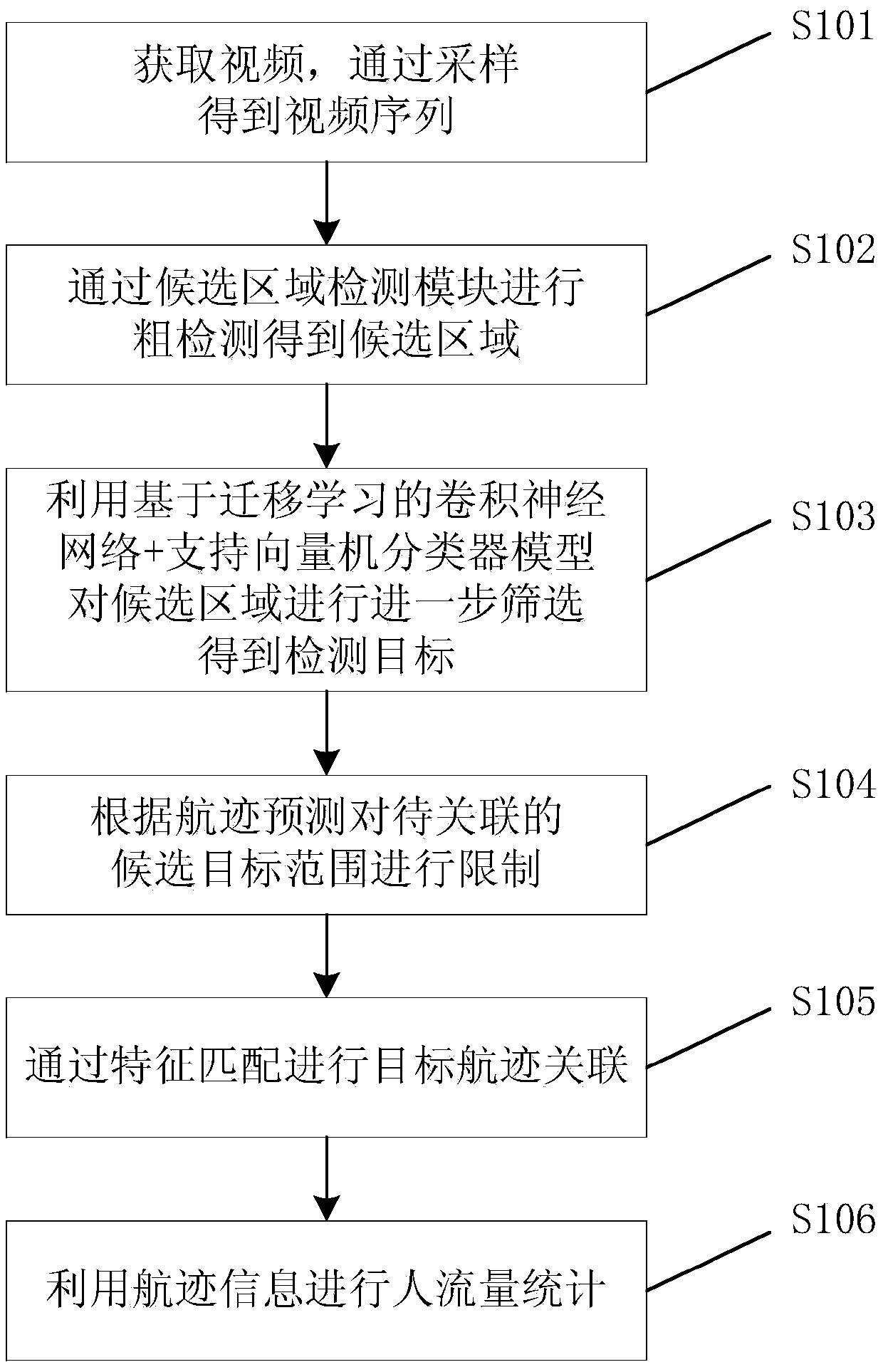
Method for acquiring people flow on the basis of video sequence
ActiveCN105512640AOvercome Counting DisadvantageSave human resourcesImage enhancementImage analysisVideo monitoringSupport vector machine classifier
The invention relates to a method for acquiring a people flow on the basis of a video sequence and belongs to the technical field of image processing and video monitoring. The method comprises the following steps of: 1), acquiring a video and obtaining the video sequence by means of sampling; 2) performing coarse detection by using a candidate area detection module so as to obtain candidate target areas; 3) further screening the candidate target areas by using a convolutional neural network based on transfer learning and a support vector machine classifier model so as to obtain a detection target; 4) restricting a candidate target range to be associated according to track prediction; 5) associating target tracks by means of feature matching; and 6) acquiring the people flow by means of track information. The method saves a large number of human resources, prevents error statistics duo to man-made factors, well overcomes the disadvantages of manual counting in some cases, and may accurately locate a single pedestrian in order to provide great significance for subsequent analysis.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Identification method for application layer protocol characteristic
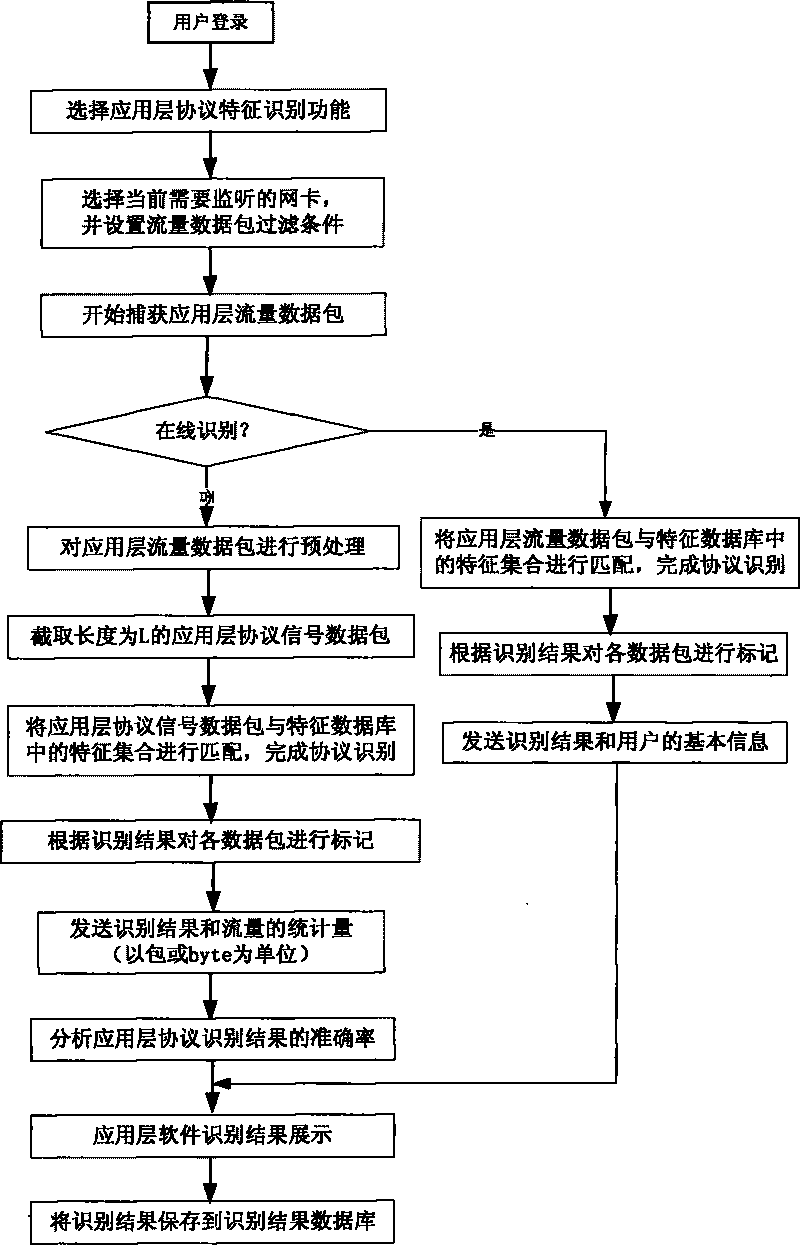
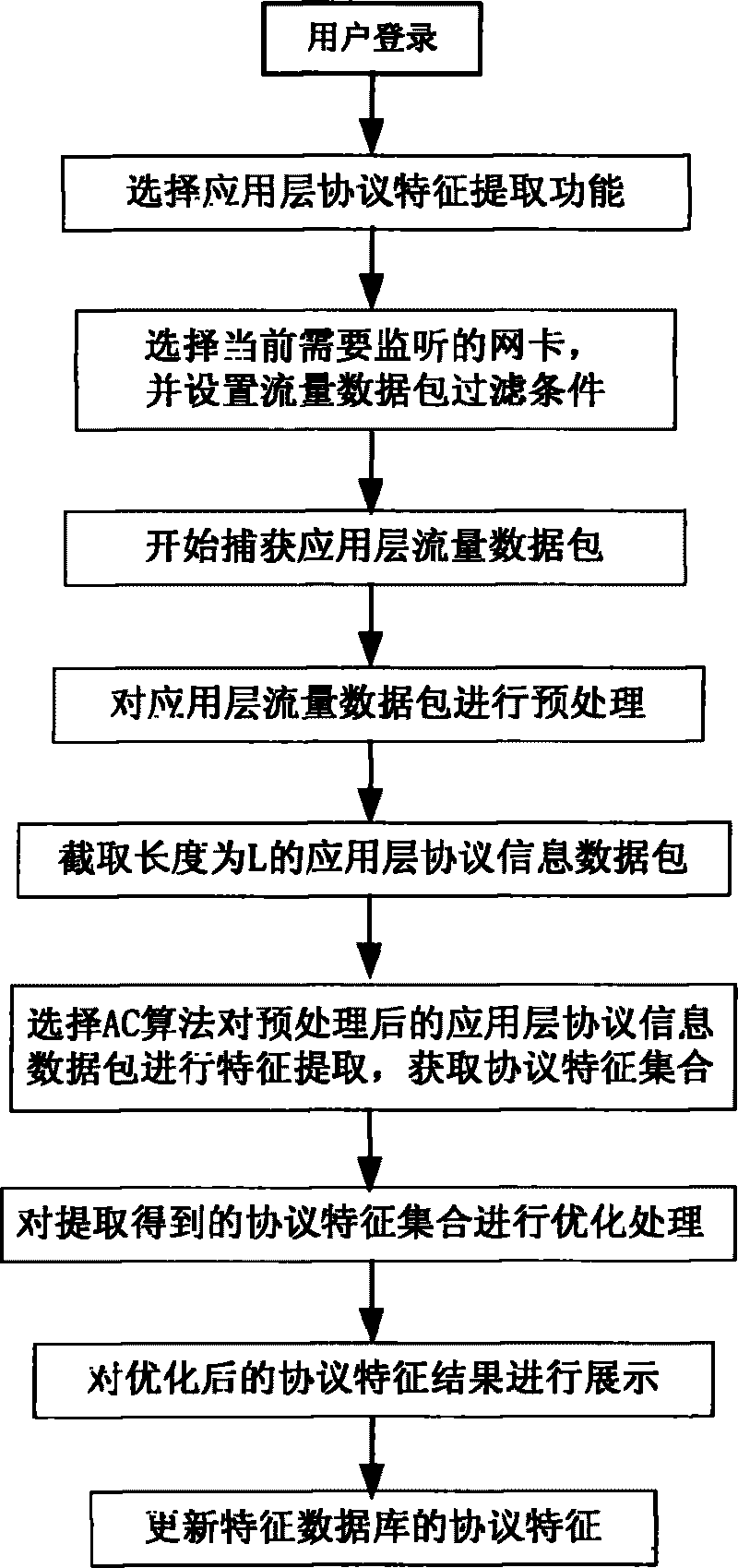
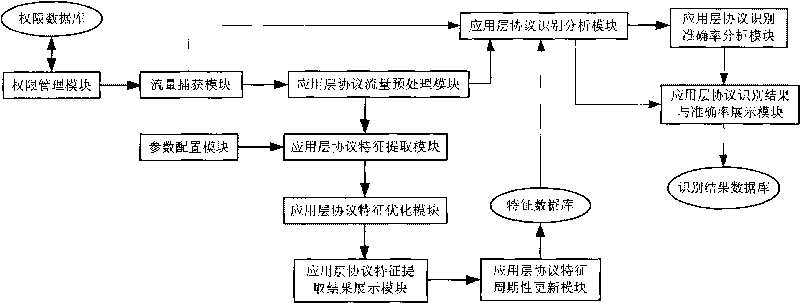
InactiveCN101741908AImprove accuracyPromote informatizationData switching networksInformatizationNetwork packet
The invention discloses an identification method for application layer protocol characteristics, comprising the following processes: capturing a flow packet, selecting an identification mode, pretreating the flow packet, combining a characteristic set in a characteristic database to identify current network flow and displaying an identification result. The characteristic set in the characteristic database is updated timely by adopting a set of data mining AC algorithm based on an Apriori algorithm, thereby improving the accuracy of identifying the application layer protocol, overcoming various disadvantages of identifying network protocols by the traditional manual analysis method, promoting the informatization and intellectualization of application layer protocol analysis work for enterprises and companies, reducing labor source load for enterprises and companies and improving work efficiency and rate of progress.
Owner:青岛朗讯科技通讯设备有限公司
SVG (Scalable Vector Graphics) technology-based distribution network modeling system
InactiveCN103559355AEffective displayIntuitive displaySpecial data processing applicationsInformation technology support systemNODALWiring diagram
The invention relates to an SVG technology-based distribution network modeling system. The single-line diagram of the distribution network modeling system is generated according to the following steps: SVG entities are respectively constructed with different patterns according to different types of distribution network structures contained in a distribution model; according to the branch information contained in a distribution network wiring diagram, the basic branch entities of an SVG topological diagram are constructed; node entities and branch entities are respectively constructed with different colors and solid and dotted patterns according to operating states; the entity shape of each equipment in a distribution network is customized in advance; the data of a power grid model are accessed and read; and the single-line diagram of the distribution network is formed by merging, and a closed loop model is automatically generated. The SVG-based pattern vector display technology disclosed by the invention can efficiently and visually display distribution network wiring diagrams in real time. The SVG technology-based distribution network modeling system can effectively increase working efficiency and provide a variety of appropriate topological diagram display modes for users, and is used in various power grid analysis works.
Owner:STATE GRID CORP OF CHINA +1
Automatic code rule checking platform
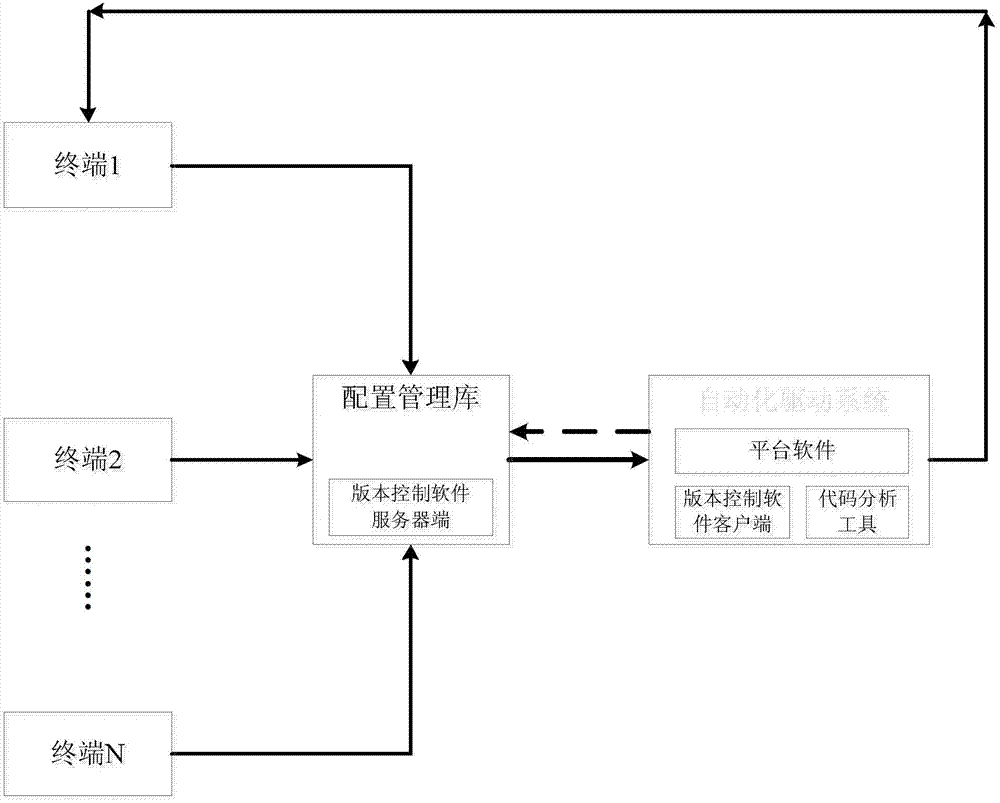
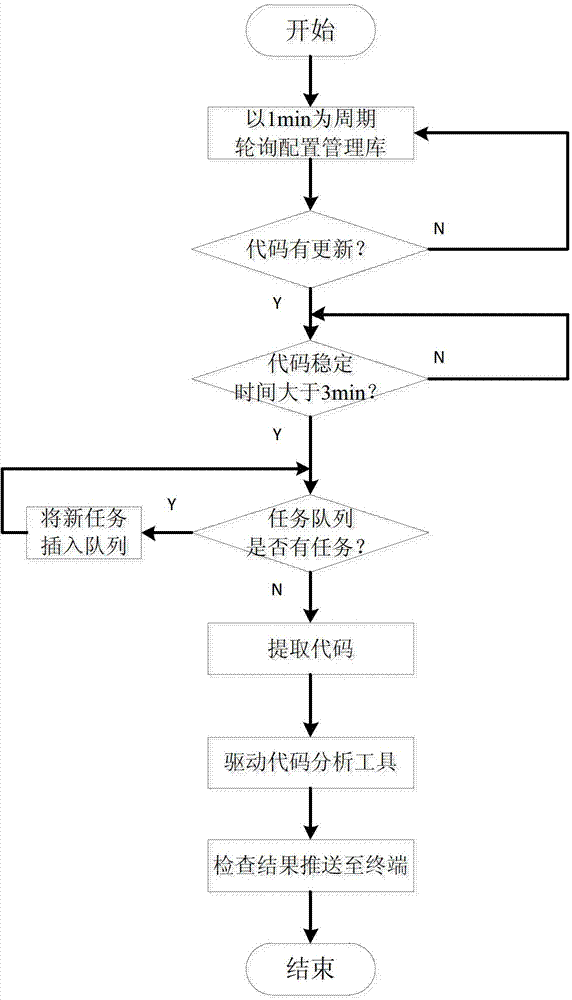
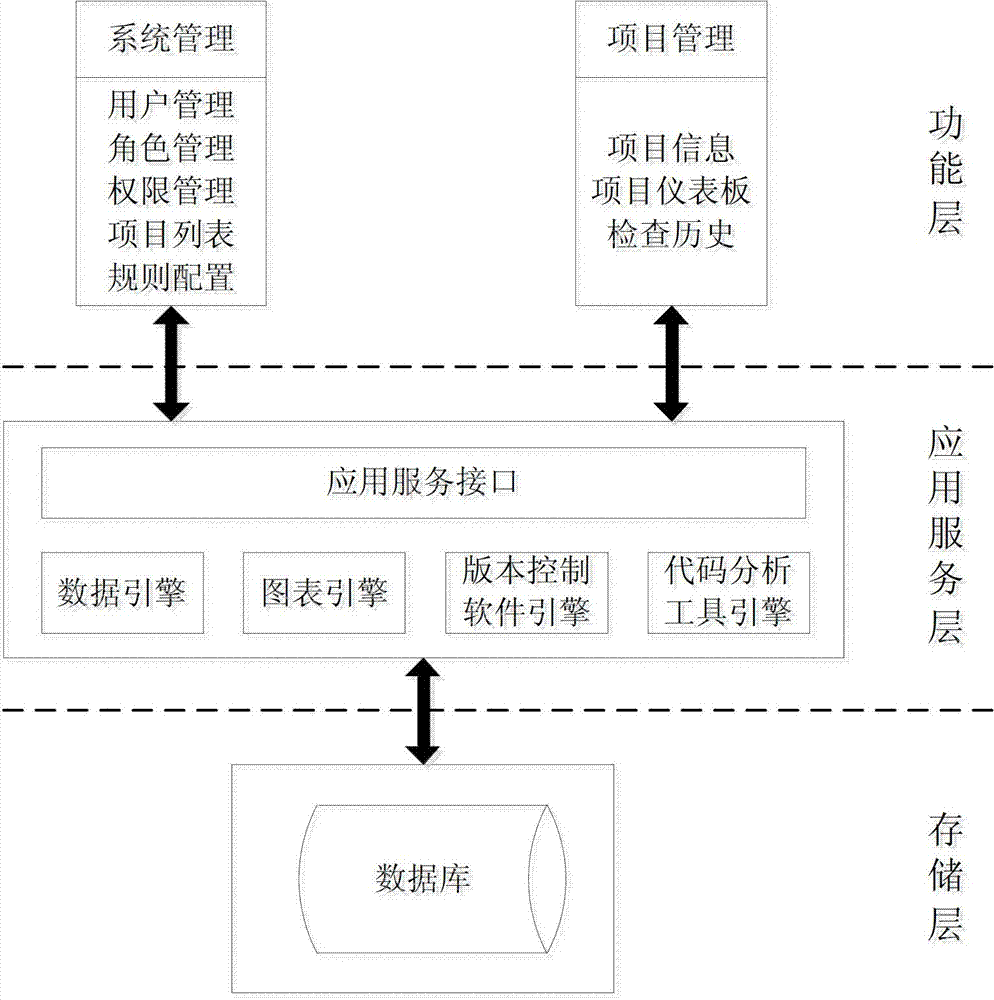
ActiveCN103309804AReduce late riskQuality improvementSoftware testing/debuggingAnalysis workingPersonal computer
The invention discloses an automatic code rule checking platform, which aims at providing the automatic code rule checking platform which helps developers find and overcome code defects in time. The automatic code rule checking platform is realized through the following technical scheme: codes which are edited or modified by a personal computer terminal are submitted to a configuration management library through a version control software client; an automatic driving system monitors the configuration management library in a polling mode; when the codes in the configuration management library are changed, platform software starts the version control software client to extract updated codes in the configuration management library, and a code analysis tool is called to check a code rule; the version control software client searches for the codes from the configuration management library and submits the codes to the code analysis tool to check the code rule; the code analysis tool executes code analysis work according to the item information, the check condition and the code check rule set configured or set by a terminal user, and the platform software shows check results to the developers.
