Patents
Literature
32 results about "Rainbow table" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
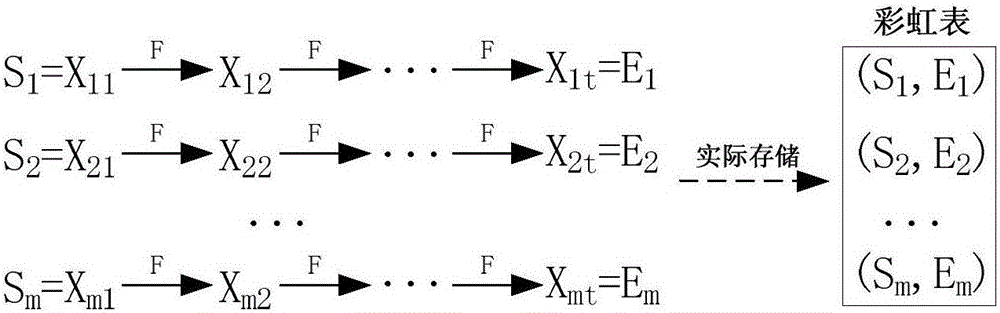
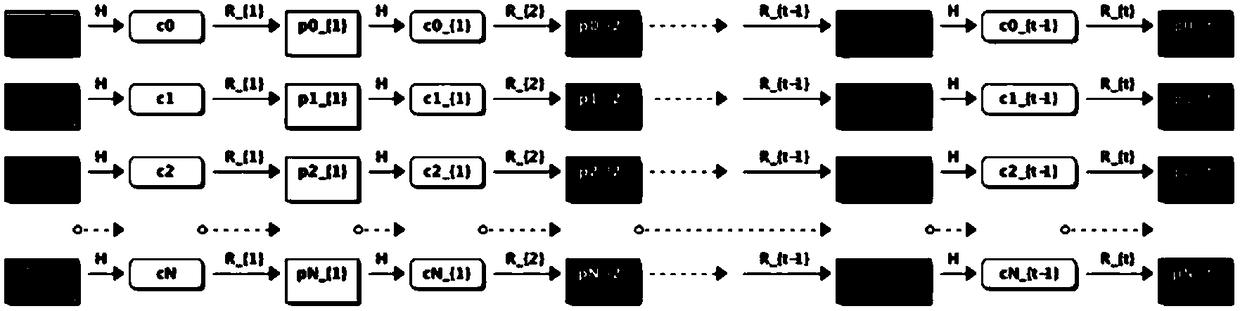
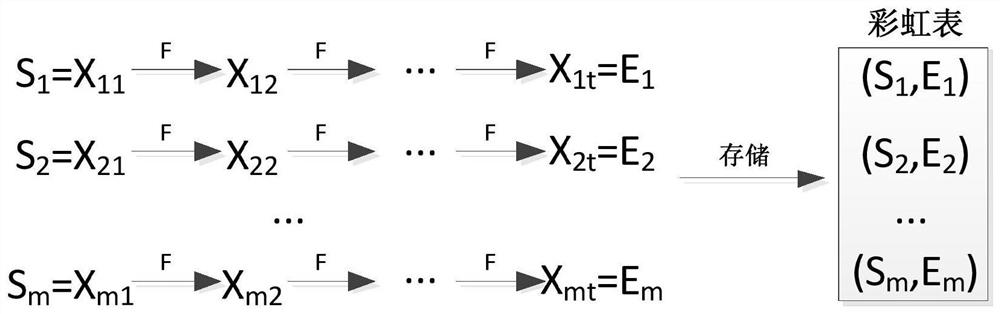
A rainbow table is a precomputed table for reversing cryptographic hash functions, usually for cracking password hashes. Tables are usually used in recovering a password (or credit card numbers, etc.) up to a certain length consisting of a limited set of characters. It is a practical example of a space–time tradeoff, using less computer processing time and more storage than a brute-force attack which calculates a hash on every attempt, but more processing time and less storage than a simple lookup table with one entry per hash. Use of a key derivation function that employs a salt makes this attack infeasible.
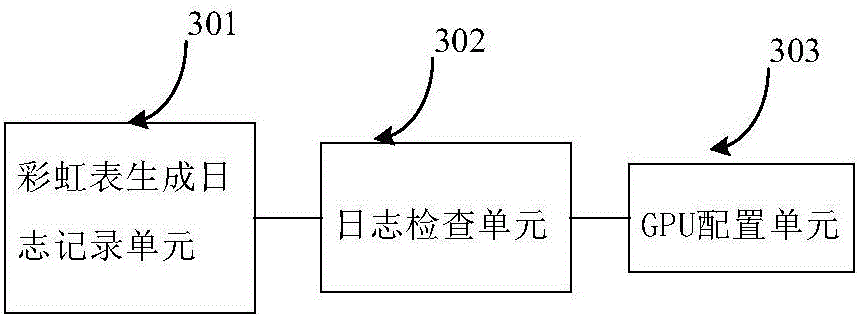
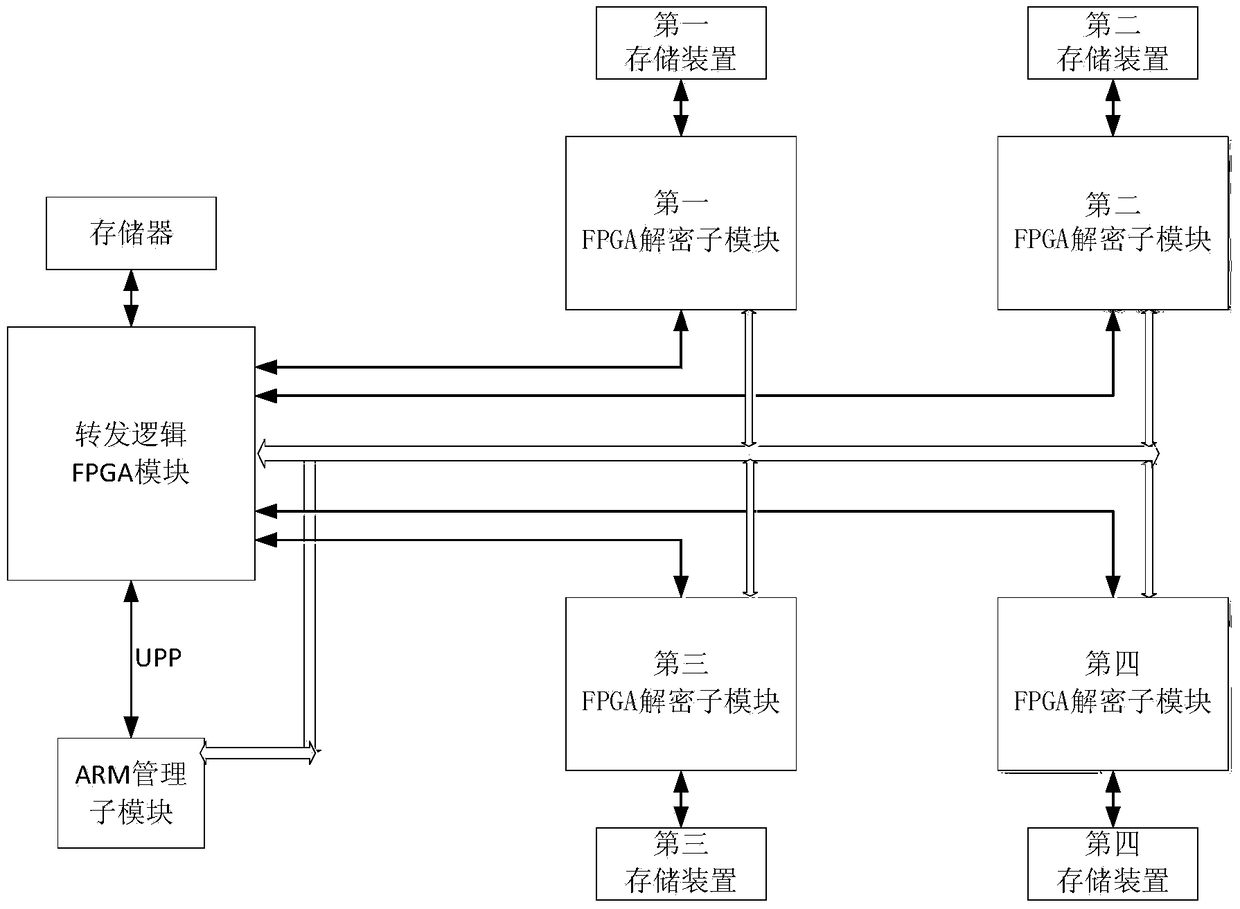
Decryption hardware platform based on FPGA
ActiveCN105376061AIncrease profitAchieve crackingKey distribution for secure communicationUser identity/authority verificationComputer hardwareRainbow
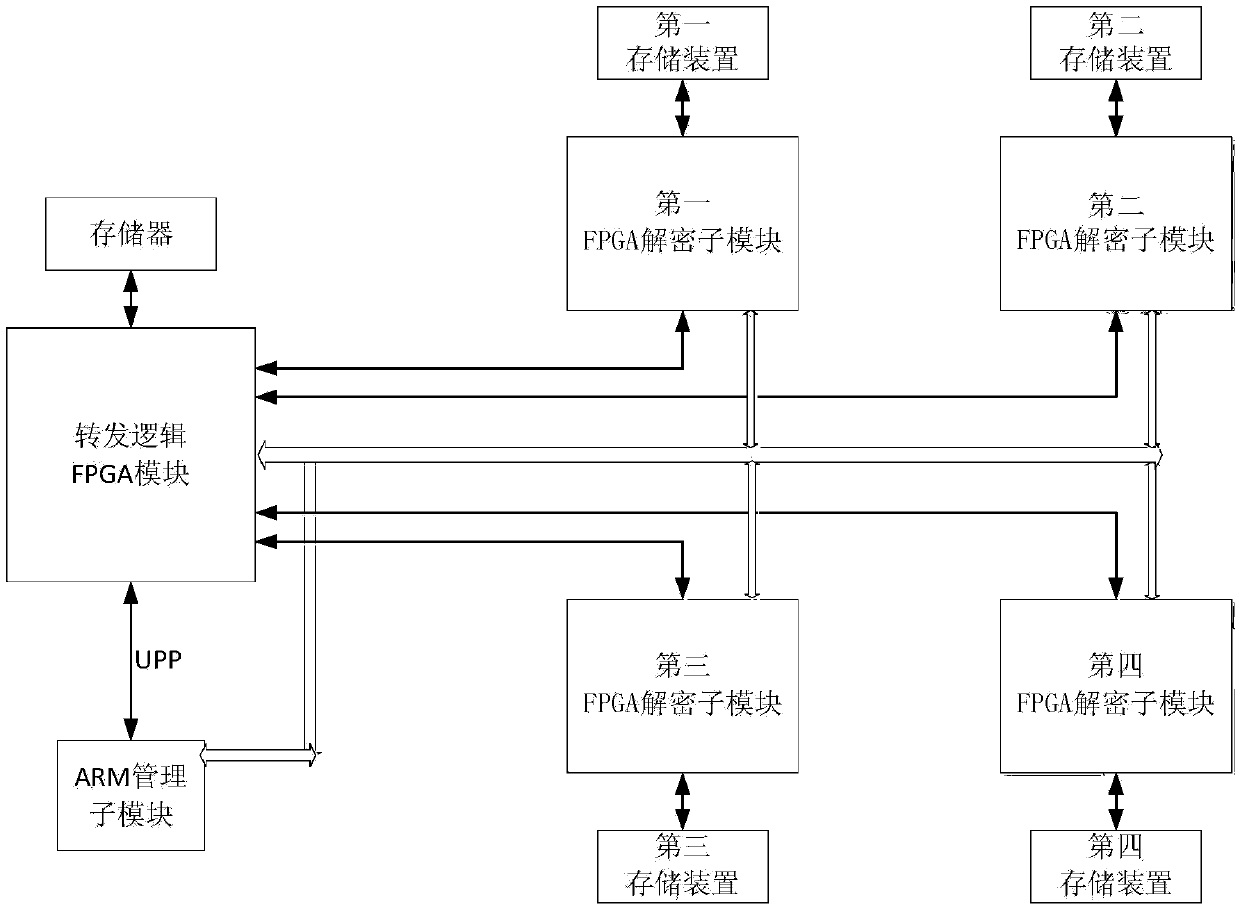
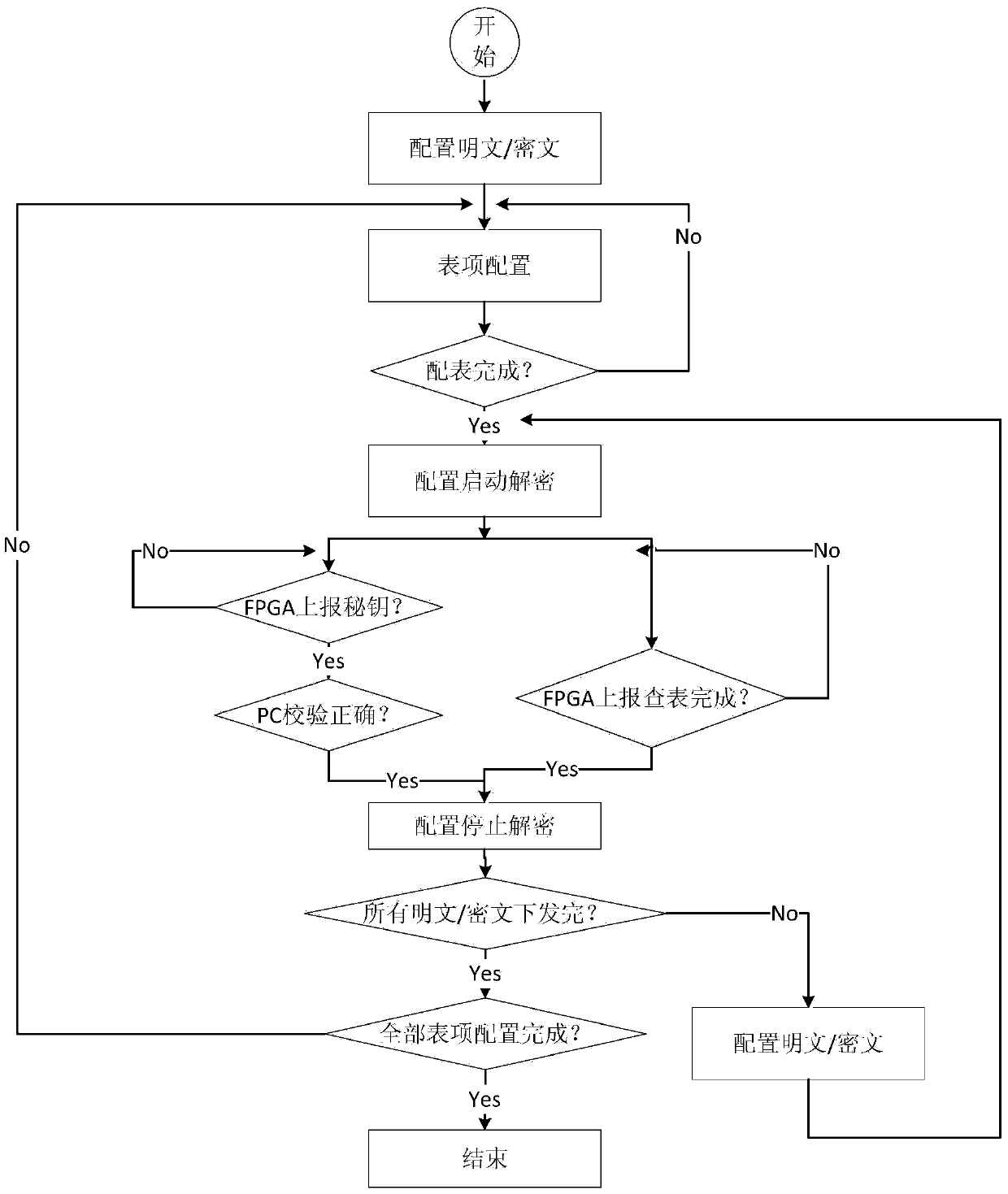
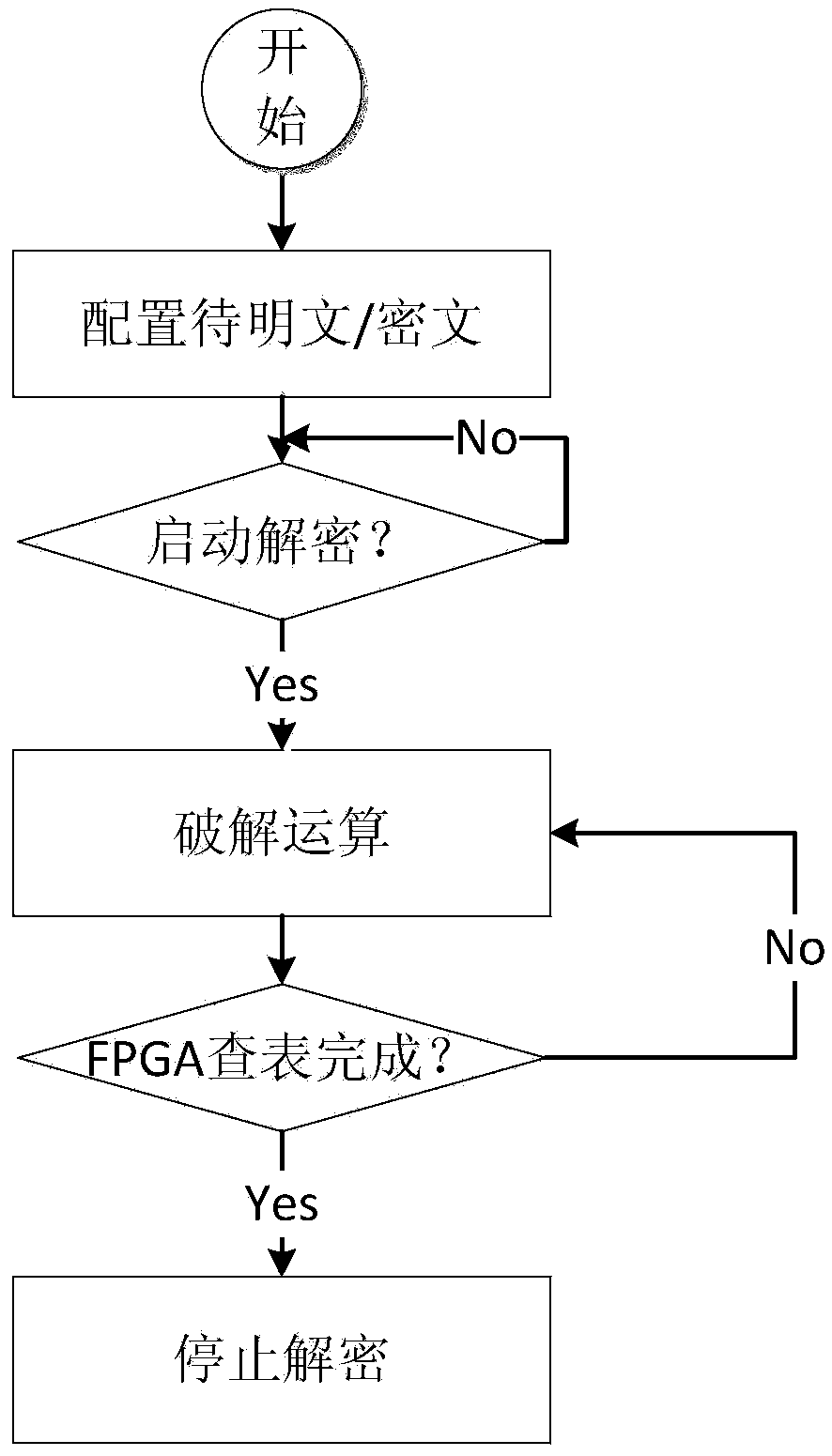
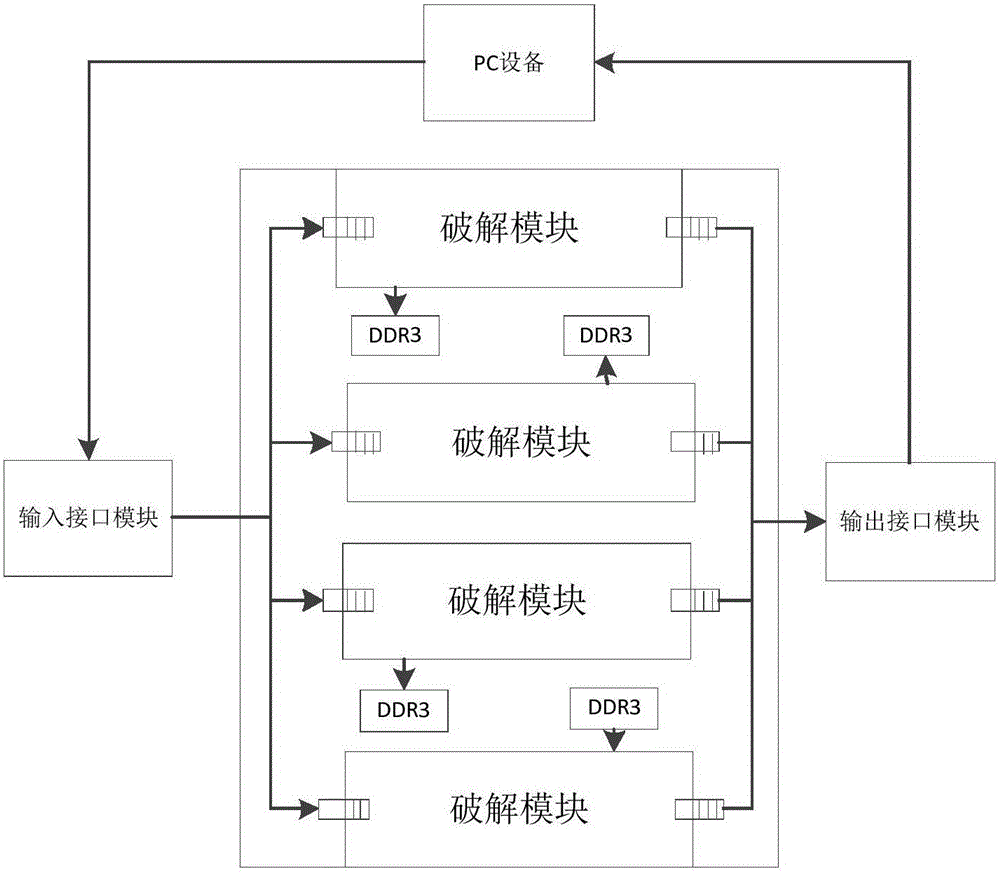
The invention discloses a decryption hardware platform based on an FPGA. The decryption hardware platform is characterized in that the decryption hardware platform comprises a forwarding logic FPGA module, N mutually-independent FPGA decryption sub-modules and an ARM management sub-module which are respectively connected with the forwarding logic FPGA module, and a power supply management module supplying power to the forwarding logic FPGA module, the N mutually-independent FPGA decryption sub-modules and the ARM management sub-module, wherein the N mutually-independent FPGA decryption sub-modules are respectively connected with the ARM management sub-module, and N is no less than 2. The decryption hardware platform provided by the invention meets the decryption requirements of different files and solves the problems that an existing decryption device is single in function and poor in universality. The FPGA has the advantages that the requirements of high-speed data transmission, interfaces and high-frequency data operation are met, high-speed data transmission and high-speed data transportation are realized, and the PFGA is externally provided with a high-speed large-capacity DDR3, so that the storage of rainbow tables is realized.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
User password management method and server
ActiveCN107689869ASave privacyGuaranteed privacyKey distribution for secure communicationMultiple keys/algorithms usageCiphertextRainbow table
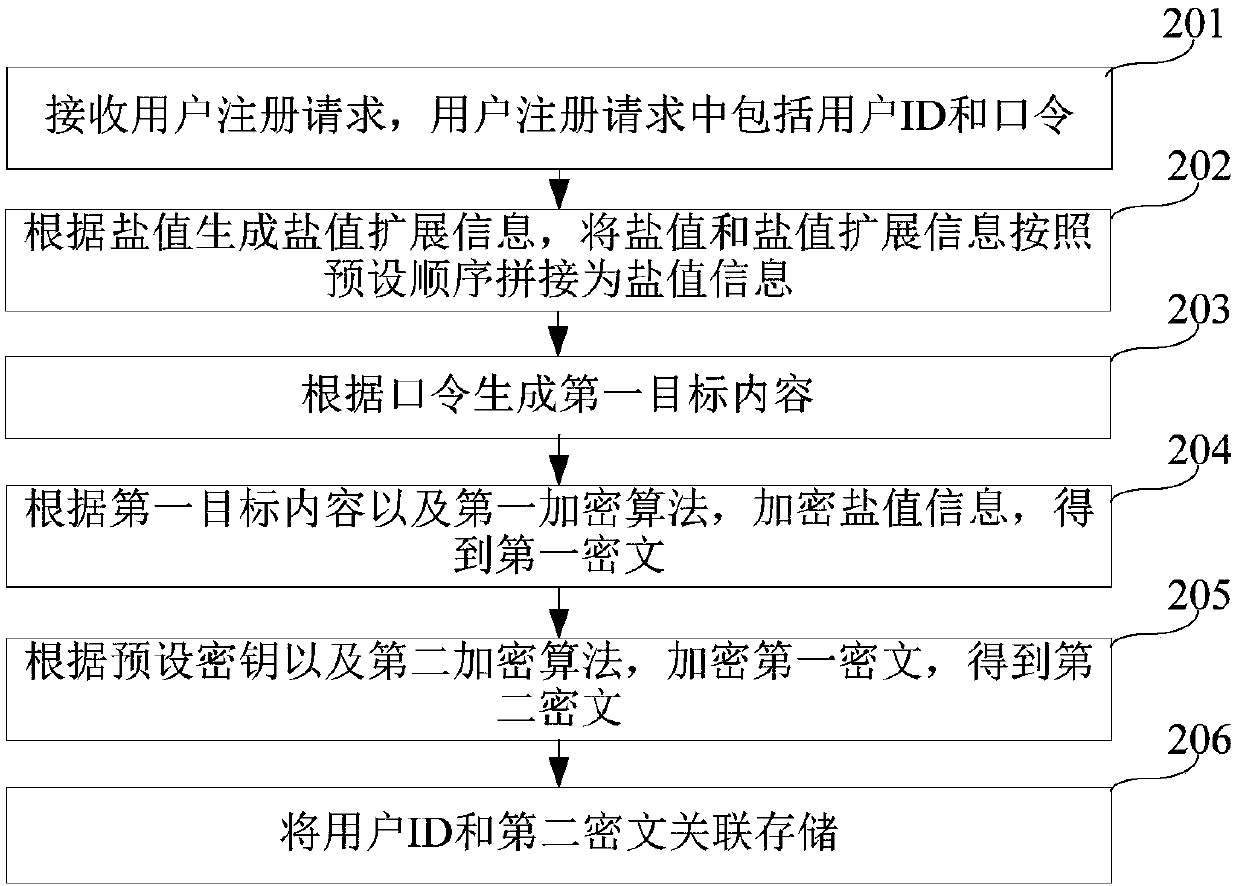
The embodiment of the invention provides a user password management method and a server, and relates to the field of computers. The method is as follows: through generating salt value extended information according to a salt value after receiving a user registration request comprising a user ID (Identification) and a password, and splicing the salt value and the salt value extended information into salt value information according to a preset sequence, after a password is encrypted, the user ID only needs to be associated with a second ciphertext after two times of encryption to store and thesalt value does not need to be stored; the problem that the server needs to consume a large number of storage spaces due to the fact that the salt value needs to be stored in the prior art is solved;and since the salt value does not need to be stored, an attacker is prevented from attacking and cracking the user password by stealing the salt value and constructing a rainbow table.
