Remote-authorization-based bidding document encryption and decryption method
A remote authorization and bidding technology, applied in electrical components, user identity/authority verification, transmission systems, etc., can solve security and efficiency problems, slow encryption and decryption speed, inconvenient management and other problems, and achieve fast data transmission speed , Guarantee safety, good safety effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] Embodiment 1: Symmetrical algorithm + asymmetrical algorithm
[0051] In this embodiment, a combination of a symmetric algorithm and an asymmetric algorithm is adopted, wherein the primary encryption (encryption of bidding documents) adopts a symmetric algorithm, and the secondary encryption (encryption of a file encryption key) adopts an asymmetric algorithm. Its purpose is to enable users to authorize other trusted people to decrypt without providing a private key, so that the decryption of encrypted documents such as bidding does not require the user to provide a remote decryption method with a private key, thereby providing efficiency and ensuring file security. The following Described further.
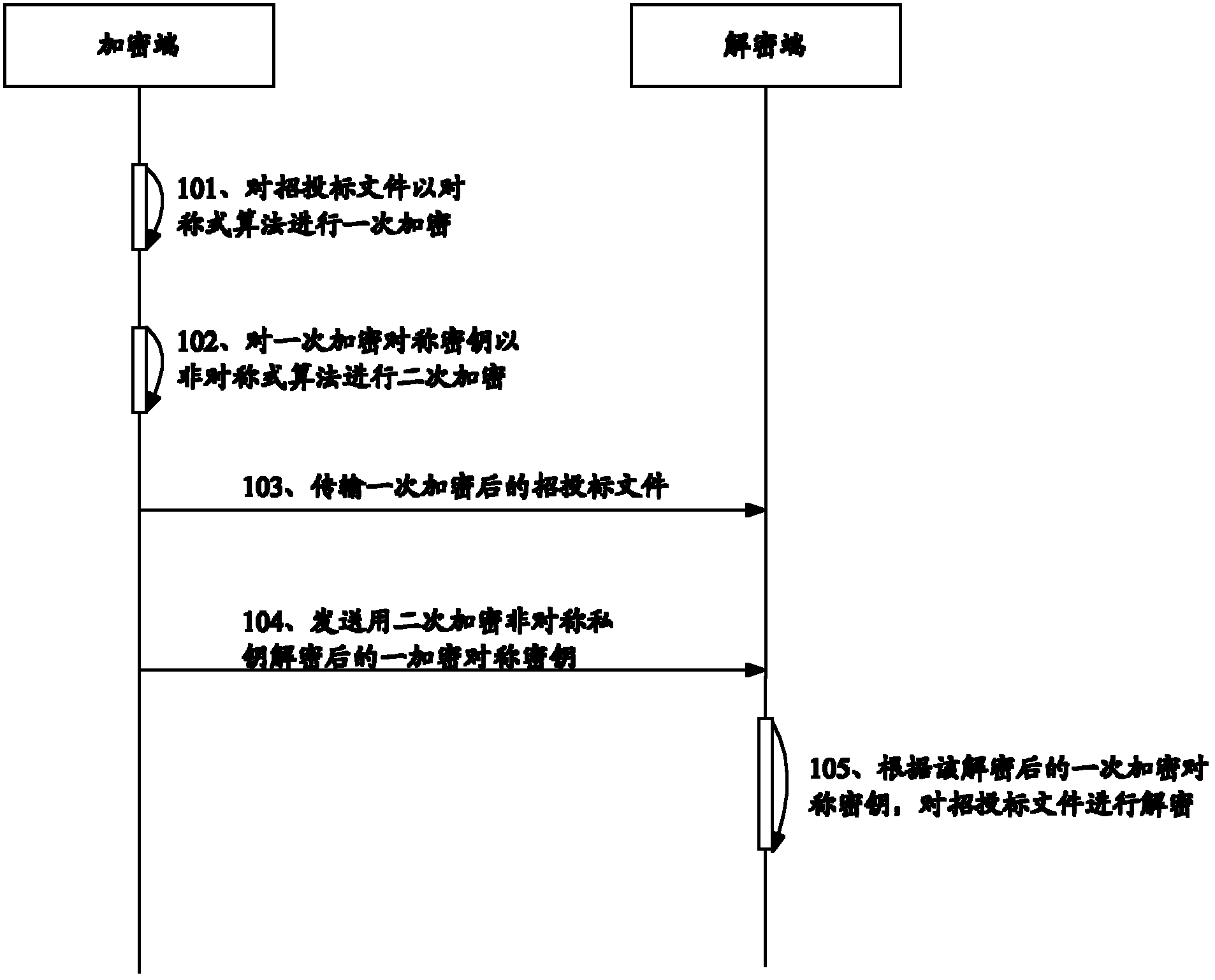
[0052] see figure 1 , represents a sequence diagram of a method for encrypting and decrypting bidding documents based on remote authorization according to an embodiment of the present invention. In this embodiment, the encryption and decryption method of bidding documents...
