Rainbow table-based matching method and device, storage medium and electronic equipment
A matching method and rainbow table technology, applied in computer security devices, electrical digital data processing, instruments, etc., can solve problems such as keyword matching of mobile data that cannot be encrypted, and achieve the effect of protecting user privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
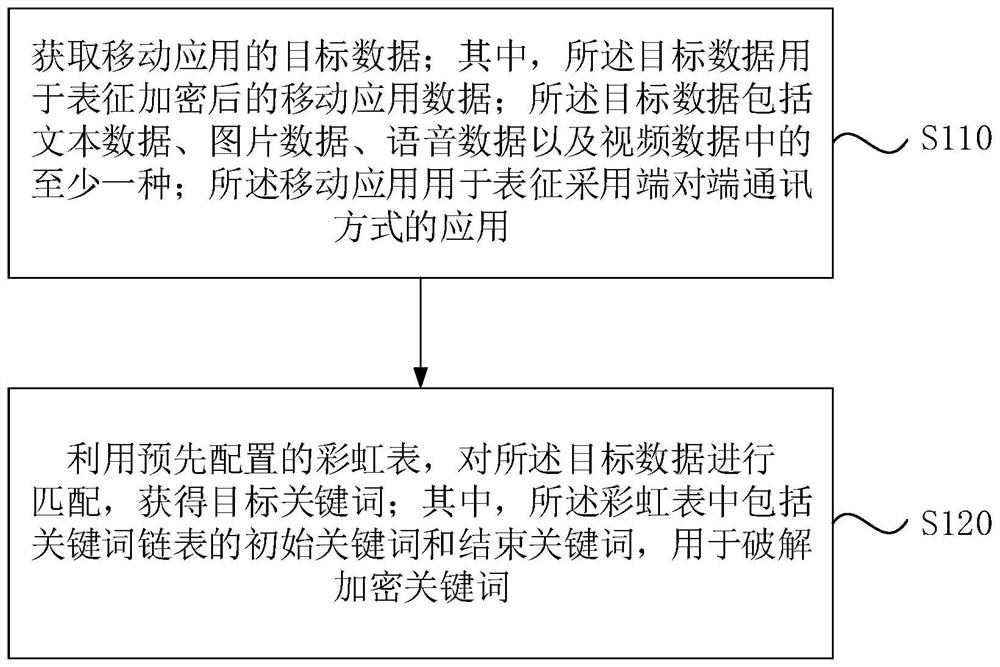
[0026] figure 1 It is a flow chart of the rainbow table-based matching method provided in Embodiment 1 of this application. This embodiment is applicable to the case of matching encrypted data transmitted by mobile applications. The matching device can be implemented by means of software and / or hardware, and can be integrated into devices such as smart terminals for encrypted data matching.
[0027] Such as figure 1 As shown, the matching method based on the rainbow table includes:
[0028] S110. Acquire target data of the mobile application; wherein, the target data is used to represent encrypted mobile application data; the target data includes at least one of text data, picture data, voice data, and video data; the mobile Application is used to characterize applications that use end-to-end communication;
[0029] In this solution, based on the rainbow table, by matching the encrypted target data, it is possible to determine whether there are some sensitive words in the n...
Embodiment 2
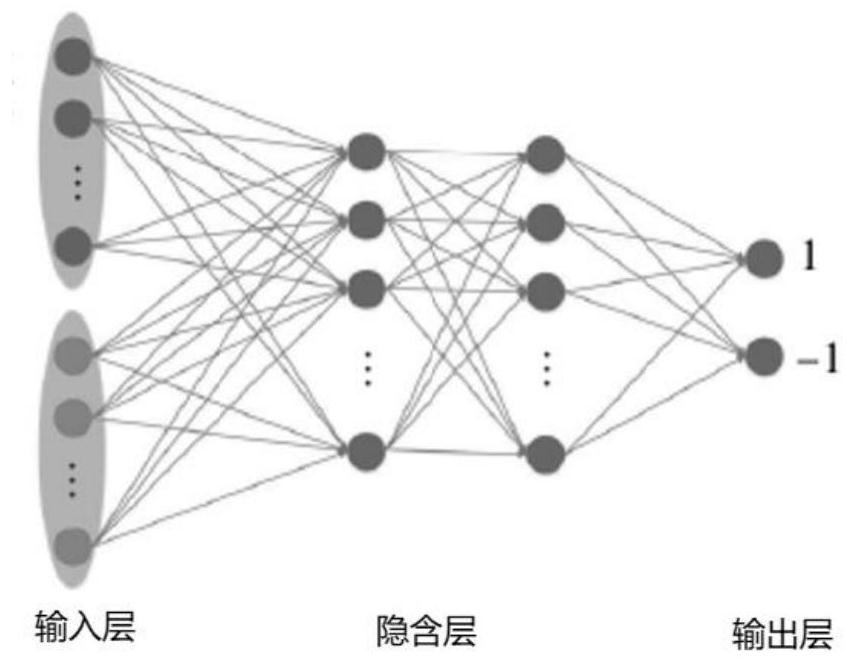
[0063] Figure 5 It is a schematic diagram of the matching process based on the rainbow table provided in the second embodiment of the present application. The second embodiment is further optimized on the basis of the first embodiment. The specific optimization is: using a pre-configured rainbow table to match the target data to obtain target keywords, including: processing the target data according to a preset algorithm to obtain keywords to be matched; Words are matched with feature vectors in a pre-configured rainbow table to determine target keywords; wherein, the feature vectors are used to represent data obtained by operating on keywords. Wherein, details that are not described in detail in this embodiment can be found in Embodiment 1. Such as Figure 5 As shown, the method includes the following steps:
[0064] S510. Acquire target data of the mobile application; wherein, the target data is used to represent encrypted mobile application data; the target data include...