Owner:HUAWEI TECH CO LTD
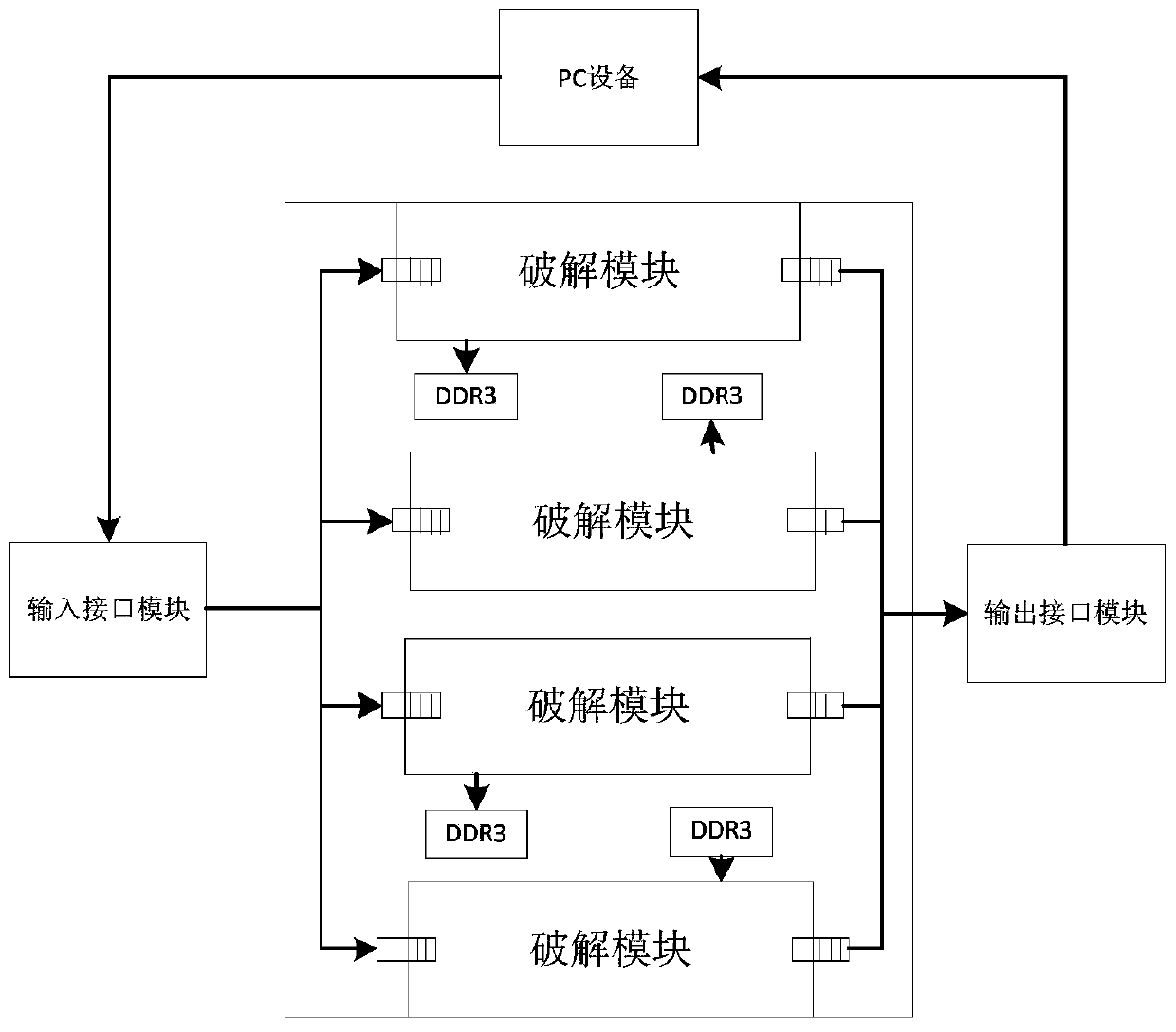
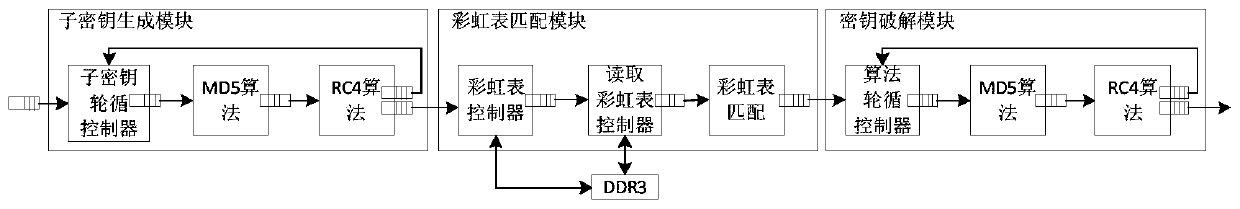
Word2003 document cracking system based on FPGA hardware and method
ActiveCN106357384AImprove cracking efficiencyDelayed cracking timeData stream serial/continuous modificationResource consumptionComputer module
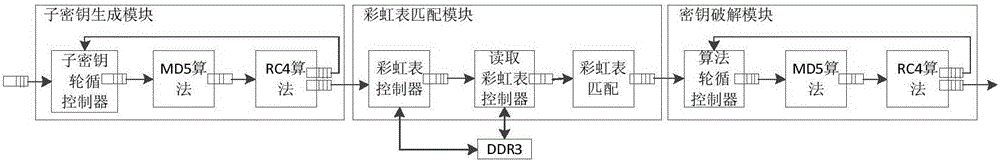
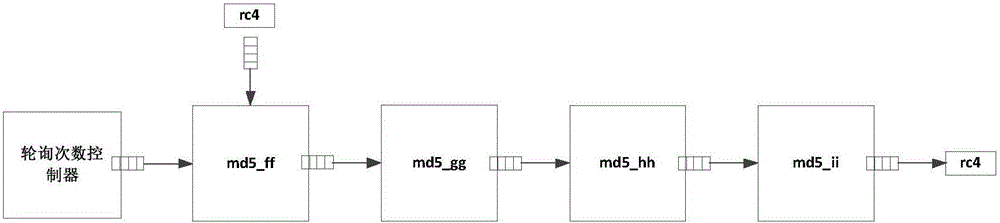
The invention discloses a word2003 document cracking system based on FPGA hardware and a method. The system comprises a PC, an input interface module, a crack module and an output interface module which are connected sequentially, and the PC is connected with the output interface module. The crack module comprises a sub-key generation module, a rainbow table matching module and a key cracking module which are connected sequentially. The sub-key generation module includes sub-key round robin controller, MD5 algorithm module and RC4 algorithm module which are connected sequentially. The key cracking module consists of algorithm round robin controller, MD5 algorithm module and RC4 algorithm module. The system achieves document cracking by using the time and space folding algorithm of the rainbow table, thus improving the crack efficiency and reducing the cracking time. On the basis of considering the technical characteristics of the rainbow table and the FPGA, the appropriate rainbow table is used for cracking, thus solving the contradiction between cracking time and resource consumption.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
User name password authentication method implemented on basis of public key algorithm
InactiveCN103701787AKeep securityKeep simplicityUser identity/authority verificationPasswordRainbow table
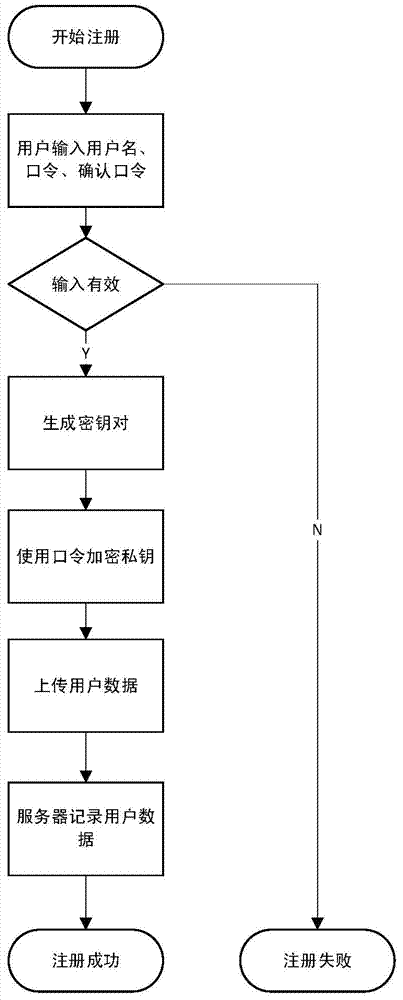
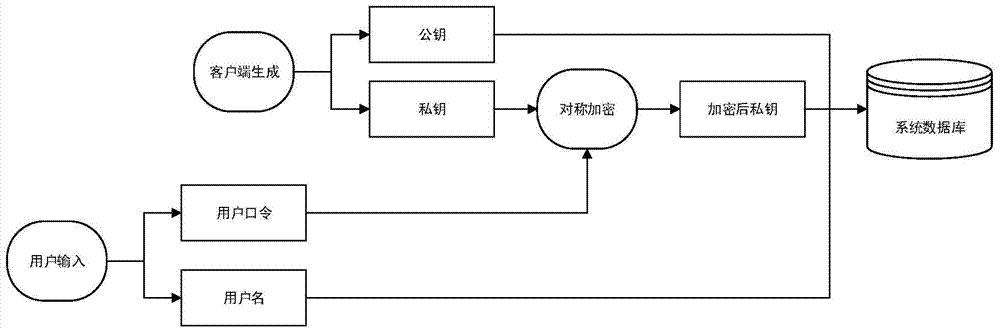
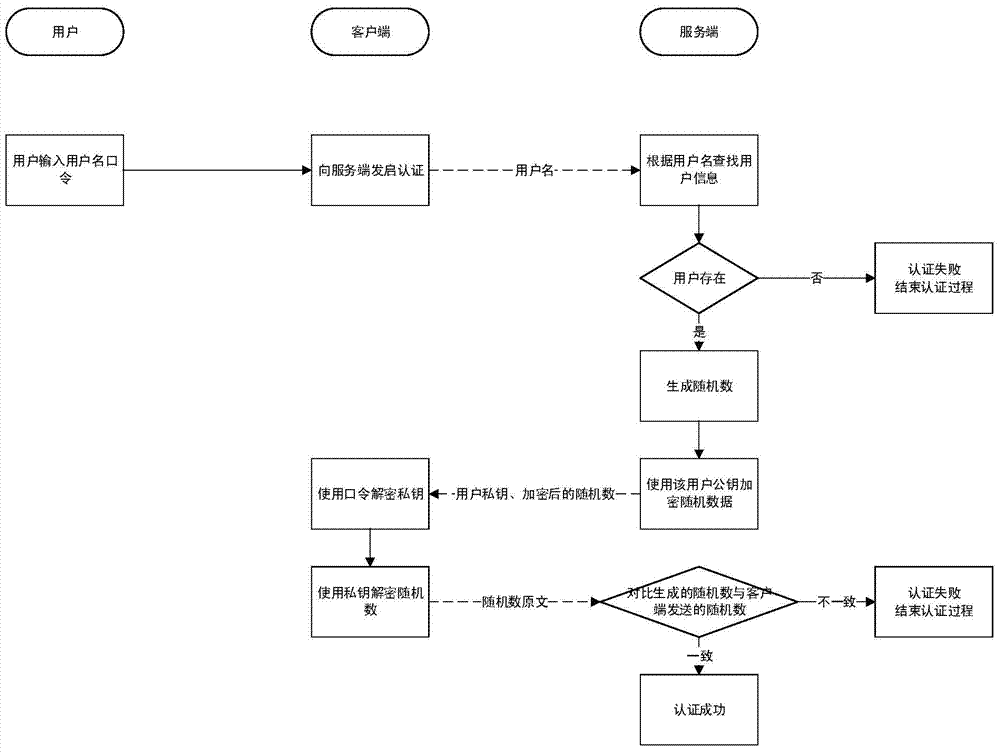
The invention discloses a user name password authentication method implemented on the basis of a public key algorithm. According to the user name password authentication method, the public key algorithm is introduced in the authenticating process; the authentication is implemented by using the public key algorithm; a user password is not directly used for authenticating, but is used for protecting a private key of a user. According to the invention, on the premise of not increasing the authentication difficulty of the user, safety of a user name password authentication mode is improved and a rainbow table attack can be effectively resisted.
Owner:KOAL SOFTWARE CO LTD
Password attacking method and apparatus, and heterogeneous acceleration platform
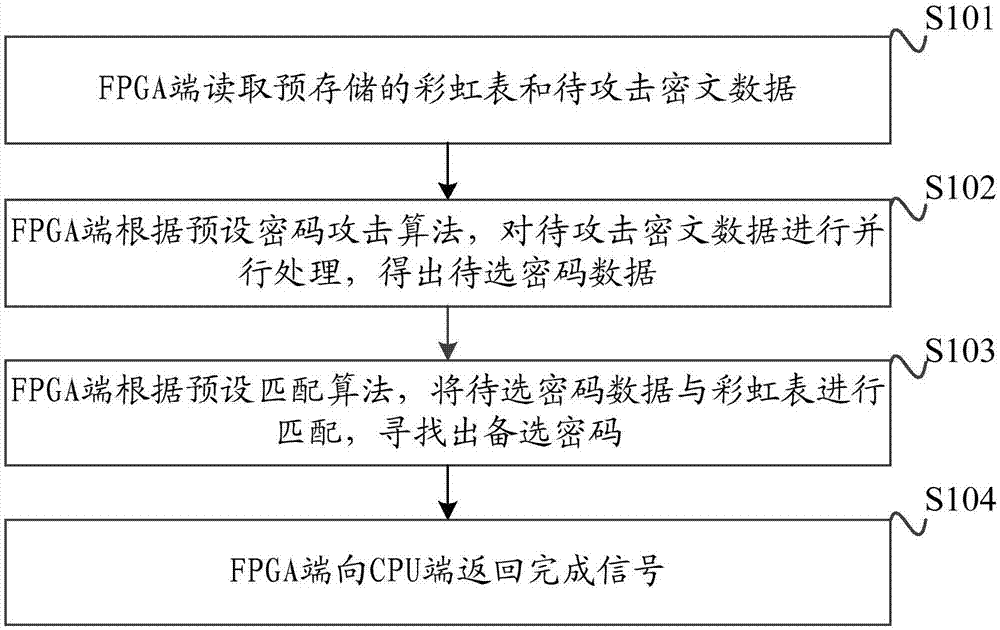
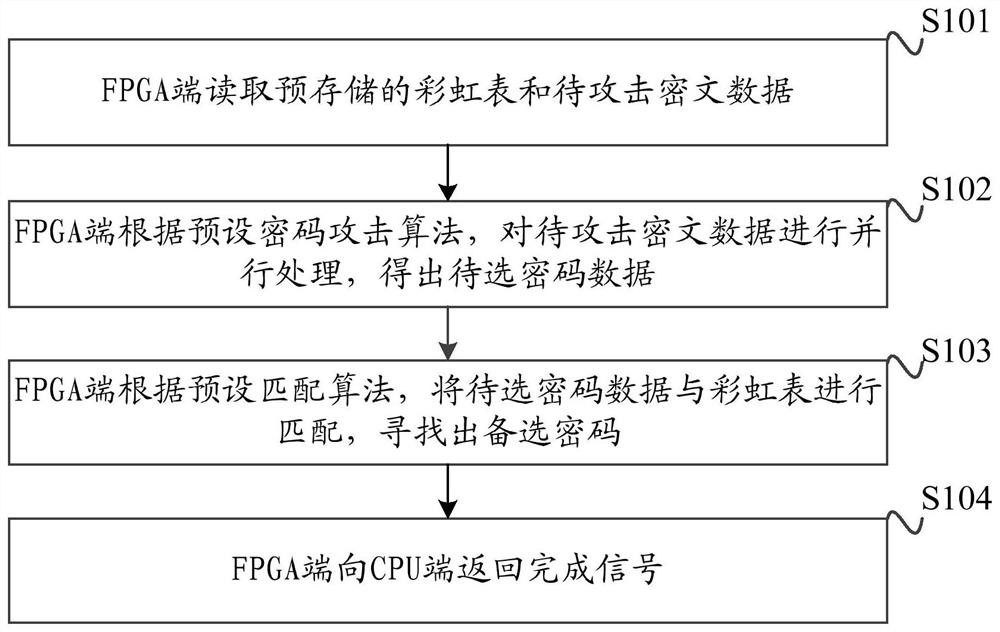
ActiveCN107425957AImprove parallelismImprove throughput performanceKey distribution for secure communicationSecret communicationCiphertextPassword
The invention discloses a password attacking method and apparatus, and a heterogeneous acceleration platform. The method is applied to the heterogeneous platform including a CPU terminal and an FPGA terminal. The method comprises the following steps: the FPGA terminal reads a pre-stored rainbow table and to-be-attacked ciphertext data; the FPGA terminal performs parallel processing on the to-be-attacked ciphertext data according to a preset password attacking algorithm to obtain to-be-selected password data; the FPGA terminal performs matching on the to-be-selected password data and the rainbow table according to a preset matching algorithm to find out an alternative password; and the FPGA terminal returns a completion signal to the CPU terminal. Therefore, according to the password attacking method and apparatus, and the heterogeneous acceleration platform, the FPGA is utilized to perform hardware acceleration of the password attacking algorithm, and the FPGA performs the password attacking algorithm in parallel, so the parallelism of the algorithm is improved, the throughput rate performance when the algorithm is executed is improved, and thus the performance of the password attacking algorithm based on the rainbow table is improved; and furthermore, the redundant fine graining of the FPGA terminal is parallel, so the hardware cost is relatively low.
