Method and device for generating access controlling policy
An access control strategy and access control technology, applied in the field of network applications, can solve problems such as error-prone and difficult for users to define, and achieve the effects of ensuring accuracy, easy understanding and operation, and reducing burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
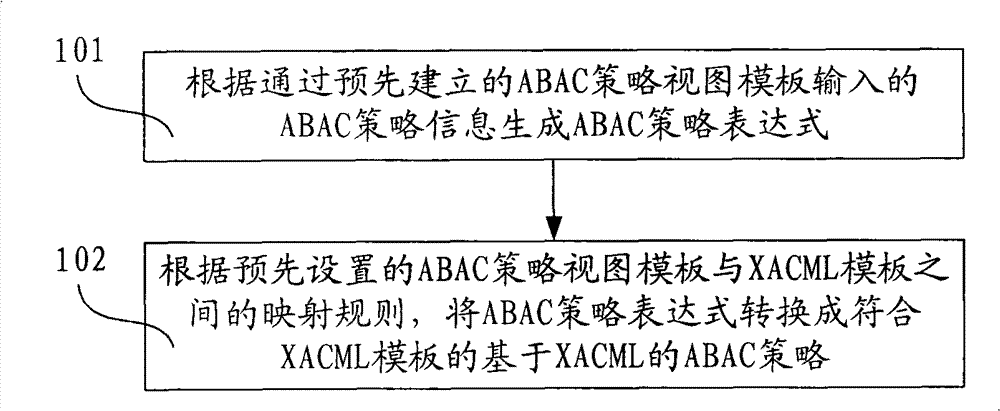
[0029] figure 1 It is a flow chart of Embodiment 1 of the access control policy generation method of the present invention, as shown in figure 1 As shown, the method includes:
[0030] Step 101, generate an ABAC policy expression according to the ABAC policy information input by the user through the pre-established ABAC policy view template;