Embodiment 2
[0075] Embodiment 2: Symmetric Algorithm + Symmetric Algorithm
[0076] In this embodiment, a combination of a symmetric algorithm and a symmetric algorithm is adopted, wherein both the primary encryption and the secondary encryption use a symmetric algorithm, and the specific methods are as follows.
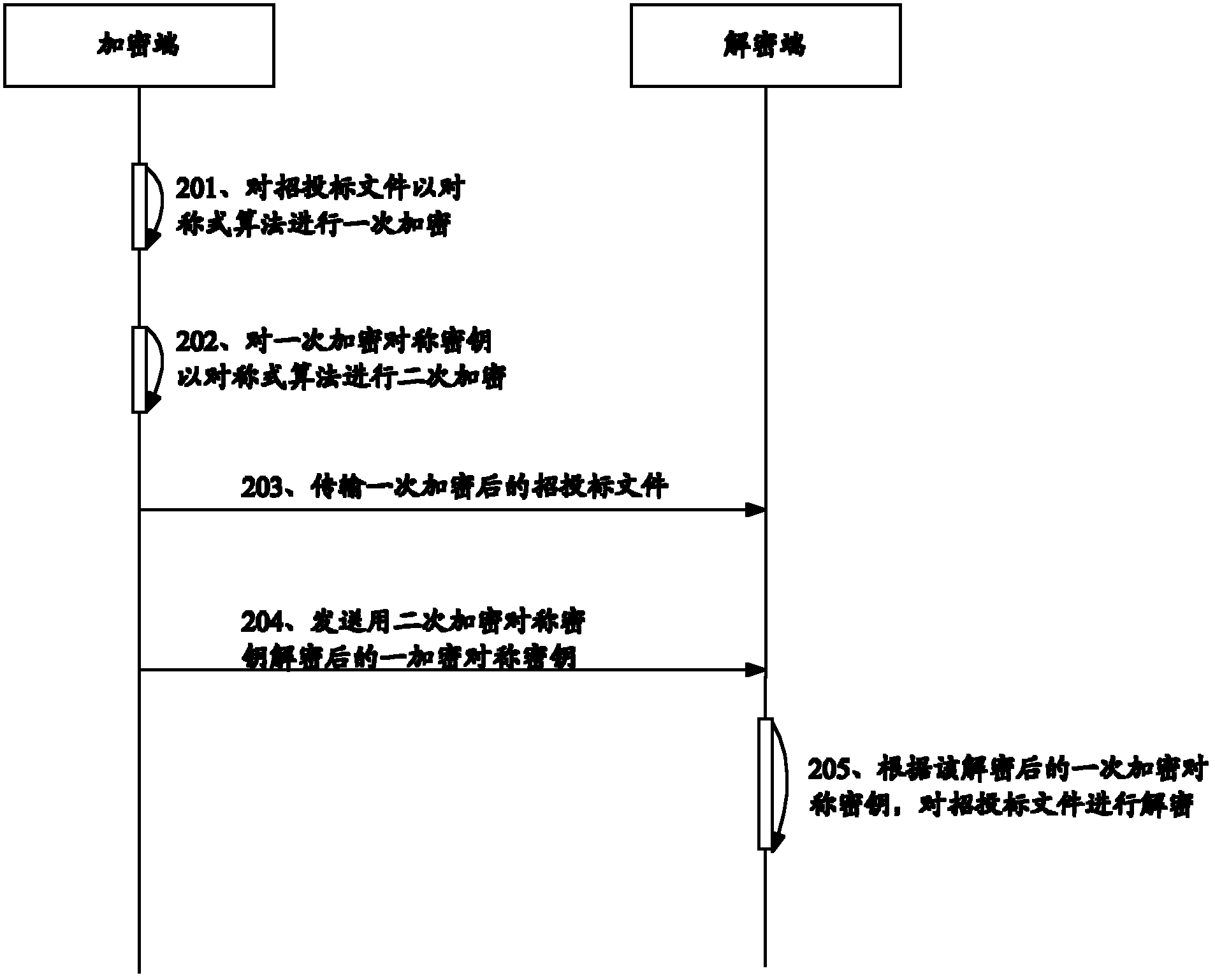
[0077] see figure 2 , represents a sequence diagram of the remote authorization-based encryption and decryption method for bidding documents according to Embodiment 2 of the present invention. This embodiment specifically comprises the following steps:
[0078] 201. The encryption terminal encrypts the bidding documents once with a symmetric algorithm;
[0079] 202. The encryption end performs secondary encryption on the primary encryption symmetric key with a symmetric algorithm;
[0080] 203. The encryption terminal transmits the encrypted bidding documents once to the decryption terminal;
[0081] 204. When the specified time is reached, the primary encryption symmetric ...