Owner:SUZHOU LANGCHAO INTELLIGENT TECH CO LTD
Hash value password recovering method and device
InactiveCN103400072AShorten recovery timeDigital data authenticationSpecial data processing applicationsRestoration methodPassword
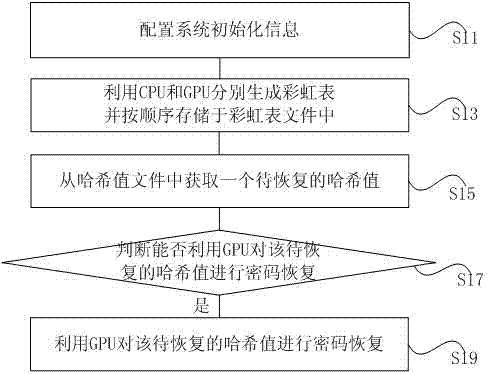
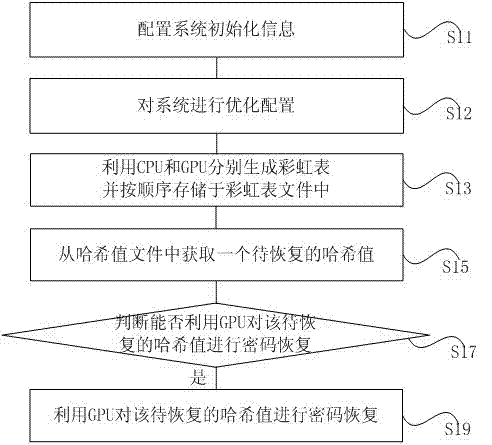
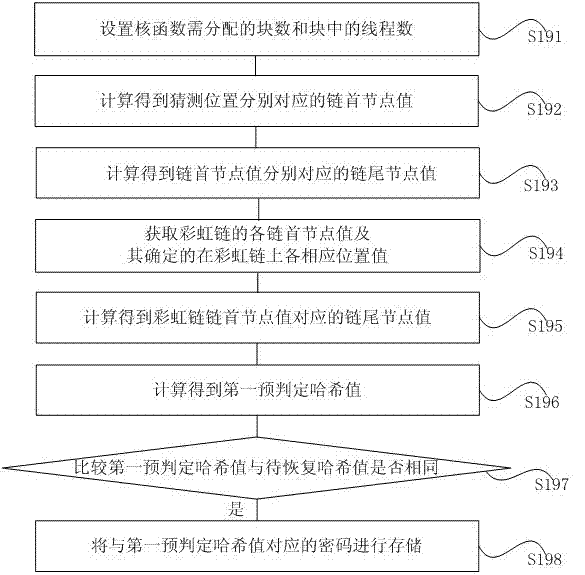
The invention provides a Hash value password recovering method and device. The method comprises the steps of configuring system initialization information; generating rainbow tables by means of a CPU and a GPU and storing the rainbow tables in a rainbow table file in sequence; acquiring a Hash value to be recovered from a Hash value file under the circumstance that the parameter of any one of the rainbow tables in the rainbow table file is matched with the parameter of a preset rainbow table; judging whether password recovery can be carried out on the Hash value to be recovered by means of the GPU; carrying out password recovery on the Hash value to be recovered by means of the GPU if the judging result is yes till passwords of all Hash values to be recovered in the Hash value file are recovered, wherein the system initialization information comprises the Hash algorithm type, information relevant to the rainbow tables and the like. According to the Hash value password recovering method and device, the rainbow tables are generated by means of the CPU and the GPU, the Hash value passwords are recovered through the combination of the GPU and the rain table algorithm, and therefore the time for recovering the Hash value passwords can be greatly shortened.
Owner:XIAMEN MEIYA PICO INFORMATION
Big data rainbow table based decryption method and device
InactiveCN106712928AIncrease generation speedSave search timeEncryption apparatus with shift registers/memoriesUser identity/authority verificationPlaintextRainbow
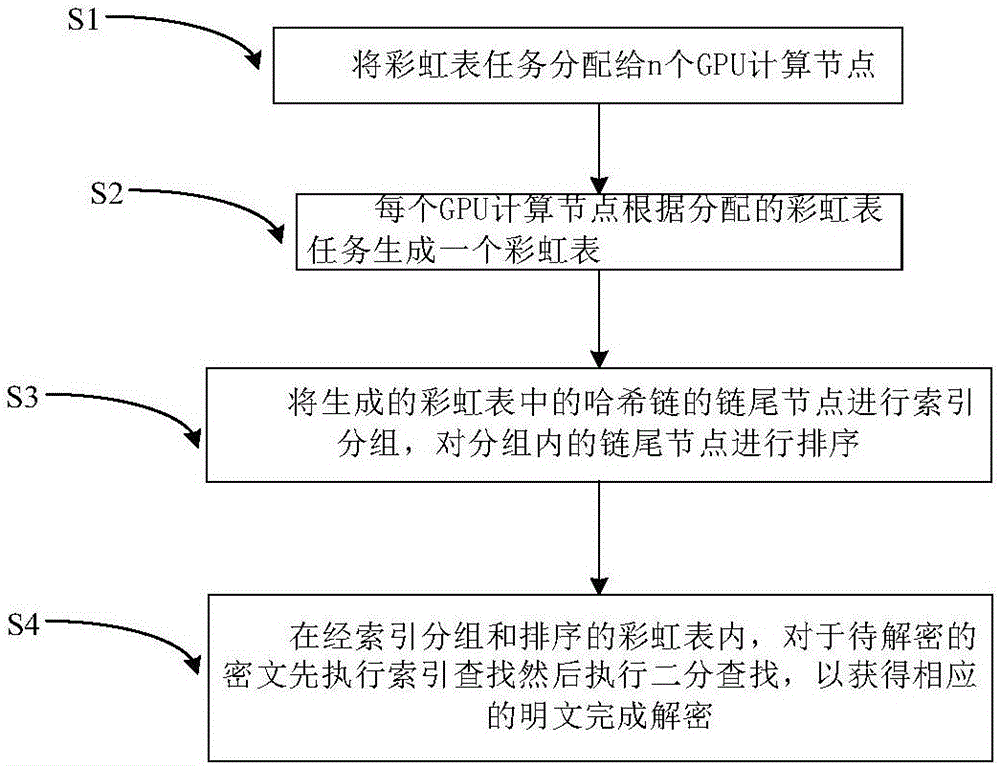
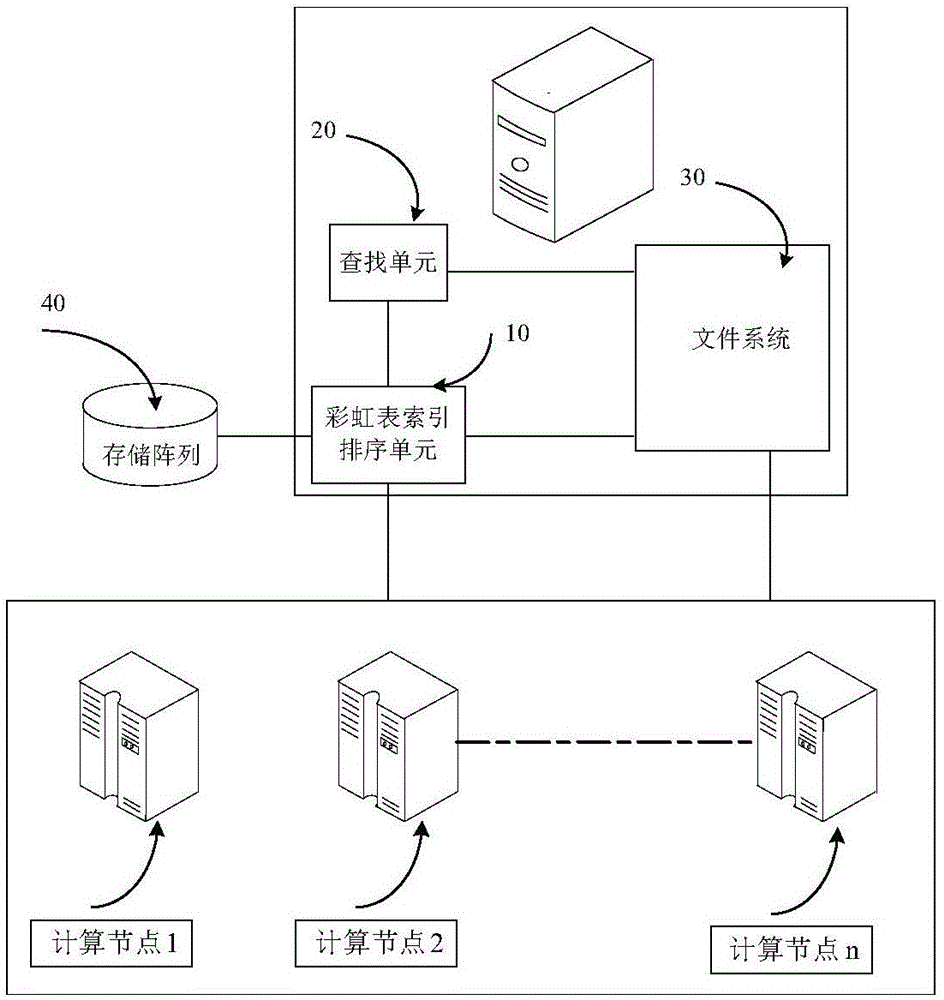
The invention discloses a big data rainbow table based decryption method and device. The decryption method comprises the steps that rainbow table tasks are allocated to n GPU (Graphic Processing Unit) computing nodes, wherein n is an integer which is greater than 1; each GPU computing node generates a rainbow table; index grouping is performed on chain end nodes of Hash chains in the generated rainbow tables, and sorting the chain end nodes in each group; and in the index grouped and sorted rainbow tables, firstly performing index searching on a ciphertext to be decrypted, and then executing binary searching so as to acquire a corresponding plaintext to complete decryption. For letter-number combination passwords with 1-12 bits, the Hash chains in the rainbow tables can be generated in a parallel manner via a plurality of GPUs by using an encryption result ciphertext, so that the generation speed of the rainbow tables is greatly improved. In addition, index sorting is performed on the generated rainbow tables, so that the rainbow table searching time in a decryption stage is greatly shortened, and the decryption time is greatly shortened.
Owner:YUNNAN POWER GRID CO LTD ELECTRIC POWER RES INST
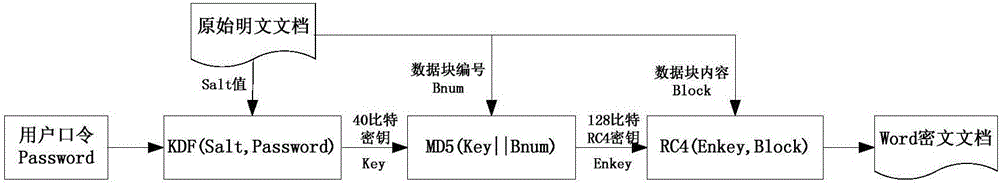
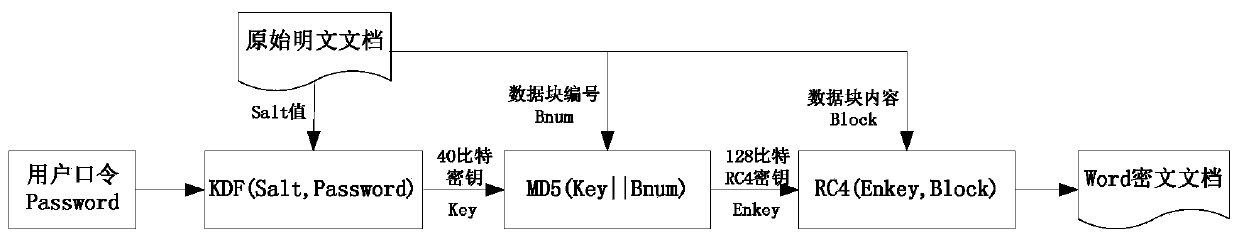
Rapid restoring method for Word encrypted documents
ActiveCN106778292AFix irreversible problemsSolve the problem that cracking timeliness cannot meet actual needsDigital data protectionPasswordCiphertext
The invention discloses a rapid restoring method for Word encrypted documents. The method comprises steps as follows: step one, a secret key rainbow table of restored Word documents is established; step two, decryption secrete keys of the encrypted documents are decoded; step three, original plaintext documents are reconstructed by use of the decryption secrete keys and structure information of Word documents. The method has the positive effects as follows: the rainbow table for decrypting the secrete keys is only needed to be generated once, and the generated rainbow table is suitable for restoring all encrypted documents; restoring is not related to the complexity of encryption passwords of encrypted documents, and the defect that a long password cannot be cracked with an existing document cracking method is overcome; Word encrypted documents of version 2003 can be effectively restored, and the success rate reaches 99% or above; the encrypted documents can be rapidly restored, tests prove that the average restoring time of the encrypted documents is within 3 min under the computation ability of ordinary desktop computers (with the basic frequency being 3.0 GHz or above), and actual demands for real-time decryption can be well met.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
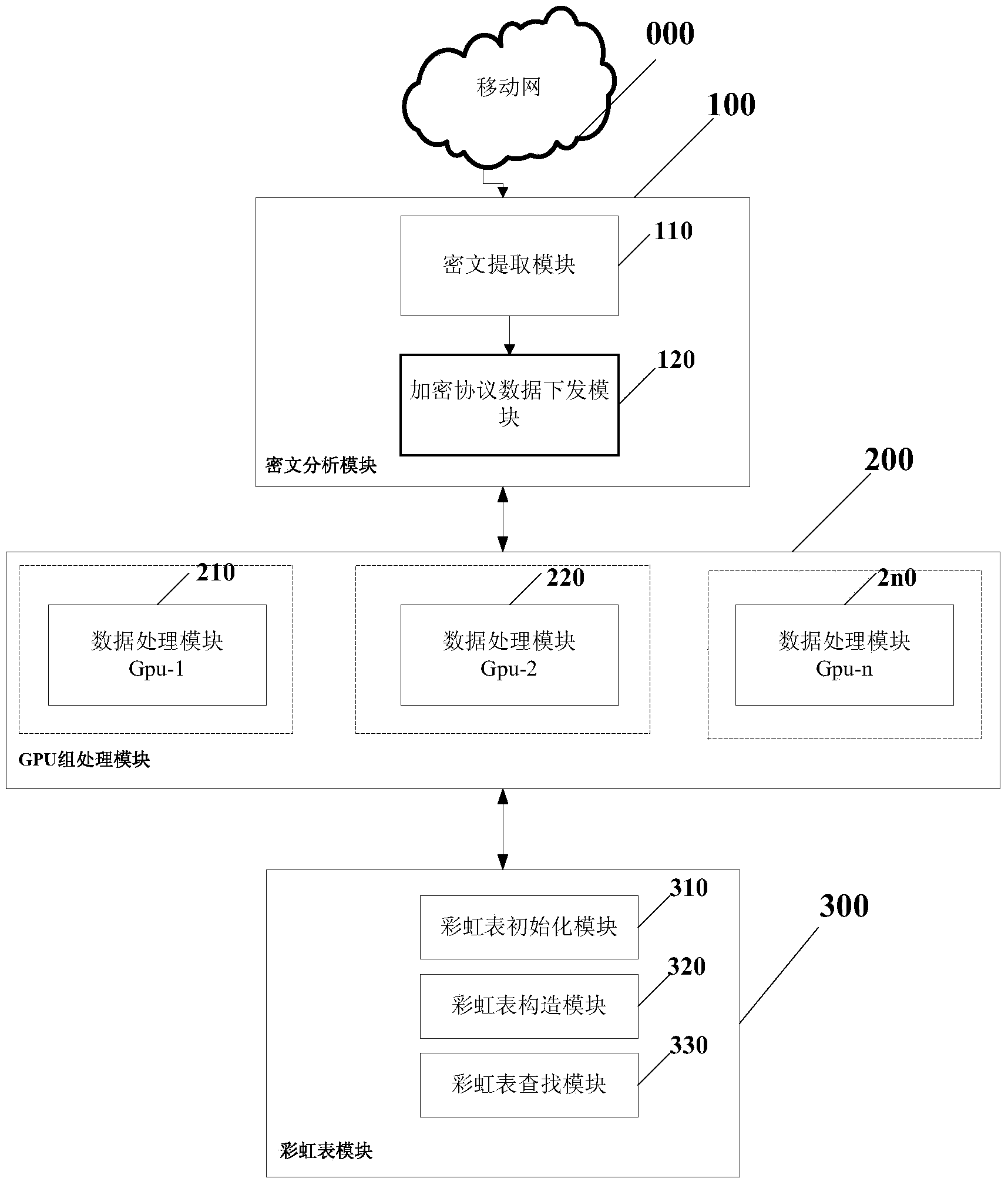
Encryption and analysis system based on distributed GPU and rainbow table and method of encryption and analysis system
InactiveCN103714300AIncrease the speed of computational analysisIncrease or decrease the numberDigital data protectionDistributed object oriented systemsCiphertextParallel computing
The invention discloses an encryption and analysis system based on a distributed GPU and a rainbow table and a method of the encryption and analysis system, and belongs to the field of mobile network encryption protocol data restoration. The system comprises a cipher text analyzing module (100), a GPU set processing module (200) and a rainbow table module (300), wherein the cipher text analyzing module (100) interacts with the GPU set processing module (200) so as to achieve extraction of front end cipher texts and distribution of encryption data of devices of the GPU; the GPU set processing module (200) interacts with the rainbow table module (300) so that the GPU can construct the rainbow table and search by means of the constructed rainbow table, and original texts are quickly restored. The system has high speed and extendibility and is suitable for mobile Internet security products.