[0031] Step 102: Convert the ABAC policy expression into an XACML-based ABAC policy conforming to the XACML template according to the preset mapping rule between the ABAC policy view template and the XACML template.
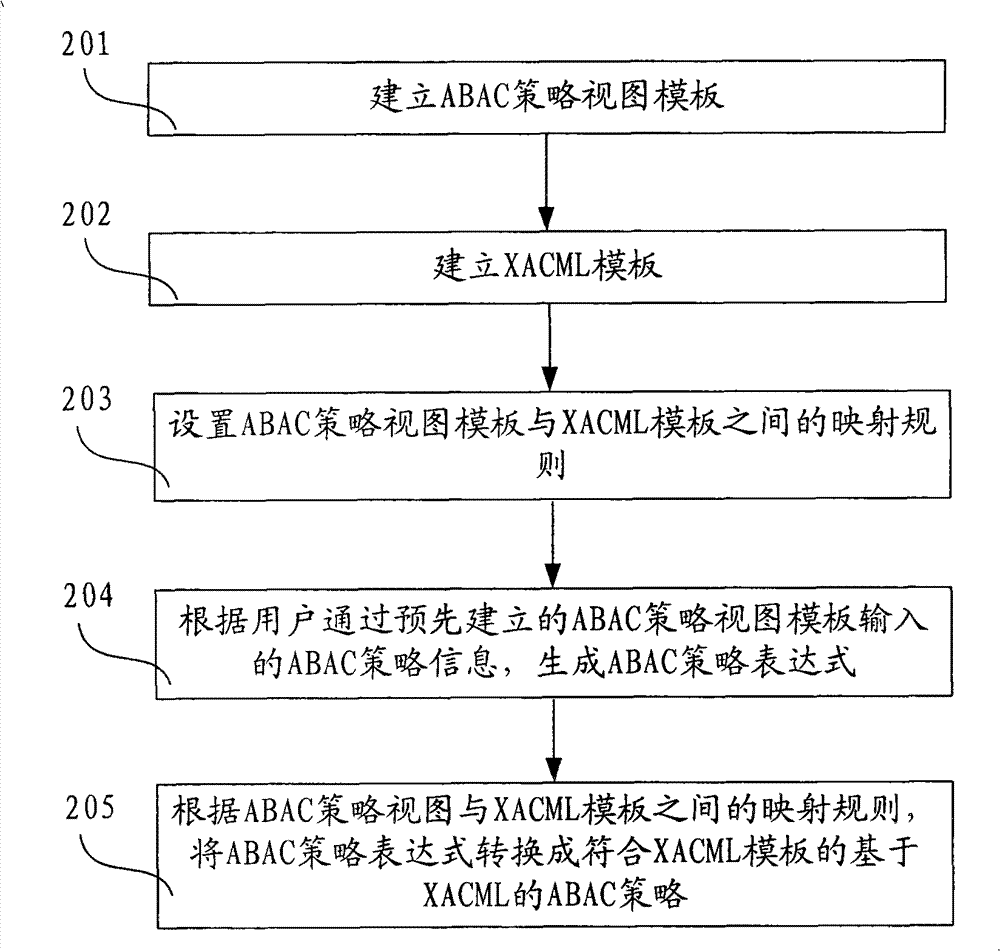
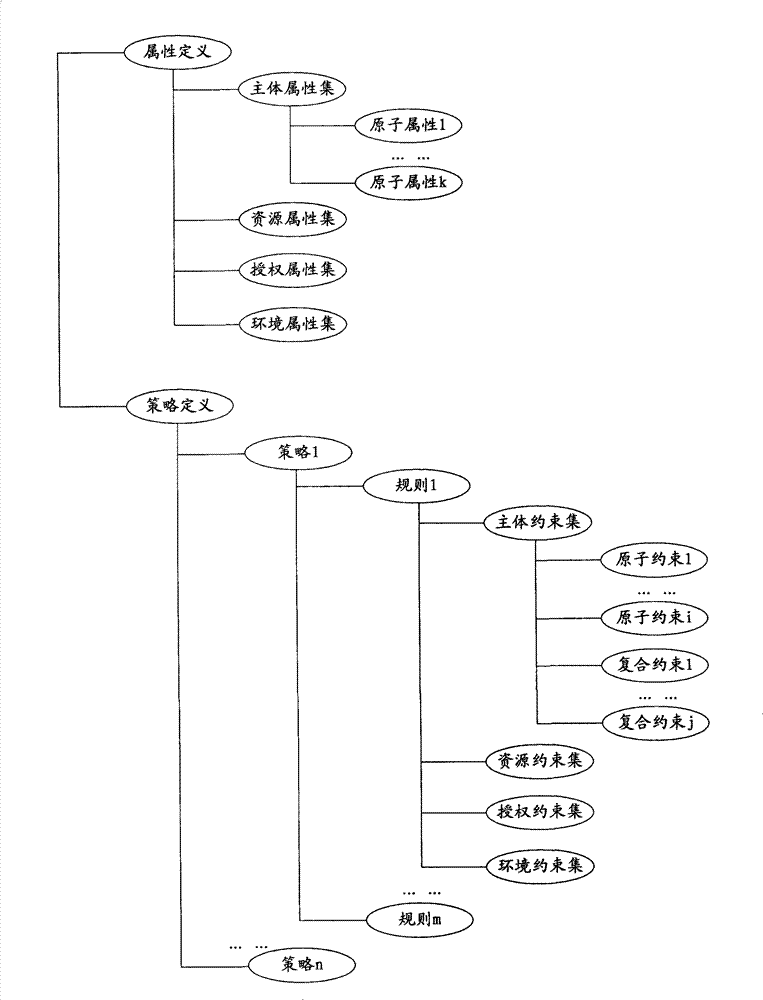
[0032] In the technical solution of this embodiment, an ABAC policy expression is generated according to the input ABAC policy information, and then the ABAC policy expression is automatically converted into an XACML-based ABAC policy through the set mapping rules. In this process, the user only needs to pass through the ABAC policy view Templates input some simple ABAC policy information, no need to manually wr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com