Owner:10TH RES INST OF CETC
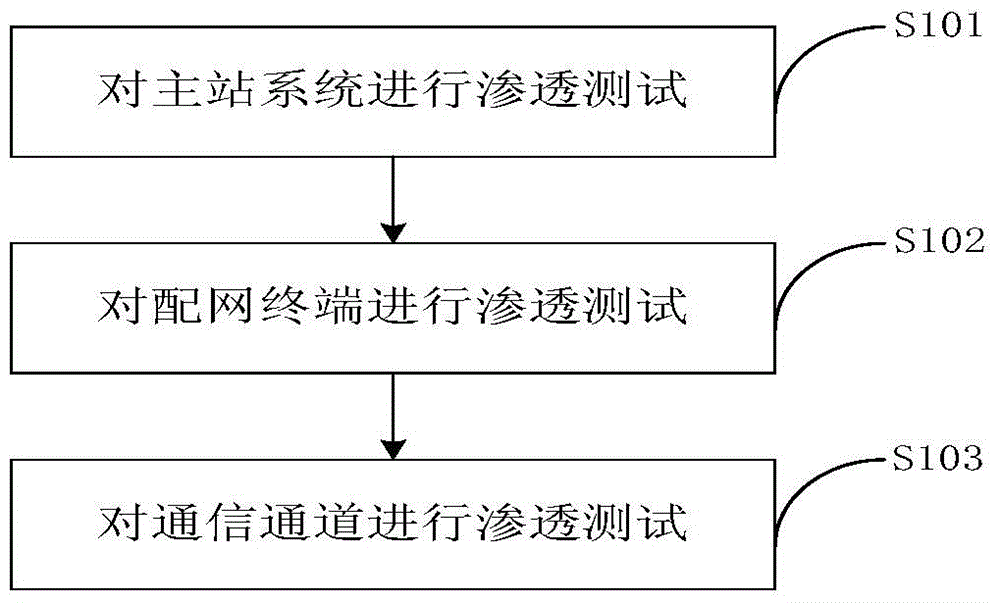
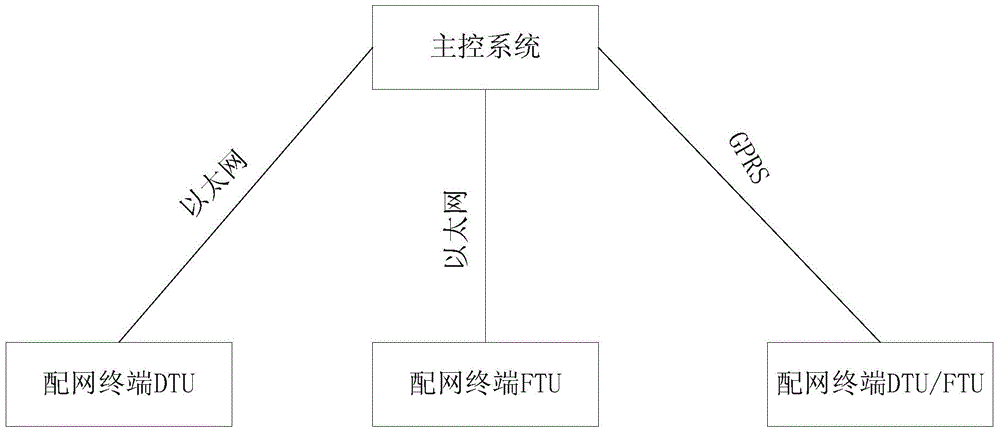
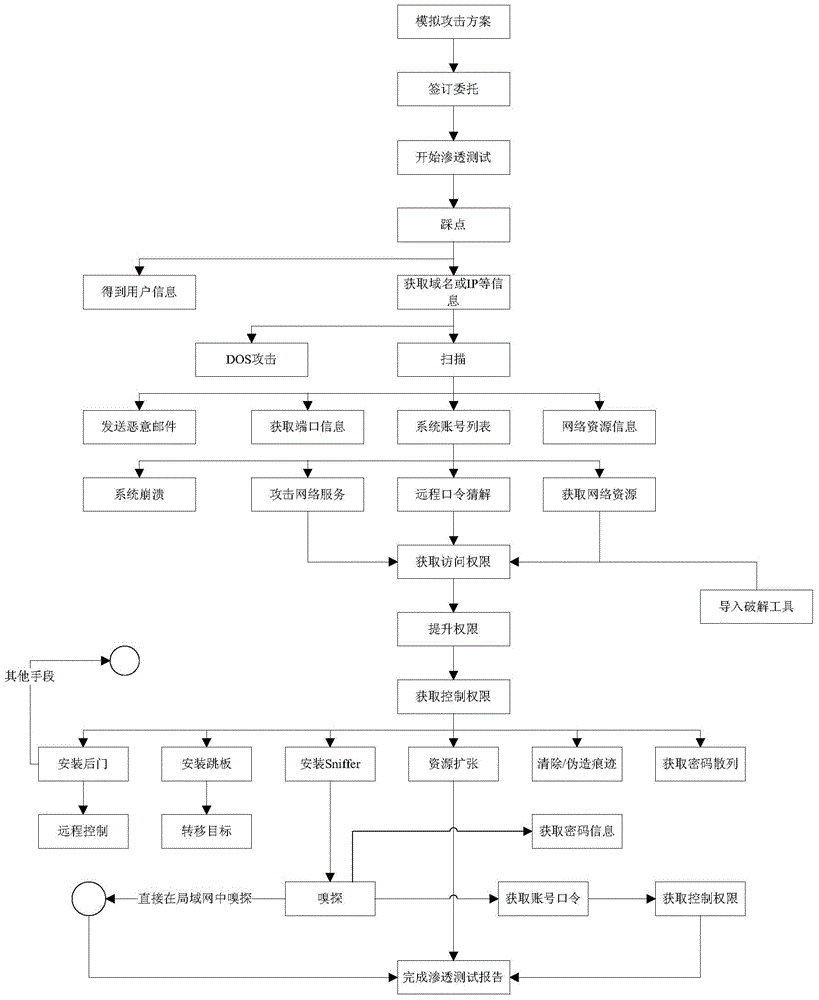
Information safety penetration testing method for distribution automation system
ActiveCN104468267AAchieve consistencyImplementations should be consistent withData switching networksThe InternetMaster station
The invention discloses an information safety penetration testing method for a distribution automation system. Penetration testing is carried out on a master station system, a distribution network terminal and a communication channel, the information system vulnerability penetration testing technology is fully used, the safety of the distribution automation system is evaluated by simulating the attack method of a hacker, and the information safety penetration testing method includes the active analysis for any weakness, technical defects or loopholes of the master station system, the communication circuit and the distribution network terminal. The information safety penetration testing method for the distribution automation system can be used for safety risk analysis work before the distribution automation system is connected to the internet, guidance is provided for finishing problem rectification and reformation and retest work of manufacturers with safety risks, and the method is high in pertinence and wide in test range. Compared with a traditional penetration testing method, the test time can be largely shortened, offline repairing events caused by safety problem failures after equipment is on line are reduced, the information safety penetration testing for the distribution automation system is realized, and the information safety penetration testing method can be applied to industrial control systems inside and outside the industry.
Owner:STATE GRID CORP OF CHINA +1
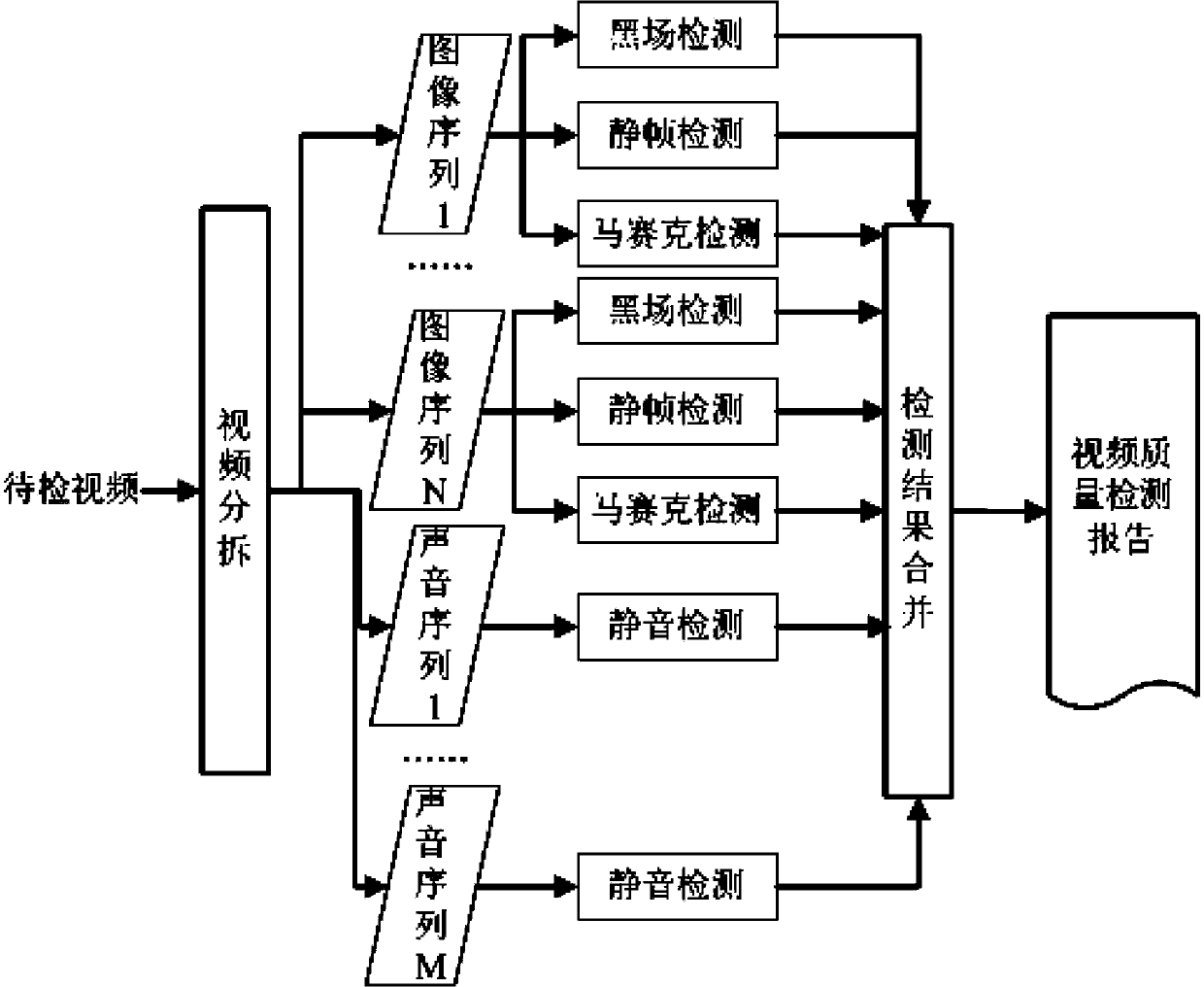
Multi-mode parallel video quality fault detection method and device
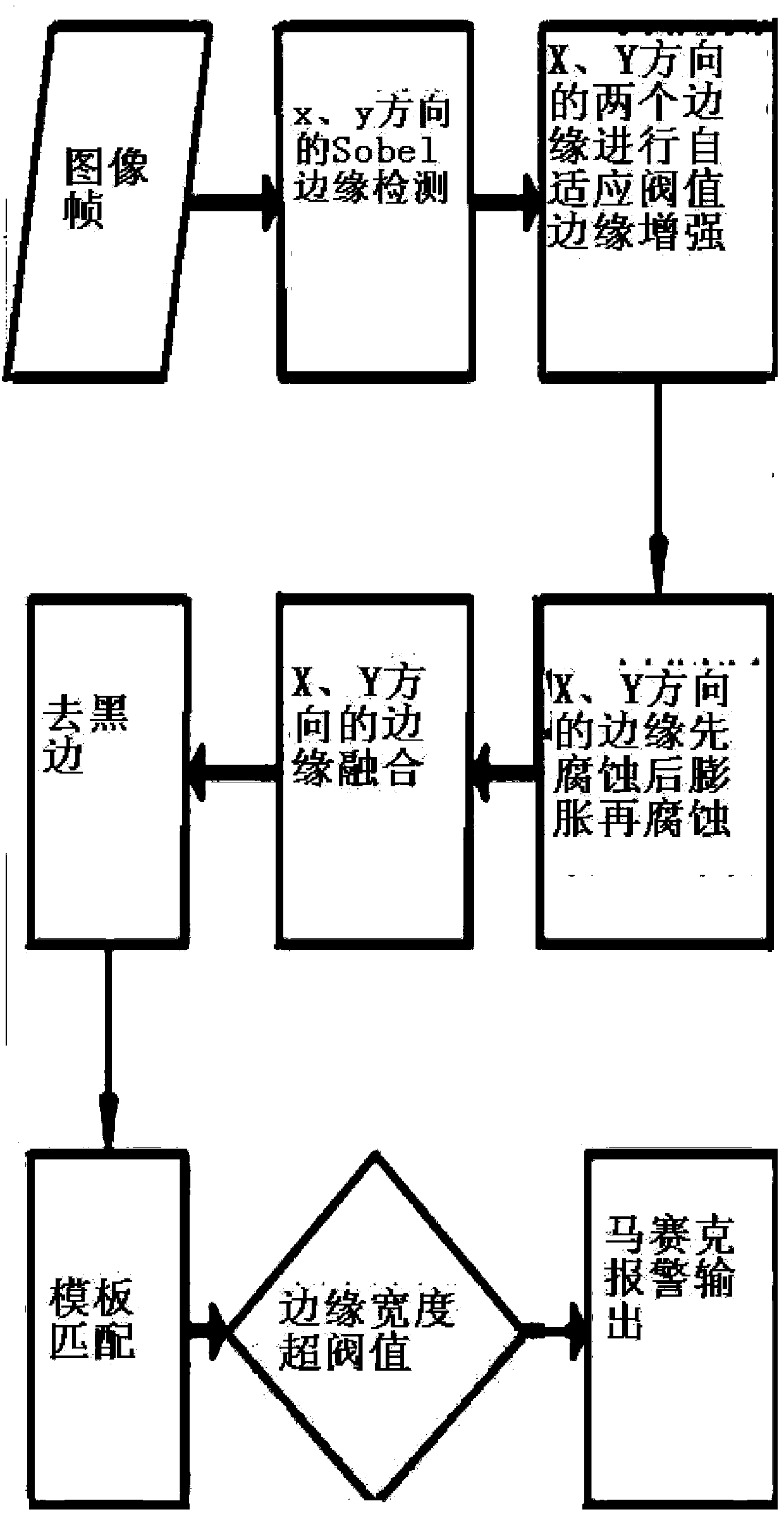
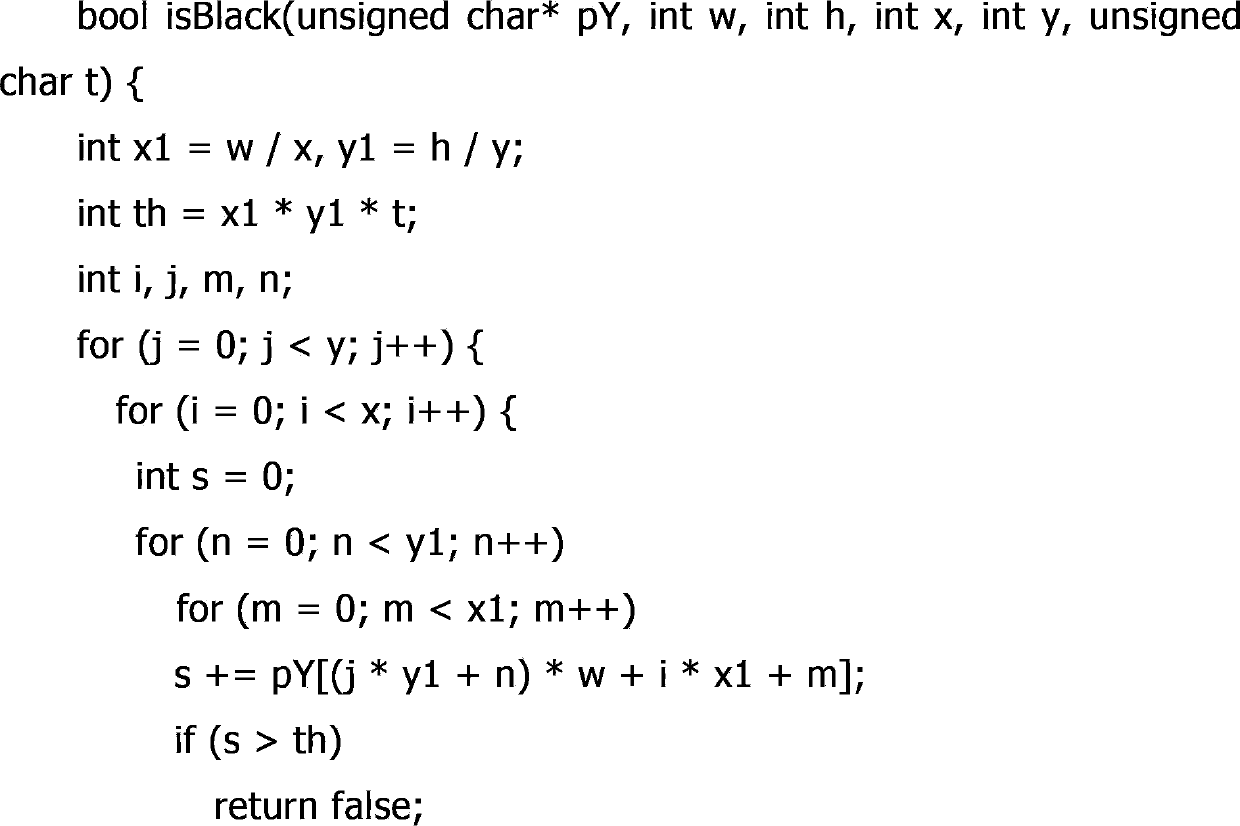
The invention discloses a multi-mode parallel video quality fault detection device and a corresponding method. The device of the invention comprises a video partitioning module, a black field detection module, a static frame detection module, a mosaic detection module, a silence detection module, and a detection result merging module. Correspondingly, the method of the invention also comprises six steps, i.e., a video partitioning step, a black field detection step, a static frame detection step, a mosaic detection step, a silence detection step, and a detection result merging step. The technical scheme of the invention is adopted, through a framework of parallelization analysis, analysis work of video quality is divided to a plurality of CPUs to be carried out, and a corresponding system is realized, thereby greatly improving the speed of video quality examination.