Embodiment 3
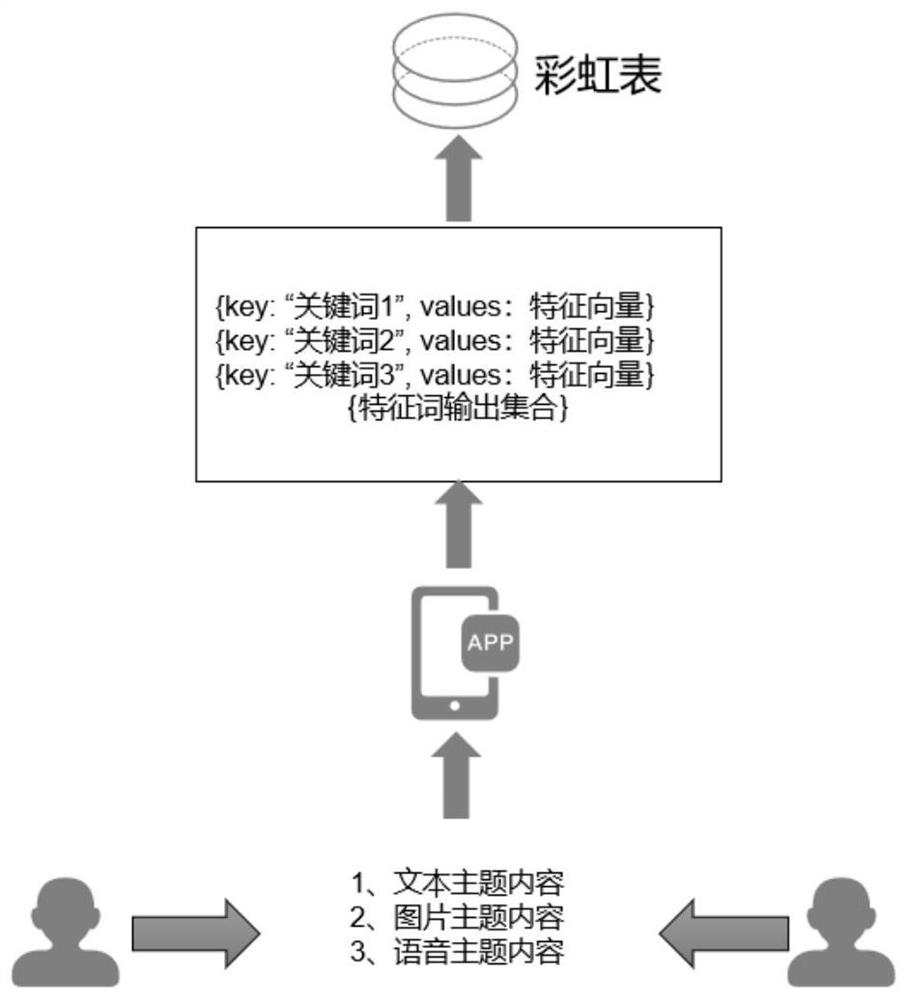
[0076] Figure 7 is a schematic structural diagram of a matching device based on a rainbow table provided in Embodiment 3 of the present application, such as Figure 7 As shown, matching devices based on rainbow tables include:
[0077] The target data acquisition module 710 is configured to acquire target data of the mobile application; wherein, the target data is used to represent encrypted mobile application data; the target data includes at least text data, picture data, voice data and video data A: The mobile application is used to characterize an application using a peer-to-peer communication mode;
[0078] The target keyword obtaining module 720 is used to utilize the pre-configured rainbow table to match the target data to obtain the target keyword; wherein, the rainbow table includes the initial keyword and the end keyword of the keyword linked list, using to decipher encrypted keywords.
[0079] In this technical solution, optionally, the target keyword obtaining ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com