Kerberos identity authentication protocol improvement method based on national cryptographic algorithm
A national secret algorithm and identity authentication technology, applied in the field of Kerberos identity authentication protocol improvement, can solve the problems of key management difficulties and increase overhead, and achieve the effect of improving security and efficiency, and realizing localization and autonomy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0052] Embodiments of the present invention will be described in further detail below in conjunction with the accompanying drawings.
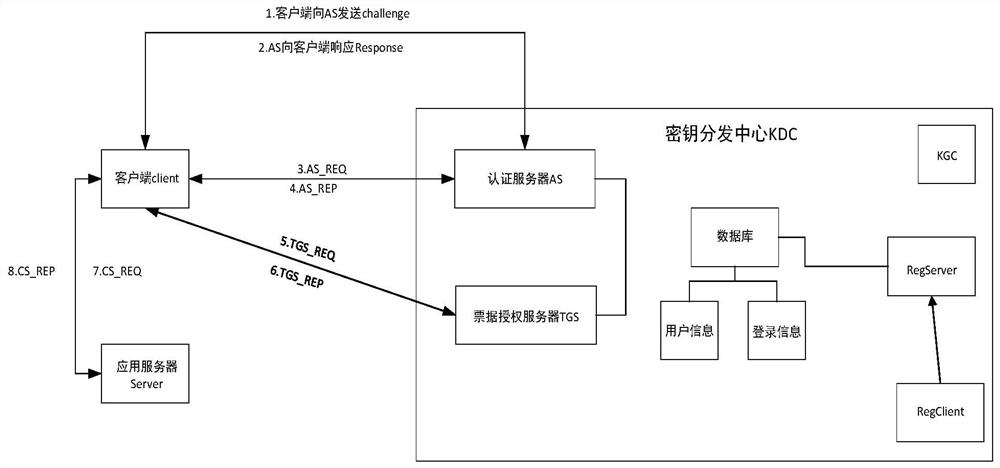
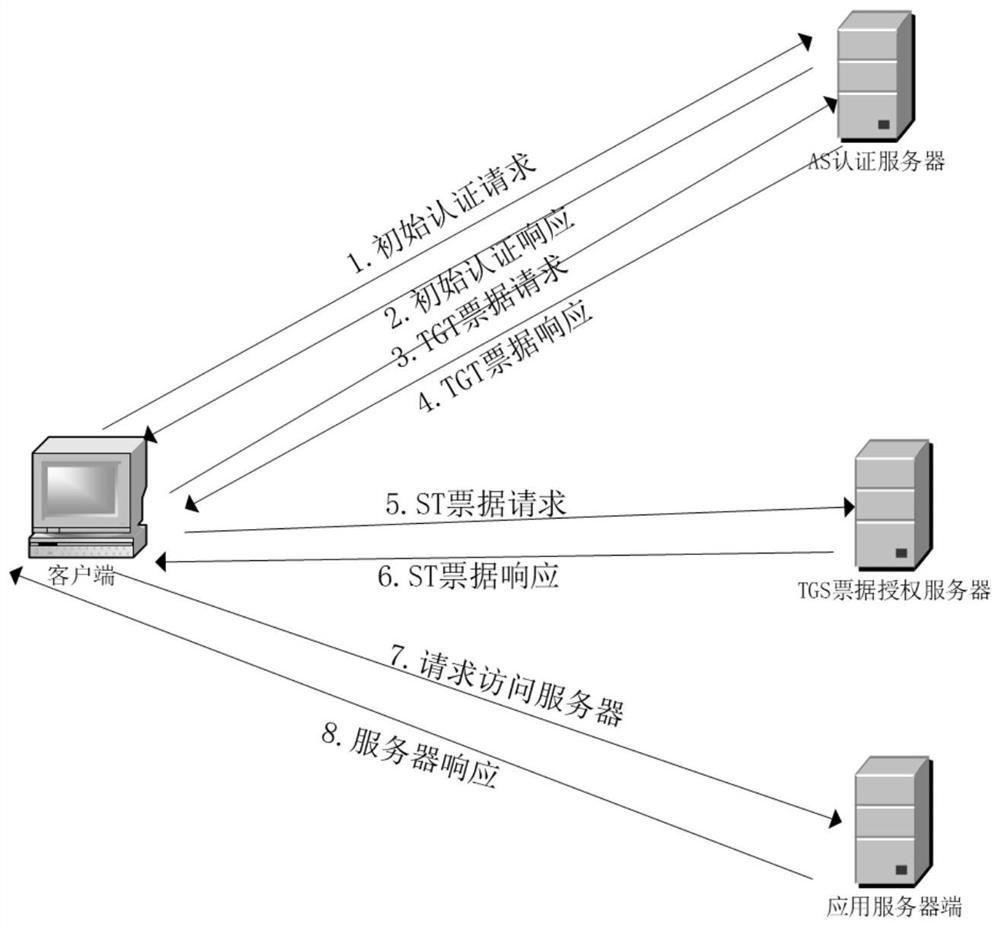
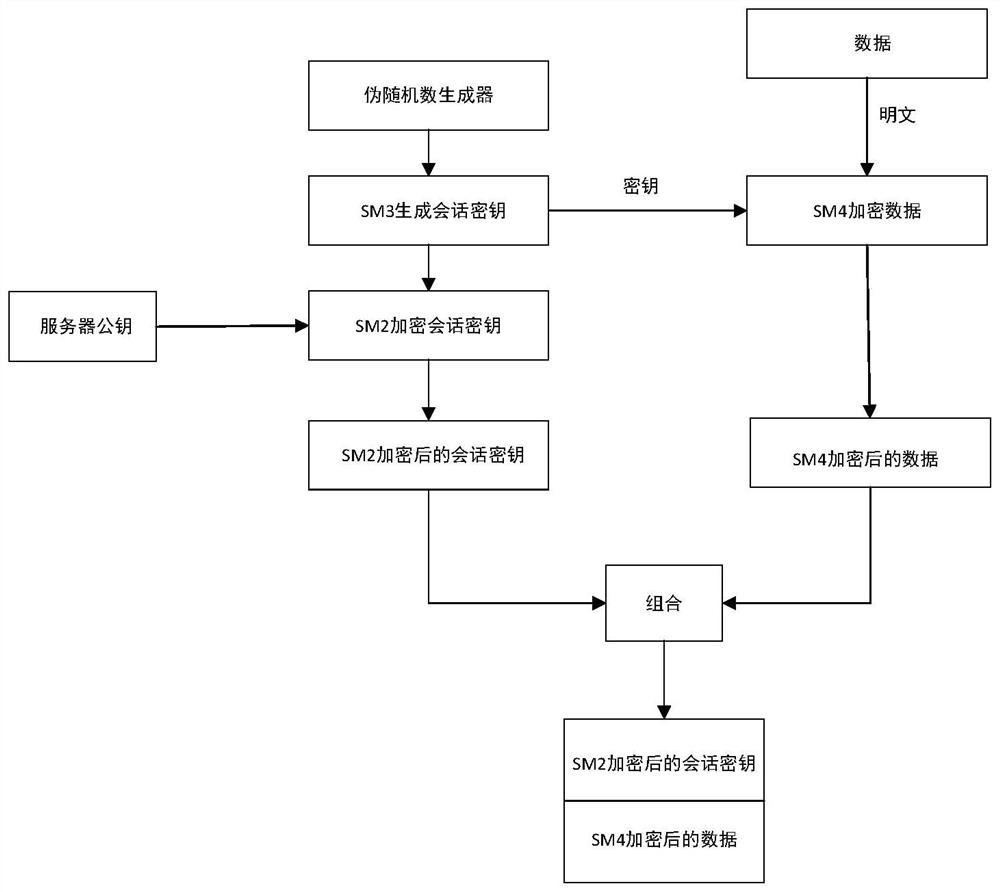
[0053] A method for improving the Kerberos identity authentication protocol based on the national secret algorithm of the present invention uses session key dynamics and a mixed cryptographic system based on the national secret algorithm to improve the traditional Kerberos protocol, and the improved Kerberos protocol includes a registration process and an authentication process ;
[0054]The authentication process retains three stages of traditional Kerberos authentication, which are:
[0055] The client and the authentication server (Authentication Server, AS) authenticate each other: the client sends AS_REQ to the AS, requesting AS authentication, the AS receives a challenge value sent to the client, the client responds to the AS after receiving it, and then the AS returns to the client AS_REP;
[0056] The client communicates with the Tick...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com