Owner:上海文广互动电视有限公司
SOA system reliability evaluation method based on complex network theory
ActiveCN104298593AEmphasis on topological featuresEasy to operateSoftware testing/debuggingCascading failureStructure and function
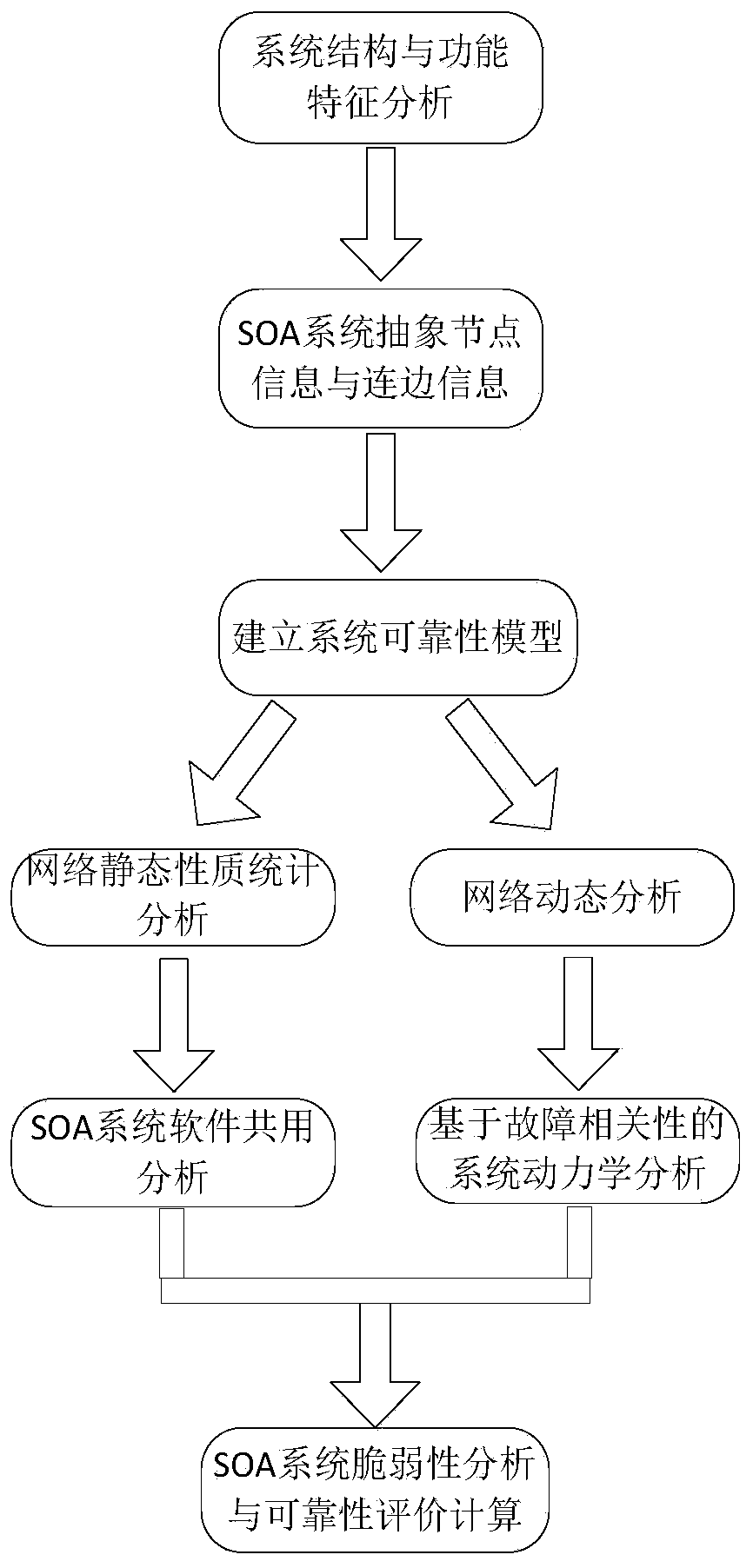
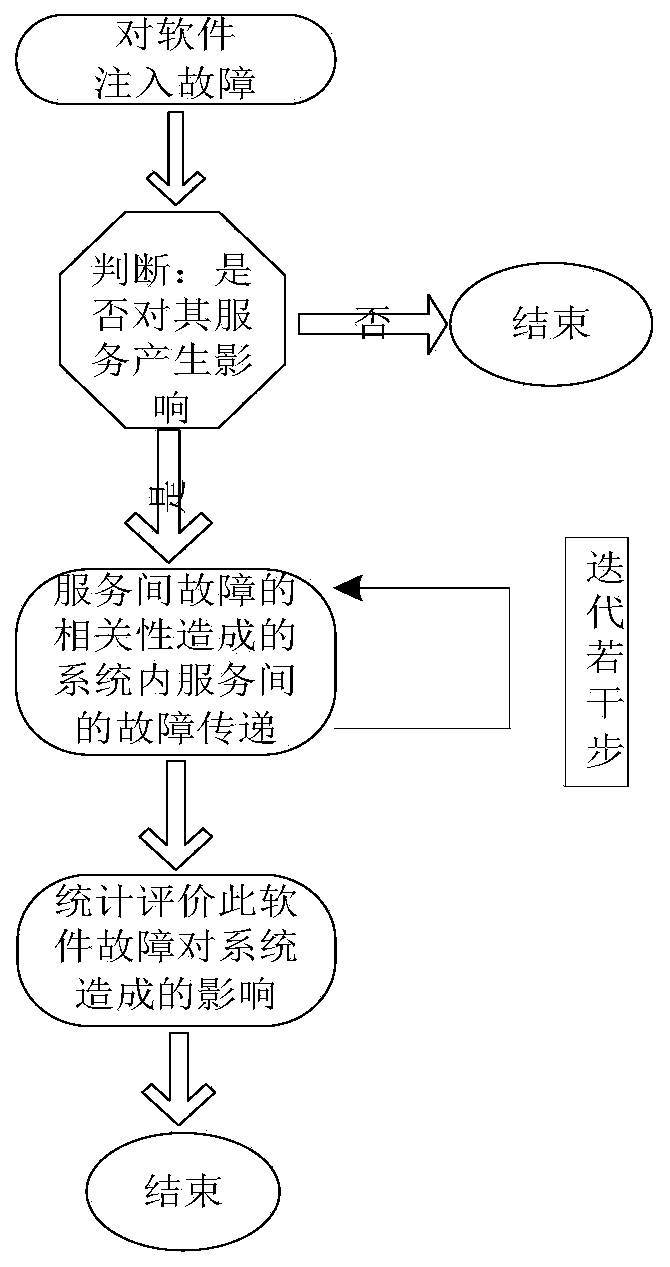
An SOA system reliability evaluation method based on a complex network theory comprises four steps, belongs to the technical field of complex system reliability and aims at solving the problem that an SOA system is complex in structure and function and a traditional reliability analysis method is difficult to implement and even cannot be implemented and putting forward a methodology for effectively analyzing the reliability of the complex SOA system. The SOA system reliability evaluation method is characterized in that the method is innovatively integrated with the complex network theory, objects in the SOA system and the mutual effect of the objects are abstracted to be nodes and connecting lines in a complex network so as to establish a complex network failure model, a cascading failure model for the SOA system is put forward, and reliability analysis work is completed by utilizing a Monte Carlo simulation experiment on the basis so as to find key software and a weak structure influencing the system reliability. The SOA system reliability evaluation method is not limited by system scale, and increase of the system scale does not enable the calculation complex degree of the method to be remarkably improved. The SOA system reliability evaluation method is clear in physical significance and easily operated and implemented by engineers.
Owner:BEIHANG UNIV
Method and device for detecting snaking motion instability of high speed train bogie
InactiveCN102706569AAccurate monitoring of snaking motion stabilityNot affectedRailway vehicle testingBogieInstability
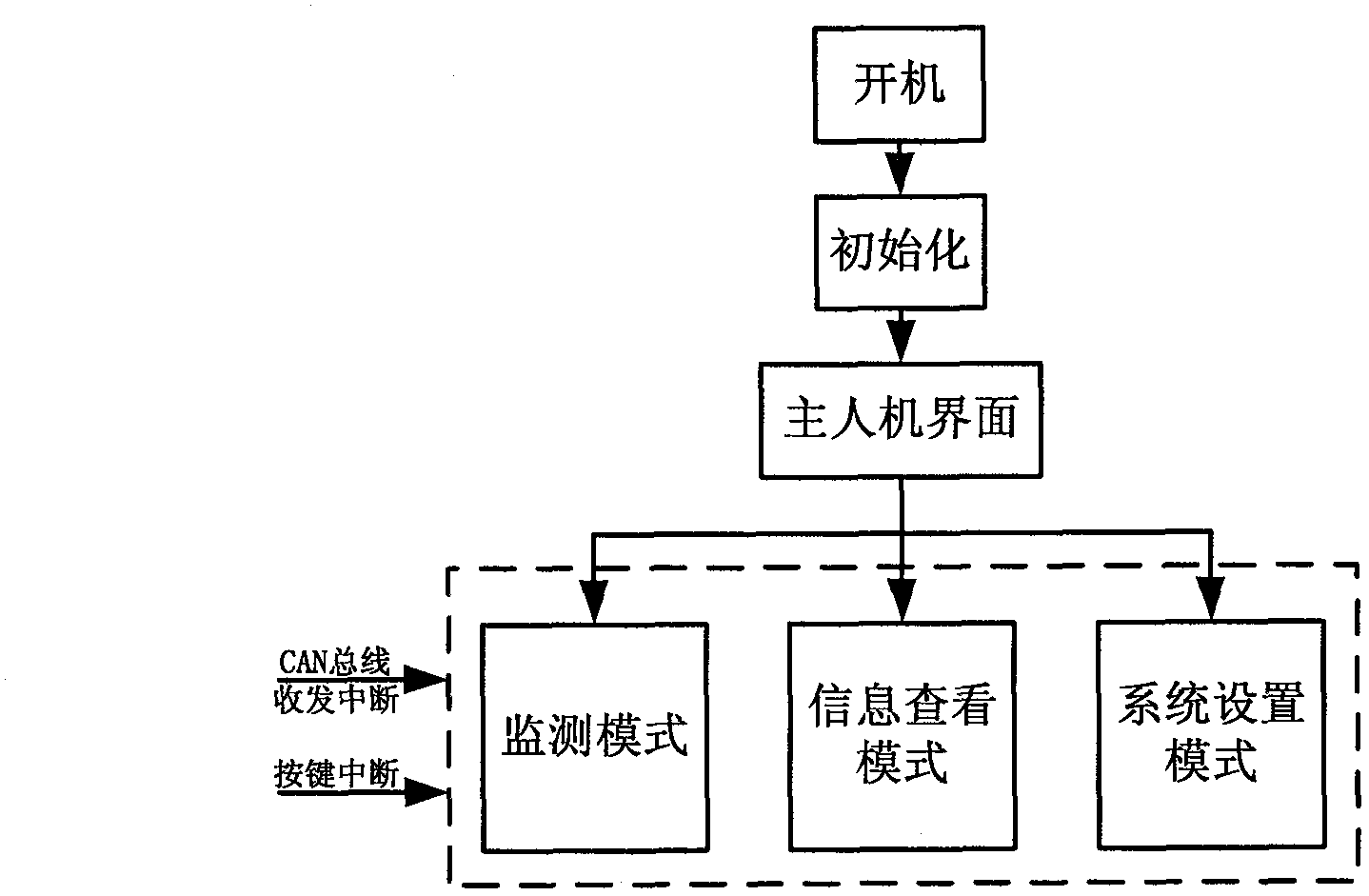
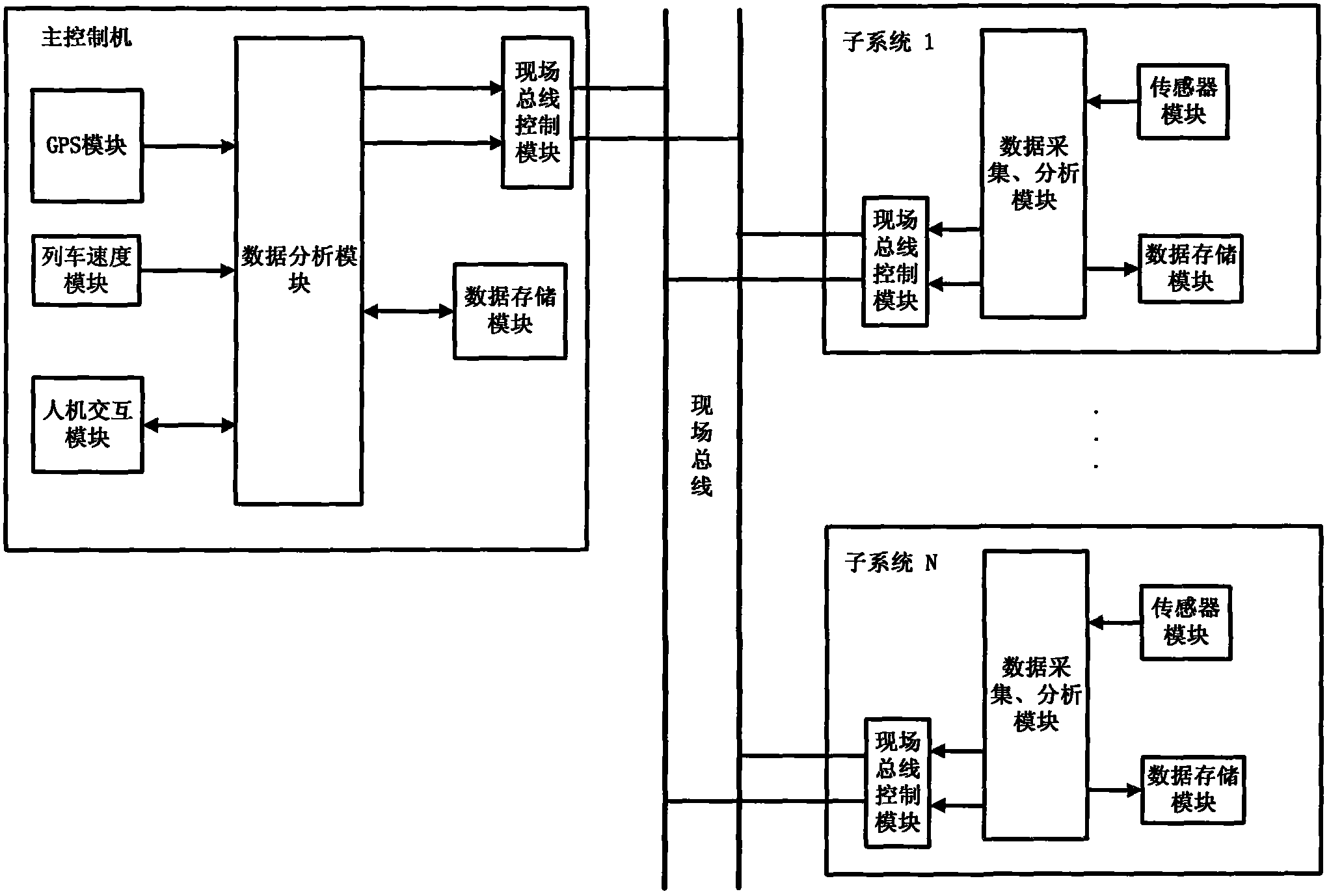
The invention relates to a device for detecting snaking motion instability of a high speed train bogie, which is used for monitoring on-line whether snaking motion instability of the bogie appears during the travel of a high speed train. The device provided by the invention comprises a main controller system and a sub-detection system. The main controller system mainly comprises a man-machine interaction module, a GPS (global position system) module, a data analysis record module and a field bus control module. The sub-detection system mainly comprises a sensor module, a data acquisition module, a data analysis module, a field bus control module and a data storage module. A main controller and the sub-detection system are subjected to data communication through a field bus. The sub-detection system monitors the transverse vibration state of the bogie in real time to judge whether the snaking motion instability appears and transmits instability information to the main controller through a field bus; and the main controller completes analysis of the instability information, combines with the GPS module and a clock module to correctly provide time and space synchronizing information at the moment of the occurrence of instability, then gives out a warning signal and stores the fault information.
Owner:SOUTHWEST JIAOTONG UNIV
Defect analyzing device for semiconductor integrated circuits, system therefor, and detection method
InactiveUS20060164115A1Accurate identificationImprove efficiencySemiconductor/solid-state device testing/measurementIndividual semiconductor device testingElectricityEngineering
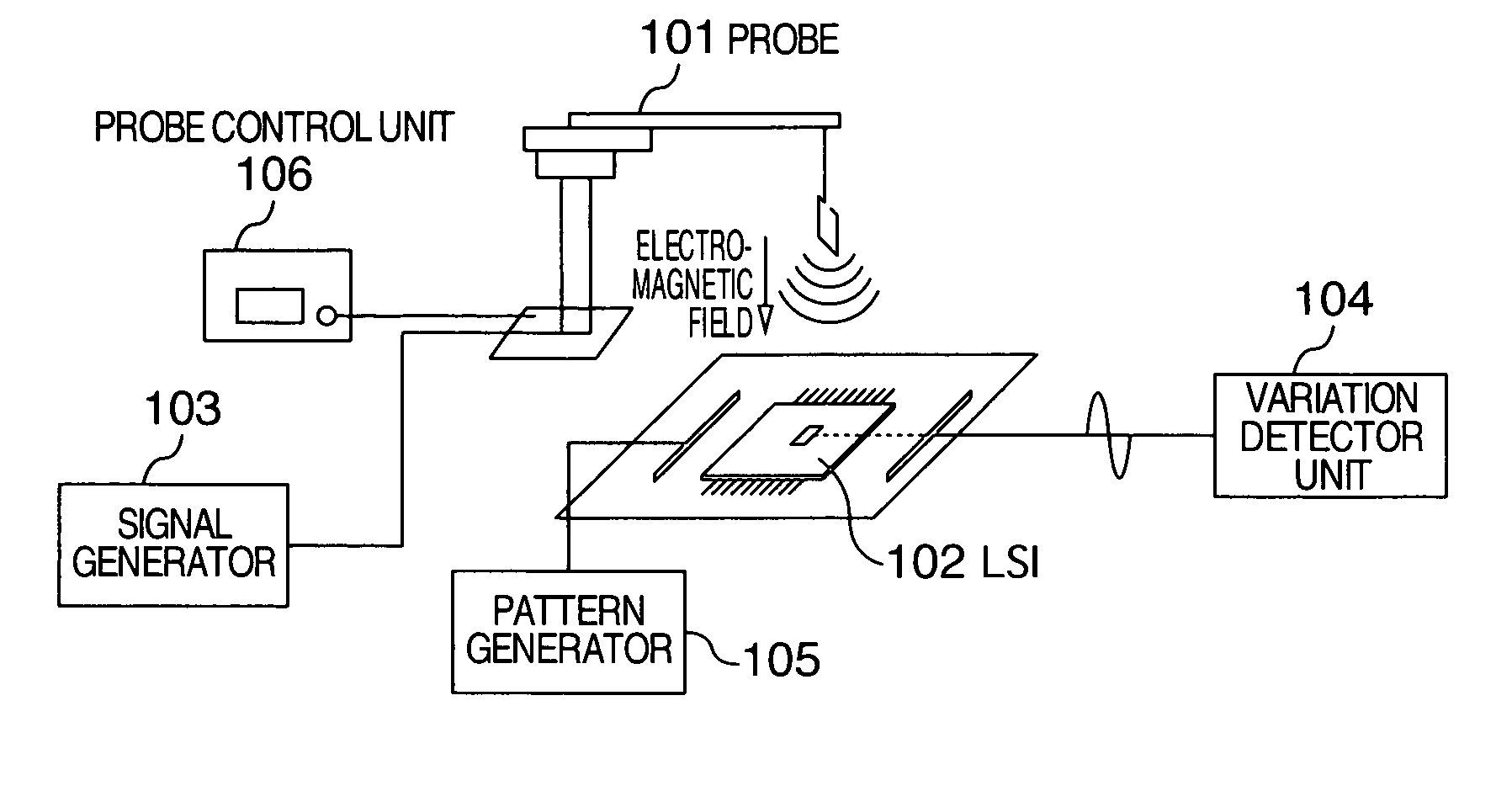
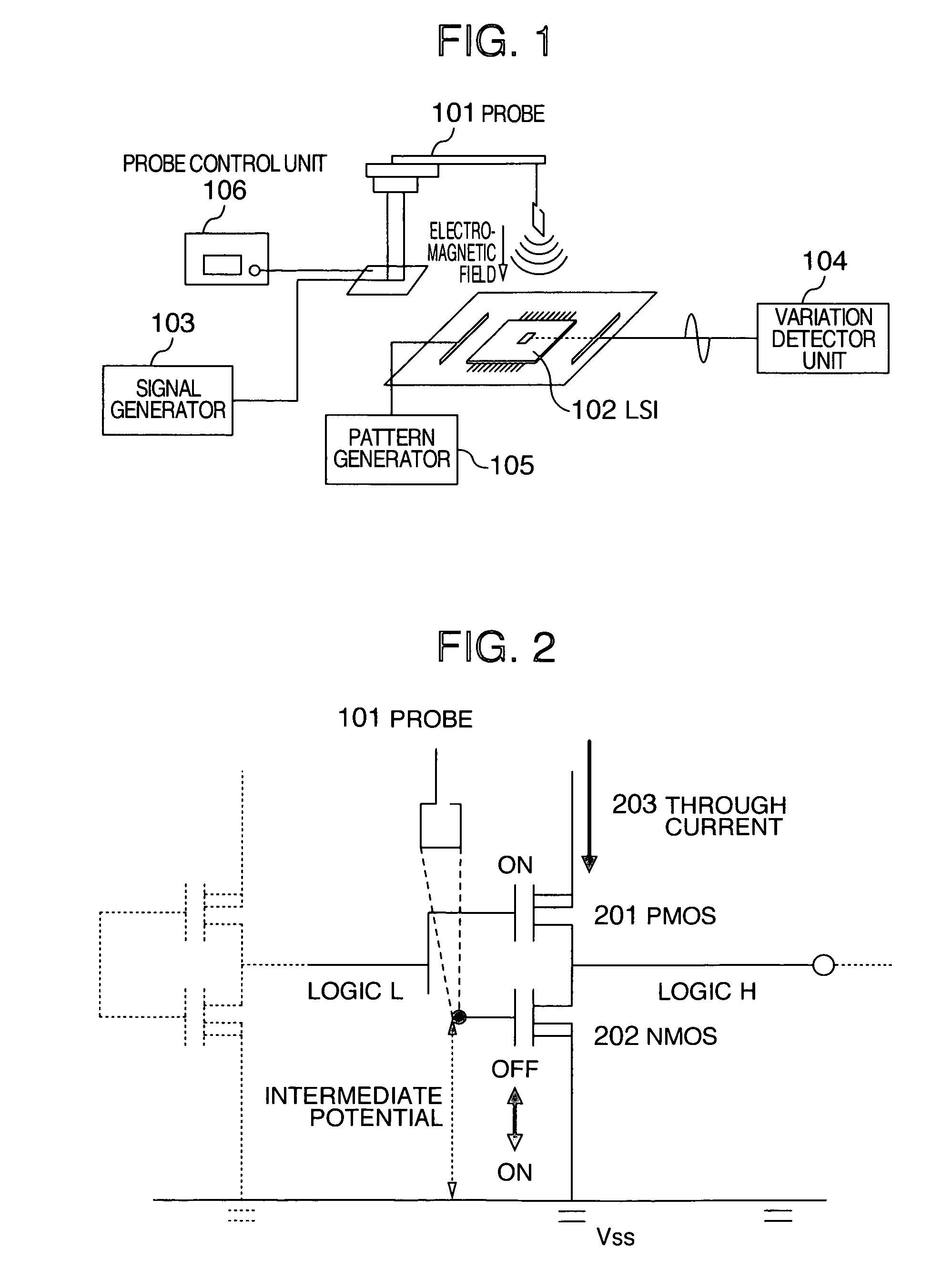
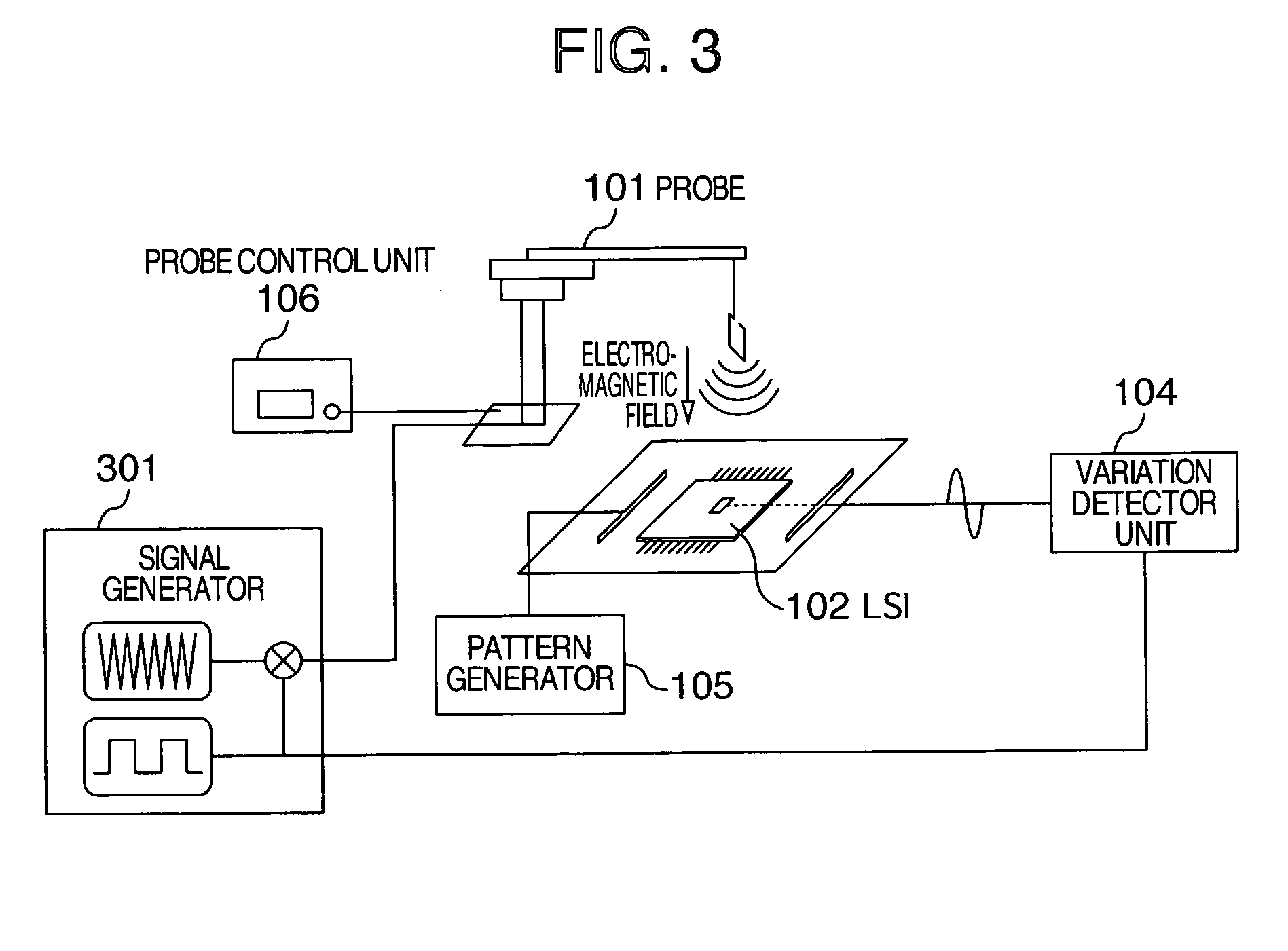
The present invention aims at performing a semiconductor integrated circuit defect analysis with a simplified analysis apparatus and simplifying a defect analysis work. A defect analysis apparatus for a semiconductor integrated circuit is characterized in that a presence / absence of a defect is detected by irradiating an electromagnetic field from a probe to the semiconductor integrated circuit and detecting an electric characteristic variation such as a power supply current variation in the semiconductor integrated circuit.
