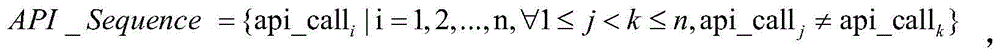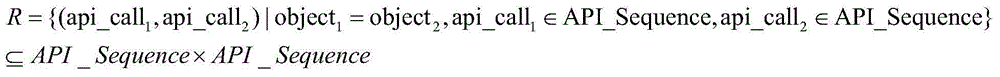Behavior characteristic similarity-based malicious code homology analysis method
A technology of homology analysis and malicious code, which is applied in the field of homology analysis of malicious code based on the similarity of behavior characteristics, can solve the problems of poor versatility and inability to analyze malicious code samples, and achieve the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
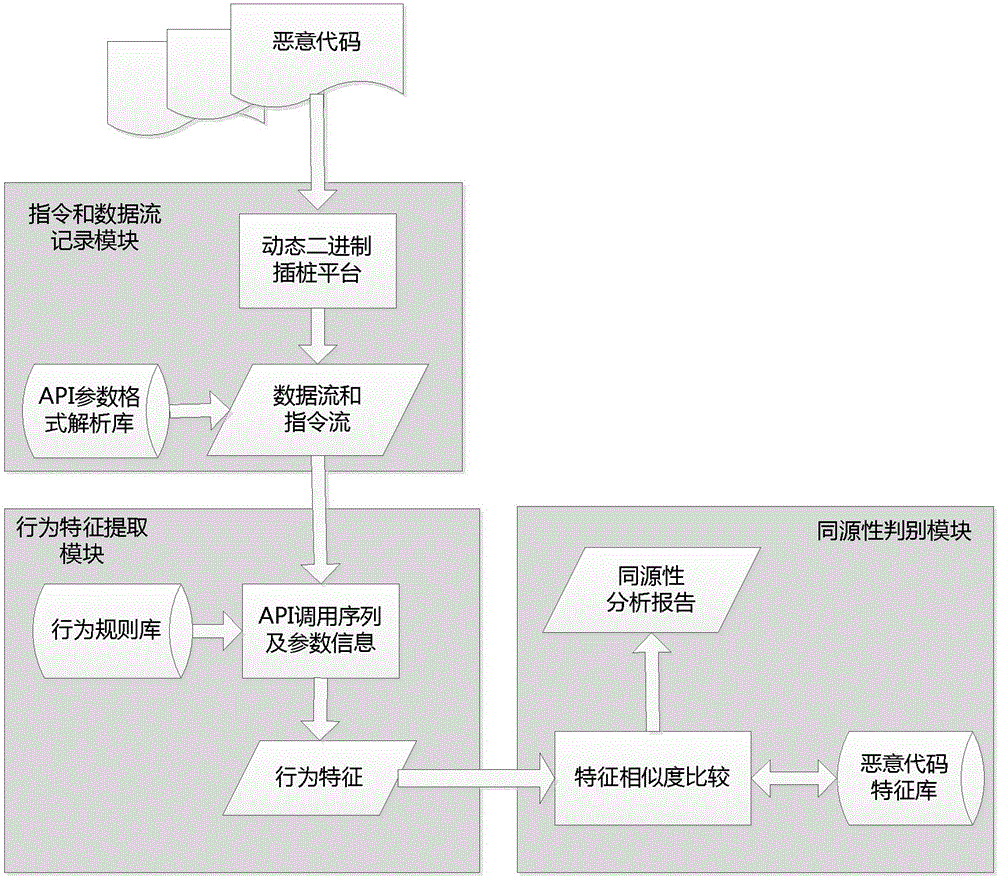
[0046] Embodiment: A method for analyzing homology of malicious codes based on behavioral feature similarity, the specific steps are as follows:
[0047] First, the instruction and data recording module is based on the dynamic binary instrumentation platform, executes malicious code samples in a protected virtual environment, analyzes key instructions through instrumentation, and records program entry points, return points, memory read and write points and other key positions, combined with the API parameter format parsing library, to obtain the call sequence and parameter information of the key API defined in the library.
[0048] Then, the feature extraction module takes the API call sequence and its parameter information as input, combines with the behavior rule library, and extracts behavior features on the basis of building an API association tree.
[0049] Finally, the homology discrimination module takes the behavioral characteristics of two malicious codes as input, an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com