Owner:WUHAN HONGXU INFORMATION TECH
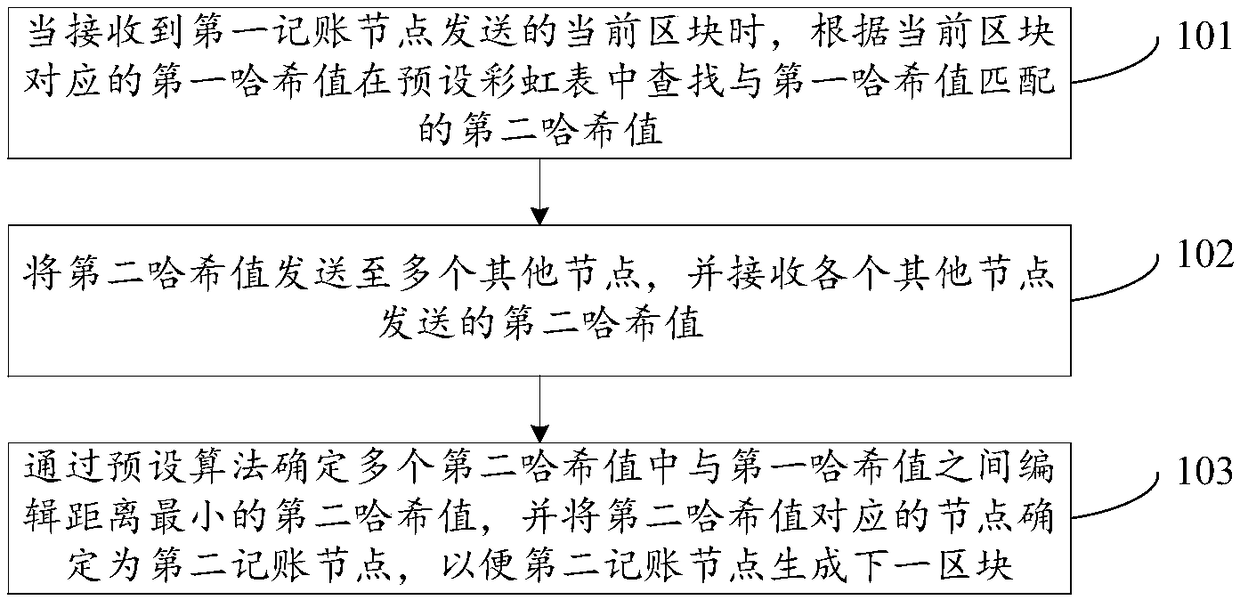
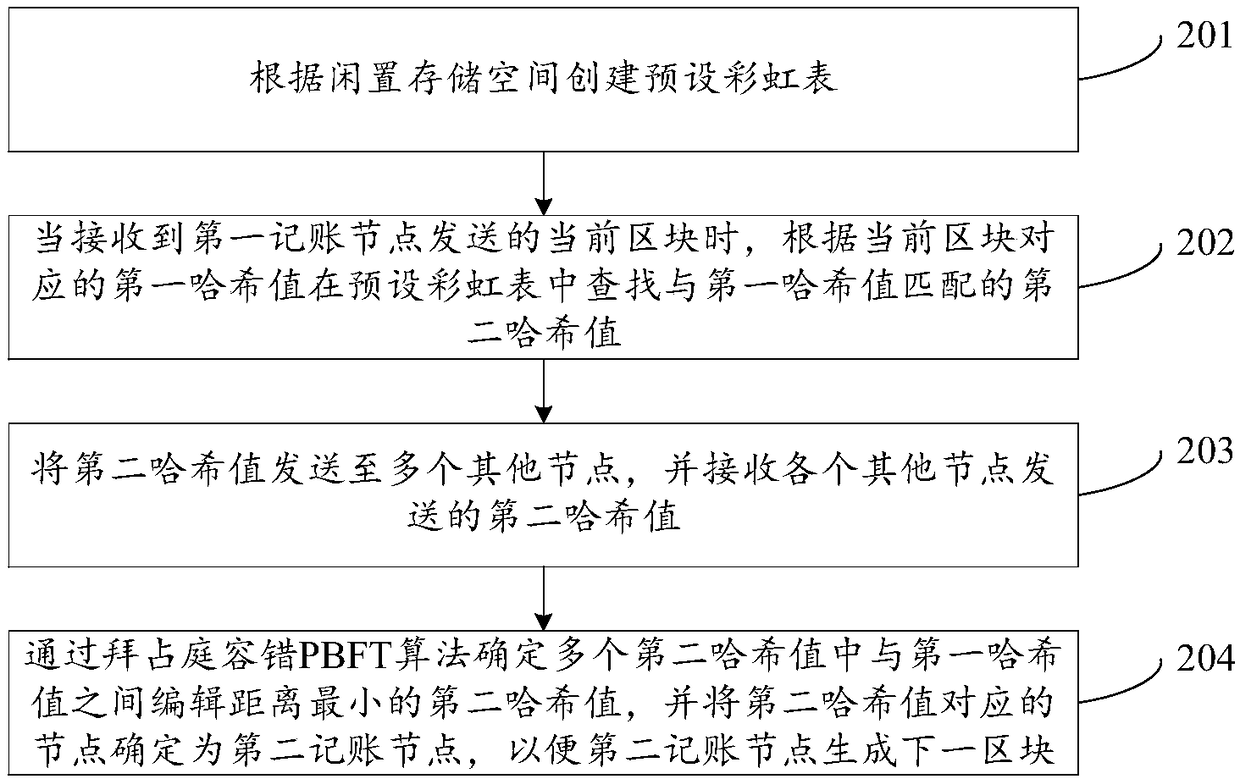
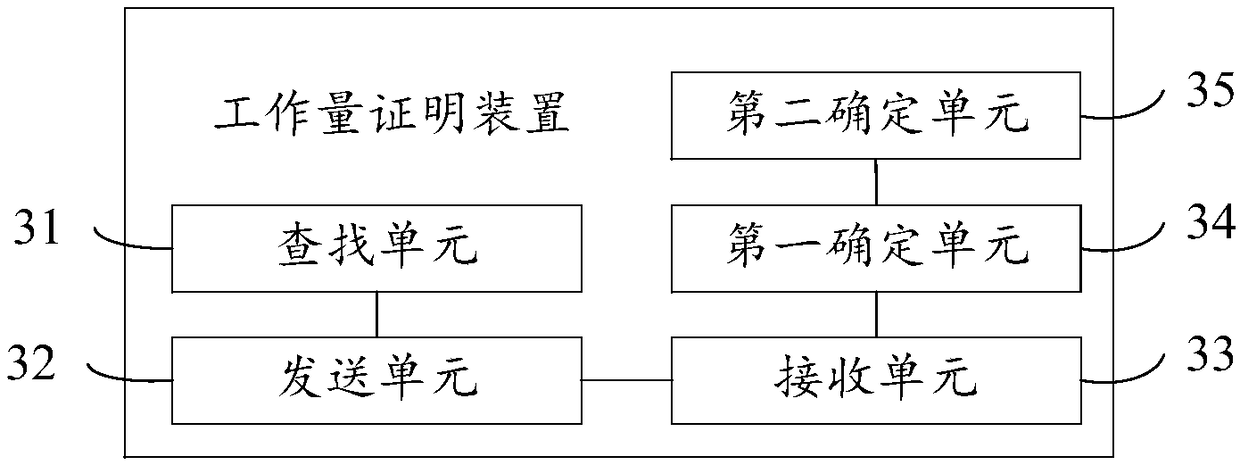
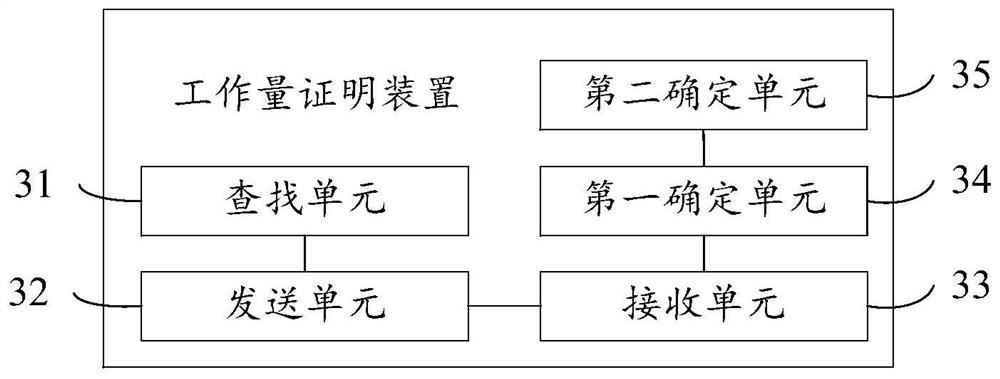
Proof-of-work method and device
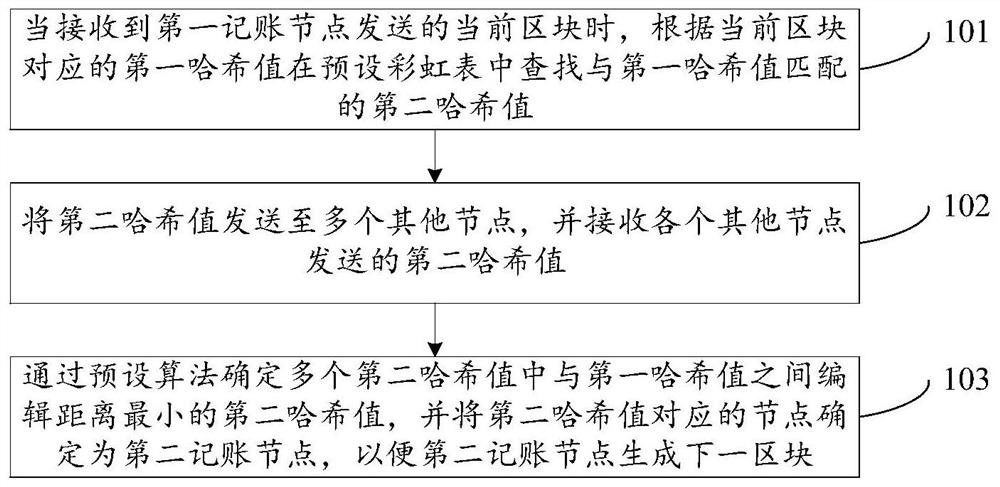
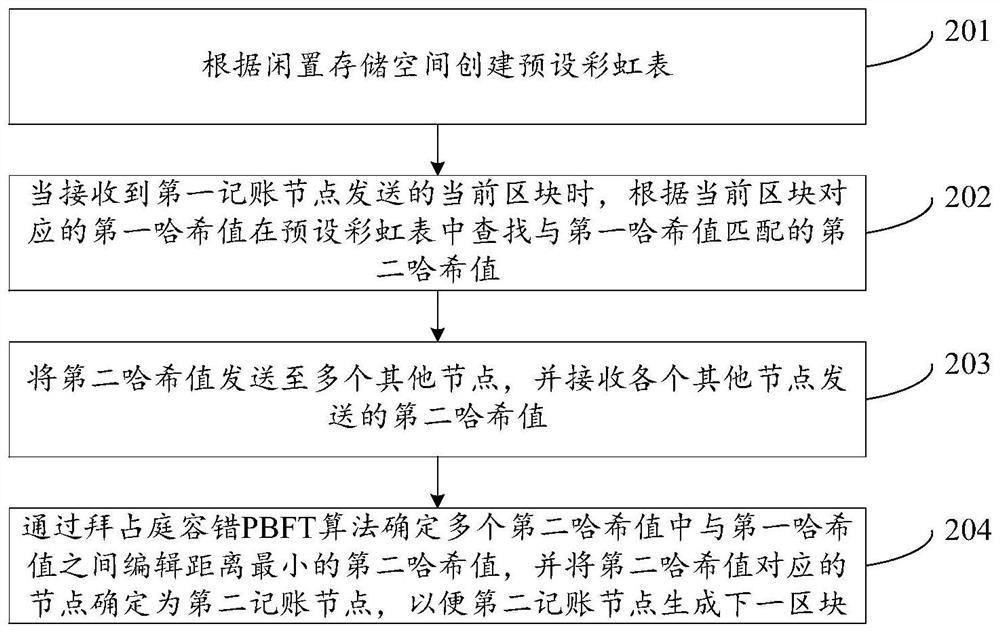
ActiveCN108712486ASmall amount of calculationImprove selection efficiencyTransmissionSpecial data processing applicationsRainbow tableChain system
The invention discloses a proof-of-work method and device, related to the technical field of data processing. The proof-of-work method and device is used to solve the problems in the prior art that the selection efficiency of selecting an accounting node is low and the computing resources of each node is occupied overly in a block chain system adopting the traditional proof-of-work mechanism. Theproof-of-work method comprises the following steps: finding a second hash value matching a first hash value in a preset rainbow table according to the first hash value corresponding to a current blockwhen the current block sent by a first accounting node is received; sending the second hash value is to a plurality of other nodes, and receiving the second hash values sent by other nodes; and confirming the second hash value which has the minimum editing distance with the first hash value in a plurality of second hash values through a preset algorithm, and confirming the node corresponding to the second hash value as a second accounting node, so that the second accounting node generates the next block. The proof-of-work method and device is applicable to the process of selecting the accounting node under the block chain system.
Owner:BEIJING QIHOO TECH CO LTD
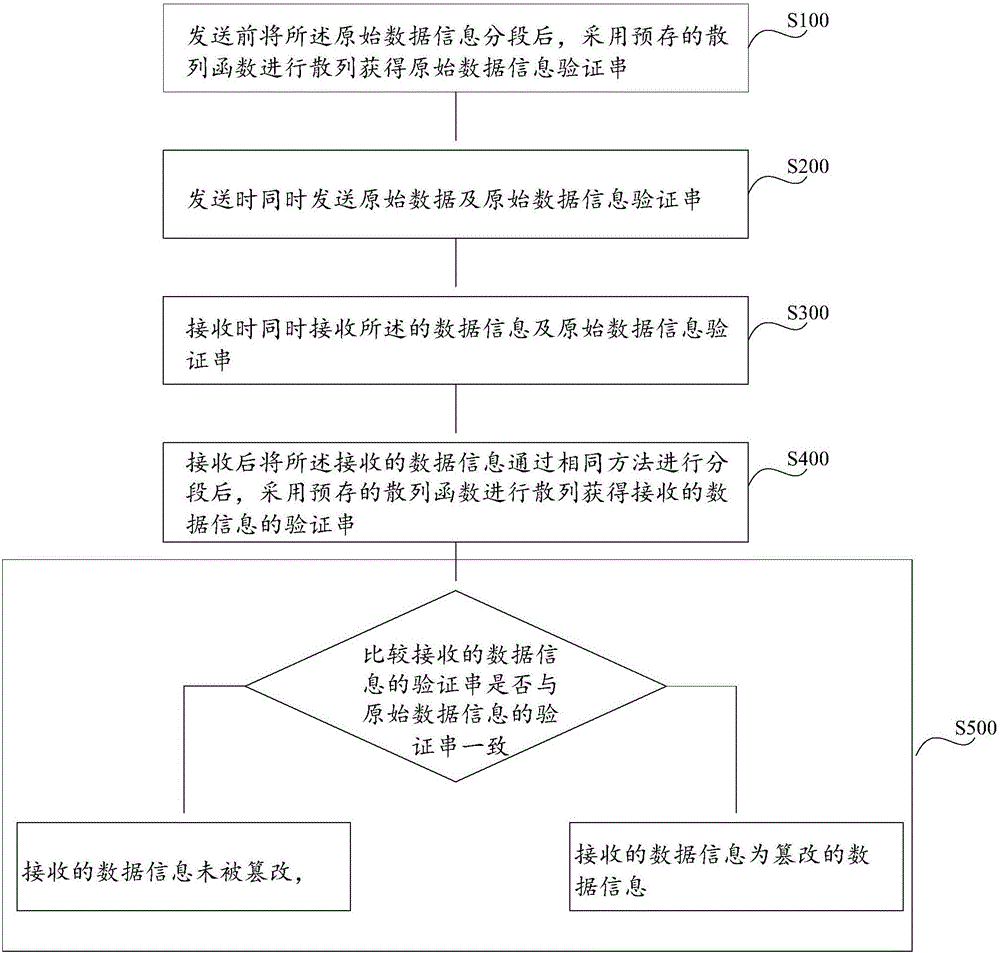
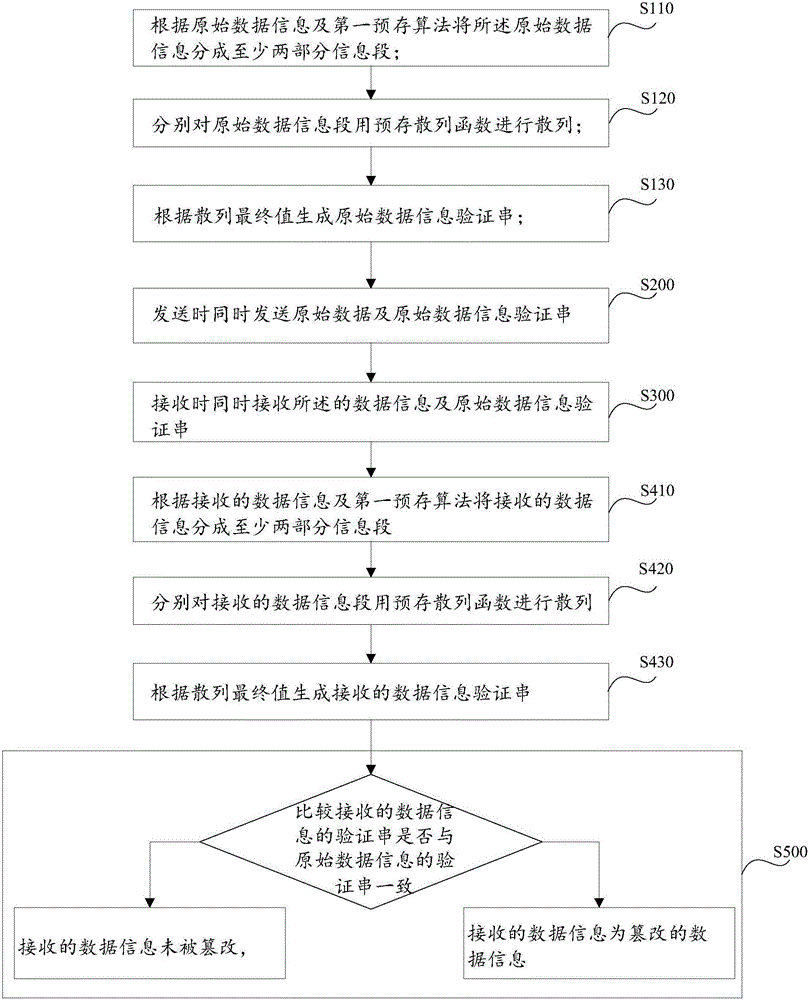
Data tamper-proofing method and system
InactiveCN106570423APrevent Collision AttacksStop falsified dataDigital data protectionTamper resistanceThird party
The invention discloses a data tamper-proofing method comprising the following steps of after original data information is segmented before sending, hashing the segmented information by using a pre-stored hash function to acquire an original data information verification string; synchronously sending the original data and the original data information verification string when in sending, synchronously receiving the sent data information and original data information verification string when in receiving; after the data information and the original data information verification string are received, segmenting the received data information, and then hashing the segmented information by using the pre-stored hash function to acquire a received data information verification string; and judging whether the received data information verification string is accordant with the original data information verification string by comparison, if yes, determining that the received data information is not tampered, and otherwise, determining that the received data information is tampered. The invention also provides a data tamper-proofing system. According to the method and the system provided by the invention, the difficulty of tampering the data by a third party is greatly increased, a collision attack from the third party with the aid of a rainbow table is effectively prevented, data falsification of a user is prevented, and data transmission security is ensured.
Owner:PHICOMM (SHANGHAI) CO LTD
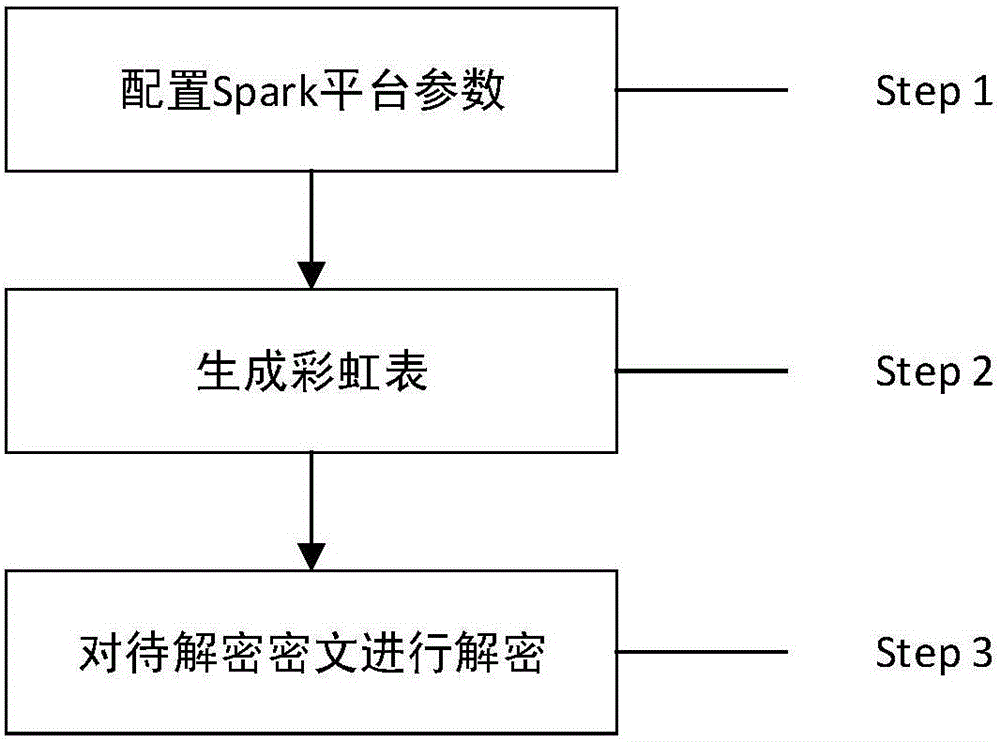
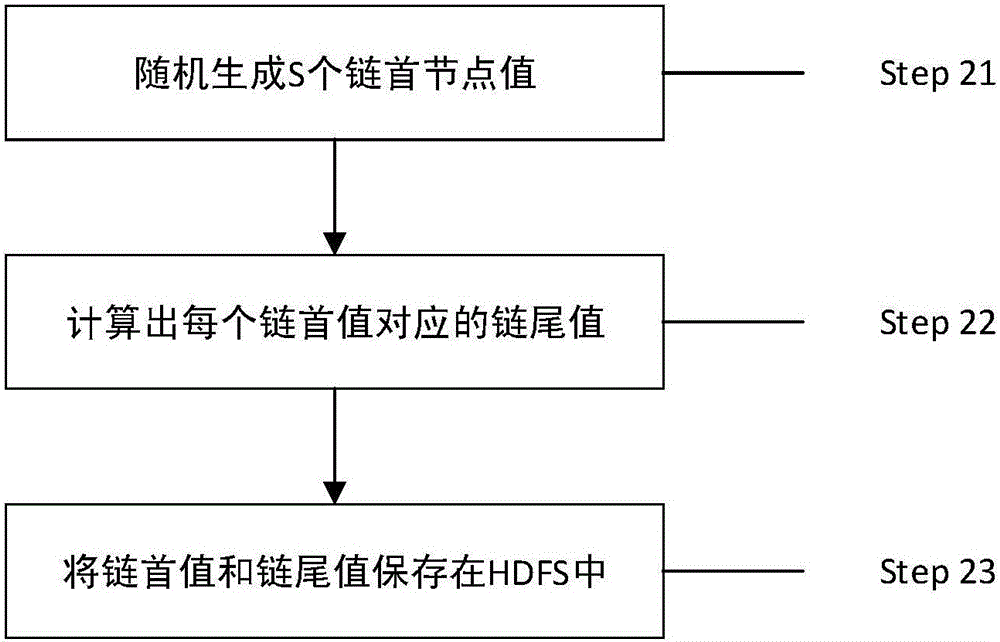
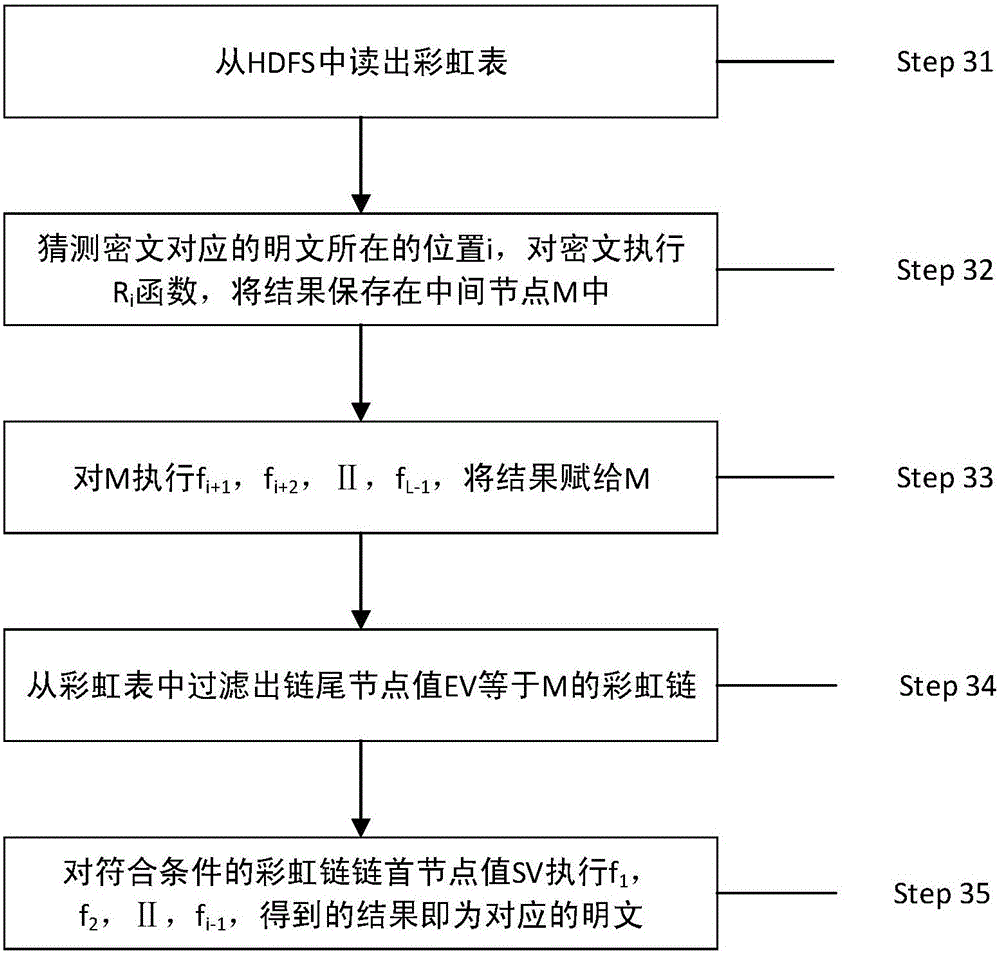
Spark platform-based password hash value recovery method and device
InactiveCN105933120ASpeed up the build processImprove efficiencyKey distribution for secure communicationUser identity/authority verificationComputer hardwareRecovery method
The invention discloses a Spark platform-based password hash value recovery method and device. The design method includes a rainbow table data generation step and a rainbow table decryption step. According to the method, the first-of-chain node value of each rainbow chain is recorded as an SV (Start Value), and the last-of-chain node value of each rainbow chain is recorded as an EV (End Value); based on the processing capability of the Spark platform for large-scale data, a map function is utilized to effectively calculate EV corresponding to SV, so that rainbow chains can be generated, and are stored in an HDFS (Hadoop distributed file system), and rainbow table data generation is completed; and a filter function is utilized to find all SV corresponding to a ciphertext to be decrypted, and a foreach function is called to generate complete rainbow chains according to each SV, and the ciphertext can be decrypted.