Owner:HITACHI LTD
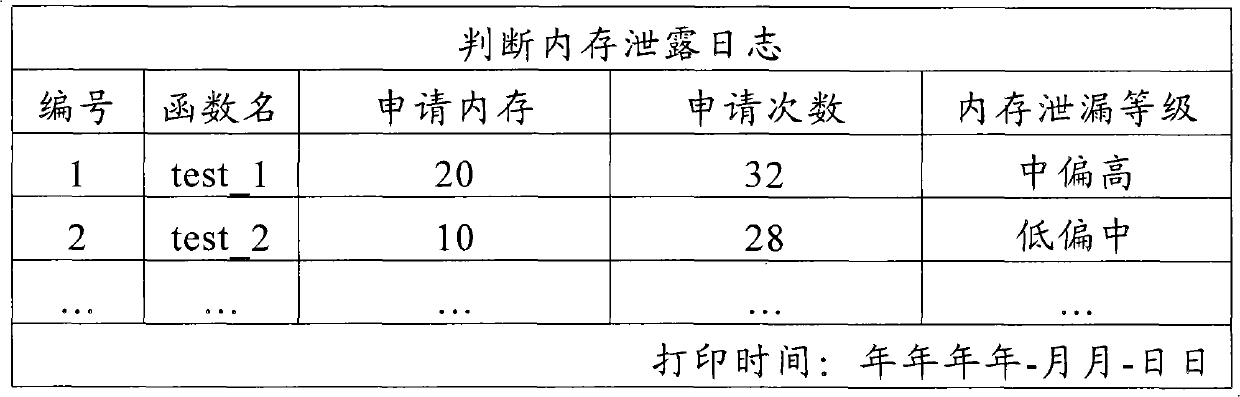
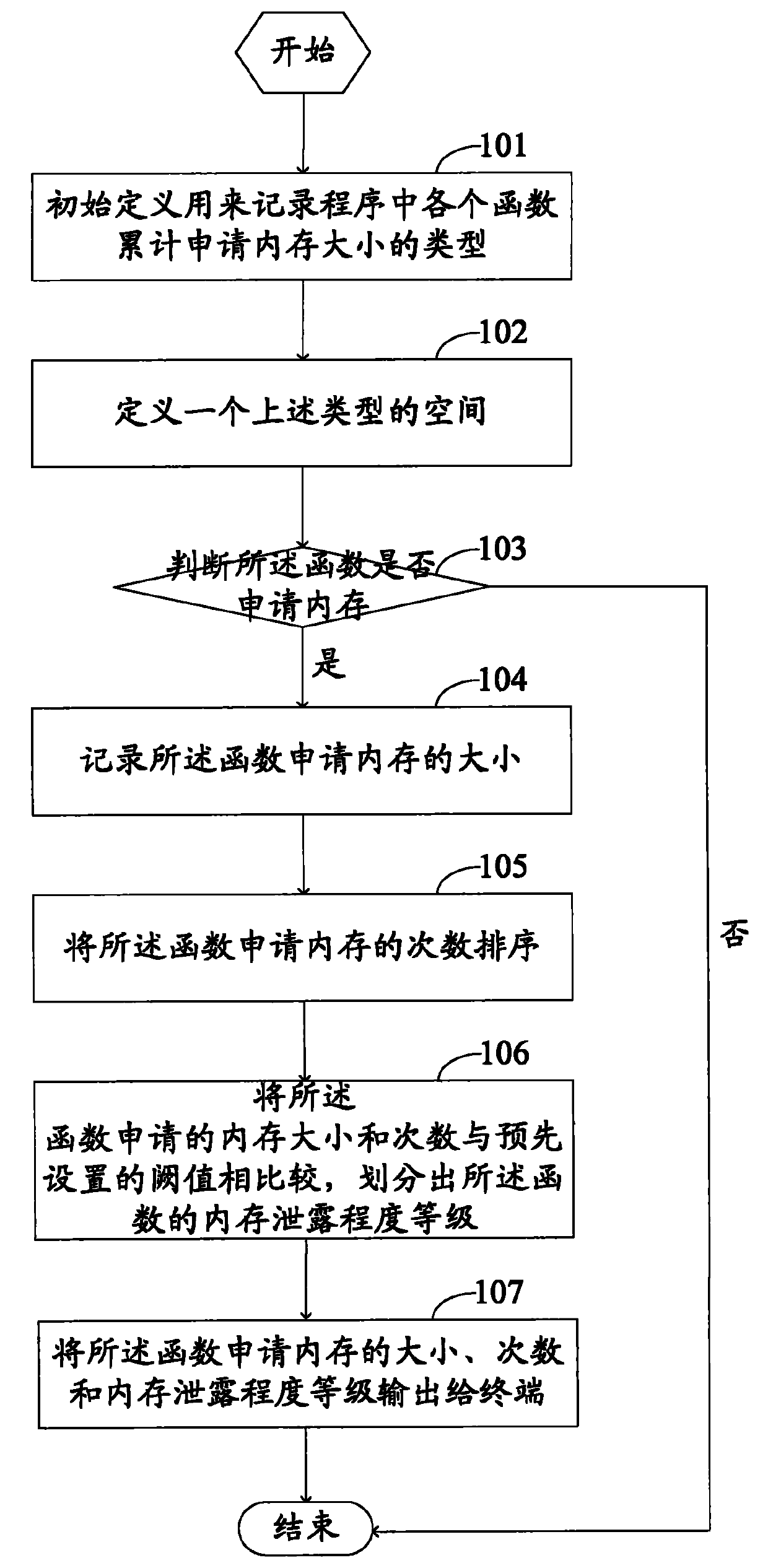
System and method for judging memory leak
The invention provides a method for judging memory leak, comprising the following steps of: when a function application memory is judged aiming at each function in a program, accumulating the memory capacity and the application times of the named function application; when a function release memory is judged, reducing the released memory capacity from the memory capacity of the named function accumulated application and reducing release memory times from accumulated application times; sequencing the memory capacity and the times of the function application in different names in a descending mode by using the memory capacity as priority; ensuring and outputting a level of a memory leak degree according to the memory capacity and the times of the function accumulated application in different names; in addition, the invention provides a system for realizing the method in order to sequence memory distribution and information release according to the memory application times and liberate a programmer from large fussy analytical work.
Owner:BEIJING HAITAI FANGYUAN HIGH TECH
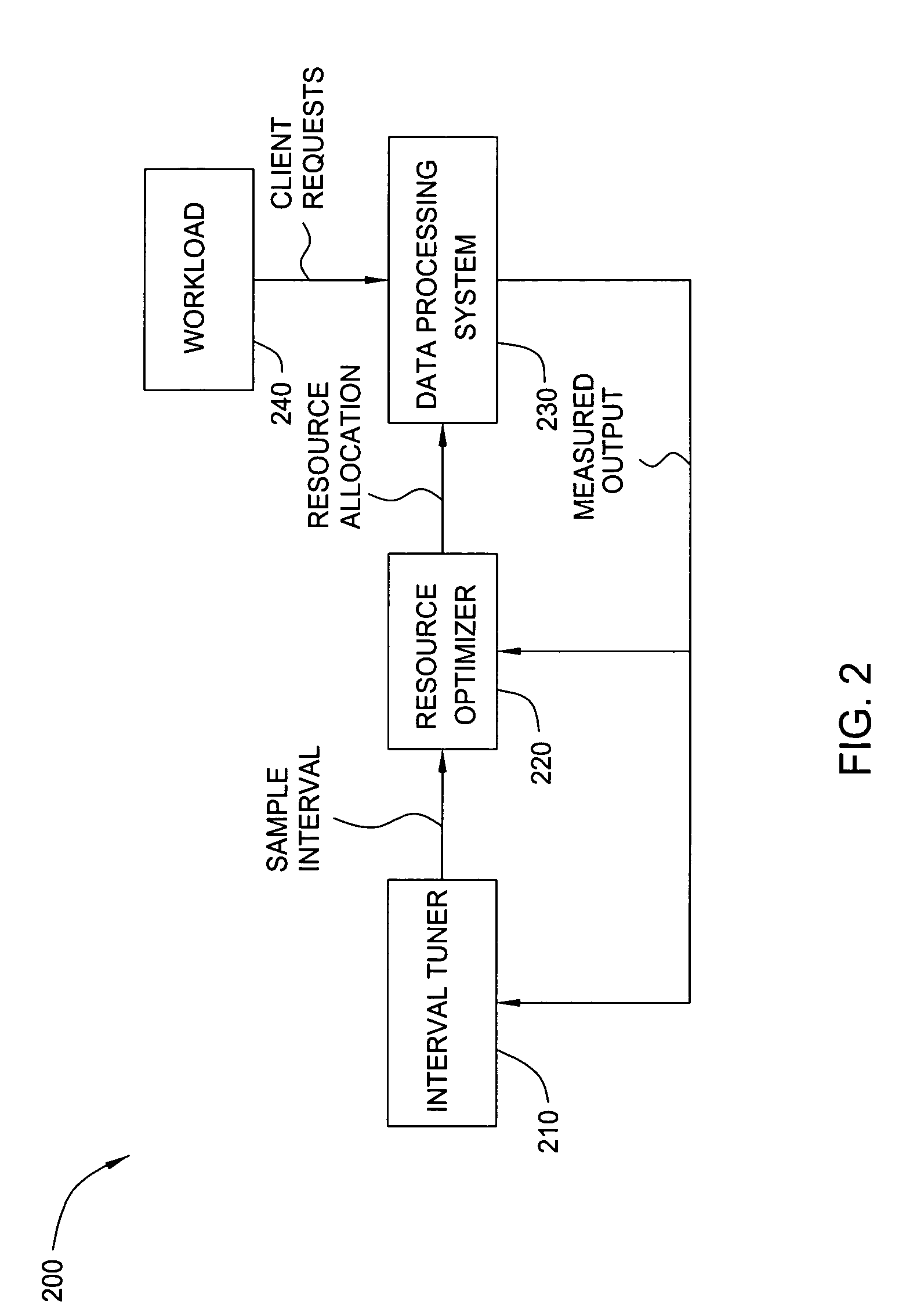
Method and apparatus for online sample interval determination
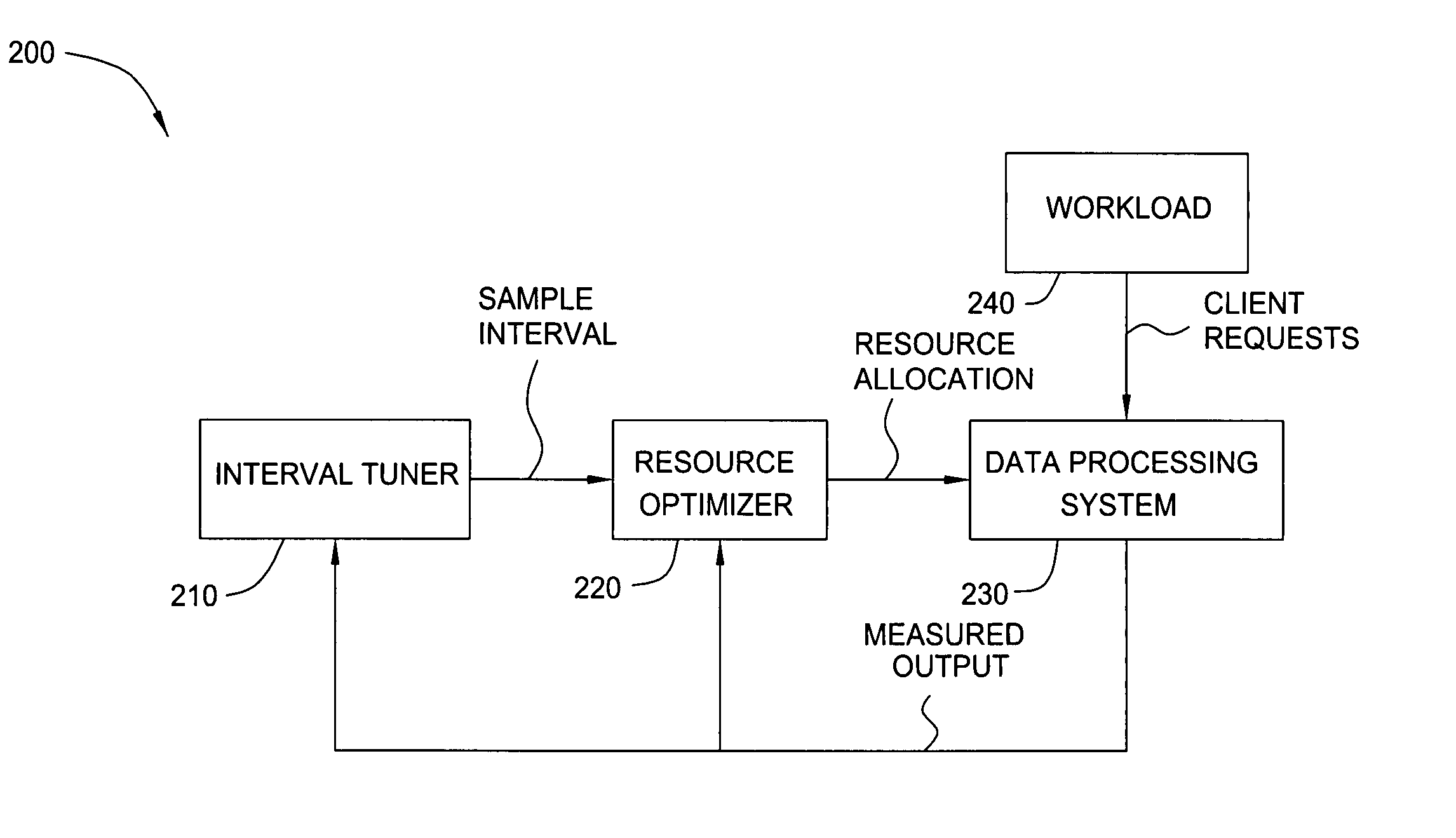
InactiveUS20050278381A1Less sensitive to system noiseEasy to manageError detection/correctionProgram controlAnalysis workingWorkload
In one embodiment, functional system elements are added to an autonomic manager to enable automatic online sample interval selection. In another embodiment, a method for determining the sample interval by continually characterizing the system workload behavior includes monitoring the system data and analyzing the degree to which the workload is stationary. This makes the online optimization method less sensitive to system noise and capable of being adapted to handle different workloads. The effectiveness of the autonomic optimizer is thereby improved, making it easier to manage a wide range of systems.
