Reduction method and device for Android terminal full-disk enciphered data
A full-disk encryption and data technology, which is applied in computer security devices, digital data protection, electronic digital data processing, etc., can solve problems such as difficult cracking by brute force, long time-consuming, etc., and achieve fast loading, simple operation, and high decryption efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
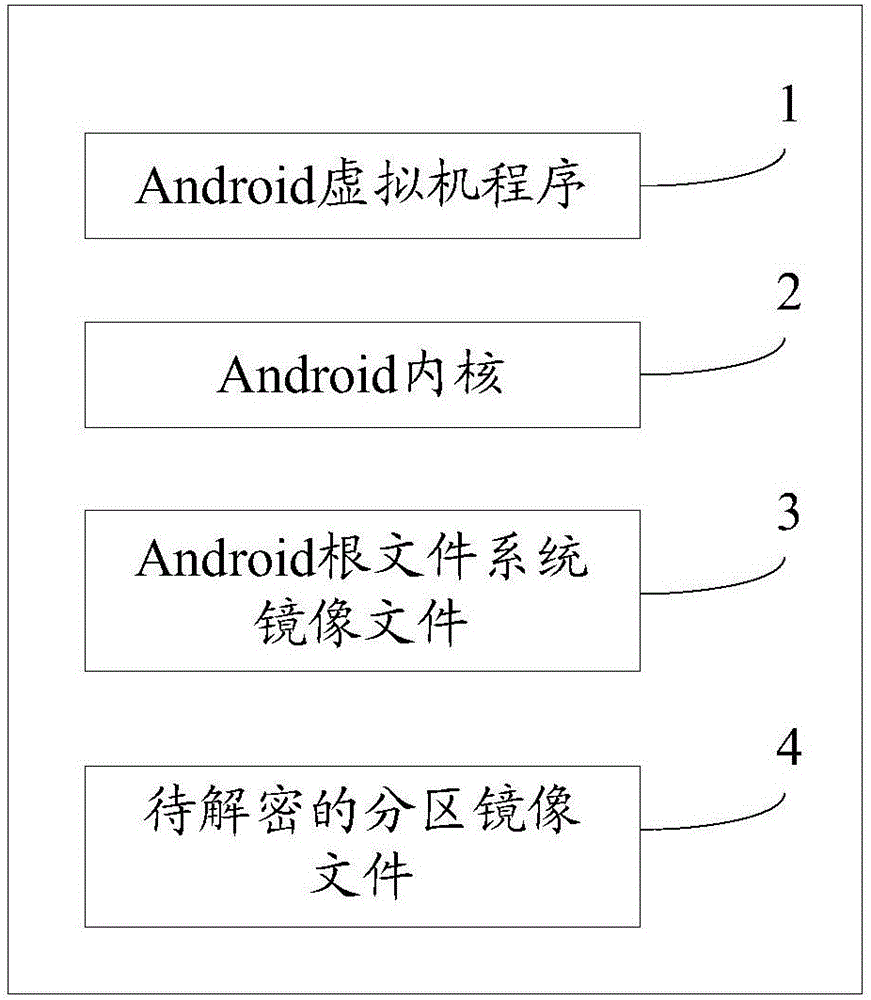
[0064] A recovery device for full-disk encrypted data of an Android terminal, comprising: an Android virtual machine program, an Android kernel, an Android root file system image file, and a partition image file to be decrypted;
[0065] The Android virtual machine program is that the host starts the Android virtual machine entry, and provides rich parameters to control the Android virtual machine to start and run. Since the present embodiment is mainly aimed at the partition to be decrypted, the virtual machine is started by optimizing a series of parameters, such as: "- no-boot-anim", "-no-audio", "-no-skin" and "-no-window"; where "-no-window" will make the Android virtual machine not start the Android system application layer related services and programs , to speed up the inventive solution decryption partition loading process; this embodiment relates to other image files and also specifies specific files for the Android virtual machine through the parameter form, specific...
Embodiment 2
[0075] A method corresponding to the recovery system of the Android terminal full-disk encrypted data of the above-mentioned embodiment 1, comprising:
[0076] Build an Android virtual machine program for starting the Android kernel;
[0077] Start the Android virtual machine program; set the relevant parameters of the Android virtual machine program to optimize the Android virtual machine, and specify specific files for the Android virtual machine, such as: "-no-boot-anim", "-no-audio", "-no -skin" and "-no-window"; wherein "-no-window" will make the Android virtual machine not start the Android system application layer related services and programs to speed up the decryption partition loading process of the inventive scheme; "-kernel" specifies Android Kernel image file, "-ramdisk" specifies the Android root file system image file, and "-data" specifies the full-disk image file to be decrypted;
[0078] The Android virtual machine program initializes the Android kernel; spe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com