Owner:TSINGHUA UNIV
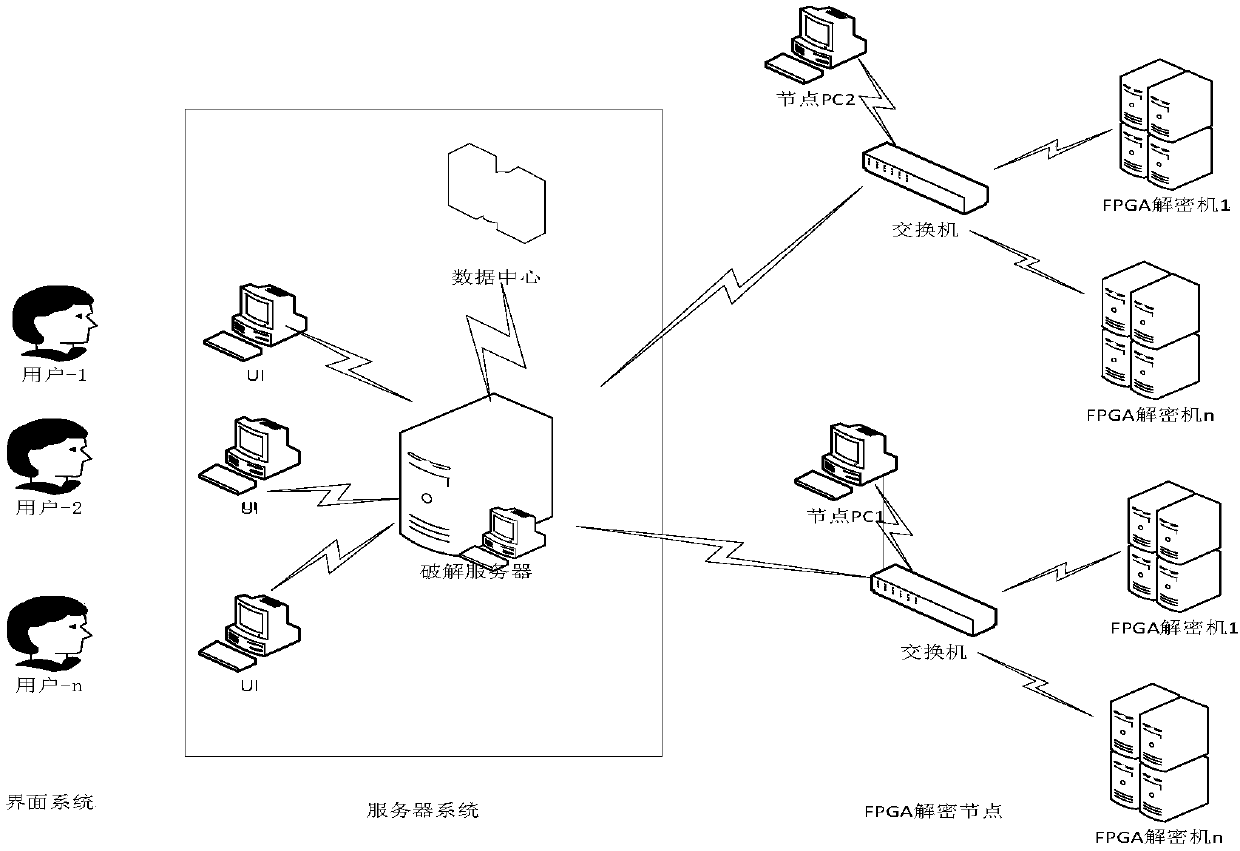
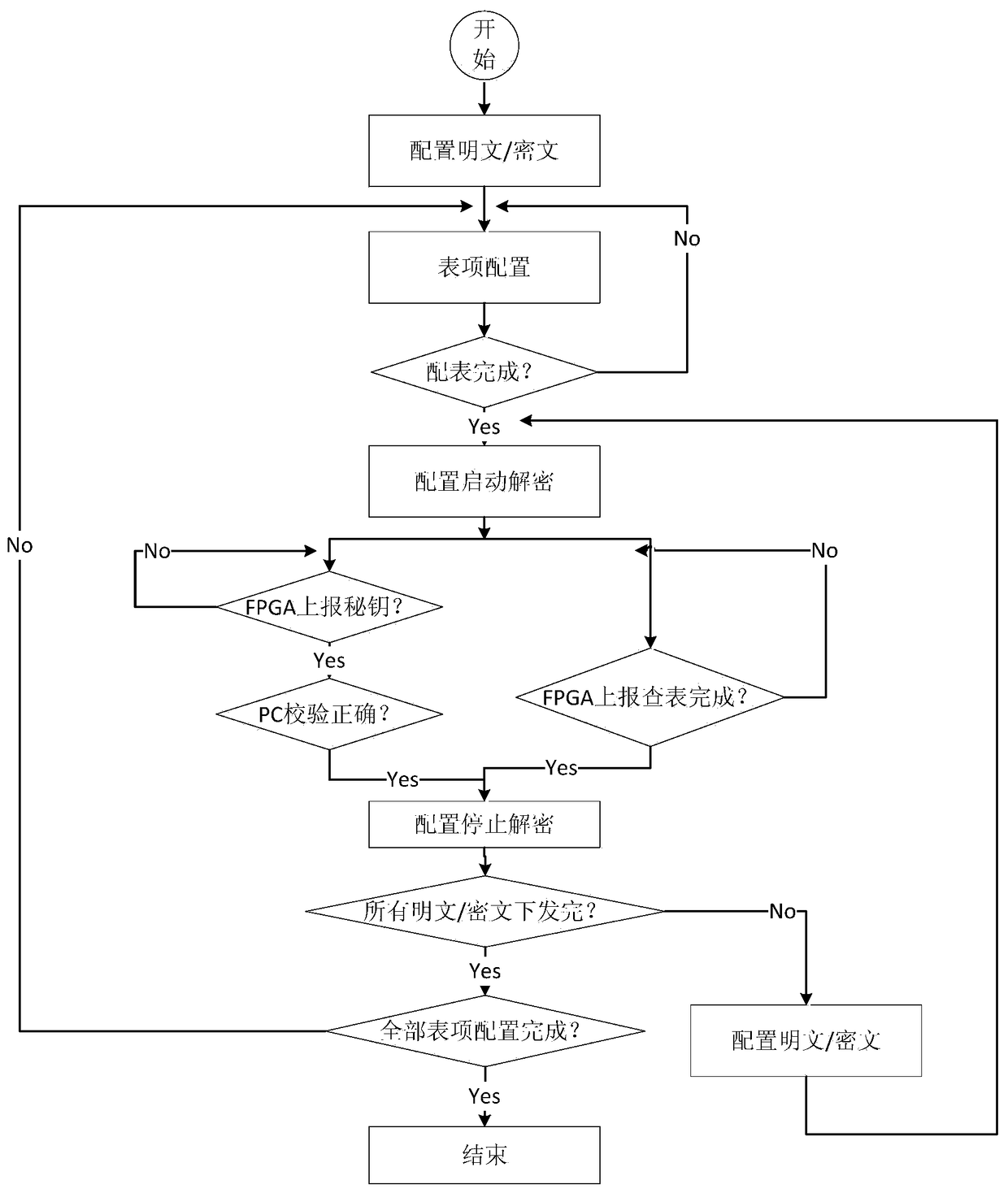
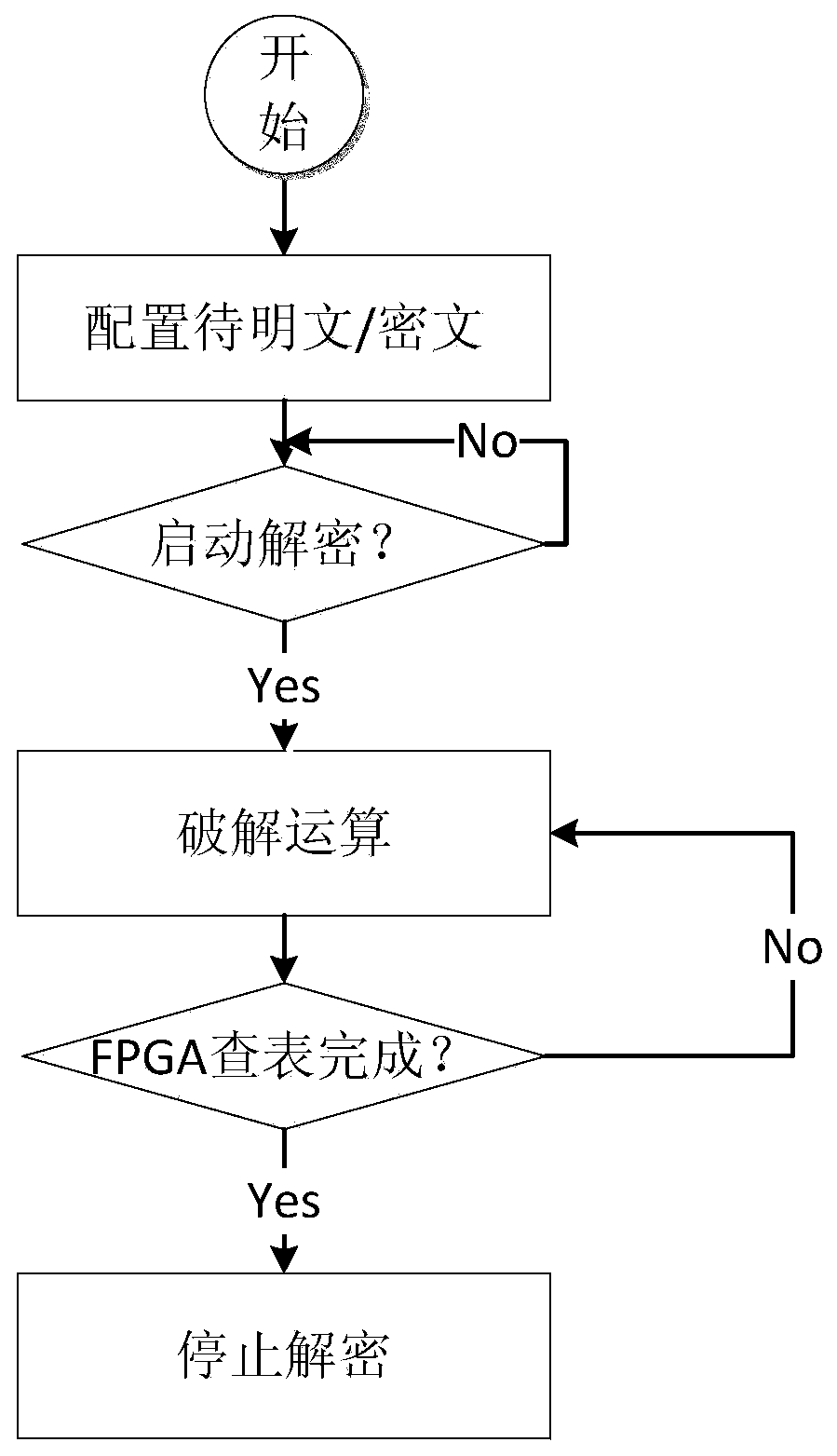
FPGA-based distributed multi-strategy decryption system and method thereof
InactiveCN107566348AAdvantage decryption performanceAdvantage power consumptionEncryption apparatus with shift registers/memoriesDigital data processing detailsCiphertextRainbow table
The invention discloses a FPGA-based distributed multi-strategy decryption system and a method thereof; the decryption system comprises interface system parts, a server system part and FPGA decryptionnode parts; the interface system part refers to an application interface for user interactions; a user can submit a to-be-decrypted cryptograph or file through the application interface, and obtainsa decrypted result through the interface; the server system part is used for releasing and controlling a task amount in the whole decryption process, and simultaneously connected with a plurality of interface system parts in the front end and a plurality of FPGA decryption node parts in the rear end; the FPGA decryption node part serves as the decryption operation core unit, and comprises a node PC jointed with the server and a plurality of FPGA decoders hung under the node PC; the FPGA decoder comprises a solid state hard disk so as to store rainbow table data of certain specific algorithm.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
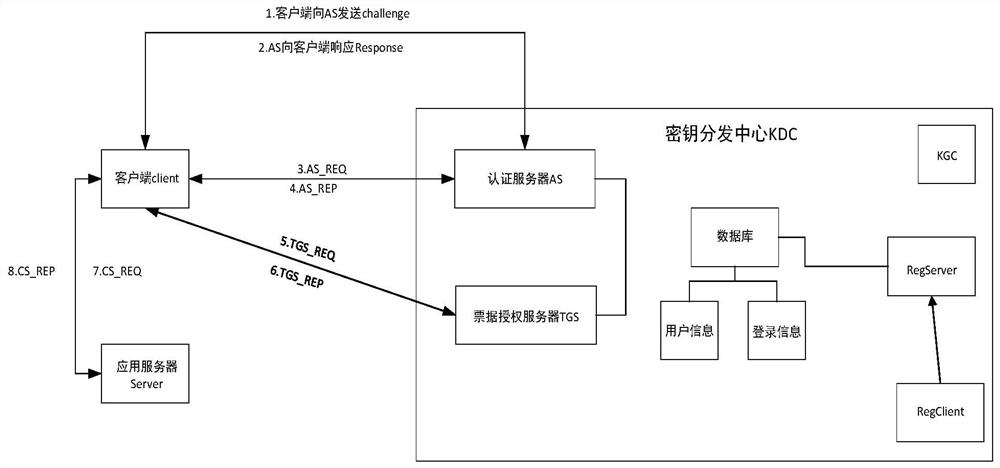
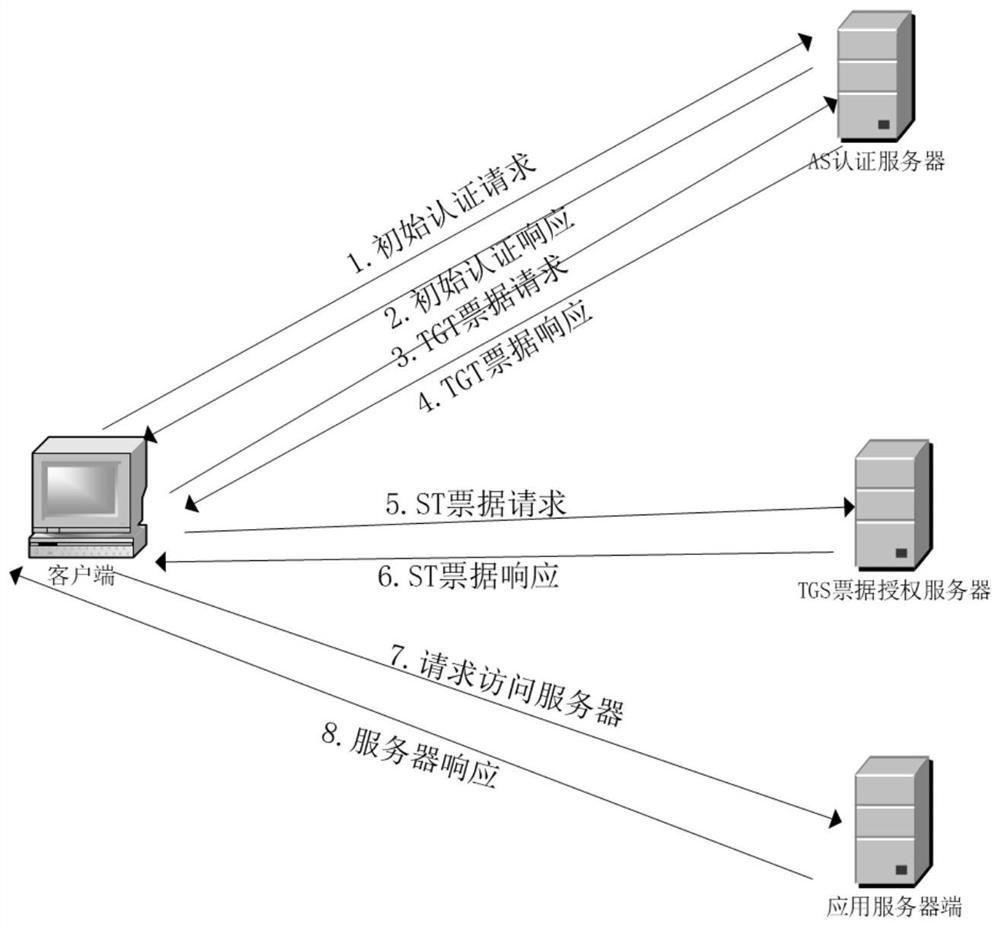
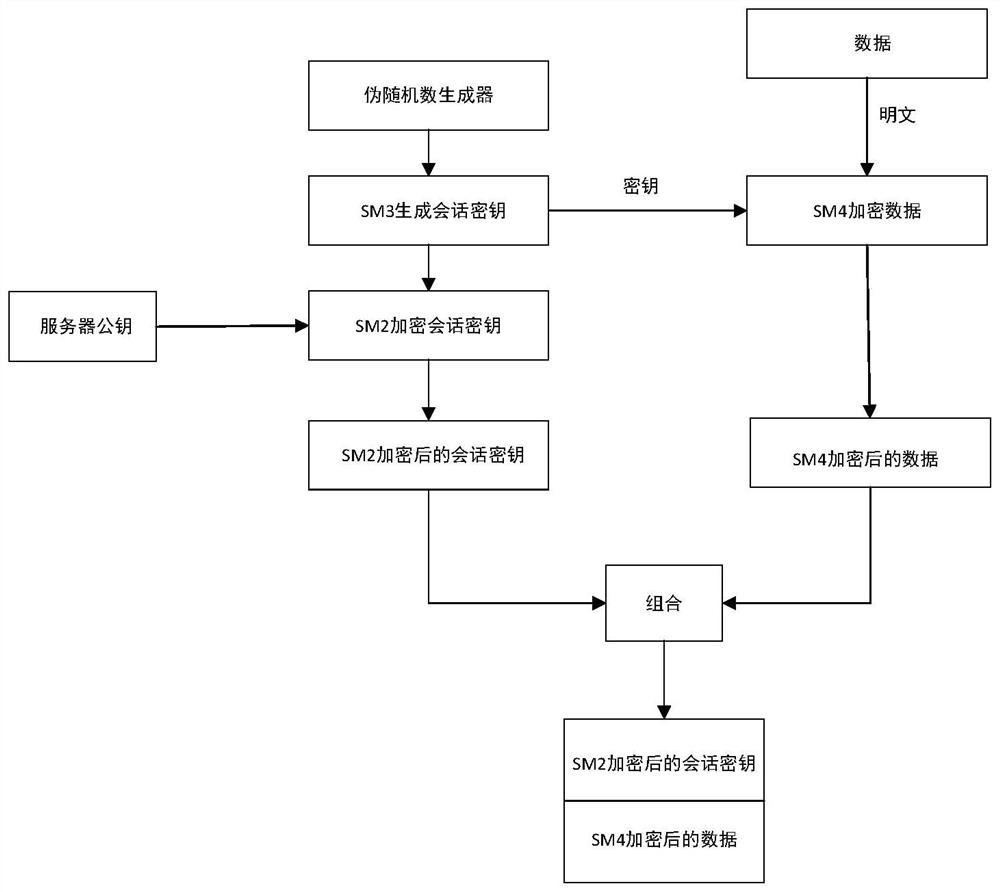
Kerberos identity authentication protocol improvement method based on national cryptographic algorithm
InactiveCN113612797AImprove securityImprove efficiencyKey distribution for secure communicationMultiple keys/algorithms usageAlgorithmEngineering
The invention discloses a Kerberos identity authentication protocol improvement method based on a national cryptographic algorithm, a traditional Kerberos protocol is improved by using session key dynamics and a hybrid cryptosystem based on the national cryptographic algorithm, and the improved Kerberos protocol comprises a registration process and an authentication process; wherein the authentication process comprises three stages: mutual authentication between the client and the AS; the client communicates with the TGS; the client communicates with the application server; a dynamic key is used as a shared key between the client and the AS, and encryption and decryption are carried out by adopting a hybrid cryptosystem based on a national cryptographic algorithm in an authentication process. According to the method, rainbow table attacks, blasting attacks and counterfeit user attacks caused by weak passwords can be effectively resisted, and replay attacks, man-in-the-middle attacks and the like caused by time synchronization can be effectively resisted, so that the security and the efficiency of a Kerberos identity authentication protocol are improved.
Owner:JINLING INST OF TECH
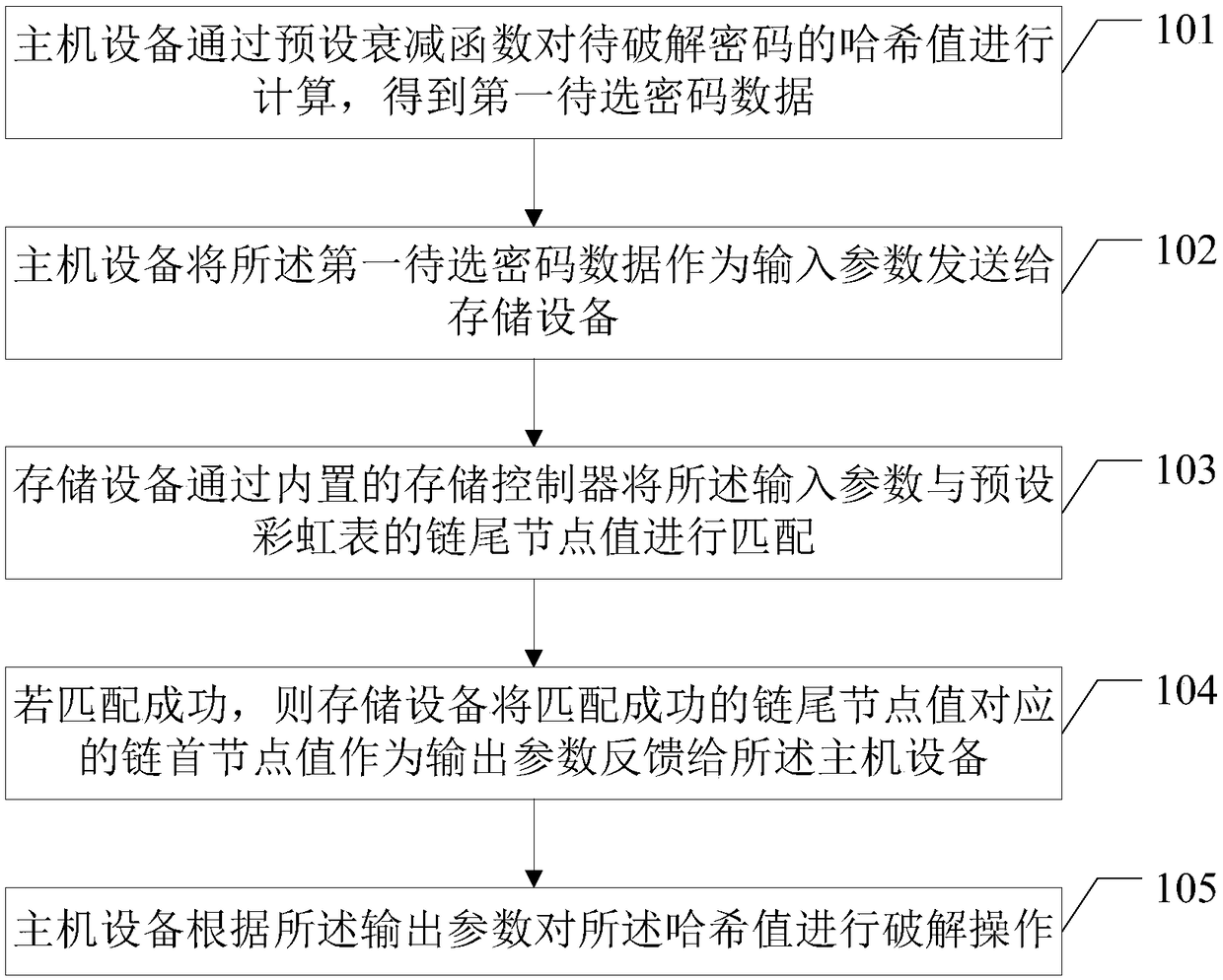
Password cracking method, host device and storage device
InactiveCN108416208AIncrease capacitySimple structureKey distribution for secure communicationEncryption apparatus with shift registers/memoriesControl storePassword
The invention discloses a password cracking method, a host device and a storage device, which achieve the purpose of increasing the cracking speed. The method comprises the steps that the host devicecalculates a hash value of a to-be-cracked password through a preset attenuation function to obtain first to-be-selected password data; the host device sends the first to-be-selected password data asan input parameter to the storage device; and the host device receives an output parameter fed back by the storage device and performs cracking operation on the hash value according to the output parameter, wherein the output parameter is a first-of-chain node value corresponding to an end-of-chain node value matched successfully after the storage device matches the input parameter with the end-of-chain node value of a preset rainbow table through an internal storage controller.