Owner:GLOBALFOUNDRIES INC
Electric-gas-heat interconnection system risk evaluation method for considering solar thermal CHP plants and electric boiler
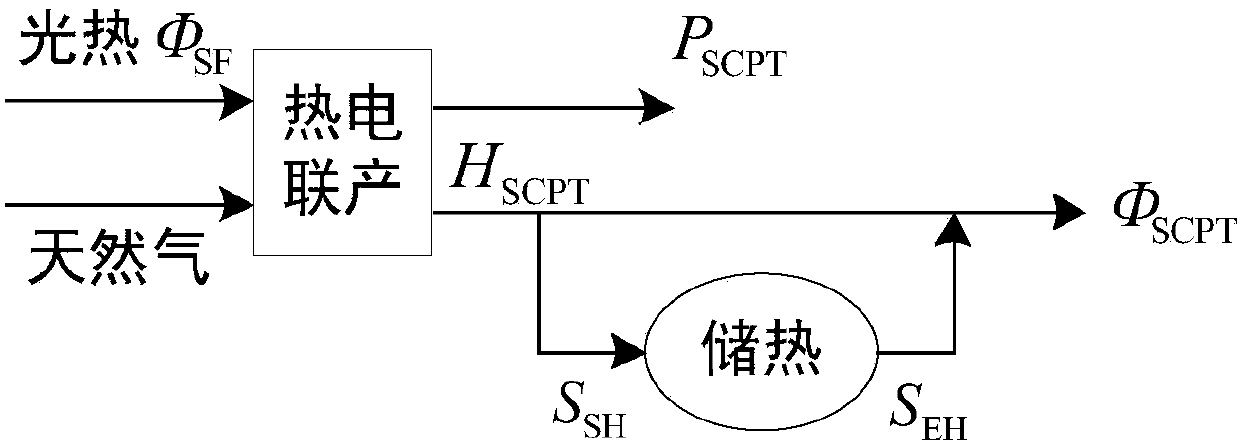
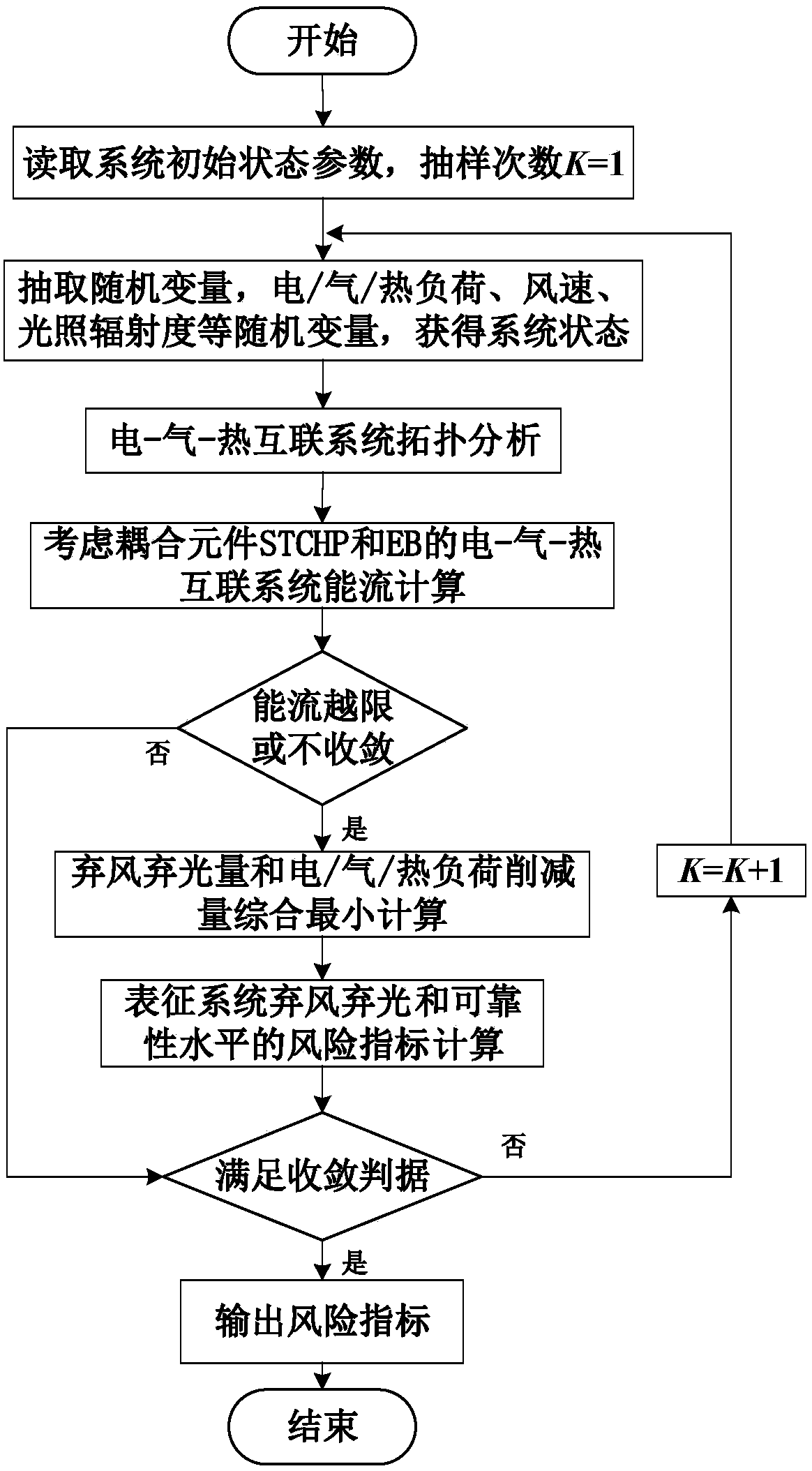
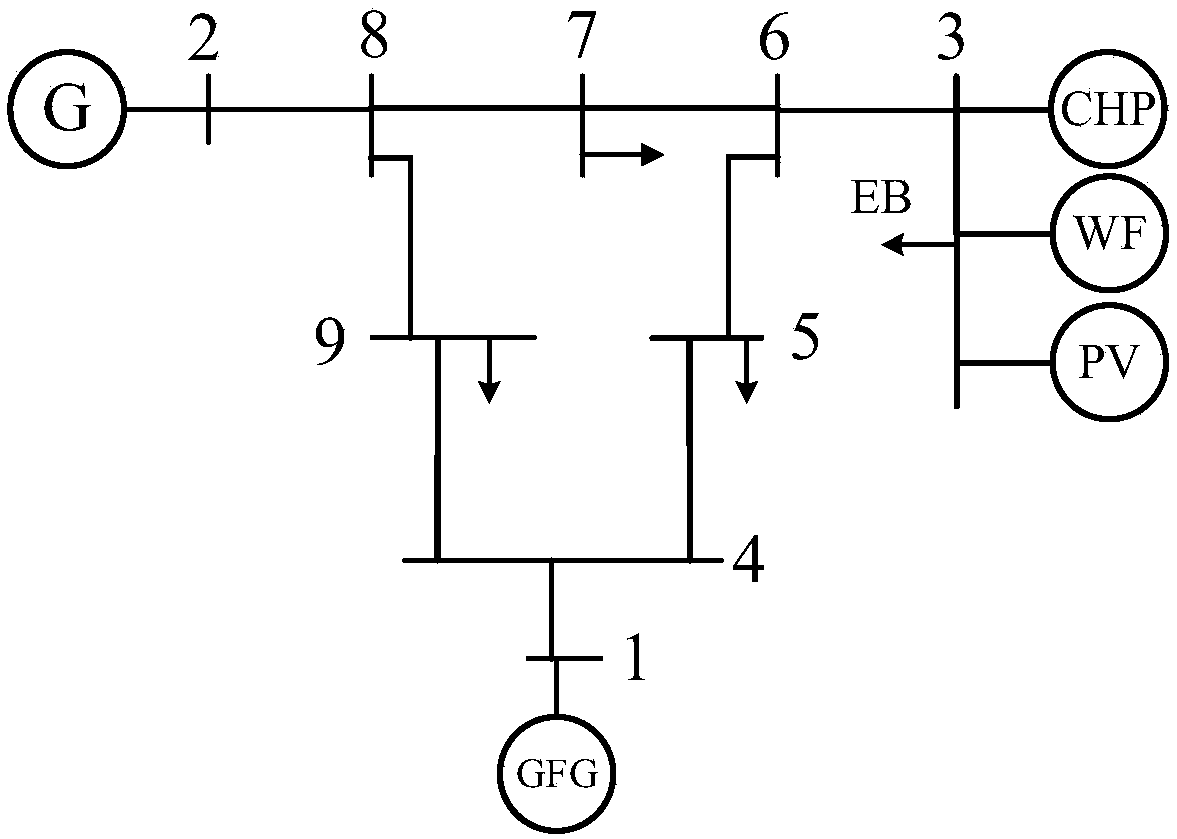
ActiveCN107730129APreserve actual operating characteristicsReasonable quantification of the severity of wind and solar curtailmentDesign optimisation/simulationResourcesCogenerationEngineering
The invention discloses an electric-gas-heat interconnection system risk evaluation method for considering solar thermal CHP plants (STCHP) and an electric boiler (EB). The method comprises steps of establishing an energy flow model based on a coupling element STCHP and EB, and a wind and light abandoning and electric / gas / heat load reduction composite minimal optimization model; establishing a system level risk index of electric power / gas quantity / heating power insufficient expectations and wind abandoning / light abandoning expectations of the electric-gas-heat interconnection system; based onthe established energy flow model, the established load reduction model and the evaluation index, further considering various random factors of element faults, electric / gas / heat load, wind electricitypower and photoelectric power and providing a step and schedule graph about electric-gas-heat interconnection system risk evaluation for considering the STCHP and the EB; and finally, achieving calculation and analysis work of the electric-gas-heat interconnection system risk evaluation for considering the STCHP and the EB on an MATLAB platform through programs.
Owner:CHONGQING UNIV
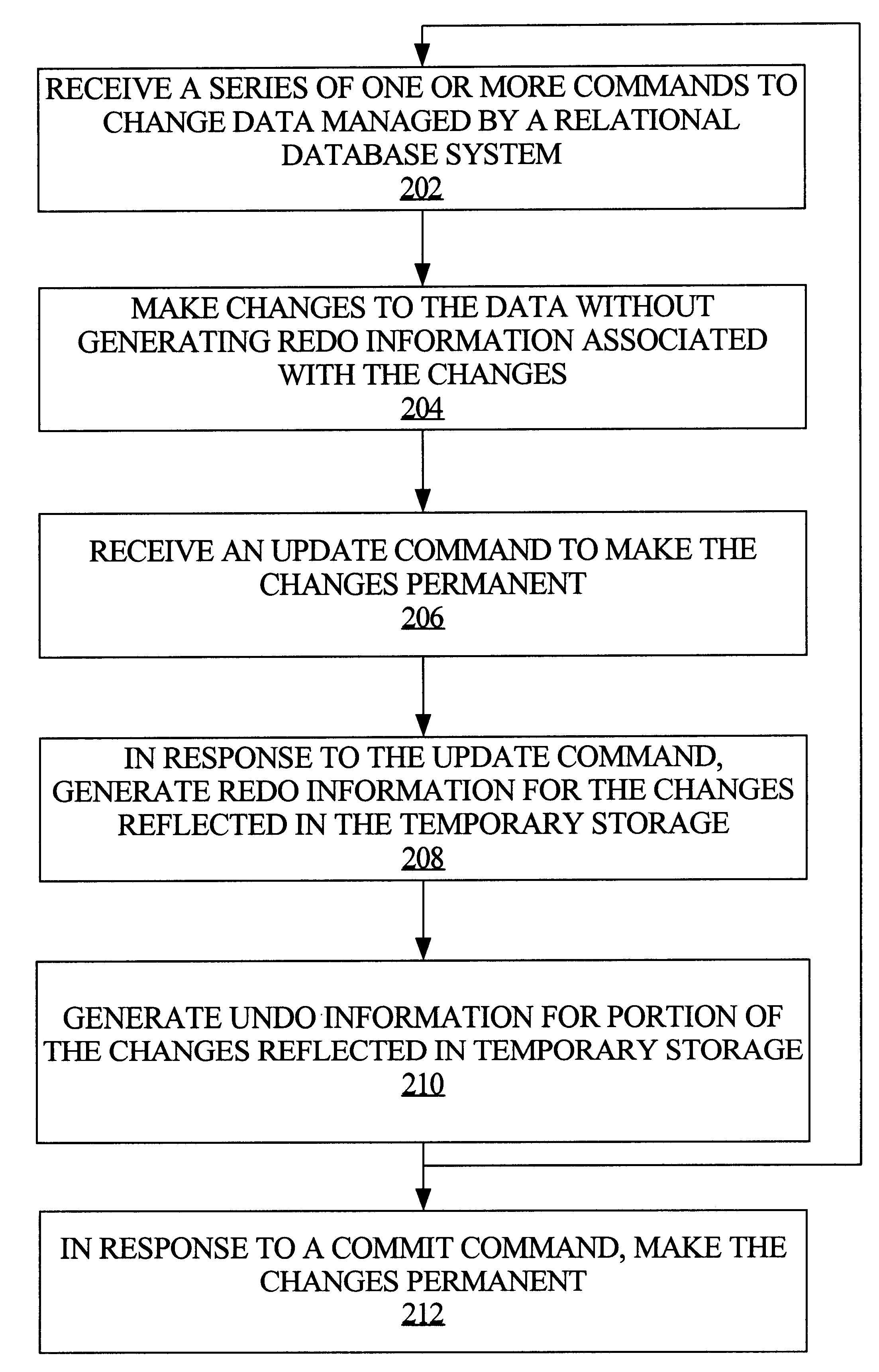
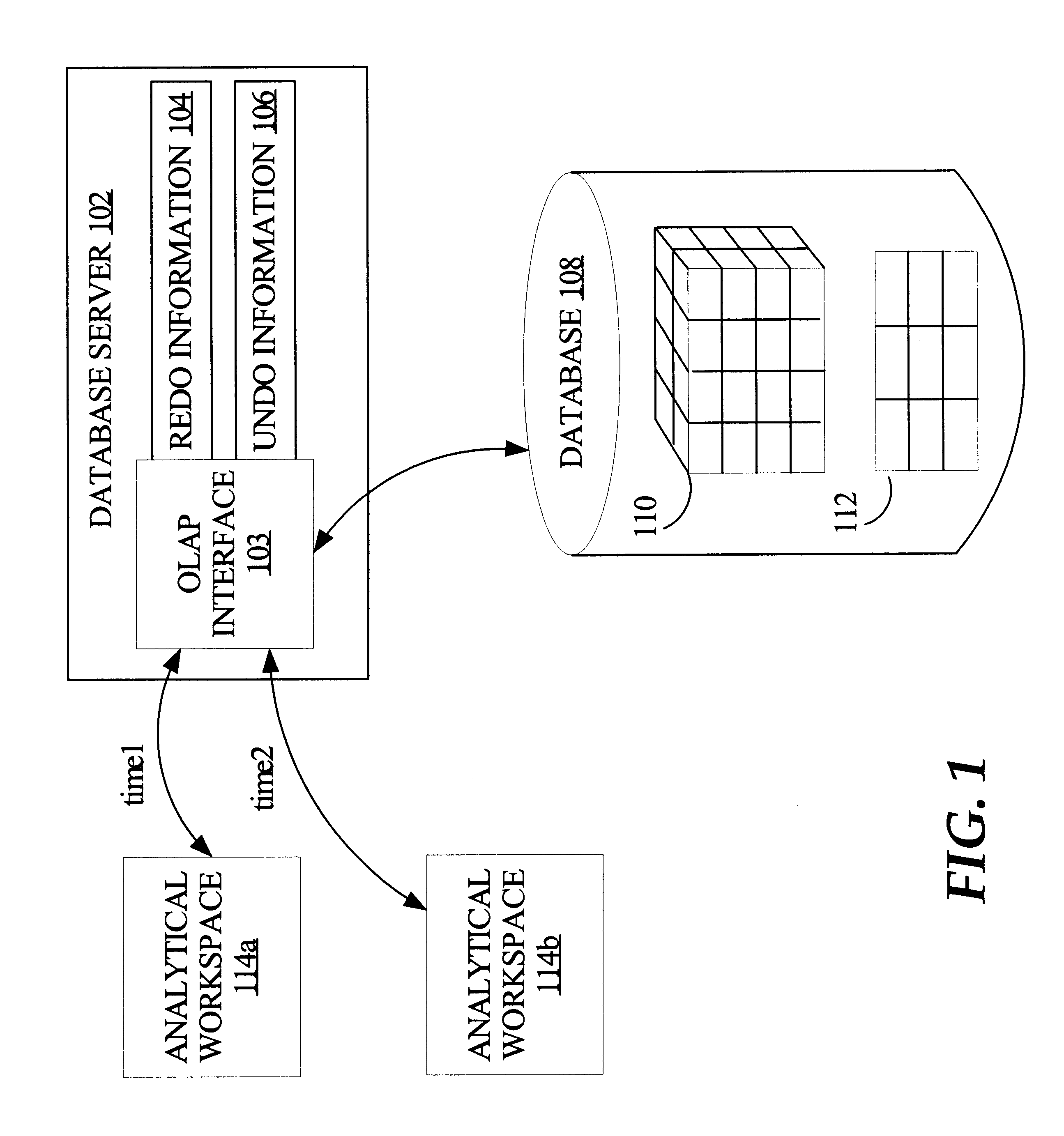
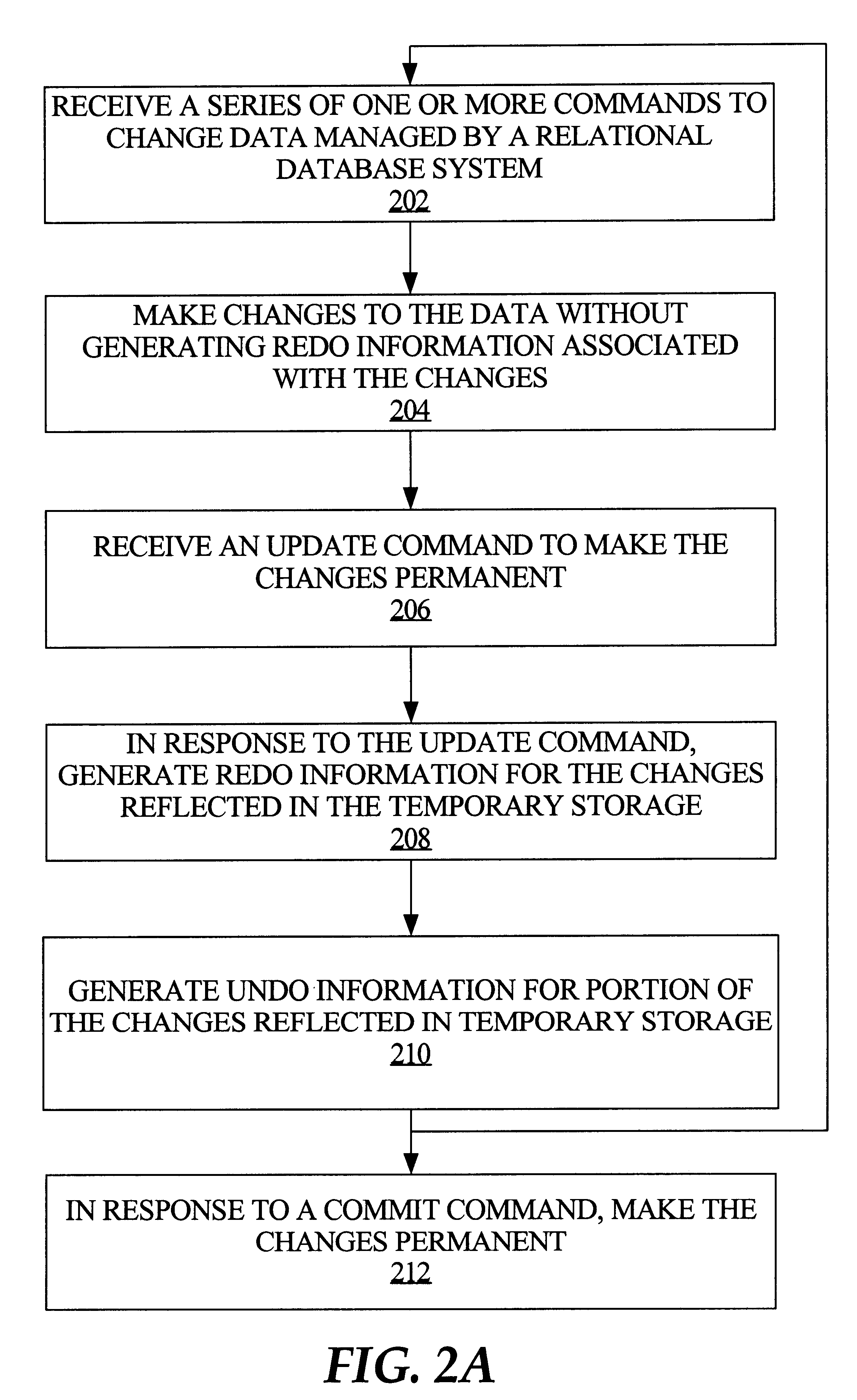
Techniques for managing what-if analysis of data managed by a relational database system
An analytical workspace includes a set of data on which what-if analysis is performed, which is stored persistently and managed in a relational database system. The data may be stored as a binary large object in relational tables, and may comprise a portion of a multidimensional cube. A series of commands on the analytical workspace is received by a database server. In response to the commands, changes are made to the data in temporary storage. Redo information is not generated at this time in association with such changes. Hence, these changes are not made permanent at this time. At some point, the server may receive an update command to make the changes permanent. In response to the update command, redo information is generated for the changes reflected in the temporary storage and the changes are made permanent, in accordance with relational database properties.
