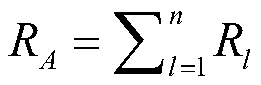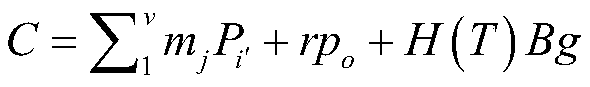Aggregation method for multi-dimensional data encryption and decryption in intelligent power grid
A technology of multi-dimensional data and aggregation method, which is applied in the field of multi-dimensional data encryption and decryption aggregation, can solve the problems of control center calculation burden and data leakage risk, high calculation cost, low key generation efficiency, etc. Risk of data leakage, improved key generation efficiency, and improved decryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
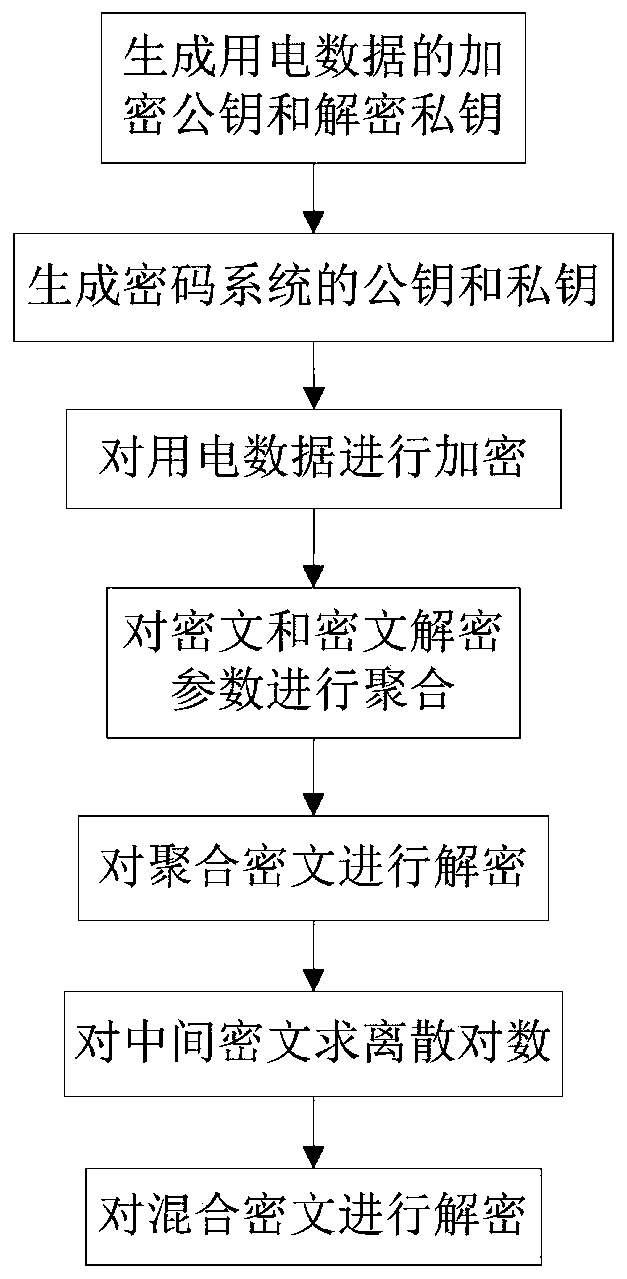
[0043] Attached below figure 1 The present invention is further described.
[0044] Step 1: Use the Chinese remainder theorem to generate the encryption public key and the decryption private key of the electricity consumption data respectively.
[0045] Generate a k-dimensional prime number sequence ρ 1 ,...,ρ i ,...,ρ k , and use this prime number sequence as the private key for decrypting electricity data, where k≥2, ρ i >2 128 .
[0046] To construct an elliptic curve whose order is modulus N, where the modulus Π represents the multiplication operation.
[0047] A cyclic group whose order is an integer N' is selected on the elliptic curve, and generators are randomly selected in the cyclic group, where N'=N.
[0048] Generate a k′-dimensional cyclic group element sequence P 1 ,...,P i′ ,...,P k′ , and use this cyclic group element sequence as the encrypted public key of electricity data, where k′=k, P i′ = M i′ m i′ -1 g, P i′ Indicates the i′th group eleme...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com