Owner:SHENZHEN DAPU MICROELECTRONICS CO LTD
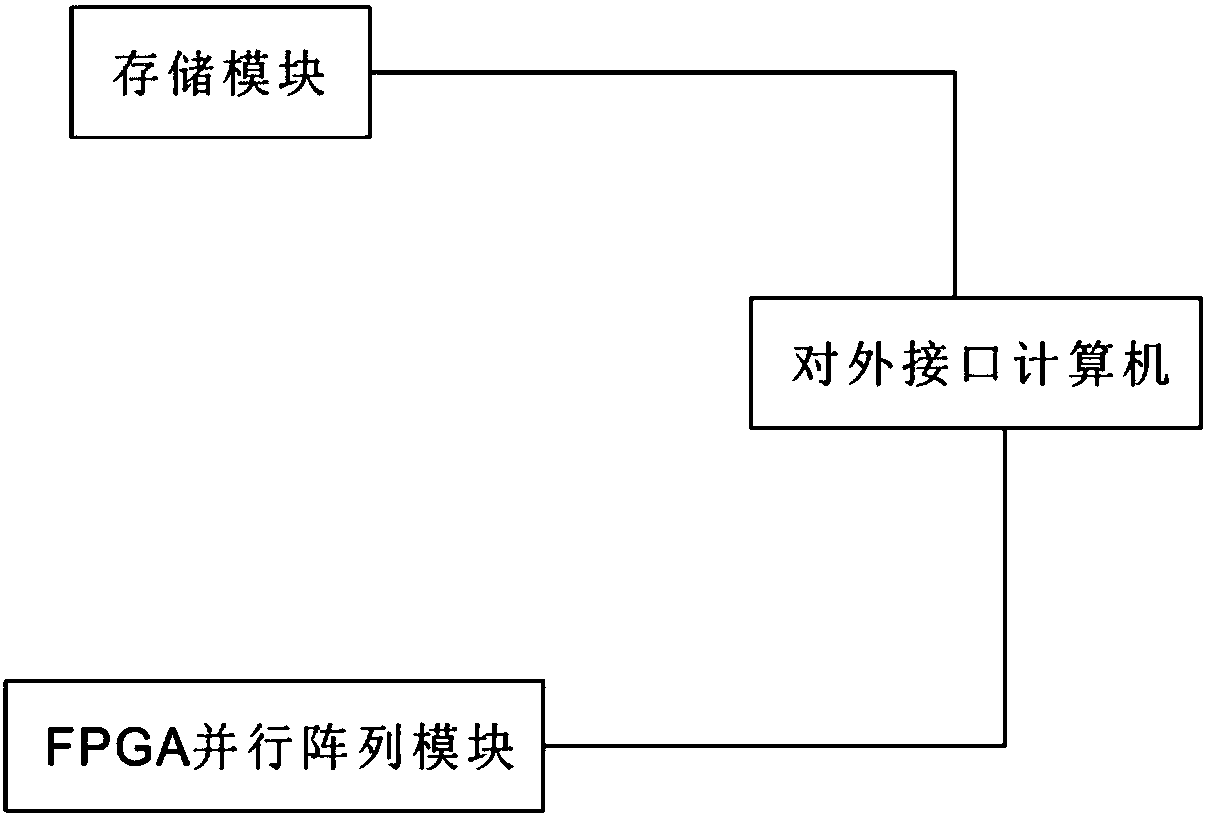
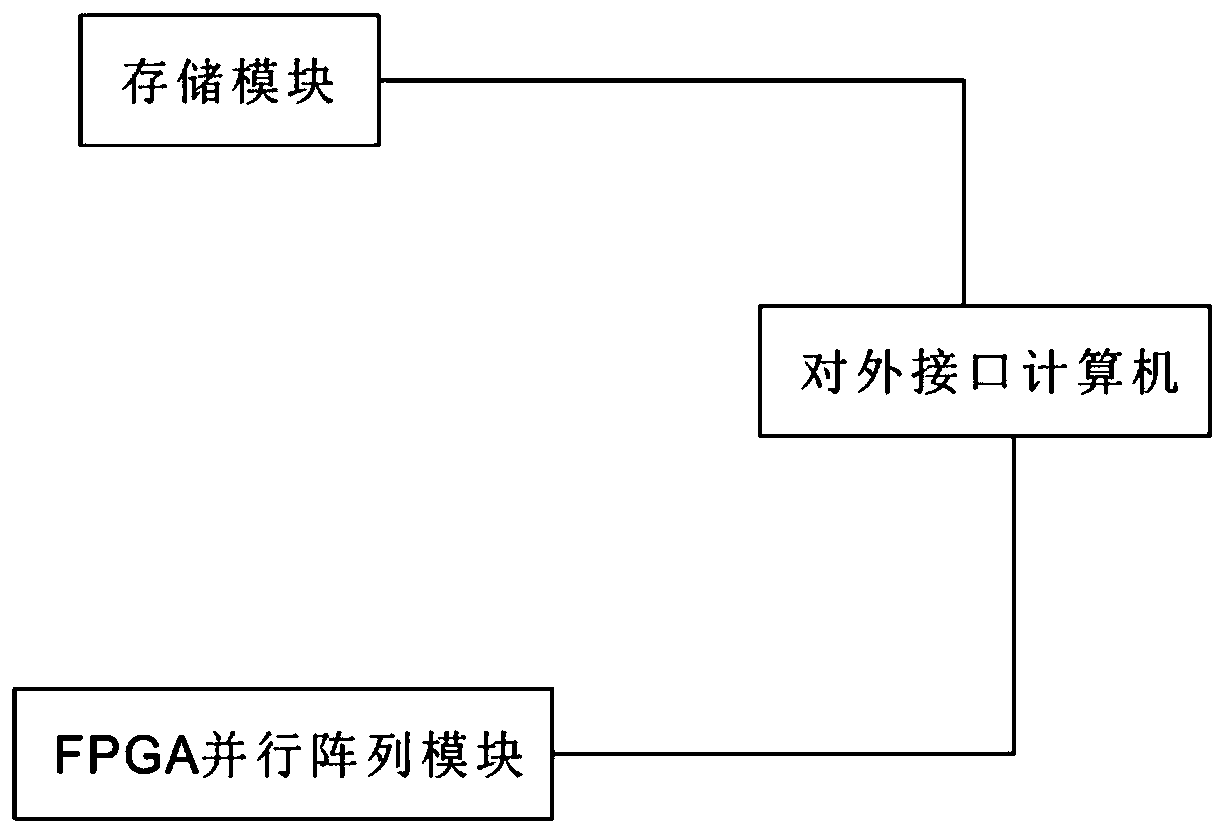
High-speed time-space computing platform
ActiveCN107590380ADeciphering speed is fastDeciphering speed increasedDigital data authenticationRainbowPassword
The invention discloses a high-speed time-space computing platform. The platform comprises a storage module, an FPGA parallel array module and an external interface computer, wherein the storage module and the FPGA parallel array module are both connected to the external interface computer; the storage module is used for compressing and storing a pre-computed result in the form of a rainbow tableand parallelly querying impact points through an SSD; the FPGA parallel array module is used for parallelly distributing encryption to each independent FPGA chip, and the impact points in the rainbowtable are searched for through parallel running of multiple FPGA chips; and the external interface computer is used for providing decoding of MD5, Sha1, Sha256 and a DES in a socket mode. According tothe platform, a rainbow table processing scheme is adopted to research and develop the high-speed time-space computing platform on the basis of an existing result FPGA parallel array module in combination with multiple years of password decoding experience, a time-space balance mode is adopted for password decoding, a password plaintext is quickly decoded within a certain range, and a security department is assisted in quickly obtaining evidence and handling a case.
Owner:NEXWISE INTELLIGENCE CHINA LTD
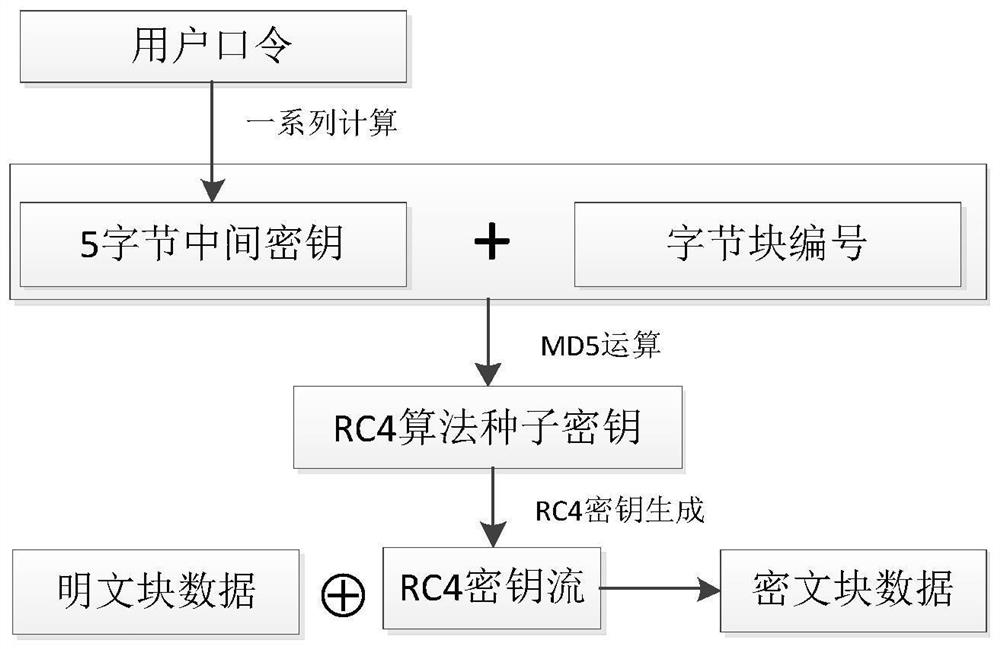
Excel ciphertext document recovery method, computer equipment and storage medium
InactiveCN112287374AAchieve recoveryAvoid the disadvantage of being uncrackableDigital data protectionRC4Ciphertext
The invention discloses an Excel ciphertext document recovery method, computer equipment and a storage medium. The document recovery method comprises the following steps: constructing a key rainbow table of an Excel document: constructing the rainbow table according to an RC4 encryption algorithm adopted by the Excel document; decoding a decryption key of the Excel ciphertext document: decoding anintermediate key of the Excel document by utilizing a rainbow table attack, and taking the intermediate key as the decryption key; decrypting and restoring the corresponding Excel plaintext document:decrypting and restoring the plaintext document by utilizing the decrypted decryption key and the Excel document ciphertext data storage structure information. According to the method, the rainbow table for cracking the secret key only needs to be constructed once, the generated rainbow table is suitable for secret key decoding of all Excel ciphertext documents, and therefore recovery of the Excel ciphertext documents is realized. The document recovery method is irrelevant to the complexity of the document encryption password, the defect that a complex password cannot be cracked in an existing document cracking method is overcome, and the RC4 encrypted Excel document can be effectively recovered.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
An encryption method and device
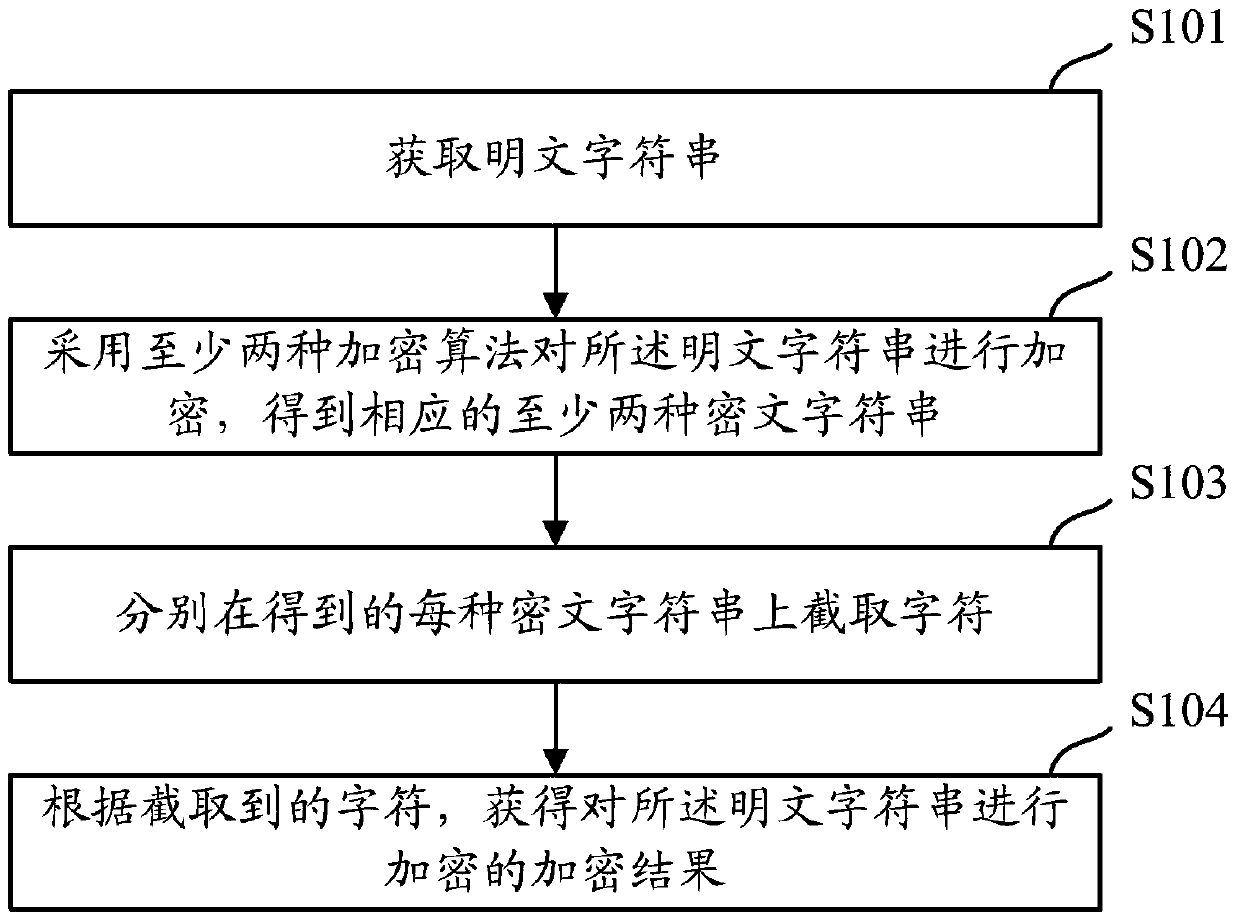
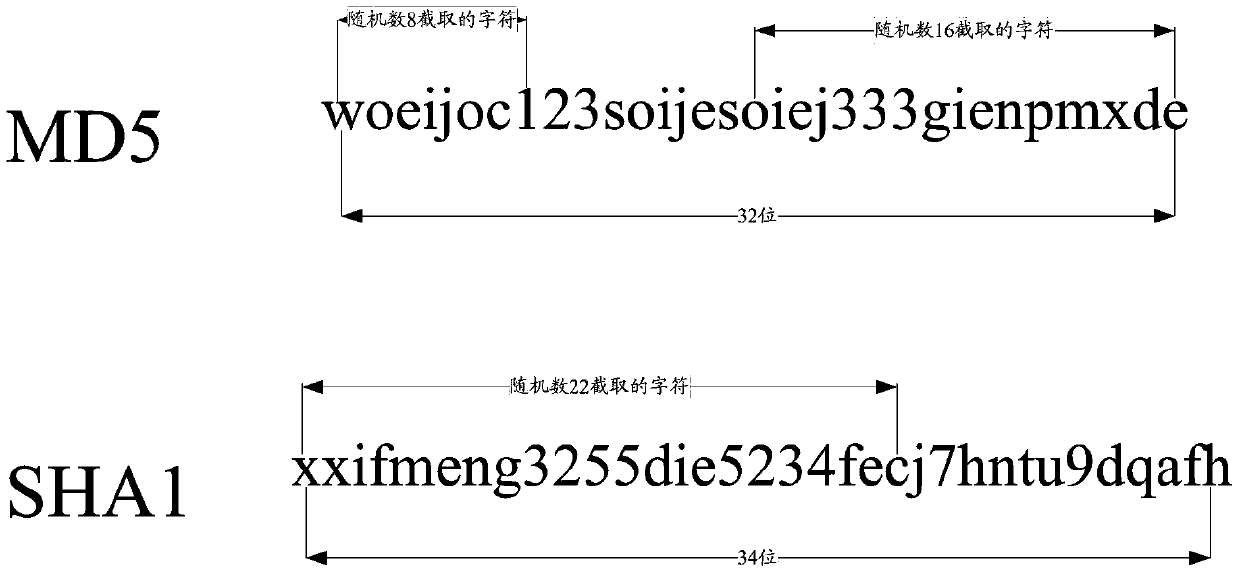
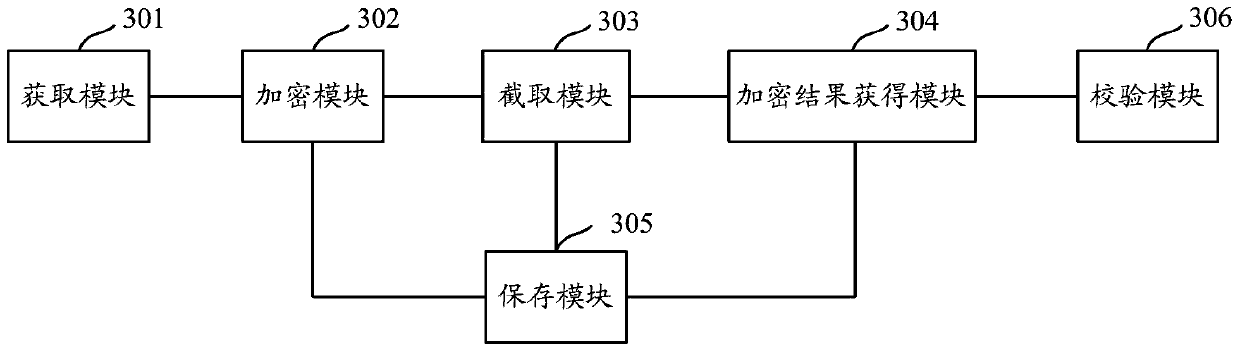
ActiveCN106549756BAvoid crackingImprove securityMultiple keys/algorithms usageComputer hardwarePlaintext
The present invention provides an encryption method and apparatus. The objective of the invention is to solve the problem that an encryption mode in the prior art may reduce the security of stored standard passwords. The method includes the following steps that: a plaintext character string is acquired; the acquired plaintext character string is encrypted through adopting at least two kinds of encryption algorithms, so that at least two corresponding ciphertext character strings can be obtained; characters are intercepted from each kind of obtained ciphertext character strings; and the encryption result of encryption performed on the plaintext character string can be obtained according to the intercepted characters. The encryption result obtained by using the above method contains the ciphertext character strings obtained after the encryption is performed with the different encryption algorithms, and the ciphertext character strings contained in the encryption result are not complete ciphertext character strings, but the incomplete intercepted character strings, and therefore, the encryption method can assist in effectively preventing the encryption result from being subjected to collision attack, violent attack or rainbow table comparison attack compared with an encryption method according to which a single encryption algorithm is adopted to perform encryption to obtain complete ciphertext character strings, and therefore, the security of the encryption result can be improved.
Owner:ADVANCED NEW TECH CO LTD
A high-speed space-time computing platform
ActiveCN107590380BDeciphering speed is fastDeciphering speed increasedDigital data authenticationPlaintextComputer architecture
The invention discloses a high-speed space-time computing platform, which includes a storage module, an FPGA parallel array module and an external interface computer, and the storage module and the FPGA parallel array module are connected to the external interface computer; The results are compressed and stored, and SSDs are used to query the collision points in parallel; the FPGA parallel array module is used to distribute encryption to each individual FPGA chip in parallel, and to find the collision point of the rainbow table through multiple FPGA chips running in parallel; the external interface computer is used to The way of socket provides the deciphering of MD5, Sha1, Sha256 and DES. The present invention combines many years of experience in password deciphering, on the basis of the existing FPGA parallel array module, adopts the rainbow table processing scheme, develops a high-speed space-time computing platform, adopts a time-space balance mode for password deciphering, and quickly deciphers the plaintext of the password within a certain range. Assist the security department to quickly obtain evidence and handle cases.