Owner:ORACLE INT CORP
Intelligent scheduler for multi-level exhaustive scheduling
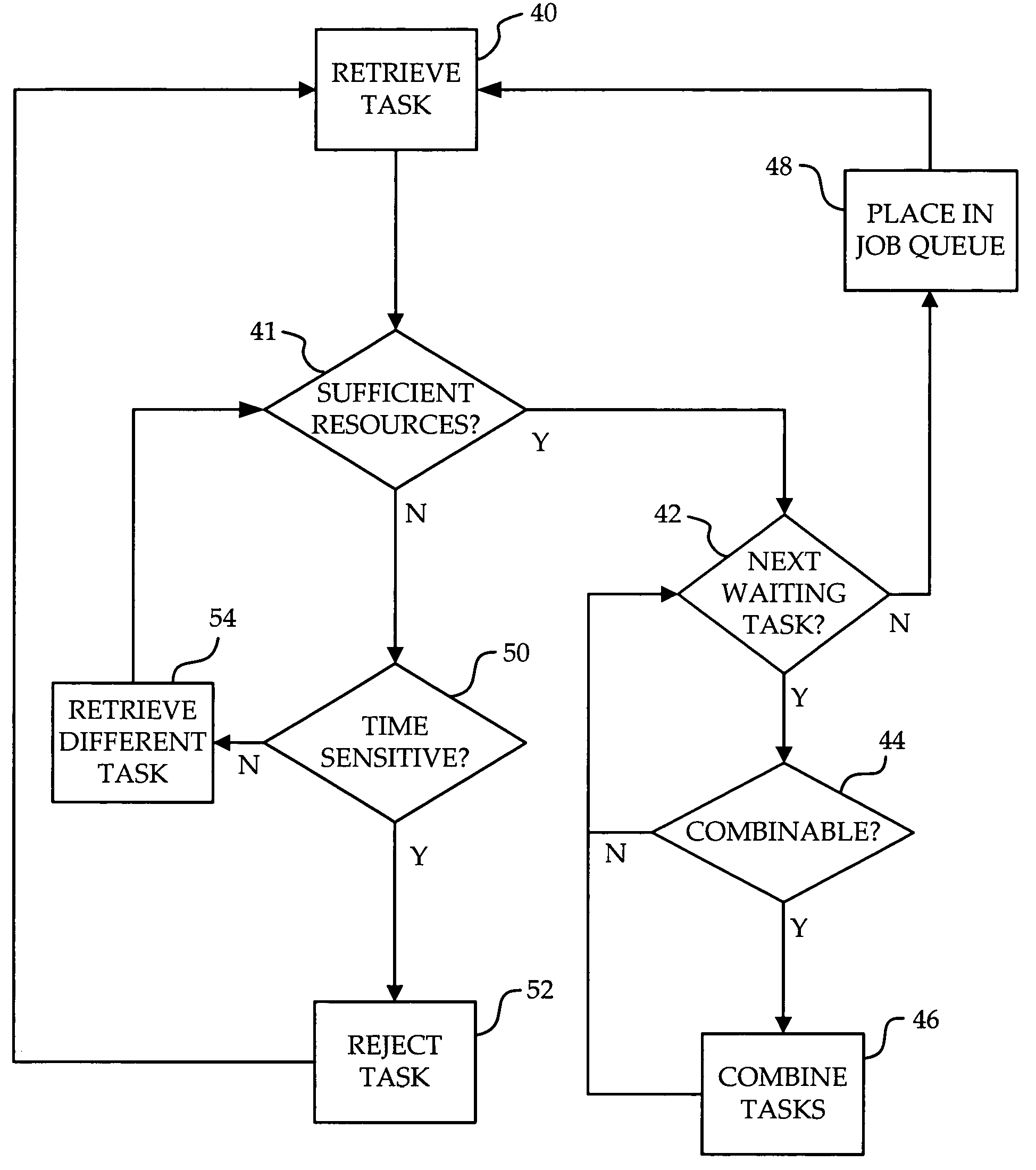
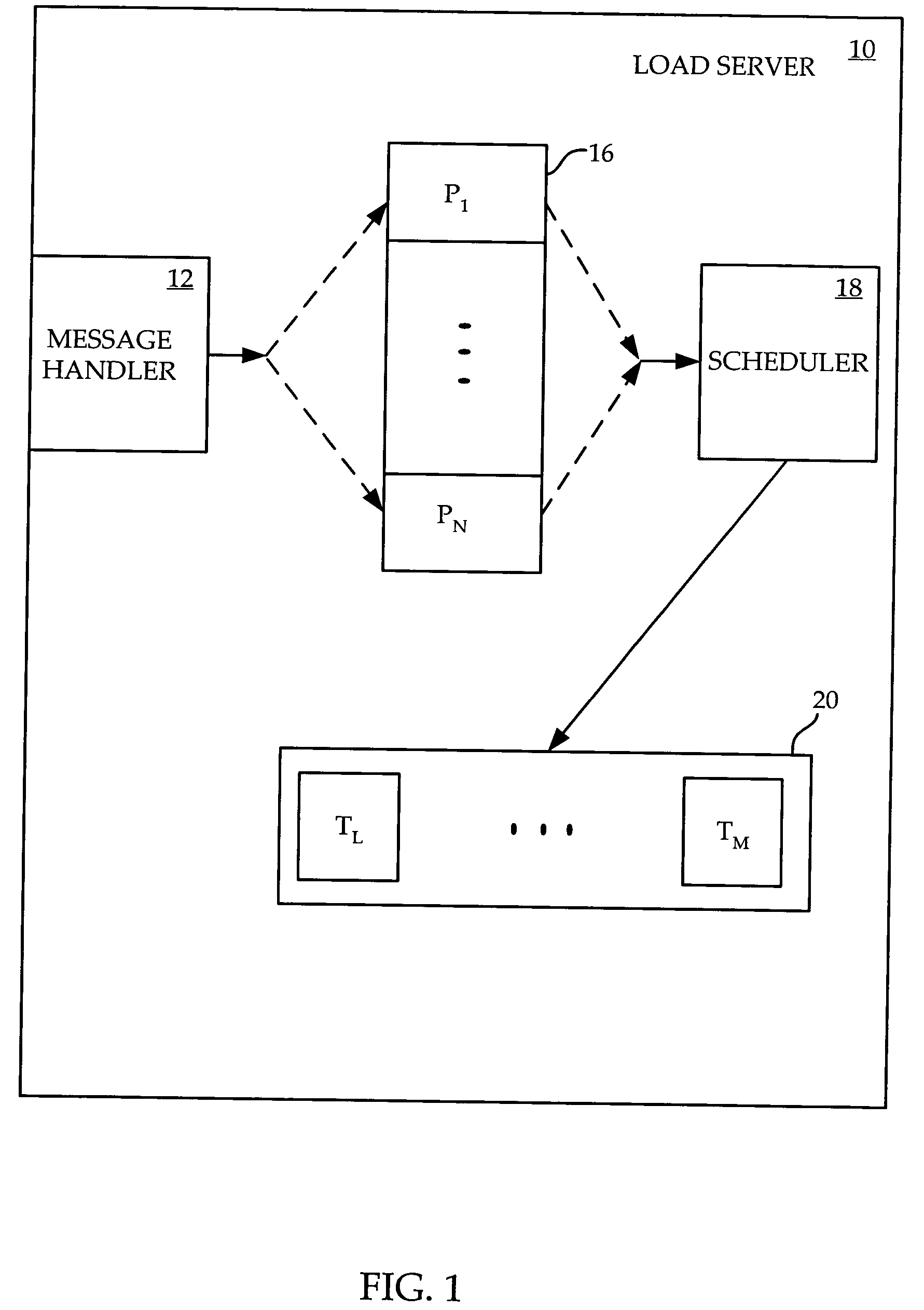
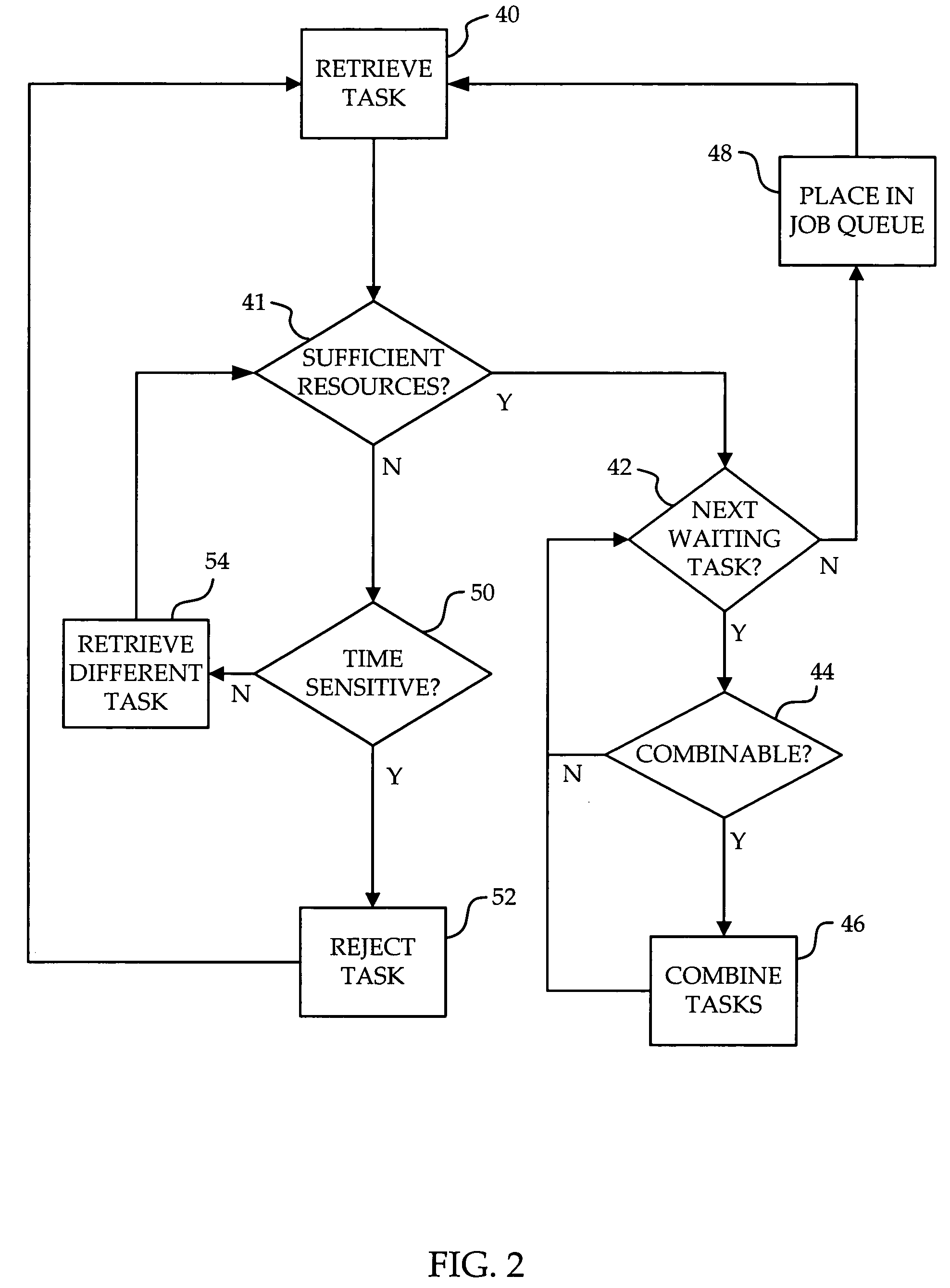
InactiveUS20050097556A1Reduced resourceTasks to be executed more efficientlyProgram initiation/switchingMemory systemsAnalysis workingLow resource
A method and apparatus are provided for scheduling tasks within a computing device such as a communication switch. When a task is to be scheduled, other tasks in the work queue are analyzed to see if any can be executed simultaneously with the task to be scheduled. If so, the two tasks are combined to form a combined task, and the combined task is placed within the job queue. In addition, if the computing device has insufficient resources to execute the task to be scheduled, the task is placed back into the work queue for future scheduling. This is done in a way which avoids immediate reselection of the task for scheduling. Task processing efficiency is increased, since combining tasks reduces the waiting time for lower priority tasks, and tasks for which there are insufficient resources are delayed only a short while before a new scheduling attempt, rather than rejecting the task altogether.
Owner:ALCATEL LUCENT SAS
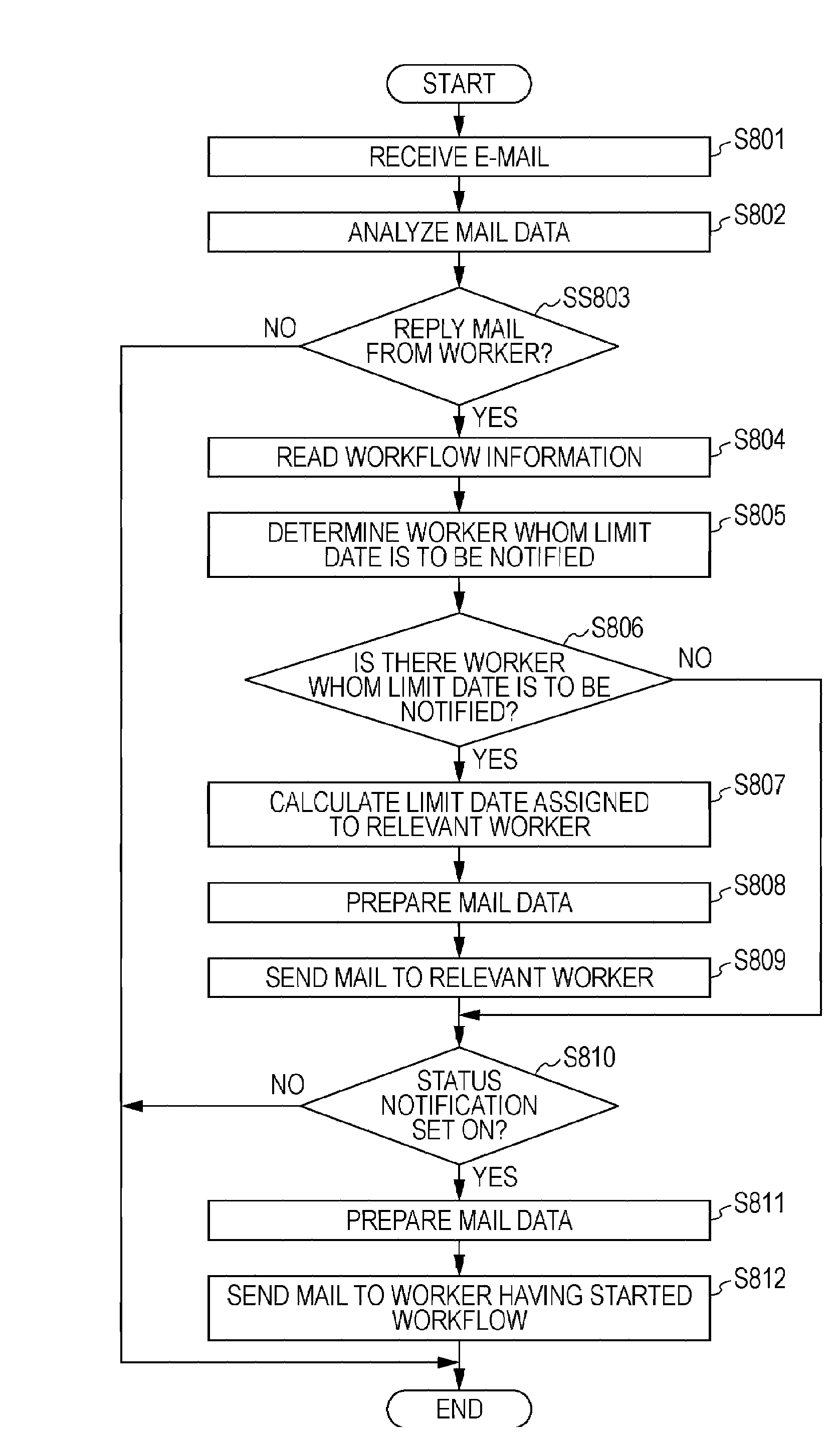
Workflow management method using an image forming apparatus
An image forming apparatus determines whether workflow information is included in a received print request. When the workflow information is included in the received print request, the image forming apparatus analyzes the workflow information and calculates a limit date / time to be notified to workers taking charge of respective steps of a workflow. The image forming apparatus prepares E-mail data including information that indicates the limit date / time. The image forming apparatus sends the prepared E-mail by referring to mail addresses of the workers taking charge of the respective steps of the workflow.
Owner:CANON KK
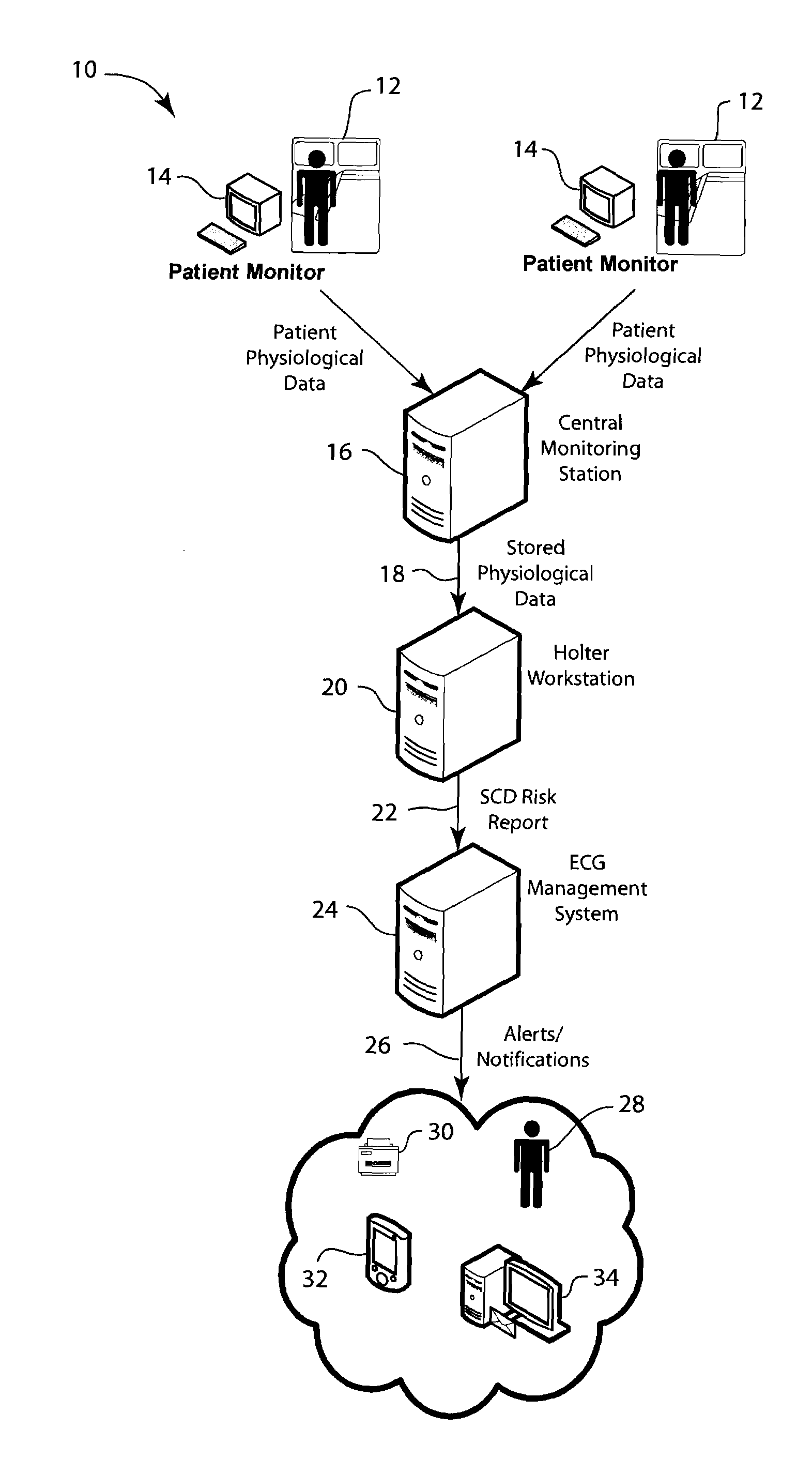
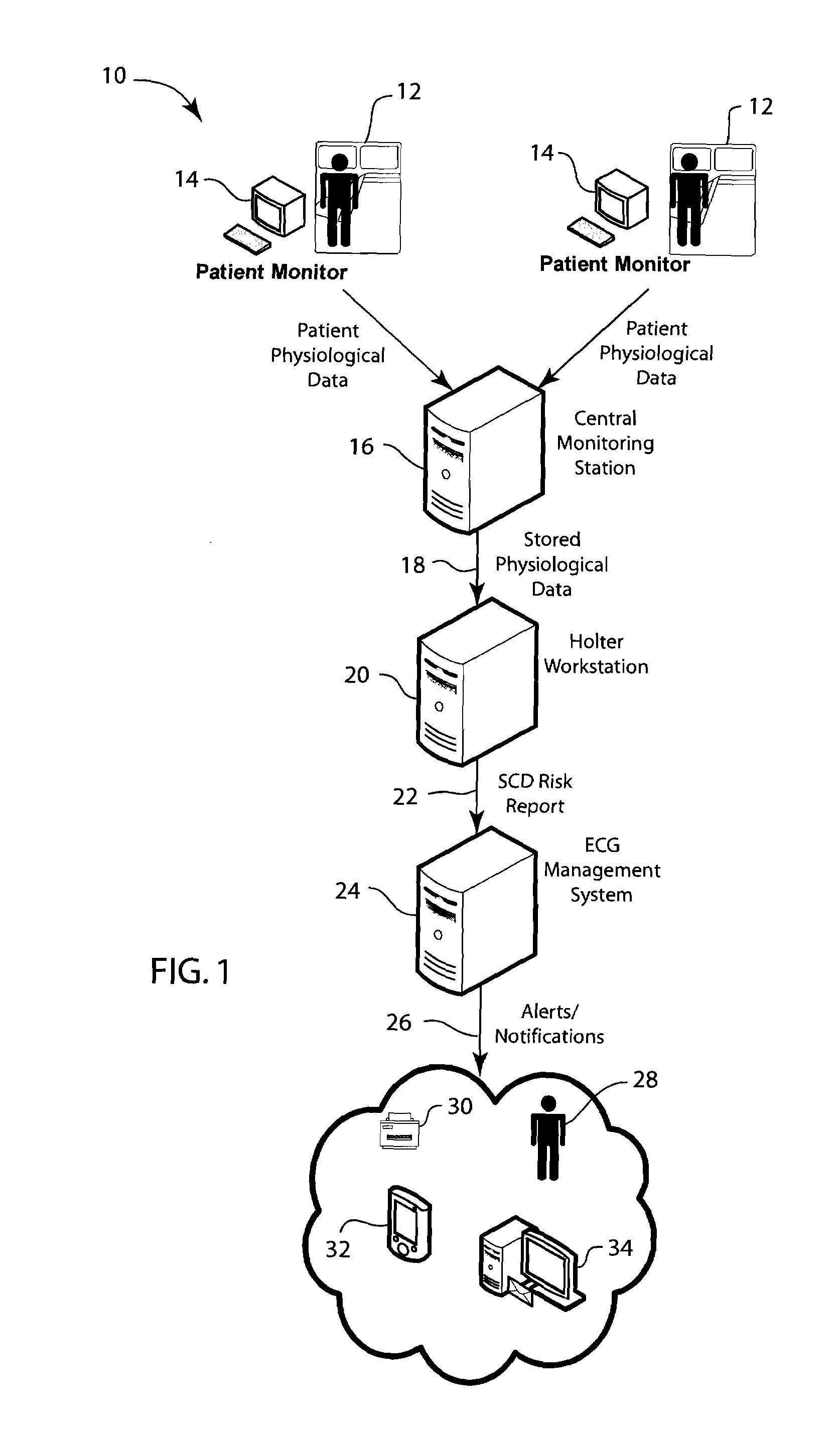
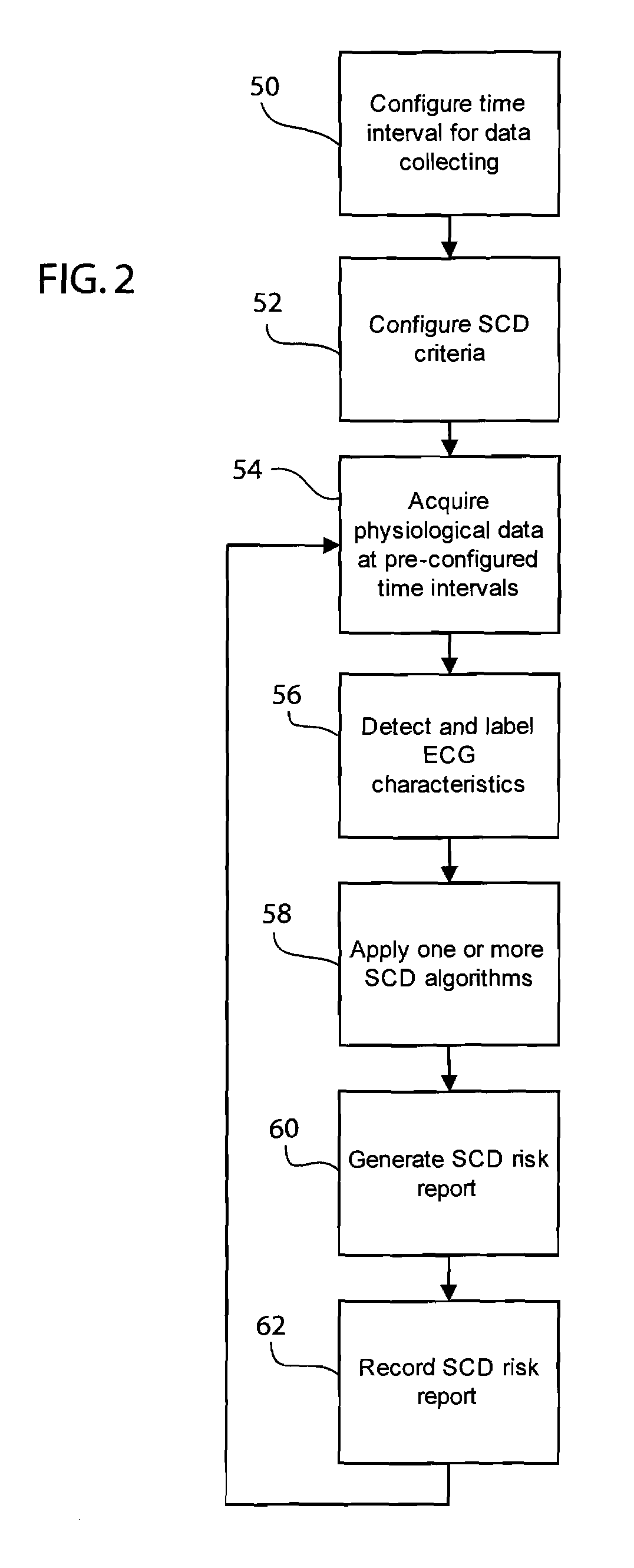
System, method and device for predicting sudden cardiac death risk
A system and method for predicting sudden cardiac death. The system includes a patient monitoring station, a Holter analysis workstation, and a hospital information network. The Holter analysis workstation being operative to apply a plurality of data analysis algorithms to create a sudden cardiac death report. The method applies a first data analysis technique and a second data analysis technique to electrocardiographic data to produce an indication of sudden cardiac death risk.
