A Method for Optimizing Access Control Policy
A technology of access control strategy and optimization method, which is applied in the field of network security, and can solve problems such as rule conflicts, rule level conflicts, and changes in the maximum number of matching times of rules are not considered.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention is described in detail below in conjunction with accompanying drawing example:
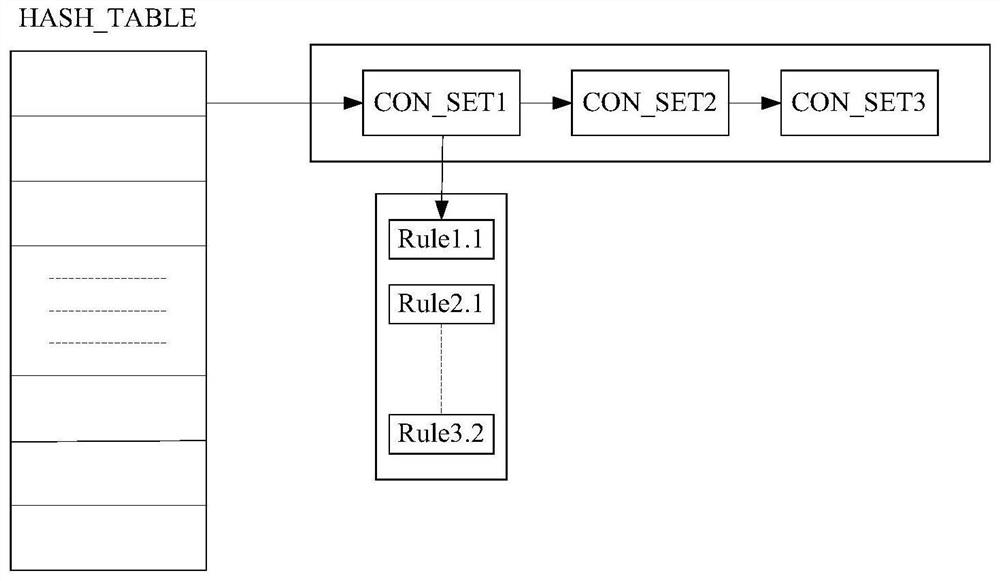
[0029] 1) Definition conflicts and redundancy.
[0030] Definition 4.1 Refuse to cover algorithm reordering: We define RS: {R 1 , R 2 ,...,R n} a policy set containing n rules, and the merging algorithm is Deny Coverage, then we put all the rules with the effect of Deny in front of all the Permit rules, which becomes: RS’: {[R D , R D ,...R D ],[R P , R P ,...,R P ]}, where RD represents all the rules whose effect is Deny in the RS, and RP represents all the rules whose effect is Permit in the RS.
[0031] Definition 4.2 allows overriding algorithm reordering: we define RS: {R 1 , R 2 ,...,R n} A policy set containing n rules, and the merging algorithm is to allow coverage, then we put all the rules with the effect of Permit in front of all the Deny rules, which becomes: RS': {[R P , R P ,...R P ],[R D , R D ,...,R D ]}, where R D Indicates all the ru...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com