Owner:NEXWISE INTELLIGENCE CHINA LTD
System and method for cracking word2003 document based on fpga hardware
ActiveCN106357384BImprove cracking efficiencyDelayed cracking timeEncryption apparatus with shift registers/memoriesResource consumptionComputer module
The invention discloses a word2003 document cracking system based on FPGA hardware and a method. The system comprises a PC, an input interface module, a crack module and an output interface module which are connected sequentially, and the PC is connected with the output interface module. The crack module comprises a sub-key generation module, a rainbow table matching module and a key cracking module which are connected sequentially. The sub-key generation module includes sub-key round robin controller, MD5 algorithm module and RC4 algorithm module which are connected sequentially. The key cracking module consists of algorithm round robin controller, MD5 algorithm module and RC4 algorithm module. The system achieves document cracking by using the time and space folding algorithm of the rainbow table, thus improving the crack efficiency and reducing the cracking time. On the basis of considering the technical characteristics of the rainbow table and the FPGA, the appropriate rainbow table is used for cracking, thus solving the contradiction between cracking time and resource consumption.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
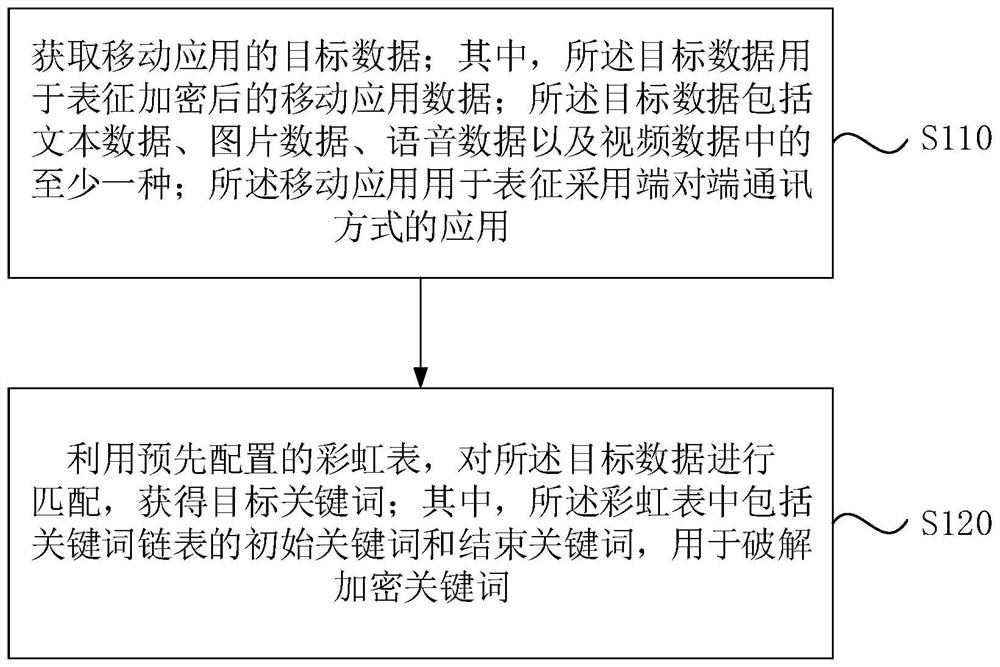
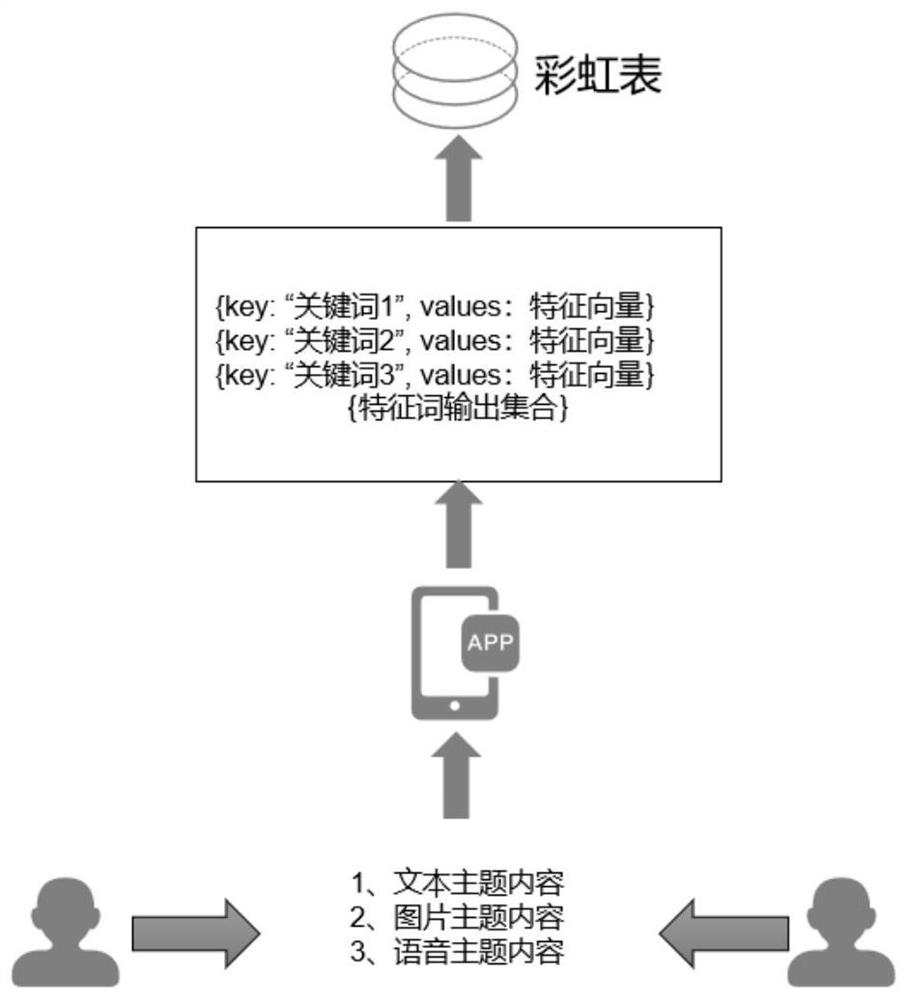
Rainbow table-based matching method and device, storage medium and electronic equipment
The embodiment of the invention discloses a rainbow table-based matching method and device, a storage medium and electronic equipment. The method comprises the steps of obtaining target data of a mobile application, wherein the target data is used for representing encrypted mobile application data; the target data comprises at least one of text data, picture data, voice data and video data; the mobile application is used for representing an application adopting an end-to-end communication mode; matching the target data by using a pre-configured rainbow table to obtain a target keyword, wherein the rainbow table comprises an initial keyword and an ending keyword of a keyword chain table and is used for cracking the encrypted keyword. According to the technical scheme, mobile application keyword matching can be supported, mobile application communication information content does not need to be decrypted, and user privacy is protected. The method has the advantage of quick deployment for mobile application matching.
Owner:NAT COMP NETWORK & INFORMATION SECURITY MANAGEMENT CENT +1
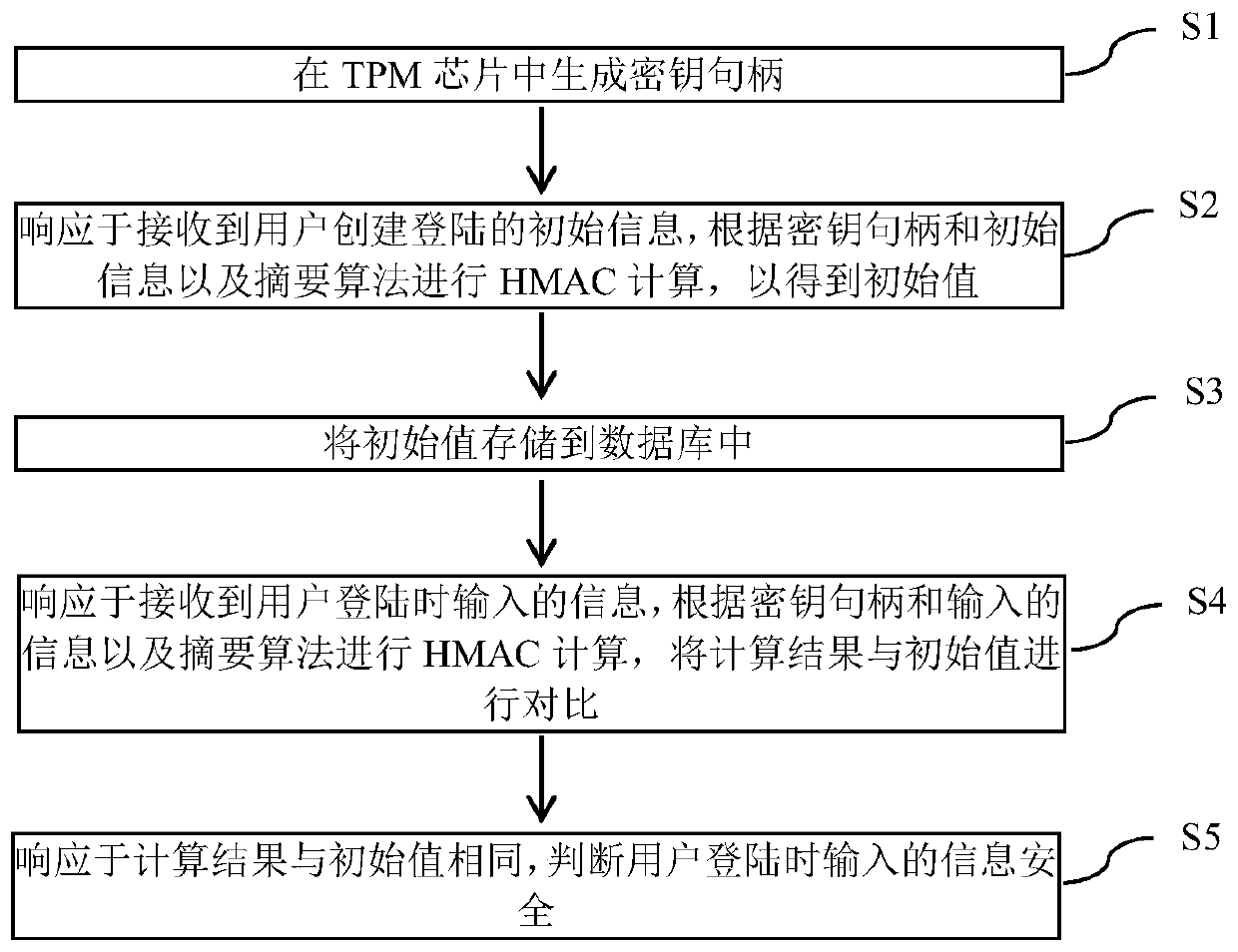
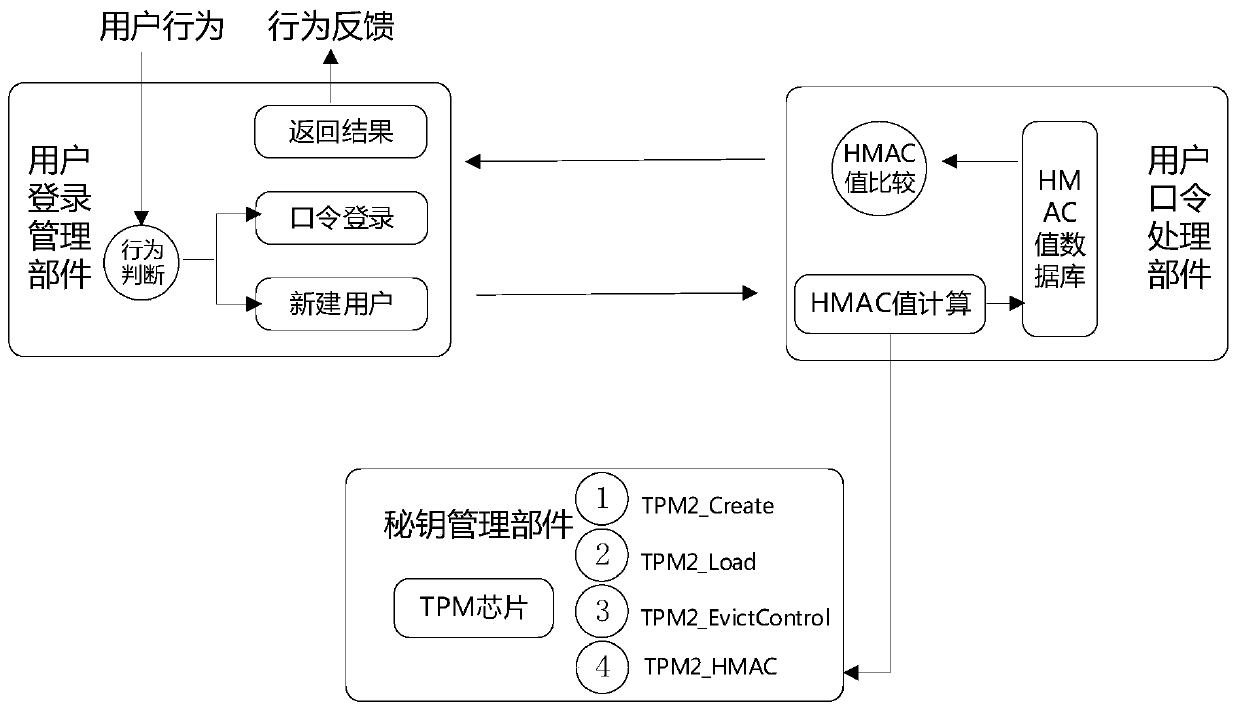
System login protection method and device based on TPM chip
InactiveCN111104667AAvoid attackAvoid crackingInternal/peripheral component protectionDigital data authenticationRainbow tableInformation security
The invention provides a system login protection method and device based on a TPM chip. The method comprises the following steps of generating a secret key handle in the TPM chip; in response to the received initial information of login created by a user, performing HMAC calculation according to the key handle, the initial information and an abstract algorithm to obtain an initial value; storing the initial value into a database; responding to the received information input by the user during login, performing HMAC calculation according to the secret key handle, the input information and an abstract algorithm, and comparing a calculation result with an initial value; and in response to the fact that the calculation result is the same as the initial value, judging information security inputby the user during login. Dictionary attacks and rainbow table cracking of user login passwords can be prevented, the safety is very high, and the competitiveness of the product is improved.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
A method and device for detecting numbers
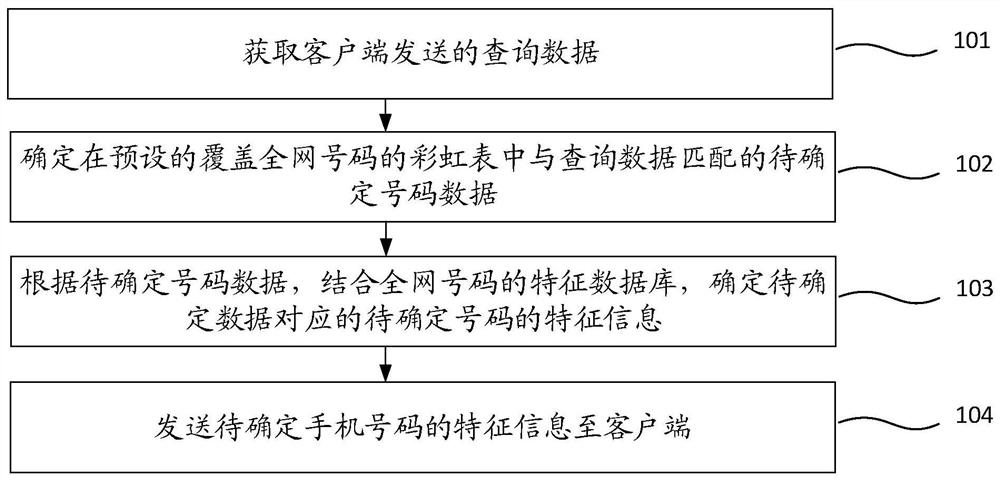
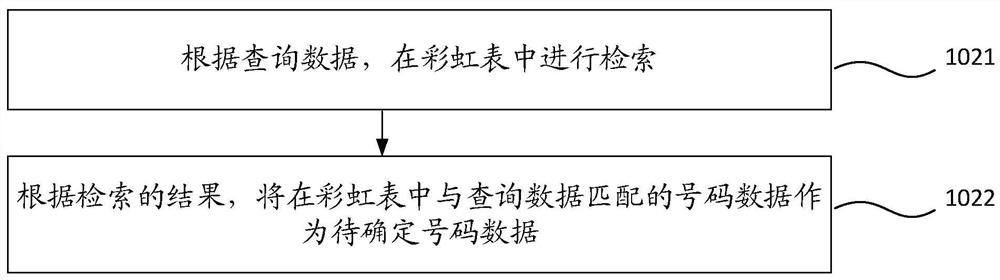
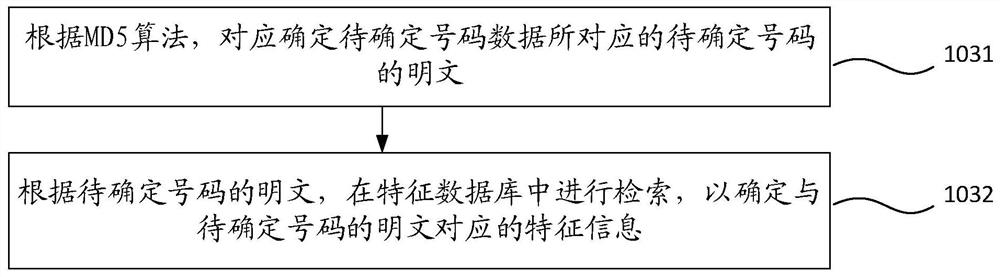
ActiveCN109635164BPrivacy protectionImprove securityEncryption apparatus with shift registers/memoriesOther databases indexingData matchingPlaintext
Embodiments of the invention provide a number detection method and device. The number detection method is applied to a server, and comprises the steps: obtaining query data sent by a client, the querydata being data of a previous preset number of bits after a target number is processed by an MD5 algorithm; determining to-be-determined number data matched with the query data in a preset rainbow table covering the whole network number; determining feature information of the to-be-determined number corresponding to the to-be-determined data according to the to-be-determined number data in combination with a feature database of the whole network number; and sending the feature information of the to-be-determined number to the client. Therefore, a plaintext is not adopted when the number is detected, the privacy of the user is protected, and the security is improved.
Owner:HANGZHOU FRAUDMETRIX TECH CO LTD
A cryptographic attack method, device and heterogeneous acceleration platform
ActiveCN107425957BImprove parallelismImprove throughput performanceKey distribution for secure communicationSecret communicationCiphertextPassword
The invention discloses a password attack method, device and heterogeneous acceleration platform. The method is applied to a heterogeneous platform including a CPU end and an FPGA end, including: the FPGA end reads a pre-stored rainbow table and ciphertext data to be attacked; According to the preset password attack algorithm, the ciphertext data to be attacked is processed in parallel to obtain the password data to be selected; the FPGA side matches the password data to be selected with the rainbow table according to the preset matching algorithm to find out the candidate password; The terminal returns a completion signal to the CPU terminal. It can be seen that this application utilizes FPGA to perform hardware acceleration of the cryptographic attack algorithm, and the FPGA executes the cryptographic attack algorithm in parallel, which improves the parallelism of the algorithm, improves the throughput performance of the algorithm execution, and then improves the performance of the cryptographic attack algorithm based on the rainbow table . Furthermore, the redundancy and fine-grained parallelism at the FPGA side make the hardware cost lower.
Owner:INSPUR SUZHOU INTELLIGENT TECH CO LTD
Data encryption method and device and data decryption method and device
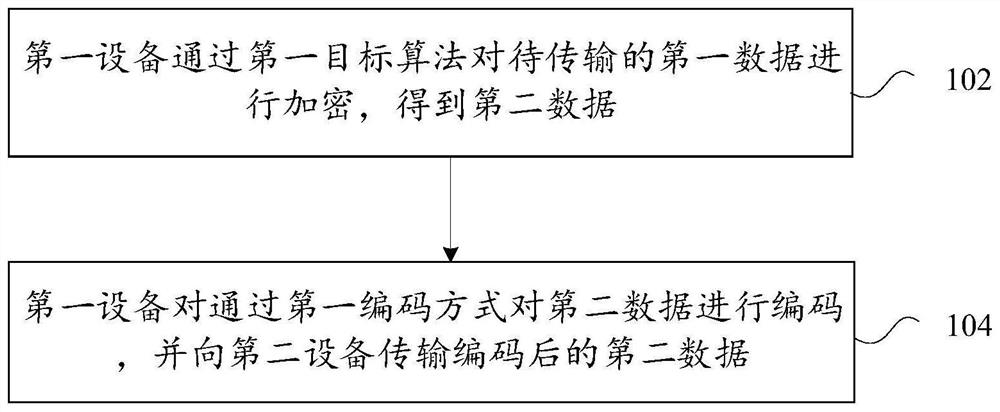
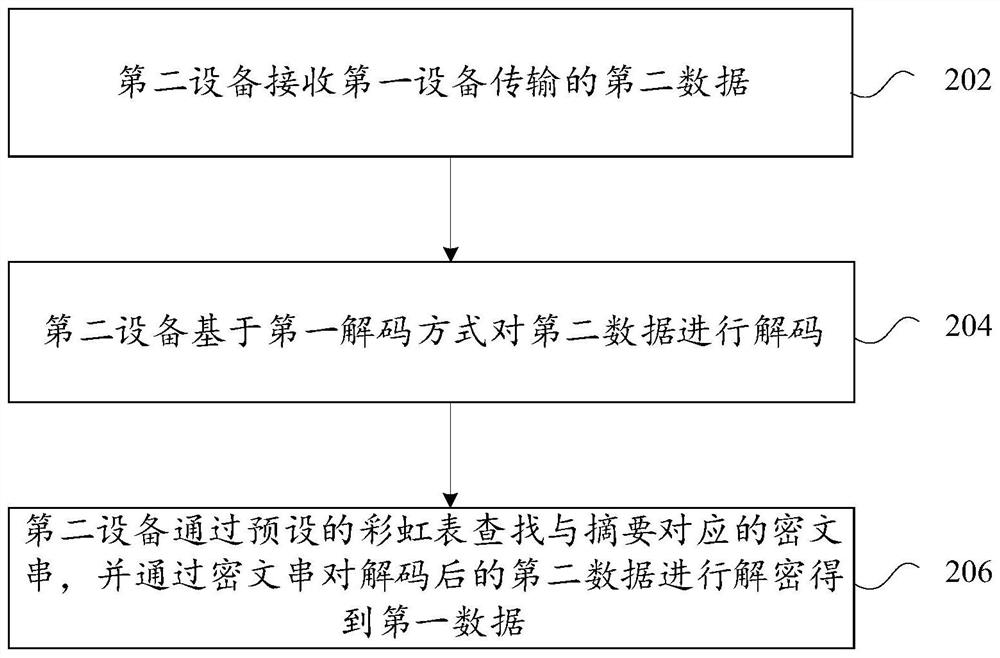
PendingCN113630237ASolve the problem of low data securityEncryption apparatus with shift registers/memoriesAlgorithmCiphertext
The invention provides a data encryption method and device and a data decryption method and device. The data encryption method comprises the steps: enabling the first equipment to encrypt first data to be transmitted through a first target algorithm to obtain second data, wherein the target algorithm comprises an irreversible algorithm, the second data comprises the first data and an abstract generated based on the irreversible algorithm, an abstract in the irreversible algorithm is an abstract in a corresponding relation represented by a preset rainbow table, the corresponding relation is a corresponding relation between the abstract and a ciphertext string, and the first device encodes the second data through a first encoding mode, and transmits the encoded second data to a second device. By means of the data transmission method and device, the problem that in the prior art, data security is low in the data transmission process of equipment is solved.