Embodiment 3
[0084] Embodiment 3: Asymmetric Algorithm + Symmetric Algorithm
[0085] In this embodiment, a combination of an asymmetric algorithm and a symmetric algorithm is adopted, wherein the primary encryption is an asymmetric algorithm, and the secondary encryption is a symmetric algorithm. The specific methods are as follows.
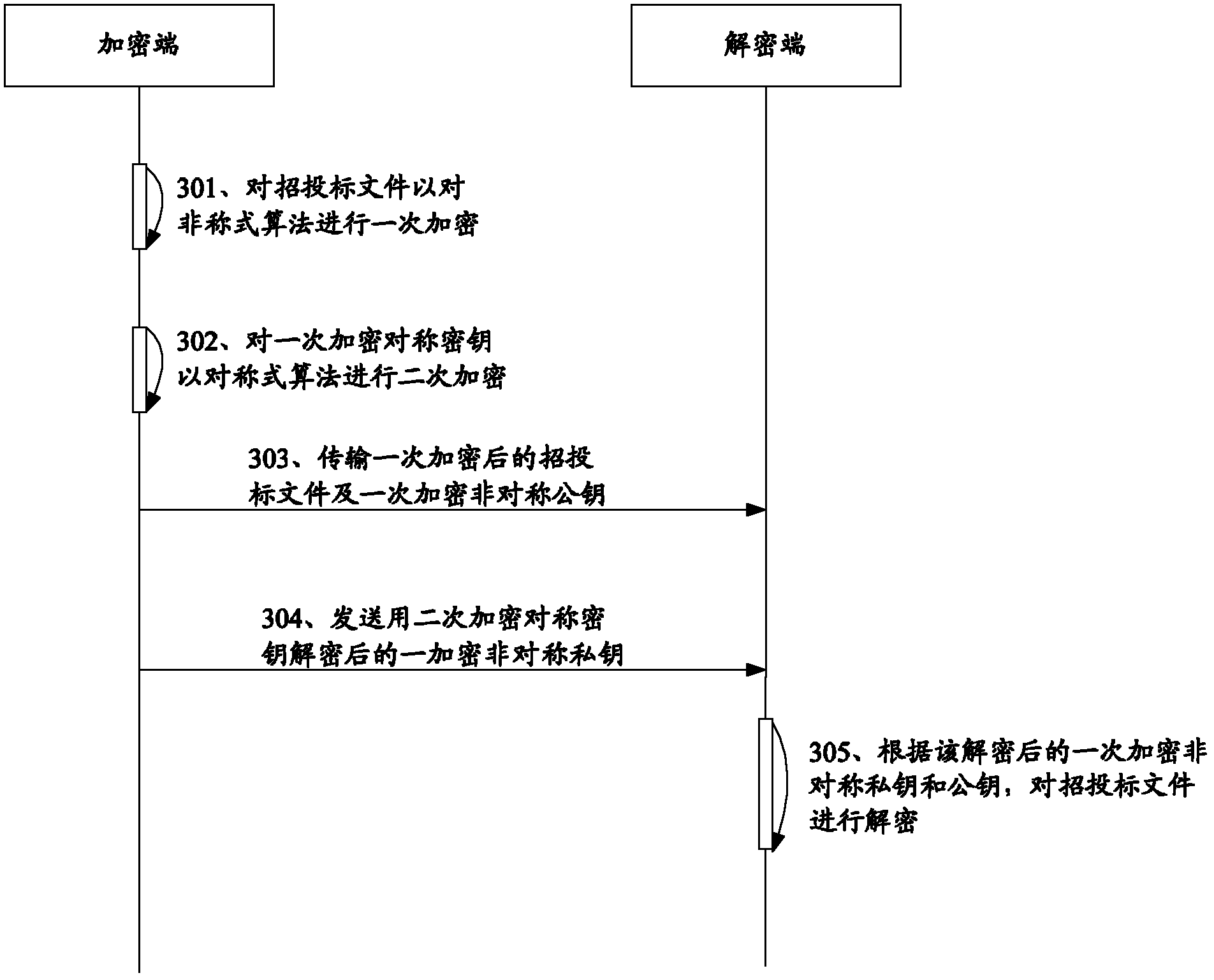
[0086] see image 3 , showing a sequence diagram of the method for encrypting and decrypting bidding documents based on remote authorization in Embodiment 3 of the present invention. This embodiment specifically comprises the following steps:
[0087] 301. The encryption end encrypts the bidding documents once with an asymmetric algorithm;
[0088] 302. The encryption end performs secondary encryption on the primary encrypted asymmetric private key with a symmetric algorithm;
[0089] 303. The encryption end transmits the once-encrypted bidding documents and the once-encrypted asymmetric public key to the decryption end;
[0090] 304. When the specified ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com