User name password authentication method implemented on basis of public key algorithm
An authentication method and public key technology, applied in the field of identity authentication based on user name and password, can solve security problems, cannot resist rainbow table attacks, website user name and password leakage and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
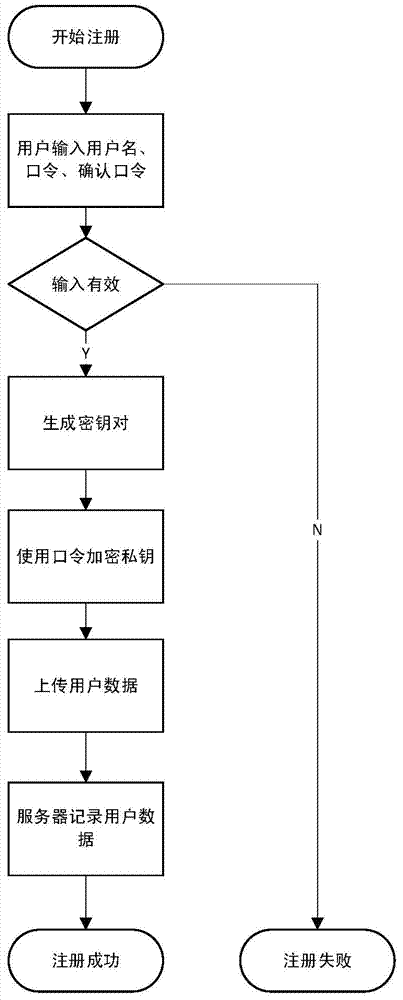
[0026] In order to make the technical means, creative features, goals and effects achieved by the present invention easy to understand, the present invention will be further described below in conjunction with specific illustrations.
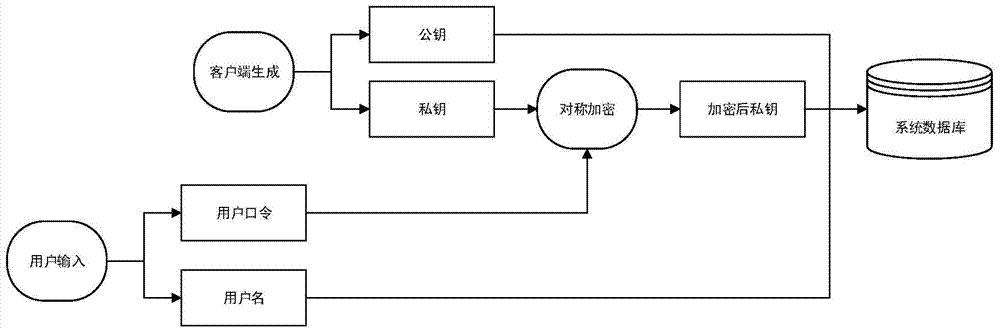
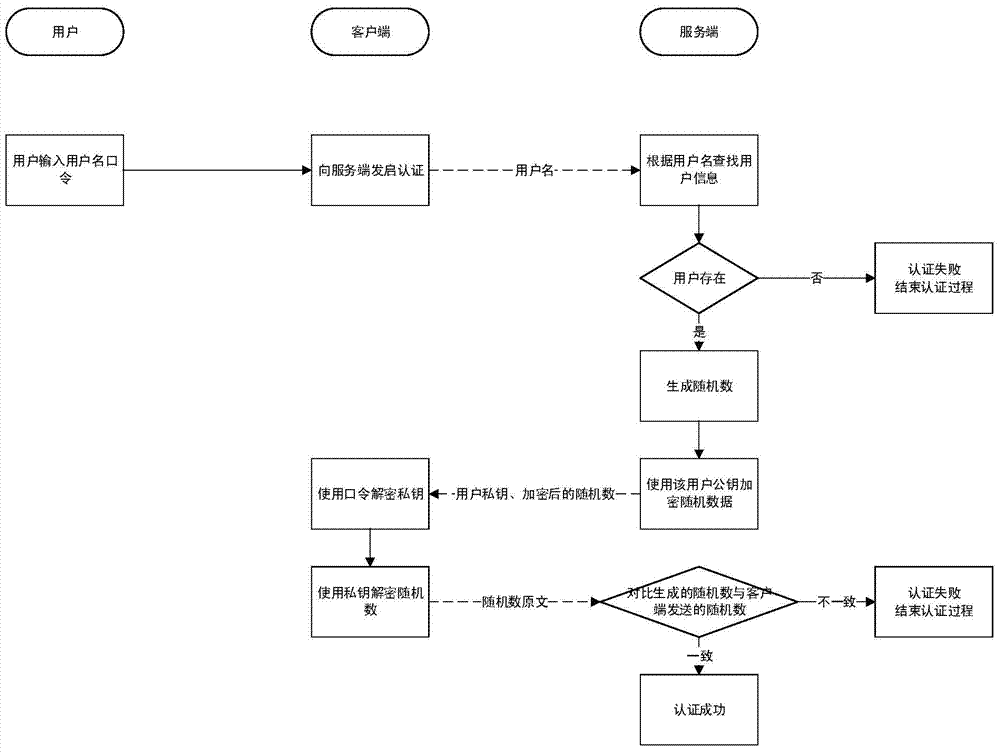
[0027] The present invention aims at the security problems existing when the software platforms such as websites and information systems use the existing password authentication method to authenticate user passwords, and introduces a public key (asymmetric) encryption algorithm into the password authentication. The most notable feature of public-key encryption algorithms is that a pair of keys are involved in the encryption: a public key and a private key. Data encrypted with a public key can only be decrypted with the corresponding private key, and data encrypted with a private key can only be decrypted with the corresponding public key.
[0028] The scheme provided by the present invention is based on this feature, and authentication is perfor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com