Owner:GENERAL ELECTRIC CO
NMR imaging equipment stability and method for measuring image-forming index
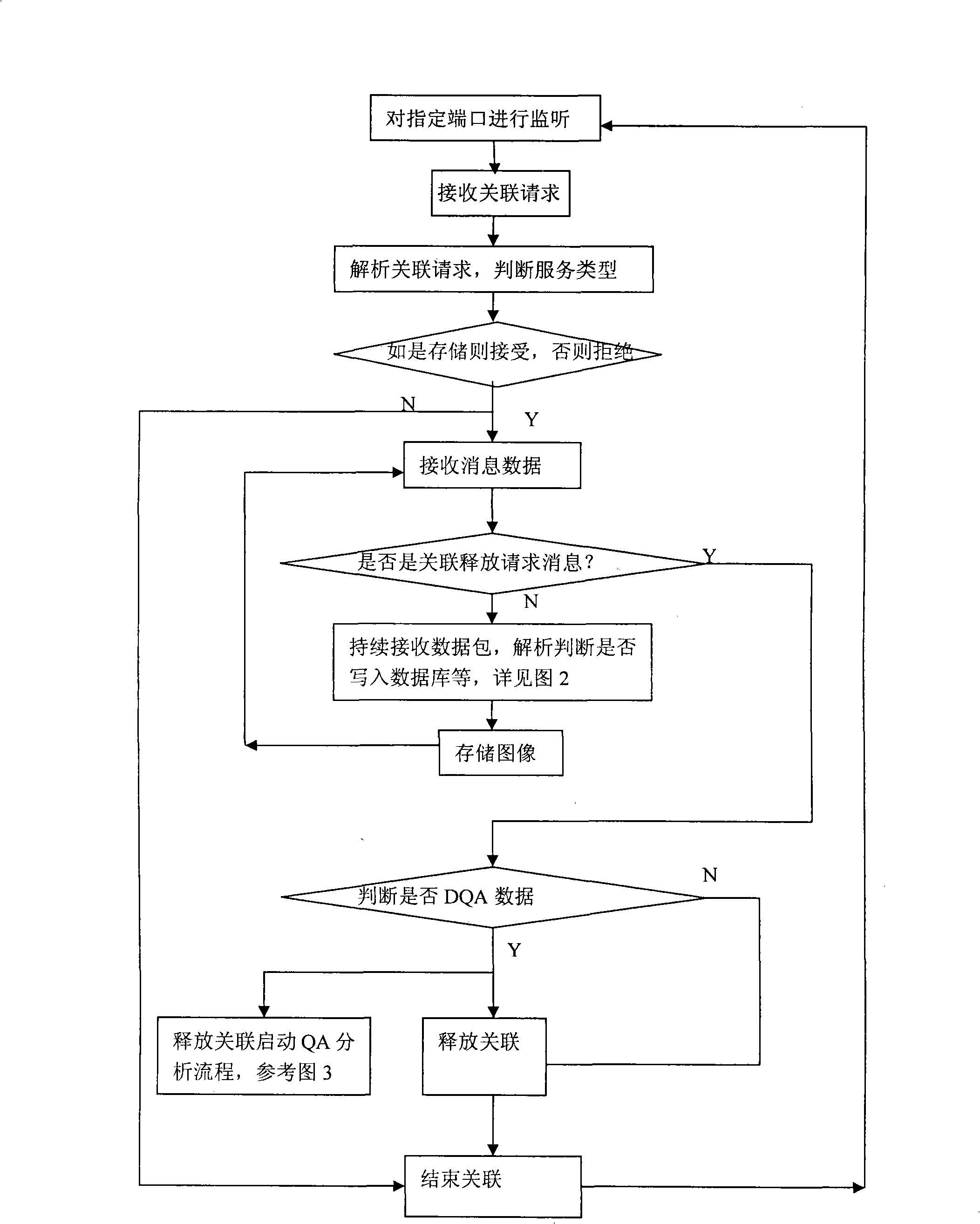
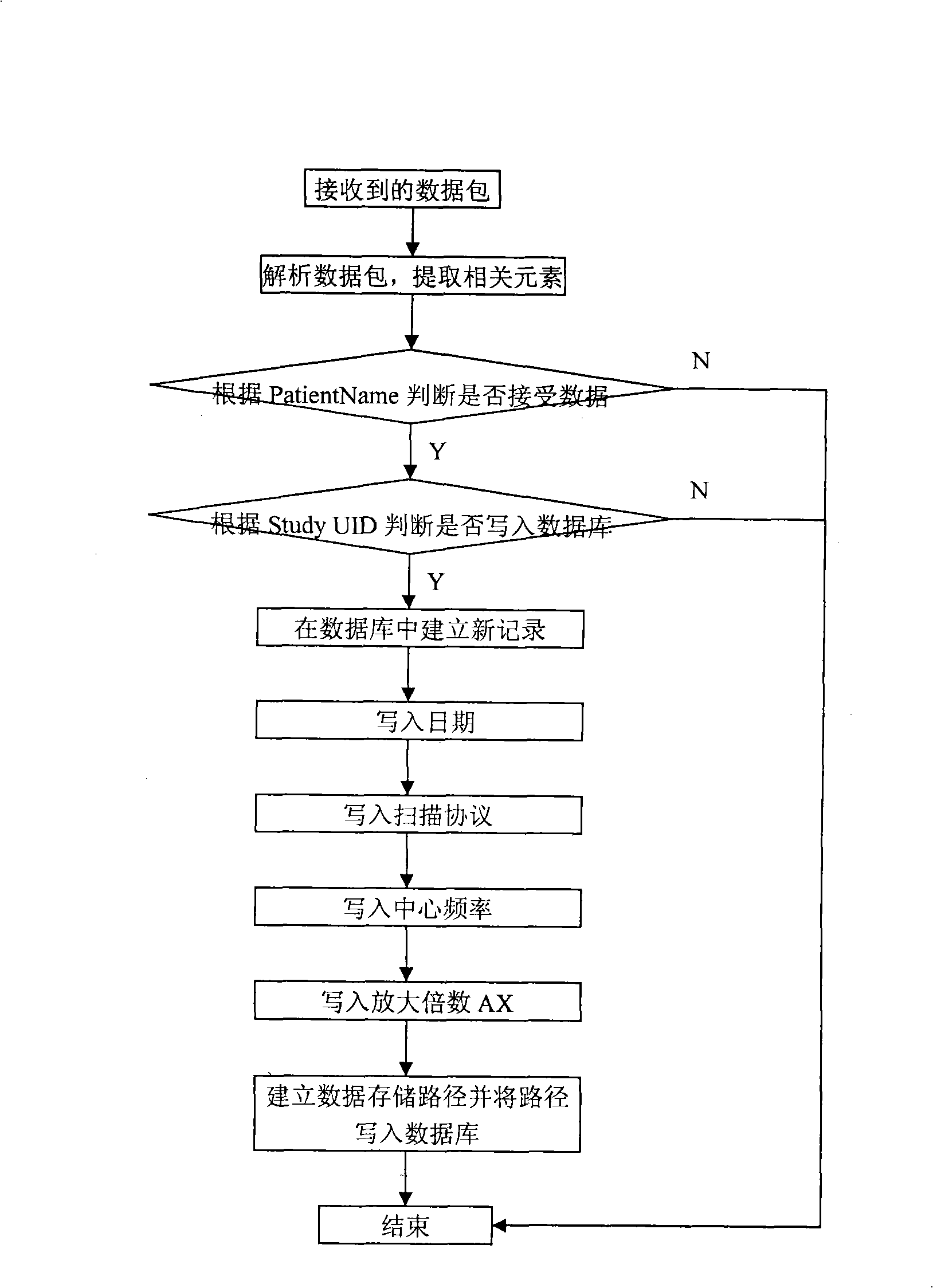
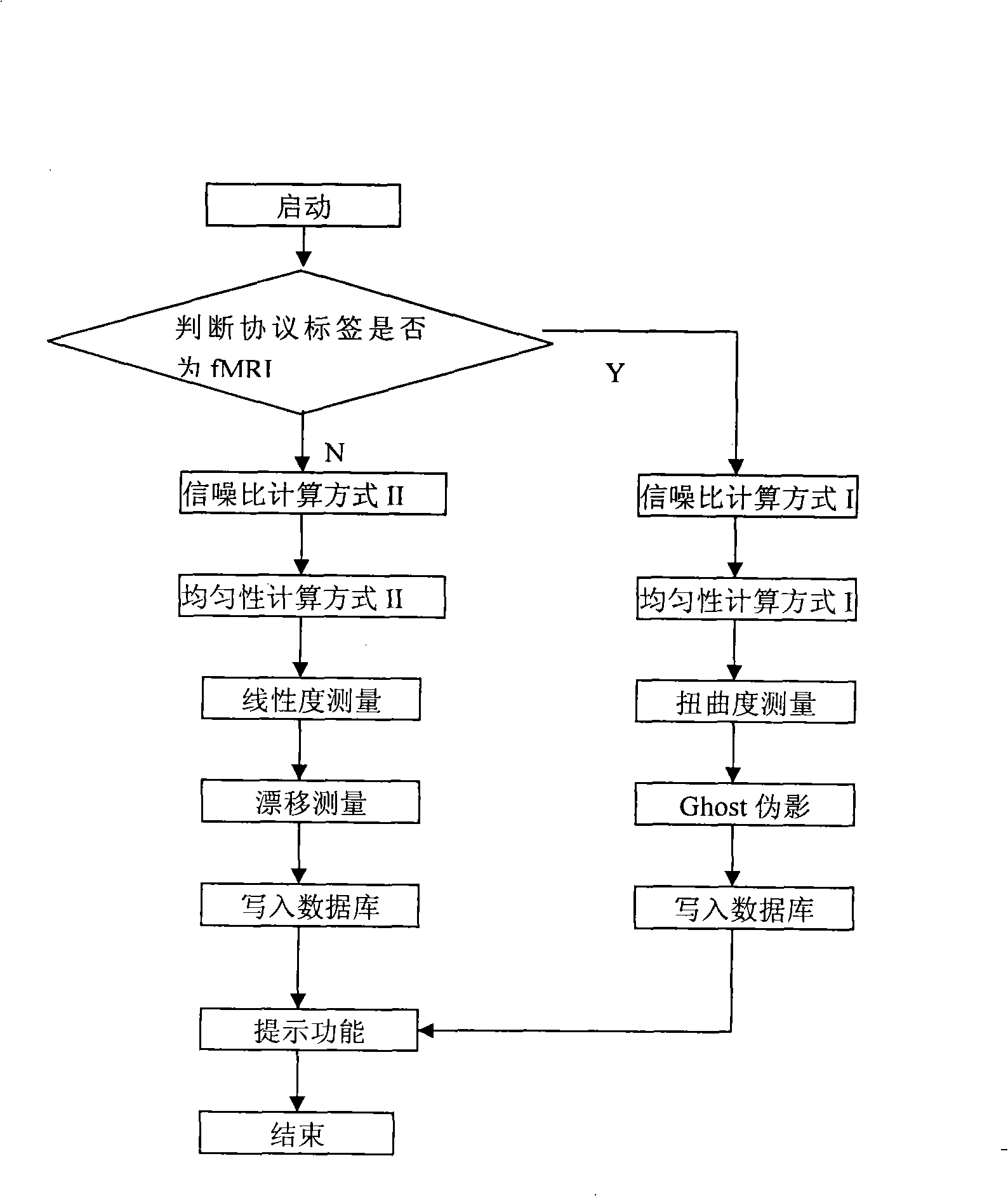
InactiveCN101322648AObjective analysisAvoid subjectivityDiagnostic recording/measuringSensorsDICOMNMR - Nuclear magnetic resonance
The invention discloses a method for measuring the stability and imaging indexes of a nuclear magnetic resonance imaging device and is characterized in that: the images of a water phantom are obtained by adopting the nuclear magnetic resonance imaging device to scan the water phantom, the images are transmitted to a specific nuclear magnetic resonance imaging quality assurance and analysis work station by a DICOM protocol, and then the quality assurance and analysis work station is self started and enters a corresponding measurement process (referring to the figure 1 in the abstract of the process) according to DICOM control elements so as to process and calculate the images of the water phantom; the measuring content includes common nuclear magnetic resonance imaging quality assurance indexes, the shifting indexes which have important significance to Functional MRI, and other indexes; meanwhile, an automatic early warning mechanism is established for auto prompting when an abnormal condition occurs and gives the possible reason, and all measured results are sent into a database for long-term analysis of data and evaluation of running state of the device, so as to offer guidance to relevant technicians to master device state and carry out equipment testing.
Owner:WEST CHINA HOSPITAL SICHUAN UNIV
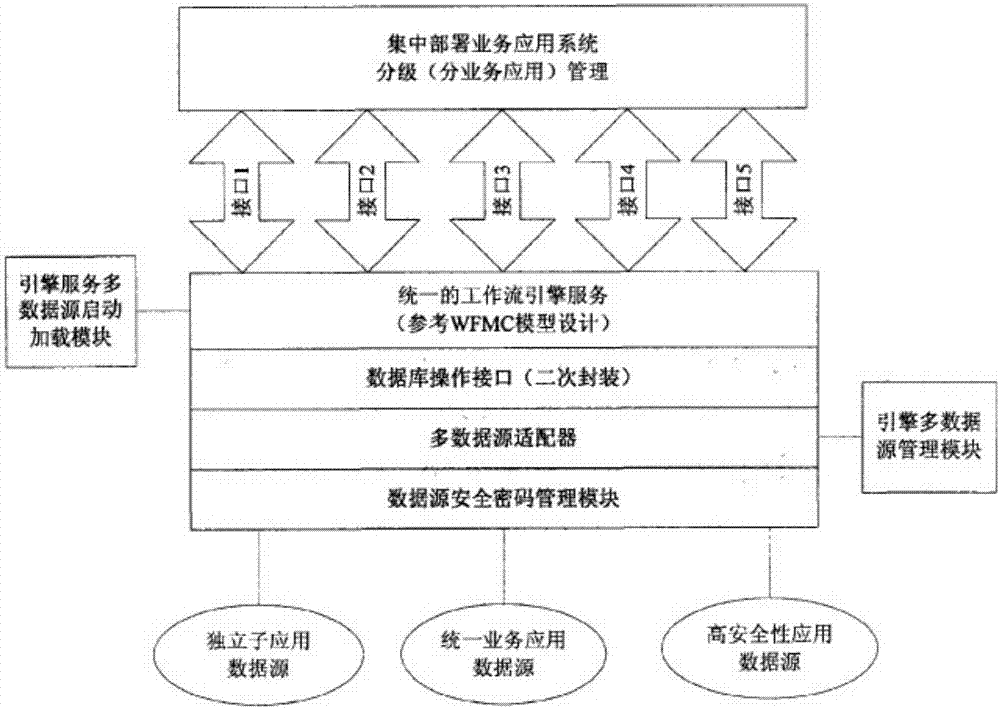
Safety access system and method with workflow engine supporting multi-data source configuration
ActiveCN106874461AMeet independenceMeet security requirementsOffice automationSpecial data processing applicationsData displayAccess method
The invention provides a safety access method with a workflow engine supporting multi-data source configuration. The method includes the steps of workflow engine initialization, multi-data source loading, data transmission encryption, data presentation and the like so that in processing of the multi-data source workflow engine, original data can be integrated for data analysis and diversified visualization functions can be provided. The invention further provides a safety access system with the workflow engine supporting multi-data source configuration. By means of the safety access method and system, multiple visual data display results can be provided for a user, and the user can understand and analyze the workflow engine more easily; meanwhile, different authorities are set for the user to protect data transmission, and thus private data can be protected.