Owner:GREE ELECTRIC APPLIANCES INC +1
Work load proof method and device
ActiveCN108712486BSmall amount of calculationImprove selection efficiencyDigital data information retrievalTransmissionComputer networkAlgorithm
The invention discloses a workload proof method and device, which relate to the technical field of data processing. In order to solve the problem in the prior art, under the block chain system adopting the traditional workload proof mechanism, the selection efficiency of bookkeeping nodes is low. And the problem of excessively occupying the computing resources of each node. The method of the present invention includes: when receiving the current block sent by the first accounting node, according to the first hash value corresponding to the current block, searching for the second hash matching the first hash value in the preset rainbow table Hash value; send the second hash value to multiple other nodes, and receive the second hash value sent by each other node; determine the edit between the multiple second hash values and the first hash value through a preset algorithm The second hash value with the smallest distance is determined, and the node corresponding to the second hash value is determined as the second bookkeeping node, so that the second bookkeeping node can generate the next block. The present invention is applicable to the process of selecting bookkeeping nodes under the block chain system.
Owner:BEIJING QIHOO TECH CO LTD
A decryption hardware platform based on fpga
ActiveCN105376061BIncrease profitAchieve crackingKey distribution for secure communicationUser identity/authority verificationComputer hardwareRainbow
The invention discloses a decryption hardware platform based on an FPGA. The decryption hardware platform is characterized in that the decryption hardware platform comprises a forwarding logic FPGA module, N mutually-independent FPGA decryption sub-modules and an ARM management sub-module which are respectively connected with the forwarding logic FPGA module, and a power supply management module supplying power to the forwarding logic FPGA module, the N mutually-independent FPGA decryption sub-modules and the ARM management sub-module, wherein the N mutually-independent FPGA decryption sub-modules are respectively connected with the ARM management sub-module, and N is no less than 2. The decryption hardware platform provided by the invention meets the decryption requirements of different files and solves the problems that an existing decryption device is single in function and poor in universality. The FPGA has the advantages that the requirements of high-speed data transmission, interfaces and high-frequency data operation are met, high-speed data transmission and high-speed data transportation are realized, and the PFGA is externally provided with a high-speed large-capacity DDR3, so that the storage of rainbow tables is realized.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
A device and method for recovering pdf files
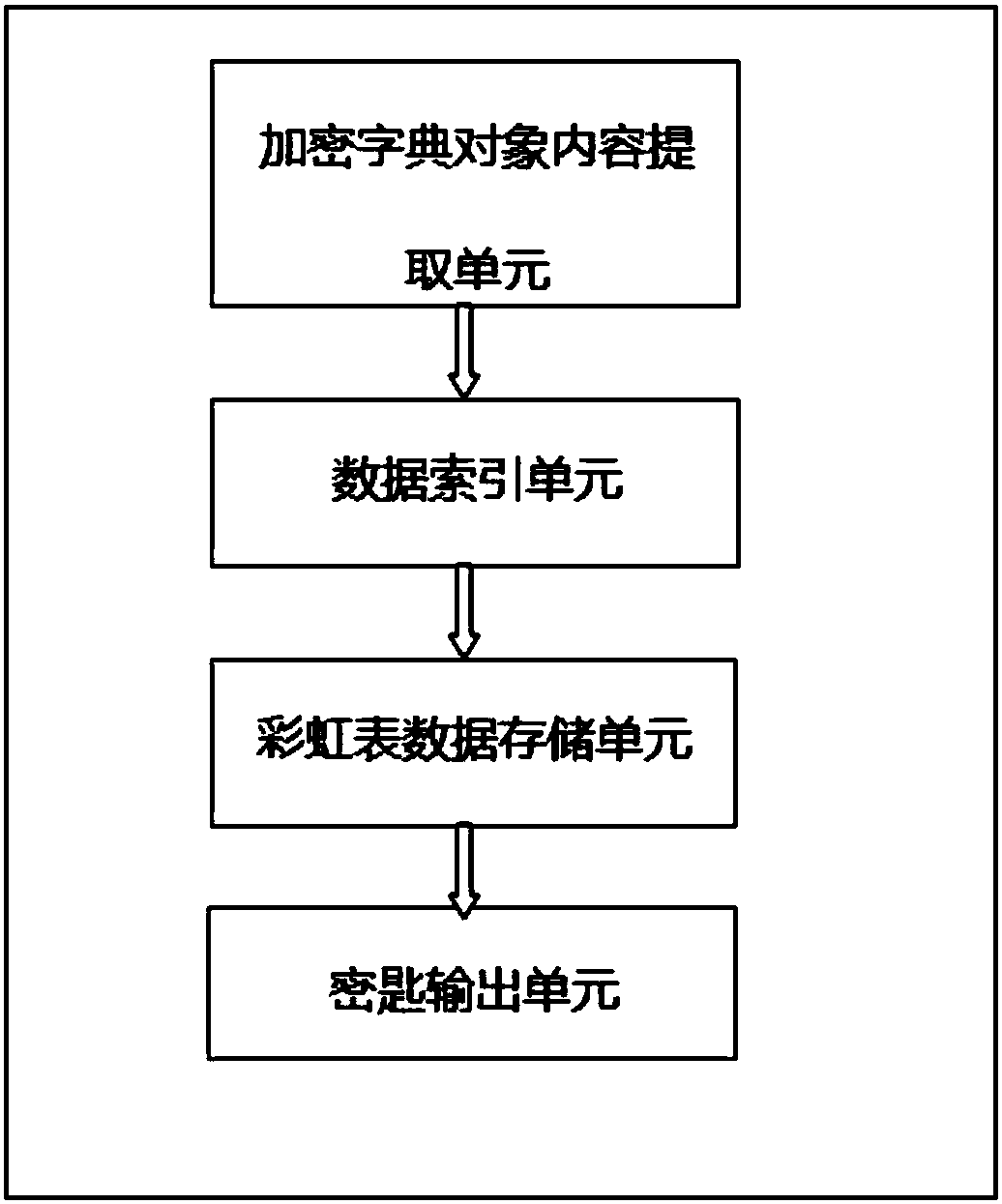
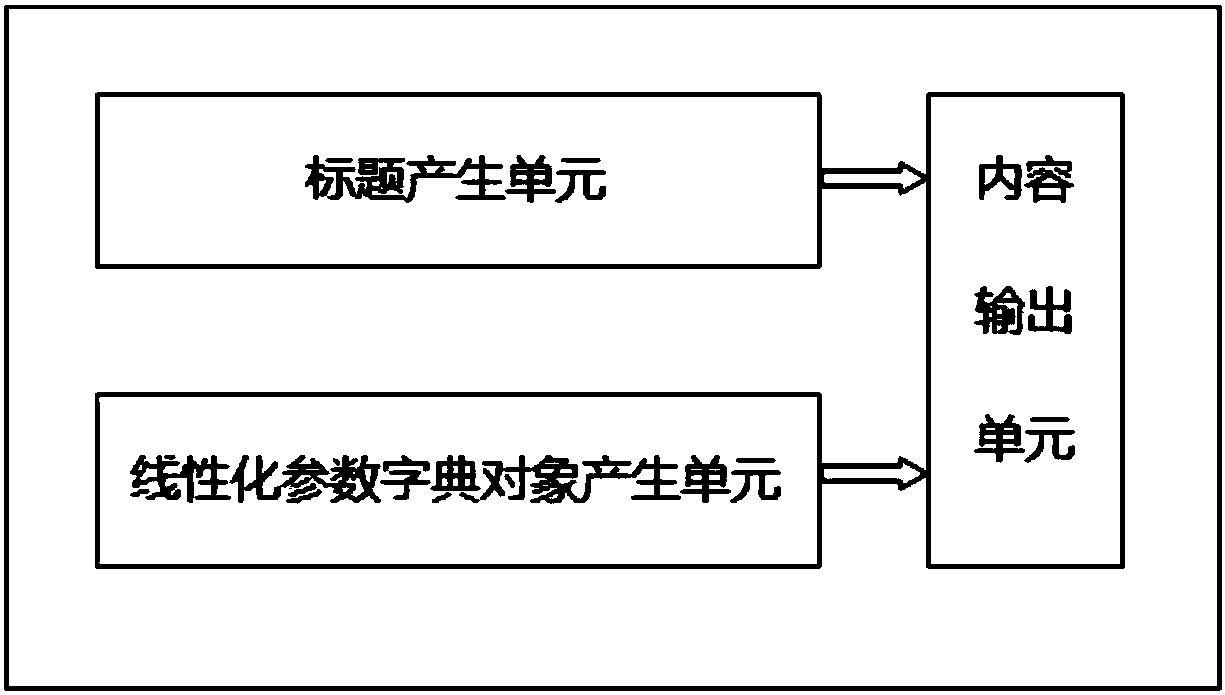
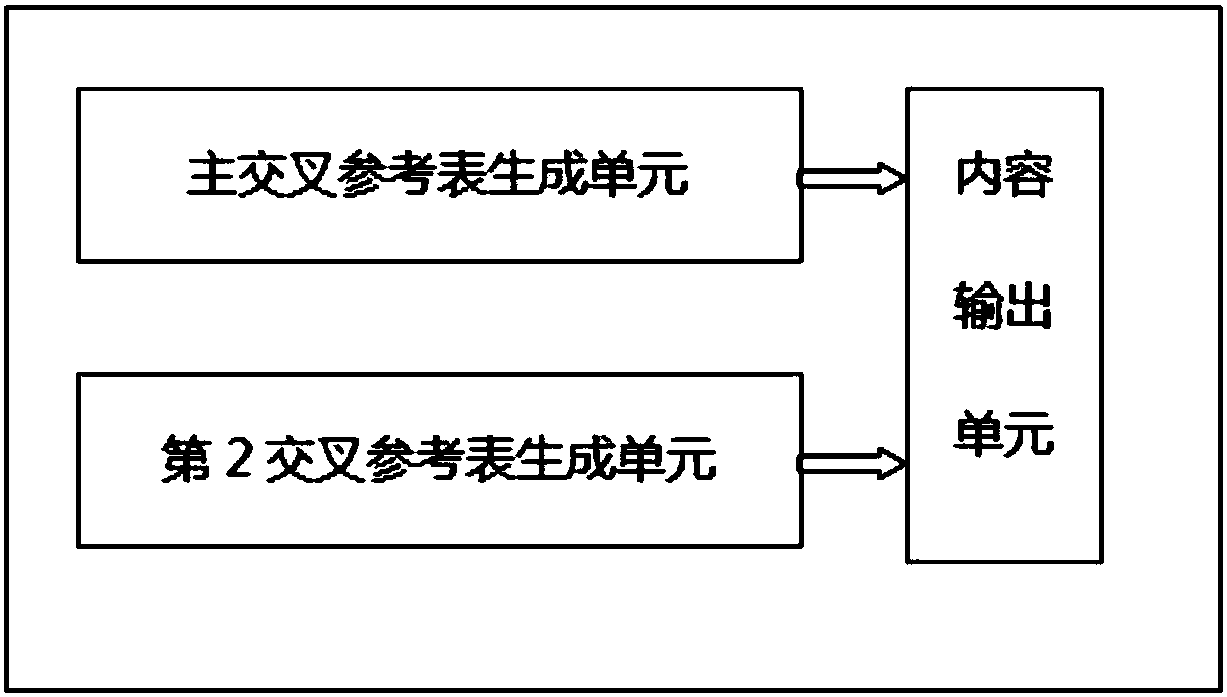
The invention discloses a PDF document recovery device and method; the device comprises the following units: an overall key obtain unit using a rainbow table to obtain the overall key of a to-be-decrypted document; a PDF title and linearization parameter dictionary object generation unit used for generating a title and linearization parameter dictionary object content; a cross-reference table generation unit used for generating a main cross-reference table and a second cross-reference table; a tail dictionary generation unit used for generating a tail dictionary corresponding to the main cross-reference table and second cross-reference table; an object number processing unit used for processing a decrypted object number; an indirect reference object processing unit used for processing object numbers of all reference objects in the present object; an object content processing unit used for determining the type of the object content, and decrypting a flow object. The novel device and method can neglect the initial deviant calculating difficulty caused by content length changes before and after decryption; modularization design is convenient, thus fast recovering PDF documents.
Owner:GUANGZHOU HUIRUI SITONG INFORMATION SCI & TECH CO LTD
A Quick Restoration Method for Word Encrypted Documents
ActiveCN106778292BAvoid the shortcomings of long passwords that cannot be crackedEffective recoveryDigital data protectionComputer hardwarePassword
The invention discloses a rapid restoring method for Word encrypted documents. The method comprises steps as follows: step one, a secret key rainbow table of restored Word documents is established; step two, decryption secrete keys of the encrypted documents are decoded; step three, original plaintext documents are reconstructed by use of the decryption secrete keys and structure information of Word documents. The method has the positive effects as follows: the rainbow table for decrypting the secrete keys is only needed to be generated once, and the generated rainbow table is suitable for restoring all encrypted documents; restoring is not related to the complexity of encryption passwords of encrypted documents, and the defect that a long password cannot be cracked with an existing document cracking method is overcome; Word encrypted documents of version 2003 can be effectively restored, and the success rate reaches 99% or above; the encrypted documents can be rapidly restored, tests prove that the average restoring time of the encrypted documents is within 3 min under the computation ability of ordinary desktop computers (with the basic frequency being 3.0 GHz or above), and actual demands for real-time decryption can be well met.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Password Recovery System and Recovery Method Based on Extended Rainbow Table of Generator
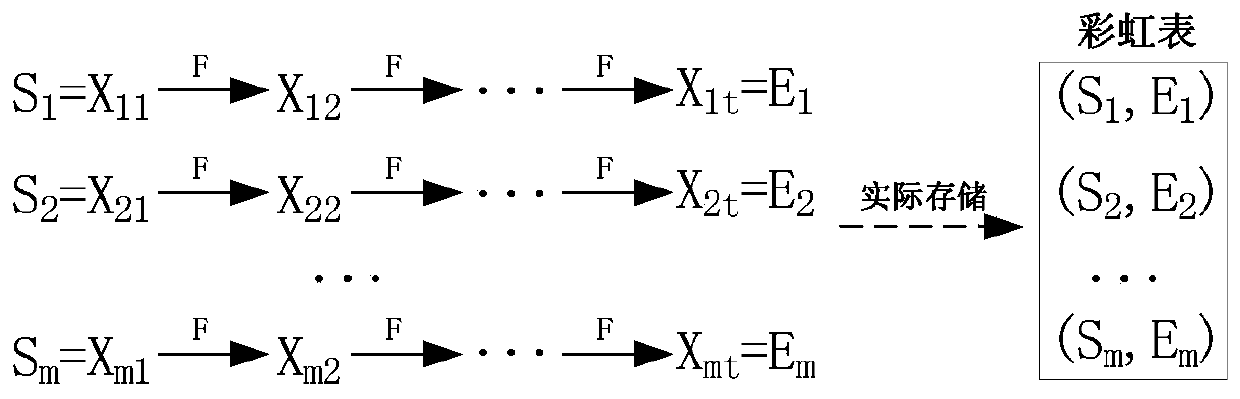
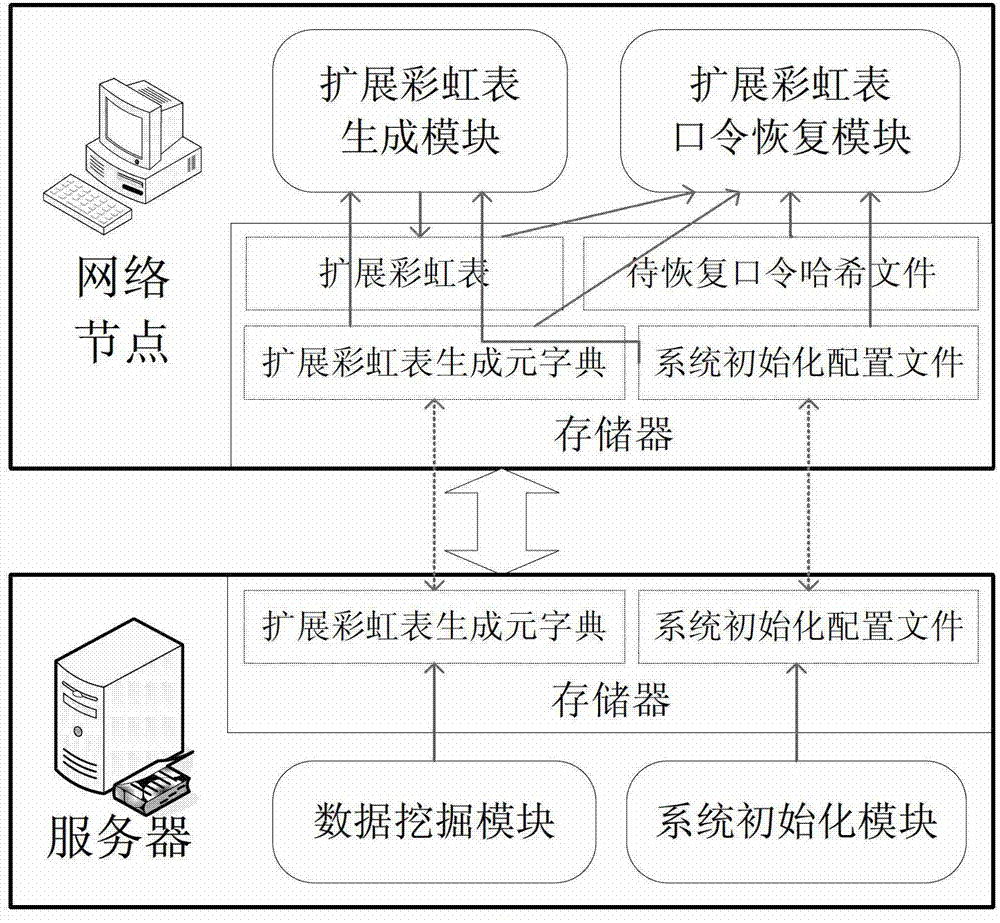
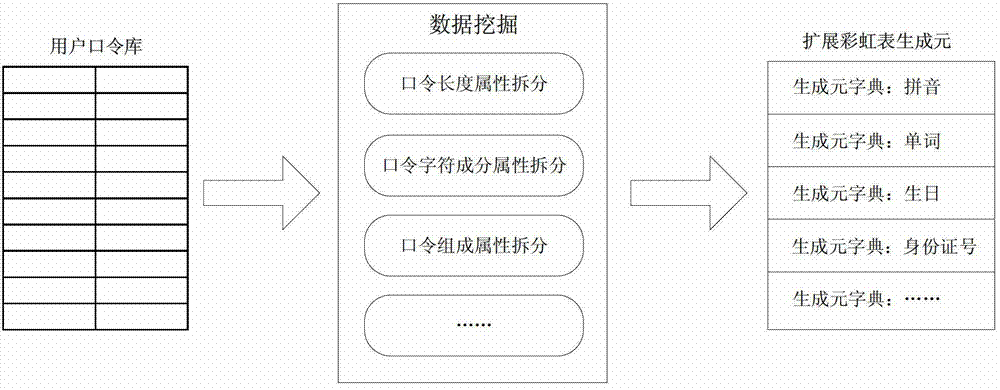
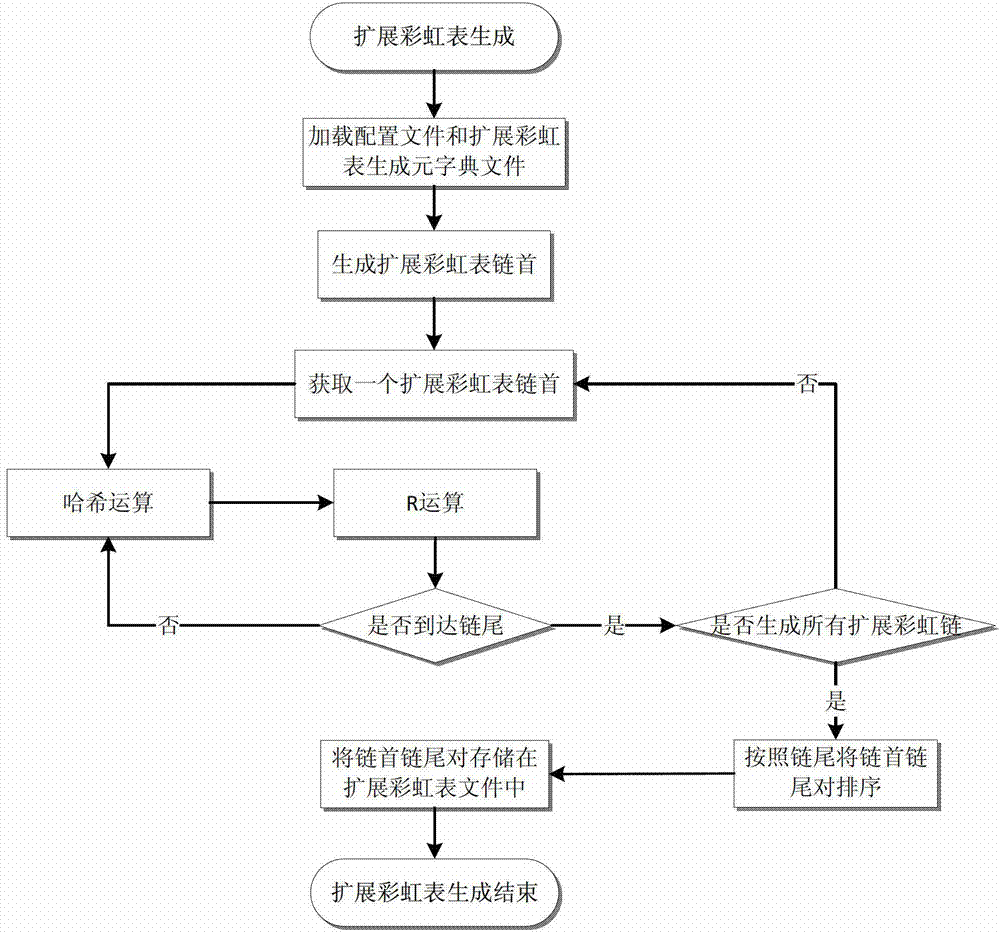
ActiveCN103049709BOptimize storageShorten recovery timeDigital data protectionRecovery methodTime range
A code recovery system and a recovery method based on a generator and an extended rainbow table belong to the technical field of computer safety and comprise an extended rainbow table generating module, a plurality of clients of an extended rainbow table recovering module and a server, wherein the server is connected with a plurality of network nodes and comprises a data mining module, a memorizer and a system initialization module. A user manages the work of the data mining module and the system initialization module of the server through managing the work of terminal networks. The data mining module of the server generates a generator dictionary; the system initialization module of the server generates a distributed initialized configuration file; the distributed initialized configuration file comprises generator dictionary information and is connected with the extended rainbow table generating module and the extended rainbow table recovering module of the network nodes and is used for transmitting system initialization configuration information. The code recovery system and the recovery method based on the generator and the extended rainbow table achieve the purpose that a long instruction rainbow table is generated within a receptible time range by reducing plaintext space and reduces the recovery time of an artificial instruction.
Owner:SHANGHAI JIAOTONG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com