Owner:北京慧正通软科技有限公司
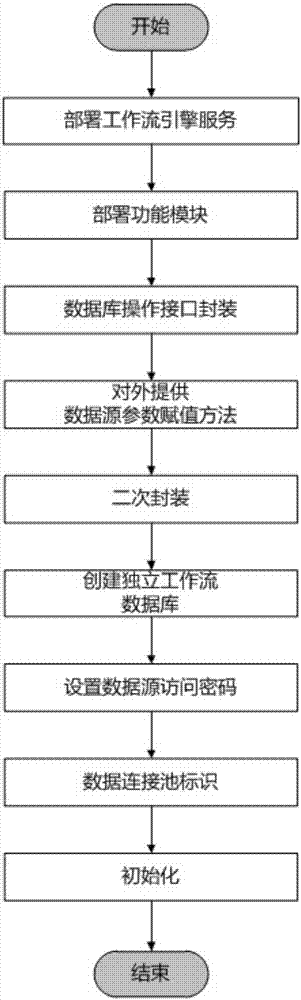
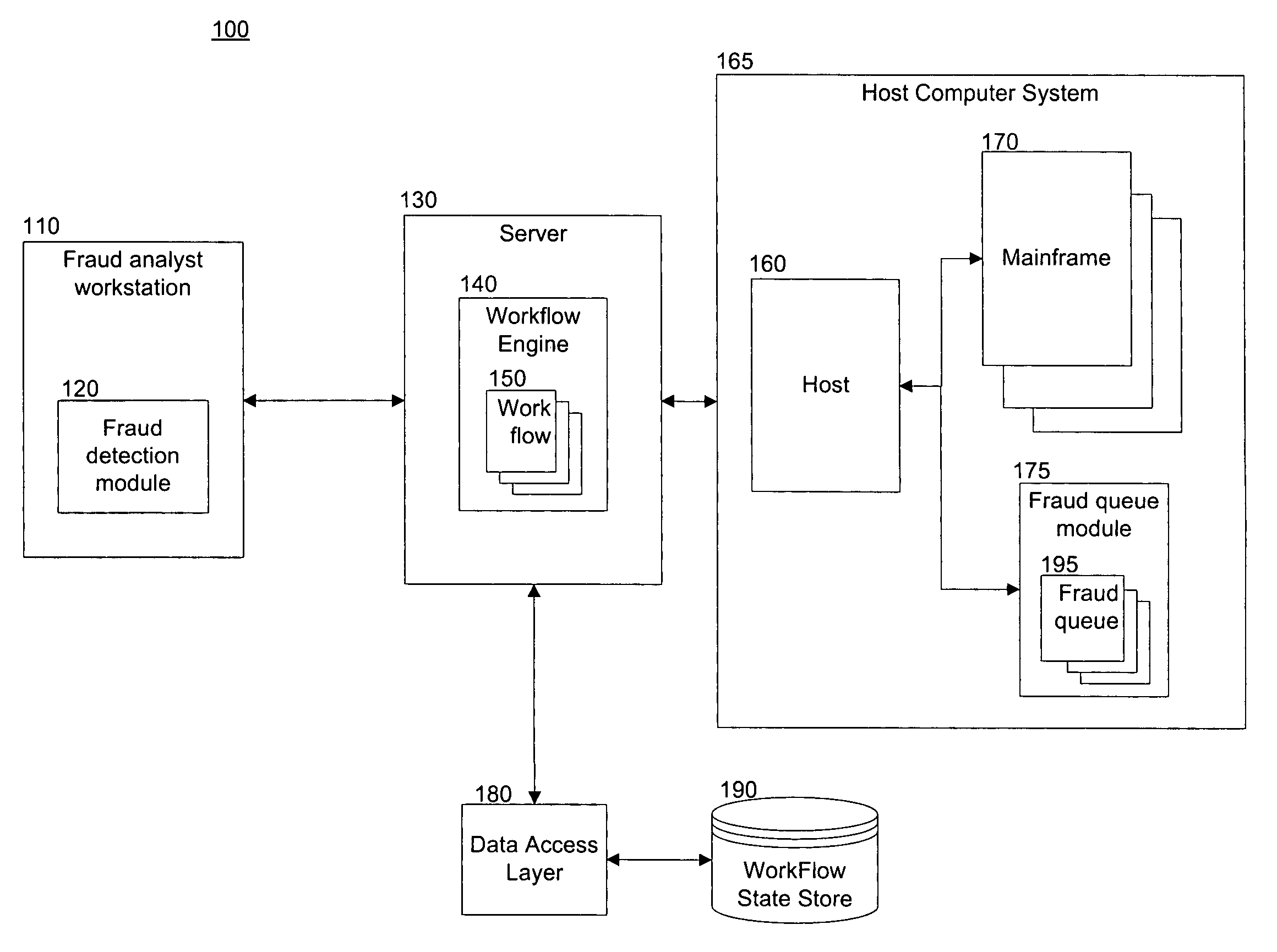
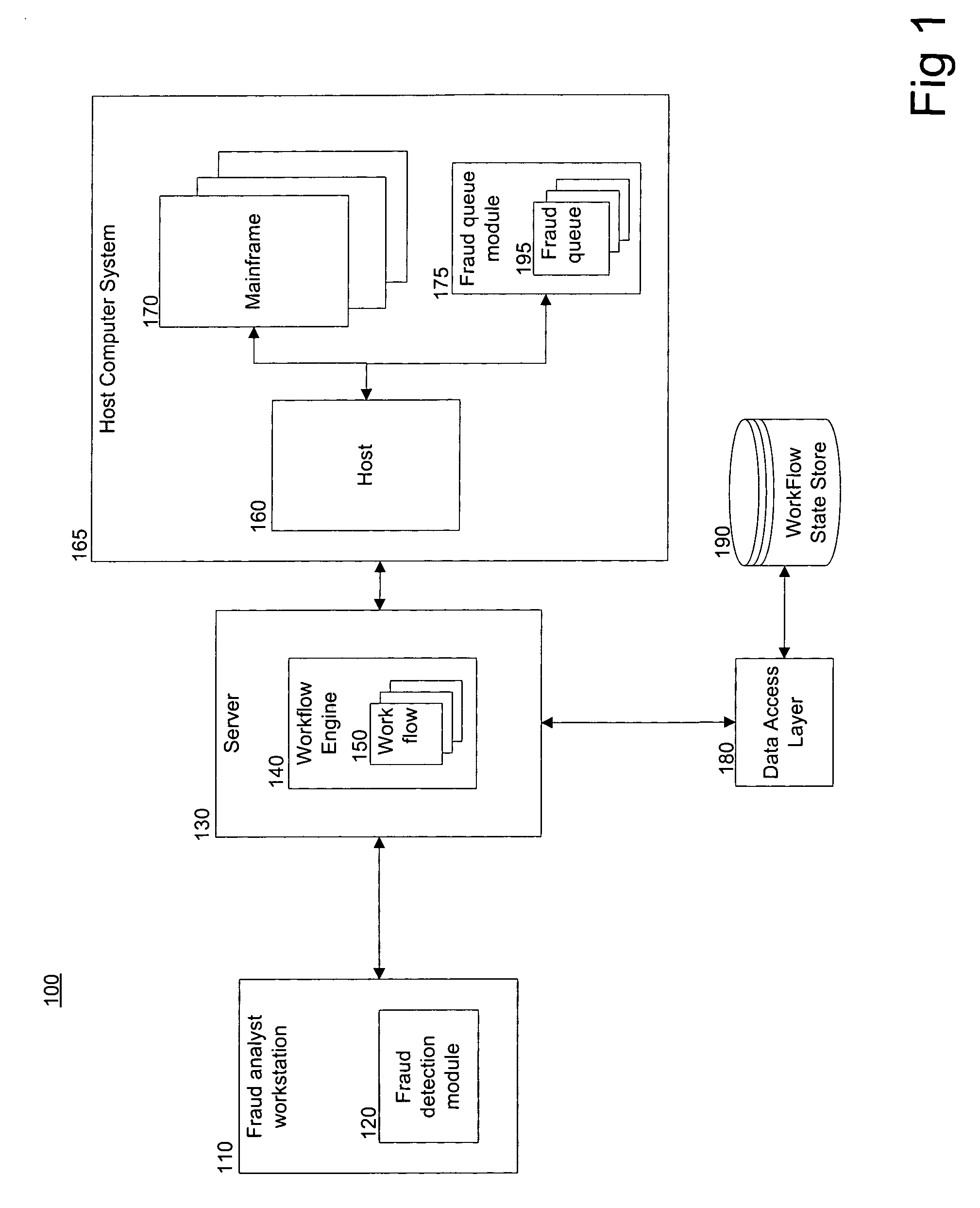
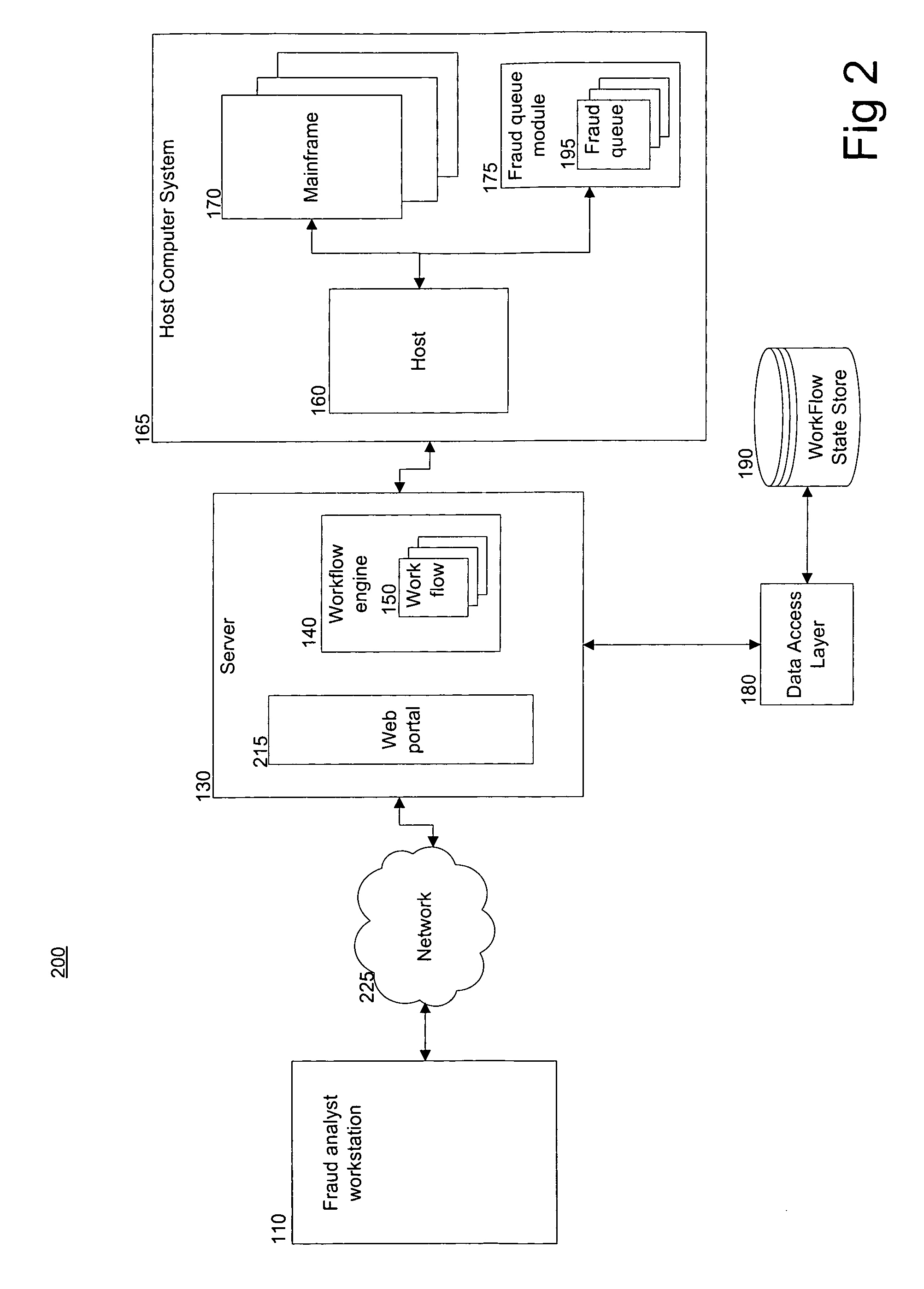
Method and system for detecting fraud in financial transactions
InactiveUS20080270303A1Efficient managementEnsure complianceFinanceProtocol authorisationGraphicsGraphical user interface
Detecting fraud in financial transactions. The systems and methods manage a fraud detection alert in a fraud queue; automatically locate the associated financial account data; display workflows on a graphical user interface; automatically navigate through workflows; ensure compliance with predetermined rules specific to a account-provider, business, or regulation; store all activity and data related to each fraud detection alert; and automatically update the fraud queue. The systems and methods include a fraud analyst workstation, a workflow engine, a host computer system, and a workflow database. The fraud analyst workstation communicates with the workflow engine, which stores and applies the predetermined rules. The workflow engine communicates with the host computer system to access the financial account data. The workflow engine communicates with a workflow database, which stores all activity and data related to each fraud detection alert for purposes of tracking, billing, and research.
Owner:TOTAL SYST SERVICES
Working Environment Positioning System, Method And Computer Program Product Thereof
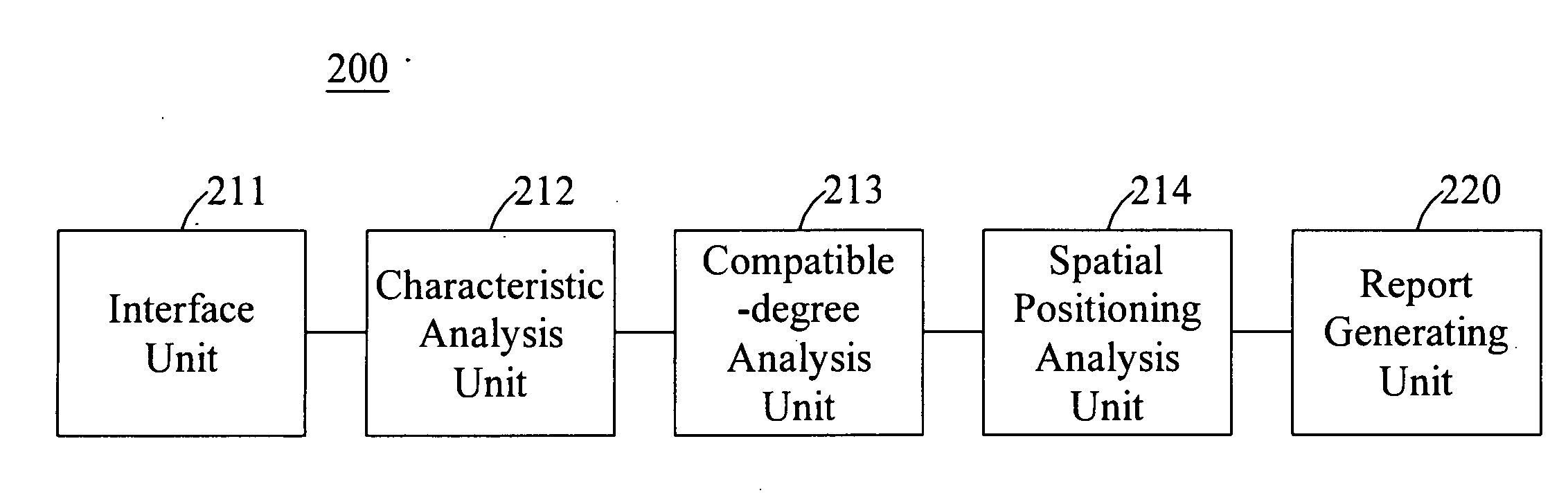
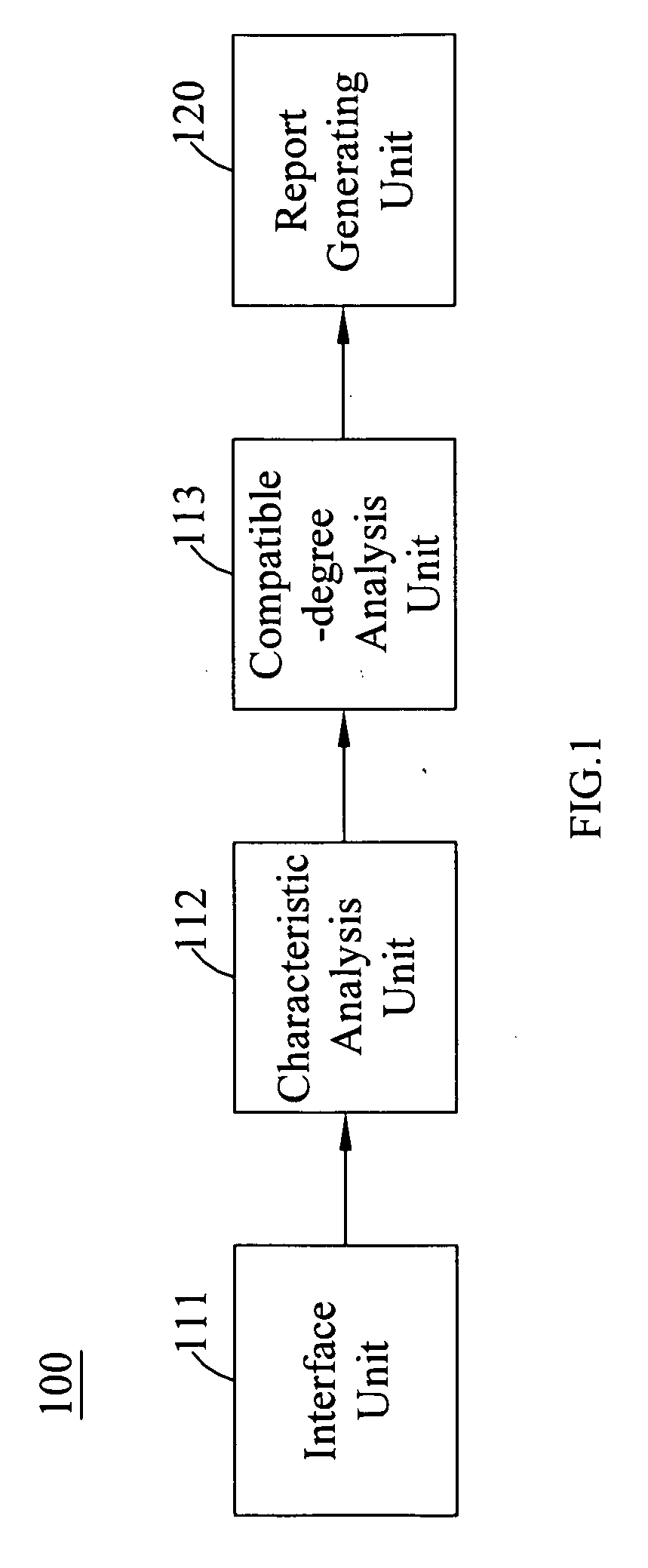
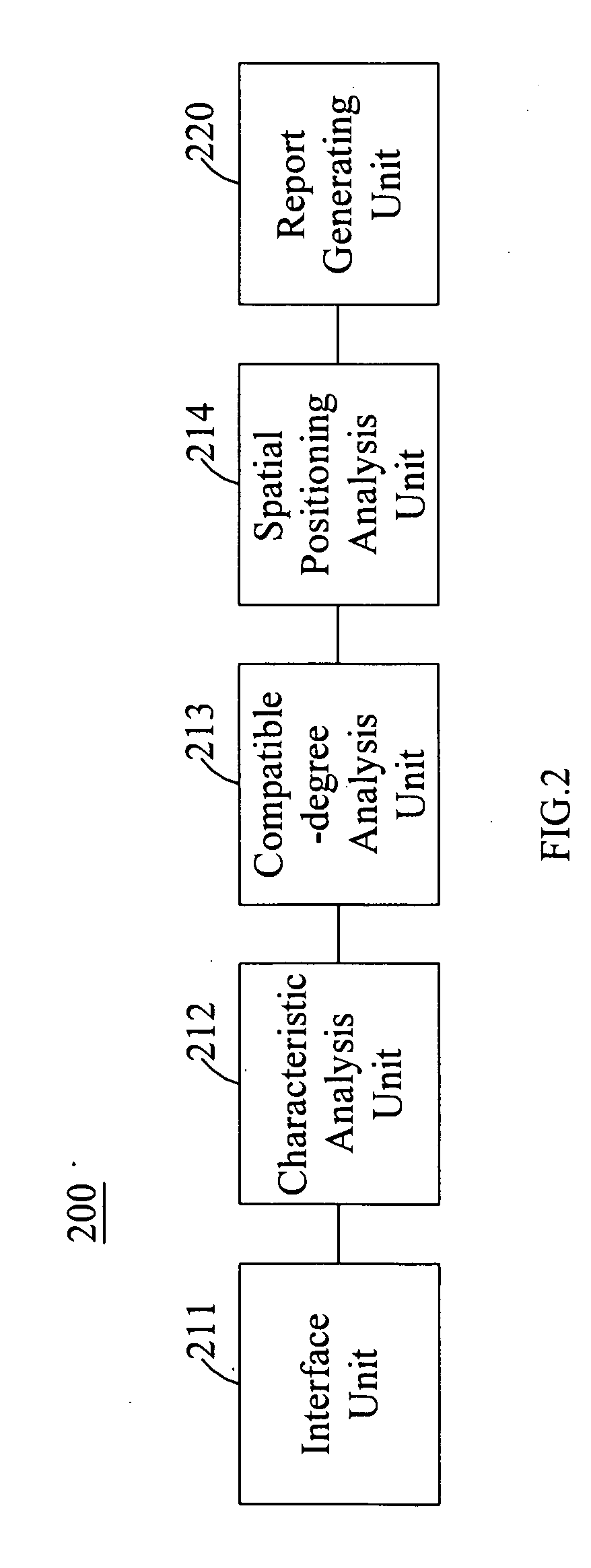
InactiveUS20100191561A1Choose accuratelyCloser lifestyleFuzzy logic based systemsKnowledge representationInformation analysisUser input
In a working environment positioning system, there is comprised an interface unit for receiving information input by users; a characteristic analysis unit coupled to the interface unit for analyzing characteristic indices of each of the users based on the input information; a compatible-degree analysis unit coupled to the characteristic analysis unit for analyzing a compatible degree of each of the users with other users based on the characteristic indices to generate a plurality of corresponding compatibility indices, from which a compatible-degree matrix is obtained; and a report generating unit for receiving analysis results from the characteristic analysis unit and the compatible-degree analysis unit, analyzing a positioning relation of each of the users in a working environment, and generating an analysis report accordingly. A working environment positioning method and a computer program product for implementing the method are also disclosed.
Owner:G5 CAPITAL MANAGEMENT
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com